juniper之常用命令
Juniper防火墙基本命令

Juniper防火墙基本命令Juniper防火墙基本命令常用查看命令Get int查看接口配置信息Get int ethx/x查看指定接口配置信息Get mip查看映射ip关系Get route查看路由表Get policy id x查看指定策略Get nsrp查看nsrp信息,后可接参数查看具体vsd组、端口监控设置等Get per cpu de查看cpu利用率信息Get per session de查看每秒新建会话信息Get session查看当前会话信息,后可匹配源地址、源端口、目的地址、目的端口、协议等选项Get session info查看当前会话数量Get system查看系统信息,包括当前os版本,接口信息,设备运行时间等Get chaiss查看设备及板卡序列号,查看设备运行温度Get counter stat查看所有接口计数信息Get counter stat ethx/x查看指定接口计数信息Get counter flow zone trust/untrust查看指定区域数据流信息Get counter screen zone untrust/trust查看指定区域攻击防护统计信息Get tech-support查看设备状态命令集,一般在出现故障时,收集该信息寻求JTAC支持常用设置命令Set int ethx/x zone trust/untrust/dmz/ha配置指定接口进入指定区域(trust/untrust/dmz/ha等)Set int ethx/x ip x.x.x.x/xx配置指定接口ip地址Set int ethx/x manage配置指定接口管理选项,打开所有管理选项Set int ethx/x manage web/telnet/ssl/ssh配置指定接口指定管理选项Set int ethx/x phy full 100mb配置指定接口速率及双工方式Set int ethx/x phy link-down配置指定接口shutdownSet nsrp vsd id 0 monitor interface ethx/x配置ha监控端口,如此端口断开,则设备发生主/备切换Exec nsrp vsd 0 mode backup手工进行设备主/备切换,在当前的主设备上执行set route 0.0.0.0/0 interface ethernet1/3 gateway 222.92.116.33配置路由,需同时指定下一跳接口及ip地址所有set命令,都可以通过unset命令来取消,相当于cisco中的no所有命令都可以通过“TAB”键进行命令补全,通过“?”来查看后续支持的命令防火墙基本配置create account [admin | user] <username> 回车输入密码:再次输入密码:configure account admin 回车输入密码:再次输入密码:2.port配置config ports <portlist> auto off {speed [10 | 100 | 1000]} duplex [half | full] auto off3.Vlan配置无论是核心还是接入层,都要先创建三个Vlan,并且将所有归于Default Vlan的端口删除:config vlan default del port allcreate vlan Servercreate vlan Usercreate vlan Manger定义802.1q标记config vlan Server tag 10config vlan User tag 20config vlan Manger tag 30设定Vlan网关地址:config vlan Server ipa 192.168.41.1/24config vlan User ipa 192.168.40.1/24config vlan Manger ipa 192.168.*.*/24Enable ipforwarding 启用ip路由转发,即vlan间路由Trunk 配置config vlan Server add port 1-3 tconfig vlan User add port 1-3 tconfig vlan manger add port 1-3 t4.VRRP配置enable vrrpconfigure vrrp add vlan UserVlanconfigure vrrp vlan UserVlan add master vrid 10 192.168.6.254configure vrrp vlan UserVlan authentication simple-password extremeconfigure vrrp vlan UserVlan vrid 10 priority 200configure vrrp vlan UserVlan vrid 10 advertisement-interval 15configure vrrp vlan UserVlan vrid 10 preempt5.端口镜像配置首先将端口从VLAN中删除enable mirroring to port 3 #选择3作为镜像口config mirroring add port 1 #把端口1的流量发送到3config mirroring add port 1 vlan default #把1和vlan default的流量都发送到36.port-channel配置enable sharing <port> grouping <portlist> {port-based | address-based | round-robin}show port sharing //查看配置7.stp配置enable stpd //启动生成树create stpd stp-name //创建一个生成树configure stpd <spanning tree name> add vlan <vlan name> {ports <portlist> [dot1d | emistp | pvst-plus]}configure stpd stpd1 priority 16384configure vlan marketing add ports 2-3 stpd stpd1 emistp8.DHCP 中继配置enable bootprelayconfig bootprelay add <dhcp server ip>9.NA T配置Enable nat #启用natStatic NA T Rule Exampleconfig nat add out_vlan_1 map source 192.168.1.12/32 to 216.52.8.32/32Dynamic NA T Rule Exampleconfig nat add out_vlan_1 map source 192.168.1.0/24 to 216.52.8.1 - 216.52.8.31Portmap NA T Rule Exampleconfig nat add out_vlan_2 map source 192.168.2.0/25 to 216.52.8.32 /28 both portmapPortmap Min-Max Exampleconfig nat add out_vlan_2 map source 192.168.2.128/25 to 216.52.8.64/28 tcp portmap 1024 - 819210.OSPF配置enable ospf 启用OSPF进程create ospf area <area identifier> 创建OSPF区域configure ospf routerid [automatic | <routerid>] 配置Routeridconfigure ospf add vlan [<vlan name> | all] area <area identifier> {passive} 把某个vlan加到某个Area中去,相当于Cisco中的network的作用configure ospf area <area identifier> add range <ipaddress> <mask> [advertise | noadvertise] {type-3 | type-7} 把某个网段加到某个Area中去,相当于Cisco中的network的作用configure ospf vlan <vlan name> neighbor add <ipaddress>OSPF中路由重发布配置enable ospf export direct [cost <metric> [ase-type-1 | ase-type-2] {tag <number>} | <route map>]enable ospf export static [cost <metric> [ase-type-1 | ase-type-2] {tag <number>} | <route map>]enable ospf originate-default {always} cost <metric> [ase-type-1 | ase-type-2] {tag <number>} enable ospf originate-router-id11.SNMP配置enable snmp accessenable snmp trapscreate access-profile <access profile> type [ipaddress | vlan]config snmp access-profile readonly [<access_profile> | none]配置snmp的只读访问列表,none 是去除config snmp access-profile readwrite [<access_profile> | none] 这是控制读写控制config snmp add trapreceiver <ip address> {port <udp_port>} community <communitystring> {from <source ip address>} 配置snmp接收host和团体字符串12.安全配置disable ip-option loose-source-routedisable ip-option strict-source-routedisable ip-option record-routedisable ip-option record-timestampdisable ipforwarding broadcastdisable udp-echo-serverdisable irdp vlan <vlan name>disable icmp redirectdisable web 关闭web方式访问交换机enable cpu-dos-protect13.Access-Lists配置create access-list icmp destination sourcecreate access-list ip destination source portscreate access-list tcp destination source portscreate access-list udp destination source ports14.默认路由配置config iproute add default <gateway>15.恢复出厂值,但不包括用户改的时间和用户帐号信息unconfig switch {all}16.检查配置show versionshow configshow sessionshow management 查看管理信息,以及snmp信息show bannershow ports configurationshow ports utilization ?show memory/show cpu-monitoringshow ospfshow access-list {<name> | port <portlist>}show access-list-monitorshow ospf area <area identifier>show ospf area detailshow ospf ase-summaryshow ospf interfaces {vlan <vlan name> | area <area identifier>} unconfigure ospf {vlan <vlan name> | area <area identifier>}switchshow switchshow configshow diagshow iparpshow iprouteshow ipstatshow logshow tech allshow version detail17.备份和升级软件download image [<hostname> | <ipaddress>] <filename> {primary | secondary}upload image [<hostname> | <ipaddress>] <filename> {primary | secondary}use image [primary | secondary]18.密码恢复。
Juniper_华为_H3C设备维护常用命令

Juniper_华为_H3C设备维护常用命令1、[Router&Swithc]华为/H3C设备常规巡检命令#系统时间display clock#系统以及各单板软件版本display version#设备温度display environment#日志信息display logbuffer#单板运行状态display device#电源状态display device#风扇状态display device#CPU占用状态display cpu-usage#存占用率display memory limit#接口流量display interface#接口、链路状态display interface#地址分配display current-configuration interface##路由扩散display current-configuration | include ospf#OSPF(Open Shortest Path First)配置display router id#路由信息display ip routing-table#端口统计数据display ip interface#当前配置文件display current-configuration#保存配置文件display saved-configuration端口使用状态display interface GigabitEthernet/Ten-GigabitEthernet briefVLAN使用状态display ip interface brief2、脚本—华为display versiondis patch-informationdisplay clockdis dustproofdis frame-typedis healthdisplay cpu-usagedisplay memorydisplay memory limitdisplay devicedisplay device manuinfodisplay powerdisplay fandisplay voltagedir cfcard2:/dir cfcard:display device pic-statusdis switchover statedisplay environmentdisplay interfacedisplay logbufferdis alarmdis bootrom ethernetdisplay current-configurationdisplay current-configuration interface#display router iddisplay ip routing-tabledisplay ip interfacedisplay ip interface briefdisplay current-configurationdisplay saved-configurationdisplay diagnostic-information3、脚本—华为NE40edisplay version 查看VRP版本等信息dis patch-information 查看版本补丁display clock 查看时钟dis dustproof 防尘网信息Dis frame-type 显示NE40E机框类型dis health 显示系统资源的使用情况display cpu-usage 查看1分钟CPU利用率display memory 查看存使用情况display memory limitdisplay device 查看母板信息display device manuinfodisplay power 查看电源状态display fan 查看风扇状态display voltage 查看板卡电压dir cfcard2:/ 查看设备crash信息dir cfcard: 查看设备cf卡信息display device pic-status 查看子卡型号,序列号(NE40E NE80E)dis switchover state 查看引擎HA情况display environmentdisplay interface 查看接口状态display logbuffer 查看日志dis alarm 查看设备告警dis bootrom ethernet 查看设备bootrom信息display current-configuration查看当前配置display current-configuration interface# 查看设备当前接口配置display router id 查看设备路由IDdisplay ip routing-table 查看设备路由display ip interface 查看设备接口情况display ip interface brief 查看设备接口状态display current-configuration 查看设备当前配置display saved-configuration 查看设备存配置(相当show start)display diagnostic-information 抓取设备完整信息相对于show tech二、JUNIPER设备常用维护巡检命令1、脚本—JUNIPERshow system uptimeshow version detailshow chassis hardware detailshow chassis environment //显示设备的环境信息,包括温度、风扇状况、电源状况、路由引擎状况。
juniper交换机命令juniper交换机配置命令整理

juniper交换机命令juniper 交换机配置命令整理导读:就爱阅读网友为您分享以下“juniper 交换机配置命令整理”的资讯,希望对您有所帮助,感谢您对 的支持!设置交换机名字set system host-name BaoGaoTing端口镜像set ethernet-switching-options analyzer debug input ingress interface ge-0/0/0.0set ethernet-switching-options analyzer debug input egress interface ge-0/0/0.0set ethernet-switching-options analyzer debug output interface ge-0/0/4.0Dual-partition的主要目的:解决异常断电设备无法启动的问题request system snapshot media internal slice alternate request system snapshot slice alternate //主备之间备份request system reboot slice alternate media internal // 指定从另外一个分区启动,下一次启动就会默认从上次启动的分区启动junos os,记忆功能QinQ 配置基本的set ethernet-switching-options dot1q-tunneling ether-type 0x8100 封装协议set vlans qinqvlan vlan-id 2821set vlans qinqvlan dot1q-tunnelingset interfaces ge-0/0/28 unit 0 family ethernet-switching vlan members 2821 上行端口set ethernet-switching-options dot1q-tunneling ether-type 0x8100set vlans cust1 vlan-id 100set vlans cust1 interface ge-0/0/1.0set vlans cust1 interface ge-0/0/2.0灵活的set ethernet-switching-options dot1q-tunneling ether-type 0x8100 ##set interfaces ge-0/0/27 unit 0 family ethernet-switching port-mode access ##下行端口set interfaces ge-0/0/27 unit 0 family ethernet-switching vlan members qinq ##用户Vlan为qinq 管理Vlan为Vlan600是透传上去的set interfaces ge-0/0/27 unit 0 family ethernet-switching vlan members vlan600 ** 注意点:一般情况下是不可以同时两个access的,--那样就做成trunk模式** 除非有一个vlan是dot1q-tunnel,而且需要tunnel vlan必须得有customer-vlan的,没有customer-vlan是无法提交成功的set vlans qinq vlan-id 4000 ##//灵活qinq,对于内层标签2-150的tag加上外层4000set vlans qinq interface ge-0/0/27.0set vlans qinq dot1q-tunneling customer-vlans 2-150接入交换机配置setinterfaces ge-0/1/1 unit 0 family ethernet-switching port-mode trunkset interfaces ge-0/1/1 unit 0 family ethernet-switching vlan members 2set interfaces ge-0/1/1 unit 0 family ethernet-switching native-vlan-id 600 **由于上联汇聚交换机的端口为Access口所以要透传的Vlan为native-Vlan##root用户名密码set system root-authentication encrypted-password "$1$z2Z28Ixe$AScMP7uMvMHY3fy8dgtm11" ##用户idset system login user juniper uid 2100 ##设置root用户为超级用户set system login user juniper class super-user##远程用户名和密码set system login user juniper authentication encrypted-password "$1$qUdu0s0Z$vGS88V0jrjhsPnQOTF9oy/" ##启用telnet set system services telnet connection-limit 10 set system services telnet rate-limit 10##端口模式为accesset interfaces ge-0/0/0 unit 0 family ethernet-switching port-mode access ##端口加入Vlan为600 set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members 600 ##端口为trunkset interfaces ge-0/1/0 unit 0 family ethernet-switching port-mode trunk ##允许通过Vlan为600 set interfaces ge-0/1/0 unit 0 family ethernet-switching vlan members 600 ##设置Vlan600的ip地址set interfaces vlan unit 600 family inet address 172.30.0.16/24 ##设置默认网关set routing-options static route 0.0.0.0/0 next-hop 172.30.0.1 ##开启Vlan的三层接口set vlans default l3-interface vlan.0 ##创建Vlan 名字为mgt id 为600 set vlans mgt vlan-id 600 ##开启Vlans mgt的三层接口set vlans mgt l3-interface vlan.600 ##开启Vlans mgt的三层接口set poe interface all X配置VLAN的L3接口地址set vlans name l3-interface vlan.xxset interface vlan xx unit xx family inet address x.x.x.x/24将某个交换端口添加到创建好的VLAN中set interface ge-0/0/x unit 0 family ethernet-switching port-mode access vlan members name 配置TRUNK端口set interface ge-0/0/23 unit 0 family ethernet-switching port-mode trunk native-vlan-id 1 vlan member xx预提交commit check清除LED灯报警clear alarm trafficclear alarm eventEX2200 ALARM告警灯亮红灯:show chassis alarmshow system alarmrequest system configuration rescue save/delete set chassis alarmmanagement-ethernet link-down ignore 管理口状态警告信息灯关闭set chassis alarm ethernet link-down ignore 交换机端口状态警告信息灯关闭igmp 开启set protocols igmp-snooping vlan alldeactivate protocols igmp-snooping开启生成树Set protocol stp恢复出厂设置load factory defaultDual-partition的主要目的:解决异常断电设备无法启动的问题request system snapshot media internal slice alternate //主备之间备份request system reboot slice alternate media internal // 指定从另外一个分区启动,下一次启动就会默认从上次启动的分区启动junos os,记忆功能dhcp 配置set system services dhcp pool 100.1.1.0/24 address-range low 100.1.1.10set system services dhcp pool 100.1.1.0/24 address-range high 100.1.1.200set system services dhcp pool 100.1.1.0/24 default-lease-time 7200set system services dhcp pool 100.1.1.0/24 router 100.1.1.254将端口设置为三层模式。
JUNIPER 路由器常用维护命令讲解

中国电信CN2网络Juniper设备常用维护命令手册V1.0(Release)Maintained By Kevin YangCorporate HeadquartersJuniper Networks ,Inc.1194 North Mathilda AvenueSunnyvale, California 94089-1206 USAPhone: 888-JUNIPER (888-586-4737)1-408-745-2000Fax: 1-408-745-2100目录前言 5设备端口5 文档目的 5 使用人员 5 内容范围 5 假设与告诫 相关文献6 运行状态维护命令7 show chassis alarms7 show chassis environment7 show chassis environment pem 9 show chassis environment sib 10 show chassis environment fpc 11 show chassis sibs12 show chassis fabric topology 13 show version16 show chassis hardware detail 16 show chassis fpc19 show chassis fpc detail 20 show chassis fpc pic ‐status22 show chassis pic fpc ‐slot <fpc> pic ‐slot <pic> 23 show chassis rouging ‐engine24 s how chassis feb (只适用于M120)26 show chassis feb detail (只适用于M120)27 show chassis fpc ‐feb ‐connectivity (只适用于M120) 28 show ntp status 29 状态维护命令30 show interfaces descriptions 30 show interfaces terse31 show interfaces diagnostics optics 32 show interfaces extensive 34 show interfaces queue40clear interfaces statist 4 ics 4路由r soft ‐inbound <neighbor> 6MPL <destination> 7其它协议状态维护命令46 show route <destination> 46 show route summary47 show route <destination> exact detail49 show route forwarding ‐table destination <destination> 51 show isis hostname 52 show isis adjacency 53 show isis interface 54 show isis database55 show configuration protocol isis 57 show bgp summary58 show bgp neighbor <neighbor ‐address>59 show route advertising ‐protocol bgp <neighbor> | match 62 show route receive ‐protocol bgp <neighbor> | match 62 show bgp receive ‐protocol bgp <neighbor> all63 show route protocol bgp <destination> exact detail 64 show route protocol bgp aspath ‐regex <aspath ‐regex> 66 clear bgp neighbor <neighbor > 67 clear bgp neighbor soft <neighbor>67 clear bgp neighbo 8 S 相关维护命令69 show mpls lsp69 clear mpls lsp name <name> 71 show mpls interface 71 show rsvp interface 72 show ldp interface 73 show ldp neighbor 74 show ldp session 75 show ldp database75 clear ldp neighbor <neighbor> 77 clear ldp session 7 相关维护命令78 show system storage 78 request chassis pic offline 79 request chassis pic online 79 request chassis fpc offline 80 request chassis fpc online 80 request chassis cb offline 80 request chassis cb online 81 request chassis sib offline 81 request chassis sib online81 request chassis routing ‐engine master switch82 request routing ‐engine login other ‐routing ‐engine82request system halt 82 request system reboot83 request system software add 83 request system snapshot 4 8故障show pfe statistics traffic 89信息收集命令85 request support information 85 show log messages 86 show log chassisd86 show chassis hardware detail | no ‐more 87前言文档目的本文档是瞻博网络公司(Juniper)工程师为中国电信CN2 网络维护人员编写的维护常用命令手册使用人员本文档资料主要面向负责中国电信CN2的网络维护技术人员内容范围本文档包含Juniper路由器设备软硬件状态,配置状态,连接状态,负载状态,路由协议, QoS 状态,运行状态记录情况,故障信息收集等方面的常用命令 假设与告诫假设阅读本文档的技术人员拥有本文中描述的Juniper路由产品的安装和运行经 验,并了解配置、升级和故障排除的基本程序。
Juniper路由器配置命令介绍

层级子层级systemrouting-options loopbackPOSGEinterfaceprotocolISISOSPFBGPMPLS-RSVP/LDP MPLS-FRRMPBGPMPLS-VPN COS功能项set system hostname hostnameset system root-authentication plain-text-passwordset system login user lab class super-user authentication plain-text-passwordset system services telnet/ftp/name-ser dns-adds et interface lo0 description descriptionset interface lo0 unit 0 family inet address ip-addressset interface lo0 unit 0 family iso address iso-addressset interface so-slot/pic/port description descriptionset interface so-slot/pic/port mtu mtu-numberset interface so-slot/pic/port hold-time up ms down msset interface so-slot/pic/port encapsultation pppset interface so-slot/pic/port sonet-options fcs [32|16]set interface so-slot/pic/port sonet-options payload-scrambler set interface so-slot/pic/port sonet-options rfc-2615set interface so-slot/pic/port unit 0 family inet address ip-addressset interface so-slot/pic/port unit 0 family isoset interface so-slot/pic/port unit 0 family mplsset interface ge-slot/pic/port description descriptionset interface so-slot/pic/port mtu mtu-numberset interface so-slot/pic/port hold-time up ms down msset interface ge-slot/pic/port unit 0 family inet address ip-addressset interface ge-slot/pic/port unit 0 family isoset interface ge-slot/pic/port unit 0 family mplsset routing-options router-id router-idset routing-options autonomous-system as-numberset routing-options static route network/mask next-hop addressset protocols isis level [ 1 | 2 ] interfaceinterface.logical-numberset protocols isis lsp-lifetime secondsset protocols isis export export-policyset protocols isis spf-delay msset protocols isis rib-group inet rg-nameset protocols isis traffic-engineering shortcutsset protocols isis level [ 1 | 2 ] wide-metrics-onlyset protocols isis level [ 1 | 2 ] preference numberset protocols isis level [ 1 | 2 ] external-preference number set protocols isis level [ 1 | 2 ] disableset protocols isis interface interface-name lsp-interval msset protocols isis interface interface-nam level [ 1 | 2 ] metric numberset protocols isis interface interface-nam level [ 1 | 2 ]hello-interval secondsset protocols isis interface interface-nam level [ 1 | 2 ]hold-time secondsset protocols isis interface interface interface-nam passive set protocols ospf area XX interface interface.logical-number set protocols ospf interface interface.logical-number metric numberset protocols ospf interface interface interface.logical-number passivset protocols ospf traffic-engineeringset protocols bgp interface interface.logical-numberset protocols bgp group group-nameset protocols bgp group group-name type external/internalset protocols bgp group group-name peer-as 1234set protocols bgp group group-name neighbor X.X.X.Xset protocols bgp hold-time secondsset protocols bgp mtu-discoveryset protocols bgp out-delay secondsset protocols bgp log-updownset protocols bgp dampingset protocols bgp group group-name description descriptionet protocols bgp group group-name local-address group-namelocal-address addressset protocols bgp group group-name family inet anyset protocols bgp group group-name neighbor address description descriptionset interfaces interface.logical-number family mplsset protocols mpls interface.logical-numberset protocols ldp interface.logical-numberset protocols rsvp interface.logical-numberset protocols mpls label-switched-path test to 10.0.9.7set protocols mpls label-switched-path test ldp-tunnelingset protocols mpls label-switched-path test link-protectionset protocols rsvp interface so-0/0/3.0 link-protectionset protocols bgp group group-name family [inet|inet-vpn|inet6|inet6-vpn|l2vpn]set routing-instances instance-nameset routing-instances instance-name instance-type VRFset routing-instances instance-name interface interface-number set routing-instances instance-name route-distinguisher xxxx set routing-instances instance-name vrf-target target:xxxx:yyyy set routing-instances instance-name routing-options static route x.x.x.x/z next-hop x.x.x.xset routing-instances instance-name protocols ospf area XX interface interface-name.logical-numberset routing-instances instance-name protocols ospf export bgp-ospfset policy-options policy-statement bgp-ospf term 1 from protocol bgpset policy-options policy-statement bgp-ospf term 1 then accept命令解释备注配置设备名必选为root帐户设置密码新建用户名为lab的帐户,并设定密码配置路由器Telnet/ftp/dns服务配置端口描述配置IP地址配置ISO地址配置端口描述配置端口MTU配置端口up/down的damping时间配置端口封装为PPP配置端口FCS的位数配置端口打开payload-scrambler配置端口FCS 32,打开payload-scrambler,C2字节为0x16配置IP地址端口允许运行ISIS端口允许运行mpls配置端口描述配置端口MTU配置端口up/down的damping时间配置IP地址端口允许运行ISIS端口允许运行mpls配置路由器Router-ID配置路由器的AS号码配置静态路由配置聚合路由配置ISIS接口并将接口加入到相应的ISIS LEVEL里必选配置IS-IS的存活时间,LSP的refresh 时间为lsp-lifetime-317秒配置IS-IS的路由分发策略配置IS-IS的SPF的延迟配置IS-IS使用的路由组配置IS-IS使用TE的shortcuts配置IS-IS的Level使用wide-metric---支持TE必选配置IS-IS内部路由的管理距离配置IS-IS外部路由的管理距离配置IS-IS禁止运行Leve 1或者2配置IS-IS端口发送LSP的间隔配置IS-IS端口的Metric值配置IS-IS端口的IIH的间隔时间配置IS-IS端口的Hold时间配置IS-IS端口运行Passive模式配置OSPF接口并将接口加入到相应的OSPF AREA里必选配置OSPF端口的Metric值配置OSPF端口运行Passive模式配置OSPF支持流量工程(启用OPAQUE LSA)配置o spf端口的IIH的间隔时间配置BGP接口必选配置BGP组必选设定BGP组为EBGP或IBGP必选设定本组内的neighbor的AS号码必选设定本组内neighbor的session IP地址必选配置BGP的Hold-timer时间,Hello时间自动调整为Hold-time的1/3配置BGP的TCP进程的MSS为路径的最大值配置BGP的的路由发送延迟配置路由器纪录BGP的邻居up/down的变化配置BGP路由启用Damping算法配置BGP的组的描述配置和BGP的组内的邻居进行通讯的时候使用的本地地址配置BGP的Group内的邻居允许运行unicast 和multicast配置BGP的邻居的描述端口允许运行mpls配置将接口加到MPLS协议组里配置将接口加到LDP协议组里配置将接口加到rsvp协议组里配置名称为test的RSVP signaled LSP, 此LSP终结点为10.0.9.7在LDP TUNNEL的路由器上配置名称为test的RSVPsignaled, LSP使得LDP能够穿越RSVP LSP启用保护的LSP保护选项在RSVP协议里,启用保护选项配置本group下的BGP session的属性,inet是启用IP路由支持,此项为默认启用,inet-vpn是启用l3mbgp-vpn路由支持,启用任意非INET属性,会将inet禁用配置routing-instances配置routing-instances的VRF将逻辑接口加入到routing-instances里配置RD,确认RD在整个routing-instance里是唯一的配置RT,确认RT在整个routing-instance里是唯一的,并且同一个routing-instance里的多个PE上RT要相同配置PE-CE之间的静态路由,这里要注意,在PE-CE之间为以太网连接的情况下,一定要加一个特定的静态路由,目的地址为PE-CE之间的互联的IP子网,下一跳地址为对端CE的接口IP地址配置PE-CE之间的OSPF路由,这里要注意,一定要加一个特定的POLICY,目的是为了将从对端PE学到的VPN路由注入PE-CE之间运行的OSPF协议,使得两端的CE互相能学到对方的路由。
Juniper命令

Juniper 防火墙的策略配置
• 在Juniper设备中策略是一个重点,因为安全设备基本上都是基于策略的管理和运行,下面就Juniper的如何配置进行 简单的说明. 在Juniper防火墙中,区域是一个比较重要的感念,一般的Juniper设备都设置了Untrust,Trust和DMZ三个区域,也可 以根据实际的需要自行定义区域,比如电信行业经常的BOSS,OA区域。 具体的使用命令: netscreenisg1000->set zone id 1000 "boss" netscreenisg1000->set zone id 1001 "oa" 然后使用命令讲相关的防火墙接口加入Zone中,具体的命令:netscreenisg1000-> set interface "ethernet2/4" zone "boss" netscreenisg1000-> set interface "ethernet2/5" zone "oa" 并且在接口上配置相关的IP地址: netscreeenisg1000-> set interface ethernet2/4 ip 10.10.161.14/25 set interface ethernet2/4 route set interface ethernet2/5 ip 192.168.19.126/28 set interface ethernet2/5 nat 然后就是需要建立MIP/VIP. 比如需要建立一个MIP,私网地址10.10.81.54,公网地址10.10.161.54, 图形界面使用比较简单,比如ethernet1/1 是一个untrust区域的接口地址。 netscreeenisg1000->set policy id 22 from "Untrust" to "Trust" "Any" "MIP(10.10.161.31)" "ANY" permit log netscreeenisg1000->set policy id 19 from "Untrust" to "Trust" "Any" "MIP(10.10.161.105)" "HTTP" permit log 关于policy就写这么多,关于MIP的是使用后面会继续手写。
Juniper基础配置命令
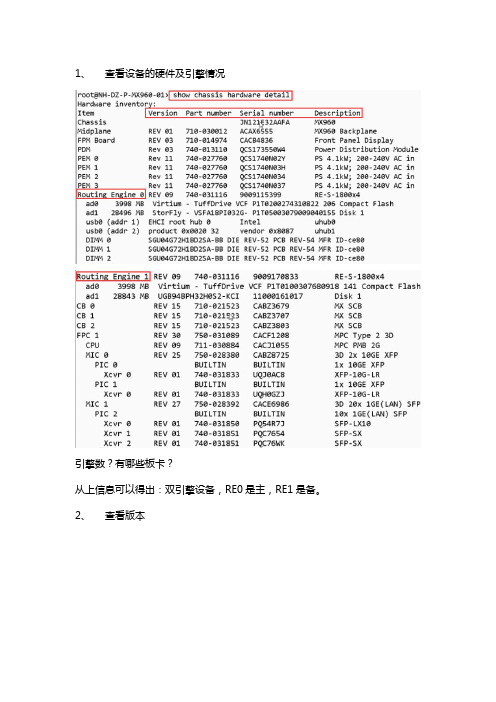
1、查看设备的硬件及引擎情况引擎数?有哪些板卡?从上信息可以得出:双引擎设备,RE0是主,RE1是备。
2、查看版本从上可看出:re0的版本是【12.3R4.6】re1的版本是【12.3R4.6】3、引擎切换4、查看当前引擎运行状态设备配置管理Juniper的配置存在2个地方:第一个:其中,juniper.conf.gz是当前的配置第二个:可以查看文件的实际配置内容:查看全局配置:或查看接口查看接口匹配信息查看路由协议信息或查看系统方面的信息查看之前的历史配置信息查看运行的文件回滚载入之前的某一个配置文件批量导入配置命令:带外管理口配置:set groups re0 interfaces fxp0 unit 0 family inet address 172.18.18.30/24set system time-zone Asia/Shanghaiset system root-authentication encrypted-password "$5$hmy2W7ar$TR/KP7qIckZ37QbfzSKJWpFW1QS70m1zAPQCsK4jth0" set system login user lab uid 2000set system login user lab class super-userset system login user lab authentication encrypted-password "$5$.Us1Dtb0$dIi5e/6/xp3IAUS/EXkntfTk3fDqESpZBNBLxrWVLHB"set system services ftpset system services sshset system services telnetset system syslog user * any emergencyset system syslog file messages any noticeset system syslog file messages authorization infoset system syslog file interactive-commands interactive-commands anyset logical-systems vr101set logical-systems vr102set interfaces ge-2/0/0 description link_to_Serv1set interfaces ge-2/0/0 unit 0 family inet address 11.1.1.1/24 deactivate interfaces ge-2/0/0 unit 0set interfaces ge-2/0/1 description link_to_Serv2set interfaces ge-2/0/1 unit 0 family inet address 11.1.2.1/24 deactivate interfaces ge-2/0/1 unit 0set routing-options static route 172.0.0.0/8 next-hop 172.18.18.254set routing-options static route 10.0.0.0/8 next-hop 172.18.18.254show configuration | display set |match traceoptionshow bgp summaryshow configuration | display set | match 100.125.154.9set protocols bgp group HZ-OOB2IN75 neighbor 100.125.154.9 export rpFW-ADCN2FW-POPshow bgp neighborshow route forwarding-tableshow configuration interfacesshow configuration policy-optionsshow configuration interfaces gr-0/0/0show configuration protocols bgpping 100.125.154.126 count 100ping 14.143.27.242 rapid count 300show configuration | display set | compare rollback 5 show version detail no-forwardingshow system core-dumps no-forwardingshow chassis alarms no-forwardingshow chassis hardware detail no-forwarding show system processes extensive no-forwarding show pfe statistics errorshow pfe statistics trafficshow chassis routing-engine no-forwarding show chassis environment no-forwarding show chassis firmware no-forwardingshow chassis fpc detailshow system boot-messages no-forwarding show system storage no-forwardingshow system virtual-memory no-forwardingshow system buffer no-forwardingshow system queues no-forwardingshow system statistics no-forwardingshow configuration | except SECRET-DATA | display omit show interfaces extensive no-forwardingshow network-access aaa statistics accountingshow route forwarding-table summaryshow ppp statistics extensiveshow accounting server statisticsshow system resource-monitor summaryshow shm-ipc statisticsshow interfaces diagnostics optics et-0/1/1。
Juniper路由器配置命令介绍

Juniper路由器配置命令介绍Juniper路由器配置命令介绍目录1、简介2、配置基础命令2.1 进入操作模式2.2 配置系统参数2.3 设置管理接口2.4 配置路由表3、高级配置命令3.1 OSPF配置3.2 BGP配置3.3 VRF配置3.4 MPLS配置4、安全配置命令4.1 配置防火墙4.2 配置安全策略4.3 配置VPN4.4 配置ACL5、故障排查命令5.1 显示命令5.2 路由故障排查5.3 硬件故障排查5.4 访问控制故障排查6、性能优化命令6.1 接口配置6.2 QoS配置6.3 缓存配置6.4 动态路由配置1、简介Juniper路由器是一种支持多种网络协议的高性能路由器。
本文档介绍了Juniper路由器的配置命令,并根据功能分类进行了细化。
2、配置基础命令2.1 进入操作模式- login:登录路由器- cli:进入命令行操作模式- configure:进入配置操作模式2.2 配置系统参数- set system hostname <hostname>:设置路由器主机名- set system domn-name <domn-name>:设置路由器域名- set system time-zone <time-zone>:设置时区- set system name-server <ip-address>:设置DNS服务器2.3 设置管理接口- set interfaces <interface> unit <unit> family inet address <ip-address/mask>:配置管理接口的IP地质- set interfaces <interface> unit <unit> family inet address dhcp:使用DHCP分配管理接口的IP地质2.4 配置路由表- set routing-options static route <destination> next-hop <next-hop>:配置静态路由- set routing-options router-id <id>:配置路由器ID- set protocols ospf area <area> interface <interface>:配置接口与OSPF区域的关联3、高级配置命令3.1 OSPF配置- set protocols ospf area <area> interface <interface>:配置接口与OSPF区域的关联- show ospf neighbor:显示OSPF邻居信息- show ospf route:显示OSPF路由表3.2 BGP配置- set protocols bgp group <group-name> neighbor<neighbor-address>:配置BGP邻居- set protocols bgp group <group-name> family <family>:配置BGP邻居的地质族- show bgp neighbor:显示BGP邻居信息- show bgp summary:显示BGP邻居摘要信息3.3 VRF配置- set routing-instances <instance-name> interface<interface>:配置接口与VRF的关联- set routing-instances <instance-name> routing-options static route <destination> next-hop <next-hop>:配置静态路由3.4 MPLS配置- set protocols mpls interface <interface>:启用接口的MPLS功能- set protocols mpls label-switched-path <LSP-name> to <destination-address> : 配置LSP的路径4、安全配置命令4.1 配置防火墙- set security policies from-zone <from-zone> to-zone <to-zone> policy <policy-name> match <match-conditions> then permit/deny:配置安全策略4.2 配置安全策略- set security zones security-zone <zone-name> address-book address <address-name> <ip-address>:配置地质对象- set security zones security-zone <zone-name> host-inbound-traffic system-services <services>:配置允许进入防火墙的服务4.3 配置VPN- set security ike proposal <proposal-name> authentication-method <method>:配置IKE提议- set security ike gateway <gateway-name> ike-policy <policy-name>:配置IKE网关- set security ipsec vpn <vpn-name> bind-interface<interface>:绑定VPN到接口4.4 配置ACL- set firewall family inet filter <filter-name> term <term-name> from protocol <protocol>:配置ACL规则- set firewall family inet filter <filter-name> term <term-name> then accept/discard:配置ACL规则动作5、故障排查命令5.1 显示命令- show interfaces <interface> detl:显示接口详细信息- show route <destination> : 显示路由信息- show chassis hardware:显示硬件信息5.2 路由故障排查- show bgp summary:显示BGP邻居摘要信息- show ospf neighbor:显示OSPF邻居信息- show route protocol <protocol>:显示指定协议的路由5.3 硬件故障排查- show chassis hardware:显示硬件信息- show log messages:显示系统日志消息- request support information:收集支持信息文件5.4 访问控制故障排查- show security policies from-zone <from-zone> to-zone <to-zone> policy <policy-name>:显示安全策略信息- show security zones interfaces:显示接口与安全域的关联信息6、性能优化命令6.1 接口配置- set interfaces <interface> mtu <mtu-size>:设置接口MTU大小- set interfaces <interface> description <description>:设置接口描述6.2 QoS配置- set class-of-service interfaces <interface> unit<unit> scheduler-map <map-name>:为接口配置调度器映射- set class-of-service scheduler-maps <map-name> forwarding-class <forwarding-class> scheduler <scheduler-name>:配置调度器映射6.3 缓存配置- set forwarding-options cache hit-cache-size <size>:设置缓存大小- set forwarding-options cache timeout <timeout-value>:设置缓存超时时间6.4 动态路由配置- set protocols ospf area <area> interface <interface> passive:将接口设置为OSPF被动接口- set routing-instances <instance-name> interface <interface> passive:将接口设置为VRF被动接口附件:无法律名词及注释:无。
juniper设备命令

juniper设备命令set system root-authentication plain-text-password 设置root 密码set system login user jianglong class super-user authentication plain-text-password 设置超级用户及密码set system services telnet 开启telnetcommit 提交生效show interfaces diagnostics optics xe-0/0/31 查看端口模块信息show chassis pic fpc-slot 0 pic-slot 0 查看模块信息show system uptime 查看系统时间及设备启动时间show log link-status 查看系统日志show | display set 查看配置show | compare 未保存之前查看做过的配置show chassis hardware 查看模块信息包括SN号show class-of-service 查看端口限速set class-of-service interfaces xe-0/0/5 shaping-rate 2g 端口限速deactivate interfaces xe-1/1/0 unit 3027 (保留端口配置,但使配置失效)activate interfaces xe-1/1/0 unit 3027(使失效的端口配置生效)两台设备之间传输vlan一、设备端口建立相关vlanset interfaces xe-1/1/0 unit 3033 vlan-id 3033 family inet address 118.186.208.141/30 (在xe1/1/0端口建立vlan3033,配IP:118.186.208.141/30)二、建立好在两段设备和传输设备上建立好vlan后在4550交换机上做传输策略show protocols l2circuit (查看传输策略)set protocols l2circuit neighbor 118.186.247.99 interface xe-0/0/24.3033 virtual-circuit-id 13033 encapsulation-typeethernet-vlan (从本端设备的xe0/0/24口将vlan3033传到118.186.247.99这个设备,并定义策略。
Juniper路由器常用命令表
配置端口
#edit routing-options
静态路由配 置
#set stati c route 61.130.49.0/24 静态路由配 置
next-hop 202.96.113.52
#commi t #commit confirmed ? #top up exit /quit
termi nal no monit or monitor stop
Ciscocomma nd
查看设备信 息命 show versi on
令
Show clock
Juniper comma nd
>show versi on
>show system uptime
show inventory show processes cpu
>show confi g show route show bgp summa ry
在用户模式下显示配置 查看路由表
show route receive-protocol bgp neigh
show ospf neigh bor
诊断工具
int erfac e
Ciscocomma nd
displays the status of
interfacesconfigured for IP
查看配置信 息
show ip route
show ip bgp
summa ry
show ip bgp
neighbors neigh
received-route s
show ip ospf
juniper 常用配置命令

1.〉模式进入#模式:configure2.配置静态路由:>set route 10.1.10.0/24 int e1 gateway 10.1.1.2543.查看接口的配置:>get interface4.查看静态路由:>get route >get route ip 10.1.10.55.Ping 测试:>ping 10.1.10.56.Traceroute 测试:>trace 10.1.10.57.配置接口的模式(nat和route):>set interface e1 nat8.保存:>save9.配置文件备份:>save config from flash to tftp 1.1.7.250 15june03.cfg10.配置文件恢复:>save config from tftp 1.1.3.250 15june03.cfg to flash11.IOS备份:>save software from flash to tftp 1.1.7.250 ns208image.bin12.IOS升级:>save software from tftp 1.1.7.250 newimage to flash13.透明模式的配置:A.建立2层的安全区(在没有使用缺省安全区的情况下):>set zonename L2-Demo L2 1 // set zone name <name> L2 <vlan_tag>B.分配接口给2层安全区:>set int e3 zone L2-DemoC.为vlan1配置管理地址:>set int vlan1 manage-ip 1.1.7.100/24a.配置IP地址:>set int vlan1 ip 1.1.7.1/24b.选择广播的方法:>set vlan1 broadcast floodc.配置管理服务:(允许所有的管理服务)>set int vlan1 manageD.(可选项)配置每个安全区的管理服务:>set zone v1-dmz manage webE.在不同的安全区之间配置策略:14.透明模式的检查工具:>get int>get arp ,>get mac-learn,>get session15.透明模式是一个非常灵活的防火墙部署解决方案,可以快速实现防火墙和VPN的功能,不需要修改网络结构,建立虚拟地址(NAT),就可以实现访问控制。
JUNIPER路由器中常用命令总结

JUNIPER路由器中常⽤命令总结前些⽇⼦认真看了⼀下Juniper路由器的⼀些命令。
在这⾥总结⼀下。
⽅便以后使⽤Juniper路由器的命令主要分为两个部分,⼀个是operational,主要是复杂查看⽬前⽹络的配置情况(只能查看,不能修改。
感觉权限⽐较低);另⼀个是configuration,主要⽤来查看和修改配置(感觉权限⾼⼀些)。
刚进⼊到Juniper路由器时,默认进⼊的是operation,输⼊edit命令之后,就进⼊到了[edit]⽬录下,也就是进⼊了configuration。
基础配置命令(如未说明则在[edit]⽬录下)1、配置主机名字:set system host-name router12、配置域名: set system domain-name 3、配置fxp0接⼝(以太⽹中通过这个接⼝进⾏路由器的配置)。
Set interfaces fxp0 unit 0 family inet address 192.168.15.1/2 44、配置备份路由器:set system backup-router 192.168.15.25、配置DNS服务器:set system name-server 192.168.15.36、配置root⽤户的密码:set system root-authentication plain-text-password(密码中不可以全是⼤写、全是⼩写、全是数字)7、设置ntp服务器: set system ntp server 192.168.2.28、提交修改:commit9、查看提交是否合法: commit check10、在当天特定时间进⾏提交 commit at 22:4511、在特定⽇期的特定时间提交: commit at “2005-02-26 10:45”12、取消commit的操作 clear system commit13、为了避免提交带来意外的损害采⽤:commit confirmed,会在10分钟以后⾃动回滚14、与14相同,但在⼀分钟以后⾃动回滚:commit confirmed 115、提交信息,并同步到备份路由器上: commit synchronize配置服务:1、设置ssh服务:set system services ssh2、配置ftp服务: set system services ftp3、删除ftp服务: delete system services ftp权限设置:1、设置root⽤户ssh登录的密码:set system root-authentication ssh password2、禁⽌root⽤户使⽤ssh登录:[edit system ] set services ssh root-login deny3、设置密码要求:[edit system login] set password maximun-length 20 set password minimum-length 8 set password mi nimum-changes 24、设置密码加密算法:set system login password formate md55、查看⾃⼰的权限,以及可以设置的权限: show cli authorization进⼊与退出命令:1、Edit2、修改root的配置:configure3、避免多⼈修改导致设置丢失采⽤ configure exclusive4、查看⽬前修改区域有谁在线:[edit]status(只能看见⽐你先登录的⼈,后⾯登录的信息看不见)5、强制要求别⼈下线:request system logout user mike6、进⼊到根⽬录 top7、退出configuration 模块:quit8、退出configuration模块:exit configuration-mode9、提交并退出:commit and-quit10、退出当前⽬录:exit11、进⼊到某⽬录 edit ⽬录名字查看命令:1、查看当前⽬录地下的设置 [edit]show2、查看你设置的命令 show | display set3、查看你新增的命令 show | compare(+表⽰你增加的命令,-表⽰你删除的命令。
Juniper防火墙基本命令

Juniper防火墙基本命令常用查看命令Get int查看接口配置信息Get int ethx/x查看指定接口配置信息Get mip查看映射ip关系Get route查看路由表Get policy id x查看指定策略Get nsrp查看nsrp信息,后可接参数查看具体vsd组、端口监控设置等Get per cpu de查看cpu利用率信息Get per sessionde查看每秒新建会话信息Get session查看当前会话信息,后可匹配源地址、源端口、目的地址、目的端口、协议等选项Get session info查看当前会话数量Get system查看系统信息,包括当前os版本,接口信息,设备运行时间等Get chaiss查看设备及板卡序列号,查看设备运行温度Get counter stat查看所有接口计数信息Get counter stat ethx/x查看指定接口计数信息Get counter flow zone trust/untrust查看指定区域数据流信息Get counter screen zone untrust/trust查看指定区域攻击防护统计信息Get tech-support查看设备状态命令集,一般在出现故障时,收集该信息寻求JTAC支持常用设置命令Set int ethx/x zone trust/untrust/dmz/ha配置指定接口进入指定区域(trust/untrust/dmz/ha等)Set int ethx/x ip x.x.x.x/xx配置指定接口ip地址Set int ethx/x manage配置指定接口管理选项,打开所有管理选项Set int ethx/x manage web/telnet/ssl/ssh配置指定接口指定管理选项Set int ethx/x phy full 100mb配置指定接口速率及双工方式Set int ethx/x phy link-down配置指定接口shutdownSet nsrp vsd id 0 monitor interface ethx/x配置ha监控端口,如此端口断开,则设备发生主/备切换Exec nsrp vsd 0 mode backup手工进行设备主/备切换,在当前的主设备上执行set route 0.0.0.0/0 interface ethernet1/3 gateway 222.92.116.33配置路由,需同时指定下一跳接口及ip地址所有set命令,都可以通过unset命令来取消,相当于cisco中的no所有命令都可以通过“TAB”键进行命令补全,通过“?”来查看后续支持的命令防火墙基本配置create account [admin | user]<username> 回车输入密码:再次输入密码:configure account admin 回车输入密码:再次输入密码:2.port配置config ports <portlist> auto off{speed [10 | 100 | 1000]} duplex [half | full] auto off3.Vlan配置无论是核心还是接入层,都要先创建三个Vlan,并且将所有归于Default Vlan的端口删除:config vlan default del port allcreate vlan Servercreate vlan Usercreate vlan Manger定义802.1q标记config vlan Server tag 10config vlan User tag 20config vlan Manger tag 30设定Vlan网关地址:config vlan Server ipa 192.168.41.1/24config vlan User ipa 192.168.40.1/24config vlan Manger ipa 192.168.*.*/24Enable ipforwarding 启用ip路由转发,即vlan间路由Trunk 配置config vlan Server add port 1-3 tconfig vlan User add port 1-3 tconfig vlan manger add port 1-3 t4.VRRP配置enable vrrpconfigure vrrp add vlan UserVlanconfigure vrrp vlan UserVlan add master vrid 10192.168.6.254configure vrrp vlan UserVlan authentication simple-passwordextremeconfigure vrrp vlan UserVlan vrid 10 priority 200configure vrrp vlan UserVlan vrid 10 advertisement-interval15configure vrrp vlan UserVlan vrid 10 preempt5.端口镜像配置首先将端口从VLAN中删除enable mirroring to port 3 #选择3作为镜像口config mirroring add port 1 #把端口1的流量发送到3config mirroring add port 1 vlan default #把1和vlandefault的流量都发送到36.port-channel配置enable sharing <port> grouping<portlist> {port-based |address-based | round-robin} show port sharing //查看配置7.stp配置enable stpd //启动生成树create stpd stp-name //创建一个生成树configure stpd <spanning treename> add vlan <vlanname> {ports<portlist> [dot1d | emistp |pvst-plus]}configure stpd stpd1 priority 16384configure vlan marketing add ports 2-3 stpd stpd1 emistp8.DHCP 中继配置enable bootprelayconfig bootprelay add <dhcp serverip>9.NAT配置Enable nat #启用natStatic NAT Rule Exampleconfig nat add out_vlan_1 map source 192.168.1.12/32 to216.52.8.32/32Dynamic NAT Rule Exampleconfig nat add out_vlan_1 map source 192.168.1.0/24 to216.52.8.1 - 216.52.8.31 Portmap NAT Rule Exampleconfig nat add out_vlan_2 map source 192.168.2.0/25 to216.52.8.32 /28 both portmap Portmap Min-Max Exampleconfig nat add out_vlan_2 map source 192.168.2.128/25 to216.52.8.64/28 tcp portmap 1024 - 819210.OSPF配置enable ospf 启用OSPF进程create ospf area <area identifier>创建OSPF区域configure ospf routerid [automatic |<routerid>] 配置Routeridconfigure ospf add vlan [<vlanname> | all] area <areaidentifier> {passive}把某个vlan加到某个Area中去,相当于Cisco中的network的作用configure ospf area <areaidentifier> add range<ipaddress><mask> [advertise | noadvertise]{type-3 | type-7} 把某个网段加到某个Area中去,相当于Cisco中的network的作用configure ospf vlan <vlan name>neighbor add <ipaddress>OSPF中路由重发布配置enable ospf export direct [cost<metric> [ase-type-1 | ase-type-2]{tag <number>}|<route map>]enable ospf export static [cost<metric> [ase-type-1 | ase-type-2]{tag <number>}|<route map>]enable ospf originate-default {always} cost<metric> [ase-type-1 | ase-type-2]{tag<number>}enable ospf originate-router-id11.SNMP配置enable snmp accessenable snmp trapscreate access-profile <accessprofile> type [ipaddress | vlan]config snmp access-profile readonly[<access_profile> |none]配置snmp的只读访问列表,none是去除config snmp access-profile readwrite[<access_profile> | none]这是控制读写控制config snmp add trapreceiver <ipaddress> {port<udp_port>}community<communitystring> {from<source ip address>} 配置snmp接收host和团体字符串12.安全配置disable ip-option loose-source-routedisable ip-option strict-source-routedisable ip-option record-routedisable ip-option record-timestampdisable ipforwarding broadcastdisable udp-echo-serverdisable irdp vlan <vlan name>disable icmp redirectdisable web 关闭web方式访问交换机enable cpu-dos-protect13.Access-Lists配置create access-list icmp destination sourcecreate access-list ip destination source portscreate access-list tcp destination source portscreate access-list udp destination source ports14.默认路由配置config iproute add default<gateway>15.恢复出厂值,但不包括用户改的时间和用户帐号信息unconfig switch {all}16.检查配置show versionshow configshow sessionshow management 查看管理信息,以及snmp信息show bannershow ports configurationshow ports utilization ?show memory/show cpu-monitoringshow ospfshow access-list {<name> | port<portlist>}show access-list-monitorshow ospf area <areaidentifier>show ospf area detailshow ospf ase-summaryshow ospf interfaces {vlan <vlanname> | area <areaidentifier>}unconfigure ospf {vlan <vlan name>| area <area identifier>}switchshow switchshow configshow diagshow iparpshow iprouteshow ipstatshow logshow tech allshow version detail17.备份和升级软件download image [<hostname> |<ipaddress>]<filename> {primary | secondary} upload image [<hostname> |<ipaddress>]<filename> {primary | secondary}use image [primary | secondary]18.密码恢复。
Juniper路由器常用命令表

Juniper路由器常用命令表Juniper路由器常用命令表:1·登录与基本操作1·1 连接与登录1·2 登录后的基本操作1·3 退出登录2·系统操作与管理2·1 系统状态与信息查看2·2 系统配置与修改2·3 系统重启与关机2·4 用户管理3·接口配置3·1 物理接口3·1·1 接口状态查看与设置3·1·2 接口带宽与速率限制设置3·2 逻辑接口3·2·1 VLAN接口配置3·2·2 Loopback接口配置4·路由配置4·1 静态路由配置4·2 动态路由配置4·2·1 OSPF配置4·2·2 BGP配置4·2·3 RIP配置5·安全配置5·1 防火墙配置5·1·1 基本防火墙规则配置5·1·2 会话表与连接追踪配置5·1·3 防火墙日志配置5·2 虚拟专用网络(VPN)配置5·2·1 IPsec VPN配置5·2·2 SSL VPN配置6·网络服务配置6·1 DHCP服务配置6·2 DNS服务配置6·3 NAT配置7·系统诊断与故障处理7·1 接口故障排查7·2 路由故障排查7·3 防火墙故障排查7·4 网络连通性测试7·5 系统日志与告警查看附:本文档涉及附件附件:无注释:本文所涉及的法律名词及注释1·路由器:一种计算机网络设备,用于在局域网或广域网之间转发数据包。
2·VLAN:虚拟局域网,将一组逻辑上的设备或用户分组,形成一个局域网。
juniper防火墙常用命令

JUNIPER防火墙常用命令常用查看命令Get int查看接口配置信息Get int ethx/x查看指定接口配置信息Get mip查看映射ip关系Get route 查看路由表Get policy id x 查看指定策略Get nsrp查看nsrp信息,后可接参数查看具体vsd组、端口监控设置等Get per cpu de 查看cpu利用率信息Get per session de 查看每秒新建会话信息Get session查看当前会话信息,后可匹配源地址、源端口、目的地址、目的端口、协议等选项Get session info 查看当前会话数量Get system查看系统信息,包括当前os版本,接口信息,设备运行时间等Get chaiss查看设备及板卡序列号,查看设备运行温度Get counter stat 查看所有接口计数信息Get counter stat ethx/x 查看指定接口计数信息Get counter flow zone trust/untrust 查看指定区域数据流信息Get counter screen zone untrust/trust 查看指定区域攻击防护统计信息Get tech-support查看设备状态命令集,一般在出现故障时,收集该信息寻求JTAC支持常用设置命令Set int ethx/x zone trust/untrust/dmz/ha配置指定接口进入指定区域(trust/untrust/dmz/ha等)Set int ethx/x ip x.x.x.x/xx 配置指定接口ip地址Set int ethx/x manage配置指定接口管理选项,打开所有管理选项Set int ethx/x manage web/telnet/ssl/ssh 配置指定接口指定管理选项Set int ethx/x phy full 100mb 配置指定接口速率及双工方式Set int ethx/x phy link-down 配置指定接口shutdownSet nsrp vsd id 0 monitor interface ethx/x配置ha监控端口,如此端口断开,则设备发生主/备切换Exec nsrp vsd 0 mode backup手工进行设备主/备切换,在当前的主设备上执行set route 0.0.0.0/0 interface ethernet1/3 gateway 222.92.116.33 配置路由,需同时指定下一跳接口及ip地址所有set命令,都可以通过unset命令来取消,相当于cisco中的no所有命令都可以通过“TAB”键进行命令补全,通过“?”来查看后续支持的命令。
juniper SRX 常用命令

juniper SRX 常用命令rollbackset interfaceset routing-options staticset system login user admin class super-userset system login user admin authentication plain-text-password 输入密码set system services sshset security zones security-zone untrust host-inbound-traffic system-services ssh/pingset security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services ssh /telnet/pingset security zones security-zone trust host-inbound-traffic system-services ssh /telnet /pingset security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services ssh /telnet/pingset security zones security-zone untrust interfaces ge-0/0/0 (不定义区域,无法配置NAT)set security zones security-zone trust interfaces ge-0/0/1###### set security zones security-zone trust interfaces ge-0/0/1 ???###### set interfaces interface-range interfaces-trust member ge-0/0/1 ????##################################################静态NAT:set security nat source rule-set interface-nat from zone trustset security nat source rule-set interface-nat to zone untrustset security nat source rule-set interface-nat rule rule1 match source-address 192.168.0.0/23 set security nat source rule-set interface-nat rule rule1 match destination-address 0.0.0.0/0 set security nat source rule-set interface-nat rule rule1 then source-nat interfaceset security zones security-zone trust address-book address 192 192.168.0.0/23set security zones security-zone trust address-book address-set 192nat address 192set security policies from-zone trust to-zone untrust policy 192nat match source-address anyset security policies from-zone trust to-zone untrust policy 192nat match destination-address any set security policies from-zone trust to-zone untrust policy 192nat match application anyset security policies from-zone trust to-zone untrust policy 192nat then permit#######################################################强制172.16.0.12走150出去(默认走物理接口146出去)set security nat source pool pool-1 address 121.9.255.112set security nat source rule-set sou-nat rule rule-mail match source-address 172.16.0.12/32set security nat source rule-set sou-nat rule rule-mail match destination-address 0.0.0.0/0set security nat source rule-set sou-nat rule rule-mail then source-nat pool pool-1insert security nat source rule-set sou-nat rule rule-mail before rule rule-sou##########################################################端口映射静态PAT: 从外到内set security nat proxy-arp interface ge-0/0/0.0 address 10.1.1.100/24set security nat proxy-arp interface ge-0/0/3.0 address 10.1.2.100/24set security nat destination pool dnat-pool-1 address 192.168.0.9/32set security nat destination pool dnat-pool-2 address 172.16.0.12/32set security nat destination rule-set dst-nat from zone untrustset security nat destination rule-set dst-nat rule rule3 match destination-address 10.1.1.100/24 set security nat destination rule-set dst-nat rule rule3 match destination-port 21set security nat destination rule-set dst-nat rule rule3 then destination-nat pool dnat-pool-1set security nat destination rule-set dst-nat rule rule2 match destination-address 10.1.2.100/24 set security nat destination rule-set dst-nat rule rule2 match destination-port 443set security nat destination rule-set dst-nat rule rule2 then destination-nat pool dnat-pool-2set security zones security-zone trust address-book address ftpserver 192.168.0.9set security zones security-zone trust address-book address mailserver 172.16.0.12set security zones security-zone trust address-book address-set servergroup address ftpserver set security zones security-zone trust address-book address-set servergroup address mailserverset security policies from-zone untrust to-zone trust policy static-nat match source-address any destination-address servergroup application junos-httpset security policies from-zone untrust to-zone trust policy static-nat match application junos-pop3set security policies from-zone untrust to-zone trust policy static-nat then permitset applications application 443 protocol tcpset applications application 443 destination-port 443##############################################################set security nat source rule-set sou-nat from zone trustset security nat source rule-set sou-nat to zone untrustset security nat source rule-set sou-nat rule rule-mail match source-address 172.16.0.30/32set security nat source rule-set sou-nat rule rule-mail match destination-address 0.0.0.0/0set security nat source rule-set sou-nat rule rule-mail then source-nat pool pool-1##############################################################管理端口:set system services web-management httpsset system services web-management httpset system services web-management http port 8084set system services web-management http interface allset system services web-management https system-generated-certificateset system services web-management http interface ge-0/0/0.0set system services web-management https interface ge-0/0/0.0###########################################################################定义端口地址池XXX_group:set applications application smtp_25 destination-port 25 protocol tcpset applications application pop3_110 destination-port 110 protocol tcpset applications application exchange_135 destination-port 135 protocol tcpset applications application smtp_465 destination-port 465 protocol tcpset applications application imap_993 destination-port 993 protocol tcpset applications application pop3_995 destination-port 995 protocol tcpset applications application-set mail_port_group application smtp_25set applications application-set XXX_group application smtpset applications application-set XXX_group application pop3引用XXX_group:set security policies from-zone untrust to-zone trust policy mail-policy match application XXX_group############################################################################## 反向静态NAT:从外到内set security nat static rule-set mail-static-nat from zone untrustset security nat static rule-set mail-static-nat rule mail1 match destination-address 121.9.255.150/32set security nat static rule-set mail-static-nat rule mail1 then static-nat prefix 172.16.0.12/32返回的安全Policy:set security policies from-zone untrust to-zone trust policy mail-policy match source-address any set security policies from-zone untrust to-zone trust policy mail-policy match destination-address Mail_serset security policies from-zone untrust to-zone trust policy mail-policy match application any(XXX_group)set security policies from-zone untrust to-zone trust policy mail-policy then permit插入insert Policy:set security zones security-zone trust address-book address deny_172 172.16.0.155set security policies from-zone trust to-zone untrust policy deny_172 match source-address deny_172set security policies from-zone trust to-zone untrust policy deny_172 match destination-address anyset security policies from-zone trust to-zone untrust policy deny_172 match application anyset security policies from-zone trust to-zone untrust policy deny_172 then denyinsert security policies from-zone trust to-zone untrust policy deny_172 before policy Trust2Utrust (Trust2Utrust允许上公网策略)#####################################################禁止192网段上网,只允许192.168.0.2,192.168.0.121上网set security zones security-zone trust address-book address deny_192 192.168.0.0/23set security zones security-zone trust address-book address permit_host_2 192.168.0.2/32set security zones security-zone trust address-book address permit_host_121 192.168.0.121/32 set security zones security-zone trust address-book address-set permit_192_online address FTP_serset security zones security-zone trust address-book address-set permit_192_online address permit_host_2set security zones security-zone trust address-book address-set permit_192_online address permit_host_121set security zones security-zone trust address-book address-set deny_192_online address deny_192返回的安全Policy:set security policies from-zone trust to-zone untrust policy permit_192_online match source-address permit_192_onlineset security policies from-zone trust to-zone untrust policy permit_192_online match destination-address anyset security policies from-zone trust to-zone untrust policy permit_192_online match application anyset security policies from-zone trust to-zone untrust policy permit_192_online then permitset security policies from-zone trust to-zone untrust policy deny_192_online match source-address deny_192_onlineset security policies from-zone trust to-zone untrust policy deny_192_online match destination-address anyset security policies from-zone trust to-zone untrust policy deny_192_online match application anyset security policies from-zone trust to-zone untrust policy deny_192_online then denyinsert security policies from-zone trust to-zone untrust policy permit_192_online before policy deny_172insert security policies from-zone trust to-zone untrust policy deny_192_online before policy deny_172###########################################################################配置WEB管理set system host-name Testset system root-authentication encrypted-password "$1$XKPZUqwc$/WdxM1Cc1GAB8gJ0nNCOt."set system name-server 202.96.128.166set system name-server 202.96.128.86set system login user admin uid 2001set system login user admin class super-userset system login user admin authentication encrypted-password HJuZerSULPfkAset system services sshset system services web-management http port 8084set system services web-management http interface allset system services web-management http interface ge-0/0/0.0set system services web-management https system-generated-certificateset system services web-management https interface ge-0/0/0.0set interfaces ge-0/0/0 unit 0 family inet address 192.168.8.125/24set interfaces ge-0/0/1 unit 0 family inet address 192.168.1.1/24set security zones security-zone untrust host-inbound-traffic system-services httpset security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services http###########################################################################开放Untrust服务端口set security zones security-zone untrust interfaces ge-0/0/0.0set security zones security-zone untrust host-inbound-traffic system-services allset security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services allset security zones security-zone trust interfaces ge-0/0/1.0set security zones security-zone trust host-inbound-traffic system-services allset security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services all配置默认路由+NATset routing-options static route 0.0.0.0/0 next-hop 192.168.8.1set security nat source rule-set sou-nat from zone trustset security nat source rule-set sou-nat to zone untrustset security nat source rule-set sou-nat rule rule-sou match source-address 0.0.0.0/0set security nat source rule-set sou-nat rule rule-sou match destination-address 0.0.0.0/0set security nat source rule-set sou-nat rule rule-sou then source-nat interface内网放行策略:set security policies from-zone trust to-zone untrust policy in_out match source-address any set security policies from-zone trust to-zone untrust policy in_out match destination-address anyset security policies from-zone trust to-zone untrust policy in_out match application anyset security policies from-zone trust to-zone untrust policy in_out then permit########################################################################### UTM 功能中防病毒功能set security utm utm-policy test-policy anti-virus http-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus ftp upload-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus ftp download-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus smtp-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus pop3-profile junos-av-defaultsset security utm utm-policy test-policy anti-virus imap-profile junos-av-defaultsset security utm utm-policy test-policy anti-spam smtp-profile junos-as-defaultsset security utm utm-policy test-policy traffic-options sessions-per-client over-limit log-and-permitset security utm utm-policy web-policy anti-virus http-profile junos-av-defaultsset security utm utm-policy web-policy traffic-options sessions-per-client over-limit log-and-permitset security policies from-zone trust to-zone untrust policy permit_192_online match source-address permit_192_onlineset security policies from-zone trust to-zone untrust policy permit_192_online match destination-address anyset security policies from-zone trust to-zone untrust policy permit_192_online match application anyset security policies from-zone trust to-zone untrust policy permit_192_online then permit application-services utm-policy web-policyset security policies from-zone untrust to-zone trust policy mail-policy match source-address any set security policies from-zone untrust to-zone trust policy mail-policy match destination-address Mail_serset security policies from-zone untrust to-zone trust policy mail-policy match application mail_port_groupset security policies from-zone untrust to-zone trust policy mail-policy then permit application-services utm-policy test-policyset security policies from-zone untrust to-zone trust policy Ftp-Policy match source-address any set security policies from-zone untrust to-zone trust policy Ftp-Policy match destination-address FTP_serset security policies from-zone untrust to-zone trust policy Ftp-Policy match application junos-ftp set security policies from-zone untrust to-zone trust policy Ftpmservices utm-policy test-policyadmin@KDS_FW> show security utm anti-spam statistics##########################################################dynamic VPN功能配置:run show chassis routing-engine (查看CPU使用user、空闲idle)show config |dis set| match utmshow log utmd-av | lastclear log utmd-av###########################################################抓包功能配置:Could you please configure the following traceoption and send the log file.You can create the packet filter as followed#set security flow traceoption file debug#set security flow traceoption flag basic-datapath#set security flow traceoption packet-filter filter1 source-prefix <ip-address> destination-prefix<ip-address> destination-port 80#set security flow traceoption packet-filter filter2 source-prefix <ip-address> destination-prefix <ip-address> destination-port 80#committhe second one is for the return traffic.show log debugrequest system license update。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
OSPF中路由重发布配置
enable ospf export direct [cost <metric> [ase-type-1 | ase-type-2] {tag <number>} | <route map>]
show ospf
show access-list {<name> | port <portlist>}
show access-list-monitor
show ospf area <area identifier>
show ospf area detail
show ospf ase-summary
13.Access-Lists配置
create access-list icmp destination source
create access-list ip destination source ports
create access-list tcp destination source ports
6.port-channel配置
enable sharing <port> grouping <portlist> {port-based | address-based | round-robin}
show port sharing //查看配置
7.stp配置
enable stpd //启动生成树
show diag
show iparp
show iproute
show ipstat
show log
show tech all
show version detail
17.备份和升级软件
download image [<hostname> | <ipaddress>] <filename> {primary | secondary}
network的作用
configure ospf area <area identifier> add range <ipaddress> <mask> [advertise | noadvertise] {type-3 | type-7} 把某个网段加到
某个Area中去,相当于Cisco中的network的作用
configure vrrp vlan UserVlan vrid 10 preempt
5.端口镜像配置
首先将端口从VLAN中删除
enable mirroring to port 3 #选择3作为镜像口
config mirroring add port 1 #把端口1的流量发送到3
config mirroring add port 1 vlan default #把1和vlan default的流量都发送到3
收host和团体字符串
12.安全配置
disable ip-option loose-source-route
disable ip-option strict-source-route
disable ip-option record-route
disable ip-option record-timestamp
10.OSPF配置
enable ospf 启用OSPF进程
create ospf area <area identifier> 创建OSPF区域
configure ospf routerid [automatic | <routerid>] 配置Routerid
configure ospf add vlan [<vlan name> | all] area <area identifier> {passive} 把某个vlan加到某个Area中去,相当于Cisco中的
create access-list udp destination source ports
14.默认路由配置
config iproute add default <gateway>
15.恢复出厂值,但不包括用户改的时间和用户帐号信息
unconfig switch {all}
16.检查配置
disable ipforwarding broadcast
disable udp-echo-server
disable irdp vlan <vlan name>
disable icmp redirect
disable web 关闭web方式访问交换机
enable cpu-dos-protect
show version
show config
show session
show management 查看管理信息,以及snmp信息
show banner
show ports configuration
show ports utilization ?
show memory/show cpu-monitoring
config vlan Server tag 10
config vlan User tag 20
config vlan Manger tag 30
设定Vlan网关地址:
config vlan Server ipa 192.168.41.1/24
config vlan User ipa 192.168.40.1/24
show ospf interfaces {vlan <vlan name> | area <area identifier>}
unconfigure ospf {vlan <vlan name> | area <area identifier>}
【2】switch
show itch
show config
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
create stpd stp-name //创建一个生成树
configure stpd <spanning tree name> add vlan <vlan name> {ports <portlist> [dot1d | emistp | pvst-plus]}
configure stpd stpd1 priority 16384
enable ospf export static [cost <metric> [ase-type-1 | ase-type-2] {tag <number>} | <route map>]
enable ospf originate-default {always} cost <metric> [ase-type-1 | ase-type-2] {tag <number>}
1.用户名和密码配置
create account [admin | user] <username> 回车
输入密码:
再次输入密码:
configure account admin 回车
输入密码:
再次输入密码:
2.port配置
config ports <portlist> auto off {speed [10 | 100 | 1000]} duplex [half | full] auto off
config vlan Manger ipa 192.168.*.*/24
Enable ipforwarding 启用ip路由转发,即vlan间路由
Trunk 配置
config vlan Server add port 1-3 t
config vlan User add port 1-3 t
config snmp access-profile readwrite [<access_profile> | none] 这是控制读写控制
config snmp add trapreceiver <ip address> {port <udp_port>} community <communitystring> {from <source ip address>} 配置snmp接
3.Vlan配置
无论是核心还是接入层,都要先创建三个Vlan,并且将所有归于Default Vlan的端口删除:
config vlan default del port all
create vlan Server
