Cross-layer Networking for Peer Databases over Wireless Ad-Hoc Communities
AI使能的信道知识地图高效构建与应用

AI使能的信道知识地图高效构建与应用目录1. 内容概括 (2)1.1 AI与信道知识地图简介 (2)1.2 高效构建与应用的必要性 (3)1.3 本文档结构概览 (4)2. 信道知识地图基础 (6)2.1 信道知识地图定义与构建原则 (7)2.2 数据的收集与整理方法 (9)2.3 分类与组织知识图谱的最佳实践 (10)3. AI技术在信道知识图谱中的角色 (11)3.1 机器学习算法的选择与训练 (12)3.2 自然语言处理在知识提取中的应用 (15)3.3 数据挖掘与深度学习算法 (16)4. 信道知识地图的构建流程 (18)4.1 需求分析 (19)4.2 数据准备 (20)4.3 模型选择与训练 (21)4.4 图谱结构设计 (23)4.5 图谱评估与质量控制 (24)4.6 部署与应用 (25)5. 信道知识地图的应用场景 (27)5.1 企业网络管理 (28)5.2 信息安全与威胁分析 (29)5.3 移动通信网络的优化 (31)5.4 智能交通系统 (33)5.5 其他潜在应用领域 (34)6. 案例研究 (35)6.1 信道知识地图在企业中的应用 (37)6.2 数据特性对信道知识图谱构建的影响 (39)6.3 信道知识图谱在学术研究中的用途 (40)6.4 信道知识图谱未来发展的展望 (41)7. 结论与建议 (42)7.1 总结已有研究成果与挑战 (43)7.2 对构建与应用信道知识图谱的最终建议 (44)7.3 未来的研究方向与发展趋势 (45)1. 内容概括本文档旨在介绍AI使能的信道知识地图高效构建与应用的相关知识和实践。
信道知识地图是一种将信道信息与网络设备、应用和服务相结合的可视化表示,有助于提高网络性能和安全性。
AI技术在信道知识地图的构建和应用过程中发挥着关键作用,包括数据挖掘、模式识别、智能优化等。
本文将详细介绍AI技术在信道知识地图构建中的应用场景、方法和技术,以及如何利用AI技术实现信道知识地图的高效管理和优化。
重叠共识名词解释

重叠共识名词解释
重叠共识 (Overlapping Consensus) 是一种分布式系统中的共识算法,旨在解决分布式系统中节点之间的信任问题,确保分布式系统中的数据一致性。
重叠共识算法在多个节点之间进行共识,这些节点之间需要完成某种形式的同步,以便它们能够共同确定区块链的状态。
在重叠共识算法中,节点之间的同步是渐进的,即节点首先发送请求给其他节点,并在收到其他节点的响应后更新自己的状态。
节点之间的同步过程是异步的,这意味着节点可以在不同的时间发送请求和接收响应,而且节点之间的通信是安全的,不需要信任其他节点。
重叠共识算法的主要优点是在不建立信任关系的情况下实现分布式系统中的数据一致性。
这意味着可以在多个节点之间共享数据,而不需要担心节点之间的信任问题。
重叠共识算法还可以提高分布式系统的性能和可扩展性,因为它们允许多个节点同时处理交易并确定区块链的状态。
重叠共识算法的示例包括 PoS(权益共识) 和 DPoS(代议制权益共识) 算法。
其中,PoS 算法中节点通过赢得选举或拥有足够的代币数量来获得对区块链的共识控制权;而 DPoS 算法中,节点可以通过提交提案并获得足够的支持来获得对区块链的共识控制权。
这两种算法都具有优点和缺点,可以根据具体情况选择。
dbn原理

dbn原理
DBN(Deep Belief Network,深度信念网络)是一种深度学习模型,由多个堆叠的受限玻尔兹曼机(Restricted Boltzmann Machines,RBM)组成。
DBN的原理涉及到概率图模型、无监督学习和逐层贪婪训练等概念。
以下是DBN的基本原理:
1.概率图模型:DBN是一种概率图模型,用于建模变量之间的概率关系。
它的基本组成部分是RBM,是一种能量模型,用于描述变量之间的概率分布。
2.受限玻尔兹曼机(RBM):RBM是概率图模型中的一种,具有两层神经元,分别是可见层和隐藏层。
RBMs之间的连接是双向的,但层内神经元之间没有连接。
RBMs用于学习数据的分布,并提取数据中的特征。
3.逐层贪婪训练:DBN的训练过程采用逐层贪婪训练的策略。
首先,每一层的RBM在无监督方式下逐层地进行训练,学习输入数据的分布和特征。
然后,将前一层RBM的隐藏层作为后一层RBM的可见层,层层堆叠形成DBN。
4.深度表示学习:由于DBN的层层堆叠,它可以学习数据的层次化表示。
底层表示捕捉原始数据的基本特征,而高层表示捕捉更抽象和复杂的特征。
这使得DBN在处理复杂数据和进行特征学习方面具有优势。
5.有监督微调:在无监督训练之后,可以通过有监督微调的方式使用反向传播算法进一步调整网络,以适应特定的任务,如分类或回归。
总体而言,DBN的原理结合了概率图模型和深度学习的思想,通过逐层贪婪训练学习数据的层次化表示,使其在处理复杂数据和进行特征学习方面表现出色。
电信英文缩写
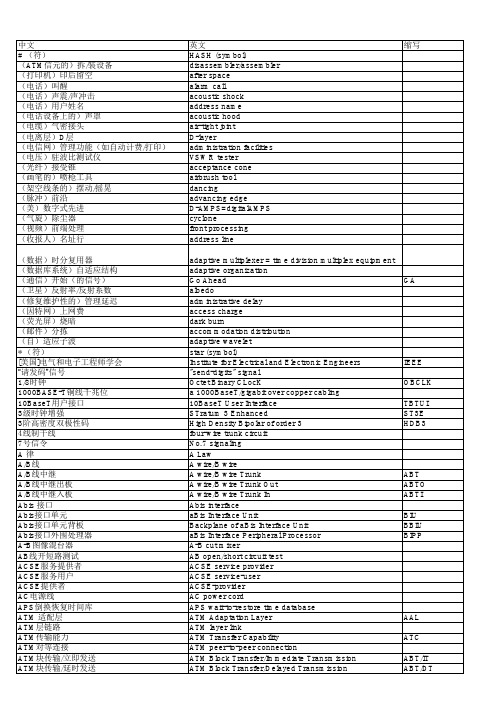
AAL CP-AAL SSP-AAL APON AU-AIS
AIU BATC AIPP
BCH code
BTSM VoDSL LAPD E&M EMT
EMVM EMUI G/T
GAZPACHO GSN GSM PLMN EDGE
IETF IC Phone IPX ISP IANA IMAP IN-SM
英文 HASH (symbol) disassembler/assembler after space alarm call acoustic shock address name acoustic hood air-tight joint D-layer administration facilities VSWR tester acceptance cone airbrush tool dancing advancing edge D-AMPS=digitalAMPS cyclone front processing address line adaptive multiplexer = time division multiplex equipment adaptive organization Go Ahead albedo administrative delay access charge dark burn accommodation distribution adaptive wavelet star (symbol) Institute for Electrical and Electronic Engineers "send-digits" signal Octet Binary CLocK a 1000BaseT/gigabit over copper cabling 10BaseT User Interface STratum 3 Enhanced High Density Bipolar of order 3 four-wire trunk circuit No.7 signaling A Law A wire/B wire A wire/B wire Trunk A wire/B wire Trunk Out A wire/B wire Trunk In Abis interface aBis Interface Unit Backplane of aBis Interface Unit aBis Interface Peripheral Processor A-B cut mixer AB open/short circuit test ACSE service provider ACSE service-user ACSE-provider AC power cord APS wait-to-restore time database ATM Adaptation Layer ATM layer link ATM Transfer Capability ATM peer-to-peer connection ATM Block Transfer/Immediate Transmission ATM Block Transfer/Delayed Transmission
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
GSM0710中文版
杭州波导软件有限公司
3.4. 过程和状态..................................................................................................................... 20 3.4.1. 建立 DLC 链路 ........................................................................................ 20 3.4.2. 释放 DLC 链路 ........................................................................................ 20 3.4.3. 信息传输 .................................................................................................. 21 3.4.4. 帧变量...................................................................................................... 21 3.4.5. 超时的考虑 .............................................................................................. 22 3.4.6. 多路控制通道 .......................................................................................... 22 3.4.6.1. 控制消息格式........................................................................................... 22 3.4.6.2. 控制消息类型参数 ................................................................................... 23 3.4.7. 电源控制与唤醒机制 .............................................................................. 32 3.4.8. 流控.......................................................................................................... 32 3.5. 集成层 Convergence Layer ............................................................................................ 34 3.5.1. 类型 1-未结构化的字节流...................................................................... 34 3.5.2. 类型 2-带参数的未结构化的字节流...................................................... 34 3.5.3. 类型 3-不可中断的帧数据...................................................................... 36 3.5.4. 类型 4-可中断的帧数据.......................................................................... 36 3.6. DLCI 值 ........................................................................................................................... 37 3.7. 系统参数......................................................................................................................... 37 3.7.1. 确认时间 T1 ............................................................................................ 37 3.7.2. 帧的最大长度 N1 .................................................................................... 38 3.7.3. 最大重发次数 N2 .................................................................................... 38 3.7.4. 窗口大小 k ............................................................................................... 38 3.7.5. 控制通道的响应时间 T2 ........................................................................ 38 3.7.6. 唤醒流程的响应时间 T3 ........................................................................ 38 3.8. 启动和关闭 MUX .......................................................................................................... 38 4. Error Recovery Mode ................................................................................................................. 39
GBFT:一种实用拜占庭容错算法改进方案

GBFT:一种实用拜占庭容错算法改进方案
李彬;张新有
【期刊名称】《计算机与数字工程》
【年(卷),期】2024(52)1
【摘要】区块链技术近年来成为研究热点,在金融、物流等行业已经有联盟链的落地案例。
共识算法作为区块链的核心技术,将对区块链的整体性能产生直接影响。
应用于联盟链的实用拜占庭容错算法(Practical Byzantine Fault Tolerance,PBFT)仍然存在着交易确认时间长、吞吐量低等问题。
面向联盟链应用场景,基于PBFT 算法,引入了非拜占庭容错协议,结合基于节点行为的选举机制,提出了三级共识机制的PBFT:GBFT。
最后从吞吐量、交易确认时延、容错性等方面对GBFT方案和原始PBFT算法进行了对比实验与分析。
实验结果表明,GBFT保持了PBFT算法1/3的容错性,有效提高了吞吐量,降低了交易确认时延。
【总页数】7页(P87-93)
【作者】李彬;张新有
【作者单位】西南交通大学信息科学与技术学院
【正文语种】中文
【中图分类】TP301
【相关文献】
1.一种区块链实用拜占庭容错算法的改进
2.一种基于积分制的改进实用拜占庭容错算法
3.一种改进的实用拜占庭容错算法
4.一种改进的实用拜占庭容错共识算法
5.一种改进的实用拜占庭容错算法
因版权原因,仅展示原文概要,查看原文内容请购买。
最新五年级语文下册-太阳-1课件-教科版教学讲义PPT

别和优化方法
eDonkey vs FTP
分组到达间隔时间,分组大小 模拟结果表明,在进行了6层小波包分解后,在1、3、6
层两种协议的差别非常显著。
Cont.
太阳能路灯
:“时间到了,小朋友。再 见吧,谢谢你们对我的关爱, 好好爱护你们的地球家园吧, 让它成为一个真正美丽可爱 的世界!”
P2P流量识别问题初探
周骏 2007.5.26
内容提要
研究背景 研究现状 分析与探讨 小结
研究背景
与传统的分布式系统相比,P2P技术的分布 化程度、可扩展性、健壮性、性价比、负载 均衡能力等都表现得更加优秀,客观来说比 较适合现有网络结构,因此,P2P应用在近 年来得到了迅猛的发展。
采用机器学习技术,使用预先分类好的样本数 据对分类器进行训练后,可以用于应用特征字 的自动提取
是一种新的思路,但该方法还不够成熟
基于行为特征的启发式识别
综合利用流的属性、统计特性以及流的行为特征, 按照启发式规则对流进行分析,达到对P2P流量分 类和识别的目的。
优点是:不依赖于流的应用层报文内容,用于分析的测 度及其导出指标容易获取,因此便于工程实现和应用。
话,没有太阳,就没有我们这个 美丽可爱的世界。
我国的太阳能利用起步于二十世纪七十年代,主 要是光热、光电转换方面的利用。在光热转换方面, 全国拥有太阳灶十几万台,居世界第一位,转换器 的性能和使用效果居发展中国家前列。热水器超过 了150万平方米,被动式太阳房已建成上千幢。在光 电转换方面,近年来主攻方向是研制各种太阳能电
基于应用协议特征字的识别
优点在于识别的准确率高、可在线处理 缺点在于
multilayernetwork 使用 和 训练

multilayernetwork 使用和训练
多层网络是一种深度学习模型,由多个节点层组成,各层之间通过连接权重进行信息传递。
每个节点接收上一层的输出并通过激活函数进行非线性转换后输出到下一层。
多层网络可以用于各种任务,如图像分类、自然语言处理等。
使用多层网络可以通过以下步骤:
1. 定义网络结构:确定网络的层数和每层的节点数。
选择适当的激活函数以及其他超参数。
2. 初始化参数:对网络的连接权重和偏置进行初始化,可以使用随机初始化方法。
3. 前向传播:将输入数据输入到网络中,通过多层的计算得到输出值。
4. 计算损失:将网络的输出与实际的标签进行比较,计算损失函数的值。
5. 反向传播:根据损失函数的值,计算每个参数对损失的梯度,并根据梯度更新参数。
6. 重复步骤3至5,直到达到停止条件或训练次数。
训练多层网络可以使用梯度下降算法或其变种进行优化。
常用的优化算法包括随机梯度下降(SGD)、动量法、Adam等。
在训练过程中,可以使用批量训练或小批量训练的方式进行参数更新。
为了提高多层网络的泛化能力,还可以采用一些正则化技术,如L1、L2正则化、dropout等。
此外,还可以使用交叉验证、
早停法等技术进行模型选择和调优。
训练多层网络可能需要大量的计算资源和时间,特别是在深层网络中。
因此,通常使用图形处理器(GPU)进行并行计算来加速训练过程。
区块链核心技术拜占庭共识算法之PBFT

区块链核心技术拜占庭共识算法之PBFT 拜占庭共识算法(Practical Byzantine Fault Tolerance,简称PBFT)是一种用于保障分布式系统中节点一致性的共识算法。
它是拜占庭容错(Byzantine Fault Tolerant,简称BFT)算法家族的一员,与其他BFT算法相比,PBFT具有高度的性能和可伸缩性。
PBFT算法最早由美国计算机科学家Miguel Castro和Barbara Liskov在1999年提出,并在2002年发表了与该算法相关的论文。
PBFT算法的核心思想是通过节点间互相通信来达成一致性决策。
具体而言,当系统中的一些节点提出一个事务请求(例如:生成一个新的区块)时,其他节点会对该请求进行验证和执行,并通过消息交换的方式达成一致。
PBFT算法的过程主要包括以下几个步骤:1.客户端发送请求:系统中的客户端向所有节点发送一个请求消息,请求执行一些具体的操作(例如:新增一个区块)。
2.节点验证请求:收到请求的节点首先要验证该请求的合法性,包括检查签名、检查请求序号等。
如果请求通过验证,则节点将该请求添加到自己的请求池中准备执行。
3. 预备阶段(Pre-prepare):节点根据请求池中的请求,选择一个请求作为本轮共识的议题,并将该请求发送给其他所有节点。
4. 准备阶段(Prepare):其他节点收到预准备消息后,对该消息进行验证,并将验证通过的消息添加到自己的预准备消息池中。
当一个节点收到2f+1个不同节点的相同预准备消息时,即意味着该消息已经收到足够多的支持。
6.客户端响应:当节点达成一致后,它们会向客户端发送一个响应消息,告知请求的结果。
PBFT算法的一大优势是具有良好的可扩展性。
节点之间的消息交换数量是n*(n-1),而不是所有节点之间都要进行交互,这大大提高了算法的性能。
然而,PBFT算法也存在一些局限性。
首先,节点之间的消息传输需要进行广播,这会引入一定的延迟。
lostgan 通俗讲解 -回复

lostgan 通俗讲解-回复什么是GANGAN,又称生成对抗网络(Generative Adversarial Networks),是一种深度学习网络的架构,其核心思想是通过让两个网络相互博弈来提高生成网络的生成能力。
GAN的结构GAN包括两个主要的网络,一个生成网络(Generator)和一个判别网络(Discriminator)。
生成网络的任务是生成与真实数据相似的数据样本,而判别网络的任务是判断给定的样本是真实数据还是生成网络生成的数据。
生成网络生成样本的过程是从一个隐空间中的随机向量(潜在向量)中提取特征,然后通过网络层将这些特征转换为生成样本。
判别网络的输入则是真实数据样本或者生成网络生成的数据样本,通过神经网络提取特征,并判断输入样本的真实性。
GAN的训练过程GAN的训练过程可以分为以下几个步骤:1. 初始化生成网络和判别网络的权重和参数。
2. 生成网络根据随机输入生成一批数据样本。
3. 判别网络根据生成网络生成的数据样本和真实数据样本进行分类判断。
4. 根据判别网络的输出结果,计算并调整生成网络和判别网络的损失函数。
5. 重复步骤2-4,优化网络的权重和参数,直到网络收敛或达到预定的训练轮次。
GAN的优势和应用GAN有几个明显的优势:1. 生成样本的多样性:生成网络可以生成与真实样本相似的样本,但又不完全一样,从而创造出更多样化的数据。
2. 可扩展性和泛化能力:GAN可以学习并生成多种不同类型的数据,具有很强的泛化能力,适用于各种任务和领域,如图像生成、音乐合成等。
3. 无监督学习:GAN在训练时不需要标注的真实样本标签,只需要生成和判别两个网络进行相互博弈,因此可以在大量无标签数据上进行无监督学习。
GAN在许多领域得到广泛应用,例如:1. 图像生成:GAN可以通过学习现有图像数据,生成与之相似但又不完全相同的图像,可用于图像合成、艺术创作等。
2. 视频生成:GAN可以生成连续帧图像,并通过生成一系列图像来合成自然流畅的视频。
堆叠自动编码器的深度信念网络解析(十)

深度信念网络(DBN)是一种基于深度学习的神经网络模型,它的核心思想是通过多层次的特征提取和抽象来学习数据的表示。
而堆叠自动编码器(SAE)则是DBN中常用的一种结构,它通过逐层的训练来逐步学习数据的抽象表示。
本文将对堆叠自动编码器的深度信念网络进行解析,从原理到应用进行全面探讨。
首先,我们来了解一下自动编码器(AE)的基本原理。
自动编码器是一种无监督学习的神经网络模型,它的目标是学习输入数据的有效表示。
自动编码器的结构包括编码器和解码器两部分,编码器将输入数据映射到隐藏层的表示,而解码器则将隐藏层的表示映射回原始数据空间。
通过最小化重构误差,自动编码器能够学习到数据的潜在结构,从而实现对数据的降维和特征提取。
而堆叠自动编码器则是通过将多个自动编码器堆叠在一起构成深度网络,从而实现对数据更加复杂的表示学习。
在堆叠自动编码器中,每个自动编码器的隐藏层都作为下一个自动编码器的输入层,通过逐层地训练,模型能够学习到数据的层次化特征表示。
这种逐层的训练方式可以有效地缓解深度学习中的梯度消失和梯度爆炸问题,同时也能够提高模型对数据的表征能力。
在实际应用中,堆叠自动编码器的深度信念网络被广泛应用于各种领域。
在图像识别领域,深度信念网络能够通过学习到的层次化特征表示来实现对图像的分类和识别。
在自然语言处理领域,深度信念网络能够学习到词向量的表示,从而提高文本分类和情感分析的性能。
此外,深度信念网络还被应用于推荐系统、信号处理、生物信息学等多个领域,取得了良好的效果。
然而,深度信念网络也面临一些挑战和限制。
首先,深度信念网络的训练过程相对复杂,需要大量的数据和计算资源。
其次,深度信念网络的模型解释性相对较弱,难以解释模型学习到的特征表示。
此外,深度信念网络在处理非结构化数据和小样本数据上的效果有限,需要更多的改进和优化。
针对深度信念网络的挑战和限制,研究者们也在不断探索和改进。
例如,通过引入正则化、Dropout、批归一化等方法来提高模型的稳定性和泛化能力;通过引入注意力机制、迁移学习等方法来提高模型的解释性和泛化能力;通过引入生成对抗网络、变分自编码器等方法来提高模型对非结构化数据和小样本数据的处理能力。
网络工程毕业外文翻译英文

WIRELESS LANIn just the past few years, wireless LANs have come to occupy a significant niche in the local area network market. Increasingly, organizations are finding that wireless LANs are an indispensable adjunct to traditional wired LANs, as they satisfy requirements for mobility, relocation, ad hoc networking, and coverage of locationsdifficult to wire. As the name suggests, a wireless LAN is one that makes use of a wireless transmission medium. Until relatively recently, wireless LANs were little used; the reasons for this included high prices, low data rates, occupational safety concerns, and licensing requirements. As these problems have been addressed, the popularity of wireless LANs has grown rapidly.In this section, we first look at the requirements for and advantages of wireless LANs, and then preview the key approaches to wireless LAN implementation. Wireless LANs ApplicationsThere are four application areas for wireless LANs: LAN extension, crossbuilding interconnect, nomadic access, and ad hoc networks. Let us consider each of these in turn.LAN ExtensionEarly wireless LAN products, introduced in the late 1980s, were marketed as substitutes for traditional wired LANs. A wireless LAN saves the cost of the installation of LAN cabling and eases the task of relocation and other modifications to network structure. However, this motivation for wireless LANs was overtaken by events. First, as awareness of the need for LAN became greater, architects designed new buildings to include extensive prewiring for data applications. Second, with advances in data transmission technology, there has been an increasing reliance on twisted pair cabling for LANs and, in particular, Category 3 unshielded twisted pair. Most older building are already wired with an abundance of Category 3 cable. Thus, the use of a wireless LAN to replace wired LANs has not happened to any great extent.However, in a number of environments, there is a role for the wireless LAN as analternative to a wired LAN. Examples include buildings with large open areas, such as manufacturing plants, stock exchange trading floors, and warehouses; historical buildings with insufficient twisted pair and in which drilling holes for new wiring is prohibited; and small offices where installation and maintenance of wired LANs is not economical. In all of these cases, a wireless LAN provides an effective and more attractive alternative. In most of these cases, an organization will also have a wired LAN to support servers and some stationary workstations. For example, a manufacturing facility typically has an office area that is separate from the factory floor but which must be linked to it for networking purposes. Therefore, typically, a wireless LAN will be linked into a wired LAN on the same premises. Thus, this application area is referred to as LAN extension.Cross-Building InterconnectAnother use of wireless LAN technology is to connect LANs in nearby buildings, be they wired or wireless LANs. In this case, a point-to-point wireless link is used between two buildings. The devices so connected are typically bridges or routers. This single point-to-point link is not a LAN per se, but it is usual to include this application under the heading of wireless LAN.Nomadic AccessNomadic access provides a wireless link between a LAN hub and a mobile data terminal equipped with an antenna, such as a laptop computer or notepad computer. One example of the utility of such a connection is to enable an employee returning from a trip to transfer data from a personal portable computer to a server in the office. Nomadic access is also useful in an extended environment such as a campus or a business operating out of a cluster of buildings. In both of these cases, users may move around with their portable computers and may wish access to the servers on a wired LAN from various locations.Ad Hoc NetworkingAn ad hoc network is a peer-to-peer network (no centralized server) set up temporarily to meet some immediate need. For example, a group of employees, each with a laptop or palmtop computer, may convene in a conference room for a businessor classroom meeting. The employees link their computers in a temporary network just for the duration of the meeting.Wireless LAN RequirementsA wireless LAN must meet the same sort of requirements typical of any LAN, including high capacity, ability to cover short distances, full connectivity among attached stations, and broadcast capability. In addition, there are a number of requirements specific to the wireless LAN environment. The following are among the most important requirements for wireless LANs:Throughput. The medium access control protocol should make as efficient use as possible of the wireless medium to maximize capacity.Number of nodes. Wireless LANs may need to support hundreds of nodes across multiple cells.Connection to backbone LAN. In most cases, interconnection with stations on a wired backbone LAN is required. For infrastructure wireless LANs, this is easily accomplished through the use of control modules that connect to both types of LANs. There may also need to be accommodation for mobile users and ad hoc wireless networks.Service area. A typical coverage area for a wireless LAN may be up to a 300 to 1000 foot diameter.Battery power consumption. Mobile workers use battery-powered workstations that need to have a long battery life when used with wireless adapters. This suggests that a MAC protocol that requires mobile nodes to constantlymonitor access points or to engage in frequent handshakes with a base stationis inappropriate.Transmission robustness and security. Unless properly designed, a wireless LAN may be interference-prone and easily eavesdropped upon. The design of a wireless LAN must permit reliable transmission even in a noisy environment and should provide some level of security from eavesdropping.Collocated network operation. As wireless LANs become more popular, it is quite likely for two of them to operate in the same area or in some area where interference between the LANs is possible. Such interference may thwart the normal operation of aMAC algorithm and may allow unauthorized access to a particular LAN.License-free operation. Users would prefer to buy and operate wireless LAN products without having to secure a license for the frequency band used by the LAN. HandoWroaming. The MAC protocol used in the wireless LAN should enable mobile stations to move from one cell to another.Dynamic configuration. The MAC addressing and network management aspects of the LAN should permit dynamic and automated addition, deletion, and relocation of end systems without disruption to other users.Physical Medium SpecificationThree physical media are defined in the current 802.11 standard:Infrared at 1 Mbps and 2 Mbps operating at a wavelength between 850 and 950 nm. Direct-sequence spread spectrum operating in the 2.4-GHz ISM band. Up to 7 channels, each with a data rate of 1 Mbps or 2 Mbps, can be used.Frequency-hopping spread spectrum operating in the 2.4-GHz ISM band. The details of this option are for further study.Wireless LAN TechnologyWireless LANs are generally categorized according to the transmission techniquethat is used. All current wireless LAN products fall into one of the following categories:Infrared (IR) LANs. An individual cell of an IR LAN is limited to a single room, as infrared light does not penetrate opaque walls.Spread Spectrum LANs. This type of LAN makes use of spread spectrum transmission technology. In most cases, these LANs operate in the ISM (Industrial, Scientific, and Medical) bands, so that no FCC licensing is required for their use in the U.S.Narrowband Microwave. These LANs operate at microwave frequencies but do not use spread spectrum. Some of these products operate at frequencies that require FCC licensing, while others use one of the unlicensed ISM bands.A set of wireless LAN standards has been developed by the IEEE 802.11 committee. The terminology and some of the specific features of 802.11 are unique tothis standard and are not reflected in all commercial products. However, it is useful to be familiar with the standard as its features are representative of required wireless LAN capabilities.The smallest building block of a wireless LAN is a basic service set (BSS), which consists of some number of stations executing the same MAC protocol and competing for access to the same shared medium. A basic service set may be isolated, or it may connect to a backbone distribution system through an access point. The access point functions as a bridge. The MAC protocol may be fully distributed or controlled by a central coordination function housed in the access point. The basic service set generally corresponds to what is referred to as a cell in the literature. An extended service set (ESS) consists of two or more basic service sets interconnected by a distribution system. Typically, the distribution system is a wired backbone LAN. The extended service set appears as a single logical LAN to the logical link control (LLC) level. The standard defines three types of stations, based on mobility:No-transition. A station of this type is either stationary or moves only within the direct communication range of the communicating stations of a single BSS.BSS-transition. This is defined as a station movement from one BSS to another BSS within the same ESS. In this case, delivery of data to the station requires that the addressing capability be able to recognize the new location of the station.ESS-transition. This is defined as a station movement from a BSS in one ESS to a BSS within another ESS. This case is supported only in the sense that the station can move. Maintenance of upper-layer connections supported by 802.11 cannot be guaranteed. In fact, disruption of service is likely to occur. details of this option are for further study.The 802.11 working group considered two types of proposals for a MAC algorithm: distributed-access protocols which, like CSMAICD, distributed the decision to transmit over all the nodes using a carrier-sense mechanism; and centralized access protocols, which involve regulation of transmission by a centralized decision maker. A distributed access protocol makes sense of an ad hoc network of peer workstations and may also be attractive in other wireless LANconfigurations that consist primarily of bursty traffic. A centralized access protocol is natural for configurations in which a number of wireless stations are interconnected with each other and with some sort of base station that attaches to a backbone wired LAN; it is especially useful if some of the data is time-sensitive or high priority.The end result of the 802.11 is a MAC algorithm called DFWMAC (distributed foundation wireless MAC) that provides a distributed access-control mechanism with an optional centralized control built on top of that. Figure 13.20 illustrates the architecture. The lower sublayer of the MAC layer is the distributed coordination function (DCF). DCF uses a contention algorithm to provide access to all traffic. Ordinary asynchronous traffic directly uses DCF. The point coordination function (PCF) is a centralized MAC algorithm used to provide contention-free service. PCF is built on top of DCF and exploits features of DCF to assure access for its users. Let us consider these two sublayers in turn.Distributed Coordination FunctionThe DCF sublayer makes use of a simple CSMA algorithm. If a station has a MAC frame to transmit, it listens to the medium. If the medium is idle, the station may transmit; otherwise, the station must wait until the current transmission is complete before transmitting. The DCF does not include a collision-detection function (i.e., CSMAICD) because collision detection is not practical on a wireless network. The dynamic range of the signals on the medium is very large, so that a transmitting station cannot effectively distinguish incoming weak signals from noise and the effects of its own transmission. To ensure the smooth and fair functioning of this algorithm, DCF includes a set of delays that amounts to a priority scheme. Let us start by considering a singledelay known as an interframe space (IFS). In fact, there are three different IFS values, but the algorithm is best explained by initially ignoring this detail. Using an IFS, the rules for CSMA access are as follows:I. A station with a frame to transmit senses the medium. If the medium is idle, the station waits to see if the medium remains idle for a time equal to IFS, and, if this is so, the station may immediately transmit.2. If the medium is busy (either because the station initially finds the medium busy or because the medium becomes busy during the IFS idle time), the station defers transmission and continues to monitor the medium until the current transmission is over.3. Once the current transmission is over, the station delays another IFS. If the medium remains idle for this period, then the station backs off using a binary exponential backoff scheme and again senses the medium. If the medium is still idle, the station may transmit.Point Coordination FunctionPCF is an alternative access method implemented on top of the DCF. The operation consists of polling with the centralized polling master (point coordinator). The point coordinator makes use of PIFS when issuing polls. Because PIFS is smaller than DIFS, the point coordinator can seize the medium and lock out all asynchronous traffic while it issues polls and receives responses.As an extreme, consider the following possible scenario. A wireless network is configured so that a number of stations with time-sensitive traffic are controlled by the point coordinator while remaining traffic, using CSMA, contends for access.The point coordinator could issue polls in a round-robin fashion to all stations configured for polling. When a poll is issued, the polled station may respond using SIFS. If the point coordinator receives a response, it issues another poll using PIFS. If no response is received during the expected turnaround time, the coordinator issues a poll. If the discipline of the preceding paragraph were implemented, the point coordinator would lock out all asynchronous traffic by repeatedly issuing polls. To prevent this situation, an interval known as the superframe is defined. During the first part of this interval, the point coordinator issues polls in a round-robin fashion to all stations configured for polling. The point coordinator then idles for the remainder of the superframe, allowing a contention period for asynchronous access.At the beginning of a superframe, the point coordinator may optionally seize control and issue polls fora give period of time. This interval varies because of the variable frame size issued by responding stations. The remainder of the superframe isavailable for contention-based access. At the end of the superframe interval, the point coordinator contends for access to the medium using PIFS. If the medium is idle, the point coordinator gains immediate access, and a full superframe period follows. However, the medium may be busy at the end of a superframe. In this case, the point coordinator must wait until the medium is idle to gain access; this results in a foreshortened superframe period for the next cycle.。
堆叠did思路

堆叠did思路全文共四篇示例,供读者参考第一篇示例:“堆叠did思路”是由一群研究人员提出的一种新颖的深度学习架构,其特点是通过堆叠多个差分输入和差分输出层来构建深度神经网络。
与传统的神经网络架构相比,“堆叠did思路”具有更强的表达能力和更好的适应性,能够更好地处理复杂的自然语言处理任务。
在“堆叠did思路”中,每个差分输入层和差分输出层都由多个神经元组成,每个神经元都连接前一层的所有神经元。
在训练过程中,首先对输入文本进行预处理,将其转换成向量表示,然后将向量输入到第一个差分输入层。
差分输入层对输入进行变换和特征抽取,然后将特征传递给下一个差分输入层。
通过多个差分输入层的堆叠,神经网络可以逐层提取文本的高层次特征,从而更好地实现对文本的理解和处理。
而差分输出层则用于将神经网络学习到的特征映射到相应的标签空间,完成分类或回归任务。
通过堆叠多个差分输入和差分输出层,神经网络可以学习到更复杂的规律和模式,从而提高自然语言处理任务的准确性和效果。
与传统的神经网络架构相比,“堆叠did思路”具有以下几个优点:通过堆叠多个差分输入和差分输出层,神经网络可以学习到更复杂的特征和规律,从而提高对文本的理解和处理能力。
差分输入和差分输出层的堆叠结构可以有效地防止梯度消失和梯度爆炸问题,使得神经网络更容易训练和优化。
“堆叠did思路”还可以更好地处理长文本和复杂结构的文本,具有更强的泛化能力。
在实际应用中,“堆叠did思路”已经被成功应用于多个自然语言处理任务,取得了显著的效果。
在情感分类任务中,“堆叠did思路”可以学习到更具有判别性的特征,提高了情感分类的准确性和效果。
在机器翻译任务中,“堆叠did思路”可以更好地捕捉输入文本与输出文本之间的依赖关系,提高了翻译的质量和流畅度。
第二篇示例:现如今,人们的生活节奏越来越快,社会的竞争压力也越来越大,如何高效地处理工作和生活中的琐事成为了人们急需解决的问题。
在这种情况下,一种名为“堆叠did思路”的方法应运而生,成为了一种备受推崇的高效工作法则。
graphsage 训练流程

graphsage 训练流程
GraphSAGE是一种用于节点分类和链接预测的图神经网络模型。
它的训练流程主要包括图构建、采样邻居节点、节点特征聚合和训练四个步骤。
在进行GraphSAGE训练之前,需要构建一个图结构。
图由节点和边组成,节点代表实体或对象,边代表节点之间的关系。
节点可以是用户、商品、文章等,边可以表示用户之间的关注、商品之间的相似性等。
接下来,为了训练模型,需要从图中采样邻居节点。
采样的目的是为了获取每个节点的邻居节点,以便进行特征聚合。
常用的采样方法有随机采样、有偏采样等。
采样的邻居节点数量可以根据问题的复杂度和计算资源进行调整。
然后,在节点采样的基础上,进行节点特征聚合。
节点特征聚合是指将每个节点的特征与其邻居节点的特征进行融合,得到一个新的表示。
这个过程可以使用图卷积神经网络(GCN)或者GraphSAGE自身提出的聚合算法。
使用聚合后的节点特征进行模型训练。
训练过程中,可以使用交叉熵损失函数进行节点分类,也可以使用二分类损失函数进行链接预测。
通过反向传播算法,不断优化模型参数,使得模型能够更好地适应节点分类或链接预测任务。
总结一下,GraphSAGE的训练流程包括图构建、采样邻居节点、节点特征聚合和模型训练四个步骤。
通过这个流程,GraphSAGE 能够学习到节点之间的关系,并根据这些关系进行节点分类和链接预测。
GraphSAGE在社交网络分析、推荐系统等领域有着广泛的应用前景,可以帮助我们更好地理解和利用图数据。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Cross-layer Networking for Peer Databases over Wireless Ad-Hoc CommunitiesEvangelos Papapetrou,Efthymia Rova,Apostolos Zarras and Panos VassiliadisDepartment of Computer Science{epap,efirova,zarras,pvassil}@cs.uoi.grUniversity of Ioannina,Dourouti Campus45110,Ioannina,GreeceAbstract—Recent advances in wireless technology as well as in electronics industry have given rise to the widespread of wireless ad-hoc networking.Expanding data-centric applications to wireless ad-hoc networks has become a hot work functions must be carefully designed to meet the application requirements and at the same time economize on the limited resources of wireless environments.In this context,there is a growing consensus among scientists on the necessity of cross-layer protocol design.In this paper we propose a new routing and transport mechanism for wireless ad-hoc networks that incorporates application layer specifics in order to support both traditional and data-centric communications and at the same time optimizes the management of scarce network resources.The proposed methodology is evaluated through extended simulations and is proved suitable for wireless mobile environments.I.I NTRODUCTIONOver the last years,the scientific community has witnessed a significant rise of data-centric networking applications.This type of applications introduced a new communication para-digm.Instead of communicating one-to-one based on their identity,users generally communicate in groups depending on the data they possess and need to exchange at that time. Take for example p2pfile sharing applications[1].Users communicate spontaneously depending on their content.The communication can be considered to consist of two phases.In thefirst phase a node has to communicate simultaneously with multiple other nodes in order to discover a node possessing the desired data.Then in the second phase a classical com-munication between the two nodes takes place.As a second example,the CarTel project at MIT[2]aims at providing a data management system for querying data collected over large communities of sensor-enabled cars.The queries that can be posed concern the position,speed and other sensor data of the involved cars.Since road and highways do not offer continuous connectivity,each time a car has access to ”islands of connectivity”the interesting data are relayed via the Internet.On the contrary,in traditional applications routing of data does not depend on the application protocol but it is rather determined by the addresses of the communicating nodes.Since data-centric communication depends on the applica-tion layer,the key for providing such communication services is to incorporate application layer specifics into networking functions.However,this is not possible in existing network infrastructure since its development has neglected application layer dependencies so far.For example,the routing services re-quired by a p2pfile sharing application(for example routing of queries)cannot be performed by existing networking technolo-gies.So far,the approach taken in order to overcome the lack offlexibility in existent infrastructures was the introduction of overlays mostly in wired[1]but also in wireless networks [3].According to this approach,data-centric communication services are implemented on the application layer by means of the overlay network.Then,traditional networking services are used to support the construction of the overlay network. However,this approach has received considerable skepticism [4]regarding the use of network resources.Although overlays are attractive for networks that can not be upgraded,such as the Internet,this is not the case for wireless ad-hoc networks.Moreover,in this case the prob-lem of limited network resources is more critical,rendering the use of overlays questionable.Recently,many researchers have focused on the implementation of efficient data-centric routing protocols in wireless ad-hoc networks.Most of the reported research concerns p2pfile and/or resource sharing applications.In this scenario,resources are available in the ers produce lookups in order to locate one node that possess the requested resource/data.Several solutions have been proposed for efficiently routing lookup messages in wireless mobile ad-hoc networks[5].Furthermore,in the same context,scientists have proposed ancillary procedures for the dissemination and replication of resources[6],[5]. Another example of data-centric communication comes from sensor networks.Several routing protocols have been proposed to efficiently route data towards a specific network node[7]. Application layer functions such as data fusion and data aggregation are introduced at the network layer in order to optimize the overall system operation.Although significant work has been already performed,there is still openfield for research.This is because the design of data-aware routing protocols is strongly related to the charac-teristics of the application to which the network has to provide its services.In this paper we are concerned with the cross-layer design of a routing protocol suitable for supporting the operation of a peer database application over a wireless mobile ad-hoc network.Recently there is an increased interest for such applications especially in wireless mobile environments[1].Although the communication scenario within such an appli-cation shares similarities with other data-centric applications,at the same time significant differences call for the design of customized networking procedures.Those differences will be analyzed in Section II where the problem is described in detail and the proposed solution is delineated.The remainder of the paper is organized as follows.Section III presents the description of the simulation model used for the assessment of the proposed protocol.Then,in section IV simulation results are presented and discussed,while conclusion remarks are drawn in section V.II.P ROPOSED C ROSS -L AYER D ESIGNA.Problem DescriptionAs mentioned in the previous paragraph,our motivation stems from distributed databases and the communication ser-vices required to support their operation over a wireless mobile ad-hoc network.The basic scenario that we consider in our work is as follows.Mobile users,which roam in an area,carry information that is organized in a local ers are organized in groups,which are called classes .All peers of the same class support the same interface (i.e.,provide the same type of data or services)to the peer network.Therefore,once a peer’s class is known,its is straightforward for other peers to pose queries to it.In order to understand the notion of class,we provide an example.Suppose that a wireless network is set up to a ers on cars,pedestrians or even users on buildings constitute different classes and their databases are organized in a manner relevant to their identity.For example,it is reasonable to assume that all cars carry information about their brand while that information does not exist in the databases of pedestrian users.An example network is depicted in fig.1.In a network like the onedescribed,Fig.1:An example network with three classes of nodes mobile users are allowed to perform queries toward other users in order to retrieve information.Depending on the type of the desired information,a query may be relevant to a specific class of users,to more than one classes,or it can even be global,that is to address all network nodes independent of their class.Furthermore,mobile users have to be capable of limiting the range of their query.After receiving a query,a user constructs a reply message based on its local database and routes this message back to the originator of the query.In the described scenario,the network has to provide users with specific services:•Routing of queries .This is the most important service and its main objective is to deliver a query to the appropriate recipients.•Delivery of reply messages .Aims at delivering the reply messages produced by a query to the originator of that query.As far as routing of queries is concerned it must be stated that although it bears similarities to the routing of lookups in p2p systems,there are also important differences that affect the network operation.The most important is that,instead of locating a user that possess the requested data,in our case the network has to deliver the query to as many as possible nodes within a specific class,so that as much information as possible is collected.A different kind of query involves querying all peers within a certain network distance (number of hops).Furthermore,techniques such as data dissemination and replication do not significantly affect the overall setting since they can take place only to a limited extent,in the sense that every peer carries its personal data that are probably highly volatile and time variant (e.g.,a car’s speed,a pedestrian’s position,etc).B.Technical requirements and challengesIt is well understood that traditional routing protocols for wireless ad-hoc networks cannot provide the communication services described previously in an efficient manner.The main issue consists in developing a mechanism for routing queries.A solution based on traditional routing protocols would be to unicast the query to each of the network nodes,leading to the waste of valuable bandwidth.Another more elaborate solution would be to use multicast routing protocols [8].However,the implementation of such a scenario would require the construction of a multicast tree based on the classes of nodes that the query refers to.This is translated to different multicast trees for different queries.Bearing in mind the overhead involved in building and maintaining multicast trees,the inefficiency of the approach is clear.Finally,the most appealing approach is to use a flood-based technique in order to reach all possible query recipients.However,in this case,the incurred overhead is also considered significant.This is because all network nodes are involved in a transmission at least once,even if they are not appropriate recipients of the query.Consider the case in fig.1where node 1wishes to perform a query for discovering data related to class 2.All nodes in the network will receive at least one copy of the query.Our objective is to minimize the involved overhead by limiting the transmission of the query.To this end,we make the observation that we must capitalize on the information provided by the application layer such as the organization of nodes into classes.In other words,we must opt for a cross-layer design of the routing protocol.In our previous example,by exploiting class information we can limit the propagation of the query within the region indicated by the dashed line,which is the minimum connected tree including node 1and nodes 4and 8that belong to class 2.In this way we economizeon the consumption on bandwidth and at the same time we are able to retrieve information from all target nodes.As far as the delivery of reply messages is concerned it is clear that traditional one-to-one communication can be used. Therefore,the proposed scheme should be compatible with existent routing protocols.Another reason in favor of this design choice is that we do not aim at building a special purpose network.On the contrary,we wish to support the coexistence of data-centric applications such as a peer database with other types of applications.To summarize,we state that the basic objectives of our new method are:•the minimization of the cost involved in routing a query by means of interaction with the application layer •the compatibility and coexistence with traditional routing protocolsC.The proposed solutionAs mentioned in the previous subsection one of our key objectives is the compatibility with existing routing protocols. Therefore,we are not interested in building a new routing protocol rather than propose generally applicable modifica-tions so that the described functionality is incorporated into existing routing protocols.We must make clear at this point that the proposed solution aims at proactive routing protocols due to the nature of the application.Keep in mind that when a node performs a query,data must be collected by as many as possible network nodes.The only way to achieve this without performing a network-wide search is to use a proactive routing protocol.Our proposed method consists of two steps:1)Introduction of Application Layer Specifics:In order to be able to make decisions based on application information at the networking layer,we must devise an efficient mechanism for making available this information(the class that a node belongs to)to the routing protocol so that we can make routing decisions.To do this we introduce the id of the node’s class to the routing updates sent by this node.Furthermore,each node receiving such updates from other nodes should store class information to the entry of its routing table that is related to the node that sent the update.In this way,each node becomes aware of the class that every other node in the network belongs to.The proposed procedure incurs some overhead due to the propagation of extra information in the network.However, this information is rather small(only a couple of bytes). Furthermore,bear in mind that the information regarding the class of a node is in most casesfixed.Therefore its propagation in the network by means of update messages is limited.Finally, we should point out that the proposed procedure does not depend on the routing protocol that is implemented.2)Query Forwarding:The cornerstone for implementing an efficient query routing mechanism is to make forwarding decisions for query messages based on the application layer information,already incorporated into the routing tables.In our approach when a node produces a query it forwards it to its network layer.To avoidflooding the routing protocol uses its routing table in order to determine the nodes thatbelongFig.2:Example of query forwardingto the class/classes that the query refers to.To understand the procedure consider the example depicted infig.2where node1issues a query towards nodes in class1.By consulting its routing table,node1can decide that the query should be forwarded towards nodes5,6and7.After determining the target nodes,the originator of the query constructs a header of the structure depicted infig.3.To construct thisheaderFig.3:Structure of query headerthe node groups the target nodes according to the next hop used to reach them.The next hop nodes that are used to reach a target node are called forwarding nodes and are stored in the headerfields F W1,F W2,....Each forwarding node is followed by a set of target nodes1which are the target nodes that can be reached through this forwarding node.In our example nodes5and7are grouped under node3and node 6under node4.Nodes3and4are the forwarding nodes. The header also contains the size of the list of forwarding nodes infield F L size and onefield per forwarding node (RT1size,RT2size,...)that contains the size of the list of target nodes for the specific forwarding node.Finally,the header contains the address of the node originating the query (QN Addr).After its construction the header is appended to the query message and the new packet is broadcasted in the network. Each node that receives the packet forwards it to its application layer.Furthermore,it checks if its address appears in the list of forwarding nodes.If this not the case the node drops the packet.However,if the node is a forwarding node then it constructs a new header by following the procedure described 1The forwarding node may be a target node as well.However,as it will be made clear later,its address does not need to be included in this set.before and using as target nodes only the nodes included in its target list.To make this clear,consider again the example offig.2.In this example,node3is a forwarding node.When receiving the query from node1,it constructs a new header following the same procedure as node1and using as targets only the nodes5and7(node6is responsibility of node4). The described procedure ends when a node that receives the query discovers that its list of target nodes is empty.The result of the proposed procedure is to minimize the number of transmissions within the network since the retrans-mission of query packets is strictly controlled.Consider again the example offig.2.The total number of transmissions used to deliver the query to all recipients is three(each transmission is depicted with a different line style).In the case that aflood-based method is used,the total number of transmissions for the same example is at least nine.The disadvantage of the method is that it relies on the accuracy of the routing protocol used to deliver queries.However,this is a tradeoff that we are willing to pay in order to save resources and to achieve the compatibility with traditional routing protocols.III.S IMULATION F RAMEWORKThe experiments conducted in this work aim at evaluat-ing the performance of the proposed cross-layer method for routing queries.For this purpose,we compare the proposed approach to the traditional approach which is to deliver queries by means offlooding.To the best of the authors’knowledge there is no other method suitable for the specific problem. The simulations were conducted using the MANET simulation environment existing within Ns2[9]after performing appro-priate modifications.In both cases the routing protocol that is used as the base protocol was the well-known DSDV[10]. It is clear from the previous discussion that the choice of the protocol affects the two methodologies in the same way as far as data delivery is concerned.Furthermore,as far as routing of queries is concerned,the routing protocol can only affect the performance of the proposed cross-layer method in terms of accuracy in delivering queries.However,the main purpose of this work is to prove the efficiency of the proposed method in terms of bandwidth consumption.A.Simulation ModelAs a simulation model we used a network consisting of a number of nodes(N)that roam in a rectangle area.For the simulation of node movement we used the well-known Random Waypoint Algorithm.Nodes are randomly organized into C cnt classes of equal size.A number Q(Q<N)of nodes performs queries using an exponential distribution with mean rateλ.Queries are propagated to a maximum number of hops(H max).Each node chooses uniformly the class to which it addresses its queries.Finally,each node receiving a query replies with a packet of1000bytes in size.The values used for the simulation parameters are summarized in table I.Unless stated,these values are valid throughout all experiments.Finally,it should be noted that the results that will be presented are obtained as average values over15TABLE I:Simulation parametersNumber of nodes(N)50Region Size1500x300Node mobility20m/secNode Range(R)250mNumber of Classes(C cnt)5Number of querying nodes(Q)10Query generation rate(λ)0.1query/secMaximum number of hops(H max)3Simulation Time900secindependent simulation runs.That number of runs provided 99%confidence intervals of±4%in the worst case.B.Evaluation metricsFor the evaluation of the proposed method we use three different metrics:a)query overhead,i.e.,the mean number of query packets involved in the routing of a single query,b) mean number of replies,i.e.,the mean number of data packets received as replies to a single query and c)delivery ratio,i.e., the percentage of packets containing data(replies)that was delivered to the node performing the query.Thefirst metric evaluates the efficient use of system resources and provides an indication of the method scalability.The second metric is an indication of the method’s ability to collect the appropriate information from peer nodes.Finally,the third metric is used to show the impact of resource consumption to the overall system operation.IV.P ERFORMANCE R ESULTSIn order to evaluate the proposed technique we conducted three different experiments.Each one aims at exploring the impact of different system parameters to the system perfor-mance.A.Variable User MobilityIn thisfirst experiment we vary the speed at which nodes are moving.The purpose of this experiment is to evaluate the system performance under various levels of mobility that affect the network connectivity.Infig.4a the overhead involved in the routing of one query is depicted for both the proposed and the competitor approach.Results prove the effectiveness of the proposed method.In fact the transmissions are reduced to approximately20%of those taking place whenflooding is used.The induced overhead is practically the same over the entire mobility range.Although this is expected forflooding, for the cross-layer approach this is a very useful feature because it shows that query forwarding is not affected by link failures.The reduced overhead in the case of the cross-layer approach has an effect on the overall system performance as illustrated infig.4c.Because the network is more congested when theflood-based approach is used,the delay in data delivery is higher.This has an increased effect in the range of high mobility where link failures become more frequent.On the contrary,the cross-layer technique manages a smoother network operation.Finally,infig.4b the mean number of replies per query is presented.As expected,both methodolo-gies are affected when mobility raises due to the increasedFig.4:Variable usermobilityFig.5:Variable number ofclassesFig.6:Queries limited in terms of maximum number of hopslevel of link failures.An interesting result is that the proposed method manages to deliver queries to less nodes as a result of the increased failure rate of the routing protocol.This is the price paid for minimizing the overall overhead.However,it is interesting that the differences between the cross-layer and theflood-based approach are small.B.The Impact of ClassesIn this experiment we vary the number of the classes into which network nodes are organized.The purpose of this ex-periment is to directly capture the impact of using application layer information.Fig.5a presents the query overhead with re-spect to the number of classes.Again the cross-layer approach achieves significantly less overhead.As actually expected,the performance of theflood-based method does not change as the number of classes increases,since it always asks all the peers of the network.Contrary to the constant performance of theflood-based method,the cross-layer approach improves its performance when the number of classes increases.This is due to the fact,that the proposed method takes advantage of class information and tries to reach only the peers of the requested class/classes.As the number of classes increases,the numberof such peers drops.It is worth noticing that even when only one class exists,i.e.,the query concerns every node in the network,the proposed method manages a reduction of67%. At the same time,the ability of the proposed method to deliver queries and therefore collect data is practically the same as in theflood-based case.This is illustrated infig.5b where the mean number of replies is presented.It is clear that the reduction of replies with the increase of classes is attributed to the smaller number of nodes belonging to each class(the total number of nodes isfixed to50).Fig.5c presents the delivery ratio for data in the system.When the number of classes increases the delivery ration increases for both approaches as a result of the reduced overhead which is confirmed byfig.5a. Again,the proposed method manages significantly improved performance with respect to theflood-based approach.Observe that the benefits gained by the increase in the number of classes increase in the proposed approach,whereas theflood-based practically remains stable.C.Performing Limited QueriesIn this last experiment,queries are limited within a certain network distance(number of hops).The objective of this experiment is to emphasize on the efficient query forwarding of the cross-layer method and provide indications regarding its ability to scale.Infig.6a the query overhead is depicted with respect to the number of maximum hops that a query packet is allowed to travel.The performance improvement of the proposed method in terms of query overhead becomes greater as the number of maximum hops increases.The interesting observation is that the proposed method presents an almost stable performance as opposed to its competitor that presents a practically linear behavior.The latter effect is typically anticipated,since,in theflood-based method,the larger the part of the network explored,the larger the number of messages exchanged.On the contrary,our proposed method limits the number of exchanged messages,since it restricts the number of contacted peers by exploiting the application-level, class information.This is a clear indication that the proposed method presents good scalability.As far as the mean number of replies is concerned(fig.6b),the cross-layer method presents a negative discrepancy from theflood-based method which increases slowly with the maximum number of hops.This is anticipated because in high mobility environments,nodes that are located far from the querying node are harder to reach due to frequent link failures.The increase in both measures is explained due to the fact that we explore a larger part of the network.Finally,infig.6c we depict the delivery ratio of the two methods.The difference in their performance is a result of the increased overhead induced in the case of theflood-based method which creates increased levels of network congestion. Furthermore,the decreasing tendency in both methods is due to the fact that data replies are originated from nodes that are far in the network and therefore,the possibility of dropping packets increases as the length of the resulting paths increases too.V.C ONCLUSIONSIn this paper we have proposed a new routing and transport mechanism for wireless ad-hoc networks that incorporates ap-plication layer specifics in order to support both traditional and data-centric communications and at the same time optimizes the management of scarce network resources.The proposed method has been evaluated through extended simulations for its query overhead,mean number of replies and delivery ratio and outperforms its competitorflood-based method.Specifi-cally,our method produces significantly lower query overhead than its competitor,achieving4to5times better performance in several cases.This is very important for the ability of the proposed method to scale and for the overall operation of the network.The delivery ratio is improved in our method,and supports the latter argument too.In terms of the mean number of replies,the effectiveness of the proposed method is quite close to the one of the exhaustive,flood-based method,without significant losses.VI.A CKNOWLEDGEMENTThis research was co-funded by the European Union in the framework of the program”Pythagoras I”of the”Operational Program for Education and Initial V ocational Training”of the 3rd Community Support Framework of the Hellenic Ministry of Education,funded by25%from national sources and by 75%from the European Social Fund(ESF).R EFERENCES[1]S.Androutsellis-Theotokis and D.Spinellis,“A survey of peer-to-peercontent distribution technologies.”ACM Comput.Surv.,vol.36,no.4, pp.335–371,2004.[2]V.Bychkovsky,K.Chen,M.Goraczko,H.Hu,B.Hull,A.Miu,E.Shih,Y.Zhang,H.Balakrishnan,and S.Madden,“Data management in the cartel mobile sensor computing system.”in SIGMOD Conference,2006, pp.730–732.[3]H.Pucha,S.Das,and Y.Hu,“Ekta:An efficient dht substrate fordistributed applications in mobile ad hoc networks,”in In Proc.of the 6th IEEE Workshop on Mobile Computing Systems and Applications (WMCSA2004).,2004.[4]M.Waldvogel and R.Rinaldi,“Efficient topology-aware overlay net-work,”SIGCOMM mun.Rev.,vol.33,no.1,pp.101–106, 2003.[5] D.Chakraborty,A.Joshi,and Y.Yesha,“Integrating service discoverywith routing and session management for ad-hoc networks.”Ad Hoc Networks,vol.4,no.2,pp.204–224,2006.[6] A.Datta,S.Quarteroni,and K.Aberer,“Autonomous gossiping:A self-organizing epidemic algorithm for selective information dissemination in wireless mobile ad-hoc networks.”in ICSNW,2004,pp.126–143.[7]K.Akkaya and M.F.Younis,“A survey on routing protocols for wirelesssensor networks.”Ad Hoc Networks,vol.3,no.3,pp.325–349,2005.[8]J.Jetcheva and D. B.Johnson,“Adaptive demand-driven multicastrouting in multi-hop wireless ad hoc networks.”in MobiHoc,2001,pp.33–44.[9]K.Fall and K.Varadhan,“The ns manual,”VINT Project,Univ.California,Berkeley,CA,2001.[Online].Available: /nsnam/ns/ns-documentation.html[10] C.E.Perkins and P.Bhagwat,“Highly dynamic destination-sequenceddistance-vector routing(dsdv)for mobile computers.”in SIGCOMM, 1994,pp.234–244.。
