Chapitre 4 RMN solide
新世纪大学英语综合教程4第四册Unit 4

Brainstorming
Directions: What words will occur to you whenever we mention the phrase “choosing a career”. Write down as many words as possible about it.
Operating engineers
Global reading
1 Structure Analysis
2
Table Completion
3
True or False
Structure Analysis
Parts Paras. Main Ideas
The author explains his understanding of work, labor, and play. Whether one is a laborer or a 1~3 worker has little to do with whether he or she is doing a physical or a mental job, but with the attitude he or she takes towards the job he or she does.
1
2
4
In the author’s eyes, the majority of people in a modern technological society are laborers rather than workers. The author stresses the two negative aspects of technology and the division of labor: by eliminating the need for special skills, they turned enjoyable work into boring labor and by increasing productivity, they give people excessive leisure time.
商务英语综合教程第4册Unit

Learn how to create a positive
relationship and establish trust with
international counterparts.
3
Negotiation Techniques
Explore proven strategies and tactics for achieving win-win outcomes in cross-border negotiations.
open dialogue among diverse teams.
3
Building Team Cohesion
Explore strategies for strengthening teamwork and leveraging diversity for innovation and success.
Master the art of effective negotiations in the international business arena.
1
Preparation
Discover the crucial steps to take
Building Rapport
2
before entering into international business negotiations.
Financial Strategies
Discover how global economic factors impact business decisions and learn effective financial management techniques.
Managing Diversity in the Workplace
商务英语综合教程第4册Unit2.ppt

Para 5 Contemporary
Contemporary, contemporaneous, simultaneous, synchronous, concurrent, coincident, concomitant are all synonyms, meaning “existing or occurring at the same time”. 1). Contemporary is used more often of persons, contemporaneous of events and facts.当代的,同时代的,同时期的 e.g. The composer Salieri was contemporary with Mozart. A rise in interest rate is often comtemporaneous with an increase in inflation.
The word “associate” has a number of parts of speech. It is used as a vt in the text. It can also be used as in vi, or a n. or an adj.
1). When used as vi, it, similar to the word “join”, means to join in a form a league. e.g. If his health permits, he will ~ in many important business ventures. As vi, it also means to spend time socially 与某人交往或打交道 e.g. She often ~ with her coworkers on weekends. 2). Used as n., “associate” may mean a person united with another or others in an act, enterprise, or business. Used in this context, it is a synonym to partner or colleague. 同事,伙伴 e.g. He never hangs out with his ~s in the evening. 3). “Associate”, as an adj., means “joined with another or others and having equal or nearly equal status or having partial status or privileges.” (与 某职业或组织)联合的,联盟的,合伙的 e.g. David is an ~ editor of Nature magazine. (副主编,助理编辑) an ~ judge 陪审法官 the ~ producer of a film 联合制片人
MICAPS4帮助文档

目录
0 快速入门手册.........................................................................................................................6 0.1 安装.............................................................................................................................. 6 0.2 快速配置......................................................................................................................6 0.2.1 数据源配置.......................................................................................................6 0.2.2 综合图配置.......................................................................................................7 0.2.3 单站雷达默认配置(工具栏)...................................................................... 9 0.2.4 模式剖面默认配置(工具栏)...................................................................... 9 0.2.5 累积降水默认配置(工具栏).................................................................... 10 0.2.6 表格数据默认配置(工具栏).....................................................................11 0.2.7 模式探空默认配置.........................................................................................11 0.2.8 基础地图信息配置.........................................................................................12 0.2.9 交互层“另存为”保存................................................................................ 13 0.2.10 系统启动配置与出图配置.......................................................................... 14 0.2.11 传真图配置.................................................................................................15
德国工业4.0原版

Intense research activities in universities and other research institutions Drastically increasing number of publications in recent years Large amount of funding by the German government
Model predictive control (MPC)
Modern, optimization-based control technique Successful applications in many industrial fields Can handle hard constraints on states and inputs Optimization of some performance criterion Applicable to nonlinear, MIMO systems
A system is strictly dissipative on a set W ⊆ Z with respect to the supply rate s if there exists a storage function λ such that for all (x , u ) ∈ W it holds that λ(f (x , u )) − λ(x ) ≤ s (x , u ) − ρ(x ) with ρ > 0.
k =0 x (k |t + 1) x (t + 1) state x input u t+1 u (k |t + 1) k =N
Basic MPC scheme
PackEdge4_whats_new

General IntroductionThe editors will be available in a stand-alone version and aclient-server version. The client-server version of the editors will be clients of BackStage server 1.2 or higher.QuickStep is no longer part of this release.PackEdge 4.0 and Plato 4.0 are not compatible with Digi 9.x.The editors will use the CertIn 1.4 PostScript import component with support for PDF1.5 import.The editors will use the OutRight 2.1 technology:•EPS-DCS•PDF for viewing/proofing•PDF 1.5•PDF 1.4•PDF 1.3•PDF for Adobe Illustrator 10OS requirementsWindows 2000 Professional / ServerWindows XP ProfessionalWindows Server 2003, Standard EditionStand-alone versus Client-Server The client-server versions of the editors will be clients ofBackStage 1.2 server or higher.The linework editor with complete interactive functionality will be called PackEdge 4.0. The client-server version of the editor has a limited set of interactive functionality and will be called BackStageEdit 4.0.•The same software build will be used for both products.•Both editor versions are available on the same CD•Service Packs and Maintenance Packs will be shared.•Functional difference between the products will be made by licenses.The Step & Repeat editor, bundled with PackEdge /BackStageEdit 4.0, will be Plato 4.0.•The Plato build is now part of the PackEdge build.•Functional difference between the products will be made by licensesBackStage 2.0 Server integration BackStage 2.0 has introduced the concept of Jobs. The Job concept is a further extension of the Job Folderconcept introduced in BackStage 1.2.If the editor is connected to a BackStage 1.2 server,the Job Folder browsing is still available.If the editor is connected to a BackStage 2.0 server,the Job folder concept is removed and replaced by the Job browser.Searching for a job or file in the BackStage 2.0 framework is done via the Find Job dialog in the Pilot Plus.It is possible to launch …an‟ editor from the BackStage 2.0 PilotPackEdge server log-onTo make PackEdge known to the BackStage server.When there are no other Esko-Graphics applications logged in on the BackStage server.File Selectors and Folder Selectors Job Folder Browsing through the Job Folders of theBackStage 1.2 server (only in server-client mode)Profiles combo box for quick selection of a specificuser’s customised setting•Reminder: a User‟s Customised Settings can contain settings for 1 or more import and export tasks: you will see the same Customised Settings sets in all import/export tasks.Stand-alone versus Client-Server The functional difference between the stand-alone and client-server versions is limited to:Stand-alone Client-serverCertin PostScript / EPS / PDF /Illustrator import runs inforeground in the editor. No PostScript / EPS / PDF / Illustrator import from within the editor. Files have to be imported using the BackStage Pilot.OutRight PostScript / EPS / PDF /Illustrator export runs inforeground in the editor. No PostScript / EPS / PDF / Illustrator export from within the editor. Files have to be exported using the BackStage Pilot.Job Parameters No support for Job Parameters Per job, Job Parameters canbe defined. E.g. Barcode.The barcode menu will beable to pull the barcode JobParameters into the menuServer AwarenessThe Graphic Editors version 4.0 can be used in client-server mode like the current PackEdge 3.0 and Plato 2.0 version. This will be typically the case in aFlexRip/FlexProof environment. Server awarenessincludes the following:•Server awareness of the editors includes use of central data resources (fonts, CMS, DGC, marks, custom data).•Editors login to the server just like the Pilot and Monitor.•File selectors allow job folder browsingExpose to FlexRipThe Expose to FlexRip dialog in the editor has beensyncronized with the FlexRip 5.2 panels with support for:•JobParameters from BackStage 2.0•Dispatcher settings indication in user interface•DynaCell screenings for Expose devices•Separate/Composite output for Proofing devices•Job Options(Anti-Alias, Number of copies) for Proofing devicesExpose to FlexRip JobParametersJob Parameters that are defined in the BackStage Pilot for a specific Job are applied in the user interface of the Expose to FlexRip dialog.These Job Parameters cannot be changed and arehighlighted in the Expose to FlexRip dialogExpose to FlexRip Dispatcher SettingsDispatcher Settings always overrules the Job Parameter settings or ticket options.These Dispatcher Settings cannot be changed and are highlighted in the Expose to FlexRip dialog.Support for Digi 9.xJust to make sure everybody is aware of:PackEdge 4.0 and Plato 4.0 will not be supported inOnRamp configurations.Support for reading old formats (GRA, GRC) is removed from the editor.Support for exporting the file to old formats (GRC) are removed from the editor.Saving files in 9.x compatible format is removed from the editor.LicensingThe Graphic Editors make use of new licenses:•PackEdge 4.0: lpbri4•BackStageEdit 4.0: lbebri4File Selectors and Folder Selectors Job Folder Browsing through the Job Folders of theBackStage 1.2 server (only in server-client mode)Profiles combo box for quick selection of a specificuser’s customised setting•Reminder: a User‟s Customised Settings can contain settings for 1 or more import and export tasks: you will see the same Customised Settings sets in all import/export tasks.CertIn 1.4Same software module for PostScript / EPS / PDF and Illustrator import in PackEdge and Plato 4.0 andBackStage 2.0Features•PDF 1.5 support•Support for PDF 1.5•Through Adobe®library PDF 1.5 to PostScript 3Benefits•Compatibility with the latest Industry standard = Acrobat®6 compatibleOutRight 2.1Same module for PostScript / EPS-DCS / PDF andIllustrator export in PackEdge and Plato 4.0 and BackStage2.0Features•PDF 1.5 export•transparency included in PDF file•Layers supported in the PDF 1.5 file•Metadata (XMP) is supported in the PDF 1.4 and PDF 1.5 fileBenefits of PDF 1.5•Better file exchangeability/Industry compatibility•Production related content of jobs can be extracted from the XMP data, without having to convert the PDF file•Layer support gives immediate feedback about e.g. used die-cuts, trapping layers, SmartMarks etc.Right Mouse click behavior Adapted to the job state, selected object(s) in the document or selected toolToolbarInk densitometer tool•Shortcut (D) to open the densitometer tool while editing •Visualization of Lpi, Angles and ScreeningFileExportExport to VRML, based on ARD files (Option)FileAdapted to the job state or selected toolPlace ARD filesPlace ARD files in a dedicated and locked layerFileAdapted to the job state or selected toolXMP Property infoConsolidated list of document status Are added to the file propertiesMetadata and Adobe®Acrobat®XMP Metadata is added to PDF 1.4 and PDF 1.5 fileCan be viewed with Esko-Graphics‟ plug-in for Adobe®Acrobat®FileAdapted to the job state or selected toolPreferences dialogRe-arrangement into logical groupsUser customizable View modes in editor via View tabViewAdapted to the job state or selected toolZoom to SelectionSelect one or multiple objectsAutomatically zoom to Selected Object(s)ViewAdapted to the job state or selected toolSelectAdapted to the job state or selected toolArrangeAdapted to the job state or selected toolMultiple selected objects•Object with target destination staysMultiple selected objects•Object with target destination staysMultiple selected objects•Object with target destination stays or•Green selected object staysMultiple selected objects•Object with target destination stays •or•Green selected object staysArrangeAdapted to the job state or selected toolHides the selected object(s) Linked with the Object BrowserHide SelectionHide –All BelowHide –All AboveShow AllArrangeAdapted to the job state or selected toolLocks the selected object(s) Linked with the Object BrowserLock SelectionLock –All BelowLock –All Above。
ProE Wildfire 4.0简介及基本操作第一章
第一讲
屏幕、内存硬盘中删除
约束:
截面3要素:2D几何图形、尺寸、约束。
要点:1、一般情况下外轮廓(截面)一定要封闭,也就是起点和终点重合。
外轮廓的路径只能有一条。
2、外轮廓中可以嵌套(包含)内轮廓,内轮廓也必须封
闭,并且内轮廓不能和外轮廓相交,内轮廓也不能和
内轮廓相交。
3、内轮廓中不能再嵌套内轮廓,也就是说只能嵌套1层,
不能有1层以上的嵌套,如果多于1层,会不符合逻
辑。
4、外轮廓和内轮廓中也不能有重复的图元。
草图绘制技巧
虽然Pro /E具有捕捉设计者意图和参数化草绘的优点。
但是在草绘时还是应该注意培养一些好的习惯,以便设计中减少错误,降低工作
量,注意以下几点:
1、绘制尺寸大致符合实际的草图,如果绘制的草图在尺寸和形状上大致准确,那么在添加、修改尺寸和几何约束时,草图就不会发生大的变化。
在绘制完第一、第二个元素(图素)时,建议立即修改尺寸,这样,以后的元素就会与已经修改尺寸的元素有一定的参考关系,后面绘制的元素就不会在尺寸上有大的差异,便于草图的绘制。
2、对于重复简单的几何元素,可以先草绘其中一个元素的草图,如何采用复制或阵列的的方法生成其他部分,这样可以减少草图中的几何元素数量。
3、一次绘制的图形不要过于复杂,不要试图一次完成一张复杂图形的绘制,最好分几步进行。
用单一实体对象的草图比用多个对象的草图更便于以后操作,复杂的几何形状可以由简单的实体对象组合而成。
4、采用夸大画法。
绘制小角度时,可以先绘制一个大角度,然后修改成小角度。
因为小角度线系统会自动认为时水平或垂直,导致你绘不出来。
普斯宾泰汉4跨体 Vereinigung所有器型页面1说明书

Individual optionsTechnical dataStandard optionsVehicle pictures Vehicle informationS-GO 801EP o r s c h e T a y c a n4C r o s s T u r i s m oI m p o r t a n t I n f o r m a t i o nA l t h o u g h t h i s i m a g e i s i n t e n d e d t o r e f l e c t y o u r a c t u a l v e h i c l e c o n f i g u r a t i o n,t h e r e m a y b e s o m e v a r i a t i o n b e t w e e n t h i s p i c t u r e a n d t h e a c t u a l v e h i c l e.S o m e i t e m s s h o w n a r e E u r o p e a n s p e c i f i c a t i o n s.T e c h n i c a l d a t aS i n g l e -S p e e d T r a n s m i s s i o n o n t h e F r o n t A x l e , 2-S p e e d T r a n s m i s s i o n o n t h e R e a r A x l eP o w e r u n i tP o w e r u p t o (k W )280 kW P o w e r u p t o (P S )380 PS P o w e r u p t o (H P ) (o n l y f o r N A R )375 hpO v e r b o o s t P o w e r w i t h L a u n c h C o n t r o l u p t o (k W )350 kW O v e r b o o s t P o w e r w i t h L a u n c h C o n t r o l u p t o (P S )476 PS O v e r b o o s t P o w e r w i t h L a u n c h C o n t r o l u p t o (H P ) (o n l y f o r N A R )469 hpM a x . t o r q u e w i t h L a u n c h C o n t r o l500 NmC o n s u m p t i o n /E m i s s i o n sE l e c t r i c i t y c o n s u m p t i o n c o m b i n e d28.1 kWh/100 kmC o n s u m p t i o n /E m i s s i o n s W L T PE l e c t r i c a l c o n s u m p t i o n l o w (W L T P )21.9 - 19.1 kWh/100 km E l e c t r i c a l c o n s u m p t i o n m e d i u m (W L T P )21.4 - 18.4 kWh/100 km E l e c t r i c a l c o n s u m p t i o n h i g h (W L T P )22.4 - 18.9 kWh/100 km E l e c t r i c a l c o n s u m p t i o n e x t r a -h i g h (W L T P )28.4 - 24.0 kWh/100 km E l e c t r i c a l c o n s u m p t i o n c o m b i n e d (W L T P )26.4 - 22.4 kWh/100 km E l e c t r i c a l c o n s u m p t i o n C i t y (W L T P )21.6 - 18.7 kWh/100 km C O 2-e m i s s i o n c o m b i n e d (W L T P )0 - 0 g/kmR a n g eR a n g e c o m b i n e d (W L T P )389 - 456 km R a n g e C i t y (W L T P )463 - 541 km L o n g -d i s t a n c e r a n g e360 kmC h a r g i n gG r o s s b a t t e r y c a p a c i t y 93.4 kWh N e t b a t t e r y c a p a c i t y83.7 kWh M a x i m u m c h a r g i n g p o w e r w i t h d i r e c t c u r r e n t (D C )270 kW C h a r g i n g t i m e f o r a l t e r n a t i n g c u r r e n t (A C ) w i t h 9.6k W (0 t o u p t o 100%)10.5 h C h a r g i n g t i m e f o r a l t e r n a t i n g c u r r e n t (A C ) w i t h 11k W (0 t o u p t o 100%)9.0 h C h a r g i n g t i m e f o r a l t e r n a t i n g c u r r e n t (A C ) w i t h 22k W (0 t o u p t o 100%)5.0 h C h a r g i n g t i m e f o r d i r e c t c u r r e n t (D C ) w i t h 50k W f o r u p t o 100k m (W L T P )28.5 min C h a r g i n g t i m e f o r d i r e c t c u r r e n t (D C ) w i t h 50k W (5 t o u p t o 80%)93.0 minT e c h n i c a l d a t a (c o n t i n u e d )S i n g l e -S p e e d T r a n s m i s s i o n o n t h e F r o n t A x l e , 2-S p e e d T r a n s m i s s i o n o n t h e R e a r A x l eC h a r g i n g t i m e f o r d i r e c t c u r r e n t (D C ) w i t h m a x i m u m c h a r g i n g p o w e r f o r u p t o 100k m (W L T P )5.25 min C h a r g i n g t i m e f o r d i r e c t c u r r e n t (D C ) w i t h m a x i m u m c h a r g i n g p o w e r (5 t o u p t o 80%)22.5 minB o d yL e n g t h4,974 mm W i d t h1,967 mm W i d t h (w i t h m i r r o r s )2,144 mm H e i g h t 1,409 mm W h e e l b a s e2,904 mm F r o n t t r a c k 1,718 mm R e a r t r a c k1,698 mm U n l a d e n w e i g h t (D I N )2,245 kg U n l a d e n w e i g h t (E U )2,320 kg P e r m i s s i b l e g r o s s w e i g h t 2,885 kg M a x i m u m l o a d640 kg M a x i m u m p e r m i s s i b l e r o o f l o a d w i t h P o r s c h e r o o f t r a n s p o r t s y s t e m75 kgC a p a c i t i e sL u g g a g e c o m p a r t m e n t v o l u m e , f r o n t84 lO p e n l u g g a g e c o m p a r t m e n t v o l u m e (u p t o t h e u p p e r e d g e o f t h e r e a r s e a t s )446 l L a r g e s t l u g g a g e c o m p a r t m e n t v o l u m e (b e h i n d f r o n t s e a t s ,u p t o r o o f )1,212 lP e r f o r m a n c eT o p s p e e d220 km/h A c c e l e r a t i o n 0 - 60 m p h w i t h L a u n c h C o n t r o l4.8 s A c c e l e r a t i o n 0 - 100 k m /h w i t h L a u n c h C o n t r o l5.1 sA c c e l e r a t i o n 0 - 160 k m /h w i t h L a u n c h C o n t r o l 10.1 s A c c e l e r a t i o n 0 - 200 k m /h w i t h L a u n c h C o n t r o l 15.6 s A c c e l e r a t i o n (80-120k m /h ) (50-75 m p h )2.6 sS t a n d a r d o p t i o n sP o w e r u n i t• Porsche E-Performance Powertrain with a Permanent Magnet Synchronous Motor on the Front and Rear Axle • Single-Speed Transmission on the Front Axle• Performance Battery Plus• 2-Speed Transmission on the Rear Axle• Porsche Traction Management (PTM)• Porsche Recuperation Management (PRM)• Sport Mode for the Activation of dynamic Performance Settings including Launch Control• Range Mode for the Activation of efficiency-oriented Settings• Gravel Mode for the Activation of Settings with increased Bad Road CapabilitiesC h a s s i s• Aluminium Double Wishbone Front Axle• Aluminium Multi-Link Rear Axle• Vehicle Stability System Porsche Stability Management (PSM) with ABS and extended Brake Functions • Integrated Porsche 4D Chassis Control• Adaptive Air Suspension including Porsche Active Suspension Management (PASM) and Smart Lift• Increased Ground Clearance in Comparison to Taycan Limousine (+20 mm)• Power SteeringW h e e l s• 19-Inch Taycan Aero Wheels• Wheel Centres with monochrome Porsche Crest• Tyre Pressure Monitoring (TPM)B r a k e s• 6-Piston Aluminium Monobloc fixed Brake Calipers at Front• 4-Piston Aluminium Monobloc fixed Brake Calipers at Rear• Brake Discs internally vented with 360 mm Diameter at Front and 358 mm Diameter at Rear• Brake Calipers painted in Black• Anti-Lock Brake System (ABS)• Electric Parking Brake• Brake Pad Wear Indicator• Auto Hold Function• Multi-Collision BrakeB o d y• Fully galvanised Steel-Aluminium-Hybrid lightweight Bodyshell• Bonnet, Tailgate, Doors, Side Sections and front Wings in Aluminium• Roof in Aluminium, contoured Design (with dynamic Recess Profile)S t a n d a r d o p t i o n s(c o n t i n u e d)• Full-surface aerodynamic Underbody Panelling• Upper Valance with vertical Air Intakes (Air Curtain)• Auto-deploying Door Handles• Side Window Trims in Black• Door Sill Guards in Black• Exterior Mirror Lower Trims including Mirror Base in Black• ‘PORSCHE' Logo in Glass Look integrated into Light Strip• Model Designation on Tailgate in Silver• Wheel Arch Cover in Black• Porsche Active Aerodynamics (PAA) with active Air Intake Flaps• Roof Spoiler painted in Black (high-gloss)• Cross Turismo specific Lower Valance with Inlay painted in Brilliant Silver• Cross Turismo specific Sideskirts in Black with Inlays painted in Brilliant Silver• Cross Turismo specific Rear Diffusor in Louvered Design with Inlay painted in Brilliant SilverL i g h t s a n d v i s i o n• LED headlights• Four-Point LED Daytime Running Lights• Automatic Headlight Activation including ‘Welcome Home’ lighting• Light Strip• Third Brake Light• LED-Innenraumbeleuchtungskonzept: Abschaltverzögerung, Innenleuchte (Dachkonsole) vorne mit Lesespots rechts und links, Auflicht in der Dachkonsole, beleuchteter Make-up-Spiegel in den Sonnenblenden (Fahrer- undBeifahrerseite), Leseleuchten hinten links und rechts, Auflicht in den Leseleuchten, Fußraumleuchte vorne und hinten, Gepäckraumleuchten vorne und hinten, Handschuhkastenleuchte, Türfachbeleuchtung• Automatically dimming Interieur and Exterior Mirrors• Illuminated Vanity Mirror for Driver and Front Passenger• Electrically adjustable and heatable Exterior Mirrors, aspherical on Driver’s Side• Front Wiper System including Rain Sensor and Washer Jets• Rear Wiper including Washer Jet• Heated Rear Screen with "Auto-Off" FunctionA i r c o n d i t i o n i n g a n d g l a z i n g• Advanced Climate Control (2 Zone) with separate Temperature Settings and Air Volume Control for Driver and Front Passenger, automatic Air-Recirculation Mode including Air Quality Sensor as well as comfortable Control of the Airflow via PCM• Parking Pre-Climatisation including Pre-Conditioning of the Battery• Thermally insulated Glass all round• Particle/pollen filter with active carbon filter, traps particles, pollen and odours and thoroughly filters fine dust out of the outside airS t a n d a r d o p t i o n s(c o n t i n u e d)S e a t s• Comfort seats in front (8-way, electric) with electric adjustment of seat height, squab and backrest angle and Fore/Aft position• Integrated Headrests front• Rear Seats with 2 Seats in Single-Seat Look, fold-out Centre Armrest and split-folding Backrests (60:40)S a f e t y a n d s e c u r i t y• Active Bonnet System Note: only in markets with legal requirements• 4 Doors with integrated Side Impact Protection• Bumpers comprising high-strength Cross Members and two Deformation Elements each with two threaded Fixture Points for Towing Eye contained in on-board Tool Kit• Full-size Airbags for Driver and Front Passenger• Knee Airbags for Driver and Front Passenger• Side Airbags in front• Curtain Airbags along entire Roof Frame and Side Windows from the A-Pillar to the C-Pillar• Rollover Detection for Activation of Curtain Airbags and Seat Belt Pretensioners• Three-Point automatic Seat Belts with Pretensioners (front and outer rear Seats) and Force Limiters• Manual Adjustment of Seat Belt Height for Driver and Front Passenger Seats• Seat Belt Warning System for Driver, Front Passenger and Rear Seat System• Immobiliser with Remote Central Locking, Alarm System with radar-based Interior Surveillance• ISOFIX Mounting System for Child Seats on outer Rear SeatsA s s i s t a n c e s y s t e m s• Lane Keeping Assist including Traffic Sign Recognition• Cruise Control including adaptive Speed Limiter• Warn and Brake Assist incl. Pedestrian protection Detects the area ahead of the vehicle. Within the system limitations, an impending frontal collision with other vehicles, pedestrians or cyclists can be detected both in the urban and extra-urban speed range. The system warns the driver visually, acoustically and if necessary through a braking jolt. Where required, the system can support the driver's braking or initiate partial or full deceleration in order to reduce the collision speed or prevent the collision in some circumstances.• ParkAssist (front and rear) with visual and audible Warning• Keyless Drive• Driver Personalisation for Ergonomic, Comfort, Infotainment and Lighting Functions as well as Assistance and Display Systems Note: Country-specific availability• Distance warning If the system detects a safety hazard due to following too close, the system can warn the driver in a vehicle speed range from approx. 65 – 250 km/h (40 – 156 mph) by displaying the symbol on the instrument clusterI n s t r u m e n t s• 16.8-Inch Curved Display - contains up to five different and freely configurable views, depending on the equipment -including external touchscreen control panels for controlling the light and chassis functions• Centre Console with Direct Touch Control - climate settings - opening and closing of the charge port doors - battery level indicator - handwriting panelS t a n d a r d o p t i o n s(c o n t i n u e d)I n t e r i o r• Partial Leather Interior• 'Taycan' Badge in the Centre Console• Accent Package Black• Storage Package Additional storage compartments in vehicle interior: - storage tray below the ascending centre console in front - storage tray on the middle tunnel in rear - net and bag hook in rear luggage compartment• Fabric roof lining• Multifunction Sports Steering Wheel Leather• Centre Console Armrest front with integrated Storage Compartment• Floor Mats• Sun Visors for Driver and Front PassengerA u d i o a n d c o m m u n i c a t i o n• Porsche Communication Management (PCM) including Online Navigation¹ - high-resolution 10.9-Inch touchscreen display in full HD resolution - multi-touch gesture control: for example, you can control the size of the map view with two fingers using the PCM touchscreen display or Direct Touch Control in the handwriting input field in the centre console -mobile phone preparation with Bluetooth® interface for telephone and music - two USB-C connectivity and charge ports in the storage compartment in the centre console, for example for connecting various iPod® and iPhone®models², as well as two USB-C charge ports in the rear - radio with RDS twin-tuner and Diversity for optimum reception - control of vehicle and comfort functions such as charging timers and climate settings - central display of notifications from the vehicle and connected external devices - voice control with natural speech interaction, activation via “Hey Porsche” and multimodal map operation Online navigation¹ with: - maps for most European countries - 3D map display and 3D navigation map supporting city³ and terrain models with satellite image overlay - dynamic route calculation with online real-time traffic and route monitor for a clear overview of charging stops and traffic conditions Note: ¹ requires Porsche Connect ² for information on compatibility with the latest iPod® and iPhone® models, please contact your Porsche Centre ³ not available in all cities• LTE Communication Module with embedded SIM Card, Internet Access and Smartphone Compartment including Inductive Charging (Qi Standard)• Porsche Connect with Apple® CarPlay - online navigation (see Porsche Communication Management) - musicstreaming and online radio - Remote Services - E-mobility services including charge management, control of vehicle parking pre-climatisation or range management - a wide range of other Porsche Connect Services Note: Porsche Connect includes a free subscription period of 36 months. The full range of Porsche Connect services or individual services thereof may not be available in some countries. An integrated LTE-enabled SIM card with data allowance for use of selected Porsche Connect services will be included in some countries. For use of the WiFi hotspot via the integrated, LTE-enabled SIM card, in some of these countries a data package is available to purchase from thePorsche Connect Store. For further information on free subscription periods, follow-on costs and availability ofindividual services in your country, please visit /connect or consult your Porsche Centre.• 2 USB-C Connectivity and Charge Ports in the Storage Compartment in the Centre Console• 2 USB-C Charge Ports in the Rear• Sound Package Plus with 10 Speakers and a total Output of 150 Watts• Digital Radio Note: Standard EU 28S t a n d a r d o p t i o n s(c o n t i n u e d)L u g g a g e c o m p a r t m e n t• Luggage Compartment front and rear• Automatic Tailgate• Tailgate Button• Storage Compartments - glove compartment - storage compartment in the front centre console - storage tray below the ascending centre console in front - storage tray between the rear seats - storage tray on the middle tunnel in rear -storage compartments in the doors front and rear - storage compartments in the sides of the rear luggage compartment and luggage compartment recess - net and two fastener straps in rear luggage compartment - bag hooks in rear luggage compartment• 12 V Electrical Socket in Storage Compartment in the Centre Console• 12 V Electrical Socket in Luggage Compartment rear• Two integrated Cupholders front and rear• Clothes Hook at B-Pillars on Driver's and Passenger's Side• Functional Luggage Compartment Cover, foldableC o l o u r s• Solid Paint Exterior Colours - White (0Q) - Black (A1)E-P e r f o r m a n c e• Charge Port on Driver and Front Passenger Side• On-Board AC-Charger with 11 kW for Alternating Current (AC)• On-Board DC-Charger with up to 150 kW for Direct Current (DC) at public Charging Stations with a Voltage of 400 V • Charging with Direct Current (DC) at public Charging Stations with a Voltage of 800 V• Mobile Charger Plus (11 kW) for charging at household and industrial electrical outlets. Compatible with the Home Energy Manager. 4.5 m cable• Supply Cable for Domestic Electrical Socket• Supply Cable for Red Industrial Electrical Outlet (400 V, 32 A, 5 Pin)I n d i v i d u a l o p t i o n sO r d e r n o.M o d e l y e a r V e h i c l eY1BBD12021Taycan 4 Cross TurismoI n d i v i d u a l i s a t i o nC a t e g o r y O r d e r n o.I n d i v i d u a l e q u i p m e n tExterior Colour R7Neptune BlueInterior Colour QA Two-Tone Leather-Free Interior,Black/Slate GreyEquipment Packages2JZ Offroad Design Package incl. Inlayspainted in Black (high-gloss) Exterior3S2Roof Rails in Black Aluminium6XV Electric folding Exterior Mirrors6FJ Exterior Mirror Lower Trims painted inExterior Colour including Mirror Basepainted in Black (high-gloss) PorscheExclusive ManufakturQJ4Side Window Trims in Black (high-gloss)6JA Door Release Levers painted in Black(high-gloss) Porsche Exclusive ManufakturNG1Preliminary Setup for Rear Bike Carrier Drive train / Chassis G1X Single-Speed Transmission on the FrontAxle, 2-Speed Transmission on the RearAxleGM3Porsche Electric Sport SoundGH3Porsche Torque Vectoring Plus (PTVPlus)8LC Sport Chrono Package includingCompass Display on Dashboard1LZ Porsche Surface Coated Brake (PSCB),Brake Calipers with White Finish0N5Rear-Axle Steering including PowerSteering PlusWheels53Y20-Inch Taycan Turbo Aero DesignWheelsWheel Accessories1G8Tyre Sealing Compound and Electric AirCompressorLights and vision4L6Automatically Dimming Interieur andExterior Mirrors3FG Panoramic Roof, fixedVW6Thermally and Noise insulated Glassincluding Privacy GlassComfort and assistance systems KA6ParkAssist including Surround ViewP49Adaptive Cruise Control4F2Comfort AccessInterior KH5Advanced Climate Control (4-Zone)I n d i v i d u a l i s a t i o n(c o n t i n u e d)C a t e g o r y O r d e r n o.I n d i v i d u a l e q u i p m e n t2V4Ioniser3L4Driver Memory PackageQQ1Ambient LightingQ1G Comfort Seats in Front (8-Way, electric)4A3Seat Heating (front)4X4Side Airbags in Rear CompartmentGT5Accent Package DarksilverInterior Race-Tex6NC Roof Lining Race-TexInterior Carbon5MH Carbon matt Interior Package2PS Steering Wheel Trim Carbon matt andSteering Wheel Rim Race-Tex includingSteering Wheel Heating (i.c.w. SportChrono Package and Leather-freeInterior) Porsche Exclusive Manufaktur7M8Door Sill Guards Carbon matt, illuminatedPorsche Exclusive ManufakturAudio / Comm.JH1Passenger DisplayE-Performance2W9Electric Charging CoverKB4On-Board AC-Charger with 22 kW9M3Heat PumpQW5Porsche Intelligent Range ManagerNW2Mobile Charger ConnectEH2Cable Connection between Control Unitand Vehicle: 7.5m76H Charging Cable (Mode 3)Y o u r P o r s c h e C o d e /PM6YI6M5I m p o r t a n t i n f o r m a t i o nThe models illustrated show equipment for the Federal Republic of Germany. For example they also include special equipment which is not supplied as standard and is only obtainable for an additional charge. Not all models are available in every country as there may be regulations and orders which are country-specific. Please obtain information about the models available through your Porsche dealer or importer. We reserve the right to change design, equipment and delivery specifications as well as vary colours.。
PRO E 命令中英文对照表

9636PRO/E命令中英文对照表XIAO修改:Modify 简化表示:Simplfd Rep再生:Regenerate 关系:Relations族表:Family 声明:Declare设置:Set Up 剖截面:X-section程序:Program 集成:Integrate创建:Create 陈列:Pattern复制:Copy 删除:Delete组:Group 压缩:Suppress恢复:Resume 重新排序:Reorder只读:Read Only 重定义:Redefine重定次序:Reroute 镜像几何:Mirror Geom插入模式:Insert Mode 实体:Solid曲面:Surface 修饰:Cosmetic用户定义:User Defined 造型:Style数据共享:Data Sharing 孔:Hole轴肩:Shaft 倒圆角:Round倒角:Chamfer 内部减材料:Slot切减材料:Cut 加材料:Protrusion退刀槽:Neck 凸橼:Flange筋:Rib 求交:Intersect方向:Direction 壳:Shell管道:Pipe 扭曲:Tweak完成/返回:Done/Return 拉伸:Extrude旋转:Revolve 扫描:Sweep混合:Blend 使用面组:Use Quilt高级:Advanced 薄板:Thin单/双侧:One Side/Both Sides 深度:Depth属性:Attributes 平整:Flat偏距:Offset 通过裁剪复制:Copy by Trim 开放/封闭终点:Open/Capped Ends 移动:Move相同参考:Same Refs 特征:Feature从属:Dependent 选取:Select独立:Independent 层:Layer围:Range 局部组:Local Group替换:Replace 撤消组:Ungroup基准/轴:Datum/Axis 尺寸:Dimension线型值:Line Style 草绘:Sketch螺纹:Thread 凹槽:Groove拔模:Draft 局部拉伸:Local Push半径圆顶:Radius Dome 截面圆盖:Section Dome耳:Ear 唇:Lip曲面片:Patch 环形折弯:ToroidalBend样条折弯:Spinal Bend 自由生成:Free Form拔模偏距:Draft Offset 扁平面组:Flatten Quilt实体折弯:Solid Bend 钣金件:Sheet Metal \查询选取:Query Sel 菜单选取:Sel By Menu法向:Normal 无关系特征:Unrelated显示设计:Show Design 编辑设计:Edit Design材料:Material 精度:Accuracy单位:Units 密度:Density参数:Parameters 注释:Notes质量属性:Mass Props 尺寸边界:Dim Bound收缩:Shrinkage 几何形状公差:Geom Tol网格:Grid 曲面光洁度:Surf Finish参照控制:Ref Control 公差设置:Tol Setup★元件:Component 重新构建:Restructure机械:Mechanism 设计管理:Design Mgr分解:ExplodeState 装配:Assemble自由放置:Package◆视图:Views 页面:Sheets 表:Table工具:Tools 表示:Represent绘图模型:Dwg Models 一般:General辅助:Auxiliary 投影:Projection详细视图:Detailed 图形:Graph半/全视图:Half /Full View 破断图:Broken View部分视图:Partial 透视:Perspective比例:Scale 增加项目:Add Items 拭除:Erase 覆盖:Overlay合并:Merge 表格:Table平移:Translate 伸展:Stretch整理尺寸:Clean Dims 分割:Divide*Split经过点:Thru Points 印贴:Formed复合:Composite 从方程:From Equation \可变截面扫描:Var Sec Swp 扫描混合:Swept Blend螺旋扫描:Helical Swp 边界:Boundaries相切曲面:Tangent To Srf 混合曲面:Blended Surf 圆锥曲面:Conic Surf N-侧曲面:N Sided Surf逼近混合:Approx Blend 点/顶点:Point /Vertex轴心方向:Pivot Dir 垂直于轨迹:Norm To Traj垂直于原始轨迹:Norm To Origin Traj 工件:Workpiece分类:Catalog 隐含:Suppress重定路径:Reroute 分型面:Parting Surf模具布局:Mold Layout 模具体积块:Mold Volume设定开模:Mold Opening 着色:Shade型腔组件:Ref Model 侧影像:Silhouette流道:Runner 水线:Water line顶针孔:EJ pin Holes 从文件:From File文档已经阅读完毕,请返回上一页!。
iphone4越狱后的美化_让你感受越狱的强大
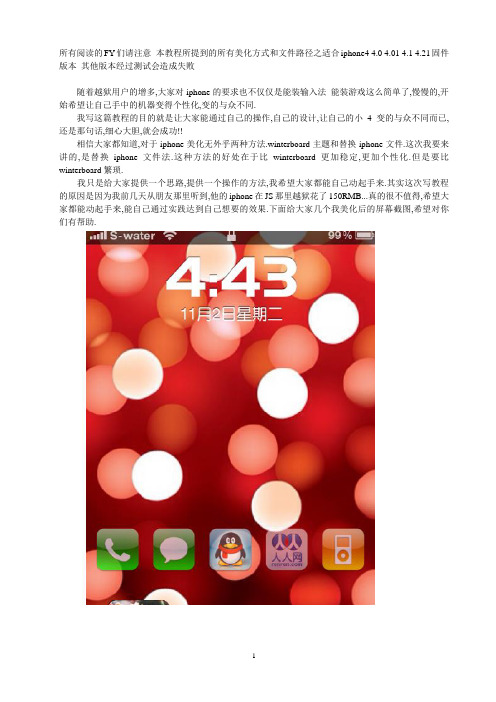
所有阅读的FY们请注意本教程所提到的所有美化方式和文件路径之适合iphone4 4.0 4.01 4.1 4.21固件版本其他版本经过测试会造成失败随着越狱用户的增多,大家对iphone的要求也不仅仅是能装输入法能装游戏这么简单了,慢慢的,开始希望让自己手中的机器变得个性化,变的与众不同.我写这篇教程的目的就是让大家能通过自己的操作,自己的设计,让自己的小4变的与众不同而已,还是那句话,细心大胆,就会成功!!相信大家都知道,对于iphone美化无外乎两种方法.winterboard主题和替换iphone文件.这次我要来讲的,是替换iphone文件法.这种方法的好处在于比winterboard更加稳定,更加个性化.但是要比winterboard繁琐.我只是给大家提供一个思路,提供一个操作的方法,我希望大家都能自己动起手来.其实这次写教程的原因是因为我前几天从朋友那里听到,他的iphone在JS那里越狱花了150RMB...真的很不值得,希望大家都能动起手来,能自己通过实践达到自己想要的效果.下面给大家几个我美化后的屏幕截图,希望对你们有帮助.首先要说的是美化的原理,在坛子里面很多FY也发布了一些美化自己iphone的方法,但是都并没有提到为什么这样做能达到美化的目的.那么下面我就来说说. IOS操作系统界面上显示所有的图标,背景都是从我们iphone机身固件里面调用出来的.也就是说,每个文件都有自己不同的名字,那么IOS会把它们调用,并放在不同的地方.很简单的例子,比如滑块文件IOS默认的是去XXX目录找寻XX 文件,找到之后调用出来之后在锁屏上显示.那么如果我们把XX文件替换为我们想要的文件,IOS就会调用那个我们替换的文件,这样,我们就能达到美化的目的.(不知道这样说大家能否能听懂,呼呼,不管了,废话不多说,开始介入正题)第一步:锁屏美化简介:锁屏美化基本上需要四小步骤1.滑块文件更改(通过更改滑块文件改变古板的解锁滑块)2.滑块背景清除(清除滑块后面半透明的背景,让我们设置的q1an9纸更好的展现)3.滑块提示标语修改(把死板的”移动滑块解锁”更改为一些我们想要表达的文字)4.时间背景清除(清除时间后面半透明的背景,让我们设置的q1an9纸更好的展现) Step.1滑块文件更改使用iFunBox或者91手机助手的文件管理打开/System/Library/PrivateFrameworks/TelephonyUI.framework文件件.(个人推荐使用91手机助手,因为可以直接复制上面的路径达到直接进入文件夹的目的,ifunbox比较繁琐,需要自己手动找)找到一下8个文件全部复制到电脑作为备份保存起来,这8个文件是在不同状态下的滑块解锁图标的源文件(有些朋友说可以直接把@2x后缀的文件删除.我尝试过,的确不影响使用,但是我不建议大家删除.原因是,它既然存在,就会有存在的道理.所以全部拷贝出来就可以了.)bottombarknobgray.pngbottombarknobgrayT.pngbottombarknobgreen.pngbottombarknobred.pngbottombarknobredT.pngbottombarknobgray.pngbottombarknobgrayT.pngbottombarknobgreen.pngbottombarknobred.pngbottombarknobredT.png重命名之后,就可以把这8个文件全部拷贝到以下文件夹,如果提示是否覆盖,选择全部覆盖(这里要注意的是,为了保证不出问题,文件权限改为777)/System/Library/PrivateFrameworks/TelephonyUI.framework复制完毕,从新启动手机,再看看,是不是滑块已经变成了你自己喜欢的样子?呵呵…Step.2滑块背景清除更换好滑块之后,清除滑块背景就相对容易的多,只需要将附件中的” 解锁滑块透明.rar”文件中的三个文件替换到以下目录即可,当然咯,不要忘记从新启动手机和更改权限同样,还是777/System/Library/PrivateFrameworks/TelephonyUI.frameworkStep.3滑块提示标语修改滑块提示标语修改要注意的是不要写过多的字,因为这样会造成文字溢出的情况出现,请大家注意.滑块提示标语修改的方法是利用91记事本打开/System/Library/CoreServices/SpringBoard.app/zh_CN.lproj文件夹下的SpringBoard文件,并找到<key>AWAY_LOCK_LABEL</key>下面的那行,将<string>XXXX</string>中间的XXXX更改为你想更改的文字,默认应该是” 移动滑块解锁” 修改完毕之后别忘记从新启动哦…PS.在这里要提一下的是,如果有朋友使用的不是中文语言,那么就要找到自己那个语言的文件夹,当然文件还是相同的,不知道大家能否明白.举例说明吧zh_CN.lproj文件夹下,所储存的是在简体中文语言下的一些数据文件. English.lproj文件夹下,所存储的是在英文下的一些数据文件. Italian.lproj文件夹下,所储存的是在意大利语下的一些数据文件.不知道这样表达,大家是否能理解.Step.4时间背景清除时间背景清除的方法和以上方法没有太大的出入,无非还是打开一些文件夹,删除或者替换某些文件而已,呼呼…那么是什么文件夹呢?就是它了!/System/Library/PrivateFrameworks/TelephonyUI.framework删除以下三个文件之后从新启动,时间背景就透明咯…BarLCD.pngBarLCD_T.png至此,锁屏基本美化已经结束!!~哈哈…辛苦辛苦!~~第二步:字体美化简介:目前我们用到的字体美化是有两个步骤1. 日常操作界面上的字体文件.2. 锁屏时,时间显示的字体文件Step.1 日常操作界面字体替换将我们需要替换的字体文件复制到/System/Library/Fonts/Cache即可复制时会提示我们是否覆盖,当然选择是咯.如果提示权限,644Step.2 锁屏时间字体替换同Step.1一样, 将我们需要替换的字体文件复制到/System/Library/Fonts/Cache即可复制时会提示我们是否覆盖,当然选择是咯.如果提示权限,644从新启动手机,至此.字体替换完毕.先看看大家的反应吧,如果有时间的话,我还会继续写下去,谢谢大家对我的支持!!!-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------从单位回来,认真的从第一页读到最后一页,每个朋友的留言我都仔细看过.首先,要感谢那些支持这个文章的人,有了你们,才会有更多人能看到这篇文章.谢谢大家!!!~大家的留言引发了我对iphone的思考,敢问,每个FY为什么要选择iphone?够炫?够高档?能引来旁人羡慕的目光?还是单纯为了自己的喜爱,喜爱它的功能,喜爱它的风格?或者其他..如果您给出的答案是前几种,那好...您不需要美化.这样大家更能认知出您使用的是时下"最流行"的iphone4!!~我不明白,为什么有那么多人说修改美化过后,我们的iphone看起来像没仿好的山寨??试问,您到底使用iphone是为了什么.这点我很不理解...就算我们手中的爱机被认为是山寨.那又如何呢?从写越狱教程开始,到现在的美化教程,总有很多FY 发表出很多让我理解不了的言论.山寨?!呵呵...我想说,我只是想通过教程让大家体会到自己动手的过程,你们可能理解不了自己修改成功之后的喜悦,也理解不了自己解决一些教程没有提到问题成功时的成就感.从moto到nokia到apple.我可以说所有我使用过能折腾的手机,都会被我折腾一番.我自认为那是乐趣.也许....你们体会不到吧.我希望一些FY如果看到我的教程感觉美化出来像山寨的话,那么就不要再留言了.我很明确的告诉你,我不爱听!!!!手里拿iphone4就很NB?恐怕别人认为你是山寨?呵呵.....。
AN-B-003_DA14580 Software Patching over the Air(SPOTA)

Company confidentialApplication noteDA14580 Software Patching overthe Air (SPOTA)AN-B-003AbstractThe DA14580 is intended for Bluetooth applications that have a duty cycle during which the system only briefly transmits data and is in deep sleep mode for most of the time. The DA14580 contains embedded SW in the ROM (Bluetooth Smart protocol functions) and the One-Time-Programmable (OTP) memory (Bluetooth Smart profile and application). Amending this code on a small or large scale can be quite a challenge. The system based on the DA14580 might not be accessible in the field. Moreover, even if the system is accessible, a special procedure and infrastructure are required to make software patches (see Application Note AN-B-002). This application note describes a method that allows a software patch to be applied to an existing system over the air.ContentsContents (2)Figures (2)Tables (3)1 Terms and definitions (4)2 References (4)3 Introduction (5)4 SPOTA profile architecture (5)4.1Configuration (5)4.1.1Roles (5)4.2Services and attributes (5)4.2.1SPOTA_MEM_DEV (8)4.2.2SPOTA_GPIO_MAP (9)SPOTA_MEM_INFO (9)4.2.34.2.4SPOTA_PATCH_LEN (10)4.2.5SPOTA_PATCH_DATA (10)4.2.6SPOTA_SERV_STATUS (10)5 ROM functions (11)6 SPotA flow (13)7 SUotA flow (14)8 UUIDs (15)9 Revision history (16)FiguresFigure 1: SPOTA flow diagram (13)Figure 2: SUOTA flow diagram (14)TablesTable 1: SPOTA attributes database (5)Table 2: SPOTA_MEM_DEV definition for SPOTA mode (8)Table 3: SPOTA_MEM_DEV definition for SUOTA mode (8)Table 4: SPOTA_GPIO_MAP definition (9)Table 5: SPOTA_MEM_INFO definition (9)Table 6: SPOTA_SERV_STATUS definition (10)Table 7: GATT CLIENT CHAR CFG definition (11)Table 8: Get_Patching_SPOTA_Length function (11)Table 9: Exec_Patching_SPOTA function (12)Table 10: Proprietary Characteristics UUIDs (15)1 Terms and definitionsEEPROM Electrically Erasable Programmable Read Only MemoryGPIO General Purpose Input OutputJTAG Joint Test Action Group (test interface)MTU Maximum Transmission UnitOTP One Time Programmable (memory)(S)RAM (Static) Random Access MemoryROM Read Only MemorySPOTA Software Patching Over The AirSW SoftWareUART Universal Asynchronous Receiver TransmitterUUID Universal Unique ID2 References1. DA14580 Datasheet, Dialog Semiconductor2. AN-B-002, DA14580 Application and ROM code patching, Dialog Semiconductor3 IntroductionThe DA14580 is capable of executing SW patches that vary regarding the target device to be amended as well as the level of changes to be implemented. A patch can just change a single SW variable value in the code which resides in the SRAM. It can also change a instruction or data value read from the ROM used for the protocol realization. Furthermore, a patch can generate an exception and guide the Program Counter to a new function bypassing the existing one. This is quite a flexible mechanism that allows radically changing code or replacing parameter values with a granularity of a single byte.The programming of patches requires physical access to the system based on the DA14580 (using a JTAG or UART interface) and manually programming the OTP with the patch code, i.e. a sequence of steps that requires the system to be carried into the lab. A proprietary profile enables SW patching over the air. Patching code is downloaded using the Bluetooth Smart link, stored in the internal RAM or an external non-volatile memory and eventually executed as described in AN-B-002.There are certain constraints with respect to the physical storage of the patching code. Furthermore, the system should be aware of the patching storage configuration in advance. Software Patching over the Air (SPOTA) is described in this document in adequate detail for application developers.4 SPOTA profile architecture4.1Configuration4.1.1RolesThe SPOTA profile defines two roles:●SPOTA Initiator: the endpoint that transmits the patch payload.●SPOTA Receiver: the endpoint that receives and applies the patch payload.4.2Services and attributesThe SPOTA profile realises a single service with a number of characteristics required to be written by the initiator. The overall attributes database structure is shown in Table 1 below.Table 1: SPOTA attributes databaseThe SPOTA profile defines one service only (yellow) and six characteristics (light blue). Their values are described in the rows following each characteristic. The profile is described in general by the following fields:●Handle: A pointer to the structure describing the characteristic.●Type: Each type is defined by the Universal Unique ID (UUID) number and the description.Custom UUIDs are 128 bits long.●The Value of the specific Service/Characteristic.●The GATT Server Permissions. Defines if the characteristic’s value can be read or wr itten bythe Client.Each characteristic value is followed by a protocol defined GATT_CHAR_USER_DESCRIPTION, which basically prints a text message for user notification. The characteristics of the profile have a UUID which is designated by ‘UUID_x’ within Table 1 and are described in detail in the following sections.4.2.1SPOTA_MEM_DEVThis characteristic defines the actual physical devices where the Patch will be stored upon reception over the air. It must be written by the SPOTA Initiator and contains 4 bytes. The encoding of these bytes depends on whether the SPOTA service is used in SPOTA mode or SUOTA mode.The encoding of SPOTA_MEM_DEV in SPOTA mode is defined in Table 2. The encoding of SPOTA_MEM_DEV in SUOTA mode is defined in Table 3.Table 2: SPOTA_MEM_DEV definition for SPOTA modeNote 1 Any valid Byte 3 value will enable or disable (Byte 3 = 0xFF) the SPOTA mode of the system accordingly. During SPOTA mode, Extended or Deep Sleep modes are disabled.Note 2 Only SPI FLASH devices need 3 bytes for the address. I2C EEPROMs only need 2 bytes.Table 3: SPOTA_MEM_DEV definition for SUOTA modeSPOTA_GPIO_MAP4.2.2This characteristic defines the mapping of the interfaces on various GPIO pins. It is defined by the SPOTA Initiator so that the system knows which pins are connected to the external Non Volatile memory. The reason of the Initiator instructing the Receiver of the GPIO mapping is that the low level functions, that will take care of storing and executing the patch, reside in the ROM and are totally configurable. This characteristic contains 4 bytes. The meaning of each byte is shown in Table 4.Table 4: SPOTA_GPIO_MAP definitionEvery byte clearly indicates which I/O pin is used for the specific interface signal. Bits[3:0] defines the Pin Number while Bits[7:4] defines the Port Number. For example, a byte value of 0x26 means that the specific interface signal (e.g. MOSI) is mapped on Port 2 and pin 6 (i.e. P2_6).4.2.3SPOTA_MEM_INFOThis characteristic provides information to the SPOTA Initiator about the already applied number of Patches as well as the overall Patch area length as a number of 32-bit words. It can be read by the Initiator and contains 4 bytes which are described in the table below:Table 5: SPOTA_MEM_INFO definition4.2.4SPOTA_PATCH_LENThis characteristic defines the length of the new Patch which is to be applied during the current SPOTA session. It must be written by the Initiator to the Receiver and contains 2 bytes. The length is defined by this value in bytes.In case of SUOTA, it defines the block length of image data to be sent at a time. This length must be greater than 64 bytes, which is the size of the image header, and should be a multiple of 20 bytes, which is the MTU of each data block sent over the BLE link. Also, the length should not be larger than the SRAM buffer in the Receiver implementation, which stores the image data received over the BLE link before burning it into the non-volatile memory.Note: The length value should be 32-bit word aligned (multiple of 4 bytes).4.2.5SPOTA_PATCH_DATAThis characteristic contains 20 bytes which represent the actual Patch payload data. This data is written by the Initiator to the Receiver. The Initiator should send the data in the following order:●Most significant word first●Least significant byte first.For example, when the patching data are 0x00077000, 0x12345678, the Initiator should send:0x00, 0x70, 0x07, 0x00, 0x78, 0x56, 0x34, 0x12.4.2.6SPOTA_SERV_STATUSThis characteristic has two attributes. The first attribute is the service status indicator, which is read-only and consists of 1 byte. The second attribute is the protocol defined GATT_CLIENT_CHAR_CFG which can be written, consists of 2 bytes and enables the service status to be sent as an indication or a notification.The attribute values are explained in the following tables.Table 6: SPOTA_SERV_STATUS definitionTable 7: GATT CLIENT CHAR CFG definitionThe difference between notification and indication is that the indication requires an acknowledgement from the Client. For further information please refer to the BLE specification (Vol. 3, Part G, Sections4.10 and 4.11).5 ROM functionsThis section describes the low level firmware functions used for the implementation of the SPOTA flow. These functions are stored in the ROM and can be called from the application if SPOTA is supported by the final product. The functions are presented in the following tables.Table 8: Get_Patching_SPOTA_Length functionExample:WORD get_patching_spota_length (0x020000F0, 0xA2A12225) is translated as follows:●Memory Device: 0x02, i.e. an external I2C EEPROM●Patch Base Address: 0xF0, i.e. Patches are placed from this address onwards.●Device Address: 0xA2A1.●SCL location: 0x22, i.e. P2_2.●SDA location: 0x25, i.e. P2_5.Table 9: Exec_Patching_SPOTA functionExample:VOID exec_patching_spota (0x020000F0, 0xA2A12225, *buffer, 0x000A); is translated as follows: ●Memory Device: 0x02, i.e. an external I2C EEPROM.●Patch Base Address: 0xF0, i.e. Patches will be placed at this address onwards.●Device Address: 0xA2A1.●SCL location: 0x22, i.e. P2_2.●SDA location: 0x25, i.e. P2_5●*buffer: points to the buffer where the Patch will be fetched in the System RAM before beingexecuted.●Patch Length: 0x000A, i.e. 10 32-bit words. This is the Patch size including the Patch Header andthe Patch Payload.For further information on the structure of a Patch Area as well as the execution of the patch, please refer to Application Note AN-B-002 (see Ref. [2]).6 SPotA flowThe process of the SPOTA flow is illustrated in the following flow diagram:Figure 1: SPOTA flow diagramSPOTA InitiatorSPOTA ReceiverADV_INDCONN_IND GATTWriteCharValue(SPOTA_MEM_DEV)Receiver advertises the SPOTAserviceInitiator sets up theconnectionInitiator defines the Memory and the Patch Base AddressACKInitiator defines the mappingof the signal on GPIOsACKGATTWriteCharValue(SPOTA_GPIO_MAP)GATTReadCharValue(SPOTA_MEM_INFO)Initiator requests for the current #of the Patches and the entirePatch sizeReceiver calls for theget_patching_spota_lenght()4 Bytes of DataThe overall size of the applied patches is returned as well as the number of PatchesGATTWriteCharValue(SPOTA_PATCH_LEN )Receiver stores the transmitted Length in atemporary variableACKInitiator defines the length of thePatch to be appliedInitiator transmits the data required for the PatchGATTWriteCharValue(SPOTA_PATCH_DATA) ACKGATTReadCharValue(SPOTA_MEM_INFO )Receiver stores the transmitted data in atemporary buffer in SRAMReceiver reads the Error flagsInitiator requests for status update on the SPOTA service4 Byte of DataAnswers with status valueAs soon all the data have been gatheredreceiver calls for theexec_patching_spata()7 SUotA flowThe process of the SUOTA flow is illustrated in the following flow diagram:Figure 2: SUOTA flow diagramSUOTA InitiatorSUOTA ReceiverADV_INDCONN_INDGATTWriteCharValue(SPOTA_MEM_DEV) Receiver advertises the SUOTAserviceInitiator sets up the connectionInitiator defines the Memorytype (SPI or EEPROM) and the bank selectionACKInitiator defines the mappingof the signal on GPIOsACKGATTWriteCharValue(SPOTA_GPIO_MAP)GATTWriteCharValue(SPOTA_PATCH_LEN) Initiator defines the length of theBlock size to be appliedACKReceiver stores the transmitted Length in atemporary variableGATTWriteNoResp (SPOTA_PATCH_DATA) Notification(SPOTA_SERV_STATUS=OK)GATTReadCharValue(SPOTA_MEM_INFO)Total number of received bytesInitiator requests the total number of bytes receivedby receiver4 Bytes of DataGATTWriteNoResp (SPOTA_PATCH_DATA) Write block in NV MemoryWrite block in 20-bytes chunks (last chunk may contain less than 20 bytes)Block TransferGATTWriteCharValue(SPOTA_PATCH_LEN)Initiator defines the length of the Last Block size (if different)to be appliedACKGATTWriteNoResp (SPOTA_PATCH_DATA) GATTWriteNoResp (SPOTA_PATCH_DATA) Notification(SPOTA_SERV_STATUS=OK)GATTWriteCharValue(SPOTA_MEM_DEV) Notification(SPOTA_SERV_STATUS=OK) GATTWriteCharValue(SPOTA_MEM_DEV) End of transfer (0xFE000000)System Reboot CommandDevice resetReceiver verifies image checksum and writes image headerReceiver stores the new block sizeWrite block in NV MemoryBlock Transfer8 UUIDsThe random 128-bit UUIDs assigned to the characteristics are summarised in Table 10: Table 10: Proprietary Characteristics UUIDs9 Revision historyStatus definitionsDisclaimerInformation in this document is believed to be accurate and reliable. However, Dialog Semiconductor does not give any representations or warranties, expressed or implied, as to the accuracy or completeness of such information. Dialog Semiconductor furthermore takes no responsibility whatsoever for the content in this document if provided by any information source outside of Dialog Semiconductor.Dialog Semiconductor reserves the right to change without notice the information published in this document, including without limitation the specification and the design of the related semiconductor products, software and applications.Applications, software, and semiconductor products described in this document are for illustrative purposes only. Dialog Semiconductor makes no representation or warranty that such applications, software and semiconductor products will be suitable for the specified use without further testing or modification. Unless otherwise agreed in writing, such testing or modification is the sole responsibility of the customer and Dialog Semiconductor excludes all liability in this respect. Customer notes that nothing in this document may be construed as a license for customer to use the Dialog Semiconductor products, software and applications referred to in this document. Such license must be separately sought by customer with Dialog Semiconductor.All use of Dialog Semiconductor products, software and applications referred to in this document are subject to Dialog Semiconductor’s Standard Terms and Conditions of Sale, unless otherwise stated.© Dialog Semiconductor GmbH. All rights reserved.RoHS ComplianceDialog Semiconductor complies to European Directive 2001/95/EC and from 2 January 2013 onwards to European Directive 2011/65/EU concerning Restriction of Hazardous Substances (RoHS/RoHS2).Dialog Semiconductor’s statement on RoHS can be found on the customer portal https:///. RoHS certificates from our suppliers are available on request.Contacting Dialog SemiconductorGermany Headquarters Dialog Semiconductor GmbH Phone: +49 7021 805-0United KingdomDialog Semiconductor (UK) Ltd Phone: +44 1793 757700The NetherlandsDialog Semiconductor B.V. Phone: +31 73 640 8822 North AmericaDialog Semiconductor Inc.Phone: +1 408 845 8500JapanDialog Semiconductor K. K.Phone: +81 3 5425 4567TaiwanDialog Semiconductor TaiwanPhone: +886 281 786 222SingaporeDialog Semiconductor SingaporePhone: +65 64 849929ChinaDialog Semiconductor ChinaPhone: +86 21 5178 2561KoreaDialog Semiconductor KoreaPhone: +82 2 3469 8291Email: Web site:。
R.P.S. Corporation 34 产品系列说明书
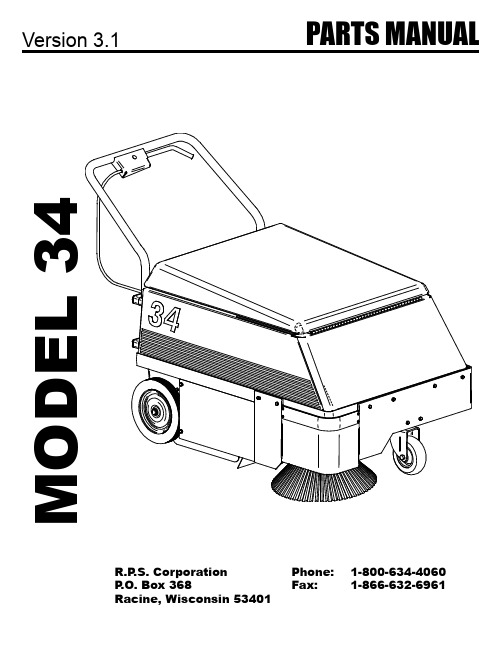
3
4 18
16
17
SIDE BROOM MOTOR ASSY P/N 4-425
34 Parts Manual V3.1
Item
Part No.
1
4-111
2
4-113
3
4-220
4
4-223
5
4-376
6
4-378
7
4-381
8
4-385
9
4-386
10
4-402
11
4-404
12
4-436
13
Description MAIN BODY R. INNER SIDE PANEL SIDE BROOM MOTOR BROOM SAFETY DRIVE CPLG BROOM LIFT LEVER BROOM LIFT SHAFT LIFT LEVER BASE, RT LIFT LEVER COLLAR LIFT LEVER SPRING SIDE BROOM POLYPROPYLENE SIDE BROOM CLUTCH PLATE ADJ. BROOM LIFT BROOM MOUNTING BLOCK SIDE BROOM ARM BROOM RETAINING PLATE BROOM MOTOR MOUNT BROOM SHAFT DRIVE TUBE BEARING GROMMET-3/8 ID X 1-1/2 OD X .375 HANDLE GRIP SIDE BROOM LONG LINK ADJUSTMENT KNOB RIGHT FLOOR SEAL RH SEAL STRIP 3/8" X 1 1/4" SPRING PIN 1/4" X 1 1/2" CLEVIS PIN 1/4" X 1 1/4" SPRING PIN FB CASHD 1/4"-20 X 1/2" 1/2" X 1" CLEVIS PIN HCN 1/4"-20 SSS CP 1/4"-20 X 3/8" NYLOK #10-32 NYLOK 1/4"-20 HITCH PIN CLIP 9 HCS 1/4"-20 X 1/2 SS" HN 5/16"- 18 SS NYLOK 5/16" - 18 SS FW 5/8 ID X 1-1/2 OD SS LW 1/4" SS PPH #10-32 X 5/8" SS FHP 1/4"- 20 X 1-3/4" PPH SMS #8 X 3/4" SS #4 HAIR PIN HCS M6-1.0 X 14 SS 3/8" X 1 1/2" CLEVIS PIN
Ubuntu 12.04 Virutal Machine User Manual

User Manual of the Pre-built Ubuntu12.04Virutal MachineCopyright c 2006-2014Wenliang Du,Syracuse University.The development of this document is/was funded by three grants from the US National Science Foundation: Awards No.0231122and0618680from TUES/CCLI and Award No.1017771from Trustworthy Computing.Permission is granted to copy,distribute and/or modify this document under the terms of the GNU Free Documentation License,Version1.2or any later version published by the Free Software Foundation.A copy of the license can be found at /licenses/fdl.html.1OverviewUsing VirtualBox,we have created a pre-built virtual machine(VM)image for UbuntuLinux(version 12.04).This VM can be used for all our SEED labs that are based on Linux.In this document,we describe the configuration of this VM,and give an overview of all the software tools that we have installed.The VM is available online from our SEED web page.Updating the VM is quite time-consuming,because not only do we need to udpate the VM image,we have to make sure that all our labs are consistent with the newly built VM.Therefore,we only plan to update our VM image once every two years,and of course update all our labs once the VM is changed.2VM Configurations2.1Configuration of the VMThe main configuration of this VM is summarized in the following.If you are using VirtualBox,you can adjust the configuration according to the resources of your host machine(e.g.,you can assign more memory to this VM if your host machine has enough memory):•Operating system:Ubuntu12.04with the Linux kernel v3.5.0-37-generic.•Memory:1024M RAM.•Disk space:Maximum80G disk space.We have created two accounts in the VM.The usernames and passwords are listed in the following:er ID:root,Password:seedubuntu.Note:Ubuntu does not allow root to login directly from the login window.You have to login asa normal user,and then use the command su to login to the root account.er ID:seed,Password:dees2.2Network setupCurrently the“Network connection”is set to“NAT”,i.e.,your VM is put in a private network,which uses your host machine as the router.The VMs in such a setting can connect to the Internet via the NAT mechanism,and they are not visible to the outside(their IP addresses are not routable from the outside,e.g., VirtualBox assigns10.0.2.15to each VM under NAT configuration).This setting is sufficient for most of our SEED labs.If you want your VMs to be visible to the outside(e.g.,you want to host a HTTP server in a VM, and you want to access it through the Internet),then,you can refer to the instruction“Network Configu-ration in VirtualBox for SEED Labs”under the following link:/˜wedu/ seed/Documentation/Ubuntu11_04_VM/VirtualBox_MultipleVMs.pdf.The instruction was written for Ubuntu11.04,however,it also works for the updated Ubuntu12.04Virtual Machine as well.3Libraries and Software3.1Libraries and Applications InstalledBesides the packages coming with the Ubuntu12.04installation,the following libraries and applications are additionally installed using the"apt-get install"command.libnet1,libnet1-dev,libpcat-dev,libpcap-dev,libattr1-dev,vim,apache2,php5,libapache2-mod-php5,mysql-server,wireshark,bind9,nmap,netwox/netwag,openjdk-6-jdk,snort,xpdf,vsftpd,telnetd,zsh,ssh,dpkg-dev,openssl,The libcap 2.21and libpcap1.2.0have been compiled and installed from the source down-loaded from the Internet.3.2Softwares configurationNetlib/netwox/wox is a network toolbox;netwag is a GUI of netwox.They can be foundin/usr/bin/.The ICMP spoofing bug of netwox has beenfixed.It should be noted that running netwox/netwag requires the root privilege.Wireshark.Wireshark is a network protocol analyzer for Unix and Windows.It is located in/usr/bin/. Wireshark requires the root privilege to run.Nmap.Nmap is a free security scanner for network exploration and hacking.It is located in/usr/bin/. Some functions of nmap require root privilege.Firefox extensions.Firefox is installed by default in Ubuntu12.04.We have installed some useful extensions,including LiveHTTPHeaders,Tamper Data,and Firebug.They can be launched in the “Tools”menu in Firefox.Elgg web application.Elgg is a very popular open-source web application for social network,and we use it as the basis for some of Web security labs.It should be noted that to access Elgg,the apache2http server and the MySQL database server must be running.Collabtive web application.For some labs,especially those related to web security,we need a non-trivial web application.For that purpose,we have installed the Collabtive web application.Several versionsof Collabtive are installed;most of them were modified from the original version to introduce different vulnerabilities.It should be noted that to access Collabtive,the apache2http server and the MySQL database server must be running.Java.We have installed openjdk-6-jdk,the OpenJDK Development Kit(JDK)6for Java.The com-mands javac and java are available to compile and run java source code.4Pre-Installed ServersSome of the SEED labs may need additional services that are not installed or enabled in the standard Ubuntu distribution.We have included them in our pre-built VM.Note:You need root privilege to start a server.4.1The MySQL ServerThe database server MySQL is installed.It can be started by running"service mysql start".Cur-rently,there are two accounts in the MySQL server.The usernames and passwords are listed below.1.root:seedubuntu2.apache:apache(web applications use this account to connect to the mysql server)You can access the MySQL database server by running the client-side application/usr/bin/mysql. The following is a simple demo on how to use mysql.$mysql-u root-pseedubuntumysql>show databases;mysql>use db_name;mysql>show tables;mysql>select username,user_email from table_name;mysql>quit4.2The Apache2Http ServerThe apache2http server was installed using"apt-get install".It can be started by issuing the "service apache2start"command.The apache2server is configured to listen on both80and 8080ports.All the web pages hosted by the server can be located under the/var/www/directory.For each SEED lab that uses the apache2http server,we have created one or several URLs.Basically, in the pre-built VM image,we use Apache server to host all the web sites used in the lab.The name-based virtual hosting feature in Apache could be used to host several web sites(or URLs)on the same machine.A configurationfile named default in the directory"/etc/apache2/sites-available"contains the necessary directives for the configuration.The following is a list of URLs that we have pre-configured; their corresponding directories are also listed:/var/www/CSRF/Collabtive//var/www/CSRF/Attacker//var/www/SQL/Collabtive//var/www/XSS/Collabtive//var/www/SOP//var/www/SOP/attacker//var/www/SOP/Collabtive/:8080/var/www/SOP/Configuring DNS.The above URL is only accessible from inside of the virtual machine,because we have modified the/etc/hostsfile to map each domain name to the virtual machine’s local IP address (127.0.0.1).You may map any domain name to a particular IP address using the/etc/hosts.For example you can map to the local IP address by appending the following entry to/etc/hostsfile:Therefore,if your web server and browser are running on two different machines,you need to modify the/etc/hostsfile on the browser’s machine accordingly to map the target domain name to the web server’sIP address.4.3Other ServersDNS server The DNS server bind9is installed.It can be started by running"service bind9 start".The configurationfiles are under/etc/bind/.Ftp server.The vsftpd(very secure ftp daemon)server is installed.It can be started by running "service vsftpd start".Telnet server.The telnetd server is installed.It can be started by running"service openbsd-inetd start".SSH server.The openssh server is installed.It can be started by running"service ssh start".5Miscellanious ConfigurationTime zone Currently the time zone is set to be New York,adjust that to the time zone of your location. Display resolution In order to adjust the display resolution in VirtualBox,we have installed guest addi-tions from the terminal(not from the menu in VirtualBox).This is done with the following3commands: sudo apt-get install virtualbox-ose-guest-utilssudo apt-get install virtualbox-ose-guest-x11sudo apt-get install virtualbox-ose-guest-dkmsAfter installing the required additions,you can adjust the display resolution at“System Settings→Dis-plays→Monitor”.6Configure Your VM securely6.1Change the passwordFor the sake of security and your own convenience,we suggest that you change the account password.To change the Ubuntu’s account password.You need to login as root and issue the"passwd username" command.To change MySQL’s root password.You can do it as following:$mysql-u root-pseedubuntuOnce in the prompt do this:mysql>update user set User=’NewRootName’,Password=’NewPassword’where user=’root’;mysql>flush privileges;6.2Configure automatically start serviceIt’s more convenient to start some commonly used service automatically during the system boot up,although most people do not want to start some server that they do not use.Currently,most of the service(except the Apache and MySQL servers)we need for SEED labs are configured not to start automatically.You can use chkconfig to get the current configuration.You can also use chkconfig to modify the configuration.For example,to start the server XYZ automatically during the system bootup,run"chkconfig XYZ on".。
5-30 Parker Hannifin Corporation O-Ring Division 动

Squeeze
Actual
%
.010
15
to
to
.018
25
.010
10
to
to
.018
17
.012
9
to
to
.022
16
.017
8
to
to
.030
14
.029
11
to
to
.044
16
E(a) Diametral Clearance
.002 to
.005
.002 to
.005
.003 to
.006
.003 to
Dynamic O-Ring Sealing
Parker O-Ring Handbook
Gland Dimensions for Industrial Reciprocating O-Ring Seals, 103.5 Bar (1500 psi) Max.†
O-Ring
Size
Parker
No. 2-
Nominal Actual
.070
1/16
± .003
.103
3/32
± .003
.139
1/8
± .004
.210
3/16
± .005
.275
1/4
± .006
L Gland Depth
.055 to
.057
.088 to
.090
.121 to
.123
.185 to
.188
.237 to
.240
C
OD (Piston)
+.000 -.001
Squirrel SWIFT 4 使用说明书

USER MANUALCongratulations on your purchase of a Squirrel SWIFT 4 (“product”). By purchasing this product, you acknowledge that engaging in sky-diving, base jumping, parachuting, and “wingsuiting” is an inherently dangerous activity that requires training, proficiency, and skill. Use of this product may result in serious injury or death. Do not use this product without inspecting it and all of its components before each and every use. You acknowledge and agree that even when properly used, this product may cause serious bodily harm or even death. You, the purchaser, acknowledge and agree that this product is intended for inherently dangerous recreational purposes, and you assume all risk, responsibility, and liability whatsoever from any and all injuries (including death), losses or damages to persons or property arising from the use of this product sold by Squirrel, LLC to you, the purchaser. Squirrel is not liable for any special, consequential, incidental, punitive, or indirect damages or anticipated profits, however caused, in relation to the purchase and use of this product. In no event shall Squirrel’s total liability to you, as purchaser, or your assigns, heirs, representatives, and other similarly situated persons, for all damages, losses, and causes of action exceed the purchase price paid by you, the purchaser, for this product. This product has been purchased by you “as is” and without warranties of any kind, either express or implied. To the fullest extent permissible pursuant to applicable law, Squirrel, LLC disclaims all warranties, express or implied, including, but not limited to, warranties of title and implied warranties of merchantability and fitness for a particular purpose.BEFORE YOU BASE, SKYDIVE. BEFORE YOU GET TOO CRAZY WITH YOUR SWIFT 4, TRAIN!Please take your responsible progression seriously: skydive your wingsuit extensively before you BASE jump it, and train in your wingsuit extensively before you attempt any advanced maneuvers. Enjoy your progression in your SWIFT, and respect the learning curve. Coaching and qualified instruction are essential.Always maintain awareness of your surroundings. It is your responsibility to avoid collisions with other wingsuit pilots, parachutes, all air-traffic, and planet Earth. Skydiving and BASE jumping are extremely dangerous, and complacency kills.Keep zippers close against MLW webbing.Handles completely exposed. Zippers tight against MLW.USE, CARE, AND FEEDING OF YOUR SQUIRRELZIPPER BUNGEESThe bungees that hold the zippers tight to the main lift webbing (MLW) of your harness must always be connected. DO NOT jump your suit without the zipper bungees set tightly around your harness MLW. Securing the bungees on the inside of the MLW usually results in the zippers being closer, and the hole being smaller. The bungees have a lifespan - inspect them regularly and replace them at the first sign of wear.NOTE: If you think that the zipper system is not functioning well with your skydive harness (i.e. your emergency handles are not always 100% accessible), please contact us immediately before your next jump. You may need to modify the zippers so that the sliders stay locked in place, as per the information at this URL: http://squirrel.ws/zipperstuffAIRFOIL CROSS-SECTION (“ARM FOAM”) OPTIONSYour SWIFT 4 is shipped with black 5mm foam inserted in the arms. You may choose to jump the suit without the foam in the beginning, and add it in once you are fully comfortable with the suit in all maneuvers, at all angles, and during all phases of the flight from exit to landing. The foam adds glide and speed performance by increasing structure in the leading edge. Without the foam, the suit is generally easier to fly.For PERFORMANCE Competitions If you intend to use the SWIFT 4 for FAI format Performance Competitions, please contact us to discuss higher performance arm foam options.CUSTOM INTERNAL PRESSUREThe SWIFT 4 is designed to allow you to choose the amount of internal pressure in the arm wings. Some pilots like full pressure (zips closed) and some like minimum pressure (zips all the way open). The difference is primarily how easy it is to bend your arm at the elbow when maneuvering.Don’t be shy with the adjustments - it is ok to try fully open, and it’s ok to try fully closed. The suit is comfortable and easy to fly in all settings.Make zipper-checks a part of your pre-flight checklist - always fly with symmetric settings.LEG WING INTERNAL ZIPPERWe recommend flying with the leg wing zip closed. You may experiment with opening it to reduce internal pressure, but the leg wing zip is primarily designed for access, not pressure adjustment. Again, make zipper-checks a part of your pre-flight checklist.N UT SA CK Z IPP ERLE G W IN G A C C ES SPosition for belly flight. Palm rests against arm wing end cell.Gripper provides structure. Hand “palms” arm wing end cell.GRIPPERSHolding your grippers correctly is an important part of controlling your SWIFT 4. It is NOT necessary to hold the gripper itself, tightly. Here is an example of a GOOD position:GOOD: Pilot’s fingers are all on the top surface (back side) of the gripper, resting against the arm wing end cell. The grip is somewhat relaxed, with the thumb in front and the top of the gripper nestled gently in the palm of your hand. Note that the gripper itself is not being held tightly.NOTE: It is NOT necessary to hold the grippers tightly in flight. You can comfortably fly your suit from exit to landing with a very light touch on the grippers. It is better to NOT hold the grippers than it is to hold them wrong, or to hold them too tightly.NUTSACKDon’t overload your nutsack, it’s made for your stuff-sack and not much heavier. Adding a lot of heavy equipment or even too much food or water will change your centerof gravity and could possibly affect your flight in a negative way.LEG WING ZIPPER PULLSHOOK KNIFEAlways fasten your leg wing zipper pulls. If you walk around with them dragging on the ground, you will ruin them. If your suit is on, have the zipper pulls connected. Do not drag them through the dirt.Every suit comes standard with an aluminum doublebladed hook knife. Check to make sure that the hook knife is loaded properly and secured.SLEEPING AND BATHING YOUR SQUIRRELDon’t smother your Squirrel! When it’s hibernating, it likes to breathe and relax in a cool, dry, comfortable nest. Do not store your suit for long periods of time in a tightly folded or compressed manner. Always fully shade-dry your suit if it becomes wet or damp. Gently rinse with fresh water to clean, or if ever exposed to salt water. Never use chemical detergents – Squirrels like it all natural, all the time!Your suit can be hand washed in cold water, or machine washed cold on a gentle cycle. Never tumble dry your suit. Hang dry in the shade.CONTACT USv.202001 - Check the SWIFT 4 product page at www.squirrel.ws for the latest PDF version of this manual.Please consider the following important points:1. We designed, tested, and built your wingsuit.2. Our job is to make sure that you fly as safely as possible, while having the most fun possible.3. Our job is to help you understand, use, and progress in, your suit.4. Our job is to answer your questions, and we like our job.For these reasons, we highly recommend that you contact US (SQRL) if you have any questions about any product that we make. We 100% guarantee that the information you receive from us will be more relevant, more accurate, and more thorough than anything you can find in facebook comments, internet forums, or even your DZ gear shop guru. So, again, call us. Email us. Together with your dealer & the local SQRL pros near you, we’re here to help.-Matt, Mike, Will, Marty, & All the TeamTHANK YOU FOR FLYING SQUIRREL!www.squirrel.ws***************+1-855-FLY-SQRL。
商务英语综合教程4 Unit 4 Business ethics课后答案

Unit 4 Business ethicsExtensive ReadingCorporate Philanthropy Responds to Disasters ExercisesI.Speed Reading ComprehensionRead the text for FIVE minutes, and find the best answer to each of the following questions.1. According to the 2nd paragraph, why some companies faced internal criticismA. These companies have donated too much money to the communities, regardless of theirown capacity.B. These companies ignored the needs of their own employees who were affected by thedisasters.C. The philanthropic programs of these companies were too cheap.D. Corporate had to go back to boards for additional donation resources.2.Why is it that somecompanies are suggested donating cash instead of products when disasters take placeA. Products are often hard to transport and warehouse.B. Using cash in the locality helps rebuild the economy.C. Product may not fit the needs of the beset community.D. All of above.3.Which of the following statement is NOT true with Pitney Bowes Inc.A. It has operated a fund that helps employees out of personal tragedies.B. Its Employee Involvement Fund can reflect employees’ interest and support.C. It has started splitting some of its corporate giving between immediate and long-termassistance in the consideration of the complicated nature of identifying appropriate disaster aid.D. Medical and funeral expenses will not be the focus of its fund.4. According to the text, which of the followingcompany’s foundation is NOTlong-term-focusedA. Baxter InternationalB. MitsubishiC. General Electric Co.D. Pitney Bowes Inc.5.The software module of MicroEdge Inc. helps the company’s community foundation the best in terms of_______.A. free-of-charge serviceB. online serviceC. accountingD. disaster reliefII.VocabularyFill in the blanks with appropriate words from the text. The initial letter of each word has been supplied for you.1.It’s wise to use just as much caution when making your charitable giving decisions as you do when making other decisions affecting your life.2.With soil that has had its biological components destroyed, the first step toward restoration is to stop adding any more chemical fertilizers.3.The global obesity pandemic combined with society's anti-fat bias is more damaging to women than to men, an expert has warned at an international conference.4.Turkey’s two major cities are grappling with water shortages after record-low snow and rain falls in the winter and searing summer temperatures.5.The importers who do not intend clearing the imported goods for "home consumption" straightaway may choose to warehouse the goods.6.The Foundation is a public charity that works with individuals, families, businesses and foundations, serving their philanthropic needs as well as initiating giving programs.7.As the little copyist proceeded with her work, she sent every now and then a responsive glance toward her admirer.8.Beset by rumors, and four months from a primary election, the Mayor yesterday for the first time gave his account of a2007 incident in which he argued with a police officer.9.Like so many others around the world, we are following the devastation caused by the earthquake and tsunami that has hit many parts of Southeastern Asia.10. Some coincidences are small, and seemingly inconsequential, but others have the potential to change lives.A Question of EthicsExercisesI.Reading Comprehension1. Which of the following statements is NOT TRUE withWaterschoot's caseA. It raised the ethical concerns regarding information technology and the managementobligation.B. Waterschootimmediately reported to her boss and the unit's legal counsel about theproblem because there was some crucial information for Lockheed Martin in the template.C. Waterschoot found the competitor’s confidentialinformation before 5 p.m.D. Waterschoot removed the document from the server with the purpose of protecting a competitor of Lockheed Martin’s.2. According to the text, as e-business and IT are developing, companies need to put the following into consideration EXCEPT _______.A. equipping the employees with essential IT ethicsB. establishing a set of ethical guidelines in a companyC. the impacts brought by IT on the employees concernedD. how to deal with the potential problem brought by e-business partnerships3. According to the InformationWeek Research survey, we can infer that _______.A. If your personal data is collected by a health-care company, they are more likely to be sold to third parties than by any other industries.B. Most companies will inform their customers know when specific types of data of theirown are being collected.C. When evaluating the ethical and moral implications of business decisions, a larger number of people will rely on their personal experience only.D. Not many people know some ethical impacts may be brought by their business decisions.4. Paragraph 7 suggests that ________.A. Canon Information Systems Inc is monitoring its employees’ online activities;B. Canon Information Systems Inc’s human resources department tries to make sure thattheir employees are using the Internet in an ethical and legal way;C. James Underwood, manager of IS, reports to the human resources department;D. Canon Information Systems Inc’s human resources department may be violating theprivacy of the employees.5. Companies nowadays concern not only about the employees’awareness of business ethics, but also about________.A. how the employees interact with the information technology in a digital context;B. the safety when the employees are handling the digital devices;C. the protection of the privacy of its customers;D. all of above.。
综合英语4Unit7TheMonster..

2018/10/6
Free Template from
11
• • • •
1. agony n. extremely physical or mental suffering <释例>She was in agony of indecision. 她陷于扰豫不决的痛苦中。
2018/10/6 Free Template from 4
• 威廉· 理查德· 瓦格纳 • (Wilhelm Richard Wagner,1813年 5月22日-1883年2月13日) • 德国作曲家。他是德国歌剧史上一位 举足轻重的人物。前面承接莫扎特、 贝多芬的歌剧传统,后面开启了后浪 漫主义歌剧作曲潮流,理查德· 施特劳 斯紧随其后。同时,因为他在政治、 宗教方面思想的复杂性,成为欧洲音 乐史上最具争议的人物。
Text I
The Monster
Background information: 1. About the text: This text first appeared as a radio talk, entitled A Monster. Later it was published with the title Of Men and Music in the United States in 1937. 2. About the author: Deems Taylor, American musician and critic.
他的代表作品有歌剧尼伯龙根的指环帕西法尔罗恩格林纽伦堡的名歌手等等11部部歌剧9首序曲1部交响乐4部钢琴奏鸣曲及大量合唱曲艺术歌曲等并写了艺术与革命歌剧与戏剧等几部关于歌剧改革的著作
Unit 8
The Monster
Practical NFC Peer-to-Peer Relay Attack using Mobile Phones

Practical NFC Peer-to-Peer Relay Attackusing Mobile PhonesLishoy Francis,Gerhard Hancke,Keith Mayes,and KonstantinosMarkantonakisInformation Security Group,Smart Card Centre,Royal Holloway University of London,Egham Hill,TW200EX,Surrey,United Kingdom.(L.Francis;Gerhard.Hancke;Keith.Mayes;K.Markantonakis)@/Abstract.NFC is a standardised technology providing short-range RFIDcommunication channels for mobile devices.Peer-to-peer applications formobile devices are receiving increased interest and in some cases theseservices are relying on NFC communication.It has been suggested thatNFC systems are particularly vulnerable to relay attacks,and that theattacker’s proxy devices could even be implemented using off-the-shelfNFC-enabled devices.This paper describes how a relay attack can beimplemented against systems using legitimate peer-to-peer NFC commu-nication by developing and installing suitable MIDlets on the attacker’sown NFC-enabled mobile phones.The attack does not need to accesssecure program memory nor use any code signing,and can use publiclyavailable APIs.We go on to discuss how relay attack countermeasuresusing device location could be used in the mobile environment.Thesecountermeasures could also be applied to prevent relay attacks on con-tactless applications using‘passive’NFC on mobile phones.1IntroductionNear Field Communication(NFC)[1]is intended as a short-range standard-ised technology for providing contactless communications for mobile devices. NFC is intended to be an intuitive method of establishing ad-hoc connections, simply requiring that two NFC-enabled devices are brought in close physical proximity to each other.NFC also allows for devices to interact with existing contactless/RFID(Radio Frequency Identification)systems.In‘passive’commu-nication mode NFC allows devices to emulate passive contactless smart cards, while‘active’mode allows for devices to act as contactless smart card readers or to communicate with each other.Although the use of NFC-enabled devices in contactless systems has received much publicity,the use of NFC to support peer-to-peer services is less well covered.One of the earliest specified uses of active NFC was to pair Bluetooth de-vices by facilitating the exchange of information needed to setup the Bluetoothcommunication channel[2].NFC can also be used for sharing data and content between mobile devices,such as digital business cards and social networking de-tails,although the data rates are currently not best suited to high-bandwidth transfers.Mobile payments are becoming increasingly popular and there are a variety of schemes using a range of data bearers.NFC is seen as an ideal tech-nology in this area with its ability to interact with existing contactless systems and facilitate peer-to-peer transactions between mobile phones[3].In short range communication systems,it is usually assumed that the devices are actually in close physical proximity when successfully communicating.How-ever,in a relay attack the communication between two devices are relayed over an extended distance by placing a proxy device within communication range of each legitimate participant and then forwarding the communication using another communication channel.The two legitimate participants receive valid transmissions from each other and therefore assume that they are in close physi-cal proximity.In some systems,especially in smart token environment,this could lead to serious security vulnerabilities[4].The risk posed to near-field channels by relay attacks and the possibility of using NFC-enabled mobile phones as a relay attack platform have been discussed[5][6],but a practical relay attack using this platform has not been demonstrated.In this paper,we describe how a relay attack against peer-to-peer NFC system could be practically implemented.The novelty of this attack is that it also uses available NFC-enabled mobile phones as attack platforms,providing the attacker with off-the-shelf proxy device.The attacker’s mobile phones are of acceptable (non-suspicious)form factor,unlike custom built emulators used in other relay attacks.The attack functionality can also be implemented using only software via publicly available APIs in a standard MIDlet(Mobile Information Device Profile or MIDP application)using JSR118API[7].The resources and technical skill required of the attacker are therefore greatly reduced.In Section2we provide a brief introduction to NFC communication and relay attacks.We describe the attack implementation in Section3and discuss current countermeasures that could be used to mitigate relay attacks in Section4.2BackgroundNFC technology allows for the integration of contactless technology into active devices,such as mobile phones.NFC operates within the13.56MHz Radio Fre-quency(RF)band and has an operating distance up to10cm.A NFC-enabled device can act as both a“contactless card”and a“contactless reader”.NFC-enabled devices,as specified in ISO-18092/ECMA-340[1]and ISO-21481/ECMA-352[8],are compatible with existing contactless systems adhering to ISO14443 [9],ISO15693[10]and FeliCa[11].The NFC standards also define a communica-tion mode for peer-to-peer(P2P)or‘active’communication,with the purpose of facilitating communication between two NFC-enabled devices.In‘active’NFC, the participants communicate in a“client-server”model.The device that starts the data exchange is known as the Initiator and the recipient is known as the Target.In‘active’mode,the Initiator and Target uses their own generated RFfield to communicate with each other.First the Initiator transmits an RF car-rier,which it uses to send data to the Target.Once an acknowledgment for the data sent has been received from Target(by modulating the existingfield),the Initiator switches the carrier off.The original Target then reprises the role of Initiator,switching on its carrier,and transmits a response to the original Initia-tor.For the purposes of reader’s clarity,we call the NFC enabled mobile phone configured as the Initiator to be in“writing”mode and the phone configured as the Target to be in“reading”mode.On NFC-enabled mobile phones the Secure Element(SE)provides the secu-rity means to establish trust between service provider and the device.The SE also provides a secure environment for hosting sensitive applications and stor-ing cryptographic keys.Currently there are three main architectures for NFC. Thefirst involves an SE that exists as an‘independent’embedded hardware module,i.e.a stand-alone IC(Integrated Chip)is built into the phone.In the second option,the SE is implemented within the UICC(Universal Integrated Circuit Card)[12].Of the existing Subscriber Identity Application(SIA)mod-ules such as the Subscriber Identity Module(SIM)[13],Universal Subscriber Identity Module((U)SIM)[14]and Removable User Identity Module((R)UIM) [15].The third option implements the SE on a removable memory component such as a Secure Multi-Media Card(Secure MMC)or Secure Digital card(Se-cure SD)[16].The discussion comparing the advantages and disadvantages of the above mentioned architectures is beyond the scope of this paper.It is im-portant to note that the NFC standards does not specify any security services apart from the Signature Record Type Definition[17],leaving the security de-sign to the application developer.The Signature RTD specifies how data is to be signed to ensure data integrity and provide data authentication.This standard is currently being reviewed by the NFC Forum[18].The handsets that were used in our practical experiments implemented inde-pendent SEs,which supported Java Card2.2.1[19](Java Card Open Platform [20]),Global Platform2.1.1[21]and Mifare Classic[22]emulation.To implement ‘passive’emulation of a contactless token an application must be installed in the secure program memory of the SE.Currently,it is possible to unlock the SE in ‘independent’architectures and to install custom applications[23].However,this would be controlled when the UICC is used as the SE,as access to the UICC is strictly managed by the mobile operator[24].When implementing‘active’NFC communication the functionality can be entirely controlled via a MIDlet installed in the non-secured application memory of the mobile phone.A developer using the mobile phone as a platform for‘active’communication does therefore not need to gain access to any secure parts of the NFC architecture.The MIDlet can implement the‘active’NFC functionality using standard functions available within the extensions of the public JSR257Contactless Communication API [25].2.1Relay Attack TheoryThe Grand Master Chess problem as discussed in[26]provides a classic example of relay attack.In this scenario a player who does not know the rules of Chess canFig.1.P2P Relay Setup using Bluetooth.simultaneously play against two grand masters.The player starts a postal game of Chess with each grand master and subsequently forwards the moves originat-ing from one grand master to the other.Although each grand master thinks that they are engaging the player they are essentially playing against each other.The application of this scenario to security protocols wasfirst discussed in[27]as ‘mafia fraud’.Subsequently this attack has also been referred to as a‘wormhole attack’[28]or as a‘relay attack’[29].Using this attack an attacker is able to bypass security protocols by only relaying challenges and responses between two legitimate entities.As the attacker is always in the position to provide the cor-rect reply,which he/she learned from the other party by forwarding the original message and recording the response,the security protocol is executed success-fully and both parties will consider the attacker to be a legitimate participant in the protocol.In this scenario the attacker never needs to know any detail of the information he/she relays,i.e.he/she does not need to know the structure of the protocol,the algorithms used,the plain text data sent or any secret key material.The attacker must only be in a position where he/she can continue to relay the communication for the entire duration of the protocol.Earlier practi-cal examples of relay attack in the contactless environment using custom-built hardware or using NFC-enabled contactless readers can be found in[30],[31] and[32].3Relay ImplementationWe implemented the relay attack against two NFC enabled mobile phones op-erating in peer-to-peer mode and participating in a legitimate transaction.As illustrated in the Figure1,Phone-A intends to interact with Phone-B to perform a legitimate peer-to-peer transaction.The attacker introduces two additional mo-bile phones into the transaction setup,namely Proxy-A and Proxy-B,to relay the communications between Phone-A and Phone-B.In our proof-of-concept at-tack experiment,we practically implemented the relay attack using four NFCenabled mobile phones,as shown in Figure2.Fig.2.Devices used in the relay attack–Device B(Nokia6131NFC),Proxy A(Nokia 6131NFC),Proxy B(Nokia6212Classic NFC)and Device A(Nokia6212Classic NFC).3.1Phone-A and Proxy-BThe role of Proxy-B,as the name suggests,is to represent Phone-B and to relay communications to and from Phone-A.To realise both Phone-A and Proxy-B we used two Nokia6212Classic NFC mobile phones which are based on Symbian S405th Edition FP1platform.On Phone-A,a MIDlet(MIDP2.1application [7])was implemented(3kilobytes in size)that utilised the JSR257extensions API to realise NFC peer-to-peer communications.Phone-A is designed to switch between“reading”and“writing”modes as required.On Proxy-B,a MIDlet(MIDP2.1application)implemented(14kilobytes in size)the JSR257extensions for NFC peer-to-peer and JSR82API[33]for IEEE802.15(Bluetooth)communications.By default,Proxy-B was configured in“reading”mode and also supports“writing”mode.The NFC platform of Phone-A and Proxy-B supported the active peer-to-peer mode of operations for both Target and Initiator.Hence these devices performed“reading”and “writing”in active mode.3.2Phone-B and Proxy-APhone-B and Proxy-A were realised on two Nokia6131NFC mobile phones, based on Symbian S403rd Edition FP1platform.Proxy-A represented Phone-A in the transactions and relayed messages with Proxy-B.Similar to Phone-A,on Phone-B a MIDlet(MIDP2.0application[7])was implemented(3kilobytes in size)that utilised JSR257extensions API to realise NFC peer-to-peer communi-cations.Phone-B is designed to switch between“reading”and“writing”modes as required.On Proxy-A,a MIDlet(MIDP2.0application)implemented(14kilobytes insize)the JSR257extensions API[25]for NFC peer-to-peer and JSR82API[33]for IEEE802.15(Bluetooth)communications.By default,Proxy-A was config-ured in“writing”mode and also supported“reading”mode.The NFC platform of Phone-B and Proxy-A supported active peer-to-peer mode of operation for Initiator,but only passive for Target.Hence these devices performed“reading”in passive mode and“writing”in active ing JSR257extensions API, the connection open and receiving data in“reading”mode were made as follows, private static final String TARGET_URL="nfc:rf;type=nfcip;mode=target";NFCIPConnection conn=(NFCIPConnection)Connector.open(TARGET_URL);byte[]data=conn.receive();byte[]ack={(byte)0xFF,(byte)0xFF};conn.send(ack);Similarly,the connection open and sending data in“writing”mode were made as follows,private static final String INITIATOR_URL="nfc:rf;type=nfcip;mode=initiator";NFCIPConnection conn=(NFCIPConnection)Connector.open(INITIATOR_URL); byte[]cmd={(byte)0x9A,(byte)0xED};conn.send(cmd);conn.receive();3.3Relay BearerProxy-A and Proxy-B established the relay channel using Bluetooth,where Proxy-B acted as the“server”and Proxy-A act as the“client”.Bluetooth is a short range radio technology developed by Bluetooth Special Interest Group (SIG)and utilises unlicensed radio in the frequency band of2.45GHz.The sup-ported data speed is approximately720kps.Bluetooth communication range from10metres to100metres.The MIDlets implemented the Bluetooth commu-nication on Proxy-A and Proxy-B using JSR82API.We used L2CAP(Logical Link Control and Adaption Protocol)available within the host stack of the Bluetooth protocol.L2CAP is layered over the Baseband Protocol and oper-ates at the data link layer in the OSI(Open System Interconnection)Reference Model.It supports data packets of up to64kilobytes in length with672bytes as the default MTU(Maximum Transmission Unit)and48bytes as the minimum mandatory MTU.For creating an L2CAP server connection,a btl2cap scheme (url),a16byte service UUID(Universally Unique Identifier),a friendly name (device name)and other parameters were provided as follows,String service_UUID="00000000000010008000006057028A06";String url="btl2cap://localhost:"+service_UUID+";ReceiveMTU=672;TransmitMTU=672;name="+deviceName;L2CAPConnectionNotifier notifier=(L2CAPConnectionNotifier)Connector.open(url);conn=notifier.acceptAndOpen();For creating an L2CAP client connection,a btl2cap scheme,unique Bluetooth MAC address(6bytes)of the server device,protocol service multiplexer(port) for the remote device and other parameters were provided as follows,String url="btl2cap://00226567009C:6001;authenticate=false;encrypt=false;master=false;ReceiveMTU=672;TransmitMTU=672";conn=(L2CAPConnection)Connector.open(url);The MIDlets used the DiscoveryAgent class to perform Bluetooth device and service discovery.The DiscoveryListener interface was implemented to handle the notifications of devices and services.When devices and services are dis-covered,the DiscoveryAgent notifies the MIDlet by invoking callback methods such as deviceDiscovered()and serviceDiscovered().The methods such as re-treivedDevices()and searchServices()caches the previously discovered devices and services,in order to reduce the time needed for discovery.The client MIDlet on Proxy-B listened for the registered service and when available,connected to the server.The sending and receiving of data were achieved by using an L2CAPConnection.We note that the MIDlets implementing the Bluetooth bearer did not require any code signing[34]and executed in the untrusted3rd party security domain. More information on Java security domains can be found in[35].Currently the attacker just needs to enable the application access privilege[36][37]for connectivity to be set as“always allowed”and enable Bluetooth to be used on the mobile phone.The device specific API access rights can be found in[38]for a Nokia6131and in[39]for a Nokia6212.Alternatively,Bluetooth can be replaced with SMS(Short Messaging Service) or mobile Internet[using intermediate server(s)via HTTP(Hyper Text Transfer Protocol)over GPRS/E–GPRS(Enhanced General Packet Radio Service)]as the data bearer in order to increase the relay range.These options were only briefly considered,but we found that these bearers introduced additional overheads. In SMS,the user interaction(key press to confirm the message sending)was required even when the MIDlet was signed in the trusted3rd party security domain.Additionally,SMS is considered to be not so reliable due to its inherent nature such as low bandwidth and variable latency.The additional key presses would also introduce suspicion on the attacker by the victim.Even though,the mobile Internet bearer does not have user interaction overhead similar to SMS, it does need signed code operating within trusted3rd party security domain. 3.4Relay ExperimentTo demonstrate a proof-of-concept attack,against peer-to-peer NFC transac-tions using enabled mobile phones,we implemented a simple application in a controlled laboratory environment.Phone-A would act as the Initiator and ‘write’a2-byte message to Phone-B,who would then become the Initiator and answer by“writing”a different2-byte message back to Phone-A.Our goal was simply to demonstrate that it is possible to relay this exchange or transaction with the mobile-based proxy platforms.(a)Device B (b)Proxy A(c)Proxy B (d)Device AFig.3.Relay attack data flow on each device involved.To start the relay experiment,Proxy-A and Proxy-B negotiates and estab-lishes the Bluetooth channel.In order to simplify the experiment,a 2-byte command message was input by the user in Phone-A configured in “writing”mode.The Phone-A exchanged the command with Proxy-B which then relayed to Proxy-A over the Bluetooth data bearer.Proxy-A being in “writing”mode transfered the payload onto Phone-B.The response for the command message was transferred by Phone-B to Proxy-A in “writing”mode and then relayed over to Proxy-B.The Proxy-B switched to “writing”mode and transfered the response message to Phone-A completing the relay process.In effect,Phone-A was made to believe that the response message to the sent command message was originating from Proxy-B.Similarly,Phone-B was made to believe that command message was originating from Proxy-A,which was actually originat-ing from Phone-A via Proxy-B.Therefore it is reasonable to conclude that,in the real world the security of applications using NFC peer-to-peer communica-tion can be potentially be bypassed using the method presented.The data flow of the relay,as processed by each device,is shown in Figure 3.4Using Location Information as Relay Attack CountermeasureProtecting a system against a relay attack is difficult because this attack circum-vents conventional application layer cryptography.Additional security measures are therefore needed to supplement existing authentication or encryption mech-anisms.Several countermeasures to relay,or wormhole,attacks have been pro-posed.These countermeasures are intended for wireless sensor network and smart token environments.Although there are differences between these environments and mobile peer-to-peer services,there are aspects of these countermeasures that could be applied.This section provides a short overview of methods proposed for detecting relay attacks and we refer to an entity verifying the proximity of another entity as the“verifier”and the entity proving its proximity as the “prover”.One way of detecting relay attacks is to monitor any additional delay in the propagation time,which could be caused by the attacker when forwarding the data over a longer distance.Simply placing a time-out constraint on the round-trip time of a challenge-response exchange is not practical as the processing time of the prover can vary and a small error in the expected processing time could have a large influence on the round-trip time[4].Distance-bounding pro-tocols are designed to enable the verifier to accurately determine the round-trip time of a chosen cryptographic challenge-response[40],thereby eliminating the variability in the time taken to calculate the response.The security of distance-bounding protocols,however,are dependent on the underlying communication channel[41]and conventional channels similar to those used in NFC have been shown to be unsuitable for distance bounding[42].Furthermore,more computa-tionally advanced devices such as mobile phones can outperform legacy tokens and therefore circumvent systems implementing timing-based countermeasures that allow for processing time of legacy tokens.The verifier could authenticate the prover based on physical characteristics of the communication ing RF‘fingerprints’has been proposed as a method for source authentication in sensor networks[43]and for smart tokens [44].An attacker would not be able to relay the communication as his proxy will not have the same RFfingerprint as the prover.This method requires that each device is‘fingerprinted’,which is likely to be difficult in practice,especially for a large number of legitimate devices of varying ages(different versions of hardware platform)that are owned,managed or manufactured by multiple entities.Relay attack could also be mitigated by asking the user to perform additional verification of the transaction.The user could be shown additional details of the underlying transaction by a trusted component to check that the transaction was executed faithfully[45],although this would place a significant responsibility on the user,reduce transaction throughput,and require that he/she has sufficient knowledge of how the transaction should be concluded.Another approach in-volving the user is multi-channel communication,where the user also verifies additional audio or visual channels[46].This complicates the relay process,and the attacker must relay multiple channels,some of which might require highbandwidth.This approach is promising although it might increase the transac-tion time and reduce simplicity of operation,which are aspects of NFC that are attractive to both users and service providers.A popular approach in wireless sensor networks is to verify proximity by comparing the location of the nodes[47].A network-wide localization algorithmis used to determine the relative or absolute location of the nodes.Nodes par-ticipating in relay attacks will cause anomalies in the network topology andthe attempted attack will be detected.This method usually requires multiple nodes to collaborate in the localization process and constructing a topology,andin the mobile environment a transaction only involved two entities.Location services are,however,becoming prominent in mobile environment providing a basis for implementing a countermeasure that is practical,effective and remains transparent to the end user.4.1Integrating Location into NFC TransactionsThere are a number of robust Location Based Services(LBS)already deployedin the mobile environment.These services are based on the fact that the locationof the handset can be accurately determined,either by the network operator,a third-party or the handset itself.It is therefore feasible that location infor-mation could be incorporated into peer-to-peer transactions in order to provide relay-resistant communication.This section briefly discusses two methods for determining handset location that are currently used in LBS.A simple,and widespread,method of retrieving and handling location in-formation starts with obtaining the information of the cell broadcast tower(or sector)identifier or the Cell-ID,and attaching it with other parameters in the network broadcast such as Mobile Country Code(MCC),Mobile Network Code (MNC)and Location Area Code(LAC).For instance,one can compute a Loca-tion Code(LC)as follows,LC=‘‘23415431824422847’’,where MCC=234|MNC=15|LAC=43182|Cell-ID=4422847 This information forms the basis for a simple/crude location of the user device,i.e.calculating the position based on the above mentioned location parameters; primarily the tower(or sector)identifier or Cell-ID which the device last ac-cessed.This is applicable to most traditional handsets(e.g.GSM/UMTS).The advanced information obtained from the device can be shown on commercial mapping services,e.g.Google Maps[48].An important point to note is that the accuracy of this form of deriving the location of a mobile device is very limited and dependent on the radius of the cell coverage,which can range from tensof metres to tens of kilometres.Global Positioning System(GPS)technology is becoming available in an increasing number of mobile handsets and it is a more accurate method of deriving the location information from the mobile phone itself.Providing the handset can detect the satellite signals(which is not alwaysthe case),the GPS-enabled handsets supply the application with the locationco-ordinates giving a precise position for the device.The co-ordinates consist of Latitude(LAT)and longitude(LNG)information.For example,LAT=51.42869568,LNG=-0.56286722The location information maybe generated by the participants or generated and attested by a trusted3rd party.An example of XML representation of location proof for mobile phones similar to that presented in[49]is given below.<location proof><issuer>Issuer’s Public Key</issuer><recipient>Recipient’s Public Key</recipient><location information><gps><lat>51.42869568</lat><lng>-0.56286722</lng></gps><mcc>234</mcc><mnc>15</mnc><lac>43182</lac><cellid>4422847</cellid></location information></signature></signature></location proof>4.2Preventing Relay Attacks with LocationExamples of enabling mobile applications with‘location proofs’can be found in [49]and in[50].Assuming that location information is available within mobile phones,the transaction data could be modified to enable the entities involved to verify their proximity.Hu et.al.[51]proposed a simple method using loca-tion information to prevent wormhole attacks in wireless sensor networks.This method required that the verifier and prover know their locations and that they have loosely synchronised clocks.The prover would basically add its location and a timestamp to the transmitted data.An additional authentication mechanism, such as a digital signature,is then used to verify that the packet was constructed by the prover.The verifier compares the prover’s location to its own and con-firms that the prover is in close proximity.If an attacker relays the data then the prover’s location should in theory be further away from the verifier’s loca-tion and the attack would be detected.The attacker cannot modify the data,or construct a new data packet as it does not know the prover’s key material.The timestamp prevents an attacker recording a valid transaction and using it at a later stage at the same location.A simple application of this principle is shown in Figure4.Implementing such a security mechanism in mobile environment is practically feasible and the success of the protocol would simply rely on the accuracy and reliability of the location information ing a digital sig-nature scheme,for the required cryptographic data authentication mechanism, is also feasible as mobile phones have sufficient processing resources.The use of digital signatures in NFC applications is also in the process of being standardised in the Signature RTD candidate specification currently being reviewed by the NFC Forum.Also,current work by the authors discusses a secure authentication method for proximity communication channels based on location information. The idea is to attest physical proximity of devices by using location information as an additional security metric.With the identity of the device or subscriber or token bound to the location information it is possible to restrict potential security threats to geographic areas or proximity zones.The method provides a means to test relative and absolute location,and to determine the proximity as well as provide non-repudiation for the devices involved in the transaction.。
proe的基本命令

改变起始点方法: 选中要作为起始点的点,右键单击→ “起始点”
截面顶点数要相同:若不同
分割命令:分割边 混合顶点:点作为边
对于圆、椭圆来说,截面混合时不需要顶点,截面间通过顺 序连接。
截面1 Rx=35.RY=70 200
截面2 Rx=28.RY=56
截面3 Rx=30.RY=60 20
建立基体
添加凸台
减除材料建立孔 添加肋板 倒角,完成模型建立
2. 由曲面生成三维模型的方法:
建立实体模型的表面(曲面)
曲面加厚
曲面内部“实体化” ,或曲面“加厚”
3.2.1零件建模的一般过程及拉伸特征
第一步:
设置工作目录 新建零件模型——选择文件类型及模板
第二步
选取拉伸特征命令
设置草绘平面的放置属性 草绘平面的选择
其截面必须全部位于中心线的一侧
生成实体旋转时,截面必须是封闭的
3.3.1 旋转特征建立过程
激活命令: “插入” →“旋转” 定义截面: “位置”→ “定义”
指定草绘平面和参照平面 绘制截面,返回旋转特征界面
选定旋转中心线:已有轴线或草图中的轴线 指定旋转角度 预览并完成模型建立
3.3.2旋转特征的模式
选择混合形式 选择截面形式 选择截面生成方式 确认或退出
平行混合对话框:指定各要素
• 指定属性:直的或光滑 • 混合特征截面:指定草绘平面、方向、参照、绘制各截面 • 指定截面间距离:各截面间距离 • 预览并完成混合特征的创建
混合形式
直的
光滑
3.5.3 平行混合特征建立过程中的问题
起始点问题: 在混合特征中各截面的起始点应该靠近,否则会生成扭曲
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Donc, l’imagerie RMN peut être utilisée pour déterminer :
a) la distribution des spins b) la distribution spatiale des paramètres RMN (T1,T2,D) c) Pour ajuster le contraste d) Les signaux RMN dans l’image dépendent des paramètres δ, T1, T2, D
4. Imagerie RMN
Fréquence et phase Excitation sélective Construction d’une image Contraste de l’image Microscopie RMN
Références
J.L. Koenig, Spectroscopy of Polymers, American Chemical Society, Washington D.C., 1992 P.T. Callaghan, Principles of Nuclear Magnetic Resonance Microscopy, Oxford University Press, 1993 Annual Reports on NMR Spectroscopy, Academic Press M.J. McCarthy & M.K. Cheung, 32, 19 (1996) X. Zhou, T.L. Peck & J.B. Litchfield, 32, 31 (1996) D.G. Cory, 24, 87 (1992) Angew. Chem. Int. Ed. Engl., VCH Publishers, Weinheim W. Kuhn, 29, 1 (1990) Macromol. Chem., Huthig & Wepf Verlag, Basel B. Blümler, 194, 2133 (1993) Concepts in Magnetic Resonance, Wiley & Sons S.L. Talagala, I.J. Lowe, 3, 145 (1991) Y. Xia, 8, 205 (1995) E. Kaldoudi & S.C. Williams, 5, 217 (1993)
89
L’imagerie RMN: beaucoup utilisée dans les diagnostics cliniques
Imagerie de H2O T1 (tissus malins) = 1,5 à 2,0 ×T1 (tissus normaux) La plupart des lésions ont des T1 et des T2 longs Contraste de l’image Æ temps de relaxation Très utile dans la détection des tumeurs dans les tissus mous. Particulièrement utile dans la détection des tumeurs cachées par les os. Autres : Infarctus, Hémorragie Ajouter une faible concentration de l’agent paramagnétique pour identifier la région où il n’y a pas de flux. Pour examiner le fonctionnement du foie, reins, etc. Æ Études médicales Métabolisme Fonctionnement des organes Avantages Non destructif Meilleur contraste Pas d’effets secondaires (comparé à la radiographie)
Les gradients le long des trois directions :
GX =
δB δB δB X GY = Y GZ = Z δZ δY δX
Objet Gradient Image
ω Z = ω 0 + γGZ Z ωY = ω 0 + γGY Y ω X = ω 0 + γGX X
∆ω = ω 2 − ω 0 = γGZ Z où le gradient est GZ =
δBZ δZ
On peut utiliser une impulsion r.f. sélective pour exciter seulement certains noyaux à une certaine position dans la dimension Z (irradiation sélective) L’amplitude des signaux RMN mesurée indique le nombre de spins à cette position Æ densité des spins (on néglige les effets des temps de relaxation T1 et T2)
93
Imagerie RMN 1D
Position ÅÆ Fréquence (frequency encoding) Image : densité des spins
L’application d’une impulsion gradient après l’impulsion r.f. peut causer des distorsions (problème des courants induits) L’application du gradient avant l’impulsion r.f. entraîne une échelle de fréquences de Larmor trop large Alors, observation du signal d’un écho Écho de spins Écho de gradient
La méthode :
a) Sélectionner une région par excitation sélective b) Détecter les signaux c) Continuer la sélection et la détection d) Construire l’image
Donc, le signal RMN : FID
S (t ) = k ∫ ρ ( X ) exp(iγG X Xt ) exp(− t )dX T2
où k est une constante de proportionnalité, i = − − 1 , et ρ(X) est la distribution (projection) de la densité des spins sur X Quand t<<T1, l’effet de T2 est négligeable Transforme de Fourier du S(t) produit un spectre RMN qui représente la distribution de la densité des spins sur la direction X.
La phase des signaux est modulée par rapport à sa position
Spectre RMN 2D :
Préparation – 90º évolution – phase encoding détection frequency encoding
Pendant l’évolution, les spins précessent en présence d’un gradient Gy (variable) Æ période de « phase encoding ». Pendant la détection, les spins précessent sous l’influence de Gx Æ Période de « frequency encoding ». La fréquence angulaire des magnétisations
La tête ou partie du corps Animaux lapins, rats, souris Rats, souris Souris, insectes, polymères
1,0 – 4,7 – 14,1
< 12 < 2,5
~5 ×103 ~ 10–5
ωY = γGY Y
Donc, l’angle de phase pendant l’évolution ty
φY = γGY Yt
L’information positionnelle est enregistrée dans la phase des magnétisations au début de la période de détection. Æ S’il y a plusieurs éléments à détecter sur la direction Y, la méthode de « phase encoding » ne marche pas bien.
92
Concepts de base de l’imagerie RMN
Champ magnétique homogène : les spins précessent à une
fréquence angulaire particulière (fréquence de Larmor)
ω 0 = γB0
94
95
