Are there multiple proteolytic to c-Fos, c-Jun and p53 protein degradation in vivo
阿米巴、阴滴、杜氏原虫

五、流行
全世界分布,估计感染者有1.8亿人 传染源----滴虫性阴道炎患者和带虫者,以及男性感染者
传播途径----直接传播和间接传播 滋养体抵抗力强
六、防治
1、普查普治
甲硝唑(灭滴灵):p.o 200mg.tid + 200mg栓剂放入阴道, 连用7-10天。
替硝唑
局部用药:滴维净、洁尔阴,并用1:5000高锰酸钾、 1%乳酸或0.5醋酸冲洗阴道。
Cysts of Giardia intestinalis (lower right) and oocysts of C. parvum (upper left) labeled with commercially available immunofluorescent antibodies
4)寄生环境的影响
致病过程
典 型 病 理 : 烧 瓶 状 溃 疡
接触性杀伤(酶溶、细胞 毒、胞噬、协同损伤)
临床表现: 1)肠内阿米巴病:
占多数,表现为痢疾、肠出血、肠穿孔 或阑尾炎, 阿米巴肿。
急性期(普通型、暴发型):阿米巴痢疾腹痛、腹
泻、脓血样大便、腐败腥臭味等痢疾 样症状。
慢性期:溃疡时发时愈,病灶组织增生,肠壁增
1. COLONIZATION OF THE LARGE INTESTINE flask-shaped lesions:
proteolytic enzymes :
Symptoms:
Ulcers may form sinuses and extend into the submucosa
外界
人体内
口
ELISA:敏感性高、特异性强、重复性好, 抗原要求更高。 McAb-ELISA :检测粪中抗原
欧姆龙PLC通信协议

欧姆龙 PLC 通信协议参考: W342 --SYSMAC CS/CJ Series Communications Commands欧姆龙通信命令可分为两类:1: C-mode commands 只可通过串口通讯 2: FINS commands 既可通过串口通讯也可通过各类网络通信(适应性较强) 面只讲 FINS 命令一、命令发送:FINS 直连发送命令如下:FINS command code见下表5-1-1 FINS COmmandSThefdlwirg table IlStS the FINS CCXnmands.命令后面紧跟着就是内存区域寻址,见下表Command Code 后面紧跟着需要访问的地址,地址可分为按字地址或按位地址,取决于你需要访的的是字还是某一位。
由紧跟着Command Code 后面的那个字节( I/O memory area designation )区分是读取字还是读取位,还是写入字或写入位,具体定义见下表:5-2-2 I/O MemOry AddreSS DeSignatiOnS按字地址:选取表中Data Type 列中为Word 的命令(命令在Memory area code 内)按字地址的三个地址位中,只使用前两个,最后一个字节为Ascii 码”00”,其后跟两个字节为需要传输的数据量,然后紧跟着就是传输的数据,数据高位在前低位在后。
例如从H12 开始读取7 个字的数据,命令为:0101 B2 001200 0007 例如将W3、W4、W5 分别置数据1234 、ABCD、7890,命令为:0102 B1 000300 0003 1234ABCD7890按位地址:选取表中Data Type 列中为Bit 的命令(命令在Memory area code 内)按位地址的三个地址位中,前两个指示位所在的字,最后一个字节指示位在字中的位置(0~15),其后跟两个字节为需要传输的数据量,然后紧跟着就是传输的数据,每一位的值用一个字节的数据代替,当寻址的位为0 时用ascii码“ 0”代替,当寻址的位为1 时用ascii 码“ 1”代替。
A programming language extension for probabilistic robot programming

A Programming Language Extension for Probabilistic Robot ProgrammingSebastian ThrunSchool of Computer ScienceCarnegie Mellon UnivrsityPittsburgh,PAAbstractIn recent years,probabilistic techniques have led to im-proved solutions for many robotics problems.However, no general tools are currently available to aid the de-velopment of probabilistic robotic software.This paper presents a programming language extension to C++that integrates probabilistic computation and learning.Its two main ideas are to make probability distributions as usable asfloating-point numbers,and to smoothly in-tegrate function approximators into C++code.These innovations facilitate the development of robust,proba-bilistic robot software,as illustrated by a proto-type pro-gram for a mail delivery robot.1IntroductionRobots,like other sensor-based systems,have to cope with uncertainty.Uncertainty arises from sensor limitations and unpredictable aspects of robot environments.In recent years, there has been an increased interest to apply probabilistic techniques and learning algorithms to problems in robotics. It is now an established fact that in many real-world domains, probabilistic algorithms are more robust than traditional non-probabilistic solutions(see[Thrun,2000]for a survey).How-ever,virtually all published algorithms in thisfield are tuned to specific robot problems and little,if any,assistance is avail-able for developing new probabilistic programs.This ob-servation raises the question:Can we distill out the princi-ples of probabilistic robotics,and package them in a domain-independent way?And if so,what are these principles? This paper describes an attempt to develop a special-purpose programming language for developing probabilistic robot programs.This language,called CES(short for:C++ for embedded systems),is an extension of C++,which to-gether with C is arguably the most popular programming lan-guage in robotics to date.CES offers two new basic fea-tures,currently not found in any programming environment: A mechanism for computing with probability distributions, and a mechanism for incorporating learning algorithms.In particular,CES makes programming with probability distri-butions as easy as programming withfloating-point numbers. The learning mechanism allows for data-driven adaptation of software,so that robot software can be shaped through teach-ing.Several existing implementations illustrate that our ap-proach reduces the programming effort for probabilistic soft-ware by an order of magnitude(or more);the one discussed here is a gesture-driven mail-delivery robot,whose programs is only137lines long but requires approximately two hours of training to be functional.2Probabilistic Computation2.1Probabilistic Data TypesA basic computational entity in CES is a probability distribu-tion.Probability distribution are defined over sets of events of underlying random variables.If the event space of a random variable is of a type base-type,the templateprob<base-type>defines a probability distribution over the type base-type. The base type may be any atomic numerical data type(int, double,etc.)or composite data type(struct,vector, etc.).For example,if the base type is double,the declara-tionprob<double>x;declares a variable x that is a probability distribution over the one-dimensional continuous space of all doubles.Just as there are multiple ways to define constants in C++, there are multiple ways to define constants for probabilistic variables.CES offers four different approaches:1.Enumeration.A probability distribution can be specifiedby a list of the type{{v1,p1},{v2,p2},...,{vN,pN}} where each tuple v,p specifies a discrete event v and its associated probability p.The length of the list may vary.For example,the statementx={{1,0.5},{2,0.5}};assigns to the probabilistic variable x the distribution that assigns probability to the two values and,and prob-ability to all other values in the domain of the variable’s base type.2.Type conversion.Point-mass distributions,which assignall probability mass to a single value in the base-type,can be specified by this very value.For example,the assign-mentx=3;assigns to x a point-mass distribution centered on the value3.This statement is an example of an implicit type conver-sion from base types to their probabilistic generalizations.mon discrete and continuous distributionsare offered through a library.For example,the assignments x=UNIFORM1D(0.0, 1.0);y=NORMAL1D(0.0, 1.0);assign to x and y a(one-dimensional)uniform distribution in,and a normal distribution with mean0and vari-ance1,respectively.4.More complex probability distributions can also be con-structed using the probloop command,which will be de-scribed further below.Type conversions are also straightforwardly defined.Of par-ticular interest is the conversion of a probabilistic variable to its base type,and vice versa.A statement of the type x=y;assigns to x a point-mass distribution if x is probabilistic, and y is its base type.Conversely,if y is the probabilistic variable and x is its base type,this statement assigns to x the expectationFor example,the code segmentprob<double>x={{1,0.3},{2,0.7}};double y=x;assigns to y the value.Notice that the expectation of cer-tain base types(e.g,.int)might not be part of their domains, in which case the result will be truncated.2.2Arithmetic OperationsAll arithmetic operators in C++are applicable to probabilis-tic variables as well.However,probability distribution are more complex than numbers.Consequently,statements af-fecting more than one probabilistic variable can be interpreted in more than one way.To see,consider the examplez=x*y;where x and y represent probability distributions.Two pos-sible interpretations of this statement are:(1)it is a multi-plication of two independent random variables defined over different(and independent)event spaces,or(2)it is a mul-tiplication of two probability distributions defined over the same event space.To illustrate these different views,let us assume we have the two probabilistic variablesx={{1,0.2},{2,0.8}};y={{1,0.5},{2,0.5}};According to ourfirst interpretation,x and y correspond to independent events.The set of possible outcomes of the mul-tiplication is then,,and,since each of the two underlying random variables may independently take on the values or .Because of our independence assumption,the resulting distribution is then:z={{1,0.1},{2,0.5},{4,0.4}};Under the second interpretation,both random variables take on the same value at all times.The product of x and y is then the product of the individual probability measures,which(af-ter normalization)is the following:z={{1,0.2},{2,0.8}};To see,we note that the product probability that the under-lying event is1is given by. Similarly,.After normalization, the resulting distribution is the one specified above.While there are more ways to interpret statements like the ones above,these are the two most important ones.We will call operations that adhere to thefirst interpretation type-I op-erations,and those that correspond to the second type-II op-erations.They will now be defined in more general terms.Type-I Operations:Let“”be a binary(2-argument)op-erator(e.g.,,,,,etc.),and let x and y be probabilistic variables over the same base type.Then x y is also a proba-bilistic variable that represents the following probability dis-tribution:Here is an indicator variable that is1if its argument is true, and0otherwise.Put into words,the probability assigned to the event that x y takes on a value is the total probability of all values and in the domains of x and y such that equals.In probability variables with discrete base-type,the integrals are replaced by sums.As the reader should quickly verify,this general definition is compliant with the example in the beginning of this section.In our implementa-tion,type-I operations are overloaded over the conventional function symbols.Type-II Operations:Type-II operators manipulate proba-bility measures directly,assuming that all operands are de-fined over the same event space(and hence fully dependent). As before,let“”be a binary operator,and x,y probabilistic variables.Then x y is the a probabilistic variable with the following distribution2.3Probabilistic Statement ExecutionAfinal,powerful tool enables programmers to extend proba-bilistic type-I calculations to more complex elements of C++, such as loops,recursions,and complex functions. Suppose we would like to manipulate the elements of aprobabilistic variable x via some complex function,but is defined in conventional,non-probabilistic variables.Follow-ing the idea of type-I operations,the resulting distribution is given by the following integral(or sum,in the discrete case):(1)The probloop command generalizes this equation to multiple input and output variables.In particular,a probloop com-mand is of the formprobloop(x1,...,xN;y1,...,yM){ <sequence-of-statements>}where the<sequence-of-statements>implements the function.The variables x1through xN are input vari-ables,and y1through yM are output variables of.All of these variables must be probabilistic,though not necessar-ily of the same type.Inside the loop,however,these vari-ables are reduced to their non-probabilistic base type—just as the use of in the definition of type-I operators applied to the base-type elements of the participating probabilistic vari-ables.This construct makes it possible to‘bootstrap’arbitrary C++statements to probabilistic variables.Let us illustrate the probloop via an example.Suppose x and y are given byx={{3,0.4},{4,0.6}};y={{6,0.2},{7,0.8}};Furthermore,consider the statementprobloop(x,y;z){if(x> 3.5)then z=0else z=y;}with input variables x and y,and output variable z.A truly probabilistic interpretation of this statement will execute the then-clause with.4probability,and the else-clause with.6 probability.The resulting variable y hence will represent the following distribution{{0,0.4},{6,0.12},{7,0.48}};In fact,this is exactly what the probloop command gener-ates.Conceptually,the probloop is executed over all val-ues of the input variables,for which it calculates the corre-sponding values of z,while keeping track of the correspond-ing probabilities defined by the input distributions.The probloop can be applied to any sequence of C++com-mands,thereby generalizing the idea of probabilistic compu-tation to loops,nested loops,recursion,and any other element of conventional C++programming.In fact,the binary opera-tors discussed above can all be viewed as special cases of the probloop command.The probloop gives a programmer control over the scope of dependencies in his program.For example,the state-mentsx={{10,0.4},{20,0.6}};probloop(x;y){y=x;y=y-x;}will return the point-mass distribution centered on0.This is because no matter what value x takes,y will be0.In contrast, the same statements without the probloop:x={{10,0.4},{20,0.6}};y=x;y=y-x;will treat x and y as independent variables in the second state-ment,and hence returny={{-10,0.16},{0,0.48},{10,0.36}}; 2.4Implementation of Probabilistic Variables CES separates the interface from the actual implementation of probabilistic variables.However,since CES allows pro-grammers to define distributions over arbitrary data types, many operations cannot be implemented exactly.For exam-ple,probabilistic variables of the type prob<double>,if implemented exactly,would require as many parameters as there are different doubles(effectively GB of RAM).Currently,two implementations exist,using two different representations for probabilistic variables:1.Histogram representations were historically thefirst[Thrun,1998].They represents probabilistic variables by histograms over their domain.For example,a variable of type prob<double>might be approximated by a histogram of cells,covering the support of the distribution in equi-distance intervals.Unfortunately, the histogram representation is not applicable to arbi-trary probabilistic variables(e.g.,variables defined over complex data structures),for which reasons it was later abandoned.2.Sampling.Here we represent distributions by a set of(weighted)samples,drawn from the base type(domain)ofa distribution.For example,consider a probabilistic vari-able x of type prob<double>.This distribution is rep-resented by values of type double,which are drawn according to the probability distribution x.Sample repre-sentations are common-place in the Markov Chain Monte Carlo(MCMC)literature.They have two pleasing proper-ties:First,they can accommodate any base type,and sec-ond,under very mild conditions[Gilks et al.,1996]they converge uniformly to the true probability distribution asincreases.Under the sampling representation,implementing constants, type-I operations including the probloop command is re-markably straightforward.For example,the following state-mentsprob<double>x=UNIFORM1D(0.0, 1.0);prob<double>y=NORMAL1D(0.0, 1.0);prob<double>z=x+y;are translated into:Generate samples according to a uni-form distribution,and memorize all samples as x.Subse-quently,generate samples according to a normal distribu-tion for y.Finally,generate pairs of samples from the sets of samples representing x and y,and memorize their sum as z.3TrainingThe second,important aspect of CES is the ability to tune code using built-in learning mechanisms.Consider,for exam-ple,a robot programmed to perform mail delivery.Imagine that the robot occasionally gets lost,or collides with obsta-cles.One way to remedy this problem would be to analyze and modify the software until the problem isfixed.An alter-native way would be to present the robot with target values of the desired behavior in specific situations.For example, if a robot collides,the programmer could specify that the de-sired behavior(in this situation)would have been a left-turn, whereas the robot executed a right-turn.Similarly,for a robot who lost track of its position,a programmer could tell the robot the correct location.Such situation-specific feedback can be interpreted as training examples for the desired output of the robot in specific situations.The key idea of learning in CES is similar to Jordan and Rumelhart’s notion of learning with a distal teacher[Jor-dan and Rumelhart,1992].Imagine a function approximator (such as a neural network)is used in the program code.One way of training the neural network would be to provide target outputs for the network,and use Back-propagation to tune the weights.However,this would require that target signals are available for the neural network.An alternative view,put forward in[Jordan and Rumel-hart,1992](and adopted here)is to provide target signals for variables that in some way depend in a function approxima-tor.Such a“distal teacher”approach releases the programmer from the burden of having to provide target values for a func-tion approximator directly.In our robot example,a specifica-tion that a right-turn was the better action is sufficient to train function approximator,as long as they influenced the actual control decision.On theflip side,such an approach creates a difficult credit assignment problem:that of assigning credit or blame to the function approximator from a“distal”target signal.Our ap-proach follows the rationale of Jordan and Rumelhart’s distal teacher.In particular,CES performs error minimization by gradient descent.But whereas in Jordan’s approach gradients were propagated through a neural network,CES propagates gradients through program code.The necessary gradients are all propagated“forward”through the code,so that no back-propagation phase is necessary.3.1Function ApproximatorsFunction approximators mapfloating-point values or vectors of such values into other values or vectors of values.They are declared via the following class template:fa<intype,outtype>;Here intype must the type of the input variables,and out-type must be the type of the output variables of the function approximator.Both can be doubles,vectors of doubles,or their probabilistic counterparts:double vector<double>prob<doube>prob<vector<doube>> Function approximator declarations require additional infor-mation:parameters specifying the type of function approxi-mator,the dimension of the input,and the dimension of the output.In addition,certain function approximators require additional parameters that specify their internal structure.For example,the declarationfa<prob<vector<double>>,prob<double>> net(twoLayerNeuronet,10,1,5); declares a neural network with5hidden units that maps a10-dimensional probabilistic vector to a one-dimensional proba-bilistic variable.Several other options are available,as doc-umented in CES,and users can program their own function approximators as long as they can be trained using gradient descent.Once declared,function approximators are used just like mathematical functions via the method fa::eval().For example,the following statement assigns to x the value of running the function approximator net on the variable y.x=net.eval(y);Type mismatches in assignments involving function approxi-mators are caught at compile time.The function train(),which is a member of probabilis-tic variables(and not of function approximators!),is used to for training.For example,the statementx.train(y);specifies that the desired value for the probabilistic variable x is y(at the current point of program execution).Here both variables,x and y,are either of the same type,or x is of type prob<foo>if y’s type is foo.CES then changes each function approximator that took part in the calculation of x accordingly.3.2ExampleTo illustrate these concepts,let us consider an example:a program that processes a sensor scan(e.g.,a sonar scan)and generates a motion command for the robot that aligns it paral-lel to the nearest wall.Let us assume thatfinding the orienta-tion of the nearest wall is a difficult problem,which we much rather train by examples than code by hand.However,once the wall orientation is known,generating the corresponding turning command is trivial.How would one go about cod-ing such a routine?Obviously,the wall orientation cannot be determined with certainty;hence,we use a probabilistic variable:prob<double>orientation;Next,we need a function approximator that maps sensor mea-surements(which are assumed to reside in a vector)to the orientation:fa<vector<double>,prob<double>>net(twoLayerNeuronet,24,1,6);orientation=net.eval(sensors);The motion command is then calculated using a conversion back to doubles.Here is a example:double turn_cmd=dou-ble(orientation)+ 3.1415;Andfinally,we need to train the code.If the correct mo-tion command resides in a variable targetFigure1:Training set result(top)and testing set result(bottom)of learning to estimate robot orientation(vertical axis)for a62second sequence(the horizontal axis is time).The white solid line indicates the true orientation.The small circles are samples,and the gray ares is the result of applying a Gaussian smoother to these samples.Notice that the orientation is tracked very well.Figure1shows,for a code segment similar to the one de-scribed here,the result of training.The solid white line de-picts the true wall angle as a function of time,for a randomlyrotating robot.The small dots are the samples,and the graylyshaded area indicates the robot’s probabilistic estimate which,after training,is quite accurate.3.3The Importance of Probabilities for LearningThe notion of probabilistic computation is essential for train-ing function approximators via gradient descent.This is be-cause conventional C++code is usually non-differentiable.An example of a typical C++statement is the following:if(x>15)then y=4else y=5;The gradient of the variable y with respect to the variable x,(a)(b)(c)Figure2:(a)The Real World Interface B21robot used in our research.(b)Schematics of the robot’s environment.(c)Plot of the robot trajectory(raw odometry)during8consecutive runs(11pieces of mail delivered).Shown here are also the raw sonar measurements.The robot reaches the various destination points with high accuracy,despite the rather significant error in the robot’s odometry.Table1shows the full program.Thefinal program is of lesser importance,since stripped of its comments it is nearly illegible(like most robot software!).More important is the process of getting there.Programming began with imple-menting an estimator for wall orientation(lines32-34and 53-58).This code uses Bayes rule to incorporate new sen-sor readings(line34)and convolution with a normal distribu-tion to accommodate robot motion(lines54-57).The map-ping from sonar sensors to angle estimates is realized using a neural network(line33)and trained using hand-labeled data (lines126/127),collected in a few minutes and labeled in less than an hour’s time.The wall orientation estimator operates in the interval;lines35-41and59-62generate an orien-tation estimate in,assuming that the initial robot ori-entation is known(for breaking symmetry).Next,we imple-mented a localization algorithm in--space,which utilizes the fact that a probabilistic orientation estimate is available by mapping sonar sensors(lines42-51and63-68).This esti-mator is again trained using a distal teacher(lines128-131). Next,we implemented a gesture recognizer(lines70-72) which uses two neural networks to map images to gestures (one for each hand that can be raised as a gesture).This net-work is trained with a few minutes worth of data(lines132-135).The probabilistic output variable becomes input a stack of target locations(lines74-99).Finally,a very rudimentary way-point navigation system is implemented that drives the robot to its predefined locations(lines102-122)while stop-ping if the path is blocked(line121).Here probabilistic vari-ables are converted back to numerical values(lines119/120) to determine the actual velocity commands for the robot’s motors.The use of probabilistic data types in this program did not require any specific skill,and the entire program was implemented and trained in a matter of one day.We found that our CES program is robust enough to con-trol a mobile robot reliably in a crowded environment.In extensive tests,the robot navigated for long periods of time (like:2hours)in a populated corridor without ever loosing its position or colliding with an obstacle.Figure2c shows an example trace(raw data),recorded during20minutes of con-tinuous deliveries(58,992sonar measurements,2,458odom-etry measurements).Notice that raw odometry is insufficient to track the robot’s position.Our program reliably navigated the robot to the correct location with acceptable accuracy(1 meter)and delivered all pieces of mail correctly.In tests with independently collected data,the error rate of the gesture interface was consistently below2.5%despite its simplicity (measured on138independently collected testing examples). Other examples are described in[Thrun,1998].5Related WorkSince CES computes with probability distribution,it is im-manently related to Bayes networks(BNs)[Pearl,1988].The relation between CES and BNs is best explained by an anal-ogy:CES is to BNs as are procedural(or object-oriented) programming languages to declarative ones(like Prolog,see also[Poole,1993]).In BNs,the inference and the knowl-edge representation are strictly separated,as is the case in Prolog;whereas in CES program statements are computa-tional,like in C and C++.This characteristic has multiple ramifications.For example,Bayes networks(like knowledge bases)can be used for inference from any subset of variables to any other.However,the representation does not include such powerful concepts as recursion,iteration,and nested function calls.CES,like C or C++,allows such things,but CES programs are computational statements that cannot be inverted,or marginalized.We therefore consider CES a vi-able alternative for software design with probabilisticflavor. Thefield of robotics has developed a multitude of special purpose languages for robot programming,such as[Kono-lige,1997;Simmons and Apfelbaum,1998].These lan-guages address important topics like concurrency and real-time control.Consequently,the issues addressed here are therefore entirely orthogonal.To our knowledge robotics lan-guage design has not addressed these issues before.The idea of learning with prior knowledge has been stud-ied extensively in the machine learning community[Russell, 1991;Towell and Shavlik,1994].Prior knowledge is usually represented in declarative form(e.g.,Horn clauses),but to our knowledge the idea of integrating learning into a procedural001:main(){002:003://=============Declarations==============004:fa<vector<double>,prob<double>>netSonar(twoLayerNeuronet,5); 005:fa<prob<vector<double>>,prob<double>>netX(twoLayerNeuronet,5), 006:netY(twoLayerNeuronet,5); 007:fa<vector<double>,prob<int>>netLeft(twoLayerNeuronet,5), 008:netRight(twoLayerNeuronet,5); 009:prob<double>alpha,alphaLocal,probRotation;010:prob<double>thetaLocal,theta,transVel,rotVel;011:prob<double>x,xLocal,y,yLocal,probTransl;012:prob<int>coin={{0,0.5},{1.0.5}};013:prob<int>gestureLeft,gestureRight;014:prob<vector<double>>newSonar(2);015:double alphaTarget,scan[24],image[300];016:double xTarget,yTarget,xGoal,yGoal,t,v;017:struct{double rotation,transl;}odometryData;018:struct{double x,y,dir;}stack[3];019:int targetLeft,targetRight;020:int numGoals=0,activeGoal;021:022://=============Initialization==============023:alpha=UNIFORM1D(0.0,M_PI);024:theta=UNIFORM1D(0.0,M_PI);025:x=XHOME;y=YHOME;026:027://=============Main Loop==============028:029:for(;;){030:031://----------------Localization----------------032:GETSONAR(scan);//get sonar scan033:alphaLocal=netSonar.eval(scan)*M_PI;034:alpha=multiply(alpha,alphaLocal);035:probloop(alphaLocal,coin;thetaLocal){036:if(coin)037:thetaLocal=alphaLocal;038:else039:thetaLocal=alphaLocal+M_PI;040:}041:theta=multiply(theta,thetaLocal);//robot’s orientation042:probloop(theta;newSonar){043:int i=int(theta/M_PI*12.0);044:int j=(i+12)%24;045:if(scan[i]<300.0)newSonar[0]=scan[i];046:if(scan[j]<300.0)newSonar[1]=scan[j];047:}048:xLocal=netX.eval(newSonar);049:yLocal=netY.eval(newSonar);050:x=multiply(x,xLocal);//robot’s x coordinate051:y=multiply(y,yLocal);//robot’s y coordinate052:053:GETODOM(&odometryData);//get odometry data054:probRotation=prob<double>(odometryData.rotation)055:+NORMAL1D(0.0,0.1*fabs(odometryData.rotation));056:alpha+=probRotation;057:if(alpha<0.0)alpha+=M_PI;058:if(alpha>=M_PI)alpha-=M_PI;059:theta+=probRotation;//new orientation060:if(theta<0.0)theta+= 2.0*M_PI;061:if(theta>= 2.0*M_PI)theta-= 2.0*M_PI;062:theta=probtrunc(theta,0.01);063:probTransl=(prob<double>)odometryData.transl064:+NORMAL1D(0.0,0.1*fabs(odometryData.transl));065:x=x+probTransl*cos(theta);066:y=y+probTransl*sin(theta);067:x.truncate(0.01);//new x coordinate068:y.truncate(0.01);//new y coordinate 069://------------Gesture Interface&Scheduler------------070:GETIMAGE(image);071:gestureLeft=netLeft.eval(image);072:gestureRight=netRight.eval(image);073:if(numGoals==0){//wait for gesture074:if(double(gestureLeft)>0.5){075:stack[numGoals].x=XA;//location A on stack 076:stack[numGoals].y=YA;077:stack[numGoals++].dir= 1.0;078:}079:if(double(gestureRight)>0.5){080:stack[numGoals].x=XB;//location B on stack 081:stack[numGoals].y=YB;082:stack[numGoals++].dir= 1.0;083:}084:if(numGoals>0){085:stack[numGoals].x=XHOME;//HOME location on stack 086:stack[numGoals].y=YHOME;087:stack[numGoals++].dir=-1.0;088:activeGoal=0;089:}090:}091:else if(stack[activeGoal].dir*//reached a goal?092:(double(y)-stack[activeGoal].y)>0.0){093:SETVEL(0,0);//stop robot094:activeGoal=(activeGoal+1)%depth;095:if(activeGoal)096:for(HORN();!GETBUTTON(););//wait for button097:else098:numGoals=0;099:}100:101:else{//----------------Navigation----------------102:xGoal=stack[activeGoal].x;103:yGoal=stack[activeGoal].y;104:probloop(theta,x,y,xGoal,yGoal;105:transVel,rotVel){106:double thetaGoal=atan2(y-yGoal,x-xGoal);107:double thetaDiff=thetaGoal-theta;//location of goal 108:if(thetaDiff<-M_PI)thetaDiff+= 2.0*M_PI;109:if(thetaDiff>M_PI)thetaDiff-= 2.0*M_PI;110:if(thetaDiff<0.0)111:rotVel=MAXROTVEL;//rotate left112:else113:rotVel=-MAXROTVEL;//rotate right114:if(fabs(thetaDiff)>0.25*M_PI)115:transVel=0;//no translation116:else117:transVel=MAXTRANSVEL;//go ahead118:}119:v=double(rotVel);//convert to double120:t=double(transVel);//convert to double121:if(sonar[0]<15.0||sonar[23]<15.0)t=0.0;122:SETVEL(t,v);//set velocity123:}124:125://----------------Training----------------126:GETTARGET(&alphaTarget);//these command are127:alpha.train(alphaTarget);//only enabled during 128:GETTARGET(&xTarget);//training.They are129:x.train(xTarget);//removed afterwards. 130:GETTARGET(&yTarget);131:y.train(yTarget);132:GETTARGET(&targetLeft);133:gestureLeft.train(targetLeft);134:GETTARGET(&targetRight);135:gestureRight.train(targetRight);136:}137:}Table1:The complete implementation of the mail delivery program.Line numbers have been added for the reader’s convenience.Functions in capital letters(GET...)are part of the interface to the robot.programming language is novel.The most related approach are evolutionary algorithms(EAs)[Koza,1992],which mod-ify program code directly instead of built-in function approx-imators.We believe that a stricter separation of learning and programming increases the human comprehensibility of pro-gram code,which is typically rather low for EAs.6ConclusionWe have presented a special-purpose language extension of C++for robot aimed at integrating probabilistic computation and learning into mainstream programming.The language condenses the essentials out of a large number of approaches in thefield of probabilistic robotics,by providing program-mers with mechanisms for handling uncertainty and learning. We conjecture that these mechanisms are essential for robust software development;however,the real strength of our ap-proach comes from the integration of these mechanism with conventional programming in C++.This research opens a range of interesting follow-up ques-tions,such as:Can the principles advocated here be stipu-lated to other programming languages and paradigms?Is it worthwhile to embed other learning approaches,such as rein-forcement learning,along with other credit assignment mech-anisms into mainstream programming?Is there a place for parametric representations of probability distributions in pro-gramming?How can a CES program be debugged,if ran-domness play a crucial part in its execution?Despite these open questions,we believe that our current results indicate that probabilistic data types and learning have a clear role to play at the core level of robotic programming language design.We also believe that the ideas presented here transcend beyond robotics,and are applicable to sensor-based embedded systems at large.。
AD637JQ中文资料

元器件交易网
AD637–SPECIFICATIONS (@ +25؇C, and ؎15 V dc unless otherwise noted)
Model TRANSFER FUNCTION CONVERSION ACCURACY Total Error, Internal Trim1 (Fig. 2) T MIN to TMAX vs. Supply, + VIN = +300 mV vs. Supply, – VIN = –300 mV DC Reversal Error at 2 V Nonlinearity 2 V Full Scale2 Nonlinearity 7 V Full Scale Total Error, External Trim ERROR VS. CREST FACTOR3 Crest Factor 1 to 2 Crest Factor = 3 Crest Factor = 10 AVERAGING TIME CONSTANT INPUT CHARACTERISTICS Signal Range, ± 15 V Supply Continuous RMS Level Peak Transient Input Signal Range, ± 5 V Supply Continuous rms Level Peak Transient Input Maximum Continuous Nondestructive Input Level (All Supply Voltages) Input Resistance Input Offset Voltage Min AD637J/A Typ
The AD637 is available in two accuracy grades (J, K) for commercial (0° C to +70°C) temperature range applications; two accuracy grades (A, B) for industrial (–40°C to +85°C) applications; and one (S) rated over the –55°C to +125°C temperature range. All versions are available in hermetically-sealed, 14-lead side-brazed ceramic DIPs as well as low cost cerdip packages. A 16-lead SOIC package is also available.
重复定义的错误MULTIPLE PUBLIC DEFINITIONS

c/c++语言中有很多地方要用到extern,但是如果没有真正的了解它的意义,会给编程带来很大的麻烦,为了使大家少走弯路,特祥细的说明一下。
对于比较小的程序,一般只有一个c文件和一个头文件,全局变量我们通常会直接定义在c文件中,在程序之前加int i定义。
如果要在头文件中定义有以下两种方法:用extern来声明:extern int i;这一句只是对变量i进行声明,在c文件的程序之前必须加上int i进行定义。
extern int i=0;这一句声明和定义都做了。
对于大一点的程序,有很多c文件和头文件,这个时候全局变量就必须在头文件中声明(不需要初始化),然后在一个c文件中定义(该初始化的要初始化)。
如果在头文件中定义,则编译的时候会出现重复定义的错误。
如果只有头文件中声明就会出现没有定义有警告。
*** ERROR L104: MULTIPLE PUBLIC DEFINITIONSSYMBOL: KMODULE: 222.obj (222)出现上述错误则是因为变量k重复定义,把你的头文件中的变量定义前加extern(只是变量声明不用初始化),再在某一个你要调用该变量的c文件的程序之前再定义(注意第一个调用的c文件要负责附带初始化该变量,其他调用的c文件就不需要初始化过程啦)今天调试时遇到了这个问题,以前都不注意这些警告错误,现在看来争取要做到:0错误,0警告。
中断中和中断外都调用了同一个串口打印函数,一直有上述的报警,没在意,今天调试时发现串口打印出了一些乱七八糟的东东,且程序也不知道跑哪里去了,很郁闷。
最后查到是上述这个问题导致的,现在解决办法为采用第二种办法,第一种办法据说要耗很多存储空间,以后慢慢体会。
说说几个小问题吧,一般我们在用KEIL的时候,只要编译器报- 0 Error(s) 一般我们都不去管多少个 Warning(s).了,一般这样程序基本都能运行,但是其实仔细想想,这里还是有问题的,否则编译器没事吃饱了撑得,报什么警告啊~~~今天来说说*** WARNING L15: MULTIPLE CALL TO SEGMENT这个问题!其实这个问题应该是引起注意的,有可能引起程序冲突,但是一般时候程序运行不会有问题,但是如果出来问题,那将会是很讨厌的问题.分析一下产生这一警告的一个根源是:例如在主循环里调用了一个函数,而在中断服务中,你又一次调用了同样的函数。
ailerontherapeutics

AILERON TherapeuticsProfile:AILERON Therapeutics is a privately held biopharmaceutical company located in Cambridge,Massachusetts,USA.AILERON Ther-apeutics is developing a revolutionary class of drugs,called Stapled Peptides,that have the capability to address thousands of currently 'undruggable'therapeutic targets and promising clinical applications for many human diseases.Website:About AILERON TherapeuticsAILERON Therapeutics was founded in2005to develop and advance a new therapeutic modality leveraging'Stapled Peptides' as a revolutionary class of drugs.AILERON's novel Stapled Pep-tides have unique chemical,biological and structural properties to address both intracellular and extracellular protein–protein interactions that serve as critical control points in disease mech-anisms,including cellular survival⁄death,signal transduction and gene regulation.Noteworthy,such protein–protein interactions have eluded small-molecule strategies,except for limited success requiring extraordinary tour de force campaigns.AILERON's pro-prietary technology platform converts peptides into their biologi-cally competent a-helical shape which endows the Stapled Peptide with inimitable properties,including efficient cell penetra-tion,high affinity binding to large target protein surfaces,and remarkable metabolic stability and pharmacokinetic properties in vivo.AILERON's R&D programs are deep-rooted in disease mechanisms pioneered by its founding scientists from Harvard University and the Dana-Farber Cancer Institute,namely,Stanley Korsmeyer,Gregory Verdine and Loren Walensky(1–10).A robust, multi-targeted disease strategy has been established to expand on AILERON's lead R&D program that is well poised to advance the first-in-class Stapled Peptide clinical candidate for the treat-ment of cancer.Drug Discovery:Tackling’Undruggable’Therapeutic TargetsRelative to existing drug discovery approaches,the pharmaceutical industry has created a vast chemical collection of small molecules and an emerging arsenal of'biologics',including proteins(e.g.anti-bodies),peptides(e.g.hormones,growth factors,cytokines)and nucleic acids(e.g.siRNAs).Collectively,approximately10–20%of known therapeutic targets(i.e. 500of about5000–10000 mapped from the human genome)have been addressed by such efforts.Beyond the identification of potential therapeutic targets,it is critically important to unravel the mechanisms of disease for drug discovery.Importantly,a considerable portion of the genomic uni-verse of therapeutic targets is yet viewed to be'undruggable'by existing small molecule and biologic modalities.In particular,intra-cellular protein–protein interactions are an extraordinary challenge for existing small molecule and biologic modalities.In particular, the large binding surfaces for intracellular protein–protein interac-tions generally exclude small-molecule modulators from being effec-tive.Furthermore,although traditional peptides and proteins may have the chemical size and functionality to effectively modulate intracellular protein–protein interactions,such biologics do not pos-sess cell-penetrating properties and are,therefore,used primarily to modulate extracellular therapeutic targets(e.g.receptors).Thus,an almost unimaginable opportunity for tackling'undruggable'thera-peutic targets has remained quiescent throughout our modern time of drug discovery.Is there yet a solution?Yes,indeed,and given the fact that a vast number of'undruggable'therapeutic targets are known to include protein–protein interactions that involve a-helical type lock-and-key mechanisms,the solution has been astonishingly obvious:design a-helical peptides having both structural and func-tional properties that enable them to penetrate into the cell,bind to the therapeutic target,and modulate the biological pathway in the desired way(Scheme1).Several proof-of-concept studies show-ing that Stapled Peptides successfully modulate protein–protein interactions(intracellular and extracellular)have been described rel-ative to Bcl-2family of apoptotic proteins(1,4,7–9;for reviews: 3,5),glucokinase(2),p53transcription factor(6),NOTCH(11),HIV capsid(12)and HIV gp41-cell fusion(13).It is predicted that about 1500–3000a-helical type protein–protein interaction therapeutic targets exist and are intimately involved in a wide scope of human diseases.Innovative Technologies:Designing Stapled Peptide DrugsPeptides are a proven class of medicines,with more than40 marketed drugs and about300molecules in clinical trials.Despite these achievements,peptide drugs have been limited to extracel-lular therapeutic targets(e.g.receptors),and only as a result of significant transformation of their chemical structures have sec-ond-generation peptidomimetic drugs been advanced for specific intracellular therapeutic targets(e.g.proteases)(14).Not surpris-ingly,a foggy distinction between peptidomimetics and small molecule drugs exists from a chemical perspective,especially in those cases where the peptide scaffold has undergone extensive modifications or replacement.In contrast,Stapled Peptide analogs of a-helical motifs of'protein keys'involved in specific intracel-lular protein–protein interactions are acknowledged as a revolu-tionary and promising class of peptide drugs endowed with aChem Biol Drug Des2009;73:3–6 R&D Spotlightª2009The AuthorJournal compilationª2009Blackwell Munksgaard doi:10.1111/j.1747-0285.2008.00744.xunique combination of cell penetrating,metabolic stability and pharmacokinetic properties (15).Stapled a -helical peptides (Fig-ure 1)exploit chemical stabilization of secondary structure by way of ring-closing metastasis via side-chain or backbone functional-ities (9,10–13,16–18,20–22for reviews 4,19).By leveraging novel building blocks and macrocyclization chemistries along with sophis-ticated drug design,molecular informatics and biophysical tools,AILERON's innovative technologies (23)are creating a molecular armamentarium of stapled a -helical peptides for a plethora of therapeutictargets.ABScheme 1:(A)Examples of therapeutic targets and pathways for Stapled Peptides.(B)A proposed model of cellular penetration by Stapled Peptides.R&D SpotlightResearch and Development:from Concept to ClinicAILERON's R&D programs embrace both scope in terms of its technology platform and depth with respect to advancing its preclinical research toward achieving the first-in-class Stapled Peptide clinical candidate for cancer therapy.In the latter case,a series of novel Stapled Peptides targeting the Bcl-2family of apoptotic proteins have shown promising in vivo efficacy in hematologic cancer and solid tumor models (24,25).As exemplified by initial proof-of-concept studies described from academic researchers on Stapled Peptides showing the potential application to multiple disease areas (e.g.cancer,diabetes,inflammation and infectious diseases)(Table 1),AILERON'S trea-sury of therapeutic targets for drug discovery is continuously growing.There is a worldwide paradigm shift in many pharma-ceutical companies towards balancing their pipelines of tradi-tional small molecule drugs with emerging biologic drugs,and AILERON's Stapled Peptides provide tremendous opportunities for strategic partnerships in both research and developmenttowardFigure 1:Structural model for helical protein–protein interaction and drug design strategies to generate novel Stapled Peptides.(A)Protein–protein interactions leverage a -helical molecular recognition ('lock'and 'key').(B)The a -helical motif or 'key'exploits multiple hydro-phobic,H-bonding and ionic interactions with a large and oftentimes flat binding surface or 'lock'.(C)The a -helical binding surface,with limited exceptions,is viewed to be 'undruggable'by traditional small-molecule ligands.(D)The a -helical motif as extracted from the cognate protein is not conformationally stabilized,but is susceptible to proteolytic cleavage and lacks cell penetrating properties.(E)The a -helical motif as a synthetically modified macrocyclc peptide using ruthenium catalyzed ring-closing metathesis is conformationally and proteolytically stabilized.The Stapled Peptide is also endowed with remarkable cell-penetrating and pharmacokinetic properties.(F)The Stapled Peptide presents the a -helical motif to effectively bind to its cognate target with high affinity and selectivity.Table 1:Examples of promising therapeutic targets involving a -helical protein–protein interactions that have been shown to be effectively modulated by Stapled Peptides in vitro and ⁄or in vivoTarget class Therapeutic target Helical peptideBiological mechanism(s)Clinical indication(s)Bcl-2Family BAX,BAK,Bcl-2,Mcl-1BH3a -helix (e.g.BIM,BID)Activation of cell death Cancer,autoimmunity KinaseGlucokinase BAD BH3a -helix (pSer form)Activation of glucokinase Diabetes Transcription factorMDM2-p53P53a -helix Activation of cell death CancerNOTCH-CSL-MAML MAML a -helix Activationofcell deathCancer (including cancer stem cells),cardiovascular disease Viral proteinHIV-1capsid assembly Capsid a -helix Inhibition of HIV particle assembly HIV (AIDS)HIV-1Gp41–CD4Gp41HR2a -helixInhibition of HIV fusionHIV (AIDS)R&D Spotlightrealizing their promising clinical applications for many human diseases.Tomi K.Sawyer Chief Scientific Officer and Senior Vice-President,Drug Discovery and Innovative Technologies,AILERON Therapeutics,Cambridge,MA,USA References1.Gavathiotis E.,Suzuki M.,Davis M.L.,Pitter K.,Bird G.H.,KatzS.G.,Tu H.-C.,Kim H.,Cheng E.H.Y.,Tjandra N.,Walensky L.D.(2008)BAX activation is initiated at a novel interaction site.Nature;455:1076–1081.2.Danial N.N.,Walensky L.D.,Zhang C.Y.,Choi C.S.,Fisher J.K.,Molina A.J.,Datta S.R.et al.(2008)Dual role of proapoptotic BAD in insulin secretion and beta cell survival.Nature Med;14:144–153.3.Pitter K.,Bernal F.,Labelle J.,Walensky L.D.(2008)Dissectionof the BCL-2family signaling network with stabilized alpha-heli-ces of BCL-2domains.Methods Enzymol;446:387–408.4.Bird G.H.,Bernal F.,Pitter K.,Walensky L.D.(2008)Synthesisand biophysical characterization of stabilized alpha-helices of BCL-2domains.Methods Enzymol;446:369–386.5.Verdine G.L.,Walensky L.D.(2007)The challenge of druggingundruggable targets in cancer:lessons learned from targeting BCL-2family members.Clin Cancer Res;13:7264–7270.6.Bernal F.,Tyler A.F.,Korsmeyer S.J.,Walensky L.D.,Verdine G.L.(2007)Reactivation of the p53tumor suppressor pathway by a stapled p53peptide.J Am Chem Soc;129:2456–2457.7.Walensky L.D.,Pitter K.,Morash J.,Oh K.J.,Barbuto S.,Fisher J.,Smith E.,Verdine G.L.,Korsmeyer S.J.(2006)A stapled BID BH3 helix directly binds and activates BAX.Mol Cell;24:199–210.8.Walensky L.D.(2006)BCL-2in the crosshairs:tipping the bal-ance of life and death.Cell Death Differ;13:1339–1350.9.Walensky L.D.,Kung A.L.,Escher I.,Malia T.J.,Barbuto S.,Wright R.D.,Wagner G.,Verdine G.L.,Korsmeyer S.J.(2004) Activation of apoptosis in vivo by a hydrocarbon-stapled BH3 helix.Science;305:1466–1470.10.Schafmeister C.E.,Po J.,Verdine G.L.(2000)An all-hydrocarboncross-linking system for enhancing the helicity and metabolic stability of peptides.J Am Chem Soc;122:5891–5892.11.Bradner J.,Moellering R.,Verdine G.L.(2008)Stablized MAMLPeptides and Uses Thereof.International Patent Application WO-2008⁄061192-A2.Geneva,Switzerland:World Intellectual Property Organisation.12.Zhang H.,Zhao Q.,Bhattacharya S.,Waheed A.A.,Tong X.,Hong A.,Heck S.,Curreli F.,Goger M.,Cowburn D.,Freed E.O.,Debnath A.K.(2008)A cell-penetrating helical peptide as a potential HIV-1inhibitor.J Mol Biol;378:565–580.13.Wang D.,Lu M.,Arora P.S.(2008)Inhibition of HIV-1fusion byhydrogen-bond-surrogate-based alpha helices.Angew Chem Int Ed Engl;47:1879–1882.14.Sawyer T.K.(2005)Synthetic peptides:chemistry,biology anddrug design.In:Meyers R.A.,editor.Encyclopedia of Molecular Cell Biology and Molecular Medicine,Vol.14.New York:Wiley-VCH Publishers,Inc;p.91–122.15.Drahl C.(2008)Harnessing helices:chemical braces hold pep-tides in place,heralding a potential new class of therapeutics.Chem Eng News;86:18–23.16.Patgiri A.,Jochim A.L.,Arora P.S.(2008)A hydrogen bond surro-gate approach for stabilization of short peptide sequences in alpha-helical conformation.Acc Chem Res;41:1289–1300.17.Liu J.,Wang D.,Zheng Q.,Lu M.,Arora P.S.(2008)Atomicstructure of a short alpha-helix stabilized by a main chain hydrogen-bond surrogate.J Am Chem Soc;130:4334–4337. 18.Bhattacharya S.,Zhang H.,Debnath A.K.,Cowburn D.(2008)Solution structure of a hydrocarbon stapled peptide inhibitor in complex with monomeric C-terminal domain of HIV-1capsid.J Biol Chem;283:16274–16278.19.Henchey L.K.,Jochim A.L.,Arora P.S.(2008)Contemporary strat-egies for the stabilization of peptides in the alpha-helical con-formation.Curr Opin Chem Biol(in press).20.Wang D.,Chen K.,Kulp J.L.,III,Arora P.S.(2006)Evaluation ofbiologically relevant short alpha-helices stabilized by a main-chain hydrogen-bond surrogate.J Am Chem Soc;128:9248–9256.21.Wang D.,Chen K.,Dimartino G.,Arora P.S.(2006)Nucleationand stability of hydrogen-bond surrogate-based alpha-helices.Org Biomol Chem;4:4074–4081.22.Chapman R.N.,Dimartino G.,Arora P.S.(2004)A highly stableshort alpha-helix constrained by a main-chain hydrogen-bond surrogate.J Am Chem Soc;126:12252–12253.23.Sawyer T.K.(2008)Stapled Peptides:A New Therapeutic Modal-ity.Waltham,MA:New England Structural Biology Association's Second Annual Protein Science Meeting.Keynote Lecture. 24.Kapeller R.,Nash H.M.,Kung A.L.,Sawyer T.K.(2008)BH3-Stapled Helical Peptides:A Novel Class of Biologic Drugs for Cancer Therapy.San Diego,CA:American Association of Cancer Research Annual Meeting.Poster Abstract No.LB-230.25.Kapeller R.,Han J.,Sun K.,Gangurde P.,Kawahata N.,IadanzaM.,Guerlevais V.,Horstick J.,Noehre J.,Annis A.,Licklider L., Nash H.M.,Kung A.L,Sawyer T.K.(2008)Stapled Peptides: Leveraging the BH3a-Helix to Create a New Class of Drugs to Treat Hematological Malignancies.San Francisco,CA:American Society of Hematology50th Annual Meeting.Poster Abstract No.2929.R&D Spotlight。
A comparative study of large-scale nonlinear optimization algorithms

subject to h(x) − w = 0, w ≥ 0, where h(x) and w are vectors representing the hi (x)’s and wi ’s, respectively. The inequality constraints are then eliminated by incorporating them in a logarithmic barrier term in the objective function, bµ (x, w) = f (x) − µ m i=1 log(wi ), transforming (2) to (3) minimize bµ (x, w) subject to h(x) − w = 0. Denoting the Lagrange multipliers for the system (3) by y , the first order conditions for the problem are (4) ∇f (x) − ∇h(x)T y = 0 −µW −1 e + y = 0 h(x) − w = 0
LARGE-SCALE NONLINEAR PROGRAMMING
3
2. LOQO: An Infeasible Interior-Point Method We begin with a description of the loqo algorithm. The basic problem we consider is minimize f (x) (1) subject to hi (x) ≥ 0, i = 1, . . . , m where x ∈ Rn are the decision variables, f : Rn → R and h : Rn → Rm . Since the algorithm involves derivatives, f (x) and the hi (x)’s are assumed to be twice continuously differentiable. Expressing nonlinear optimization problems in the form given by (1) is rather restrictive—the actual implementation of loqo allows for much greater variety in the form of expression, including bounds on variables, ranges on inequalities, and equality constraints. We will discuss the case of equality constraints in Section 5. For further details on the general case, see [14]. loqo starts by adding slacks to the inequality constraints in (1), which becomes (2) minimize f (x)
Code Review Checklist

以下是用于开发人员代码review的 Macadamian's指南 . 在代码提交控制前,它们应该按照以下的规则检查。
我们公开这份检查表是希望给任何开发部门的同行代码评审提供一个简要的参考。
你可以直接按本表开始评审,当然,更好的办法是按照开发实际作出修改后使用。
目录General Code Smoke Test通用测试Comments and Coding Conventions注释和代码风格Error Handling错误处理Resource Leaks资源泄漏Control Structures控制结构Performance性能Functions函数Bug Fixes bug修复Math数学General Code Smoke Test 通用测试Does the code build correctly?No errors should occur when building the source code. No warnings should be introduced by changes made to the code.代码可以正确编译:编译代码时应无错误。
Does the code execute as expected?When executed, the code does what it is supposed to.代码是否像预期结果那样执行?Do you understand the code you are reviewing?As a reviewer, you should understand the code. If you don't, the review may not be complete, or the code may not be well commented.你理解正在review(评审)的代码了吗?作为一个评审者,你应该理解这些代码;否则将导致评审不充分或效果不太好。
HSP50210 DCL Lock Detector接口说明书
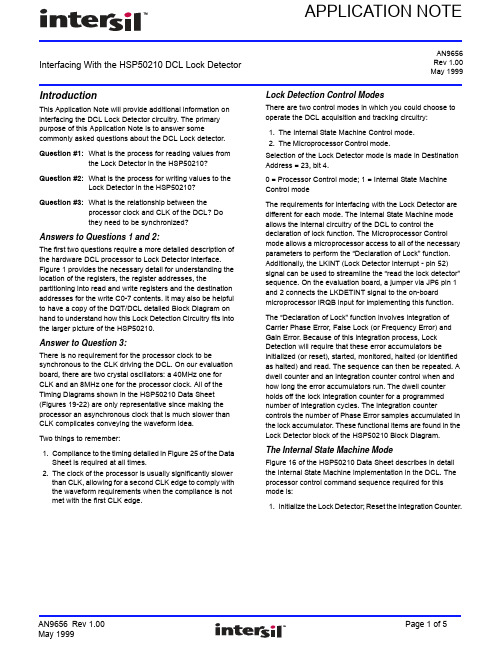
Interfacing With the HSP50210 DCL Lock Detector APPLICATION NOTEAN9656Rev 1.00May 1999IntroductionThis Application Note will provide additional information on interfacing the DCL Lock Detector circuitry. The primary purpose of this Application Note is to answer some commonly asked questions about the DCL Lock detector. Question #1:What is the process for reading values fromthe Lock Detector in the HSP50210? Question #2:What is the process for writing values to theLock Detector in the HSP50210?Question #3:What is the relationship between theprocessor clock and CLK of the DCL? Dothey need to be synchronized?Answers to Questions 1 and 2:The first two questions require a more detailed description of the hardware DCL processor to Lock Detector interface. Figure 1 provides the necessary detail for understanding the location of the registers, the register addresses, the partitioning into read and write registers and the destination addresses for the write C0-7 contents. It may also be helpful to have a copy of the DQT/DCL detailed Block Diagram on hand to understand how this Lock Detection Circuitry fits into the larger picture of the HSP50210.Answer to Question 3:There is no requirement for the processor clock to be synchronous to the CLK driving the DCL. On our evaluation board, there are two crystal oscillators: a 40MHz one for CLK and an 8MHz one for the processor clock. All of the Timing Diagrams shown in the HSP50210 Data Sheet (Figures 19-22) are only representative since making the processor an asynchronous clock that is much slower than CLK complicates conveying the waveform idea.Two things to remember:pliance to the timing detailed in Figure 25 of the DataSheet is required at all times.2.The clock of the processor is usually significantly slowerthan CLK, allowing for a second CLK edge to comply with the waveform requirements when the compliance is not met with the first CLK edge.Lock Detection Control ModesThere are two control modes in which you could choose to operate the DCL acquisition and tracking circuitry:1.The Internal State Machine Control mode.2.The Microprocessor Control mode.Selection of the Lock Detector mode is made in Destination Address = 23, bit 4.0 = Processor Control mode; 1 = Internal State Machine Control modeThe requirements for interfacing with the Lock Detector are different for each mode. The Internal State Machine mode allows the internal circuitry of the DCL to control the declaration of lock function. The Microprocessor Control mode allows a microprocessor access to all of the necessary parameters to perform the “Declaration of Lock” function. Additionally, the LKINT (Lock Detector Interrupt - pin 52) signal can be used to streamline the “read the lock detector” sequence. On the evaluation board, a jumper via JP6 pin 1 and 2 connects the LKDETINT signal to the on-board microprocessor IRQB input for implementing this function.The “Declaration of Lock” function involves integration of Carrier Phase Error, False Lock (or Frequency Error) and Gain Error. Because of this integration process, Lock Detection will require that these error accumulators be initialized (or reset), started, monitored, halted (or identified as halted) and read. The sequence can then be repeated. A dwell counter and an integration counter control when and how long the error accumulators run. The dwell counter holds off the lock integration counter for a programmed number of integration cycles. The integration counter controls the number of Phase Error samples accumulated in the lock accumulator. These functional items are found in the Lock Detector block of the HSP50210 Block Diagram.The Internal State Machine ModeFigure 16 of the HSP50210 Data Sheet describes in detail the Internal State Machine implementation in the DCL. The processor control command sequence required for this mode is:1.Initialize the Lock Detector; Reset the Integration Counter.(W101)A0-2CARRIER LOOP FILTERLAG ACCUMULATOR (32 MSBs)SYMBOL TRACKING LOOP FILTERLAG ACCUMULATOR (32 MSBs)AGC GAIN ACCUMULATOR (8 MSBs)UPDATE READ REGISTER(FROM WRITE ADDRESS DESTINATION)LOCK DETECTOR PHASE ERRORACCUMULATOR (16 MSBs)LOCK DETECTOR GAIN ERRORACCUMULATOR (16 MSBs)INTERNAL STATUS REG(R000)2A0-2READ HOLDING REG’SREAD MUXSTATUS/DATA MUX CONTROL(R001)2A0-2(R010)2A0-2(R011)2A0-28C0-7(R100)2A0-232781516232431R E A DA D D R2431162381507W R I T E A D D RWRITE MUX (W000)1A0-2(W001)1A0-2(W010)1A0-2(W011)1A0-2321.2.3.4.5.8C0-7(W100)1A0-2FIGURE 1.A CONCEPTUAL BLOCK DIAGRAM OF THE READ/WRITE MICROPROCESSOR INTERFACE29.30SEE “WRITE DATA DESTINATIONS”302.Start the Lock Detector.3.Stop the Lock Detector.4.Monitor the Lock Status Bit.Note that on the write commands (steps 1-3), the C0-7 values will become valid processor clock edges and on the read commands (step 4), the C0-7 values will become valid on the CLK rising edges. The RD, WR and A0-2 signals are always synchronous to the processor clock edges.The Processor Control ModeThe Processor Control Mode allows a designer the ability to implement a design unique “Lock Declaration” function. The primary difference between this mode and the State Machine mode is in the way the error accumulators work. In the Processor Mode, the error integration process stops after every integration, rather than continuing into anotherintegration cycle. This allows the processor to take advantage of the LKINT signal to streamline the process of knowing when the error accumulators are finished an integration cycle and can be read. Thus, there are two ways to operate in the Processor Mode:ing the LKINT signal as an interrupt for recognizing the end of an integration cycle.2.Reading the internal status bit SR-7 to determine the inte-gration cycle state.LKINT Interrupt Driven OperationWith the LKINT Interrupt Driven technique, the processor command sequence is:1.Initialize the Lock Detector; Reset the Integration Counter.2.Start the Lock Detector.3.Set the Read Address for a Phase Error or Gain Error Read.4.Read the Lock Detector Error MSByte.5.Read the Lock Detector Error LSByte.6.Processor uses Application Specific Lock Declaration Logic on Values (Note).7.Restart the Lock Detector.NOTE:This step does not involve writing to the DCL.Figure 22 of the HSP50210 Data Sheet details the timing waveforms required to implement this processor command sequence. Note that on the write commands (steps 1-3, 7), the C0-7 values will become valid on the processor clock edges and on the read commands (steps 4-5), the C0-7 values will become valid on the CLK rising edges. The RD, WR and A0-2 signals are always synchronous to the processor clock edges.DATA PATH CONFIGURATIONPOWER DETECT THRESHOLD REGISTER AGC LOOP PARAMETERSCARRIER PHASE ERROR DETECTOR FREQUENCY DETECTORFREQUENCY ERROR DETECTORCARRIER LOOP FILTER CONTROL #1CARRIER LOOP FILTER CONTROL #2CARRIER LOOP FILTER UPPER LIMIT CARRIER LOOP FILTER LOWER LIMITCARRIER ACQUISITION LOOP FILTER GAINS CARRIER TRACKING LOOP FILTER GAINS FREQUENCY SEEP/AFC LOOP CONTROLCARRIER LAG ACCUMULATOR INITIALIZATION SYMBOL TRACKING LOOP CONFIGURATION SYMBOL TRACKING LOOP FILTER UPPER LIMIT SYMBOL TRACKING LOOP FILTER LOWER LIMITSYMBOL TRACKING LOOP FILTER GAINS:ACQUISITION SYMBOL TRACKING LOOP FILTER GAINS:TRACKINGSYMBOL TRACKING LOOP FILTER LAG ACCUMULATOR INITIALIZATION LOCK DETECTOR CONFIGURATION LOCAL ACCUMULATOR PRE-LOADSFALSE LOCK ACCUMULATOR PRE-LOADS ACQ/TRK CONTROLHALT LOCK DETECTOR FOR READING RESTART LOCK DETECTORSOFT DECISION SLICER CONFIGURATIONSERIAL OUTPUT CONFIGURATION OUTPUT SELECTOR CONFIGURATIONUPDATE READ REGISTERINITIALIZE LOCK DETECTOR ( P CONTROL MODE)1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.29.30.TO PAGE 1NOTES:1.The prefix W indicates that a rising edge of WR is required to load the contents (C0-7) of the addressed requestor (A0-2).2.The prefix R indicates that a low assertion of RD is required to load the contents (C0-7) of the addressed register (A0-2. The contents will be available on the first rising edge of CLK after RD is asserted low.WRITE DATA DESTINATIONSProcessor Read Status Driven OperationWith the Processor Read Status Driven technique, the processor command sequence is:1.Initialize the Lock Detector; Reset the Integration Counter.2.Start the Lock Detector.3.Halt the Lock Detector at end of cycle.4.Set the Read Address for Phase Error or Gain Error Read.5.Read (Monitor) the Internal Status (SR-7).6.Read the Lock Detector Error MSByte.7.Read the Lock Detector Error LSByte.8.Processor uses Application Specific Lock Declaration Logicon Values (Note).9.Monitor the Lock Status Bit.10.Restart the Lock Detector.NOTE:This step does not involve writing to the DCL.Figure 21 of the HSP50210 Data Sheet details the timing waveforms required to implement this processor command sequence. Note that on the write commands (steps 1-4, 10), the C0-7 values will become valid on the processor clock edges and on the read commands (steps 5-7, 9), the C0-7 values will become valid on the CLK rising edges. The RD, WR and A0-2 signals are always synchronous to the processor clock edges.Refer to "/" for the latest and detailed information.Renesas Electronics America Inc.1001 Murphy Ranch Road, Milpitas, CA 95035, U.S.A.Tel: +1-408-432-8888, Fax: +1-408-434-5351Renesas Electronics Canada Limited9251 Yonge Street, Suite 8309 Richmond Hill, Ontario Canada L4C 9T3Tel: +1-905-237-2004Renesas Electronics Europe LimitedDukes Meadow, Millboard Road, Bourne End, Buckinghamshire, SL8 5FH, U.K Tel: +44-1628-651-700, Fax: +44-1628-651-804Renesas Electronics Europe GmbHArcadiastrasse 10, 40472 Düsseldorf, Germany Tel: +49-211-6503-0, Fax: +49-211-6503-1327Renesas Electronics (China) Co., Ltd.Room 1709 Quantum Plaza, No.27 ZhichunLu, Haidian District, Beijing, 100191 P. R. China Tel: +86-10-8235-1155, Fax: +86-10-8235-7679Renesas Electronics (Shanghai) Co., Ltd.Unit 301, Tower A, Central Towers, 555 Langao Road, Putuo District, Shanghai, 200333 P. R. China Tel: +86-21-2226-0888, Fax: +86-21-2226-0999Renesas Electronics Hong Kong LimitedUnit 1601-1611, 16/F., Tower 2, Grand Century Place, 193 Prince Edward Road West, Mongkok, Kowloon, Hong Kong Tel: +852-2265-6688, Fax: +852 2886-9022Renesas Electronics Taiwan Co., Ltd.13F, No. 363, Fu Shing North Road, Taipei 10543, Taiwan Tel: +886-2-8175-9600, Fax: +886 2-8175-9670Renesas Electronics Singapore Pte. Ltd.80 Bendemeer Road, Unit #06-02 Hyflux Innovation Centre, Singapore 339949Tel: +65-6213-0200, Fax: +65-6213-0300Renesas Electronics Malaysia Sdn.Bhd.Unit 1207, Block B, Menara Amcorp, Amcorp Trade Centre, No. 18, Jln Persiaran Barat, 46050 Petaling Jaya, Selangor Darul Ehsan, Malaysia Tel: +60-3-7955-9390, Fax: +60-3-7955-9510Renesas Electronics India Pvt. Ltd.No.777C, 100 Feet Road, HAL 2nd Stage, Indiranagar, Bangalore 560 038, India Tel: +91-80-67208700, Fax: +91-80-67208777Renesas Electronics Korea Co., Ltd.17F, KAMCO Yangjae Tower, 262, Gangnam-daero, Gangnam-gu, Seoul, 06265 Korea Tel: +82-2-558-3737, Fax: +82-2-558-5338SALES OFFICES© 2018 Renesas Electronics Corporation. All rights reserved.(Rev.4.0-1 November 2017)Notice1. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products and application examples. You are fully responsible forthe incorporation or any other use of the circuits, software, and information in the design of your product or system. Renesas Electronics disclaims any and all liability for any losses and damages incurred by you or third parties arising from the use of these circuits, software, or information.2. Renesas Electronics hereby expressly disclaims any warranties against and liability for infringement or any other claims involving patents, copyrights, or other intellectual property rights of third parties, by orarising from the use of Renesas Electronics products or technical information described in this document, including but not limited to, the product data, drawings, charts, programs, algorithms, and application examples.3. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics or others.4. You shall not alter, modify, copy, or reverse engineer any Renesas Electronics product, whether in whole or in part. Renesas Electronics disclaims any and all liability for any losses or damages incurred byyou or third parties arising from such alteration, modification, copying or reverse engineering.5. Renesas Electronics products are classified according to the following two quality grades: “Standard” and “High Quality”. The intended applications for each Renesas Electronics product depends on theproduct’s quality grade, as indicated below. "Standard":Computers; office equipment; communications equipment; test and measurement equipment; audio and visual equipment; home electronic appliances; machine tools; personal electronic equipment; industrial robots; etc."High Quality": Transportation equipment (automobiles, trains, ships, etc.); traffic control (traffic lights); large-scale communication equipment; key financial terminal systems; safety control equipment; etc.Unless expressly designated as a high reliability product or a product for harsh environments in a Renesas Electronics data sheet or other Renesas Electronics document, Renesas Electronics products are not intended or authorized for use in products or systems that may pose a direct threat to human life or bodily injury (artificial life support devices or systems; surgical implantations; etc.), or may cause serious property damage (space system; undersea repeaters; nuclear power control systems; aircraft control systems; key plant systems; military equipment; etc.). Renesas Electronics disclaims any and all liability for any damages or losses incurred by you or any third parties arising from the use of any Renesas Electronics product that is inconsistent with any Renesas Electronics data sheet, user’s manual or other Renesas Electronics document.6. When using Renesas Electronics products, refer to the latest product information (data sheets, user’s manuals, application notes, “General Notes for Handling and Using Semiconductor Devices” in thereliability handbook, etc.), and ensure that usage conditions are within the ranges specified by Renesas Electronics with respect to maximum ratings, operating power supply voltage range, heat dissipation characteristics, installation, etc. Renesas Electronics disclaims any and all liability for any malfunctions, failure or accident arising out of the use of Renesas Electronics products outside of such specified ranges.7. Although Renesas Electronics endeavors to improve the quality and reliability of Renesas Electronics products, semiconductor products have specific characteristics, such as the occurrence of failure at acertain rate and malfunctions under certain use conditions. Unless designated as a high reliability product or a product for harsh environments in a Renesas Electronics data sheet or other Renesas Electronics document, Renesas Electronics products are not subject to radiation resistance design. You are responsible for implementing safety measures to guard against the possibility of bodily injury, injury or damage caused by fire, and/or danger to the public in the event of a failure or malfunction of Renesas Electronics products, such as safety design for hardware and software, including but not limited to redundancy, fire control and malfunction prevention, appropriate treatment for aging degradation or any other appropriate measures. Because the evaluation of microcomputer software alone is very difficult and impractical, you are responsible for evaluating the safety of the final products or systems manufactured by you.8. Please contact a Renesas Electronics sales office for details as to environmental matters such as the environmental compatibility of each Renesas Electronics product. You are responsible for carefully andsufficiently investigating applicable laws and regulations that regulate the inclusion or use of controlled substances, including without limitation, the EU RoHS Directive, and using Renesas Electronics products in compliance with all these applicable laws and regulations. Renesas Electronics disclaims any and all liability for damages or losses occurring as a result of your noncompliance with applicable laws and regulations.9. Renesas Electronics products and technologies shall not be used for or incorporated into any products or systems whose manufacture, use, or sale is prohibited under any applicable domestic or foreign lawsor regulations. You shall comply with any applicable export control laws and regulations promulgated and administered by the governments of any countries asserting jurisdiction over the parties or transactions.10. It is the responsibility of the buyer or distributor of Renesas Electronics products, or any other party who distributes, disposes of, or otherwise sells or transfers the product to a third party, to notify such thirdparty in advance of the contents and conditions set forth in this document.11. This document shall not be reprinted, reproduced or duplicated in any form, in whole or in part, without prior written consent of Renesas Electronics.12. Please contact a Renesas Electronics sales office if you have any questions regarding the information contained in this document or Renesas Electronics products.(Note 1) “Renesas Electronics” as used in this document means Renesas Electronics Corporation and also includes its directly or indirectly controlled subsidiaries.(Note 2) “Renesas Electronics product(s)” means any product developed or manufactured by or for Renesas Electronics.。
Thue 定理

(Alon, Grytczuk, Hałuszczak, Riordan, 2001)
Every graph of maximum degree at most satisfies (G) 162.
(Alon, Grytczuk, Hałuszczak, Riordan, 2001)
There is a constant c > 0 such that for each there is a graph G with maximum degree satisfying (G) c2/ln .
y x x
x y
Theorem: Every tree hasxThue chromatic number at most 4
0 20 1 0020 0010 20 1 0 10 20 0 2 1000...
The new sequence has no repetition and no palindrome.
00
There is no infinite sequence consisting of 2 symbols which has no repetitions.
01
There is no infinite sequence consisting of 2 symbols which has no repetitions.
There are many generalizations of Thue Theorem
One direction of generalization is to find ``more restrictive’’ or ``less restrictive” infinite sequences.
Semi-Infinite Anisotropic Spherical Model Correlations at T = T_c

arXiv:cond-mat/9803230v4 [cond-mat.stat-mech] 26 May 1998
(Received 12 February 1998) The ordinary surface magnetic phase transition is studied for the exactly solvable anisotropic spherical model (ASM), which is the limit D → ∞ of the D-component uniaxially anisotropic classical vector model. The bulk limit of the ASM is similar to that of the spherical model, apart from the role of the anisotropy stabilizing ordering for low lattice dimensionalities, d ≤ 2, at finite temperatures. The correlation functions and the energy density profile in the semi-infinite ASM are calculated analytically and numerically for T ≥ Tc and 1 ≤ d ≤ ∞. Since the lattice dimensionalities d = 1, 2, 3, and 4 are special, a continuous spatial dimensionality d′ = d − 1 has been introduced for dimensions parallel to the surface. However, preserving a discrete layer structure perpendicular to the surface avoids unphysical surface singularities and allows numerical solitions that reveal significant shortrange features near the surface. The results obtained generalize the isotropic-criticality results for 2 < d < 4 of Bray and Moore [Phys. Rev. Lett. 38, 735 (1977); J. Phys. A 10, 1927 (1977)]. PACS numbers: , 75.10.Hk, 75.30.Pd
7种水果摆脱大肚腩

1、苹果腹部减肥早在好几年前,就有人为苹果量身定做出一套瘦身来,还曾经引起一阵苹果减肥法的热潮呢!事实上苹果的确是瘦身的风云水果,它有丰富的果胶,加速排毒功效并降低热量吸收,此外苹果的钾质也多,可以防止腿部水肿。
慢慢的咀嚼有点硬度的苹果,将成分释放出来,不仅有饱足感,而且他的卡路里热量也不高。
2、葡萄柚腹部减肥酸性物质可以帮助消化液的增加,藉此促进消化功能,而且营养也容易被吸收。
此外为什么葡萄柚再减肥时也会被列为必食的风云水果,原因是它含有丰富的维他命C,大约一颗葡萄柚就有100豪克,不仅可以消除疲劳,还可以美化肌肤呢!重要的是它的含糖份少,减肥食用来补充维他命C最适合不过了。
至于很多女孩害怕的重酸味,建议你,可以滴一点点蜂蜜在葡萄柚上,酸味马上被中和。
3、蕃茄腹部减肥。
严格说起来,蕃茄应该是被归为蔬菜类才正确吧!所以在食材中常看到它。
蕃茄含有茄红素,食物纤维及果胶成份可以降低热量摄取,促进肠胃蠕动。
而且独特的酸味可以刺激胃液分泌,甚至提升食物的口感,是很好料理健康的食材呢。
4、菠萝腹部减肥有没有听过人家说菠萝很“利”,一定要在饭后吃才不会伤胃的说法。
这说法可是有凭据的呦!因为菠萝的蛋白分解酵素相当强力,虽然可以帮助肉类的蛋白质消化,但是如果在餐前吃的话,很容易造成胃壁受伤呦!因此利用吃菠萝来瘦身一定要注意时间问题。
5、香蕉腹部减肥。
便便出不来的女生都会被建议,吃香蕉试试看吧!因为香蕉含有丰富食物纤维,维他命A,钾质等,所以有很棒的整肠、强化肌肉、利尿软便功能。
对于常便秘、肌肤干燥的美眉而言,这是款又瘦又美的水果!此外以糖质为主成分的香蕉,吃了以后可以马上消化,迅速补充体力。
而且香蕉很有饱足感,只要吃上一根就可以裹腹,而且热量卡路里颇低的,可别因它甜滋滋的就以为他不利。
6、奇异果腹部减肥维他命C超多的奇异果(猕猴桃),一直是爱漂漂的美眉的最爱。
至于它位居水果之冠的食物纤维和丰富的钾,的确可以让它列入瘦身水果的风云榜内!和凤梨一样,奇异果也有大量的蛋白分解酵素所以和肉类菜肴搭配是最好不过的。
计算机网络英文题库(附答案)chapter5

Chapter 5 The Link Layer and Local Area Network1.A ( ) protocol is used to move a datagram over an individual link.A application-layerB transport-layerC network-layerD link-layer2.The units of data exchanged by a link-layer protocol are called ( ).A datagramsB framesC segmentsD messages3.Which of the following protocols is not a link-layer protocol? ( )A EthernetB PPPC HDLCD IP4.In the following four descriptions, which one is not correct? ( )A link-layer protocol has the node-to-node job of moving network-layer datagrams over a single link in the path.B The services provided by the link-layer protocols may be different.C A datagram must be handled by the same link-layer protocols on the different links in the path.D The actions taken by a link-layer protocol when sending and receiving frames include error detection, flow control and random access.5.Which of the following services can not offered by a link-layer protocol? ( )A congestion controlB Link AccessC Error controlD Framing6.( ) protocol serves to coordinate the frame transmissions of the many nodes when multiple nodes share a single broadcast link.A ARPB MACC ICMPD DNS7.In the following four descriptions about the adapter, which one is not correct? ( )A The adapter is also called as NIC.B The adapter is a semi-autonomous unit.C The main components of an adapter are bus interface and the link interface.D The adapter can provide all the link-layer services.8.Consider CRC error checking approach, the four bit generator G is 1011, and suppose that the data D is 10101010, then the value of R is( ).A 010B 100C 011D 1109.In the following four descriptions about random access protocol, which one is not correct? ( )A I n slotted ALOHA, nodes can transmit at random time.B I n pure ALOHA, if a frame experiences a collision, the node will immediately retransmit it with probability p.C T he maximum efficiency of a slotted ALOHA is higher than a pure ALOHA.D I n CSMA/CD, one node listens to the channel before transmitting.10.In the following descriptions about MAC address, which one is not correct? ( )A T he MAC address is the address of one node’s adapter.B N o two adapters have the same MAC address.C T he MAC address doesn’t change no matter where the adapter goes.D M AC address has a hierarchical structure.11.The ARP protocol can translate ( ) into ( ). ( )A h ost name, IP addressB h ost name, MAC addressC I P address, MAC addressD broadcast address, IP address12.The value of Preamble field in Ethernet frame structure is ( )A 10101010 10101010……10101010 11111111B 10101011 10101011……10101011 10101011C 10101010 10101010……10101010 10101011D 10101010 10101010……10101010 1010101013.There are four steps in DHCP, the DHCP server can complete ( ).A DHCP server discoveryB DHCP server offersC DHCP requestD DHCP response14.In CSMA/CD, the adapter waits some time and then returns to sensing the channel. In the following four times, which one is impossible? ( )A 0 bit timesB 512 bit timesC 1024 bit timesD 1028 bit times15.The most common Ethernet technologies are 10BaseT and 100BaseT. “10” and “100” indicate( ).A the maximum length between two adaptersB the minimum length between two adaptersC the transmission rate of the channelD the transmission rate of the node16.The principal components of PPP include but not( ).A framingB physical-control protocolC link-layer protocolD network-layer protocol17.In the following four options, which service can not be provided by switch? ( )A filteringB self-learningC forwardingD optimal routing18.In the following four services, which one was be required in PPP? ( )A packet framingB error detectionC error correctionD multiple types of link19.The ability to determine the interfaces to which a frame should be directed, and then directing the frame to those interfaces is( ).A filteringB forwardingC self-learningD optimal routing20.In ( ) transmission(s), the nodes at both ends of a link may transmit packets at the same time.A full-duplexB half-duplexC single-duplexD both full-duplex and half-duplex21.Consider the data D is 01110010001, if use even parity checking approach, the parity bit is( ① ), if use odd parity checking approach, the parity bit is( ② ). ( )A ①0 ②1B ①0 ②0C ①1 ②1D ①1 ②022.In the following four descriptions about parity checks, which one is correct? ( )A Single-bit parity can detect all errors.B Single-bit parity can correct one errors.C Two-dimensional parity not only can detect a single bit error, but also can correct that error.D Two-dimensional parity not only can detect any combination of two errors, but also can correct them.23.MAC address is ( ) bits long.A 32B 48C 128D 6424.Wireless LAN using protocol ( ).A IEEE 802.3B IEEE 802.4C IEEE 802.5D IEEE 802.1125.The following protocols are belonging to multiple access protocols except for ( ).A channel partitioning protocolsB routing protocolsC random access protocolsD taking-turns protocols26.Which of the following is not belonging to channel partitioning protocols? ( )A CSMAB FDMC CDMAD TDM27.In the following four descriptions about CSMA/CD, which one is not correct? ( )A A node listens to the channel before transmitting.B If someone else begins talking at the same time, stop talking.C A transmitting node listens to the channel while it is transmitting.D With CSMA/CD, the collisions can be avoided completely.28.( ) provides a mechanism for nodes to translate IP addresses to link-layer address.A IPB ARPC RARPD DNS29.A MAC address is a ( )address.A physical-layerB application-layerC link-layerD network-layer30.Which of the following is correct? ( )A No two adapters have the same MAC address.B MAC broadcast address is FF-FF-FF-FF-FF-FF.C A portable computer with an Ethernet card always has the same MAC address, no matter where the computer goes.D All of the above31.In the following four descriptions, which one is not correct? ( )A ARP resolves an IP address to a MAC address.B DNS resolves hostnames to IP addresses.C DNS resolves hostnames for hosts anywhere in the Internet.D ARP resolves IP addresses for nodes anywhere in the Internet.32.In the LAN, ( )protocol dynamically assign IP addresses to hosts.A DNSB ARPC DHCPD IP33.DHCP protocol is a four-step process: ①DHCP request. ②DHCP ACK. ③DHCP server discovery. ④DHCP server offer(s). The correct sequence is ( )A ①②③④B ③②①④C ③④①②D ①④③②34.In the Ethernet frame structure, the CRC field is ( )bytes.A 2B 4C 8D 3235.In the Ethernet frame structure, the Data field carries the ( ).A IP datagramB segmentC frameD message36.In the following four descriptions, which one is not correct? ( )A Ethernet uses baseband transmission.B All of the Ethernet technologies provide connection-oriented reliable service to the network layer.C The Ethernet 10Base2 technology uses a thin coaxial cable for the bus.D The Ethernet 10BaseT technology uses a star topology.37.Ethernet’s multiple access protocol is ( ).A CDMAB CSMA/CDC slotted ALOHAD token-passing protocol38.In the following four descriptions about CSMA/CD, which one is not correct? ( )A An adapter may begin to transmit at any time.B An adapter never transmits a frame when it senses that some other adapter is transmitting.C A transmitting adapter aborts its transmission as soon as it detects that another adapter is also transmitting.D An adapter retransmits when it detects a collision.39.Which of the following descriptions about CSMA/CD is correct? ( )A No slots are used.B It uses carrier sensing.C It uses collision detection.D All of the above.40.The Ethernet 10BaseT technology uses( )as its physical media.A fiber opticsB twisted-pair copper wireC coaxial cableD satellite radio channel41.For 10BaseT, the maximum length of the connection between an adapter and the hub is ( )meters.A 100B 200C 500D 1042.A ( )is a physical-layer device that acts on individual bits rather than on frames.A switchB hubC routerD gateway43.A hub is a ( )device that acts on individual bits rather than on frames.A physical-layerB link-layerC network-layerD ransport-layer44.A switch is a( )device that acts on frame.A physical-layerB link-layerC network-layerD transport-layer45.In the following four descriptions, which one is not correct? ( )A Switches can interconnect different LAN technologies.B Hubs can interconnect different LAN technologies.C There is no limit to how large a LAN can be when switches are used to interconnect LAN segments.D There is restriction on the maximum allowable number of nodes in a collision domain when hubs are used to interconnect LAN segments.46.The ability to determine whether a frame should be forwarded to some interface or should just be dropped is ( ).A f ilteringB f orwardingC s elf-learningD o ptimal routing47.Which of the following devices is not a plug and play device? ( )A hubB routerC switchD repeater48.Which of the following devices is not cut-through device? ( )A hubB routerC switchD repeater49.In the following four descriptions, which one is not correct? ( )A Switches do not offer any protection against broadcast storms.B Routers provide firewall protection against layer-2 broadcast storms.C Both switches and routers are plug and play devices.D A router is a layer-3 packet switch, a switch is a layer-2 packet switch. 50.Which device has the same collision domain? ( )A HubB SwitchC RouterD Bridge51.IEEE802.2 protocol belong to ( )layerA networkB MACC LLCD physical52.IEEE802.11 protocol defines ( )rules.A Ethernet BusB wireless WANC wireless LAND Token Bus53.In data link-layer, which protocol is used to share bandwidth? ( )A SMTPB ICMPC ARPD CSMA/CD54.When two or more nodes on the LAN segments transmit at the same time, there will be a collision and all of the transmitting nodes well enter exponential back-off, that is all of the LAN segments belong to the same( ).A collision domainB switchC bridgeD hub55.( )allows different nodes to transmit simultaneously and yet have their respective receivers correctly receive a sender’s encoded data bits.A CDMAB CSMAC CSMA/CDD CSMA/CA56.Because there are both network-layer addresses (for example, Internet IPaddresses) and link-layer addresses (that is, LAN addresses), there is a need to translate between them. For the Internet, this is the job of ( ).A RIPB OSPFC ARPD IP57.PPP defines a special control escape byte, ( ). If the flag sequence, 01111110 appears anywhere in the frame, except in the flag field, PPP precedes that instance of the flag pattern with the control escape byte.A 01111110B 01111101C 10011001D 1011111058.The device ( ) can isolate collision domains for each of the LAN segment.A modemB switchC hubD NIC59.In the following four descriptions about PPP, which one is not correct? ( )A PPP is required to detect and correct errors.B PPP is not required to deliver frames to the link receiver in the same order in which they were sent by the link sender.C PPP need only operate over links that have a single sender and a single receiver.D PPP is not required to provide flow control.60.In the PPP data frame, the( ) field tells the PPP receivers the upper-layer protocol to which the received encapsulated data belongs.A flagB controlC protocolD checksum61.PPP’s link-control protocols (LCP) accomplish ( ).A initializing the PPP linkB maintaining the PPP linkC taking down the PPP linkD all of the above62.The PPP link always begins in the ( ) state and ends in the ( ) state. ( )A open, terminatingB open, deadC dead, deadD dead, terminating63.For( ) links that have a single sender at one end of the link and a single receiver at the other end of the link.A point-to-pointB broadcastC multicastD all of the above64.With ( )transmission, the nodes at both ends of a link may transmit packets at the same time.A half-duplexB full-duplexC simplex(单工)D synchronous65.With ( ) transmission, a node can not both transmit and receive at the same time.A half-duplexB full-duplexC simplex(单工)D synchronous66.Which of the following functions can’t be implemented in the NIC? ( )A encapsulation and decapsulationB error detectionC multiple access protocolD routing67.Which of the following four descriptions is wrong? ( )A The bus interface of an adapter is responsible for communication with the adapter’s parent node.B The link interface of an adapter is responsible for implementing the link-layer protocol.C The bus interface may provide error detection, random access functions.D The main components of an adapter are the bus interface and the link interface. 68.For odd parity schemes, which of the following is correct? ( )A 011010001B 111000110C 110101110D 00011011069.( )divides time into time frames and further divides each time frame into N time slots.A FDMB TMDC CDMAD CSMA70.With CDMA, each node is assigned a different ( )A codeB time slotC frequencyD link71.Which of the following four descriptions about random access protocol is not correct? ( )A A transmission node transmits at the full rate of the channelB When a collision happens, each node involved in the collision retransmits at once.C Both slotted ALOHA and CSMA/CD are random access protocols.D With random access protocol, there may be empty slots.72.PPP defines a special control escape byte 01111101. If the data is b1b201111110b3b4b5, the value is( )after byte stuffing.A b1b20111110101111110b3b4b5B b1b20111111001111101b3b4b5C b5b4b30111111001111101b2b1D b5b4b30111110101111110b2b173.MAC address is in ( ) of the computer.A RAMB NICC hard diskD cache74.Which of the following is wrong? ( )A ARP table is configured by a system administratorB ARP table is built automaticallyC ARP table is dynamicD ARP table maps IP addresses to MAC addresses75.NIC works in ( )layer.A physicalB linkC networkD transport76.In LAN, if UTP is used, the common connector is( ).A AUIB BNCC RJ-45D NNI77.The modem’s function(s) is(are) ( ).A translates digital signal into analog signalB translates analog signal into digital signalC both translates analog signal into digital signal and translates digital signal into analog signalD translates one kind of digital signal into another digital signal78.( )defines Token-Ring protocol.A IEEE 802.3B IEEE 802.4C IEEE 802.5D IEEE 802.279.( )defines Token-Bus protocol.A IEEE 802.3B IEEE 802.4C IEEE 802.5D IEEE 802.280.( ) defines CSMA/CD protocol.A IEEE 802.3B IEEE 802.4C IEEE 802.5D IEEE 802.281.The computer network that concentrated in a geographical area, such as in a building or on a university campus, is ( )A a LANB a MANC a WAND the Internet82.The MAC address is ( ) bits long.A 32B 48C 128D 25683.Which of the following four descriptions about MAC addresses is wrong? ( )A a MAC address is burned into the adapter’s ROMB No two adapters have the same addressC An adapter’s MAC address is dynamicD A MAC address is a link-layer address84.Which of the following four descriptions about DHCP is correct? ( )A DHCP is C/S architectureB DHCP uses TCP as its underlying transport protocolC The IP address offered by a DHCP server is valid foreverD The DHCP server will offer the same IP address to a host when the host requests an IP address85.The ( )field permits Ethernet to multiplex network-layer protocols.A preambleB typeC CRCD destination MAC address86.For 10BaseT, the maximum length of the connection between an adapter and the hub is ( ) meters.A 50B 100C 200D 50087.An entry in the switch table contains the following information excepts for ( )A the MAC address of a nodeB the switch interface that leads towards the nodeC the time at which the entry for the node was placed in the tableD the IP address of a node88.Consider the 4-bit generator , G is 1001, and suppose that D has the value 101110000. What is the value of R?89.Consider the following graph of the network. Suppose Host A will send a datagram to Host B, Host A run OICQ on port 4000, Host B run OICQ on port 8000. All of ARP tables are up to date. Enumerate all the steps when message “Hello” is sent from host A to host B.。
抗体类药物的质量控制—张伯彦

• 可能改变结合特异性 Altered binding specificity
– Possible change in antigen specificity and, ultimately, tissue specificity
– High impact but low probability-- the altered specificity is achieved only with a great deal of engineering and multiple alterations
目前针对多种癌症的大量 临床研究的ADC使用这种模式。
这种模式尚处于早期研发阶段 (点突变的Thio-Mab或Ambrx 的非天然氨基酸)。
罗氏/基因泰克公司 KADCYLA模式 (2013年2月)
抗体结构和其电荷变量产生的原因
酸性峰 - Red 碱性峰 - Blue 视具体情况- Green
链间二硫键位置
克隆筛选 for Ph III GMP
Regulatory filing with USA FDA
IND
INDa
BLA
一般来说,一个创新抗体药从DNA质粒构建到BLA上市,需要8-10年时间。 临床前到拿到临床批件约13到15个月。
依赖临床周期的生产工艺开发(仿制药)
Page 11
中国生物制药公司:
• 可能增加免疫原性 Increased immunogenicity
– Idiotypic markers
– Epitope spreading: increased immunogenicity of therapeutic possibly leading to broader immune response to the therapeutic antibody
Direct

CHAPTER4Direct ProofI t is time to prove some theorems.There are various proof techniques,and this chapter describes the most straightforward approach,a tech-nique called direct proof.As we begin,it is important to keep in mind the meanings of three key terms:Theorem,proof and definition.A theorem is a mathematical statement that is true and that can be verified as true.A proof of a theorem is a written verification that shows that the theorem is definitely and unequivocally true.A proof should be understandable and convincing to anyone who has the requisite background and knowledge.This knowledge includes an understanding of the meanings of the mathematical words,phrases and symbols that occur in the theorem and its proof.It is crucial that both the writer of the proof and the readers of the proof agree on the exact meanings of all the words, for otherwise there is an intolerable level of ambiguity.A definition is an exact,unambiguous explanation of the meaning of a mathematical word or phrase.We will elaborate on the terms theorem and definition in the next two sections,and thenfinally we will be ready to begin writing proofs.4.1TheoremsA theorem is a statement that is true and has been proved to be true. You have encountered many theorems in your mathematical education. Here are some theorems taken from an undergraduate calculus text.They will be familiar to you,though you may not have read all the proofs. Theorem:Let f be continuous on an open interval I and let c∈I.If f(c)is the maximum or minimum value of f on I and if f (x)exists, then f (x)=0.Theorem:If ∞k=1a k converges,then lim k→∞a k=0.Theorem:Suppose f is continuous on the interval[a,b].Then f is integrable on[a,b].84Direct Proof Theorem:Every absolutely convergent series converges.Observe that each of these theorems either has the conditional form“If P,then Q.”or can be put into that form.Thefirst theorem has an initial sentence“Let f be continuous on an open interval I,and let c∈I.”which sets up some notation,but a conditional statement follows it.The third theorem has form“Suppose P.Then Q.”but this means the same thing as“If P,then Q.”The last theorem can be re-expressed as“If a series is absolutely convergent,then it is convergent.”A theorem of form“If P,then Q.”can be regarded as a device that produces new information from P.Whenever we are dealing with a situation where P is true,then the theorem guarantees that,in addition, Q is true.Since this kind of“expansion of information”is useful,theorems of form“If P,then Q.”are very common.But not every theorem is a conditional statement.Some have the form of the biconditional P⇔Q,but,as we know,that can be expressed as two conditional statements.Other theorems simply state facts about specific things.For example,here is another theorem from your study of calculus. Theorem:The series1+1+13+14+15+···diverges.2It would be difficult(or at least awkward)to restate this as a conditional statement.Still,it is true that most theorems are conditional statements, so much of this book will concentrate on that type of theorem.It is important to be aware that there are a number of words that mean essentially the same thing as the word“theorem,”but which are used in slightly different ways.In general the word“theorem”is reserved for a statement that is considered important or significant(the Pythagorean Theorem,for example).A statement that is true but not as significant is sometimes called a proposition.A lemma is a theorem whose main purpose is to help prove another theorem.A corollary is a result that is an immediate consequence of a theorem or proposition.It is not important that you remember all these words now,for their meanings will become clear with usage.Our main task is to learn how to prove theorems.As the above examples suggest,proving theorems requires a clear understanding of the meaning of the conditional statement,and that is the primary reason we studied it so extensively in Chapter2.In addition,it is also crucial to understand the role of definitions.Definitions854.2DefinitionsA proof of a theorem should be absolutely convincing.Ambiguity must be avoided.Thus everyone must agree on the exact meaning of each mathematical term.In Chapter1we defined the meanings of the sets N, Z,R,Q and ,as well as the meanings of the symbols∈and⊆,and we shall make frequent use of these things.Here is another definition that we use often.Definition4.1An integer n is even if n=2a for some integer a∈Z.Thus,for example,10is even because10=2·5.Also,according to the definition7is not even because there is no integer a for which7=2a. While there would be nothing wrong with defining an integer to be odd if it’s not even,the following definition is more concrete.Definition4.2An integer n is odd if n=2a+1for some integer a∈Z.Thus7is odd because7=2·3+1.We will use these definitions whenever the concept of even or odd numbers arises.If in a proof a certain number turns out to be even,the definition allows us to write it as2a for an appropriate integer a.If some quantity has form2b+1where b is an integer,then the definition tells us the quantity is odd.Definition4.3Two integers have the same parity if they are both even or they are both odd.Otherwise they have opposite parity.Thus5and−17have the same parity,as do8and0;but3and4have opposite parity.Two points about definitions are in order.First,in this book the word or term being defined appears in boldface type.Second,it is common to express definitions as conditional statements even though the biconditional would more appropriately convey the meaning.Consider the definition of an even integer.You understand full well that if n is even then n=2a (for a∈Z),and if n=2a,then n is even.Thus,technically the definition should read“An integer n is even if and only if n=2a for some a∈Z.”However,it is an almost-universal convention that definitions are phrased in the conditional form,even though they are interpreted as being in the biconditional form.There is really no good reason for this,other than economy of words.It has just become the standard way of writing definitions,and we have to get used to it.Here is another definition that we will use often.86Direct Proof Definition4.4Suppose a and b are integers.We say that a divides b, written a|b,if b=ac for some c∈Z.In this case we also say that a is a divisor of b,and that b is a multiple of a.For example,5divides15because15=5·3.We write this as5|15. Similarly8|32since32=8·4,and−6|6since6=−6·1.However,6does not divide9because there is no integer for which9=6·c.We express this as 6|9,which we read as“6does not divide9.”Be careful of your interpretation of the symbols.There is a big difference between the expressions a|b and a/b.The expression a|b is a statement, while a/b is a fraction.For example,8|16is true and8|20is false.By contrast,8/16=0.5and8/20=0.4are numbers,not statements.Be careful not write one when you mean the other.Every integer has a set of integers which divide it.For example the set of divisors of6is{a∈Z:a|6}={−6,−3,−2,−1,1,2,3,6}.The set of divisors of5is{−5,−1,1,5}.This brings us to the following definition,with which you are already familiar.Definition4.5A natural number p is prime if it has exactly two positive divisors,1and p.Of course not all terms can be defined.If we defined every word that appeared in a definition,we would need separate definitions for the words that appeared in those definitions,and so on until the chain of defined terms became circular.Thus we accept some ideas as being so intuitively clear that they do not require definitions.For example,we will notfind it necessary to define exactly what an integer is,nor will we define what addition,multiplication,subtraction and division are.We will freely use such things as the distributive and commutative properties of addition and multiplication,along with all the usual properties of arithmetic and algebra.In addition,we accept the following statements as being so obviously true that they do not need to be proved.Fact4.1Suppose a and b are integers.Then:•a+b∈Z•a−b∈Z•ab∈ZThese three statements can be combined.For example,we see that if a,b and c are integers,then a2b−ca+b is also an integer.Another fact that we will accept without proof(at least for now)is that every natural number greater than1has a unique factorization intoDirect Proof87 primes.For example,the number1176can be factored into primes as 1176=2·2·2·3·7·7=23·3·72.By unique we mean that any factorization of1176into primes will have exactly the same factors(i.e.three2’s,one3, and two7’s.)Thus,for example,there is no valid factorization of1176that has a factor of5.You may be so used to factoring numbers into primes that you think it is obvious that there cannot be different prime factorizations of the same number,but in fact this is a fundamental result whose proof is not transparent.Nonetheless,we will be content to assume that every natural number greater than1has a unique factorization into primes. (Though you may wish to revisit the issue of a proof once you become fluent at proving theorems.)We will introduce other accepted facts,as well as other definitions,as they are needed.4.3Direct ProofThis section explains a simple technique for proving theorems or propo-sitions which have the form of conditional statements.The technique is called direct proof.To simplify the discussion,ourfirst examples will involve proving statements that are almost obviously true.Thus we will call the statements propositions rather than theorems.(Remember,a proposition is a statement that,although true,is not as significant as a theorem.)To understand how the technique of direct proof works,suppose we have some proposition of the following form.Proposition If P,then Q.This proposition is a conditional statement of form P⇒Q.Our goal is to show that this conditional statement is true.To see how to proceed, look at the truth table.P Q P⇒QT T TT F FF T TF F TThe table shows that if P is false,the statement P⇒Q is automatically true.This means that if we are concerned with showing P⇒Q is true,we don’t have to worry about the situations where P is false(as in the last88Direct Proof two lines of the table)because the statement P⇒Q will be automatically true in those cases.But we must be very careful about the situations where P is true(as in thefirst two lines of the table).We must to show that the condition of P being true forces Q to be true also,for that means the second line of the table cannot happen.This gives a fundamental outline for proving statements of the form P⇒Q.Begin by assuming that P is true(remember,we don’t need to worry about P being false)and show this forces Q to be true.We summarize this as follows.Outline for Direct Proof.Proposition If P,then Q.Proof.Suppose P....Therefore Q.■So the setup for direct proof is remarkably simple.Thefirst line of the proof is the sentence“Suppose P.”The last line is the sentence“Therefore Q.”Between thefirst and last line we use logic,definitions and standard math facts to transform the statement P to the statement Q.It is common to use the word“Proof”to indicate the beginning of a proof,and the symbol to indicate the end.As ourfirst example,let’s prove that if x is odd then x2is also odd. (Granted,this is not a terribly impressive result,but we will move on to more significant things in due time.)Thefirst step in the proof is tofill in the outline for direct proof.This is a lot like painting a picture,where the basic structure is sketched infirst.We leave some space between the first and last line of the proof.The following series of frames indicates the steps you might take tofill in this space with a logical chain of reasoning.Proposition If x is odd,then x2is odd.Proof.Suppose x is odd.Therefore x2is odd.■Now that we have written thefirst and last lines,we need tofill in the space with a chain of reasoning that shows that x being odd forces x2to beDirect Proof89 odd.In doing this it’s always advisable to use any definitions that apply. Thefirst line says x is odd,and by Definition4.2it must be that x=2a+1 for some a∈Z,so we write this in as our second line.Proposition If x is odd,then x2is odd.Proof.Suppose x is odd.Then x=2a+1for some a∈Z,by definition of an odd number.Therefore x2is odd.■Now jump down to the last line,which says x2is odd.Think about what the line immediately above it would have to be in order for us to conclude that x2is odd.By the definition of an odd number,we would have to have x2=2a+1for some a∈Z.However,the symbol a now appears earlier in the proof in a different context,so we should use a different symbol,say b.Proposition If x is odd,then x2is odd.Proof.Suppose x is odd.Then x=2a+1for some a∈Z,by definition of an odd number.Thus x2=2b+1for an integer b.Therefore x2is odd,by definition of an odd number.■We are almost there.We can bridge the gap as follows.Proposition If x is odd,then x2is odd.Proof.Suppose x is odd.Then x=2a+1for some a∈Z,by definition of an odd number.Thus x2=(2a+1)2=4a2+4a+1=2(2a2+2a)+1.So x2=2b+1where b is the integer b=2a2+2a.Thus x2=2b+1for an integer b.Therefore x2is odd,by definition of an odd number.■Finally,we may wish to clean up our work and write the proof in paragraph form.Here is ourfinal version.90Direct Proof Proposition If x is odd,then x2is odd.Proof.Suppose x is odd.Then x=2a+1for some a∈Z,by definitionof an odd number.Thus x2=(2a+1)2=4a2+4a+1=2(2a2+2a)+1,so x2=2b+1where b=2a2+2a∈Z.Thus x2=2b+1for an integerb.Therefore x2is odd,by definition of an odd number.■It’s generally a good idea to write thefirst and last line of your proof first,and thenfill in the gap,sometimes jumping alternately between top and bottom until you meet in the middle,as we did above.This way you are constantly reminded that you are aiming for the statement at the bottom.Sometimes you will leave too much space,sometimes not enough.Sometimes you will get stuck beforefiguring out what to do.This is normal.Mathematicians do scratch work just as artists do sketches for their paintings.Here is another example.Consider writing a proof of the following proposition.Proposition Suppose a,b and c are integers.If a|b and b|c,then a|c.Let’s apply the basic outline for direct proof.To clarify the procedure we will write the proof in stages again.Proposition Suppose a,b and c are integers.If a|b and b|c,then a|c. Proof.Suppose a|b and b|c.Therefore a|c.■Ourfirst step is to apply Definition4.4to thefirst line.The definition says a|b means b=ac for some integer c,but since c already appears in a different context on thefirst line,we must use a different letter,say d. Similarly let’s use a new letter e in the definition of b|c.Proposition Suppose a,b and c are integers.If a|b and b|c,then a|c. Proof.Suppose a|b and b|c.By Definition4.4,we know a|b means there is an integer d with b=ad. Likewise,b|c means there is an integer e for which c=be.Therefore a|c.■Direct Proof 91We have almost bridged the gap.The line immediately above the last line should show that a |c .According to Definition 4.4,this line should say that c =ax for some integer x .We can get this equation from the lines at the top,as follows.Proposition Suppose a ,b and c are integers.If a |b and b |c ,then a |c .Proof.Suppose a |b and b |c .By Definition 4.4,we know a |b means there is an integer d with b =ad .Likewise,b |c means there is an integer e for which c =be .Thus c =be =(ad )e =a (de ),so c =ax for the integer x =de .Therefore a |c .■Here is another example,though this time the proof is presented all at once rather than in stages.Proposition If x is an even integer,then x 2−6x +5is odd.Proof.Suppose x is an even integer.Then x =2a for some a ∈Z ,by definition of an even integer.So x 2−6x +5=(2a )2−6(2a )+5=4a 2−12a +5=4a 2−12a +4+1=2(2a 2−6a +2)+1.Therefore we have x 2−6x +5=2b +1,where b =2a 2−6a +2∈Z .Consequently x 2+3x +5is odd,by definition of an odd number.■In writing a proof you do not have to put each sentence on a separate line.But we will do this for clarity in the first few chapters of this book.The examples we’ve looked at so far have all been proofs of statements about integers.In our next example,we are going to prove that if x and y are positive real numbers for which x ≤y ,then x ≤ y .You may feel that the proof is not as “automatic”as the proofs we have done so far.Finding the right steps in a proof can be challenging,and that is part of the fun.Proposition Let x and y be positive numbers.If x ≤y ,then x ≤ y .Proof.Suppose x ≤y .Subtracting y from both sides gives x −y ≤0.This can be written as x 2− y 2≤0.Factor this to get ( x − y )( x + y )≤0.Dividing both sides by the positive number x + y produces x − y ≤0.Adding y to both sides gives x ≤ y .■92Direct ProofThis proposition tells us that whenever we have x ≤y ,we can take the square root of both sides and be assured that x ≤ y .This can actually be useful,as we will see in our next proposition.The next proposition will concern the expression 2 xy ≤x +y .Notice when you plug in random positive values for the variables,the expression is true.For example,in plugging in x =6and y =4,the left side is 2 6·4=4 6≈9.79,which is less than the right side 6+4=10.Is it true that 2 xy ≤x +y for any positive x and y ?How could we prove it?To see how,let’s first cast this into the form of a conditional statement:If x and y are positive real numbers,then 2 xy ≤x +y .The proof begins with the assumption that x and y are positive,and ends with 2 xy ≤x +y .In mapping out a strategy,it can be helpful to work backwards,working from 2 xy ≤x +y to something that is obviously true.Then the steps can be reversed in the proof.In this case,squaring both sides of 2 xy ≤x +y gives us4xy ≤x 2+2xy +y 2.Now subtract 4xy from both sides and factor.0≤x 2−2xy +y 20≤(x −y )2But this last line is clearly true,since the square of x −y cannot be negative!This gives us a strategy for the proof,which follows.Proposition If x and y are positive real numbers,then 2xy ≤x +y .Proof.Suppose x and y are positive real numbers.Then 0≤(x −y )2,so 0≤x 2−2xy +y 2.Adding 4xy to both sides gives 4xy ≤x 2+2xy +y 2,which gives 4xy ≤(x +y )2.Taking the square root of both sides produces 2 xy ≤x +y .■Notice that in going from the next-to-last line to the last line of the proof,we took the square root of both sides of 4xy ≤(x +y )2and got 4xy ≤ (x +y )2.The fact that taking roots of both sides does not alter the ≤follows from our previous proposition.This is an important point.Sometimes the proof of a proposition or theorem uses another proposition or theorem.4.4Using CasesIn proving a statement is true,we sometimes have to examine multiple cases before showing the statement is true in all possible scenarios.This section illustrates a few examples.Using Cases93 Our examples will concern the expression1+(−1)n(2n−1).Here is a table that shows what we get when plugging in various integers for n. Notice that1+(−1)n(2n−1)is a multiple of4in every line.n1+(−1)n(2n−1)10243−4485−8612Is1+(−1)n(2n−1)always a multiple of4?We will prove the answer is“yes”in our next example.Notice,however,that the expression1+(−1)n(2n−1) behaves differently depending on whether n is even or odd,for in thefirst case(−1)n=1,and in the second(−1)n=−1.Thus the proof must examine these two possibilities separately.Proposition If n∈N,then1+(−1)n(2n−1)is a multiple of4.Proof.Suppose n∈N.Then n is either even or odd.Let’s consider these two cases separately. Case1.Suppose n is even.Then n=2k for some k∈Z,and(−1)n=1. Thus1+(−1)n(2n−1)=1+(1)(2·2k−1)=4k,which is a multiple of4. Case2.Suppose n is odd.Then n=2k+1for some k∈Z,and(−1)n=−1. Thus1+(−1)n(2n−1)=1−(2(2k+1)−1)=−4k,which is a multiple of4. These cases show that1+(−1)n(2n−1)is always a multiple of4.■Now let’s examine theflip side of the question.We just proved that 1+(−1)n(2n−1)is always a multiple of4,but can we get every multiple of4 this way?The following proposition and proof give an affirmative answer. Proposition Every multiple of4has form1+(−1)n(2n−1)for some n∈N. Proof.In conditional form,the proposition is as follows:If k is a multiple of4,then there is an n∈N for which1+(−1)n(2n−1)=k. What follows is a proof of this conditional statement.Suppose k is a multiple of4.This means k=4a for some integer a.We must produce an n∈N for which1+(−1)n(2n−1)=k.This is done by cases,depending on whether a is zero,positive or negative.94Direct ProofCase1.Suppose a=0.Let n=1.Then1+(−1)n(2n−1)=1+(−1)1(2−1)=0 =4·0=4a=k.Case2.Suppose a>0.Let n=2a,which is in N because a is positive.Also n is even,so(−1)n=1.Thus1+(−1)n(2n−1)=1+(2n−1)=2n=2(2a)=4a=k. Case3.Suppose a<0.Let n=1−2a,which is an element of N because a is negative,making1−2a positive.Also n is odd,so(−1)n=−1.Thus 1+(−1)n(2n−1)=1−(2n−1)=1−(2(1−2a)−1)=4a=k.The above cases show that no matter whether a multiple k=4a of4is zero,positive or negative,it always equals1+(−1)n(2n−1)for some natural number n.■4.5Treating Similar CasesOccasionally two or more cases in a proof will be so similar that writing them separately seems tedious or unnecessary.Here is an example. Proposition If two integers have opposite parity,then their sum is odd.Proof.Suppose m and n are two integers with opposite parity.We need to show that m+n is odd.This is done in two cases,as follows. Case1.Suppose m is even and n is odd.Thus m=2a and n=2b+1for some integers a and b.Therefore m+n=2a+2b+1=2(a+b)+1,which is odd(by Definition4.2).Case2.Suppose m is odd and n is even.Thus m=2a+1and n=2b for some integers a and b.Therefore m+n=2a+1+2b=2(a+b)+1,which is odd(by Definition4.2).In either case,m+n is odd.■The two cases in this proof are entirely alike except for the order in which the even and odd terms occur.It is entirely appropriate to just do one case and indicate that the other case is nearly identical.The phrase “Without loss of generality...”is a common way of signaling that the proof is treating just one of several nearly identical cases.Here is a second version of the above example.Proposition If two integers have opposite parity,then their sum is odd.Proof.Suppose m and n are two integers with opposite parity.We need to show that m+n is odd.Without loss of generality,suppose m is even and n is odd.Thus m=2a and n=2b+1for some integers a and b.Therefore m+n=2a+2b+1=2(a+b)+1,which is odd(by Definition4.2).■Treating Similar Cases 95In reading proofs in other texts,you may sometimes see the phrase “Without loss of generality”abbreviated as “WLOG.”However,in the interest of transparency we will avoid writing it this way.In a similar spirit,it is advisable—at least until you become more experienced in proof writing—that you write out all cases,no matter how similar they appear to be.It is now very important that you practice what you have learned by doing the following exercises.Exercises for Chapter 4Use the method of direct proof to prove the following statements.1.If x is an even integer,then x 2is even.2.If x is an odd integer,then x 3is odd.3.If a is an odd integer,then a 2+3a +5is odd.4.Suppose x ,y ∈Z .If x and y are odd,then xy is odd.5.Suppose x ,y ∈Z .If x is even,then xy is even.6.Suppose a ,b ,c ∈Z .If a |b and a |c ,then a |(b +c ).7.Suppose a ,b ∈Z .If a |b ,then a 2|b 2.8.Suppose a is an integer.If 5|2a ,then 5|a .9.Suppose b is an integer.If 7|4a ,then 7|a .10.Suppose a and b are integers.If a |b ,then a |(3b 3−b 2+5b ).11.Suppose a ,b ,c ,d ∈Z .If a |b and c |d ,then ac |bd .12.If x ∈R and 0<x <4,then 4x (4−x )≥1.13.Suppose x ,y ∈R .If x 2+5y =y 2+5x ,then x =y or x +y =5.14.If n ∈Z ,then 5n 2+3n +7is odd.(Try cases.)15.If n ∈Z ,then n 2+3n +4is even.(Try cases.)16.If two integers have the same parity,then their sum is even.(Try cases.)17.If two integers have opposite parity,then their product is even.18.Suppose x and y are positive real numbers.If x <y ,then x 2<y 2.19.Suppose a ,b and c are integers.If a 2|b and b 3|c ,then a 6|c .20.If a is an integer and a 2|a ,then a ∈{−1,0,1}.21.If p is prime and k is an integer for which 0<k <p ,then p divides p k .22.If n ∈N ,then n 2=2 n 2 + n 1 .(You may need a separate case for n =1.)23.If n ∈N ,then 2n n is even.24.If n ∈N and n ≥2,then the numbers n !+2,n !+3,n !+4,n !+5,...n !+n are all composite.(This means that for any n ,no matter how big,there exist n consecutive composite numbers.In other words there are arbitrarily large “gaps”between prime numbers.)25.If a ,b ,c ∈N and c ≤b ≤a ,then a b b c = a b −c a −b +c c .。
Backended

1. 数据准备对于CDN的Silicon Ensemble而言后端设计所需的数据主要有是Foundry厂提供的标准单元、宏单元和I/O Pad的库文件,它包括物理库、时序库及网表库,分别以.lef、.tlf和.v的形式给出。
前端的芯片设计经过综合后生成的门级网表,具有时序约束和时钟定义的脚本文件和由此产生的.gcf约束文件以及定义电源Pad的DEF(Design Exchange Format)文件。
(对synopsys 的Astro 而言,经过综合后生成的门级网表,时序约束文件SDC是一样的,Pad的定义文件tdf,.tf 文件technology file,Foundry厂提供的标准单元、宏单元和I/O Pad的库文件就与FRAM,CELL view,LM view形式给出(Milkway 参考库and DB,LIB file)。
2. 布局规划主要是标准单元、I/O Pad和宏单元的布局。
I/OPad预先给出了位置,而宏单元则根据时序要求进行摆放,标准单元则是给出了一定的区域由工具自动摆放。
布局规划后,芯片的大小,Core的面积,Row的形式、电源及地线的Ring和Strip都确定下来了。
如果必要在自动放置标准单元和宏单元之后,你可以先做一次PNA(power network analysis)--IR drop and EM。
3.Placement自动放置标准单元布局规划后,宏单元、I/O Pad的位置和放置标准单元的区域都已确定,这些信息SE(Silicon Ensemble)会通过DEF文件传递给PC(Physical Compiler),PC根据由综合给出的.DB文件获得网表和时序约束信息进行自动放置标准单元,同时进行时序检查和单元放置优化。
如果你用的是PC+Astro那你可用write_milkway,read_milkway传递数据。
4.时钟树生成(CTS Clock tree synthesis)芯片中的时钟网络要驱动电路中所有的时序单元,所以时钟源端门单元带载很多,其负载延时很大并且不平衡,需要插入缓冲器减小负载和平衡延时。
昆虫杆状病毒细胞表达系统 课件

6) Simplicity of technology
This technology has made expression of full-length proteins fast, easy and reliable. Recombinant Baculovirus can be obtained in two simple steps–cloning and co-transfection–in as little as 5 days. The ease of use now rivals that of bacterial expression systems and BEVS technology does not require that the recombinant protein be expressed as a fusion protein.
5) Capacity to express unspliced genes
Insect cells have the capability to perform intron/exon splicing. However, certain virus-, tissue- or species-specific splicing patterns will not be obtained if they require the presence of particular splicing factors which are not available in the infected insect cell environment. In general, for high protein expression levels, a cDNA insert rather than a genomic DNA fragment is recommended.
5Biochemistry生物化学

Monosaccharides Are Joined to Alcohols and Amines Through Glycosidic Bonds
The new bond formed between the anomeric carbon atom of glucose and the hydroxyl oxygen atom of methanol is called a glycosidic bond— specifically, an O-glycosidic bond. The anomeric carbon atom of a sugar can be linked to the nitrogen atom of an amine to form an N-glycosidic bond.
Regulatory Strategies: Enzymes and Hemoglobin
The activity of proteins, including enzymes, often must be regulated so that they function at the proper time and place. The biological activity of proteins is regulated in four principal ways:
Isozymes Provide a Means of Regulation Specific to Distinct Tissues and Developmental Stages
Covalent Modification Is a Means of Regulating Enzyme Activity
d-Aldoses containing three, four, five, and six carbon atoms. d-Aldoses contain an aldehyde group (shown in blue) and have the absolute configuration of d-glyceraldehyde at the asymmetric center (shown in red) farthest from the aldehyde group. The numbers indicate the standard designations for each carbon atom.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
46at several places(in and out of the chromatin)and undergo phosphorylation at multiple sites.p53is a multifunctional tumor suppressor protein essential for maintaining the integrity of higher eu-caryote genomes[4,5].The functional protein is an homotetramer,the structure of which oscillates be-tween various conformations recognizable by specific sets of monoclonal antibodies[6,7].It is supposed that the various conformers show different biological activities in vivo.p53is also an unstable protein which shows a number of similarities with c-Fos and c-Jun: (i)it can localize both in the cytoplasm and in the nucleus according to the experimental/physiological conditions,(ii)its turnover is regulated upon activa-tion of intracellular signalling cascades,(iii)it can associate with various protein partners,(iv)mutant proteins found in spontaneously occurring tumors are more stable than the wild-type protein and(v)sev-eral catabolic pathways operate on it.Thus,p53is mostly degraded following the ubiquitin/proteasome pathway.However,calpains also seem to contribute to its degradation,at least under specific conditions. Where are c-Fos and c-Jun degraded?The nuclear turnover of c-Fos has long been known to be rapid.Paradoxically,the definite proof that c-Fos can be degraded within the nucleus is still lacking. Efficient destruction within this compartment is,how-ever,very likely,because of the presence of both the proteasome and of enzymes of the ubiquitin pathway [8].However,it cannot be ruled out formally that c-Fos has to return to the cytoplasm,after a post-translational modification for example,for being de-graded at the nuclear periphery.Along this line,(i)it is worth noting that the human immunodeficiency virus Rev regulator is very unstable within the cytoplasm and relatively long-lived within the nucleus[9]and (ii)it has been suggested that interaction between the Mdm2protooncoprotein and p53triggers the nuclear export of the latter for degradation into the cytoplasm [10].Work by the laboratory has shown that c-Fos transport from the cytoplasm,where it is synthesized, into the nucleus,where it plays its part as a transcrip-tion factor,is regulated by extracellular signals[11, 12].In other words,c-Fos can be retained within the cytoplasm where it shows a very short half-life indi-cating that cytoplasmic proteases,which remain to be identified,can operate on c-Fos(Figure2).Retention of c-Jun within the cytoplasm has also been docu-mented[12]but it remains to determine whether the protein is unstable in this compartment.In vitro proteolysis of c-Fos and c-Jun by calpains Milli-and micro-calpain(which are both called the ubiquitous calpains),are abundant cytoplasmic cys-teine proteases activated by calcium.They recognize structural determinants rather than primary motifs and they display a relatively strict specificity for their sub-strates which they usually cleave at only a limited number of sites(for reviews,see[13,14]).So far,only a few substrates for calpains have been identified in vivo.c-Fos and c-Jun being short-lived in the cytoplasm when their transport into the nucleus is inhibited,pos-sible degradation by calpains has been addressed by several groups.It was shown that both proteins are highly susceptible to both milli-and microcalpain in vitro[15–17].Moreover,inhibition of ubiquitous cal-pains by overexpression of their endogenous protein inhibitor,calpastatin,in transient transfection assays leads to2-3-fold higher c-Fos and c-Jun transcription activity in mouse embryofibroblasts([16]and our non-published results).This observation is consistent with the idea of a limited contribution of calpains to c-Fos and c-Jun degradation in living cells although an indirect effect of calpains could not be ruled out.Since calpains degrade their substrates to a limited extent,it remains to characterize the proteolytic system taking over for complete breakdown of c-Fos and c-Jun.In vitro study of Fos and Jun protein degradation has led to a series of interesting observations regard-ing to the mode of action of calpains.PEST sequences are peptide motifs rich in Pro,Glu,Asp,Ser and Thr commonly found in unstable proteins[18,19].They have thus been proposed to constitute instability mo-tifs as well as sites for cleavage by calpains since it was speculated that they could bind calcium,owing to their negative charge,and,thus,present the activat-ing co-factor to the protease at the level of substrates [18].However,analysis of c-Fos deletion mutants,as well as of a variety of calpain-sensitive and calpain-resistant proteins,has shown that PEST motifs are neither necessary nor sufficient for degradation by cal-pains[20].Interestingly,the viral v-FosFBR protein, but not the viral v-FosFBJ and v-JunASV17ones,is resistant to cleavage by calpains[21].Resistance to degradation is not due to the mutations in the Fos part of the protein,but to addition of exogenous motifs de-47 Figure1.Schematic representation of c-Fos and its viral counterparts.v-FosFBJ harbors5point mutations(asteriscs)plus a frameshift which replaces its last48amino acids(aa)by49others.v-FosFBR is a mutated Fos protein fused,at its N-terminus,with310amino acids derived from the Gag protein of the parental retrovirus and,at its C-terminus,with a8amino acid sequence derived from a cellular locus called fox(or fau).The Fos moiety of v-FosFBR is deleted of the N-terminal24amino acids and of the C-terminal98amino acids of c-Fos.In addition,it contains two in frame deletions of13and9amino acids(triangles)andfive point mutations that are different from those in v-FosFBJ.rived from both the gag gene of the parental retrovirus and a cellular locus called fox or fau(see Figure1). This observation is interesting since it indicates that the Fos moiety of v-FosFBR either adopts a conforma-tion significantly different of that of the same region in the cellular protein or is not as accessible as the latter, which might explain the higher oncogenic activity of the viral protein.Finally,susceptibility to calpains is primarily determined by conformational determinants of the monomers and not by the quaternary structure of c-Fos and c-Jun.The multiple cleavage sites borne by both proteins can be divided into at least two classes of sensitivity.One site located at position90–91in c-Fos is extremely sensitive.However,efficient proteolysis at this site does not show any strict dependence on the nature of the amino acids on either side of the scis-sile bond in the region extending from P2to P 2.The integrity of the monomers is not crucial for recogni-tion by calpains.Rather,recognition of sensitive sites appears to be dependent on the local conformation of peptide regions that may span several tens of amino acids and,maybe,more in the case of the identified c-Fos hypersensitive site[22].Proteolysis by calpains:a possible contribution to degradation of p53Although p53is prominently degraded following the ubiquitin/proteasome pathway,several groups have shown that calpains might also contribute to its turnover[5,23,24].In vitro,wild type p53is a sensi-tive substrate for milli-and microcalpain.Degradation is dependent on p53protein conformation.Mutants of p53with altered tertiary structure display a wide range of susceptibility to calpains,some of them be-ing largely resistant to degradation and others being more sensitive.This suggests that the different mutants tested adopt slightly different conformations,to which calpains are sensitive,but that cannot be discriminated using classical sets of monoclonal antibodies(such as PAb1620and PAb240).Inhibition of calpains using the physiological inhibitor calpastatin leads to an el-evation of p53steady-state level in human MCF7cells expressing wild type p53.Conversely,activation of calpains by calcium ionophore leads to a reduction of p53in mousefibroblasts and the effect is blocked by cell-permeant calpain inhibitors.Co-transfection of p53-null cell lines with p53and calpastatin expres-sion vectors results in an increase in p53-dependent transcription activity[23].Morover,Kubbutat and V ousden[5]have shown that inhibition of calpains in MCF7cells results in longer half-life of wild type p53and Zhang et al.[24]have reported cell cycle-dependent degradation of wild type p53by calpain,or by a calpain-like protease,in a humanfibroblast cell line.Taken together,these observations support the idea that calpains may also contribute to the regulation of wild type p53protein levels in vivo although the extent of this contribution is modest.48Figure2.Potential complexity of the degradation of c-Fos,c-Jun and p53proteins.Ubiquitous milli-and micro-calpains could contribute to the degradation of c-Fos,c-Jun and p53in vivo.This pathway would only concern the degradation of the3proteins when they have not yet entered the nucleus as calpains are cytoplamic proteases.However,it has been reported that a fraction of calpains could enter the nucleus under specific conditions.c-Fos,c-Jun and p53have been described to be substrate of the ubiquitin/proteasome pathway.However the formal proof that they are degraded within the nucleus is still lacking and it cannot be excluded that they would have to return to the cytoplasm,after a possible modification,for being broken down.A fraction of cytoplasmic c-Fos can also be selectively taken up by lysosomes for degradation. The relative contribution of these pathways in the degradation of these proteins is not known,although the ubiquitin/proteasome pathway is very likely to be the principal pathway.Characterization of the thermosensitive E1 ubiquitin-activating enzyme A31N-ts20cell line According to our current knowledge,protein ubiqui-tination involves three steps:(i)activation of ubiq-uitin through formation of an energy-rich bond with an E1ubiquitin-activating enzyme,(ii)transfer of activated ubiquitin onto E2ubiquitin-conjugating en-zymes which,in turn,(iii)alone,or in combination with E3ubiquitin-protein ligase enzymes,transfer ubiquitin onto target proteins.Cell mutants harboring a thermosensitive E1 ubiquitin-activating enzyme are useful tools for study-ing the involvement of the ubiquitin pathway in the control of specific cell functions or of the degradation of specific proteins.A31N-ts20cells are thermosen-sitive mutant cells derived from Balb/c3T3mouse embryofibroblasts subjected to chemical mutagen-esis.They were initially characterized for a defect in DNA synthesis since they accumulated in early S phase upon shift from the permissive(32◦C)to the non-permissive(39◦C)temperature(for details,see [25])The ts defect was subsequently shown to be due to a deficient E1enzyme[26]and expression of a wild type E1enzyme upon cell transfection rescued the ts phenotype[27].Since it was important to determine to which degree the ubiquitin pathway is repressed upon shift to the non permissive temperature in these cells, we have undertaken a detailed biochemical character-ization of A31N-ts20cells.Our data show that:(i) A31N-ts20-E1enzymatic activity is heat-inactivatable in vitro and(ii)a major mechanism responsible for its inactivation in vivo consists of accelerated destruction. We also showed that,surprisingly,considerable reduc-tion in E1abundance little alters the formation of the bulk of protein-ubiquitin conjugates when A31N-ts20 cells are grown at the non-permissive temperature. However,specific proteins such as p53,c-Jun and his-tone H2A are no longer ubiquitinated/degraded under these conditions.Further biochemical characterization of A31N-ts20cells argues against the existence of an E1-independent ubiquitination pathway operating in this cellular context.Rather,our data support the idea that ubiquitination of the various protein substrates in A31N-ts20cells requires different amounts of a unique E1enzyme in vivo[28].Our data thus indicate that A31N-ts20cells show a leaky phenotype with regard to the inactivation of the ubiquitin pathway.In consequence,continued degradation of a specific protein in heat-treated A31N-ts20cells must be interpreted with caution and does not necessarily signify ubiquitin-independent degra-dation.However,because of the differential behavior of certain proteins in A31N-ts20cultured at the non-49Figure 3.Degradation of c-Fos and c-Jun during the g 0-to-S phase transition.E1-thermosensitive A31N-ts20mouse embryo fibrob-lasts were grown at the permissive temperature (32◦C).Cells were serum-deprived for 36hours to bring them in G 0.They were,then,stimulated for growth by addition of 20%serum.In these con-ditions,c-fos and c-jun genes are rapidly and transiently induced (A and Ba).To identify the proteolytic pathway(s)involved in the degradation of c-Fos and c-Jun,different cell-permeant protease in-hibitors were added together with the serum and possible delay in protein disappearance was assayed by immunoblotting analysis of total cell extracts using specific antibodies.A typical experiment where the proteasome is inhibited in the presence of lactacystin is presented in (Bb).Similarly,requirement upon a functional E1ubiq-uitin-activating enzyme was tested by transfering cells from 32◦C to 39◦C 16hours prior serum stimulation (A).A typical experiment,showing that c-Jun is stabilized whereas c-Fos is not,is presented in (Bc).permissive temperature,our data indicate that such a cell line might be useful for unveiling the existence of differences in the intimate mechanisms responsible for the ubiquitination of the various cell proteins in vivo .Moreover,it should constitute an invaluable tool for providing with criteria of reliability when developing in vitro ubiquitination assays for specific proteins [28].Differential directing of c-Fos and c-Jun to the proteasome during the g 0-to-S phase transition in mouse embryo fibroblasts c-Fos and c-Jun accumulation is transiently induced at the begining of the g 0-to-S phase transition in qui-escent cells stimulated for growth (Figure 3).To ad-dress the mechanisms responsible for rapid clearance of c-Fos and c-Jun proteins under these experimen-tal conditions,we used A31N-ts20mouse embryo fibroblasts.The use of cell-permeant protease in-hibitors indicates that both proteins are degraded by the proteasome and excludes any major contribution for calpains and lysosomes during the G 0-to-S phase transition.Synchronisation of A31N-ts20cells at the non permissive temperature blocks the degradation of c-Jun,indicating that this process is E1-dependent.This observation is consistent with the observation by others that the ability to be ubiquitinated corre-lates with instability in exponentially growing human HeLa cells [29].In contrast,c-Fos is broken down according to an apparently E1-independent pathway in ts20cells.Interestingly,c-Jun is highly unstable in c-Fos-null mouse embryo fibroblasts stimulated for growth.Taken together,these observations show that in vivo during a g 0-to-S phase transition (i)the precise mechanisms triggering c-Fos and c-Jun directing to the proteasome are not identical,(ii)the presence of c-Fos is not an absolute prerequisite for the degradation of c-Jun and (iii)the degradation of c-Jun is not required for that of c-Fos.In another E1-thermosensitive hamster cell line E36-ts20[30]observed a 3-fold reduction in c-Fos degradation rate in cells grown at the non-permissive temperature.Invoking a possible leakiness of the mu-tant and taking into account that c-Fos can be ubiquiti-nated in vitro in reconstituted ubiquitinylation systems [30,31],the authors reasonably concluded to an ex-clusively ubiquitin-and E1-dependent degradation for c-Fos.Although such a scenario is highly probable,we feel that additional experiments are still required be-fore a definitive conclusion can be drawn.Particularly,it will be necessary (i)to show that c-Fos is actually ubiquitinated in vivo ,(ii)to identify the critical lysines ubiquitinated in c-Fos and to analyse the stability ofcorresponding c-Fos mutants in vivo and (iii)to de-termine whether the enzymes showing ubiquitination activity on c-Fos in vitro also operate in vivo .This last issue,however,appears complex since the possibil-ity of redundancy in c-Fos ubiquitinylation enzymes has been raised by the work of two laboratories which50have developed different cell-free c-Fos ubiquitination assays[30,31].One important conclusion of our experiments is that the degradation of c-Fos is not necessary for that of c-Jun and vice-versa.Several lines of evidence, however,raise the possibility that interaction with c-Jun may modulate the degradation rate of c-Fos. Stancovski et al.[30]have observed that,in an in vitro assay,c-Jun significantly stimulates both the ubiquiti-nation and the degradation of c-Fos.In another in vitro degradation assay,c-Jun,ubiquitin,MAP kinase,ca-sein kinase II and cdc2kinase are all necessary for the rapid breakdown of c-Fos[32].In another cell-free as-say,addition of an appropriately phosphorylated c-Jun can trigger the degradation of c-Fos in the reticulocyte lysate[33].In contrast,delayed degradation of c-Fos correlates with association with Jun family members in Swiss3T3cells stimulated with serum[34,35].It is worth noting that Fos and Jun family members are constantly associating and dissociating in vivo with an interaction half-life of no more than a few minutes [34].One mechanism for c-Fos degradation taking into account all these observations would be that c-Fos is(preferentially)recognized by the proteasome in the form of a monomer and that the various kinases influencing its half-life would in fact affect the disso-ciation and/or association rates of dimers.Analysis of dimerization mutants of c-Fos might help to solve this issue.Finally,contrasting with our observation that c-Jun breakdown is both proteasome-and E1-dependent during the G0-to-S phase transition and,complicating our view of c-Jun degradation,we have previously observed that this protein can be specifically and ef-ficiently proteolyzed by the26S proteasome in an E1-and ubiquitin-independent manner in in vitro degra-dation assays using either rat liver cell extracts or purified rat liver proteasome[36].Whether ubiquitin-independent breakdown of c-Jun by the proteasome corresponds in vivo to rapid degradation under specific physiological conditions or in specific cell types or to basal degradation accelerated upon ubiquitination is however not known.Such a situation has already been described in the case of the IkBa transcription factor inhibitor,whose ubiquitin-independent basal degradation becomes ubiquitin-dependent in TNF-treated cells with a half-life shortening from30to5 minutes[37].Experiments are underway for determin-ing whether such a mechanism also applies to c-Jun in vivo.AcknowledgementsThis work was supported by grants from the Centre National de la Recherche Scientifique,the Ligue Na-tionale contre le Cancer,the Association de Recherche contre le Cancer(ARC),the Agence Nationale de Recherche contre le Sida(ANRS)and the EC Biotech Programm.References1.Angel P&Herrlich P(1994)(Angel P&Herrlich P,Eds.)CRC press,Boca Raton2.Piechaczyk M&Blanchard J-M(1994)Critic.Rev.Oncol.Hematol.17:93–1313.Salvat C,Jariel-Encontre I,Pariat M,Acquaviva C,Robbins I&Piechaczyk m(1997)Recent Res.Devel.in Molecular Biol.1:1–274.Oren M(1994)Semin.Cancer Biol.5:221–2275.Kubbutat M&V ousden K(1998)Mol.Med.Today4:250–256ner J(1994)Cancer Biol.5:211–219ner J(1995)Trends Biochem.Sci.20:49–518.Coux O,Tanaka K&Goldberg AL(1996)Ann.Rev.Biochem.65:801–8479.Kubota S,Duan L,Furuta RA,Hatanaka M&Pomerantz R(1996)J.Virol.70:1282–128710.Roth J,Dobblestein M,Freedman DA,Shenk T&Levine AJ(1998)EMBO J17:554–56411.Roux P,Blanchard J-M,Fernandez A,Lamb N,Jeanteur P&Piechaczyk M(1990)Cell63:341–35112.Roux P,Carillo S,Blanchard J-M,Jeanteur P&Piechaczyk M(1994)in:Angel P&Herrlich P(Ed)The c-fos and c-jun fam-ilies of transcription factors(pp87-93)CRL Press,Bocaraton, Floride,USA13.Croall DE&DeMartino GN(1991)Physiol.Rev.71:813–84714.Sorimachi H,Ishiura S&Suzuki K(1997)Biochem.J.328:721–73215.Carillo S,Pariat M,Steff A-M,Roux P,Etienne-Julan M,Lorca T&Piechaczyk M(1994)Oncogene9:1679–1689 16.Hirai S-I,Kawasaki H,Yaniv M&Susuki K(1991)FEBSLett.287:57–6117.Watt F&Molloy PL(1993)Nucl.Acids Res.21:5092–510018.Rogers S,Wells R&Rechsteiner M(1986)Science234:364–36819.Rechsteiner M&Rogers S(1996)Trends Biochem.Sci.21:267–27120.Carillo S,Pariat M,Jariel-Encontre I,Steff A-M,Poulat F,Bertha P&Piechaczyk M(1996)Biochem.J.313:245–251 21.Steff A-M,Carillo S,Pariat M&Piechaczyk M(1997)Biochem.J.323:685–69222.Pariat M,Salvat C,Bébien M,brockly F,Carillo S,Jariel-Encontre I&Piechaczyk M(submitted)23.Pariat M,Carillo S,Mollinari M,Salvat C,Debüssche L,Bracco L,Milner J&Piechaczyk M(1997)Molec.Cell Biol.17:2806–281524.Zhang W,Lu Q,Xie ZJ&Mellgren R(1997)Oncogene14:255–26325.Zeng G-C,Donegan HL,Ozer HL&Hand R(1984)Mol.CellBiol.4:1815–18225126.McGrath JP,Jentsch S&Varshavsky A(1991)EMBO J.10:227–23627.Chowdary DR,Bermody JJ,Jha KK&Ozer HL(1994)Mol.Cell Biol.14:1997–200328.Salvat C,Acquaviva C,Scheffner M,Robbins I,PiechaczykM&Jariel-Encontre I(submited)29.Treier M,Staszewsk LM&Bohman D(1994)Cell78:787–79830.Stancovski I,Gonen H,Orian A,Schwartz AL&CiechanoverA(1995)Mol.Cell Biol.15:7106–711631.Hermida-Matsumoto M-L,Chock PB,Curran T&Yang DCH(1996)J.Biol.Chem.271:4930–493632.Tsurumi C et al.(1995)Mol.Cell.Biol.15:5682–568733.Papavassiliou AG,Treier M,Chavrier C&Bohman D(1992)Science258:1941–194434.Kovary K&Bravo R(1992)Molec.Cell Biol.12:5015–502335.Kovary K&Bravo R(1991b)Mol.Cell Biol.11:4466–447236.Jariel-Encontre I,Pariat M,Martin F,Carillo S,Salvat C&Piechaczyk M(1995)J.Biol.Chem.270:11623–11627 37.Krappmann D,Wulczyn FG&Scheidereit C(1996)EMBOJournal15:6716–6726。
