cisco防火墙配置手册
思科防火墙配置

11、给内部某个主机配置一个静态的公网IP地址
打开某端口给某台机器(假设IP为1.1.1.1):
conduit permit tcp host 1.1.1.1 eq 2000 any any
查看端口打开状态,应该用show static吧,记不清了。
以下是pix506的基本配置:
1、 给PIX506接上电源,并打开电脑主机。
2、 将CONSOLE口连接到主机的串口上,运行Hyperterminal程序,从CONSOLE口进入PIX系统。
3、 进入特权模式
PIX> enable
PIX#
4、 进入全局控制模式并设置密码
PIX#configure terminal
PIX(config)#passwd chenhong
arp inside 192.168.1.66 0017.316a.e5e8 alias
arp inside 192.168.1.70 0017.316a.e140 alias
/*允许访问外网的IP,其他IP都不能访问*/
access-list 110 permit ip host 192.168.1.86 any
icmp-object echo-reply
icmp-object unreachable
object-group network WWWSERVERS
network-object host 外网IP
access-list ACLIN permit tcp 外网IP 子网掩码 object-group WWWSERVERS object-group MYSERVICES
cisco防火墙配置手册

ASA防火墙配置笔记二〇〇六年十月二十七日序言:Cisco新的防火墙ASA系列已经面市了,将逐步取代PIX防火墙,网上关于ASA配置资料很少,现把我积累的ASA配置技术编写一个文档,供大家参考。
如有问题,可发邮件给我。
1. ....................................................................................... 常用技巧12. ....................................................................................... 故障倒换13. ....................................................... 配置telnet、ssh及http管理34. ........................................................................ v pn常用管理命令35. ............................................................................... 配置访问权限36. .................................................................. 配置sitetosite之VPN47. .............................................................. w ebvpn配置(ssl vpn)48. .............................................................................. 远程拨入VPN59. ........................................................................... 日志服务器配置610. .......................................................................... Snmp网管配置711. .................................................................................... ACS配置712. ................................................................................... AAA配置713. ..................................................................................... 升级IOS814. ..................................................................................... 疑难杂症81.常用技巧Sh ru ntp查看与ntp有关的Sh ru crypto 查看与vpn有关的Sh ru | inc crypto 只是关健字过滤而已2.故障倒换failoverfailover lan unit primaryfailover lan interface testint Ethernet0/3failover link testint Ethernet0/3failover mac address Ethernet0/1 0018.1900.5000 0018.1900.5001failover mac address Ethernet0/0 0018.1900.4000 0018.1900.4001failover mac address Ethernet0/2 0018.1900.6000 0018.1900.6001failover mac address Management0/0 0018.1900.7000 0018.1900.7001failover interface ip testint 10.3.3.1 255.255.255.0 standby 10.3.3.2注:最好配置虚拟MAC地址sh failover显示配置信息write standby写入到备用的防火墙中failover命令集如下:configure mode commands/options:interface Configure the IP address and mask to be used for failoverand/or stateful update informationinterface-policy Set the policy for failover due to interface failureskey Configure the failover shared secret or keylan Specify the unit as primary or secondary or configure theinterface and vlan to be used for failover communication link Configure the interface and vlan to be used as a link forstateful update informationmac Specify the virtual mac address for a physical interface polltime Configure failover poll intervalreplication Enable HTTP (port 80) connection replicationtimeout Specify the failover reconnect timeout value forasymmetrically routed sessionssh failover 命令集如下:history Show failover switching historyinterface Show failover command interface informationstate Show failover internal state informationstatistics Show failover command interface statistics information| Output modifiers<cr>3.配置telnet、ssh及http管理username jiang password Csmep3VzvPQPCbkx encrypted privilege 15aaa authentication enable console LOCALaaa authentication telnet console LOCALaaa authentication ssh console LOCALaaa authorization command LOCALhttp 192.168.40.0 255.255.255.0 managementssh 192.168.40.0 255.255.255.0 inside4.vpn常用管理命令sh vpn-sessiondb full l2l 显示site to site 之vpn通道情况sh ipsec stats 显示ipsec通道情况sh vpn-sessiondb summary 显示vpn汇总信息sh vpn-sessiondb detail l2l 显示ipsec详细信息sh vpn-sessiondb detail svc 查看ssl client信息sh vpn-sessiondb detail webvpn 查看webvpn信息sh vpn-sessiondb detail full l2l 相当于linux下的ipsec whack –status 如果没有建立连接,则表示ipsec通道还没有建立起来。
Cisco防火墙模块安装配置手册

WS-SVC-FWM-1
Serial No. SAD062302U4
例如,刚才我们查看的防火墙模块是在 Mod 4 上,我们就可以输入登陆防火 墙
Router# session slot 4 processor 1
第三步,输入登陆密码默认是 cisco
password:
第四步,输入 enable 密码,默认没有密码
防火墙模块安装配置
防火墙模块安装配置
1 内容介绍
为配合 PICC 项目防火墙模块的安装,此防火墙配置说明文档将对防火墙基 本配置和使用情况进行介绍。
本文章包括防火墙基本性能介绍、安装方法、防火墙配置命令说明等内容, 并通过实例对命令进行一一讲解。
2 防火墙模块介绍
2.1 防火墙模块介绍
Cisco Catalyst® 6500 交换机和 Cisco 7600 系列路由器的防火墙服务模块 (FWSM)是一种高速的、集成化的服务模块,可以提供业界最快的防火墙数据 传输速率:5Gb 的吞吐量,100000CPS,以及一百万个并发连接。在一个设备中 最多可以安装四个 FWSM,因而每个设备最高可以提供 20Gb 的吞吐量。作为世 界领先的 Cisco PIX 防火墙系列的一部分,FWSM 可以为大型企业和服务供应商 提供无以伦比的安全性、可靠性和性能。
4
防火墙模块安装配置
3.2 确认防火墙模块
安装完防火墙模块后,开启交换机,确认防火墙模块是否被交换机识别。 Cisco IOS software 通过命令 show module 查看防火墙模块状态是否正常
Router> show module
Mod Ports Card Type
Model
--- ----- -------------------------------------- ------------------ -----------
Cisco ASA 5585-X 高密度状态式防火墙数据手册说明书

Data SheetCisco ASA 5585-X Stateful FirewallToday’s enterprise networks struggle to keep up with a mobile workforce. Users expect on-demand access from their many devices, even as applications multiply and push performance levels. And of course security remains a priority. How do you scale and still preserve the integrity of the network? Start with the Cisco® ASA 5585-X Firewall, a compact yet high-density firewall that delivers tremendous scalability, performance, and security in a two-rack-unit (2RU) footprint.Using a single firewall blade, the Cisco ASA 5585-X meets the growing needs of dynamic organizations by providing eight times the performance density, very high VPN session counts, twice as many connections per second, and four times the connection capacity of any competitive firewall.Firewall FeaturesSupport for Layer 3 and Layer 4 stateful firewall inspection features, including access control and network address translation, enables organizations to keep existing stateful inspection policies that are essential for compliance regulations and securing critical data center resources.In addition to comprehensive stateful inspection capabilities, Layer 7 next-generation policies act intelligently on contextual information. Cisco AnyConnect® technology provides information on the type and location, and endpoint posture of a mobile device before it accesses the network, so that administrators can maintain high levels of network visibility, protection and control. Threat intelligence feeds from Cisco Collective Security Intelligence (CSI) use the global footprint of Cisco security deployments to analyze approximately one-third of the world’s Internet traffic for near-real-time protection from new and emerging threats.Flexible Deployment OptionsThe Cisco ASA 5585-X supports two hardware blades in a single 2RU chassis. The bottom slot (slot 0) hosts the ASA stateful inspection firewall module, while the top slot (slot 1) can be used for adding up to two Cisco ASA 5585-X I/O modules for high interface density for mission-critical data centers that require exceptional flexibility and security.ClusteringUsing Cisco ASA Software Release 9.0 and later, customers can combine up to 16 Cisco ASA 5585-X firewall modules in a single cluster for up to 640 Gbps of throughput, 2 million connections per second, and more than 100 million concurrent connections. This “pay as you grow” model enables organizations to purchase what they need today and dynamically add more when their performance needs grow. To protect high-performance data centers from internal and external threats, the cluster can be augmented by adding IPS modules.Cisco ASA software clustering delivers a consistent scaling factor, irrespective of the number of units in the cluster, for a linear and predictable increase in performance. Complexity is reduced, as no changes are required to existing Layer 2 and Layer 3 networks. Support for data center designs based on the Cisco Catalyst® 6500 Series Virtual Switching System (VSS) and the Cisco Nexus virtual PortChannel (vPC) as well as the Link Aggregation Control Protocol (LACP) provides high availability (HA) with better network integration.For operational efficiency, Cisco ASA clusters are easy to manage and troubleshoot as a single entity. Policies pushed to the master node are replicated across all the units within the cluster. The health, performance, and capacity statistics of the entire cluster, as well as individual units within the cluster, can be assessed from a single management console. Hitless software upgrades are supported for ease of device updates.Clustering supports HA in both active/active and active/passive modes. All units in the cluster actively pass traffic, and all connection information is replicated to at least one other unit in the cluster to support N+1 HA. In addition, single and multiple contexts are supported, along with routed and transparent modes. A single configuration is maintained across all units in the cluster using automatic configuration sync. Clusterwide statistics are provided to track resource usage.Cisco TrustSec IntegrationUsing Cisco ASA Software Release 9.0 and later, the Cisco ASA 5585-X provides context awareness through the integration of identity-based firewall security and Cisco TrustSec® security group tags for enhanced visibility and control. Identity-based firewall security provides more flexible access control to enforce policies based on user and group identities and the point of access. Administrators can write policies that correspond to business rules, a process that increases security, enhances ease of use, and requires fewer policies to manage. Similarly, Cisco TrustSec integration enables security group tags to be embedded into the network, providing administrators with the ability to develop and enforce better, more precise policies.Cut Costs While Improving Performance and SecurityThe Cisco ASA 5585-X Next-Generation Firewall delivers superior scalability, performance, and security to handle high data volumes without sacrificing performance. Most firewalls require up to 16RUs and 5100 watts to scale to the level of performance that the Cisco ASA 5585-X achieves with only 2RUs and 785 watts. This performance helps enterprises meet the increasing demands for network connectivity without the need to invest in additional data center space and incur the corresponding maintenance costs.Based on tests conducted by Cisco, the Cisco ASA 5585-X significantly reduces initial procurement costs by 80 percent, power consumption costs by 85 percent, and rack space requirements by 88 percent in addition to significant reductions in overall integration and management complexity and costs. In addition, you can install up to two firewall modules in a single Cisco ASA 5585-X chassis, providing scalability to 80 Gbps.Table 1 gives the capabilities of the four Cisco ASA 5585-X models.Table 1. Cisco ASA 5585-X Next-Generation Firewall Capabilities and CapacitiesEdge Edge Data center Data centerUnlimited Unlimited Unlimited Unlimited1 Maximum throughput with UDP traffic measured under ideal test conditions.2“Multiprotocol” refers to a traffic profile consisting primarily of TCP-based protocols and applications like HTTP, SMTP, FTP, IMAPv4, BitTorrent, and DNS.3 Available for the firewall feature set.4 VPN throughput and maximum peers depend on the ASA device configuration and VPN traffic patterns, including average packet size. These elements should be taken into consideration as part of your capacity planning. Throughput represents the maximum possible IPsec throughput. Maximum sessions may be further limited by your throughput requirements. AnyConnect licenses required. See the AnyConnect Ordering Guide for details. Maximum sessions may be further limited by your throughput requirements.5 AnyConnect licenses required. See the AnyConnect Ordering Guide for details. Maximum sessions may be further limited by your throughput requirements.6 Available for the firewall feature set.SafetyUL 60950-1, CAN/CSA-C22.2 No. 60950-1EN 60950-1, IEC 60950-1, AS/NZS 60950-1GB4943 UL 60950-1, CAN/CSA-C22.2 No. 60950-1EN 60950-1, IEC 60950-1, AS/NZS 60950-1GB4943 UL 60950-1, CAN/CSA-C22.2 No. 60950-1EN 60950-1, IEC 60950-1, AS/NZS 60950-1GB4943 UL 60950-1, CAN/CSA-C22.2 No. 60950-1EN 60950-1, IEC 60950-1, AS/NZS 60950-1GB4943 Electromagnetic compatibility (EMC)47CFR Part 15 (CFR 47) Class A, AS/NZS CISPR22 Class A, CISPR2 2 Class A, EN55022 Class A, ICES003 Class A, VCCI Class A EN61000-3-2, EN61000-3-3, KN22 Class A, CNS13438 Class A, EN50082-1, EN55024, CISPR24, EN300386, KN 61000-4 Series47CFR Part 15 (CFR 47) Class A, AS/NZS CISPR22 Class A, CISPR2 2 Class A, EN55022 Class A, ICES003 Class A, VCCI Class A EN61000-3-2, EN61000-3-3, KN22 Class A, CNS13438 Class A, EN50082-1, EN55024, CISPR24, EN300386, KN 61000-4 Series47CFR Part 15 (CFR 47) Class A, AS/NZS CISPR22 Class A, CISPR2 2 Class A, EN55022 Class A, ICES003 Class A, VCCI Class A EN61000-3-2, EN61000-3-3, KN22 Class A, CNS13438 Class A, EN50082-1, EN55024, CISPR24, EN300386, KN 61000-4 Series47CFR Part 15 (CFR 47) Class A, AS/NZS CISPR22 Class A, CISPR2 2 Class A, EN55022 Class A, ICES003 Class A, VCCI Class A EN61000-3-2, EN61000-3-3, KN22 Class A, CNS13438 Class A, EN50082-1, EN55024, CISPR24, EN300386, KN 61000-4 SeriesNote: Performance numbers were tested and validated with Cisco ASA Software Release 8.4.Cisco ASA 5585-X I/O ModulesMission-critical data centers running Cisco ASA Software Release 8.4.4 and later can use the top slot of the Cisco ASA 5585-X to add up to two Cisco ASA 5585-X I/O modules for exceptional flexibility and security. With two Cisco ASA 5585-X I/O modules, a single Cisco ASA 5585-X can support up to twenty 10 Gigabit Ethernet ports or up to fifty 1 Gigabit Ethernet ports. Using the Cisco ASA 5585-X Divider, the top slot is partitioned into two half-slots, with each I/O module occupying one half-slot. When only one I/O module is installed, a half-slot blank cover is required to cover the empty half-slot.Table 2 describes each of the Cisco ASA 5585-X I/O modules in more detail.Table 2.Cisco ASA 5585-X I/O ModulesTable 3 lists the 10 Gigabit Ethernet Enhanced Small Form-Factor Pluggable (SFP+) and 1 Gigabit Ethernet SFPs that are supported.Table 3. Supported SFP and SFP+ ModulesOptional DC Power SuppliesService providers and data centers that require data-center-powered equipment can purchase Cisco ASA 5585-X data center power supply modules with built-in fans. These power supplies deliver up to 1150 watts of data center power for Cisco ASA 5585-X Next-Generation Firewalls. Two data center power supplies are required for each Cisco ASA 5585-X chassis. The minimum software required is Cisco ASA Software Release 8.4.5.Warranty InformationFind warranty information on at the Product Warranties page.Ordering InformationHelp customers understand all the components or parts they need to purchase in order to install and use the product.To place an order, visit the Cisco How to Buy homepage.Table 4 lists part numbers for customer convenience. Table 4. Ordering InformationTo Download the SoftwareVisit the Cisco Software Center to download Cisco ASA Software.Service and SupportCisco services help you protect your network investment, improve network operations, and prepare your network for new applications to extend network intelligence and the power of your business.Included in the "Operate" phase of the service lifecycle are the Cisco Security IntelliShield® Alert Manager Service, Cisco SMARTnet™ services, the Cisco SP Base, and Cisco Services for IPS. These services are suitable for enterprise, commercial, and service provider customers.Cisco Security IntelliShield Alert Manager Service provides a customizable, web-based threat and vulnerability alert service that allows organizations to easily access timely, accurate, and credible information about potential vulnerabilities in their environment.Cisco Services for IPS supports modules, platforms, and bundles of platforms and modules that feature Cisco IPS capabilities. Cisco SMARTnet and Cisco SP Base support other products in this family.For More InformationFor more information, please visit the following links:●Cisco ASA 5500-X Series Next-Generation Firewalls:/en/US/products/ps6120/index.html●Cisco Cloud Web Security: /en/US/products/ps11720/index.html●Cisco TrustSec Solutions: /en/US/netsol/ns1051/index.html●Cisco AnyConnect: /go/anyconnect●Cisco AnyConnect Ordering Guide: /c/en/us/products/security/anyconnect-secure-mobility-client/sales-resources-listing.html●Cisco Security Manager: /en/US/products/ps6498/index.html●Cisco Adaptive Security Device Manager: /en/US/products/ps6121/index.html●Cisco Security Services: /en/US/products/svcs/ps2961/ps2952/serv_group_home.html。
cisco防火墙配置清单

配置防火墙拓扑图路由器UP配置(模拟内部网络)Router(config)# hostname UPUp(config)# ena secret ciscoUp(config)#line vty 0 4Up(config-line)#password ciscoUp(config-line)#loginUp(config)# int fa0/0Up(config-if)# ip address 192.168.1.1 255.255.255.0Up(config-if)# no shutUp(config-if) # exitUp(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.2路由器Down配置(模拟外部网络)Router(config)# hostname downdown(config)# ena secret ciscodown(config)#line vty 0 4down(config-line)#password ciscodown(config-line)#loginDown(config)# int fa0/1Down(config-if)# ip addr 200.200.200.2 255.255.255.0Down(config-if)# no shutDown(conifg-if)#exitDown(conifg)#ip route 0.0.0.0 0.0.0.0 200.200.200.1防火墙基本配置:PIXfirewall>enaPIXfirewall# conf t设置接口安全级别,跟接口命名PIXfirewall(config)# nameif ethernet0 inside security100 (系统已默认) PIXfirewall(config)#nameif ethernet1 outside security0 (系统已默认)设置接口工作方式PIXfirewall(config)# interface ethernet0 auto (系统已默认)PIXfirewall(config)# interface ethernet1 auto (系统已默认)设置接口IP地址:PIXfirewall(config)# ip address inside 192.168.1.2 255.255.255.0PIXfirewall(config)# ip address outside 200.200.200.1 255.255.255.0在防火墙上配置内部网络访问外部网络定义地址池1PIXfirewall(config)#global (outside) 1 200.200.200.3-200.200.200.10 netmask 255.255.255.0 配置inside口内部主机访问外网NATPIXfirewall(config)#nat (inside) 1 0 0配置到外网的路由PIXfirewall(config)# route outside 0.0.0.0 0.0.0.0 200.200.200.2前面的工作已完成从内部网络(在路由器UP上)访问外部网络的配置。
Cisco网络防火墙配置方法

Cisco⽹络防⽕墙配置⽅法由于⽹络防⽕墙默认禁⽌所有的通信,因为,只有对其进⾏适当配置后,才能实现正常的⽹络通信。
1.进⼊全局配置模式ciscoasa# configure terminal2.选择欲作为⽹络防⽕墙外部接⼝的⽹络接⼝ciscoasa(config)# interface interface-id3.为该接⼝指定IP地址和⽹掩码ciscoasa(config-if)#4.将该接⼝指定IP地址和⽹掩码ciscoasa(config-if)# nameif outsideINFO:Security level for "outside" set to 0 by default5.激活该外部接⼝ciscoasa(config-if)# no shutdown6.返回⾄全局配置模式ciscoasa(config-if)# exit7.选择欲作为⽹络防⽕墙内部接⼝的⽹络接⼝ciscoasa(config-if)# interface interface-id8.为了该接⼝指定为内部接⼝。
ciscoasa(config-if)# ip address ip-address subnet-mask9.将该接⼝指定为内容接⼝ciscoasa(config-if)# nameif insideINFO:Security level for "outside" set to 100 by default10.激活该外部接⼝ciscoasa(config-if)# no shutdown11.返回⾄全局配置模式ciscoasa(config-if)# exit12.启动Web VPNciscoasa(config)# webvpn13.允许VPN对外访问ciscoasa(config-webvpn)#enable outside14.指定SSL VPN客户端(SSL VPN Clinet,SVC)⽂件位置。
Cisco Firepower NGFW数据手册说明书

Data SheetCisco Firepower NGFWThe Cisco Firepower ® NGFW (next-generation firewall) is the industry’s first fully integrated, threat-focused next-gen firewall with unified management. It uniquely provides advanced threat protection before, during, and after attacks.Stop more threatsGain more insight Reduce complexityPerformance HighlightsTable 1 summarizes the performance highlights of the Cisco Firepower 4100 Series NGFW, 9300 Series Security Appliances, and select Cisco ASA 5500-X appliances.Table 1.Appliance Performance Highlights1 HTTP sessions with an average packet size of 1024 bytes 21024 bytes TCP firewall performanceNote: NGFW performance varies depending on network and traffic characteristics. Consult your Cisco representative for detailed sizing guidance. Performance is subject to change with new software releases.Cisco Firepower 2100 Series:The industry’s first midr ange NGFWs delivering sustainable performance when threat inspection is enabledCisco Firepower 4100 Series:The industry’s first 1RU NGFWs with 40-GbpsinterfacesCisco Firepower 9300:Ultra-high-performance NGFW, expandable as yourneeds growCisco ASA 5500-X Series:Models for branch offices, industrial applications, and the Internet edgeFirepower NGFWv:The NGFW for virtual and cloud environmentsPlatform Image SupportThe Cisco Firepower NGFW includes Application Visibility and Control (AVC), optional next-gen IPS (NGIPS), Cisco ® Advanced Malware Protection (AMP) for Networks, and URL Filtering. The Cisco Firepower 2100 Series, 4100 Series, and 9300 appliances use the Cisco Firepower Threat Defense software image. Alternatively, Cisco Firepower 4100 Series, and 9300 appliances can support the Cisco Adaptive Security Appliance (ASA) software image.Management OptionsCisco Firepower NGFWs may be managed in a variety of ways depending on the way you work, your environment, and your needs.The Cisco Firepower Management Center (formerly FireSIGHT) provides centralized management of the Cisco Firepower NGFW, the Cisco Firepower NGIPS, and Cisco AMP for Networks. It also provides threat correlation fornetwork sensors and Advanced Malware Protection (AMP) for Endpoints.The Cisco Firepower Device Manager is available for local management of 2100 Series and select 5500-X Series devices running the Cisco Firepower Threat Defense software image.The Cisco Adaptive Security Device Manager is available for local management of the Cisco Firepower 4100 Series, Cisco Firepower 9300 Series, and Cisco ASA 5500-X Series devices running the ASA software image.Cisco Defense Orchestrator cloud-based management is also available for consistent policy management across Cisco security devices running the ASA software image, enabling greater management efficiency for the distributed enterprise.Firepower DDoS MitigationAlso available on the Cisco Firepower 4100 Series and 9300 appliances is tightly integrated, comprehensive, behavioral DDoS mitigation for both network and application infrastructure protection. This DDoS mitigation is Radware’s Virtual DefensePro (vDP). It i s available from and supported directly by Cisco.Cisco Firepower 2100 Series AppliancesThe Cisco Firepower 2100 Series is a family of four threat-focused NGFW security platforms that deliver business resiliency through superior threat defense. It offers exceptional sustained performance when advanced threat functions are enabled. These platforms uniquely incorporate an innovative dual multicore CPU architecture that optimizes firewall, cryptographic, and threat inspection functions simultaneously. The ser ies’ firewall throughput ranges from 1.9 to 8.5 Gbps, addressing use cases from the Internet edge to the data center.Cisco Firepower 4100 Series AppliancesThe Cisco Firepower 4100 Series is a family of four threat-focused NGFW security platforms. Their throughput ranges from 35 to 75 Gbps, addressing data center use cases. They deliver superior threat defense, at faster speeds, with a smaller footprint.Cisco Firepower 9300 Security ApplianceThe Cisco Firepower 9300 is a scalable (beyond 1 Tbps when clustered), carrier-grade, modular platform designed for service providers, high-performance computing centers, large data centers, campuses, high-frequency trading environments, and other environments that require low (less than 5-microsecond offload) latency and exceptional throughput. Cisco Firepower 9300 supports flow-offloading, programmatic orchestration, and the management of security services with RESTful APIs. It is also available in Network Equipment Building Standards (NEBS)-compliant configurations.Cisco ASA 5500-FTD-X Series AppliancesThe Cisco ASA 5500-FTD-X Series is a family of eight threat-focused NGFW security platforms. Their throughput ranges from 750 Mbps to 4 Gbps, addressing use cases from the small or branch office to the Internet edge. They deliver superior threat defense in a cost-effective footprint.Cisco Firepower NGFW Virtual (NGFWv) AppliancesCisco Firepower NGFWv is available on VMware, KVM, and the Amazon Web Services (AWS) and Microsoft Azure environments for virtual, public, private, and hybrid cloud environments. Organizations employing SDN can rapidly provision and orchestrate flexible network protection with Firepower NGFWv. As well, organizations using NFV can further lower costs utilizing Firepower NGFWv.Performance Specifications and Feature HighlightsTable 2 summarizes the capabilities of the Cisco Firepower NGFWv, Firepower 2100 Series, and 4100 Series and 9300 appliances as well as the Cisco ASA 5500-FTD-X appliances when running the Cisco Firepower Threat Defense image.Table 2.Performance Specifications and Feature Highlights for Physical and Virtual Appliances with the Cisco Firepower Threat Defense Image211021202130214041104120414041509300 1 249300 1 369300 1 4493003 4455065506550655085516552555455555 Throughput: FW + AVC 1.2 Gbps 2.0 Gbps 3 Gbps 4.75 Gbps 8.5 Gbps 12 Gbps 20 Gbps 25 Gbps 30 Gbps 30 Gbps 42 Gbps 54 Gbps 135 Gbps 250 Mbps 250 Mbps 250 Mbps 450 Mbps 850 Mbps 1100 Mbps 1500 Mbps 1750 Mbps Throughput: AVC + IPS 1.1 Gbps 2.0 Gbps 3 Gbps 4.75 Gbps 8.5 Gbps 10 Gbps 15 Gbps 20 Gbps 24 Gbps 24 Gbps 34 Gbps 53 Gbps 133 Gbps 125 Mbps 125 Mbps 125 Mbps 250 Mbps 450 Mbps 650 Mbps 1000 Mbps 1250 Mbps Maximum concurrent sessions, with AVC 100,0001 millio n1.2 million2 millio n3.0 millio n9 millio n15 millio n25 millio n30 millio n30 millio n30 millio n30 millio n60 millio n20,00020,00020,000100,000250,000500,000750,0001,000,000Maximum new connections per second, with AVC 10,00012,00016,000 24,00040,00068,000120,000160,000200,000120,000160,000300,000900,0003,000 3,000 3,000 7,000 8,000 10,00015,00020,000IPSec VPN Throughput (1024B TCP w/Fastpath) - 750 Mbps1000 Mbps1500 Mbp s3000 Mbps- - - - - - - - - - - - - - -- Maximum VPN Peers - 1500 3500 7500 10000- - - - - - - - - - - - - - --Cisco Firepower Device Manager (local managemen t)Yes (VMw are only)Yes Yes Yes Yes - - - - - - - - Yes Yes Yes Yes Yes Yes Yes YesCentralized managemen tCentralized configuration, logging, monitoring, and reporting are performed by the Management Center or alternatively in the cloud with Cisco Defense OrchestratorApplication Visibility and Control (AVC) Standard, supporting more than 4000 applications, as well as geolocations, users, and websitesAVC: OpenAppID support for custom, open source, application detectors StandardCisco Security Intelligence Standard, with IP, URL, and DNS threat intelligenceCisco Firepower NGIPS Available; can passively detect endpoints and infrastructure for threat correlation and indicators of compromise (IoC) intelligenceCisco AMPAvailable; enables detection, blocking, tracking, analysis, and containment of targeted and persistent malware, addressing the attack continuum both during and after attacks. IntegratedNote: Throughput assumes HTTP sessions with an average packet size of 1024 bytes.Performance will vary depending on features activated, and network traffic protocol mix, packet size characteristics and hypervisor employed (NGFWv). Performance is subject to change with new software releases. Consult your Cisco representative for detailed sizing guidance.Table 3 summarizes the performance and capabilities of the Cisco Firepower 4100 Series and 9300 appliances when running the ASA image. For Cisco ASA 5500-X Series performance specifications with the ASA image, please visit the Cisco ASA with FirePOWER Services data sheet.Table 3. ASA Performance and Capabilities on Firepower Appliances1 Throughput measured with User Datagram Protocol (UDP) traffic measured under ideal test conditions.2“Multiprotocol” refers to a traffic profile consisting primarily of TCP-based protocols and applications like HTTP, SMTP, FTP, IMAPv4, BitTorrent, and DNS.3 Available for the firewall feature set.4 In unclustered configuration.Table 4. Operating Requirements for Firepower NGFWv Virtual AppliancesHardware SpecificationsTables 5, 6, and 7 summarize the hardware specifications for the 2100 Series, 4100 Series, and 9300 Series, respectively. Table 8 summarizes regulatory standards compliance. For Cisco ASA 5500-X Series hardware specifications, please visit the Cisco ASA with FirePOWER Services data sheet.Table 5. Cisco Firepower 2100 Series Hardware Specifications1 Dual power supplies are hot-swappable.2 Fans operate in a 3+1 redundant configuration where the system will continue to function with only3 operational fans. The 3 remaining fans will run at full speed.3 FPR-2130 platform is designed to be NEBS ready. The availability of NEBS certification is pending.Table 6. Cisco Firepower 4100 Series Hardware Specifications1 Dual power supplies are hot-swappable.2 DC power option is expected on Cisco Firepower 4110 and 4120 in the second half of 2016.Table 7. Cisco Firepower 9300 Hardware Specifications* Minimum turn-on voltage is -44V DCTable 8. Cisco Firepower 4100 Series and Cisco Firepower 9300 NEBS, Regulatory, Safety, and EMC ComplianceCisco Trust Anchor TechnologiesCisco Trust Anchor Technologies provide a highly secure foundation for certain Cisco products. They enable hardware and software authenticity assurance for supply chain trust and strong mitigation against a man-in-the-middle compromise of software and firmware.Trust Anchor capabilities include:●Image signing: Cryptographically signed images provide assurance that the firmware, BIOS, and othersoftware are authentic and unmodified. As the system boots, the system’s software signatures are checked for integrity.●Secure Boot: Secure Boot anchors the boot sequence chain of trust to immutable hardware, mitigatingthreats against a system’s foundational state and the software that is to be loaded, regardless of a user’s privilege level. It provides layered protection against the persistence of illicitly modified firmware.●Trust Anchor module: A tamper-resistant, strong-cryptographic, single-chip solution provides hardwareauthenticity assurance to uniquely identify the product so that its origin can be confirmed to Cisco, providing assurance that the product is genuine.Firepower DDoS MitigationFirepower DDoS Mitigation is provided by Radware Virtual DefensePro (vDP), available and supported directly from Cisco on the following Cisco Firepower 9300 and 4100 series appliances:Radware vDP is an award-winning, real-time, behavioral DDoS attack mitigation solution that protects organizations against multiple DDoS threats. Firepower DDoS mitigation defends your application infrastructure against network and application degredation and outage.DDoS Mitigation: Protection SetFirepower’s vDP DDoS mitigation consists of patent-protected, adaptive, behavioral-based real-time signature technology that detects and mitigates zero-day network and application DDoS attacks in real time. It eliminates the need for human intervention and does not block legitimate user traffic when under attack.The following attacks are detected and mitigated:●SYN flood attacks●Network DDoS attacks, including IP floods, ICMP floods, TCP floods, UDP floods, and IGMP floods●Application DDoS attacks, including HTTP floods and DNS query floods●Anomalous flood attacks, such as nonstandard and malformed packet attacksPerformanceThe performance figures in Table 9 apply to all Cisco Firepower 4100 series models.Table 9. Key DDoS Performance Metrics for Cisco Firepower 4100 SeriesThe performance figures in Table 10 are for Cisco Firepower 9300 with 1 to 3 Security Modules irrespective of Security Module type (SM-24, SM-36 or SM-44).Table 10. Key DDoS Performance Metrics for Cisco Firepower 9300 with 1, 2, or 3 Security Modules.Ordering InformationCisco Smart LicensingThe Cisco Firepower NGFW is sold with Cisco Smart Licensing. Cisco understands that purchasing, deploying, managing, and tracking software licenses is complex. As a result, we are introducing Cisco Smart Software Licensing, a standardized licensing platform that helps customers understand how Cisco software is used across their network, thereby reducing administrative overhead and operating expenses.With Smart Licensing, you have a complete view of software, licenses, and devices from one portal. Licenses are easily registered and activated and can be shifted between like hardware platforms. Additional information is available here: /web/ordering/smart-software-licensing/index.html. Related information, on Smart Licensing Smart Accounts, is available here: /web/ordering/smart-software-manager/smart-accounts.html.Cisco Smart Net Total Care Support: Move Quickly with Anytime Access to Cisco Expertise and ResourcesCisco Smart Net Total Care™ is an award-winning technical support service that gives your IT staff direct anytime access to Technical Assistance Center (TAC) engineers and resources. You receive the fast, expert response and the dedicated accountability you require to resolve critical network issues.Smart Net Total Care provides the following device-level support:●Global access 24 hours a day, 365 days a year to specialized engineers in the Cisco TAC●Anytime access to the extensive online knowledge base, resources, and tools●Hardware replacement options include 2-hour, 4-hour, next-business-day (NDB) advance replacement, aswell as return for repair (RFR)●Ongoing operating system software updates, including both minor and major releases within your licensedfeature set●Proactive diagnostics and real-time alerts on select devices with Smart Call HomeIn addition, with the optional Cisco Smart Net Total Care Onsite Service, a field engineer installs replacement parts at your location and helps ensure that your network operates optimally. For more information on Smart Net Total Care please visit: /c/en/us/services/portfolio/product-technical-support/smart-net-total-care.html.Select Part NumbersTables 11, 12, and 13 provide details on part numbers for Cisco Firepower NGFW solutions. Please consult the Ordering Guide for additional configuration options and accessories.Table 11. Cisco Firepower 2100 Series: Select Product ComponentsTable 12. Cisco Firepower 4100 Series: Select Product ComponentsTable 13. Cisco Firepower 9300: Select Product Components*Note: Firepower 9300 may also be deployed as a dedicated threat sensor, with fail-to-wire network modules. Please contact your Cisco representative for details.Warranty InformationFind warranty information on at the Product Warranties page.Cisco ServicesCisco offers a wide range of service programs to accelerate customer success. These innovative services programs are delivered through a unique combination of people, processes, tools, and partners, resulting in high levels of customer satisfaction. Cisco Services help you protect your network investment, optimize network operations, and prepare your network for new applications to extend network intelligence and the power of your business. For more information about Cisco services for security, visit /go/services/security.Cisco CapitalFinancing to Help You Achieve Your ObjectivesCisco Capital® financing can help you acquire the technology you need to achieve your objectives and stay competitive. We can help you reduce CapEx. Accelerate your growth. Optimize your investment dollars and ROI. Cisco Capital financing gives you flexibility in acquiring hardware, software, services, and complementary third-party equipment. And there’s just one predictable payment. Cisco Capital is available in more than 100 countries. Learn more.More Information for Service ProvidersFor information about Cisco Firepower in service provider environments, please visit:●/c/en/us/solutions/enterprise-networks/service-provider-security-solutions/More Information about Firepower NGFWsFor further information about Cisco Firepower NGFWs, please visit:●/go/ngfwMore Information about Cisco AnyConnect●Cisco AnyConnect Secure Mobility Client/go/anyconnect●Cisco AnyConnect Ordering Guide/c/dam/en/us/products/security/anyconnect-og.pdf。
cisco-asa 防火墙 配置

cisco-asa 防火墙配置hostname CD-ASA5520 //给防火墙命名domain-namedefault.domain.invalid //定义工作域enable password 9jNfZuG3TC5tCVH0 encrypted // 进入特权模式的密码names dns-guard!interface GigabitEthernet0/0 //内网接口:duplex full //接口作工模式:全双工,半双,自适应nameif inside //为端口命名:内部接口inside security-level 100 //设置安全级别 0~100 值越大越安全ip address192.168.1.1 255.255.255.0 //设置本端口的IP地址!interface GigabitEthernet0/1 //外网接口nameif outside //为外部端口命名:外部接口outside security-level 0 ip address 202.98.131.122 255.255.255.0 //IP地址配置!interface GigabitEthernet0/2 nameif dmz security-level 50 ip address 192.168.2.1 255.255.255.0!interface GigabitEthernet0/3 shutdown no nameif no security-level no ip address!interface Management0/0 //防火墙管理地址shutdown no nameif no security-level no ip address!passwd 2KFQnbNIdI.2KYOU encrypted ftp mode passive clock timezone CST 8 dns server-group DefaultDNS domain-name default.domain.invalid access-list outside_permit extended permit tcp any interface outside eq 3389 //访问控制列表access-list outside_permit extended permit tcp any interface outside range 30000 30010 //允许外部任何用户可以访问outside 接口的30000-30010的端口。
深信服防火墙 手册

深信服防火墙手册深信服防火墙是一种高性能、多业务安全的网络安全设备,适用于各种网络环境,如企业、政府、教育、医疗等行业。
以下是深信服防火墙的使用手册:1. 设备安装与配置:设备连接:将深信服防火墙连接到电源和网络接口,确保网络连接正常。
配置IP地址:在浏览器中输入设备的IP地址,登录防火墙的管理界面,设置防火墙的IP地址、子网掩码和网关等网络参数。
2. 登录管理界面:在浏览器中输入设备的IP地址,然后输入用户名和密码(默认为admin)登录防火墙的管理界面。
3. 防火墙网关部署:新建区域:在管理界面中新建区域,选择相应的接口,如WAN区域和LAN区域。
配置网络接口:为每个区域配置相应的网络接口,如eth1和eth2。
4. 配置默认路由和去往内网的回包路由:根据实际网络环境,配置默认路由和去往内网的回包路由。
5. 配置源地址转换:代理内网用户上网,将内网用户的源地址转换为出接口的IP地址。
6. 防火墙默认拒绝所有:设置防火墙的默认策略为拒绝所有请求,以增强安全性。
7. 应用控制策略放通:根据实际需求,配置应用控制策略,允许或拒绝特定的应用程序或协议通过防火墙。
8. 配置僵尸网络防护:为了保护内网PC免受僵尸网络的攻击,可以配置相应的僵尸网络防护功能。
9. 配置IPS防护内网客户端:根据实际需求,配置入侵防御系统(IPS),保护内网客户端免受攻击。
10. 配置流量管控:对内网PC的带宽进行限制,以避免因个别用户占用过多带宽而影响整个网络的性能。
以上是深信服防火墙的使用手册,具体配置可能因实际网络环境和需求而有所不同。
建议参考深信服防火墙的官方文档或联系专业技术人员进行配置和优化。
cisco ASA防火墙开局配置指南

一,配置接口配置外网口:interface GigabitEthernet0/0nameif outside 定义接口名字security-level 0ip address 111.160.45.147 255.255.255.240 设定ipnoshut!配置内网口:interface GigabitEthernet0/1nameif insidesecurity-level 100ip address 20.0.0.2 255.255.255.252noshut二,配置安全策略access-list outside_acl extended permit icmp any any配置允许外网pingaccess-group outside_acl in interface outside 应用策略到outside口access-list inside_access_in extended permit ip any any配置允许内网访问外网access-group inside_access_in in interface inside应用到inside口三,设置路由route outside 0.0.0.0 0.0.0.0 111.160.45.145 1配置到出口的默认路由route inside 10.1.0.0 255.255.0.0 20.0.0.1 1 配置到内网的静态路由四,配置natobject network nat_net配置需要nat的内网网段subnet 0.0.0.0 0.0.0.0nat (inside,outside) source dynamic nat_net interface配置使用出接口ip做转换ip 五,配置远程管理配置telet管理:telnet 0.0.0.0 0.0.0.0 outsidetelnet 0.0.0.0 0.0.0.0 insidetelnet timeout 30配置ssh管理:crypto key generate rsa建立密钥并保存一次wrissh 0.0.0.0 0.0.0.0 outsidessh 0.0.0.0 0.0.0.0 insidessh timeout 30ssh version 1配置用户名密码:username admin password yfz4EIInjghXNlcu encrypted privilege 15。
Cisco ASA5500 配置手册

Cisco ASA5500系列防火墙基本配置手册一、配置基础1.1用户接口思科防火墙支持下列用户配置方式:Console,Telnet,SSH(1.x或者2.0,2.0为7.x新特性),ASDM的http方式,VMS的Firewall Management Center。
支持进入Rom Monitor模式,权限分为用户模式和特权模式,支持Help,History和命令输出的搜索和过滤。
用户模式:Firewall> 为用户模式,输入enable进入特权模式Firewall#。
特权模式下输入config t 可以进入全局配置模式。
通过exit,ctrl-z退回上级模式。
配置特性:在原有命令前加no可以取消该命令。
Show running-config 或者 write terminal显示当前配置。
Show running-config all显示所有配置,包含缺省配置。
Tab可以用于命令补全,ctrl-l可以用于重新显示输入的命令(适用于还没有输入完命令被系统输出打乱的情况),help和history相同于IOS命令集。
Show命令支持 begin,include,exclude,grep 加正则表达式的方式对输出进行过滤和搜索。
Terminal width 命令用于修改终端屏幕显示宽度,缺省为80个字符,pager命令用于修改终端显示屏幕显示行数,缺省为24行。
1.2初始配置跟路由器一样可以使用setup进行对话式的基本配置。
二、配置连接性2.1配置接口接口基础:防火墙的接口都必须配置接口名称,接口IP地址和掩码和安全等级。
接口基本配置:Firewall(config)# interface hardware-id 进入接口模式Firewall(config-if)# speed {auto | 10 | 100 | nonegotiate} 设置接口速率Firewall(config-if)# duplex {auto | full | half} 接口工作模式Firewall(config-if)# [no] shutdown 激活或关闭接口Firewall(config-if)# nameif if_name 配置接口名称Firewall(config-if)# security-level level 定义接口的安全级别例:interface GigabitEthernet0/0nameif outsidesecurity-level 0ip address 125.78.33.22 255.255.255.248!interface GigabitEthernet0/1nameif insidesecurity-level 100ip address 192.168.18.254 255.255.255.0在配置中,接口被命名为外部接口(outside),安全级别是0;被命名为内部接口(inside),安全级别是100.安全级别取值范围为1~99,数字越大安全级别越高。
cisco pix防火墙基本配置命令使用手册

cisco pix防火墙基本配置命令使用任何企业安全策略的一个主要部分都是实现和维护防火墙,因此防火墙在网络安全的实现当中扮演着重要的角色。
防火墙通常位于企业网络的边缘,这使得内部网络与internet之间或者与其他外部网络互相隔离,并限制网络互访从而保护企业内部网络。
设置防火墙目的都是为了在内部网与外部网之间设立唯一的通道,简化网络的安全管理。
在众多的企业级主流防火墙中,cisco pix防火墙是所有同类产品性能最好的一种。
cisco pix 系列防火墙目前有5种型号pix506,515,520,525,535。
其中pix535是pix 500系列中最新,功能也是最强大的一款。
它可以提供运营商级别的处理能力,适用于大型的isp等服务提供商。
但是pix特有的os操作系统,使得大多数管理是通过命令行来实现的,不象其他同类的防火墙通过web管理界面来进行网络管理,这样会给初学者带来不便。
本文将通过实例介绍如何配置cisco pix防火墙。
在配置pix防火墙之前,先来介绍一下防火墙的物理特性。
防火墙通常具有至少3个接口,但许多早期的防火墙只具有2个接口;当使用具有3个接口的防火墙时,就至少产生了3个网络,描述如下:ø内部区域(内网)。
内部区域通常就是指企业内部网络或者是企业内部网络的一部分。
它是互连网络的信任区域,即受到了防火墙的保护。
ø外部区域(外网)。
外部区域通常指internet或者非企业内部网络。
它是互连网络中不被信任的区域,当外部区域想要访问内部区域的主机和服务,通过防火墙,就可以实现有限制的访问。
ø停火区(dmz)。
停火区是一个隔离的网络,或几个网络。
位于停火区中的主机或服务器被称为堡垒主机。
一般在停火区内可以放置web服务器,mail服务器等。
停火区对于外部用户通常是可以访问的,这种方式让外部用户可以访问企业的公开信息,但却不允许他们访问企业内部网络。
注意:2个接口的防火墙是没有停火区的。
cisco ASA5200防火墙详细配置手册

: Saved
:
ASA Version 8.2(5)
!
hostname ASA5520
enable password mXBgE0BelDHjYBDU encrypted
passwd mXBgE0BelDHjYBDU encrypted
access-list vpnclient_splitTunnelAcl standard permit 172.20.1.0 255.255.255.0
access-list ipsec-vpn extended permit ip 172.20.1.0 255.255.255.0 10.144.196.0 255.255.255.0
ssh timeout 30
ssh version 1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
crypto map outside_map 10 match address ipsec-vpn
crypto map outside_map 10 set peer 202.4.201.252
crypto map outside_map 10 set transform-set myset
crypto dynamic-map outside-dyn-map 10 set transform-set vpnset
crypto dynamic-map outside-dyn-map 10 set security-association lifetime seconds 288000
CISCOASA5520配置手册

CISCOASA5520配置手册CISCO ASA5520配置手册CD-ASA5520# show run: Saved:ASA V ersion 7.2(2)!hostname CD-ASA5520 //给防火墙命名domain-name default.domain.invalid //定义工作域enable password 9jNfZuG3TC5tCVH0 encrypted // 进入特权模式的密码Namesdns-guard!interface GigabitEthernet0/0 //内网接口:duplex full //接口作工模式:全双工,半双,自适应nameif inside //为端口命名:内部接口insidesecurity-level 100 //设置安全级别0~100 值越大越安全ip address 192.168.1.1 255.255.255.0 //设置本端口的IP地址!interface GigabitEthernet0/1 //外网接口nameif outside //为外部端口命名:外部接口outsidesecurity-level 0ip address 202.98.131.122 255.255.255.0 //IP地址配置!interface GigabitEthernet0/2nameif dmzsecurity-level 50ip address 192.168.2.1 255.255.255.0!interface GigabitEthernet0/3Shutdownno nameifno security-levelno ip address!interface Management0/0 //防火墙管理地址shutdownno nameifno security-levelno ip address!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passiveclock timezone CST 8dns server-group DefaultDNSdomain-name default.domain.invalidaccess-list outside_permit extended permit tcp any interface outside eq 3389//访问控制列表access-list outside_permit extended permit tcp any interface outside range 30000 30010//允许外部任何用户可以访问outside 接口的30000-30010的端口。
Cisco-ASA-5500防火墙个人基本配置手册-去水印
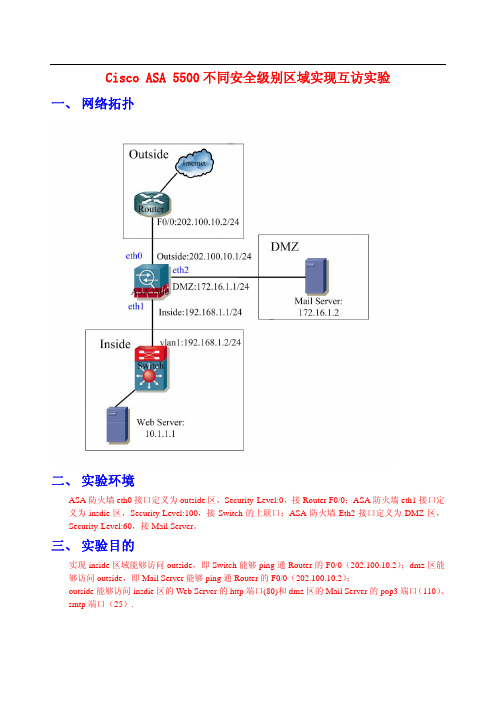
Cisco ASA 5500不同安全级别区域实现互访实验一、 网络拓扑二、 实验环境ASA防火墙eth0接口定义为outside区,Security-Level:0,接Router F0/0;ASA防火墙eth1接口定义为insdie区,Security-Level:100,接Switch的上联口;ASA防火墙Eth2接口定义为DMZ区,Security-Level:60,接Mail Server。
三、 实验目的实现inside区域能够访问outside,即Switch能够ping通Router的F0/0(202.100.10.2);dmz区能够访问outside,即Mail Server能够ping通Router的F0/0(202.100.10.2);outside能够访问insdie区的Web Server的http端口(80)和dmz区的Mail Server的pop3端口(110)、smtp端口(25).四、 详细配置步骤1、端口配置CiscoASA(config)# interface ethernet 0CiscoASA(config)#nameif ousideCiscoASA(config-if)# security-level 0CiscoASA(config-if)# ip address 202.100.10.1 255.255.255.0CiscoASA(config-if)# no shutCiscoASA(config)# interface ethernet 1CiscoASA(config)#nameif insideCiscoASA(config-if)# security-level 100CiscoASA(config-if)# ip address 192.168.1.1 255.255.255.0CiscoASA(config-if)# no shutCiscoASA(config)# interface ethernet 2CiscoASA(config)#nameif dmzCiscoASA(config-if)# security-level 50CiscoASA(config-if)# ip address 172.16.1.1 255.255.255.0CiscoASA(config-if)# no shut2、路由配置CiscoASA(config)# route outside 0.0.0.0 0.0.0.0 202.100.10.2 1 #默认路由CiscoASA(config)# route inside 10.0.0.0 255.0.0.0 192.168.1.2 1 #外网访问内网服务器的路由3、定义高安全接口区域需要进行地址转换的IP范围CiscoASA(config)# nat (inside) 1 0 0CiscoASA(config)# nat (dmz) 1 0 04、定义低安全接口区域用于高安全接口区域进行IP转换的地址范围CiscoASA(config)# global (outside) 1 interfaceCiscoASA(config)# global (dmz) 1 interface5、定义静态IP映射(也称一对一映射)CiscoASA(config)# static (inside,outside) tcp 202.100.10.1 www 10.1.1.1 www netmask 255.255.255.255#实现从outside区访问inside区10.1.1.1的80端口时,就直接访问10.1.1.1:80 对outside区的映射202.100.10.1:80CiscoASA(config)# static (dmz,outside) tcp 202.100.10.1 pop3 172.16.1.2 pop3 netmask 255.255.255.255#实现从outside区访问dmz区172.16.1.2的110时,就直接访问172.16.1.2:110 对outside区的映射202.100.10.1:110CiscoASA(config)# static (dmz,outside) tcp 202.100.10.1 smtp 172.16.1.2 smtp netmask 255.255.255.255#实现从outside区访问dmz区172.16.1.2的25时,就直接访问172.16.1.2:25 对outside区的映射202.100.10.1:256、定义access-listCiscoASA(config)# access-list 101 extended permit ip any anyCiscoASA(config)# access-list 101 extended permit icmp any anyCiscoASA(config)# access-list 102 extended permit tcp any host 10.1.1.1 eq wwwCiscoASA(config)# access-list 102 extended permit icmp any anyCiscoASA(config)# access-list 103 extended permit tcp any host 172.16.1.2 eq pop3CiscoASA(config)# access-list 103 extended permit tcp any host 172.16.1.2 eq smtp7、在接口上应用access-listCiscoASA(config)# access-group 101 in interface outsideCiscoASA(config)#access-group 102 in interface insideCiscoASA(config)#access-group 103 in interface dmz五、 实验总结1、当流量从高权限区域流向低权限区域时1、只要路由配通了,无须配置nat/global,也无须配置access-list,就可以直接telnet低权限区域主机;2、只要路由配通了,同时配置了access-list,无须配置nat/global,就可以直接ping通低权限区域主机;3、只要路由配通了,同时配置了nat/global/access-list,此时telnet/ping均会执行地址转换2、当流量从低权限区域流向高权限区域时1、即使路由已经配通了,也不能成功访问;2、路由已经配通了,同时必须正确配置了static IP地址映射及access-list,才能成功访问;3、调通路由是基础,同时只跟static/access-list有关,而跟nat/global毫无关系。
思科ASA 5510防火墙实战配置中文手册

配置设备介绍:(只为做实验实际应用请根据自己具体情况更改相关参数即可)核心交换机4507 提供VLAN3 网关地址:192。
168.3.254 提供DNS 服务器连接:192。
168。
0.1 接入交换机2960 提供VLAN3 TURNK 连接,可用IP 地址为192.168.3.0-192.168。
3。
240 掩码:255.255。
255。
0 网关:192。
168.3。
254DNS:192.168。
0。
1 内网实验防火墙CISCO ASA 5510E0/0 IP:192。
168.3.234E0/1 IP 10。
1.1.1 实现配置策略1。
动态内部PC1 DHCP 自动获得IP 地址,可访问INTERNET,并PING 通外部网关.PC1 Ethernet adapter 本地连接:Connection-specific DNS Suffix . : gametuziDescription 。
. 。
. . 。
:Broadcom 440x rollerPhysical Address。
. . . 。
. :00-13-77—04-9Dhcp Enabled. 。
. . 。
. : YesAutoconfiguration Enabled 。
. 。
. :YesIP Address。
. . 。
. 。
. 。
. . :10。
1.1。
20Subnet Mask . . . . . . . 。
. 。
:255.255。
0.0Default Gateway 。
. 。
. :10.1.1。
1DHCP Server . . . . 。
. . 。
. . :10.1.1.1DNS Servers 。
. . 。
. 。
. : 192。
168。
0.12. 静态内部PC2 手动分配地址,可访问INTERNET ,并PING 通外部网关。
PC1 Ethernet adapter 本地连接:Connection—specific DNS Suffix . : gametuziDescription . 。
思科防火墙基本配置指导

思科防火墙基本配置指导下面我讲一下一般用到的最基本配置1、建立用户和修改密码跟Cisco IOS路由器基本一样。
2、激活以太端口必须用enable进入,然后进入configure模式PIX525>enablePassword:PIX525#config tPIX525(config)#interface ethernet0 autoPIX525(config)#interface ethernet1 auto在默然情况下ethernet0是属外部网卡outside, ethernet1是属内部网卡inside, inside在初始化配置成功的情况下已经被激活生效了,但是outside必须命令配置激活。
3、命名端口与安全级别采用命令nameifPIX525(config)#nameif ethernet0 outside security0PIX525(config)#nameif ethernet0 outside security100security0是外部端口outside的安全级别(0安全级别最高)security100是内部端口inside的安全级别,如果中间还有以太口,则security10,security20等等命名,多个网卡组成多个网络,一般情况下增加一个以太口作为DMZ(Demilitarized Zones非武装区域)。
4、配置以太端口IP 地址采用命令为:ip address如:内部网络为:192.168.1.0 255.255.255.0外部网络为:222.20.16.0 255.255.255.0PIX525(config)#ip address inside 192.168.1.1 255.255.255.0PIX525(config)#ip address outside 222.20.16.1 255.255.255.05、配置远程访问[telnet]在默然情况下,PIX的以太端口是不允许telnet的,这一点与路由器有区别。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Pix系列产品默认只有两个端口及0和1,DMZ端口都是另外添加的模块,DMZ端口的默认安全级别50,配置DMZ接口的地址和配置inside和outside类似
配置外接口地址
Pix(config)#ip address inside 1.1.1.1 255.255.255.0
配置内接口地址
Pix(config)#interface ethernet0 auto
激活外端口
Pix(config)#interface ethernet1 auto
激活内端口 (默认端口是出于shutdown状态的)
Pix(config)#ip address dmz 3.3.3.3 255.255.255.0
Pix(config)# interface gb-ethernet0 1000auto 激活DMZ端口,DMZ的端口号需要您用show
running-config命令查看,如:
Pix(config)#show running-config
防火墙的nat和global是同时工作的,nat定义了我们要进行转换的地址,而global定义了要被转换为的地址,这些配置都要在全局配置模式下完成,
2.2、Nat配置如下:
Pix(config)#nat (inside) 1 0 0
上面inside代表是要被转换得地址,
1要和global 后面的号对应,类似于访问控制列表号,也是从上往下执行,
Firewall(config)#access-group outside in interface outside
必须将用access-group命令将访问控制列表应用到外端口,上述完成后就可以从外网上来访问服务器了。
5、防火墙上常用的show命令
Firewall (config) #show interface 查看所有端口的状态,端口是否出于连接状态
查看防火墙的当前配置文件 来自二、防火墙配置简介 1、以前的防火墙的系统版本是6.3以下,在这种版本里面不能用“tab”键补齐命令,而且用“?”来查询命令也很不方便;
目前的ASA5500的系统版本为7.0以上,和路由器的命令相同,可以用“tab”键补齐命令,可以用“?”来查看参数、同样也可以在全局模式用show命令。
firewall(config)#telnet 192.168.10.0 255.255.255.0 inside 允许内网此网断内的机器Telnet到防火墙
配置从外网远程登陆到防火墙
Firewall(config)#domain-name
firewall(config)# crypto key generate rsa
CPU utilization for 5 seconds = 1%; 1 minute: 1%; 5 minutes: 1%
如果内部有终端中毒(或利用P2P下载)向网关送大量的数据包,会导致防火墙只能来处理病毒机器的请求,而无暇顾及正常流量,导致正常用户不能上网,要找到不正常终端可以利用show conn来查看
上述命令便将内部的web服务器放到了公网上面,但外面的用户并不能访问到,因为防火墙的外界口安全级别最低,从低安全级别到高安全级别主动发起的链接请求需要我们在防火墙上利用访问控制列表手动放开,如下:
Firewall(config)#access-list outside permit tcp any host 222.128.124.1 eq 80
一、Cisco Pix日常维护常用命令
1、Pix模式介绍
“>”用户模式
firewall>enable
由用户模式进入到特权模式
password:
“#”特权模式
firewall#config t
由特权模式进入全局配置模式
“(config)#”全局配置模式
firewall(config)#
firewall(config)# interface ethernet0 100full
激活外端口
firewall(config)# interface gb-ethernet0 1000auto
激活内端口
2、telnet、ssh、web登陆配置及密码配置
防火墙默认是不允许内/外网用户通过远程登陆或WEB访问的,需要相应得开启功能。
Fierwall(config)#clear arp
清除ARP表
Firewall(config)#clear xlate
清除内部所有地址的转换项,网络中断一下
Firewall(config)#clear xlate local 192.168.40.69
清除内部具体一台机器的转换项
Firewall(config)#show runnint-config
firewall(config)#hostname firewall
设备名称
firewall(config)#ip address outside 1.1.1.1 255.255.255.0
内外口地址设置
firewall(config)#ip address inside 172.16.1.1 255.255.255.0
t
全局配置模式:当您看到(config)#时,表示现在处于全局配置模式,可以对防火墙的设置进行修改。
在“>”、“#”、“(config)#”左侧显示的为设备的名称。
2、
1)、防火墙接口配置
Pix配置
Pix>enable
进入特权模式
Pix#config
t
进入全局配置模式
Pix(config)#ip address outside 222.128.1.1 255.255.255.0
由用户模式进入特权模式的口令
firewall(config)#passrd cisco
ssh远程登陆时用的口令
firewall(config)#username Cisco password Cisco
Web登陆时用到的用户名
firewall(config)#http enable
打开http允许内网10网断通过http访问防火墙
interface ethernet0 "outside" is up, line protocol is up 端口和协议都出于“up”状态,正常。
pixfirewall# sh cpu usage
查看CPU的使用情况,如果CPU的使用情况超过60%是不正常的,说明内部有PC对外占用了设备大量资源
做完上面的配置内网用户就可以上网了,内部有3层交换机且划分了Vlan,若要保证每个Vlan都能够上网,还要在防火墙上指回到其他VLan的路由,如:
Firewall (config) # route inside 192.168.20.0 255.255.255.0 172.16.1.2
4、内网服务器映射
firewall(config)#ssh 0.0.0.0 0.0.0.0 outside
允许外网所有地址可以远程登录防火墙,也可以定义一格具体的地址可以从外网登陆到防火墙上,如:
firewall(config)#ssh 218.240.6.81 255.255.255.255 outside
firewall(config)#enable password cisco
防火墙的几种工作模式:
用户模式:如果您看到>那么现在代表是在用户模式下,在用户模式下只有简单的命令可以操作。由用户模式进入特权模式的命令为:enable
特权模式:如果您看到当前的位置显示#那么您处于特权模式下,在特权模式下用户可以查看所有信息,而前可以进入全局配置模式对防火墙配置进行修改。由特权模式进入全局配置模式下的命令为:config
sh run
: Saved
:
PIX Version 6.3(5)
interface ethernet0 100full
interface ethernet1 auto
interface gb-ethernet0 1000auto
新添加的DMZ端口
2)、防火墙nat设置
2.1、内网用户要上网,我们必须对其进行地址转换,将其转换为在公网上可以路由的注册地址,
fierwall(config)#nat (inside) 1 192.168.20.0 255.255.255.0
firewall (config) # global
(outside) 1 interface
对进行nat转换得地址转换为防火墙外接口地址
firewall (config) # route 0.0.0.0 0.0.0.0 1.1.1.2 指一条默认路由器到ISP
Firewall(config)#show conn local 192.168.40.69
查看具体一个IP地址的链接项:
Firewall(config)#show version 查看防火墙的硬件信息
Firewall(config)#show xlate
查看内部地址时否转换成外端口地址来上网
3、保证防火墙能上网还要有以下的配置
firewall(config)#nat (inside)1 0 0
对内部所有地址进行NAT转换,或如下配置,对内部固定配置的地址进行NAT转化,未指定的不予转发
