网络编程大作业4
JAVA网络编程大作业

XX大学考查课考试(大作业) SocketChannel通信系统设计与实现学号姓名所在学院学科、专业考试科目考试日期课程学时考试形式_____ _____ 评语:1. javasocket通信开发原理:所谓javasocket通信通常也称作"套接字",用于描述IP地址和端口,是一个通信链的句柄。
应用程序通常通过"套接字"向网络发出请求或者应答网络请求。
服务器,使用ServerSocket监听指定的端口,端口可以随意指定(由于1024以下的端口通常属于保留端口,在一些操作系统中不可以随意使用,所以建议使用大于1024的端口),等待客户连接请求,客户连接后,会话产生;在完成会话后,关闭连接。
客户端,使用Java socket通信对网络上某一个服务器的某一个端口发出连接请求,一旦连接成功,打开会话;会话完成后,关闭Socket。
客户端不需要指定打开的端口,通常临时的、动态的分配一个1024以上的端口。
2.设计目的:利用ServerSocketChannel和SocketChannel这两个套接字创建一个由阻塞模式的客户端与非阻塞模式的服务器端组成的网络通信应用程序。
它能实现客户端到服务器端之间的互发消息的功能。
并且由非阻塞模式构建的服务器端可以实现与多个客户端之间的通信。
3.设计思路及源代码:客户端:客户端的主要方法有talk(),在该方法中,通过socketChannel.socket()方法获得与socketchannel关联的Socket对象然后从这个Socket对象中获取输入流和输出流在一行行的接受和发送数据。
客户端不需要同时建立与多个服务器的连接,因此用一个线程,按照阻塞模式运行就能满足需求。
阻塞模式比较适用于同步通信,并且通信双方可稳定的发送小批量的数据,双方都不需要花很长时间等待对方的回应,并且能保持数据的完整性。
创建一个EchoClient的实例类,并且调用socketChannel.connect()方法连接远程服务器。
计算机网络大作业

计算机网络大作业专业:班级:姓名:学号:一、介绍该通信软件是基于C/S模式开发,是用MFC的WinSock编程原理。
该应用程序的技术主要有一下几点:1、从CAsyncSocket类派生出自己所需要的WinSock类2、WinSock类与应用程序框架之间的关系3、流式套接字的使用4、网络事件CAsyncSocket类是在很底程度上对Winsock API的封装,他提供的低级接口几乎与WinSock API的函数调用直接对应,CAsyncSocket类是从CObject类派生而来。
所谓套接字(socket)是一种网络变成接口,它是对通信短点的一种抽象,提供了一种发送和接收数据的机制。
套接字是通信的基石,一个套接字是通信的一端。
在通信的任何一端上,用户可以找到与套接字对应的一个套接字名字,每一个正在被使用的套接字都有它的类型和与其相关的进程。
套接字存在于通信域中,通信域是为了处理一般的通过套接字通信的线程而引进的一种抽象概念。
二、整体流程图1、启动与发送开始启动服务器,使其处于侦听状态启动客户机,与服务器进行连接发送数据是否发送成功否提示:发送失败!是将数据显示在发送的数据列表框中2、接收开始接收数据的事件被触发显示受到的数据到接收的数据列表框中二、主要代码1、创建派生的套接字类之后,向该套接字中添加一个成员变量,用作指向父对话框口德指针。
//设置CTalkDlg类的指针void CMySocket::SetParent(CTalkDlg *pDlg){//设置成员变量m_pDlg=pDlg;}2、接收、连接、关闭是近啊处理函数//事件处理函数void CMySocket::OnAccept(int nErrorCode){if(nErrorCode==0)//call the dialog's OnAccept functionm_pDlg->OnAccept();}//事件处理函数void CMySocket::OnConnect(int nErrorCode){if (nErrorCode==0)m_pDlg->OnConnect();}void CMySocket::OnRecive(int nErrorCode){if(nErrorCode==0)m_pDlg->OnReceive();}void CMySocket::OnClose(int nErrorCode){if(nErrorCode==0)m_pDlg->OnClose();}3、因为对话框需要两个套接字,所以要向对话框类(CTalkDlg)中添加两个成员变量。
网络编程作业

网络编程大作业学号:姓名:班级:指导老师:一、绪论近年来,互联网发展日新月异,网络使空间的距离不再成为人们沟通的障碍,世界各个角落的人们可以通过Internet收发邮件、实时聊天、获取最新的资讯,本文将讨论一种基于Socket的局域网通信工具的设计与实现方法。
基于Socket的局域网通信软件可以为企业原有的局域网提供一种良好、安全、快速的通信机制。
它的实现无需对企业原有的局域网硬件进行任何改动,具有实现成本低廉的优点,它的使用能有效地降低局域网通信负荷,提高局域网的使用效率,可以很好地解决企业内部局域网的各种通信需求。
它很好地诠释了Socket通信的原理,并且在企业内部通信、教学、讨论等应用中都具有一定的实用价值。
它具有信息收发速度快,保密性好,占用网络带宽资源低,占用服务器吞吐能力低,易于编程实现等优点。
基于Socket的局域网通信软件应用范围广阔,不但可以处理传统的通信需求,而且也能扩展以适应新型的网络应用,如网络教育,数据影音传输等,拥有广泛的应用前景。
二、总体设计(一)聊天室的设计目标本课题是建立聊天通信模型,设计一个聊天室软件,包括服务器端和客户端。
服务器端功能:初始化Socket,创建服务器端;)维护一个链表,保存所有用户的IP地址、端口信息;接受用户传送来的聊天信息,然后向链表中的所用用户转发;接受用户传送来的连接判断命令,并向用户发出响应命令。
客户端功能:客户端界面上的两个文本框,一个用于显示接受的聊天信息,一个用来接受用户输入的聊天信息。
当按下“发送”按钮时将信息发送给服务器。
通过本课题的毕业设计,可以比较深入的了解和掌握Winsock控件基本属性、方法和事件,理解网络聊天通信的概念,输控制协议(TCP)进行数据交流,初步掌握网络聊天通信程序的设计方法。
并能巩固和扩展大学期间的学习内容,进行项目的设计开发训练,更好的适应社会的需求。
(二)聊天室的实现思想聊天室程序一般都是以服务器提供服务端连接响应,使用者通过客户端程序连接到服务器,就可以与在同一服务器上的用户交谈,这是一个面向连接的通信过程。
网络编程大作业

华北科技学院《网络编程B》大作业班级: 计科B08-1 姓名:___ _____作业题目:网上答疑系统评阅成绩:____教师:_____年月日1 引言1.1课程设计选题《网上答疑系统》1.2课程设计的目的通过这次设计的程序,可以帮助我们更进一步掌握的相关编程知识。
更数量掌握的各控件的用法。
网上答疑系统方便学生老师在课下进行交流沟通,从而摆脱地点时间的限制,更有利于学生的学习。
2 系统分析与设计2.1 功能及性能分析2.1.1 功能需求在Internet飞速发展的今天,互联网成为人们快速获取、发布和传递信息的重要渠道,它在人们政治、经济、生活等各个方面发挥着重要的作用。
Internet上发布信息主要是通过网站来实现的,获取信息也是要在Internet“海洋”中按照一定的检索方式将所需要的信息从网站上下载下来。
因此网站建设在Internet应用上的地位显而易见,它已成为政府、企事业单位信息化建设中的重要组成部分,从而倍受人们的重视。
为了更好的办学,提高学校知名度。
网上答疑系统,是一种运用计算机网络为工具来帮助教师与学生教学的方式,在这个过程中它利用多媒体技术,人工智能技术,网络技术等多种技术手段。
通过教学软件,学习平台的开发和应用,使学生和计算机之间相互作用达到教学目的,这是一种现代化教学手段。
网上答疑系统是一种教育观念与教育方式的结合,它的引入,丰富了教育教学手段,向教育现代化迈出了一大步。
2.1.2 性能需求这个网上答疑系统需要设计成用户和管理员两部分。
管理员子系统管理员通过登录进入后台管理界面,可以对有关信息进行编辑,删除。
而用户通过注册登陆答疑系统,进行相关操作。
其中为了便于管理,用户包括教师和学生。
下面进行详细的功能描述:1)管理员功能:管理员登录输入用户名和密码,通过系统判断是否为管理员正确的用户名和密码,确认正确之后即可进入后台管理界面。
管理员可以对用户信息进行删除,修改,查询等功能,比如有的学生或老师密码忘记了,那么管理员帮他们查询密码,也可以帮他们修改密码,当然如果存在多次违反规矩的用户,管理员可以将其删除,也可以重新编辑一下用户的信息。
网络编程大作业

网络编程大作业选题一、基于UDP的聊天程序要求:1、能实时地收发文字消息;2、能实时地传输文件;3、用底层的socket api实现网络通信部分,不允许使用高级类的形式;4、分为服务器和客户端程序,客户端启动,连接服务器,获取当前在线的用户信息,然后再用UDP插口与另一个客户端通信。
其中服务器和客户端相连的是TCP插口;客户端和另一个客户端通信用的是UDP插口。
(类似QQ的原理)5、应用形式是基于Dialog的。
二、基于TCP的聊天程序要求:1、能实时地收发文字消息;2、能实时地传输文件;3、用底层的socket api实现网络通信部分,不允许使用高级类的形式;4、分为服务器和客户端程序,客户端启动时连接服务器,获取当前在线的用户信息,然后再用TCP插口与另一个客户端通信。
其中服务器和客户端相连的是TCP插口,并且客户端和另一个客户端相连的也是TCP插口。
(类似QQ的原理)5、应用形式是基于Dialog的。
三、FTP客户端程序1、能上传文件到ftp服务器;2、能从ftp服务器下载文件;3、用底层的socket api实现网络通信部分,不允许使用高级类的形式;4、应用形式是基于Dialog的。
四、发送邮件程序要求:1、能发送邮件;2、支持多个收信人;3、邮件至少可以附2个附件;4、用底层的socket api实现网络通信部分,不允许使用高级类的形式;5、应用形式是基于Dialog的。
五、接收邮件程序要求:1.获取所有的邮件列表;2.当指定某个邮件,显示邮件内容,若有附件,可以把所有的附件保存到本地;;3.用底层的socket api实现网络通信部分,不允许使用高级类的形式;4.应用形式是基于Dialog的。
六、类似木马程序要求:1、服务器是被施木马的机器,而客户端就是主控方。
2、客户端可以获取服务器端的驱动器名、目录名、文件名;可以强制关闭或重启服务器端的计算机;可以屏蔽服务器的开始菜单;可以按照客户机端传过来的文件名或目录名,而删除它;可以获取服务器的正在运行的进程;可以锁定和解锁服务器的鼠标;3、用底层的socket api实现网络通信部分,不允许使用高级类的形式;4、客户端程序是基于Dialog的,而服务器程序应该具有隐蔽性;提交作业内容:1、UML的静态结构图(即类图)2、程序主要流程图(UML序列图或协作图)3、程序代码4、程序说明文档。
网络编程_参考答案
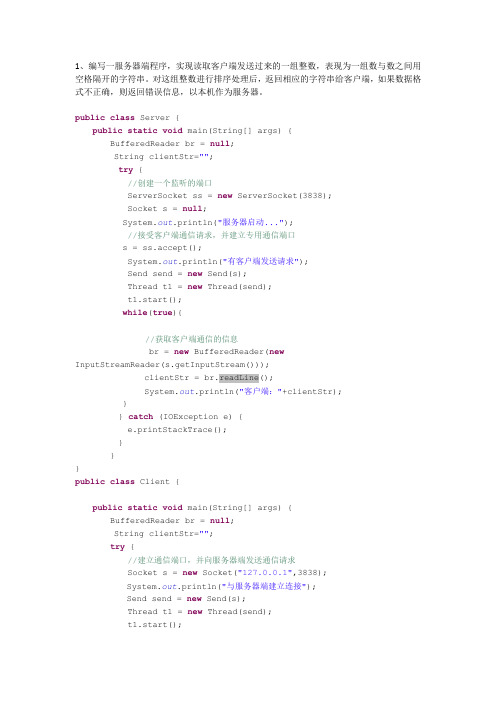
1、编写一服务器端程序,实现读取客户端发送过来的一组整数,表现为一组数与数之间用空格隔开的字符串。
对这组整数进行排序处理后,返回相应的字符串给客户端,如果数据格式不正确,则返回错误信息,以本机作为服务器。
public class Server {public static void main(String[] args) {BufferedReader br = null;String clientStr="";try {//创建一个监听的端口ServerSocket ss = new ServerSocket(3838);Socket s = null;System.out.println("服务器启动...");//接受客户端通信请求,并建立专用通信端口s = ss.accept();System.out.println("有客户端发送请求");Send send = new Send(s);Thread t1 = new Thread(send);t1.start();while(true){//获取客户端通信的信息br = new BufferedReader(newInputStreamReader(s.getInputStream()));clientStr = br.readLine();System.out.println("客户端:"+clientStr);}} catch (IOException e) {e.printStackTrace();}}}public class Client {public static void main(String[] args) {BufferedReader br = null;String clientStr="";try {//建立通信端口,并向服务器端发送通信请求Socket s = new Socket("127.0.0.1",3838);System.out.println("与服务器端建立连接");Send send = new Send(s);Thread t1 = new Thread(send);t1.start();while(true){//获取客户端通信的信息br = new BufferedReader(new InputStreamReader(s.getInputStream()));clientStr = br.readLine();System.out.println("服务器端说:"+clientStr);}} catch (UnknownHostException e) {// TODO Auto-generated catch blocke.printStackTrace();} catch (IOException e) {// TODO Auto-generated catch blocke.printStackTrace();}}}public class Send implements Runnable{Socket s ;Scanner in = new Scanner(System.in);BufferedReader br = new BufferedReader(new InputStreamReader(System.in));public Send(Socket s){this.s = s;}public void run() {// TODO Auto-generated method stubPrintWriter out = null;try {while(true){out = new PrintWriter(newOutputStreamWriter(s.getOutputStream()),true);String str = in.next();//br.readLine();out.println(str);}} catch (Exception e) {// TODO Auto-generated catch blocke.printStackTrace();}finally{out.close();}}}4、编写一个简单的socket通讯程序:1)、客户机程序,从控制台输入字符串,发送到服务器端,并将服务器返回的信息显示出来。
网络程序设计考试大作业

ﻩﻩﻩﻩnewThread(hs)、start();
ﻩﻩﻩ}
ﻩ}catch(IOExceptione){
ﻩSystem、out、println(”客户连接服务器失败”);
ﻩ}
ﻩ}
}
ﻩ//内部类处理一个Socket,接收一个Client发送过来得消息,并且服务器原封不动得返回给所有客户端,客户端对消息进行过滤
ﻩﻩSocketclient=clientConnection、get(i);
ﻩﻩOutputStreamos=client、getOutputStream();
ﻩPrintStreamps=newPrintStream(os);
ﻩﻩﻩﻩps、println(s);
ﻩﻩﻩﻩ}
ﻩﻩ}while(flag);
网络程序设计考试大作业
题目:聊天室程序
班级:
学号:
姓名:
成绩:
网络程序设计考试大作业ﻩ1
二。 程序设计思想及程序设计流程框图ﻩ3
三.主要代码及代码运行结果ﻩ4
1、启动服务器ﻩ4
2、登录ﻩ6
3、注册ﻩ10
4、 登录与注册判定ﻩ12
5、进入聊天界面ﻩ13
6、私聊页面17
一
背景:根据现在最流行得聊天工具QQ,模仿一部分主要功能来完成.
ﻩﻩﻩInputStreamis=client、getInputStream();
ﻩInputStreamReaderisr=newInputStreamReader(is);
ﻩBufferedReaderbr=newBufferedReader(isr);
ﻩﻩSystem、out、println(”第"+clientNum+”个客户端连接进入服务器");
网络程序设计考试大作业

网络程序设计考试大作业题目: 聊天室程序班级:学号:姓名:成绩:网络程序设计考试大作业 (1)一. 所使用的背景知识、主要函数的描述 (3)二. 程序设计思想及程序设计流程框图 (3)三. 主要代码及代码运行结果 (4)1.启动服务器 (4)2.登录 (6)3.注册 (10)4.登录和注册判定 (12)5.进入聊天界面 (13)6.私聊页面17一. 所使用的背景知识、主要函数的描述背景:根据现在最流行的聊天工具QQ, 模仿一部分主要功能来完成。
主要函数:public class Server;服务器的创建。
public class Client;客户端的创建。
public class UserInformation;用户信息的保存和验证。
二. 程序设计思想及程序设计流程框图设计思想:利用socket与server socket在客户端与客户端之间的通信, InputStream InputStreamReader输入输出流进行信息的发送与接收。
程序设计流程:主页面: 输入账号与密码, 点击登录或者注册进入下一页面。
登录:判定是否正确, 正确则进去聊天界面。
注册: 进去注册界面, 成功则返回主页面。
进入聊天室: 能发送信息让在线的所有人看到。
私聊界面:能与一个人单独聊天, 信息只能被双方看到。
三. 主要代码及代码运行结果1.启动服务器代码:public class Server {ServerSocket server ;static int clientNum = 0;// 存放与服务器连接上的对应的Socket, 作用是保存服务器与客户端之间的流, 便于服务器给每个客户端进行回发消息List<Socket> clientConnection = new ArrayList<Socket>();public Server() {try {server = new ServerSocket(9999);System.out .println("服务器已经启动");} catch (IOException e ) {e .printStackTrace();System.out .println("服务器启动失败");}}// 内部类, 监听客户端是否有连接到服务器, 并将此客户端的Socket传递给HandleSocket进行处理, 同时将client存放到List中, 即clientConnection中class SocketListener implements Runnable {public void run() {Socket client;try {while (true) {client = server.accept();// 连接上一个就压入List中, 即clientConnection中clientConnection.add(client);HandleSocket hs = new HandleSocket(client);// 连接上就让HandleSocket去处理new Thread(hs).start();}} catch (IOException e) {System.out.println("客户连接服务器失败");}}}// 内部类处理一个Socket,接收一个Client发送过来的消息, 并且服务器原封不动的返回给所有客户端, 客户端对消息进行过滤class HandleSocket implements Runnable {Socket client;HandleSocket(Socket client) {this.client = client;}public void run() {try {clientNum++;// 启用输入流InputStream is = client.getInputStream();InputStreamReader isr = new InputStreamReader(is);BufferedReader br = new BufferedReader(isr);System.out.println("第" + clientNum + "个客户端连接进入服务器");boolean flag = true;String s;do {// 对用户发来的消息进行群发给客户端s = br.readLine();System.out.println("接受到一个客户端消息: " + s);for (int i = 0; i < clientConnection.size(); i++) {Socket client = clientConnection.get(i);OutputStream os = client.getOutputStream();PrintStream ps = new PrintStream(os);ps.println(s);}} while (flag);client.close();} catch (IOException e) {System.out.println("有一个客户断开与服务器的连接");}}}界面:2.登录代码:package com.qq.main;import java.awt.Color;import java.awt.Dimension;import java.awt.Toolkit;import java.awt.event.ActionEvent;import java.awt.event.ActionListener;import javax.swing.JButton;import javax.swing.JFrame;import javax.swing.JLabel;import javax.swing.JOptionPane;import javax.swing.JPasswordField;import javax.swing.JTextField;import com.qq.regist.Regist;import erInformation;/*** 主界面*/public class Main extends JFrame {//组件的内容private JLabel userId;private JLabel userPassword;private JTextField inputId;private JPasswordField inputPassword;private JButton btLogin;private JButton btRegist;Main() {userId = new JLabel("帐号");userPassword = new JLabel("密码");inputId = new JTextField(6);inputPassword = new JPasswordField();btLogin = new JButton("登陆");btRegist = new JButton("注册");// 设置窗体属性Toolkit tk = Toolkit.getDefaultToolkit();Dimension screenSize = tk.getScreenSize();//得到当前屏幕的长和宽int x = (int) screenSize.getWidth();int y = (int) screenSize.getHeight();this.setBounds((x - 240) / 2, (y - 600) / 2, 240, 600);//窗口显示的大小 , 位置this.setResizable(false);//窗口大小不能改变this.setLayout(null);//默认的格式this.setBackground(Color.BLACK);// 窗口的颜色this.setDefaultCloseOperation(JFrame.EXIT_ON_CLOSE);//退出程序// 设置JLabel属性userId.setBounds(30, 160, 40, 20);userPassword.setBounds(30, 200, 40, 20);// 设置文本域属性inputId.setBounds(90, 160, 100, 20);inputPassword.setBounds(90, 200, 100, 20);inputPassword.setEchoChar('*');//用*显示代替你输入的密码// 设置JButton属性btLogin.setBounds(50, 240, 60, 20);btRegist.setBounds(120, 240, 60, 20);// 注册“登陆”按钮监听器btLogin.addActionListener(new ActionListener() {public void actionPerformed(ActionEvent e) {UserInformation user = new UserInformation();String userName = inputId.getText();String userPassword = new String(inputPassword.getPassword());if (userName.equals("")) {JOptionPane.showMessageDialog(null, "用户名不能为空");} else if ("".equals(userPassword)) {JOptionPane.showMessageDialog(null, "密码不能为空");} else if (user.isExist(userName)&& erInfomation.getProperty(userName).equals(userPassword)) {new AllTalkFrame(userName).setVisible(true);// 判断成功后new一个群聊窗口Main.this.dispose();} else {JOptionPane.showMessageDialog(null, "此用户名不存在或者密码不正确");}}});// 注册“注册”按钮监听器btRegist.addActionListener(new ActionListener() {public void actionPerformed(ActionEvent e) {new Regist();//注册页面}});this.add(userId);this.add(userPassword);this.add(inputId);this.add(inputPassword);this.add(btLogin);this.add(btRegist);this.setVisible(true);}public static void main(String[] args) {new Main();}}界面:3.注册代码:// 注册“提交”按钮的监听器btSubmit.addActionListener(new ActionListener() {public void actionPerformed(ActionEvent e) {String userName = inputId.getText();String userPassword = newString(inputPassword.getPassword());String userPasswordConfirm= new String(inputPasswordConfirm.getPassword());System.out.println("您点击了提交按钮");if (userName.equals("")) {JOptionPane.showMessageDialog(null, "用户名不能为空");} else if ("".equals(userPassword)|| "".equals(userPasswordConfirm)) {JOptionPane.showMessageDialog(null, "密码和密码重复都不能为空");} else if (!userPassword.equals(userPasswordConfirm)) {JOptionPane.showMessageDialog(null, "密码和密码重复不一致");} else {UserInformation user = new UserInformation();if (user.isExist(userName)) {JOptionPane.showMessageDialog(null, "此用户名已存在");} else {JOptionPane.showMessageDialog(null, "注册成功");user.insert(userName,userPassword);//UserInformation类Regist.this.dispose();}}}});// 注册“取消”按钮的监听器btCancel.addActionListener(new ActionListener() {public void actionPerformed(ActionEvent e) {System.out.println("您点击了取消按钮");Regist.this.dispose();}});界面:4.登录和注册判定代码://注册一个用户public void insert(String userName, String userPassword) { try {userInfomation = new Properties();InputStream is;OutputStream os;is = new ("c:/userInfo.properties");os = new ("c:/userInfo.properties", true);userInfomation.load(is);// 将用户名和密码存储到内存中userInfomation.setProperty(userName, userPassword);// 将用户名和密码保存到文件中userInfomation.store(os, null);} catch ( e1) {System.out.println("文件userInfo.properties没有找到 ");} catch (IOException e) {System.out.println("写 userInfo.properties 出错");}}//判断此用户名是否存在public boolean isExist(String userName) {try {userInfomation = new Properties();InputStream is;is = new ("c:/userInfo.properties");userInfomation.load(is);if (userInfomation.containsKey(userName)) {return true;}} catch ( e1) {System.out.println("文件userInfo.properties没有找到 ");} catch (IOException e) {System.out.println("写 userInfo.properties 出错");}return false;}5.进入聊天界面代码:class showOldMessageThread implements Runnable {public void run() {boolean flag = true;while (flag) {try {// 接收群聊服务器端回发过来的消息String serverOutput = client.br.readLine() + "\r\n";if (!serverOutput.startsWith("私聊")&& !serverOutput.startsWith("*")&& !(serverOutput.substring(serverOutput.indexOf(": ") + 1).equals("\r\n"))) {String s1 = serverOutput.replace('说', ' ');String s = s1.replaceAll("�", "\r\n ");oldMessageTextArea.append(s);}// 添加客户端的用户在线列表if (!serverOutput.startsWith("*")&& !serverOutput.startsWith("私聊")&& (serverOutput.indexOf("说") != -1)) {String listName = serverOutput.substring(0,serverOutput.indexOf('说'));// 如果JList中有相同名字的用户, 则不添加, 否则添加if (!users.contains(listName)) {System.out.println("用户" + listName + "上线了");users.add(listName);userList.setListData(users);}}// 判断服务器回发过来的消息是不是以"私聊"开头的, 是的话就提取出这两个用户名if (serverOutput.startsWith("私聊")) {String siliaoName1 = serverOutput.substring(serverOutput.indexOf("*") + 1, serverOutput.indexOf("和"));String siliaoName2 = serverOutput.substring(serverOutput.indexOf("和") + 1, serverOutput.indexOf("\r"));String siliaoBenshen = "";String siliaoDuixiangName = "";if (siliaoName1.equals(clientName)) {siliaoBenshen = siliaoName1;siliaoDuixiangName = siliaoName2;} else {siliaoBenshen = siliaoName2;siliaoDuixiangName = siliaoName1;}// 判断这两个名字中是否有与自己同名的, 有的话就弹出个私聊窗口if (siliaoName1.equals(clientName)|| siliaoName2.equals(clientName)) {new PointToPointTalkFrame(siliaoBenshen + "和"+ siliaoDuixiangName).setVisible(true);}}} catch (IOException e1) {System.out.println("读取服务器端消息出错");}}}}// 注册JList的点击事件, 进入私聊界面userList.addMouseListener(new MouseAdapter() {public void mouseClicked(MouseEvent e) {if (e.getClickCount() == 2) {if (erList.getSelectedValue().toString().equals(clientName)) {JOptionPane.showMessageDialog(null, "不能和自己聊天");} else {String PToPMemberName = "私聊"+ "*"+ clientName+ "和"+erList.getSelectedValue().toString();client.ps.println(PToPMemberName);}}}});界面:6.私聊页面代码:// 线程: 只要服务器端有消息, 就将消息显示到oldMessageTextAreaclass showOldMessageThread implements Runnable {public void run() {boolean flag = true;while (flag) {try {// 接收服务器端回发过来的消息String serverOutput = client.br.readLine() + "\r\n";System.out.println("私聊服务器发过来的消息: " + serverOutput);// 将消息中的两个用户名提取出来String s1 = "";if (serverOutput.startsWith("私聊")) {String[] s;if (serverOutput.startsWith("私聊*")) {s = serverOutput.substring(3,serverOutput.indexOf("\r")).split("和");} else {s = serverOutput.substring(2,serverOutput.indexOf("说")).split("和");}for (int i = 0; i < s.length; i++) {s1 = s1 + s[i];}}// 将标题中的两个用户名提取出来,有两种顺序String[] title = clientName.split("和");String s2 = "";for (int i = 0; i < title.length; i++) {s2 = s2 + title[i];}String s3 = "";for (int i = title.length - 1; i >= 0; i--) {s3 = s3 + title[i];}// 判断服务器端返回消息中的两个用户名等于客户端的两个用户名(忽略顺序), 则将消息显示出来(也就是显示在私聊窗口上)if (s1.equals(s2) || s1.equals(s3)) {String ss1 = serverOutput.substring(2, serverOutput.indexOf("和"));String ss2 = serverOutput.substring(serverOutput.indexOf(": "));// 将私聊客户端返回来的一行字符串按"�"进行拆分成多行, 显示在私聊的oldMessageArea中if (ss2.indexOf("�") != -1) {ss2 = ss2.replaceAll("�", "\r\n ");}oldMessageTextArea.append(ss1 + ss2);}} catch (IOException e1) {System.out.println("读取服务器端消息出错");}}}}界面:。
网络编程实训大作业报告

一、引言随着信息技术的飞速发展,网络编程已经成为计算机科学与技术领域的一个重要分支。
为了提高我们的实际动手能力和理论联系实际的能力,我们选择了网络编程实训作为本次大作业。
通过本次实训,我们不仅掌握了网络编程的基本知识,还锻炼了团队协作和解决问题的能力。
以下是本次实训的大作业报告。
二、实训背景与目标1. 实训背景随着互联网的普及,网络编程技术在各个领域都得到了广泛应用。
为了提高我们的网络编程技能,我们选择了网络编程实训作为本次大作业。
2. 实训目标(1)掌握网络编程的基本概念和原理;(2)熟悉常用的网络编程技术,如TCP/IP、HTTP等;(3)掌握编程工具的使用,如Visual Studio、NetBeans等;(4)提高团队协作和解决问题的能力。
三、实训内容1. 项目概述本次实训大作业要求我们设计并实现一个基于TCP协议的简易聊天室。
该聊天室能够实现多用户同时在线聊天,用户之间可以发送文本消息。
2. 技术选型(1)编程语言:Java;(2)网络协议:TCP/IP;(3)开发工具:NetBeans;(4)数据库:无。
3. 功能模块(1)客户端模块:负责接收用户输入的消息,并将消息发送给服务器;同时,接收服务器发送的消息,显示在聊天窗口中。
(2)服务器模块:负责接收客户端发送的消息,并将消息广播给所有在线用户;同时,处理客户端的登录、注册等请求。
4. 实现步骤(1)搭建开发环境:安装Java、NetBeans等开发工具;(2)设计客户端界面:使用Swing组件设计聊天窗口、输入框、发送按钮等;(3)编写客户端代码:实现用户登录、注册、发送消息等功能;(4)编写服务器端代码:实现消息广播、用户管理等功能;(5)测试与调试:在本地环境中运行程序,进行功能测试和性能测试;(6)优化与完善:根据测试结果,对程序进行优化和改进。
四、实训成果与总结1. 成果展示本次实训大作业成功实现了一个基于TCP协议的简易聊天室,功能如下:(1)用户登录:用户可以通过用户名和密码登录聊天室;(2)发送消息:用户可以在聊天窗口中输入消息,点击发送按钮将消息发送给所有在线用户;(3)接收消息:用户可以接收其他用户发送的消息,并在聊天窗口中显示;(4)用户管理:管理员可以管理在线用户,包括查看在线用户列表、封禁用户等。
Socket网络编程大作业

网络编程技术大作业修改履历TCP/IP协议的概述TCP/IP(Transmission Control Protocol/Internet Protocol)的简写,中文译名为传输控制协议/因特网互联协议,又叫网络通讯协议,这个协议是Internet最基本的协议、Internet国际互联网络的基础,简单地说,就是由网络层的IP协议和传输层的TCP协议组成的。
TCP/IP 协议使用范围极广,是目前异种网络通信使用的唯一协议体系,适用于连接多种机型,既可用于局域网,又可用于广域网,许多厂商的计算机操作系统和网络操作系统产品都采用或含有TCP/IP协议。
TCP/IP协议已成为目前事实上的国际标准和工业标准。
基于TCP/IP协议组的网络模型分为应用层、传输层、网络层、链路层和物理层这样五个层次。
TCP/IP协议组位于应用程序和硬件之间,指挥数据在网络各层中传递。
其中传输层的协议包括传输控制协议(TCP)和用户数据报协议(UDP) ,它们都建立在IP协议的基础上,其中TCP提供可靠的面向连接服务,UDP提供简单的无连接服务。
传输层提供端到端,即应用程序之间的通信,主要功能是数据格式化、数据确认和丢失重传等。
TCP协议是面向连接的协议,它提供可靠的字节流服务,在进行数据传输之前必须先建立连接,经三次握手确定后才开始数据传送。
UDP进行数据报传输使用的是不可靠、无连接的协议。
网络层包括互连网协议 IP,互连网控制报文协议 ICMP和互连网组管理协议IGMP。
其中IP协议完成大部分的工作,负责数据传输和路由的选择等。
I P报头中的地址和网卡相联系( 具体还涉及地址解析和反向地址解析协议),TCP 、UDP报头中的端口号侧对应着网络主机上不同的程序。
TCP/IP体系结构如图一所示:TCP/IP体系结构Socket通常也称作"套接字",用于描述IP地址和端口,是一个通信链的句柄。
应用程序通常通过"套接字"向网络发出请求或者应答网络请求。
网络编程与Socket复习 题集附答案

网络编程与Socket复习题集附答案网络编程和Socket是计算机科学中重要的概念,涉及到了计算机网络的通信和数据传输。
在网络编程中,Socket是一种对TCP/IP协议的封装,通过Socket可以在网络之间建立可靠的通信连接。
在这篇文章中,我们将回顾网络编程和Socket的相关知识,并附上一些题目及其答案,帮助读者复习和加深理解。
一、网络编程基础知识1. 什么是网络编程?答:网络编程是指通过计算机网络实现程序之间的通信和数据交换的过程。
它涉及到了数据传输协议、数据格式、网络连接等方面的知识。
2. 计算机网络的通信模型有哪些?答:计算机网络的通信模型主要有两种:客户端-服务器模型和对等模型。
在客户端-服务器模型中,客户端向服务器发起请求,服务器响应客户端的请求;在对等模型中,各网络节点之间的通信是对等的,彼此可以相互发送和接收数据。
3. TCP和UDP是什么?它们有什么区别?答:TCP(传输控制协议)和UDP(用户数据报协议)是两种常用的传输层协议。
TCP提供可靠的连接,它确保数据可正确传输,并且保持连接的状态;UDP则是一种无连接的传输协议,它不保证数据的可靠性,但传输速度比TCP快。
4. 什么是Socket?它在网络编程中的重要性是什么?答:Socket是一种在网络编程中使用的编程接口,它提供了一组函数和方法,用于在网络之间建立连接、发送和接收数据。
Socket在网络编程中扮演着重要的角色,它要负责建立连接、传输数据以及处理网络通信的各种问题。
二、Socket编程题1. 编写一个简单的TCP服务器,监听本地的8000端口,并在接收到客户端的连接请求后,向客户端发送一条欢迎消息。
```pythonimport socketdef main():HOST = '127.0.0.1'PORT = 8000server_socket = socket.socket(socket.AF_INET,socket.SOCK_STREAM)server_socket.bind((HOST, PORT))server_socket.listen(10)print("Server started!")while True:client_socket, addr = server_socket.accept()print("Connected by", addr)message = "Welcome to the server!"client_socket.sendall(message.encode('utf-8'))client_socket.close()if __name__ == "__main__":main()```2. 编写一个UDP客户端,向服务器发送一条消息,并接收服务器返回的响应。
网络编程大作业

网络技术编程大作业3100103844 王博3100103896 马天亮1.文档概述撰写本文档的目的是为使用者提供必要的参考文档,使其能够通过文档说明了解一对一聊天程序的使用过程以及通信原理,为使用者提供基本的指导。
使用者或者程序开发人员可以通过本文档,快速的了解本程序的UDP通信机制,本文档还提供了程序代码,方便用户修改、学习。
适用范围:聊天程序使用者,功能相似的程序开发人员,以及其他需要了解本系统工作原理的人员。
2.软件设计目标以及开发平台本软件是基于java虚拟机,运用java语言编程,主要平台是电脑,通过UPD 通信协议,输入对方IP,实现局域网内的一对一聊天。
3.项目分工王博(主要负责软件通信协议部分的编写),马天亮(主要界面的美化)4.软件功能说明以及运行截图软件能够实现通信双方的相互交流,通信双方都具有收发信息的能力。
对方输入我的IP 222.205.56.205我输入他的IP5.软件概要设计5.1通信流程5.2 重点与难点客户端1填写对方IP 地址绑定一个固定的端口收到对方信息后处理显示客户端2收到对方信息后处理显示绑定一个固定的端口 填写对方IP 地址结束后断开连接结束后断开连接对于socket本身的编程,必须要清楚的了解相互之间的通信协议,而这一块又不是非常容易,因此可以说这块是难点也是重点6源代码以及注释import java.util.*;import .*;import java.io.*;import java.awt.*;import java.awt.event.*;import javax.swing.*;public class UDPChat extends JFrame {PrintStream st=null;private int port;//端口定义private JButton sendmessage;//发送按钮private JTextField nicknamefield;//昵称private JLabel nickname,IP,Content;java.awt.List list=new java.awt.List(20);//java.awt.List list1=new java.awt.List(20);//接收信息列表(实际上是java.awt类里一个提供可滚动的列表Vector vector=new Vector();//已发IP列表(vector本身是可以自动增加长度的)JComboBox ipInput=new JComboBox(vector);//发送对象ip(JComboBox复选框)JTextField textInput=new JTextField(50);//编辑发送内容组件DatagramSocket socket=null;//(DatagramSocket追求速度并且省去了很多连接麻烦)public UDPChat (int port) {this.port=port;try{st=new PrintStream("log.txt");//打印启动}catch(FileNotFoundException e){e.printStackTrace();}try{socket=new DatagramSocket(port);//新建socket}catch(Exception e){e.printStackTrace(st);}Container contentPane=this.getContentPane();ipInput.setPreferredSize(new Dimension(120,20));ipInput.setEditable(true);//允许编辑JPanel panel=new JPanel();//JPanel 为javax.swing包中的,为面板容器,可以加入到JFrame中 , 它自身是个容器,可以把其他compont加入到JPanel 中,如JButton,JTextArea,JTextFiled等,另外也可以在它上面绘图nicknamefield = new JTextField(5);nicknamefield.setFont(new Font("宋体", Font.BOLD, 16)); nicknamefield.setForeground(Color.black);nickname = new JLabel("昵称");nickname.setFont(new Font("宋体", Font.BOLD,16));nickname.setForeground(Color.black);IP = new JLabel("IP");IP.setFont(new Font("宋体", Font.BOLD,16));IP.setForeground(Color.black);Content = new JLabel("内容");Content.setFont(new Font("宋体", Font.BOLD,16)); Content.setForeground(Color.black);sendmessage=new JButton("发送信息");panel.setLayout(new BoxLayout(panel,BoxLayout.X_AXIS)); contentPane.add(list,BorderLayout.CENTER); contentPane.add(panel,BorderLayout.SOUTH);panel.add(nickname);//面板设置panel.add(nicknamefield);panel.add(IP);panel.add(ipInput);panel.add(Content);panel.add(textInput);panel.add(sendmessage);receive();addListener();}/***加入并处理事件听侦void addListener(){//当在textField组件中输入内容后发送按钮,即发送出输入信息。
TCPIP网络编程技术作业汇总

TCP与UDP各自特点TCP与UDP是网络层常用通信协议两者主要有以下特点:TCP:1.TCP是一种面向连接的、可靠的传输层协议;2.进行拥塞控制,当前网络发生通信拥塞时,发送者降低发送的速率,以便接收方能够有效的对数据包进行接收,尽可能的避免了发生丢包现象。
3.具有数据流的特性,数据没有边界4. 要提供可靠交付,具有差错控制功能,需要遵守三次握手协议,需要建立维持连接后,才能进行与通信方进行三次握手。
主要的应用有:HTTP超文本传输协议、FTP文件传输协议、Telnet远程连接协议、SMTP邮件传输协议UDP:1.UDP是面向无连接服务,不可靠的传输协议2.传输数据之前源端和终端不建立连接,直接将要传送的数据包发送到网络上即可,简单方便,效率高。
3.没有流量控制,极有可能会在网络通信情况不好的时候发生丢包现象。
4.没有差错控制,不能确定数据包在传输过程中信息是否发生了改变,可靠性不高主要应用:流媒体、视频会议、DNS数据包发送、Internet电话详细说明简单UDP和TCP网络编程流程TCP流程图解:对于TCP的网络编程,我认为主要分为如图所示:对于tcp接连方式服务器来说的6个流程步骤:1.程序初始化:启动SOCKET库,创建socket套接字,包括网络头文件的添加,网络编程初始化函数的调用。
2.填写本机地址信息:填写SOCKADDR_IN中能数据,设定对自身通信地址与端口号,调用bind()函数进行端口绑定。
3.监听绑定的固定的端口,调用listen()函数进行端口监听。
4.当通过accept()函数收到Client的连接请求后建立一个socket连接,或没有收到则继续监听,构成一个循环监听模块。
5.产生一个新的进程与Client进行通信和信息处理,通过receive()函数接收客户端发过来的信息并通过send()函数反馈处理后的信息。
6.子通信结束后中断与Client的连接,运用close()关闭套接字。
java语言程序设计期末考查大作业报告 3-4

《Java语言程序设计》大作业报告2019-2020学年第一学期班级:--------自己填--------学号:--------自己填--------姓名:--------自己填--------1、设计题目⑴假设车库有3个车位(可以用boolean [ ]数组来表示车库)可以停车,使用多线程模拟多个用户开车离开、停车入库的过程。
注意:车位有车时不能停车。
⑵编写一个菜单程序,要求菜单的结构如下:文件------打开------关闭系统管理------用户管理------新增用户------删除用户------退出系统要求:对退出系统添加事件、并加入快捷键CTRL+E;对新增用户添加事件、并加入快捷键CTRL+A;当点击新增用户菜单,出现一个对话框,对话框中有两个文本框(用户名和密码),同时出现两个按钮(确定和取消)。
确定按钮要有事件功能,且将输入的用户名和密码存入到一个文件中。
取消按钮事件负责完成关闭对话框功能。
2、程序设计思路(要求分步骤写清设计思路,并画出类的UML图)2.1作业32.1.1主要模块划分Park类:里面私有属性parting为车位数量初始化为3个,成员方法into (),也就是停车方法,调用该方法车位减一。
成员方法out(),调用该方法代表车子离开,车位加一。
OutThread类:继承Thread类,重写run方法,并且调用out()方法IntoThread类:继承Thread类,重写run方法,并且调用into()方法Test类:测试类,用来测试,启动OutThread类和IntoThread类线程进行测试。
2.1.2类图2.2作业42.2.1主要模块划分addActionListener:监听事件,主要用于实现鼠标事件,完成页面的打开,关闭,调用文件流;JMenuItem :菜单下拉框列表,让页面的交互性更强,提升用户体验;KeyStroke:快捷键的加入,同JMenuItem 一样,是为了提高用户的体验;2.2.2类图Jframe 类2.2.3 流程图3、 运行结果分析(截图每个关键运行点界面)菜单页面完成添加添加失败关闭窗口取消添加打开添加用户页面作业3:第一次测试,在测试类里面启动IntoThread类的线程和OutThread线程循环调用两个线程,发现只有有车位时,其他车子才能停进去作业4:运行Main函数,run us 得到一个窗口基本菜单列表展示点击新增用户,弹出添加新用户页面(默认文字为请输入新用户名):点击取消或者按ctrl+E,关闭当前窗口,并返回到窗口页面;按照要求填好用户信息,点击确认,则提示添加成功:此时打开指定文档jfram.txt则可以查看到输入的用户名和密码:4、设计中遇到的问题,解决途径及思路,经验总结。
4北邮JAVA期末大作业 聊天室开发文档

JAVA期末大作业开发文档学院:电子工程学院专业:电子信息科学与技术班级:2013211202姓名:学号:小组成员:一.选题我们三人选择了网络通信程序这一题目,题目要求包括:能够实现双方通过服务器建立通信连接,实现一对一的聊天;能够通过服务器,采用多线程实现多人间的群聊;能够实现文字通信和传输图片;能够保存通信记录到本地。
我们在此基础上还实现了发送振动消息以及发送文件的功能。
二.需求分析1.首先我们进行了系统的功能分析,这个通信程序分为客户端和服务器两个部分:服务器端主要负责监听客户端的连接请求,把这个请求通过网络发送给服务器端进行处理,把客户端(请求方)的聊天请求、发送文件请求、发送振动消息请求等转发给目标客户端(接收方):而客户端负责发送请求并处理服务器端返回的响应消息。
整体框图构造如下1.当前在线用户服 1.ServerMain.java---启动监听器 2.已注册的用户务 3.当前监听端口器监 1.用户注册听 2.用户登录模 2.server.controller.java—处理客户端的请求 3.断开连接块 4.聊天5.振动6.文件收发网络 1.当前在线用户通 3.server.ui.java—服务器信息显示窗体 2.所有注册用户信 3.时间系 1.clientMain.java---连接服务器、启动登录窗口统 1.登录窗体用 2.注册窗体整户 2.client.ui.java—显示客户端各个窗体 3.聊天窗体体模 4.提示对话框构块 5.窗体振动器架搭建3.client.clientThread.java—--客户端后台线程接收和处理服务器返回的响应4.client.util.JFrameShaker---实现窗体振动三.概要设计通过之前的需求分析,可以看出项目的包主要包括服务器和客户端两个包,然而主要功能的实现,具体需要分为以下六个模块:1)服务器监听模块2)客户端用户登录模块3)客户端客户注册模块4)聊天模块5)发送文件模块6)发送振动消息模块四.主要功能实现及大体设计过程1.服务器监听模块功能实现服务器监听模块实现了在服务器监听窗口中显示当前在线用户列表和已注册用户列表,可以通过单击标签切换选项卡。
【免费下载】计算机网络编程技术大作业

2. 运行程序进行测试
(1)首先运行 Server.java,打开“聊天室服务器”。服务器 IP 地址为 192.168.0.2 如图 2 所示。
图 2 服务器控制台 (2)服务器监听是否有新聊天者连接,如果没有,一直等待。如图 3 所示。
图 3 服务器等待 (3)运行客户端程序 client.java,打开“多人聊天室“界面,客户端 1 的 IP 地址为 192.168.0.3 客户端 2 的 IP 地址为 192.168.0.49,如图 4 所示。
(4)在“多人聊天室”界面输入框输入聊天信息。如图 5 所示。
图 5 在输入框输入聊天信息 (5)在“多人聊天室”界面发送信息。如图 6 所示。
对全部高中资料试卷电气设备,在安装过程中以及安装结束后进行高中资料试卷调整试验;通电检查所有设备高中资料电试力卷保相护互装作置用调与试相技互术关,系电,力根通保据过护生管高产线中工敷资艺设料高技试中术卷资,配料不置试仅技卷可术要以是求解指,决机对吊组电顶在气层进设配行备置继进不电行规保空范护载高与中带资负料荷试下卷高问总中题体资,配料而置试且时卷可,调保需控障要试各在验类最;管大对路限设习度备题内进到来行位确调。保整在机使管组其路高在敷中正设资常过料工程试况中卷下,安与要全过加,度强并工看且作护尽下关可都于能可管地以路缩正高小常中故工资障作料高;试中对卷资于连料继接试电管卷保口破护处坏进理范行高围整中,核资或对料者定试对值卷某,弯些审扁异核度常与固高校定中对盒资图位料纸置试,.卷保编工护写况层复进防杂行腐设自跨备动接与处地装理线置,弯高尤曲中其半资要径料避标试免高卷错等调误,试高要方中求案资技,料术编试交写5、卷底重电保。要气护管设设装线备备置敷4高、调动设中电试作技资气高,术料课中并3中试、件资且包卷管中料拒含试路调试绝线验敷试卷动槽方设技作、案技术,管以术来架及避等系免多统不项启必方动要式方高,案中为;资解对料决整试高套卷中启突语动然文过停电程机气中。课高因件中此中资,管料电壁试力薄卷高、电中接气资口设料不备试严进卷等行保问调护题试装,工置合作调理并试利且技用进术管行,线过要敷关求设运电技行力术高保。中护线资装缆料置敷试做设卷到原技准则术确:指灵在导活分。。线对对盒于于处调差,试动当过保不程护同中装电高置压中高回资中路料资交试料叉卷试时技卷,术调应问试采题技用,术金作是属为指隔调发板试电进人机行员一隔,变开需压处要器理在组;事在同前发一掌生线握内槽图部内 纸故,资障强料时电、,回设需路备要须制进同造行时厂外切家部断出电习具源题高高电中中源资资,料料线试试缆卷卷敷试切设验除完报从毕告而,与采要相用进关高行技中检术资查资料和料试检,卷测并主处且要理了保。解护现装场置设。备高中资料试卷布置情况与有关高中资料试卷电气系统接线等情况,然后根据规范与规程规定,制定设备调试高中资料试卷方案。
计算机网络课程设计大作业

研究生课程《计算机网络》课程设计论文题目:利用Java语言的Socket编程实现网络环境下两台计算机之间的字符聊天功能学院:信息工程与自动化学院专业:电子与通信工程年级:2013级学号:姓名:分数1设计项目分析1.1需求分析1.1.1性能需求利用Java 语言的Socket编程实现网络环境下两台计算机之间的字符聊天功能。
一个QQ系统由一个服务器和若干个客户端组成。
服务器和叫客户端之间通过TCP/IP网络协议通信。
客户端的为用户服务的。
客户端的功能:一是用户通过登入界面启动与服务器的连接,并发送用户的基本信息给服务器;二是客户端界面可以收到好友发送的信息,也能给好友发送信息。
服务器为客户端服务的。
服务器提供的功能是:一是等待客户端的连接,客户端连接上,保存客户端信息,并发信息告诉其它在线客户XX已经上线;二是起消息的转发作用,所有的客户聊天信息都有服务器来转发。
1.1.2环境需求运行环境:Windows xp、eclipse必要环境:JDK 1.5 以上1.2实现目标(1)登录界面,好友列表界面,聊天界面。
(2)当用户点击登录后,把QQ号码和密码发送给QqServer去验证,如果该用户合法,则返回ok,反之返回Err。
(3)完成多个好友互相聊天功能。
(4)如果好友在线,则显示彩色头像,反之,显示灰色头像。
(5)当好友上线后,提示。
(6)把接收到的消息,显示到该显示聊天界面。
(7)当一个用户上线是能看到所有的在线好友,用户可以群聊也可以选择某个人单独聊天。
2 系统设计2.1模型分析客户端:建立与服务器的连接并登陆,能显示登陆错误信息,完成界面登录。
并在每次用户接收到聊天信息后将会开始分析聊天信息,然后将适合自己的信息人性化地显示在与好友聊天界面上。
服务器:检查登陆信息是否正确,并向客户端返回登陆信息。
如信息正确,就将用户发送给该用户。
可以将聊天信息,转发给消息指定的客户端。
整体模型如图1所示。
图1整体通信模型2.2流程分析(1)服务器端:运行服务器程序(2)客户端:进入登陆界面,输入QQ号码和密码,点登录按扭。
网络编程上机操作题

网络编程上机操作题一、题目描述请使用Python编程语言完成以下网络编程操作题。
二、题目要求1. 编写一个客户端程序,能够连接到指定的服务器,并发送一条消息给服务器。
2. 编写一个服务器程序,能够接收来自客户端的消息,并将消息显示出来。
3. 客户端和服务器之间的通信使用TCP协议。
4. 客户端和服务器的IP地址和端口号需要在程序中指定。
三、编程思路1. 创建一个客户端的Socket对象,并指定服务器的IP地址和端口号。
2. 使用`connect()`方法连接到服务器。
3. 使用`send()`方法发送消息给服务器。
4. 创建一个服务器的Socket对象,并指定绑定的IP地址和端口号。
5. 使用`bind()`方法绑定Socket对象到指定的IP地址和端口号。
6. 使用`listen()`方法监听客户端的连接请求。
7. 使用`accept()`方法接收客户端的连接,并返回与客户端通信的Socket对象。
8. 使用`recv()`方法接收客户端发送的消息,并显示出来。
四、代码示例客户端代码import socketdef client():SERVER_IP = '127.0.0.1'SERVER_PORT =client_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)client_socket.connect((SERVER_IP, SERVER_PORT))message = "Hello, server!"client_socket.send(message.encode())client_socket.close()if __name__ == '__main__':client()服务器端代码import socketdef server():SERVER_IP = '127.0.0.1'SERVER_PORT =server_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)server_socket.bind((SERVER_IP, SERVER_PORT)) server_socket.listen(1)print("Server is listening...")client_socket, client_addr = server_socket.accept()print(f"Connected to client: {client_addr}")data = client_socket.recv(1024).decode()print(f"Received message: {data}")client_socket.close()server_socket.close()if __name__ == '__main__':server()五、测试1. 运行服务器程序。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Network Security– Secure Multi-user ChatProgramming Assignment 4 (40 points)Objective:To use Java Cryptography Extension (JCE) to develop a fully-secured multi-user chat program. Background:In your previous course, Network Programming, you developed a multi-user chat program, which your older sister frequently uses to communicate with her boyfriend over the Internet. However, by hiring the CNSA (the Chinese equivalent of the USA's National Security Agency) to eavesdrop on her communication, your big mother discovered that she and her boyfriend plan to drop out of 大连理工大学and run away to get married. Your sister, although much smarter than you, knows little about computers and specifically, computer and network security and has agreed to pay you 1,000,000Ұ to develop a fully-secured multi-user chat program so that she and her boyfriend can continue to communicate but this time, secretly. Most importantly, your sister demands that all communications should be fully secured not just from your nosy and intrusive mother, but also from anybody, including the CNSA and the NSA.Requirements:Using your last program from Network Programming as the building block, we now need to add several layers of security.First, the communication between the server and user should be encrypted using RC4 and a session key, which is a temporary key used only for securing the communication between the server and user. As you know, RC4 is a stream cipher, but is as secure as block ciphers such as 3DES and AES. The main advantage of using RC4 here is because it is very fast and is ideal for encrypting streams of data (arbitrary lengths of data), such as users' messages.The server not only acts as the chat server, but also as the authentication center. The chat server keeps a list of all the users' (users who have already set up an account with the server) names and passwords in a file on the hard drive. The file should at all times be encrypted with AES using a 128-bit key (See below for the key) that only the server knows.Login Procedure for an existing user1.It contacts the server and requests its public key. The public key is sent to the user.2.The user generates a session key (RC4) and sends its user name, password, and thesession key to the server.3.The server decrypts the message with its private key and recovers the user name,password, and session key.4.The server checks to see if the password is correct for this user. If so, it sends a status(either "OR" or "USER NOT EXIST", or "PASSWORD INCORRECT") back to the user encrypted with the session key.5.If the status is OK, the user and server can continue communicating with the session key.If the status is anything but OK, the server terminates the connection with the user andthe user begins at step 1 again.Creating a new account for new user1.When a new user wants to create an account, it contacts the server and requests its publickey. The public key is sent to the user.2.The user generates a session key, and encrypts its name, password, and session key withthe server's public key and sends the message to the server.3.The server checks to see if the user already exists. If exists, it sends a status back to user("USER EXISTS"). If it doesn't exist, the server creates a new account for this user (the user name and password are recorded by the server). In this case, the server returns an"OK" status back to the user. The server uses the session key to encrypt the responsessent back to the user.4.If the account was successfully created, the user can begin communicating with theserver as usual. If the account was not created (user already exists), the server closes the connection and the user begins at step 1 again.Please note there is always a chance that a third party can intercept this communication and impersonate the server, but there is no way around that unless the user already knows the public key of the server or there is a third party authentication service (digital certificates).At times, A may want to send a private message to another user (B). In this case, the server should only forward that message to B and not to any one else.The client's GUI should include a list of all the users so that 1) every user can see the currently logged on users (such as QQ and MSN) and 2) the user can choose which users should receive a private message.The session (communication) between the server and user should use128-bit RC4 (algorithm name = "ARCFOUR").The following user accounts should already exist. (Their information should be stored in an encrypted file that is read by the server when it first starts up. So you should create a separate program that saves the user accounts into an encrypted file that will later be used by the server.)User Name Passwordjohn catbob dogsue pigKey Information:Server's 128-bit AES Key: C5F9D65AEB7165562E38CE328108167AServer's RSA 512-bit Key:N (system modulus) in hexadecimal =BE211D1627D0FA0EDE557CB342256C9B6B7CEDB5A727BF732499393428EF2EC8704AD E733C65B2340B9C1DA282A57EC3B8352D6382E3DC32951EE741181A60FFd(in hexadecimal) =463367CFF4679ECCBA9F09EA0E344F439B8E871E99577DC2FFF26B42AD12934CDE8A43 617F97D277F856A42EA37D9936A2CE81351A432EB9B8A4DF818DA506F1e (in hexadecimal) = 10001Please note these keys should be stored inside the program. (They should not be read from a file.) Furthermore, your program should implement an additional significant feature in your chat program. You are free to decide what this feature is, but it should be somewhat significant (not just some trivial task). This feature should be clearly documented in Part I.Some examples include:∙Allowing users to display their pictures (just like in MSN) with their names. So whenever uses log in, they can send the server an optional picture which will then be forwarded to all other uses. Thus each picture will be displayed along side the user’s name.∙Allowing users to directly communicate. In other words, two clients can open up a direct communication link (bypassing the server). Of course, the server would now act as aKDC (key distribution center) who would forward the session keys to the clients. One of the users would then contact the other user (as described in the key distribution protocol).∙Allow users to send any kind of files to other users (e.g. songs, pictures, etc.). Of course, the receiver should be first notified and asked whether to accept or reject such file fromthe sender.∙Detecting intruders and hackers. For example, if a user tries to login unsuccessfully aftera certain number of attempts (e.g. 3), your program will detect a possible intruder and notallow the user to try again until after a fixed amount of time (e.g. 5 minutes).Part I (20%) – Due: Wed, December 19Write a 4-page requirements and design specification for your program. The requirements should include the ones outlined in this homework specification in addition to any other you would like to make. Furthermore, you requirements specification should identify and describe possible errors that may arise during the execution of the program (e.g. errors in messaging formats, unexpected connection drops, corrupted data, users’ password file not found). You also describe how your program will detect and handle those errors. Furthermore, you should also describe in detail what your optional feature will be. The design specifications should describe how you plan to implement your program such that it meets all of your requirements. For example, you should list and describe any major classes. Your document should include pictures and diagrams (e.g. use case diagrams, class hierarchy, message and packet formats) whenever appropriate.If there are any other requirements not clearly specified in this homework, you are free to make anyreasonable assumptions but they should be clearly documented in your specification. This should be written in English.One suggestion is to make a table with one column identifying possible errors and another column describing how your program handles those errors.This document (Microsoft Word 2003 format) should be emailed tomarvelwork@. In the subject, please only write: Program 4. In the body of the email, write your Chinese names, English names, student ID numbers, and class numbers.Part II (80%) – Due: Wed, December 26 (or later if necessary and requested in advance)You should implement your program in accordance with the requirements described in both this homework specification and your requirements specification. In your implementation, both the server and client applications should be robust; in other words, they should expect and be able to handle any kind of error. In other words, your program should never exit due to an exception being uncaught. For most errors, your program should detect the error and then recover from such errors. In cases of unrecoverable errors, your program should exit gracefully (display a message to the user and then exit). As an example of recoverable error, if there is a drop in the connection, the client can still renegotiate a new connection with the server without prompting (asking) the user for the user name and password again (just like in MSN). An unrecoverable error is insufficient disk space. In this case, the program can just inform the user of such errors and then exit. Your program should also handle possible errors in user names and passwords (e.g. size constraints, unexpected characters (e.g. spaces), and case-sensitivity (big vs. small letters)).Your program should be well documented. In other words, be sure to sufficiently comment your code in order to enhance readability of your code. You will lose points if you fail to properly document your code.Suggestions:1.Refer to this website to get more information and examples:/j2se/1.4.2/docs/guide/security/jce/JCERefGuide.html2.You are free to design the protocol between the user and server. For example, you willneed to create kinds of messages (e.g. login, create new account, send message to allusers, send message to specific user).3.You are free to use either blocking or non-blocking I/O for both the server and client. Butto save you time, you can use your last program to complete this homework.4.You will need to synchronize some portions of your code to ensure thread-safety.5.You should find all the classes you need for security in java.security and javax.crypto.6.You are free to develop and use any formats you wish (e.g. such as the format and sizesof messages and packets). Also, it’s up to you how keys are exchanged (raw data orstrings).7.You can assume user names are case insensitive but passwords are case sensitive.8.You can assume that the maximum length of the user name is 12 characters and themaximum length of passwords is 8 characters.In other words, by fixing sizes, you cancreate fixed-size messages for logging in, etc.9.Remember the maximum size of the block size is limited by the key size. In other words,your message must be less than the modulus (M<n). So if your plaintext is larger than this, you should first divide your data into smaller blocks or chunks.10.For converting raw data (array of bytes) to keys, you should study the KeySpec class.This class is useful for converting array of bytes into keys (e.g. AES, RC4).er CipherInputStream and CipherOutputStream to writing and reading data whileperforming encryption and decryption.12.You may work in groups of 2 on this homework (in other words, you and one partner). Summary:In this exercise, you will learn how to take advantage of Java's built-in support for cryptography and security to develop secured network applications. Specifically, you will learn not just how to use and apply various kinds of cryptographic algorithms (RC4 for symmetric stream cipher, RSA for asymmetric block cipher, and AES for symmetric block cipher), you will learn how to design and implement a totally secure network system by creating your own communication protocols and message formats.。
