chap24-IOcks
itchat总结(转)

itchat总结(转)python实现微信接⼝sudo pip install itchatitchat.auto_login()这种⽅法将会通过微信扫描⼆维码登录,但是这种登录的⽅式确实短时间的登录,并不会保留登录的状态,也就是下次登录时还是需要扫描⼆维码,如果加上hotReload==True,那么就会保留登录的状态,⾄少在后⾯的⼏次登录过程中不会再次扫描⼆维码,该参数⽣成⼀个静态⽂件itchat.pkl⽤于存储登录状态这⾥主要使⽤的是灰调函数的⽅法,登录完成后的⽅法需要赋值在loginCallback 中退出后的⽅法,需要赋值在exitCallback 中.若不设置loginCallback 的值, 将会⾃动删除⼆维码图⽚并清空命令⾏显⽰.import itchat, timedef lc():print("Finash Login!")def ec():print("exit")itchat.auto_login(loginCallback=lc, exitCallback=ec)time.sleep()itchat.logout() #强制退出登录send(msg="Text Message", toUserName=None)参数:msg : ⽂本消息内容@fil@path_to_file : 发送⽂件@img@path_to_img : 发送图⽚@vid@path_to_video : 发送视频toUserName : 发送对象, 如果留空, 将发送给⾃⼰.返回值True or False实例代码# coding-utf-8import itchatitchat.auto_login()itchat.send("Hello World!")ithcat.send("@fil@%s" % '/tmp/test.text')ithcat.send("@img@%s" % '/tmp/test.png')ithcat.send("@vid@%s" % '/tmp/test.mkv')send_msg(msg='Text Message', toUserName=None),其中的的msg是要发送的⽂本,toUserName是发送对象, 如果留空, 将发送给⾃⼰,返回值为True或者False 实例代码import itchatitchat.auto_login()itchat.send_msg("hello world.")send_file(fileDir, toUserName=None)fileDir是⽂件路径, 当⽂件不存在时, 将打印⽆此⽂件的提醒,返回值为True或者False实例代码mport itchatitchat.auto_login()itchat.send_file("/tmp/test.txt")send_image(fileDir, toUserName=None)参数同上实例代码import itchatitchat.auto_login()itchat.send_img("/tmp/test.txt")send_video(fileDir, toUserName=None)参数同上实例代码import itchatitchat.auto_login()itchat.send_video("/tmp/test.txt")itchat将根据接受到的消息类型寻找对应的已注册的⽅法.如果⼀个消息类型没有对应的注册⽅法, 该消息将会被舍弃.在运⾏过程中也可以动态注册⽅法, 注册⽅式与结果不变.不带具体对象注册, 将注册为普通消息的回复⽅法.import itchatfrom itchat.content import *@itchat.msg_register(TEXT) #这⾥的TEXT表⽰如果有⼈发送⽂本消息,那么就会调⽤下⾯的⽅法def simple_reply(msg):#这个是向发送者发送消息itchat.send_msg('已经收到了⽂本消息,消息内容为%s'%msg['Text'],toUserName=msg['FromUserName'])return "T reveived: %s" % msg["Text"] #返回的给对⽅的消息,msg["Text"]表⽰消息的内容带对象参数注册, 对应消息对象将调⽤该⽅法,其中isFriendChat表⽰好友之间,isGroupChat表⽰群聊,isMapChat表⽰公众号import itchatfrom itchat.content import *@itchat.msg_register(TEXT, isFriendChat=True, isGroupChat=True,isMpChat=True)def text_reply(msg):er.send("%s : %s" % (mst.type, msg.text))消息类型向注册⽅法传⼊的msg包含微信返回的字典的所有内容.itchat增加Text, Type(也就是参数) 键值, ⽅便操作.itcaht.content 中包含所有的消息类型参数, 如下表参数l类型Text 键值TEXT⽂本⽂本内容(⽂字消息)MAP地图位置⽂本(位置分享)CARD名⽚推荐⼈字典(推荐⼈的名⽚)SHARING分享分享名称(分享的⾳乐或者⽂章等)PICTURE 下载⽅法图⽚/表情RECORDING语⾳下载⽅法ATTACHMENT附件下载⽅法VIDEO⼩视频下载⽅法FRIENDS好友邀请添加好友所需参数SYSTEM系统消息更新内容的⽤户或群聊的UserName组成的列表NOTE通知通知⽂本(消息撤回等)itchat的附件下载⽅法存储在msg的Text键中.发送的⽂件名(图⽚给出的默认⽂件名), 都存储在msg的FileName键中.下载⽅法, 接受⼀个可⽤的位置参数(包括⽂件名), 并将⽂件响应的存储.注意:下载的⽂件存储在指定的⽂件中,直接将路径与FileName连接即可,如msg["Text"]('/tmp/weichat'+msg['FileName'])@itchat.msg_register([PICTURE, RECORDING, ATTACHMENT, VIDEO])def download_files(msg):#msg.download(msg['FileName']) #这个同样是下载⽂件的⽅式msg['Text'](msg['FileName']) #下载⽂件#将下载的⽂件发送给发送者itchat.send('@%s@%s' % ('img' if msg['Type'] == 'Picture' else 'fil', msg["FileName"]), msg["FromUserName"])增加了三个键值,如下:isAt判断是否 @ 本号ActualNickName : 实际NickName(昵称)Content : 实际Content测试程序import itcahtfrom itchat.content import TEXT@itchat.msg_register(TEXT, isGroupChat=True)def text_reply(msg):if(msg.isAt): #判断是否有⼈@⾃⼰#如果有⼈@⾃⼰,就发⼀个消息告诉对⽅我已经收到了信息itchat.send_msg("我已经收到了来⾃{0}的消息,实际内容为{1}".format(msg['ActualNickName'],msg['Text']),toUserName=msg['FromUserName'])itchat.auto_login()itchat.run()注意:所有的消息内容都是可以⽤键值对来访问的,如msg["FromUserName]就是查看发送者,itchat.search_friends(userName=msg['FromUserName'])['NickName']查看的是当发送者昵称⼀般的消息都遵循以下的内容:{"FromUserName": "","ToUserName": "","Content": "","StatusNotifyUserName": "","ImgWidth": 0,"PlayLength": 0,"RecommendInfo": {},"StatusNotifyCode": 0,"NewMsgId": "","Status": 0,"VoiceLength": 0,"ForwardFlag": 0,"AppMsgType": 0,"Ticket": "","AppInfo": {},"Url": "","ImgStatus": 0,"MsgType": 0,"ImgHeight": 0,"MediaId": "","MsgId": "","FileName": "","HasProductId": 0,"FileSize": "","CreateTime": 0,"SubMsgType": 0}MsgType: 51FromUserName: ⾃⼰IDToUserName: ⾃⼰IDStatusNotifyUserName: 最近联系的联系⼈IDContent:<msg><op id='4'><username># 最近联系的联系⼈filehelper,xxx@chatroom,wxid_xxx,xxx,...</username><unreadchatlist><chat><username># 朋友圈MomentsUnreadMsgStatus</username><lastreadtime>1454502365</lastreadtime></chat></unreadchatlist><unreadfunctionlist># 未读的功能账号消息,群发助⼿,漂流瓶等</unreadfunctionlist></op></msg>MsgType: 1FromUserName: 发送⽅IDToUserName: 接收⽅IDContent: 消息内容itchat 增加了 Text 键, 键值为下载该图⽚的⽅法.MsgType: 3FromUserName: 发送⽅IDToUserName: 接收⽅IDMsgId: ⽤于获取图⽚,⽤于表⽰每⼀条消息Content:<msg><img length="6503" hdlength="0" /><commenturl></commenturl></msg>拓展:如果想要得到Content中的具体内容可以使⽤正则表达式匹配出来*itchat增加了Text键, 键值为下载该视频的⽅法.*MsgType: 62FromUserName: 发送⽅IDToUserName: 接收⽅IDMsgId: ⽤于获取⼩视频Content:<msg><img length="6503" hdlength="0" /><commenturl></commenturl></msg>itchat 增加了 Text 键, 键值为该地点的⽂本形式.MsgType: 1FromUserName: 发送⽅IDToUserName: 接收⽅IDContent: /cgi-bin/redirectforward?args=xxxOriContent:<?xml version="1.0"?><msg><location x="34.195278" y="117.177803" scale="16" label="江苏省徐州市铜⼭区新区海河路" maptype="0" poiname="江苏师范⼤学⼤学⽣公寓园区" /></msg>itchat 增加了Text 键, 键值为该调⽤ add_friend 需要的属性.MsgType: 42FromUserName: 发送⽅IDToUserName: 接收⽅IDContent:<?xml version="1.0"?><msg bigheadimgurl="" smallheadimgurl="" username="" nickname="" shortpy="" alias="" imagestatus="3" scene="17" province="" city="" sign="" sex="1" certflag="0" certinfo="" brandIconUrl="" brandHomeUrl="" brandSubscriptConfigUr RecommendInfo:{"UserName": "xxx", # ID,这⾥的是昵称"Province": "xxx","City": "xxx","Scene": 17,"QQNum": 0,"Content": "","Alias": "xxx", # 微信号"OpCode": 0,"Signature": "","Ticket": "","Sex": 0, # 1:男, 2:⼥"NickName": "xxx", # 昵称"AttrStatus": 4293221,"VerifyFlag": 0}下⾯是添加好友的测试代码@itchat.msg_register(itchat.content.CARD,isFriendChat=True)def simply(msg):print msg['Text']print msg['Content']itchat.add_friend(userName=msg['Text']['UserName']) #添加推荐的好友print msg['RecommendInfo']print msg['RecommendInfo']['UserName']*itchat增加了Text键,键值为下载该语⾳⽂件的⽅法,下载下来的是MP3的格式MsgType: 34FromUserName: 发送⽅IDToUserName: 接收⽅IDMsgId: ⽤于获取语⾳Content:<msg><voicemsg endflag="1" cancelflag="0" forwardflag="0" voiceformat="4" voicelength="1580" length="2026" bufid="216825389722501519" clientmsgid="49efec63a9774a65a932a4e5fcd4e923filehelper174_1454602489" fromusername=</msg>下载⽅法:msg['Text'](msg['FileName'])itchat添加了Text键,键值为下载该图⽚表情的⽅法。
ChatClient

// ChatClient.cpp : 定义应用程序的入口点。
//#include "stdafx.h"#include "ChatClient.h"#include <WinSock2.h>#include <time.h>#pragma comment(lib, "WS2_32")//用于处理“无法解析的外部符号__imp__WSAStartup@8”#define MAX_LOADSTRING 100// 全局变量:HINSTANCE hInst; // 当前实例TCHAR szTitle[MAX_LOADSTRING]; // 标题栏文本TCHAR szWindowClass[MAX_LOADSTRING]; // 主窗口类名// 此代码模块中包含的函数的前向声明:ATOM MyRegisterClass(HINSTANCE hInstance);BOOL InitInstance(HINSTANCE, int);LRESULT CALLBACK WndProc(HWND, UINT, WPARAM, LPARAM);INT_PTR CALLBACK About(HWND, UINT, WPARAM, LPARAM);int APIENTRY _tWinMain(HINSTANCE hInstance,HINSTANCE hPrevInstance,LPTSTR lpCmdLine,int nCmdShow){UNREFERENCED_PARAMETER(hPrevInstance);UNREFERENCED_PARAMETER(lpCmdLine);// TODO: 在此放置代码。
MSG msg;HACCEL hAccelTable;// 初始化全局字符串LoadString(hInstance, IDS_APP_TITLE, szTitle, MAX_LOADSTRING);LoadString(hInstance, IDC_CHATCLIENT, szWindowClass, MAX_LOADSTRING);MyRegisterClass(hInstance);// 执行应用程序初始化:if (!InitInstance (hInstance, nCmdShow)){return FALSE;}hAccelTable = LoadAccelerators(hInstance, MAKEINTRESOURCE(IDC_CHATCLIENT));// 主消息循环:while (GetMessage(&msg, NULL, 0, 0)){if (!TranslateAccelerator(msg.hwnd, hAccelTable, &msg)){TranslateMessage(&msg);DispatchMessage(&msg);}}return (int) msg.wParam;}//// 函数: MyRegisterClass()//// 目的: 注册窗口类。
vxWorks PAL库函数

ZebOS vxWorks PAL库函数PAL修改列表不需修改的函数条件:未被调用且自身为空函数;IPv6相关;MPLS相关;VRF相关;VRRP相关;VxWorks 系统调用pal_auth.c全部pal_daemon.c全部pal_kernel.cpal_kernel_fib_createpal_kernel_fib_deletepal_kernel_if_bind_vrfpal_kernel_if_unbind_vrfpal_kernel_virtual_ipv4_addpal_kernel_virtual_ipv4_deletepal_kernel_virtual_mac_addpal_kernel_virtual_mac_deletepal_kernel_vrrp_startpal_kernel_vrrp_stoppal_kernel_gratuitous_arp_sendpal_socket.cpal_sock_get_ipv6_checksumpal_sock_get_ipv6_hoplimitpal_sock_get_ipv6_multicast_hopspal_sock_get_ipv6_multicast_looppal_sock_get_ipv6_pktinfopal_sock_get_ipv6_unicast_hopspal_sock_set_ipv6_checksumpal_sock_set_ipv6_hoplimitpal_sock_set_ipv6_icmp_filterpal_sock_set_ipv6_multicast_hopspal_sock_set_ipv6_multicast_joinpal_sock_set_ipv6_multicast_leavepal_sock_set_ipv6_multicast_looppal_sock_set_ipv6_pktinfopal_sock_set_ipv6_unicast_hopspal_sock_set_ipv4_mrt_add_mfcpal_sock_set_ipv4_mrt_add_vifpal_sock_set_ipv4_mrt_assertpal_sock_set_ipv4_mrt_del_mfcpal_sock_set_ipv4_mrt_del_vifpal_sock_set_ipv4_mrt_donepal_sock_set_ipv4_mrt_igmp_donepal_sock_set_ipv4_mrt_igmp_initpal_sock_set_ipv4_mrt_initpal_sock_set_ipv4_mrt_spt_bitpal_sock_set_ipv4_pimpal_sock_raw.cpal_in6_recv_packetpal_in6_send_packetpal_sock_in6_cmsg_finishpal_sock_in6_cmsg_hoplimit_getpal_sock_in6_cmsg_hoplimit_setpal_sock_in6_cmsg_initpal_sock_in6_cmsg_len_getpal_sock_in6_cmsg_lookuppal_sock_in6_cmsg_pktinfo_getpal_sock_in6_cmsg_pktinfo_setpal_sock_set_icmp6_checksum pal_stdlib.cpal_cryptpal_stdlib_startpal_stdlib_stoppal_unamepal_log.c全部pal_mcast.c全部pal_memory.c全部pal_mpls_client.c全部pal_mpls_stats.c全部pal_semaphore.c全部pal_string.c全部pal_time.c全部需要或可能需要被修改:(共计130 个,17个c文件)plat_kernel_fwd_ctrl.c(全部5个)该文件和linux PAL中pal_kernel_ipv4_forwardingpal_kernel_ipv4_forwarding_getpal_kernel_ipv4_forwarding_offpal_kernel_ipv4_forwarding_onpal_kernel_ipv4_forwarding_setplat_kernel_if.c(全部3个)pal_if_stat_updatepal_kernel_if_scanpal_kernel_if_updateplat_kernel_if_api.c(全部19个)pal_kernel_if_addr_getpal_kernel_if_flags_getpal_kernel_if_flags_setpal_kernel_if_flags_unsetpal_kernel_if_get_bwpal_kernel_if_get_hwaddrpal_kernel_if_get_indexpal_kernel_if_get_metricpal_kernel_if_get_mtupal_kernel_if_ipv4_address_addpal_kernel_if_ipv4_address_deletepal_kernel_if_ipv4_address_delete_allpal_kernel_if_ipv4_address_secondary_addpal_kernel_if_ipv4_address_secondary_deletepal_kernel_if_ipv4_address_updatepal_kernel_if_listpal_kernel_if_set_metricpal_kernel_if_set_mtusignedTounsignedLongplat_kernel_rte_mgmt.c(全部4个),或保持接口不变,只修改pal_kernel_rtm_ipv4 pal_kernel_ipv4_addpal_kernel_ipv4_delpal_kernel_ipv4_updatepal_kernel_rtm_ipv4plat_kernel_rte_scan.c(3个)pal_ipv4_route_readpal_kernel_route_scanpal_populate_ipv4_route其中可以只修改pal_populate_ipv4_route plat_kernel_rte_socket.c(17个)IFAMADDRGETIFAMMASKGETpal_af_checkpal_ifam_readpal_ifam_read_mesgpal_ifm_readpal_kernel_readpal_routing_socketpal_rtmsg_debugpal_rtm_flag_dumppal_rtm_readpal_rtm_read_mesgROUNDUPRTMADDRGETRTMMASKGETSOCKADDRSETWRAPUPpal_if_types.cpal_if_typepal_igmp.c(2个)pal_igmp_type_strpal_handle_igmp_messagepal_inet.c(5个)pal_inet_ntoapal_inet_atonpal_inet_ntoppal_inet_ptonpal_inet_pton4pal_kernel.c(2个)pal_kernel_startpal_kernel_stoppal_kernel_arp.c(2个)pal_kernel_l2_ipv4_resolvepal_kernel_L2_ipv4_resolvepal_socket.c(44个)pal_fcntlpal_getservbynamepal_sock_checkpal_sock_get_bindtodevicepal_sock_get_bindtofibpal_sock_get_broadcastpal_sock_get_ipv4_multicast_hopspal_sock_get_ipv4_multicast_looppal_sock_get_ipv4_pimpal_sock_get_ipv4_tos_precpal_sock_get_ipv4_unicast_hopspal_sock_get_ip_hdr_inclpal_sock_get_ip_recvifpal_sock_get_nonblockingpal_sock_get_recvbufpal_sock_get_reuseaddrpal_sock_get_reuseportpal_sock_get_sendbufpal_sock_get_soerrpal_sock_get_tcp_nodelaypal_sock_set_bindtodevicepal_sock_set_bindtofibpal_sock_set_broadcastpal_sock_set_ipv4_dstaddrpal_sock_set_ipv4_tos_precpal_sock_set_ipv4_unicast_hopspal_sock_set_ip_hdr_inclpal_sock_set_ip_recvifpal_sock_set_ipv4_multicast_hopspal_sock_set_ipv4_multicast_ifpal_sock_set_ipv4_multicast_joinpal_sock_set_ipv4_multicast_leavepal_sock_set_ipv4_multicast_looppal_sock_set_ll_multicast_joinpal_sock_set_ll_multicast_leavepal_sock_set_nonblockingpal_sock_set_recvbufpal_sock_set_reuseaddrpal_sock_set_reuseportpal_sock_set_router_alertpal_sock_set_sendbufpal_sock_set_tcp_nodelaypal_sock_startpal_sock_stoppal_sock_ll.c(10个)pal_sock_ll_cisco_hdlcpal_sock_ll_defpal_sock_ll_def_closepal_sock_ll_def_phyaddr_getpal_sock_ll_def_phyaddr_setpal_sock_ll_def_promisc_disablepal_sock_ll_def_promisc_enablepal_sock_ll_def_recvmsgpal_sock_ll_def_sendmsgpal_sock_ll_ethernetpal_sock_raw.c(9个)pal_in4_ip_hdr_len_getpal_in4_ip_hdr_len_setpal_in4_ip_hdr_tos_setpal_in4_ip_packet_len_getpal_in4_ip_packet_len_setpal_in4_packet_peekpal_in4_recv_packetpal_in4_recv_packet_lenpal_in4_send_packetpal_sock_udp.c(1个)pal_in4_udp_recv_packetpal_stdlib.c(3个)pal_in4_header_lengthpal_getcwdpal_system_errpal_utils.c(1个)pal_sin_masklenPAL函数调用关系及功能说明pal_auth.c : 802.1x控制请求vxWorks中没有实现802.1x,因此这部分API均为空函数,均未被ZebOS中任何函数调用。
qstringlist readlist; -回复

qstringlist readlist; -回复如何读取QStringList。
QStringList是Qt中的一个类,用于存储字符串列表。
它提供了一系列方法和函数,用于操作和访问列表中的字符串。
在本文中,我们将介绍如何使用QStringList来读取字符串列表。
首先,我们需要创建一个QStringList对象,并向其添加一些字符串。
可以使用add方法来向列表中添加字符串。
例如,我们可以有以下代码:cppQStringList readlist;readlist << "字符串1" << "字符串2" << "字符串3";在上述代码中,我们创建了一个名为readlist的QStringList对象,并使用左移运算符(<<)向其添加了三个字符串。
接下来,我们可以使用下标运算符([])来访问列表中的字符串。
例如,我们可以使用以下代码来访问列表中的第一个字符串:cppQString firstString = readlist[0];此处,我们将第一个字符串赋值给了名为firstString的QString对象。
除了使用下标运算符,我们还可以使用at方法来访问指定位置的字符串。
例如,我们可以使用以下代码来访问第二个字符串:cppQString secondString = readlist.at(1);此处,我们将第二个字符串赋值给了名为secondString的QString对象。
如果我们想获取列表的大小(即列表中包含的字符串个数),可以使用count方法。
例如,我们可以使用以下代码获取列表的大小:cppint size = readlist.count();此处,我们将列表的大小赋值给了一个名为size的整型变量。
另外,如果我们想遍历整个列表并访问每个字符串,可以使用foreach循环。
例如,我们可以使用以下代码来遍历列表:cppforeach(QString str, readlist) {在此处访问每个字符串}在上述代码中,我们创建了一个名为str的QString对象,用于依次存储列表中的每个字符串。
ASC88xx_Kilrogg_Reference_Application_UG

User Guide
Rev 3.0 — 24 Aug 2011
5 of 61
NXP Semiconductors
ASC88xx_Kilrogg_Reference_Application_UG
2.3 Hardware installation
Refer Figure 6 to check the ports available on the back-panel of RDK.
User Guide
Rev 3.0 — 24 Aug 2011
2 of 61
NXP Semiconductors
ASC88xx_Kilrogg_Reference_Application_UG
1. Overview
1.1 Introduction
This user manual describes the execution of reference Kilrogg application on ASC88xx (where xx=48/49/50/51) target. The purpose of Kilrogg is to demonstrate capability of ASC88xx SoC encoder and to provide a multi-channel and multi-stream reference design of feature products of IP and Video server box (VS) at professional security and surveillance market. This user manual will explain • Running of Pre-build application • Generating of reference application image • Downloading image to Target
《Python程序设计》实验指导书

Infoprint 250 導入と計画の手引き 第 7 章ホスト
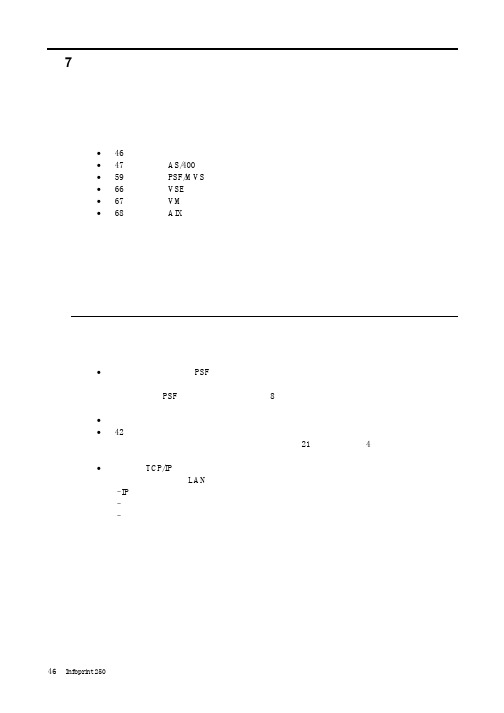
SUBNETMASK
255.255.255.128
Type of service...............: TOS
*NORMAL
Maximum transmission unit.....: MTU
*LIND
Autostart.....................:
AUTOSTART
*YES
: xx.xxx.xxx.xxx
: xx.xxx.xxx.xxx
*
(
)
IEEE802.3
60 1500
: xxxx
48 Infoprint 250
31. AS/400
IP
MTU
1
1
IPDS TCP
CRTPSFCFG (V3R2)
WRKAFP2 (V3R1 & V3R6)
RMTLOCNAME RMTSYS
MODEL
0
Advanced function printing............:
AFP
*YES
AFP attachment........................:
AFPATTACH
*APPC
Online at IPL.........................:
ONLINE
FORMFEED
*CONT
Separator drawer......................:
SEPDRAWER
*FILE
Separator program.....................:
SEPPGM
*NONE
Library.............................:
DKK-1在宫颈癌中的研究进展

于这一转化是典型的wn∥p—catenin信号传导途 径激活的特点之一,因此认为Wn∥B—catenin—
TcF信号途径激活是官颈癌发生的重要环节之一。
20蛐d
DKKl
a陀咖8cripti∞al
beta—cateIlin明d
EMBO
FGF一20 is implicgted in
c锄cer曲d development[J].
万方数据
验中发现由人乳头瘤病毒(HPv)导致的永生人角 质化细胞是由SV40small—t(smt)抗原转化的。由
lon
cancer[J].0rIcoge舱,2005,24(6):1098—1103 [6]Ck曲问∞MN,SchwaItz
DR,VoIlic8 A,et 81.FGF一 taIget8 0f
‰men受体间接与LRP受体结合,从而形成三聚
体复合物,降低wnt蛋白向细胞内传导信号,阻断 经典wnt—B—c砒enin—T淋巴细胞臭氧层性转录 因子(TCF)传导途径,以及wnt—c—Jun氨基末端 激酶(JNK)与细胞平面极化(PCP)传导途径。 脊椎动物的DKK蛋白有DKK—l、DKK一2、 DⅪ(一3和DKK一4四种形式,它们有较高同源性,
3
Winhs等啪1指出,DKK一1在肝母细胞瘤
(HBs)和wilms瘤中表达升高可能与wnt信号失控 有关。高水平的DKK一1可作为HBs和wilms瘤的 一个标记。在DKK一1表达降低或者缺失的肿瘤, 外源的DKK一1表达或许可以抑制肿瘤增殖。 suraweera等旧u报道没有发现人结肠癌的DKK一1
J,2005,24(1):73—84
P6rez—Pl鹪encia等【271通过对感染HPVl6的宫颈癌
组织进行免疫组化分析,也发现其中存在B—cate・ nin和TCF的异常表达,认为异常激活经典的Wnt 通路在HPV阳性患者宫颈癌发生中具有促进作用。 以上研究证实,DKK—l具有明显抑制宫颈癌
ZDO——Z-Stack中的Zigbee设备对象

一个(yīɡè)端点对应一个任务,每一个任务都有唯一的任务号及任务处理函数,ZDO_RegisterForZDOMsg( )在相应(xiāngyīng)的任务中注册事件,并且每一个事件只能被成功注册一次,每一个任务也只能注册一次事件,因为(yīn wèi):ZStatus_t ZDO_RegisterForZDOMsg( uint8 taskID, uint16 clusterID ){ZDO_MsgCB_t *pList;ZDO_MsgCB_t *pLast;ZDO_MsgCB_t *pNew;// Look for duplicatepList = pLast = zdoMsgCBs;//zdoMsgCBs此指针变量(biànliàng)始终指向注册事件链表的头while ( pList ){if ( pList->taskID == taskID && pList->clusterID == clusterID )return ( ZSuccess );//若之这个任务(rèn wu)已注册了事件(本事件或其他事件),那pLast = pList; //么此次注册将不会把注册信息加入链表,就相当于没有注册pList = (ZDO_MsgCB_t *)pList->next;}// Add to the list若没有被注册过(之前链表里没有),则将其添加到链表的末尾(注册)pNew = (ZDO_MsgCB_t *)osal_mem_alloc( sizeof ( ZDO_MsgCB_t ) );if ( pNew ){pNew->taskID = taskID;pNew->clusterID = clusterID;pNew->next = NULL;if ( zdoMsgCBs ){pLast->next = pNew;}elsezdoMsgCBs = pNew;return ( ZSuccess );}elsereturn ( ZMemError );}/***********************************************************遗留问题:链表中的事件,在何时何地,什么情况下被销毁呢?************************************************************/接着说,那么注册(zhùcè)了以后它有什么用?怎么用呢?先看Z-Stack API中对此函数(hánshù)的解释:Call this function request an OTA message. A copy of the message will be send to a task in an OSAL message .The task recevice the OTA message can either prase the message themselves or call a ZDO prase function to prase the message.Only response messages have a ZDO prase function.After registering for a message ,and the message(OTA) is receviced,the message is send to the application/task as a ZDO_CB_MSG(OSAL Msg).大意(dàyì):调用这个函数用来请求一个无线消息,这个消息的备份(bèi fèn)将被作为一个系统消息送给一个任务。
VIAVI T-BERD MTS-5800产品说明书
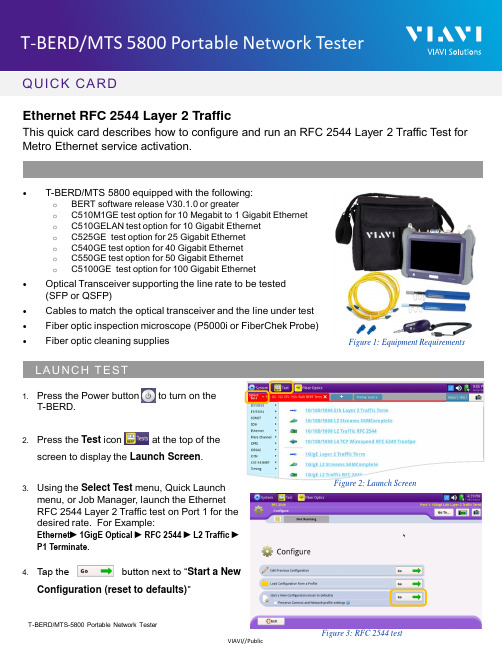
QUICK CARDEthernet RFC 2544 Layer 2 TrafficThis quick card describes how to configure and run an RFC 2544 Layer 2 Traffic Test for Metro Ethernet service activation.•T-BERD/MTS 5800 equipped with the following:o BERT software release V30.1.0 or greatero C510M1GE test option for 10 Megabit to 1 Gigabit Etherneto C510GELAN test option for 10 Gigabit Etherneto C525GE test option for 25 Gigabit Etherneto C540GE test option for 40 Gigabit Etherneto C550GE test option for 50 Gigabit Etherneto C5100GE test option for 100 Gigabit Ethernet•Optical Transceiver supporting the line rate to be tested(SFP or QSFP)•Cables to match the optical transceiver and the line under test•Fiber optic inspection microscope (P5000i or FiberChek Probe)•Fiber optic cleaning supplies Figure 1: Equipment Requirements1.Press the Power button to turn on theT-BERD.2.Press the Test icon at the top of thescreen to display the Launch Screen.ing the Select Test menu, Quick Launchmenu, or Job Manager, launch the EthernetRFC 2544 Layer 2 Traffic test on Port 1 for the desired rate. For Example:Ethernet►1GigE Optical ►RFC 2544 ►L2 Traffic ►P1 Terminate.4.Tap the button next to “Start a NewConfiguration (reset to defaults)”Figure 2: Launch ScreenQUICK CARD►The following Information is needed to configure the test:•VLAN ID, if VLAN tagging is used.•Maximum Transmission Unit (MTU), if Jumbo Frames are used.•Committed Information Rate (CIR)•Pass/Fail Threshold for Throughput, Frame Loss, Latency and Jitter1.Tap the button to display theL2 Network Settings screen.2.If you are testing a VLAN, setEncapsulation to VLAN and enter yourVLAN ID.3.Tap the button twice to displaythe Select Tests screen.4.Select the Throughput, Latency, FrameLoss, and Packet Jitter tests.5.Tap the button to display theUtilization screen.6.Set Max Bandwidth to the CommittedInformation Rate (CIR).7.Tap the button to display theFrame Lengths screen.Figure 4: Work OrderFigure 6: Select TestsFigure 5: L2 Network SettingsQUICK CARD8.Select the 1st, 4th, and 8th Frame Lengths.9.If the MTU is greater than 1518 (1522 with VLAN tagging), also enter and select the frame length of the MTU.10.Deselect (uncheck) all other frame lengths.11.Tap the button four times to display the Test Thresholds screen.12.Check all boxes for which a Pass/Fail Threshold is known. Enter the Threshold for each selection.13.Tap the button 3 times to display theRun J-QuickCheck screen.Figure 8: Frame LengthsFigure 9: Test ThresholdsFigure 10: J-QuickCheckQUICK CARD►For Optical Interfaces:e the VIAVI P5000i or FiberChek Probemicroscope to inspect both sides of everyconnection being used (SFP, attenuators,patch cables, bulkheads)o Focus the fiber on the screen.o If it appears dirty, clean the fiber end-face and re-inspect.o If it appears clean, run the inspection test.o If it fails, clean the fiber and re-runinspection test. Repeat until it passes.2.Insert desired Optical Transceiver into thePort 1 SFP or QSFP slot on the top of theT-BERD.3.If necessary, insert optical attenuators intothe SFP TX and/or RX ports.4.Connect the SFP to the port under testusing a jumper cable compatible with theline under test.►For Copper 10/100/1000BASE-T interfaces: Connect the 10/100/1000 RJ-45 jack tothe port under test using CAT 5E or bettercable.►Verify that Local Port status UP and Full Duplex (FD)►Tap the button.►Verify that the Remote Loop is recognized, and that Measured Throughput is greater than or equal to the Committed Information Rate.►Tap the button to display the Run RFC 2544Tests screen. Figure 12: Local Port statusFigure 11: Inspect Before You Connect Figure 13: Run J-QuickCheckQUICK CARD© 2022 VIAVI Solutions, Inc,Product specifications and descriptions in this Contact Us+1 844 GO VIAVI(+1 844 468-4284)1.Tap the button three times to display the Report screen.2.Tap .3.Tap buttons three times toclose the report and exit the RFC 2544 test.1.Tap the button.2.Wait for the test to complete and verify that all tests pass or complete as indicated by agreen or blue checkmark.E RE P ORTFigure 14: Run RFC 2544 TestsFigure 15: Create ReportFigure 16: Exit。
linux socket状态 函数 -回复

linux socket状态函数-回复Linux socket状态函数是指用于获取和设置socket连接状态信息的特定函数集合。
这些函数非常重要,因为它们允许开发人员监视和控制网络连接的各个方面,从而确保网络应用程序的可靠性和稳定性。
本文将详细介绍Linux socket状态函数的使用和原理,并提供一些常见的实例和应用场景。
一、什么是socket状态函数Socket状态函数是一组用于获取和设置socket连接状态的API函数。
它们允许开发人员查询和修改socket连接的各个方面,包括连接的状态、缓冲区状态、传输层协议状态等。
通过使用这些函数,开发人员能够更好地监控和管理其网络应用程序,以确保其可靠性和稳定性。
在Linux系统中,socket状态函数主要包括以下几个关键函数:1. getsockopt:用于获取socket选项的值,如缓冲区大小、超时值等。
2. setsockopt:用于设置socket选项的值,如缓冲区大小、超时值等。
3. ioctl:用于控制socket的属性和状态,如非阻塞I/O、接收和发送缓冲区大小等。
4. poll/epoll:用于监视和等待多个socket文件描述符的状态变化,以便及时处理网络事件。
二、getsockopt函数详解getsockopt函数用于获取socket选项的值。
它的原型如下:cint getsockopt(int sockfd, int level, int optname, void *optval, socklen_t *optlen);其中,sockfd是socket文件描述符,level表示选项所属的协议层,如SOL_SOCKET表示socket级选项,optname表示具体的选项名称,optval是用于存放选项值的缓冲区,optlen表示缓冲区的长度。
3.1)常见使用场景getsockopt函数广泛应用于网络编程中,主要用于获取和查询socket的各个状态和属性。
腾讯云 IoT MQTT AT 指令说明书

4.4
模组配合腾讯云 IOT 平台实现 MCU 测 OTA 功能流程图 ............................23
5 URC,模组主动上报 MCU 消息.............................................................................................24
3.1
AT+TCMQTTCONN(配置 MQTT 连接参数) .................................................14
3.2
AT+TCMQTTDISCONN(断开 MQTT 连接)...................................................15
8.1
密钥认证方式连接 TENCENT MQTT 服务器...............................................31
8.2
证书认证方式连接 TENCENT MQTT 服务器...............................................31
7.4
网关子设备命令相关错误类型 ...................................................................... 30
8 应用说明.................................................................................................................................31
(完整版)计算机网络英文题库(附答案)chapter3

Chapter 3 Transport Layer1. A transport-layer protocol provides for logical communication between ____.A Application processesB HostsC RoutersD End systems2. Transport-layer protocols run in ____.A ServersB ClientsC RoutersD End systems3. In transport layer, the send side breaks application messages into ____, passes to network layer.A FramesB SegmentsC Data-gramsD bit streams4. Services provided by transport layer include ____.A HTTP and FTPB TCP and IPC TCP and UDPD SMTP5. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers6. These two minimal transport-layer services----____ and ____----are the only two services that UDP provides!A process-to-process data delivery, error checkingB congestion control, reliable data transferC flow control, congestion controlD In-order data transfer, error checking7. Port number’s scop e is ____ to ____.A 0, 1023B 0, 65535C 0, 127D 0,2558. The port numbers ranging from ____to ____ are called well-known port number and are restricted.A 0, 1023B 0, 65535C 0, 127D 0,2559. UDP socket identified by two components, they are ____.A source IP addresses and source port numbersB source IP addresses and destination IP addressesC destination IP address and destination port numbersD destination port numbers and source port numbers10. TCP socket identified by a (an) ____.A 1-tupleB 2-tupleC 3-tupleD 4-tuple11. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP12. Reliable data transfer protocol over a perfectly reliable channel is____.A rdt1.0B rdt2.0C rdt3.0D rdt2.113. Reliable data transfer protocol over a channel with bit errors and packet losses is _ ___.A rdt1.0B rdt2.0C rdt3.0D rdt2.114. Which of the following about reliable data transfer over a channel with bit errors i s not correct?A RDT2.0: assuming ACK and NAK will not be corruptedB RDT2.1: assuming ACK and NAK can be corruptedC RDT2.2: only use ACK-sD RDT2.2: use both ACK-s and NAK-s15. Which of the following protocols is not pipelining protocols?A TCPB rdt3.0C GO-BACK-ND selective repeat16. Which of the following is not correct about GBN protocol?A Only using ACK-sB Using cumulative ACK-sC Receiver discards all out-of-order packetsD It is not pipelined protocol17. Which of the following is not correct about SR protocol?A receiver individually acknowledges all correctly received packetsB sender only resends packets for which ACK not receivedC It limits sequence number of sent but un-ACK-ed packetsD It is not a pipelined protocol18. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection19. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection20. The FIN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection21.How does TCP sender perceive congestion?A Through a timeout eventB Through a receiving duplicate ACK-s eventC Both A and BD Either A or B22. Extending host-to-host delivery to process-to-process delivery is called transport-layer ____ and .A multiplexing and de-multiplexingB storing and forwardingC forwarding and filteringD switching and routing23. UDP is a ____ service while TCP is a connection-oriented service.A ConnectionlessB ReliableC Connection-orientedD In-order24. The UDP header has only four fields, they are____.A Source port number, destination port number, length and checksumB Source port number, destination port number, source IP and destination IPC source IP, destination IP, source MAC address and destination MAC addressD source IP, destination IP, sequence number and ACK sequence number25. There are two 16-bit integers: 1110 0110 0110 0110, 1101 0101 0101 0101. Their checksum is____.A 0100010001000011B 1011101110111100C 1111111111111111D 100000000000000026.The maximum amount of data that can be grabbed and placed in a segment is limited by the____.A Maximum segment size (MSS)B MTUC ChecksumD Sequence number27.The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host----the so-called____.A Maximum transmission unit (MTU)B MSSC ChecksumD Sequence number28. A File size of 500,000bytes, MSS equals 1000bytes. When we want to transmit this file with TCP, the sequence number of the first segment is 0, and the sequence number of the second segment is ____.A 1000B 999C 1001D 50000029.Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide____.A Cumulative acknowledgementsB Selective acknowledgementsC 3 duplicate ACKsD positive ACKs30. Provided α=0.125, current value of Estimated-RTT is 0.4s, Sample-RTT is 0.8s, then the new value of Estimated-RTT is ____s.A 0.45B 0.6C 0.7D 0.831.Provided RcvBuffer=20,LastByteRcvd=20,LastByteRead=15, thenRcvWindow=____.A 14B 15C 16D 1032. TCP service does not provide____.A Reliable data transferB Flow controlC Delay guaranteeD Congestion control33. There are two states in TCP congestion control, which are ____.A slow start and congestion avoidanceB safe start and congestion avoidanceC slow start and congestion abandonD safe start and congestion abandon34. The transport-layer protocol provides logical communication between ____, and the network-layer protocol provides logical communication ____.A hosts, processesB processes, hostsC threads, processesD processes, threads35. To implement the multicast services the Internet employs the ____ protocol.A FTPB TCPC IGMPD UDP36. If an application developer chooses ____ protocol, then the application process is almost directly talking with IP.A HTTPB RIPC CSMA/CDD UDP37. ____ maintains connection-state in the end systems. This connection state includes receive and send buffers, congestion-control parameters, and sequence and acknowledgment number parameters.A UDPB TCPC DNSD HTTP38. The host that initiates the session in the Internet is labeled as ____.A serverB user agentC clientD router39. With TCP there is no _____ between sending and receiving transport-layer entities.A flow controlB handshakingC. congestion control D VC setup40. The Internet’s ____service helps prevent the Internet from entering a state of gridlock.A datagramB congestion controlC sliding windowD timeout event41. Connection setup at the transport layer involves ____.A serverB only the two end systemsC clientD router42. A ____layer protocol provides for logical communication between applications.A transportB applicationC networkingD MAC43. In static congestion window, if it satisfies W*S/R > RTT + S/R, the Latency is ____.A W*S/R – ( RTT+ S/R)B 2RTT + O/RC 2RTT + O/R + (k-1)[W* S/R- (RTT + S/R)]D 2RTT + S/R44. The receive side of transport layer reassembles segments into messages, passes to ____layer.A ApplicationB NetworkingC PhysicalD MAC45. In the following four options, which one is correct?A The variations in the SampleRTT are smoothed out in the computation of the EstimatedRTTB The timeout should be less than the connection’s RTTC Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≥1 secD Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≤1 sec46. The port number used by HTTP is ____.A 80B 25C 110D 5347. The port number used by SMTP is ____.A 80B 25C 110D 5348. The port number used by pop3 is ____.A 80B 25C 110D 5349. The port number used by DNS is ____.A 80B 25C 110D 5350. The port number used by FTP is ____.A 20 and 21B 20C 21D 5351. A UDP socket identified by a ____ tuple(s).A 2B 4C 1D 352. A TCP socket identified by a ____ tuple(s).A 2B 4C 1D 353. A TCP socket does not include____.A Source MAC addressB Source port numberC Destination IP addressD Destination port number54. Which of following about UDP is not correct.A It is a reliable data transfer protocolB It is connectionlessC no handshaking between UDP sender, receiverD it is a best effort service protocol55. DNS uses ____ service.A TCPB UDPC Both TCP and UDPD None of above56. Which of following about UDP is correct?A Finer application-level control over what data is sent, and whenB No connection establishment (which can add delay), so no delay for establish a connectionC No connection state (so, UDP can typically support many active clients)D Large packet header overhead (16-B)57. Streaming media uses a ____ service normally.A TCPB UDPC Both TCP and UDPD None of above58. The UDP header has only ____ fields.A 2B 4C 1D 359. Which of the following does not included in UDP header.A Source port numberB Destination port numberC ChecksumD Sequence number60. Which of the following is not a pipelining protocol.A Rdt1.0B Go-Back-NC Selective repeatD TCP61. In the following four descriptions about MSS and MTU, which one is not correct?A The MSS is the maximum amount of application-layer data in the segmentB The MSS is the maximum size of the TCP segment including headersC The MSS is typically set by MTUD The MTU means the largest link-layer frame62. The job of gathering data chunks, encapsulating each data chunk with header information to create segments and passing the segments to the network is called ____.A multiplexingB de-multiplexingC forwardingD routing63. In the following four descriptions about the relationship between the transport layer and the network layer, which one is not correct?A The transport-layer protocol provides logical communication between hostsB The transport-layer protocol provides logical communication between processesC The services that a transport-layer protocol can provide are often constrained by the service model of the network-layer protocolD A computer network may make available multiple transport protocols64. Suppose the following three 8-bit bytes: 01010101, 01110000, 01001100. What’s the 1s complement of the sum of these 8-bit bytes?A 00010001B 11101101C 00010010D 1000100065. The following four descriptions about multiplexing and de-multiplexing, which one is correct?A A UDP socket is identified by a two-tuples consisting of a source port number and a destination port number.B If two UDP segment have different source port number, they may be directed to the same destination process.C If two TCP segments with different source port number, they may be directed to the same destination process.D If two TCP segments with same destination IP address and destination port number, they must be the same TCP connection.66. UDP and TCP both have the fields except ____.A source port numberB destination port numberC checksumD receive window67. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [nextseqnum,base+N-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged68. Which of the following about TCP is not correct?A It is a connectionless protocolB Point-to-point protocolC Reliable, in-order byte steam protocolD Pipelined protocol69. Which of the following about TCP is not correct?A It is a connectionless protocolB full duplex data transfer protocolC connection-oriented protocolD flow controlled protocol70. The maximum amount of data that can be grabbed and placed in a segment is limited by the ____.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum71. The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host (the so-called____), and then will fit into a single link-layer frame.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum72. The MSS is the maximum amount of ____layer data in the segment, not the maximum size of the TCP segment including headers.A ApplicationB TransportC NetworkingD Link73. Which of the following field is not used for connection setup and teardown?A Sequence numberB TSTC SYND FIN74. ____ is the byte stream number of first byte in the segment.A Sequence numberB ACK numberC ChecksumD port number75. ____ is the byte sequence numbers of next byte expected from other side.A Sequence numberB ACK numberC ChecksumD port number76. Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide ____ acknowledgements.A CumulativeB SelectiveC SingleD Negative77. Fast retransmit means in the case that ____ duplicate ACK-s are received, the TCP sender resend segment before timer expires.A 3B 4C 5D 678. TCP____ means sender won’t overflow receiver’s buffer by tran smitting too much, too fast.A Flow controlB Congestion controlC Reliable data transferD Connection-oriented service79. TCP provides flow control by having the sender maintain a variable called the ____.A Receive windowB Congestion windowC Sliding windowD buffer80. How does TCP sender perceive congestion?A TimeoutB 3 duplicate ACK-sC Both A and BD None of above81. Transport protocols run in ____.A ServersB ClientsC RoutersD End systems82. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers83. Which service does UDP not provide?A multiplexingB de-multiplexingC error-detectionD error-correction84. There are three major events related to data transmission and retransmission in the TCP sender, which one is not in it?A data received from application aboveB de-multiplexing segmentC timer timeoutD ACK receipt85. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP86. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection87. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection88. Which service helps prevent the internet from entering a state of gridlock?A reliable data transferB flow controlC congestion controlD handshaking procedure89. The Internet’s _____is responsible for moving packets from one host to another.A application layerB transport layerC network layerD link layer90.In the following applications, which one is a bandwidth-sensitive application?A E-mailB web applicationC real-time audioD file transfer91. In the following applications, which one uses UDP?A E-mailB web applicationC file transferD DNS92. In the following four descriptions, which one is correct?A If one host’s transport layer uses TCP, then its network layer must use virtual-circuit network.B Datagram network provides connection serviceC The transport-layer connection service is implemented in the routerD The network-layer connection service is implemented in the router as well as in the end system.93.____ is a speeding-matching service---matching the rate which the sender is sending against the rate at which the receiving application is reading.A congestion controlB flow controlC sliding-window controlD variable control94. In the following four descriptions about Rcv-Window, which one is correct?A The size of the TCP RcvWindow never changes throughout the duration of the connectionB The size of the TCP RcvWindow will change with the size of the TCP RcvBufferC The size of the TCP RcvWindow must be less than or equal to the size of the TCP RcvBufferD Suppose host A sends a file to host B over a TCP connection, the number of unacknowledged bytes that A sends cannot exceed the size of the size of the RcvWindow.95. There are 6 flag fields. Which one is to indicate that the receiver should pass the data to the upper layer immediately?A PSHB URGC ACKD RST96. Suppose the TCP receiver receives the segment that partially or completely fills in gap in received data, it will ____.A immediately send ACKB immediately send duplicate ACKC wait some time for arrival of another in-order segmentD send single cumulative97. _____ imposes constrain on the rate at which a TCP sender can send traffic into the network.A sliding windowB congestion windowC receive windowD variable window98. Flow control and congestion control are same at that they all limit the rate of the sender, but differ in that ____.A flow control limits its rate by the size of RcvWindow, but congestion control by the traffic on the linkB congestion control limits its rate by the size of RcvWindow, but flow control by the traffic on the linkC flow control mainly is accomplished by the sender, but congestion control by the receiver.D flow control mainly is accomplished by the receiver, but congestion control bythe link.99. This job of delivering the data in a transport-layer segment to the correct socket is called ____.A multiplexingB de-multiplexingC forwardingD routing100. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [base, nextseqnum-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged101. ____ are the two types of transport services that the Internet provides to the applications.A TCP and UDPB connection-oriented and connectionless serviceC TCP and IPD reliable data transfer and flow control102. In the following descriptions about persistent connection, which one is not correct?A The server leaves the TCP connection open after sending a responseB Each TCP connection is closed after the server sending one objectC There are two versions of persistent connection: without pipelining and with pipeliningD The default mode of HTTP uses persistent connection with pipelining103. The field of Length in UDP segment specifies the length of ____.A the UDP segment, not including the headerB the UDP segment, including the headerC the UDP segment’s headerD the Length field104. In TCP segment header, which field can implement the reliable data transfer?A source port number and destination port numberB sequence number and ACK numberC urgent data pointerD Receive window105. In the following four descriptions about TCP connection management, which one is not correct?A Either of the two processes participating in a TCP connection can end the connectionB If the FIN bit is set to 1, it means that it wants to close the connectionC In the first two step of the three-way handshake, the client and server randomly choose an initial sequence numberD In the three segments of the three-way handshake, the SYN bit must be set to 1 106. Suppose host A sends two TCP segments back to back to host B over a TCP connection. The first segment has sequence number 42, and the second has sequence number 110. If the 1st is lost and 2nd arrives at host B. What will be the acknowledgment number?A 43B ACK42C 109D ACK1101.Consider sending an object of size O=500,000bytes from server to client. LetS=500 bytes and RTT=0.2s. Suppose the transport protocol uses static windows with window size 5. For a transmission rate of 100Kbps, determine the latency for sending the whole object. Recall the number of windows K=O/ WS), and there is K-1 stalled state (that is idle time gaps).2.Consider the following plot of TCP congestion window size as a function of time.Fill in the blanks as follow:a) The initial value of Threshold at the first transmission round is ____. b) The value of Threshold at the 11st transmission round is ____. c) The value of Threshold at the 21st transmission round is ____. d) After the 9th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKe) After the 19th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKf) During ____ transmission round, the 18th segment is sent.3.Consider the TCP reliable data transfer in the given graph. If in Segment 1’s Sequence number =10,data=“AC”, please fill in the following blanks. a) In Segment 2, ACK number=____;b) In Segment 3, Sequence number =____; data=“0123456789”c) If there are some bits corrupted in segment 3 when it arrives Host B, then the ACK number in Segment 5 is ____; and the ACK number in Segment 6 is ____.14 180 26 3000 2 6 4 8 10 12 16 20 22 240 28 32Congestion window sizeTransmission round48121612345674. The client A wants to request a Web page from Server B. Suppose the URL of the page is 172.16.0.200/experiment, and also it wants to receive French version of object. The time-sequence diagram is shown below, please fill in the blanks.12345Packet① to Packet③are TCP connection’s segment, then:Packet ①: SYN flag bit= aACK flag bit= bSequence number= 92Packet ②: SYN flag bit=1ACK flag bit= c Sequence number=100 Packet ③: SYN flag bit= d ACK flag bit=1Sequence number= e5. Consider sending an object of size O=100 Kbytes from server to client. Let S=536 bytes and RTT=100msec. Suppose the transport protocol uses static windows with window size W.(1) For a transmission rate of 25 kbps, determine the minimum possible latency. Determine the minimum window size that achieves this latency. (2) Repeat (1) for 100 kbps.6. Consider the following plot of TCP congestion window size as a function of time. Please fill in the blanks as below.a) The initial value of Threshold at the first transmission round is____. b) The value of Threshold at the 11th transmission round is_____. c) The value of Threshold at the 21st transmission round is_____.14 18 26 30 0 2 6 4 8 10 12 16 20 22 24 28 32 Congestion window sizeTransmission round481216d) After the 9th transmission round, _____ occurs.e) After the 19th transmission round, ____ are detected.。
Live Chat

LiveChat进阶配置 进阶配置
下面根据客户可能会提出的几项要求来做下详细的设置: 1、修改LiveChat在网页中的位置: <script language='javascript'> window.onload = function(){setFloat(0,0)}; </script> setFloat函数的两个参数分别表示LiveChat距离浏览器左边和顶部 的距离,单位为像素,用户可以根据需要自行设置。 2、更改成英文版:en表示英文,cn表示中文 <a href="###" onclick="talk('101.68.92.138','6660','cn','zwz','张维 忠','','','','','','')">
LiveChat进阶配置 进阶配置
3、更换LiveChat客服人员状态图标:状态值0表示离线 <script language=javascript> if (UserList[0].Online == 0) document.write("<img src='http://101.68.92.138:6660/livechatfile/images/img_Man.gif' align='absmiddle'/>"); else document.write("<img src='http://101.68.92.138:6660/livechatfile/images/img_ManOnline.gi f' align='absmiddle'/>"); </script>
RackSwitch G8264 产品指南(已撤销产品)说明书

RackSwitch G8264Product Guide (withdrawn product)The RackSwitch™ G8264 that leverages 10Gb SFP+ and 40Gb QSFP+ Ethernet technology is specifically designed for the data center. It is ideal for today's big data, cloud, and optimized workload solutions. It is an enterprise class Layer 2 and Layer 3 full featured switch that delivers line-rate, high-bandwidth switching, filtering, and traffic queuing without delaying data. Large data-center grade buffers help keep traffic moving, while the redundant power and fans along with numerous high availability features help provide high availability for business sensitive traffic.The RackSwitch G8264, shown in Figure 1, is ideal for latency sensitive applications such as high performance computing clusters and financial applications. In addition to the 10 Gb Ethernet (GbE) and 40 GbE connections, the G8264 also has the capability for traditional 1 GbE connections. The G8264 supports the newest protocols including Data Center Bridging/Converged Enhanced Ethernet (DCB/CEE) for Fibre Channel over Ethernet (FCoE) in addition to iSCSI and network-attached storage (NAS).Figure 1. RackSwitch G8264Did you know?The G8264 supports Virtual Fabric, which helps clients significantly reduce cost and complexity related to I/O requirements of many virtualization deployments. Virtual Fabric helps reduce the number of multiple I/O adapters to a single dual-port 10 G adapter and reduces the number of cables and required upstream switch ports. By using Virtual Fabric, you can carve a dual-port 10 G server adapter into 8 virtual network interface cards (vNICs) and create dedicated virtual pipes between the adapter and switch for optimal performance, higher availability, and improved security. With Virtual Fabric, you can make dynamic changes and allocate bandwidth per vNIC so that you can adjust it over time without downtime.The RackSwitch G8264 is the first 10 GbE switch to offer benefits of OpenFlow. OpenFlow is the new open application programming interface (API) that enables the network administrator to easily configure and manage virtual networks that control traffic on a “per-flow” basis. It creates multiple independent virtual networks and related policies without dealing with the complexities of the underlying physical network and protocols. With OpenFlow, clients can easily create user-controlled virtual networks, optimize performance dynamically, and minimize complexity when used with an industry compliant OpenFlow controller.Click here to check for updatesFigure 2. Front panel of the RackSwitch G8264Figure 3. Rear panel of the RackSwitch G8264Network cabling requirementsThe network cables that can be used with the switch are listed in Table 5.Table 5. G8264 network cabling requirementsTransceiver Standard Cable Connector 40 Gb Ethernet40GBASE-SR4 QSFP+ Transceiver (49Y7884)40GBASE-SR410 m or 30 m MTP fiber optics cables supplied by Lenovo(see Table 3); support for up to 100 m with OM3 multimodefiber or up to 150 m with OM4 multimode fiberMTP40GBASE-LR4 QSFP+Transceiver (00D6222)40GBASE-LR41310 nm single-mode fiber cable up to 10 km LCDirect attach cable40GBASE-CR4QSFP+ to QSFP+ DAC cables up to 7 m; QSFP+ to 4xSFP+ DAC break-out cables up to 5 m for 4x 10 GbE SFP+connections out of a 40 GbE port (see Table 3)QSFP+ 10 Gb Ethernet10GBASE-SR SFP+ Transceiver (46C3447)10GBASE-SR Up to 30 m with fiber optic cables supplied by Lenovo (seeTable 3); 850 nm OM3 multimode fiber cable up to 300 m orup to 400 m with OM4 multimode fiberLC10GBASE-LR SFP+Transceiver (90Y9412)10GBASE-LR1310 nm single-mode fiber cable up to 10 km LC10GBASE-ER SFP+Transceiver (90Y9415)10GBASE-ER1310 nm single-mode fiber cable up to 40 km LC Direct attach cable10GSFP+Cu SFP+ DAC cables up to 7 m (see Table 3)SFP+ 1 Gb Ethernet1000BASE-T SFPTransceiver (00FE333)1000BASE-T UTP Category 5, 5E, and 6 up to 100 meters RJ-451000BASE-SX SFP Transceiver (81Y1622)1000BASE-SX Up to 30 m with fiber optic cables supplied by Lenovo (seeTable 3); 850 nm multimode fiber cable up to 550 m (50 µ)or up to 220 m (62.5 µ)LC1000BASE-LX SFPTransceiver (90Y9424)1000BASE-LX1310 nm single-mode fiber cable up to 10 km LC Management ports1 GbE management port1000BASE-T UTP Category 5, 5E, and 6 up to 100 meters RJ-45 RS-232 management port RS-232DB-9-to-mini-USB or RJ-45-to-mini-USB console cable(comes standard with the switch)Mini-USB WarrantyFigure 4. 10 GbE port aggregationFigure 5. 1 GbE port aggregationFigure 6. The 2560-node logical designFigure 7. The Virtual Fabric logical designFigure 8. IP storage connectivityTrademarksLenovo and the Lenovo logo are trademarks or registered trademarks of Lenovo in the United States, other countries, or both. A current list of Lenovo trademarks is available on the Web athttps:///us/en/legal/copytrade/.The following terms are trademarks of Lenovo in the United States, other countries, or both:Lenovo®BladeCenter®Flex SystemIntelligent ClusterLenovo ServicesNeXtScaleNeXtScale System®RackSwitchSystem x®VMready®iDataPlex®The following terms are trademarks of other companies:Microsoft® and Hyper-V® are trademarks of Microsoft Corporation in the United States, other countries, or both. Other company, product, or service names may be trademarks or service marks of others.。
cloudflare chatgpt原理

文章标题:探索Cloudflare ChatGPT的工作原理1.引言在当今信息爆炸的时代,人工智能技术在各个领域的应用愈发广泛,其中自然语言处理技术更是成为了研究和应用的热点。
而Cloudflare 近日发布的ChatGPT产品引起了广泛关注,本文将从深度和广度的角度,探讨ChatGPT的工作原理及其对未来的影响。
2.对ChatGPT的概述ChatGPT是一种基于人工智能技术的自然语言处理工具,旨在提供更加智能化和个性化的对话体验。
其基于大规模文本数据的学习和模式识别,能够进行对话场景下的语义理解和生成,为用户提供贴近人类对话水平的交互体验。
3.ChatGPT的工作原理ChatGPT的工作原理主要基于深度学习模型,其中包括Transformer 模型和GPT模型。
在使用ChatGPT进行对话时,用户输入的文本会经过编码和嵌入处理后,传入GPT模型进行解码和生成回复。
在这个过程中,模型将通过预训练的方式学习语言的语义和逻辑规律,从而生成更加智能化和流畅的回复。
4.由浅入深的探究从表面上看,ChatGPT的工作原理似乎只是简单地输入和输出,但其中涉及到的深层模型和参数优化却是复杂而精密的。
Transformer模型的自注意力机制以及GPT模型的多层架构,为ChatGPT的智能对话提供了坚实的基础。
通过对这些技术要点的深入探讨,我们可以更好地理解ChatGPT在对话任务中背后的精妙之处。
5.对ChatGPT的个人观点和理解对于ChatGPT这样的自然语言处理工具,我认为它不仅仅是一种技术革新,更是对人类与机器之间交流方式的一次革命性尝试。
随着ChatGPT等技术的不断进步和普及,人们将获得更加智能化和个性化的对话体验,同时也为人机交互模式带来了全新的可能性。
结语通过对ChatGPT的工作原理进行全面评估,我们能更好地理解自然语言处理技术在人工智能领域的应用,并对ChatGPT在未来的发展和应用提供了更深刻的认识。
scapy 常用命令 -回复

scapy 常用命令-回复Scapy是一个强大的网络分析工具,它可以用来创建、发送和捕获网络数据包,并对这些数据包进行修改和解析。
这篇文章将介绍Scapy的常用命令,并详细说明它们的用法和作用。
1.命令1:srp/srp1srp命令用于发送和接收数据包,并返回响应。
srp1命令与srp类似,但只返回第一个响应。
用法示例:pythonans, unans =srp(Ether(dst="ff:ff:ff:ff:ff:ff")/ARP(pdst="192.168.1.1/24"), timeout=2)这个命令将发送一个ARP请求广播包给目标网络的所有主机,并等待2秒钟的响应。
返回的ans变量包含响应数据包列表,unans包含未收到响应的数据包列表。
2.命令2:send/srp1send命令用于发送数据包,它不会等待响应。
用法示例:pythonsend(IP(dst="192.168.1.1")/ICMP())这个命令将发送一个ICMP数据包到目标主机。
3.命令3:lsls命令用于列出Scapy支持的所有协议。
用法示例:pythonls()这个命令将列出所有支持的协议,包括其字段和默认值。
4.命令4:Ether/IP/TCP/UDP/DNS等这些是Scapy中用于创建各种协议的命令,它们可以用于自定义和修改数据包的协议字段。
用法示例:pythonEther(src="00:11:22:33:44:55",dst="aa:bb:cc:dd:ee:ff")/IP(src="192.168.1.1",dst="192.168.1.2")/TCP(sport=1234, dport=80)这个命令将创建一个以太网包,其中源MAC地址为00:11:22:33:44:55,目标MAC地址为aa:bb:cc:dd:ee:ff。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
(b) 双同步数据格式
数据1
…… 数据n
如接口尺寸、形状等
6
机械性能
7
协议组件
8
2.3.2 总线组织
1 单总线
特点
存储器和I/O分时使用同一总线 优点 结构简单,成本低廉,易于扩充 缺点 带宽有限,传输率不高(可能造成物理长度过长)
2 双总线
特点
存储总线+I/O总线 优点 提高了总线带宽和数据传输速率 缺点 CPU繁忙
3 多级总线
一. 串行总线标准 二. 并行总线标准
8位的PC/XT总线
总线串行化趋势
RS232、USB、1394、SPI、现场总线 系 统 内 总 线
16位的PC/AT(ISA)总线
32位的PC386(EISA)总线 32位或64位的PCI局部总线 VXI、IEEE488
5
系统外总线
1. 线路介质
特性
2.3.1 总线要素
二、优点 三、缺点
地址信号 主设备 联络信号
全互锁方式可靠性高,适应性强 控制复杂,交互的联络过程会影响系统工作速度
① 准备好接收 (M发送地址信号)
③ ①
②已送出数据 (S发送数据信号)
从设备 联络信号 数据信号
②
④
③已收到数据 (M撤销地址信号) ④完成一次传送 (S撤销数据信号) 20
半同步总线时序
载波传送方式下
通信线路状态改变一次可能送出n位数据,这时比特率=n×波特率
31
如某相位调制系统中可能发送的相位状态有0(代 表数据“00”)、π/2(代表数据“01”)、π(代 表数据“10”)、3π/2(代表数据“11”)四种, 则通信线路的相位状态每改变一次将送出两位数据, 这时 比特率=2×波特率
(综合性强,偏应用的一门课程)
电子工程学院
陈客松
1
第2/4章(2) 计算机总线接口技术
一. 总线基础 组织、仲裁、带宽、时序 二. 接口基础 I/O连接模式、 I/O编址方式、I/O控制方式、接口组成
硬件:地址译码、读写控制、总线隔离 软件:驱动程序(初始化、传送控制、结束控制等)
三. 接口设计技术 并行接口 零握手(无条件)、带握手信号(条件、中断)、可编程并 行接口 串行接口 传输方向、传输距离、传输速率、差错控制、传输时序和格式 AD/DA接口 定时/计数 2 DMA接口
为提高串行数据的传输速率和传送距离,我们通常采用载 波传送(利用调制解调技术将信号加在高频载波上再进行传输)。 如:可将数字信号利用MODEM调制到300 ~ 3300Hz频 段以利用公用电话线进行传输。
串 计 行 算 接 机 口
计 算 机
串 行 接 口
MODEM
……
MODEM
常用的调制解调方法包括频移键控FSK、幅移键控ASK、 30 相移键控PSK等方式。
收/发时钟频率=波特率。 同步串行通信通常采用CRC校验方法进行数据 34 的检错和纠错。
同步串行通信的数据格式可能有以下几种。但都必须 首先确定传送的起始位置(用同步字符或同步标志或采 用硬件同步信号),然后传送准备好的信息数据,最后 发送校验字符。
同步字符 数据1 …… 数据n CRC字符1 CRC字符2 CRC字符2 (a) 单同步数据格式 同步字符1 同步字符2 数据1 … 数据n CRC字符1
奇偶校验 CRC校验
33
常用差错控制方式:
1.检错重发ARQ 2.前向纠错FEC 3.混合纠错HEC
同步串行通信
同步串行通信以数据块为基本单位,传输时字 节与字节之间、位与位之间都需要严格同步,因此 收发双方需要使用(传送)同一时钟信号。
发送方在时钟信号的下降沿发送字节 接收方在时钟信号的上升沿接收字节 时钟 数据(61H) 位 0 1 1 0 0 0 0 位 1
按组织方式
单总线 双总线 多重总线
片内总线
非通用总线 芯片总线(片间总线、元件级总线) (与具体芯 按所处位置 片有关) (数据传送范围) 系统内总线(插板级总线)
系统外总线(通信总线)
并行总线 按数据格式 (本质) 同步 半同步 异步 同步 异步
通用标准总线
按时序关系 (握手方式)
4
串行总线
常用总线标准
分别指明总线操作周期的开始和结束。 地址、数据及读/写等控制信号可在时钟沿处改变。
二、优点 三、缺点
同步时钟 地址信号
电路设计简单,总线带宽大,数据传输速率快
时钟以最慢速设备为准,高速设备性能将受到影响
延时 数据信号
控制信号
19
异步总线时序
一、特点
系统中可以没有统一的时钟源,模块之间依靠各种联络(握 手)信号进行通信,以确定下一步的动作。
特点
缺点
高速外设和低速外设分开使用不同的总线
复杂
9
优点 高效,进一步提高系统的传输带 Nhomakorabea和数据传输速率
常见的几种总线组织
10
微机的典型多级总线结构
核
前端总线Front Side Bus
北桥
南桥
i845PE芯片组由北桥芯片82845PE GMCH和南桥芯片ICH4组成
11
2.3.3 总线仲裁
每个时钟周期内传送数据的次数系统功能设计
时钟频率
总线偏离(skew)、兼容性
16
总线带宽的充分利用
1. 总线共享技术(多路复用)
TDM、FDM、CDM、SDM、WDM
时分复用 频分复用
2. 其它
信源编码(如数据压缩)、信道编码(如调制解调)……
17
2.3.5 总线时序
总线周期一般包括4个阶段:总线请求与仲裁、寻 址、传数、结束; 总线时序是指总线事件的协调方式,以实现可靠 的寻址和数据传送。 一.同步
并行仲裁
主模块1
主模块2
……
请求BR 允许BG 忙BB
主模块N
总 线 仲 裁 器
特点:各主控模块有独立的请求信号线和允许信号线,其 优先级别由总线仲裁器内部模块判定; 优点:总线请求响应的速度快; 14 缺点:扩充性较差;
串并行二维仲裁
请求BR 允许BG 忙BB
从下一设备
到下一设备
总 线 仲 裁 器
程序
程序地址 程序读总线 程序/数据写 数据读总线 数据写地址 数据读地址 25
DSP
数据
数据
I/O接口
外设
一.片上总线特点
1.简单高效
结构简单:占用较少的逻辑单元 时序简单:提供较高的速度 接口简单:降低IP核连接的复杂性
2.灵活,具有可复用性
地址/数据宽度可变、互联结构可变、仲裁机制可变
3.功耗低
27
2.3.6 串行总线
高速串行总线体现了成功的网络通信 技术向计算机体系结构的渗入:差分信号 传输、数据包、点对点
一.传输方向
单工、 半双工、双工、多工
二.传输距离
三.传输速率
基波、载波
比特率、波特率
四.差错控制
五.传输时序
ARQ、FEC、HEC
同步、异步
六.数据格式及含义
控制信息、数据信息
28
种类 有限(电缆、光缆)、无线(电磁波)
原始数据传输率
带宽 传输介质可用的最高和最低频率之差 对噪声的敏感性 内部或外部干扰 对失真的敏感性 信号和传输介质之间的互相作用引起 对衰减的敏感性 信号通过传输介质时的功率损耗
2. 总线协议
电气性能
总线信号 有效电平、传输方向/速率/格式等 总线时序 规定通信双方的联络方式 总线仲裁 规定解决总线冲突的方式 其它 如主/从设备、差错控制等
运算器
系 统 三总线形式
控 制 器 寄存器 I/O 芯片
扩展 接口板
③系统总线、 (系统)内总线 如ISA、PCI 其 他 仪 器 系 统 ④外部总线、 (系统)外总线 如并口、串口
22
23
24
AB
MPU
CB DB
冯•诺依曼 体系结构
哈佛体系结构
RAM
ROM
I/O接口
外设
普雷斯顿 体系结构
程序
串行数据的传输方向
发送器
A
B
接收器
A
发送器 接收器
B
接收器 发送器
单工方式
实例:广播
双工方式
实例:电话机
A
发送器
接收器
B
发送器 接收器
1
1 复 用 器
复 用 器 2
2
n ……
…… n
半双工方式
实例:对讲机
多工方式
TDM、FDM等
实例:数据通信网 29
串行数据的调制解调
串行数据在基波传送方式下(指信号按原样传输),通常 只能传输几十米至几百米,并且传输速率越大,传输距离越短。
常用的标准波特率包括110、300、1200、2400、 4800、9600、19200波特等。
32
串行数据的差错控制
在串行数据长距离的传送过程中,很容易由于突发性 干扰(电气干扰、天电干扰等)而引起误码,所以差错 控制能力是衡量串行通信系统性能的一个重要指标。
差错控制通常包括两方面的内容:
检错: 如何发现传输中的错误 纠错: 发现错误后,如何消除和纠正错误
采用专门的控制器或仲裁器 总线控制或仲裁器可以是独立的模块或集成在CPU中 协议简单而有效,但总体系统性能较低
12
菊花链(串行)总线仲裁
总 线 仲 裁 器
允许BG
主控 模块1
主控 模块2
……
主控 模块N
请求BR 忙BB
特点:各主控模块共用请求信号线和忙信号线,其优先级 别由其在链式允许信号线上的位置决定; 优点:具有较好的灵活性和可扩充性; 缺点:主控模块数目较多时,总线请求响应的速度较慢; 13
