思科DC虚拟化技术和部署指南
虚拟化技术总体介绍

电信网络NFV引入价值和策略
基于云的自愈和弹性机制实现低冗余率/高利用率不成功/过时业务退出时,硬件资源可循环利用,减少部分重复投资软硬件分离开发/采购,降低技术门槛和开发成本,竞争充分,通用硬件开发成本的规模效应
CAPEX
统一硬件降低多种专用设备规划和运维复杂度,运维效率提升集中部署和自动化运维,减少运维人员,提升效率统一基础设施平台,缩短TTM网络切片能力在统一基础设施平台上快速提供服务不同用户的软网络/业务
虚拟化技术总体介绍
虚拟化发展背景虚拟化基本概念虚拟化架构特性虚拟化产品介绍
目录
通信行业的演进
通信网的发展是一个不断学习新技术、不断焕发青春的过程,在经历了模拟通信、数字通信、IP化后,当前通信网正加速转向基于虚拟化、软件化等IT技术的通信4.0时代。
过去十年的变革核心是IP化,其特征是CT的网络实质,IP化的外在通信方式(承载、协议等)下一步变革的核心是IT化,网络采用IT化的内在实现形式,保留CT的网络内涵和品质,更加深刻地再造电信网络
VNF(xGW)
VNF(CG)
虚拟化网元,对应vEPC、vIMS、vMSC等业务网元
公共基础设置
计算
存储
网络
TECS在网络架构中的位置
TECS(Telecom Elastic Cloud System)在ETSI NFV框架中对应MANO域的VIM,以及NFVI域中的虚拟化层、虚拟计算、虚拟存储、虚拟网络部分
OPEX
网络能力开放,从封闭的业务供给到广泛合作网络架构灵活,业务感知和适配能力更强、更快,相对僵化的网络更适合不可预知新业务创新,提高收益
REVENUE
开放,软硬件分开开发和采购,更低的投资、技术门槛,更多的player,更充分的竞争开放,更快地更换硬件/软件供应商,消除vendor-locking以更低的成本和风险更快地提供业务
服务器虚拟化部署方案

引言:服务器虚拟化是目前企业IT基础设施中的重要技术之一,它通过将一个物理服务器分成多个虚拟服务器,并在虚拟服务器上运行独立的操作系统和应用程序,实现资源的有效利用和管理。
本文将详细介绍服务器虚拟化部署方案的具体内容,包括硬件选择、虚拟化平台选择、网络配置、存储方案以及性能优化等方面。
概述:在进行服务器虚拟化部署的过程中,需要考虑多个因素,包括硬件设备的选择、虚拟化平台的选型、网络配置的规划、存储方案的设计以及性能优化等方面。
只有在这些方面都进行充分的考虑和规划,才能确保虚拟化环境的稳定性和可靠性,提高整个系统的性能和效率。
正文内容:一、硬件选择1.CPU选择:根据虚拟化环境中应用程序的需求来选择适合的CPU型号,并确保CPU支持硬件虚拟化技术,如Intel的VTx或者AMD的AMDV。
2.内存选择:根据虚拟机实例的数量和工作负载的需求来选择合适的内存容量,并确保服务器支持ECC内存以提高系统的稳定性。
3.磁盘选择:根据虚拟机磁盘和存储需求来选择适合的磁盘类型,包括SSD和HDD,并考虑RD配置以提高数据的冗余性和读写性能。
4.网卡选择:选择支持虚拟化的高性能网卡,以提供足够的网络带宽和低延迟的传输性能。
5.电源选择:选择高效能的电源以降低功耗和热量的产生,确保系统能够长时间稳定运行。
二、虚拟化平台选择1.基于硬件的虚拟化平台:如VMware的ESXi、Microsoft的HyperV等,这些平台提供了硬件虚拟化的能力,可以更好地隔离不同的虚拟机实例,提供更高的性能和安全性。
2.容器化平台:如Docker、Kubernetes等,这些平台采用轻量级的容器技术,可以更高效地利用服务器资源,并提供快速部署和可伸缩性。
3.开源平台:如OpenStack等,这些平台提供了全面的虚拟化管理功能,可以方便地配置和管理多个虚拟机实例。
三、网络配置1.VLAN划分:根据虚拟机实例的不同需求,划分不同的VLAN,确保虚拟机之间的网络隔离和安全性。
思科DC虚拟化技术和部署指南

解析思科数据中心虚拟化技术和部署数据中心的发展正在经历从整合,虚拟化到自动化的演变,基于云计算的数据中心是未来的更远的目标。
整合是基础,虚拟化技术为自动化、云计算数据中心的实现提供支持。
数据中心的虚拟化有很多的技术优点:可以通过整合或者共享物理资产来提高资源利用率,调查公司的结果显示,全球多数的数据中心的资源利用率在15%~20%之间,通过整合、虚拟化技术可以实现50%~60%的利用率;通过虚拟化技术可以实现节能高效的绿色数据中心,如可以减少物理设备、电缆,空间、电力、制冷等的需求;可以实现对资源的快速部署以及重部署以满足业务发展需求。
数据中心虚拟化的简单示意图。
数据中心的资源,包括服务器资源、I/O资源、存储资源组成一个资源池,通过上层的管理、调度系统在智能的虚拟化的网络结构上实现将资源池中的资源根据应用的需求分配到不同的应用处理系统。
虚拟化数据中心可以实现根据应用的需求让数据中心的物理IT资源流动起来,更好的为应用提供资源调配与部署。
数据中心虚拟化发展的第一个阶段是通过整合实现服务器和应用的虚拟化服务,这阶段的数据中心也是很多公司已经做的或正要做的。
在这一阶段,数据中心虚拟化实现的是区域内的虚拟化,表现为数据中心的服务如网络服务、安全服务、逻辑服务还是与物理服务器的部署相关联;虚拟机上的VLAN与网络交换层上的VLAN对应;存储LUN以类似映射到物理服务器的方式映射到虚拟机。
如下图。
数据中心虚拟化发展的第二个阶段是通过虚拟主机迁移技术(VM's Mobility)实现跨物理服务器的虚拟化服务。
如下图。
在这个阶段,实现了数据中心内的跨区域虚拟化,虚拟机可以在不同的物理服务器之间切换,但是,为满足虚拟机的应用环境和应用需求,需要网络为应用提供智能服务,同时还需要为虚拟化提供灵活的部署和服务。
思科在下一代的数据中心设计中采用统一交换的以太网架构,思科数据中心统一交换架构的愿景图如下。
改进之前的数据中心物理上存在几个不同的网络系统,如局域网架构、SAN 网络架构、高层的计算网络架构、管理控制网络架构,各个网络上采用的技术不同,如局域网主要采用以太网技术,SAN网络主要采用Fiber Channel技术。
思科数据中心虚拟化 vPC技术和配置

思科数据中心虚拟化vPC技术和配置最近在研究数据中心功能时发现CISCO有一个虚拟化技术叫vPC的技术,今天就把我研究的成果分享出来。
什么是 vPC(virtual port channel)?研究了大半天,其实它就是一个可以跨不同设备的port-channel技术。
它的作用:可以实现网络冗余,可以跨设备进行端口聚合,增加链路带宽,当链路故障时比生成树协议收敛时间还快。
下面我们就说说为什么会出现vPC技术。
="WIDOWS: 2; TEXT-TRANSFORM: none; TEXT-INDENT: 0px; LETTER-SPACING: normal; BORDER-COLLAPSE: separate; FONT: 16px Simsun; WHITE-SPACE: normal; ORPHANS: 2; COLOR: rgb(0,0,0); WORD-SPACING: 0px;-webkit-border-horizontal-spacing: 0px;-webkit-border-vertical-spacing: 0px;-webkit-text-decorations-in-effect: none; -webkit-text-size-adjust: auto; -webkit-text-stroke-width: 0px" class=Apple-style-span>如上图所示,在传统的网络拓扑中要实现网络的冗余,一般都会使用双链路上连的方式,而这种方式明显有一个环路,在这种拓扑下都会开起生成树协议,这时就会有一种链路是block 状态的。
所以这种方式实现冗余,并不会增加网络带宽。
如果想用链路聚合方式来做双链路上连到两台不同的设备,port- channel功能又不支持跨设备聚合。
所以在这种背景下就出现了vPC 的概念,和port-channel功能相比区别是:vPC功能解决了传统聚合端口不能跨设备的问题。
思科新一代数据中心级交换机中文配置向导Nexus7000

Nexus Configuration Simple Guide目录Nexu7000缺省端口配置 (2)CMP连接管理处理器配置 (3)带外管理VRF (4)划分Nexus 7010 VDC (5)基于EthernetChannel的vPC (7)割裂的vPC:HSRP和STP (11)vPC的细部配置 (12)Nexus的SPAN (13)VDC的MGMT接口 (13)DOWN的VLAN端口 (13)Nexus的路由 (14)Nexus上的NLB (15)标识一个部件 (15)Nexus7000基本配置汇总 (16)Cisco NX-OS/IOS Configuration Fundamentals Comparison (16)Cisco NX-OS/IOS Interface Comparison (24)Cisco NX-OS/IOS Port-Channel Comparison (30)Cisco NX-OS/IOS HSRP Comparison (35)Cisco NX-OS/IOS STP Comparison (40)Cisco NX-OS/IOS SPAN Comparison (44)Cisco NX-OS/IOS OSPF Comparison (49)Cisco NX-OS/IOS Layer-3 Virtualization Comparison (54)vPC Role and Priority (61)vPC Domain ID (62)vPC Peer Link (62)Configuration for single 10 GigE Card (62)CFSoE (64)vPC Peer Keepalive or FT Link (64)vPC Ports (64)Orphan Ports with non-vPC VLANs (65)HSRP (66)HSRP Configuration and Best Practices for vPC (66)Advertising the Subnet (67)L3 Link Between vPC Peers (67)Cisco NX-OS/IOS TACACS+, RADIUS, and AAA Comparison (68)Nexus5000的配置同步 (73)初始化Nexus 2000 Fabric Module (75)Nexu7000缺省端口配置缺省时所有端口是关闭的no system default switchport shutdowncopy running-config startup-config vdc-all 存配置dir bootflash:dir bootflash://sup-standby/dir bootflash://sup-remoteshow roleshow inventory显示系统详细目录,或称为存货清单,可以看到各组件产品编号以及序列号show hardware 显示系统硬件详细信息show sprom backplane 1 显示交换机序列号show environment power 显示电源信息power redundancy-mode ps-redundant 如果没有双电网供电则使用此模式power redundancy-mode insrc-redundant 如果有双电网供电则使用此模式show module 检验各模块状态attach module slot_numberdir bootflash dir slot0:查看ACTIVE引擎的FLASH空间如果查看备份引擎的FLASH空间呢?首先attach module command to attach to the module number, and then use the dir bootflash: or dir slot0:out-of-service module slot Shutting Down a Supervisor or I/O Moduleout-of-service xbar slot Shutting Down a Fabric Moduleshow environmentshow environment temperatureshow environment fanbanner motd #Welcome to the switch#clock timezoneclock setreload 重启交换机reload module numberswitchto VDC切换至某VDC管理界面switchbackpoweroff module slot_numberno poweroff module slot_numberpoweroff xbar slot_numberCMP连接管理处理器配置CMP配置:You should also configure three IP addresses—one for each cmp-mgmt interface and one that is shared between the active and standby supervisor mgmt 0 interfaces.attach cmp 进入CMP命令输入后自动存盘,不需要copy run start通过NX-OS CLI来配置CMP1. configure terminal2. interface cmp-mgmt module slot 通过module 槽号分别为5/6来实现主备引擎上的CMP配置3. ip address ipv4-address/length4. ip default-gateway i pv4-address5. show running-config cmp通过CMP CLI来配置CMP1. attach cmp2. configure terminal3. ip default-gateway i pv4-address4. interface cmp-mgmt5. ip address ipv4-address/length6. show running-config在CMP上可执行的动作:show cp statereload cpattach cpmonitor cpping or traceroute 192.0.2.15reload system To reload the complete system, including the CMPs带外管理VRFManagement VRF and Basic ConnectivityThe management interface is, by default, part of the management VRF. The management interface “mgmt0” is the only interface allowed to be part of this VRF.The philosophy beyond Management VRF is to provide total isolation for the management trafficfrom the rest of the traffic flowing through the box by confining the former to its own forwarding table.In this step we will:- Verify that only the mgmt0 interface is part of the management VRF- Verify that no other interface can be part of the management VRF- Verify that the default gateway is reachable only using the management VRF如果想Ping 带外网管的网关等地址必须在Ping命令后面加上vrf managementping 10.2.8.1 vrf management划分Nexus 7010 VDCVDC是Nexus7000系列的特色功能。
思科虚拟设备技术白皮书

White PaperTechnical Overview of Virtual Device ContextsThe Cisco® Nexus 7000 Series Switches introduce support for the Cisco NX-OS Software platform, a new class of operating system designed for data centers. Based on the Cisco MDS 9000 SAN-OS platform, Cisco NX-OS introduces support for virtual device contexts (VDCs), which allows the switches to be virtualized at the device level. Each configured VDC presents itself as a unique device to connected users within the framework of that physical switch. The VDC runs as a separate logical entity within the switch, maintaining its own unique set of running software processes, having its own configuration, and being managed by a separate administrator.This document provides an insight into the support for VDCs on Cisco NX-OS.1. Introduction to Cisco NX-OS and Virtual Device ContextsCisco NX-OS is based on Cisco MDS 9000 SAN-OS and has been developed for data center deployments. It incorporates all of the essential Layer 2 and 3 protocols and other key features found in Cisco IOS® Software. Features such as Cisco In Service Software Upgrades (ISSU), superior fault detection, and isolation mechanisms such as Cisco Generic Online Diagnostics (GOLD) and Embedded Event Manager (EEM) as well as a traditional Cisco IOS Software look and feel for configuration purposes are all included. Cisco NX-OS is based on a modular architecture that supports the independent starting and stopping of processes, and supports multi-threaded processes that run in their own protected memory space.The Cisco Nexus 7000 Series inherits a number of virtualization technologies present in Cisco IOS Software. From a Layer 2 perspective, virtual LANs (VLAN) virtualize bridge domains in the Nexus 7000 chassis. Virtualization support for Layer 3 is supported through the concept of virtual route forwarding instances (VRF). A VRF can be used to virtualize the Layer 3 forwarding and routing tables. The virtualization aspect of the Cisco NX-OS Software platform has been extended to support the notion of virtual device contexts (VDCs). A VDC can be used to virtualize the device itself, presenting the physical switch as multiple logical devices. Within that VDC it can contain its own unique and independent set of VLANs and VRFs. Each VDC can have assigned to it physical ports, thus allowing for the hardware data plane to be virtualized as well. Within each VDC, a separate management domain can manage the VDC itself, thus allowing the management plane itself to also be virtualized.The definition of a switch control plane includes all those software functions that are processed by the switch CPU (found on the central supervisor). The control plane supports a number of crucial software processes such as the routing information base, the running of various Layer 2 and Layer 3 protocols, and more. All of these processes are important to the switches interaction with other network nodes. The control plane is also responsible for programming the data plane that enables many hardware-accelerated features.In its default state, the switch control plane runs a single device context (called VDC 1) within which it will run approximately 80 processes. Some of these processes can have other threads spawned, resulting in as many as 250 processes actively running on the system at a time depending on the services configured. This single device context has a number of layer 2 and 3 services running on top of the infrastructure and kernel components of the OS as shown in the following diagram.Figure 1. Default Operating Mode with Single Default VDCThis collection of processes constitutes what is seen as the control plane for a single physical device (that being with no other virtual device contexts enabled). VDC 1 is always active, always enabled, and can never be deleted. It is important to reiterate that even in this default mode, virtualization support via VRF and VLAN is still applicable within the default VDC (or any VDC). This can also be viewed as virtualization nesting. At the higher level, you have the VDC. Within the VDC, you can have multiple VRFs and VDCs. In future software releases, you could potentially have further nested levels with features like MTR within a VRF.The notion of enabling a subsequent (additional) VDC takes these processes and replicates it for each device context that exists in the switch. When this occurs, duplication of VRF names and VLAN IDs is possible. For example, you could have a VRF called manufacturing in one device context and the same “manufacturing” name applied to a VRF in another virtual device context. Hence, each VDC administrator essentially interfaces with its own set of processes and its own set of VRFs and VLANs, which in turn, represents its own logical (or virtual) switch context. This provides a clear delineation of management contexts and forms the basis for configuration separation and independence between VDCs.Figure 2 depicts the major software elements that enable VDCs. In VDC mode, many benefits can be achieved such as per-VDC fault isolation, per-VDC administration, separation of data traffic,and enhanced security. Hardware resources such as physical interfaces can also be divided between VDCs. Support for hardware partitioning is discussed later in this document.Figure 2. VDC ModeThe use of VDC opens up a number of use cases that can provide added benefits for the administrators of this switch. Use cases for VDCs could include:●Offering a secure network partition between different user departments traffic●Provides empowered departments the ability to administer and maintain their ownconfigurations●One key use for VDC is to provide a device context for testing new configuration orconnectivity options without impacting production systems●Consolidation of multiple departments switch platforms into a single physical platform whilestill offering independence from the OS, administration and traffic perspective●Use of a device context for network administrator and operator training purposes2. VDC ArchitectureThe Cisco NX-OS Software platform provides the base upon which virtual device contexts are supported. The following sections provide more insight into the support for VDCs within this software platform.2.1 VDC Architectural LayersIn analyzing the architectural diagram of the system running in VDC mode (see Figure 2 above), it becomes apparent that not all of the architectural elements of the platform are virtualized. Even though not all layers are virtualized, all of the major components have been built with the purpose to support the concept of VDCs.At the heart of the OS is the kernel and infrastructure layer. The kernel is able to support all processes and all VDCs that run on the switch but only a single instance of the kernel will exist at any one point in time. The infrastructure layer provides an interface between the higher layer processes and the hardware resources of the physical switch (TCAM, etc.). Having a single instance of this layer reduces complexity (when managing the hardware resources). Having a single infrastructure layer also helps scale performance by avoiding duplication of this system’s management process.Working under control of the infrastructure layer is a number of other important system processes, which also exist as a unique entity. Of these, the VDC manager is a key process when it comes to supporting VDCs. The VDC manager is responsible for the creation and deletion of VDCs. More important, it provides VDC-related APIs for other infrastructure components such as the system manager and resource manager to perform their own related functions.When a VDC is created, the system manager is responsible for launching all services required for VDC startup that run on a per-VDC basis. As new services are configured, the system manager will launch the appropriate process. For example, if OSPF were enabled in the VDC named Marketing, then the system manager would launch an OSPF process for that VDC. If a VDC is deleted, then the system manager is responsible for tearing down all related processed for that VDC.The resources manager is responsible for managing the allocation and distribution of resources between VDCs. More about this topic is discussed later in this document, but resources such as VLANs, VRFs, PortChannels, and physical ports are examples of resources that are managed by the resource manager.Sitting above the infrastructure layer and its associated managers are processes that run on a per-VDC basis. Each of these processes runs in its own set of protected memory space. Fault isolation is one of the main benefits derived from the use of a VDC. Should a process fail in one VDC, it will not have an effect on processes running in another VDC.2.2 Virtual Device Context Resource AllocationWhen a VDC is created, selected switch resources can be allocated to that VDC, helping ensure that it has exclusive use of that resource. A resource template controls the allocation of resources and defines how much of that resource can be allocated to a VDC. VDC administrators and users within the VDC cannot change this template. Only the super user is able to change this template. The super user is a user with the highest level of authority to invoke changes to the configuration in the switch. The super user exists within the domain of VDC 1 (the default VDC). Aside from being able to assign physical switch resources between device contexts, the super user has the ability to invoke change in any VDC configuration, create and delete VDCs, and create and delete administrators and users for each VDC. The template is administered separately from the switch configuration, which allows the super user to edit a template without affecting the resource allocation for the VDC that the template has previously been applied to. When the super user wants to apply an updated template to a VDC, that person will have to reapply the template so that it is activated, copied, and merged with the running configuration. For transparent backup purposes, merging templates with the configuration adds the benefit of being able to back up all configurations specific to a VDC by simply backing up the primary configuration. Most, but not all, of the switch resources can be allocated to a VDC. Table 1 lists the resources that can be allocated to VDCs and those that cannot be.Table 1. Switch ResourcesSwitch Resources that Can Be Allocated to a VDC Switch Resources that Cannot Be Allocated to a VDCPhysical Interfaces, PortChannels, Bridge Domains and VLANs, HSRP and GLBP Group IDs, and SPAN CPU*, Memory*, TCAM Resources such as the FIB, QoS, and Security ACLs* Future releases may allow allocation of CPU or memory to a VDC.For many of the resources that can be allocated on a per-VDC basis, it is important to note that the resource is typically managed globally. For example, there are 256 Cisco EtherChannel® link bundles per chassis that can be apportioned across the active VDCs. If those 256 Cisco EtherChannel link bundles are consumed by two VDCs, then there are no more link bundles available for any other VDC in the chassis. Configuring the load balancing option for Cisco EtherChannel is a global configuration and cannot be set on a per-VDC basis. Another example is SPAN. There are two SPAN sessions available for the switch. Both VDC A and VDC B can configure a SPAN session as “monitor session 1”; however, internal to the hardware they are recognized as different SPAN sessions. This is again as a direct result of SPAN being managed as a global resource. As with the link bundle example above, once these two sessions are consumed, there are no more SPAN sessions available for other VDCs.The creation of a VDC builds a logical representation of the Cisco Nexus 7000 Series Switch, albeit initially with no physical interfaces assigned to it. Physical switch ports are resources that cannot be shared between VDCs. By default, all ports on the switch are assigned to the default VDC (VDC 1). When a new VDC is created, the super user is required to assign a set of physical ports from the default VDC to the newly created VDC, providing the new VDC with a means to communicate with other devices on the network. Once a physical port is assigned to a VDC, it is bound exclusively to that VDC, and no other VDC has access to that port. Inter-VDC communication is not facilitated from within the switch. A discrete external connection must be made between ports of different VDCs to allow communication between them.Different port types can be assigned to a VDC. These include Layer 2 ports, Layer 3 ports, Layer 2 trunk ports, and PortChannel (Cisco EtherChannel) ports. Note that the ports on the 32 port 10GI/O Module (N7K-M132XP-12) must be allocated to a VDC in port groupings of four ports. The ports on the 48 port 10/100/1000 I/O Module (N7K-M148GT-11) can be allocated on a per-port basis. Logical interfaces such as SVIs that are associated with the same physical interface cannot be allocated to different VDCs in the current implementation. Thus, it is not possible to virtualize a physical interface and associate the resulting logical interfaces to different VDCs. However, it is possible to virtualize a physical interface and associate the resulting logical interfaces with different VRFs or VLANs. Thus, VDCs can be assigned physical interfaces, while VLANs and VRFs can be assigned logical and physical interfaces.An example of this can be seen in Figure 3. Ports 1 through 8 belong to VDC 5 while ports 41 through 48 belong to VDC 10. Within each VDC, ports are further virtualized belonging to either a VLAN or VRF.Figure 3. VDC VirtualizationAfter a port is allocated to a VDC by the root-admin at default-VDC level, it is up to the VDC-admin to manage (configure and use) the previously assigned port. Running other related commands such as a show interface command, for example, will allow the user to see only those interfaces that have been assigned to the VDC.Each VDC maintains its own configuration file, reflecting the actual configuration of ports under the control of the VDC. In addition, the local configuration will contain any VDC specific configuration elements such as a VDC user role and the command scope allocated to that user. Having a separate configuration file per VDC also provides a level of security that protects this VDC from operation configuration changes that might be made on another VDC.VLANs are another important resource that has been extended in Cisco NX-OS. Up to 16,384 VLANs, defined across multiple VDCs, are supported in a Cisco Nexus 7000 Series Switch. Each VDC supports a maximum of 4096 VLANs as per the IEEE 802.1q standard. The new extended VLAN support will allow an incoming VLAN to be mapped to a per-VDC VLAN. We will refer to this per-VDC VLAN as a bridge domain for clarity. In this manner, a VDC administrator can create VLANs numbered anywhere in the 802.1q VLAN ID range, and the VDC will map that newly created VLAN to one of the default 16,384 bridge domains available in the switch. This will allow VDCs on the same physical switch to reuse VLAN IDs in their configurations, while at the OS level the VLAN is in fact a unique bridge domain within the context of the physical switch. For example, VDC A and VDC B could both create VLAN 100, which in turn could be mapped to bridge domains 250 and 251, respectively. Each administrator would use show commands that reference VLAN 100 to monitor and manage that VLAN.3. Scaling Nexus 7000 Switch Resources Using Virtual Device ContextsEach line card uses a local hardware-forwarding engine to perform Layer 2 and Layer 3 forwarding in hardware. The use of VDCs enables this local forwarding engine to optimize the use of its resources for both Layer 2 and Layer 3 operations. The following section provides more detail on this topic.3.1 Layer 2 Address Learning with Virtual Device ContextsThe forwarding engine on each line card is responsible for Layer 2 address learning and will maintain a local copy of the Layer 2 forwarding table. The MAC address table on each line card supports 128,000 MAC addresses. When a new MAC address is learned by a line card, it will forward a copy of that MAC address to other line cards. This enables the Layer 2 address learning process to be synchronized across line cards.Layer 2 learning is a VDC local process and as such has a direct effect on what addresses are placed into each line card.Figure 4 shows how the distributed Layer 2 learning process is affected by the presence of VDCs. On line card 1, MAC address A is learned from port 1/2. This address is installed in the local Layer 2 forwarding table of line card 1. The MAC address is then forwarded to both line cards 2 and 3. As line card 3 has no ports that belong to VDC 10, it will not install any MAC addresses learnt from that VDC. Line card 2, however, does have a local port in VDC 10, so it will install MAC address A into its local forwarding tables.Figure 4. MAC Address LearningWith this implementation of Layer 2 learning, the Cisco Nexus 7000 Series Switch offers a way to scale the use of the Layer 2 MAC address table more efficiently when VDCs are unique to line cards.3.2 Layer 3 Resources and Virtual Device ContextsThe forwarding engine on each line card supports 128,000 entries in the forwarding information base (used to store forwarding prefixes), 64,000 access control lists, and 512,000 ingress and 512,000 egress NetFlow entries.When the default VDC is the only active VDC, learnt routes and ACLs are loaded into each line card TCAM tables so that each line card has the necessary information local to it to make an informed forwarding decision. This can be seen in Figure 5, where the routes for the default “red” VDC are present in the FIB and ACL TCAMs.Figure 5. Default Resource AllocationWhen physical port resources are split between VDCs, then only the line cards that are associated with that VDC are required to store forwarding information and associated ACLs. In this way, the resources can be scaled beyond the default system limits seen in the preceding example. An example is defined in Table 2.Table 2. Resource Separation ExampleVDC Number of Routes Number of Access Control Entries (ACE) Allocated Line Cards10 100,000 50,000 LC 1, LC 320 10,000 10,000 LC 4, LC 830 70,000 40,000 LC 6In this example, the resources would be allocated as shown in Figure 6.Figure 6. Resource SplitThe effect of allocating a subset of ports to a given VDC results in the FIB and ACL TCAM for the respective line cards being primed with the forwarding information and ACLs for that VDC. This extends the use of those TCAM resources beyond the simple system limit described earlier. In the preceding example, a total of 180,000 forwarding entries have been installed in a switch that, without VDCs, would have a system limit of 128,000 forwarding entries. Likewise, a total of100,000 ACE's have been installed where a single VDC would only allow 64,000 Access Control Entries. More important, FIB and ACL TCAM space on line cards 2, 5, and 7 is free for use by additional VDCs that might be created. This further extends the use of those resources well beyond the defined system limits noted here.As with the TCAMs for FIB and ACLs, the use of the NetFlow TCAM is more granular when multiple VDCs are active. Let us assume the same setup as before, where we have a set of line cards, each of which belong to a different VDC.When a flow is identified, a flow record will be created on the local NetFlow TCAM resident on that line card. Both ingress and egress NetFlow are performed on the ingress line card so it is this ingress line card’s NetFlow TCAM where the flow will be stored. The collection and export of flows is always done on a per-VDC basis. No flow in VDC X will be exported to a collector that is part of VDC Y. Once the flow is created in a NetFlow TCAM on line card X, it will not be replicated to NetFlow TCAMs on other line cards that are part of the same VDC. In this manner, the use of the TCAM is optimized.4. Effect of Virtual Device Contexts on Control Plane ProcessesThe previous sections have highlighted that some system resources have global significance and are managed at the global level while other system resources do not have that global significance and are managed at the VDC level. As with these resources, there are certain control plane processes that, when enabled, have global or per-VDC implications. The following section provides some insight into the main control plane processes that have VDC relevance.4.1 Control Plane Policing (CoPP)The switch control plane controls the operation of the switch, and compromising this entity could affect the operation of the switch. Control plane policing provides a protection mechanism for the control plane by rate limiting the number of packets sent to the control plane for processing.Control plane policing is enabled from the default VDC and runs only in the default VDC. Its application, however, is system wide, and any packet from any VDC directed to the control plane is subject to the control plane policer in place. In other words, there is not any VDC awareness that can be used in the policy to police traffic differently depending on the VDC it came from.4.2 Quality of Service (QoS)Unlike control plane policing, quality of service has configuration implications that have either global or per-VDC significance.Policers, which can be used to provide a rate limiting action on target traffic, are an example of a QoS resource specific to a VDC. Even though the policer is a systemwide resource, once configured it will have relevance only to the ports within that VDC. Any QoS configurations specific to a physical port also have significance only to the VDC that the port belongs to. An example of this type of QoS policy is Weighted RED (WRED), which is used to provide congestion management for port buffers.Classification ACLs used to identify which traffic a QoS policy is going to be applied to are another example of a per-VDC resource. These ACLs are configured within a VDC and applied to ports in that VDC. More important, these QoS ACLs will be installed into the ACL TCAM only on those line cards that have ports in that VDC. In this instance, creating more than one VDC can have a positive effect on scaling TCAM resources beyond what is available for a single VDC.Many of the QoS maps that are used to provide services such as CoS- and DCSP-to-queue mapping and markdown maps for exceed and violate traffic are examples of QoS configuration elements that have global significance. DSCP mutation maps, which offer a way to modify the ingress DSCP value, also have global significance. If these mutation- or CoS-to-queue maps are modified, they will affect packets entering all VDCs.4.3 Embedded Event Manager (EEM)Embedded Event Manager is an event-led subsystem that can automate actions based on a certain event occurring. When an event occurs, such as an OIR event or the generation of a certain syslog message, the system can invoke a user-written script (called an applet) that defines a preset list of actions to invoke.An EEM policy (applet) is configured within the context of a VDC. While most events are seen by each VDC, there are some events that can be seen only from by the default VDC. An example of this event type is those events that are generated by the line cards themselves such as a Cisco GOLD diagnostic run result.EEM maintains a log of EEM events and statistics, and this log is maintained on a per-VDC basis. When a policy is configured, only the VDC administrator can configure and administer that policy. VDC users are not able to administer EEM policies.5. Virtual Device Context Fault IsolationWhen multiple VDCs are created in a physical switch, inherently the architecture of the VDC provides a means to prevent failures within that VDC from affecting other VDCs. So, for instance, a spanning tree recalculation that might be started in one VDC is not going to affect the spanning tree domains of other VDCs in the same physical chassis. An OSPF process crash is another example where the fault is isolated locally to that VDC. Process isolation within a VDC thus plays an important role in fault isolation and serves as a major benefit for organizations that embrace the VDC concept.As can be seen in Figure 7, a fault in a process running in VDC 1 does not affect any of the running processes in the other VDCs. Other equivalent processes will continue to run uninhibited by any problems associated with the faulty running process.Figure 7. Per-VDC Fault IsolationFault isolation is enhanced with the ability to provide per-VDC debug commands. Per-VDC logging of messages via syslog is also another important characteristic of the VDC fault isolation capabilities. When combined, these two features provide a powerful tool for administrators in locate problems.The creation of multiple VDCs also permits configuration isolation. Each VDC has its own unique configuration file that is stored separately in NVRAM. There are a number of resources in each VDC whose associated numbers and IDs can overlap between multiple VDCs without having an effect on another VDCs configuration. For example, the same VRF IDs, PortChannel numbers, VLAN IDs, and management IP address can exist on multiple VDCs. More important, configuration separation in this manner not only secures configurations between VDCs but also isolates a VDC from being affected by an erroneous configuration change in another VDC.6. High Availability and Virtual Device ContextsThe Cisco NX-OS Software platform incorporates a high-availability feature set that helps ensure minimal or no effect on the data plane should the control plane fail. Different high-availability service levels are provided, from service restart to stateful supervisor switchover to ISSU without affecting data traffic.Should a control plane failure occur, the administrator has a set of options that can be configured on a per-VDC basis defining what action will be taken regarding that VDC. There are three actions that can be configured: restart, bringdown, and reset. The restart option will delete the VDC and then re-create it with the running configuration. This configured action will occur regardless of whether there are dual supervisors or a single supervisor present in the chassis. The bringdown option will simply delete the VDC. The reset option will issue a reset for the active supervisor when there is only a single supervisor in the chassis. If dual supervisors are present, the reset option will force a supervisor switchover.The default VDC always has a high-availability option of reset assigned to it. Subsequent VDCs created will have a default value of bringdown assigned to them. This value can be changed under configuration control.Stateful switchover is supported with dual supervisors in the chassis. During the course of normal operation, the primary supervisor will constantly exchange and synchronize its state with the redundant supervisor. There is a software process (watchdog) that is used to monitor the responsiveness of the active (primary) supervisor. Should the primary supervisor fail, a fast switchover is enacted by the system. Failover occurs at both the control plane and data plane layers. At supervisor switchover, the data plane continues to use the Layer 2– and Layer 3–derived forwarding entries simply by maintaining the state written into the hardware. For the control plane,。
思科虚拟办公室 (CVO) Cisco 871和Cisco 881路由器家庭或小型办公室设置说明说明

Americas Headquarters:Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706USA Cisco Virtual Office – End User Instructions for Cisco 871 and Cisco 881 Router Set Up at Home or Small OfficeIntroductionThis document describes the end-user instructions to deploy the Cisco Virtual Office (CVO) for home or small office use.Cisco Virtual Office (CVO) solution offers a seamless home/small office experience comparable to working in your company’s central office. CVO features support secure, always-on wired and wireless (WLAN) data connectivity, voice services, and video capabilities.Setup Your CVO HardwareIn this section you will be able to identify the basic hardware configuration needed to install the CVO solution in your home/office. This is a known working configuration to assist you in your initial set-up and is not intended to cover all variations of home/office network environments. This guide is written based on Cisco 871 and Cisco 881 routers.Ports on the CVO RouterIt is important that you understand which ports on the back of your CVO router are used for what purposes.•FE0, FE1, FE2, and FE3: LAN Ports FE0 to FE3 are end-user device secure ports. Connect your PC/Mac/Linux/IP phone equipment here. •FE4: Use the WAN/FE4 port to connect your CVO router to your Internet Service Provider (ISP) device.Cisco Virtual Office – End User Instructions for Cisco 871 and Cisco 881 Router Set Up at Home or Small Office SETUP YOUR CVO HARDWARE How to Connect Your EquipmentThis scenario shows an example of your company’s provided devices and the Internet Service Provider (ISP) device (modem/router) properly connected to a CVO 871W router. The same ports should be used to connect to a CVO Cisco 881W or non-wireless router.For detailed descriptions, see below Step-by-Step Instructions .Figure 1End-to-end View of How Your Devices Should Connect TogetherCONFIGURE YOUR ROUTERStep-by-Step InstructionsFollow these steps to connect your CVO router to the ISP device and to your PCStep1Make sure your ISP device (DSL modem, cable modem, etc) is plugged in and turned on. If your ISP device is already on, power off your ISP device and wait 10 seconds. Remove the cables. Then power itup and wait 30 seconds to complete the reset and reconnect your cables. Plug in your CVO router asshown and power it up. Do not do any type of soft reboot on your ISP devices at this point.Step2Plug the CVO router into the ISP modem/router using an Ethernet cable going from the Ethernet port on the ISP device, to the WAN/FE4 port on the CVO router as shown in Figure1.Step3Plug your PC into the CVO router using the LAN trusted port FE0 as shown in Figure1.Configure Your RouterOnce you have set up your CVO hardware you will need to configure your router so that you can accessthe Internet and your company’s corporate network.After the Internet connectivity is established you need to follow the steps that invoke the Secure DeviceProvisioning (SDP) tool to communicate with your company’s core infrastructure and complete yourCVO router's configuration.Internet ConnectivityThe configuration needed to connect to the Internet is determined by the IP address assignment type.DHCP AssignmentIf you have a DHCP connection, your PC should already be able to access the Internet at this point, noadditional work is needed.Other (PPPoE or Static) AssignmentIf your IP address assignment type is anything other than DHCP some additional configuration isneeded to access the Internet. You must run the Cisco Configuration Professional Express (CCP Express)tool and follow the steps to get the router connected to the Internet before you can proceed. You mustknow what type of connectivity your ISP is providing you, typically PPPoE or static IP. Your ISP shouldbe able to give you this information. Go to “Appendix A: CCP Configuration” in this document andfollow the instructions to get internet access. Once done, return to the “Corporate NetworkConnectivity” section and complete the SDP provisioning process.Corporate Network ConnectivityStep1Test your Internet connection.To double check that your PC is now connected to the Internet, open a browser window and type anyInternet website, for example, .Step2Initiate the Secure Device Provisioning (SDP) Process.Cisco Virtual Office – End User Instructions for Cisco871 and Cisco881 Router Set Up at Home or Small OfficeCisco Virtual Office – End User Instructions for Cisco 871 and Cisco 881 Router Set Up at Home or Small Office CONFIGURE YOUR ROUTERYou will need to complete the process for Secure Device Provisioning (SDP) so that your CVO router can access the corporate network and securely download its configuration.If you are using Static addressing or PPPoE and used CCP Express for the initial configuration of your router, specifying SDP for provisioning, then CCP Express will automatically direct you to the SDP welcome page, where you have to authenticate using the login username/password that you configured during the CCP Express setup (Figure 2).Figure 2SDP AuthenticationIf you’re using DHCP, to initiate the SDP process, go to the PC which is connected to the CVO router and open a browser window. Then type in the address bar: http://10.10.10.1/ezsdd/welcome . You will be prompted to authenticate, and you must use username/password cisco/cisco.You will see the screen shown in Figure 3 while the router prepares for the rest of the SDP process. Figure 3SDP ScreenCisco Virtual Office – End User Instructions for Cisco 871 and Cisco 881 Router Set Up at Home or Small Office CONFIGURE YOUR ROUTERStep 3Securely download the CVO router configuration.When the screen refreshes you will notice a field for site URL . Enter the URL provided by your network administrator (Figure 4).Figure 4URL FieldAfter you click Next you will see a Security Request confirmation window; select Yes to proceed. Step 4Authenticate yourself.When the system attempts to connect to the corporate CVO management server, you are prompted to authenticate yourself. You must use the credentials provided by your network administrator (Figure 5). Figure 5Connect to SDP ServerWhen your authentication is accepted you will see the confirmation screen shown in Figure 6.CONFIGURE YOUR ROUTERFigure6Confirmation ScreenSelect Next to proceed.Step5CVO router auto-configuration.You should now see the enrollment window and your CVO router will automatically download theconfiguration from the CVO management server (Figure7).Note Do not select any of the options on this screen. This will interrupt your CVO routerconfiguration.Please be patient during this process. This can take 5 or more minutes to complete. Any interruption will cause an incomplete deployment.Figure7Enrollment WindowStep6Verify that your CVO router has a VPN Light on in the front.After 5 minutes, your router should have its VPN LED lit solid green.At this point you need to have your PC register with the new router configuration to renew its IP address.You have two options to renew your IP address:a.restart your PC – this will automatically renew its IP addressb.(advanced users) right click on your network adaptor icon in the systray and click repair as show inFigure8:Cisco Virtual Office – End User Instructions for Cisco871 and Cisco881 Router Set Up at Home or Small OfficeCisco Virtual Office – End User Instructions for Cisco 871 and Cisco 881 Router Set Up at Home or Small Office CONFIGURE YOUR ROUTER Figure 8Renew IP AddressOnce you have a valid IP Address, open your browser and attempt to connect to an external Website. This should be something other than your company’s internal home page; e.g. . If this is successful then proceed with testing an internal Website.Step 7Verify connectivity to your company’s corporate network.Once your CVO router’s configuration is complete you will be able to access your company’s internal network via the VPN tunnels that have been created. Before you are allowed to access any internalresources you will have to authenticate in accordance with your company’s corporate policy. Just open a browser in the PC connected to the CVO router and type an internal Website of your company.Congratulations! You are now ready to begin using your Cisco Virtual Office.The CVO router will build a direct connection to the corporate network. Once the CVO router is installed and configured, there is no need to run a VPN client or SSLVPN to be connected to your company network.Please refer to the CVO overview further information about the solution, its architecture, and all of its components.For more details about the Cisco 800 Series Routers please visit/en/US/products/hw/routers/ps380/index.htmlFor additional information about Cisco Configuration Professional (CCP), please visit/en/US/products/ps9422/index.htmlAppendix A: CCP ConfigurationTo start configuring the CVO router with Cisco Configuration Professional Express (CCP Express) make sure the PC is physically connected to CVO router on port FE0. Open an Internet browser and type http://10.10.10.1. When prompted for username/password , please enter: cisco/cisco . CCP Express will guide you to remove or configure a new username/password. The Cisco Configuration Professional (CCP) Express wizards will guide you through the process of configuring your CVO router to connect to the Internet, as described next.1.Figure 9 shows the welcome screen of CCP Express. Click “Next” to start the wizard.Cisco Virtual Office – End User Instructions for Cisco 871 and Cisco 881 Router Set Up at Home or Small Office CONFIGURE YOUR ROUTER Figure 9Welcome Screen2.Enter the desired login credentials and enable password, as well as the hostname and domain namefor the router (Figure 10), then click “Next”.Cisco Virtual Office – End User Instructions for Cisco 871 and Cisco 881 Router Set Up at Home or Small Office CONFIGURE YOUR ROUTER Figure 10Basic Configuration3.Specify “Secure Device Provisioning” as the method for provisioning the router, as SDP will be usedfor the bootstrap config (Figure 11), then click “Next”Cisco Virtual Office – End User Instructions for Cisco 871 and Cisco 881 Router Set Up at Home or Small Office CONFIGURE YOUR ROUTER Figure11SDP for Router Provisioning4.Choose the corresponding IP address assignment method (PPPoE or Static).For PPPoE, select the authentication method (CHAP or PAP), and provide the appropriate credentials provided to you by your ISP (Figure 12)Figure12PPPoEFor Static IP addresses, specify the IP address and subnet mask to be used by the router (Figure13).Figure13Static IP Addresses5.Choose whether or not to create a default route (Figure14), then click “Next”.Figure14Default RouteP Express displays a summary page of the basic configuration that you setup for the router. Click“Finish” to deliver it to the router (Figure15 and Figure16).Figure15Summary Page PPPoECisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of trademarks, go to this URL: /go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.。
Cisco思科数据中心网络架构和设计指南

定义数据中心汇聚层
服务器之间的通信路径
What Types of Server to Server Traffic Will Exist?
Multi-Tier Interaction, Backup, Replication, Cluster Messaging, Storage over IP
DC Core
Packet Magazine: Second Quarter 2005 Designing the Data Center Access Layer
定义集群的服务器
高可用性集群
• Common goal: combine multiple servers to appear as a unified system through special s/w and network interconnects • A 2 Node HA cluster can use a dedicated crossover cable for exchange of data, session state, monitoring… • Two or more servers use a switch to provide the interconnect on an isolated layer 2 segment/VLAN • Examples: MS-Windows 2003 Advanced Server 2003 Cluster Service (MSCS), for Exchange and SQL Servers (up to eight nodes) • Veritas Clustering for HA • L2 Adjacency is required
数据中心服务器群交换架构
思科ISE硬件和虚拟设备要求说明书

思科安全网络服务器3500/3600系列设备和虚拟机要求•思科ISE的硬件和虚拟设备要求,第1页•Amazon Web服务和Azure VMware解决方案上VMware云的思科ISE支持,第11页•思科ISE的虚拟机设备大小建议,第12页•思科ISE部署中的虚拟机磁盘空间要求,第13页•思科ISE的磁盘空间准则,第14页思科ISE的硬件和虚拟设备要求思科身份服务引擎(ISE)可以安装在思科SNS硬件或虚拟设备上。
为了实现可与思科ISE硬件设备相媲美的性能和可扩展性,为虚拟机分配的系统资源应与为思科SNS3500或3600系列设备分配的系统资源相当。
本节列出安装思科ISE所需的硬件、软件和虚拟机要求。
注释强化您的虚拟环境,并确保所有安全更新都是最新的。
思科对于虚拟机监控程序中发现的任何安全问题概不负责。
思科安全网络服务器3500和3600系列设备有关思科安全网络服务器(SNS)硬件设备规范,请参阅思科安全网络服务器产品手册中的“表1:产品规范”。
有关思科SNS3500系列设备,请参阅Cisco SNS-3500系列设备硬件安装指南。
有关思科SNS3600系列设备,请参阅Cisco SNS-3600系列设备硬件安装指南。
注释思科ISE3.1不支持思科SNS3515设备。
有关思科ISE3.1支持的硬件平台的信息,请参阅支持的硬件。
思科ISE 的VMware 虚拟机要求思科ISE 支持以下VMware 服务器和客户端:•适用于ESXi 6.5及更高版本的VMware 版本11(默认)•适用于ESXi 7.x 的VMware 版本13(默认)您可以使用VMware 迁移功能在主机之间迁移虚拟机(VM)实例(运行任何角色)。
思科ISE 支持热迁移和冷迁移。
•热迁移也称为实时迁移或vMotion 。
热迁移期间无需关闭或关闭思科ISE 。
您可以在不中断其可用性的情况下迁移思科ISE VM 。
•思科ISE 必须关闭并关闭电源才能进行冷迁移。
Cisco云计算平台设计方案

Cisco云计算平台设计方案Cisco云计算平台设计方案随着云计算技术的快速发展,云计算平台成为了企业构建高效、灵活IT系统的核心组件。
Cisco作为全球领先的网络解决方案提供商,致力于为企业提供稳定、安全的云计算平台。
本文将介绍Cisco云计算平台的设计方案,包括网络拓扑结构、虚拟化技术、安全措施以及测试与优化等方面。
1、确定主题Cisco云计算平台设计方案的主题为:为企业构建高效、灵活的IT 系统,满足企业的业务需求。
其中,设计的重点在于确保平台的稳定性、安全性和可扩展性。
2、整理思路首先,需要明确云计算平台的设计目标。
这些目标包括提供稳定、高效的IT系统,满足企业的业务需求;采用虚拟化技术,提高硬件资源的利用率;实施安全措施,保障数据和业务的安全;以及设计可扩展的系统,方便未来升级和扩展。
其次,针对以上目标,我们需要整理出详细的设计方案。
这包括选择合适的网络拓扑结构、采用虚拟化技术进行资源管理、通过安全措施确保系统安全以及设计可扩展的系统架构。
最后,需要对设计方案进行详细规划和实施。
这包括规划网络拓扑、设计虚拟化环境、实施安全措施以及进行系统测试和优化等。
3、撰写开头Cisco云计算平台设计方案旨在为企业构建高效、灵活的IT系统,以满足企业的业务需求。
本文将介绍Cisco云计算平台的设计方案,包括网络拓扑结构、虚拟化技术、安全措施以及测试与优化等方面。
我们将通过分析这些关键要素,阐述如何实现云计算平台的高效设计和实施。
4、设计云平台架构首先,在确定网络拓扑结构时,我们选择了层次化的设计。
这种设计能够将网络流量分担到不同的层次,降低核心层网络的负载,从而提高整个网络的性能。
同时,层次化的设计还有利于管理和维护网络设备。
其次,在虚拟化技术方面,我们采用了Cisco的UCS(Unified Computing System)刀片服务器。
这种服务器具有高度的可扩展性和灵活性,能够满足企业的业务需求。
思科IPS产品线安装部署指南V3

思科IPS 设备配置部署简述目录1 概述 (3)2 IPS 4200典型工作模式 (4)2.1 IPS 4200 IDS 工作模式部署步骤 (6)2.1.1 IDS 4200 IDS模式部署图例 (6)2.1.2 配置IPS初始化安装 (7)2.1.3 配置业务承载交换机 (7)2.1.4 配置IDM访问 (8)2.1.5 配置IPS 4200软件升级 (11)2.1.6 配置IPS 4200接口采集信息 (15)2.1.7 配置IPS 4200与网络设备联动 (16)2.1.8 配置IPS 4200与网络设备联动策略执行 (19)2.1.9 观察IPS 4200联动效果 (22)2.1.10 使用IEV管理IPS 4200 (22)2.2 IPS 4200 IPS 工作模式部署步骤 (25)2.2.1 Inline 工作模式结构图 (25)2.2.2 Inline模式配置步骤 (26)3 NM-CIDS IDS部署步骤 (29)3.1 NM-CIDS 模式部署图例 (31)3.2 安装NM-CIDS (31)3.3 初始化配置NM-CIDS (32)3.4 配置IDM访问 (33)3.5 配置NM-CIDS软件升级 (35)3.6 配置NM-CIDS接口采集信息 (38)3.7 配置NM-CIDS与网络设备联动 (39)3.8 观察NM-CIDS联动效果 (42)4 IOS IPS部署步骤 (43)4.1 ISR IOS IPS模式部署图例 (43)4.2 ISR IOS IPS部署概述 (43)4.2.1 配置ISR路由器更新软件 (43)4.2.2 配置ISR路由器SDF文件 (43)4.2.3 配置ISR路由器启用IPS功能 (44)4.2.4 检查配置 (46)4.3 ASA/PIX IOS IPS部署概述 (48)4.3.1 配置ASA/PIX防火墙启用IPS功能 (48)4.3.2 检查配置 (49)5 ASA AIP IPS部署步骤 (50)5.1 配置AIP-IPS初始化安装 (50)5.2 配置ASDM 访问IPS (51)5.3 配置ASA 重定向流量到IPS模块 (53)5.5 调整AIP-IPS 策略 (56)6 C6K IDSM部署步骤 (60)6.1 IDSM-2 Inline模式数据流图解 (60)6.2 确认IDSM-2 模块 (60)6.3 IDSM-2 模块和Catalyst 6500 关联配置 (62)6.4 IDSM-2 IPS 配置 (64)7 CSA 主机IPS/IDS部署步骤 (64)7.1 CSA 终端安全防护软件功能概述 (64)7.2 CSA 5.1 安装需求 (64)7.3 CSA 5.1 扩展功能总结 (65)7.3.1 禁止客户端卸载CSA、关闭CSA、停止CSA服务 (65)7.3.2 禁止客户端修改CSA安全级别 (69)7.3.3 管理可移动介质的使用:光驱、软驱、U盘 (71)8 IPS与MARS集成部署概要 (72)8.1 配置MARS 管理IPS 4200 (72)8.2 配置MARS IPS监控的网段 (73)8.3 检查配置结果 (74)8.4 观察网络结构图 (75)8.5 检测攻击拓扑 (76)9 IPS 6.0 新特性部署指南 (77)9.1 升级过程描述 (77)9.2 新增特性说明-虚拟Sensor (80)9.2.1 特性功能说明 (80)9.2.2 拓扑结构图 (81)9.2.3 实施部署说明 (82)9.3 新增特性说明-异常流量检测 (89)9.4 新增特性说明-与CSA MC联动 (93)9.5 新增特性说明-OS 系统识别 (95)1 概述很多人在使用和配置IPS系列产品中遇到很多问题,甚至怀疑系列产品的功能及作用,其实这个产品的功能及特性勿庸置疑!只是如何利用好这个强大的产品真正的帮助最终用户解决问题才是目前的重点, 特此撰写一篇关于IPS实施部署指南的文章,供大家参加。
思科模拟器学习教程

这是公司针对其CCNA认证开发的一个用来设计、配置和故障排除网络的模拟软件。使用者自己创建网络拓扑,并通过一个图形接口配置该拓扑中的设备。软件还提供一个分组传输模拟功能让使用者观察分组在网络中的传输过程。
适合新手学习CCNA用
具有真实的操作界面
官方地址:直接打开连接好像不行 不过可以通过讯雷的新建任务把连接复制进去就可以了:
PC0
PC1
PC2
PC3
Step 2
Verify that the network is working. All the link lights should be green if the connections are correct. If not, start troubleshooting the network.
三、ACL实例全程讲解
下面让我们自己做一个试验
首先,知道TOPO,明白需求
拿CCNA考试的ACL做例子吧试验
题目要求只允许主机 C 能访问 Finace Web Server 的 Web 服务,阻止局域网的其他主机访问此台的 Web 服务,其他所有流量全部允许通过;在 Corp1 上建立一个由三条语句组成的列表完成以上需求。
桌面出现快捷方式然后运行本程序出现下面的界面1最上面的还是和一些其他的软件一样新建打开保存之类的2中间的白框是工作区域你操作就是在这个框里面操作的3框右边是圈划设备移动设备删除设备之类的注意那个信封以后要是查看包的传输路径主要是看这个4左下面是自己搭建topo时可以随意的添加以下的设备点着左边的router右边就会出现可用的所有router设备的类型列表如下在这里我主要强调下那个连线的问题这里面的线分为直连线交叉线级连线dce和dte线等连接不同的设备请选用合适的线否则通信不了是很正常的
思科 ISE 网络部署 网络配置和部署指南说明书

思科ISE中的网络部署•Cisco ISE网络架构,第1页•Cisco ISE部署术语,第1页•分布式部署中的节点类型和角色,第2页•独立和分布式ISE部署,第3页•分布式部署方案,第3页•小型网络部署,第4页•中型网络部署,第5页•大型网络部署,第6页•每个部署模式的最大支持会话数,第8页•支持Cisco ISE功能所需的交换机和无线局域网控制器配置,第10页Cisco ISE网络架构Cisco ISE架构包括以下组件:•节点和角色类型•Cisco ISE节点-Cisco ISE节点可以承担以下任意或所有角色:管理、策略服务、监控或pxGrid•网络资源•终端策略信息点表示外部信息传达给策略服务角色所在的点。
例如,外部信息可以是轻量级目录访问协议(LDAP)属性。
Cisco ISE部署术语本指南在讨论Cisco ISE部署方案时使用以下术语:定义术语角色提供的特定功能,例如网络访问、分析、状态、安全组访问、监控和故障排除。
服务单个物理或虚拟思科ISE 设备。
节点思科ISE 节点可以承担下列任何角色:管理、策略服务、监控节点类型确定节点提供的服务。
思科ISE 节点可以承担以下任一或全部角色:。
通过管理用户界面可使用的菜单选项取决于节点承担的角色和人员。
角色确定节点是独立节点、主要节点还是辅助节点,并且仅适用于管理和监控节点。
角色分布式部署中的节点类型和角色Cisco ISE 节点可以根据它承担的角色提供各种服务。
部署中的每个节点均可承担管理、策略服务、pxGrid 和监控角色。
在分布式部署中,您可以在网络中使用以下节点组合:•实现高可用性的主要和次要管理节点•实现自动故障切换的监控节点对•实现会话故障切换的一个或多个策略服务节点•pxGrid 服务的一个或多个pxGrid 节点管理节点通过具有管理角色的Cisco ISE 节点,您可以在Cisco ISE 上进行所有管理操作。
它处理与诸如身份验证、授权和记帐等功能有关的所有系统相关配置。
思科HyperFlex超融合平台部署手册
思科HyperFlex 超融合平台部署手册目录1概述 (3)1.1准备 (3)1.2安装 (3)1.3优化 (3)2安装前准备 (4)2.1规划安装参数 (4)2.1.1网络拓扑图 (4)2.1.2带外管理信息 (4)2.1.3外联设备信息 (6)2.1.4VLAN信息规划(请注意,各种设备都会有保留的VLAN段,请不要采用这些VLAN段) (9)2.1.5IP和Host信息规划 (10)2.2下载所需软件 (13)2.3上联交换机设置 (14)2.3.1单台交换机 (15)2.4部署vCenter/HX Installer/NTP/NDS (16)2.4.1部署物理服务器 (16)2.4.2部署vCenter (16)2.4.3部署DNS/NTP (17)2.4.4部署HX Installer (18)2.5初始化Hyperflex系统(UCSM初始化配置) (20)2.5.1FI初始化(略) (20)2.6检查UCS Firmware版本 (21)2.6.1进入HX Installer (22)2.6.2分步安装Service Profile (22)2.6.3进入KVM检查ESXi版本 (30)2.7ESXi版本升级(可选) (30)2.7.1上联交换机设置再确认一下MTU/Port Channel/Trunk Allowed VLAN (30)2.7.2UCSM拓扑是否都发现了 (31)2.7.3可以访问Installer web GUI,vCenter web client和UCSM (31)2.7.4Installer 可以ping通 vCenter和FI带外管理端口 (31)2.7.5Installer是否可以访问HX Management网段 (31)2.7.6从Installer是否可以访问NTP/DNS服务 (31)3安装步骤 (32)3.1进入HX Installer界面 (32)3.2输入参数(JSON文件导入方式) (37)3.3输入参数(手工输入) (38)3.3.1输入UCSM/vCenter和ESXi登录信息 (39)3.3.2选择被发现的并且是HX Server Node的服务器 (39)3.3.3输入UCSM 信息创建Service Profile (40)3.3.4输入Hypervisor信息配置ESXi (41)3.3.5输入HX Cluster IP地址规划信息 (41)3.3.6输入HX cluster配置信息 (41)3.3.7输入HX Cluster其他配置信息 (42)3.3.8保存一下配置参数为JSON文件 (43)3.4安装Hyperflex (43)3.4.1UCSM配置阶段 (44)3.4.2安装HXDP软件和生成Cluster阶段 (48)3.4.3安装完毕 (49)3.4.4安装失败如何办 (49)3.5安装后检查 (49)3.5.1再保存一次JSON配置 (49)3.5.2vCenter HX Plugin是否安装 (49)3.5.3通过HX plugin创建Data Store (50)4安装后优化 (51)4.1运行Post install脚本 (51)4.2DRS配置 (52)4.3VM Network和其他Network的VLAN配置 (54)4.4测试一下是否可以建虚机 (56)4.5测试一下HX Plugin Snapshot功能 (57)4.6测试一下HX Plugin Clone功能 (58)5附录 (58)5.1升级UCS Firmware步骤 (58)5.2升级ESXi 步骤 (61)5.3创建一个临时Service Profile和IP Pool (70)5.3.1IP Pool创建 (70)5.3.2创建一个Service Profile Template (70)5.3.3生成service profile (71)5.4分步安装 (73)5.5万一安装报错如何办 (74)5.5.1网络连接??? (74)5.5.2一般报错的处理方法 (74)5.5.3输入参数错误 (74)5.5.4没有发现HX Server Node包含SAS Controller (74)5.5.5IP Pool地址冲突 (75)5.5.6MTU检查错误 (75)5.5.7登录CVM错误 (76)5.5.8SSO报错 (77)5.5.9vCenter配置host报错 (79)5.5.10HX Plugin在vCenter中显示不出来 (79)5.5.11在“format disk”节点报错 (80)5.5.12节点安装软件报错 (82)1概述1.1准备1.规划HX安装参数信息,包括IP/VLAN/Account等信息,这些信息在运行HX安装脚本时和其他设置时需要。
CISCO之VSS技术和配置
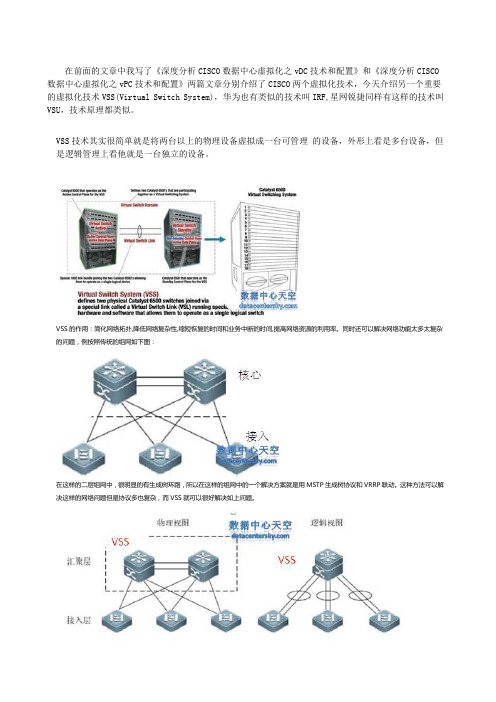
在前面的文章中我写了《深度分析CISCO数据中心虚拟化之vDC技术和配置》和《深度分析CISCO 数据中心虚拟化之vPC技术和配置》两篇文章分别介绍了CISCO两个虚拟化技术,今天介绍另一个重要的虚拟化技术VSS(Virtual Switch System),华为也有类似的技术叫IRF,星网锐捷同样有这样的技术叫VSU,技术原理都类似。
VSS技术其实很简单就是将两台以上的物理设备虚拟成一台可管理的设备,外形上看是多台设备,但是逻辑管理上看他就是一台独立的设备。
VSS的作用:简化网络拓扑,降低网络复杂性,缩短恢复的时间和业务中断的时间,提高网络资源的利用率。
同时还可以解决网络功能太多太复杂的问题,例按照传统的组网如下图:在这样的二层组网中,很明显的有生成树环路,所以在这样的组网中的一个解决方案就是用MSTP生成树协议和VRRP联动。
这种方法可以解决这样的网络问题但是协议多也复杂,而VSS就可以很好解决如上问题。
上图可以看到在物理拓扑看来网络环境和普通网络环境搭建没有区别,但是实际上从逻辑面上看两台物理设备已经虚拟成一台设备,对接入层设备而言两个核心设备实际就是一台设备。
这样VSS就解决了上链带宽增加,又可以不使用MSTP+VRRP方案,简化管理减少网络协议的同时又可以加快收敛性能。
实现网络系统虚拟化,提供机箱间的状态化切换(SSO),改进无中断通信,切换时间〈200ms;跨机箱EtherChannel,优化路径选择。
虚拟交换系统技术是通过一条特殊的链路来绑定两个机箱成为一个虚拟的交换系统,这个特殊的链路称之为虚拟交换机链路(Virtual Switch Link,VSL)。
经过主机箱处理的协议报文,通过VSL转发到从机箱。
VSS在控制层面上两个交换机有主从之分,但在数据面上处理是双活的。
虚拟交换系统允许合并两个交换机成为一台无论是从网络控制层面和管理视图上在网络上都是一个单独的设备实体。
对于邻居,这个虚拟交换系统相当于一台单独的交换机或者路由器。
服务器常用的三种虚拟化技术介绍

虚拟化技术优势与挑战
优势
虚拟化技术可以提高硬件资源的 利用率、降低能耗、减少硬件成 本、提高业务灵活性和快速响应 能力。
挑战
虚拟化技术也面临着安全性、性 能损耗、管理复杂性等方面的挑 战,需要采取相应的措施进行管 理和优化。
02
CATALOGUE
第一种虚拟化技术:全虚拟化
全虚拟化技术原理及特点
04
CATALOGUE
第三种虚拟化技术:容器化技术
容器化技术原理及优势分析
原理
容器化技术是一种轻量级的虚拟化技术,它通过将应用程序及其依赖项打包到一个可移植的容器中, 实现应用程序的快速部署和一致性运行环境。
优势
相比于传统虚拟化技术,容器化技术具有更高的资源利用率、更快的启动速度和更好的可移植性。同 时,容器之间相互隔离,保证了应用程序的安全性和稳定性。
轻量级应用部署
对于轻量级的应用部署,如Web服务器或数据库服务器,LXC等容器化技术可能是一个更 好的选择,因为它们具有较低的资源占用和快速的启动时间。
未来发展趋势预测和新技术展望
容器化技术的进一步发展
随着Docker和Kubernetes等容器化技术的广泛应用,未来容器化技术将继续发展并优化,以更好地满足各 种应用场景的需求。
应用于企业级虚拟化环境。
KVM
KVM是基于Linux内核的虚拟化技 术,具有开源、免费、性能优异等 特点,适用于多种场景下的虚拟化 需求。
Hyper-V
Hyper-V是微软推出的全虚拟化产 品,与Windows操作系统深度集成 ,易于管理和部署,适用于 Windows平台下的虚拟化应用。
全虚拟化技术实施步骤与注意事项
3. 关闭不必要的虚拟机和 服务;
思科虚拟无线控制器部署指南(7.5版本)

思科虚拟无线控制器部署指南(7.5版本) Contents简介 (2)准备条件 (3)在ISR-G2的UCS-E模块上部署虚拟无线控制器。
(5)加载ISR-G2镜像 (6)为UCS-E下载定制化的VMWare Hypervisor镜像。
(7)在UCS-E模块上安装VMware Hypervisor 镜像 (9)在UCS-E模块上安装VMware Hypervisor镜像 (15)为WMware vSphere Hypervisor指定网络和静态IP地址 (21)在UCS-E模块上安装虚拟无线控制器 (25)在ISR-G2的服务就绪引擎SRE 710/910的模块上部署虚拟无线控制器 (25)下载SRE服务模块的软件包 (26)为SRE服务模块提取软件文件 (27)配置SRE服务模块接口 (29)开始SRE服务模块上的Hypervisor安装脚本 (29)连接到ISR G2 上SRE710/910上的Hypervisor (31)在SRE服务模块上安装虚拟无线控制器 (33)附录 (33)参考资料- 使用UCS-E控制台接入命令行界面选项 (36)简介在7.3版本之前,无线控制器软件要运行在需要购买的专门硬件上。
现在虚拟无线控制器(vWLC)软件可以运行在符合虚拟化基础设施行业标准的一般硬件上。
vWLC对有虚拟化基础架构并且需要自建无线控制器的中小型部署非常理想。
分布式分支场景也能从一个集中式部署的虚拟无线控制器受益(较少分支,上限200)。
本文档是vWLC基于CUWN7.5软件版本的更新。
vWLC并非要替代基于硬件芯片的无线控制器。
vWLC的功能和特性为有虚拟化基础架构的数据中心提供了部署上的优势和无线控制器服务的收益。
vWLC的优势:•基于需求的硬件选择灵活性。
•减少开销,空间要求以及其他的日常管理费用,因为许多机箱可以被一个运行许多实例比如无线控制器、网络管理设备(NCS)和其他服务器(ISE,MSE,VSG/firewall)的硬件设备代替。
FusionSphere-OpenStack部署配置指南

AZ间不允许共享,每套blockstorage-driver对接一套存储,默认部署 一套blockstorage-driver 使用FusionStorage分布式存储服务时需要部署,默认每个节点都部 署
AZ间不允许共享,每个AZ都需要部署swift,默认部署3个实例
OpenStack部署方案2 - 3Controller
Sys-server controller
auth zookeeper
image router measure database Sys-client compute Blockstorag e driver
FM VM
baremetal rabbitMQ
在WEB UI的配置界面选择配置网络
配置物理网络
系统默认创建一个物理网络,系统平面默认承载在该物理网络上,用户 可根据实际情况新增物理网络
第22页
配置物理网络 (2/3)
配置物理网络和网口的映射关系
第23页
配置物理网络(3/3)
配置系统平面和物理网络的对应关系
external_api和external_om默认承载在默认的物理网络上,用户可 根据 实际情况调整:
第6页
角色介绍 (2/2)
database:提供OpenStack管理数据存储服务 mongodb:提供OpenStack采样数据存储服务 zookeeper:提供分布式集群服务 rabbitMQ:提供分布式通信服务 baremetal :提供裸机管理服务 loadbalancer:提供网络负载均衡能力 sys-client:提供配置代理和组件状态监控的能力
swift
host3
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
思科DC虚拟化技术和部署指南解析思科数据中心虚拟化技术和部署数据中心的发展正在经历从整合,虚拟化到自动化的演变,基于云计算的数据中心是未来的更远的目标。
整合是基础,虚拟化技术为自动化、云计算数据中心的实现提供支持。
数据中心的虚拟化有很多的技术优点:可以通过整合或者共享物理资产来提高资源利用率,调查公司的结果显示,全球多数的数据中心的资源利用率在15%~20%之间,通过整合、虚拟化技术可以实现50%~60%的利用率;通过虚拟化技术可以实现节能高效的绿色数据中心,如可以减少物理设备、电缆,空间、电力、制冷等的需求;可以实现对资源的快速部署以及重部署以满足业务发展需求。
数据中心虚拟化的简单示意图。
数据中心的资源,包括服务器资源、I/O 资源、存储资源组成一个资源池,通过上层的管理、调度系统在智能的虚拟化的网络结构上实现将资源池中的资源根据应用的需求分配到不同的应用处理系统。
虚拟化数据中心可以实现根据应用的需求让数据中心的物理IT资源流动起来,更好的为应用提供资源调配与部署。
数据中心虚拟化发展的第一个阶段是通过整合实现服务器和应用的虚拟化服务,这阶段的数据中心也是很多公司已经做的或正要做的。
在这一阶段,数据中心虚拟化实现的是区域内的虚拟化,表现为数据中心的服务如网络服务、安全服务、逻辑服务还是与物理服务器的部署相关联;虚拟机上的VLAN与网络交换层上的VLAN对应;存储LUN以类似映射到物理服务器的方式映射到虚拟机。
如下图。
数据中心虚拟化发展的第二个阶段是通过虚拟主机迁移技术(VM’s Mobility)实现跨物理服务器的虚拟化服务。
如下图。
在这个阶段,实现了数据中心内的跨区域虚拟化,虚拟机可以在不同的物理服务器之间切换,但是,为满足虚拟机的应用环境和应用需求,需要网络为应用提供智能服务,同时还需要为虚拟化提供灵活的部署和服务。
思科在下一代的数据中心设计中采用统一交换的以太网架构,思科数据中心统一交换架构的愿景图如下。
改进之前的数据中心物理上存在几个不同的网络系统,如局域网架构、SAN网络架构、高层的计算网络架构、管理控制网络架构,各个网络上采用的技术不同,如局域网主要采用以太网技术,SAN网络主要采用Fiber Channel技术。
而在思科的下一代统一交换架构数据中心中,数据中心的服务器资源、存储资源、网络服务等都通过统一的交换架构连接在一起,数据中心只有一个物理网络架构,可以实现动态的资源调配,提升效率和简化操作。
统一交换架构下数据中心的虚拟化如下图。
统一交换架构下数据中心虚拟化简化了数据中心的管理和运维,实现了真正的任意IT资源之间的灵活连接,实现了统一的I/O,在统一的I/O上可以实现最新的万兆网、无丢失(FCoE)、低延时的数据中心以太网技术。
统一交换架构下数据中心虚拟化为未来的进一步的虚拟化和基于云计算的数据中心提供了平台。
数据中心虚拟化架构包括数据中心前端虚拟化、服务器虚拟化、数据中心后端虚拟化。
如下图。
思科设计数据中心时采用分层、分区的设计方式,层次设计包括核心层、汇聚层、接入层,接入层的不同功能的服务器位于不同的区域,服务器经过每个区域的汇聚层连接到核心层。
数据中心前端虚拟化是指对服务器网络接口之前的数据中心基于以太网的网络架构的虚拟化。
服务器虚拟化指在一台物理服务器上为多个应用需求实现多个虚拟机,并且实现区域内资源的动态调配、迁移,服务器虚拟化技术的实现需要网络的支持配合。
数据中心后端虚拟化指通过虚拟化技术将服务器和存储资源更好的调配使用起来。
下面按数据中心层次化设计中的核心层、汇聚层、接入层依次介绍思科在前端虚拟化上的最新的一些技术实现。
思科数据中心核心层虚拟化技术。
思科为数据中心级和园区骨干网级网络提供了Nexus交换机网络技术和Nexus系列产品。
Nexus系列产品中采用了VDC(Virtual Device Content)技术,可以将一台物理交换机逻辑上模拟成多台虚拟交换机,如下图模拟出的两个虚拟交换机VDC1和VDC2。
VDC技术可以实现每个模拟出的VDC 都拥有它自身的软件进程、专用硬件资源(接口)和独立的管理环境,可以实现独立的安全管理界限划分和故障隔离域。
VDC技术有助于将分立网络整合为一个通用基础设施,保留物理上独立的网络的管理界限划分和故障隔离特性,并提供单一基础设施所拥有的多种运营成本优势。
VDC可以实现故障域隔离,如下图。
一个VDC为所有的运行在它上面的进程建立故障隔离域,如图中VDC B中的“DEF”进程发生故障后不会影响到VDC A中的“DEF”进程。
VDC的端口分配如下图。
端口分配到各VDC后不能在VDC之间共享,一旦某一端口分配到一个VDC,就只能在那个VDC中对该端口进行配置。
(*注上图中右下角应为VDC D)。
VDC 资源使用示意图一如下。
在一个VDC中的MAC 地址只会广播到有接口分配到该VDC 上的Linecard地址表中,如图中的Linecard 1和Linecard 2,它们都有接口分配到VDC 10。
VDC 资源使用示意图如下。
Linecard 1和Linecard 2都给VDC-2分配了100k的FIB TCAM和50k的ACL TCAM资源。
VDC安全分区技术应用如下图。
最上面的两个模型是现在应用的比较多的,但用户可能希望能实现中间的内外分明的架构,这可以通过最下面的两个VDC的应用来实现,其中一个VDC为Outside,另一个为Inside,之间通过防火墙连接。
每个VDC可以运行独立的转发机制、路机制、管理机制和登录机制。
VDC可以实现数据中心设计的水平整合,如下图。
当两个汇聚区不是很大时可以通过将一个Nexus设备划分为VDC 1和VDC 2来分别代替实现两个汇聚区。
VDC实现数据中心设计的垂直整合,如下图。
一个Nexus 设备模拟成Core VDC 和Agg VDC分别实现核心层和汇聚层功能。
VDC实现数据中心设计水平和垂直的综合的整合应用,如下图。
vPC(virtual Port-Channel)技术。
下图是传统的和使用了vPC技术的交换机互联逻辑拓扑图。
vPC技术可以在Cisco Nexus 7000系列产品上实现。
传统的技术实现交换机互联时,如果互联结构中存在环路,则会block环路中的部分支路。
vPC技术可以实现在单个设备上使用port-channel连接两个上行交换机,完全使用所有上行链路的带宽,并消除STP blocked ports,在link/device失效下提供快速收敛。
VPC设计和传统设计相比的优势如下图。
虚拟交换系统VSS(Virtual Switch System)。
两台Cisco Catalyst 6500系列交换机通过VSS 连接后可以实现如同操作单一逻辑交换机的效果。
如下图。
虚拟交换系统VSS与vPC技术有一些不同的地方,如在控制层面上两个交换机有主次之分,但在数据处理上是双活的。
6500-VSS应用于数据中心接入:不再需要复杂的、难于诊断的STP;可以简化管理,实现一个管理点,一个路和STP节点;系统总带宽提升至。
6500-VSS应用于核心/汇聚层:实现网络系统虚拟化;提供机箱间的状态化切换(SSO),改进无中断通信,切换时间〈200ms;跨机箱EtherChannel,优化路径选择。
VSS和vPC技术比较如下图。
ACE模块,实现服务器负载均衡和SSL,可以将一个物理设备虚拟成不同的功能区域,虚拟的功能区有独立的配置文件、路表、应用规则设置等。
防火墙模块FWSM,可实现最多250个虚拟防火墙。
虚拟局域网VLANs需要时可以共享,如上图左边的VLAN 10,各虚拟防火墙可以有各自的策略设置。
虚拟技术联合应用示例如下图。
VSS 技术框架下ACE和FWSM模块设计示例如下图。
汇聚层网络服务的部署设计。
数据中心接入层的可选设计有Top of Rack(架顶)和Middle of Row(列头),如下。
架顶式,一个机柜中一台或两台交换机连接1-RU(1机架单元,如20台)服务器。
列头式,可用于服务器占用空间较大时,交换机集中放置。
采用Nexus 5000做控制中心可控制多台远端Nexus 2000,联合使用效果图如下。
部署Nexus 2000的物理拓扑结构。
逻辑拓扑结构。
前端网络虚拟化技术各层面的简单汇总如下。
服务器虚拟化服务器虚拟化有全部虚拟化、部分虚拟化、应用虚拟化三个发展需求,如下图。
在服务器VMotion(虚拟机迁移)过程中存在以下的问题:VMotion可以跨网络动态迁移虚拟机,管理策略上如何适应;无法察看本地交换流量和为其设定策略;无法识别一条物理链路上多个虚拟机的流量。
Cisco VN-Link技术针对这些问题实现:将网络延伸到服务器虚拟机;提供一致的连接服务;协调、统一的管理。
VN-Link将网络交换延伸到服务器虚拟机,在服务器虚拟机的迁移过程中网络信息将伴随迁移。
VN-Link 技术实现基于策略的虚拟机连接、网络与安全技术的移动、不间断的运行模式,示意图如下。
在虚拟机资源的迁移中,需要一起移动DRS,SW 升级文件/补丁,硬件错误记录等。
VN-Link能实现网络的虚拟迁移,虚拟机的安全防护,保留之前的连接状态等。
Cisco Nexus 1000V是思科最新的基于VN-Link技术的软件,也是业界首个第三方软件交换机,提供VN-Link特性,确保在VMotion过程中虚拟机的可视性和连通性。
后端虚拟化的主要内容如下图。
包括虚拟化服务器、HBAs,统一输入输出/Fabrics、存储等。
后端虚拟化可以优化资源的使用、增加灵活性和敏捷能力、简化管理、减少TCO。
传统的基于应用/部门的SAN存储网络的架构如下图。
总体上看各个SAN网络如一座座的孤岛,每个岛上的端口都过量,需要管理大量的交换机,并且他们的资源无法共享。
整合的VSAN存储网络架构如下图。
它是一个供所有应用系统使用的公用存储网络,能够做到:最大化端口利用率,无需多余扩展端口;减少整体交换设备数量,降低管理复杂度;更灵活的配置存储资源,提高资源利用率;为未来的存储虚拟化打下基础。
VSAN技术的工作原理和流程如下。
VSAN实现不需要端设备的特殊支持,SAN交换机会在输入输出数据时添加和去除表明数据属性的标签,实现基于硬件层面上的不同VSAN流量的隔离,SAN交换机中的Fibre Channel为不同的VSAN数据提供服务,如图中的蓝色和红色。
N-Port ID 虚拟化技术(NPIV)能将一个HBA卡接口虚拟成多个接口,相应的,在交换机上也有多个对应接口,如下图。
虚拟的N-Port能为同一个VSAN的不同数据(如E-Mail,Web)提供独立接口,并且可以在应用层面上实现对各虚拟接口的存取控制、域控制、端口安全控制等。
