2003数据结构英文试卷
数据结构 英文试题

以下是一份关于数据结构的英文试题,供您参考:1. What is the difference between an array and a linked list?Answer: An array and a linked list are two fundamental data structures used in computer science. An array is a linear data structure that stores elements in a consecutive memory location. It has a fixed size and the elements are accessed by their indices. On the other hand, a linked list is a dynamic data structure that consists of a set of nodes where each node contains the data and a reference (pointer) to the next node. The size of a linked list can vary dynamically and the elements are accessed in the order of their appearance.2. Explain the operation of binary search tree.Answer: A binary search tree is a tree-like data structure in which each node has at most two children, usually referred to as the left child and the right child. The value of each node in the binary search tree is greater than or equal to the value of all nodes in its left subtree and less than or equal to the value of all nodes in its right subtree. This property allows for efficient search, insertion, and deletion operations in the binary search tree. The search operation starts from the root node and compares the value with the target value, following the appropriate branch based on the comparison result until the target value is found or the appropriate action is taken. Insertion and deletion operations also involve maintaining the binary search tree property by adjusting the tree accordingly.3. What is the difference between a stack and a queue?Answer: A stack and a queue are two fundamental data structures used in computer science. A stack is a linear data structure that follows the Last In First Out (LIFO) principle. It allows the addition and removal of elements only at one end, usually referred to as the top of the stack. Elements are added to or removed from the stack using the push and pop operations, respectively. On the other hand, a queue is a linear data structure that follows the First In First Out (FIFO) principle. It allows the addition of elements at one end (rear) and removal of elements at the other end (front). Elements are added to or removed from the queue using the enqueue and dequeue operations, respectively.。
2003年考研英语—真题及答案

2003年考研英语真题及答案2003 text1Wild Bill Donovan would have loved the Internet. The American spymaster who built the Office of Strategic Services in the World W ar Ⅱand later laid the roots for the CIA was fascinated with information. Donovan believed in using whatever tools came to hand in the "great game" of espionage — spying as a "profession". These days the Net, which has already re-made such everyday pastimes as buying books and sending mail, is reshaping Donovan's vocation as well.The latest revolution isn't simply a matter of gentlemen reading other gentlemen's e-mail. That kind of electronic spying has been going on for decades. In the past three or four years, the W orld Wide W eb has given birth to a whole industry of point-and-click spying. The spooks call it "open-source intelligence", and as the Net grows, it is becoming increasingly influential. In 1995 the CIA held a contest to see who could compile the most data about Burundi. The winner, by a large margin, was a tiny Virginia company called Open Source Solutions, whose clear advantage was its mastery of the electronic world.Among the firms making the biggest splash in this new world is Straitford, Inc., a private intelligence-analysis firm based in Austin, Texas. Straitford makes money by selling the results of spying (covering nations from Chile to Russia) to corporations like energy-services firm McDermott International. Many of its predictions are available online at .Straiford president George Friedman says he sees the online world as a kind of mutually reinforcing tool for both information collection and distribution, a spymaster's dream. Last week his firm was busy vacuuming up data bits from the far corners of the world and predicting a crisis in Ukraine. "As soon as that report runs, we'll suddenly get 500 new Internet sign-ups from Ukraine," says Friedman, a former political science professor. "And we'll hear back from some of them." Open-source spying does have its risks, of course, since it can be difficult to tell good information from bad. That's where Straitford earns its keep.Friedman relies on a lean staff of 20 in Austin. Several of his staff members have military-intelligence backgrounds. He sees the firm's outsider status as the key to its success. Straitford's briefs don't sound like the usual W ashington back-and-forthing, whereby agencies avoid dramatic declarations on the chance they might be wrong. Straitford, says Friedman, takes pride in its independent voice.41. The emergence of the Net has ________.[A] received support from fans like Donovan[B] remolded the intelligence services[C] restored many common pastimes[D] revived spying as a profession42. Donovan's story is mentioned in the text to ________.[A] introduce the topic of online spying[B] show how he fought for the US[C] give an episode of the information war[D] honor his unique services to the CIA43. The phrase "making the biggest splash" (line 1, paragraph 3) most probably means ________.[A] causing the biggest trouble[B] exerting the greatest effort[C] achieving the greatest success[D] enjoying the widest popularity44. It can be learned from paragraph 4 that ________.[A] Straitford's prediction about Ukraine has proved true[B] Straitford guarantees the truthfulness of its information[C] Straitford's business is characterized by unpredictability[D] Straitford is able to provide fairly reliable information45. Straitford is most proud of its ________.[A] official status[B] nonconformist image[C] efficient staff[D] military background 试题解析:这是一篇说明性的文章,介绍了互联网技术对情报行业的影响。
2003年研究生入学数据结构试题和答案

A2003年研究生入学试题已知一棵度为12 的树,它的根结点的地址为root。
该树是用顺序存储方式存储的,说明如下:struct node { i nt data;// 树中结点的数据场。
int son[12]; //给出结点的第一个、第二个……第12个儿子结点//地址。
}tnode[M]; //注意:M是一个常量。
请设计一个非递归的程序,按前序遍历该树,打印每个结点的的数据场之值,注意:如用递归程序实现,作零分处理。
(本题15 分。
)二.从键盘上输入一串正整数,最后输入-1作为结束标志。
如:8,7,1,22,98,46,……,75,-1。
请设计一个非递归程序,创建一棵二叉排序树,并且该二叉排序树业必须是中序线索二叉树。
设该二叉排序树上的结点结构为:其中:data 域为结点的数据场。
ltag=0,那么left域中存放的是该结点的左儿子结点的地址。
ltag=1,那么left域中存放的是该结点的按中序周游次序的前驱结点的地址。
rtag=0,那么right域中存放的是该结点的右儿子结点的地址。
rtag=1,那么right域中存放的是该结点的按中序周游次序的后继结点地址。
(本题20 分。
)三.已知中序线索二叉树的某结点的地址为P请设计一个程序给出地址为P 的结点的按前序周游次序的后继结点的地址q。
注意:本程序要求辅助空间只能为O(1),否则作零分处理。
另外,结点形式可参考第2 题。
(本题15 分。
)四.已知某有向图用邻接表表示。
该邻接表的结点及边表说明如下:#define TOTAL 1000struct arcnode { int adjvex; // 该边所指向的结点的下标地址。
struct arcnode *nextarc; // 给出下一条边的边结点的地址。
} arcnode ; // 边结点说明。
struct vnode { int data; // 结点数据场,其值为整数。
arcnode * firstarc; //指向离开本结点的第一条边的边结点。
斯坦福大学2003年操作系统期末考试题(英文)

FINAL EXAM – INTRODUCTION TO OPERATING SYSTEMS CSE421May 2, 2003 (Spring 2003)NAME : _____________________________________________________________ STUDENT NUMBER : _________-_________INSTRUCTIONSThis is a closed book but you are allowed two sheets of information to refer to. You have 180 minutes to complete 10 questions. Please write neatly and clearly. To receive partial credit, you must show all work for your answers. You should have 11 pages in this exam book, some of which are blank to allow room for your answers.Raw Score : ___________/ 140 = ____________/ 1001) [20 Points] DeadlockConsider the following snapshot of a system (P=Process, R=Resource) :Answer the following questions using banker’s algorithm:a) Calculate the Needs matrix:b) Is the system in a safe state? If so, show a safe order in which the processes can run. c) Can a request of one instance of RA by Process P0 be granted safely according to Banker’s algorithm?2) [20 points] Logical and Physical Address SpacesThe Kiwi™ memory architecture design team has a dilemma. The team is considering several different memory configuration variations for an upcoming machine design. Consider the following designs (All memory accesses are in terms of bytes, and all are using paging techniques):a) [6 points] For each design, list the maximum number of pages each process can access in logical address space.b) [6 points] For each design, list the maximum number of frames in physical memory.c) [6 points] For design 3, if the outermost page table holds 32 entries, how many bits are needed in the logical address to represent the outer page table? How many bits are used for representing the offset within a page? How many bits are needed in the logical address in order to represent the inner page table?Given the following reference string:0 2 1 3 0 1 4 0 1 2 3 4showa)Page faults occur during the processing of the reference scheme?b)The hit ratio is for each of the following policies in a pure demand paging system?c)What do you observe when you move from Scheme 1 to Scheme 2? Explain. Scheme 1: FIFO with three pages of main memoryScheme 2: FIFO with four pages of main memoryConsider a system where the virtual memory page size is 2K (2048 bytes), and main memory consists of 4 page frames. Now consider a process which requires 8 pages of storage. At some point during its execution, the page table is as shown below:1.List the virtual address ranges for each virtual page.2.List the virtual address ranges that will result in a page fault.3.Give the main memory (physical) addresses for each of the following virtual addresses(all numbers decimal): (i) 8500, (ii) 14000, (iii) 5000, (iv) 2100.5) [20 points] File System ImplementationSuppose a file system is constructed using blocks of 8 words each. In this system, a word has a length of 4 bytes. The disk pack used to hold the file system consists of 32 blocks. The initial block (block 0) contains a directory entry. The directory entry contains the filename of a single file in this file system, and a pointer to the first I-node in block 1. The I-node structure is as follows (word, value):The file contains 16 words of data: the first direct index points at block 31, and the second direct index points at block 29. Blocks 4,7,10,and 15 are marked bad. Assume that free blocks are allocated in logical order starting with block 0 and that write operations modify the file system 1 block at a time.What will the state of the system look like after 100 additional words are appended to the file (draw a block diagram showing the structure of the I-node and the blocks that are allocated)6) [16 points] Disk SchedulingDisk requests come into the disk driver for cylinders 10, 22, 20, 2, 40, 6, and 38, in that order. Assume that the disk has 100 cylinders.A seek takes 6msec per cylinder moved. Compute the average seek time for the request sequence given above for1.First-come, First-served2.Shortest Seek Time First (SSTF)3.LOOK (with the disk-arm initially moving towards higher number cylinders from lowernumber cylinders)4.C-SCANIn all the cases, the arm is initially at cylinder 20.7) [10 points] Security: Public Key EncryptionConsider the public key encryption defined by the RSA (Rivest, Shamir, Adelman) scheme. Assume that the two starting primes are p and q are 3 and 7 respectively and determine the (nontrivial) private key and public key pairs according to the RSA scheme.8) [10 Points] Networking: TCP/IPThe following flowchart shows the client and server portions of a TCP communication session. Fill in the empty bubbles/boxes with the appropriate socket system call names.CLIENT SERVER9) [10 points] Enduring Principles in System Design1.When a system gets complex in design what is a common solution to manage thecomplexity? Give an example.2.When you experience incompatibilities between system modules, how will you solve thisproblem? Give an example.3.What is a common data structure used to manage (the slots for) n resources? Give anexample.4.The data items such as inodes and files are typically located in external memory that issluggish relative to the local main memory. How are the effective access times of these structures minimized?5.When a table maintaining a list of pointers grows unmanageably large how will you solvethis problem so that (i) search times of the table is reasonable and (ii) only the region of interest in the table need to be in the memory?10) [10 points] Nachos Operating Systems1.List the two main operations (methods) that have the potential for resulting in a pagefault.2.Where is the address that caused the page fault stored?3.You incremented the PC after every system call you implemented? Why not for pagefault system call?4.What is the purpose of Exec, Join and Exit system calls?5.Explain the above with an example.6.How would you control the access to a shared resource by multiple threads?11。
2003考研英语真题(英一二通用)答案+解析
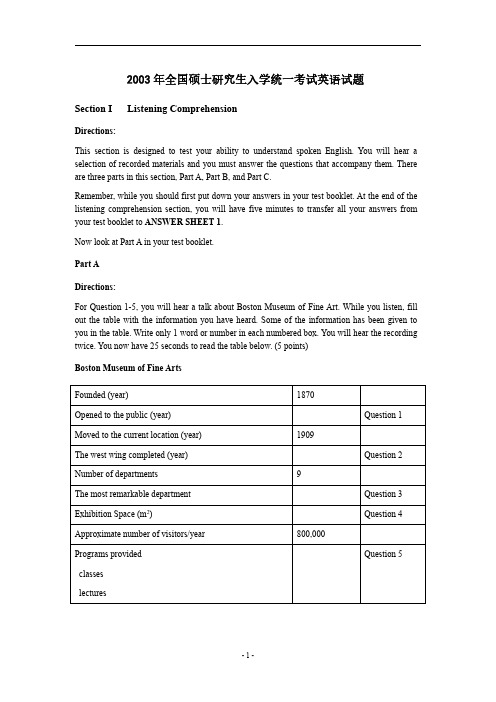
2003年全国硕士研究生入学统一考试英语试题Section I Listening ComprehensionDirections:This section is designed to test your ability to understand spoken English.You will hear a selection of recorded materials and you must answer the questions that accompany them.There are three parts in this section,Part A,Part B,and Part C.Remember,while you should first put down your answers in your test booklet.At the end of the listening comprehension section,you will have five minutes to transfer all your answers from your test booklet to ANSWER SHEET1.Now look at Part A in your test booklet.Part ADirections:For Question1-5,you will hear a talk about Boston Museum of Fine Art.While you listen,fill out the table with the information you have heard.Some of the information has been given to you in the table.Write only1word or number in each numbered box.You will hear the recording twice.You now have25seconds to read the table below.(5points)Boston Museum of Fine ArtsFounded(year)1870Opened to the public(year)Question1Moved to the current location(year)1909The west wing completed(year)Question2Number of departments9The most remarkable department Question3Exhibition Space(m2)Question4Approximate number of visitors/year800,000Programs providedQuestion5classeslecturesPart BDirections:For Questions6-10,you will hear an interview with an expert on marriage problems.While you listen,complete the sentences or answer the e not more than3words for each answer.You will hear the recording twice.You now have25seconds to read the sentences and questions below.(5points)What should be the primary source of help for a troubled couple?________.Question6Writing down a list of problems in the marriage may help a troubled couple discuss them ________.Question7Who should a couple consider seriously turning to if they can’t talk with each other? ________.Question8Priests are usually unsuccessful in counseling troubled couples despite their________. Question9According to the old notion,what will make hearts grow fonder?________.Question10 Part CDirections:You will hear three pieces of recorded material.Before listening to each one,you will have time to read the questions related to it.While listening,answer each question by choosing[A],[B],[C] or[D].After listening,you will have time to check your answers you will hear each piece once only.(10points)Questions11-13are based on the following talk about napping,you now have15seconds to read questions11-13.11.Children under five have abundant energy partly because they________.[A]sleep in three distinct parts[B]have many five-minute naps[C]sleep in one long block[D]take one or two naps daily12.According to the speaker,the sleep pattern of a baby is determined by________.[A]its genes[B]its habit[C]its mental state[D]its physical condition13.The talk suggests that,if you feel sleepy through the day,you should________.[A]take some refreshment[B]go to bed early[C]have a long rest[D]give in to sleepQuestions14-16are based on the following interview with Sherman Alexie,an American Indian poet.You now have15seconds to read Questions14-16.14.Why did Sherman Alexie only take day jobs?[A]He could bring unfinished work home.[B]He might have time to pursue his interests.[C]He might do some evening teaching.[D]He could invest more emotion in his family.15.What was his original goal at college?[A]to teach in high school[B]to write his own books[C]to be a medical doctor[D]to be a mathematician16.Why did he take the poetry-writing class?[A]To follow his father.[B]For an easy grade.[C]To change his specialty.[D]For knowledge of poetry.Questions17-20are based on the following talk about public speaking.You now have20 seconds to read Questions17-20.17.What is the most important thing in public speaking?[A]Confidence.[B]Preparation.[C]Informativeness.[D]Organization.18.What does the speaker advise us to do to capture the audience’s attention?[A]Gather abundant data.[B]Organize the idea logically.[C]Develop a great opening.[D]Select appropriate materials.19.If you don’t start working for the presentation until the day before,you will feel________.[A]uneasy[B]uncertain[C]frustrated[D]depressed20.Who is this speech most probably meant for?[A]Those interested in the power of persuasion.[B]Those trying to improve their public images.[C]Those planning to take up some public work.[D]Those eager to become effective speakers.You now have5minutes to transfer all your answers from your test booklet to ANSWER SHEET1.Section II Use of EnglishDirections:Read the following text.Choose the best word(s)for each numbered blank and mark[A],[B], [C]or[D]on ANSWER SHEET1.(10points)Teachers need to be aware of the emotional,intellectual,and physical changes that young adults experience.And they also need to give serious大21家to how they can best 大22家such changes.Growing bodies need movement and大23家,but not just in waysthat emphasize competition.大24家they are adjusting to their new bodies and a whole host of new intellectual and emotional challenges,teenagers are especially self-conscious and needthe大25家that comes from achieving success and knowing that their accomplishments are大26家by others.However,the typical teenage lifestyle is already filled with so much competition that it would be大27家to plan activities in which there are more winners thanlosers,大28家,publishing newsletters with many student-written book reviews,大29家student artwork,and sponsoring book discussion clubs.A variety of small clubs can provide 大30家opportunities for leadership,as well as for practice in successful大31家dynamics.Making friends is extremely important to teenagers,and many shy students need the 大32家of some kind of organization with a supportive adult大33家visible in the background.In these activities,it is important to remember that the young teens have大34家attention spans.A variety of activities should be organized大35家participants can remain active as long as they want and then go on to大36家else without feeling guilty and without letting the other participants大37家.This does not mean that adults must accept irresponsibility.大38家,they can help students acquire a sense of commitment by大39家for roles that are within their大40家and their attention spans and by having clearly stated rules.21.[A]thought[B]idea[C]opinion[D]advice22.[A]strengthen[B]accommodate[C]stimulate[D]enhance23.[A]care[B]nutrition[C]exercise[D]leisure24.[A]If[B]Although[C]Whereas[D]Because25.[A]assistance[B]guidance[C]confidence26.[A]claimed[B]admired[C]ignored[D]surpassed27.[A]improper[B]risky[C]fair[D]wise28.[A]in effect[B]as a result[C]for example[D]in a sense29.[A]displaying[B]describing[C]creating[D]exchanging30.[A]durable[B]excessive[C]surplus[D]multiple31.[A]group[B]individual[C]personnel[D]corporation32.[A]consent[B]insurance[C]admission[D]security33.[A]particularly[B]barely[D]rarely34.[A]similar[B]long[C]different[D]short35.[A]if only[B]now that[C]so that[D]even if36.[A]everything[B]anything[C]nothing[D]something37.[A]off[B]down[C]out[D]alone38.[A]On the contrary[B]On the average[C]On the whole[D]On the other hand39.[A]making[B]standing[C]planning[D]taking40.[A]capabilities[B]responsibilities[C]proficiency[D]efficiencySection III Reading ComprehensionPart ADirections:Read the following four texts.Answer the questions below each text by choosing[A],[B],[C]or [D].Mark your answers on ANSWER SHEET1(40points)Text1Wild Bill Donovan would have loved the Internet.The American spymaster who built the Office of Strategic Services in the World War II and later laid the roots for the CIA was fascinated with information.Donovan believed in using whatever tools came to hand in the “great game”of espionage--spying as a“profession.”These days the Net,which has already re-made such everyday pastimes as buying books and sending mail,is reshaping Donovan’s vocation as well.The latest revolution isn’t simply a matter of gentlemen reading other gentlemen’s e-mail. That kind of electronic spying has been going on for decades.In the past three or four years,the World Wide Web has given birth to a whole industry of point-and-click spying.The spooks call it “open-source intelligence,”and as the Net grows,it is becoming increasingly influential.In1995 the CIA held a contest to see who could compile the most data about Burundi.The winner,by a large margin,was a tiny Virginia company called Open Source Solutions,whose clear advantage was its mastery of the electronic world.Among the firms making the biggest splash in this new world is Straitford,Inc.,a private intelligence-analysis firm based in Austin,Texas.Straitford makes money by selling the results of spying(covering nations from Chile to Russia)to corporations like energy-services firm McDermott International.Many of its predictions are available online at .Straitford president George Friedman says he sees the online world as a kind of mutually reinforcing tool for both information collection and distribution,a spymaster’s st week his firm was busy vacuuming up data bits from the far corners of the world and predicting a crisis in Ukraine.“As soon as that report runs,we’ll suddenly get500new Internet sign-ups from Ukraine,”says Friedman,a former political science professor.“And we’ll hear back from some of them.”Open-source spying does have its risks,of course,since it can be difficult to tell good information from bad.That’s where Straitford earns its keep.Friedman relies on a lean staff of20in Austin.Several of his staff members have military-intelligence backgrounds.He sees the firm’s outsider status as the key to its success. Straitford’s briefs don’t sound like the usual Washington back-and-forthing,whereby agencies avoid dramatic declarations on the chance they might be wrong.Straitford,says Friedman,takes pride in its independent voice.41.The emergence of the Net has________.[A]received support from fans like Donovan[B]remolded the intelligence services[C]restored many common pastimes[D]revived spying as a profession42.Donovan’s story is mentioned in the text to________.[A]introduce the topic of online spying[B]show how he fought for the U.S.[C]give an episode of the information war[D]honor his unique services to the CIA43.The phrase“making the biggest splash”(Line1,Paragraph3)most probably means________.[A]causing the biggest trouble[B]exerting the greatest effort[C]achieving the greatest success[D]enjoying the widest popularity44.It can be learned from Paragraph4that________.[A]Straitford’s prediction about Ukraine has proved true[B]Straitford guarantees the truthfulness of its information[C]Straitford’s business is characterized by unpredictability[D]Straitford is able to provide fairly reliable information45.Straitford is most proud of its________.[A]official status[B]nonconformist image[C]efficient staff[D]military backgroundText2To paraphrase18th-century statesman Edmund Burke,“all that is needed for the triumph of a misguided cause is that good people do nothing.”One such cause now seeks to end biomedical research because of the theory that animals have rights ruling out their use in research.Scientists need to respond forcefully to animal rights advocates,whose arguments are confusing the public and thereby threatening advances in health knowledge and care.Leaders of the animal rights movement target biomedical research because it depends on public funding,and few people understand the process of health care research.Hearing allegations of cruelty to animals in research settings,many are perplexed that anyone would deliberately harm an animal.For example,a grandmotherly woman staffing an animal rights booth at a recent street fair was distributing a brochure that encouraged readers not to use anything that comes from or is tested in animals—no meat,no fur,no medicines.Asked if she opposed immunizations,she wanted to know if vaccines come from animal research.When assured that they do,she replied,“Then I would have to say yes.”Asked what will happen when epidemics return,she said,“Don’t worry,scientists will find some way of using computers.”Such well-meaning people just don’t understand.Scientists must communicate their message to the public in a compassionate, understandable way--in human terms,not in the language of molecular biology.We need to make clear the connection between animal research and a grandmother’s hip replacement,a father’s bypass operation,a baby’s vaccinations,and even a pet’s shots.To those who are unaware that animal research was needed to produce these treatments,as well as new treatments and vaccines,animal research seems wasteful at best and cruel at worst.Much can be done.Scientists could“adopt”middle school classes and present their own research.They should be quick to respond to letters to the editor,lest animal rights misinformation go unchallenged and acquire a deceptive appearance of truth.Research institutions could be opened to tours,to show that laboratory animals receive humane care. Finally,because the ultimate stakeholders are patients,the health research community should actively recruit to its cause not only well-known personalities such as Stephen Cooper,who has made courageous statements about the value of animal research,but all who receive medical treatment.If good people do nothing,there is a real possibility that an uninformed citizenry will extinguish the precious embers of medical progress.46.The author begins his article with Edmund Burke’s words to________.[A]call on scientists to take some actions[B]criticize the misguided cause of animal rights[C]warn of the doom of biomedical research[D]show the triumph of the animal rights movement47.Misled people tend to think that using an animal in research is________.[A]cruel but natural[B]inhuman and unacceptable[C]inevitable but vicious[D]pointless and wasteful48.The example of the grandmotherly woman is used to show the public’s________.[A]discontent with animal research[B]ignorance about medical science[C]indifference to epidemics[D]anxiety about animal rights49.The author believes that,in face of the challenge from animal rights advocates,scientistsshould________.[A]communicate more with the public[B]employ hi-tech means in research[C]feel no shame for their cause[D]strive to develop new cures50.From the text we learn that Stephen Cooper is________.[A]a well-known humanist[B]a medical practitioner[C]an enthusiast in animal rights[D]a supporter of animal researchText3In recent years,railroads have been combining with each other,merging into supersystems, causing heightened concerns about monopoly.As recently as1995,the top four railroads accounted for under70percent of the total ton-miles moved by rails.Next year,after a series of mergers is completed,just four railroads will control well over90percent of all the freight moved by major rail carriers.Supporters of the new supersystems argue that these mergers will allow for substantial cost reductions and better coordinated service.Any threat of monopoly,they argue,is removed by fierce competition from trucks.But many shippers complain that for heavy bulk commodities traveling long distances,such as coal,chemicals,and grain,trucking is too costly and the railroads therefore have them by the throat.The vast consolidation within the rail industry means that most shippers are served by only one rail company.Railroads typically charge such“captive”shippers20to30percent more than they do when another railroad is competing for the business.Shippers who feel they are being overcharged have the right to appeal to the federal government’s Surface Transportation Board for rate relief,but the process is expensive,time-consuming,and will work only in truly extreme cases.Railroads justify rate discrimination against captive shippers on the grounds that in the long run it reduces everyone’s cost.If railroads charged all customers the same average rate,they argue,shippers who have the option of switching to trucks or other forms of transportation would do so,leaving remaining customers to shoulder the cost of keeping up the line.It’s a theory to which many economists subscribe,but in practice it often leaves railroads in the position of determining which companies will flourish and which will fail.“Do we really want railroads to be the arbiters of who wins and who loses in the marketplace?”asks Martin Bercovici,a Washington lawyer who frequently represents shippers.Many captive shippers also worry they will soon be hit with a round of huge rate increases. The railroad industry as a whole,despite its brightening fortunes,still does not earn enough to cover the cost of the capital it must invest to keep up with its surging traffic.Yet railroads continue to borrow billions to acquire one another,with Wall Street cheering them on.Consider the$10.2billion bid by Norfolk Southern and CSX to acquire Conrail this year.Conrail’s netrailway operating income in1996was just$427million,less than half of the carrying costs of the transaction.Who’s going to pay for the rest of the bill?Many captive shippers fear that they will,as Norfolk Southern and CSX increase their grip on the market.51.According to those who support mergers,railway monopoly is unlikely because________.[A]cost reduction is based on competition[B]services call for cross-trade coordination[C]outside competitors will continue to exist[D]shippers will have the railway by the throat52.What is many captive shippers’attitude towards the consolidation in the rail industry?[A]Indifferent.[B]Supportive.[C]Indignant.[D]Apprehensive.53.It can be inferred from Paragraph3that________.[A]shippers will be charged less without a rival railroad[B]there will soon be only one railroad company nationwide[C]overcharged shippers are unlikely to appeal for rate relief[D]a government board ensures fair play in railway business54.The word“arbiters”(Line7,Paragraph4)most probably refers to those________.[A]who work as coordinators[B]who function as judges[C]who supervise transactions[D]who determine the price55.According to the text,the cost increase in the rail industry is mainly caused by________.[A]the continuing acquisition[B]the growing traffic[C]the cheering Wall Street[D]the shrinking marketText4It is said that in England death is pressing,in Canada inevitable and in California optional. Small wonder.Americans’life expectancy has nearly doubled over the past century.Failing hips can be replaced,clinical depression controlled,cataracts removed in a30-minute surgical procedure.Such advances offer the aging population a quality of life that was unimaginablewhen I entered medicine50years ago.But not even a great health-care system can cure death--and our failure to confront that reality now threatens this greatness of ours.Death is normal;we are genetically programmed to disintegrate and perish,even under ideal conditions.We all understand that at some level,yet as medical consumers we treat death as a problem to be solved.Shielded by third-party payers from the cost of our care,we demand everything that can possibly be done for us,even if it’s useless.The most obvious example is late-stage cancer care.Physicians--frustrated by their inability to cure the disease and fearing loss of hope in the patient--too often offer aggressive treatment far beyond what is scientifically justified.In1950,the U.S.spent$12.7billion on health care.In2002,the cost will be$1,540billion. Anyone can see this trend is unsustainable.Yet few seem willing to try to reverse it.Some scholars conclude that a government with finite resources should simply stop paying for medical care that sustains life beyond a certain age--say83or so.Former Colorado governor Richard Lamm has been quoted as saying that the old and infirm“have a duty to die and get out of the way,”so that younger,healthier people can realize their potential.I would not go that far.Energetic people now routinely work through their60s and beyond, and remain dazzlingly productive.At78,Viacom chairman Sumner Redstone jokingly claims to be53.Supreme Court Justice Sandra Day O’Connor is in her70s,and former surgeon general C. Everett Koop chairs an Internet start-up in his80s.These leaders are living proof that prevention works and that we can manage the health problems that come naturally with age.As a mere 68-year-old,I wish to age as productively as they have.Yet there are limits to what a society can spend in this pursuit.As a physician,I know the most costly and dramatic measures may be ineffective and painful.I also know that people in Japan and Sweden,countries that spend far less on medical care,have achieved longer,healthier lives than we have.As a nation,we may be overfunding the quest for unlikely cures while underfunding research on humbler therapies that could improve people’s lives.56.What is implied in the first sentence?[A]Americans are better prepared for death than other people.[B]Americans enjoy a higher life quality than ever before.[C]Americans are over-confident of their medical technology.[D]Americans take a vain pride in their long life expectancy.57.The author uses the example of cancer patients to show that________.[A]medical resources are often wasted[B]doctors are helpless against fatal diseases[C]some treatments are too aggressive[D]medical costs are becoming unaffordable58.The author’s attitude toward Richard Lamm’s remark is one of________.[A]strong disapproval[B]reserved consent[C]slight contempt[D]enthusiastic support59.In contrast to the U.S.,Japan and Sweden are funding their medical care________.[A]more flexibly[B]more extravagantly[C]more cautiously[D]more reasonably60.The text intends to express the idea that________.[A]medicine will further prolong people’s lives[B]life beyond a certain limit is not worth living[C]death should be accepted as a fact of life[D]excessive demands increase the cost of health carePart BDirections:Read the following text carefully and then translate the underlined segments into Chinese.Your translation should be written clearly on ANSWER SHEET2.(10points)Human beings in all times and places think about their world and wonder at their place in it. Humans are thoughtful and creative,possessed of insatiable curiosity.61)Furthermore,humans have the ability to modify the environment in which they live,thus subjecting all other life forms to their own peculiar ideas and fancies.Therefore,it is important to study humans in all their richness and diversity in a calm and systematic manner,with the hope that the knowledge resulting from such studies can lead humans to a more harmonious way of living with themselves and with all other life forms on this planet Earth.“Anthropology”derives from the Greek words anthropos:“human”and logos“the study of.”By its very name,anthropology encompasses the study of all humankind.Anthropology is one of the social sciences.62)Social science is that branch of intellectual enquiry which seeks to study humans and their endeavors in the same reasoned,orderly, systematic,and dispassioned manner that natural scientists use for the study of natural phenomena.Social science disciplines include geography,economics,political science,psychology,and sociology.Each of these social sciences has a subfield or specialization which lies particularly close to anthropology.All the social sciences focus upon the study of humanity.Anthropology is a field-study oriented discipline which makes extensive use of the comparative method in analysis.63)The emphasis on data gathered first-hand,combined with a cross-cultural perspective brought to theanalysis of cultures past and present,makes this study a unique and distinctly important social science.Anthropological analyses rest heavily upon the concept of culture.Sir Edward Tylor’s formulation of the concept of culture was one of the great intellectual achievements of19th century science.64)Tylor defined culture as“…that complex whole which includes belief,art, morals,law,custom,and any other capabilities and habits acquired by man as a member of society.”This insight,so profound in its simplicity,opened up an entirely new way of perceiving and understanding human life.Implicit within Tylor’s definition is the concept that culture is learned,shared,and patterned behavior.65)Thus,the anthropological concept of“culture,”like the concept of“set”in mathematics, is an abstract concept which makes possible immense amounts of concrete research and understanding.Section IV Writing66.Directions:Study the following set of drawings carefully and write an essay in which you should1)describe the set of drawings,interpret its meaning,and2)point out its implications in our life.You should write about200words neatly on ANSWER SHEET2.(20points)2003年考研英语真题答案解析Section I:Listening Comprehension(20points)Part A(5points)1.18762.19813.textiles4.19,1375.concerts Part B(5points)6.(the couple)themselves7.constructively8.a qualified psychologist9.good intentions10.absencePart C(10points)11.[D]12.[A]13.[D]14.[B]15.[C]16.[B]17.[B]18.[C]19.[A]20.[D]Section II:Use of English(10points)一、文章总体分析文章主要论述了教师们应该关注青少年在成长时期所经历的情感、心智和生理上的变化,并采取方法帮助他们适应这些变化,健康成长。
2003年英语真题及答案(全国卷)

2003年英语真题及答案(全国卷)绝密★启⽤前2003年普通⾼等学校招⽣全国统⼀考试英语第⼆部分:英语知识运⽤(共两节,满分45分)第⼀节:单项填空(共15⼩题:每⼩题1分,满分15分)21.Don’t be afraid of asking for help it is needed.A.unless B.since C.although D.when22.A cook will be immediately fired if he is found in the kitchen.A.smoke B.smoking C.to smoke D.smoked23.Allen had to call a taxi because the box was to carry all the way home.A.much too heavy B.too much heavy C.heavy too much D.too heavy much24.—Sorry, Joe, I didn’t mean to…—Don’t call me “Joe”. I’m Mr Parker to you, and you forget it!A.do B.didn’t C.did D.don’t25.If anybody calls, tell them I’m out, and ask them to their name and address.A.pass B.write C.take D.leave26.The sign reads “In case of fire, break the glass and push red button.”A.不填;a B.不填;the C.the; the D.a;a27.All morning as she waited for the medical report from the doctor, her nervouseness .A.has grown B.is growing C.grew D.had grown28.A left luggage office is a place where bags be left for a short time, especially at a railway station.A.should B.can C.must D.will29.We’re going to the bookstore in John’s car. You can come with us you can meet us there later.A.but B.and C.or D.then30.Why don’t you put the meat in the fridge? It will fresh for several days.A.be stayed B.stay C.be staying D.have stayed31.News reports say peace talks between the two countries with no agreement reached.A.have broken down B.have broken out C.have broken in D.have broken up 32.—There’s coffee and tea: you can have .—Thanks.A.either B.each C.one D.it33.—Susan, go and join your sister cleaning the yard.—Why ? John is sitting there doing nothing.A.him B.he C.I D.me34.The old couple have been married for 40 years and never once with each other.A.they had quarreled B.they have quarreledC.have they quarreled D.had they quarreled35.—I think you should phone Jenny and say sorry to her.— .It was her fault.A.No way B.Not possible C.No chance D.Not at all第⼆节:完形填空(共20⼩题:每⼩题1.5分,满分30分)阅读下⾯短⽂,掌握其⼤意,然后从36—55各题所给的四个选项(A、B、C和D)中,选出最佳选项。
2003年考研英语试题及参考答案(2)

2003年考研英语试题及参考答案(2)Straifford president George Friedman says he sees the online world as a kind of mutually reinforcing tool for both information collection and distribution, a spymaster's dream. Last week his firm was busy vacuuming up data bits from the far corners of the world and predicting a crisis in Ukraine." As soon as that report runs, we'll suddenly get 500 new internet sign-ups from Ukraine," says Friedman, a former political science professor. "And we'll hear back from some of them." Open-source spying does have its risks, of course, since it can be difficult to tell good information from bad. That 'sswheresStraitford earns its keep.Friedman relies on a lean staff in Austin. Several of his staff members have military-intelligence backgrounds. He sees the firm's outsider status as the key to its success. Straitford's briefs don't sound like the usual Washington back-and forthing, whereby agencies avoid dramatic declarations on the chance they might be wrong. Straitford, says Friedman, takes pride in its independent voice.41. The emergence of the Net hasA. received support from fans like Donovan.B. remolded the intelligence services.C. restored many common pastimes.D. revived spying as a profession.42.Donovan's story is mentioned in the text toA. introduce the topic of online spying.B. show how he fought for the U.S.C. give an episode of the information war.D. honor his unique services to the CIA.43.The phrase“making the biggest splash”(line 1,paragraph 3)most probably meansA. causing the biggest trouble.B. exerting the greatest effort.C. achieving the greatest success.D. enjoying the widest popularity.44.It can be learned from paragraph 4 thatA. Straitford's prediction about Ukraine has proved true.B. Straitford guarantees the truthfulness of its information.C. Straitford's business is characterized by unpredictability.D. Straitford is able to provide fairly reliable information.45.Straitford is most proud of itsA. official status.B. nonconformist image.C. efficient staff.D. military background.BACDBText 2 To paraphrase 18th-century statesman Edmund Burke,“all that is needed for the triumph of a misguided cause is that good people do nothing.”One such cause now seeks to end biomedical research because of the theory that animals have rights ruling out their use in research. Scientists need to respond forcefully to animal rights advocates, whose arguments are confusing the public and thereby threatening advances in health knowledge and care. Leaders of the animal rights movement target biomedical research because it depends on public funding, and few people understand the process of health care research. Hearing allegations of cruelty to animals in research settings, many are perplexed that anyone would deliberately harm an animal.For example, a grandmotherly woman staffing an animal rights booth at a recent street fair was distributing a brochure that encouraged readers not to use anything that opposedimmunizations, she wanted to know if vaccines come from animal research. When as sured that they do, she replied,“Then I would have to say yes.”Asked what will happen when epidemics return, she said,“Don’t worry, scientists will find some way of using computers.”Such well-meaning people just don's understand. Scientists must communicate their message to the public in a compassionate, understandable way-in human terms, not in the language of molecular biology. We need to make clear the connection between animal research and a grandmother's hip replacement, a father's bypass operation a baby's vaccinations, and even a pet's shots. To those who are unaware that animal research was needed to produce these treatments, as well as new treatments and vaccines, animal research seems wasteful at best and cruel at worst.Much can be don e. Scientists could“adopt”middle school classes and present their own research. They should be quick to respond to letters to the editor, lest animal rights misinformation go unchallenged and acquire a deceptive appearance of truth. Research institutions could be opened to tours, to show that laboratory animals receive humane care. Finally, because the ultimate stakeholders are patients, the health research community should actively recruit to its causenot only well-known personalities such as Stephen Cooper, who has made courageous statements about the value of animal research, but all who receive medical treatment. If good people do nothing there is a real possibility that an uninformed citizenry will extinguish the precious embers of medical progress.46.The author begins his article with Edmund Burke's words toA. call on scientists to take some actions.B. criticize the misguided cause of animal rights.C. warn of the doom of biomedical research.D. show the triumph of the animal rights movement.47.Misled people tend to think that using an animal in research isA. cruel but natural.B. inhuman and unacceptable.C. inevitable but vicious.D. pointless and wasteful.48.The example of the grandmotherly woman is used to show the public'sA. discontent with animal research.B. ignorance about medical science.C. indifference to epidemics.D. anxiety about animal rights.49.The author believes that, in face of the challenge from animal rights advocates, scientists shouldA. communicate more with the public.B. employ hi-tech means in research.C. feel no shame for their cause.D. strive to develop new cures.50. From the text we learn that Stephen Cooper isA. a well-known humanist.B. a medical practitioner.C. an enthusiast in animal rights.D. a supporter of animal research.ABBADText 3In recent years, railroads have been combining with each other, mergingsintossuper systems, causing heightened concerns about monopoly. As recently as 1995,the top four railroads accounted for under 70 percent of the total ton-miles moved by rails. Next year, after a series of mergers is completed, just four railroads will control well over 90percent of all the freight moved by major rail carriers.Supporters of the new super systems argue that these mergers will allow for substantial cost reductions and better coordinated service. Any threat of monopoly, they argue, is removed by fierce competition from trucks. But many shippers complain that for heavy bulk commodities traveling long distances, such as coal, chemicals, and grain, trucking is too costly and the railroads therefore have them by the throat. The vast consolidation within the rail industry means that most shippers are served by only one rail company. Railroads typically charge such“captive”shippers 20 to 30 percent more than they do when another railroad is competing for the business. Shippers who feel they are being overcharged have the right to appeal to the federal government's Surface Transportation Board for rate relief, but the process is expensive, time consuming, and will work only in truly extreme cases.Railroads justify rate discrimination against captive shippers on the grounds that in the long run it reduces everyone's cost. If railroads charged all customers the same average rate, they argue, shippers who have the option of switching to trucks or other forms of transportation would do so, leaving remaining customers to shoulder the cost of keepingup the line. It's theory to which many economists subscribe, but in practice it often leaves railroads in the position of determining which companies will flourish and which will fail.“Do we really want railroads to be the arbiters of who wins and who loses in the marketplace?”asks Martin Bercovici, a Washington lawyer who frequently represents shipper.Many captive shippers also worry they will soon be his with a round of huge rate increases. The railroad industry as a whole, despite its brightening fortuning fortunes. still does not earn enough to cover the cost of the capital it must invest to keep up with its surging traffic. Yet railroads continue to borrow billions to acquire one another, with Wall Street cheering them on. Consider the .2 billion bid by Norfolk Southern and CSX to acquire Conrail this year. Conrail's net railway operating income in 1996 was just million, less than half of the carrying costs of the transaction. Who's going to pay for the rest of the bill? Many captive shippers fear that they will, as Norfolk Southern and CSX increase their grip on the market.51.According to those who support mergers railway monopoly is unlikely becauseA. cost reduction is based on competition.B. services call for cross-trade coordination.C. outside competitors will continue to exist.D. shippers will have the railway by the throat.52.What is many captive shippers' attitude towards the consolidation in the rail industry?A. Indifferent.B. Supportive.C. Indignant.D. Apprehensive.53.It can be inferred from paragraph 3 thatA. shippers will be charged less without a rival railroad.。
数据结构样卷1(英文)答案by郑
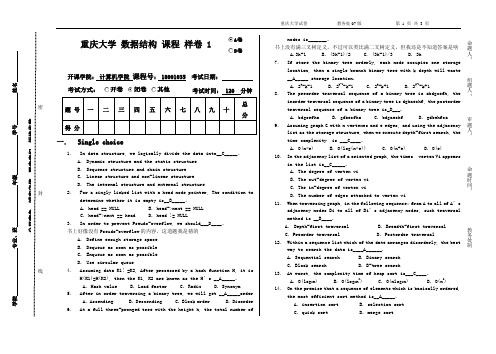
重庆大学 数据结构 课程 样卷1开课学院: 计算机学院 课程号: 18001035 考试日期:考试方式:考试时间: 120 分钟一. Single choice1. In data structure, we logically divide the data into__C_____。
A. Dynamic structure and the static structureB. Sequence structure and chain structureC. Linear structure and non-linear structureD. The internal structure and external structure2. For a singly linked list with a head node pointer, The condition todetermine whether it is empty is__B_____。
A. head == NULLB. head->next == NULLC. head->next == headD. head != NULL3. In order to prevent Pseudo-overflow, we should___D____。
书上好像没有Pseudo-overflow 的内容,这道题我是猜的A. Define enough storage spaceB. Dequeue as soon as possibleC. Enqueue as soon as possibleD. Use circular queue4. Assuming data K1! =K2, After processed by a hash function H, it isH(K1)=H(K2), then the K1, K2 are known as the H’s __A_____。
2003数据结构英文试卷

2003 Data Structure Test (120 minutes) Class: Student Number: Name:1.Single-Choice(20 points)(1) The Linked List is designed for conveniently b data item.a. gettingb. insertingc. findingd.locating(2) Assume a sequence list as 1,2,3,4,5,6 passes a stack, an impossible output sequence listIs c .a. 2,4,3,5,1,6b.3,2,5,6,4,1c.1,5,4,6,2,3d.4,5,3,6,2,1(3) A queue is a structure not implementing b .a. first-in/first-outb. first-in/last-outc. last-in/last-outd. first-come/first-serve(4) Removing the data item at index i from a sequential list with n items, d items needto be shifted left one position.a. n-ib. n-i+1c. id. n-i-1(5) There is an algorithm with inserting an item to a ordered SeqList and still keeping theSeqList ordered. The computational efficiency of this inserting algorithm is c .a. O(log2n)b. O(1)c. O(n)d.(n2)(6) The addresses which store Linked List d .a. must be sequentialb. must be partly sequentialc. must be no sequentiald. can be sequential or discontiguous(7) According the definition of Binary Tree, there will be b different Binary Treeswith 5 nodes.a. 6b. 5c. 4d. 3(8) In the following 4 Binary Trees, c is not the complete Binary Tree.a b c d(9) A Binary Tree will have a nodes on its level i at most.a.2ib. 2ic.2i+1d.2i-1(10) If the Binary Tree T2 is transformed from the Tree T1, then the postorder of T1 is theb of T2.a. preorderb. inorderc. postorderd. level order(11) In the following sorting algorithm, c is an unstable algorithm.a. the insertion sortb. the bubble sortc. quicksortd. mergesort(12) Assume there is a ordered list consisting of 100 data items, using binary search to find aspecial item, the maximum comparisons is d .a. 25b.1c. 10d.7(13) The result from scanning a Binary Search Tree in inorder traversal is in c order.a. descending or ascendingb. descendingc. ascendingd. out of order(14) The d case is worst for quicksort.a. the data which will be sorted is too larger.b. there are many same item in the data which will be sorted .c. the data will be sorted is out of orderd. the data will be sorted is already in a sequential order.(15) In a Binary Tree with n nodes, there is a non-empty pointers.a. n-1b. n+1c. 2n-1d.2n+1(16) In a undirected graph with n vertexs, the maximum edges is b .a. n(n+1)/2b. n(n-1)/2c. n(n-1)d.n2(17) The priority queue is a structure implementing c .a. inserting item only at the rear of the priority queue.b. inserting item only at the front of the priority queue.c. deleting item according to the priority of the item.d. first in/first out(18) The output from scanning a minimum heap with level traversal algorithm c .a. must be an ascending sequence.b. must be descending sequencec. must have a minimum item at the head position.d. must have a minimum item at the rear position.(19) Assume the preorder of T is ABEGFCDH, the inorder of T is EGBFADHC, then thepostorder of T will be a .a. GEFBHDCAb. EGFBDHCAc. GEFBDHCAd. GEBFDHCA(20) When a recursive algorithm is transformed into a no recursive algorithm, a structureb is generally used.a. SeqListb. Stackc. Queued. Binary Tree2. Please convert the following infix expression (a*(b+c))+(b/d-e)*a into postfix expression,in the converting process, please draw the change of operator stack and the change of the output. (10 points)3. Assume a list is {xal, wan, wil, zol, yo, xul, yum, wen, wim, zi, xem, zom}, please insert these items to an empty Binary Search Tree and then construct the AVL tree. Please draw the whole processes including inserting an item, or rotate nodes to restore height balance.(10 points)4. Assume a list is {48,35,64,92,77,13, 29,44}, firstly insert these items to an empty complete Binary Tree according to the sequence one by one, then please heapify the complete Binary Tree and implement the heap sort. Please draw the whole heapigying process and sorting process. (10 points)5. For the following directed graph, give the adjacency matrix and adjacency list. Then according your adjacency list, please scan the graph using the depth-first search and the breadth-first search and give the corresponding result. (10 points)6. Assume a list is 35,25,47,13,66,41,22,57, please sorting the list with quicksort algorithm. Please write every sorting pass result (no programming).(10 points)7. Assume keys={32,13,49,55,22,39,20}, Hash function is h(key)=key%7. The linear probe open addressing is used to resolve collisions. Please try to calculate the value of Hash for each key and give the final hash table. (10 points)8. Programming (All methods have been declared in textbook can be used directly, or you can rewrite them if they are not same in your answer) (20 points)(1) Assume there are two ascending ordered lists L1 and L2, please merge L1 and L2 into a new list L3. There will be no duplicate items in L3. Then please reverse the L3 into a descending ordered list.(10 points)(2) Please give the complete declaration of Queue in circle model, then write the insert algorithm and delete algorithm. (10 points)。
数据结构样卷3(英文)

重庆大学 《数据结构》 课程样卷 3开课学院: 计算机学院 课程号: 18001035 考试日期:考试方式:考试时间: 120 分钟一、 Single choice1. Merge two ordered list, both of them contain n elements, the least timesof comparison is ( ).A. nB. 2n-1C. 2nD. n-12. Sequential stored linear list with the length of 1000, if we insertan element into any position, the possibility is equal, when we insert a new element, the average number of removing elements is ( ). A. 1000 B. 1001 C. 500 D. 4993. Assume that the initial status of stack S and queue Q are both NULL,push elements e1,e2,e3,e4,e5,e6 into the stack S one by one, an element pops from stack, then enter into queue Q. If the sequence which the six elements in the dequeue is e2,e4,e6,e5,e3,e1, the capacity of stack S is at least ( ).A. 6B. 4C. 3D. 24. Two-dimensional array A [10 .. 20,5 .. 10] stores in line sequence,each element occupies 4 storage location, and the memory address of A[10,5] is 1000, then the address of A[20,9] is ( ). A. 1212 B. 1256 C. 1368 D. 13645. A tree with degree 3, it has 2 nodes with the degree 3, one node withthe degree 2, and 2 nodes with the degree 1, so the number of nodes with degree 0 is ( ).A. 4.B. 5.C. 6.D. 76. The inorder sequence of a binary tree is ABCDEFG, and its postordersequence is BDCAFGE, so its pre-order sequence is ( ) A. EGFACDB B. EACBDGF C. EAGCFBD D. EGAFCDB7. A Huffman tree with n leaf nodes, its total number of nodes is ( )A. n-1B. n+1C. 2n-1D. 2n+18. In an adjacency list of undirected graph with n vertexes and e edges,the number of edge node is ( ).A. nB. neC. eD. 2e9. The degree (sum of in-degree and out-degree) of a directed graph isk1, and the number of out-degree is k2. Therefore, in its adjacency list, the number of edge nodes in this singly linked list is ( ). A. k1 B. k2 C. k1-k2 D. k1+k210. If the graph has n vertexes is a circle, so it has ( ) spanning tree.A. nB. 2nC. n-1D.n+111. When look up a sequential list with the length 3, the possibility thatwe find the first element is 1/2, and the possibility that we find the second element is 1/3, the possibility that we find the third element is 1/6, so the average searching length to search any element (find it successfully and the sentry is at the end of the list) is ( ) A. 5/3 B.2 C. 7/3 D.4/312. There is an ordered list {3,5,7,8,11,15,17,22,23,27,29,33}, by binarysearch to search 27, so the number of comparison is ( ) A. 2 B. 3 C. 4 D. 513. Sort the following keyword sequences by using Quicksort, and theslowest one is ( )A. 19,23,3,15,7,21,28B. 23,21,28,15,19,3,7C. 19,7,15,28,23,21,3D. 3,7,15,19,21,23,28 14. Heapsort needs additional storage complexity is ( )A. O(n)B. O(nlog 2n)C. O(n 2) D. O(1)15. If we sort an array within the time complexity of O(nlog2n), needingsort it stably, the way that we can choose is ( )A. Merge sortB. Direct insertion sortC. Heap sortD. Quicksort二、 Fill the blanks1.Assume that the structure of the nodes in doubly circular linked list is (data,llink,rlink), without a head node in the list, if we want命题人:组题人:审题人:命题时间: 教务处制学院 专业、班 年级 学号 姓名公平竞争、诚实守信、严肃考纪、拒绝作弊封线密to insert the node which pointer s points after the node pointer ppoints, then execute as the following statements:; ; ___ _; ;2.Both stack and queue are _______linear structure.3.The four leaf nodes with the weight 9,2,5,7 form a Huffman tree, itsweighted path length is ________.4.In order to ensure that an undirected graph with six vertexes isconnected, need at least ______ edges.5.An n-vertex directed graph, if the sum of all vertices’ out-degreeis s, then the sum of all vertices’ degree is__ ___.6.The Depth-First traversal of a graph is similar to the binarytree_______ traversal; the Breadth-first graph traversal algorithmis similar to the binary tree ______traversal.7. A connected graph with n vertexes and e edges has ____ edges of itsspanning tree.8.The time complexity of binary searching is _____; if there are 100elements, the maximum number of comparisons by binary searching is____.9.Sort n elements by merge sort, the requiring auxiliary space is _____.10.Sort a linear list with 8 elements by Quicksort, at the best, thecomparison time is ______.三、 Application1. Begin from the vertex A, seek the minimum spanning tree by using Primalgorithms2. The following is AOE network:(1) How much time does it take to complete the whole project?(2) Find out all of the critical path.(9 points)3. Assume that a set of keywords is {1,12,5,8,3,10,7,13,97},tryto complete the following questions:(9 points)(1) Choose the keywords in sequence to build a binary sort tree Bt;(2) Draw the structure of the tree after deleting node “12”from thebinary tree Bt.4. The keyword sequence is {503,87,512,61,908,170,897,275,653,462}, usingradix sorting method to sort them in ascending order, try to write every trip results of sort. (9 points)四、 Algorithm1.The following algorithm execute on a singly linked list without headnode, try to analyze and write its function.(5 points)void function(LinkNode *head){LinkNode *p,*q,*r;p=head;q=p->next;while(q!=NULL){r=q->next;q->next=p;p=q;q=r;}head->next=NULL;head=p;}2.Design an algorithm to divide a singly linked list ‘A’ with a headpointer ‘a’ into two singly linked list ‘A’ and ‘B’, whose head pointers are ‘a’and ‘b’, respectively. On the condition that linked list A has all elements of odd serial number in the previous linked listA and linked listB has all elements of even serial number in the previouslinked list A, in addition, the relative order of the original linked list are maintained.(7 points)3. The type of binary tree is defined as follows:typedef struct BiTNode {char data;struct BiTNode *lchild,*rchild;}BiTNode, *BiTree;Please design an algorithm to count how many leaf nodes the binary tree have. (8 points)。
数据结构例题(英文版)

I Single Choice(10 points)1. ( )For the following program fragment the running time(Big-Oh) is .i = 0;s = 0;while(s <( 5*n*n + 2)){ i++;s = s + i;}a. O(n)b. O(n2)c. O(n1/2)d. O(n3)2. ( )Which is non-linear data structure_____.a. queueb.stackc. treed. sequence list3.( )The worst-time for removing an element from a sequence list (Big-Oh) is .a. O(1)b. O(n)c. O(n2)d. O(n3)4.( )In a circular queue we can distinguish(区分) empty queues from full queues by .a. using a gap in the arrayb. incrementing queue positions by 2 instead of 1c.keeping a count of the number of elementsd. a and c5.( )A recursive function can cause an infinite sequence of function calls if .a.the problem size is halved at each stepb.the termination condition is missingc.no useful incremental computation is done in each stepd.the problem size is positive6.( )The full binary tree with height 4 has nodes.a. 15b. 16c.31d.327. ( )Searching in an unsorted list can be made faster by using .a.binary searchb. a sentinel(哨兵)at the end of the listc.linked list to store the elementsd. a and c8.()Suppose there are 3 edges in an undirected graph G, If we represent graph G with a adjacency matrix, How many “1”s are there in the matrix?a. 3b. 6c. 1d. 99. ( ) Construct a Huffman tree by four leaf whose weights are 9, 2, 5, 7 respectively. The weighted path length is___________.a. 29b. 37c. 46d.4410. Consider the following weighted graph.Consider Dijkstra’s algorithm on this graph to find the shortest paths with s as a starting vertex. Which are the first four vertices extracted from the priority queue by the algorithm (listed in the order they are extracted) ?a. s, y, t, xb. s, y, x, zc. s, t, y, xd. s, y, x, tFig. 111. Here is an array of ten integers:5 3 8 9 1 7 0 26 4Suppose we partition this array using quicksort's partition function and using 5 for the pivot. Which shows the array after partition finishes:a. 5 3 4 2 1 0 7 9 6 8b. 0 3 4 2 1 5 7 9 6 8c. 3 1 0 2 4 5 8 9 6 7d. 3 1 0 2 4 5 8 9 7 6e. None of the aboveII Fill in Blank (10 points)1. For the following program fragment the running time(Big-Oh) is .for ( int i = 0; i < n; i++ )for ( int j = 0; j < =i; j++)s; //s为某种基本操作2. We store a 4×4 symmetric matrix A into an array B with row major order, Store the lower triangle only. the index of element a[2][3] in B is .3.We can use 3 vector type to store value and of non-zero elements in a sparse matrix.4. A______________ is a list where removal and addition occur at the same end . Frequently knowna LIFO (Last-In-First-Out) structure.5.T( n ) = 2T( n/2 )+ cn, T(n) = T( n-1)+cn, T( n ) = O(___________)6. There is a binary tree whose elements are characters. Preorder list of the binary tree is “ABECDFGHIJ” and inorder list of the binary tree is “EBCDAFHIGJ”. Postorder traversal sequence of the binary tree is .7.There are leaf nodes in a full binary tree with n nodes.8.When the input has been sorted ,the running time of insertion sort(Big-Oh) is .9.We sort the sequence(43,02,80,48,26,57,15,73,21,24,66)with shell sort for increment 3, the result is ______ _ .10、In a circular queue, “front” and “rear” are the front pointer and rear pointer respectively. Queue size is “maxsize”. When insert an element in the queue, rear = _________11. A ____________________________________________ is an example of a search tree which is multiway (allows more than two children).12. A tree in which every node is no smaller than its children is termed______________________.III Application of Algorithms(35 points)1.Graph G shown in Fig 2 is a directed graph, please describe G with adjacency matrix and write the orders of breadth first traversal and depth first traversal.Fig.22.The sequence of input keys is shown below:19,1,23,14,55,20,84,27,68,11,10,17A fixed table size of 19 and a hash function H(key)=key%13,with linear probing(线性探测), fill the table below and compute the average length of successful search.3. Show the results of inserting 53,17,78,09,45,65,87 each , one at a time, in a initially empty max heap(大根堆)4. write the sequence of preorder,postorder traversals and add inorder threads in the tree.Fig. 35. Build a Huffman tree and determine Huffman code when the probability distribution(概率分布) over the 8 alphabets ( c1, c2, c3, c4, c5, c6, c7, c8 ) is (0.05, 0.25, 0.03, 0.06, 0.10, 0.11, 0.36, 0.046. Graph G shown in Fig 4 is a directed graph, please describe G with adjacency list and write topological ordering.Fig. 4IV Fill in blank of algorithms.(15)1.Here is single source shortest path algorithm Dijkstra. Fill in blank of the algorithm.class Graph {//图的类定义private:float Edge[NumVertices][NumVertices];float dist[NumVertices];//最短路径长度数组int path[NumVertices];//最短路径数组int S[NumVertices];//最短路径顶点集public:void ShortestPath ( int, int );int choose ( int );};void Graph :: ShortestPath ( int n, int v ){//在具有n 个顶点的带权有向图中, 各边上权值由Edge[i][j]给出。
2003年英语真题及解析

2003年全国攻读硕士学位研究生入学考试英语试题Section I Use of EnglishDirections:Read the following text. Choose the best word(s) for each numbered blank and mark A, B, C OR D on ANSWER SHEET 1. (10 points)Teachers need to be aware of the emotional, intellectual, and physical changes that young adults experience. And they also need to give serious 1 to how they can best 2 such changes. Growing bodies need movement and 3 , but not justin ways that emphasize competition. 4 they are adjusting to their new bodies and a whole host of new intellectual and emotional challenges, teenagers are especially self-conscious and need the 5 that comes from achieving success and knowing that their accomplishments are 6 by others. However, the typical teenage lifestyle is already filled with so much competition that it would be 7 to plan activities in which there are more winners than losers, 8 ,publishing newsletters with many student-written book reviews, 9 student artwork, and sponsoring book discussion clubs. A variety of small clubs can provide 10 opportunities for leadership, as well as for practice in successful 11 dynamics. Making friends is extremely important to teenagers, and many shy students need the 12 of some kind of organization with a supportive adult 13 visible in the background.In these activities, it is important to remember that the young teens have 14 attention spans. A variety of activities should be organized 15 participants can remain active as long as they want and then go on to 16 else without feeling guilty and without letting the other participants 17 . This does not mean that adults must accept irresponsibility. 18 they can help students acquire a sense of commitment by 19 for roles that are within their 20 and their attention spans and by having clearly stated rules.1. [A] thought [B] idea [C] opinion [D] advice2. [A] strengthen [B] accommodate [C] stimulate [D] enhance3. [A] care [B] nutrition [C] exercise [D] leisure4. [A] If [B] Although [C] Whereas [D] Because5. [A] assistance [B] guidance [C] confidence [D] tolerance6. [A] claimed [B] admired [C] ignored [D] surpassed7. [A] improper [B] risky [C] fair [D] wise8. [A] in effect [B] as a result [C] for example [D] in a sense9. [A] displaying [B] describing [C] creating [D] exchanging10. [A] durable [B] excessive [C] surplus [D] multiple11. [A] group [B] individual [C] personnel [D]corporation12. [A] consent [B] insurance [C] admission [D] security13. [A] particularly [B] barely [C] definitely [D] rarely14. [A] similar [B] long [C] different [D] short15. [A] if only [B] now that [C] so that [D] even if16. [A] everything [B] anything [C] nothing [D] something17. [A] off [B] down [C] out [D] alone18. [A] On the contrary [B] On the average [C] On the whole [D] On the other hand19. [A] making [B] standing [C] planning [D] taking20. [A] capability [B] responsibility [C] proficiency [D] efficiencySection II Reading ComprehensionPart ADirections:Read the following four texts. Answer the questions below each text by choosing [A], [B], [C] or [D]. Mark your answers on ANSWER SHEET 1. (40 points)Text 1Wild Bill Donovan would have loved the Inter net. The American spymaster who built the Office of Strategic Services in the World War Ⅱ and later laid the roots for the CIA was fascinated with information. Donovan believed in using whatever tools came to hand in the “great game”of espionage—spying as a “profession.”These days the Net, which has already re-made such everyday pastimes as buying books and sending mail, is reshaping Donovan’s vocation as well.The latest revolution isn’t simply a matter of gentlemen reading other gentlemen’s e-mail. That kind of electronic spying has been going on for decades. In the past three or four years, the World Wide Web has given birth to a whole industry of point-and-clic k spying. The spooks call it “open source intelligence,” and as the Net grows, it is becoming increasingly influential. In 1995 the CIA held a contest to see who could compile the most data about Burundi. The winner, by a large margin, was a tiny Virginia company called Open-Source Solutions,whose clear advantage was its mastery of the electronic world.Among the firms making the biggest splash in the new world is Straitford, Inc., a private intelligence-analysis firm based in Austin, Texas. Straitford makes money by selling the results of spying (covering nations from Chile to Russia) to corporations like energy-services firm McDermott International. Many of its predictions are available online at .Straiford president George Friedman says he sees the online world as a kind ofmutually reinforcing tool for both information collection and distribution, a spymaster’s dream. Last week his firm was busy vacuuming up data bits from the far corners of the world and predicting a crisis in Ukraine. “As soon as that report runs, we’ll suddenly get 500 new internet sign-ups from Ukraine,”says Friedman, a former political science professor. “And we’ll hear back from some of them.”Open-source spying does have its risks, of course, since it can be difficult to tell good information from bad. That’s where Straitford earns its keep.Friedman relies on a lean staff of 20 in Austin. Several of his staff members have military-intelligence backgrounds. He sees the firm’s outsider status as the key to its success. Straitford’s briefs don’t sound like the usual Washington back-and-forthing, whereby agencies avoid dramatic declarations on the chance they might be wrong. Straitford, says Friedman, takes pride in its independent voice.21. The emergence of the Net has .[A] received support from fans like Donovan[B] remolded the intelligence services[C] restored many common pastimes[D] revived spying as a profession22. Donovan’s story is mentioned in the text to .[A] introduce the topic of online spying[B] show how he fought for the US[C] give an episode of the information war[D] honor his unique services to the CIA23. The phrase “making the biggest splash” (line 1,paragraph 3) most probablymeans .[A] causing the biggest trouble[B] exerting the greatest effort[C] achieving the greatest success[D] enjoying the widest popularity24. It can be learned from paragraph 4 that .[A] straitford’s prediction about Ukraine has proved true[B] straitford guarantees the truthfulness of its information[C] straitford’s business is characterized by unpredictability[D] straitford is able to provide fairly reliable information25. Straitford is most proud of its .[A] official status[B] nonconformist image[C] efficient staff[D] military backgroundText 2To paraphrase 18th-century statesman Edmund Burke, “all that is needed for thetriumph of a misguided cause is that good people do nothing.” One such cause now seeks to end biomedical research because of the theory that animals have rights ruling out their use in research. Scientists need to respond forcefully to animal rights advocates, whose arguments are confusing the public and thereby threatening advances in health knowledge and care. Leaders of the animal rights movement target biomedical research because it depends on public funding, and few people understand the process of health care research. Hearing allegations of cruelty to animals in research settings, many are perplexed that anyone would deliberately harm an animal.For example, a grandmotherly woman staffing an animal rights booth at a recent street fair was distributing a brochure that encouraged readers not to use anything that comes from or is tested in animals—no meat, no fur, no medicines. Asked if she opposed immunizations, she wanted to know if vaccines come from animal research. When assured that they do, she replied, “Then I would have to say yes.”Asked what will happen when epidemics return, she said, “Don’t worry, scientists will find some way of using computers.” Such well-meaning people just don’t understand.Scientists must communicate their message to the public in a compassionate, understandable way—in human terms, not in the language of molecular biology. We need to make clear the connection between animal research and a grandmother’s hip replacement, a father’s bypass operation, a baby’s vaccinations, and even a pet’s shots. To those who are unaware that animal research was needed to produce these treatments, as well as new treatments and vaccines, animal research seems wasteful at best and cruel at worst.Much can be done. Scientists could “adopt” middle school classes and present their own research. They should be quick to respond to letters to the editor, lest animal rights misinformation go unchallenged and acquire a deceptive appearance of truth. Research institutions could be opened to tours, to show that laboratory animals receive humane care. Finally, because the ultimate stakeholders are patients, the health research community should actively recruit to its cause not only well-known personalities such as Stephen Cooper, who has made courageous statements about the value of animal research, but all who receive medical treatment. If good people do nothing, there is a real possibility that an uninformed citizenry will extinguish the precious embers of medical progress.26. The author begins his article with Edmund Burke’s words to .[A] call on scientists to take some actions[B] criticize the misguided cause of animal rights[C] warn of the doom of biomedical research[D] show the triumph of the animal rights movement27. Misled people tend to think that using an animal in research is .[A] cruel but natural[B] inhuman and unacceptable[C] inevitable but vicious[D] pointless and wasteful28. The example of the grandmotherly woman is used to show the public’s .[A] discontent with animal research[B] ignorance about medical science[C] indifference to epidemics[D] anxiety about animal rights29. The author believes that, in face of the challenge from animal rights advocates,scientists should .[A] communicate more with the public[B] employ hi-tech means in research[C] feel no shame for their cause[D] strive to develop new cures30. From the text we learn that Stephen Cooper is .[A] a well-known humanist[B] a medical practitioner[C] an enthusiast in animal rights[D] a supporter of animal researchText 3In recent years, railroads have been combining with each other, merging into supersystems, causing heightened concerns about monopoly. As recently as 1995, the top four railroads accounted for under 70 percent of the total ton-miles moved by rails. Next year, after a series of mergers is completed, just four railroads will control well over 90 percent of all the freight moved by major rail carriers.Supporters of the new supersystems argue that these mergers will allow for substantial cost reductions and better coordinated service. Any threat of monopoly, they argue, is removed by fierce competition from trucks. But many shippers complain that for heavy bulk commodities traveling long distances, such as coal, chemicals, and grain, trucking is too costly and the railroads therefore have them by the throat.The vast consolidation within the rail industry means that most shippers are served by only one rail company. Railroads typically charge such“captive”shippers 20 to 30 percent more than they do when another railroad is competing for the business. Shippers who feel they are being overcharged have the right to appeal to the federal government's Surface Transportation Board for rate relief, but the process is expensive, time consuming, and will work only in truly extreme cases.Railroads justify rate discrimination against captive shippers on the grounds that in the long run it reduces everyone's cost. If railroads charged all customers the same average rate, they argue, shippers who have the option of switching to trucks or other forms of transportation would do so, leaving remaining customers to shoulder the cost of keeping up the line. It's theory to which many economists subscribe, but in practice it often leaves railroads in the position of determining which companies will flourish and which will fail.“Do we really want railroads to be the arbiters of who wins and who loses in the marketplace?”asks Martin Bercovici, a Washington lawyer who frequently represents shipper.Many captive shippers also worry they will soon be hit with a round of huge rate increases. The railroad industry as a whole, despite its brightening fortuning fortunes, still does not earn enough to cover the cost of the capital it must invest to keep up with its surging traffic. Yet railroads continue to borrow billions to acquire one another, with Wall Street cheering them on. Consider the $10.2 billion bid by Norfolk Southern and CSX to acquire Conrail this year. Conrail's net railway operating income in 1996 was just $427 million, less than half of the carrying costs of the transaction. Who's going to pay for the rest of the bill? Many captive shippers fear that they will, as Norfolk Southern and CSX increase their grip on the market.31. According to those who support mergers, railway monopoly is unlikelybecause .[A] cost reduction is based on competition.[B] services call for cross-trade coordination.[C] outside competitors will continue to exist.[D] shippers will have the railway by the throat.32. What is many captive shippers' attitude towards the consolidation in the railindustry?[A] Indifferent.[B] Supportive.[C] Indignant.[D] Apprehensive.33. It can be inferred from paragraph 3 that .[A] shippers will be charged less without a rival railroad.[B] there will soon be only one railroad company nationwide.[C] overcharged shippers are unlikely to appeal for rate relief.[D] a government board ensures fair play in railway business.34. The word “arbiters”(line 7,paragraph 4)most probably refers to those .[A] who work as coordinators.[B] who function as judges.[C] who supervise transactions.[D] who determine the price.35. According to the text, the cost increase in the rail industry is mainly causedby .[A] the continuing acquisition.[B] the growing traffic.[C] the cheering Wall Street.[D] the shrinking market.Text 4It is said that in England death is pressing, in Canada inevitable and in California optional. Small wonder. Americans’ life expectancy has nearly doubled over the past century. Failing hips can be replaced, clinical depression controlled,cataracts removed in a 30-minute surgical procedure. Such advances offer the aging population a quality of life that was unimaginable when I entered medicine 50 years ago. But not even a great health-care system can cure death—and our failure to confront that reality now threatens this greatness of ours.Death is normal; we are genetically programmed to disintegrate and perish, even under ideal conditions. We all understand that at some level, yet as medical consumers we treat death as a problem to be solved. Shielded by third-party payers from the cost of our care, we demand everything that can possibly be done for us, even if it’s useless. The most obvious example is late-stage cancer care. Physicians —frustrated by their inability to cure the disease and fearing loss of hope in the patient—too often offer aggressive treatment far beyond what is scientifically justified.In 1950, the US spent $12.7 billion on health care. In 2002, the cost will be $1,540 billion. Anyone can see this trend is unsustainable. Yet few seem willing to try to reverse it. Some scholars conclude that a government with finite resources should simply stop paying for medical care that sustains life beyond a certain age—say 83 or so. Former Colorado governor Richard Lamm has been quoted as saying that the old and infirm “have a duty to die and get out of the way”, so that younger, healthier people can realize their potential.I would not go that far. Energetic people now routinely work through their 60s and beyond, and remain dazzlingly productive. At 78, Viacom chairman Sumner Redstone jokingly claims to be 53. Supreme Court Justice Sandra Day O’Connor is in her 70s, and former surgeon general C. Everett Koop chairs an Internet start-up in his 80s.These leaders are living proof that prevention works and that we can manage the health problems that come naturally with age. As a mere 68-year-old, I wish to age as productively as they have.Yet there are limits to what a society can spend in this pursuit. As a physician, I know the most costly and dramatic measures may be ineffective and painful. I also know that people in Japan and Sweden, countries that spend far less on medical care, have achieved longer, healthier lives than we have. As a nation, we may be overfunding the quest for unlikely cures while underfunding research on humbler therapies that could improve people’s lives.36. What is implied in the first sentence?[A] Americans are better prepared for death than other people.[B] Americans enjoy a higher life quality than ever before.[C] Americans are over-confident of their medical technology.[D] Americans take a vain pride in their long life expectancy.37. The author uses the example of caner patients to show that .[A] medical resources are often wasted[B] doctors are helpless against fatal diseases[C] some treatments are too aggressive[D] medical costs are becoming unaffordable38. The author’s attitude toward Richard Lamm’s remark is one of.[A] strong disapproval [B] reserved consent[C] slight contempt [D] enthusiastic support39. In contras to the US, Japan and Sweden are funding their medical care.[A] more flexibly [B] more extravagantly[C] more cautiously [D] more reasonably40. The text intends to express the idea that.[A]medicine will further prolong people’s lives[B]life beyond a certain limit is not worth living[C] death should be accepted as a fact of life[D] excessive demands increase the cost of health carePart BDirections:Read the following text carefully and then translate the underlined segments into Chinese. Your translation should be written clearly on ANSWER SHEET 2. (10 points)Human beings in all times and places think about their world and wonder at their place in it. Humans are thoughtful and creative, possessed of insatiable curiosity.(41)Furthermore, humans have the ability to modify the environment in which they live, thus subjecting all other life forms to their own peculiar ideas and fancies. Therefore, it is important to study humans in all their richness and diversity in a calm and systematic manner, with the hope that the knowledge resulting from such studies can lead humans to a more harmonious way of living with themselves and with all other life forms on this planet Earth.“Anthropology” derives from the Greek words anthropos “human” and logos “the study of.” By its very name, anthropology encompasses the study of all humankind.Anthropology is one of the social sciences.(42)Social science is that branch of intellectual enquiry which seeks to study humans and their endeavors in the same reasoned, orderly, systematic, and dispassioned manner that natural scientists use for the study of natural phenomena.Social science disciplines include geography, economics, political, science, psychology, and sociology. Each of these social sciences has a subfield or specialization which lies particularly close to anthropology.All the social sciences focus upon the study of humanity. Anthropology is a field-study oriented discipline which makes extensive use of the comparative method in analysis.(43)The emphasis on data gathered first-hand, combined with a cross-cultural perspective brought to the analysis of cultures past and present, makes this study a unique and distinctly important social science.Anthropological analyses rest heavily upon the concept of culture. Sir EdwardTylor’s formulation of the concept of culture was one of the great intellectual achievements of 19th century science.(44)Tylor defined culture as “…that complex whole which includes belief, art, morals, law, custom, and any other capabilities and habits acquired by man as a member of society.” This insight, so profound in its simplicity, opened up an entirely new way of perceiving and understanding human life. Implicit within Tylor’s definition is the concept that culture is learned. shared, and patterned behavior.(45)Thus, the anthropological concept of “culture,” like the concept of “set” in mathematics, is an abstract concept which makes possible immense amounts of concrete research and understanding.Section III Writing46. Directions:Study the following set of drawings carefully and write an essay entitled in which you should1)describe the set of drawings, interpret its meaning, and2)point out its implications in our life.You should write about 200 words neatly on ANSWER SHEET 2. (20 points)第一部分英语知识运用试题解析一、文章总体分析文章主要论述了教师们应该关注青少年在成长时期所经历的情感、心智和生理上的变化,并采取方法帮助他们适应这些变化,健康成长。
数据结构英文试题(修改)

200X年试题选择题(1)Suppose 1,2,3,4 is the order which these elements push onto a stack. The sequence obtained is(B)A.4.1.2.3B.3.2.4.1C.3.4.1.2D.4.3.1.2(2)Suppose that a linear list contains n=31 nodes, the binary search is applied to the list, the maximum times in searching is (B)A 4B 5C 25-1D 24-1(3)In the following sorting algorithms, which is unstable(A)A Selection sortB Merge sortC Bubble sortD Insertion sort(4)Bubble sort is used for n nodes, the minimum number of comparisons is (A)A n-1B nC n(n-1/2)D n(n+1)/2(5)How many binary trees in different forms can at most be built by three nodes?(B)A 4B 5C 6D 7填空题.(1)The stack takes on character of ___________后进先出____________________(2)The postfix expression is ‘abcdef*/-*+’. Its infix expression is_a+b[c-d/(e*f)]____(3)The advantage of circular queues is _______克服队满溢出_________.(4)If the depth of full binary tree is k, then the number of nodes in the tree at least_2^k+1-1__ (5)The selection sort is used to sort n nodes, the number of its comparisons is __n(n-1)/2____ 三.(1) Write a function Deletion in C for linear list. (5 points)int sq_elete(list,p_n,i)int list[];/*形参数组可不指定大小*/int *p_n,i;{int j;if(i<0||i>=*p_n) return(1);for(j=i+1,j<*p_n;j++) list[j-1]=list[j];(*p_n)--;return(0);}(2)Write a function Pop in C for linked stack. (5 points)(3)Write a function in C for binary search. (10 point )int bisect(a,n,v)int a[],v, n;{ int i,j,m;i=0;j=n-1;while(i<=j){ m=(i+j)/2;if(v==a[m])return(m);if(v<a[m]) j=m-1;else i=m+1;}return(-1);}(4)Write some sentences in C which delete the node b in the following figure. (5 point)(附图)(5)Write some sentences in C which insert the node b in the following figure(5pont)(附图)四.(2)Write a function in C of quick sort. (10 point )Position Partition(List *list, Posotion low, Position high){ ListEntry pivot;Position i, lastsmall, pivotpos;Swap(low,(low+high)/2,list);pivot=list->entry[low];pivotpos=low;for(i=low+1; i<=high;i++)if(LT(list->entry[i].key, pivot.key))Swap(++pivotpos, i, list);Swap(low, pivotpos, list);return pivotpos;}(3)Suppose that a hash table contains 5 entries indexed from 0 through 4 and that the following keys are to be mapped into the table.12,19,17,14,10,24,15Hash function h(k)=k mod 5.(a)Determine the hash addresses and resolute collision by chaining.(b)Write a function in C for search by chaining. (10point)void search2(t,k,p,q)NODE *t[ ];int k;NODE *p,*q;{ *p=NULL;*q=t[h(k)];while(*q!=NULL)if ((*q)->key==k) return;else{*p=*q;*q=(*q)->link;}}五.(1)Write a function in C which will inter change all left and right subtrees in binary tree. (10 point)(2)Write a function in C for linked queue.(10 point)void Append(QueueEntry x,Queue *q){if (QueueFull(q))Error(“cannot append an entry to a full queue.”);else{q->count++;q->rear=(q->rear+1)%MAXQUEUE;q->entry[q->rear]=x;}}选择题(1)In a simple linked list with n nodes, the number of pointer fields with NULL Totals(D).A. nB.2C.n/2D.1(2)In the linear lists, two concepts which are the same as each other is(AB)A node B. record C. field D. type of structure(3)In the binary search tree, for any root of subtree, the keys of all nodes in its left subtree is (D) the keys of all nodes in its right subtree.A less thanB equal toC great thanD less than or equal to(4)For general trees, the correct choice is (B)A it may be emptyB at least one nodeC at least two nodesD A.B and C are incorrect(5)The bubble sort is used to n nodes, least number of comparison is(A)A n-1B nC n(n-1)/2D n(n+1)/2填空题(1)A binary tree with n nodes storaged by standard form, there are ___2n__ pointers where _n-1___pointers are used to point to sub-nodes, and _n+1___ pointers are empty.(2)The postfix expression is abc*+de/f*-, then its infix expression is _a+b*c-d/e*f___(3)The basic operations of linear lists are___插入删除访问______(4)The character of stack is__后进先出__________(5)Hash storage faced with two problems of __Hash函数____ and ____冲突___三.(1)Write a function Pop for stack (5point )V oid Pop(StackEntry *item, Stack *s){if(StackEmpty(s))Error;else*item=S->entry[--s->top] ;}(2)Translate the quadratic formula.(a+b*c)↑d↑(e*f/g)-h*iinto postfix form. (10point)(3)Write a function in C which changes the linked list in Figure 1 to another linked list in Figure2.(10point)(附图)(4)(1).(a)By hand, trace through the steps bubble sort will use on the list. The following seven number to be sorted into increasing order.(b)Write a function of bubble sort. (10point)void bubble_sort(a,n)int a[],n;{ int i,j,t;n ;while(n>0){j=0;for(i=0;i<n;i++)if(a[i]>a[i+1]){t=a[i];a[i]=a[i+1];a[i+1]=t;j=i;}n=j;}}(2)By hand, sort the list 46.26.22.68.48.42.36.84.66 using selection sort.Write a function of selection sort.(10point)void insertion_sort(a, n)int a[ ];int n;{ int i, j;int t;for(i=1;i<n;i++){t=a[i];for(j=i-1;j>=0&&t<a[j];j--)a[j+1]=a[j];a[j+1]=t;}}(3).Suppose that a hash table contains 11 entries from 0 through 10 and that the following keys are to be mapped into the table.(32,75,63,48,94,25,36,18,70)Hash function h(k)=k mod 11(a)Determine the hash addresses and resolute collision by linear probing.(b)Determine the hash addresses and resolute collision by chaining. (10point )(4)For each of the following binary trees, determine the order in which the nodes will be visitedmixed order given by invoking function A(5point)Void A(TreeNode *root, void(*Visit)(TreeEntry x) ){If(root){Visit(root->entry)’B(root->left, Visit);B(root->right, Visit);}}void B(TreeNode *root, void(*Visit)(TreeEbtry x)){If(root){A(root->left, Visit);Visit(root->entry);A(root->right, Visit);}}五.(2)Insert a new node r taken as the right child of node s and draw a threaded-tree.(a) By hand(b) By some sentences in C (10 point)(a)(b)r->rightchild=s->rightchild; // s的右子女指针或后继线索传给rr->rightthread=s->rightthread;//标志一同传送//ar->leftchild=s;r->leftthread=1; // r为leftchild或为s的前驱线索//bs->rightchild=r;s->rightthread=0; //r成为s的右子女//c。
2003年考研英语—真题及答案

考 生 选出了 正 确案 , 答对率 不 高 。 更多的考生选择的是 D。选错的原因可能在于考生对“reshap与e ”“revive的”词义差别区分不清。“revive一”词
的含义是“to come or bring back into use osrtexnice(”<使>复兴 ,<使>复活),暗含的意思是某事物已不存 在或已 丧失作用。第一段并没有提到间谍 行业曾经消失的信息, 从第二段中我们了解到互联网推动了情报行业的发 展, 也 没有找 到 任何 关于 情 报行业 曾经 中断 的内 容 ,所 以 D 选项 的说法 是不正 确的 。
一段的最后一句话。在后面的几段中,作者介绍了互联网对情报工作的Байду номын сангаас响。所以答案是
truthfulness of
its
information
characterized by
unpredictability
45.
Stratiford
is
most
proud
of
its
________.
[A]
official
status
[B]
nonconformist
image
[C] [D]
efficient military
Friedman reelis on ael an staff of 20ni Austin. Severaolf his staff members have military-intelligence backgrounds. He
sees the firm's outsider status as the key to its success.Straitford's briefs don't sound like the usual Washington
2003年考研英语—真题与答案

2003 年考研英语真题及答案2003 text1Wild Bill Donovan would haveovedl the Internet. The American spymaster who built the Office of Strategic Servicesni the World War Ⅱ and aterl aidl the roots for the CIAwas fascinated with information. Donovan believed in using whatever tools came tohand in the "great game"of espionage— spying as a "profession".These days the Net, which has alreadyre-made such everyday pastimes as buying books and sendingreshapingmail, Donovan's vocation as .well The atestl revolutionsn'ti simply a matter of gentlemen reading other gentlemen's e-mail. That kind ofectronicel spyinghas been going on for decades. In the past three or four years, orldthe W ide Web has given birth to a whole industry ofpoint-and-click spying. The spooks call it "open-sourceintelligence",and as the Net grows, it is becoming increasingly influential. In 1995 the CIA held a contest to see who could compile the most data about Burundi. The winner, byargelmargin, was a tiny Virginia company called Open Source Solutions, whosearcl advantage was its mastery of theectroniel world.Among the firms making the biggestashpl in this new world is Straitford, Inc., a private intelligence-analysifirm based in Austin, Texas.Straitford makes money by selling the results of spying (covering nations from Chile to Russia) to corporations like energy-services firm McDermott International. Many of its predictions are available online at .Straiford presidentGeorge Friedman says he sees the online world as kinda of mutually reinforcing tool for both information collection and distribution, a spymaster's dream. Last sweekfirm hiwas busy vacuuming up data bits from the far corners of the world and predicting a crisis in Ukraine. "As soon as that report runs, we'llsuddenly get 500 new Internet sign-ups from Ukraine," saysFriedman, a formerpolitical science professor."And we'll hear back from some of them." Open-source spying does havets risks, of course, since it can be difficult to tell good information from bad. That's where Straitford earns its keep.Friedman relies on a eanl staff of 20ni Austin. Severalof his staff members have military-intelligence backgrounds. He sees the firm's outsider status as the key to its success.Straitford's briefs don't sound like the usual Washington back-and-forthing,whereby agencies avoid dramatic declarations on the chance they might be wrong. Straitford, says Friedman, takes pride in its independentcevoi.41.The emergence of the Net has________.[A]received support from fans like Donovan[B]remolded the intelligence services[C]restored many common pastimes[D] revived spying as a profession42.Donovan's story is mentioned in the text to________.[A]introduce the topic of online spying[B]show how he fought for the US[C]give an episode of the information war[D] honor his unique services to the CIA43.The phrase"making the biggest splash" (line 1,paragraph 3)most probably means ________.[A]causing the biggest trouble[B]exerting the greatest effort[C]achieving the greatest success[D] enjoying the widest popularity44.It can be learned from paragraph4that________.[A]Straitford's prediction about Ukraine has proved true[B]Straitford guarantees the truthfulness of its information[C]Straitford's business is characterized by unpredictability[D] Straitford is able to provide fairly reliable information45.Straitford is most proud of its________.[A]official status[B]nonconformist image[C]efficient staff[D]military background 试题解析:这是一篇说明性的文章,介绍了互联网技术对情报行业的影响。
数据结构考试题(英文版)C++

数据结构考试题(英文版)C++Final Examination Paper On Data Structures(B)I、Fill Vacant Position (1′×10=10′)1、Only ______________________graph has topological order.2、In a______ data structure, all insertions and deletions of entries are madeat one end. It is particularly useful in applications involving______.3、In c++ , we use _______________operator to implement the circularqueues.4、In processing a contiguous list with n entries: insert and remove requiretime approximately to ___. And List, clear, empty, full, size, replace, and retrieve operate in _________ time.5、One of method of searching is ____________________that requiresordered list.6、The time complexity of the insertionsort on average is______________.7、____________is the name for the case when a function invokes itself orinvokes a sequence of other functions,one of which eventually invokes the __________again.II、Multiple choice (2′×10=20′)1、A queue is a version of ( )A. linked listB. LIFO listC. sequential listD. FIFO list2、In a tree, ______are vertices with the same parent. ( )A. childrenB. siblingC. adjacentD. leaf3、How many shapes of binary trees withthree nodes are there ( )A. 12B.15C. 6D. 54、Among sorting algorithms, which kind of algorithm is divide-and-conquer sorting ( ).A. shell sortB. heap sortC. quick sortD. insertionsortIn a binary tree, if the result of traversing under preorder is the same as that under inorder,then ( )A. It is only a binary tree with one nodeB. It is either empty, or the left subtree of any node of the tree is emptyC. It is only an empty binary treeD. It is either empty, or the right subtree of an node of the tree is empty6、For the following graph, one of results ofbreadth-first traversal is ( )A. acbdieghfB. abcideghfC. abcdefghiD. abdeighfc7、The time requirement of retrieving a given target in hash table with n entries is ( )A. O(n)B. O(log2n)C. O(1)D.O(nlog2n)8、Which function is smallest order of magnitude? ( )A. 2 nB. n + lgnC.n 0.1D.100009、There are _______solutions to the problem of placing four queens on a 4×4 board. ( )A. 2B. 3C. 6D. 410、For the following binary tree, the result of traversing under inorder is ( )A. abcdefghiB. dgbechfiaC. dgbaechfiD. gdbehifcaIII、Analyze and Calculate ( 10′×1=10′)1、Let A be a lower triangular matrix andSuppose that (a) Elements of A are stored in row-major ordering(b) Each element occupies k memory locations(c) Indexing begins at 0Please give the calculating formula ofLoc(aij)(address of the element aij) IV、Comprehensive Problem( 8′×5=40′)1、Draw a diagram to illustrate the configuration of linked nodes that iscreated by the following statement.Node *p0=new Node (a);Node *p1=p0→next=new Node(b);Node *p2=p1→next=new Node(c,p1);2、 By hand, trace the action ofquick-sort on the following lists. Given pivot is first entry .35 41 46 38 29 22 3243、Suppose that(a) A hash table contains hash_size=16 position indexed from0 to 15(b) A hash function H(key)=(key*3-2)%13(c) The following keys are to be mapped into the table:10 120 33 45 58 26 3 27 200 400 2Draw the hash table with the collision resolution of chaining.4、Construct a minimal spanning tree of the following connected network.Please give key steps.5、Given a sequence of keys:B , Z,A,Y, C,V, D, W, E,X, FInsert the keys in the order shown above, to build them into an AVL tree (draw the principal AVL tree).V、Develop Algorithm( 10′×2=20′)1、Assume we have the following class specifications:const int maxstack=10;class Stack{public:Stack( );bool empty( )const;Error_code pop( );Error_code top(int &item)const;Error_code push(const int &item);Private:int count;int entry[maxstack]; };Write a program that uses a Stack to read an integer and print all its prime divisors in descending order. For example, with the integer 2100 the output should be 7 5 5 3 2 2 .2、For linked implementation of binary trees, we have the folowing classspecifications:templatestruct Binary_node {Entry data;Binary_node *left;Binary_node *right;};templateclass Binary_tree{protected:Binary_node *root;void recursive_exchange (Binary_node *sub_root);public:void exchange ();};templatevoid Binary_tree:: exchange () {recursive_ exchange (root);}Write the auxiliary function recursive_ exchange to exchange the left subtree and the right subtree of any node ina binary tree.Answer of Final Examination Paper On Data Structures (B)I.1、directed with no cycle(有向无环图) 2、stack栈 reversing 逆序3、 modulus (or i=(i+1)%max)求余、模4、 n constant 常数5、 binary search二分查找6、 0.25n 2 +O(n) 或O(n 2 )7、 Recursion 递归 first function 第一个函数、自身II. 1、D 2、B 3、D 4、C 5、B 6、B 7、C 8、D 9、A10、CIII.:IV.1、2、first pass: 32 29 22 35 41 46 38second pass: 22 29 32 35 38 41 46third pass: 22 29 32 35 38 41 463、 4、5、V. 1、# inlcude# inlcudeVoid main( ){ stack s;int m,n,t;cout<<”please input a number:”;cin>>n;m=n/2;for( i=2; i<=m; i++ )while( n%i==0 ){ s.push(i); n=n/I; }cout<<”descending order is:”<<endl;< p="">while( !s.empty() ) {s.top(t);cout<<t<<="">s.pop(); }cout<<endl;< p="">}3、templatevoidBinary_tree::recursive_exchange(Binary_node*sub_root) { Binary_node *temp;if(sub_root==NULL) return;temp= sub_root->left;sub_root->left=sub_root->right;sub_root->right=temp;recursive_exchange(sub_root->left);recursive_exchange(sub_root->right);}</endl;<></t<</endl;<>。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
2003 Data Structure Test (120 minutes) Class: Student Number: Name:1.Single-Choice(20 points)(1) The Linked List is designed for conveniently b data item.a. gettingb. insertingc. findingd.locating(2) Assume a sequence list as 1,2,3,4,5,6 passes a stack, an impossible output sequence listIs c .a. 2,4,3,5,1,6b.3,2,5,6,4,1c.1,5,4,6,2,3d.4,5,3,6,2,1(3) A queue is a structure not implementing b .a. first-in/first-outb. first-in/last-outc. last-in/last-outd. first-come/first-serve(4) Removing the data item at index i from a sequential list with n items, d items needto be shifted left one position.a. n-ib. n-i+1c. id. n-i-1(5) There is an algorithm with inserting an item to a ordered SeqList and still keeping theSeqList ordered. The computational efficiency of this inserting algorithm is c .a. O(log2n)b. O(1)c. O(n)d.(n2)(6) The addresses which store Linked List d .a. must be sequentialb. must be partly sequentialc. must be no sequentiald. can be sequential or discontiguous(7) According the definition of Binary Tree, there will be b different Binary Treeswith 5 nodes.a. 6b. 5c. 4d. 3(8) In the following 4 Binary Trees, c is not the complete Binary Tree.a b c d(9) A Binary Tree will have a nodes on its level i at most.a.2ib. 2ic.2i+1d.2i-1(10) If the Binary Tree T2 is transformed from the Tree T1, then the postorder of T1 is theb of T2.a. preorderb. inorderc. postorderd. level order(11) In the following sorting algorithm, c is an unstable algorithm.a. the insertion sortb. the bubble sortc. quicksortd. mergesort(12) Assume there is a ordered list consisting of 100 data items, using binary search to find aspecial item, the maximum comparisons is d .a. 25b.1c. 10d.7(13) The result from scanning a Binary Search Tree in inorder traversal is in c order.a. descending or ascendingb. descendingc. ascendingd. out of order(14) The d case is worst for quicksort.a. the data which will be sorted is too larger.b. there are many same item in the data which will be sorted .c. the data will be sorted is out of orderd. the data will be sorted is already in a sequential order.(15) In a Binary Tree with n nodes, there is a non-empty pointers.a. n-1b. n+1c. 2n-1d.2n+1(16) In a undirected graph with n vertexs, the maximum edges is b .a. n(n+1)/2b. n(n-1)/2c. n(n-1)d.n2(17) The priority queue is a structure implementing c .a. inserting item only at the rear of the priority queue.b. inserting item only at the front of the priority queue.c. deleting item according to the priority of the item.d. first in/first out(18) The output from scanning a minimum heap with level traversal algorithm c .a. must be an ascending sequence.b. must be descending sequencec. must have a minimum item at the head position.d. must have a minimum item at the rear position.(19) Assume the preorder of T is ABEGFCDH, the inorder of T is EGBFADHC, then thepostorder of T will be a .a. GEFBHDCAb. EGFBDHCAc. GEFBDHCAd. GEBFDHCA(20) When a recursive algorithm is transformed into a no recursive algorithm, a structureb is generally used.a. SeqListb. Stackc. Queued. Binary Tree2. Please convert the following infix expression (a*(b+c))+(b/d-e)*a into postfix expression,in the converting process, please draw the change of operator stack and the change of the output. (10 points)3. Assume a list is {xal, wan, wil, zol, yo, xul, yum, wen, wim, zi, xem, zom}, please insert these items to an empty Binary Search Tree and then construct the AVL tree. Please draw the whole processes including inserting an item, or rotate nodes to restore height balance.(10 points)4. Assume a list is {48,35,64,92,77,13, 29,44}, firstly insert these items to an empty complete Binary Tree according to the sequence one by one, then please heapify the complete Binary Tree and implement the heap sort. Please draw the whole heapigying process and sorting process. (10 points)5. For the following directed graph, give the adjacency matrix and adjacency list. Then according your adjacency list, please scan the graph using the depth-first search and the breadth-first search and give the corresponding result. (10 points)6. Assume a list is 35,25,47,13,66,41,22,57, please sorting the list with quicksort algorithm. Please write every sorting pass result (no programming).(10 points)7. Assume keys={32,13,49,55,22,39,20}, Hash function is h(key)=key%7. The linear probe open addressing is used to resolve collisions. Please try to calculate the value of Hash for each key and give the final hash table. (10 points)8. Programming (All methods have been declared in textbook can be used directly, or you can rewrite them if they are not same in your answer) (20 points)(1) Assume there are two ascending ordered lists L1 and L2, please merge L1 and L2 into a new list L3. There will be no duplicate items in L3. Then please reverse the L3 into a descending ordered list.(10 points)(2) Please give the complete declaration of Queue in circle model, then write the insert algorithm and delete algorithm. (10 points)。
