H3C IPSec配置
H3C-ER系列路由器IPSEC-VPN的典型配置

H3C-ER系列路由器IPSEC-VPN的典型配置H3CER 系列路由器 IPSECVPN 的典型配置在当今数字化的时代,企业对于数据安全和远程访问的需求日益增长。
IPSECVPN 作为一种常用的安全通信技术,能够为企业提供可靠的数据加密和远程接入服务。
H3CER 系列路由器以其出色的性能和丰富的功能,成为了实现 IPSECVPN 的理想选择。
接下来,我们将详细介绍 H3CER 系列路由器 IPSECVPN 的典型配置过程。
一、前期准备在进行配置之前,我们需要明确一些基本信息和准备工作:1、确定两端路由器的公网 IP 地址,这是建立 VPN 连接的关键。
2、规划好 IPSECVPN 的参数,如预共享密钥、IKE 策略、IPSEC 策略等。
3、确保两端路由器能够正常连接到互联网,并且网络连接稳定。
二、配置步骤1、配置 IKE 策略IKE(Internet Key Exchange,互联网密钥交换)策略用于协商建立IPSEC 安全联盟所需的参数。
在 H3CER 系列路由器上,我们可以按照以下步骤进行配置:(1)进入系统视图:```systemview```(2)创建 IKE 安全提议:```ike proposal 1```(3)设置加密算法和认证算法:```encryptionalgorithm aescbc-128authenticationalgorithm sha1```(4)创建 IKE 对等体:```ike peer peer1```(5)设置对等体的预共享密钥:```presharedkey simple 123456```(6)指定对等体使用的 IKE 提议:```ikeproposal 1```(7)指定对等体的对端 IP 地址:```remoteaddress ____```2、配置 IPSEC 策略IPSEC 策略用于定义数据的加密和认证方式。
以下是配置步骤:(1)创建 IPSEC 安全提议:```ipsec proposal proposal1```(2)设置封装模式和加密算法:```encapsulationmode tunneltransform espesp encryptionalgorithm aescbc-128esp authenticationalgorithm sha1```(3)创建 IPSEC 策略:```ipsec policy policy1 1 isakmp```(4)指定引用的 IKE 对等体和 IPSEC 安全提议:```ikepeer peer1proposal proposal1```(5)指定需要保护的数据流:```security acl 3000```(6)创建访问控制列表,定义需要保护的数据流:```acl advanced 3000rule 0 permit ip source 19216810 000255 destination 19216820 000255```3、在接口上应用 IPSEC 策略完成上述配置后,需要在相应的接口上应用 IPSEC 策略,以启用VPN 功能:```interface GigabitEthernet0/1ipsec apply policy policy1```三、配置验证配置完成后,我们可以通过以下方式进行验证:1、查看 IKE 安全联盟状态:```display ike sa```2、查看 IPSEC 安全联盟状态:```display ipsec sa```3、从一端向另一端发送测试数据,检查数据是否能够正常加密传输。
H3C华为-IPsecVPN配置教程

H3C华为-IPsecVPN配置教程H3C&华为-IPsecVPN配置教程第⼀篇:⽹关对⽹关IPSec-VPN⼀、H3C路由1、型号:MER5200;软件版本: version 7.1.064, Release 0809P07;固定外⽹IP;2、添加静态路由添加⾄对端公⽹和对端私⽹路由两条,如下图:3、创建IPsecVPN3.1 “虚拟专⽹”---“IPsecVPN”---新建-如下图:3.2 名称----⾃⾏编辑;接⼝---选择外⽹出⼝,组⽹⽅式---分⽀节点;对端⽹关---对端外⽹IP;认证⽅式---预共享密钥;预共享密钥要与对端路由⼀致;3.3 保护流配置H3C路由器下有个内⽹段需要与对端通信,就添加⼏个。
本例172.16.10.0/24与10.10.11.0/24为本地内⽹,172.24.0.0/24为对端内⽹。
注:H3C设备不需要单独再做NAT配置。
4、显⽰⾼级配置4.1 ike配置:主模式、本地外⽹、对端外⽹,关闭对等体检测,算法组推荐。
如下图:4.2 IPsec配置:按照默认配置即可。
5、监控信息待对端华为路由配置完成且正确后,监控会显⽰如下信息。
6、命令⾏检查[H3C]dis acl allDis ike saDis ipsec sa⼆、华为路由1、型号:AR1220-S,软件版本:[V200R007C00SPC900],固定外⽹IP。
2、添加静态路由添加⾄对端公⽹和对端私⽹路由两条,如下图:2、配置⾼级ACL2.1 新建“nonat”,添加⽬的地址10.10.11.0/24,172.16.10.0/24不做NAT转换两条,其他允许NAT转换;如下图2.2 新建“nj-g”,i添加本地内⽹172.24.0.0/24⾄⽬的内⽹10.10.11.0/24,172.16.10.0/24的acl,此路由⾛IPsec。
如下图2.3 创建“⽣效时间”3、NAT应⽤⾼级acl“ip业务”--“NAT”---“外⽹访问”---编辑----ACL名称选择“nonat”。
H3C IPV6之ipsec(ike预共享)典型组网配置案例

组网说明:本案例采用H3C HCL模拟器来模拟IPV6 IPSEC+IKE预共享密钥典型组网配置。
为了保证数据传输安全,在R1与R2建立Ipsec vpn隧道。
全网采用OSPFv3协议互通。
配置思路:1、按照网络拓扑图正确配置IP地址。
2、R1与R2建立IPSEC VPN隧道配置过程:第一阶段调试(基础网络配置:)R1:<H3C>sysSystem View: return to User View with Ctrl+Z.[H3C]sysname R1[R1]int loopback 0[R1-LoopBack0]ip address 1.1.1.1 32[R1-LoopBack0]quit[R1]ospfv3 1[R1-ospfv3-1]import-route direct[R1-ospfv3-1]router-id 1.1.1.1[R1-ospfv3-1]quit[R1]int gi 0/0[R1-GigabitEthernet0/0]ipv6 address 1::1 64[R1-GigabitEthernet0/0]ospfv3 1 area 0[R1-GigabitEthernet0/0]quit[R1]int gi 0/1[R1-GigabitEthernet0/1]des <connect to R2>[R1-GigabitEthernet0/1]ipv6 address 2::1 64[R1-GigabitEthernet0/1]ospfv3 1 area 0[R1-GigabitEthernet0/1]quitR2:<H3C>sysSystem View: return to User View with Ctrl+Z. [H3C]sysname R2[R2]int loopback 0[R2-LoopBack0]ip address 2.2.2.2 32[R2-LoopBack0]quit[R2]ospfv3 1[R2-ospfv3-1]router-id 2.2.2.2[R2-ospfv3-1]import-route direct[R2-ospfv3-1]quit[R2]int gi 0/1[R2-GigabitEthernet0/1]des <connect to R1> [R2-GigabitEthernet0/1]ipv6 address 2::2 64 [R2-GigabitEthernet0/1]ospfv3 1 area 0[R2-GigabitEthernet0/1]quit[R2]int gi 0/0[R2-GigabitEthernet0/0]des <connect to SW1> [R2-GigabitEthernet0/0]ipv6 address 3::1 64 [R2-GigabitEthernet0/0]ospfv3 1 area 0[R2-GigabitEthernet0/0]quitSW1:<H3C>sysSystem View: return to User View with Ctrl+Z. [H3C]sysname SW1[SW1]int loopback 0[SW1-LoopBack0]ip address 3.3.3.3 32[SW1-LoopBack0]quit[SW1]ospfv3 1[SW1-ospfv3-1]import-route direct[SW1-ospfv3-1]router-id 3.3.3.3[SW1-ospfv3-1]quit[SW1]int gi 1/0/1[SW1-GigabitEthernet1/0/1]port link-mode route [SW1-GigabitEthernet1/0/1]des <connect to R2> [SW1-GigabitEthernet1/0/1]ipv6 address 3::2 64 [SW1-GigabitEthernet1/0/1]ospfv3 1 area 0 [SW1-GigabitEthernet1/0/1]quit第一阶段测试:物理机填写IP地址:物理机能PING通SW1:第二阶段调试(IPSEC预共享密钥关键配置点):R1:[R1]acl ipv6 advanced 3000[R1-acl-ipv6-adv-3000]rule 0 permit ipv6 source 1::/64 destination 3::/64 [R1-acl-ipv6-adv-3000]quit[R1]ike keychain james[R1-ike-keychain-james]pre-shared-key address ipv6 2::2 64 key simple james [R1-ike-keychain-james]quit[R1]ike proposal 1[R1-ike-proposal-1]quit[R1]ike profile james[R1-ike-profile-james]keychain james[R1-ike-profile-james]proposal 1[R1-ike-profile-james]match remote identity address ipv6 2::2 64[R1-ike-profile-james]local-identity address ipv6 2::1[R1-ike-profile-james]quit[R1]ipsec transform-set james[R1-ipsec-transform-set-james]protocol esp[R1-ipsec-transform-set-james]encapsulation-mode tunnel[R1-ipsec-transform-set-james]esp authentication-algorithm md5[R1-ipsec-transform-set-james]esp encryption-algorithm des-cbc[R1-ipsec-transform-set-james]quit[R1]ipsec ipv6-policy james 1 isakmp[R1-ipsec-ipv6-policy-isakmp-james-1]security acl ipv6 3000[R1-ipsec-ipv6-policy-isakmp-james-1]ike-profile james[R1-ipsec-ipv6-policy-isakmp-james-1]transform-set james[R1-ipsec-ipv6-policy-isakmp-james-1]remote-address ipv6 2::2[R1-ipsec-ipv6-policy-isakmp-james-1]quit[R1]int gi 0/1[R1-GigabitEthernet0/1]ipsec apply ipv6-policy james[R1-GigabitEthernet0/1]quitR2:[R2]acl ipv6 advanced 3000[R2-acl-ipv6-adv-3000]rule 0 permit ipv6 source 3::/64 destination 1::/64 [R2-acl-ipv6-adv-3000]quit[R2]ike keychain james[R2-ike-keychain-james]pre-shared-key address ipv6 2::1 key simple james [R2-ike-keychain-james]quit[R2]ike proposal 1[R2-ike-proposal-1]quit[R2]ike profile james[R2-ike-profile-james]keychain james[R2-ike-profile-james]proposal 1[R2-ike-profile-james]local-identity address ipv6 2::1[R2-ike-profile-james]match remote identity address ipv6 2::1 64[R2-ike-profile-james]quit[R2]ipsec transform-set james[R2-ipsec-transform-set-james]protocol esp[R2-ipsec-transform-set-james]encapsulation-mode tunnel[R2-ipsec-transform-set-james]esp authentication-algorithm md5 [R2-ipsec-transform-set-james]esp encryption-algorithm des-cbc [R2-ipsec-transform-set-james]quit[R2]ipsec ipv6-policy james 1 isakmp[R2-ipsec-ipv6-policy-isakmp-james-1]security acl ipv6 3000[R2-ipsec-ipv6-policy-isakmp-james-1]transform-set james[R2-ipsec-ipv6-policy-isakmp-james-1]ike-profile james[R2-ipsec-ipv6-policy-isakmp-james-1]remote-address ipv6 2::1 [R2-ipsec-ipv6-policy-isakmp-james-1]quit[R2]int gi 0/1[R2-GigabitEthernet0/1]ipsec apply ipv6-policy james[R2-GigabitEthernet0/1]quit第二阶段测试:查看R1的IPSEC显示信息:查看R2的IPSEC显示信息:物理机依然能PING通SW1:SW1也可以PING通物理机:至此,IPV6之IPSEC预共享密钥典型组网配置案例已完成!。
H3C配置IPSEC教程实例介绍

H3C配置IPSEC教程实例介绍作为不同网络之间互相连接的枢纽,路由器系统构成了基于TCP/IP 的国际互联网络Internet 的主体脉络,也可以说,路由器构成了Internet的骨架。
这篇文章主要介绍了H3C配置IPSEC VPN教程实例(图文),需要的朋友可以参考下方法步骤H3C配置IPSEC VPN思路跟思科差不多,无非就是命令不一样的,下面就演示一下拓扑:RT1背后有个1.1.1.1网段,RT3背后有个3.3.3.3网段,ISP没有这两条路由RT2:system-viewSystem View: return to User View with Ctrl+Z.[RT2]int g0/0/0[RT2-GigabitEthernet0/0/0]ip add 12.1.1.2 24[RT2-GigabitEthernet0/0/0]quit[RT2]int g0/0/1[RT2-GigabitEthernet0/0/1]ip add 23.1.1.2 24[RT2-GigabitEthernet0/0/1]quitRT1:acl number 3000rule 0 permit ip source 1.1.1.0 0.0.0.255 destination 3.3.3.0 0.0.0.255ike proposal 1encryption-algorithm 3des-cbcauthentication-algorithm md5authentication-metod pre-sharedh group2ike peer ciscoid-type ippre-shared-key simple ciscoremote-address 23.1.1.3local-address 12.1.1.1#ipsec proposal ciscotransform espesp authentication-algorithm md5esp encryption-algorithm 3desipsec policy cisco 10 isakmpsecurity acl 3000ike-peer ciscoproposal ciscoint g0/0/0ipsec policy ciscoip route-static 0.0.0.0 0.0.0.0 12.1.1.2RT3:acl number 3000rule 0 permit ip source 3.3.3.0 0.0.0.255 destination 1.1.1.0 0.0.0.255ike proposal 1encryption-algorithm 3des-cbcauthentication-algorithm md5authentication-metod pre-sharedh group2ike peer ciscoid-type ippre-shared-key simple ciscoremote-address 12.1.1.1local-address 23.1.1.3#ipsec proposal ciscotransform espesp authentication-algorithm md5esp encryption-algorithm 3desipsec policy cisco 10 isakmpsecurity acl 3000ike-peer ciscoproposal ciscoint g0/0/1ipsec policy ciscoip route-static 0.0.0.0 0.0.0.0 23.1.1.2相关阅读:路由器安全特性关键点由于路由器是网络中比较关键的设备,针对网络存在的各种安全隐患,路由器必须具有如下的安全特性:(1)可靠性与线路安全可靠性要求是针对故障恢复和负载能力而提出来的。
H3C路由器两种ipsec gre配置总结

H3C路由器gre over ipsec和ipsec over gre的差别与配置方法概念区分IPSEC Over GRE即IPSEC在里,GRE在外。
先把需要加密的数据包封装成IPSEC包,然后再扔到GRE隧道里。
作法是把IPSEC的加密图作用在Tunnel口上的,即在Tunnel口上监控(访问控制列表监控本地ip网段-源ip和远端ip 网段-目的地),是否有需要加密的数据流,有则先加密封装为IPSEC包,然后封装成GRE包进入隧道(这里显而易见的是,GRE隧道始终无论如何都是存在的,即GRE隧道的建立过程并没有被加密),同时,未在访问控制列表里的数据流将以不加密的状态直接走GRE隧道,即存在有些数据可能被不安全地传递的状况。
GRE Over IPSEC是指,先把数据分装成GRE包,然后再分装成IPSEC包。
做法是在物理接口上监控,是否有需要加密的GRE流量(访问控制列表针对GRE 两端的设备ip),所有的这两个端点的GRE数据流将被加密分装为IPSEC包再进行传递,这样保证的是所有的数据包都会被加密,包括隧道的建立和路由的建立和传递。
无论是哪种数据流,若一方进行了加密,而另一方没有配,则无法通讯,对于GRE则,路由邻居都无法建立。
另一个概念是隧道模式和传输模式。
所谓的隧道模式还是传输模式,是针对如ESP如何封装数据包的,前提是ESP在最外面,如果都被Over到了GRE里,自然谈不上什么隧道模式和传输模式(都为隧道模式)。
只有当GRE Over IPSEC 的时候,才可以将模式改为传输模式。
IPSEC不支持组播,即不能传递路由协议,而GRE支持。
配置方法两者配置方法上差别不大,注意定义访问控制列表的流量、配置过程中的对端地址以及策略应用位置即可。
总结一下就是:gre ove ipsec在配置访问控制列表时应配置为物理端口地址,而IPSEC Over GRE中则应配置为兴趣流量网段地址。
在gre ove ipsec配置对端地址过程中全都配置为相应物理地址,而IPSEC Over GRE中则全都配置为对端tunnel口虚拟地址。
h3cer系列路由器ipsecvpn的典型配置

ER 系列路由器一端地址是静态 IP ,另一端是拨号方式获取 IP 时野蛮模式下的一对一 IPSEC VPN 的典型配置一、 组网需求:某公司存在分支机构 A 和分支机构 B ,两端的出口路由器都是 ER5200,分别为 Router A 和 Router B , Router A 处为静态 IP , Router B 处为拨号方式获取的 IP 。
现在客户想在 两个分支之间建立二、 组网图: 三、 配置步骤:当一边的地址都是静态 IP ( Router A ),别的一边是拨号 IP ( Router B )时,可采用野蛮模式建立 IPSEC VPN 。
Router A 设置: (1)设置虚接口:VPN →VPN 设置→虚接口选择一个虚接口名称和与其相应的WAN1口绑定,单击 <增加 >按钮。
(2) 设置 IKE 安全建议VPN →VPN 设置→ IKE 安全建议输入安全建议名称,并设置考据算法和加密算法分别为 MD5、3DES ,单击 <增加 >按钮。
(3) 设置 IKE 同等体VPN →VPN 设置→ IKE 同等体输入同等体名称,选择对应的虚接口 ipsec0 。
在“对端地址”文本框中输入地址为全 0,选择野蛮模式的NAME 种类,分别填写两端的 ID 。
Router B 的IP(4)设置IPSec 安全建议VPN →VPN 设置→ IPSec安全建议输入安全建议名称, 选择安全协议种类为ESP ,并设置考据算法和加密算法分别为MD5、3DES ,单击 <增加 >按钮。
(5)设置 IPSec 安全策略VPN →VPN 设置→ IPSec 安全策略Router B 设置:( 1)设置虚接口、 (2)设置 IKE 安全建议、( 4)设置 IPSEC 安全建议、( 5)设置 IPSec 安全策略,以上四步的设置与 Router A 对应的步骤设置一致。
( 3)设置 IKE 同等体VPN →VPN 设置→ IKE 同等体输入同等体名称,选择对应的虚接口ipsec0 。
H3C 华为 IPsec 配置步骤

IPsec VPN工作中感受(2010-10-11 14:06:48)来这边工作2个月。
一直没有什么大的case做,每天基本都是不知道在做什么,终于有一个Case,就是和mexico对接VPN.这两个月也看了不少的VPN方面的书籍,一直等待实践的机会。
机会来了。
我就小心翼翼完成这case。
这篇文章只是心里总结。
我配置的时候也是分两个阶段配置的,根据VPN对接表来操作的,设备是HUAWEI EUDEMON 1000.有的是默认的配置,用display curr 命令看不到你配置过的命令。
1 配置IKE,其中要配置Ike proposal 和ike peer.1.1 配置 ike proposal(各种加密算法,验证算法都是在这个里面)ike proposal 6encryption-algorithm 3des-cbcdh group2sa duration 288001.2 配置ike peerike peer mexico_moralespre-shared-key 123456!AaFWike-proposal 6remote-address *.*.*.*2 配置ipse,其中要配置ipsec proposal ,ACL和ipsec policy2.1 配置 ipsec proposal(各种加密算法,验证算法都是在这个里面)ipsec proposal 6esp authentication-algorithm sha1esp encryption-algorithm 3des2.2 配置ACL(双方的ACL要相互对称)acl number 3600rule 15 permit ip source *.*.*.* 0 destination *.*.*.* 02.3配置ipsec policy (配置这个之前要断了出口VPN组)ipsec policy 1 60 isakmpsecurity acl 3600pfs dh-group2ike-peer mexico_morales proposal 6local-address *.*.*.*sa duration time-based 3600。
H3C中IPSec的配置和应用
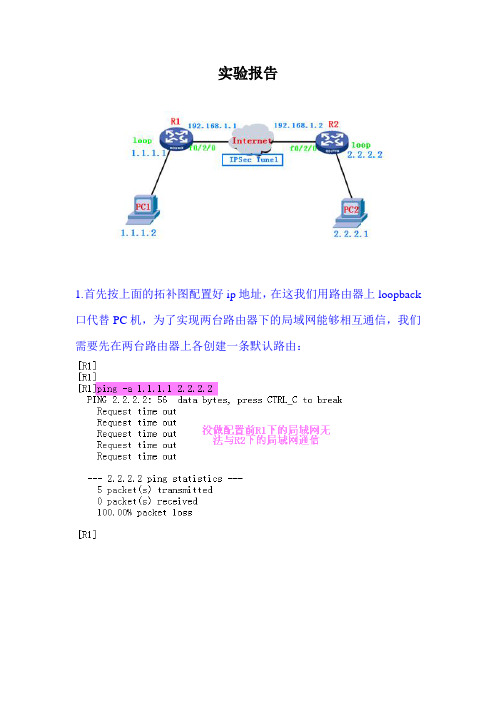
实验报告
1.首先按上面的拓补图配置好ip地址,在这我们用路由器上loopback 口代替PC机,为了实现两台路由器下的局域网能够相互通信,我们需要先在两台路由器上各创建一条默认路由:
2.现在测试一下:
3.然后我们现在路由器R1上进行配置,首先定义一条ACL列表,允许哪些数据包能够通过:
4.进行创建并配置安全提议(包含一些加密方式、认证方式、工作模
式):
5.接着进行创建并配置IKE对等体(协商时的共享密钥、远程地址):
6.然后进行创建一个安全策略,进行把刚才配置的ACl列表、安全提议和对等体进行综合在一块:
7.所有配置做完后为了使配置生效,我们进行应用到接口中:
8.此时,一端已配置好了,现在我们再到R2上进行配置:
9.然后进行创建并配置安全提议:
10. 然后进行创建并配置IKE对等体(协商时的共享密钥、远程地址):
11. 然后进行创建一个安全策略,进行把刚才配置的ACl列表、安全提议和对等体进行综合在一块:
12.然后把配置应用到接口中:
13.此时两端的配置都已做完了,我们检测一下:
14.现在进行与R1下的网络通信一下:
15.然后进行查看一些相关信息:
16.完成!!。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
目录
目录
第 1 章 IPSec配置 ...................................................................................................................1-1 1.1 IPSec简介 .......................................................................................................................... 1-1 1.1.1 IPSec的实现 ............................................................................................................ 1-2 1.1.2 IPSec基本概念 ........................................................................................................ 1-2 1.1.3 加密卡...................................................................................................................... 1-4 1.1.4 协议规范 .................................................................................................................. 1-4 1.2 IPSec配置任务简介............................................................................................................ 1-5 1.3 配置访问控制列表 .............................................................................................................. 1-6 1.4 配置安全提议 ..................................................................................................................... 1-6 1.5 配置安全策略 ..................................................................................................................... 1-7 1.5.1 手工配置安全策略.................................................................................................... 1-8 1.5.2 配置IKE协商安全策略.............................................................................................. 1-9 1.6 在接口上应用安全策略组 ................................................................................................. 1-12 1.7 在加密卡接口上绑定安全策略组或者安全策略................................................................. 1-13 1.8 使能加密引擎功能 ............................................................................................................ 1-14 1.9 使能主体软件备份功能..................................................................................................... 1-14 1.10 配置会话空闲超时时间................................................................................................... 1-14 1.11 使能解封装后IPSec报文的ACL检查功能 ....................................................................... 1-15 1.12 配置IPSec抗重放功能 .................................................................................................... 1-15 1.13 配置共享源接口安全策略组............................................................................................ 1-16 1.14 IPSec显示和维护 ........................................................................................................... 1-17 1.15 IPSec典型配置举例........................................................................................................ 1-18 1.15.1 采用手工方式建立IPSec安全隧道 ....................................................................... 1-18 1.15.2 采用IKE方式建立IPSec安全隧道......................................................................... 1-21 1.15.3 使用加密卡进行加/解密和认证 ............................................................................ 1-24 1.15.4 配置IPSec接口备份 ............................................................................................. 1-27iΒιβλιοθήκη 操作手册 安全分册 IPSec
目录
2.4 配置IKE安全提议................................................................................................................ 2-4 2.5 配置IKE对等体 ................................................................................................................... 2-5 2.6 配置Keepalive定时器 ......................................................................................................... 2-7 2.7 配置NAT Keepalive定时器................................................................................................. 2-8 2.8 配置对等体存活检测 .......................................................................................................... 2-9 2.9 配置取消对next payload域的检查 ...................................................................................... 2-9 2.10 IKE显示和维护 ............................................................................................................... 2-10 2.11 IKE典型配置举例 ........................................................................................................... 2-10
第 2 章 IKE配置.......................................................................................................................2-1 2.1 IKE简介 .............................................................................................................................. 2-1 2.1.1 IKE的安全机制......................................................................................................... 2-1 2.1.2 IKE的交换过程......................................................................................................... 2-2 2.1.3 IKE在IPSec中的作用............................................................................................... 2-2 2.1.4 IPSec与IKE的关系 .................................................................................................. 2-3 2.2 IKE配置任务简介................................................................................................................ 2-3 2.3 配置本端安全网关的名字 ................................................................................................... 2-4
