CCNA3 思科第三学期 v3.0 ESwitching Chapter 6最新答案
思科CCNA第三学期官方试题(完整版)[有答案解析]
![思科CCNA第三学期官方试题(完整版)[有答案解析]](https://img.taocdn.com/s3/m/d3a11424f18583d0496459c9.png)
参加考试 - ESwitching Final Exam - CCNA Exploration: LAN 交换和无线 (版本 4.0)剩余时间正在显示第 1 页,共 4页下一页>页跳转<上一页1 以下哪项参数用于唯一标识一个无线网络,使其与其它网络区分开来?SSID OFDMWEPDSSS2 分层网络模型具有哪三项优点?(选择三项。
)带宽争用现象减少物理布局范围减小网络的容错能力提高无需配线间无需第三层功能管理和故障排除工作简化3在将 Catalyst 交换机迁移到其它 VTP 管理域之前,应该进行哪三项任务?(选择正确的 VTP 模式和版本。
使用新管理域的名称配置交换机。
从新域中的 VTP 服务器上下载 VTP 数据库。
配置新域内的 VTP 服务器,使其识别该交换机的 BID。
重置 VTP 计数器,使交换机可与新域内的其它交换机同步。
检验交换机的配置修订版号是否比新域内的其它交换机的低。
4下列哪两种说法正确地描述了生成树协议?(选择两项。
)它只在第 2 层使用。
它在交换机上配置。
它消除了网络拓扑中的第 2 层环路。
它限制了端口上所允许的有效 MAC 地址的数量。
它使 VLAN 信息得以传播到网络中的其它交换机。
5下列哪种方法可建立用于配置 Linksys WRT300N 无线接入点的管理连接?与接入点关联,然后与接入点建立超级终端会话。
以物理方式连接到接入点,然后重新启动计算机以启动配置软件。
在接入点所在的 IP 子网内的计算机上的 web 浏览器中输入接入点的默认修改与接入点连接的计算机的 TCP/IP 属性,使其与接入点处于同一个网机以建立连接。
6请参见图示。
源地址并非 0019.d2e4.d9f7 的帧进入接口 Fa0/24 时会发生什么情况?Fa0/24 会变为 error-disabled(错误-禁用)状态。
传入帧会被丢弃。
Fa0/24 端口 LED 会关闭。
安全违规计数会增加。
思科ccna第3学期_final_第1套_V_4
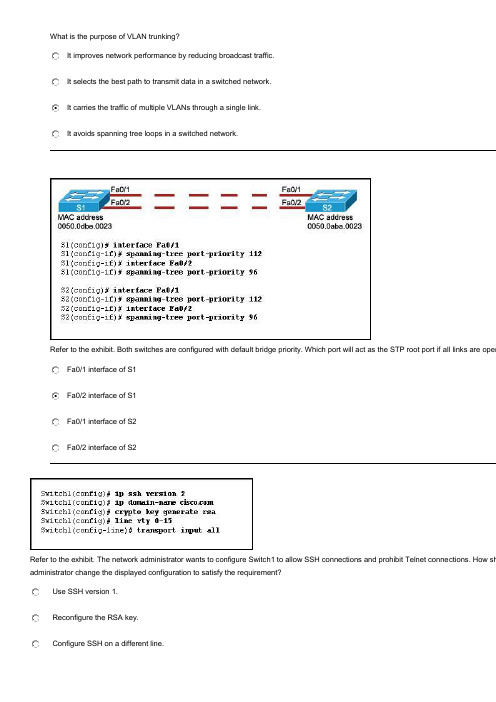
What is the purpose of VLAN trunking?It improves network performance by reducing broadcast traffic.It selects the best path to transmit data in a switched network.It carries the traffic of multiple VLANs through a single link.It avoids spanning tree loops in a switched network.Refer to the exhibit. Both switches are configured with default bridge priority. Which port will act as the STP root port if all links are oper Fa0/1 interface of S1Fa0/2 interface of S1Fa0/1 interface of S2Fa0/2 interface of S2Refer to the exhibit. The network administrator wants to configure Switch1 to allow SSH connections and prohibit Telnet conne ctions. How sh administrator change the displayed configuration to satisfy the requirement?Use SSH version 1.Reconfigure the RSA key.Configure SSH on a different line.Modify the transport input command.Refer to the exhibit. Which two facts about STP can be determined from the displayed output? (Choose two.)Switch S1 has the lowest configured STP priority in the network.Switch S1 is configured as the root bridge for VLAN1.Fa0/21 is the root port of switch S1.Fa0/22 is the redundant link.Fa0/24 is considered the best path to the root bridge.Which statement correctly describes the spanning-tree path cost?It is calculated based on the total number of switches connected in a loop.It is calculated based on the utilization of all the switches along a given path.It is calculated based on the bridge priority of the switches along a given path.It is calculated based on the sum of the port cost value, determined by link speed, for each switch port along a given path What are two requirements for configuring inter-VLAN routing using the router-on-a-stick model? (Choose two.)Each subinterface should be configured with its own IP address, subnet mask, and unique VLAN assignment.The physical interface of the router must be connected to a trunk link on the adjacent switch.The number of physical interfaces on the router should match the number of VLANs.Different static VLANs should be assigned to different interfaces of the router.The router should be configured as the VTP serverRefer to the exhibit. Which two options correctly describe the router configuration that is shown? (Choose two.)Routing between the 192.168.1.0 and 192.168.3.0 networks will not succeed until a routing protocol is configured on the route r.VLANs have not been appropriately configured on the router subinterfaces.The configuration is appropriate for a router-on-a-stick network design.Trunking has been appropriately configured on the router subinterfaces.An IP address should be applied to interface Fa0/1 for routing to occurRefer to the exhibit. What is true of the configuration of switch S1?A Cisco proprietary protocol is in use for ports Fa0/1 and Fa0/3.Switch ports Fa0/1 and Fa0/3 have been configured with the switchport mode access command.Untagged frames received on ports Fa0/1 and Fa0/3 will be placed on VLAN 1.Switch ports Fa0/1 and Fa0/3 are configured to carry data from multiple VLANs.Refer to the exhibit. Switches S2 and S3 are properly connected using an ethernet cable. A network administrator has configured both s is unable to propagate VLANs to S2. What could be the reason for this?The VTP configuration revision is different on both switches.The VTP domains are different on both switches.VTP pruning is disabled.VTP v2 is disabled.Refer to the exhibit. Router R1 is properly configured for router on a stick inter-VLAN routing, but PC1 is unable to ping PC2. What needs problem?Rename VLAN1.Connect one more port of S1 to R1.Configure the Fa0/1 port of S1 as a trunk port.Move the Fa0/0 interface of R1 to another VLAN.Refer to the exhibit. Router R-West and switch S-West1 are connected via a single ethernet cable between the router interface fa0/0 an fa0/1. The router and switch have been configured with the commands that are displayed in the exhib it. The network administrator ente trunk command and receives the output as shown. What is the cause of the "not-trunking" status for switch port Fa0/1?The trunk is established, but no VLANs have been configured to use it.The router is missing the dynamic trunking protocol statements necessary to form a trunk.Because the router does not support Dynamic Trunking Protocol, the trunk has not been established.The router, the switch, or both must be configured with the dynamic desirable option for Dynamic Trunking Protocol to establish aRefer to the exhibit. All trunk links are operational and all VLANs are allowed on all trunk links. An ARP request is sent by computer 5. W receive this message?only computer 4computer 3 and RTR-Acomputer 4 and RTR-Acomputer 1, computer 2, computer 4, and RTR-Acomputer 1, computer 2, computer 3, computer 4, and RTR-Aall of the computers and the routerRefer to the exhibit. A network administrator enters the displayed commands to configure VLAN 30. What is the result of running these commVLAN 30 will be added to S1, S2, and S3, but not to S4.VLAN 30 will be pruned from the VLAN database of S3.VLAN 30 will be added to the VLAN database of S3 but will not be propagated to S4, S2 or S1.VLAN 30 will not be added to the VLAN database of S3 and an error message will be displayedRefer to the exhibit. VTP pruning is enabled in the VTP domain that is shown. How will switch ST-1 handle Layer 2 broadcast traf host A on switch ST-C?It will be dropped.It will be forwarded out port Fa0/5 only.It will be forwarded out ports Fa0/5 and Fa0/10.It will be forwarded out ports Fa0/5, Fa0/10, and Fa0/15Refer to the exhibit. The devices in the network are operational and configured as indicated in the exhibit. However, hosts A and D other. What is the most likely cause of this problem?The link between the switches is up but not trunked.The Fa0/11 interface of Switch1 is not configured as a trunk.Hosts A and D are configured with IP addresses from different subnets.VLAN 20 and VLAN 30 are not allowed on the trunk between the switches.After unpacking a new Linksys WRT300N wireless multifunction device, a user needs to change the default administrator passwor d and make other configuration changes. What must the user do to access the device in order to make these changes?Use a wireless client to associate with the WRT300N and then open a HyperTerminal session with the device.Establish a wired connection with the device and then reboot the attached computer to launch the configuration software.Establish a wired connection from a computer in the same IP subnet as the WRT300N and enter the default IP address of the device into a web browser on the computer.Modify the TCP/IP properties of the computer that is connected to the WRT300N so that the computer and the WRT300N exist on the same network. Then reboot the computer to establish a connection.Refer to the exhibit. How is port Gi1/1 on SWT-A functioning in the spanning-tree topology?It is sending and receiving data frames.It is receiving BPDUs, but not sending data frames.It is participating in the election process by forwarding the BPDUs it receives.It is receiving BPDUs and populating the MAC address table, but not sending data.Refer to the exhibit. The switches have been configured as shown. The hosts that are connected to switch 101-2FL are not able to communicate with the hosts in their corresponding VLANs that are connected to switch 101-3FL. What should be done to fix the problem?Configure port Fa0/2 on switch 101-3FL as a static trunk link.Introduce a Layer 3 device or a switch with Layer 3 capability into the topology.Utilize the switchport trunk allowed vlan all command on switch 101-3FL to permit the VLAN traffic.Apply IP addresses that are in the same subnet to the interfaces that are used to connect switches 101-2FL and 101-3FLAfter listening for the presence of a signal on the network media, hosts A and C transmit data at the same time. In what two ways do the hosts respond to this situation? (Choose two.)The hosts transmit a jam signal to ensure that all hosts on the network are aware that a collision has occured.Because they are operating in full-duplex mode, the hosts resume listening for traffic in preparation for sending future messages.Because the hub will temporarily block traffic from one of the hosts, that host will be allowed to transmit once the wire is clear.Hosts A and C are assigned shorter backoff values to provide them priority to access the media for retransmission.After the backoff period of a host, the host checks to determine if the line is idle before retransmittingRefer to the exhibit. Hosts PC_A and PC_B send traffic simultaneously, and the frames from the transmitting stations collide.What is the last device to receive the collision?hub HB1switch SW1router R1switch SW2router R2switch SW4Refer to the exhibit. Switch SW2 has been newly purchased and added to the network. What configuration should be applied to SW2 so thatit participates in the same VTP domain as switch SW1, receives VLAN information from SW1, and synchronizes VLAN information?Disable VTP pruning on SW2.Configure SW2 in VTP transparent mode.Configure SW2 with the VTP domain password.Configure SW2 as a VTP server with a higher revision numberWhen configuring a router to act as an SSH server, what should be configured before issuing the crypto key generate rsacommand?the security domain namethe VTP domain namethe IP domain namethe host nameRefer to the exhibit. The switch VTY lines have been properly configured, but PC1 is unable to remotely manage the switch. How can this problem be resolved?Configure the Fa0/1 interface of the switch in trunk mode.Configure a default gateway on the switch.Configure the native VLAN on the switch.Configure the Fa0/1 interface of the switch to allow all VLANsRefer to the exhibit. A network administrator has segmented the network into two VLANs. The connected hosts can only access r esources in their own VLAN. What is the most scalable and cost effective solution to allow inter-VLAN communication in this network?Replace S1 with a router that has one FastEthernet interface for each PC.Add a second switch and divide the PCs so that each VLAN is connected to its own switch.Configure a router with two subinterfaces on one of its FastEthernet ports and connect it to S1 using a trunk link.Connect a router to a port on S1 and assign the IP address of VLAN1 to the connecting router interfaceRefer to the exhibit. An administrator documented the output of a CAM table from an Ethernet switch as shown. What action will the switch take when it receives the frame shown at the bottom of the exhibit?discard the frameforward the frame out port 2forward the frame out port 3forward the frame out all portsforward the frame out all ports except port 3add station 00-00-3D-1F-11-05 to port 2 in the forwarding tableWhich statement regarding the service password-encryption command is true?The service password-encryption command is entered at the privileged EXEC mode prompt.The service password-encryption command encrypts only passwords for the console and VTY ports.The service password-encryption command encrypts all previously unencrypted passwords in the running configuration.To see the passwords encrypted by the service password-encryption command, enter the no servicepassword-encryption commandWhich statement correctly describes the function of a Layer 2 switch?It performs switching and filtering based on the destination network layer address.It automatically uses STP to prevent switching loops in redundant topologies.It uses VTP to allow data from multiple VLANs to travel across a single link.It routes packets between different LAN segmentsWhich three statements are correct concerning the default configuration of a new switch? (Choose three.)It is configured in VTP server mode.STP is automatically enabled.The first VTY line is automatically configured to allow remote connections.VLAN1 is configured with a management IP address.All switch ports are assigned to VLAN1.The enable password is configured as ciscoRefer to the exhibit. How will switch S2 manage traffic coming from host PC1?S2 will drop the traffic, unless it is management traffic.S2 will tag the frame with VLAN ID 99 when it forwards it over the trunk link.S2 will leave the traffic untagged when it forwards it over a trunk link.S2 will tag the traffic with the highest VLAN ID value when it forwards it over the trunk link.Refer to the exhibit. The network administrator needs to remove the east-hosts VLAN and use the switch port from that VLAN in one of the existing VLANs. Which two sets of commands should be used when completely removing VLAN 2 from S1-Central while leaving the switch and all its interfaces operational? (Choose two.)S1-Central>enableS1-Central# reloadS1-Central>enableS1-Central# erase flash:S1-Central>enableS1-Central# delete flash:vlan.datS1-Central>enableS1-Central# configure terminalS1-Central(config)# no vlan 2S1-Central>enableS1-Central# configure terminalS1-Central(config-if)# interface fastethernet 0/1 S1-Central(config-if)# switchport access vlan 3Refer to the exhibit. The network administrator configures both switches as displayed. However, host C is unable to ping host D and host E is unable to ping host F. What action should the administrator take to enable this communication?Include a router in the topology.Associate hosts A and B with VLAN 10 instead of VLAN 1.Remove the native VLAN from the trunk.Configure one trunk port in the dynamic desirable mode.Add the switchport nonegotiate command to the configuration of S2Which two statements are correct about wireless infrastructure components? (Choose two.)An AP converts the TCP/IP data packets from their 802.11 frame encapsulation format to the 802.3 Ethernetframe format on the wired Ethernet network.A wireless AP does not require any physical connection to allow wireless clients to access the Internet.An AP is a layer 2 device, similar to a switch, that provides dedicated bandwidth to each connected wireless host.Collisions do not occur between wireless NICs and APs.The wireless router performs the roles of AP and router.Refer to the exhibit. The switches are configured for VTP as shown. Which two statements correctly describe the operation of these switches? (Choose two.)A new VLAN can be added to Switch1 and that information will be added only to Switch2.A new VLAN can be added to Switch1 and that information will be added to Switch2 and Switch4.An existing VLAN can be deleted from Switch4 and that VLAN will be deleted from Switch1 and Switch2.An existing VLAN can be deleted from Switch2 and that VLAN will be deleted from Switch1 and Switch4.A new VLAN can be added to Switch4 and that information will be added to Switch1, Switch2, and Switch3.A new VLAN can be added to Switch3 and that information will be added to Switch1, Switch2, and Switch4A new switch is to be added to an exis ting network in a remote office. The network administrator does not wantthe technicians in the remote office to be able to add new VLANs to the switch, but the switch should receive VLAN updates from the VTP domain. Which two steps must be performed to configure VTP on the new switch to meet these conditions? (Choose two.)Configure an IP address on the new switch.Configure the existing VTP domain name on the new switch.Configure all ports of both switches to access mode.Configure the new switch as a VTP client.Enable VTP pruningWhich two statements describe Spanning Tree Protocol? (Choose two.)It is only used at Layer 2.It is configured on routers.It eliminates Layer 2 loops in network topologies.It limits the number of valid MAC addresses allowed on a port.It allows VLAN information to propagate to other switches in the network.Refer to the exhibit. Which switch will be elected as the root bridge of the spanning tree topology?Cat-ACat-BCat-CCat-DRefer to the exhibit. What three statements describe why Host1 and Host2 are unable to communicate? (Choose three.)The switch ports are on different VLANs.The switch IP address is on the wrong subnet.The hosts are configured on different logical networks.A router is required to forward traffic between Host1 and Host2.The VLAN port assignments must be contiguous for each VLAN.The host default gateway addresses must be on the same logical network.Refer to the exhibit. A new host needs to be connected to VLAN 3. Which IP address should be assigned to this new host?192.168.1.22 /28192.168.1.31 /28192.168.1.32 /28192.168.1.52 /28192.168.1.63 /28Refer to the exhibit. Router RA receives a packet with a source address of 192.168.1.65 and a destination address of 192.168.1.161. What will the router do with this packet?The router will drop the packet.The router will forward the packet out interface FastEthernet 0/1.1.The router will forward the packet out interface FastEthernet 0/1.2.The router will forward the packet out interface FastEthernet 0/1.3.The router will forward the packet out interface FastEthernet 0/1.2 and interface FastEthernet 0/1.3Refer to the exhibit. On which of the devices in this network should routing between VLANs take place?the core layer devicesthe access layer devicesthe distribution layer devicesthe core and distribution layer devicesRefer to the exhibit. The teacher host is connected to port Fa0/7 on switch STW. A student has decided to share access to the Internet by attaching a hub and laptop to STW as shown. What will be the result of the student making this connection?The Fa0/7 port of STW will be shutdown.The student will gain full access to the Internet.Both the teacher and student will be able to receive data but only the teacher will be able to send.The frames from the laptop will be dropped, but the teacher host will maintain connectivity with the network.Refer to the exhibit. In what two ways will the router handle VLAN traffic that is received on the trunk? (Choose two.)Traffic to VLAN 1 received by the router interface Fa0/0 will be dropped by the router.Because interface Fa0/0 requires an IP address, the router will not be able to route between the VLANs.Packets that are received from network 192.168.20.0 /24 will be handled by subinterface Fa0/0.20.The router will use subinterface MAC addresses to identify the VLAN traffic that is received on the physical interface.The router will continue to process traffic from the attached VLANs even if the physical interface goes downRefer to the exhibit. Switch SW-A is to be used as a temporary replacement for another switch in the VTP Studentdomain. What two pieces of information are indicated from the exhibited output? (Choose two.)The other switches in the domain can be running either VTP version 1 or 2.There is a risk that the switch may cause incorrect VLAN information to be sent through the domain.VTP will block frame forwarding on at least one redundant trunk port that is configured on this switch.VLAN configuration changes made on this switch will be sent to other devices in the VTP domain.This switch will update its VLAN configuration when VLAN changes are made on a VTP server in the same domainWhat are three benefits of employing a hierarchical network design? (Choose three.)Hierarchically designed networks can more easily be expanded to suit future needs.Hierarchical design models enhance existing bandwidth through the use of link aggregation.The hierarchical model allows for specialized functionality at each layer, simplifying devicemanagement.Use of a hierarchical design allows replacement of redundant devices with high-capacity network equipment.A hierarchical design uses firewalls instead of complicated port-based and distribution layer securitypolicies.The hierarchical model allows the use of high-performance switches at all design layers, thus allowing for a fully-meshed topologyRefer to the exhibit. Hosts A and B attempt to transmit a frame at the same time and a collision occurs. When will host D be able to transmit?immediatelyafter sending its jam signalafter host A and host B have completed transmissionafter the jam signal clears and its backoff delay expiresWhat provides an authentication mechanism for 802.11-based wireless networks?DSSSOFDMSSIDWPARefer to the exhibit. What is the effect of setting the security mode to WEP on the Linksys integrated router?WEP identifies the wireless LAN.WEP allows the access point to inform clients of its presence.WEP translates IP addresses into easy-to-remember domain names.WEP encrypts data between the wireless client and the access point.WEP ensures that only authenticated users are allowed access to the WLAN.WEP translates an internal address or group of addresses into an outside, public address.Refer to the exhibit. SW-T has been configured with a single trunking interface. Which VLANs will be allowed across the trunk?Only VLAN 1 will be allowed across the trunk.All configured VLANs will be allowed across the trunk.Only the native VLAN will be allowed across the trunk.Only the the management and native VLANs will be allowed across the trunk.Only VLANs that are configured on the VTP server in the dom ain will be allowed across the trunkRefer to the exhibit. What does the term DYNAMIC indicate in the output that is shown?This entry can only be removed from the MAC address table by a network administrator.When forwarding a frame to the device with address 0060.5c5b.cd23, the switch does not have to perform a lookup to determine the final destination port.Only the device with MAC address 0060.5c5b.cd23 will be allowed to connect to port Fa0/18.The switch learned this MAC address from the source address in a frame received on Fa0/18.Refer to the exhibit. What is the purpose of the configuration commands that are shown?to activate port Fa0/10to make the port a member of VLAN 30to activate port security on port Fa0/10to add VLAN 30 to the trunk that is connected to port Fa0/10。
CCNA思科第三学期ESwitchingEam正确答案

单臂路由器VLAN 间路由有哪三项特征?(选择三项。
)需要使用VTP需要使用子接口减少广播域的数量使用过多VLAN 时会影响性能需要在路由器和至少一台交换机之间采用接入链路比用于VLAN 间路由的其它方法更加经济规定至少要在路由器和交换机之间使用两个交换机端口2如果将允许使用中继链路的VLAN 范围设置为默认值,表示允许哪些VLAN?仅管理VLAN除扩展范围VLAN 之外的所有VLAN除VLAN 1 和VLAN 1002-1005 之外的所有VLAN所有的VLAN3请参见图示。
哪一个口令可让管理员进入特权执行模式?cisco1cisco2cisco3cisco4请参见图示。
假设所有交换机的网桥优为默认值,那么哪台交换机将当选为生成树拓扑的根桥?Cat-ACat-BCat-CCat-D5请参见图示。
最近安装了SW1 用于取代集线器。
主机1 和传送数据。
网络设备会如何处理此事件?(选择两项。
)当冲突发生时,会调用回退算法。
由于主机 1 和主机4 都连接到交换机,因此不会发生冲突。
交换机将根据交换机MAC 地址表中的信息将数据转发到相应的端口。
主机 2 和主机3 会获分配更短的回退值,从而获得访问介质的优先权。
为了防止再发生冲突,交换机会在设定时间内阻塞与主机2、主机 3 和主机4 连接的端口。
6请参见图示。
网络管理员east-hosts VLAN 并将属于该VLAN 的交换机端口用到一个现有VLAN 中。
如果要从S1-Central 完全删除VLAN 2,同时及其所有接口工作正常,应该使用哪两组命令?(选择两项。
)S1-Central> enable S1-Central# reloadS1-Central> enable S1-Central# erase flash:S1-Central> enable S1-Central# delete flash:vlan.datS1-Central> enable S1-Central# configure terminal S1-Central(config)# no vlan 2S1-Central> enable S1-Central# configure terminal S1-Central(config-if)# interface fastethernet 0/1S1-Centralswitchport access vlan 37请参见图示。
思科第三学期实训报告

日照职业技术学院思科交换技术实训报告学号:201015030107姓名:红领巾班级:2010级网络技术1班实训日期:2011-2012年第一学期2011年12月26日二、正文2.1 摘要2.1.1 实训内容:第七章综合实验2.1.2 场地:地滋楼A5342.1.3 时间: 2011年12月19-30日2.1.4 实训目的:巩固加深对思科网络知识的了解,知识与实践相结合,提供学生综合能力。
2.2 主体任务 1:执行基本的路由器配置∙路由器主机名∙禁用 DNS 查找∙配置执行模式口令class∙为控制台连接配置口令cisco∙为 vty 连接配置口令cisco任务 2:执行交换机配置配置三台交换机:∙配置主机名∙禁用 DNS 查找∙配置执行模式口令class∙为控制台连接配置口令cisco∙为 vty 连接配置口令cisco任务 3:WRT300N 无线路由器练习●执行基本路由器配置●执行交换机配置●连接到 Linksys WRT300N 路由器●访问 WRT300N 无线路由器●为 Linksys WRT300N 无线路由器配置 IP 设置●配置 DHCP 设置●基本无线设置●启用无线安全●管理和保护路由器的 Web 实用程序●配置 WRS2●建立和检验完全连通性●配置端口安全2.3 总结每年都有实训,每年带给我们的知识都有新的感觉。
纸上得来终觉浅,实践才是检验真理的王道。
实训,是我们实习前的演练,只有实训过关,实习才有能力。
实训不仅仅锻炼了我们个人能力,还提高了我们团队配合能力,有困难大家一起解决,就变得容易多了。
实训,它使我们在实践中了解社会,让我们学到了很多在课堂上根本就学不到的知识,也打开了视野,增长了见识,为我们以后进一步走向社会打下坚实的基础。
现在思科不管是在国内还是在国外都是非常有前途的,为了自己,更为了自己的将来,我们也要好好的去学习思科,学校给提供了一个非常好的环境让我们实训,虽然实训非常紧张,但也是短暂的,在这几天的实训中我学到了很多,同时也让自己变了很多、这几天的思科实训时间就这样在忙碌中匆匆过去了,留给我的都是丰富的经验和深深的体会。
ccna第3本期末

c c n a第3本期末work Information Technology Company.2020YEAR1请参见图示。
需要将一台新主机连接到 VLAN 3。
应该为此新主机分配什么 IP 地址?192.168.1.22 /28192.168.1.31 /28192.168.1.32 /28192.168.1.52 /28192.168.1.63 /282请参见图示。
将 Linksys 集成路由器上的安全模式设置为 WEP 有什么作用?WEP 可标识无线 LAN。
WEP 允许该接入点通知客户端它的存在。
WEP 将 IP 地址转换为容易记忆的域名。
WEP 可加密无线客户端与接入点之间的数据。
WEP 可确保只有授权用户可以访问该 WLAN。
WEP 将一个或一组内部地址转换为外部公有地址。
3请参见图示。
交换机的配置如图所示。
连接到交换机 101-2FL 的主机无法与连接到交换机 101-3FL 且位于对应 VLAN 中的主样才能纠正此问题?将交换机 101-3FL 的 Fa0/2 端口配置为静态中继链路。
在拓扑中加入第 3 层设备或具备第 3 层功能的交换机。
在交换机 101-3FL 上使用switchport trunk allowed vlan all命令允许 VLAN 流量。
4下列哪两种说法正确地描述了生成树协议(选择两项。
)它只在第 2 层使用。
它在交换机上配置。
它消除了网络拓扑中的第 2 层环路。
它限制了端口上所允许的有效 MAC 地址的数量。
5请参见图示。
教师主机连接到交换机 STW 的 Fa0/7 端口。
一位学生想要共享 Internet 访问,于是决定将集线器和笔记本电脑示连接到 STW。
学生如此连接的结果是什么?STW 的 Fa0/7 端口会关闭。
学生会获得访问 Internet 的安全权限。
教师和学生都能接收数据,但只有教师才能发送数据。
从笔记本电脑发出的帧将被丢弃,但教师主机仍与网络保持连通。
思科第三学期第四章试题及答案

思科第三学期第四章试题及答案思科第三学期第四章试题及答案/doc/8ea3ed944a2fb4daa58da0116c175f0e7dd119e1.html work Information Technology Company.2020YEAR下列关于实施 VTP 的说法中哪两项正确(选择两项。
)交换机必须通过中继链路来连接。
V TP 域名区分⼤⼩写。
透明模式下的交换机不能配置新 VLAN。
必须使⽤ VTP ⼝令且区分⼤⼩写。
使⽤ VTP 的交换机必须具有相同的交换机名称。
2VTP 以客户端模式⼯作具有哪两项特点(选择两项。
)⽆法添加 VLAN可添加在本地有效的 VLAN⽆论 VLAN 信息如何,将⼴播从所有端⼝转发出去只能传递 VLAN 管理信息⽽⽆法接受更改可向同⼀ VTP 域中的其它交换机转发 VLAN 信息3请参见图⽰。
交换机 S1 处于 VTP 服务器模式。
交换机 S2 和 S3 处于客户端模式。
管理员意外断开了 S2 的 F0/1 接⼝上的S2产⽣什么后果?S2 会⾃动转换到 VTP 透明模式。
S2 会将所有 VLAN 从 VLAN 数据库中删除,直到重新接好电缆为⽌。
S2 会保存已知的最新修订版本的 VLAN ,但如果它重新加载,就会丢失这些 VLAN。
当电缆重新接好时,S2 会⾃动向 172.17.99.11 发送⼀个 VTP 通告请求。
4请参见图⽰。
VTP 域内的所有交换机均是新的。
交换机 SW1 被配置为 VTP 服务器,交换机 SW2 和 SW4 被配置为 VTP 客SW3 被配置为 VTP 透明模式。
哪台或哪些交换机会收到 VTP 更新并根据更新来同步 VLAN 配置?所有交换机均会收到更新并同步 VLAN 信息。
仅交换机 SW2 会收到更新并同步 VLAN 信息。
仅交换机 SW3 和 SW4 会收到更新并同步 VLAN 信息。
S W3 和 SW4 会收到更新,但仅交换机 SW4 会同步 VLAN 信息。
cisco CCNA官方第三学期第三章官方测试题和答案

1网络管理员正在从交换机删除多个VLAN。
当管理员输入no vlan 1命令时,收到错误消息。
此命令为什么产生错误消息?在任何情况下都不能删除VLAN 1。
只能通过删除vlan.dat 文件来删除VLAN 1。
只有删除VLAN 1 的所有端口后才能删除VLAN 1。
只有将VLAN 1 的角色分配给其它VLAN 后,才能删除VLAN 1。
2网络管理员希望将大楼A 中的主机划分到编号分别为20 和30 的VLAN 中,下列关于VLAN 配置的说法中哪两项正确项。
)可以为这些VLAN 命名。
VLAN 信息保存在启动配置中。
手动创建的非默认VLAN 必须使用扩展范围的VLAN 编号。
网络管理员可在全局配置模式或VLAN 数据库模式下创建VLAN。
两个VLAN 都可命名为BUILDING_A 以与处于不同地理位置的其它VLAN 区分。
3下列有关802.1q 中继协议的说法中哪项正确?802.1q 是Cisco 专有协议。
802.1q 帧通过MAC 地址映射到VLAN。
802.1q 不需要重新计算原始帧的FCS。
802.1q 对通过接入端口转发出去的帧不会执行操作。
4下列哪两种说法正确描述了VLAN 的优点?(选择两项。
)VLAN 通过调节流量控制和窗口大小来提升网络性能。
VLAN 使交换机可通过VLAN ID 过滤将数据包路由到远程网络。
VLAN 通过减少交换机上所需的物理端口数量来降低网络开销。
VLAN 通过识别有权访问敏感数据和应用程序的用户来提升网络安全性。
VLAN 将网络划分为较小的逻辑网络,这降低了网络对广播风暴的敏感性。
5请参见图示。
SW1 和SW2 是将要安装到图中所示拓扑中的新交换机。
交换机SW1 的Fa0/1 接口已将中继模式配置为“打于交换机SW1 和SW2 之间形成中继链路的说法中哪项正确?交换机SW2 的Fa0/2 接口如果支持DTP,则会协商成为中继链路。
交换机SW2 的Fa0/2 接口只有在静态配置为中继接口的情况下才能成为中继链路。
CCNA新版题库知识点总结_CCNA(200-120)_CCNA新版题库
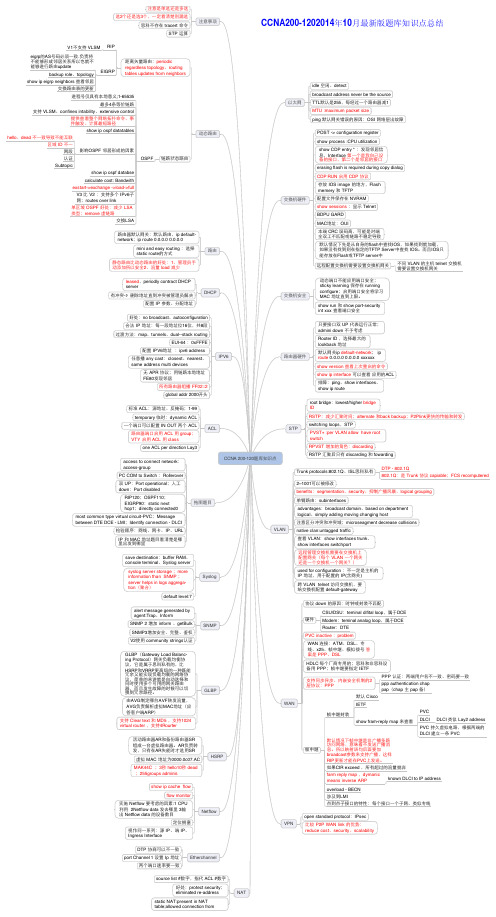
只要接口口双 UP 代表运行行正常; admini down 不予考虑
Rooter ID ,选择最大大的 lookback 地址
默认⺴网网关ip default-network; ip route 0.0.0.0 0.0.0.0 xxxxxx
show version 查看上次重启的命令
show ip interface 可以查看 应用用的ACL
好处:protect security; eliminated re-address
static NAT:present in NAT table;allowed connection from
PVC 持久虚拟电路,根据两端的 DLCI 建立立一一条 PVC
如果CIR exceed ,所有超过的流量抛弃
farm reply map ,dymanic
means inverse ARP
known DLCI to IP address
overload - BECN 涉及到LMI 点到点子子接口口的特性:每个接口口一一个子子⺴网网、类似专线
注意是单选还是多选 选2个还是选3个,一一定看清楚别漏选
思科不存在 tracert 命令 STP 运算
注意事项
本页已使用福昕阅读器进行编辑。 福昕软件(C)2005-2009,版权所有, 仅供试用。
CCNA200-1202014年10月最新版题库知识点总结
V1不支支持 VLSM RIP
eigrp的AS号码必须一一致.负责将 不能够形成邻居关系所以也就不 能够进行行路由update
远程配置交换机需要设置交换机⺴网网关
不同 VLAN 的主机 telnet 交换机 需要设置交换机⺴网网关
leased,periodly contract DHCP server
【最新2018】思科数据中心3.0解决方案-实用word文档 (3页)

本文部分内容来自网络整理,本司不为其真实性负责,如有异议或侵权请及时联系,本司将立即删除!== 本文为word格式,下载后可方便编辑和修改! ==思科数据中心3.0解决方案课件思科数据中心3.0解决方案数据中心一直是重要的企业资产,也是IT用以保护、优化和发展业务的战略性重点机构,但如果您的数据中心出现了服务器、存储资源使用率低下,能源和人员成本占数据中心总运行成本的25%-30%,在IT预算中,70%花费都在维护方面,而不是使企业更具竞争力,这是当前 CIO 最需要迫切解决的问题。
数据中心转型的需要当今的许多企业都在努力解决数十年来无计划发展的遗留问题,面对大量变更、管理、集成、安全和备份都成为越来越昂贵和困难的技术孤岛。
这些数据中心运营的现实问题,对于寻找创新方式来满足不断提高的企业需求的CIO来说,已成为严重的限制因素。
现在,许多公司都致力于改变数据中心设施的整合和虚拟化。
尽管这是优化现有技术、消除运营孤井的正确做法,但这只是起点而已。
公司必须拓宽视角,以创新方式来看待数据中心架构,以使IT效率、响应能力和永续性都达到新的高度。
思科数据中心3.0既能解决当前迫切的运营限制问题,而且也能过渡到未来的虚拟数据中心。
数据中心3.0改变了目前的数据中心域环境-服务器、存储和网络作为独立孤井运行的情况,将它们统一到单一架构和一套共享网络服务中。
因为网络是无所不在的,网络的特征就是支持一切,只有网络能在异构环境中提供连接,统一行为,通过开放标准建设和互操作性,与任何厂商、设备或内容无关。
思科数据中心3.0的业务优势思科数据中心3.0能够战略性地迁移到一个完全不同的基础设施模式:能够根据需要,混合、匹配和配置位于任意物理地点的共享服务的统一架构。
这个模式从根本上改变了IT运行其核心资源的方式,在效率和企业响应能力方面获得了突破性的优势。
提高响应能力:因为网络能自动从虚拟化服务器、存储和网络服务池中部署基础设施,所以能按需发现和配置资源,与人工配置方法相比,大大缩短了响应时间,减少了错误率,能将富有经验的IT人员重新分配到更高价值的工作。
CCNA思科第三学期ESwitchingExam正确答案

C C N A思科第三学期E S w i t c h i n g E x a m正确答案集团标准化办公室:[VV986T-J682P28-JP266L8-68PNN]单臂路由器VLAN间路由有哪三项特征(选择三项。
)需要使用VTP需要使用子接口减少广播域的数量使用过多VLAN时会影响性能需要在路由器和至少一台交换机之间采用接入链路比用于VLAN间路由的其它方法更加经济规定至少要在路由器和交换机之间使用两个交换机端口如果将允许使用中继链路的VLAN范围设置为默认值,表示允许哪些VLAN仅管理VLAN除扩展范围VLAN之外的所有VLAN除VLAN1和VLAN1002-1005之外的所有VLAN所有的VLAN请参见图示。
哪一个口令可让管理员进入特权执行模式c isco1cisco2cisco3cisco请参见图示。
假设所有交换机的网桥优先级值都设置为默认值,那么哪台交换机将当选为生成树拓扑的根桥Cat-ACat-BCat-CCat-D请参见图示。
最近安装了SW1用于取代集线器。
主机1和主机4同时传送数据。
网络设备会如何处理此事件(选择两项。
)当冲突发生时,会调用回退算法。
由于主机1和主机4都连接到交换机,因此不会发生冲突。
交换机将根据交换机MAC地址表中的信息将数据转发到相应的端口。
主机2和主机3会获分配更短的回退值,从而获得访问介质的优先权。
为了防止再发生冲突,交换机会在设定时间内阻塞与主机2、主机3和主机4连接的端口。
请参见图示。
网络管理员需要删除east-hostsVLAN并将属于该VLAN的交换机端口用到一个现有VLAN中。
如果要从S1-Central VLAN2,同时保证交换机及其所有接口工作正常,应该使用哪两组命令(选择两项。
)S1-Central>enableS1-Central#reloadS1-Central>enableS1-Central#eraseflash:S1-Central>enableS1-Central#deleteflash:S1-Central>enableS1-Central#configureterminalS1-Central(config)#novlan2S1-Central>enableS1-Central#configureterminalS1-Central(config-if)#interfacefastethernet0/1S1-Central(config-if)#switchportaccessvlan3请参见图示。
思科网院[Cisco]第三学期Final题目及答案
![思科网院[Cisco]第三学期Final题目及答案](https://img.taocdn.com/s3/m/8c75bd0c7cd184254b353560.png)
1请参见图示。
网络支持技术人员需要为新路由器的一个FastEthernet 接口设置IP 地址。
但接口拒绝该地址,其原因是什么该IP 地址已在使用中。
技术人员使用的是网络地址。
技术人员为/26 使用了错误的子网掩码。
技术人员必须在该接口上启用VLSM。
2一个销售代表准备从酒店使用Internet 向公司总部发送敏感信息。
旅行前,IT 工作人员进行了必要工作以允许其安全访问该销售代表实施了什么解决方VPN帧中继带有CHAP 身份验证的PPP带有PAP 身份验证的PPP3下列哪两种说法正确描述了IEEE STP 的功能?(选择两项。
)它会立即将不处于丢弃状态的所有端口转换为转发状态。
它提供了一种在交换网络中禁用冗余链路的机制。
它有三种端口状态:丢弃、学习和转发。
它可确保交换网络中没有环路。
它可在不到 1 秒的时间内使交换网络收敛。
4请参见图示。
网络管理员必须为ISP 手动总结POP 路由器上的所有IP 地址。
下列哪项是正确的总结地址?192.168.0.0/2192.168.0.0/23192.168.0.0/24192.168.0.0/255请参见图示。
所有路由器都配置为使用带有默认设置的OSPF 协议。
如果同时启动所有路由器,哪台路由器将被选为BDRR1R2R3R46有关单区域OSPF 网络的说法中,哪两项正确?(选择两项。
)DR 和BDR 会减少在广播网络中发送的更新数量。
BDR 负责将更改发布到所有其它的OSPF 路由器。
路由器使用hello 数据包建立和维护邻居邻接关系。
所有OSPF 路由器都会接收组播地址224.0.0.6 上的更新。
区域 1 必须始终存在。
7请参见图示。
网络管理员按图示配置R1。
但是,网络 A 的一些主机无法访问Internet。
下列哪两个措施可解决此问题?(在正确的接口上配置ip nat inside和ip nat outside命令。
在NAT 地址池中增加IP 地址数量。
CCNA_第三学期__期末完整版考试
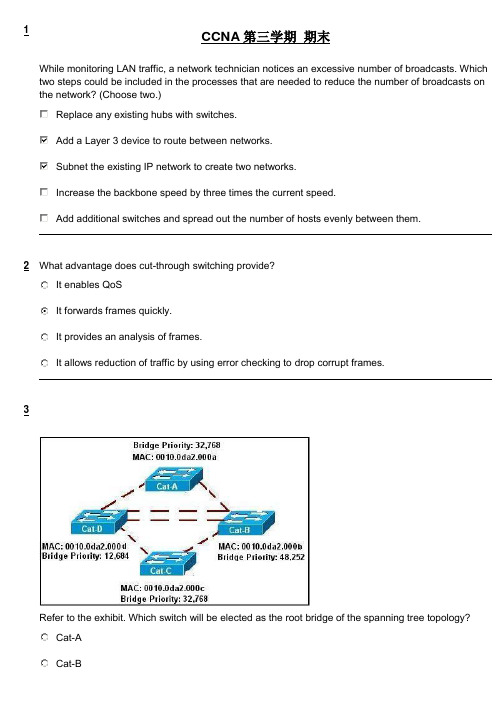
1CCNA 第三学期 期末While monitoring LAN traffic, a network technician notices an excessive number of broadcasts. Which two steps could be included in the processes that are needed to reduce the number of broadcasts onthe network? (Choose two.)Replace any existing hubs with switches.Add a Layer 3 device to route between networks.Subnet the existing IP network to create two networks.Increase the backbone speed by three times the current speed.Add additional switches and spread out the number of hosts evenly between them.2What advantage does cut-through switching provide?It enables QoSIt forwards frames quickly.It provides an analysis of frames.It allows reduction of traffic by using error checking to drop corrupt frames.3Refer to the exhibit. Which switch will be elected as the root bridge of the spanning tree topology?Cat-ACat-BCat-CCat-D4W hich stackable switch feature allows for interconnection of multiple switches and will provide a cost effective solution for networks that require high bandwidth and high availability?modular line cardsspecial backplane portdedicated gigabyte line portsaggregated FastEthernet ports5Refer to the exhibit. This switch is to be added to the production network. Which two facts about VLANs and VTP operation can be confirmed by this output? (Choose two.)The network administrator will be able to configure VLANs of local significance on this switch.VLANs can only be added to the VLAN database on this switch by a VTP advertisement.All VLANs that are configured on this switch will be sent to all other switches in the same VTP domain.This switch will drop all VTP advertisements that come from switches that are configured in the same VTP domain.Adding this switch to the network will cause no disruption in the VTP domain operations if the rest of the switches in the same VTP domain have a higher configuration revision number.6Refer to the exhibit. The hosts connected to switch SW1 are not able to communicate with the hosts in the same VLANs connected to switch SW2. What should be done to fix the problem?Configure VLANs with different VLAN IDs on switch SW2.Reconfigure the trunk port on switch SW2 with static trunk configuration.Introduce a Layer 3 device or a switch with Layer 3 capability in the topology.Apply IP addresses that are in the same subnet to the interfaces used to connect SW1 and SW2.7Refer to the exhibit. A new host needs to be connected to VLAN 3. Which IP address should beassigned to this new host?192.168.1.22 /28192.168.1.31 /28192.168.1.32 /28192.168.1.52 /28192.168.1.63 /288Refer to the exhibit. SW-T has been configured with a single trunking interface. Which VLANs will be allowed across the trunk?Only VLAN 1 will be allowed across the trunk.All configured VLANs will be allowed across the trunk.Only the native VLAN will be allowed across the trunk.Only the the management and native VLANs will be allowed across the trunk.Only VLANs that are configured on the VTP server in the domain will be allowed across the trunk.9Refer to the exhibit. How will switch S2 manage traffic coming from host PC1?S2 will drop the traffic, unless it is management traffic.S2 will tag the frame with VLAN ID 99 when it forwards it over the trunk link.S2 will leave the traffic untagged when it forwards it over a trunk link.S2 will tag the traffic with the highest VLAN ID value when it forwards it over the trunk link. 10Refer to the exhibit. Both switches are interconnected via a trunk link. Host A and host B are on the default VLAN but are not able to exchange traffic. What should be done to fix the problem?Allow all VLANs on the trunk link.Remove the native VLAN from the trunk.Include a router or switch with Layer 3 capabilities.Configure the same native VLAN on both ends of the trunk.11Refer to the exhibit. What does the term DYNAMIC indicate in the output that is shown?This entry can only be removed from the MAC address table by a network administrator.When forwarding a frame to the device with address 0060.5c5b.cd23, the switch does not have to perform a lookup to determine the final destination port.Only the device with MAC address 0060.5c5b.cd23 will be allowed to connect to port Fa0/18.The switch learned this MAC address from the source address in a frame received on Fa0/18.12W hy is MAC address filtering considered a poor choice in securing a WLAN?Available bandwidth is reduced.MAC addresses are easily spoofed.APs are more susceptible to DoS attacks.The payload encryption is easily broken.13How does a switch that is configured for 802.1Q trunking handle untagged frames that are receivedon a trunk port?The frames are dropped.The frames are assigned to the native VLAN.The frames are assigned to the default VLAN.The frames are assigned to the management VLAN.14Refer to the exhibit. Which three options correctly describe the router configuration that is shown?(Choose three.)An IEEE standard trunking protocol is in use.Interface Fa0/1 has been configured with subinterfaces.The shutdown command has been applied to interface Fa0/1.Interface Fa0/1.3 is mapped to the default management VLAN.The configuration is appropriate for a router-on-a-stick network design.An IP address should be applied to interface Fa0/1 for routing to occur.15RSTP is enabled in a switched network that is active and converged. Which switch port type assumesa discarding state on non-root switches?root portedge portalternate portdesignated port16What provides an authentication mechanism for 802.11-based wireless networks?DSSSOFDMSSIDWPA17W hat is the benefit of the auto-MDIX feature on a Cisco Catalyst switch?dynamically assigns a new management VLAN IDautonegotiates IP address information for initial management connectionsallows the use of straight-through patch cables regardless of connected device typesplaces a port immediately in the forwarding state to reduce the time for the spanning tree toreconverge18Refer to the exhibit. VTP pruning is enabled in the VTP domain that is shown. How will switch ST-1 handle Layer 2 broadcast traffic originating from host A on switch ST-C?It will be dropped.It will be forwarded out port Fa0/5 only.It will be forwarded out ports Fa0/5 and Fa0/10.It will be forwarded out ports Fa0/5, Fa0/10, and Fa0/15.19Refer to the exhibit. The network administrator wants to allow both SSH and Telnet connections to Switch1. However, the SSH connections fail. What is the most likely cause of this problem?The RSA key has been removed.SSH has been configured on the wrong line.The transport input command is applied incorrectly.The domain name has been configured in the wrong configuration mode.20Refer to the exhibit. The devices in the network are operational and configured as indicated in the exhibit. However, hosts B and D cannot ping each other. What is the most likely cause of this problem?The link between the switches is up but not trunked.The Fa0/11 interface of Switch1 is not configured as a trunk.Hosts B and D are configured with IP addresses from different subnets.VLAN 20 and VLAN 30 are not allowed on the trunk between the switches.21Refer to the exhibit. Hosts A and B, connected to hub HB1, attempt to transmit a frame at the same time but a collision occurs. Which hosts will receive the collision jamming signal?only hosts A and Bonly hosts A, B, and Conly hosts A, B, C, and Donly hosts A, B, C, and E22 A network administrator implements inter-VLAN routing by configuring subinterfaces on a router.What is one important fact that must be considered?The physical interface must have an IP address configured.The subinterface numbers must match the VLAN ID number.The no shutdown command must be issued on each subinterface.The IP address of each router subinterface must be used as the default gateway for hosts on the corresponding VLAN.23W hat is the purpose of VLAN trunking?It improves network performance by reducing broadcast traffic.It selects the best path to transmit data in a switched network.It carries the traffic of multiple VLANs through a single link.It avoids spanning tree loops in a switched network.24Which parameter is used to uniquely identify one wireless network from another?SSIDOFDMWEPDSSS25W hich layers should support QoS in a hierarchical network?only the distribution and core layersonly the access and distribution layersthe access, distribution, and core layers26Refer to the exhibit. What does "FORWARDING" mean in the command output shown?The switch is sending and receiving data frames.The switch is receiving BPDUs, but not sending data frames.The switch is participating in an election process by forwarding the BPDUs it receives.The switch is receiving BPDUs and populating the MAC address table, but not sending data.27Refer to the exhibit. A network administrator is configuring RT1 for inter-VLAN routing. The switch is configured correctly and is functional. Host1, Host2, and Host3 cannot communicate with each other.Based on the router configuration, what is causing the problem?Interface Fa0/0 is missing IP address configuration information.IP addresses on the subinterfaces are incorrectly matched to the VLANs.Each subinterface of Fa0/0 needs separate no shutdown commands.Routers do not support 892.1Q encapsulation on subinterfaces.28Which switch forwarding method should be used on a network that employs frame classification based on an assigned Quality of Service (QoS) value?cut-throughfast-forwardfragment-freestore-and-forward29Refer to the exhibit. A network administrator has segmented the network into two VLANs. The connected hosts can only access resources in their own VLAN. What is the most scalable and cost effective solution to allow inter-VLAN communication in this network?Replace S1 with a router that has one FastEthernet interface for each PC.Add a second switch and divide the PCs so that each VLAN is connected to its own switch.Configure a router with two subinterfaces on one of its FastEthernet ports and connect it to S1 using a trunk link.Connect a router to a port on S1 and assign the IP address of VLAN1 to the connecting router interface.30Refer to the exhibit. A network administrator issues the show interfaces fastEthernet 0/8switchport command to check the status of the port. What can be concluded from the output?Port Fa0/8 is configured as a trunk with 802.1q encapsulation.Port Fa0/8 is configured as a trunk in VLAN 1.Port Fa0/8 is configured in access mode and associated with VLAN 1.31What will be the effect of the command S1# copy system:running-configtftp://172.16.2.155/tokyo-config?The IOS will be copied to the TFTP server.The configuration file named tokyo-config will overwrite the startup configuration file on S1.The running configuration file on S1 will be saved via TFTP to a file named tokyo-config.The contents of NVRAM on S1 will become the startup configuration file on the tokyo switch.32W hich three statements are correct concerning the default configuration of a new switch? (Choose three.)It is configured in VTP server mode.STP is automatically enabled.The first VTY line is automatically configured to allow remote connections.VLAN1 is configured with a management IP address.All switch ports are assigned to VLAN1.The enable password is configured as cisco.33Refer to the exhibit. What would happen if the network administrator moved the network cable of Host A from interface Fa0/1 to Fa0/3 on switch SW1?Host A remains a member of VLAN 10, because the router is routing traffic between VLANs.Host A is no longer a member of VLAN 10, because port Fa0/3 has been manually assigned to VLAN 30.Host A remains a member of VLAN 10, because the switch provides dynamic VLAN assignment for the port.Host A maintains connectivity to all members of VLAN 10, because it is connected to the same physical network.Host A is no longer a member of VLAN 10, but because port Fa0/3 was unused, it is now amember of VLAN 1.34Refer to the exhibit. Switches S2 and S3 are properly connected using an ethernet cable. A network administrator has configured both switches with VTP, but S3 is unable to propagate VLANs to S2.What could be the reason for this?The VTP configuration revision is different on both switches.The VTP domains are different on both switches.VTP pruning is disabled.VTP v2 is disabled.35Refer to the exhibit. Users A and B are reporting intermittent connectivity problems. Pre-installation surveys showed strong signal strength from the AP locations to the client locations. Outside electricalIncrease the distance between the clients.Change the channel on AP-B to 6 or 11.Place AP-A and AP-B on the same wireless channel.36I n which mode is a VTP switch operating if it does not allow for the creation of local VLANs but it does accept VLAN updates from other switches in the same domain?clientrootservertransparent37Refer to the exhibit. The Layer 2 switching design that is shown has been implemented in a campus environment that is using Spanning Tree Protocol. All inter-switch links that are shown are trunks.Whenever an inter-switch link fails, the network takes nearly a minute to completely converge. How can the convergence time be reduced?Increase the capacity of the distribution and core trunk links to 10 Gb/s.Use Layer 3 switching on the core switch.Implement Rapid Spanning Tree Protocol.38Refer to the exhibit. Router R1 is properly configured for router on a stick inter-VLAN routing, but PC1 is unable to ping PC2. What needs to be done to resolve the problem?Rename VLAN1.Connect one more port of S1 to R1.Configure the Fa0/1 port of S1 as a trunk port.Move the Fa0/0 interface of R1 to another VLAN.39What is a result of improperly implementing a network with redundancy at Layer 2?an increase of unicast and multicast errors at Layer 3a decrease in the amount of broadcast trafficend device malfunction because of broadcast storms40W hy is it important that the network administrator consider the spanning-tree network diameter when choosing the root bridge?The network diameter limitation is 9.BPDUs may be discarded because of expiring timers.The cabling distance between the switches is 100 meters.The network diameter must be set to the number of meters of the cable between the root bridge and its farthest connected switch.41Refer to the exhibit. A network administrator needs to add IP phones to the network. To whichdevices should the IP phones connect?AS1 and AS2DS1 and DS2DS1, DS2, and CS1AS1, AS2, DS1, and DS242Which device or devices should have the Spanning Tree Protocol enabled to prevent host traffic from creating a broadcast storm?Core_S1Access_S2 and Access_S3Core_S1, Access_S2, and Access_S3Core_S1, Access_S2, Access_S3, and R143Refer to the exhibit. All edge ports are configured with the spanning-tree portfast command. Host1 is recently connected to port Fa0/1 on switch SW1 . Which statement is true about the status of port Fa0/1?The port will transition into blocking state.The port will transition immediately into forwarding state.The port will transition into blocking state and then immediately into forwarding state.The port will transition into blocking state and immediately transition through the listening and learning states.44A network administrator enables sticky learning on all access mode interfaces of a Catalyst switch, saves the configuration, then connects hosts to the switch. After the switch operates for several days, the administrator reboots the switch without saving the running configuration. What is the result?All previously learned MAC addresses are lost.The switch reverts to non-sticky dynamic learning.Connected hosts are no longer able to communicate with the switch.Previously learned sticky addresses are retained in the switch configuration.45The network administrator wants to configure a switch to pass VLAN update information to other switches in the domain but not update its own local VLAN database. Which two steps should the administrator perform to achieve this? (Choose two.)Reset the VTP counters.Configure VTP version 1 on the switch.Configure the VTP mode of the switch to transparent.Verify that the switch has a higher configuration revision number.Configure the switch with the same VTP domain name as other switches in the network.46Which statement regarding the service password-encryption command is true?The service password-encryption command is entered at the privileged EXEC mode prompt.The service password-encryption command encrypts only passwords for the console and VTY ports.The service password-encryption command encrypts all previously unencrypted passwords in the running configuration.To see the passwords encrypted by the service password-encryption command, enter the no service password-encryption command.47Refer to the exhibit. The network consists of four hubs and a switch. The hosts connected to each hub are assigned addresses in the respective VLAN as shown. PC1 on VLAN 1 becomes infected with a virus and initiates a continuous IP broadcast. Which hubs will receive the broadcasts?Hub AHubs A and BHubs A and CHubs A, B, C, and D48 A wireless LAN access point will convert traffic between which two frame encapsulation types?802.1 and 802.11802.3 and 802.11802.3 and 802.16802.5 and 802.1649I n the implementation of PVST+ in a specific VLAN where all switches have default spanning tree priorities, which spanning-tree command setting could be assigned to force one of the Catalyst switches to become and remain the root bridge?root primarypriority 8192priority 2048spanning-tree mode rapid pvst50Refer to the exhibit. The teacher host is connected to port Fa0/7 on switch STW. A student hasdecided to share access to the Internet by attaching a hub and laptop to STW as shown. What will be the result of the student making this connection?The Fa0/7 port of STW will be shutdown.The student will gain full access to the Internet.Both the teacher and student will be able to receive data but only the teacher will be able to send.The frames from the laptop will be dropped, but the teacher host will maintain connectivity with the network.51Refer to the exhibit. Switch SW2 was tested in a lab environment and then inserted into a production network without reloading its configuration. After the trunk link between SW1 and SW2 was brought up, all users lost connectivity to the network. What could be the source of the problem?All the VLANs were pruned from the trunk port between SW1 and SW2.SW1 and SW2 cannot be both set as VTP servers in the same VTP domain.VTP configuration revision number of SW2 was higher than the configuration revision number of SW1.The additional VLANs from SW2 created more VLANs than the VLAN database of SW1 could contain.。
ccna第三学期1-7套练习题答案(最新)

ESwitching Chapter 1 - CCNA Exploration: LAN 交换和无线(版本4.0)1、分层网络设计模型中的哪一层称为互连网络的高速主干层,其中高可用性和冗余性是该层的关键?A.接入层B. 核心层C. 数据链路层D. 分布层E. 网络层F. 物理层2、分层网络设计模型中的哪一层提供了将设备接入网络的途径并控制允许那些设备通过网络进行通信?A. 应用层B. 接入层C. 分布层D. 网络层E. 核心层3、分层设计模型中的哪一层使用策略来控制网络流量的流动并通过在虚拟局域网 (VLAN) 之间执行路由功能来划定广播域的边界?A. 应用层B. 接入层C. 分布层D. 网络层E. 核心层4、从传统的公司网络架构迁移到完全融合网络后,很可能产生什么影响?A. 可将本地模拟电话服务完全外包给收费更低的提供商B. 以太网 VLAN 结构会简化C. 会形成共享的基础架构,因此只需管理一个网络。
D. QoS 问题会大大减轻5、语音数据流和视频数据流争夺带宽的问题会减轻。
应该在分层网络的哪一层或哪几层实现链路聚合?A. 仅核心层B. 分布层和核心层C. 接入层和分布层D. 接入层、分布层和核心层6、下列哪种说法正确描述了模块化交换机?A. 外形纤细B. 允许通过冗余背板进行交换机互连C. 物理特性固定D. 特性灵活多变7、下列哪项功能可在交换网络中通过合并多个交换机端口来支持更高的吞吐量?A. 收敛B. 冗余链路C. 链路聚合D. 网络直径8、在处于不同的 VLAN 中的设备间配置通信需要使用 OSI 模型中的哪个层?A. 第 1 层B. 第 3 层C. 第 4 层D. 第 5 层9、企业级交换机有哪两项特点?(选择两项。
)A. 端口密度低B. 转发速度高C. 延时水平高D. 支持链路聚合E.端口数量预先确定10、Cisco 三层式分层模型中的三层都支持哪两项功能?(选择两项。
)A. 以太网供电B. 在冗余中继链路之间进行负载均衡C. 冗余组件D. 服务质量E. 链路聚合11、网络管理员选择的交换机将在网络核心层工作。
2009年CCNA最新中文版题库第三学期第五单元到final3全部答案
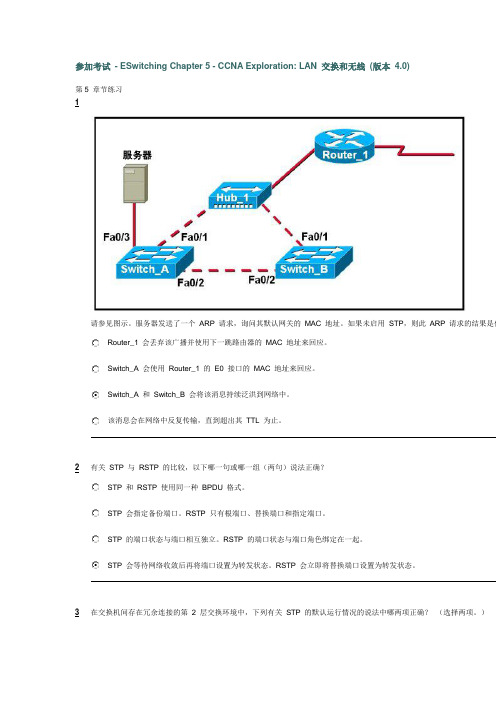
参加考试- ESwitching Chapter 5 - CCNA Exploration: LAN 交换和无线(版本 4.0)第5 章节练习1请参见图示。
服务器发送了一个ARP 请求,询问其默认网关的MAC 地址。
如果未启用STP,则此ARP 请求的结果是什Router_1 会丢弃该广播并使用下一跳路由器的MAC 地址来回应。
Switch_A 会使用Router_1 的E0 接口的MAC 地址来回应。
Switch_A 和Switch_B 会将该消息持续泛洪到网络中。
该消息会在网络中反复传输,直到超出其TTL 为止。
2有关STP 与RSTP 的比较,以下哪一句或哪一组(两句)说法正确?STP 和RSTP 使用同一种BPDU 格式。
STP 会指定备份端口。
RSTP 只有根端口、替换端口和指定端口。
STP 的端口状态与端口相互独立。
RSTP 的端口状态与端口角色绑定在一起。
STP 会等待网络收敛后再将端口设置为转发状态。
RSTP 会立即将替换端口设置为转发状态。
3在交换机间存在冗余连接的第2 层交换环境中,下列有关STP 的默认运行情况的说法中哪两项正确?(选择两项。
)根交换机是具有最高速端口的交换机。
当两个端口开销相等时,有关阻塞哪个端口的决策取决于端口优先级和身份标识。
所有中继端口均为指定端口,不会被阻塞。
根交换机上的所有端口均被设置为根端口。
每台非根交换机仅拥有一个根端口。
4在具有一个生成树实例的已收敛的网络中,将存在哪两项要素?(选择两项。
)每个网络有一个根桥所有非指定端口转发每个非根桥有一个根端口每个网段有多个指定端口每个网络有一个指定端口5每个交换以太网LAN 网段选举出的转发端口会被指派什么快速生成树协议(RSTP) 角色?备用备份指定根6当开发PVST+ 时,修改了网桥ID 是为了加入什么信息?网桥的优先级MAC 地址协议VLAN ID7端口处于哪种STP 状态下时会记录MAC 地址但不转发用户数据?阻塞学习禁用侦听转发8交换机通过哪两种方式使用BPDU 中的信息?(选择两项。
思科CCNA第三学期期末考试完整版

参加考试-ESwitchingFinalExam-CCNAExploration:LAN交换和无线(版本4.0)以下哪项参数用于唯一标识一个无线网络,使其与其它网络区分开来?SSIDOFDMWEPDSSS分层网络模型具有哪三项优点?(选择三项。
)带宽争用现象减少物理布局范围减小网络的容错能力提高无需配线间无需第三层功能管理和故障排除工作简化在将Catalyst交换机迁移到其它VTP管理域之前,应该进行哪三项任务?(项。
)选择正确的VTP模式和版本。
使用新管理域的名称配置交换机。
从新域中的VTP服务器上下载VTP数据库。
配置新域内的VTP服务器,使其识别该交换机的BID。
重置VTP计数器,使交换机可与新域内的其它交换机同步。
检验交换机的配置修订版号是否比新域内的其它交换机的低。
下列哪两种说法正确地描述了生成树协议?(选择两项。
)它只在第2层使用。
它在交换机上配置。
它消除了网络拓扑中的第2层环路。
它限制了端口上所允许的有效MAC地址的数量。
它使VLAN信息得以传播到网络中的其它交换机。
下列哪种方法可建立用于配置LinksysWRT300N无线接入点的管理连接?与接入点关联,然后与接入点建立超级终端会话。
以物理方式连接到接入点,然后重新启动计算机以启动配置软件。
在接入点所在的IP子网内的计算机上的web浏览器中输入接入点的默认址。
修改与接入点连接的计算机的TCP/IP属性,使其与接入点处于同一个然后重新启动计算机以建立连接。
请参见图示。
源地址并非0019.d2e4.d9f7的帧进入接口Fa0/24时会发生什么Fa0/24会变为error-disabled(错误-禁用)状态。
传入帧会被丢弃。
Fa0/24端口LED会关闭。
安全违规计数会增加。
可采用哪两种方法删除交换机的MAC地址表中的条目?(选择两项。
)关闭交换机电源并再次打开以清除所有动态获知的地址。
可采用clearswitching-tables命令删除静态配置的条目。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1窗体顶端在实施VLAN 间路由的过程中,在配置路由器的子接口时必须考虑什么重要事项?该物理接口必须配置有IP 地址。
子接口编号必须与VLAN ID 号匹配。
必须在每个子接口上运行no shutdown命令。
各个子接口的IP 地址必须是各个VLAN 子网的默认网关地址。
窗体底端2窗体顶端请参见图示。
Switch1 已正确配置图中所示VLAN。
图示配置被应用于RTA,旨在使连接到Switch1 的主机之间获得VLAN 间连通性。
管理员在测试网络后记录的报告如下:每个VLAN 中的主机可以相互通信。
VLAN5 中的主机能与VLAN33 中的主机彼此通信。
通过Fa0/5 连接到Fa0/1 的主机无法与其它VLAN 中的主机连通。
通过Fa0/5 连接到Fa0/1 的主机为何无法与位于不同VLAN 中的主机通信?路由器接口关闭。
VLAN ID 不符合子接口号。
路由器上的所有子接口地址均属于同一子网。
未将路由器配置为转发VLAN2 的流量。
物理接口FastEthernet0/0 未配置IP 地址。
窗体底端3窗体顶端网络中的设备连接到了一台配置了VLAN 的24 端口第 2 层交换机。
交换机端口0/2 至0/4 被分配给VLAN 10。
端口0/5 至0/8 被分配给VLAN 20,端口0/9 至0/12 被分配给VLAN 30。
其它所有端口被分种方案可使所有VLAN 相互通信,同时还使连接VLAN 所需的端口数量最少?使用适当的IP 地址配置端口0/13 至0/16 以进行VLAN 间路由。
向拓扑中添加一台路由器,并为路由器上的一个FastEthernet 接口配置多个子接口,分别用于VLAN 1、10、20 和30。
使用一台带有多个LAN 接口的路由器,为每个子网分配一个独立的接口,这样即可实现VLAN 间通信。
使用一台第 3 层交换机,在该交换机与路由器之间配置中继链路,并采用本征VLAN 中的一个IP 地址配置路由器的物理接口。
窗体底端4窗体顶端请参见图示。
下列哪三种说法正确描述了图中所示的网络设计?(选择三项。
)此设计不易扩展。
路由器将VLAN 合并到单个广播域内。
此设计使用了一些不必使用的交换机端口或路由器端口。
此设计超出了交换机可连接的VLAN 的最大数量。
此设计需要在交换机与路由器之间的链路上使用ISL 或802.1q 协议。
如果交换机与路由器之间的物理接口可以正常工作,则不同VLAN 中的设备可通过路由器通信。
窗体底端5窗体顶端当将路由器接口配置为VLAN 中继端口时,必须遵循哪三点要素?(选择三项。
)每个VLAN 对应一个子接口每个子接口对应一个物理接口每个子接口对应一个IP 网络或子网每个VLAN 对应一条中继链路每个子接口对应一个管理域每个子接口对应一种兼容的中继协议封装窗体底端6窗体顶端下列关于使用子接口进行VLAN 间路由的说法中哪两项正确?(选择两项。
)子接口不会争用带宽所需交换机端口多于传统的VLAN 间路由所需路由器端口少于传统的VLAN 间路由第 3 层故障排除比传统的VLAN 路由简单物理连接比传统的VLAN 路由简单窗体底端7窗体顶端请参见图示。
路由器R1 的Fa0/0 端口与交换机S1 的Fa0/1 端口相连。
在两台设备上输入图中所示的命令后,网络管理员发现VLAN 2 中的设备无法ping VLAN 1 中的设备。
此问题可能的原因是什么?R1 被配置为单臂路由器,但S1 上未配置中继。
R1 的VLAN 数据库中未输入VLAN。
生成树协议阻塞了R1 的Fa0/0 端口。
尚未使用no shutdown命令打开R1 的子接口。
窗体底端8窗体顶端某路由器有两个快速以太网接口,需要连接到本地网络中的四个VLAN。
在不降低网络必要性能的情况下,如何才能使用数量最少的物理接口达到此要求?实施单臂路由器配置。
另加一台路由器来处理VLAN 间的通信。
使用集线器将四个VLAN 与路由器上的一个快速以太网接口相连。
VLAN 之间通过另外两个快速以太网接口互连。
窗体底端9窗体顶端请参见图示。
网络管理员正确配置了RTA 以执行VLAN 间路由。
管理员将RTA 连接到SW2 上的0/4 端口,但VLAN 间路由无法工作。
原因可能是SW2 配置存在什么问题?端口0/4 未激活。
端口0/4 不属于VLAN1。
端口0/4 被配置为接入模式。
端口0/4 使用的中继协议不正确。
窗体底端10窗体顶端请参见图示。
图中所示命令用于将路由器连接到中继的上行链路。
收到的数据包发自IP 地址192.168.1.54。
The packet destination address is 192.168.1.120.路由器会如何处理此数据包?路由器会将该数据包从接口FastEthernet 0/1.1(VLAN 10 的接口)转发出去。
路由器会将该数据包从接口FastEthernet 0/1.2(VLAN 60 的接口)转发出去。
路由器会将该数据包从接口FastEthernet 0/1.3(VLAN 120 的接口)转发出去。
路由器不会处理该数据包,原因在于源地址和目的地址在同一个子网内。
路由器会丢弃该数据包,原因在于路由器所连接的网络中不存在该源地址。
窗体底端11窗体顶端请参见图示。
下列关于子接口工作情况的说法中哪两项正确?(选择两项。
)VLAN ID 为2 的传入流量由子接口fa0/0.2 处理。
VLAN ID 为0 的传入流量由接口fa0/0 处理。
子接口通过将802.1Q VLAN ID 添加到硬件地址上生成独特的MAC 地址。
此路由器上的入站流量由不同的子接口处理,具体取决于流量来自哪个VLAN。
两个子接口的可靠性都不高,因为ARP 将超时。
尽管fa0/0 线路协议已关闭,两个子接口仍处于工作状态,其线路协议也处于工作状态。
窗体底端12窗体顶端请参见图示。
从图中所示的输出可得出哪两条结论?(选择两项。
)未在FastEthernet 0/0 接口上发出no shutdown命令。
图中所示的两条直连路由会共用路由器的同一个物理接口。
必须在网络中配置路由协议才能成功实现VLAN 间路由。
在此网络中,网络172.17.10.0/24 与网络172.17.30.0/24 中的主机之间的VLAN 间路由成功完成。
必须将路由器的物理接口的IP 地址配置为此网络中主机的默认网关。
窗体底端13窗体顶端请参见图示。
所有设备的配置如图所示。
PC2 可成功ping 通R1 的F0/0 接口。
PC2 无法ping 通PC1。
此故障的原因可能是什么?R1 的F0/1 接口上未配置子接口。
需要将S1 的F0/6 接口配置为在VLAN10 中工作。
S1 的F0/8 接口处于错误的VLAN 中。
S1 的F0/6 端口不在VLAN10 中。
窗体底端14窗体顶端当网络中使用VLAN 间路由时,下列关于ARP 的说法中哪项正确?当采用单臂路由器VLAN 间路由时,每个子接口在响应ARP 请求时都会发送独立的MAC 地址。
当采用VLAN 时,交换机收到PC 发来的ARP 请求后,会使用通向该PC 的端口的MAC 地址来响应该ARP 请求。
当采用单臂路由器VLAN 间路由时,路由器会使用物理接口的MAC 地址响应ARP 请求。
当采用传统的VLAN 间路由时,所有VLAN 中的设备均使用同一个物理路由器接口作为它们的代理ARP 应答来源。
窗体底端15窗体顶端请参见图示。
PC1 尝试ping PC2 但未成功。
此故障的原因可能是什么?PC1 和R1 的F0/0.1 接口不在同一个子网内。
R1 的F0/0 接口上缺少封装。
没有为R1 的物理接口分配IP 地址。
对R1 的F0/0.3 接口的封装命令不正确。
窗体底端16窗体顶端在哪种情况下可使用单独的路由器物理接口代替单臂路由器配置进行VLAN 间路由?子网数量超过100 的网络VLAN 数量有限的网络由经验丰富的人员提供支持的网络所用路由器只有一个LAN 接口的网络窗体底端17窗体顶端传统路由与单臂路由器有何区别?传统路由只能使用单个交换机接口。
单臂路由器可使用多个交换机接口。
传统路由需要使用路由协议。
单臂路由器只需要将数据路由到直连网络。
传统路由在每个逻辑网络中使用一个端口。
单臂路由器使用子接口将多个逻辑网络连接到单个路由器端口。
传统路由使用通向路由器的多条路径,因此需要STP。
单臂路由器不提供多个连接,因此不需要使用STP。
窗体底端18窗体顶端下列关于interface fa0/0.10命令的说法中哪两项正确?(选择两项。
)该命令将VLAN 10 分配给路由器的fa0/0 接口。
该命令在单臂路由器的VLAN 间路由配置中使用。
该命令用于配置子接口。
该命令用于将fa0/0 接口配置为中继链路。
由于IP 地址应分配给物理接口,因此该命令不包括IP 地址。
窗体底端19窗体顶端启用使用单臂路由器的VLAN 间路由必须完成什么步骤?在路由器上配置物理接口并启用路由协议。
在路由器上创建VLAN 并在交换机上定义端口成员分配方案。
在交换机上创建VLAN,包含端口成员分配方案并在路由器上启用路由协议。
在交换机上创建VLAN,包含端口成员分配方案并在路由器上配置与VLAN 匹配的子接口。
窗体底端20窗体顶端请参见图示。
R1 在网络192.168.10.0/28 和网络192.168.30.0/28 之间进行路由。
PC1 可以ping 通R1 的F0/1 接口,但无法ping 通PC3。
此故障的原因是什么?PC1 和PC3 不在同一个VLAN 中。
PC3 的网络地址配置不正确。
应该将S1 的F0/11 接口分配给VLAN30。
R1 的F0/0 接口和F0/1 接口必须配置为中继接口。
