释锐CAS实战4.0
神舟链威C4000手持终端用户手册说明书

SHENZHEN CHAINWAY INFORMATION TECHNOLOGY CO., LTDC4000 Handheld TerminalUser Manual1ContentsStatement (4)1.Getting Started (6)1.1 Brief Instruction (6)1.2Precaution before Using Battery (7)2.About The Device (8)2.1 Structure (8)2.2 SD Card Installation (10)2.3 SIM Card Installation (11)2.4 Battery Installation (12)2.5 Battery Charging (13)2.5.1 Direct Charging (13)2.5.2 Cradle Charging (13)2.6 Device Power on/off (13)3.Call Function (14)3.1 Phone (14)3.2 Contacts (15)3.3 Messaging (16)4. Barcode Reader (17)4.1 1D Barcode (17)4.2 2D Barcode (18)4.3 2D(S) Barcode (19)5.RFID Reader (20)5.1 Low Frequency (20)25.2 High Frequency (22)5.2.1 14443A (22)5.2.215693 (23)5.3 Ultra High Frequency (24)6.Fingerprint Reader (26)7.Other Functions (27)7.1 PING (27)7.2Bluetooth (28)7.3 GPS (30)7.4 Volume Settings (31)7.5 Sensor (32)7.6 Keyboard (33)7.7 Network (34)7.8 Keyboardemulator (35)8. Device Specifications (36)3Statement2013 by Shenzhen Chainway Information Technology Co., Limited. All rights reserved.No part of this publication may be reproduced or used in any form, or by any electrical or mechanical means, without permission written from Shenzhen Chainway. This includes electronic or mechanical means, such as photocopying, recording, or information storage and retrieval systems. The material in this manual is subject to change without notice.The software is provided strictly on an “as is” basis. All software, including firmware, furnished to the user is on a licensed basis. Shenzhen Chainway grants to the user a non-transferable and non-exclusive license to use each software or firmware program delivered hereunder (licensed program). Except as noted below, such license may not be assigned, sublicensed, or otherwise transferred by the user without prior written consent of Shenzhen Chainway. No right to copy a licensed program in whole or in part is granted, except as permitted under copyright law. The user shall not modify, merge, or incorporate any form or portion of a licensed program with other program material, create a derivative work from a licensed program, or use a licensed program in a network without written permission from Shenzhen Chainway.Shenzhen Chainway reserves the right to make changes to any software or product to improve reliability, function, or design.Shenzhen Chainway does not assume any product liability arising out of, or in connection with, the application or use of any product, circuit, or application described herein.No license is granted, either expressly or by implication, estoppel, or otherwise under any Shenzhen Chainway intellectual property rights. An implied license only exists for equipment, circuits, and subsystems contained in Shenzhen Chainway products.Shenzhen Chainway Information Technology Co., LtdAddress: 9/F, Building 2, Phase 2, Gaoxinqi Industrial Park, Liuxian 1st Rd, District 67, Bao’an, Shenzhen, Guangdong, ChinaTelephone:+0086-755-23223300 Fax: +0086-755-23223310Web Site: Email:*******************451. G etting Started1.1 Brief InstructionChainway C4000 is a series of Android powered smart terminals, with data capture, data processing, wireless communication. It is with high-reliability &high-expansibility. Auto & Accurate data collection is achieved in various business fields via a complete solution of premium options, the flexible solution among options and operators is suited-up. You will find out with C4000, much easier deployment, reduced complexity, decreased maintenance, are the benefits for enterprises.C4000 meets industrial level IP64 (IEC sealing), is sufficient to routine applications, eg, railway inspection, road parking toll, vehicle inspection, logistics express, power inspection, warehousing management, chain retail, etc. Whether the mobile operators are working indoor or outdoor, with Chainway C4000, your business is always &highly efficient on-line.Meeting industrial standards, designed to support a various of mobile solutions. With the build-in high performance Cortex-A7 1.3GHZ quad core processor technology, the operators need only one device to enjoy a convenient and easy job, C4000 will be the ideal choice for key-fact business in mobile solutions, for simplified task flow, enhanced work efficiency, for shortened time to customer response, more satisfied customer care service.Chainway C4000 comes with world wide band WCDMA technology. Multi channels data and voice communication guarantees the real-time communication and data efficiency, C4000 brings you the best ROI.61.2 Precaution before Using Battery•Do not leave batteries unused for extended periods of time, either in the product or in storage. When the battery has been unused for 6 months, check the charge status and charge or dispose of the battery as appropriate. •The typical estimated life of a Lithium-Ion battery is about two to three years or 300 to 500 charge cycles, whichever occurs first. One charge cycle is a period of use from fully charged, to fully discharged, and fully recharged again. Use a two to three year life expectancy for batteries that do not run through complete charge cycles.•Rechargeable Lithium-Ion batteries have a limited life and will gradually lose their capacity to hold a charge. This loss of capacity (aging) is irreversible. As the battery loses capacity, the length of time it will power the product (run time) decreases.•Lithium-Ion batteries continue to slowly discharge (self-discharge) when not in use or while in storage. Routinely check the battery’s charge status. The user manual typically includes information on how to check battery status, as well as battery charging instructions.•Observe and note the run time that a new fully-charged battery provides for powering your product. Use the new battery run time as a basis to compare run times for older batteries. The run time of your battery will vary depending on the product’s configuration and the applications that you run. •Routinely check the battery’s charge status. Carefully monitor batteries that are approaching the end of their estimated life.Consider replacing the battery with a new one if you note either of thefollowing conditions:The battery run time drops below about 80% of the original run time.•The battery charge time increases significantly.•If a battery is stored or otherwise unused for an extended period, be sure to follow the storage instructions in this document. If you do not follow theinstructions, and the battery has no charge remaining when you check it,consider it to be damaged. Do not attempt to recharge it or to use it. Replace it with a new battery.•Always follow the charging instructions provided with your product. Refer to your product’s user manual and/or online help for detailed information about charging its battery.•Charge or discharge the battery to approximately 50% of capacity before storage. Charge the battery to approximately 50% of capacity at least once every six months.•Remove the battery and store it separately from the product.•Store the battery at temperatures between 5 °C and 20 °C (41 °F and 68 °F).72. A bout The Device2.1 Structure<Front>89<Back>Buttons:ButtonFunctionPower ButtonPress and hold to turn the device on or off App List View Button View a list of apps running Home ButtonPress to return to the home screen Cancel ButtonTap to return to the previous screenDetailed installation steps are as follows:•Open the SIM slot as the direction of ‘Open/Lock’ labeled.•Open the SD slot as the direction of ‘Open/Lock’ labeled.•Install the SD card properly.•Lock the SD slot and SIM slot properly.101. Open the SIM slot as the direction of ‘Open/Lock’ labeled.2. Install the SIM card correctly.3. Lock the SIM slot properly.2 3112.4 Battery Installation1. Push the battery down into the bottom of the battery.2. Push the battery to the direction of the array.3. Turn the battery lock.122.5 Battery Charging2.5.1 Direct ChargingUse the adapter to charge the battery via the USB connector of the snap-on. 2.5.2 Cradle ChargingConnect the adapter with the power cable to charge the device.2.6 Device Power on/offPress the ‘Power’ button on the side shortly due to turn on/off.13143. C all Function3.1 Phone1. Click this icon.2. Click the number button to input the numbers.3. Click the button to confirm and dial.4. Click theto end the calling.Contacts LogsVoice CallingEmulated Numeric Keypad3.2 Contacts1. Click ‘Contacts’ to open the contacts list.2. Click ‘’ to add the new contact.3. Click ‘’ to import/export or delete the contact list.FavoritesContact List Group153.3 Messaging1. Click ‘’ to open the message list.2. Click ‘’ to input the content.3. Click ‘’ to send the message.4. Click ‘’ to add photos, videos.164. Barcode Reader4.1 1D Barcode1. Open the 1D Barcode Demo in Appcenter.2. Press the ‘Scan’ button to start scanning, then the auto interval parameterscan also be set.174.2 2D Barcode1. Open the 2D Barcode Demo in Appcenter.2. Press the ‘Scan’ button to start scanning, then the auto interval parameterscan also be set.184.3 2D(S) Barcode1. Open the 2D(S) Barcode Demo in Appcenter.2. Press the ‘Scan’ button to start scanning, then the auto interval parameterscan also be set.3. Also, the barcode types enabling/disabling can also be set.Note: Please scan the barcode in a correct way, otherwise the scanningmight be failed.19205. R FID Reader5.1 Low Frequency1. Open the RFID_LF Demo within Appcenter and then press the ‘Scan’ button tostart reading.2. Tag types including ID Card/Animal Tag/Hitag/HDX Tag/EM4450 can be alsoselected, and Hitag-S and EM4305 reading/writing are already supported by the device.Please ensure that the LF module is embedded in the device, also please select the tag type correctly, otherwise the operation might not work. Meanwhile, please pay attention to the HDX and FDX-B since they are using different hardware due to the different working principles.215.2 High Frequency5.2.1 14443A1. Open the 14443A demo within Appcenter, and press the ‘Scan’ button to startreading.2. Mifare and Ultra Light reading/writing are also supported.225.2.2 156931. Open the RFID_15693 demo within Appcenter, and press the ‘Scan’ button tostart scanning.2. 15693 writing are also supported.235.3 Ultra High Frequency1. Open the UHF demo within Appcenter, and press the ‘Start’ button to startscanning.2. Multiple tags reading and single tag reading/writing are also supported.2425266. F ingerprint Reader1. Open the Fingerprint Demo in Appcenter.2. Put the finger to the fingerprint module and set the ID/name of the templateunder ‘ACQUISITION’.3. Put the finger to the fingerprint module properly and identify by ID/Name/Scoreunder ‘IDENTIFICATION’.4. The local templates can also be checked under ‘Data’.Please be aware that ISO standards are only supported by devices with ISO fingerprint hardware modules.7. O ther Functions7.1 PING1. Open the Ping in Appcenter.2. Set the Ping parameters and select the internal/external addresses.277.2 Bluetooth1. Open the Bluetooth demo in Appcenter and turn on the Bluetooth.2. Input the content or select the file, then scan the nearby Bluetooth printer andpair them.3. Select the printer and click ‘Print’ to print the content.2829307.3 GPS1. Open the GPS demo in Appcenter and turn on GPS module.2. Set the GPS parameters and get the GPS data information.7.4 Volume Settings1. Open the Volume Setting demo in Appcenter.2. Set the volumes based on the requirements.317.5 Sensor1. Open the Sensor demo in Appcenter.2. Test the sensor based on the requirements.321. Open the Keyboard demo in Handset Appcenter.2. Set and test the key values of the device.331. Open the Network demo in Appcenter.2. Test the WIFI/Mobile signal based on the requirements.34357.8 KeyboardemulatorKeyboard Emulator can be used directly for multiple using environments and the output formats can include prefix/suffix/enter/tap can also be defined, please define the options properly based on the features of the device.1. Open the Keyboardemulator which is preinstalled in the device.2. Click the options correctly based on the features of the device hardware,please also press the physical button to define the scan button, then please define the output formats based on the requirements, finally click ‘Open’ to save and enable it.8. Device SpecificationsPhysical CharacteristicsDimensions 153mm*75mm*29mm/6.02*2.95*1.14in.Weight 286g/10.09oz. (includes main battery)Screen 4in.WVGA (480*800) TFT-LCD, capacitive dual touchKeyboard 3 function keys, 3 side buttonsBattery Main bat. (rechargeable li-ion polymer, 3.7V, 3200 mAh)Pistol bat. (rechargeable li-ion polymer, 3.7V, 5200 mAh)Expansion Slot MicroSD/TF, maximum capacity of 32GSIM Slot 1 PSAM, 1 SIM, 1 MicroSDAudio 0.5WCamera OV 8M pixels, auto focus with LED flashPerformance CharacteristicsCPU Cortex-A7 1.3GHz quad coreOS Android 4.4.2Memory 1GB RAM, Build-in 4GB FlashInterface USB Micro-B, serial port RS-232(TTL)Storage Card Type MicroSD cardMaximum Expansion Storage 32GBUser Environmental CharacteristicsOperating Temperature -10℃to 50℃Storage Temperature -40℃to 70℃Humidity 5%RH-95%RH(non-condensing)Dropping Survive 1.2m/3.9ft. drop, 6 sides (concrete floor under operating temp.)Sealing IP64, IEC complianceWireless CommunicationWAN WCDMA/HSDPA/HSPA+ (850/1900/2100MHz)GSM/GPRS/EDGE (850/900/1800/1900MHz)WLAN IEEE802.11b/g/n, internal antenna36WPAN Bluetooth v4.0 Low EnergyBluetooth 3.0+HSBluetooth v4.0 Low Energy (LE)Data CollectionBarcode Scan Engine 1D barcode(Symbol SE955, laser)(optional)2D CMOS laser scanner: Symbol SE4750(optional) Sensor resolution: 750 * 480Roll tolerance: 360ºRFID LF 125KHz/134.2KHz, HDX/FDX-B(optional)HF 13.56MHz, ISO14443A/ISO15693(optional)UHF 860-960MHz, EPC C1 GEN2/ISO18000-6C(optional) Developing EnvironmentSDK Chainway SDKProgramming Language JavaDeveloping Tool Eclipse37。
ZeroTech 三角瞄准镜系列说明书

ZEROTECH RIFLESCOPESINTRODUCTIONLIFETIME WARRANTYSCOPE FEATURESSETTING THE DIOPTREMOUNTING YOUR SCOPEADJUSTING PARALLAXZEROING YOUR RIFLELOCKING WINDAGE & ELEVATION TURRETS ZEROING THE WINDAGE TURRET THRIVE & THRIVE HD MODELS ILLUMINATION FEATURE LENS COVER & TURRET MULTI-TOOL SCOPE CARE RETICLES WARRANTY INFORMATION4 5 6 8 10 12 14 17 21 2325 2731 32 34PAGESWELCOME TO THE ZEROTECH RIFLESCOPE FAMILY!Customer First - We listened to you and came up with a family of riflescopes that will satisfy the needs of our most discerning and experienced customers.Backed by Experience - ZeroTech enjoys 55 years of experience in the Optics Market supplying high quality brands to retailers throughout Australia and the Asia Pacific.Built for the Australian Shooter - Designed and built to endure the harsh conditions of the Australian bush and the exacting demands of the precision shooter.Lifetime Warranty - Be safe in the knowledge that your scope is backed by our Triple A Lifetime Warranty: ‘ANY OWNER, ANY PROBLEM, ALWAYS COVERED’Bespoke Reticles - Practical reticles for the everyday shooter. Helping you putrounds on target!BACKED FOR LIFE!Be safe in the knowledge that your scope isbacked by our Triple A Lifetime Warranty:- F ully transferable, covers accidental damage aswell as defects in materials and workmanship.- N o receipt or warranty card is required.- W e will repair or replace product with equal orsimilar value and/or specifications.- We will return product to you at no charge.‘ANY OWNER, ANY PROBLEM,ALWAYS COVERED’ZEROTECH - INSTRUCTION MANUAL Zerotech_Int_Thrive/Thrive HD/Trace_V3_March_2021Locking Elevation Turret Locking Windage TurretMagnification Power Change Ring(side focus)Dioptre Adjuster Half Magnification Indicator (HMI) – Second Focal Plane (SFP) models only30mm MaintubeTRACE & TRACE ADVANCED FEATURESWindage Turret Cap Elevation Turret Half Magnification Indicator (HMI)Change Ring (side focus)Push Button Reticle Illumination (on illuminated models only)OcularDioptre AdjusterFlip up HD THRIVE & THRIVE HD FEATURESSet your magnification to the maximum power.If fitted, set the parallax turret to the infinity marker.Find a blank, featureless and bright surface, such as a white wall or clear blue skyand look through your scope for no more than 5 seconds at a time.NEVER LOOK THROUGH YOUR SCOPE DIRECTLY AT THE SUN.1.2.3.4.When briefly looking through the scope, the reticle should appear sharp and clear immediately. If the reticle is not immediately sharp and clear, twist the dioptreadjuster to bring the reticle into sharp focus. The dioptre adjuster has approximately 1¾ turns of adjustment. We recommend starting with the dioptre assembly twisted flush up against the ocular and making adjustments in an anticlockwise (towards the + symbol marked on the ocular) direction until the optimal setting is reached.Once you are satisfied the base(s) is correctly fitted to the receiver of your firearm,proceed to fit the rings to the base(s) and ensure the ring clamps are tightened to the recommend torque settings as specified by the manufacturer.With the ring tops removed, place the scope in the ring bases and gently slide thescope back and fourth in the ring bases to ensure the scope slides freely. If the scope does not slide freely, lapping of the rings may be necessary to avoid damage 1.2.to the scope maintube. ZeroTech always recommends the use of high quality rings and bases to ensure the best possible fitting of your scope.Avoid mounting the scope with the rings contacting the junction of the maintube/erectorhousing, magnification ring/maintube junction or the objective/maintube junction.It is essential to confirm that no part of the scope is contacting the barrel or receiverwhen the scope is mounted in the rings.Once you have confirmed the fit of the scope in the ring bases, fit the ring tops andtighten the ring top bolts to between 22 – 25 in lbs or 2.5 – 2.8NM.ZeroTech highly recommends the use of a scope level (bubble level) fitted to therings or the scope maintube to ensure the reticle can consistently be aligned with the fall of gravity every time a shot is fired. This is particularly important for precision shooting applications.*If your level mounts to the maintube of the scope, follow the same guidelines as observed for scope ring fitting to ensure the level does not damage the maintube of your scope.3.4.5.6.If your ZeroTech scope is fitted with a parallax turret, it is important to adjust the parallax turret for shots taken at different distances. Some shooters refer to the parallax turret as the ‘side focus’. It is referred to as the ‘side focus’ because by turning the turret, it will bring your target image into focus. As a general rule and as long as your dioptre is set correctly (refer to page 8 – ‘Setting the Dioptre’) the sharper the target image is focused, the parallax error will be less.Parallax error is quite easy to detect when following the instructions below;Acquire your target image at any distance and make sure your rifle is well supportedby the use of a bipod and rear bag (or similar).Use the parallax turret to obtain the sharpest/ clearest possible target image andestablish a refined point of aim on the target.Once you have established a refined point of aim and a sharp target image, move 1.2.your head gently up and down whilst looking through the scope. Be sure not to disturb the rifle/ sights.If you are able to observe the reticle departing slightly from the intended point of aim, make small adjustments on the parallax turret until the reticle remains fixed on your point of aim.You will need to repeat this process when shooting at different distances or in different environmental conditions. The distance markings on the parallax turret are intended asa guide only. Dioptre settings and environmental factors are likely to cause the distance markings to vary in relation to the actual distance of the target.Adjust the parallax turret to bring the target image into focus4.5.6.ZEROTECH - INSTRUCTION MANUALZEROING DISTANCESCentrefire rifles: Zerotech recommends zeroing most centrefire rifles at approximately 100 metres +/- 10 metres. 100 metres enables the shooter to overcome any offset problems caused by the centre height of the scope above bore but is not too far as to accidentally build in an error due to unobserved environmental conditions such as wind. Rimfire rifles: Most commonly, rimfire hunting rifles are zeroed at 50 – 75 metres depending on the type of ammunition being used. Rimfire target rifles may have different zeroing requirements depending on purpose.We always recommend that you zero your rifle in the same manner as you typically shoot your rifle. For example, if you mainly shoot your rifle from a bench, zero your rifle by shooting from a bench. If you predominately shoot your rifle inBefore you fire your first shot, you should bore sight your rifle to ensure your scope and your barrel are both aligned at the intended point of impact on your target. To do this with a bolt action rifle, remove the bolt with the rifle securely supported (front and rear) and align the bore with the target.Without disturbing the rifle, carefully look through the scope and check that the reticle is also aligned with the same point as the bore on the target. If the reticle is not aligned, use the windage end elevation adjustments on your scope to adjust the reticle to the intended point of impact on the target.Once you are satisfied that the scope and the bore of your rifle are aligned to the same point on the target, fire a shot at the target and observe the point of impact (bullet hole). If required, use the windage and elevation turrets on your scope to adjust the bullet impact.ZEROING DISTANCES CONTINUED...Dialling the elevation turret in the direction of the ‘U’ symbol will adjust the bullet impact upwards on the target. Likewise, dialling the windage turret in the direction of the ‘R’ symbol will adjust the bullet impact to the right on the target.�If your scope turrets are indexed in ¼ Minutes of Angle (0.25 MOA), each ‘click’ of your scope turret will adjust you bullet impact approximately 7-8mm at 100 metres (approx. ¼” at 100 yards).�If your scope turrets are indexed in 0.1 Milrad (0.1 MRAD), each ‘click’ of your scope turret will adjust your bullet impact 1cm at 100 metres (0.36” at 100 yards).Once you have established a zero for your rifle, the zero stop feature can be set to ensure a consistent return to zero after dialling the elevation turret to compensate forSETTING THE ZERO STOPRemove the elevation turret byloosening the three (3) opposinggrub screws located in the top ofthe elevation turret with a 2mmhex key. Remove the elevationturret and set aside.points. Loosen each grub screw 4 to 5 revolutions witha 2mm hex key.SETTING THE ELEVATION ZERO STOP 1.With the elevation turret removed, the orange zero stop ring will be visible. Similar tothe elevation turret cap, the orange zero stop ring also has three (3) opposing grub screws. Use your 2mm hex key to loosen the grub screws 1 to 2 revolutions each. This will allow the orange zero stop ring to spin freely.Slide the orange zero stop ring downwards until it stops. During this process, it isimportant to note the small black lug located on side of the orange zero stop ring. There is also a lug located the top face of the lower assembly, directly underneath the orange zero stop ring. It is critical that the lug on the side of the orange zero stop ring is positioned on the right hand side of the lug on the lower assembly. Failure to follow this step will result in the elevation adjustment being locked out and unusable until the zero stop is reset. If this occurs, simply position the lug on the orange zero stop ring on the other side of the lug on the lower assembly.Tighten the three (3) 2mm grub screws in the orange zero stop ring. The zerostop is now set.2.3.4.The zero stop is now set. Tighten the three 2mm grub screws and replace the elevationturret indexed to the ‘0’ position.Note the position of the lugs asdescribed in step 3.SETTING THE ZERO STOP CONTINUED...Loosen the three 2mm grub screws inthe orange zero stopand slide the zerostop downwards untilit stops.1. 2. 3.Replace the elevation turret and make sure to align the ‘0’ on the elevation turret cap to the vertical marker on the lower turret assembly to enable an easy and precise reference when dialling the elevation turret. Tighten the three (3) 2mm grub screws to secure the turret cap. We recommend using the short end of your hex key to apply adequate torque to the grub 2mm grub screws.5.The windage turret can be reset to ‘0’ without completely removing the windageturret cap from the scope. It is important to note that the windage turret does not have a zero stop feature as the turret needs to be able to adjust the bullet impact both left and right equally at all times.With the windage turret in the unlocked position, loosen the three (3) 2mm grubscrews approximately ½ - 1 revolution each. This will allow the windage turret to spin freely.With the windage turret spinning freely, align the ‘0’ on the turret with the indexline on the lower turret assembly and tighten the three (3) 2mm grub screws, using the short end of your hex key for adequate leverage.1.2.3.ZEROING THE WINDAGE TURRET CONTINUED...ZEROTECH - INSTRUCTION MANUALRESETTING THE TURRETS AFTER ZEROINGAfter you have followed the mounting and zeroing instructions on pages 14 – 16, you are ready to reset the elevation and windage turrets to zero (‘0’).Holding the turret in place, use the ZT multi-tool to unscrew the turret keeper anticlockwise. Remove the keeper and the turret. (For more info on ZT multi-tool see page 27).Replace the turret with the reference set to ‘0’ (zero). Replace and tighten the keeper using the ZT multi-tool. It is not necessary to overtighten the keeper.1.Check your turret to make sure the ‘0’ on the turret is aligned with the index markon the turret bodyRepeat this process for the windage turret.Replace the turret caps to ensure your zero settings aren’t disturbed.Make sure the ‘0’ marker aligns withthe index marker on the turret body.2.3.4.RESETTING THE TURRETS AFTER ZEROING CONTINUED...Thrive HD models fitted with the push button illumination function have 6 settings (5 illumination settings + OFF setting).Before use, install the CR2032 battery by removing the illumination turret batterycover. Unscrew in an anticlockwise direction.Press the illumination control button once to illuminate the reticle. You can thentoggle between the brightness settings by quickly pressing the button.IMPORTANT - To turn the reticle illumination off, press and hold the button for 2 – 3seconds.Models fitted with the push button illumination have an auto shutdown feature.The reticle will automatically power-off after 3 hours to avoid excessive battery consumption.Our push button illumination has a memory function that resumes on the samebrightness setting the next time the illumination is activated.1.2.3.4.5.Unscrew battery cap anticlockwise.Insert battery and replace illuminationturret cap.ILLUMINATION FEATURE CONTINUED...Various size lens coveradjustment toolVarious size lens coveradjustment toolKeyring holeThrive Series Turret Tool(THRIVE HD AND TRACE MODELS)Zerotech Thrive HD and Trace models are fitted with HD Alloy Flip Up lens covers. The HD Alloy lens covers are removable and can be rotated to the preferred position of the shooter. For example, some shooters prefer their objective flip up cover to fold out to the side of the scope instead of folding to the top.It is likely that you will also need to adjust the position of the ocular flip up cover after you have obtained the correct dioptre setting (as described on page 8).To adjust the position of the flip up lens covers, follow the steps below:If you wish to completely remove the flip up lens covers, simply use the multi-tool to rotate the lens cover lock ring in an anticlockwise direction until the lens cover completely detaches from the scope.Select the end of the multi-tool that fits the slots in the lock ring of your lens cover Loosen the lens cover lock ring by twisting the multi-tool in an anticlockwise direction Rotate the lens cover to the desired positionTighten the lens cover lock ring but twisting the multi-tool in a clockwise direction 1.2.3.4.USING THE ZEROTECH MULTI-TOOL TO RESET THE ELEVATION AND WINDAGE TURRETS (THRIVE SERIES ONLY)Once you have zeroed your rifle at the desired distance, it is recommended that you reset your elevation and windage turrets back to ‘0’. This gives the shooter the ability to use the turrets to precisely dial elevation and windage onto the scope when shooting at distances other than the zero distance for the rifle.To reset the turrets on the Thrive and Thrive HD models, you will require the Zerotech multi tool (or a coin). Follow the steps below.Holding the turret firmly, insert the multi tool into the slot in the turret centre bolt andcompletely remove the centre bolt but twisting the multi tool in an anticlockwise direction. Once the centre bolt has been removed, simply lift the turret away from the scope. Refit the turret to the scope, making sure to align the ‘0’ marking on the turret withthe index line on the scope body.Hold the turret firmly and tighten the centre bolt back down by twisting the multi tool1.2.3.4.SECOND FOCAL PLANE RETICLESAvailable in;THRIVE HD 2.5-15x50THRIVE HD 2.5-15x50 Illum.THRIVE HD 6-24x50THRIVE HD 6-24x50 Illum. THRIVE HD 3-18x56 Illum.VENGEANCE 4-20x50PHR-IIAvailable in;THRIVE 3-9x40THRIVE 3-12x44PHR 3Available in;TRACE 3-18x50TRACE 4.5-27x50THRIVE HD 3-18x56VENGEANCE 4-20x50VENGEANCE 4-20x50 Illum.R3Available in;THRIVE 3-12x44THRIVE 4-16x50MildotAvailable in;THRIVE 3-9x40THRIVE 3-12x44THRIVE 4-16x50DuplexSECOND FOCAL PLANE RETICLESFor specific information on your reticle, refer to the reticle spec sheet provided in your scope box or visit .auTHRIVE HD - 6-24x50For specific information on your reticle, refer to the reticle spec sheet provided in yourscope box or visit .auWipe dust and debris from your scope body using a damp microfibre cleaning cloth.If necessary, clean dust and dirt from the scope lenses using a lens brush andthe ZeroTech lens cleaning cloth.Never spray cleaners or solvents on any part of your scope. Irreversible damagemay be caused by such products.Avoid touching the scope lenses. Wipe fingerprints off the scope lenses using theZeroTech lens cleaning cloth.1.2.3.4.Ph: +612 9938 3244Email: ******************.auPlease direct all enquiries to ********************.au Company details;ZEROTECH INTERNATIONAL PTY LTDAddress: PO BOX 6176, Frenchs Forest, NSW, 2086AUSTRALIA.au。
SIR4中文说明书中文图最终版 (1)

高频电源安装操作运行维护手册
目录
1. 概述 .................................................................................................................................................................. 9 1.1. 型 号 .................................................................................................................................................... 10 1.2. SIR: 静 电 除 尘 器 控 制 装 置 系 列 的 一 员 ....................................................................................... 10
4. 电气数据 ........................................................................................................................................................ 26 4.1. 概 述 .................................................................................................................................................... 26 4.2. 电 源 电 流 ........................................................................................................................................... 27 4.3. 要 求 的 电 缆 ....................................................................................................................................... 27
os-b101_2012-10 DNV海洋结构物设计规范 Metallic Materials 钢制材料规范

Main changes
• — — — Ch.2 Sec.1: Transverse impact values included in Table B4 and Table C5. Combinations of grain refining elements to be in line with Ship Rules Pt.2 Ch.2. Figure 3d to be in line with Ship Rules Pt.2 Ch.2.
A. A A A A A A
Introduction ........................................................................................................................................ 9
Offshore Standard DNV-OS-B101, October 2012 Changes – Page 3
CHANGES
General
This document supersedes DNV-OS-B101, April 2009. Text affected by the main changes in this edition is highlighted in red colour. However, if the changes involve a whole chapter, section or sub-section, normally only the title will be in red colour.
© Det Norske Veritas AS October 2012 Any comments may be sent by e-mail to rules@
电泳颗粒EDX分析结果
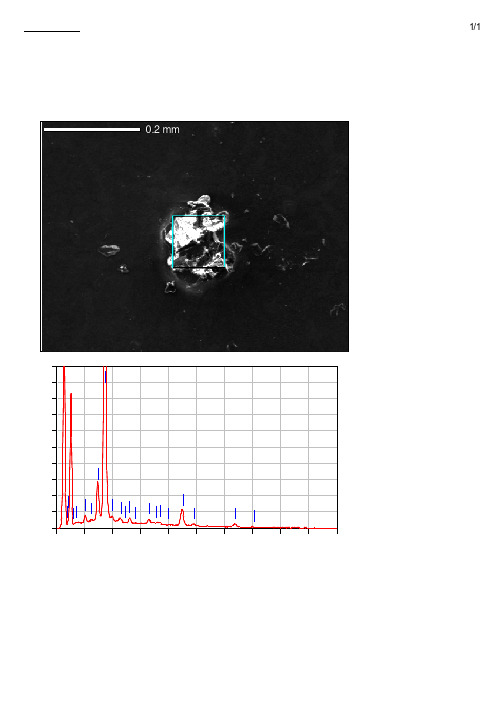
Fe Fe
0 0.00 1.00 2.00 3.00 4.00 5.00 6.00 7.00 8.00 9.00 10 .00 keV ZA |!f [š‘ÏR F lÕ g• 0Õ0£0Ã0Æ0£0ó0.718 0° OÂep : 4 QC} (ke) Œê Ï Š¤î %SŸ[P S T ri V ‘% ] ep % Œê Ï 0«0Á0ª ‘% 0ó ep Na K 1.041 0.35 1.91 0.50 Al K 1.486 11.44 1.66 14.01 Si K 1.739 50.81 1.97 59.79 P K 2.013 0.92 2.83 0.98 Ti K 4.508 31.79 5.40 21.94 Fe K 6.398 4.69 11.96 2.77 TŠ 10 00 0. 10 00 0.
批注本地保存成功开通会员云端永久保存去通
0Ö 0Ä•è0 No1
1/1
0.2 mm 0.2 mm
-------------------------0¿0¤0È0ë : IM1 G -------------------------ˆÅ•n : 606 A 0(L ) R • –ûW' : 15. 00kV P s‡ : x 20 0 n,[šeåfB : 200 02/ 26 9/ u;} ep : 512 38 x 4 --------------------------
CPS
50 40 30 20 10 Fe g Ti M a TiFeN
Fe Fe
0 0.00 1.00 2.00 3.00 4.00 5.00 6.00 7.00 8.00 9.00 10 .00 keV ZA |!f [š‘ÏR F lÕ g• 0Õ0£0Ã0Æ0£0ó0.796 0° OÂep : 6 QC} (ke) Œê Ï Š¤î %SŸ[P S T ri V ‘% ] ep % Œê Ï 0«0Á0ª ‘% 0ó ep Na K 1.041 1.25 2.91 1.98 Mg K 1.253 0.65 2.41 0.97 Al K 1.486 17.45 2.41 23.57 Si K 1.739 17.06 2.88 22.13 P K 2.013 2.18 3.21 2.56 S K 2.307 0.50 2.72 0.57 Cl K 2.621 0.48 3.18 0.49 K K 3.312 0.59 4.35 0.55 Ca K 3.690 16.23 5.20 14.75 Ti K 4.508 36.76 7.14 27.96 Fe K 6.398 6.87 15.70 4.48 TŠ 10 00 0. 10 00 0.
Si操作手册

输入通道.........................................................................................3 ‐ 1
输入面板概述.................................................................................................. 3 ‐ 1 INPUT FADER SELECT输入推子选择按键(推子层选择).................. 3 ‐ 2 输入通道推子.................................................................................................. 3 ‐ 3 ON按键............................................................................................................ 3 ‐ 3 SOLO按键....................................................................................................... 3 ‐ 3 SELect按键...................................................................................................... 3 ‐ 4 输入通道状态窗口.......................................................................................... 3 ‐ 4 旋钮.................................................................................................................. 3 ‐ 4
合体版Zero4.0Final更新说明

57 附魔法术全面更改。不再有负效果,效果大幅提升但不可叠加(包括类似属性的相互叠加)
58 追加新武器——各种电锯。双手:[史诗]长柄电锯、[神话]碎尸者、[传说]肢解;单手:[史诗]便携电锯、[神话]电动斧刃I型、[神话]电动斧刃II型、[传说]时光切割者
38 原【英雄传说I II III】三套套装共六件装备全部更改建模,套装名称改为【达拉然的守卫者】【黑翼之巢的宝藏】【大元帅的指挥】,套装效果重写
39 原【盗贼之欲】套装武器模型更改,套装名称改为【堕落之欲】
40 弱化怪物的毒雾效果
41 暗夜行者初始武器改为手里剑(手持不显示,投掷时显示,剑类武器)
这个大概是最终版了吧……毕竟火炬2也差不多快出来了~~
谢谢大家一直以来的支持和帮助^_^
如果你玩过其他版本的火炬之光、mod或合体版的旧版本的话,建议人物洗点、宠物变回原版猫、狗、龙宠物,同时人物回到初始城镇
===============
4.0版相对3.0版的改动说明:
===============
46 圣骑士的【捍卫】【天使之剑】视觉效果修改
47 猎人追加【恐吓野兽】【毒蝎钉刺】【蝰蛇钉刺】【毒蛇钉刺】技能
48 战士【霜盾】技能效果增强(护甲加成增多)
50 雇佣兵营地的雇佣兵最高等级限制为30级,将不适应与高级怪物的战斗
51 去除所有人物的【炎爪】技能(如果有)。原因:和淬毒匕首效果重复
42 强化舞者的三大舞蹈基础伤害
43 追加新武器【狂野之斧】28级左右单手斧、【[传说]五管爆击炮】140级左右短射程高输出步枪、【[传说]战场狙击步枪】140级左右长射程步枪、【[传说]恶魔的诱惑】140级左右权杖、【[传说]无锋之剑】120级左右高输出单手剑
ACS4.1基本配置手册
Cisco ACS4.1基本配置手册1、ACS的基本设置在ACS服务器或远程PC上,IE浏览器URL中输入:http://acs服务器ip:2002可以进去ACS的配置界面,总的ACS界面如下图所示:图1-1deretsigeRnU1.1ACS软件基本选项设置1.1.1设置ACS4.1管理员帐号为了防止未经授权的人员配置ACS服务器,我们首先建立管理ACS的人员的帐号和密码,建立方式如下:(1) 进入ACS 管理控制栏目中,并点击右边ADD Administrator 选项: 图1-2(2) 输入管理员帐号密码,并点击Grant all 选项授予所有权限,最后Submit 提交一下:图1-3Un Re gi st er ed这样ACS 管理员帐号和密码就设置好了,下次通过远程登入ACS 界面系统就会提示需要提供管理员帐号和密码。
为了安全起见,可以考虑把ACS 网页超时时间设置的短一些,设置方法如下: (1) 点击图中的Seeeion Policy 选项,图1-4(2) 修改默认的idle timeout 时间,改成15min图1-5U n Re gi st er ed1.1.2 Log 信息的设置我们可以对ACS 对log 记录的默认设置进行一些修改,修改的步骤如下所示: (1) 进入ACS 的system configuration 栏目,并点击Service Contorl 选项: 图1-6(2) 对默认的LOG 记录选项按下图方式进行修改完后,点击Restart:图1-7U n R e gi st er ed1.1.3 高级用户选项设置为了ACS 用户属性等后续的设置需求,需要先把一些ACS 的高级用户选项开启一下:(1) 点击ACS 的Interface Configuration 栏目,可以看到右边有User DataConfiguration 和Advanced Options 这两个选项,如下图: 图1-8(2) 需要首先添加一个TACACS+属性的设备,这样上图中才会增加出另外一个TACACS+ (Cisco IOS)的选项。
ASB犯罪与治安法2014禁令说明书

PRACTITIONER GUIDE4IntroductionThis Practitioner Guide has been developed to assist officers in making applications for Injunction Orders under the provisions of Part 1 of the ASB, Crime and Policing Act 2014. The guide contains information about legal requirements and also tips on practical implementation and best practice. It is compatible with the ASB, Crime and Policing Act itself and the Home Office Statutory Guidance which was published in July 2014. A link to this document is available here http://goo.gl/JC6WH6Included towards the end of the document is a quick reference flowAnthony Collins Solicitors has kindly provided a legal edit of this document however it is not meant to replace the legal advice that you should seek in relation to individual cases. Resolve Antisocial Behaviour would also like to thank the members of the ASB working group who assisted in providing the content for the document.CriteriaIn an application for an injunction, the perpetrator is called the“Respondent” and the person applying for the order is the “Applicant”.mental health team and document your findings.An injunction against a young person (under 18) can last up to 12 months. There is no minimum or maximum duration for an adult – the Court will decide what they think is proportionate and necessary.Which Court?10-17 years old = Youth Court Adult = County CourtIf there are multiple respondents, who are both adults andjuveniles, the youth court can be asked to hear all of them together if the evidence is broadly the same and is in the “interests of justice”.Injunctions can also be used to hold someone responsible for others e.g. an injunction can be sought against a tenant to restrict how many visitors they can have at their address and when.Definition of ASBWhere the ASB is housing related or linked to a residential property, the definition is behaviour causing or likely to cause a nuisance or annoyance.In all other cases, the definition is behaviour causing or likely to cause harassment, alarm or distress.For both definitions of ASB, you will need to prove that the incidents have occurred on the balance of probabilities i.e. that it is more likely than not that the incident/s have occurred.Behaviour that might be suitable for an injunction:• Noise nuisance (loud music, DIY at unreasonable hours, dogs barking, fighting / shouting etc.)• Foul and abusive behaviour towards others • Threats of violence or actual violence • Overgrown/hazardous gardens • Littering / fly-tipping43Content – ProhibitionsIf seeking a non-association clause make sure you have the name, addresses and dates of birth of the associates and have evidence of each causing problems with the Respondent.You can include any prohibitions that you can evidence as being necessary to prevent further ASB – make sure that everything you ask for is:• Clear and specific enough for the Respondent to know what they cannot do• Is linked to your evidence e.g. if you want to stop the Respondent using foul language, have you got examples in your evidence of foul language being used before?Exclusions:• You can exclude someone from somewhere if youcan prove that it is necessary to prevent further ASB. Areas might include shops, certain streets, community buildings, entire estates or sometimes a wide area such as a town or local authority area.• You can exclude an adult from the place where they live if their behaviour is serious enough. In order to do this you must be able to show that there have been threats of or actual violence or a significant risk of harm.• A registered provider can only exclude someone from a home if they own or manage the property concerned.• You cannot exclude a minor from their home address.• Exclusion should only be used in “extreme caseswhere proportionate.” (p24 Home Office Guidance)Make sure you attend Court prepared – take plenty ofcopies of a map, clearly marking the areas where you want the exclusion to apply in red pen and also unmarked copies. Make sure:• The road names are clear and legible• Maps are copied in colour so the red line is still visible • You draw the line on the correct side of the road so asnot to miss an area you want includingThe Judge will want to see that the areas you wish to exclude from are reasonable and proportionate. You may wish to produce a “hotspot” map – using red dots to indicate where incidents have occurred. This will visually show the Judge areas where the incidents have occurred andtherefore where it is proportionate to exclude the Respondent from.Be reasonable – if you are askingfor exclusion from a large area, make sure you can evidence why it is proportionate. If the area includes the homes of close family members or access to GP/dentist etc consider allowing the respondent a route in and out of the exclusion area or specified times/days whenContent – Positive RequirementsIn order to meet all the criteria for positiverequirements, it would be goodpractice for the person/organisation responsiblefor the requirement to fill out a report, including:• An overview of therespondent’s needs• The positive requirements suggested and why you think these will assist in meeting the need and reducing the likelihood of reoccurring ASB • Who is the named individual responsible for each r equirement • Confirmation that any resource required is available• Confirmation that none of them conflict with any other order, education or employment, caring responsibilities etc.This can then be exhibited to the most appropriate witnessstatement to illustrate to the Court your actions.See example towards the end of this guide.Make sure that the Responsible Person understands what will be required of them, including that they will be legally bound to inform the Applicant of whether the order is being complied with or not, that they make necessary arrangements and that theypromote compliance (e.g. reminding the Respondent of theirobligations or when an appointment is due).Positive requirements can only be ordered at a final hearing (not without notice or on an interim basis).No power of arrest can be attached to a positive requirement.An injunction, whether for an adult or a minor, can include positive requirements e.g. making it a legal requirement for them to do something. The following must be shown:• If more than one positive requirement exists then they must be compatible with each other• Each positive requirement must specify a person or organisationresponsible for supervising it. This ‘Responsible Person’ / organisation must supply evidence of the suitability and enforceability of the requirement • That the requirements won’t interfere with the respondent’s work or education • That the requirements won’t conflict with the terms of any other Court order A positive requirement can require someone to do anything which you believe will assist in preventing further ASB. It may be the opportunity to make something that you identify as being beneficial for the Respondent, but is otherwise voluntary, into a legal requirement. Examples may becompelling the Respondent to attend an alcohol awareness course, accept tenancy support, or attend an initial assessment with a support worker.A Respondent to an injunction must:• Keep in touch with the ‘Responsible Person’ or organisation specified for each requirement• Notify the same of any change of addressIf the respondent does not comply with the above it is treated as a breach of the injunction.45ConsultationThink about the forums that you may already attend that have multi agency representation – can you add consultation on to the agenda, rather than arranging a separate meeting?Get a certificate of consultation signed to evidence you have met the requirement.If an organisation is refusing to consult with you, make sure you have evidenceof this, through copies of emails, file notes from conversations etc. Exhibiting these to the relevant statement will show the Court your attempts to meet the consultation requirement.There are certain people that you must consult with or inform of your actions.The difference is:CONSULTYou have taken that person’s/organisation’s views on board when making a decision (although they need not agree with your actions).INFORMTelling a person information.You will have probably already spoken with the people who are “appropriate” to inform as part of your case management process. It is therefore even more important to make sure that these conversations and meetings are documented through file notes and minutes.Who do I need to speak with?MinorsAdults CONSULTThe Youth Offending Team (YOT) for the area where the Respondent lives; and INFORMAny other person you think appropriate – this may include:• Parent / Guardian • Police • Local Authority • School• Support Worker / Social CareINFORMAny person that you think appropriate – this may include:• Police • Local Authority • Support Worker • Adult care• ProbationThe Consultation MeetingIt is best practice to invite everybody who has an interest in the matter to the meeting. This is so you can make a fully informed decision, ensure everyone is aware what is happening and deliver consistent messages to the Respondent.The following items may be discussed at the meeting:• The behaviour that has led to the meeting, theinterventions already tried and remaining options• Whether there is already an order in place (e.g. through the YOT or probation) and what is contained in it so you can make sure you do not duplicate anything or contradict existing terms• The terms appropriate for the injunction• Whether any positive requirements should be contained, who will complete an assessment and be the Responsible person for them?• What other actions might also be considered e.g. if the problem relates to a Registered Provider’s property, will tenancy warnings be considered, is a parenting tool also required?• How any breaches might be managed andpossible consequences?• Whether the order is to be publicised and how?If you follow the agenda suggested and illustrate this in your injunction application (e.g. through exhibiting the minutes and certificate of consultation to the mostappropriate witness statement), you will comply with a number of the legal criteria, including:• Showing why the application as a whole is proportionate and necessary• Illustrating that each individual prohibition and positive requirement has been discussed and is believed necessary• That no terms conflict with the Respondent’s education or employment• That it does not conflict/duplicate any other order • That a named person / organisation is allocated to each positive requirementWhilst it is best practice to have a meeting to consult, there may be some occasions where it is simply not possible or would unduly delay matters. In thesecircumstances consultation could occurremotely e.g. via email but make sure you clearly document your actions and the reasons why.47Without Notice ApplicationsYou do not have to consultbefore making anapplication for a withoutnotice injunction but youwill have to make sure thatyou have consulted beforethe first on notice hearing. General points• The Home Office Statutory Guidance states withoutnotice applications should be used in “exceptionalcases to stop serious harm to victims”• A without notice injunction means it is obtained withouttelling the Respondent – the first time they will knowabout it is when they are served with the order• It is an interim order – this means that it is temporary anda full hearing date will be set, giving the respondent thechance to attend and defend• At the without notice hearing you are not required tocall evidence to prove that the incidents have happenedbut that there is a significant risk of harm or there hasbeen a use or threat of violence and immediateprotection is required• The without notice terms granted at this stage will bejust enough to provide protection/prevent further issues –the final order may contain more conditions than theinterim order• You will generally need to apply for the order within ashort timeframe (24-48 hours) after the incident, in orderto justify the application• Find out whether you have legal cover on a Saturday and an out of hours contact – if someone is arrested on a Friday, they may be produced to the Court on a Saturday to fulfil the 24 hours timescale. Usually Saturday cases are just adjourned for a few days.• Make sure that the Police are aware of the process for dealing with breach of injunctions.• Speak to the victims and witnesses to make sure they know what to say when reporting a breach and have a copy of the power of arrest order to show any attending police officers.Not all terms in an injunction will have a power of arrest attached to them – you must show that the behaviour which the term relates to consists of threats of or actual violence OR represents asignificant risk of harm (which includes psychological harm). A positive requirement cannot have a power of arrest attached to it.Dealing with Breaches – Power of ArrestThe process4PRACTITIONER GUIDE9A breach of injunction must beproven beyond reasonable doubt. This means that you will need first hand evidence of the breach.A breach of an injunction is contempt of court, NOT a criminal offence.If a breach occurs and there is no power of arrest attached to it, an application must be made to the Court before the Respondent can be arrested for the matter or a committal application made (details of which fall outside the scope of this document).Dealing with Breaches –No Power of ArrestYou can vary and extend an injunction if the terms included do not cover a situation or the order is coming to an end and you want it to continue. You can do this in a separateapplication, making sure you include evidence of why the variation or extension is necessary. If you are already dealing with a breach of an injunction, you can apply for a variation or extension as part of the breach application.If the Respondent was a minor when the order was obtained but is over 18 when the order is breached, the breach hearing is dealt with by the County Court.The process for warrant applications• The injunction breach must have been proven inCourt to be able to use the absolute ground• The Possession Notice must have been served within 12 months of the breach finding (or outcome of any appeal)• The ground only applies where a breach of a prohibition has occurred, not a breach of a positive requirement• The Court may still consider Human Rights challenges so ensure you can show that your actions are “proportionate” – you may wish to complete a proportionality assessment to evidence your considerations1. Sentence Respondent Age Possible Consequences Minor10 -13 years Supervision Order 14 years and overSupervision Order or Detention Order (up to three months)AdultUnlimited fine and/or custodial sentence of up to 2 years2. Potential Use of Absolute Ground for Possession If the Respondent is a social housing tenant OR ahousehold member OR a visitor to a social housing tenant and a breach of their injunction occurs which is:• In the locality of the tenant’s property; or• Outside the locality but is a breach of a term intended to prevent nuisance or annoyance to someone who lives in the locality of the property (e.g. a neighbour); or• Outside the locality but is a breach of a term intended toprevent nuisance or annoyance to the landlord orsomeone employed to carry out the landlord’s duties Then the new absolute ground for possession may be relied upon by the landlord.The aim of the absolute ground for possession is to make itConsequences of Breach4PRACTITIONER GUIDECertificate of Consultation – Injunction OrderIn the County Court [or the Youth Court at [insert name]]In the matter of an application for an Injunction Order, pursuant to s1 of the ASB Crime and Policing Act 2014Applicant …………………………………………………………………………………………….Respondent …………………………………………………………………………………………The following have consulted in respect of this application, pursuant to s14 of the ASB Crime and Policing Act 2014:To be completed by the representative of the ApplicantI, [insert name], [insert role], hereby certify that I am duly authorised to consult on behalf of [name of applicant]. I consulted with [insert name and role] of [insert agency/organisation name] on [insert date] Signature……………………………………………………………………………………………Print name…………………………………………………………………………………………Date……………………………………………………………………………………………………To be completed by the representative of the Youth Offending TeamI, [insert name], [insert role], hereby certify that I am duly authorised to consult on behalf of [name of Youth Offending Team]. I have been consulted by [insert name and role] of [name of applicant] on [insert date] Signature……………………………………………………………………………………………Print name…………………………………………………………………………………………Date……………………………………………………………………………………………………Positive Requirements Report – ASB Crime and Policing Act 2014 This is a report prepared to assist the Court in deciding the suitability and content of positive requirements in an Injunction under the ASB Crime and Policing Act 2014.The RespondentNameTenant/householdmember/visitor?AgeDate of BirthAddressPostcodeSources of Information for ReportWho has beenspoken to whenpreparing thisreport? Has therespondentbeen assessedby any agency?Has theparent/guardianbeen involved ifa minor?The Requested Terms:REQUIREMENTS The specific positive requirement(s) that is being asked for E.g. to attend a 1 hour drug awareness session with the Young Persons Drug and Alcohol Service on a weekly basisEVIDENCE OF NECESSITY Why is the positive requirement(s) believed necessary? E.g. Callum has been seen frequently smoking Cannabis (re. PC Cooper’s evidence). It is believed that this is contributing towards the ASB he is committing and reducing his intake would assist in preventing further ASB.RESPONSIBLEPERSON ORORGANISATIONFor promotingcompliance andmonitoringadherence.E.g. Cherry Wilson – Young Persons Drug and Alcohol Service WorkerPROPOSEDLENGTHHow long is therequirement(s)needed for?E.g. Sessions will run weekly for a period of three months.All of the above requirements are available, are compatible with each other and there is no known conflict with:•the times when the Respondent must attend school or any other educational establishment•the times when the Respondent attends work•any known caring responsibilities.[We are satisfied that although the Respondent has a disability they are capable of complying with these proposed terms]OR[We are not aware that the Respondent has any disability].Existing OrdersIs theRespondentsubject to anyexisting Courtimposed Orders?If yes, what are the terms of the Orders?Confirm that the proposed terms above will not conflict, duplicate or contradict anything in any existing Orders. E.g. Johnny is currently subject to a Supervision Order that is managed through the Youth Offending Team. The terms of this order are: ∙To attend an emotional well-being session once per week∙To be subject to a curfew from 8pm through until 7am.I confirm that none of the requirements of this Order conflict with any of the proposed requirements for this Injunction application.I confirm that the information contained in this document is true to the best of my knowledge.Signed ……………………………………………………………………………Print name ………………………………………………………………………Role …………………………………………………………………………………Date …………………………………………………………………………………Injunction –Process Map for Registered Providers4PRACTITIONER GUIDE17Notes419PRACTITIONER GUIDE4134 Edmund Street。
2020年Q1新势力TOP10-KOL大盘点

2020年2020年Q1新势力TOP10-KOL大盘点【克劳锐出品】2020.04报告说明研究范围•本报告中新势力KOL是指2020年Q1各平台涨粉量TOP-10KOL;•报告选取微博、抖音、快手、B站、小红书五个平台的粉丝量TOP100-KOL进行研究,分析各平台涨粉较高的垂类类型,以及相应KOL的内容、粉丝、玩法等特点,解读KOL高幅涨粉的原因;•新势力代表KOL盘点主要从各平台不同垂类中选取标杆KOL进行复盘。
数据说明•报告中数据来源为克劳锐指数研究院,非各平台全量数据,仅供参考;•各平台KOL的日常统计数据,可通过“克劳锐指数”微信小程序免费查看。
报告核心发现:1.“疫情”让大量用户宅在家,从而增加了短视频等社交平台的使用时长,给KOL增加了涨粉的机会。
2.2020年Q1餐饮行业受“疫情”冲击较大,居家做饭教程类的美食KOL获得了更多的曝光机会,头部KOL在Q1大幅涨粉。
3.学生群体不断延长的假期,让游戏行业景气度上升,游戏主播通过短视频平台快速吸粉。
4.持续保持高质量内容输出是KOL涨粉的关键,各平台涨粉较高的KOL普遍在Q1作品数量多,且爆款多。
2020年Q1 新势力KOL大盘点2020Q1三大平台涨粉较高垂类集中在游戏、幽默搞笑和美食领域游戏17%幽默搞笑17%美食12%明星7%音乐6%其他24%萌宠5%舞蹈3%影视3%美妆3%创意3%抖音2020Q1 KOL 涨粉量TOP10垂类占比游戏23%美食17%音乐12%其他15%萌宠4%情感5%时尚3%运动健身2%幽默搞笑15%舞蹈3%萌娃2%快手2020Q1 KOL 涨粉量TOP10垂类占比明星10%幽默搞笑7%美妆7%时尚6%其他33%游戏4%影视5%音乐5%美食8%娱乐9%母婴亲子6%微博2020Q1 KOL 涨粉量TOP10垂类占比•新冠疫情让14亿中国人宅在家,也增加了各短视频、社交平台的流量和使用时长。
•抖音涨粉居前的垂类为游戏、幽默搞笑、美食等,涨粉TOP10垂类占平台Q1总涨粉量的76%。
THR5 THR5A THR10 THR10C THR10X 使用手册

连接................................................ 142
厂名 :雅马哈电子(苏州)有限公司 厂址 :中国江苏省苏州市新区鹿山路18号
保护环境 如果需要废弃设备(及电池)时,请与本地相关机构联系,获取正确的废弃方法。 请勿将设备(及电池)随意丢弃或作为生活垃圾处理。
135
名称和功能
n 控制面板
!9
THR10/10C/10X
!8
q
* 所示为 THR10
!7
将计算机连接到设备........................... 144
安装软件.................................................................144 连接和操作.............................................................145
24..装入电池时,请务必使其正负极与 +/-.极标 记保持一致。否则,可能会导致过热、火 灾或电解液泄漏。
25.. 当电池耗尽或长时间不使用本乐器时,请 将电池从乐器中取出以防电解液可能泄漏。
26..将本机安装在墙壁电源插座附近和容易连接 电源线的地方。
27.. 为了加强对於本产品的保护,在雷电期间, 或无人管理时以及长时间不使用时,请将 电源线从墙壁上的电源插座上拔下。这样 将防止该产品在闪电和电网出现电涌时受 到损害。
黑索今基含铝炸药烤燃实验和数值模拟

摇 第5期
黑索今基含铝炸药烤燃实验和数值模拟
979
and analyze the thermal reaction characteristics of the explosives. In the simulation,the endothermic and heat conduction of aluminum powder for RDX / Al / binder, the phase transition and multi鄄step thermal de鄄 composition reactions for TNT / RDX / Al, and the heat absorption of aluminum powder were considered, and a multi鄄component grid cell calculation method was used. The correctness of the calculated results was verified by comparing to the experimental results. The results show that the addition of aluminum powder accelerates the internal heat transfer rate of RDX / Al / binder (60 / 31 / 9) , of which ignition time is shorten so that the thermal safety of explosive is lower, and has no significant effect on the heat transfer process of TNT / RDX / Al (60 / 24 / 16) . Keywords: aluminized explosive; thermal reaction characteristic; cook off experiment; numerical simu鄄 lation
2020年12月份丰田车辆安全系统(Toyota Vehicle Security System,T

● ECE 116 Certification ● UK Thatcham Equivalent ● Standards and Industrial Research Institute of Malaysia (SIRIM)
Please read this manual for proper operation and keep it for future reference.
3.4
Auto Relock Function
3.5
Replacing Battery in Transmitter
3.6
Activate Alarm System
3.7
Deactivate Alarm System
3.8
Invalidity of Invasion and Tilt Sensor
3.9
Operating Toyota Vehicle Security System (TVSS)
3.4 Auto Relock Function
Operation ● Alarm unset by pressed Unlock button at transmitter. ● Auto relock will not occur when : 1) Any door is not fully closed. 2) Push Start Button remain ON.
Result ● All doors turn lock & signal light flash once after 30 secs.
3.5 Replacing Battery in Transmitter
Operation You will need the following items: ● Small flathead screwdriver or coin ● Lithium battery CR2032 ( Please refer to vehicle owner manual )
dsplib中文版 TMS32054X 函数库中文用户指南

TMS320C54x DSP 函数库用户指南TMS32C54X 优化C 函数库北京金信诺科技June, 1999目录第一章概述 (3)一、DSP 函数数据类型 (3)二、从C 程序中调用DSP 函数 (3)三、从汇编程序中调用DSP 函数 (5)四、其他说明 (6)第二章DSP 数学函数库 (7)a dd 向量相加 (7)s ub 向量相减 (8)m ul32 32 位向量相乘 (9)n eg 向量求反 (10)n eg32 双精度向量求反 (11)m mul 矩阵相乘 (12)m trans 矩阵转置 (13)m axidx 向量最大元素的序号 (14)m axval 向量元素的最大值 (15)m inidx 向量最小元素的序号 (16)m inval 向量的最小元素 (17)a tan16 反正切 (18)a tan2_16 反正切2 (19)s ine 三角正弦 (20)s qrt_16 16 位数的平方根 (21)l og_2 以2 为底的对数 (22)l og_10 以10 为底的对数 (23)l ogn 以e 为底的对数 (24)r ecip16 16 位数的倒数 (25)e xpn 指数 (26)p ower 向量的功率 (27)b exp 块的幂 (28)r and16init 初始化随机数生成器 (29)r and16 随机向量生成器 (30)f ltoq15 浮点数到Q15 数据转换 (31)q15tofl Q15 到浮点数转换 (32)第三章FFT 函数库 (33)cbrev 复数逆序 (33)cfft 复数FFT (34)c ifft 复数逆FFT (36)r fft 实数FFT(替换) (38)r ifft 逆实数FFT(替换) (40)第四章卷积与FIR 滤波器 (42)convol 卷积 (42)c fir 复数FIR 滤波器 (43)f ir FIR 滤波器 (44)f irs 对称FIR 滤波器 (45)f irs2 对称FIR 滤波器(常用) (47)f irdec 抽样FIR 滤波器 (48)f irinterp 插值FIR 滤波器 (50)f irlat FIR Lattice 滤波 (51)1hilb16 Hilbert 变换器 (52)第五章IIR 滤波器 (54)i ircas4 使用4 个参数的IIR 滤波(直接实现形式II) (54)i ircas5 使用5 个参数的IIR 滤波(直接实现形式II) (56)i ircas51 使用5 个参数的IIR 滤波(直接实现形式I) (58)iirlat IIR lattice 滤波 (59)iir32 双精度IIR 滤波 (60)第六章自适应滤波器 (62)d lms 自适应延迟LMS 滤波 (62)n blms 标准化的LMS 块滤波 (64)ndlms 标准化的延迟LMS 滤波 (66)第七章相关函数库 (68)a corr 自相关 (68)corr 互相关 (70)2第一章概述一、DSP 函数数据类型DSP 函数库处理以下的小数数据类型:Q3.12 :包含3 个整数位和12 个小数位,其各位的定义如下:位15 14 13 12 11 10 9 0值符号I3 I2 I1 Q11 Q10 Q9 …Q0它表示的数据范围是(-8,8),最小的小数分辨率为2−12 =2.441×10−4 。
Juniper ScreenOS 參考指南

概念與範例ScreenOS 參考指南第1 卷:綜述版本 6.0.0,修訂本 02Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089USA408-745-2000產品編號: 530-017767-01-TC,修訂本 02Copyright NoticeCopyright © 2007 Juniper Networks, Inc. All rights reserved.Juniper Networks and the Juniper Networks logo are registered trademarks of Juniper Networks, Inc. in the United States and other countries. All other trademarks, service marks, registered trademarks, or registered service marks in this document are the property of Juniper Networks or their respective owners. All specifications are subject to change without notice. Juniper Networks assumes no responsibility for any inaccuracies in this document or for any obligation to update information in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice.FCC StatementThe following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. The equipment generates, uses, and can radiate radio-frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference, in which case users will be required to correct the interference at their own expense.The following information is for FCC compliance of Class B devices: The equipment described in this manual generates and may radiate radio-frequency energy. If it is not installed in accordance with Juniper Networks’ installation instructions, it may cause interference with radio and television reception.This equipment has been tested and found to comply with the limits for a Class B digital device in accordance with the specifications in part 15 of the FCC rules. These specifications are designed to provide reasonable protection against such interference in a residential installation. However, there is no guarantee that interference will not occur in a particular installation.If this equipment does cause harmful interference to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following measures:Reorient or relocate the receiving antenna.Increase the separation between the equipment and receiver.Consult the dealer or an experienced radio/TV technician for help.Connect the equipment to an outlet on a circuit different from that to which the receiver is connected.Caution: Changes or modifications to this product could void the user's warranty and authority to operate this device.DisclaimerTHE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITEDWARRANTY, CONTACT YOUR JUNIPER NETWORKS REPRESENTATIVE FOR A COPY.ii目錄第 1 卷:綜述關於《概念與範例 ScreenOS 參考指南》xlv本書的結構.................................................................................................xlvii文件慣例........................................................................................................liiiWeb 使用者介面慣例..............................................................................liii指令行介面慣例.......................................................................................liv命名慣例和字元類型...............................................................................liv插圖慣例..................................................................................................lv技術文件與支援.............................................................................................lvi總索引........................................................................................................................IX-I第 2 卷:基本原理關於本卷ix文件慣例 (x)Web 使用者介面慣例 (x)指令行介面慣例 (xi)命名慣例和字元類型 (xi)插圖慣例 (xii)技術文件與支援 (xiii)第 1 章ScreenOS 架構1安全區 (2)安全區介面 (3)實體介面 (3)子介面 (3)虛擬路由器 (4)政策 (5)虛擬私人網路 (6)虛擬系統 (9)封包流動順序 (10)特大框架 (12)ScreenOS 架構範例 (13)範例: (第 1 部份) 具有六個區域的企業 (13)範例: (第 2 部份) 六個區域的介面 (15)範例: (第 3 部份) 兩個路由設定網域 (17)範例: (第 4 部份) 政策 (19)目錄 iii概念與範例 ScreenOS 參考指南第 2 章區域25檢視預先組態的區域 (26)安全區 (28)Global 區域 (28)SCREEN 選項 (28)將通道介面連結至通道區 (29)設定安全區和通道區 (30)建立區域 (30)修改區域 (31)刪除區域 (32)功能區 (33)第 3 章介面35介面類型 (36)邏輯介面 (36)實體介面 (36)無線介面 (36)橋接群組介面 (37)子介面 (37)聚集介面 (37)冗餘介面 (37)虛擬安全性介面 (38)功能區介面 (38)管理介面 (38)高可用性介面 (38)通道介面 (38)刪除通道介面 (41)檢視介面 (42)設定安全區介面 (43)將介面連結到安全區 (43)從安全區解除介面連結 (44)為 L3 安全區介面定址 (45)公開 IP 位址 (45)私人 IP 位址 (46)編址介面 (46)修改介面設定 (47)在根系統中建立子介面 (48)刪除子介面 (48)建立次要 IP 位址 (49)備份系統介面 (49)設定備份介面 (50)設定 IP 追蹤備份介面 (50)設定 Tunnel-if 備份介面 (51)設定路由器監看備份介面 (55)回傳介面 (56)建立回傳介面 (57)設定用於管理的回傳介面 (57)設定回傳介面上的 BGP (57)設定回傳介面上的 VSI (58)設定回傳介面作為來源介面 (58)介面狀態變更 (59)實體連接監看 (61)追蹤 IP 位址 (61)iv 目錄目錄介面監看 (66)監看兩個介面 (67)監看介面迴路 (68)安全區監看 (71)不工作中介面和通訊流量傳遞 (72)出口介面上的失敗 (72)入口介面上的失敗 (74)第 4 章介面模式77透明模式 (78)區域設定 (79)VLAN 區域 (79)預先定義的第 2 層區域 (79)通訊流量轉寄 (79)未知的 Unicast 選項 (80)氾濫方法 (81)ARP/Trace-Route 方法 (82)組態用於管理的 VLAN1 介面 (84)組態透明模式 (86)NAT 模式 (89)向內與向外 NAT 通訊流量 (91)介面設定 (92)組態 NAT 模式 (92)路由模式 (95)介面設定 (96)組態路由模式 (96)第 5 章為政策建構區塊99位址 (99)位址項目 (100)新增位址 (100)修改位址 (100)刪除位址 (101)位址群組 (101)建立位址群組 (102)編輯位址群組項目 (103)移除成員與群組 (103)服務 (104)預先定義的服務 (104)網際網路控制訊息通訊協定 (105)處理 ICMP 無法到達錯誤 (107)網際網路相關的預先定義服務 (107)Microsoft 遠端程序呼叫服務 (108)動態路由設定通訊協定 (110)資料流視訊 (111)Sun 遠端程序呼叫服務 (111)安全性與通道服務 (112)IP 相關服務 (112)即時通訊服務 (112)管理服務 (113)郵件服務 (113)UNIX 服務 (114)雜項服務 (114)目錄 v概念與範例 ScreenOS 參考指南自訂服務 (114)新增自訂服務 (115)修改自訂服務 (116)移除自訂服務 (116)設定服務逾時 (116)服務逾時組態與查詢 (116)意外情況 (117)範例 (118)定義自訂網際網路控制訊息通訊協定服務 (118)遠端 Shell ALG (119)Sun 遠端程序呼叫應用程式層閘道 (119)一般 RPC 呼叫情況 (120)自訂 Sun RPC 服務 (120)自訂 Microsoft 遠端程序呼叫 ALG (121)即時資料流傳遞通訊協定應用程式層閘道 (122)RTSP 要求方式 (123)RTSP 狀態代碼 (125)在私人網域中組態媒體伺服器 (126)在公開網域中組態媒體伺服器 (127)服務群組 (129)修改服務群組 (130)移除服務群組 (131)動態 IP 集區 (131)連接埠位址轉譯 (132)建立有 PAT 的 DIP 集區 (132)修改 DIP 集區 (133)相黏 DIP 位址 (134)在不同子網路中使用 DIP (134)在回傳介面上使用 DIP (139)建立 DIP 群組 (143)設定遞迴排程 (147)第 6 章政策149基本元素 (150)三種類型的政策 (151)區域間政策 (151)區域部政策 (151)全域政策 (152)政策組清單 (153)政策定義 (154)政策和規則 (154)政策的結構 (155)ID (156)區域 (156)位址 (156)服務 (156)動作 (157)應用程式 (157)名稱 (158)VPN 通道 (158)L2TP 通道 (158)深入檢查 (159)政策清單上方配置 (159)來源位址轉譯 (159)vi 目錄目錄目的地位址轉譯 (159)使用者驗證 (159)HA 會話備份 (161)Web 篩選 (161)記錄 (161)計數 (161)通訊流量警示臨界值 (161)排程 (162)防毒掃瞄 (162)通訊流量整理 (162)套用的政策 (163)檢視政策 (163)建立政策 (163)建立區域間政策郵件服務 (163)建立區域間政策組 (167)建立區域內部政策 (171)建立全域政策 (172)輸入政策內容 (173)各政策元件的多重項目 (174)設定位址否定 (174)修改和停用政策 (177)政策驗證 (177)重新排序政策 (178)移除政策 (179)第 7 章通訊流量整理181在政策層級管理頻寬 (181)設定通訊流量整理 (182)設定服務優先順序 (186)設定優先順序佇列 (187)入口政策制訂 (191)整理虛擬介面上的通訊流量 (191)介面層級通訊流量整理 (192)政策層級通訊流量整理 (193)封包流動 (194)範例: 具入口政策制訂,以路由為基礎的 VPN (194)範例: 具入口政策制訂的以政策為基礎的 VPN (198)使用回傳介面的通訊流量整理 (202)DSCP 標記與整理 (202)第 8 章系統參數205網域名稱系統支援 (205)DNS 查詢 (206)DNS 狀態表 (207)設定 DNS 伺服器並重新整理排程 (207)設定 DNS 重新整理間隔 (208)動態網域名稱系統 (208)設定 DynDNS 伺服器的 DDNS (209)設定 DDO 伺服器的 DDNS (210)代理 DNS 位址分割 (210)動態主機組態通訊協定 (213)組態 DHCP 伺服器 (214)自訂 DHCP 伺服器選項 (218)目錄 vii概念與範例 ScreenOS 參考指南在 NSRP 叢集中放置 DHCP 伺服器 (219)DHCP 伺服器偵測 (219)啟用 DHCP 伺服器偵測 (219)停用 DHCP 伺服器偵測 (219)將安全性裝置指派為 DHCP 轉接代理程式 (220)轉寄所有 DHCP 封包 (224)設定 Next-Server-IP (224)將安全性裝置作為 DHCP 用戶端使用 (225)傳播 TCP/IP 設定 (227)在虛擬系統中設定 DHCP (229)在虛擬系統中設定 DHCP 訊息中繼 (229)乙太網路上的點對點通訊協定 (230)設定 PPPoE (230)組態主要與備份 Untrust 介面上的 PPPoE (233)設定多個 PPPoE 會話使用單一介面 (234)PPPoE 與高可用性 (236)許可金鑰 (237)訂閱服務的註冊與啟動訂閱 (238)試用服務 (238)更新訂閱金鑰 (239)將防毒、Web 篩選、反垃圾郵件及深入檢查新增至現有或新裝置 (239)系統時鐘 (240)日期與時間 (240)日光節約時間 (240)時區 (240)網路時間通訊協定 (241)組態多重 NTP 伺服器 (241)組態備份 NTP 伺服器 (241)最大時間調整 (242)NTP 和 NSRP (242)將最大時間調整值設定至 NTP 伺服器 (243)保護 NTP 伺服器 (243)索引............................................................................................................................IX-I 第 3 卷:管理關於本卷vii文件慣例 (vii)Web 使用者介面慣例 (vii)指令行介面慣例 (viii)命名慣例和字元類型 (viii)插圖慣例 (ix)技術文件與支援 (x)第 1 章管理1透過 Web 使用者介面進行管理 (2)WebUI 說明 (2)將說明檔案複製到本機磁碟機 (3)將 WebUI 指向新的說明位置 (3)超文字傳輸通訊協定 (4)會話 ID (4)viii 目錄目錄目錄 ix安全通訊端階層 (5)SSL 組態 (7)將 HTTP 重新導向到 SSL (8)透過指令行介面進行管理.................................................................................9Telnet.. (9)保證 Telnet 連線的安全 (10)安全 Shell (11)用戶端要求 (12)裝置上的基本 SSH 組態 (13)驗證 (14)SSH 和 Vsys (16)主機金鑰 (16)範例: SSHv1 使用 PKA 進行自動登入 (17)安全副本 (18)序列主控台 (19)遠端主控台 (20)使用 V.92 數據機連接埠的遠端主控台 (20)使用 AUX 連接埠的遠端主控台 (21)數據機連接埠 (22)透過 NetScreen-Security Manager 進行管理 (22)初始化 NSM Agent 與 MGT 系統間的連線 (23)啟用、停用及取消 NSM Agent (24)設定管理系統的主伺服器 IP 位址 (25)設定警示和統計資訊報告 (25)組態同步處理 (26)範例: 檢視組態狀態 (27)範例: 擷取組態雜湊 (27)擷取組態時戳 (27)控制管理式通訊流量 (28)MGT 和 VLAN1 介面 (29)範例: 透過 MGT 介面進行管理.........................................................29範例: 透過 VLAN1 介面進行管理 (29)設定管理介面選項 (30)設定多個介面的管理 IP (31)管理層級 (33)根管理員 (33)讀/寫管理員 (34)唯讀管理員 (34)虛擬系統管理員 (34)虛擬系統唯讀管理員 (35)定義管理員使用者 (35)範例: 新增唯讀管理員 (35)範例: 修改管理員 (35)範例: 刪除管理員 (36)範例:設定撥號連線的管理員帳戶 (36)範例: 清除一個管理員的會話 (37)管理之通訊流量的安全化 (37)變更連接埠號碼 (38)變更管理員登入名稱和密碼 (39)範例: 變更管理員使用者的登入名稱和密碼 (40)範例: 變更您本身的密碼 (40)設定根管理員密碼的最小長度 (41)將裝置重設為出廠預設設定 (41)概念與範例 ScreenOS 參考指南限制管理式存取 (42)範例: 限制對單一工作站的管理 (42)範例: 限制對子網路的管理 (42)將根管理員限制為主控台存取 (42)用於管理式通訊流量的 VPN 通道 (43)透過以路由為基礎的手動金鑰VPN通道進行管理 (44)透過以政策為基礎的手動金鑰VPN通道進行管理 (47)密碼政策 (51)設定密碼政策 (51)移除密碼政策 (52)檢視密碼政策 (52)移除拒絕的預設管理員密碼 (52)建立登入橫幅 (53)第 2 章監看安全性裝置55儲存日誌資訊 (55)事件日誌 (56)按嚴重性和關鍵字檢視事件日誌 (57)排序和過濾事件日誌 (58)下載事件日誌 (58)範例: 下載整個事件日誌 (59)範例: 下載關鍵事件的事件記錄 (59)通訊流量記錄 (60)檢視通訊流量記錄 (61)範例: 檢視通訊流量記錄項目 (61)排序和過濾通訊流量記錄 (62)範例: 按時間排序通訊流量記錄 (62)下載通訊流量記錄 (62)移除關閉理由欄位 (63)自我記錄 (65)檢視自我記錄 (65)排序和過濾自我記錄 (65)範例: 按時間過濾自我記錄 (66)下載自我記錄 (66)下載資源修復日誌 (67)通訊流量示警 (67)範例: 以政策為基礎的入侵偵測 (68)範例: 折衷系統通知 (69)範例: 傳送電子郵件警訊 (70)系統日誌 (70)範例: 啟用多個系統日誌伺服器 (71)啟用通知事件的 WebTrends (72)簡易網路管理通訊協定 (72)建置概觀 (75)定義讀/寫的 SNMP 社群 (76)自行產生通訊流量的 VPN 通道 (77)範例: 透過以路由為基礎的通道自行產生的通訊流量 (78)範例: 透過以政策為基礎的通道自行產生的通訊流量 (85)檢視螢幕計數器 (91)索引............................................................................................................................IX-I x 目錄第 4 卷:攻擊偵測與防禦機制關於本卷ix文件慣例 (x)Web 使用者介面慣例 (x)指令行介面慣例 (xi)命名慣例和字元類型 (xi)插圖慣例 (xii)技術文件與支援 (xiii)第 1 章保護網路1攻擊階段 (2)偵測與防禦機制 (2)攻擊監看 (5)範例: 從 Untrust 區域中監看攻擊活動 (5)第 2 章勘查妨礙7IP 位址掃瞄 (8)連接埠掃瞄 (9)使用 IP 選項的網路勘查 (10)作業系統探查 (12)已設定 SYN 和 FIN 旗標 (12)不含 ACK 旗標的 FIN 旗標 (13)未設定旗標的 TCP 標頭 (14)迴避技術 (15)FIN 掃瞄 (15)非 SYN 旗標 (15)IP 位址詐騙 (17)範例: L3 IP 位址詐騙保護 (19)範例: L2 IP 位址詐騙保護 (22)IP 來源路由選項 (23)第 3 章服務中斷攻擊防禦25防火牆 DoS 攻擊 (26)會話表氾濫 (26)以來源與目的為基礎的會話限制 (26)範例: 以來源為基礎的會話限制 (27)範例: 以目的為基礎的會話限制 (28)挑釁過期 (28)範例: 挑釁超過存留期會話 (29)SYN-ACK-ACK Proxy 氾濫 (30)網路 DoS 攻擊 (31)SYN 氾濫 (31)範例: SYN 氾濫保護 (36)SYN Cookie (40)ICMP 氾濫 (42)UDP 氾濫 (43)Land 攻擊 (44)OS 指定的 DoS 攻擊 (45)Ping of Death (45)Teardrop 攻擊 (46)WinNuke (47)目錄 xi第 4 章內容監看與篩選49片段重組 (50)惡意 URL 保護 (50)應用程式層閘道 (51)範例: 在封包片段中阻斷惡意 URL (52)防毒掃瞄 (53)外部 AV 掃瞄 (53)掃瞄模式 (55)負載平衡 ICAP 掃瞄伺服器 (55)內部 AV 掃瞄 (56)IM 通訊流量的 AV 掃瞄 (57)IM 用戶端 (57)IM 伺服器 (58)IM 通訊協定 (58)即時通訊安全性問題 (59)IM 安全性問題 (59)掃瞄聊天訊息 (59)掃瞄檔案傳輸 (60)AV 掃瞄結果 (60)基於政策的 AV 掃瞄 (61)掃瞄應用程式通訊協定 (62)掃瞄 FTP 通訊流量 (63)掃瞄 HTTP 通訊流量 (64)掃瞄 IMAP 及 POP3 通訊流量 (66)掃瞄 SMTP 通訊流量 (67)將通訊流量重新導向至 ICAP AV 掃瞄伺服器 (69)更新內嵌掃瞄程式的 AV 模式檔案 (70)訂閱 AV 簽名服務 (70)更新 AV 模式 (71)AV 掃瞄程式全域設定 (72)AV 資源分配 (73)失敗模式行為 (73)最大內容大小和最大訊息數 (僅內部 AV) (73)HTTP Keep-Alive (74)HTTP 滴流 (僅內部 AV) (75)AV 設定檔 (76)將 AV 設定檔指派至防火牆政策中 (77)初始化內部 AV 的 AV 設定檔 (77)範例: (內部 AV) 掃瞄全部通訊流量類型 (78)範例: 僅 SMTP 與 HTTP 通訊流量的 AV 掃瞄 (78)AV 設定檔設定 (79)反垃圾郵件篩選 (83)黑名單和白名單 (83)基本組態 (84)篩選垃圾郵件通訊流量 (84)卸除垃圾郵件訊息 (84)定義黑名單 (85)定義白名單 (85)定義預設動作 (85)啟用垃圾郵件阻斷清單伺服器 (86)測試反垃圾郵件功能 (86)Web 篩選 (87)使用 CLI 以初始化 Web 篩選模式 (87)xii 目錄整合式 Web 篩選 (88)SurfControl 伺服器 (89)Web 篩選快取 (89)組態整合式 Web 篩選 (90)範例: 整合式 Web 篩選 (95)重新導向 Web 篩選 (96)虛擬系統支援 (98)組態重新導向 Web 篩選 (98)範例: 重新導向 Web 篩選 (101)第 5 章深入檢查105綜述 (106)攻擊物件資料庫伺服器 (110)預先定義的簽名封包 (110)更新簽名封包 (111)在啟動更新攻擊物件前 (111)直接更新 (112)自動更新 (112)自動通知與立即更新 (113)手動更新 (115)攻擊物件與群組 (116)支援的通訊協定 (118)狀態簽名 (120)TCP 資料流簽名 (121)通訊協定異常 (122)攻擊物件群組 (122)變更嚴重性層級 (122)範例: P2P 的深入檢查 (123)停用攻擊物件 (125)攻擊動作 (126)範例: 攻擊動作 - 關閉伺服器、關閉、關閉用戶端 (127)暴力攻擊動作 (134)暴力攻擊物件 (134)暴力攻擊目標 (135)暴力攻擊逾時 (135)範例 1 (135)範例 2 (136)範例 3 (136)攻擊記錄 (136)範例: 依攻擊群組停止記錄 (136)對應自訂服務至應用程式 (138)範例: 對應應用程式至自訂服務 (139)範例: HTTP 攻擊之應用程式至服務對應 (141)自訂的攻擊物件與群組 (142)使用者定義的狀態簽名攻擊物件 (142)規則運算式 (143)範例: 使用者定義的狀態簽名攻擊物件 (144)TCP 資料流簽名攻擊物件 (146)範例: 使用者定義的資料流簽名攻擊物件 (147)可組態的通訊協定異常參數 (148)範例: 修改參數 (148)否定 (149)範例: 攻擊物件否定 (149)目錄 xiiiHTTP 元件的點狀阻斷 (153)ActiveX 控制 (154)Java Applet (154)EXE 檔案 (154)ZIP 檔案 (154)範例: 阻斷 Java Applet 與 .exe 檔案 (154)第 6 章侵入偵測和預防155可執行 IDP 的安全性裝置 (156)具 IDP 功能的裝置內的通訊流量 (157)組態侵入偵測和預防 (158)組態前工作 (158)範例 1: 基本 IDP 組態 (159)範例 2: 為 IDP 設定主動/被動故障後移轉 (161)範例 3: 設定主動/主動/故障後移轉的 IDP (163)設定安全政策 (165)關於安全政策 (165)管理安全政策 (165)安裝安全政策 (165)使用 IDP 規則庫 (166)IDP 規則庫中以角色為基礎的管理 (166)設定 IDP 規則的物件 (167)使用安全政策範本 (167)在防火牆規則中啟用 IDP (168)啟用 IDP (168)指定 Inline 或 Inline Tap 模式 (169)設定 IDP 規則 (169)新增 IDP 規則庫 (170)對應通訊流量 (171)來源與目的地區域 (171)來源與目的地位址物件 (172)範例: 設定 Source 與 Destination (172)範例: 設定多個 Sources 與 Destinations (172)服務 (173)範例: 設定預設服務 (173)範例: 設定特定服務 (174)範例: 設定非標準的服務 (174)終止規則 (175)範例: 設定終止規則 (176)定義動作 (177)設定攻擊物件 (178)個別新增攻擊物件 (178)以目錄來新增攻擊物件 (178)範例: 以服務來新增攻擊物件 (178)以作業系統來新增攻擊物件 (178)以嚴重性來新增攻擊物件 (179)設定 IP 動作 (179)選擇 IP 動作 (179)選擇阻斷選項 (180)設定記錄選項 (180)設定逾時選項 (180)設定通知 (180)設定記錄 (180)設定警告 (180)記錄封包 (181)xiv 目錄設定嚴重性 (181)設定目標 (181)輸入意見 (181)設定豁免規則 (182)新增豁免規則庫 (182)定義對應 (184)來源與目的地區域 (184)來源與目的地位址物件 (184)範例: 豁免來源/目的對 (184)設定攻擊物件 (185)範例: 豁免特定攻擊物件 (185)設定目標 (185)輸入意見 (185)從日誌檢視器中建立豁免規則 (186)設定後門程式規則 (187)新增後門程式規則庫 (187)定義對應 (188)來源與目的地區域 (188)來源與目的地位址物件 (189)服務 (189)設定操作 (189)設定動作 (189)設定通知 (190)設定記錄 (190)設定警告 (190)記錄封包 (190)設定嚴重性 (190)設定目標 (191)輸入意見 (191)設定 IDP 攻擊物件 (191)關於 IDP 攻擊物件類型 (191)簽名攻擊物件 (191)通訊協定異常攻擊物件 (191)複合攻擊物件 (192)檢視預先定義的 IDP 攻擊物件與群組 (192)檢視預先定義的攻擊 (192)檢視預先定義的群組 (193)建立自訂 IDP 攻擊物件 (194)建立簽名攻擊物件 (195)建立通訊協定異常攻擊 (200)建立複合攻擊 (200)編輯自訂攻擊物件 (202)刪除自訂攻擊物件 (202)建立自訂 IDP 攻擊群組 (203)設定靜態群組 (203)設定動態群組 (204)範例: 建立動態群組 (205)更新動態群組 (206)編輯自訂攻擊群組 (206)刪除自訂攻擊群組 (206)將裝置設定為獨立的 IDP 裝置 (207)啟用 IDP (207)範例: 設定獨立 IDP 的防火牆規則 (207)設定以角色為基礎的管理 (208)範例: 設定僅 IDP 管理員 (208)目錄 xv管理 IDP (210)關於攻擊資料庫更新 (210)下載攻擊資料庫更新 (210)使用更新的攻擊物件 (210)更新 IDP 引擎 (211)檢視 IDP 日誌 (212)第 7 章可疑的封包屬性213ICMP 片段 (214)大型 ICMP 封包 (215)錯誤的 IP 選項 (216)未知的通訊協定 (217)IP 封包片段 (218)SYN 片段 (219)附錄A使用者定義簽名環境A-I索引............................................................................................................................IX-I 第 5 卷:虛擬私人網路關於本卷vii文件慣例 (viii)Web 使用者介面慣例 (viii)指令行介面慣例 (ix)命名慣例和字元類型 (ix)插圖慣例 (x)技術文件與支援 (xi)第 1 章網際網路通訊協定安全性1虛擬私人網路簡介 (2)IPSec 概念 (3)模式 (4)傳輸模式 (4)通道模式 (4)通訊協定 (5)驗證標頭 (6)封裝安全性負載 (6)金鑰管理 (6)手動金鑰 (6)自動金鑰 IKE (7)安全性關聯 (7)通道交涉 (8)階段 1 (8)主要模式和挑釁式模式 (8)Diffie-Hellman 交換 (9)階段 2 (10)完美轉送安全性 (10)重播保護 (10)IKE 與 IPSec 封包 (11)IKE 封包 (11)IPSec 封包 (14)xvi 目錄第 2 章公開金鑰密碼編譯17公開金鑰密碼編譯簡介 (18)簽名認證 (18)確認數位簽名 (18)公開金鑰基礎結構 (20)認證和 CRL (22)手動要求認證 (23)載入認證和認證撤銷清單 (25)組態 CRL 設定 (26)自動取得本機認證 (28)自動認證更新 (30)金鑰組產生 (31)線上認證狀態通訊協定 (31)指定認證撤銷檢查方法 (32)檢視狀態檢查屬性 (32)指定線上認證狀態通訊協定回應程式 URL (32)移除狀態檢查屬性 (33)自助簽名認證 (33)認證驗證 (34)手動建立自助簽名認證 (35)設定管理員定義的自助簽名認證 (35)自動產生認證 (39)刪除自助簽名認證 (40)第 3 章虛擬私人網路準則41加密選項 (42)站台到站台加密選項 (42)撥接 VPN 選項 (49)以路由為基礎和以政策為基礎的通道 (56)封包流動: 站台對站台 VPN (57)通道組態準則 (61)以路由為基礎的虛擬私人網路安全性考量 (63)Null 路由 (64)撥接或租借線路 (65)VPN 故障後移轉至租借線路或 Null 路由 (66)誘導式通道介面 (68)通道介面的虛擬路由器 (69)重新路由至另一個通道 (69)第 4 章站台對站台的虛擬私人網路71站台對站台 VPN 組態 (72)以路由為基礎的站台對站台 VPN,自動金鑰 IKE (78)以政策為基礎的站台對站台 VPN,自動金鑰 IKE (86)以路由為基礎的站台對站台 VPN,動態對等方 (92)以政策為基礎的站台對站台 VPN,動態對等方 (100)以路由為基礎的站台對站台 VPN,手動金鑰 (109)以政策為基礎的站台對站台 VPN,手動金鑰 (115)使用 FQDN 的動態 IKE 閘道 (120)別名 (121)設定具有 FQDN 的自動金鑰 IKE 對等方 (122)具有重疊位址的 VPN 站台 (130)透明模式 VPN (141)目錄 xvii第 5 章撥接虛擬私人網路149撥接 (150)以政策為基礎的撥接 VPN,自動金鑰 IKE (150)以路由為基礎的撥接 VPN,動態對等方 (156)以政策為基礎的撥接 VPN,動態對等方 (163)用於撥接 VPN 使用者的雙向政策 (168)群組 IKE ID (173)有認證的群組 IKE ID (173)萬用字元和容器 ASN1-DN IKE ID 類型 (174)建立群組 IKE ID (認證) (177)設定具預先共享金鑰的群組 IKE ID (181)共享 IKE ID (187)第 6 章第 2 層通道通訊協定193L2TP 簡介 (193)封包的封裝和拆裝 (196)封裝 (196)拆裝 (197)設定 L2TP 參數 (198)L2TP 和 IPSec 上的 L2TP (200)設定 L2TP (200)設定 IPSec 上的 L2TP (205)IPSec 上的雙向 L2TP (212)第 7 章進階虛擬私人網路功能219NAT-Traversal (220)探查 NAT (221)跨越 NAT 裝置 (223)UDP 總和檢查碼 (225)Keepalive 封包 (225)初始程式/回應程式對稱 (225)啟用 NAT-Traversal (226)使用具有 NAT-Traversal 的 IKE ID (227)VPN 監看 (229)重新建立金鑰和最佳化選項 (230)來源介面和目的地位址 (231)政策考量 (232)組態 VPN 監看功能 (232)SNMP VPN 監看物件和陷阱 (240)每個通道介面,多個通道 (242)路由到通道的對應 (243)遠端對等方的位址 (244)手動和自動表項目 (245)手動表項目 (245)自動表項目 (245)設定重疊子網路的通道介面上的 VPN (247)連結自動路由和 NHTB 表項目 (265)使用自動路由表項目的 OSPF (277)備援 VPN 閘道 (278)VPN 群組 (279)監看機制 (280)IKE 活動訊號 (281)Dead 對等方偵測 (281)IKE 修復程序 (282)xviii 目錄TCP SYN 旗標檢查 (284)建立冗餘 VPN 閘道 (285)建立背對背 VPN (291)建立集中星型 VPN (298)第 8 章AutoConnect 虛擬私人網路309綜述 (309)運作方式 (309)NHRP 訊息 (310)AC-VPN 通道初始化 (311)組態 AC-VPN (312)網路位址轉譯 (312)中心站台上的組態 (313)各星型站台上的組態 (313)範例 (314)索引............................................................................................................................IX-I第 6 卷:網際網路通訊協定語音通訊關於本卷v文件慣例 (vi)Web 使用者介面慣例 (vi)指令行介面慣例 (vii)命名慣例和字元類型 (vii)插圖慣例 (viii)技術文件與支援 (ix)第 1 章H.323 應用程式層閘道1綜述 (1)範例 (2)範例: Trust 區域中的看守者 (2)範例: Untrust 區域中的看守者 (3)範例: 透過 NAT 的向外呼叫 (4)範例: 透過 NAT 的向內呼叫 (7)範例: NAT 模式 Untrust 區域中的看守者 (10)第 2 章會話初始化通訊協定應用程式層閘道13綜述 (13)SIP 要求方式 (14)SIP 回應類別 (16)SIP 應用程式層閘道 (17)會話說明通訊協定會話 (18)針孔建立 (19)會話靜止逾時 (20)SIP 攻擊保護 (21)範例: SIP 防止拒絕服務攻擊 (21)範例: 發訊靜止與媒體靜止逾時 (22)範例: UDP 氾濫保護 (22)範例: SIP 連接最大值 (23)目錄 xix使用網路位址轉譯的 SIP (23)向外呼叫 (24)向內呼叫 (24)轉寄的呼叫 (24)呼叫終止 (24)呼叫 Re-INVITE 訊息 (25)呼叫會話計時器 (25)呼叫取消 (25)分叉 (25)SIP 訊息 (25)SIP 標頭 (26)SIP 內文 (27)SIP NAT 情況 (28)範例 (29)使用 SIP Registrar 支援向內 SIP 呼叫 (30)範例: 向內呼叫 (介面 DIP) (31)範例: 向內呼叫 (DIP 集區) (33)範例: 透過 MIP 的向內呼叫 (35)範例: 私人區域中的 Proxy (37)範例: 公開區域中的 Proxy (40)範例: 三區、DMZ 中的代理 (42)範例: Untrust 區域內部 (45)範例: Trust 區域內部 (49)範例: SIP 的全網狀 VPN (51)VoIP 服務的頻寬管理 (60)第 3 章媒體閘道控制通訊協定應用程式層閘道63綜述 (63)MGCP 安全性 (64)關於 MGCP (64)MGCP 中的實體 (64)端點 (65)連接 (65)呼叫 (65)呼叫代理 (65)指令 (66)回應代碼 (68)範例 (69)用戶家中的媒體閘道 ISP 處的呼叫代理 (69)ISP 託管服務 (71)第 4 章小用戶端控制通訊協定應用程式層閘道77綜述 (77)SCCP 安全性 (78)關於 SCCP (79)SCCP 元件 (79)SCCP 用戶端 (79)Call Manager (79)叢集 (79)SCCP 異動 (80)用戶端初始化 (80)用戶端註冊 (80)呼叫設定 (81)媒體設定 (81)xx 目錄SCCP 控制訊息與 RTP 流動 (82)SCCP 訊息 (83)範例 (83)範例: Call Manager/TFTP 伺服器位於 Trust 區域中 (84)範例: Untrust 區域中的 Call Manager/TFTP 伺服器 (86)範例: 三區域,Call Manager/TFTP 伺服器位於 DMZ 中 (88)範例: 區域內部,Call Manager/TFTP 伺服器位於 Trust 區域中 (91)範例: 區域內部,Call Manager/TFTP 伺服器位於 Untrust 區域中 (95)範例: SCCP 的全網狀 VPN (97)索引............................................................................................................................IX-I第7 卷:路由設定關於本卷ix文件慣例 (x)Web 使用者介面慣例 (x)指令行介面慣例 (xi)命名慣例和字元類型 (xi)插圖慣例 (xii)技術文件與支援 (xiii)第 1 章靜態路由設定1綜述 (2)靜態路由的運作方式 (2)組態靜態路由的時機 (3)設定靜態路由 (5)設定靜態路由 (5)設定通道介面的靜態路由 (9)啟用閘道追蹤 (10)將通訊流量轉寄至 Null 介面 (11)避免在其他路由設定表中查詢路由 (11)避免在非通道介面上傳送通道通訊流量 (11)避免摘要路由建立的迴路 (11)永遠處於活動狀態的路由 (12)變更具等值多途的路由設定優先順序 (12)第 2 章路由設定13綜述 (14)虛擬路由器路由設定表 (15)以目的地為基礎的路由設定表 (16)以來源為基礎的路由設定表 (17)以來源介面為基礎的路由設定表 (19)建立與修改虛擬路由器 (21)修改虛擬路由器 (21)分配虛擬路由器 ID (22)在虛擬路由器之間轉寄通訊流量 (23)組態兩個虛擬路由器 (23)建立與刪除虛擬路由器 (25)建立自訂虛擬路由器 (26)刪除自訂虛擬路由器 (26)目錄 xxi。
fitbit inspire 3 用户手册说明书

用户手册版本 1.3目录开始 (6)包装盒内容 (6)为智能设备充电 (6)设置Inspire 3 (8)在 Fitbit 应用程序上查看您的数据 (8)解锁 Fitbit Premium (9)佩戴 Inspire 3 (10)全天候佩戴和锻炼时佩戴 (10)用手习惯 (11)将 Inspire 3 置于配夹中 (11)佩戴配夹 (12)佩戴与保养技巧 (13)更换腕带 (13)移除腕带 (13)安装腕带 (14)基础信息 (15)操作 Inspire 3 (15)基本浏览指南 (15)快速设置 (16)调整设置 (18)显示设置 (18)安静模式 (19)其他设置 (19)检查电池电量 (20)调整屏幕常亮 (20)关闭屏幕 (21)钟面和应用程序 (22)更改钟面 (22)打开应用程序 (22)寻找手机 (23)来自手机的通知 (24)2设置通知 (24)查看收到的通知 (24)管理通知 (25)关闭通知 (25)接听或拒绝来电 (26)回复消息(Android 手机) (27)计时功能 (28)设置闹钟 (28)关闭或延后闹钟 (28)使用计时器或秒表 (29)活动和健康 (30)查看您的统计数据 (30)追踪每日活动目标 (30)选择目标 (31)追踪每小时的活动 (31)追踪您的睡眠 (31)设定睡眠目标 (32)了解您的长期睡眠习惯 (32)了解您的睡眠习惯 (32)管理压力 (32)练习引导式呼吸 (32)查看您的压力管理分数 (33)高级健康指标 (33)锻炼和心脏健康 (34)自动追踪您的锻炼 (34)使用“锻炼”应用程序追踪和分析锻炼 (34)GPS 要求 (34)自定义您的锻炼设置 (35)检查您的锻炼汇总信息 (37)查看您的心率 (37)默认心率区间 (37)自定义心率区间 (38)获得活跃区间分钟数 (38)接收心率通知 (39)查看您的每日准备状态分数 (40)3查看您的心肺有氧健康指数 (40)分享您的活动 (41)更新、重启和清除 (42)更新 Inspire 3 (42)重启 Inspire 3 (42)清除 Inspire 3 (43)故障排除 (44)心率信号丢失 (44)GPS 信号丢失 (44)其他问题 (45)通用信息和规格 (46)传感器与组件 (46)材料 (46)无线技术 (46)触觉反馈 (46)电池 (46)内存 (46)显示屏 (47)腕带尺寸 (47)环境条件 (47)了解更多 (47)退货政策和保修 (47)Regulatory and Safety Notices (48)USA: Federal Communications Commission (FCC) statement (48)Canada: Industry Canada (IC) atement (49)European Union (EU) (50)Argentina (52)Australia and New Zealand (52)Ghana (52)Indonesia (52)Israel (52)Japan (53)Kingdom of Saudi Arabia (53)Malaysia (53)Mexico (53)4Morocco (54)Nigeria (54)Oman (54)Paraguay (54)Philippines (55)Serbia (55)Singapore (55)South Korea (55)Taiwan (56)Thailand (59)United Arab Emirates (59)United Kingdom (60)About the Battery (60)IP Rating (61)Safety Statement (61)Regulatory Markings (61)56开始了解 Fitbit Inspire 3——这是一款帮助您寻获活力、享受自己的兴趣并改善健康的智能设备。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CAS实战4.0-增加了non-secure connection配置法2012年6月26号上海释锐教育软件有限公司内部培训教材CAS Server:192.168.18.55 :8080 apache-tomcat-7.0.25CAS Client:192.168.18.55 JBOSS5.1-GA目录一. 带证书的配置方法 (1)二. 不带证书的非加密传输(non-secure connection)配置方法 (9)一. 带证书的配置方法第1步:安装tomcat7 并配置好jdk1.7的环境变量。
第2步:创建证书注意事项:1、名字与姓氏必须填写验证服务器的域名2、密钥库口令是threenet@123第3步:导出证书至此导出证书完成,可以分发给应用的JDK使用了,接下来讲解客户端的JVM怎么导入证书第4步:为客户端的JVM导入证书注意事项:1、将.key.crt证书文件拷贝到客户端应用程序的机器上C:\jboss_test\jdk1.7.0\bin2、客户端的JRE密钥库默认口令是changeit 而非threenet@123至此证书的创建、导出、导入到客户端JVM都已完成,下面开始使用证书到Web服务器中,本教程使用tomcat如果不完成本步骤,运行应用系统时会出现如下错误:ng.RuntimeException:.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target第5步:应用证书到CAS Web服务器-Tomcat,就是启用Web服务器(Tomcat)的SSL<!-- Define a SSL HTTP/1.1 Connector on port 8443This connector uses the JSSE configuration, when using APR, theconnector should be using the OpenSSL style configurationdescribed in the APR documentation --><Connector port="443" protocol="HTTP/1.1" SSLEnabled="true"maxThreads="150" scheme="https" secure="true"clientAuth="false" sslProtocol="TLS" keystoreFile="C:/apache-tomcat-7.0.25/keys/.key" keystorePass="threenet@123" />好了,到此Tomcat的SSL启用完成,现在你可以启动tomcat试一下了第6步:启动TOMCA T,发现如下错误:ng.Exception: Connector attribute SSLCertificateFile must be defined when using SSL with APR解决办法:注释掉一行配置Try this as your server.xml file. I removed some of the comments and commented out the APR listener.<!-- <Listener className="org.apache.catalina.core.AprLifecycleListener" SSLEngine="on" /> -->至此,测试一下打开https:///提醒:在该步骤,客户端浏览器用户可以按提示一步一步安装证书,安装成功后,下次就不会出现这个提示了。
接下来配置CAS服务器。
第7步:安装CAS服务器软件7-1)下载完成后将cas-server-3.4.11.zip解压,解压cas-server-3.4.11/modules/cas-server-webapp-3.4.11.war,然后复制到你的tomcat/webapp目录下。
7-2)CAS深入配置,配置CAS服务器怎么读取数据库的信息进行身份验证,修改cas/WEB-INF/deployerConfigContext.xml 文件。
先复制数据库驱动程序sqljdbc4.jar拷贝到tomcat7/lib下、cas-server-support-jdbc-3.4.11.jar、commons-dbcp.jar、commons-pool-1.3.jar和释锐自定义MD5加密编码包threeoa_utility.jar到cas/WEB-INF/lib/下。
注释掉:SimpleTestUsernamePasswordAuthenticationHandler,改用QueryDatabaseAuthenticationHandler。
新增如下配置代码:<!--| 验证数据库连接配置信息,by 周清华上海释锐公司+--><bean id="dataSource"class="mons.dbcp.BasicDataSource"><property name="url"><value>jdbc:sqlserver://localhost:1433;databaseName=threenet_cas</value></property><property name="driverClassName"><value>com.microsoft.sqlserver.jdbc.SQLServerDriver</value></property><property name="username"><value>sa</value></property><property name="password"><value>threenet</value></property></bean><!--| 禁用cas内置的MD5加密法,改用释锐公司自己的MD5加密解密法,+--><!--bean id="MD5PasswordEncoder" class="org.jasig.cas.authentication.handler.DefaultPasswordEncoder" autowire="byName"> <constructor-arg value="MD5" /></bean --><bean id="MD5PasswordEncoder"class="com.threeoa.tools.encoder.ThreeoaPasswordEncoder"/>修改代码:<!--<bean class="org.jasig.cas.authentication.handler.support.SimpleTestUsernamePasswordAuthenticationHandler" />--> <bean class="org.jasig.cas.adaptors.jdbc.QueryDatabaseAuthenticationHandler"><property name="dataSource"ref="dataSource"/><property name="sql"value="SELECT password FROM passports WHERE username=? "/><property name="passwordEncoder"ref="MD5PasswordEncoder"/></bean>至此,CAS服务器安装和配置成功,如下图https:///cas-server-webapp-3.4.11/login证书按上图处理。
修改tomcat/conf/server.xml 文件,在<Host name="localhost" appBase="webapps" unpackW ARs="true" autoDeploy="true">中添加<Context path="" docBase="/cas-server-webapp-3.4.11" debug="0" reloadable="true"/> ,重启实现<!-- 配置直接通过域名访问/cas应用 --> 。
新的验证网址为https:///login第8步:配置CAS客户端,添加cas-client的jar包8-1)将cas-client-core-3.2.1.jar和threeoa_utility.jar文件拷贝到应用程序\WebRoot\WEB-INF\lib下。
8-2)编辑web.xml,增加下列内容:<!-- ======================== 单点登录开始 ======================== --><!-- 用于单点退出,该过滤器用于实现单点登出功能,可选配置--><listener><listener-class>org.jasig.cas.client.session.SingleSignOutHttpSessionListener</listener-class></listener><!-- 该过滤器用于实现单点登出功能,可选配置。
