ProtectDrive8.1用户指南
动力电源系列用户指南说明书
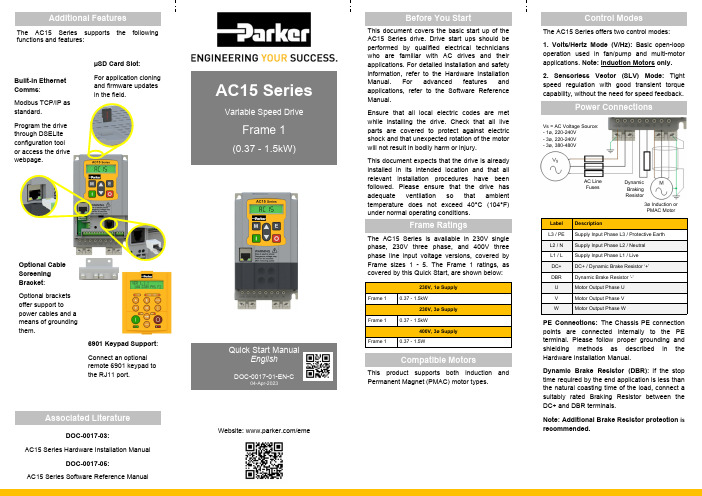
Power ConnectionsPE Connections: The Chassis PE connection points are connected internally to the PE terminal. Please follow proper grounding and shielding methods as describedin the Hardware Installation Manual.Dynamic Brake Resistor (DBR): If the stop time required by the end application is less than the natural coasting time of the load, connect a suitably rated Braking Resistor between the DC+ and DBR terminals.Note: Additional Brake Resistor protectionis recommended.Frame RatingsControl ModesLabel DescriptionL3 / PE Supply Input Phase L3 / Protective Earth L2 / N Supply Input Phase L2 / Neutral L1 / L Supply Input Phase L1 / Live DC+ DC+ / Dynamic Brake Resistor ‘+’ DBR Dynamic Brake Resistor ’-’ U Motor Output Phase U V Motor Output Phase V WMotor Output Phase WThe AC15 Series offers two control modes: 1. Volts/Hertz Mode (V/Hz): Basic open-loop operation used in fan/pump and multi-motor applications. Note: Induction Motors only. 2. Sensorless Vector (SLV) Mode: Tight speed regulation with good transient torque capability, without the need for speed feedback.Compatible MotorsThis product supports both Induction and Permanent Magnet (PMAC) motor types.230V, 1ø SupplyFrame 10.37 - 1.5kW230V, 3ø SupplyFrame 10.37 - 1.5kW400V, 3ø SupplyFrame 1 0.37 - 1.5WThe AC15 Series is available in 230V single phase, 230V three phase, and 400V three phase line input voltage versions, covered by Frame sizes 1 - 5. The Frame 1 ratings, as covered by this Quick Start, are shown below:µSD Card Slot :For application cloning and firmware updates in the field.6901 Keypad Support : Connect an optional remote 6901 keypad to the RJ11 port.Built-in Ethernet Comms :Modbus TCP/IP as standard.Program the drive through DSELite configuration tool or access the drive webpage.Optional Cable Screening Bracket :Optional brackets offer support to power cables and a means of grounding them.AC Line Fuses3ø Induction or PMAC MotorDynamic Braking ResistorVs = AC Voltage Source: - 1ø, 220-240V - 3ø, 220-240V - 3ø, 380-480VAC15 Series drive. Drive start ups should be performed by qualified electrical technicians who are familiar with AC drives and their applications. For detailed installation and safety information, refer to the Hardware InstallationManual. For advanced features and applications, refer to the Software Reference Manual.Ensure that all local electric codes are met while installing the drive. Check that all live parts are covered to protect against electric shock and that unexpected rotation of the motor will not result in bodily harm or injury.This document expects that the drive is already installed in its intended location and that all relevant installation procedures have been followed. Please ensure that the drive hasadequate ventilation so that ambient temperature does not exceed 40°C (104°F) under normal operating conditions.AC15 SeriesVariable Speed DriveFrame 1(0.37 - 1.5kW)The AC15 Series supports the following functions and features:DOC-0017-03:AC15 Series Hardware Installation ManualDOC-0017-05:AC15 Series Software Reference ManualQuick Start ManualEnglishDOC-0017-01-EN-C04-Apr-2023Website: /emeLabel Description16 110-230Vac / 24Vdc Supply 17 Healthy : Relay output (to lamp) 18 Motor thermistor ‘+’ 19 Motor thermistor ‘-’ 1 Setpoint (%): 0-10V input 2 Setpoint Trim (%): 4-20mA input 3 Speed Demand (%): 0-10V output 4 Value = 100%: +10V fixed output7 Run Forward : 24V input 8 Remote Reverse : 24V input 9 Jog : 24V input 10 Not Stop : 24V input 11 Not Coast Stop : 24V input 13, 14, 15STO DISABLED (drive operational)Label Description18 Motor thermistor ‘+’ (or link to TH2) 19 Motor thermistor ‘-’13, 14, 15STO DISABLED (drive operational)‘REMOTE’ Operation: Below is an example of the hardware connections required to run the drive in the ‘Standard’ (Basic Speed Mode) macro in ‘Remote’ operator mode:‘LOCAL’ Operation: Below is an example of the minimum hardware connections required to run the drive in ‘Local’ operator mode through the onboard keypad:Parameters: Set > Ctrl > CtrlNo. NameValue0892 Thermistor Type 0 (PTC) / 1 (NTC) 0030Motor Type0 (Induction) / 1 (PMAC)0031Control Strategy 0 (Volts-Hertz) / 1 (Vector)Parameters: Set > Ctrl > nPLA No. NameDefault Value0224Base Frequency 50 (Hz)0223Base Voltage400 (V) 0227 Motor Power0.75 (kW)0226 Nameplate Speed 1450 (rpm) 0228 Power Factor 0.71 0222 Rated Current 1.56 (A) 0182 IM Wiring0 (FALSE)1. Control Strategy Settings: The following parameters in the ‘Ctrl ’ setup menu must first be set:Initial Drive Setup2. Motor Nameplate Settings: Next, motor parameters must be set in the ‘nPLA ’ setup menu (Induction motor parameters shown for illustration):Note: By default, parameter value changes are saved automatically.Menu Navigation:= Enters sub-menu = Exits sub-menu= Scrolls up and down through menu listEdit Parameter Value:= Enters into parameter = Exits parameter = Increases or decreases valueOn drive power-up, the display will revert to the ‘Oper ’ menu. Press the ‘E ’ key three times to exit to the top menu level, so “r x.x ” is shown on the display (where ‘x.x’ is firmware version).Note: Setting ‘IM Wiring’ to ‘1’ (TRUE) swaps phases V & W - inverting motor direction.3. Running the Drive: In the ‘Oper’ menu, enter a speed setpoint (parameter 0459), and press the ‘Run ’ key. The drive will enable, rotating the motor at the speed demanded. Parameter 0105 (Speed Percent ) provides the speed feedback (%):Parameters: OperNo. Name Value 0459 Local Setpoint 0 -> 100 (%) 0105Speed Percent0 - > 100 (%)1. Enable ‘Local’ Control Mode: Hold the ‘Stop ’ key for approx. 3 seconds, until the hand icon appears on the display:2. ‘Autotune’ Routine (SVC Mode only): If parameter 0031 (Control Strategy ) is set to ‘1’ (Vector Control ), then an autotune routinemust be performed prior to running the drive. A ‘Rotating ’ autotune on an uncoupled motor is always the preferred ‘Atn Mode ’, whenever possible .To do this, set the ‘Atn Enable ’ parameter 0035 in the ’Ctrl ’ menu to ’1’ (TRUE ), and press the ‘Run ’ key to start the autotune routine:Parameters: Set > Ctrl > AutnNo. Name Value0036 Atn Mode 0 (Stationary) / 1 (Rotating) 0035Atn Enable0 (FALSE) / 1 (TRUE)Once the autotune routine has completed, the motor will decelerate to a stop and the drive will disable:The drive is now ready to run in ‘VectorControl’ (SVC) mode.Motor ‘Running’ icon ‘rotates’ in the direction of the shaft and “AL26” textis displayed.Press ‘Run’key.Motor ‘Running’ icon will continue ‘rotating’until the motor has come to a stop.3 seconds...Hold‘Stop’key.‘Local’ mode.To run the drive in ‘Remote’ operation using push-buttons, switches or PLC’s:2. Loading a Macro: Pre-defined application macro’s have been configured for remote operation. To load an Application macro, navigate to the ’App ’ setup menu:Parameters: Set > AppNo.NameValue1150 Application0 (Null) / 1 (Standard) / 2 (Auto/Manual) / 3 (Presets) / 4 (Raise/Lower) / 5 (PID) / 6 (Aux Comms) / 9 (Saved)1152Application Lock 0 (FALSE) / 1 (TRUE) 1151Load Application0 (FALSE) / 1 (TRUE)3. Running the Drive: Providing the drive is in ‘Remote’ operating mode, ’Initial Drive Setup’ is completed, and an ‘Autotune’ has been completed (if in SVC mode), the drive is ready to be run from the remote switches.Set parameter 1150 to the desired macro i.e. ‘1’ for the Standard ‘Basic Speed Control’ application (as per the ’Remote’ Control Connection example).Set parameter 1151 from ‘0’ to ‘1’ (FALSE to TRUE ) to load the application.To ‘lock’ the application so it can not be changed, set parameter 1152 from ‘0’ to ‘1’.1. Enable ‘Remote’ Control Mode: Hold the ‘Stop ’ key for approx. 3 seconds, until the hand icon disappears from the display:‘Remote’ Operation3 seconds...Hold ‘Stop’key.‘Remote’ mode.RunStop / ResetEscape Enter SVC Mode ‘Active’ Drive ‘Running’ Status Parameter Units Local Control ‘Active’ Comms Control‘Active’ Parameter Number / ValueROTATING MOTOR5. To Change the Motor Direction: With the drive stopped, press the ‘Stop ’ key and either the ‘Up ’ (Forward), or ‘Down ’ (Reverse) key simultaneously.Press ‘Stop’key.Motor ‘Running’ icon will continue ‘rotating’until the motor has come to a stop.4. Stopping the Drive: Press the ‘Stop ’ key to bring the motor to a standstill and disable the drive:Motor ‘Running’ icon ‘rotates’ in thedirection of the shaft.Press ‘Run’key.。
Windows 8.1、Windows RT 8.1创建 USB 恢复驱动器

Windows 8.1、Windows RT 8.1创建USB 恢复驱动器适用于Windows 8.1、Windows RT 8.1如果你的电脑遇到问题,即使它已无法启动,USB 恢复驱动器仍可以帮助你排除故障和解决这些问题。
你的电脑可能已经附带了一个恢复映像,用来刷新或重置你的电脑。
恢复映像存储在电脑上的专用恢复分区中,大小通常为3-6 GB。
为了节省电脑的空间,你可以从电脑中删除恢复映像,改而使用恢复驱动器。
Windows 8.1 包括用来创建USB 恢复驱动器的内置工具。
Windows 将告知你恢复分区的大小,而所需的U 盘大小至少要与之相同。
•创建恢复驱动器将擦除U 盘上已存储的所有内容。
使用空的U 盘或确保先将所有重要数据从U 盘转移到其他存储设备,然后再用它来创建USB 恢复驱动器。
检查你的电脑是否具有恢复分区在创建恢复驱动器之前,应该检查你的电脑是否具有恢复分区。
如果没有,你可以创建一个恢复分区,然后再创建恢复驱动器。
检查恢复分区1.从屏幕右边缘向中间轻扫,然后点击“搜索”。
(如果使用鼠标,则指向屏幕右上角,然后将指针向下移动,再单击“搜索”。
)2.在搜索框中输入“命令”,向下轻扫或右键单击“命令提示符”,然后点击或单击“以管理员身份运行”。
需要管理员权限系统可能要求你提供管理员密码或确认你的选择。
3.输入recimg /showcurrent,然后按Enter。
如果你看到一条错误消息,指出“没有活动的自定义恢复映像”,则需要创建一个自定义恢复映像,然后才能创建恢复驱动器。
创建恢复分区只有在你的电脑上目前还没有恢复分区的情况下,才应创建一个恢复分区。
1.从屏幕右边缘向中间轻扫,然后点击“搜索”。
(如果使用鼠标,则指向屏幕右上角,然后将指针向下移动,再单击“搜索”。
)2.在搜索框中输入“命令”,向下轻扫或右键单击“命令提示符”,然后点击或单击“以管理员身份运行”。
需要管理员权限系统可能要求你提供管理员密码或确认你的选择。
马克途一点外置硬盘用户指南说明书
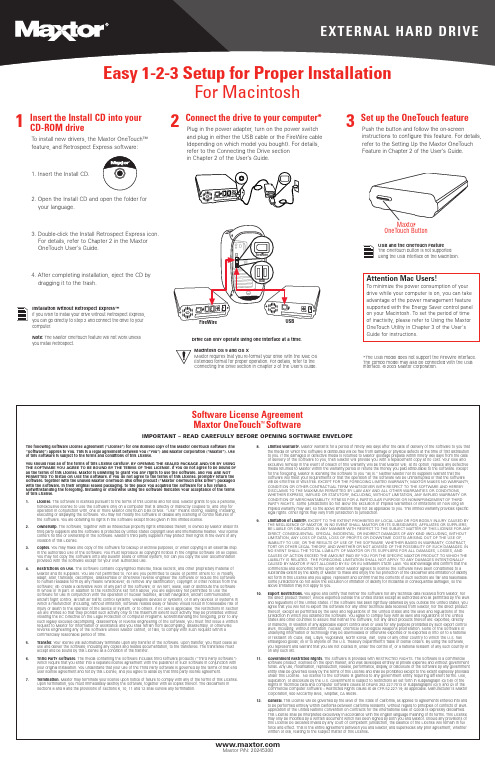
1Insert the Install CD into your CD-ROM driveTo install new drivers, the Maxtor OneTouch™feature, and Retrospect Express software:1. Insert the Install CD.2. Open the Install CD and open the folder for your language.3. Double-click the Install Retrospect Express icon. For details, refer to Chapter 2 in the Maxtor OneTouch User’s Guide.4. After completing installation, eject the CD by dragging it to the trash.FireWireFireWireUSBUSB3Set up the OneTouch featurePush the button and follow the on-screeninstructions to configure this feature. For details,refer to the Setting Up the Maxtor OneTouch Feature in Chapter 2 of the User’s Guide.2Connect the drive to your computer*Plug in the power adapter, turn on the power switch and plug in either the USB cable or the FireWire cable (depending on which model you bought). For details,refer to the Connecting the Drive sectionin Chapter 2 of the User’s Guide.Maxtor OneTouch ButtonMacintosh OS 9 and OS XMaxtor requires that you re-format your drive with the Mac OS Extended format for proper operation. For details, refer to the Connecting the Drive section in Chapter 2 of the User’s Guide.*The USB model does not support the FireWire interface.The combo model may also be connected with the USB interface.©2003 Maxtor Corporation.For MacintoshInstallation without Retrospect Express™If you wish to install your drive without Retrospect Express,you can go directly to Step 2 and connect the drive to your computer.Note: The Maxtor OneTouch feature will not work unless you install Retrospect.Drive can only operate using one interface at a B and the OneTouch FeatureThe OneTouch button is not supported using the USB interface on the Macintosh.The following Software License Agreement (“License”) for one licensed copy of the Maxtor OneTouch Software (the “Software”) applies to you. This is a legal agreement between you (“You”) and Maxtor Corporation (“Maxtor”). Use of this Software is subject to the terms and conditions of this License.You should read all of the terms of this License carefully. BY OPENING THE SEALED PACKAGE AND/OR BY USING THE SOFTWARE YOU AGREE TO BE BOUND BY THE TERMS OF THIS LICENSE. If you do not agree to be bound by all the terms of this License, Maxtor is unwilling to grant you any rights to use the Software, and you ARE NOT PERMITTED TO install OR USE the Software. If you do not agree to the terms of this License, promptly return the Software, together with the unused Maxtor OneTouch disk drive product (“Maxtor OneTouch Disk Drive”) packaged with the Software, in their original sealed packaging, to the place you acquired the Software for a full refund.Notwithstanding the foregoing, installing or otherwise using the Software indicates your acceptance of the terms of this License. 1.License. The Software is licensed pursuant to the terms of this License and not sold. Maxtor grants to you a personal,nonexclusive license to Use the Software only on a computer that is directly or indirectly coupled to, and only for operation in conjunction with, one or more Maxtor OneTouch Disk Drives. “Use” means storing, loading, installing,executing or displaying the Software. You may not modify the Software or disable any licensing or control features of the Software. You are obtaining no rights in the Software except those given in this limited license.2.Ownership. The Software, together with all intellectual property rights embodied therein, is owned by Maxtor and/or its third party suppliers and the Software is protected by United States copyright laws and international treaties. Y our license confers no title or ownership in the Software. Maxtor’s third party suppliers may protect their rights in the event of any violation of this License.3.Copies. You may make one copy of the Software for backup or archival purposes, or when copying is an essential step in the authorized Use of the Software. You must reproduce all copyright notices in the original Software on all copies.You may not copy the Software onto any bulletin board or similar system, nor can you copy the user documentation provided with the Software except for your own authorized use.4.Restrictions on Use. The Software contains copyrighted material, trade secrets, and other proprietary material of Maxtor and its suppliers. You are not permitted to, nor are you permitted to cause or permit others to: (i) modify,adapt, alter, translate, decompile, disassemble or otherwise reverse engineer the Software or reduce the Software to human-readable form by any means whatsoever; (ii) remove any identification, copyright or other notices from the Software; (iii)create a derivative work of any part of the Software; or (iv) rent, lease, loan or distribute the Software in whole or in part. In addition to the restrictions set forth above, you are expressly not permitted to Use the Software for use in conjunction with the operation of nuclear facilities, aircraft navigation, aircraft communication,aircraft flight control, aircraft air traffic control systems, weapons devices or systems, or in any devices or systems in which a malfunction (including, without limitation, software related delay or failure) would result in foreseeable risk of injury or death to the operator of the device or system, or to others. If EC law is applicable, the restrictions in Section 4(i) are limited so that they prohibit such activity only to the maximum extent such activity may be prohibited without violating the EC Directive on the Legal Protection of Computer Programs. Notwithstanding the foregoing, prior to any such legally excused decompiling, disassembly or reverse engineering of the Software, you must first issue a written request to Maxtor for information or assistance and you shall refrain from decompiling, disassembly, or otherwise reverse engineering any of the Software unless Maxtor cannot, or fails, to comply with such request within a commercially reasonable period of time.5.Transfer. Your license will automatically terminate upon any transfer of the Software. Upon transfer, you must cease all use and deliver the Software, including any copies and related documentation, to the transferee. The transferee must accept and be bound by this License as a condition of the transfer.6.Third Party Software. The media containing the Software includes third software products (“Third Party Software”)which require that you enter into a separate license agreement with the publisher of such software in conjunction with your original installation. You understand that your use of the Third Party Software is governed by the terms of that end user license agreement and not by this License, and you agree to abide by that third party license agreement.7.Termination. Maxtor may terminate your license upon notice of failure to comply with any of the terms of this License.Upon termination, you must immediately destroy the Software, together with all copies thereof. The disclaimers in Sections 8 and 9 and the provisions of Sections 6, 10, 11 and 12 shall survive any termination.8.Limited Warranty. Maxtor warrants for a period of ninety (90) days after the date of delivery of the Software to you that the media on which the Software is distributed will be free from damage or physical defects at the time of first distribution to you. If the damaged or defective media is returned to Maxtor (postage prepaid) within ninety (90) days from the date of delivery of the Software to you, then Maxtor will provide you with a replacement copy at no cost. Your sole and exclusive remedy in the event of breach of this warranty will be that Maxtor will, at its option, replace any defective media returned to Maxtor within the warranty period or refund the money you paid attributable to the Software. Except for the foregoing, Maxtor is licensing the Software to you “as is.” Neither Maxtor nor its suppliers warrant that the Software will meet your requirements or that the operation of the Software will be uninterrupted or that the Software will be error-free or virus-free. EXCEPT FOR THE FOREGOING LIMITED WARRANTY , MAXTOR MAKES NO WARRANTY ,CONDITION OR OTHER CONTRACTUAL TERM WHATSOEVER WITH RESPECT TO THE SOFTWARE AND HEREBY DISCLAIMS TO THE MAXIMUM PERMITTED BY LAW ANY AND ALL OTHER WARRANTIES OR CONDITIONS,WHETHER EXPRESS, IMPLIED OR STATUTORY , INCLUDING, WITHOUT LIMITATION, ANY IMPLIED WARRANTY OR CONDITION OF MERCHANTABILITY , FITNESS FOR A PARTICULAR PURPOSE OR NONINFRINGEMENT OF THIRD PARTY RIGHTS. Some jurisdictions do not allow the exclusion of implied warranties or limitations on how long an implied warranty may last, so the above limitations may not be applicable to you. This limited warranty provides specific legal rights. Other rights may vary from jurisdiction to jurisdiction.9.Limitation of Liability. EXCEPT TO THE EXTENT PROHIBITED BY LOCAL LAW OR FOR BODILY INJURY CAUSED BY THE NEGLIGENCE OF MAXTOR, IN NO EVENT SHALL MAXTOR OR ITS SUBSIDIARIES, AFFILIATES OR SUPPLIERS,BE LIABLE OR OBLIGATED IN ANY MANNER WITH RESPECT TO THE SUBJECT MATTER OF THIS LICENSE FOR ANY DIRECT, CONSEQUENTIAL, SPECIAL, INCIDENTAL, OR INDIRECT DAMAGES OF ANY KIND (INCLUDING, WITHOUT LIMITATION, ANY LOSS OF DATA, LOSS OF PROFITS OR DOWNTIME COSTS) ARISING OUT OF THE USE OF ,INABILITY TO USE, OR THE RESULTS OF USE OF , THE SOFTWARE, WHETHER BASED IN WARRANTY , CONTRACT,TORT OR OTHER LEGAL THEORY , AND WHETHER OR NOT ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. IN NO EVENT SHALL THE TOTAL LIABILITY OF MAXTOR OR ITS SUPPLIERS FOR ALL DAMAGES, LOSSES, AND CAUSES OF ACTION EXCEED THE AMOUNT PAID BY YOU FOR THE SPECIFIC MAXTOR PRODUCT TO WHICH THE LIABILITY IS RELATED. THE FOREGOING LIMITATION SHALL NOT APPLY TO ANY DAMAGES INTENTIONALLY CAUSED BY MAXTOR IF NOT ALLOWED BY EU OR EU MEMBER STATE LAW. Y ou acknowledge and confirm that the commercial and economic terms upon which Maxtor agrees to license the Software have been conditioned to a substantial extent by the ability of Maxtor to make and enjoy the full protection of the disclaimer and limitation of liability set forth in this License and you agree, represent and confirm that the contents of such sections are fair and reasonable.Some jurisdictions do not allow the exclusion or limitation of liability for incidental or consequential damages, so the above limitation may not apply to you.10.Export Restrictions. You agree and certify that neither the Software nor any technical data received from Maxtor, nor the direct product thereof, will be exported outside the United States except as authorized and as permitted by the laws and regulations of the United States. If the Software has been rightfully obtained by you outside the United States, you agree that you will not re-export the Software nor any other technical data received from Maxtor, nor the direct product thereof, except as permitted by the laws and regulations of the United States and the laws and regulations of the jurisdiction in which you obtained the Software. You agree to comply fully with all laws and regulations of the United States and other countries to assure that neither the Software, not any direct products thereof are: exported, directly or indirectly, in violation of any applicable export control laws or used for any purpose prohibited by such export control laws, including, without limitation, nuclear, chemical or biological weapons proliferation. None of the Software or underlying information or technology may be downloaded or otherwise exported or re-exported (i) into (or to a national or resident of) Cuba, Iraq, Libya, Yugoslavia, North Korea, Iran, Syria or any other country to which the U.S. has embargoed goods; (ii) or to anyone on the U.S. Treasury Department’s Table of Denial Orders. By using the Software,you represent and warrant that you are not located in, under the control of, or a national resident of any such country or on any such list.ernment Restricted Rights. The Software is provided with RESTRICTED RIGHTS. The Software is a commercial software product, licensed on the open market, and was developed entirely at private expense and without government funds. Any use, modification, reproduction, release, performance, display, or disclosure of the Software by any government entity shall be governed solely by the terms of this License and shall be prohibited except to the extent expressly provided under this License. No license to the Software is granted to any government entity requiring different terms. Use,duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 or subparagraphs (c)(1) and (2) of the Commercial Computer Software – Restricted Rights clause at 48 CFR 52.227-19, as applicable. Manufacturer is Maxtor Corporation, 500 McCarthy Blvd., Milpitas, CA 95035.12.General. This License will be governed by the laws of the State of California, as applied to agreements entered into and to be performed entirely within California between California residents, without regard to principles of conflicts of laws.Application of the United Nations Convention on Contracts for the International Sale of Goods is expressly disclaimed.This License shall be interpreted exclusively in accordance with the English language meaning of its terms. This License may only be modified by a written document which has been signed by both you and Maxtor. Should any provisions of this License be declared invalid by any court of competent jurisdiction, the balance of the License will remain in full force and effect. This is the entire agreement between you and Maxtor, and supersedes any prior agreement, whether written or oral, relating to the subject matter of this License .Software License Agreement Maxtor OneTouch ™SoftwareIMPORTANT – READ CAREFULLY BEFORE OPENING SOFTWARE ENVELOPEAttention Mac Users!To minimize the power consumption of your drive while your computer is on, you can take advantage of the power management feature supported with the Energy Saver control panel on your Macintosh. To set the period of time of inactivity, please refer to Using the Maxtor OneTouch Utility in Chapter 3 of the User's Guide for instructions.1Insert the Install CD into your CD-ROM drive1. Insert the Install CD.2. Wait for the Maxtor screen to appear.3. Follow the on-screen instructions to install drivers, the Maxtor OneTouch feature, and Retrospect software. For details, refer to Chapter 2 in the User’s Guide.4. After completing installation, eject the CD.FireWireUSB1394USBMaxtor OneTouchButton*The USB model does not support the 1394 interface.The combo model may also be connected with the USB interface. ©2003 Maxtor Corporation.3Set up the OneTouch featurePush the button and follow the on-screeninstructions to configure this feature. For details,refer to the Setting Up the Maxtor OneTouch Feature in Chapter 2 of the User’s Guide.2Connect the drive to your computer*Plug in the power adapter, turn the power switch on and plug in either the USB cable or the 1394 cable (depending on which model you have). For details,refer to the Connecting the Drive sectionin Chapter 2 of the User’s Guide.Windows 2000 and XPIf you get an error message regarding Administrative Privileges, refer to chapter 6 of the User’s Guide.Windows 98SE and 1394* interfaceYou must install Microsoft’s 98SE Storage Supplement.For details, refer to chapter 2 of the User’s Guide.Drive can only operate using one interface at a time.Allow up to 2 minutes for your computer to recognize the drive.For WindowsInstallation without Retrospect™If you wish to only install your drive without Retrospect, you can choose the ‘Custom Install’ option to install the Maxtor software only. For more information, go to Chapter 2 in the User’s Guide .Note: The Maxtor OneTouch feature will not work unless you install Retrospect.Attention Windows Users!Your Maxtor OneTouch drive has beenprogrammed to automatically spin down after 1 hour of inactivity to minimize the power consumption of the drive. To change the period of time of inactivity, please refer to Using the Maxtor OneTouch Utility in Chapter 3 of the User's Guide for instructions on using the Maxtor OneTouch Utility for Windows.。
Fortinet Protect 安装手册说明书

FORTINET® PROTECT MANUAL FOR ERECTING FORTINET PROTECT FENCETable of contents1. The Betafence concept. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31.1 Post system. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31.2 Tools for professional installation . . . . . . . . . . . . . . . . . . . . . . . . . 32. Preparation of the perimeter fence line . . . . . . . . . . . . . . . . . 43. Embedding the posts into the concrete . . . . . . . . . . . . . . . . . 64. Installation of the mesh . . . . . . . . . . . . . . . . . . . . . . . . . . . .75. To continue . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106. Supplementary fixation. . . . . . . . . . . . . . . . . . . . . . . . . . . . 107. Supplementary indications to keep in mind . . . . . . . . . . . . . . 118. Reparation of fortinet welded mesh . . . . . . . . . . . . . . . . . . . 178.1 Tools. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178.2 Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179.Fixing of Y-extension arms with barbed wire and clipped razortape on Bekaclip posts . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20A. Fixation of the Y-extension arms on straight posts. . . . . . . . . . . . . .20B. Fixation of the barbed wire on the Y-extension . . . . . . . . . . . . . . . .20C.Installation & fixation of the concertina coil on top of theY-extension arms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .211.THE BETAFENCE CONCEPTPOST SYSTEMTOOLS FOR PROFESSIONAL INSTALLATIONTension combClip tongsCrimping tongsProfessional Bekaclip postsThe welded mesh is fixed to the posts using stainless steel fixing clips.For even distribution of thetension across the welded mesh.For netting 1,50 meter to 2 meterhigh.For fixing the clips to theattachment strips on the posts.For adjusting the tension(increases the crimping in thehorizontal wires of the mesh)2.PREPARATION OF THE PERIMETER FENCELINELevel the fence line as much as possible over a width of about 3 meter and over the total length: endless undulations make the erecting of the fence very difficult.Normal ground constitutionHoles can be drilled by means of a drill screwed on an excavator: see dimensions as indicated on attached shopdrawing.Sandy groundWork with precast concrete foundation blocks ( off-site or “in sito” )Make full slots following the fence line and install the foundation blocks.Fill up the slot with back fill, gravel or something alike. Level the area in front (=outside the property) over about 3 meter.Hard rocky groundDrill holes with diameter +/- 20 cm, 60 cm deep by means of an adapted widia drill screwed on an excavator: posts can be shortened.After putting the postst in the holes fill up the holes with rigid liquid concrete.In areas where there is water accumulationDepending on the dept, use longer posts or check the possibility to put the fence on another track.Important note:▪Take at least one week for hardening of the concrete▪Make wet several times a day and protect against sunshine especially when temperatures are high▪We advice to use concrete as dry as possibleSample of a propertyInner- and outer cornersVerify the details related to the direction of the fixing strip on the post when making inner- and outer-corners.OUTER CORNER3.EMBEDDING THE POSTS INTO THE CONCRETE (+ ONE WEEK FOR HARDENING)STEP 1Start embedding the corner-, first- and end- posts and the intermediate tension posts first, together with the brace posts. STEP 2Fix the brace posts properly: each hole has to be directed to the mid point of the Bekaclip post; screws have to be fixed properly. Holes diameter 8 mm for hook bolts to be drilled on site/off site by a contractor. STEP 3Tension a rope from top to top of these tension units and embed theintermediate posts properly whilst touching the rope on top of the intermediateposts to ensure the right level and direction.4.INSTALLATION OF THE MESHBekaclip post with Bekaclip tong andstainless steel clipsSTEP 1 & STEP 2Unroll two Fortinet Protect rolls over the ground in front of the posts. STEP 3Connect them by means of the Fortinet clips.Lift up the start of the roll and fix on the first post.Fix each horizontal wire to start.Horizontal wires of the welded mesh on the outside of theproperty.The overhangs directed to the top of the fence.Secure the fixation by means of double knotted tie wire all over the height of the fence. STEP 5Insert the tension comb in the welded mesh acouple of meters over the first intermediatetension unit (at least 30 meter away from the firstpost).Hang on the belt/rope between tension comb andthe scoop of the excavator and start tensioning.The welded mesh will lift up by itself.Once you have full tension (= welded mesh isperfectly straight and “feels hard”, fix the rollon the fixation strip of the tension post withclips about each 30 cm.ORVerify the distance between the lower part of the roll and ground level before fixing properly.STEP 7Do the same on each intermediate post: distance between two clips is about 40 cm.Check height above ground level on each post before fixing.OR5.TO CONTINUEOnce the first 30 linear meter are installedproperly, untension the tension comb and thebelt/rope.Connect 2 or 3 new rolls on the first end andtension by means of the tension comb, the beltand the excavator.Always check the distance between welded meshand ground level and make yourself pleased withthe tension on the welded mesh before fixing.Always fix the mesh first on the tension units(step 6 each +/- 30 linear meter) and later on theintermediate posts (step 7) .6.SUPPLEMENTARY FIXATIONSupplementary double tie wire can be added afterwards and knotted on the inside of the property. We advice once at the top, once at the bottom and once in the middle of the welded mesh.7.SUPPLEMENTARY INDICATIONS TO KEEP IN MIND1.We advice to start erecting the fence on a normal, flat and horizontal groundlevel to learn and to feel how to handle .2.Inner and outer cornersIt is very important to think about the position of the fixation strip of theBekaclip posts before embedding them into the concrete, see the details. Also think about the direction of tensioning before embedding and drilling thecorner posts: sometimes it can be better to turn the post over 90°. Ensure yourself before starting.3.Slopes▪Fix all intermediate posts/fence(detail 3).4.It is important to have some rigid ladders to allow labourers to work up to2,5 meter high .5.Never walk over the welded mesh when spread over the ground, except tojoin two rolls. Otherwise, each step damages/deforms the fence and willinfluence the look afterwards. Of course, this can be adjusted by means of the crimp tong but takes supplementary time afterwards. If there areundulations in the fence after fixing properly, they can be removed by means of the same crimp tong.Crimp tong Tension fork6.When interrupting erecting fence ( for instance after a shift/before aweekend), always fix the last end of the welded mesh on the “lastintermediate tension unit” with clips 10 to 15cm spacing between.7.Prepare the fence line as straight levelled as possible and remove all dirt(rock blocs, wooden planks,….) over a width of about 3 meter in front of the posts: this decreases damages on the welded mesh and increases safety on the job, the speed and the end look of the fence.8.In case of concrete on the lower part of the Bekaclip posts, clean them beforeeverything is hardened, otherwise it will be difficult or impossible to install the clips properly.9.If axe holes of the Fortinet Protect rolls are damaged during uncharging thecontainers, cut away two or tree meshes. Keep in mind that, when fixing two rolls together, it is important that the join is as flat as possible .10.If intermediate posts are not perfectly levelled, it is possible to adjust beforefixing the mesh by means of the black small tension forks by pushing theposts to the left or to the right: this will upgrade the look afterwards .11.Number of clips : For a 2 meter high fenceFor a 2,5 meter high fence with extension arm :12.Unloading a container :To avoid damage to the rolls, replace the standard flat forks on the forklift by round pointed beam.Make sure the forklift can drive into the container to unload to unload. Try to organise a ramp for unloading the container.Such a tool will increase the speed of unloading substantially.13.Verify the dimensions and capacities of the excavator:This is an essential tool to tension in a proper way in all conditions and eliminates working with a winch. In the mean time, the workman with the excavator can transport the heavy rolls, level and backfill the perimeter area.PROCEDURE1.Problem of broken mesh2.Hang on both sides of the mesh a tension comb as close as possible on the inside of the fence, connected with the winch.3.Pull both ends together by using the winch4.Adjust the pieces of Fortinet welded mesh and connect all parts using the Fortinet clips9.FIXING OF Y-EXTENSION ARMS WITH BARBED WIRE AND CLIPPED RAZOR TAPE ON BEKACLIP POSTSA.Fixation of the Y-extension arms on straight postsOff the site▪Enter the Bekaclip post into the small part of the extension arm. If there isa hole diameter 8 mm in the Bekaclip post. This is the part of the post tobe embedded into the concrete .▪Using the self drilling screws 4,8x25 mm, you also need a hard steel drive pen to prepare a hole, a specific bit WERA type 851/1 BDC f.i. and a drilland driver with variable speed (450..1500 r/min.) and adjustable torque(3Nm…10Nm).On site▪Install the extension arm in top of the post .▪Using the self drilling screws 4,8x25 mm : you will need the same tooling as described above AND a contra block f.i. a hammer of min. 1.25kg), toprepare a hole in the extension arm to make drilling and screwing easier .B.Fixation of the barbed wire on the Y-extension▪Unroll a 250 meter long coil of barbed wire in front of the fence.▪Fix the barbed wire on top of an Y-extension, +/- 3 cm beyond the top of the extension arm, at about 125 meter distance from the first post, therewhere you have brace posts.▪Turn the barbed wire around the Bekaclip extension arm and secure the fixation b.m.o. the standard stainless steel clip on the fixing strip.▪Fix a tensioner on both ends of the barbed wire, see drawing below, and tension the barbed wire properly.▪Start with a second layer of barbed wire in the same way, taking into account a spacing of about 20 cm from the top layer.▪Do the installation of the barbed wire on both sites of the fence simultaneously to avoid sacks in the barbed wire rope or lower tension on one of both sides of the fence.C.Installation & fixation of the concertina coil ontop of the Y-extension arms▪necessary tools:-high truck with platform or hollow tube 12 meter long about 5 forks, 3 meter long, to be arranged locally▪using a high truck passing the fence:-whilst truck is moving slowly along the fence, have the coilextended and lay down on the barbed wire ropes over 12 meter ▪using a hollow tube of >12 meter:-Extend the coil over 12 meter-Enter the tube throughout the axe hole of the coil-Fix start & end of the extended coil on the tube = 12 meterextended-Lift up the extended 12 meter long coil by means of minimum 5 forks & 5 people and drop the extended coil on the barbed wireropes▪connection of two coils by means of 3 stainless steel clips▪connection of the coil on the barbed wire ropes: with about 27 stainless steel clips between two extension arms = join each contact point between razor tape and barbed wire.。
永久win8.1激活工教程-win8.1激活工具教程

永久win8.1激活工教程:win8.1激活工具教
程
现在除了用密钥激活win8系统以外,还有一种永久
win8.1激活工具也非常好用,那就是KMSpico这款软件,大
家可以上网搜一下口碑哦,那可是杠杠的。
那么这款永久
win8.1激活工具究竟为何这么神奇咧?大家脑袋里一定充满了
问号吧?接下来是小编为大家收集的永久win8.1激活工教程,
欢迎大家阅读:
永久win8.1激活工教程
一、win8.1激活工具(KMSpico) 永久激活版简介
win8.1激活工具(KMSpico) 永久激活版随着win8升级版
win8.1的上线,很多用户都为自己的电脑进行了升级,因此
激活就成了很多人非常关心的事情,小编这里为大家带来的这
款KMSpico 是一款最新Win8.1激活工具!可成功激活Win8.1
系统专业版,一些通过电话激活不成功的朋友也可以试一试喔!
二、KMSpico使用说明
1、下载之后首先运行 KMSpico_setup.exe 激活工具;
2、安装完成后,会自动跳出操作窗口,点击红色的大按
钮既可进行激活(点击Create可以备份激活文件);
3、耐心等待片刻,Win8.1系统就激活完成了;
4、激活完成之后大家可以到win8.1系统属性中查看到激活状态。
看了“永久win8.1激活工教程”还想看:
1.win8.1如何永久激活
2.win8.1系统怎么永久激活
3.Win8.1怎么一键永久激活
4.win8/win8.1激活工具一键激活工具使用教程
5.win8.1 激活教程。
DELLwin8.1使用指南

重新启动中 请稍候……
上一页
下一页
5、还原出厂映像
等待 启动完成
上一页
下一页
5、还原出厂映像
启动完成 点击下一步
上一页
5、还原出厂映像
继续 下一步
上一页
5、还原出厂映像
首先选择 出厂映像
上一页
然后 下一步
5、还原出厂映像
选择下面的这一项
继续 下一步
上一页
5、还原出厂映像
耐心等待……
上一页
DELL(戴尔) Win8.1使用指南
撰文:袁庆毅
序
本书是专为DELL正版用户量身定制的专 用使用说明。即可作为随机说明书用,也可 当做经销商新入职员工的基础知识普及教材。 还可作为技术速查手册,用到哪里看哪里。 版权所有,翻版必究 本文版权归袁庆毅所有
目录
• • • • • • • • • • • • •
上一页
下一页
9、电脑的快与慢及性能监视
看一台电脑的性能,主要就是看软件是否运行流畅,能同时运行几 个你需要的任务。每一个软件或系统程序都会占用一定的CPU运行时间 、内存空间、或网络带宽、及输入和输出设备的优先使用权等等。 要看这些信息就要用到特殊的软件。这个软件系统本身就有。叫做 “任务管理器”。在任务栏点击 鼠标右键:
这 是 侧 边 栏
上一页 下一页
3、查找已安装的应用
上一页
下一页
3、查找已安装的应用
关闭应程序
上一页
返回目录
4、卸载软件
鼠标移至左下角右键点击 按钮打开“控制面板”
点击卸载程序 上一页 下一页
4、卸载软件
卸红 载框 的内 试是 用解 版包 软分 件区 及以 广后 告需 。 要
WD My Passport Ultra 移动硬盘说明书

Equipped with USB-C ™ technology, the My Passport ™ Ultra portable drive offers an easy way to expand your storage with a modern metal design that complements your PC. It’s Windows ® 10-ready out of the box to seamlessly deliver plug-and-play storage, while password protection with hardware encryption helps enforce the security of your content.MY PASSPORT™ULTRAPORTABLE STORAGEBuilt for today.Ready for tomorrow.• USB-C ™ and USB 3.1 compatible • I nnovative style with refined metal cover • W D Discovery ™ allows you to choose an auto backup plan, password protect your drive and import from social media and cloud storage**• C ontrol your backup plan either hourly, daily or monthly• P assword protection with 256-bit AES hardware encryption • Formatted for Windows ® 10MY PASSPORT ™ ULTRAPORTABLE STORAGEAs used for storage capacity, one terabyte (TB) = one trillion bytes. Total accessible capacity varies depending on operating environment. Product specifications subject to change without notice. Pictures shown may vary from actual products.WD, the WD logo, My Passport, WD Discovery, WD Drive Utilities and WD Security are registered trademarks or trademarks of Western Digital Corporation or its affiliates in the U.S. Mac, the Mac logo and macOS are trademarks of Apple, Inc. USB Type-C is a trademark of USB Implementers Forum, Inc. All other marks are the property of their respective owners. Product specifications subject to change without notice. Pictures shown may vary from actual products. 4078-705133-A04 Aug 2019USB-C and USB 3.1 CompatibleFeaturing USB-C ™ technology, the My Passport ™ Ultra portable drive delivers quick and easy storage for your PC, while the included USB 3.1 adapter makes sure it’s compatible with older machines.Password Protection with 256-bit AES Hardware EncryptionThe WD Security function within WD Discovery helps keep your files private with a password you can choose, making it easy to enable password protection and 256-bit AES Hardware Encryption.Innovative Style and FunctionFusing modern anodized metal and textures, the My Passport ™Ultra portable drive is available in a variety of colors to seamlessly match your personal style and the latest computers.Get More Out of WD DiscoveryIncluded WD Discovery ™ software* makes it easy to back up your photos, videos and documents to the My Passport Ultradrive. To help preserve your online life, WD Discovery allows you to import your content from popular social media and cloud storage services, like Facebook, Dropbox and Google Drive ™.** WD Discovery software can also be used to manage your drive settings like reformatting, LED control and more.Easy-to-Use Auto Backup SoftwareFor your photos, videos or business documents, the WD Backup ™ software included in WD Discovery makes it easy to help protect what’s important to you by automating your backup routine. Simply download WD Backup ™, plug in your drive and set your hourly, daily or monthly schedule.Windows ReadyMy Passport Ultra is formatted for Windows® 10 to deliver plug-and-play storage out of the box. With WD Discovery ™ software, you can also download the NTFS driver for macOS, so you canwork seamlessly between operating systems without reformatting.Product Features。
Hitachi Protection Platform S-Serie V8.1.1软件版本说明书

Hitachi Protection PlatformS-Series V8.1.1Software Release Notes RN-95HPP009-00V8.1.1 uses the Hitachi Protection Platform S-Series system with themultinode D51B-2U storage server, updated S-Series software, and HitachiData Systems Virtual Storage Platform (VSP) G-series 200, 400, 600, 800,1000 arrays.The S2750 system does not require the backend DeltaView Managerstorage node that earlier S-Series systems used because the arrays are nowbeing monitored by the VSP node. Customers with earlier HPP deploymentswill continue to use DVM nodes. Updates to Hi-Track and SNM2 areperformed by HDS Global Services (GS) with the user documentation thatcomes with those applications.On D51B-2U platforms, you will not see fault notifications for fans, powersupplies, hard disk drives, and temperature abnormalities in the S-Seriesconsole manager as these components are now monitored by and reportedfrom Hi-Track.These customer software release notes cite enhancements, issues fixed,known issues and vendor-specific considerations. Enhancements16-GB Fibre Channel Port SupportThis release supports 16-GB Fibre Channel ports. Sep-19918Capacity-Based LicensingThis release introduces a new method of licensing. Previously, you paid fora storage LUN-based license plus any optional features that you wanted.Now, you license a system based on the amount of physical storage capacityyou want to have available plus any optional features. You can increase theamount of storage licensed at any time.Issue Fixed in V8.1.1Proper Bonding Mode Is Now Retained after Software Updating toV8.1.1An issue that caused bonding modes to change when software updatingfrom V7.3.x to V8.1 or V8.1.1has been fixed. The proper bonding mode isnow retained during the upgrade and is properly displayed. In case of anydiscrepancy, clear your browser’s cache and check again. Seps-20042,20053Improved OST Storage Server Connection ManagementA software fix improves OST storage server connection management. Thisadds robustness to the S-Series while also suppressing inapplicableconditions while error checking. Sep-19949Reduced Fragmentation and Increased Ingest RatesA fix was made to the S-Series OST software that prevents unnecessaryfragmentation. This results in significantly improved data ingest rates.Sep-19559Issues fixed in V8.1.0.1 Patch1V8.1.0.1P1 provides fixes to OST reclamation that are included with thisV8.1.1 release.OST Image ReclamationAn issue about the projected amount of OST images that could be reclaimedhas been addressed. Sep-20034OST Reclamation SlownessAn issue that was causing the OST reclamation process to run slowly hasbeen fixed and the reclamation process now runs more efficiently.Seps-20049, 20050, 20055Known IssuesThis release includes the following issues.Ethernet Ports Labeling Is Incorrect on D51B-2U PlatformsThe available Ethernet ports listings are incomplete on D51B-2U platforms.The label should display 4x10 GbE when configured with a 10-GbE networkinterface card. Sep-20013You Can only Create a 4-port Bond on D51B-2U PlatformsA software issue is preventing the creation of any other bonds than a 4-portbond on D51B-2U platforms. Sep-20036Shredded Filenames Are Not Being Removed as ExpectedThere is an issue whereby a significant amount of manual shredding andremoval of filenames has to be performed by a Global Servicesrepresentative. Sep-19903Setting the Appropriate OST Storage Server Plug-In Name TypeExisting customers should continue to use the plug-in name “SEPATON.”New customers should use “HPP-S.” SEP-19655VSP G-Series Storage Arrays Active-Active ReportingThe new Hitachi VSP G-Series storage arrays display configuration pathsdifferently than the HUS and AMS storage. The VSP G-Series storage arraysreport the configuration as Active-Active whereby the HUS and AMS storagearrays report the configuration as Active-Passive. Each is properly reported.Sep-19826Contact HDS Global Services for Large Bulk Deletion of BackupsIf you need to delete 5,000 or more cartridges at one time, contact HDS GSfor the most efficient method to do so. Sep-19935Browser Certificate Considerations with the S-SeriesX.509 Certificate Subject Common Name (CN) Does Not Match theEntity NameA known S-Series security vulnerability is that its X.509 Certificate SubjectCommon Name (CN) does not match the Entity Name rendering acertificate-common-name-mismatch.Self-Signed TLS/SSL Certificate Generates Browser SecurityWarningsYour S-Series appliances comes by default with a self-signed TransportLayer Security and Secure Sockets Layer (TLS/SSL) protocol certificate.Self-signed certificates cannot be trusted by default, especially becauseTLS/SSL man-in-the-middle attacks typically use self-signed certificates toeavesdrop on TLS/SSL connections. If you want to install your owncertificate, contact Global Services (GS) for assistance.Manually Disabling SSLv3 in the Tomcat Configuration FileSSLv3 is enabled by default. Contact GS to disable this service. Sep-19595V8.1.1 Compatibility MatricesThese tables list the backup applications, and the backup server and client operating systems that are supported by V8.1.1. Data Protector is not yet qualified and a bulletin will provide the known information when available. The maximum number of supported virtual devices is 192.Table 1: TSM Compatibility MatrixTable 2: NetBackup Compatibility Matrix BackupApplicationsTivoli Storage Manager 5.3, 5.4, 5.5, 6.1, 6.1.1, 6.1.2, 6.1.3, 6.2, 6.2.1, 6.2.2, 6.3, 7.1Backup ServerHost OperatingSystems Windows Server 2003 SP2Windows Server 2008 SP1Windows Server 2008 R2 (AMD64)Windows 2012 R2 (AMD64)Red Hat Enterprise and CentOS Linux6, 5, 4Solaris 9 and 10AIX 5.3, 6.1Client Operating SystemsWindows Server 2003 SP2Windows Server 2008 SP1Windows Server 2008 R2 (AMD64)Windows 2012 R2 (AMD64)Red Hat Enterprise Linux 5 and 4 andCentOS Linux 6, 5SUSE Linux 10Solaris 9 and 10AIX 5.3, 6.1, 6.3BackupApplicationsNetBackup 5.5, 6.0, 6.5.1, 6.5.3, 6.5.4, 6.5.5, 7.0, 7.1, 7.5, 7.6, 7.6.1, 7.6.1.1, 7.6.1.2, 7.7.1Backup ServerHost OperatingSystems Windows Server 2003 SP2Windows Server 2008 SP1Windows Server 2008 R2 (AMD64)Windows 2012 R2 (AMD64)HP-UX 11Red Hat Enterprise and CentOS Linux6, 5, and 4AIX 5.3, 6.1Solaris 9 and 10Client Operating SystemsWindows Server 2003 SP2Windows Server 2008 SP1Windows Server 2008 R2 (AMD64)Windows 2012 R2 (AMD64)HP-UX 11Red Hat Enterprise Linux 5, and 4 andCentOSLinux 6, 5AIX 5.3, 6.1SUSE Linux 10Solaris 9 and 10Table 3: NetWorker Compatibility MatrixThere are two known issues pertaining to NetWorker . • A restore fails after having processed a number of cartridges. Sep-19880•The S-Series console manager and backup reports incorrectly cite the backup data type as Windows Files instead of an Exchange Server backup. Sep-19912Supported OST Media Servers and Operating SystemsTable 4: OST Media Servers and Operating SystemsSupported OST FeaturesTable 5: Supported OST Features*Requires the NetBackup Data ProtectionOptimization Option license.Virtual Machine Deduplication SupportTable 6: Virtual Machine Deduplication Support Backup Application NetWorker 8.2.0.1Backup ServerHost OperatingSystemsWindows 2008 R2CentOS Linux 6.4Client OperatingSystemsWindows 2008 R2 CentOS Linux 6.4Database Exchange Server 2010 on Windows 2008 R2 SP1Supported OST Media Servers and OS Versions Windows 2012 R2 (AMD64)Windows Server 2008 R2 (AMD64)RHEL5 and RHEL6, CentOS 5 and CentOS 6x(x86_64)Solaris 10 and 11 (SPARC64)AIX 6.1 and 7.1 (PPC)SUSE ES10 and ES11 (x86_64)Symantec 5xxx applianceAuto Image Replication (A.I.R.)AcceleratorAccelerator VMware*Instant Recovery VMwareOptimized Duplication (OptDup)Optimized Synthetic (OptSyn)VMware esx4NetBackup 6.5agent on theVMware ServiceConsole VMDKs as a flat file Fixed and dynamic disks VMSS Configuration LogsAccessing Product DocumentationThis section lists documents related to installation, hardware, software,configuration, monitoring, troubleshooting, best practices, and updates forthe S-Series Hitachi Protection Platform. You can access the HitachiProtection platform documentation from the HPP service console, http://.Related Documents•Hitachi Protection Platform S-Series V8.1.1 User Manual (MK-95HPP001-03)•Hitachi Protection Platform S-Series Software Installation Instructions (FE-95HPP002-02)•Hitachi Protection Platform S-Series V8.1.1 Software UpdateInstructions (MK-95HPP003-02)Contact InformationTechnical SupportIf your unit does not offer a function described in this document, pleaseopen a Global Services case by visiting the HPP support portal at https://, or call Global Services at 800-446-0744. Beprepared to provide your company name, serial number, contactinformation, and a detailed description of your issue.Web SiteFor more information about Hitachi Data Systems and its products, visit: CommentsOur goal is to provide accurate, useful, and easy-to-understanddocumentation. If you have any comments about this manual or havenoticed any errors, we would appreciate your feedback. You may provideyour comments by opening a Global Services case by visiting the HPPsupport portal located at https://. You may alsocontact us directly at the following locations.Hitachi Data Systems Corporate Headquarters2845 Lafayette StreetSanta Clara, California 95050-2639U.S.A.Regional Contact InformationAmericas408-970-1000************Europe, Middle East, and Africa44-0-1753-618000*****************Asia Pacific852-3189-7900**************************。
Drive移动应用用户指南说明书
Drive ............................................. 2
Drive
If the user's company uses Drive, they can automatically use GPS to track their travel – either manually or automatically – on their mobile device. The SAP Concur mobile app captures their route data - which is available in Concur Expense and on the mobile app - where they can select the segments to add to an expense report.
• Use smart sensors to track when their vehicle is in motion and to capture distance from their mobile device
• Turn mileage logs into expense line items in Concur Expense with one click
Yes: iPhone Yes: iPad Yes: Android
IMPORTANT: Be aware that your company's configuration may not allow for all of the features described here. Generally, if a feature is not available in your configuration of the web version of SAP Concur, then it is not available in the mobile app.
蓝光 DVD写机英文用户手册说明书
T o enjoy fully all the features and functions of your product, please read this owner’s manual carefully and completely.OWNER’S MANUAL Blu-ray/DVD WriterENGLISHWH16NS40iii CAUTION :CLASS 3B VISIBLE AND INVISIBLE LASER RADIATION WHEN OPEN.AVOID EXPOSURE TO THE BEAM.ADVARSEL :KLASSE 3B SYNLIG OG USYNLIG LASERSTRÅLING VED ÅBNING.UNDGÅ UDSÆTTELSE FOR STRÅLING.ADVARSEL :KLASSE 3B SYNLING OG USYNLIG LASERSTRÅLING NÅRDEKSEL ÅPENS. UNNGÅ EKSPONERING FOR STRÅLEN.VARNING :KLASSE 3B SYNLING OCH OSYNLIG LASERSTRÅLNING NÄR DENNALDEL ÄR ÖPPNAD. STRÅLEN ÄR FARLIG.VARO! :KURSSI 3B NÄKYVÄ JA NÄKYMÄTÖN AVATTAESSA OLETALTTIINA LASERSÄTEILYLLE. ÄLÄ KATSO SÄTEESEN.The appliance is not intended for use by young children or infirm persons without supervision.ContentsFeatures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1 Important Precautions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2 System Environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3 Location and Function of Controls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4 Installing the Drive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5 Device Drivers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .7 How to Use the Discs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .8 Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9 Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10 Features• Serial ATA interface.• Power tray loading and ejection of disc. (The disc can also be ejected manually.)• CD-R/RW, DVD-R/RW/+R/RW/+/-R DL, DVD-RAM, BD-R(SL/DL/XL(3 Layer)/ XL(4 Layer))/ RE(SL/DL/XL(3 Layer)), BD-R (SL LTH)read and write compatible, CD Family, DVD-ROM and BD-ROM read compatible.• Supports Regional Playback Control Phase II for DVD-Video.• Automatic buffer underrun error prevention technology.• Supports BD 3D movie play.1Important PrecautionsFollow these precautions when handling the drive or discs.• Please take notice that the manufacturer of this equipment does not offer any warranty against data loss due to inappropriate installation or handling, or direct or indirect damages.• Please take notice that the manufacturer will bear no responsibility for direct or indirect damages caused by the use of this product or its malfunction.• Please take notice that the manufacturer will bear no responsibility for damage to data caused by this product.• Please backup (copy) all important data as a protection against data loss.• Avoid placing the drive in a location subject to:- high humidity, high temperature, excessive dust, mechanical vibration,direct sunlightWe recommend using the drive in a horizontal or vertical position.Do not use it in tilted position.• Don’t move the drive suddenly from a cold place to a warm one or raise the room temperature suddenly. Condensation may occur, causing abnormal operation.• Make sure to remove the disc before moving the drive. The disc may become damaged, causing data loss.• Be careful to prevent foreign objects, such as liquids or metal, from entering the drive.• Don’t interrupt the electric power while the drive is operating.• Please pay attention to handling Electrostatic Sensitive Devices, you may use anti-static products such as wrist straps, heel straps, mats to protect your body from electrostatic.23Operating EnvironmentThis unit can be operated in the system environment explained here.System Environmentmanufacturing quality. Maximum write (or read) speed depends on system environments.* There may be some cases when motion picture playback is not smooth depending on bit rate.* Under Windows 8 operating system, a specific mainboard with nVidia GeForce 7025 Chipset may cause an abnormal operation.* Please visit to learn more about the M-DISC .• Playing Blu-ray Disc Movies *NOTICE*Due to copyright protection features, certain requirements must be met in order to playback BD movies on a computer. When using digital video connections, the monitor and graphics card must support High-bandwidth Digital Content Protection (HDCP). Note that most monitors and graphics cards currently don’t support HDCP .But, most High Definition TVs and multimedia monitors do support HDCP . Refer to the PC or graphic card maker’s web site to see if your card supports HDCP .*Graphic Cards with following GPUs (Graphic Processing Unit) are recommended.- Blu-ray Disc playback: Intel G45, ATA radeon HD 2400, nVdia GeForce 7600GT or above.- 3D playback: Intel G45, ATA radeon HD2400, nVdia GeForce 8800GT or above.*When using ATI Radeon HD 1000 Series Graphic Card, some BLURAY movie title can not be played on Windows7 normally. It caused by giving up supporting the device driver of this Graphic Card by ATI Radeon.For more information, Please contact to customer service center or website of ATI Radeon .Graphic card driver shall meet AACS compliance criteria. Please consult your graphics card vendor for proper driver solution.HDCP (High Bandwidth Digital Content Protection): Required to view pre-recoded Blu-ray Disc which is copy protected.4Location and Function of ControlsFront Panel 1. SATA Power Connector (15 pin)2. SATA Data Connector (7 pin)Rear Panel1.Disc Tray2.Emergency Eject Hole3.Drive activity indicatorThe LED is used to indicate the operation ofWriter.4.Eject Button❏ Occasionally CD-R and CD-RW discs written by a CD-R/RW drive cannot be read by otherCD drives. These unreadable discs may need to be read using the CD-R/RW drive they were created with. The disc written using the CD-R/RW drive might not be readable by CD-ROMs other than Multi-read compatible (UDF compatible) CD-ROMs.Multiread compatible (UDF compatible) CD-ROMs are CD-ROMs that can read lowreflectance and support Packet Write.❏ Please note: Certain software (i.e. particularly those including Video playback) may requirea considerably increased specification PC to give acceptable results. While this Blu-ray Disc Rewriter can read DVD-video or BD-MV(BD-ROM) discs, decoding them todisplay on your pc’s monitor requires separate MPEG, H.264 or VC-1 decoding that is done by separate hardware (either an MPEG, H.264 or VC-1 decoder card or MPEG, H.264 or VC-1 decoding done by your video card), or separate software that you install to doMPEG, H.264 or VC-1 decoding. For further details, refer to the documentation that comes with MPEG, H.264 or VC-1 software.5Before installing the drive, please note the following points.■You will need the following:• A screw driver of a suitable size to fit the securing screws for the drive unit.• The manual for the computer, so you can find the mounting positions for the SATA cable.■Turn off all peripheral appliances of the computer and the computer itself, anddisconnect their power cords from the wall sockets.■Discharge any static electricity on your person by touching the computer covers, etc.Removing the Computer CoverMake sure all peripheral devices of the computer and the computer itself are turned off,and then remove the cover. Refer to the manual for the computer for details about removing the cover.NOTE : There may be sharp edges inside the computer so take care to avoid injury.Mounting the Drive1. Remove the a 51/4″ drive bay panel from the computer. Refer to the manual for the computer for details.2. Insert the drive unit into the bay. Do not apply excessive pressure to the cables inside the computer.3.Secure the drive with the screws. If there is not much space behind the drive,NOTE : This is a general installation guide. If your PC hardware appears different, please consult your hardware manual for installing peripheral devices.Installing the Drive6PC ConnectionThe Writer connects to the motherboard of the host computer using a SATA interfaceConnect the power cable so the projection of the cable connector side to come to the left side. Be careful not to connect upside down.NOTE :Improper connection may damage the drive and void the warranty. Generally, the power connector can only fit one way.Connecting the SATAData Cable Connect the data cable. Be careful not to connect upside down.Connect to the SATA connectoron the PC's Motherboard.Connect to the powerconnector of the PC.Device DriversWhen using Windows XP SP3, Vista, Windows 7 and Windows 8/8.1, no special device driver is required. Your system, upon Power On and bootup after installing and connecting the new Blu-ray Disc Rewriter will recognize and load native software drivers automatically.For Windows Users■In order to ensure normal drive operation, please check the following:•The drive is displayed inWindows XP: [Control Panel]-([Performance and Maintenance])-[System]-[Hardware]-[Device Manager]-[DVD/CD-ROM-drives]■If the drive is not recognized by your computer, please check the following items.indicator is displayed on the IDE ATA/ATAPI controllers in [Control•board’s manufacturer and get the appropriate IDE controller driver.■Run Add New Hardware in Control Panel to let PC search again for new device.Included SoftwareRetail versions of this drive come with CD/DVD/BD authoring Software.Before installing, please uninstall any previous CD/DVD/BD burning software you may have loaded on your PC in order to prevent possible compatibility issues. Once you have installed the application software, you may (if you wish) begin to reinstall previous software, taking note for errors. Check for software updates for all of your writing software.7How to Use the DiscsDon’t attach any stickers or labels to discs, It could cause read/write errors and data loss.use damaged, cracked orDO NOT use non-standard discs. NON-standard discs may not play or store data properly.Emergency EjectThis drive has a feature that allows the disc to be ejected manually if this becomes necessary such as failure of the drive or a power outage.NOTE:Don’t use this feature except in an emergency.1)Turn the power to OFF.2)Poke a fine-tipped object (such as a straightened heavy duty paper clip) into thesmall hole above the eject button. The front door will pop open and the disk tray will come partway out.This feature is a last measure to be or spring clamp to pull it out.8TroubleshootingBefore Requesting ServiceBefore calling for service, check this list.•The drive doesn’t have power.•Is the power supply cable from the host computer plugged in?•Is the Power Connector to the drive securely attached?•The system doesn’t start.•Are the power and SATA cables to the PC correctly connected?•Is the total length of the SATA cable 20 inches or less?•Is each connector completely attached?Other connections may have been knocked lose while installing the drive.•Cannot Read or Write Discs.•Is the condition of everything else in the system (CPU, hard disc, and others) as it should be? (See system environment.)•Does the CD, DVD or BD disc have dirt or scratches?•Did a screen saver or other application operate while writing to the disc?•Is there enough free space on the CD, DVD and BD disc?•Does writing fail even using the simulation test for CD or DVD disc?•Is the disc loaded in the drive with the read/write surface facing the right direction?(label up)•Is the drive installed in the correct orientation?•Was the drive or disc moved from a low temperature environment to a high temper-ature environment? (There is a possibility of condensation on the lens in the drive or on the surface of the disc.)When you call for service, be prepared to give as much information as possible of your system, environment, and the specific problem. (What happened? When? How long? What was going on? Were there any error messages displayed? etc.)Please Note: Since this product supports Regional Playback Control Phase II forDVD-Video with CSS, a certain MPEG decoder card or Software without regional code setting may cause this drive not to read DVD-Video with CSS discs. This Drive enables you to change the regional code up to 5 times.9SpecificationsBD-RE: The disc of version 1.0 is not supported.There might be some cases when this drive can not satisfy the best performance depending on the conditions of the disc, the drive, and the recording format.* The drive’s appearance and specifications may change without prior notice.1011Caution!The disc rotates at high speed in the drive unit.Use of worn, damaged, or non-standard discs can adversely affect the drive and cause the disc to shatter or crush while in use.Disc crush can only occur when you use a damaged disc in the drive. It is an extremely rare occurrence, but there are steps which can be taken to prevent it. Always check your discs before inserting them into the drive.1. Take care not to use worn, cracked, damaged,warped or poor quality discs, as this maycause damage to your drive.2. Check the clear plastic on the center of thedisc, cracks here are the main cause of disccrush.3. Do not play discs which are a non-standard(I.e. non-circular)shape, such as heart shapeddiscs, or discs in the shape of a businesscard.How can you keep your discs from becoming damaged?1. When not in use, remove discs from the drive.2. Keep discs in the packaging supplied withthem and out of direct sunlight and away from heat sources.Excessive vibration or a sudden jolt to the drive during operation may cause a malfunction.Avoid exposing the drive to sudden changes in temperature as it may cause condensation to collect inside the drive.Please visit and install the automaticfirmware download program, “LG ODD Online F/W update.”This program will automatically check for new firmwarereleases and download them. It is also included on thesoftware discs that accompany our drives.©2014 Made by LG Electronics.。
Hitachi Protection Platform S-Series V8.1.1软件更新指南说

Hitachi Protection Platform S-SeriesV8.1.1 Software Update InstructionsF AST F IND L INKSPrefaceChanges in this revisionGetting helpTable of contentsMK-95HPP003-02© 2008-2016 Hitachi, Ltd. All rights reserved.No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, or stored in a database or retrieval system for any purpose without the express written permission of Hitachi, Ltd. and Hitachi Data Systems Corporation (hereinafter referred to as “Hitachi”).Hitachi, Ltd. and Hitachi Data Systems reserve the right to make changes to this document at any time without notice and assume no responsibility for its use. Hitachi, Ltd. and Hitachi Data Systems products and services can only be ordered under the terms and conditions of Hitachi Data Systems' applicable agreements. All of the features described in this document may not be currently available. Refer to the most recent product announcement or contact your local Hitachi Data Systems sales office for information on feature and product availability.Notice: Hitachi Data Systems products and services can be ordered only under the terms and conditions of Hitachi Data Systems’ applicable agreements. The use of Hitachi Data Systems products is governed by the terms of your agreements with Hitachi Data Systems.By using this software, you agree that you are responsible for:a) Acquiring the relevant consents as may be required under local privacy laws or otherwise from employees and other individuals to access relevant data; andb) Verifying that data continues to be held, retrieved, deleted, or otherwise processed in accordance with relevant laws.Hitachi is a registered trademark of Hitachi, Ltd. in the United States and other countries. Hitachi Data Systems is a registered trademark and service mark of Hitachi in the United States and other countries. All other trademarks, service marks, and company names are properties of their respective owners.Export authorization is required for Data At Rest Encryption. Import/Use regulations may restrict export of the S-Series platform to certain countries:•China – S-Series is eligible for import but the License Key and encryption may not be sent to China •France – Import pending completion of registration formalities•Hong Kong – Import pending completion of registration formalities•Israel – Import pending completion of registration formalitiesiiHitachi Protection Platform S-Series1Hitachi Protection Platform S-Series V8.1.1 Update InstructionsHitachi Protection PlatformS-Series V8.1.1Software Update InstructionsThese instructions provide the steps necessary to update an existing S-Series Protection Platform software to V8.1.1. You will need the V8.1.1 software reimage.zip file from the Hitachi Data Systems Global Services site Https://.This document is intended for personnel who assist in installing, maintaining, and managing the S-Series platform in the backup environment.This document includes the following main sections:•“Update paths” on page 2•“Platform requirements for S-Series software version 8.1.1” on page 2•“Updating the software to version 8.1.1” on page 3•“Updating the S-Series platform with tape image replication” on page 6•“Updating the OST plug-ins to V8.1.1” on page 10•“Accessing product documentation” on page 112Hitachi Protection Platform S-Series V8.1.1 Update InstructionsUpdate pathsFollowing are the supported update paths to S-Series platform software version 8.1.1.Platform requirements for S-Series software version 8.1.1Hardware•A D51B-2U, HP Gen8p, HP G7, or CR220S processor node NOTE:You cannot currently mix a D51B-2U with Gen 8 or G7 nodes •Hitachi Virtual Storage Platform (VSP) G-series 200, 400, 600, 800, 1000 arrays, Hitachi Unified Storage (HUS) or Adaptable Modular Storage (AMS) arrays •Appropriate Ethernet or Fibre Channel switches • A system on which to install Hi-Track and VSP softwareSoftwareFor maximum performance the S-Series V8.1.1 software supports a maximum block size of 512 KB for all backup applications. HDS recommends that you set the block size to 256 KB.NetBackupIf you are using the NetBackup application, you should set the SIZE_DATA_BUFFERS value to 262144 or lower or the backups will not work. Refer to NetBackup documentation for details on how to configure SIZE_DATA_BUFFERS.NetWorkerDeltaStor is optimized for at least 256-KB size blocks/tape records. HDS recommends setting the tape drives to use a 256-KB block size. Otherwise, NetWorker uses a block size based on the device type used; for example, LTO-2 is set by EMC to 64 KB, assuming that the operating system is configured for variable block size mode. Refer to the EMC NetWorker documentation for additional information.Data ProtectorIf you are using the Data Protector application, the maximum that you can set the block size to is 256 KB.Supported Update Paths to S-Series Software V8.1.1V7.3.x and V8.0(VTL 8_1_1-10-reimage.zip)V8.1.1V8.1 and V8.1.0.1(VTL 8_1_1-10.zip update)3Hitachi Protection Platform S-Series V8.1.1 Update InstructionsUpdating the software to version 8.1.1NOTE:If you are running tape image replication technology on your S-Series platform, see “Updating the S-Series platform with tape image replication” on page 6, before performing a software update on your S-Series platform.NOTE:You can use VTL_8.1.1-10.zip only to upgrade from V8.1 to V8.1.1. Other upgrade paths must use VTL_8.1.1-10.reimage.zip (reimages the system).To update your system:1.Make sure you are logged into the Console Manager as administrator . Navigate to the Chassis Status screen (System > Chassis).2.Click Save Config in the MAINTENANCE TASKS list to save the current configuration.3.Click on Software Update in the MAINTENANCE TASKS list. The Software Update screen is displayed (Figure 1).Figure 1: Software Update Screen4.Download the appropriate update file (reimage or update, see “Update paths” ) from the HDS FTP site and save it to a local directory on the system that runs the S-Series Console Manager .5.From the Software Update Wizard, browse to where you saved the VTL_8_1_1-x .zip file if you are updating from V8.1 to V8.1.1, and open it.6.Click Next Step . A message appears, indicating that the upload process may take a few minutes.NOTE:Reimaging requires two reboots, thus longer than a software update.Figure 2: Software Update Upload Screen7.When the upload is complete, the screen displays the SOFTWARE UPDATE WARNING. This warning states that the system will reboot after the update and will interrupt your backup and restore operations if you have not shut them down.4Hitachi Protection Platform S-Series V8.1.1 Update InstructionsFigure 3: Software Update Warning Screen8.Click Next Step . The Software License Terms appears.Figure 4: Software License Terms Screen 9.Click ACCEPT . The files are extracted and the update begins.Figure 5: Software Update Extracting Files ScreenThe update is complete when the SOFTWARE UPDATE FINISHED screen appears (Figure 6). This screen displays a message that the system is rebooting, and directs you to log in once the system reboot is complete.5Hitachi Protection Platform S-Series V8.1.1 Update InstructionsFigure 6: Sample Software Update Finished Screen10.Click Done . This does not interrupt the reboot process.If you click Done before the process is complete, you may see a browser error or a “Cannot communicate with chassis” error on the Login screen. Wait a few more minutes before trying to log in again.The system is ready for use when the Notifications screen reports that “Initialization for node x completed” for all nodes in the system after you log in. If you have email notifications enabled, the system will report via email when the S-Series platform is again ready for use.Figure 7: Sample Notifications ScreenRefer to the S-Series platform user manual for additional information on configuringand managing your system.6Hitachi Protection Platform S-Series V8.1.1 Update InstructionsUpdating the S-Series platform with tape image replication If you are running tape image replication on your S-Series platform, it is important to place the source and the target libraries into an offline state before continuing with the software update procedure . This ensures that the source and the target systems are not running incompatible versions of the S-Series platform software while the source and the target systems are being software updated.Tape image replication supports bidirectional replication between the following software versions:NOTE:Data will not be replicated while the replication source and the target libraries are offline. Any data backed up to the S-Series source platform during this window will be replicated when the source and the target libraries are brought back online. Therefore, you should keep the update window as short as possible.The HDS-recommended best practice for tape image replication upgrades is to update your target system first followed by the source system.Performing a software update on the target system1.Make sure that all backups and restores are complete.2.Place the replication target libraries into an offline state. See “Placing a replication target into an offline state” on page 8.3.Perform the software update. See “Updating the S-Series platform with tape image replication” and perform a software update depending on your current S-Series software version.4.Place the replication target into an online state. See “Placing an existing offline replication target into an online state” on page 9.Figure 8: Performing a Software Update on the Source System1.Make sure that all backups and restores are complete.2.Place the destination library into an offline state. See “Placing a destination library in an offline state” on page 7.V8.1.1V8.1.17Hitachi Protection Platform S-Series V8.1.1 Update Instructions3.Perform the software update. See “Update paths” on page 2 and perform a software update depending on your current software version.4.Place the destination library into an online state. See “Placing an existing offline destination library into an online state” on page 8.On the source systemPlacing a destination library in an offline state1.Log in to the Console Manager as administrator .2.Click the Tape Image Replication tab and navigate to the LAN/WAN Replication Libraries screen (Replication > Destination Libraries > LAN/WAN Replication Libraries). The list of existing managed destination libraries is displayed.3.Select a library from the LAN/WAN Replication Library Summary screen and click Offline in the Tasks bar . A confirmation dialog is displayed (Figure 9).Figure 9: Place a Destination Library Offline Screen4.Click OK to confirm. A success dialog appears on the screen and the library is placed offline temporarily (Figure 10).NOTE:The library is offline from the replication perspective only and not from the backup application perspective.Figure 10: Placing a Destination Library Offline Success Screen5.Repeat the steps 3 and 4 to place all the existing online libraries on the source system into an offline state.8Hitachi Protection Platform S-Series V8.1.1 Update Instructions Placing an existing offline destination library into an online state1.Log in to the Console Manager as administrator .2.Click the Tape Image Replication tab and navigate to the LAN/WAN Replication Libraries screen (Replication > Destination Libraries > LAN/WAN Replication Libraries). The list of existing managed destination libraries is displayed.3.Select the offline library and click Online in the Tasks bar . A confirmation dialog is displayed (Figure 11).Figure 11: Placing a Destination Library Online Screen4.Click OK to confirm. A success dialog appears on the screen and the library is placed into an online state.Figure 12: Placing a Destination Library Online Success Screen5.Repeat steps 3 and 4 to place all the existing offline libraries on the source system into an online state.On the target systemPlacing a replication target into an offline state1.Log in to the Console Manager as the administrator .2.Click the Tape Image Replication tab and navigate to the LAN/WAN Replication Target screen (Replication > Tape Image Replication LAN/WAN Targets). The Summary of all LAN/WAN Replication Targets screen is displayed.3.Click the target name from the list of targets. The Target Details screen is displayed.4.Click Offline in the Tasks bar . A confirmation dialog is displayed (Figure 13).9Hitachi Protection Platform S-Series V8.1.1 Update InstructionsFigure 13: Placing a Replication Target Offline Screen5.Click OK to confirm that you want to place the selected target offline. The target is placed into an offline state and the following screen is displayed (Figure 14).Figure 14: Replication Target Screen - Status Offline6.Repeat steps 3 to 5 to place all the existing online targets on the target system into an offline state.NOTE:When a replication target is placed offline, all the replication jobs are canceled.Placing an existing offline replication target into an online state1.Log in to the Console Manager as the administrator .2.Click the Tape Image Replication tab and navigate to the LAN/WAN Replication Target screen (Replication > Tape Image Replication LAN/WAN Targets). The Summary of all LAN/WAN Replication Targets screen is displayed.3.Click the target name from the list of targets. The Target Details screen is displayed.4.Click Online in the Tasks bar . The existing offline target is placed into an online state and Figure 15 is displayed.10Hitachi Protection Platform S-Series V8.1.1 Update InstructionsFigure 15: Replication Target Screen - Online Status5.Repeat steps 3 and 4 to place all the existing offline targets on the target system into an online state.Updating the OST plug-ins to V8.1.1You should get the latest version of the OST Plug-ins for your media servers to be compatible with the latest S-Series software version (System > Status > OST: OST Plug-in Downloads). In fact, if you are using the OST A.I.R or Optimized Duplication features, you must update the source and destination S-Series systems on the same day so that you do not end up with a mixed software environment that will not work.Updating OST A.I.R. replicationIf you are running OST A.I.R. replication, HDS recommends that you offline all A.I.R. Disk Volume Pairs from their source prior to the software update.1.Bring the Disk Volume Pairs online after the software update.11Hitachi Protection Platform S-Series V8.1.1 Update InstructionsAccessing product documentationYou can access the end user documentation by clicking the Hitachi Support link provided on the Help tab. Click , and then provide a user name, password, and email address, then click Register . You will then receive a log in and password via email.Figure 16: Help ScreenNOTE:If you are having problems not addressed by this online help, contact your HDS Global Services representative.12Hitachi Protection Platform S-Series V8.1.1 Update InstructionsHitachi Protection Platform S-Series Software Update InstructionsHitachi Data Systems Corporate Headquarters2845 Lafayette StreetSanta Clara, California 95050-2639 U.S.A.Regional Contact Information Americas+1 408 970 1000************Europe, Middle East, and Africa +44 (0)1753 618000*****************Asia Pacific+852 3189 7900**************************MK-95HPP003-02。
Serena 软件的 ZMF 8.1 快速参考手册说明书

SERENA®ChangeMan® ZMF 8.1Quick Reference Serena Proprietary and Confidential InformationCopyright © 2001–2014 Serena Software, Inc. All rights reserved.This document, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. Except as permitted by such license, no part of this publication may be reproduced, photocopied, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of Serena. Any reproduction of such software product user documentation, regardless of whether the documentation is reproduced in whole or in part, must be accompanied by this copyright statement in its entirety, without modification.This document contains proprietary and confidential information, and no reproduction or dissemination of any information contained herein is allowed without the express permission of Serena Software.The content of this document is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Serena. Serena assumes no responsibility or liability for any errors or inaccuracies that may appear in this document.TrademarksSerena, TeamTrack, StarTool, PVCS, Comparex, Dimensions, Prototype Composer, Mariner and ChangeMan are registered trademarks of Serena Software, Inc. The Serena logo, Version Manager and Mover are trademarks of Serena Software, Inc. All other products or company names are used for identification purposes only, and may be trademarks of their respective owners.U.S. Government RightsAny Software product acquired by Licensee under this Agreement for or on behalf of the U.S. Government, its agencies and instrumentalities is “commercial software” as defined by the FAR. Use, duplication, and disclosure by the U.S. Government is subject to the restrictions set forth in the license under which the Software was acquired. The manufacturer is Serena Software, Inc., 1850 Gateway Drive, 4th Floor, San Mateo California, 94404-4061.Publication date: November 2014Note: Settings in ChangeMan ZMF administration and customization of panels, skeletons, and exits may alter the functions described in this Quick Reference.General Information⏹Actions can be initiated by either choosing from menu andoption panels, or by typing line commands on the Package List (see page 12).⏹To process panel information, press [Enter].⏹To cancel without processing panel information, type“CANCEL” on the Command line or in the Option field, andpress [Enter].⏹To access online Help, press the [PF1] key.⏹To jump between panels, use the equal “=” sign. Example: Tojump to the Create A New Package panel, type “=1.1” inCommand or Option, and press [Enter].⏹To see long panel fields (marked by "+"), scroll right and leftwith [PF11] and [PF10]. Press [PF4] for a pop-up window.⏹Sort is now available on many lists. Press [PF1] for moreinformation where there is a list.Creating a Change Package1From the Primary Option Menu, choose 1 (Build) and press [Enter].2From the Build Options menu, choose 1 (Create) and press [Enter].3On the Create A New Package panel:•Type “L” (Long method), “S” (Short method), “D” (No Description) or “I” (No Implementation instructions) in theOption field.•Type the package title, the application, and the requestor’s name and telephone number.•Optionally type the work request ID and the department (these field names may be changed).•Type the package level:1 - Simple2 - Complex3 - SuperQuick Reference34 - Participating•Type the package type (Planned or Unplanned).•Type the package time span (Permanent or Temporary).•Optionally type a package to copy forward.•For unplanned packages, type a reason code.•For temporary packages, type a change duration.•Press [Enter].Steps 4-5 are skipped if the Short Method was chosen in Step 3. 4On the Package Description panel, type a free-formdescription of the package and press [Enter].5On the Installation Instructions panel:•Type the problem contingency action (for documentation only).•Type the installation method:CMN - ChangeMan ZMF schedulerMAN - Manual installationOTHER - External scheduler•Type free-form implementation instructions. Press [Enter]. 6Optionally type on the User Panel, as required. Press [Enter]. 7On the Site Information panel, type the install date and time, the primary and backup contact names and phone numbers, and then Press [Enter].For more details, see the “Creating a Change Package” chapter in the ChangeMan ZMF User Guide.Checking Out a Component1From the Primary Option Menu, choose 1 (Build) and press [Enter].2From the Build Options menu, choose 5 (Checkout) and press [Enter].3On the Checkout Options panel, type the package ID, type “1”(Baseline/Promotion) in the Option field, and press [Enter].4Serena® ChangeMan® ZMF4On the Checkout panel:•Leave the Option field blank to perform checkout, or type “L” in the Option field to display a list of the libraries thatcontain the component.•Type the component name to check out, or leave blank fora list.•Type the component library type, or leave blank for a list.•Type the source library (-n to 0 for a prior or current baseline, or level number +n for a promotion level).•Type the checkout target library option:S - StagingP - Personal (if enabled by administrator)•For a personal target library, type both the library name and the library data set organization.•Select ‘Confirm overlay’ or omit to bypass.•Type the checkout mode:1 - Online2 - Batch job•Select ‘Lock component’ to place an immediate lock, or omit to bypass.•Select Display component user options if desired.•Press [Enter].For more details, see the “Checking Out a Component” chapter in the ChangeMan ZMF User Guide.Staging a Component1From the Primary Option Menu, choose 1 (Build) and press [Enter].2From the Build Options menu, choose 6 (Stage) and press [Enter].3On the Stage Options panel:•Type the package ID.•Type a stage action in the Option field:Quick Reference51 - Dev (Copy a component to the staging library from adevelopment library, then stage the component.)2 -Package (Stage a component already in the package.)3 -Parms (Specify component list selection criteria.)•Press [Enter].Stage From Development (Dev Option)If you chose option 1 Dev on the Stage Options panel:1On the Stage From Development panel:•Type the dataset name.•Type a dataset organization if it is not PDS or SEQ.•Type the library type, or leave blank for a list.•Type a stage name if a new component name is needed.•Select a stage mode (1=Online 2=Batch).•Select ‘Expand HFS subdirectories’ to return the contents of all subdirectories or omit to list only the specifieddirectory.•Select other options desired.•Press [Enter].2For like-source components, continue with "Stage Build" on page 8.Stage Package Components (Package Option)If you chose option 2 Package on the Stage Options panel:1On the Stage Package Components panel:•Component status values:Status DescriptionACTIVE Component has been successfully stagedCHECKOUT Component has been checked out but notyet stagedFROZEN Component cannot not be updated6Serena® ChangeMan® ZMFQuick Reference 7•Type a line command next to one or more component names:INACTIVE Name of the component was copied forward from another package, but the component has not been checked out to the staging libraryINCOMP Build job has not completed or has failedUNFROZENPreviously frozen component is available for update Cmd Description B Browse component BABrowse component activity file (if enabled by administrator)BDBrowse component general description BLBrowse component listing DDelete component from staging library EEdit and stage component EAEdit activity file EDEdit component general description HShow history LCLock component from checkout/stage in this package by another user RRecompile component from staging library SBStage component in batch mode SLDisplay source-load relationship (like-source components only)STStage component (S will also work)UC Unlock component (if locked) to allow checkout/stageStatusDescription8Serena® ChangeMan® ZMF•Press [Enter].2For like-source components, continue with "Stage Build" on page 8.Stage BuildContinue staging a like-source component.1On the Stage Build panel:•Type the language and compile procedure name, or leave blank for selection lists.•Type additional compile and link edit (binder) parameters.•Select ‘DB2 preprocessing’, and select ‘Other DB2 options’ if desired.•Select ‘Other options’ if desired for user panels.•Select ‘Suppress messages’ to prevent the ‘Activated’ messages from the stage job.•Type the JCL job statements to be used for the build job.•Press [Enter].2If you selected Other DB2 options or ‘User Options’, type values desired on those panels and press [Enter].For more details, see the “Staging a Component” chapter in the ChangeMan ZMF User Guide.ULDisplay User ID Work List (if enabled by administrator)UVUpdate Component User Variables VView component VCDisplay Version Control (if enabled by administrator)VL View component listingCmdDescriptionAuditing a Package1From the Primary Option Menu, choose 1 (Build) and press [Enter].2From the Build Options menu, choose 7 (Audit) and press [Enter].3On the Audit Change Package panel:•Type the package ID.•For Audit Part. Package, input:- 1 - the participating package as a simple package.- 2 - the participating package as a primary package.- 3 - the participating package by department number.•Autoresolve parms - Optionally type a dataset name for additional automatic resolve processing parameters.•Select desired options:-Audit staging libraries only-Include history records-Format report for printing-Specify the application scope-Suppress Passed/Failed message from audit job-Include Cross Appl Headings-Print top line only of Cross Appl Headings-Lock the package while audit is running-Reset the audit lock if the audit job did not finish-Automatically resolve out-of-synch conditions-Update only this package rc•Type the JCL job statement to be used for the audit job.•Press [Enter].4Review the audit report in the audit job. See "Out-of-Synch Conditions" on page 15.For more details, see the “Auditing a Package” chapter in the ChangeMan ZMF User Guide.Quick Reference9Promoting/Demoting a Package1From the Primary Option Menu, choose 3 (Promote) and press [Enter].2On the Promote/Demote A Change Package panel:•Type the package ID.•Type “P” (Promote) or “D” (Demote) in the Option field.•Press [Enter].3On the Promote or Demote Site List panel, select a site, and press [Enter].4On the Promote or Demote Options panel:•Type an action in the Option field.•Type a next promotion level or type a demote from level, if the field is available for input.•For promote only, type a date and time to schedule the promote for later, or leave blank for immediate execution.•For promote only, select ‘Short selection list’ for selective promotion to only display the components not currentlypromoted to the next target level.•For promote only, select ‘Bypass overlay check’ to prevent warnings of overlays.•Select ‘Suppress batch messages’ to suppress success/ failure messages from the promote or demote job.•Type the JCL job statement to be used for the promote or demote job.•Press [Enter].5If you chose Selective for the promote or demote option, then on the Promote To or the Demote From panel:•Type “S” to select or “D” to deselect components.•Press [Enter].•Press [PF3] to process.For more details, see the “Promoting and Demoting a Package” chapter in the ChangeMan ZMF User Guide.10Serena® ChangeMan® ZMFFreezing a Package1From the Primary Option Menu, choose 2 (Freeze) and press [Enter].2On the Freeze Options panel:•Type the package ID.•Type the freeze mode in the Option field:1 - Online Freeze package online2 - Batch Freeze package in batch3 - Selective Selectively unfreeze/refreeze packagecomponents4 - Reset Reset indicator after unsuccessful batchfreeze5 - Re-Build Re-submit install JCL build request•Press [Enter].3If a freeze processing error occurs, type “4” (Reset) in the Option field and press [Enter] to resume freeze processing at Step 2.For more details, see the “Freezing a Package” chapter in the ChangeMan ZMF User Guide.Approving/Rejecting a Package1From the Primary Option Menu, choose 4 (Approve) and press [Enter].2On the Approve Package Parameters panel, type the package ID of a frozen package, or type package selection parameters.Press [Enter].3If more than one package satisfies the package selection criteria, select a package on the Approve Package List panel and press [Enter].4On the Approve/Reject Options panel, type “1” (Approve) in the Option field and press [Enter].5On the Approval List panel, type “A” on a line command to approve the package, or type “R” to reject the package, and press [Enter].For more details, see the “Approving or Rejecting a Package” chapter in the ChangeMan ZMF User Guide.Package List1From the Primary Option Menu, choose 5 (List) and press [Enter].2Type selection criteria on the Package List Parameters panel, and press [Enter].3On the Change Package List panel:•Type “CREATE” on the Command line and press [Enter] to create a package.•Type a two-character option on the line command for a package and press [Enter] to take action on the package.Option DescriptionAP Audit change packageA1Approve/Reject change packageA2Display approver’s reject reasonsA4Reset Approval-In-Progress indicatorOption DescriptionA5Re-submit installation JCL build request for package in APR statusBB Browse/Print baseline/promotion librariesBL Browse compressed listingB1Back out change packageCC Compare components in staging library against baseline/promotion libraryC1Check out components from baseline/promotionC2Check out components using package component listC3Check out components from release (ERO only) DM Demote change packageD1Memo delete change packageD2Undelete a memo deleted change packageF1Freeze change package onlineF2Freeze change package in batchF3Selectively unfreeze or refreeze change package componentsF4Reset Freeze-In-Progress indicatorF5Re-submit installation JCL build request for package in FRZ statusOF Work with Online FormsPR Promote change packageQP Query change package informationRC Recompile source code from baseline/promotion librariesRL Re-link (using the binder) load moduleRP Generate application/package reportsRV Revert change package back to development statusOption DescriptionSC Scan baseline for character stringsS1Stage components into change package from an external datasetS2Edit and stage components in change packageS3Specify parameters to select a subset of change package componentsUA Manage Rename or Scratch request in changepackageUB Create Rename or Scratch request for baseline componentUD Update change package DB2 information (DB2Option only)UI Update change package IMS information (IMSOption only)UR Update change package release information (ERO only)U1Update change package control informationU2Update change package descriptionU3Update change package installation instructionsU4Update package install scheduling dependencies for external schedulerU5Update participating package affected applications U6Update complex/super package informationU7Update change package install site and dateinformationU8Change complex/super package to CLO statusU9Change complex/super package to OPN statusUE Update change package user informationZP Compress change package staging librariesOut-of-Synch ConditionsSynch DescriptionDUPLIC!Components in staging and baseline libraries are identical.SYNCH0!Package Master contains no record of thiscomponent.SYNCH1!Non-load component has no ISPF statistics. SYNCH2!Like-source component was compiled withoutusing the designated compile procedure andoptions.SYNCH3!IDRDATA in a load component cannot be read. SYNCH4!Like-copy component in a staging library waschanged more recently than the calling like-source component in a staging library in thesame package.SYNCH5!Like-copy component in a staging library wasaltered more recently than the calling like-sourcecomponent in the baseline library.SYNCH6!Component in a staging library has nocorresponding Component Activity File member inthe package.SYNCH7!Statically linked called load in a staging librarywas changed more recently than the calling loadcomponent in a staging library in the samepackage.SYNCH8!Statically linked called load in a staging librarywas changed more recently than the calling loadcomponent in the baseline library.SYNCH9!Load component in a staging library does notmatch the corresponding like-source componentin the package.SYNCH10!Component in the baseline library has changedsince the component was checked out to apackage staging library.Synch DescriptionSYNCH11!Component in a staging library was changedwithout using ChangeMan ZMF.SYNCH12!Component was copied into a staging librarywithout using ChangeMan ZMF, or it is left overfrom a stage job that abended.SYNCH13!Component in the baseline library was changed more recently than the component in a staginglibrary.SYNCH14!Package component is not in Active status. SYNCH15!More recent version of like-copy or LCTcomponent resides in a staging, promotion, orbaseline library than was used to stage a like-source component in a package.SYNCH16!Like-copy component in the package, whichdoesn’t contain the calling like-source, waschanged after the baseline version of the like-copy but before the calling like-source inbaseline.SYNCH17!Like-copy component in a staging library wasdeleted after it was used to stage or recompile alike-source in the package.SYNCH18!Called load in a staging library was deleted after it was statically linked into a composite load in thepackage.SYNCH19! A package master record points to a packagecomponent that is not in the staging library. SYNCH20!Statically linked called load in staging library has timestamp (SETSSI) that does not match thetimestamp expected by audit.SYNCH21!Remove either the scratch/rename request or the component it refers to from the relevant package.Synch DescriptionSYNCH22!The sub-component to be scratched is in use by the indicated top-level component. Remove thereference to the sub-component or remove thescratch request.SYNCH23!The sub-component to be renamed is in use by the indicated top-level component. It may not bepossible to resolve this until after the rename hasbeen processed in baseline. Change the referenceto the sub-component or remove the renamerequest.Serena® ChangeMan® ZMF Lifecycle。
PCI-PDISO8 用户指南说明书

Table of ContentsPrefaceAbout this User's Guide ...................................................................................................................... i v What you will learn from this user's guide ........................................................................................................ i v Conventions in this user's guide ........................................................................................................................ i v Chapter 1Introducing the PCI-PDISO8 ............................................................................................................. 1-1 Overview: PCI-PDISO8 features .................................................................................................................... 1-1 Software features ............................................................................................................................................ 1-1 Chapter 2Installing the PCI-PDISO8 ................................................................................................................. 2-1 What comes with your PCI-PDISO8 shipment? ............................................................................................. 2-1 Hardware ....................................................................................................................................................................... 2-1 Additional documentation .............................................................................................................................................. 2-1 Optional components ..................................................................................................................................................... 2-1 Unpacking the board ....................................................................................................................................... 2-2 Installing the software .................................................................................................................................... 2-2 Installing the hardware ................................................................................................................................... 2-2 Connecting the board for I/O operations ........................................................................................................ 2-2 Connectors, cables – main I/O connector ....................................................................................................................... 2-2 Field wiring and signal termination accessories ............................................................................................................. 2-4 Chapter 3Functional Details ............................................................................................................................. 3-1 Relay outputs .................................................................................................................................................. 3-1 Form C relays ................................................................................................................................................................ 3-1 Form A relays ................................................................................................................................................................ 3-1 Isolated inputs ................................................................................................................................................. 3-2 Extending the input range .............................................................................................................................................. 3-2 AC input filter ................................................................................................................................................................ 3-2 Chapter 4Specifications .................................................................................................................................... 4-1 Relay specifications ........................................................................................................................................ 4-1 Isolated inputs ................................................................................................................................................. 4-1 Power consumption ........................................................................................................................................ 4-1 Environmental ................................................................................................................................................ 4-2 Main connector and pin out ............................................................................................................................ 4-2About this User's GuideWhat you will learn from this user's guideThis user's guide explains how to install, configure, and use the PCI-PDISO8 so that you get the most out of its digital input and relay output features.This user's guide also refers you to related documents available on our web site, and to technical support resources.Conventions in this user's guideCaution!Shaded caution statements present information to help you avoid injuring yourself and others, damaging your hardware, or losing your data.<:> Angle brackets that enclose numbers separated by a colon signify a range of numbers, such as those assigned to registers, bit settings, etc.bold text Bold text is used for the names of objects on the screen, such as buttons, text boxes, and check boxes. For example:1. Insert the disk or CD and click the OK button.italic text Italic text is used for the names of manuals and help topic titles, and to emphasize a word or phrase. For example:The InstaCal installation procedure is explained in the Quick Start Guide.Never touch the exposed pins or circuit connections on the board.Introducing the PCI-PDISO8Overview: PCI-PDISO8 featuresThe PCI-PDISO8 is an eight channel-isolated high voltage digital input and eight relay output interface board.You can use the PCI-PDISO8 for control and sensing applications where high voltages need to be sensed or controlled.Caution!High voltages are present on the PCI-PDISO8 board when you connect high voltage inputs or outputs to the PCI-PDISO8 connector. Use extreme caution! Never handle the PCI-PDISO8 whensignals are connected to the board through the connector.Never remove the protective plates from the PCI-PDISO8.The eight inputs are individual, optically-isolated (500 V) inputs that can be read back as a single byte. The inputs are not polarity sensitive and may be driven by either AC (50 - 1000 Hz) or DC. Each input channel has a programmable low-pass filter with a time constant of 5 ms (200 Hz).The eight outputs are electromechanical relays. Five relays provide Form C connections, and three relaysprovide normally-open Form A connections. The relays are controlled by writing to an eight-bit port. The relay control register can be read back from the same port.Software featuresFor information on the features of Insta Cal and the other software included with your PCI-PDISO8, refer to the Quick Start Guide that shipped with your device.PCI-PDISO8 User's Guide Introducing the PCI-PDISO8 PCI-PDISO8 functions are illustrated in the block diagram shown here.Figure 1-1. PCI-PDISO8 block diagramChapter 2 Installing the PCI-PDISO8What comes with your PCI-PDISO8 shipment?The following items are shipped with the PCI-PDISO8.Hardware▪PCI-PDISO8 board. The PCI-PDISO8 is shipped with a protective plate covering some components.PCI-PDISO8 with protective plate PCI-PDISO8 without protective plate Additional documentationIn addition to this hardware user's guide, you should also receive the Quick Start Guide. This booklet supplies a brief description of the software you received with your PCI-PDISO8 and information regarding installation of that software. Please read this booklet completely before installing any software or hardware.Optional components▪CablesC37FFS-x C37FF-x▪Signal termination and conditioning accessoriesOmega provides signal termination products for use with the PCI-PDISO8. Refer to Field wiring, signaltermination and conditioning on page 2-4 for a complete list of compatible accessory products.Unpacking the boardAs with any electronic device, you should take care while handling to avoid damage from staticelectricity. Before removing the PCI-PDISO8 from its packaging, ground yourself using a wrist strap or by simply touching the computer chassis or other grounded object to eliminate any stored static charge.If any components are missing or damaged, notify Omega immediately by phone, fax, or e-mail: ▪Phone: (203) 359-1660▪Fax: (203) 359-7700▪Email:**************Installing the softwareRefer to the Quick Start Guide for instructions on installing the software on the OmegaSoft DAQ Software CD.Installing the hardwareThe PCI-PDISO8 board is completely plug-and-play. There are no switches or jumpers to set on the board.Configuration is controlled by your system's BIOS. To install your board, follow the steps below.1.Turn your computer off, open it up, and insert your board into an available PCI slot.2.Close your computer and turn it on.If you are using an operating system with support for plug-and-play (such as Windows 2000 or Windows XP), a dialog box pops up as the system loads indicating that new hardware has been detected. If theinformation file for this board is not already loaded onto your PC, you will be prompted for the diskcontaining this file. The OmegaSoft DAQ software contains this file. If required, insert the CD and click OK.3.To test your installation and configure your board, run the Insta Cal utility installed in the previous section.Refer to the Quick Start Guide that came with your board for information on how to initially set up andload Insta Cal.Connecting the board for I/O operationsConnectors, cables – main I/O connectorTable 2-1 lists the board connectors, applicable cables and compatible accessory boards.Table 2-1. Board connectors, cables, accessory equipmentPin out – main I/O connector12345678910111213141516171819202122232425262728293031323334353637INPUT 7A INPUT 6A INPUT 5A INPUT 4A INPUT 3A INPUT 2A INPUT 1A INPUT 0A RELAY 7(C)RELAY 6(C)RELAY 5(C)RELAY 4 (NC)RELAY 4 (NO)RELAY 3 (C)RELAY 2 (NC)RELAY 2 (NO)RELAY 1 (C)RELAY 0 (NC)RELAY 0 (NO)INPUT 7B INPUT 6B INPUT 5B INPUT 4B INPUT 3B INPUT 2B INPUT 1B INPUT 0B RELAY 7(NO)RELAY 6(NO)RELAY 5(NO)RELAY 4 (C)RELAY 3(NC)RELAY 3 (NO)RELAY 2 (C)RELAY 1 (NC)RELAY 1 (NO RELAY 0 (C)Figure 2-1. Main I/O connector pin outCaution! High voltages are present on the PCI-PDISO8 when you connect high voltage inputs or outputs tothe board’s connector. Use extreme caution! Never handle the PCI-PDISO8 when signals are connected to the board through the connector.Do not remove the protective plate from the PCI-PDISO8. Cabling20137192013719The red stripe identifies pin # 1Figure 2-2. C37FF-x cableFigure 2-3. C37FFS-x cableField wiring and signal termination accessoriesYou can connect the PCI-PDISO8 to the following accessory boards using the C37FF-x cable.CIO-MINI37 – 37-pin screw terminal board.Caution!Do not use exposed-screw terminal boards if your field voltage is more than 24 volts. Using a screw terminal board with high voltage inputs or outputs exposes you and others to those highvoltage signals. Construct a safe cable to carry your signals directly from your equipment to thePCI-PDISO8 connector.Chapter 3 Functional DetailsRelay outputsForm C relaysThe Form C relay has a common, normally open (NO) and normally closed (NC) contact. Figure 3-1 shows the schematic for a Form C relay, like those connected at relay 0 through relay 4.Figure 3-1. Form C Relay (0) contacts▪When 0 is written to the output, the common and NC are in contact.▪When 1 is written to the output, the common and NO are in contact.Form A relaysThe Form A relay has a common and a normally open (NO) contact. Figure 3-2 shows the schematic for a FormA relay, like those connected at relay 5 through relay 7.Figure 3-2. Form A Relay (5) contactsWhen 0 is written to the output, the common and NO are NOT in contact.When 1 is written to the output, the common and NO are in contact.The Form A and Form C relays on the PCI-PDISO8 board are the same type. Only the connections to the relay poles differ.PCI-PDISO8 User's Guide Functional DetailsIsolated inputsThe PCI-PDISO8 has eight isolated input channels. A schematic of a single channel is shown in Figure 3-3. The signals are routed through a bridge rectifier so that the inputs are not polarity sensitive.Figure 3-3. Isolated input schematic - simplifiedExtending the input rangeTo extend the input range beyond the 5-28V specified, add an external resistor. Figure 3-4 shows the resistor and the equations used to calculate resistor values for a given V in.Figure 3-4. Input range-extending resistorAC input filterThe inputs are eight individual, optically isolated (500 V) inputs that can be read back as a single byte. The inputs are not polarity sensitive and may be driven by either AC (50 - 1000 Hz) or DC.Each input has a software enabled/disabled low-pass filter with a time constant of 5 ms (200 Hz). You enable or disable each input with Insta Cal. The filter is required for AC inputs, and should be used for almost all DC inputs. Unless you have reason to turn off a filter, you should enable itChapter 4 SpecificationsTypical for 25°C unless otherwise specified.Specifications in italic text are guaranteed by design.Relay specificationsTable 1. Relay specificationsIsolated inputsTable 2. Isolated input specificationsPower consumptionTable 3. Power consumption specificationsPCI-PDISO8 User's Guide SpecificationsEnvironmentalTable 4. Environmental specificationsMain connector and pin outTable 5. Main connector specificationsTable 6. Connector pin out。
Parker PSD Servo Drive用户指南说明书
PSD: Parker Servo DriveSupport PageDownloads Date Version PSD ServoManager (incl. help files)Please copy the zip - content to a folder (not C:\programs) and start "PSD-ServoManager.exe". No installation required!2023-01-11V01.10.05 PSD Firmware Download(Registration required) 2022-09-28V01.10.05 PSD1 Release History *2022-11-22PSD Error List(see ServoManager → Help → Show Error Info…)2021-02-15PSD1 Functional Safety over EtherCAT downloads2019-04-29PSD1 Programmable Target(Package for CODESYS Development System, rename to*.package after download)CODESYS Development System(link to CODESYS Store, free)2020-12-18 V1.00.01 PSD1 Programmable Application Examples-Electronic_gearing-Recipe Table via digital I/O-Recipe Table via Fieldbus-XYZ_Application-Press-Force Application with Torque Limitation -PROFIDrive State Machine (S7 <-> PSD)-DS402 State Machine (PAC <-> PSD)2021-02-022021-02-022021-02-022021-02-022021-02-022021-08.182021-08-18V1.01V1.01V1.01V1.01V1.01V1.01V1.00PSD Programmable Quick Start Guide2020-12-18 V1.0PSD1 EtherCAT Description XML (= ESI – EtherCAT Slave Information – File)2020-09-23 V1.24 PSD1 CODESYS DriveInterface (also part of CODESYS SoftMotion)-Installation Guide-before Codesys V3.5 SP7-up from Codesys V3.5 SP7 -up from CoDeSys V3.5 SP142016-10-132016-10-132020-09-28V09V10V4.6.0.0PROFINET GSD for PSD1-S, PSD1-M2018-12-20Function Blocks for Siemens S7-1200/1500 with TIA-Portal V14/V15/V15.1-Function Block Overview-FB50 ControlManager (V1.2)-FB51 ControlManager Advanced (V1.6)-FB52 SpeedControl (V1.5)-FB53 Acyclic Parameter Access (V1.1)2021-02-16Ethernet/IP eds Files for PSD1S, PSD1M_1, PSD1M_2, PSD1M_32020-04-21 V1.02 EC declaration of conformity: PSD1-M, PSD1-SStep files: PSD1S, PSD1M (except PSD1MW1800), PSD1MW1800, PSD1MWP010,PSD1MWP0202018-02-15 Manuals / Help systems English German French Italian PSD1-M Short description (PDF)2019-06-272019-06-272019-06-272019-06-27 PSD1-S Short description (PDF)2019-06-272019-06-272019-06-272019-06-27 PSD1 Installation Guide (PDF)2019-10-152019-10-022021-03-03na PSD1 EtherCAT Help files*2022-02-162022-02-162021-03-03na PSD1 PROFINET Help files*2022-02-162022-02-162021-03-03na PSD1 Ethernet/IP Help files*2022-02-162022-02-162021-03-03na PSD1 Programmable Help files* 2022-02-162022-02-162021-03-03na Please download the file by clicking the right mouse button and choosing "…s ave as"*Please copy to your local pc before opening the help file!HTML Help CHM File is Not DisplayedBitte kopieren Sie die Hilfe auf Ihren lokalen PC bevor Sie diese öffnen! CHM Hilfedatei wird nicht angezeigt。
windows 8.1使用手册

Windows 8.1是微软新一代操作系统,整体上Win8的操作方式有了很大的改变,这主要是为了迎合平板电脑的操作习惯,从而使Win8成为一款能在平板电脑上有所作为的操作系统……这一点上,个人还是很看好微软的实力的,Surface正式发售的时候,价格如果合适,说不定本人也会购入一台,毕竟Windows 的兼容性比苹果的系统好很多。
下面咱们就来看看这81个Win8小技巧,相信能在你学习Windows8的道路上,助上一臂之力。
1、边角热区新版Win8取消了开始菜单,但用鼠标点击左下角时仍可进入Metro界面,其实剩余的几个角也都有着类似功用。
比如左上角代表在打开的Metro应用间循环切换、右上角代表可以一键激活Charm工具栏、左下角是Metro与传统桌面的切换键,至于右下角则表示将所有已打开程序最小化(Metro界面下代表全局展示Metro分组)。
2、程序关闭我们知道Metro应用是没有关闭按钮的,当系统从一个应用切换到另一个应用时,Win8会将其自动“挂起”。
虽说挂起状态除了少许的内存占用,对于CPU及网络带宽毫无消耗,但很多人还是不习惯“悬挂”过多的Metro进程。
消费者预览版允许关闭Metro应用,方法是进入应用切换栏右击关闭目标应用。
当然你也可以利用Win7时代的“土法”,直接借助任务管理器搞定它!3、一键MetroMetro是Win8中的最大亮点,但你知道有几种办法可以快速进入Metro界面吗?首先也是最简单的,就是直接点击桌面左下角,其次键盘上的Win键也是一个不错的选择,再者通过Charm中的“开始”图标也能达到同样目的。
注:ESC键、Win键也可用作由Metro退回传统界面的快捷键。
4、“开始菜单”很多人都知道将鼠标悬停到桌面左下角会激活一个缩略图标,点击即可进入Metro界面。
但你也许不知道,如果在这个地方右击鼠标,还会激活另一个隐藏菜单——一个酷似旧版“开始菜单”的小菜单。
此外Win+X也能达到同样的目的,别忘了呀。
HP ProtectTools 安全管理器用户指南说明书

Table of contentsIntroduction (2)Overview of HP ProtectTools Security Manager (2)Supported keyboard layouts in Preboot Security and Drive Encryption (3)HP ProtectTools Security Manager filter logic (4)How Preboot Security handles dead keys (5)Exceptions (6)Windows Input Method Editor (IME) is not supported (6)Password changes using different keyboard layouts (6)Some Asian Keyboards don‟t support numeric characters (7)What to do when a password is rejected (7)Special key handling (7)Chinese, Slovakian, Canadian French, Czech, and Korean (7)Characters not supported (7)For more information (9)IntroductionThe purpose of this paper is to describe how HP ProtectTools Security Manager for Microsoft Windows implements password filter logic and to explain the requirements for setting a proper Windows password when using HP ProtectTools. HP has implemented the One Step Logon feature through HP ProtectTools software on 2008 and newer commercial HP Notebook PCs. The HP ProtectTools Security Manager wizard enables various security levels to protect the computer system and data from unauthorized access. Three security levels can be set:∙HP Credential Manager—Consolidates user passwords and networks accounts into a single data unit called User Identity, which is protected by strong authentication and encryption methods∙Preboot Security—Protects your computer before it boots the operating system (OS)∙HP Drive Encryption—Protects data on your computer by encrypting the hard driveIn addition, you can select a single security login method for authentication at all security levels. The possible login methods include using a Windows® password or fingerprint sensor. When the Windows password is used as the login method, and all security levels are enabled, the One Step Logon feature requires you to enter the Windows password only in the Preboot Security environment or in the full volume encryption (FVE) preboot environment if BIOS isn‟t enabled. Then the One Step Login feature verifies your password at all subsequent security levels and logs you in to the appropriate Windows account. However, you can be locked out of the computer if you select a Windows password that is rejected at the Preboot Security or Drive Encryption levels. This can occur if you select or change your Windows password when the input locale setting of the computer is different from the physical keyboard being used.Windows supports hundreds of input locales. Each locale is a set of information based on user preferences related to language, environment and/or cultural conventions. For example, a user may choose to type a password in German using the International US keyboard layout or by setting up a password combining words from different languages. This makes password verification more difficult because input language translation (localization) support is limited at the Preboot Security and HP Drive Encryption levels. In Windows it is possible to mix keyboard layouts within a single password, particularly by using the right-ALT key in conjunction with the numeric keypad to enter characters.Pre-boot environments do not support all keyboards or keyboard combinations that are possible within Windows. It is the role of HP ProtectTools Security Manager to prevent the user from being locked out due to password rejection at the Preboot Security and/or HP Drive Encryption levels. Overview of HP ProtectTools Security ManagerWith respect to typed authentication tokens such as passwords and HP Spare Key answers, the goal of HP ProtectTools Security Manager is to apply filters when the Windows password is set up or changed to ensure that the password can be typed at the Preboot Security level or Drive Encryption level. This filtering prevents the user from being inadvertently locked out of the computer by rejecting passwords that require a combination of keyboards or an unsupported keyboard layout. HP ProtectTools Security Manager achieves its goal by passing the keyboard layout information to the Preboot Security and Drive Encryption software. Preboot Security and Drive Encryption use preloaded tables of characters to map key strokes from scan code to Unicode based on the supported keyboard layout. When you enter a password before the OS starts, the Preboot Security and Drive Encryption software convert your key strokes to the correct Unicode characters based on the key mapping table. Each software component compares the entered password with the stored password.Preboot Security and Drive Encryption may implement additional methods to assist you when entering your password. For example, in the 2008and newer HP Notebook PC BIOS, if you fail to type a password correctly, a soft keyboard is displayed on the screen so that you can click characters with themouse rather than pressing keys. The Drive Encryption software allows you to dynamically load the keyboard layouts if an incorrect keyboard is currently being used.Supported keyboard layouts in Preboot Security and Drive EncryptionTable 1 contains a list of keyboards which HP supports in Preboot Security and Drive Encryption. The Preboot Security and Drive Encryption login screens support a portion of available Windows keyboard layouts due to space and other limitations particular to their operating environments. In some cases, the common name for a particular keyboard layout in Windows Vista® or Windows 7 differs from the HP designation; therefore, both names are listed in the table.Table 1. HP keyboards supported in Preboot Security and Drive EncryptionHP keyboards supported Common name in Windows Vista or Windows 7 Code (hex)Arabic (101) Arabic (101) 0401Belgian (Comma) Belgian (Comma) 1080cCanadian French (Legacy) Canadian French (Legacy) 0c0cCanadian French Canadian French 1009Chinese Bopomofo Chinese (Traditional) - US Keyboard 0404Chinese ChaJei Chinese (Simplified) - US Keyboard 0804Czech Czech 0405Danish Danish 0406Dutch Dutch 0413Estonian Estonian 0425Finnish Finnish 040bFrench French 040cGerman German 0407Greek Greek 0408Hebrew Hebrew 040dHungarian Hungarian 040eIcelandic Icelandic 040fItalian Italian 0410Japanese Japanese 0411Kazakh Kazakh 043fKorean Korean 0412Latin American Latin American 080aNorwegian Norwegian 0414Polish (Programmers) Polish (Programmers) 0415Polish (214) Polish (214) 10415Portuguese Portuguese 0816Portuguese (Brazilian) Portuguese (Brazilian ABNT) 0416Romanian Romanian (Legacy) 0418Slovakian Slovak 041bSlovenian Slovenian 0424Spanish Spanish 0c0aSpanish (International) Spanish Variation 1040aSwedish Swedish 041dSwiss Swiss German 0807Thai (Kedmanee) Thai Kedmanee 041eTurkish F Turkish F 1041fTurkish Q Turkish Q 041fUK United Kingdom 0809HP keyboards supported Common name in Windows Vista or Windows 7 Code (hex)US US 0409US (International) United States-International 20409HP ProtectTools Security Manager filter logicTo prevent the user from being locked out by the Preboot Security or Drive Encryption logins, HP ProtectTools Security Manager uses a password filter to reject Windows passwords that may be unacceptable. The logic behind the password filter is shown in Figure 1. After a ProtectTools user enters or changes a password, Security Manager verifies that each character entered can be typed by the keyboard layout loaded into the current user‟s profile. If a character is not supported, the password is rejected.Figure 1. Operational logic of the ProtectTools Security Manager password filterHP BIOS implements a second level password filter to ensure that the user is not locked out of the computer. Preboot Security and Drive Encryption contain the keyboard mappings for all the supported keyboards. When a user sets up or changes a password while the Preboot Security or Drive Encryption levels are enabled, Preboot Security and Drive Encryption receive the Unicode password hash from the OS. Password filtering logic verifies that the keyboard layout associated with the user is able to type the password. Otherwise, the password filter will reject the password.Changing the keyboard in Windows without verification by the password filter or choosing a password while unaware that an unintended keyboard layout is selected may prevent you from physically typing your password. After three unsuccessful login attempts, Preboot Security login will automatically display an on-screen keyboard with all possible characters from the associated keyboard layout and allow you to “click” each character in the password.NoteThe on-screen keyboard in the Preboot Security login displays manycharacters, some of which look very similar to characters on otherkeyboards. To enter the correct characters, you should look at allavailable characters before attempting to enter the password.How Preboot Security handles dead keysA dead key is a keyboard key that modifies the next key that is typed. For example, in Windows, some keyboards allow you to type combinations like the following: pressing the dead key ‘and then “e” produces “é.” In other cases, applications themselves allow for dead keys. Many Windows applications allow you to press the dead key Ctrl - ‘and then “e” to produce “é”, independent of the keyboard layout being used. At the Preboot Security login, the use of dead keys has been added to provide you with as much keyboard functionality as possible. If a character can be produced in Windows and cannot be typed at the Preboot Security login, the password will be rejected. If the dead key is not rejected when changing the password of a ProtectTools user within Windows, the user can also use the dead key when logging in at the Preboot Security login screen. Typically, Preboot Security supports dead keys that are supported by a keyboard and does not support dead keys that are supported by particular applications. Thus, the Spanish keyboard layout in Preboot allows for the ‘ and then “e” combination to produce “é”; it does not support the Ctrl - ‘and then “e” combination to produce “é.”Preboot Security ensures that the Windows password chosen can always be typed at the Preboot Security and Drive Encryption login screens, as neither of these two operating environments supports all the advanced typing features available in Windows. Therefore, all characters that require special typing methods that are not common to all keyboards, such as the use of the Kana key (Japanese) or the Input Method Editor (IME) function of Windows, will result in password rejection by the password filtering logic.ExceptionsWindows Input Method Editor (IME) is not supportedWARNINGWhen HP ProtectTools is deployed, passwords entered withWindows IME will be rejected.Windows features an IME that allows a user to compose thousands of complex characters and symbols, such as the many Japanese or Chinese characters, using a standard keyboard. IME is an OS component that extends the capability of the keyboard, but it is not a supported keyboard layout that can be used to enter a password at the Preboot Security or Drive Encryption login screens. Therefore, any password typed with an IME is rejected by the ProtectTools password filtering logic.For example, in some Japanese installations of Windows XP, the default IME is called “Microsoft IME Standard 2002.”1 Because this IME is not a keyboard layout that can be used during the password prompt at the Preboot Security or Drive Encryption login screens, the password typed with this IME in Windows is rejected by ProtectTools. The solution is to switch to a supported keyboard layout, such as Microsoft® IME for Japanese (despite its IME designation) or the Japanese keyboard layout itself, both of which translate to keyboard layout 00000411. Another IME that actually translates to keyboard layout 00000411 is the “Office 2007 IME” for Japanese2.Password changes using different keyboard layoutsThere are potential issues if a user initially sets up a password using one keyboard layout and then changes the password using a different keyboard layout. In general, the password filtering logic attempts to determine the user‟s current keyboard layout and uses this keyboard layout to update the password token information in both the Preboot Security and Drive Encryption authentication domains. If the user enters a character that exists on the latter keyboard but not on the former, the password change will be accepted in Drive Encryption but it will be rejected in the BIOS.A simple solution to this problem is to remove the user in question from HP ProtectTools by running the HP ProtectTools Administrative Console. After ensuring that the desired keyboard layout is selected in the OS, add the user again through the Administrative Console. This allows the Preboot Security and Drive Encryption authentication domains to store the desired keyboard layout, and allows passwords that are typed on the stored keyboard layout to be properly typed at the login screens for either domain.Another potential issue is the use of different keyboard layouts that can produce similar characters. For example, both the U.S. International keyboard layout (20409) and the Latin American keyboard layout (80A) can produce the character é although different keystroke sequences might be used. If a password is initially set with the Latin American keyboard layout, the Latin American keyboard layout is set in the BIOS, even if the password is subsequently changed using the U.S. International keyboard layout.1This name is different from the “Common Name in Microsoft Windows Vista” shown in Table 1 because Windows maps some IMEs to a keyboard layout. In such cases, the IME is supported by HP ProtectTools because the underlying keyboard layout is defined, as designated by the Code (hex) column in Table 1.2The use of the terms “IME” and “Input Method Editor” by Microsoft or a third party can be confusing because the input method could be a keyboard layout instead of an IME. However, the software always looks at the hexadecimal code representation to determine if an IME maps to a supported keyboard layout. Thus, if an IME maps to a supported keyboard layout, HP ProtectTools can support the configuration.Some Asian Keyboards don‟t support numeric charactersSome standard Asian keyboards don‟t allow numeric characters. If a user tries to enter a number for password, it will be rejected on these keyboards.∙Chinese Bopomofo∙JapaneseWhat to do when a password is rejectedIf a password is rejected by HP ProtectTools for one of the reasons listed below, follow the appropriate procedure.∙The password was typed using an unsupported IME keyboard. This is a common issue withdouble-byte languages, such as Korean, Japanese, and Chinese. To avoid password rejection by ProtectTools:1.Select Windows > Control Panel > Regional and Language Options.2.Select the Languages tab3.Click the Details button4.In the Settings tab, click the Add button to add a supported keyboard. For example, add USkeyboards under Chinese Input Language.5.Set the supported keyboard as the default input. Close ProtectTools.6.Open ProtectTools. Enter the password again.∙One or more characters in the password is not supported (see Characters not supported). To resolve this problem, select a Windows password that includes only supported characters. Then open the HP ProtectTools Security Manager wizard again to enter the new Windows password. Special key handlingChinese, Slovakian, Canadian French, Czech, and KoreanWhen a user selects one of the supported keyboard layouts and enters a password (e.g. abcdef), the same password has to be entered with a SHIFT key for lower case and the SHIFT key and CAPS LOCK key for upper case in Preboot Security and Drive Encryption. With the Korean keyboard layout, it is not the SHIFT key that is used to produce English characters but rather the ALT key. Depressing ALT will allow the Preboot Security or Drive Encryption login screens to type English lowercase characters. Depressing ALT and CAPS LOCK will produce English uppercase characters.Characters not supportedTable 2. Characters not supportedKeyboard Layout Windows BIOS Drive EncryptionArabic The لأ, لإ, لا keys generate twocharacters.The لأ, لإ, لا keysgenerate one character.The لأ, لإ, لا keysgenerate onecharacter.French Canadian ç, è, à, é with cap locks are Ç,È, À, Éç, è, à, é with cap locksis ç, è, à, è in bios.ç, è, à, é with caplocks is ç, è, à, è inFVE.Spanish 40a is not supported.US International On the top row, the ¡, ¤, …, ‟, ¥,Keyboard Layout Windows BIOS Drive Encryption × keys are rejected.On the second row, the å, ®, þkeys are rejected.On the third row, the á, ð, økeys are rejected.On the bottom row, the æ key isrejected.Czech The ğ key is rejected.The į key is rejected.The ų key is rejected.The ė ı ż keys are rejected.The ģ ķ ļ ņ ŗ keys are rejectedSlovakian The ż key is rejected The š, ś, ş keys arerejected when typed, butaccepted with the softkeyboard.The ţ dead keygenerates twocharacters.Hungarian The ż key is rejected The ţ key generates twocharacters.Slovenian żŻ key is rejected in Windowsand BIOS alt gr dead key ú, Ú, ů, Ů, ş, Ş, ś, Ś, š, and Š keys are rejected in BIOS.Login is possible with soft keyboard for all keys.For more informationTo learn more about HP business notebooks, contact your local HP sales representative or visit/go/notebooks.© Copyright 2011 Hewlett-Packard Development Company, L.P. The information contained herein is subject tochange without notice. The only warranties for HP products and services are set forth in the express warranty Array statements accompanying such products and services. Nothing herein should be construed as constituting anadditional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation.664183-001, Created May 2011。
win8.1激活工具最新Win8.1激活工具一键激活教程
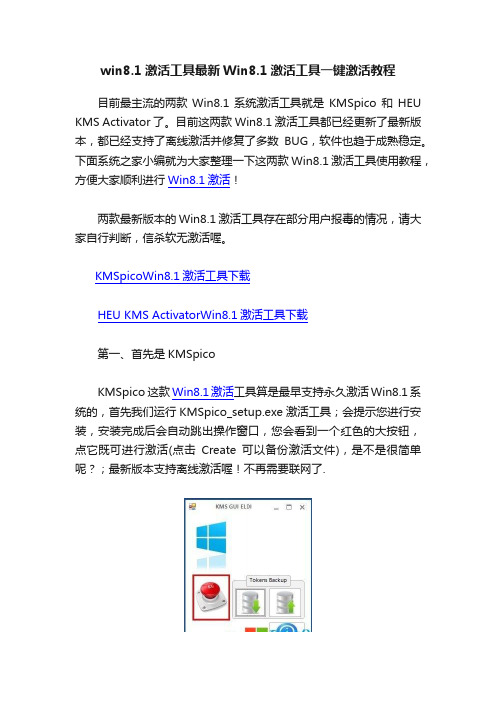
win8.1激活工具最新Win8.1激活工具一键激活教程目前最主流的两款Win8.1系统激活工具就是KMSpico 和HEU KMS Activator 了。
目前这两款Win8.1激活工具都已经更新了最新版本,都已经支持了离线激活并修复了多数BUG,软件也趋于成熟稳定。
下面系统之家小编就为大家整理一下这两款Win8.1激活工具使用教程,方便大家顺利进行Win8.1激活!两款最新版本的Win8.1激活工具存在部分用户报毒的情况,请大家自行判断,信杀软无激活喔。
KMSpicoWin8.1激活工具下载HEU KMS ActivatorWin8.1激活工具下载第一、首先是KMSpicoKMSpico 这款Win8.1激活工具算是最早支持永久激活Win8.1系统的,首先我们运行KMSpico_setup.exe激活工具;会提示您进行安装,安装完成后会自动跳出操作窗口,您会看到一个红色的大按钮,点它既可进行激活(点击Create可以备份激活文件),是不是很简单呢?;最新版本支持离线激活喔!不再需要联网了.第二、接下来是HEU KMS ActivatorHEU KMS Activator 使用起来更加简单,下载完成后解压缩,中文绿色版无需安装,我们点击对应的Win8.1/8/7/Vista/Ser VL按钮就可以进行Win8.1激活了。
同样也支持离线激活Win8.1系统!本文来自于【系统之家】相关热词搜索:win8.1激活工具 win8.1激活 Win8激活上一篇:Win8系统安装教程:Win8硬盘安装工具使用方法下一篇:Win8.1系统如何删除任务栏中的微软拼音输入法版权声明:本站收录的文章及教程都是本站小编精心制作,仅供学习交流之用,如转载请注明出处。
劳动最光荣,请尊重!。
win8.1正版激活密钥怎么使用
win8.1正版激活密钥怎么使用
有时候,我们使用win8.1电脑会遇到想要用密钥激活系统的问题,许多用户反应不知道怎么办,那么该如何解决使用win8.1正版激活密钥这个难题呢?下面是小编收集的关于win8.1正版激活密钥使用的步骤,希望对你有所帮助。
win8.1正版激活密钥使用的步骤
首先点击任务栏的‘库’图标
打开后,点击对话框上面的‘打开控制面板’
打开后,在对话框里找到‘系统’图标
找到后,点击打开,再找到‘windows激活’
点击后再输入输入密匙
激活成功的图片就是这样的了
win8.1正版激活密钥怎么使用相关文章:
1.Win8.1正版不能激活怎么解决
2.win8.1看产品密钥的步骤
3.win8.1怎么查看密钥呢
4.win8.1系统激活工具怎么使用。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
ProtectDrive 8.1 用户指南SafeNet(北京)2007年3月目录1PROTECTDRIVE 8.1概述 (3)2如何计划部署PROTECTDRIVE (4)2.1系统兼容性说明 (4)3PROTECTDRIVE安装使用说明 (5)3.1产品的安装 (5)3.1.1服务端系统安装 (5)3.1.2客户端安装: (6)3.1.3卸载ProtectDrive (9)3.2使用P ROTECT D RIVE (9)3.2.1保护您的硬盘 (10)4使用注意事项 (12)地址:北京市海淀区西三环北路100号金玉大厦1603室 - 2 -1ProtectDrive 8.1概述ProtectDrive是一款已通过Common Criteria (CC) EAL2认证的、功能完善的磁盘保护解决方案,可有效保护存储在笔记本、工作站及服务器硬盘中的全部数据(包括操作系统文件)。
在发生硬件设备丢失或盗窃事件时,ProtectDrive可确保敏感信息不会泄漏出去。
此外,在硬件设备被出售或出租人收回租赁硬件之后,ProtectDrive还可确保其中存储的数据不可重复使用。
图:普通Windows,实施PD和使用智能卡登录的PD启动过程比较相比以前的版本,8.1有以下一些新功能:1.完善的License 控制功能, 免费的30日客户试用版本发放2.日文支持3.iKey 1000(无需部署PKI就可以使用双因素认证令牌)4.可移动媒体管理功能增强,支持USB接口硬盘保护5.支持安全的第三方硬盘恢复6.SSO 助手功能PD 8.0 主要功能:1.AD集中管理,部署B移动媒体保护支持本文档为客户初次使用/试用 ProtectDrive 软件提供一个快速指引。
下面两个文档是ProtectDrive产品最详细的说明(英文版本):1.管理员手册:“pd_administration_guide.pdf”2.用户手册:“pd_user_manual.pdf”地址:北京市海淀区西三环北路100号金玉大厦1603室 - 3 -地址:北京市海淀区西三环北路100号金玉大厦1603室 - 4 -2 如何计划部署ProtectDrive进入系统安装光盘目录,可以看到以下文件:ProtectDrive 为用户提供整机的保护,分为单机版本和网络版本,这两个版本使用同一个软件安装包。
对于不在Windows 域内的机器,需要使用单机版本,如果在域内的机器,推荐使用网络版本。
单机版本: 对于单机版本,安装的时候选择安装客户端版本就可以了,设置选择使用本地设置,安装前需要准备:一个网络共享目录或刻录光盘,用于备份进行PD 系统恢复所需要的数据,不超过1M 。
单机版本支持以下环境:1. Windows 2000 Pro, Service Pack 42. Windows 2000 Server, Service Pack3. Windows Server 2003, Service Pack4. Windows XP Home, Service Pack 25. Windows XP Pro, Service Pack 2网络版本: 对于网络版本,部署ProtectDrive 服务器需要以下环境作为域服务器:1. Windows 2003 Server, Service Pack 12. Windows 2000 Server, Service Pack 42.1 系统兼容性说明磁盘工具在安装PD 后,不允许任何对磁盘的修改大小,重新分配,修改镜像配置等操作。
如果需要做这些操作,请卸载PD 后再操作。
Windows 文件夹压缩PD 允许对文件夹的压缩操作,但PD 安装后的目录“C:\SECUREDISK ”除外。
Windows 系统还原安装PD 之前的系统还原点在PD 安装后就不可以再使用,但PD 安装后的系统还原点可以使用。
XP 快速用户切换:PD 禁止XP 的快速用户切换功能,必须使用CTRL+ALT+DELETE 键登录系统。
地址:北京市海淀区西三环北路100号金玉大厦1603室 - 5 -3 ProtectDrive 安装使用说明3.1 产品的安装3.1.1服务端系统安装1) 点击安装包中的SafeNet ProtectDrive.msi ,程序启动后出现版权申明界面:2)选择典型服务器安装,点击下一步,3) 选择语言,点击下一步4)ProtectDrive Schema 扩展工具将启动,工具将在服务器中安装PD所需要的ADSchema。
5)服务端安装完成。
3.1.2客户端安装:1)点击安装包中的SafeNet ProtectDrive.msi,程序启动后出现版权申明界面:地址:北京市海淀区西三环北路100号金玉大厦1603室 - 6 -2)选择典型客户端安装,点击下一步:3)选择语言,点击下一步4)选择License类型,默认为试用版本,点击下一步:地址:北京市海淀区西三环北路100号金玉大厦1603室 - 7 -地址:北京市海淀区西三环北路100号金玉大厦1603室 - 8 -5) 选择配置类型和密钥产生方法,点击下一步:6) 选择密钥生成的目录,点击下一步注意:不要将钥保存在本地硬盘,可以选择将密钥生成到到先前准备的网络目录或U 盘。
如果放在本地硬盘,注意要做好备份。
7) 如果是新生成密钥的话,晃动鼠标作为随机数种子,待进度条变成绿色,点击OK地址:北京市海淀区西三环北路100号金玉大厦1603室 - 9 -8) 密钥产生完成,点击OK 完成安装。
9) 根据提示完成安装。
3.1.3 卸载ProtectDrive 进入控制面板->添加删除程序选择删除。
系统卸载ProtectDrive ,点击Yes 卸载,卸载完成后点击“是”重新启动计算机完成卸载。
3.2 使用ProtectDrive安装完成后,重新启动计算机,Windows 启动前将会出现认证界面。
如下图:地址:北京市海淀区西三环北路100号金玉大厦1603室 - 10 -注意:如果是单机版本,那么重新启动会直接出现启动前认证界面,使用安装用户的用户名口令,在域栏选择本机,就可以直接进入系统。
如果是网络版本,那么需要重新启动完成安装,并待域策略同步到客户端后,才会出现启动前认证界面,就是说重新启动一次后,必须至进行一次域同步才会在再次启动出现启动前认证界面。
3.2.1保护您的硬盘进入系统后,如果是单机版本,通过菜单进入PD 管理界面,如下图:或者点击右下角任务栏中的有PD 图标来进入PD 管理界面。
在“PD Settings ”属性页中的“Encryption Status ”选项页中选择要保护的分区进行保护:地址:北京市海淀区西三环北路100号金玉大厦1603室 - 11 -选择一个算法后点击确定,系统就会自动开始进行后台加密,不影响电脑上的其他活动。
如果是网络管理,要保护硬盘应该在服务端进行设置,具体操作方法见“ProtectDriveAdministration Guide ” 77页,“Chapter 9 System and User Management ”。
4使用注意事项1)备份必要的数据备份的数据包括:syskey.bin 文件,还有通过安装目录下的 Recovery目录中的工具“backup.exe”备份出来的数据。
使用方法是在安装完PD的机器上直接运行“backup.exe”, PD 会在当前目录下生成一个新目录,备份这个目录。
2)域用户登陆当域用户第一次加入到PD用户中后,域用户并不能直接使用他的用户名/口令登陆PD启动前认证,而需要使用用户名+默认的密码登陆,然后到Windows登陆窗口出现后输入自己的正确口令后,以后就可以正常登陆。
3)移动设备保护移动硬盘受到保护后,如果需要在另外的一台机器上访问这个移动设备,必须保证: 这台机器上安装了ProtectDrive并且安装ProtectDrive使用的Syskey和保护这个移动设备的Yyskey相同访问的时候还需要移动设备的保护口令这些限制在保证了移动设备只能在内部使用的功能。
关于移动设备的备份见“ProtectDrive Administration Guide” P12。
需要下载微软提供的磁盘工具dskprobe.exe恢复见“ProtectDrive Administration Guide” P30。
4)卸载ProtectDrive卸载前一定要先将所有的已经加密的磁盘先进行解密,另外,解密的动作需要待加密100%完成后才能进行。
如果不解密,卸载程序会提示错误。
5)License问题如果License过期,系统在每次登陆的时候会有过期的提示,另外在关于信息里面有License信息的显示,不会影响系统的使用。
6)安装目录和PD需要的数据目录PD安装后,在C盘会有一个PD目录“c:\SECUREDISK”, PD程序安装目录默认是“c:\Program Files\Safenet ProtectDrive”,除非卸载程序,不要手动删除里面的数据。
地址:北京市海淀区西三环北路100号金玉大厦1603室 - 12 -。
