chap2_6_2007
918639-08-4 Reference_08_17_2013_132209

1. A Robust, Streamlined Approach to Bosutinib MonohydrateBy: Withbroe, Gregory J.; Seadeek, Chris; Girard, Kevin P.; Guinness, Steven M.; Vanderplas, Brian C.; Vaidyanathan, RajappaSource: Organic Process Research & Development, Volume: 17, Issue: 3, Pages: 500-504, Journal; Online Computer File, 2013, CODEN: OPRDFK, ISSN: 1083-6160, DOI: 10.1021/op300087rCompany/Organization: Chemical Research and Development, Pfizer Inc., Groton, CT, USA, 06340Accession Number: 2012:965310, CAN 158:340940, CAPLUSPublisher: American Chemical SocietyLanguage: EnglishAbstractThis article describes a systematic approach used to streamline the process for the isolation of bosutinib monohydrate, a promiscuous solvate former. A thorough understanding of the complex solid form landscape was garnered, and this knowledge was used to develop a process that routinely delivered the correct solid form and excellent purity at the end of the last bond-formation step, without the need for addnl. recrystn. and/or solid form conversion steps.IndexingPharmaceuticals (Section 63-5)Substances64-17-5Ethanol, miscellaneous67-56-1Methanol, miscellaneous67-64-1Acetone, miscellaneous71-23-8n-Propyl alcohol, miscellaneous71-36-3n-Butyl alcohol, miscellaneous74-87-3Chloromethane, miscellaneous75-05-8Acetonitrile, miscellaneous75-09-2Dichloromethane, miscellaneous75-85-4tert-Amyl alcohol78-93-3Methyl ethyl ketone, miscellaneous108-10-1Methyl isobutyl ketone108-21-4Isopropyl acetate108-88-3Toluene, miscellaneous109-60-4n-Propyl acetate109-86-42-Methoxyethanol109-99-9Tetrahydrofuran, miscellaneous123-86-4n-Butyl acetate123-91-11,4-Dioxane, miscellaneous141-78-6Ethyl acetate, miscellaneous142-82-5n-Heptane, miscellaneous1330-20-7Xylene, miscellaneous7732-18-5Water, miscellaneousA robust, streamlined approach to bosutinib monohydrateMiscellaneous1384969-66-7A robust, streamlined approach to bosutinib monohydrateProperties918639-08-4PA robust, streamlined approach to bosutinib monohydratePurification or recovery; Synthetic preparation; Therapeutic use; Biological study; Preparation; Uses846023-56-1A robust, streamlined approach to bosutinib monohydrateCopyright © 2013 American Chemical Society (ACS). All Rights Reserved.Reactant; Reactant or reagentSupplementary Termssolvent bosutinib monohydrate purity prepn Citations1)Sutherland, K; US 20050043537 A1 20052)Boschelli, D; J Med Chem 2004, 47, 15993)Boschelli, D; J Med Chem 2001, 44, 39654)Olszewski, J; US 20070208164 A1 20075)Feigelson, G; Unpublished results 6)Tesconi, M; WO 2007005462 20077)Brenek, S; Org Process Res Dev 2000, 4, 585.2. 3-cyanoquinoline tablet formulations and uses thereofBy: Kaul, Goldi; Chatlapalli, Ramarao; Nagi, Arwinder; Ghosh, Krishnendu Assignee: Wyeth LLC, USAPatent Information: Jan 06, 2011, WO 2011002857, A2Application: Jun 30, 2010, WO 2010-US40555Priority: Jul 02, 2009, US 2009-222537P , Jun 30, 2010, WO 2010-US40555Source: PCT Int. Appl., 70pp., Patent , 2011, CODEN: PIXXD2Accession Number: 2011:18123, CAN 154:118710, CAPLUS Language: EnglishAbstractThe present invention provides solid compns. comprising a 3-cyanoquinoline, SKI-606, and further comprisingcroscarmellose sodium, Tween, or both. Compressed tablet contained SKI-606 monohydrate (equiv. to SKI-606 free base) 69, microcryst. cellulose (Avicel PH 101TM) 6.5, Crospovidone Croscarmellose sodium 2, Poloxamer 188TM (Lutrol F-68)3, Povidone (Kollidon 25) 2 % in intragranular components and microcryst. cellulose (Avicel 1 02) 15,croscarmellose sodium 2 magnesium stearate 0.5% in extragranular components.Patent InformationPatent No.KindDateApplication No.DateWO 2011002857A2Jan 06, 2011WO 2010-US40555Jun 30, 2010WO 2011002857A3Mar 10, 2011CA 2766067A1Jan 06, 2011CA 2010-2766067Jun 30, 2010AU 2010266342A1Jan 19, 2012AU 2010-266342Jun 30, 2010EP 2448563A2May 09, 2012EP 2010-732568Jun 30, 2010KR 2012046216A May 09, 2012KR 2012-7002851Jun 30, 2010CN 102470109A May 23, 2012CN 2010-80029479Jun 30, 2010IL 217298A Feb 28, 2013IL 2010-217298Jun 30, 2010JP 2011012063A Jan 20, 2011JP 2010-151063Jul 01, 2010AR 77546A1Sep 07, 2011AR 2010-102373Jul 02, 2010IN 2011DN10085A Oct 19, 2012IN 2011-DN10085Dec 20, 2011MX 2012000048A Jan 27, 2012MX 2012-48Jan 02, 2012ZA 2012000366AOct 31, 2012ZA 2012-366Jan 17, 2012Priority Application US 2009-222537P P Jul 02, 2009WO 2010-US40555WJun 30, 2010IndexingPharmaceuticals (Section 63-6)Substances557-04-0Magnesium stearate9003-39-8Povidone74811-65-7Croscarmellose sodium106392-12-5Poloxamer380843-75-4918639-08-4cyanoquinoline tablet formulations and uses thereofTherapeutic use; Biological study; Uses9004-34-6Cellulose, biological studiesmicrocryst.; cyanoquinoline tablet formulations and uses thereofTherapeutic use; Biological study; UsesSupplementary Termscyanoquinoline tablet SKI606 croscarmelloseCopyright © 2013 American Chemical Society (ACS). All Rights Reserved.3. Crystalline forms of 4-[(2,4-dichloro-5-methoxyphenyl)amino]-6-methoxy-7-[3-(4-methyl-1-piperazinyl)propoxy]-3-quinolinecarbonitrileBy: Tesconi, Marc Sadler; Feigelson, Gregg; Strong, Henry; Wen, HongAssignee: Wyeth, John, and Brother Ltd., USAPatent Information: Jan 11, 2007, WO 2007005462, A1Application: Jun 28, 2006, WO 2006-US25160Priority: Jul 01, 2005, US 2005-696381P, Jun 28, 2006, WO 2006-US25160, Jun 29, 2006, US 2006-478216Source: PCT Int. Appl., 38pp., Patent, 2007, CODEN: PIXXD2Accession Number: 2007:35837, CAN 146:128644, CAPLUSLanguage: EnglishAbstractThis invention is directed to a cryst. 4-[(2,4-dichloro-5-methoxyphenyl)amino]-6-methoxy-7-[3-(4-methyl-1-piperazinyl)propoxy]-3-quinolinecarbonitrile monohydrate having a transition temp. of 109-115°.Patent InformationPatent No.Kind Date Application No.DateWO 2007005462A1Jan 11, 2007WO 2006-US25160Jun 28, 2006 AU 2006266045A1Jan 11, 2007AU 2006-266045Jun 28, 2006 CA 2613053A1Jan 11, 2007CA 2006-2613053Jun 28, 2006EP 1902029A1Mar 26, 2008EP 2006-774184Jun 28, 2006JP 2009500332T Jan 08, 2009JP 2008-519519Jun 28, 2006 US 20070015767A1Jan 18, 2007US 2006-478216Jun 29, 2006 US 7767678B2Aug 03, 2010AR 54505A1Jun 27, 2007AR 2006-102806Jun 29, 2006 CR 9596A Mar 06, 2008CR 2007-9596Dec 17, 2007IN 2007KN04959A Aug 01, 2008IN 2007-KN4959Dec 20, 2007 KR 2008028386A Mar 31, 2008KR 2007-7030989Dec 31, 2007 NO 2008000051A Jan 29, 2008NO 2008-51Jan 04, 2008 MX 2008000384A Mar 07, 2008MX 2008-384Jan 07, 2008 CN 101248047A Aug 20, 2008CN 2006-80031171Feb 26, 2008 US 20100324066A1Dec 23, 2010US 2010-820306Jun 22, 2010 US 8445496B2May 21, 2013Priority ApplicationUS 2005-696381P P Jul 01, 2005WO 2006-US25160W Jun 28, 2006US 2006-478216A3Jun 29, 2006IndexingPharmaceuticals (Section 63-6)Substances64-19-7Acetic acid, biological studiescryst. forms of methylpiperazinylpropoxyquinolinecarbonitrile deriv.Biological use, unclassified; Biological study; Uses918639-10-8cryst. forms of methylpiperazinylpropoxyquinolinecarbonitrile deriv.Properties; Reactant; Reactant or reagent380843-75-44-[(2,4-Dichloro-5-methoxyphenyl)amino]-6-methoxy-7-[3-(4-methyl-1-piperazinyl)propoxy]-3-quinolinecarbonitrilecryst. forms of methylpiperazinylpropoxyquinolinecarbonitrile deriv.Properties; Reactant; Therapeutic use; Biological study; Uses; Reactant or reagent918639-08-4P918639-09-5Pcryst. forms of methylpiperazinylpropoxyquinolinecarbonitrile deriv.Properties; Synthetic preparation; Therapeutic use; Biological study; Preparation; Uses50-70-4D-Glucitol, biological studies69-65-8Mannitol87-99-0Xylitol9004-34-6Cellulose, biological studiescryst. forms of methylpiperazinylpropoxyquinolinecarbonitrile deriv.Therapeutic use; Biological study; UsesSupplementary Termspiperazinylpropoxyquinolinecarbonitrile cryst form prepn; quinolinecarbonitrile piperazinylpropoxy cryst form prepnCitations1)Wyeth Corp; WO 2005047259 A 20052)Wyeth Corp; WO 03093241 A 20033)Brian, F; WO 2005019201 A 2005Copyright © 2013 American Chemical Society (ACS). All Rights Reserved.。
2017社交软件APP排行榜前十名

2017社交软件APP排行榜前十名社交是人类作为社会性群体的基本属性,2017年全世界全球和中国安卓手机社交软件app排行榜前十名名单有哪些呢?下面是小编精心为你们整理的关于2017社交软件APP排行榜前十名的相关内容,希望你们会喜欢!2017社交软件APP排行榜前十名_安卓手机社交软件排行榜_全球世界中国社交软件排行榜2017社交软件APP排行榜1.微信微信(wechat)是腾讯公司于2011年1月21日推出的一个为智能终端提供即时通讯服务的免费应用程序,微信支持跨通信运营商、跨操作系统平台通过网络快速发送免费语音短信、视频、图片和文字,同时,也可以使用通过共享流媒体内容的资料和基于位置的社交插件“摇一摇”、“漂流瓶”、“朋友圈”、”公众平台“、”语音记事本“等服务插件。
2017社交软件APP排行榜2.QQ腾讯QQ(简称“QQ”)是腾讯公司开发的一款基于Internet的即时通信(IM)软件。
腾讯QQ支持在线聊天、视频通话、点对点断点续传文件、共享文件、网络硬盘、自定义面板、QQ邮箱等多种功能,并可与多种通讯终端相连。
其标志是一只戴着红色围巾的小企鹅。
2017社交软件APP排行榜3.新浪微博新浪微博是一个由新浪网推出,提供微型博客服务类的社交网站。
用户可以通过网页、WAP页面、手机客户端、手机短信、彩信发布消息或上传图片。
新浪可以把微博理解为微型博客或者一句话博客。
用户可以将看到的、听到的、想到的事情写成一句话,或发一张图片,通过电脑或者手机随时随地分享给朋友,一起分享、讨论;还可以关注朋友,即时看到朋友们发布的信息。
2017社交软件APP排行榜4.MOMO陌陌陌陌是陌陌科技于2011年8月推出的一款基于地理位置的泛社交、泛娱乐平台。
在陌陌,您可以通过短视频、直播等方式生动的展示自己;认识附近的人;加入附近的群组;查看附近的留言;参加附近的活动。
还可以和朋友交换各自的地理位置,用有趣的表情聊天等等。
CV_Chi_Harold_Liu

Chi(Harold) Liu55, West Kensington Court+44(0)78-0968-2396, chiliu@ London, W14 9AA, U.K. /~chiliu P ROFILE:•Four-year international research experience in telecoms industry, strong collaborations in UK, USA, and EU. •Two-year team leading experience for network simulation (OPNET), to support various projects and products. •Proven problem solving and analytical skills in modelling wireless networking problems.•Extensive technical presentation experience for international projects reviews and conferences. •Knowledge of working in an international corporate environment as a team player.R ESEARCH I NTERESTS:•Cross-layer design and optimization of multi-hop wireless ad hoc/mesh/sensor networks•Algorithm and protocol designs for distributed scheduling, QoS routing, and admission control•Network management and operations for Quality of Information (QoI), and middleware•Mobile control theory for inter-domain communications•General artificial intelligence, MDP/POMDP, data ferry, and data collection problemsE DUCATION:Imperial College, London, U.K. 2006 – Jan. 2010 (Exp.) Department of Electrical and Electronic Engineering Ph.D. in Electrical Engineering •Supervisor: Prof. Kin K. Leung•Thesis: Cross-Layer Design for Multi-Hop Wireless Networks•Participated in European Union FP6 MEMBRANE mesh network and US Army-UK MoD co-funded ITA sensor network research projects and led some collaborations•Published more than 20 conference, journal papers, deliverables, and technical reportsTsinghua University, Beijing, China 2002 - 2006 Department of Electronic Engineering B.Eng. in Electronic and Information Engineering •Supervisors: Prof. Xin Su and Prof. Jing Wang•Achieved overall 88.5/100 score with equivalence to first-class degree•Demonstrated excellent analytical skills that achieved average math/physics 95.0/100•Demonstrated excellent pragmatic skills that lab reports are used as grading samplesH ONOURS AND A WARDS:•Scholarship of US Army-UK Ministry of Defence co-funded ITA Project 2008 - 2009 •Scholarship of EU-Funded FP6 MEMBRANE Project 2006 - 2008 •Scholarship of Electrical Engineering Department, Imperial College, U.K. 2006 - 2009 •Analog Device Inc. Scholarship, Tsinghua University, China 2005 •First-class Scholarship, Tsinghua University, China 2004 •Second Prize of Hardware Design Contest, Tsinghua University, China 2003 •Champion of the 7th Scientific Award for Young Pioneers, Beijing, China 2002 •Champion of the Mathematical Modelling Contest, China 2001, 2002 P ROFESSIONAL E XPERIENCES:IBM’s T. J. Watson Research Centre, Hawthorne, USA June 2009 – September 2009 Research Intern US Army-UK MoD ITA Project •Mentors: Dr. Ting He and Dr. Kang-Won Lee (Manager)•Contributions: WCNC2010, MobiHoc2010, IBM Tech Rep.•Investigated the interoperability issues of heterogeneous wireless networks and systems, by using unmanned, sensor-mounted data ferries to maintain the inter-domain communications.•Proposed a complete mathematical model using partially observable Markov decision process (POMDP);investigated the optimal policy and various suboptimal heuristics through analytical analysis; proved two tight upper bounds and one tight lower bound for these algorithms.•Performed extensive both synthetic simulations and human mobility trace studies using Matlab/C++. Imperial College, London, UK October 2006 – September 2009 Research Assistant EU FP6 MEMBRANE Project •Collaborators: Dr. Athanasios Gkelias, Dr. Yun Hou, and Prof. Kin Leung•Contributions: ICOIN08, VTC-Spring08, ISWPC08, WiMob08, PIMRC08, Globecom09, IEEE Trans. on Networking, Springer Wireless Personal Comm.•Investigated cross-layer design for multi-hop wireless mesh networks.•Proposed a multi-constrained QoS routing algorithm, a distributed, proportional fair scheduling algorithm for long-term QoS provision, and a connection admission control for grade of services guarantees.•Proposed a unique generic admission control methodology for all packet networks, wired/wireless, transparent to lower protocol layers, by modelling the whole network as a black box to estimate thetime-vary network capacity through real-time performance measurements.IBM’s T. J. Watson Research Centre, Hawthorne, USA October 2008 – December 2009 Industry collaboration under US-UK ITA Project•Collaborators: Dr. Chatschik Bisdikian and Dr. Joel Branch•Contributions: SPIE DSS09, ACITA09, SECON 2010, MobiCom 2010 IBM Tech Rep.•Developed a QoI-aware sensor network management framework for multi-task operations, where an adaptive negotiation process is proposed between task QoI requirement and sensor network resources.•Investigated the fundamental tradeoffs among task QoI requirements, sensor network lifetime, and traffic models, on a comprehensive intruder detection user scenario using Matlab/C++.•Investigated distributed duty-cycling schemes to achieve global optimization optimum.•Participated regular conference calls, initiated and won bi-annual research grants, gave technical presentations, and drafted quarterly research deliverables and newsletters to meet the deadline.•Developed problem solving skills against military requirements in a pragmatic approach, applying innovative design methods where appropriate.CEFRIEL-Politecnico di Milano, Milan, Italy February 2007 - October 2008 Industry collaboration under EU-FP6 MEMBRANE Project•Collaborators: Sara Grilli Colombo, Dr. Erwu Liu, and Giovanni Paltenghi•Contributions: SimuTools09, UKSim09, 4 Deliverables•Led OPNET simulation campaign among a group of five researchers•Developed a complex cross-layer simulation platform that covers TCP/IP, MAC and PHY layers for wireless mesh networks, fulfilling project requirement; enhanced standard OPNET PHY layer pipelinestages to include Rayleigh fading channel, adaptive modulation and coding schemes and directional antenna.•Initialized and leaded the collaborations, managed timeliness and set up milestones.Tsinghua Unisplendour Corporation Ltd., Beijing, China June 2005 - August 2005 Summer Technical Intern•Supervisor: Zhuo Chen•Designed automatic highway accident alarming systems and weighing systems that have been transformed into commercial products.•Improved fast-learning, self-motivating, team working and communication skills in industry.Peer Reviewers:2007 - present •Journals: Int’l J. of Comm. Networks and Information security (IJCNIS), IEEE Trans. on Comm., IEEE Comm. Letter, IEEE Trans. on Wireless Comm. EURASIP J. on Wireless Comm. and Networking •2010 Conferences: Infocom, WCNC, VTC-Spring.•2009 Conferences: WCNC, VTC-Spring, VTC-Fall, Globecom, PIMRC, ACITA.•2008 Conferences: ISWPC, GlobeCom, IWCMC, WiMob.A CTIVITIES:Technical University of Delft, Delft, the Netherland September 2008 IDEA League Summer Workshop•Organized EU IDEA League summer workshop aiming to draft research agendas on "Next Generation ICT for the Next Generation"; fostered collaborations among 50 PhD students in EU.•Proposed a human-interactive mobile sensor environment for elderly people, delivered elevator pitch and final presentations, won second prize.Imperial College, London, U.K. 2007-2009 Student Helper•Helped annual graduation award ceremonies and annual alumni reunion event at Royal Albert Hall.•Student caller to help raise annual funds for Imperial College.Tsinghua University, Beijing, ChinaStudent Helper July 2005 •Helped organizing 1st Tsinghua International Forum for PhD students, ChinaChief Radio Presenter2002 - 2004 •Hosted and presented popular music series and awarded best presenter for two years.•Being university ambassador of P&G, IBM for product marketing in advert slots.C OMPUTER AND O THER S KILLS:•Network Simulator: extensive use of OPNET, some use of NS-2•Languages: extensive use of C/C++, MATLAB, Pascal, some use of Unix shell scripts.•Applications: extensive use of LATEX, MS Office, MS Visual, Windows database.•Statistical Packages: extensive use of SAS, SPSS, C and MATLAB statistical libraries.•Full clean driving licenses in both U.K. and China.•Language: English (fluent), French (intermediate), Chinese (mother tongue).P UBLICATIONS: Full list of publications is attached.R EFERENCES:•Professor Kin K. Leung, Fellow IEEETanaka Chair Professor in Internet Technology E-mail: kin.leung@ Electrical Engineering and Computing Departments, Imperial College, U.K.•Dr. Chatschik Bisdikian, Fellow IEEEResearch Staff Member, Policy and Networking Department E-mail: bisdik@ IBM T. J. Watson Research Center, Hawthorne, USA•Dr. Kang-Won LeeManager, Wireless Networking Research Group E-mail: kangwon@ IBM T. J. Watson Research Center, Hawthorne, USA•Academician Hequan Wu E-mail: wuhq@ Vice President of Chinese Academy of Engineering, ChinaChi(Harold) LiuJ OURNAL P APERS:1. C. H. Liu, K. K. Leung, and A. Gkelias, “A Generic Admission Control Methodology for Packet Networks,”submitted to IEEE/ACM Trans. on Networking.2. C. H. Liu, A. Gkelias, Y. Hou, and K. K. Leung. “Cross-Layer Design for QoS in Wireless Mesh Networks,”Springer Wireless Personal Communications, Special Issue on Cross-Layer Design for Future GenerationWireless Networks, 2009.3.J. Cheng, C. H. Liu, S. Zhou, and Y. Yao. “Linear Precoding based on Sub-channel Permutation inPost-combining MIMO-HARQ Systems,” IEICE Transactions on Communications, Volume E89-B, No. 11, pp.3139-3142, 2007.C ONFERENCE P APERS:1.T. He, C. H. Liu, K. W. Lee, K. K. Leung, and A. Swami, “Flying in the Dark: Dynamic Control of MobileGateways,” submitted to ACM MobiHoc 2010, Chicago, USA.2. C. H. Liu, C. Bisdikian, J. Branch, and K. K. Leung, “QoI-Aware Wireless Sensor Network Management forDynamic Multi-Task Operations,” submitted to IEEE SECON 2010, Boston, USA.3. C. H. Liu, T. He, K. W. Lee, K. K. Leung, and A. Swami, “Dynamic Control of Data Ferries under PartialObservations,” in IEEE WCNC 2010, Sydney, Australia.4. C. H. Liu, K. K. Leung, and A. Gkelias, “Route Capacity Estimation Based Admission Control and QoS Routingfor Mesh Networks,” in IEEE GlobeCom 2009, Hawaii, USA.5. C. H. Liu, J. Branch, C. Bisdikian, and K. K. Leung “A QoI-aware Middleware for Mission-oriented Applicationsin Wireless Sensor Networks,” in ACITA 2009, Maryland.6. C. H. Liu, S. G. Colombo, E. Liu, A. Gkelias, and G. Paltenghi. “Efficient Cross-Layer Simulator for PerformanceEvaluation of Wireless Mesh Networks,” in ACM/ICST SIMUTools 2009, 2-6 March, Rome, Italy.7. C. H. Liu, S. G. Colombo, A. Gkelias, E. Liu, and K. K. Leung. “An Efficient Cross-Layer SimulationArchitecture for Wireless Mesh Networks,” in IEEE UKSim 2009, UK.8. C. H. Liu, K. K. Leung, C. Bisdikian, and J. Branch, “A New Approach to Architecture of Sensor Networks forMission-Oriented Applications,” in SPIE Defence, Security, and Sensing 2009, 14-17 Apr., Orlando, USA.9. C. H. Liu, A. Gkelias, Y. Hou, and K. K. Leung. “A Distributed Scheduling Algorithm with QoS Provisions inMulti-Hop Wireless Mesh Networks,” in IEEE WiMob 2008, pp. 253-258, 12-14 Oct., Avignon, France.10. C. H. Liu, A. Gkelias, and K. K. Leung. “Connection Admission Control and Grade of Service for QoS Routing inWireless Mesh Networks,” in IEEE PIMRC 2008, pp. 1-5, 15-18 Sept., Canne, France.11. C. H. Liu, A. Gkelias, and K. K. Leung. “A Cross-Layer Framework of QoS Routing and Distributed Schedulingfor Mesh Networks”, in IEEE VTC Spring 2008, pp. 2193-2197, 11-14 May, Singapore.12. A. Gkelias, B. Federico, C. H. Liu, and K. K. Leung, “MIMO Routing with QoS Provisioning”, in Proc. of IEEEISWPC 2008, pp. 46-50, 7-9 May, Santorini, Greece.13. C. H. Liu, K. K. Leung, and A. Gkelias. “A Novel Cross-layer QoS Routing Algorithm for Wireless MeshNetworks”, in IEEE ICOIN 2008, pp. 1-5, 22-25 Jan., Busan, Korea.DELIEVERABLES AND REPORTS (Joint Contributions):1. C. H. Liu, C. Bisdikian, J. Branch, and K. K. Leung, “QoI-Aware Operations and Management inMulti-Task-Oriented Wireless Sensor Networks,” IBM Res. Tech. Rep. RC24840, August, 2009.2. C. H. Liu, K. K. Leung, C. Bisdikian, and J. Branch, “A New Approach to Architecture of Sensor Networks forMission-Oriented Applications,” IBM Res. Tech. Rep. RC24765, March, 2009.3. C. H. Liu et al. “D4.2.3: Further Extensions and Performance Studies of Routing and Scheduling Algorithms forthe MEMBRANE Network”, EU-funded MEMBRANE project annul report, 30 Sep. 2008.4. C. H. Liu et al., “D4.3.2: Network Simulations of the Overall Wireless Multihop Backhaul IP Network”,EU-funded MEMBRANE project annul report, 31 Jul 2008.5. C. H. Liu et al., “D4.2.2: Performance Studies of the New Routing, Scheduling and Power Control Algorithms bySimulation and/or Mathematical Analysis”, EU-funded MEMBRANE project annul report, 31 Dec. 2007.6. C. H. Liu et al., “D4.3.1: Network Simulations of the Overall Wireless Multihop Backhaul IP Network”,EU-funded MEMBRANE project annul report, 31 Dec. 2007.7. C. H. Liu et al., “D4.2.1: Joint Routing, Scheduling and Power Control Algorithms”, EU-funded MEMBRANEproject annul report, 31 Dec. 2007.。
New_Standard_College_English_Book_2_Unit_1_

Reading Activities Intensive Reading 1 Active Reading (1):
College just isn’t special any more
Intensive Reading 1
College just isn’t special any more
1 If you can remember anything about the 1960s, you weren’t really there, ― so the saying goes. It may be true for those who spent their college years in a haze of marijuana smoke. But there is one thing everyone remembers about the 1960s: Going to college was the most exciting and stimulating experience of your life.
Pre-Reading Activities
Teaching Objectives
Introduction
Topic IntroductionPre-Reding Activities
Teaching Objectives
By the end of the unit, students will be better able to
1) What is a typical day for Sarah? going to lectures, tutorials or seminars and staying in the library. 2) What does Sarah do after finishing her study? going out having fun, such as debating or going to the pub. 3) Why is Sarah fond of debating? It gives her a lot of fun and also makes her look great on the CV when she graduates.
httpweslchinaorgmba2007video-ad-marketing-st...
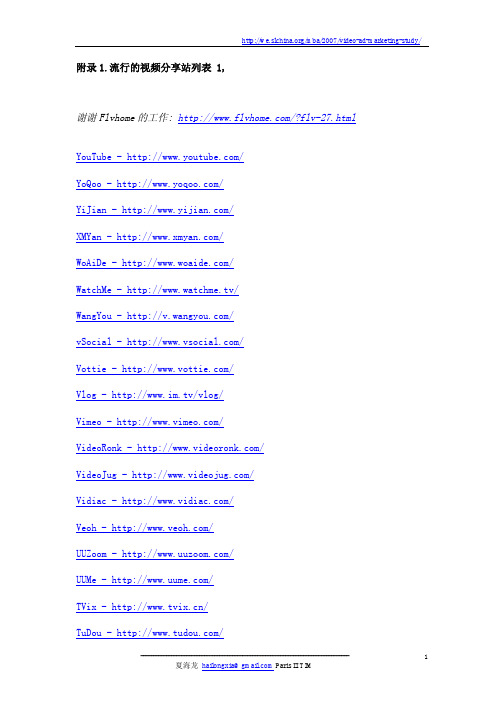
附录1.流行的视频分享站列表1,谢谢Flvhome的工作:/?flv-27.html YouTube-/YoQoo-/YiJian-/XMYan-/WoAiDe-/WatchMe-/WangYou-/vSocial-/Vottie-/Vlog-/vlog/Vimeo-/VideoRonk-/VideoJug-/Vidiac-/Veoh-/UUZoom-/UUMe-/TVix-/TuDou-/SoKiKi-/Show5-/Sharkle-/videos/ SeGoo-/media/ SeeHaHa-/ Revver-/QuXiu-/QQ-/Qooqle-http://video.qooqle.jp/QiRSS-/Qihoo-/ PornoTube-/ PoMoHo-/PodLook-/PodKo-/oYoo-/OpenV-/OuOu-/NiPai-/ MyVideo-http://www.myvideo.de/MoViZo-/ MotionBox-/Mop-/MoFile-/Mobuzz-/MNCast-/MetaCafe-/MaxDuo-/MaiDee-/LuLu-/Ku6-/iFilm-/JumpCut-/iAsk-/HuboTV-/Heavy-/GuBa-/GPrime-/video/Google-Glumbert-/GameTrailers-/umlisting.php FriendEarth-/FlashMov-/FKee-/FeeSee-/EyeSpot-/EinHand-/flv/eBaumsWorld-/tags/video/ DuSee-DuoWan-/video/video-index.html Daum-/Damoim-/DailyMotion-/video/ CurrentTV-/studio/ CollegeHumor-/CNBoo-/ClipFish-http://www.clipfish.de/BoLaa-/video/Bokecc-/Blip-/BiKu-/Beedeo-/BeBo-/BaLa-/Acrr-/9You-/91VC-/6Rooms-/5T-/5Show-/56-/54CK-/51TV-/21GT-/1Zart-/1Ting-/17club-/VideoIndex.club17173-/163888-/dv/155-/附录2.流行的视频分享站列表2来源:好123/wangmei.htm优酷网土豆网六间房百度视频搜索新浪播客腾讯宽频偶偶视频Tvix第九频道酷6网Mofile视频分享56原创视频我秀新华视频搜狐娱乐播报东方宽频华聚网视频新浪宽频爆米花视频三杯水DV网友影秀OpenV视频搜索菠萝网Maidee播客网看看吧视频搜索第一视频爱播网视频飞视播客网CCTV视频点播琥珀网17173游戏视频Funny Movies[英]SeeHaHa YouTube[英]Video Bomb[英]附录3.国内流行的社交网站:来源:好123/love.htm世纪佳缘交友网百合网嫁我网爱情公寓QQ交友中心亿友网珍爱网51个人空间知己交友网新浪交友赛我网网友天下雅虎友缘人MySpace中国Linkist联络家UBLove国际网上交友未名交友中国站百度空间-找朋友若邻网络校内网上海爱情网贵州e友社区河北银河交友网古城热线交友频道天涯佳缘齐鲁交友六人行青年社交新浪情感恋爱-百度知道百度情感吧百度婚姻吧中青在线--情感话题校内广场-情感屋奥一非常男女百度爱情吧天涯社区情感天地榕树下-爱情城市幸福婚嫁婚姻-搜狐女人秘密花园中国结婚网久久婚嫁附录4.国外社交网站列表Thanks for the great work of Yasns Wiki /Brief DescriptionWebsite(target demographic-themes-focus)**43Things Folksonomy/Tagging–Reference Links to Things 43Places Folksonomy/Tagging–Reference Links to People 43People Folksonomy/Tagging–Reference Links to PlacesAIM Pages Instant Messaging Asian-Americans–Social Networking–Multiple FeaturesaSmallWorld Travel EnthusiastsBabbello Australia–Teens–Social Networking–Multiple FeaturesBebo United Kingdom–Teens–Schools,Colleges,Music Bands Christians–Social Networking African-Americans–Social Networking–Multiple FeaturesBlurty Blogging(based on open-source LiveJournal code) Bolt Teens–Exploring/Sharing Links,Photos,VideosBolt2Teens/early20s–Exploring/Sharing Links, Photos,VideosCampusbug Online Education,E-CommerceCare2ActivistsCarSpace Auto EnthusiastsCatster Cat Owners and Enthusiasts–Social Networking Christians–Social NetworkingclaimID Folksonomy/Tagging–Online Identity and Organizing Personal Links Sites School,Work,Military ConnectionsConnect.ee Estonia–Social Networking–Multiple Features Craigslist Online Trading-Searchable User ClassifiedsCyworld Sites South Korea,China–Exploring/Sharing Links, Photos,Videos Folksonomy/Tagging–Organizing, Exploring/Sharing LinksDeadJournal"Dark"Blogs(based on open-source LiveJournal code)DeviantArt Graphic Artists–Blogging–Exploring/Sharing Links,ArtDigg Folksonomy/Tagging–Organizing, Exploring/Sharing News LinksDogster Dog Owners and Enthusiasts–Social Networking DowneLink Gay and Lesbian Community–Social NetworkingDWC Faces Female Professionals;Part of Draugiem.lv Latvia–Social Networking–Multiple Features eBay E-Commerce,Online Trading–AuctionsEcademy Business NetworkingEvite Setting up/Sharing Announcements and Events Facebook College and High School StudentsFaceparty Great Britain–Teens/early20s–Social Networking–Multiple Features Family-based Networks–Sharing Photos,Events, Discussion Boards Farmers/Rural Interests–Online DatingFlickr Folksonomy/Tagging–Organizing/Sharing/Suggesting ImagesFriendster20s–Social Networking–Multiple FeaturesFrühstückstreff International–Multi-lingual Social NetworkingGaia Online Video Gamers;Creating Avatars;Sharing Music, Photos,VideosGather Folksonomy/Tagging–Writers–Exploring/Sharing News Links and Blogs–Social/Public AffairsGolfBuzz Golfers and Courses–Host and Peer-to-Peer ContentGreatestJournal Exploring/Sharing Blogs(based on open-source LiveJournal code) Poland–Social Networking–Multiple Features Travel Enthusiasts–Tagging,Blogging,ReviewsHi5Networks Latin America,Caribbean,Europe,North America, Australia–Teens–Social Networking–Multiple FeaturesHotSoup American Politics–Campaigns and Elections Hyves Netherlands–High School and College StudentsInsider Pages 20s/30s–Reviews of Local Attractions and InterestsIRC-Galleria Finland–Social Networking–Multiple Features iWiW Hungary–Social Networking–Multiple Features Football(soccer)and Nike-sponsored players–World Cup Social Networking–Emphasizes Search RankingsJudysBook Local Area Reviews/Articles/Interests–Emphasizes TrustScore and Social SearchLast.FM Teens/20s–Exploring/Sharing Music Tracks/Files –Use of"Scrobbling"Feature Teens/20s–Musicians,Bands,Musical Interests–Spanish Language(MTV-sponsored)LinkedIn Business Networking(in more than130industries)LinkUp Central Emphasis on Social Search–Making Local Contacts to Cultivate Offline Interests and GoalsListography Organizing Personal Lists–Social Bookmarking/TaggingLiveJournal Blogging–Social Search and NetworkingLunarStorm Sweden,Denmark,United Kingdom–Teens/early20s –Social Networking Online Dating–Social Search Social Search–Making Local Contacts to Cultivate Offline Interests and GoalsMiaplaza Photos,Recommendations,Discussion Boards,Chat, Internet Phone,Classifieds Second,Third Generation Latino Americans–Social NetworkingMixi Japan–Exploring/Sharing Blogs,Reviews,Photos, Music DownloadsMOBANGO Exploring/Sharing Files and Content for Cell PhonesMOG Teens/20s–Blogging and Tagging–Exploring/Sharing Files;Content Based on Musical TastesMSN Spaces Social Search and Networking–Blogging and Sharing PhotosMultiply Teens/20s–Social Networking–Organizing/Sharing Media-Blogs,Photos,Videos, MusicMyGamma Teens/20s–International Social Networking-Mobile Phone Features Teens/20s–Social Networking–Multiple FeaturesMySpace Teens/20s–Social Networking–Multiple FeaturesmyYearbook Teens–Social Networking–Multiple FeaturesNeurona Spain,Latin America–Business Networking Nexopia Canada–Teens–Social NetworkingNHLConnect Official Online Community of the National Hockey League–Host and Peer-to-Peer ContentOmidyar Network Social Entrepreneurship/Activism–Extranet OkCupid Online Dating–Social SearchopenBC Business Networking–Emphasis on International Networks(16Languages)Opinity Folksonomy/Tagging–Online Identity–Employs Online Reputation Profileorkut Social Networking(Google affiliate) Passado Social Networking,Business Networking Pet OwnersPiczo Teens–Social Networking–Exploring/Sharing PhotosPlatial Folksonomy/Tagging–Online/Shared Mapping Tool –Emphasis on PlacesProfileHeaven Great Britain–Teens–General Social Networking –Ratings Mental Health Issues–Provides Profiles,Blogs, Forums–Host and Peer-to-Peer ContentRediff Connexions India–Social Networking Sharing Contacts/Important Announcements and Events –Life TransitionsRyze Business NetworkingSchoolParentNet Parents,Teachers–Schooling AffairsSconex High school Students–Encourages Keeping Online Class Schedules,Photos,Journals Bridal Social Networking–References for Weddings "Girlfriendships"–Feminism Ages7-17–“Dress”,Share Personal Avatar(called a MeDoll)Studybreakers High School Students–Social Networking(formerly )Stylefeeder Folksonomy/Tagging–Reference Shopping ItemsSulekha India–Searchable Blogs,Classifieds,Discussion Boards/mba/2007/video-ad-marketing-study/----------------------------------------------------------------------------------夏海龙hailongxia@ Paris II TIM 11Tagged Teens–Social Networking,Tagging–Exploring/Sharing Photos,Videos,BookmarksTagWorld Social Networking,Tagging–Exploring/Sharing Blogs,Photos,Videos,BookmarksTakingITGlobal Youths Interested in Social Initiatives–Blogs, Discussion Boards–Host and Peer-to-Peer Content Family-based Networks–Sharing Photos,Events, "Family Blogs"The Student Center Teens/early20s–Social NetworkingTickle Teens/20s–Topic-based Social Networking–Features Polls,Quizzes–Host and Peer-to-Peer Content Online Trading–Searchable Local/City User Classifieds–Forums,Events,Reviews, Recommendations Online Dating–Social SearchVampire Freaks Social Search–Gothic Industrial CultureWAYN Social Search–Travel Enthusiasts–Worldwide FocusXanga General Social Search and Networking–Blogging, Sharing PhotosXuqa Teens/earl20s–United States,United Kingdom, Ireland,Canada–College StudentsYahoo!Personals Online Dating–Social SearchYahoo!360°General Social Search and Networking(integrated with multiple Yahoo!Properties)。
rfc4919.IPv6 over Low-Power Wireless Personal Area Networks (6LoWPANs) Overview, Assumptions, Proble

Network Working Group N. Kushalnagar Request for Comments: 4919 Intel Corp Category: Informational G. Montenegro Microsoft Corporation C. Schumacher Danfoss A/S August 2007 IPv6 over Low-Power Wireless Personal Area Networks (6LoWPANs):Overview, Assumptions, Problem Statement, and GoalsStatus of This MemoThis memo provides information for the Internet community. It doesnot specify an Internet standard of any kind. Distribution of thismemo is unlimited.Copyright NoticeCopyright (C) The IETF Trust (2007).AbstractThis document describes the assumptions, problem statement, and goals for transmitting IP over IEEE 802.15.4 networks. The set of goalsenumerated in this document form an initial set only.Table of Contents1. Introduction (2)2. Overview (2)3. Assumptions (3)4. Problems (4)4.1. IP Connectivity (4)4.2. Topologies (5)4.3. Limited Packet Size (6)4.4. Limited Configuration and Management (6)4.5. Service Discovery (6)4.6. Security (6)5. Goals (7)6. Security Considerations (9)7. Acknowledgements (10)8. References (10)8.1. Normative References (10)8.2. Informative References (10)Kushalnagar, et al. Informational [Page 1]1. IntroductionLow-power wireless personal area networks (LoWPANs) comprise devices that conform to the IEEE 802.15.4-2003 standard by the IEEE[IEEE802.15.4]. IEEE 802.15.4 devices are characterized by shortrange, low bit rate, low power, and low cost. Many of the devicesemploying IEEE 802.15.4 radios will be limited in their computational power, memory, and/or energy availability.This document gives an overview of LoWPANs and describes how theybenefit from IP and, in particular, IPv6 networking. It describesLoWPAN requirements with regards to the IP layer and the above, andspells out the underlying assumptions of IP for LoWPANs. Finally, it describes problems associated with enabling IP communication withdevices in a LoWPAN, and defines goals to address these in aprioritized manner. Admittedly, not all items on this list may benecessarily appropriate tasks for the IETF. Nevertheless, they aredocumented here to give a general overview of the larger problem.This is useful both to structure work within the IETF as well as tobetter understand how to coordinate with external organizations.2. OverviewA LoWPAN is a simple low cost communication network that allowswireless connectivity in applications with limited power and relaxed throughput requirements. A LoWPAN typically includes devices thatwork together to connect the physical environment to real-worldapplications, e.g., wireless sensors. LoWPANs conform to the IEEE802.15.4-2003 standard [IEEE802.15.4].Some of the characteristics of LoWPANs are as follows:1. Small packet size. Given that the maximum physical layer packet is 127 bytes, the resulting maximum frame size at the mediaaccess control layer is 102 octets. Link-layer security imposes further overhead, which in the maximum case (21 octets ofoverhead in the AES-CCM-128 case, versus 9 and 13 for AES-CCM-32 and AES-CCM-64, respectively), leaves 81 octets for datapackets.2. Support for both 16-bit short or IEEE 64-bit extended mediaaccess control addresses.3. Low bandwidth. Data rates of 250 kbps, 40 kbps, and 20 kbps for each of the currently defined physical layers (2.4 GHz, 915 MHz, and 868 MHz, respectively).4. Topologies include star and mesh operation.Kushalnagar, et al. Informational [Page 2]5. Low power. Typically, some or all devices are battery operated.6. Low cost. These devices are typically associated with sensors, switches, etc. This drives some of the other characteristicssuch as low processing, low memory, etc. Numerical values for"low" elided on purpose since costs tend to change over time.7. Large number of devices expected to be deployed during thelifetime of the technology. This number is expected to dwarfthe number of deployed personal computers, for example.8. Location of the devices is typically not predefined, as theytend to be deployed in an ad-hoc fashion. Furthermore,sometimes the location of these devices may not be easilyaccessible. Additionally, these devices may move to newlocations.9. Devices within LoWPANs tend to be unreliable due to variety ofreasons: uncertain radio connectivity, battery drain, devicelockups, physical tampering, etc.10. In many environments, devices connected to a LoWPAN may sleepfor long periods of time in order to conserve energy, and areunable to communicate during these sleep periods.The following sections take into account these characteristics indescribing the assumptions, problems statement, and goals forLoWPANs, and, in particular, for 6LoWPANs (IPv6-based LoWPANnetworks).3. AssumptionsGiven the small packet size of LoWPANs, this document presumesapplications typically send small amounts of data. However, theprotocols themselves do not restrict bulk data transfers.LoWPANs, as described in this document, are based on IEEE802.15.4-2003. It is possible that the specification may undergochanges in the future and may change some of the requirementsmentioned above.Some of these assumptions are based on the limited capabilities ofdevices within LoWPANs. As devices become more powerful, and consume less power, some of the requirements mentioned above may be somewhat relaxed.Kushalnagar, et al. Informational [Page 3]While some LoWPAN devices are expected to be extremely limited (theso-called "Reduced Function Devices" or RFDs), more capable "FullFunction Devices" (FFDs) will also be present, albeit in much smaller numbers. FFDs will typically have more resources and may be mainspowered. Accordingly, FFDs will aid RFDs by providing functions such as network coordination, packet forwarding, interfacing with othertypes of networks, etc.The application of IP technology is assumed to provide the following benefits:1. The pervasive nature of IP networks allows use of existinginfrastructure.2. IP-based technologies already exist, are well-known, and provento be working.3. An admittedly non-technical but important consideration is thatIP networking technology is specified in open and freelyavailable specifications, which is favorable or at least able to be better understood by a wider audience than proprietarysolutions.4. Tools for diagnostics, management, and commissioning of IPnetworks already exist.5. IP-based devices can be connected readily to other IP-basednetworks, without the need for intermediate entities liketranslation gateways or proxies.4. ProblemsBased on the characteristics defined in the overview section, thefollowing sections elaborate on the main problems with IP forLoWPANs.4.1. IP ConnectivityThe requirement for IP connectivity within a LoWPAN is driven by the following:1. The many devices in a LoWPAN make network auto configuration and statelessness highly desirable. And for this, IPv6 has readysolutions.2. The large number of devices poses the need for a large addressspace, well met by IPv6.Kushalnagar, et al. Informational [Page 4]3. Given the limited packet size of LoWPANs, the IPv6 address format allows subsuming of IEEE 802.15.4 addresses if so desired.4. Simple interconnectivity to other IP networks including theInternet.However, given the limited packet size, headers for IPv6 and layersabove must be compressed whenever possible.4.2. TopologiesLoWPANs must support various topologies including mesh and star.Mesh topologies imply multi-hop routing, to a desired destination.In this case, intermediate devices act as packet forwarders at thelink layer (akin to routers at the network layer). Typically theseare "full function devices" that have more capabilities in terms ofpower, computation, etc. The requirements on the routing protocolare:1. Given the minimal packet size of LoWPANs, the routing protocolmust impose low (or no) overhead on data packets, hopefullyindependently of the number of hops.2. The routing protocols should have low routing overhead (lowchattiness) balanced with topology changes and powerconservation.3. The computation and memory requirements in the routing protocolshould be minimal to satisfy the low cost and low powerobjectives. Thus, storage and maintenance of large routingtables is detrimental.4. Support for network topologies in which either FFDs or RFDs maybe battery or mains-powered. This implies the appropriateconsiderations for routing in the presence of sleeping nodes.As with mesh topologies, star topologies include provisioning asubset of devices with packet forwarding functionality. If, inaddition to IEEE 802.15.4, these devices use other kinds of networkinterfaces such as ethernet or IEEE 802.11, the goal is to seamlessly integrate the networks built over those different technologies.This, of course, is a primary motivation to use IP to begin with. Kushalnagar, et al. Informational [Page 5]4.3. Limited Packet SizeApplications within LoWPANs are expected to originate small packets. Adding all layers for IP connectivity should still allow transmission in one frame, without incurring excessive fragmentation andreassembly. Furthermore, protocols must be designed or chosen sothat the individual "control/protocol packets" fit within a single802.15.4 frame. Along these lines, IPv6’s requirement of sub-IPreassembly (see Section 5) may pose challenges for low-end LoWPANdevices that do not have enough RAM or storage for a 1280-octetpacket.4.4. Limited Configuration and ManagementAs alluded to above, devices within LoWPANs are expected to bedeployed in exceedingly large numbers. Additionally, they areexpected to have limited display and input capabilities.Furthermore, the location of some of these devices may be hard toreach. Accordingly, protocols used in LoWPANs should have minimalconfiguration, preferably work "out of the box", be easy tobootstrap, and enable the network to self heal given the inherentunreliable characteristic of these devices. The size constraints of the link layer protocol should also be considered. Networkmanagement should have little overhead, yet be powerful enough tocontrol dense deployment of devices.4.5. Service DiscoveryLoWPANs require simple service discovery network protocols todiscover, control and maintain services provided by devices. In some cases, especially in dense deployments, abstraction of several nodes to provide a service may be beneficial. In order to enable suchfeatures, new protocols may have to be designed.4.6. SecurityIEEE 802.15.4 mandates link-layer security based on AES, but it omits any details about topics like bootstrapping, key management, andsecurity at higher layers. Of course, a complete security solutionfor LoWPAN devices must consider application needs very carefully.Please refer to the security consideration section below for a moredetailed discussion and in-depth security requirements.Kushalnagar, et al. Informational [Page 6]5. GoalsThe goals mentioned below are general and not limited to IETFactivities. As such, they may not only refer to work that can bedone within the IETF (e.g., specification required to transmit IP,profile of best practices for transmitting IP packets, and associated upper level protocols, etc). They also point at work more relevantto other standards bodies (e.g., desirable changes to or profilesrelevant to IEEE 802.15.4, W3C, etc). When the goals fall under the IETF’s purview, they serve to point out what those efforts shouldstrive to accomplish, regardless of whether they are pursued withinone (or more) new (or existing) working groups. When the goals donot fall under the purview of the IETF, documenting them here serves as input to other organizations [LIAISON].Note that a common underlying goal is to reduce packet overhead,bandwidth consumption, processing requirements, and powerconsumption.The following are the goals according to priority for LoWPANs:1. Fragmentation and Reassembly layer: As mentioned in the overview, the protocol data units may be as small as 81 bytes. This isobviously far below the minimum IPv6 packet size of 1280 octets, and in keeping with Section 5 of the IPv6 specification[RFC2460], a fragmentation and reassembly adaptation layer mustbe provided at the layer below IP.2. Header Compression: Given that in the worst case the maximum size available for transmitting IP packets over an IEEE 802.15.4 frame is 81 octets, and that the IPv6 header is 40 octets long,(without optional headers), this leaves only 41 octets forupper-layer protocols, like UDP and TCP. UDP uses 8 octets inthe header and TCP uses 20 octets. This leaves 33 octets fordata over UDP and 21 octets for data over TCP. Additionally, as pointed above, there is also a need for a fragmentation andreassembly layer, which will use even more octets leaving veryfew octets for data. Thus, if one were to use the protocols asis, it would lead to excessive fragmentation and reassembly, even when data packets are just 10s of octets long. This points tothe need for header compression. As there is much published and in-progress standardization work on header compression, the6LoWPAN community needs to investigate using existing headercompression techniques, and, if necessary, specify new ones. Kushalnagar, et al. Informational [Page 7]3. Address Autoconfiguration: [6LoWPAN] specifies methods forcreating IPv6 stateless address auto configuration. Statelessauto configuration (as compared to stateful) is attractive for6LoWPANs, because it reduces the configuration overhead on thehosts. There is a need for a method to generate an "interfaceidentifier" from the EUI-64 [EUI64] assigned to the IEEE 802.15.4 device.4. Mesh Routing Protocol: A routing protocol to support a multi-hop mesh network is necessary. There is much published work on ad-hoc multi hop routing for devices. Some examples include[RFC3561], [RFC3626], [RFC3684], all experimental. Also, theseprotocols are designed to use IP-based addresses that have large overheads. For example, the Ad hoc On-Demand Distance Vector(AODV) [RFC3561] routing protocol uses 48 octets for a routerequest based on IPv6 addressing. Given the packet-sizeconstraints, transmitting this packet without fragmentation andreassembly may be difficult. Thus, care should be taken whenusing existing routing protocols (or designing new ones) so that the routing packets fit within a single IEEE 802.15.4 frame.5. Network Management: One of the points of transmitting IPv6packets is to reuse existing protocols as much as possible.Network management functionality is critical for LoWPANs.However, management solutions need to meet the resourceconstraints as well as the minimal configuration and self-healing functionality described in Section 4.4. The Simple NetworkManagement Protocol (SNMP) [RFC3410] is widely used formonitoring data sources and sensors in conventional networks.SNMP functionality may be translated "as is" to LoWPANs with the benefit to utilize existing tools. However, due to the memory,processing, and message size constraints, further investigationis required to determine if the use of SNMPv3 is suitable, or if an appropriate adaptation of SNMPv3 or use of different protocols is in order.6. Implementation Considerations: It may be the case thattransmitting IP over IEEE 802.15.4 would become more beneficialif implemented in a "certain" way. Accordingly, implementationconsiderations are to be documented.7. Application and higher layer Considerations: As headercompression becomes more prevalent, overall performance willdepend even more on efficiency of application protocols.Heavyweight protocols based on XML such as SOAP [SOAP], may notbe suitable for LoWPANs. As such, more compact encodings (andperhaps protocols) may become necessary. The goal here is tospecify or suggest modifications to existing protocols so that Kushalnagar, et al. Informational [Page 8]they are suitable for LoWPANs. Furthermore, application levelinteroperability specifications may also become necessary in the future and may thus be specified.8. Security Considerations: Security threats at different layersmust be clearly understood and documented. Bootstrapping ofdevices into a secure network could also be considered given the location, limited display, high density, and ad-hoc deployment of devices.6. Security ConsiderationsIPv6 over LoWPAN (6LoWPAN) applications often require confidentiality and integrity protection. This can be provided at the application,transport, network, and/or at the link layer (i.e., within the6LoWPAN set of specifications). In all these cases, prevailingconstraints will influence the choice of a particular protocol. Some of the more relevant constraints are small code size, low poweroperation, low complexity, and small bandwidth requirements.Given these constraints, first, a threat model for 6LoWPAN devicesneeds to be developed in order to weigh any risks against the cost of their mitigations while making meaningful assumptions andsimplifications. Some examples for threats that should be considered are man-in-the-middle attacks and denial of service attacks.A separate set of security considerations apply to bootstrapping a6LoWPAN device into the network (e.g., for initial keyestablishment). This generally involves application level exchanges or out-of-band techniques for the initial key establishment, and may rely on application-specific trust models; thus, it is consideredextraneous to 6LoWPAN and is not addressed in these specifications.In order to be able to select (or design) this next set of protocols, there needs to be a common model of the keying material created bythe initial key establishment.Beyond initial key establishment, protocols for subsequent keymanagement as well as to secure the data traffic do fall under thepurview of 6LoWPAN. Here, the different alternatives (TLS, IKE/IPsec, etc.) must be evaluated in light of the 6LoWPAN constraints.One argument for using link layer security is that most IEEE 802.15.4 devices already have support for AES link-layer security. AES is ablock cipher operating on blocks of fixed length, i.e., 128 bits. To encrypt longer messages, several modes of operation may be used. The earliest modes described, such as ECB, CBC, OFB and CFB provide only confidentiality, and this does not ensure message integrity. Othermodes have been designed which ensure both confidentiality and Kushalnagar, et al. Informational [Page 9]message integrity, such as CCM* mode. 6LoWPAN networks can operate in any of the previous modes, but it is desirable to utilize the mostsecure modes available for link-layer security (e.g., CCM*), andbuild upon it.For network layer security, two models are applicable: end-to-endsecurity, e.g., using IPsec transport mode, or security that islimited to the wireless portion of the network, e.g., using asecurity gateway and IPsec tunnel mode. The disadvantage of thelatter is the larger header size, which is significant at the 6LoWPAN frame MTUs. To simplify 6LoWPAN implementations, it is beneficial to identify the relevant security model, and to identify a preferred set of cipher suites that are appropriate given the constraints.7. AcknowledgementsThanks to Geoff Mulligan, Soohong Daniel Park, Samita Chakrabarti,Brijesh Kumar, and Miguel Garcia for their comments and help inshaping this document.8. References8.1. Normative References[RFC2460] Deering, S. and R. Hinden, "Internet Protocol, Version 6 (IPv6) Specification", RFC 2460, December 1998.[IEEE802.15.4] IEEE Computer Society, "IEEE Std. 802.15.4-2003",October 2003.8.2. Informative References[EUI64] "GUIDELINES FOR 64-BIT GLOBAL IDENTIFIER (EUI-64)REGISTRATION AUTHORITY", IEEE,/regauth/oui/tutorials/EUI64.html.[6LoWPAN] Thomson, S., Narten, T., and T. Jinmei, "IPv6Stateless Address Autoconfiguration", Work inProgress, May 2005.[RFC3411] Harrington, D., Presuhn, R., and B. Wijnen, "AnArchitecture for Describing Simple Network Management Protocol (SNMP) Management Frameworks", STD 62, RFC3411, December 2002.Kushalnagar, et al. Informational [Page 10][RFC3561] Perkins, C., Belding-Royer, E., and S. Das, "Ad hocOn-Demand Distance Vector (AODV) Routing", RFC 3561,July 2003.[RFC3626] Clausen, T. and P. Jacquet, "Optimized Link StateRouting Protocol (OLSR)", RFC 3626, October 2003.[RFC3684] Ogier, R., Templin, F., and M. Lewis, "TopologyDissemination Based on Reverse-Path Forwarding(TBRPF)", RFC 3684, February 2004.[SOAP] "XML Protocol Working Group", W3C,/2000/xp/Group/.[LIAISON] "IETF Liaison Activities", IETF,/liaisonActivities.html.Authors’ AddressesNandakishore KushalnagarIntel CorpEMail: nandakishore.kushalnagar@Gabriel MontenegroMicrosoft CorporationEMail: gabriel.montenegro@Christian Peter Pii SchumacherDanfoss A/SEMail: schumacher@Kushalnagar, et al. Informational [Page 11]Full Copyright StatementCopyright (C) The IETF Trust (2007).This document is subject to the rights, licenses and restrictionscontained in BCP 78, and except as set forth therein, the authorsretain all their rights.This document and the information contained herein are provided on an "AS IS" basis and THE CONTRIBUTOR, THE ORGANIZATION HE/SHE REPRESENTS OR IS SPONSORED BY (IF ANY), THE INTERNET SOCIETY, THE IETF TRUST AND THE INTERNET ENGINEERING TASK FORCE DISCLAIM ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OF THE INFORMATION HEREIN WILL NOT INFRINGE ANY RIGHTS OR ANY IMPLIEDWARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Intellectual PropertyThe IETF takes no position regarding the validity or scope of anyIntellectual Property Rights or other rights that might be claimed to pertain to the implementation or use of the technology described inthis document or the extent to which any license under such rightsmight or might not be available; nor does it represent that it hasmade any independent effort to identify any such rights. Information on the procedures with respect to rights in RFC documents can befound in BCP 78 and BCP 79.Copies of IPR disclosures made to the IETF Secretariat and anyassurances of licenses to be made available, or the result of anattempt made to obtain a general license or permission for the use of such proprietary rights by implementers or users of thisspecification can be obtained from the IETF on-line IPR repository at /ipr.The IETF invites any interested party to bring to its attention anycopyrights, patents or patent applications, or other proprietaryrights that may cover technology that may be required to implementthis standard. Please address the information to the IETF atietf-ipr@.AcknowledgementFunding for the RFC Editor function is currently provided by theInternet Society.Kushalnagar, et al. Informational [Page 12]。
The_post-everything_generation

The post-everything generationFrank Thomas is a sophomore at Princeton, majoring in literary theory. He hopes to become a human rights lawyer.1 I never hoped to understand the nature of my generation or how American colleges are changing by going to Lit Theory classes. This is the class where you look cool, a bit sleepy from too many late nights and wearing a T-shirt with some ironic comment such as "Been there, done that and yes, this IS the T-shirt". That's how I spent my time on the course, struggling through difficult subjects like gender theory and post-colonialism, and at the same time checking my iPod for something good to listen to. But when I started to study postmodernism, something clicked and made me sit up and take a fresh look at college life.2So what is postmodernism? Hard to say, almost by definition it can't be defined ... it's just kind of negative and against everything that came before it. And that makes it difficult to see what it is. The term was first used in 1949, but no one has yet decided what postmodern attitudes mean for the future of culture or society. Yet for me, it made me curious, because "postmodern" seemed to describe my cool, sleepy and ironic, T-shirt wearing friends.3We're "post" in so many ways, post-Cold War, post-industrial, post-baby boom, post-9/11. We're a generation that comes from what has been called the short century (1914—1989), at the end of a century of war and revolution which changed civilizations, overthrew repressive governments, and left us with extraordinary opportunities and privilege, more than any generation before.4And yet what do we do? Do we revolt and rebel, like all students of generations before? Do we take to the streets and chant, "We're not leaving until we see change"? No, we do the opposite, we go to war, and we don't ask why, we give up our civil liberties, and we watch death and destruction on the evening news every day. 5At college, we sign petitions, join organizations, sign up for mailing lists, wear our Live Strong bracelets, and watch Live Aid and Live Earth on the television—go tothe concerts even, if we can get the tickets. But what do we stand for? Like a true postmodern generation, we have no way to describe our political commitment, we have no inspirational characters, we have no philosophy, we have no direction or theme. We're only defined by what came before us, we're the generation of the Che Guevara T-shirt.6 It's a movement which appears to encourage individuals to assert themselves collectively. It seems to be waiting for the revolution. And as young people, we're expected to be angry because that's what young people do.7But how do we rebel against our parents' generation which is nostalgic for revolution? How do we rebel against parents who sometimes want revolution more than we do? We don't. We rebel by not rebelling.8The real energy is not on the campus, it's on the Internet. It provides us with a developing opportunity to communicate ideas and frustrations. We don't do demonstrations any more, we go to chat rooms, instead of going onto the streets.9The American college as we used to know it is coming to an end. To my generation, radicalism is associated with al-Qaeda, not the Weathermen. "Campus takeover" sounds less like Berkeley 1968, more like Virginia Tech 2007. The resonance of the words belongs to another era and doesn't reflect the realities of today. 10But the technological revolution is just as real and just as profound as the revolution of the 1960s—it's just not as obvious. It's work in progress, but it's there. Perhaps when our parents stop pointing out everything they were and everything we're not, maybe they'll see that the post-everything generation is speaking a language which makes sense. We're writing the revolution, and we're using our own words to do so.。
Windows系统文件扩展名

Windows系统文件扩展名文件扩展名文件扩展名是操作系统用来标志文件格式的一种机制。
通常来说,一个扩展名是跟在主文件名后面的,由一个分隔符分隔。
在一个像“readme.txt”的文件名中,readme是主文件名,txt 为扩展名,表示这个文件被认为是一个纯文本文件。
目录文件扩展名包括A 对象代码库文件B 对象代码库文件C 对象代码库文件D 对象代码库文件E 对象代码库文件F 对象代码库文件G 对象代码库文件H 对象代码库文件I 对象代码库文件J 对象代码库文件K 对象代码库文件L 对象代码库文件M 对象代码库文件N 对象代码库文件O 对象代码库文件P对象代码库文件T 对象代码库文件Q 对象代码库文件R 对象代码库文件V 对象代码库文件我们经常接触的扩展名有:doc————(Word文档,用微软的word等软件打开)wps————(Wps文档,用金山公司的wps软件打开)xls————(Excel电子表格,用微软的excel软件打开)ppt————(Powerpoint演示文稿,用微软的powerpoint等软件打开)txt————(纯文本,用记事本、写字板、word等都可以打开)rar————(WinRAR压缩文件,用WinRAR等打开)htm————(网页文件,用浏览器、Microsoft Office FrontPage打开)pdf————(用pdf阅读器打开、用pdf编辑器编辑)dwg————(CAD图形文件,用AutoCAD等软件打开)exe————(可执行文件[1])jpg————(图形文件)bmp————(位图文件)swf————(flash影片)1.文件扩展名是一个文件的必要构成部分。
任何显示文件扩展名一个文件可以有或没有扩展名。
对于打开文件操作,没有扩展名的文件需要选择程序去打开它,有扩展名的文件会自动用设置好的程序(如有)去尝试打开(是“尝试打开”,而不是“打开”的原因参看下面的第2个误区),文件扩展名是一个常规文件的构成部分,但一个文件并不一定需要一个扩展名。
补全短文6选5+(名校模拟+地区真题)-冲刺2024年中考英语必考题型终极预测(成都专用)

冲刺2024年中考英语必考题型终极预测(成都专用)专题10 补全短文6选5名校模拟+地区真题(2023·四川成都·校联考模拟预测)补全短文根据短文内容,从短文后的A~F 选项中,选出5个适当的选项补全短文。
Have you ever wished that an AI could write something for you? Instead of spending hours typing away, you could simply input a few keywords and have articles written for you. 1ChatGPT was developed by US company OpenAI. 2 You can ask it to write stories and emails, create recipes(食谱), translate languages, and answer all kinds of questions.According to a US survey of more than 1, 000 students, over 89 percent of them have used ChatGPT to help with a homework assignment(任务). 3 For example, New York City public schools banned(禁止)students and teachers from using ChatGPT on the district’ s networks and devices(设备).The measure(措施)comes out of worries that the tool could make it easier for students to cheat on assignments.4 It may have a bad influence on students. “It does not build thinking quality and problem-solving skills, which are necessary for studying and lifelong success, “said Jenna Lyle, the secretary of the New York City Department of Education.5 Some Canadian universities are making rules on its use, for both students and teachers. Some teachers think that bans on AI software like ChatGPT are not wise. “We have to know that AI is a tool people will use, “John, the biology professor, told the school newspaper of the university. “What we need to do is to change our way of learning, teaching and examinations”. That way, we can “have integrity(诚信)while recognizing the use of the tool”.A.It is a powerful tool.B.Well, ChatGPT may make that dream a reality.C.However, not all educators say “no” to ChatGPT.D.Some schools in the US do not allow students to use it.E.The use of ChatGPT has raised heated discussions in the education world.F.Some also worry that ChatGPT could be used to spread incorrect information.(2023·四川成都·四川省成都市七中育才学校校考模拟预测)补全短文。
2007-2008学年度下学期07级期初考试英语试卷

第一部分:英语知识运用(共两节,满分45分)第一节:单项填空(共15小题;每小题1分,满分15分)(命题人:丛冠捷)1. -----The light in the office is still on.----- Oh, I forgot ______.A turning it offB to turn it offC to turn it onD turning it down2. The teacher as well as his students______ visiting the museum now.A areB isC wasD were3. Environment will ______one’s character.A effectB causeC affordD influence4 .______people who learn English as a foreign language ______more than 750 million.A A number of ;reachB A number of ; reachesC The number of; isD The number of ;are5 . The cost of living in Glasgow is among the lowest in Britain ,_____the quality of life is probably one of the highest.A sinceB whenC asD while6 . My father , together with some of his old friends ,______there already.A will beB had beenC has beenD have been7 . Jack is the only one of the few students who ______English well.A speaksB speakC sayD tell8 . Is Tom still working _____the new book?A inB onC againstD out9. I like this country, _____ in spring.A especiallyB speciallyC basicallyD luckily10. My daughter ______get up late ,but now she______ rising early in the morning.A was used to ;is used toB used to ; was used toC was used to ; usedD used to; is used to11 . If law and order ______, neither the citizen nor his property is safe.A will not be preservedB is not preservedC were not preservedD haven’t preserved12 . When and where to go for the on-salary holiday ______yet.A are not decidedB have not been decidedC is not being decidedD has not been decided13 . ______with the developed area ,people’s living standard of our province is not high at all.A CompareB While comparingC ComparedD Comparing 14 . It is high time that we ______the plan to see whether it is effective.A will try outB tried outC will carry outD will try on15 .He concluded his speech with a remark ______failure ______the mother of success.A which; wasB that ;isC which ;isD that ;was第二节:完形填空(共20小题;每小题1.5分,满分30分)(命题人:蒋琦)About a year ago, I went to stay at a Detroit hotel. I didn’t want to 16 too much money with me, so I asked the desk clerk to put a hundred-dollar bill in the safe for me.The next morning, 17 , the clerk said that he knew nothing about my money. I didn’t have any proof (证据) 18 I had given the man the money. There was clearly nothing to do but go to the 19 lawyer at once.The lawyer advised me to return to the hotel with him and give 20 hundred-dollar bill to the clerk. So we 21 . An hour later, I went back to the desk and asked for the money. 22 I had the lawyer as an eyewitness (证人) to the 23 hundred-dollar bill, the clerk couldn’t say he 24 nothing about it.Another hour later, I put the second part of the lawyer’s plan into action. This time both the lawyer and I went to the hotel to 25 for the hundred-dollar bill once again and 26 the clerk insisted that he had given 27 to me, I said it was not 28 . The lawyer said to him, “I 29 this gentleman give you a hundred-dollar bill. If you don’t hand it in immediately, I’ll be forced to call the 30 ” The clerk realised he had been 31 , so he gave me back the first hundred-dollar bill.“I don’t know 32 to thank you enough for 33 my money back,” I said to the lawyer. And what do you 34 his answer?He said, “Oh, don’t 35 me. That will be one hundred dollars, please.”( ) 16. A. carry B. lend C. spend D. hold( ) 17. A. but B. yet C. however D. instead( ) 18. A. where B. which C. why D. that( ) 19. A. nearest B. farthest C. cheapest D. slowest( ) 20. A. the other B. another C. other D. others( ) 21. A. returned B. did C. gave D. acted( ) 22. A. Though B. When C. Unless D. Since( ) 23. A. one B. last C. first D. second( ) 24. A. believed B. had C. knew D. heard( ) 25. A. search B. ask C. look D. beg( ) 26. A. when B. though C. because D. as( ) 27. A. these B. this C. them D. it( ) 28. A. real B. good C. true D. exact2007-2008学年度下学期07级期初考试英语试卷满分:150分时间:120分钟( ) 29. A. agreed B. saw C. let D. permitted( ) 30. A. police B. officer C. official D. clerk( ) 31. A. punished B. helped C. cheated D. understood( ) 32. A. what B. how C. when D. where( ) 33. A. returning B. giving C. getting D. asking( ) 34. A. suppose B. find C. mean D. suggest( ) 35. A. believe B. thank C. leave D. fool第二部分:阅读理解(共20小题,每小题2分,满分40分)(命题人:赫晶、石宇航)(A)England is the largest part of Britain. Its capital is London, which is on the Thames. The port of London is one of the greatest ports in the world. Ships from all countries go up and down the Thames. They bring food to the people of Britain. Then they take British machines and other things back to the ports from which they come.There are many scenic spots(风景区)in the west of England for tourists. The lakes here are the most beautiful in England. There are trees, flowers and green grass round them.The water is almost always very still, and you can see the green hills, the brown mountains and everything else round the lake upside-down in the water. There are boats on all the larger lakes, which take people from one side to the other. There are always a lot of boats on the lakes in summer.Travellers from many countries of the world go to the west of England in summer. There are boat races on the largest lakes, and people from many places in Great Britain and Europe come to see them. Young people travel from one place to another on their bicycles, or walk from one lake to another.( ) 36. The port of London________A only takes business within the countryB is greater than the others in the worldC is the busiest in the worldD plays an important part in carrying in and out food, machines and other things. ( ) 37. A tourist to Britain will probably first visit_______A the British museumB the River ThamesC scenic spots in the west of EnglandD the port of London( ) 38. As a foreign traveller to England, you will have the chance of______A climbing the green hills and brown mountainsB watching boat races on the largest lakesC testing fish from the ThamesD swimming in the lakes( )39. Young people go to see______A beautiful lakes on footB boat races by bicycleC the port of London in their carsD the still water in the lake by air(B)As prices and building costs keep rising , the “do-it-yourself”(DIY)trend(趋势) in the U.S. continues to grow.“We needed furniture for our living room,” said John Ross, “and we just didn’t have enough money to buy it. So we decided to try making a few tables and chairs.” John got married six months ago, and like many young people these days, they are struggling to make a home at a time when the cost of living is very high. The Rosses took a 2-week course for $280 at a night school. Now they build all their furniture and make repairs around the house.Jim Hatfield has three boys and his wife died. He has a full-time job at home as well as in a shoe factory. Last month, he received a car repair bill for $420. “I was deeply upset about it . Now I’ve finished a car repair course, I should be able to fix the car by myself.”John and Jim are not unusual people. Most families in the country are doing everything they can to save money so they can fight the high cost of living. If you want to become a “do-it-yourself”, you can go to DIY classes. And for those who don’t have time to take a course, there are books that tell you how to do things by yourself.( ) 40. John and his wife went to evening classes to learn how to______A run a DIY shopB make or repair thingsC save time and moneyD improve the quality of life( ) 41. When the writer says that Jim has a full-time job at home, he means when______A makes shoes in his homeB does extra work at nightC does his own car and home repairsD keeps house and looks after it( ) 42. Jim Hatfield decided to become a do-it-yourself when______A his car repairs cost too muchB the car repair class was not helpfulC he could not possibly do two jobsD he had to raise the children all by himself( ) 43. Which would be the best title for text?A The Joy of DIYB You Can Do It Too!C Welcome to Our DIT Course!D Ross and Hatfield: Believes in DIY(C)Never give out identifying information such as name, home, address, school name, ortelephone number in a public place such as at a chat room or on bulletin boards. Never send a person your picture without first checking with your parents.Be careful when someone offers something, such as gifts and money. Be very careful about any offers that get you to meet someone or have someone visit your home.Tell your parents right away if you come across any information that makes you feel uncomfortable.Never arrange a face-to-face meeting without telling your parents. If your parents agree to the meeting, make sure that you meet in a public place and have a parent with you.Remember that people online may not be whom they seem to be. Because you can’t see or even hear the person, it would be easy for someone to misrepresent himself/herself. If someone says that “I’m a 12-year-old girl,” it could really be an old man.Be sure that it is dealing with someone that you and your parents know and trust before giving out any personal information through email.( )44. The best title for the passage is “______”A Warnings Against Making Online FriendsB Messages One Can Get on the InternetC How to Make Friends on the InternetD Safety Tips for Kids on the Internet( )45. If you have a face-to-face meeting, you should ______A have your father or mother with youB go aloneC not tell your parentsD meet secretly( ) 46. The underlined word “misrepresent” in the passage means to “______”A make a wrong impression aboutB understand somebody wronglyC give a wrong description ofD form a wrong opinion about( )47. In the last four paragraphs, the writer suggests that one should______A believe nobody on the InternetB be careful about the online friendC not be honest on the InternetD make friends with those you believe in(D)As we all know, great culture differences lie between China and the west. As a result, they have their own different diet habits.●The way of paying the bill is differentChinese like to invite people to dinner and the inviters pay the bill. In England and America, if classmates or friends have a meal together, they usually share the cost. Ifa man has a meal with a woman, he usually pays the bill. When people hold abirthday dinner party for their friend, they usually share the cost.●The diet behaviour is differentIf Chinese get together to have a meal, they always talk and laugh freely. In England and America, if people have a meal together, they try not to make any noise, but it’s also impolite to say nothing. They always try to find a topic to talk about.●The background of sending gifts is differentChinese seldom send the host gifts, but if the host has a certain kind of great event such as a marriage or a funeral, the guest should give the host some dear gifts.In England and America, when people are invited to have a meal by a newly-made friend, they usually give the host some flowers or a bottle of wine or a box of chocolates.●The way of saying goodbye is differentIf a Chinese leave the host after a meal, they usually thank the host for his/her kindness. In America and England, the guests always thank the host by saying, “Thank you very much for the meal.”( ) 48. Who will usually pay the bill if a man invites a woman in England?A.The man.B.The woman.C. They share the bill.D. Their friend.( ) 49. What is the manner of English people at the table?A.They never talk but eat.B.They talk but make no noise.C.They talk and laugh.D.They never talk but laugh.( ) 50. In England, do they usually give flowers to the host as a gift?A.They never give money.B.They sometimes do.C.They always do.D.They usually do.( ) 51. When you leave your American host’s home, what do you say?A.Thank you anyway.B.Thank you all the same.C.I like your meal.D.Thank you for the meal.(E)In ancient times, a young farmer who loved horses lived in northern China. It was a great blow to him when, one day, his favourite mare(母马)ran away and crossed the frontier into the land of other tribes. His neighbours and friends came to sympathize with him—and indeed he was inconsolable—but they found the young man’s father strangely cheerful.“Sorrow?”he said. “Ah yes, it is sad to lose one’s horse. But who knows what blessing might come from this bad fortune? We shall just have to wait and see.”Several months later the mare came back home, bringing a handsome stallion(种马)running alongside. Now the neighbours and friends gathered to admire the stallion and celebrate the young farmer’s good fortune. This time they found the father shaking his head in the other direction.“Ah, yes,” he said darkly, “this seems like good fortune, but who knows what bad thing might come of it?” He continued to shake his head. “We must wait and see.”With his favourite mare back, the young man began to enjoy a life of luxury. He spent more and more time riding and less and less time farming. Then one day while riding the stallion, he fell and broke his hip. Again his neighbours and friends came to sympathize, but there was the farmer’s father looking happy.“ Oh!” he cried.” Let us not be sad. Who knows what blessing is on its way because of this accident. Wait and see! Wait and see!”They didn’t wait for long. Before the month was over, barbarians attacked the frontier and all the able-bodied men were called to fight against them. The fighting was fierce and nine out of ten young men died in battle.Not so the young farmer.His unfortunate fall from the horse left him unfit for battle. When everyone else went off to fight the barbarians, he was forced to stay at home with his father.In later years, when winter chills sent an ache through his hips, he was only grateful for the pain. It reminded him of his good fortune to be alive.( ) 52. Which statement is a possible theme of the passage?A.You know who your friends are when you have bad luck.B.Things are not always as they appear to be.C.Fathers and sons do not always agree.D.Fathers are always wise.( )53. It can be inferred from the passage that later on, the young farmer_______.A.want to go to warB.became a rich farmerC.was glad he fell off the stallionD.was grateful to his father( ) 54. A good title for this passage is “__________”A.An Evil Life, an Evil EndB.From Good to Bad to Good to BadC.Actions Speak Louder Than WordsD.A Friend in Need Is a Friend Indeed( ) 55. The subject matter of this passage is about _________.A.legends about farmerB.legends about horsesC.folk talesD.ancient philosophers.第三部分:用方框中单词或短语的正确形式填空(共15小题,每小题2分,满分30分)(命题人:丛冠捷)12We are ______a lot of difficulties now.3He is very poor , so he lives ______his income.4Sorry, you answered __________.5Their country is________ by the Party they trust.6We have written a ______ on the subject.7Are you at the top or bottom of the ______?8Our ______is to help poorer countries.9Read ________page 10.10There are _________50 students in our class.11On the one hand I want to sell the house, but ______________I don’t like moving. 12He was _______at a very good school.13We should try our best to ________speaking English.14______ of them know the answer.15__________ Paris is very beautiful.第四部分:写作(共两节,满分35分)第一节:短文改错(共10小题,每小题1分,满10分)(命题人:蒋琦)Before John was taken to hospital, two men carried him 1.to a bed and put him in it carefully. A nurse came and write 2.his name and address on a book. She gave him some tea to 3.drink, and then the doctor came. He looked at his arm careful 4.and put hands on it. “Yes, it is broken,” he said. We 5.will do something about it this afternoon. It won’t hurt you. 6.You will all right soon. “Thank you, doctor,” John said. 7.John was in the hospital for a week. The nurses were very kind. 8.The first night, he couldn’t fall sleep. A nurse gave him some 9.medicine, and he goes to sleep until the next morning. 10.第二节:书面表达(满分25分)(命题人:丛冠捷)假设你是李华,住在江城。
Chatp3-汉化实战 软件汉化

Logo主讲:高芳銮Logo内容提要标准资源汉化 非标准资源汉化 升级汉化 字 典 处 理1 2 3 4Company LogoLogo第一节 标准资源汉化Passolo 2007 Sisulizer 2008Logo标准资源汉化之 Passolo 2007Passolo 是目前世界上最流行的软件本地化专业工具之一。
它支持众多文件格式,包括可执行程序文件、资源文件和基于 XML 的文件。
文本可以被翻译为多种语言,包括亚洲语系 (Unicode 码)以及书写方式为从右向左的语言,比如希伯来 语和阿拉伯语。
Passolo 包含多种所见即所得(WYSIWYG)编辑器来处 理软件的用户界面,包括对话框、菜单、位图、图标和指针编 辑器。
用户界面的处理非常安全,绝对不会意外删除或者改变 现有的元素或结构。
官方网站:LogoLogo标准资源汉化设置方案Passolo 2007 汉化三步曲翻译列表生成目标Logo 一、 方案创建及设置Logo 添加源文件Company LogoLogo 设置源文件属性Logo 二进制资源提取添加目标语言目标语言设置二、创建字串列表更新翻译列表翻译字串控件调整控件调整控件恢复重复翻译验证翻译三、生成目标文件标准资源汉化之Sisulizer2008Sisulizer2008Sisulizer一款软件本地化工具,可以将软件翻译成支持多种语言,只需三步:1)扫描程序并定位所有的文本;2)使用Sisulizer的可视化编辑器翻译文本;3)创建本地化版本。
官方网址:/LogoLogo Sisulizer2008 汉化三步曲扫描 1 扫描 1 翻译 2 翻译 2 构建 3 构建 3Logo一、工程向导Logo选择源文件Logo支持的文件类型Logo识别的文件类型Logo提取资源类型Logo输出文件设置Logo目标语言设置Logo自动扫描文件 扫描翻译字串重复翻译与翻译引擎控件调整与还原菜单翻译构建目标文件生成目标语言文件第二节非标准资源汉化点睛字符替换器点睛字符替换器(OverNimble Localize Plus)主要用于非标准资源的汉化•支持多种编译程序的字符串及文本格式的字符串等的提取及替换。
日本网站

http://www.bekkoame.ne.jp
http://www.lycos.co.jp
新闻报纸
朝日新闻
http://www.yomiuri.co.jp 读卖新闻
每日新闻
留学信息
http://www.aiej.or.jp/index1.html财团法人日本国际教育协会
http://www.iijnet.or.jp/jrf/jlpt/contents/main.html日本国际交流基金
/htdocs/study/map.htm日本大学索引
/daigaku/日本大学
http://www.yozemi.ac.jp/日本大学入试情况
http://www.interq.or.jp/www1/xzu/sitetop1/school/gb.htm东京语文学院日本语中心
/SCHOOL NAVI
http://www.naigai.or.jp/index.htm财团法人内外学生中心
/carifo日本就业信息
http://www.tfemploy.go.jp/ch/index-c.html东京外国人职业介绍服务中心
科技信息
http://www.jst.go.jp科学技术振兴事业团
北京千之叶日语培训
学日语就到日语专门培训机构,日语初级/3级、2级提高/1级精读/初中级外教口语/各级别考试冲刺班/300句日语通;晚班、周末班、脱产班。现正打折优惠中。
上海中野日语专修学校
日语教育机构、拥有语言教师、小班教学方式。
http://pr.jst.go.jp/outline/outline1.html提供国内外科技信息
毕业设计(论文)-基于安卓的聊天App的设计与实现

本文在分析了当前环境下聊天 App 的发展前景后,进行了系统的设计和实现,并对 系统进行了完整的测试。系统具有界面友好,操作简单,方便实用的特点。 关键词: Android;即时通讯;环信;聊天 计与实现
Design and Imple mentation of Android Chat room
2.3.4 Broadcast Receiver ...................................................................................................... - 9 2.4 ANDROID 和其它手机操作系统的比较................................................................................ - 9 2.5 本章小结........................................................................................................................- 10 -
安徽工程大学毕业设计(论文)
AI_for_Science:智能化科学设施变革基础研究

专题:大力推进科研范式变革Vigorously Promote Scientific Research Paradigm Transform引用格式:杨小康, 许岩岩, 陈露, 等. AI for Science:智能化科学设施变革基础研究. 中国科学院院刊, 2024, 39(1): 59-69, doi: 10.16418/j.issn.1000-3045.20230820004.Yang X K, Xu Y Y, Chen L, et al. AI for Science:AI enabled scientific facility transforms fundamental research. Bulletin of Chinese Academy of Sciences, 2024, 39(1): 59-69, doi: 10.16418/j.issn.1000-3045.20230820004. (in Chinese)AI for Science:智能化科学设施变革基础研究杨小康1许岩岩1陈露1,2王韫博1高岳1田济东1俞凯1,2金耀辉1梅宏3*1 上海交通大学人工智能研究院上海2002402 上海交通大学计算机科学与工程系上海2002403 北京大学信息科学技术学院北京100871摘要近年来,人工智能(AI)在前沿科技领域取得了诸如AlphaFold2、核聚变智能控制、新冠药物设计等诸多令人瞩目成果,表明AI for Science正在成为一种新的研究范式。
实现智能时代的基础科学源头创新及其下游重大技术创新,需破解2个方面的核心问题:(1)如何利用新一代AI(特别是生成式AI及大模型)的通用性和创造性推动新范式的形成;(2)如何利用AI实现对传统科学设施的赋能与改造。
文章提出一种智能化科学设施的建设构想,兼顾“高度智能化的科学新设施”和“AI赋能已有科学大设施”2个层面的需求,构筑AI for Science的科学设施体系,形成科学领域大模型、生成式模拟与反演、自主智能无人实验及大规模可信科研协作等创新功能,加速重大科学发现、变革性物质合成,以及重大工程技术应用。
幼儿社会交往发育筛查表在社区的应用

幼儿社会交往发育筛查表在社区的应用发表时间:2012-03-30T15:18:18.513Z 来源:《心理医生》2011年7月总第195期供稿作者:张宗茜王慧[导读] 孤独症谱系障碍(ASDs)是一组发生于儿童早期的神经系统发育障碍。
张宗茜王慧(上海市闵行区梅陇社区卫生服务中心201100)摘要:【目的】了解幼儿社会交往筛查表(M-CHAT-23简称社交筛查表)在我社区的社交筛查应用情况。
【方法】选取闵行区梅陇镇18-36月龄儿童作为筛查对象,按照儿科医院心理科提供的筛查流程,运用M-CHAT-23量表对其进行社交筛查。
【结果】我区进行社交筛查共筛查了7385人,社交筛查阳性36例,其中发现1名孤独症,1名疑似孤独症。
【结论】M-CHAT-23可以作为社区儿童早期社交筛查的工具,及早筛查出孤独症及疑似病例。
关键词:孤独症;社交筛查表;M-CHAT-23;社区;中图分类号:R179 文献标识码:B孤独症谱系障碍(ASDs)是一组发生于儿童早期的神经系统发育障碍,包括孤独症、阿斯伯格综合症和广泛性发育障碍未分类型。
虽然现有的医疗手段还未能达到治愈孤独症的水平,但近几十年的研究表明早期筛查、早期诊断和早期康复训练对孤独症患儿的症状控制和预后十分重要。
上海复旦大学儿科医院心理科引进了香港M-CHAT-23筛查量表,应用于初级社区儿童保健机构进行孤独症的早期筛查。
我社区按照儿科医院提供的社交筛查流程对18个月-36个月儿童作为对象,进行社交筛查,筛查情况分析如下。
1 对象和方法1.1对象选取2009年9月-2010年10月间在上海市闵行区梅龙镇社区卫生服务中心儿童保健门诊体检的18-36月龄小儿作为筛查对象。
儿童信息来源于社区儿保门诊的健康体检资料,均已录入电脑系统。
筛查对象总计7385人。
1.2方法由我区保健院牵头,经过儿科医院心理科专家对社区医生进行社交筛查表应用的专门培训,社区医生在对小儿进行完体检后,即按照电脑上社交筛查表(M-CHAT-23),无提示性地逐条询问小儿家长和主要带养人,让他们按照孩子的平时状况回答每一问题,然后严格按照筛查表的阳性标准评定,任意3项回答相反为阳性或者7项核心项目中(第2、7、9、13、14、15)任意2项回答相反为阳性。
2024届上海浦东新区高三一模英语试题及答案

上海浦东新区2023-2024学年第一学期期末教学质量检测高三英语试卷(本试卷满分140分,考试时间120分钟)第一卷I.Listening Comprehension(25分)Section ADirections:In Section A,you will hear ten short conversations between two speakers.At the end of each conversation,a question will be asked about what was said.The conversations and the questions will be spoken only once.After you hear a conversation and the question about it,read the four possible answers on your paper,and decide which one is the best answer to the question you have heard.1.A.5:15. B.5:30. C.5:45. D.6:45.2.A.At a reception desk. B.At a trade fair.C.At a Lost and Found.D.At an exhibition.3.A.Manager and secretary. B.Waiter and diner.C.Customer and salesman.D.Guest and front desk staff.4. A.He'll take her to the hospital. B.He'll tell her what she's missed.C.He'll inform her of the latest news.D.He'll bring her the class notes.5. A.Wash his clothes by hand. B.Wash fewer clothes at a time.e a different washing machine.D.Let her use the washing machine first.6.A.Sell the car to the woman. B.Help the woman paint her car.C.Buy a brand new car.D.Bargain for the old car.7.A.He no longer watches much television.B.He prefers the comedies from the nineties.C.The old shows are not as popular as the new ones. comedies haven't improved since the nineties.8. A.They need a new radio, B.The radio should be repaired.C.The batteries should be taken out.D.They needn't replace the batteries.9.A.He has got everything set for the trip. B.They could stay in the mountain until June.C.They might have to change their plan.D.He has a heavier workload than the woman.10.A.He has been to the library twice to look for the bookB.He will return the book to a library out of town.C.He called the library to say the book would be overdueD.He couldn't return the book because he was away.Section BDirections:In Section B,you will hear two short passages and one longer conversation,and you will be asked several questions on each of the passages and the conversation.The passages and conversation will be read twice,but the questions will be spoken only once.When you hear question,read the four possible answers on your paper and decide which one is the best answer to the question you have heard.Questions11through13are based on the following passage.11.A.To remind himself of his grandfather's love.B.To give himself a positive psychological hint.C.To ensure his safety during the exam.D.To boost his brain power and memory.12.A Enrolling in extra courses at tutorial centers.B.Sticking to their daily diets and avoiding oily food.C Rewarding themselves with some breaks.D.Wearing green underwear in hope of blessing.13.Cramming for the exam the night before it.B.Avoiding sleeping late before the exam.C.loading yourself with much reviewing work.D.Starting revision plans well ahead of time.Questions14through16are based on the following passage.14.A.Belgium. B.France. C.U.K. D.China.15,A.12hours. B.18hours. C.24hours. D.6hours.16,A.Public transportation workers.B.Motorists with a special helmet.C.People living at the Green Areas.D.Persons with a special permit.Questions17through20are based on the following conversation.17.A.Various cultural activities, B.Their hobbies and talents.C.A plan for the summer holiday.D.An adventure in a foreign country18.A.By borrowing money from parents, B.By organizing a talent show.C.By doing part-time jobs,D.By applying for a travel grant19.A.Explaining the educational value of the trip.B.Demonstrating necessary surviving skills.C.Keeping them informed of their travel,ND.Taking them to a travel reality show.20.A.To convince their parents.B.To fund-raise activities.C.To research destinations and planning the route.D.To document the journey through blogs.I.Grammar and Vocabulary(20分)Section ADirections:After reading the passage below.fill in the blanks to make the passage coherent and grammatically correct.For the blanks with a given word,fill in each blank with the proper form of the given word;for the other blanks,use one word that best fits each blank.Wildlife Report Calls for ActionThe World Wide Fund for Nature released its Living Planet Report,which found that the Earth's wildlife populations have fallen by69%in the past50years.The report is produced every two years to show how the natural world is changing,so governments,businesses,and conservationists understand(21)whet needs to be done to protect the Earth.The team looks at several factors.One is the Living Planet Index(LPI), (22)____examines how wildlife populations have changed over time.A total of5,268species across the world have been tracked,including birds,fish,insects,and mammals.The change in wildlife varies around the world.South America and the Caribbean are the most affected.In these areas,the average wildlife populations have dropped by94%over50 years.Central Asia and Europe have(23)_____(small)decline,with an18%drop.The WWF says the changes are caused by human activity(One of the biggest threats(24)______(face)wildlife is the number of acres of forest that are being chopped down(25)___________the land can be used for farming instead.To find the best way to protect animals worldwide,the International Union for Conservation of Nature(IUCN)is studying how easy or hard(26)_____will be to help different species.It has so far found that the populations of several animals,including the pink pigeon and the Sumatran rhino,(27)_____be boosted.While some news from the Living Planet Report is worrisome,there is good news,too.Up to now the numbers of many species(28)_____(rise)around the world because of people's efforts to protect them.In India,the number of tigers has nearly doubled since2009.And in2020, there were more than50sightings of the critically(29)_____(endanger)Antarctic blue whale.In the US,conservation efforts in recent decades have helped to save several species, including the bald eagle,which(3)______(remove)from the threatened species list in2007.Section BDirections:Fill in each blank with a proper word chosen from the box.Each word can be used only once.Note that there is one word more than you need.A.assigned.B.bond.C.consequently.D.deliberately.E.discomfortF.eliminateG.measured.H.pass.I.reluctantJ.revealK.sympatheticThere are plenty of complaints about how social media—texting in particular—may be harming children's social and intellectual development.But a new study suggests that constant instant messaging(IM'ing)and texting among teens may also provide benefits,particularly for introverts,who are___31___to tell their thoughts to others.British researchers analyzed150conversations exchanged by231teens.In100of these chats,the study participant began IM'ing while in a negative emotional state such as sadness or anger.The rest were conversations begun when the participant was feeling good or neutral.After the chat,participants reported a20%reduction in their distress—not enough to completely___32___it but enough to leave them feeling better than they had before reaching out.“Our findings suggest that IM'ing between distressed adolescents and their peers may___33___contribute to their well-being,"the authors write,noting provide emotional relief and that prior research has shown that people___34___to talk to strangers either in real life or online improved their mood in both settings,but even more with IM.And people who talk with their real-life friends online also report(feeling closer to them than those who just communicate with each other face-to-face,implying a strengthening of their___35___.Why would digital communication beat human contact?The regions are complex,but may have something to do with the fact that users can control their expressions of sadness and other emotions they may be having via IM without having to___36___emotional elements such as tears,which some may consider as embarrassing or sources of___37___.Studies also show that the anonymity(匿名)of writing on a device blankets the users in a sense of safely.Prior research has shown that expressive writing itself can"vent"emotions and provide a sense of relief—and doing so,knowing that your words are reaching a(n)___38___friend may be even more therapeutic.Researchers also found that introverted participants reported more relief from IM conversations when they were distressed than extroverts did.In fact,introverts care deeply for their friends,family and colleagues,but even the most socially skilled ones sometimes long for a free___39___from having to socialize or having to talk on the phone.This is what the Internet___40___offers:the chance to connect—but ins(剂量)and from behind a screen.III.Reading Comprehension(45分)Section ADirections:For each blank in the following passage there are four words or phrases marked A,B, C and D.Fill in each blank with the word or phrase that best fits the context.A skywell,or"tian jing",is a tvpical feature of a traditional home in China.___41___a northern Chinese courtyard,or“yuan zi”a skvwell is smaller and less exposed to the outdoor environment.They are___42___seen in homes dating to Ming and Qing dynasties,which were designed to____43_____different generations of relatives.Although a skywell's size and design vary from region to region,it is always rectangular and located in the Core of a house,either___44___by rooms on four sides or three sides plus a wall. Skywells were designed to cool buildings before air-conditioning existed.When wind blows above a skywell house,it can enter the indoor space through the opening.Because outdoor air is often cooler than indoor air,the___45___breeze travels down the walls to the lower storeys and create air___46___by replacing warmer indoor air,which rises and leaves through the opening.The main purpose of a skywell is to allow in light,improve ventilation(通风)and___47___ rainwater.In Huizhou,a skywell is small but tall,and the rooms around it can___48___sunlight on hot days,enabling the bottom of the skywell to stay cool.___49___hot air inside the house can rise and escape through the opening above the skywell,which“works just like a___50___”As a(n)___51___space between indoor life and the outdoor environment,a skywell acts as an effective heat buffer(缓冲)to shield residents from the hot air outside.But the largest part of skywell's cooling effect actually comes when there are bodies of water in the enclosure.Evaporated water cools hot air,a process known as evaporative cooling which is___52___in Huizhou skywells.In the past,Huizhou families collected rainwater in their skywells because they believed this could safeguard and boost their wealth.Skywells therefore have channels around them to___53___rainwater coming from the roofs.Though existing in China for hundreds of years,in recent times they have often been forgotten by people who prefer modern___54___.Over the past two decades,however,due to a___55___of traditional Chinese architecture,skywell buildings have been making a comeback.41.A.Parallel with B.Different from. C.Close to D.Symbolic ofmonly B.rarely C.apparently D.currently43.A.bind B.gather C.house. D.honor44.A.enclosed B.separated C.accompanied. D.replaced45.A.calming B.refreshing C.incoming. D.upcoming 46,A pollution B.pressure C.current. D.circulation47.A,promise B.harvest C.stop. D.process48.A.block out B,bathe in C.allow for. D.let out49.A.Nevertheless B.Meanwhile C.Similarly D.Rather.50.A.well B.column C.chimney. D.ceiling51.A.ideal B.leisure. C.alternative. D.transition52.A.well-reflected B.well-shaded. C.well-developed. D.well-organized53.A.collect. B.purify. C.drain. D.evaporate54.A.techniques. B.facilities. C.styles. D.inventions55.A.reunion. B.reminder. C.renewal. D.rearrangementSection BDirections:Read the following three passages.Each passage is followed by several questions or unfinished statements.For each of them there are four choices marked A,B,C and D.Choose the one that fits best according to the information given in the passage you have just read.(A)As mountains go,1,642-foot Squaw Peak isn't particularly imposing.But its inviting views of western Massachusetts have tricked hikers into becoming less cautious among its steep,slippery cliffs,resulting in countless injuries and even deaths.Henry Grant,a week before starting his freshman year,respected Squaw Peak's record.As such,he stayed a good ten feet from the edge while waiting for his mother to catch up to him one day in August2019.He watched15or so other hikers enjoy the view;one hiker,around60 and dressed in pink,was peeking over the lip of the cliff with her husband.Suddenly he heard something frightening:“Paula!Paula!”a man yelled frantically.Grant turned around.The woman in pink was nowhere to be seen.Several hikers immediately started looking for her.Uncertain they could help,Grant and his mother headed down the trail.But when he saw hikers still searching,he decided to lend a hand.“My young dumb brain was like,I can do it,"he says.After15minutes of scrambling over rocks,Grant spotted a figure in pink.The woman had fallen about75feet.Miraculously,she was alive.“Paula!”Grant shouted.“Paula.Is that you?”The woman barely responded.She was clearly hurt and delirious.Grant called911and waited,but she kept trying to move,and every time she moved,she slipped a little more.Afraid that in her disorderly state of mind she might fall off the rock to her death,Grant crawled on all fours up a tight,narrow path,gaining friction by digging into the dirt with his fingers and feet until he reached Paula.Securing himself against a tree,Grant tried to keep her mind off the pain by intervening with questions;“Where are you from?What do you do for a living?Do you have kids?”About 45minutes later,first responders arrived,To reach them,a rescuer lowered down and lifted Paulaup.Paula,who has fully recovered,is Paula Kaplan-Reiss,a New Jersey psychologist who had traveled to the Berkshire mountains of Massachusetts for some relief following her mother's death.Instead,she met a young man who,as she stated in a letter to the Boston Globe,was her new hero.56.Paula's accident on Squaw Peak is most likely the result of_________.A.the heavy blow caused by her mother's deathB.the slippery cliffs that resulted in many injuries and deathsC.her being less safety-conscious at the breathtaking views.D.her husband's neglect of care while accompanying her57.What does the underlined word“delirious”in Paragraph6mean according to the context?A.Unable to move.B.Unable to stay conscious.C.Unable to talk.D.Unable to think clearly.58.Why did Grand keep asking Paula questions?A.To distract her attention from the pain.B.To find out her condition.C.To encourage her to hold on.D.To get to know her better.59.What kind of person is Henry Grant according to the article?A.Dumb and brave.B.Decisive and sensible.C.Respectful and caring.D.Reserved and calm.(B)While writing plain English is no challenge,most of us struggle to find words or phrases to perfectly fall in place with the content.To help you improve your writing skills in English,we have collected some of the best web resources dedicated to this mission.Grammarly●Grammarly is one of the best online resources togrammarly significantly improve your vocabulary and writing.Itis basically an online word processor,which goes beyond othersin correcting over250types of English mistakes.Thespell-checker and vocabulary enhancer are the standout features of Grammarly.●Since the Grammarly app is also available for your web browser,you can simply install the extension and edit all of your Emails,social media posts,or any content that you create from your web browser.●Although Grammarly is offered as free installation,a premium plan does exist which costs around$29.95/month.Thesaurus●Thesaurus is one of the vital tools that every goodEnglish writer has in their storehouse.Building onvocabulary is essential and that is what Thesaurus justoffers.Thesaurus helps users by providing alternativewords and phrases to perfectly express themselves.Italso offers the best collection of synonyms and antonyms.●Overuse of cliches.adverbs or bulky phrases is some examples of poor writing,which needs to be addressed.In this case,the Thesaurus has a collection of some of the most overused expressions that must be avoided in written English.●Sharpen your English skills with this powerful online and mobile application tool for free. Hemingway App●The Hemingway App is a wonderful web-based and desktop software to help you edit your written English.It tackles a lot of subtle differences in English writing,like very complex sentences,uses of passive voice and much ing Hemingway App,all of your wordysentences are highlighted in yellow and irrelevant content in red.●The Hemingway app also provides a readability score for theentered text,which you could use to analyze the structure of thecontent you've written and build a connection with your readers.●Though available as a free version for web interfaces,thestandalone desktop software for Mac and Windows costs$9.99/month.60.Which of the following can be learned from the passage?A.Grammarly is primarily focused on helping improve spelling and grammar in writing.B.Thesaurus offers a large collection of word entries to enhance vocabulary.C.The Hemingway App's premium desktop software is available for a one-time payment of S9.99.D.The Hemingway App assigns a distinct color to each type of grammar mistake it detects in the text.61.If you expect to objectively assess how effectively your content will connect with your readers,you are likely to turn to______.A.GrammarlyB.ThesaurusC.Hemingway AppD.all62.Who are probably NOT the intended readers of this passage?A.Fiction writers looking for real life materials to spark their creativity.B.Non-native English speakers wanting to improve their writing proficiency?nguage enthusiasts interested in exploring different web-based tools.D.Magazine editors whose role involves reviewing and polishing/manuscripts.(C)I was among31murderers sent to the Louisiana State Penitentiary in1962to be executed or imprisoned for life.We were unskilled,impulsive and uneducated misfits,mostly black,who had done dumb,impulsive things—failures,rejects from the larger society.Now a generation has passed since I've been here,and everything is much the same as I found it.The vast majority of us are handed over to suffer and die here so politicians can sell the illusion that permanently putting.people to prison will make society safe.Getting tough has always been a"silver bullet",a quick FIX for the crime and violence that society fears.Each year in Louisiana—where excess is a way of life—law-makers have tried to outdo each other in legislating harsher penalties.The only thing to do with criminals,they say,is get tougher.In the process,the state boasts one of the highest look-up rates in the country,and imposes the most severe penalties in the nation.If getting tough resulted in public safety,Louisiana citizens would be the safest in the nation. They're not.Louisiana has the highest murder rate among states.Prison,like the police and the courts,has a minimal impact on crime because it is a response after the fact,Ht doesn't work. The idea of punishing the few to discourage the many is fake because potential criminals either think they're not going to get caught or they're so psychologically distressed that they don't care. about the consequences of their actions.The threatened punishment,regardless of its severity,is never a factor in the equation.Prison has a role in public safety,but it is not a cure-all.The only effective way to contain crime is for society to work to prevent the criminal act in the first place.Our youngsters must be taught to respect humanity of others and to handle dispute without violence.It is essential to educate and equip them with the skills to pursue their life ambitions in a meaningful way.As a community, we must address the adverse life circumstances that breed criminality.These things are not quick, and they are not easy,but they are effective.Politicians think that's too hard a sell.They want something they can point to at re-election time.So the drumbeat goes on for more police,more prisons,more of the same failed policies.Ever see a dog chase its own tail?63,Which of the following situations is not regarded as a"silver bullet"?A Employing a roundabout way to help students correct their mistakes.B.Setting up refuges to shelter the homeless war victims.C.Training farmers with farming techniques to help them out of poverty.D.Adopting effective policies to save economy from worsening.64.According to the passage,law makers'failure to make proper legislation is due to the factthat_______.A.they are proud and boastful of high lock-up ratesB.they fail to address the root of the problemC.they don't treat people of different races alikeD.they give priority to precaution over punishment65.The idiom best describing the effective way to ease the severity of crime in Louisiana is_____A.turn over a new leaf.B.get a kick out of itC.an eye for an eye.D.prevention is better than cure66.What is the best title for the passage?A.Prisons—A Tool for Election.B.Why Prisons Don't WorkC.An Appeal from a Murderer.D.Why Society Is a Safer PlaceSection CDirections:Read the following passages.Fill in each blank with a proper sentence given in the box. Each sentence can be used only once.Note that there are two more sentences than you need.A.They are culturally distant,and so have far less borrowed European vocabulary too.B.This more than anything else accounts for the difficulty of the language.C.Indeed,none of the hardest languages is written with the Latin alphabet used by most European languages.D.But foreign writing systems need not be difficult.E.The overall hardness of a language can be seen as the sum of the difficulty of its writing system,sounds,words and grammar.F.But just as hart is the problem of languages that make distinctions our language does notWhich Languages Take the Longest to LearnThe difficulty in learning a foreign language lies not only in its inherent complexity.The main reason a language is hard is that it is different from your own.What underlies the difficulty of such languages for an English-speaker?The first thing many learners will think of is the writing system. ______67______Chinesestands out for its difficulty.It is commonly said that a learner must memorize around2,000characters to be able to read a newspaper.But even this estimate is criticized.Someone with2,000characters will still have to look up unfamiliar ones in every few lines of text.A second way languages can be hard is with sounds and distinctions that do not exist in the learner's language,To an English-speaker,the novelties include the clicks of many African languages._______68_______Mandarin and Cantonese have tones,meaning ma with an even pitch and ma with a falling one are different words.The vocabulary obviously matters too.Most European languages share an ancestor(called proto-Indo European)and so their words,too,often come in related pairs.If you know water in Spanish is agua,it is easy to figure out Italian acqua and English nguages unrelated to the European ones(Arabic from the Semitic family,or Chinese from the Sino-Tibetan one) will not only lack the“genetic”overlap in vocabulary.____69______.Finally,there is grammar.Many people associate tricky grammar with long lists of endings that change according to a word's use in a sentence Many languages even feature an ending on verbs indicating how the speaker knows the information to be true._____70_____If you want to learn a language just for fun,start with Swedish,If you want to accumulate an impressive number.Stay in Europe.But if you really want to impress. mastering Mandarin is the sign of the true linguistic Ironman.IV.Summary Writing(10分)71.Directions:Read the following passage.Summarize the main idea and the main point(s)of the passage in no more e your own words as far as possible.Does Reading Improve HealthWhen thinking about our well being and taking care of ourselves,some things that we should do are harder than others.Reading is one of the easier ones.What follows are a number of ways in which reading can help maintain and improve health.Reading allows you to de-stress by unplugging and escaping.In one study,reading was found to be as effective as yoga and humor in reducing subjective feelings of stress over a30-minute period,as well as blood pressure and heart rate.Note that a good old-fashioned book or a dedicated eBook reader is the best way to do this.Readers may live longer than non-readers.One study found that this was supposed to be due to the effect that reading has on maintaining cognitive abilities over time.In another study of individuals aged64and over,those who read at least once a week were less likely to experience cognitive decline than those who did not.At the14-year mark of the study,and regardless of educational level,those who read more enjoyed greater protection.This effect is maintained into readers'80's.Bibliotherapy,or the use of various reading materials for the promotion of psychological health,is a well-known aid to mental health treatment.Bibliotherapy can consist of any type of literature and may include self-help books,focused readings,first-hand accounts of others' experiences,and even relevant fiction.This can be a powerful strategy and has been used successfully to reduce depression,suicidal thinking,anxiety,stress and etc.The benefits of reading are innumerable and reading is a low to no-cost activity.Cheap and no-cost books are everywhere,Public libraries continue to be one of the most amazing resources. If you aren't a natural reader,you have nothing to lose by giving it a try.第二卷V.Translation(15分)Directions:Translate the following sentences into English,using the words given in the brackets.72.虽然青少年爱和父母顶嘴,但是他们内心是尊重父母的。
7a2007

Unit2 Let ’s play sports!Task班级姓名学号等第书写________【学习目标】1.学会根据提纲组织写作材料。
2.熟练运用本单元所学单词、词组、句型组织语言。
3.合理架构文章,向别人介绍自己的体育爱好。
【重难点】1.重点:书面描绘各种体育爱好。
2.难点:学会表达喜欢某种体育活动的相关信息。
本课通过对David 体育爱好的描述,着重学习一些短语,句型,在写作前理清思路,从而能够完成介绍喜欢的体育运动的短文。
3.通过查字典和教材参考书了解以下单词和词组的用法,并将此项预习内容写在课堂笔记上。
team, match, hero,talk about/ of, watch matches on TVI often play basketball with my friends after school.We often talk about basketball and watch basketball matches on TV. He is my hero! 【学法指导】1.自主学习记忆本课单词,重点短语和句型并标记疑点。
2.小组或同桌合作解决上述重难点,合作解决在学习中遇到的新问题,教师点拨。
【学习过程】A.课前预习:1.预习本课:在书上用铅笔,直尺划出重难点并标注疑点。
2.预习Page28-29课文,将下面的短语或句型在书中找出并加以记忆。
3.预习检测:1)校篮球队的一员_________________________________________________________ 2). 放学后和朋友一起打篮球_________________________________________________ 3) 谈论篮球_______________________________________________________________4) 看电视上的篮球比赛__________________________________________________ 5) 打篮球打得非常好_______________________________________________________6) 姚明是我最喜欢的篮球运动员。
AD生化-2007

在体内作用的依据. • 弥漫性Aβ斑块主要含Aβ17~40,而老年斑主要含
Aβ1~42,所以弥漫性斑块很少变成典型的老年斑. • APP转基因小鼠出现大量Aβ沉积,对神经原损伤并不严
• 体外实验:正在发育的神经原依赖于 NGF,否则产生蛋白合成-依赖凋亡.
• NGF是涉及调节正在发育的基底胆碱能 神经原的存活和分化的重要因子之一.
2021/1/7
SP
• SP:弥漫性斑块及典型SP • 弥漫性SP以Aβ17~40为主,典型SP以
Aβ1~42为主. • 区别:典型SP周围围绕激活的小胶质细胞
2021/1/7
神经细胞凋亡
• 程序性细胞死亡(programmed cell death ,PCD): 为功能性概念.指以发育为背景 的细胞生理性死亡.
2021/1/7 伤的继发现象.
AD的神经病理
• 神经原纤维缠结(NFT) 双螺旋细丝(PHF)
• 神经纤维网状细丝(NT) • 老年斑(SP)或神经炎斑(NP)
β-淀粉样蛋白(A β)沉积
2021/1/7
神经病理定位
• NFT
内嗅区
边缘系统周围同生皮质 的Ⅱ及Ⅵ层 海马
扁桃体
额叶和颞叶相关新皮层 的Ⅲ层和Ⅴ层 基低前脑胆碱能神经原
kinase • PKA:protein kinase A
2021/1/7
重要激酶
• PKC:protein kinase • CaM Kinase:CaM-dependent kinase • CK-1:casein kinase 1 • SAPK/JNK:stress-activated protei胞外老年斑是有毒的
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
6
(2) 无心外圆磨床
Байду номын сангаас
无心外圆磨床的工作原理
7
2.6.2
平面磨床
图2-56 平面磨床的主要类型
8
9
1
磨床简介 :精度保证措施 主运动的转速高而要求稳定 的转速高而要求稳定, 主运动的转速高而要求稳定,故多采用带传动或内 连式电机等原动机直接驱动主轴。 连式电机等原动机直接驱动主轴。 砂轮主轴轴承广泛采用各种精度高、吸振性好的动 砂轮主轴轴承广泛采用各种精度高、 广泛采用各种精度高 压或静压滑动轴承。 压或静压滑动轴承。 直线进给运动多为液压传动。 直线进给运动多为液压传动。 多为液压传动 对旋转件的静、动平衡,冷却液的洁净度,进给机 旋转件的静、动平衡,冷却液的洁净度, 的静 的洁净度 构的灵敏度和准确度等都有较高的要求。 的灵敏度和准确度等都有较高的要求。
2.6
磨床简介 磨床简介
磨床
定义:用磨料,磨具 砂轮 砂轮、 定义:用磨料,磨具(砂轮、 研磨料等)为工 砂带 、油石 、研磨料等 为工 具对工件进行切削加工的机床, 具对工件进行切削加工的机床, 统称为磨床。 统称为磨床。 用途:精加工,工艺范围广, 用途:精加工,工艺范围广, 平面、 内外圆柱和圆锥面、 平面、 内外圆柱和圆锥面、螺 纹面、 齿面、各种成形面, 纹面、 齿面、各种成形面,都 可以用相应的磨床加工。 可以用相应的磨床加工。 种类:外圆磨床、内圆磨床、 种类:外圆磨床、内圆磨床、 平面磨床、工具磨床、 平面磨床、工具磨床、加工特 定零件如曲轴、 定零件如曲轴、花键轴等的各 种专门化磨床。 种专门化磨床。
2
2.6.1
外圆磨床
(1) M1432A型万能外圆磨床 型万能外圆磨床
3
万能外圆磨床的典型加工方式
4
万能外圆磨床应有的几种运动 万能外圆磨床应有的几种运动 砂轮旋转主运动n 砂轮旋转主运动n1,由电动机经带传动驱动砂轮主轴作 高速转动。 高速转动。 工件圆周进给运动n 转速较低,可以调整。 工件圆周进给运动n2,转速较低,可以调整。 工件纵向进给运动f 通常由液压传动, 工件纵向进给运动f1通常由液压传动,以使换向平稳并能 无级调速。 无级调速。 砂轮架周期或连续横向进给运动f 可由手动或液压实现。 砂轮架周期或连续横向进给运动f2可由手动或液压实现。 辅助运动:砂轮的横向快进、快退和尾座套筒的缩回, 辅助运动:砂轮的横向快进、快退和尾座套筒的缩回, 它们也用液压传动。 它们也用液压传动。
