翻译5000字
四级翻译练习参考译文

1. 刺绣(embroidery)是一种具有悠久传统的民间艺术,在中国艺术和手工艺品史上占有重要地位。
刺绣的长期发展离不开蚕的饲养与纺丝技术的发展。
中国是世界上第一个发现和使用丝绸的国家。
早在5000年前,中国就已经开始饲养蚕。
丝线和丝制品的生产促进了刺绣艺术的诞生。
时至今日,丝绣几乎传遍整个中国。
最好的绣品通常被认为来源于下面四省:江苏(尤其是苏州)、湖南、四川和广东,各省绣品各有特色。
Embroidery, a folk art with a long tradition, has an important position in the history of Chinese arts and crafts. During the course of its long development, embroidery has become inseparable from the raising of silkworms, silk reeling and weaving.China was the first country in the world where silk was woven. Silkworms were domesticated as early as some 5,000 years ago. The production of silk threads and fabrics gave rise to the art of embroidery. Today, silk embroidery is practiced nearly all over China. it is generally agreed that the best commercial products come for four provinces: Jiangsu(notably), Hunan, Sichuan and Guangdong , each with its distinctive features.2. 川剧(Sichuan Opera)就像四川火锅以及其他的名菜一样动人、丰富。
在线翻译工具DeepL
1. 工具简介DeepL是德国的一家为语言开发人工智能的深度学习公司,成立于2009年,原名Linguee,并推出了用于翻译的互联网搜索引擎。
Linguee曾应答了超过10亿用户的100多亿次查询。
2017年,公司推出了基于机器翻译系统的DeepL翻译器。
DeepL翻译器绝对是目前最受欢迎的翻译软件之一,最初的翻译服务主要以欧洲语系为主,后来加入了中文、日文的翻译。
目前支持简体中文、英语、德语、法语、日语、西班牙语等共26门语言之间的互译,并且可以翻译Word、PPT或者PDF格式的文件。
它使用了 AI 机器学习、神经网络算法、大数据等各种高大上的技术,自称“全世界最好的机器翻译”工具。
作为一款新时代的“AI”翻译软件,DeepL 最大的特点在于它利用了各种先进的人工智能技术、神经网络来不断训练和提升AI的翻译能力和准确性,解决“机器翻译质量差”的业界大难题,让用户能获得比同类工具更好的翻译结果。
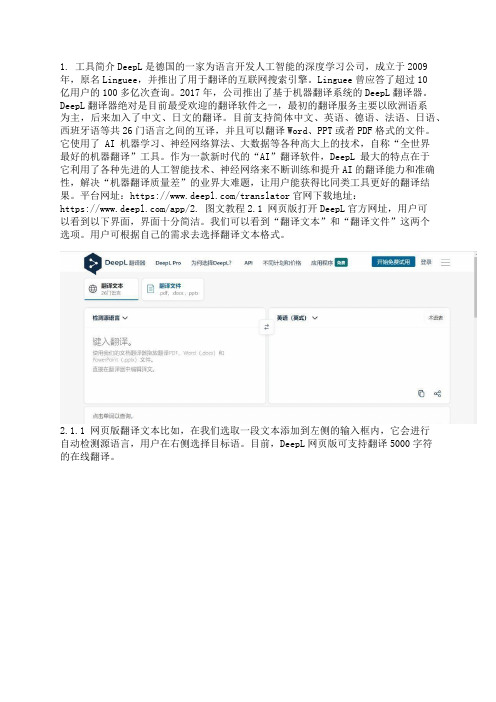
平台网址:https:///translator官网下载地址:https:///app/2. 图文教程2.1 网页版打开DeepL官方网址,用户可以看到以下界面,界面十分简洁。
我们可以看到“翻译文本”和“翻译文件”这两个选项。
用户可根据自己的需求去选择翻译文本格式。
2.1.1 网页版翻译文本比如,在我们选取一段文本添加到左侧的输入框内,它会进行自动检测源语言,用户在右侧选择目标语。
目前,DeepL网页版可支持翻译5000字符的在线翻译。
我们可以看到,不管是源语还是译入语,都有朗读功能。
当我们选定某一个字或者单词,下方出现多个查询结果。
而在右侧,当我们选定某个单词时,不仅在下方会有单词表,在译文中也会弹出其他选择,用户可自行选择替换。
当然,译文也支持复制以及分享。
用户也可以对译文进行评价。
当然,DeepL可以提供术语表,用户可以自行添加。
2.1.2 网页版翻译文件我们可以点击“从你的电脑上选择”或者将文件拖到框内,但温馨提示,DeepL免费版仅可翻译小于5Mb的文件。
驱动桥5000字外文翻译文献
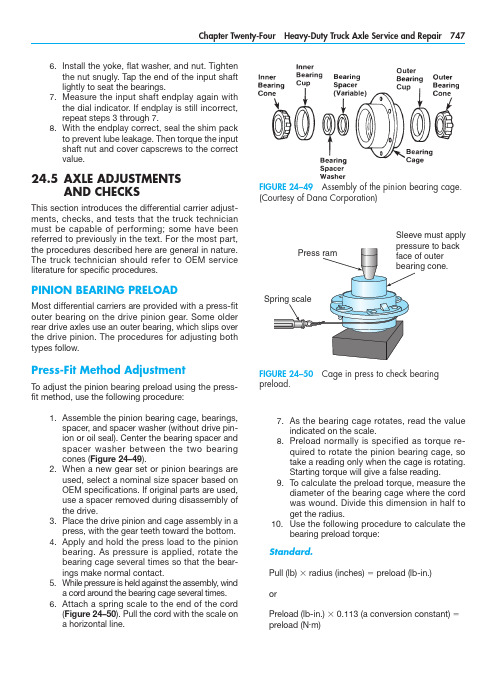
As the bearing cage rotates, read the value7. indicated on the scale.Preload normally is specified as torque re-8. quired to rotate the pinion bearing cage, so take a reading only when the cage is rotating. Starting torque will give a false reading.To calculate the preload torque, measure the 9. diameter of the bearing cage where the cord was wound. Divide this dimension in half to get the radius.10. U se the following procedure to calculate thebearing preload torque:Standard.Pull (lb) 3 radius (inches) 5 preload (lb-in.)orPreload (lb-in.) 3 0.113 (a conversion constant) 5 preload (N .m)Install the yoke, flat washer, and nut. Tighten 6. the nut snugly. Tap the end of the input shaft lightly to seat the bearings.Measure the input shaft endplay again with 7. the dial indicator. If endplay is still incorrect, repeat steps 3 through 7.With the endplay correct, seal the shim pack 8. to prevent lube leakage. Then torque the i nput shaft nut and cover capscrews to the correct value.24.5 A XLE ADJUSTMENTSAND CHECKSThis section introduces the differential carrier adjust-ments, checks, and tests that the truck technician must be capable of performing; some have beenr eferred to previously in the text. For the most part, the procedures described here are general in nature. The truck technician should refer to OEM servicel iterature for specific procedures.PINION BEARING PRELOADMost differential carriers are provided with a press-fit outer bearing on the drive pinion gear. Some older rear drive axles use an outer bearing, which slips over the drive pinion. The procedures for adjusting both types follow.Press-Fit Method AdjustmentTo adjust the pinion bearing preload using the press-fit method, use the following procedure:Assemble the pinion bearing cage, bearings, 1. spacer, and spacer washer (without drive pin-ion or oil seal). Center the bearing spacer and spacer washer between the two bearing cones (Figure 24–49).When a new gear set or pinion bearings are 2. used, select a nominal size spacer based on OEM specifications. If original parts are used, use a spacer removed during disassembly of the drive.Place the drive pinion and cage assembly in a 3. press, with the gear teeth toward the bottom.Apply and hold the press load to the pinion 4. bearing. As pressure is applied, rotate the bearing cage several times so that the bear-ings make normal contact.While pressure is held against the assembly, wind 5. a cord around the bearing cage several times.Attach a spring scale to the end of the cord 6. (Figure 24–50). Pull the cord with the scale ona horizontal line.FIGURE 24–49 Assembly of the pinion bearing cage.(Courtesy of Dana Corporation)FIGURE 24–50 Cage in press to check bearingp reload.Sleeve must applymust be against the outer bearing. If the fit between the yoke or flange splines and drive pinion splines is tight, use a press to install the yoke or flange (Figure 24–51).Temporarily install the drive pinion and cage 4. assembly in the carrier (Figure 24–52). Do not install shims under the bearing cage.Install the bearing cage to the carrier cap-5. screws. Washers are not required at this time. Hand-tighten the capscrews.Fasten a yoke or flange bar to the yoke or 6. flange (Figure 24–53). The bar will hold the drive pinion in position when the nut ist ightened.Metric.Pull (kg) 3 radius (cm) 5 preload (kg-cm) orPreload (kg-cm) 3 0.098 (a conversion constant) 5 preload (N .m)Examples. We can convert the foregoing equa-tions into examples by applying some data to them:Standard7.5 lb 3 3.31 in. 5 24.8 lb-in. (preload) or24.8 lb-in. 3 0.113 5 2.8 N .m (preload)Metric3.4 kg 3 8.4 cm 5 28.6 kg-cm (preload) or28.6 kg-cm 3 0.098 5 2.8 N .m (preload)11. I f necessary, adjust the pinion bearing preloadby changing the pinion bearing spacer. A thicker spacer will decrease preload, whereas a thinner spacer will increase the preload.12. O nce the correct bearing preload has beenestablished, note the spacer size used. Select a spacer 0.001 inch (0.025 mm) larger for use in the final pinion bearing cage assembly pro-cedures. The larger spacer compensates for slight expansion of the bearing, which occurs when pressed on the pinion shank. The trial spacer pack should result in correct pinion bearing preload in three times out of four cases.Y oke Method of AdjustmentTo adjust the pinion bearing preload using the yoke or flange method, proceed as follows:Assemble the complete pinion bearing cage 1. as recommended in the press-fit method.A forward axle pinion is equipped with a heli-2. cal gear. For easier disassembly during bear-ing adjustment procedures, use a dummy yoke (if available) in place of the helical gear.Install the input yoke or flange, nut, and 3.washer on the drive pinion. The yoke or flangeFIGURE 24–51 Using a press to install the yoke orflange to the drive pinion. (Courtesy of Arvin Meritor)FIGURE 24–52 Install the pinion and cage assembly in the carrier housing. (Courtesy of Arvin Meritor)indicated on the torque wrench (see Figure 24–55). Typical value is 50 lb-ft. (68 N .m)m aximum applied to one side gear.If the torque value exceeds the specification, 5. disassemble the differential gears from the case halves.Check the case halves, spider, gears, and 6. thrust washers for the problem that caused the torque value to exceed specifications. Re-pair or replace defective parts as required. Remove any foreign debris.Check/Adjust Pinion Cage Shim PackThis procedure is used to check and adjust the thick-ness of the shim pack used in the pinion bearing cage. Use this procedure if a new drive pinion and crownTighten the nut on the drive pinion to specifi-7. cation, typically 400 to 700 lb-ft. (542 to 950 N .m).Remove the yoke or flange bar.8. Attach a torque wrench to the drive pinion 9. nut. Rotate the drive pinion and read the value indicated on the torque wrench. Preload is correct when the torque required to rotate the pinion bearing cage is from 15 to 35 lb-in. (1.7 to 4.0 N .m).To adjust the pinion bearing preload, disas-10. semble the pinion bearing cage and change the pinion bearing spacer size. A thicker spacer will decrease preload, whereas a thin-ner spacer will increase preload.Differential Rolling ResistanceA check to measure and establish differential rolling resistance follows. To perform this check, a special tool must be made. You can easily make this tool from an old axle shaft that matches the spline size of the differential side gear. Figure 24–54 illustrates the fab-rication specifications for this special tool.To check differential resistance to rotation, use the following procedure:Install soft metal covers over the vise jaws to 1. protect the ring gear (Figure 24–55).Place the differential and crown gear assem-2. bly in the vise.Install the special tool into the differential until 3. the splines of the tool and one side gear are engaged.Attach a torque wrench to the nut of the spe-4. cial tool and rotate the differential gears. As the differential gears rotate, read the valueFIGURE 24–55 Reading the torque value to check the rolling resistance. (Courtesy of Arvin Meritor)FIGURE 24–53 Using a flange bar to hold the drivepinion in position. (Courtesy of Arvin Meritor)FIGURE 24–54 Fabrication details for a tool to checkthe rolling resistance. (Courtesy of Arvin Meritor)If the new pinion cone number is a minus (–), sub-8. tract the number from the standard shim packthickness that was calculated in step 3 or 4.The value calculated in step 7 or 8 is the 9.t hickness of the new shim pack that will bei nstalled. Figure 24–59 illustrates several e xamples of determining shim pack t hickness.Install the drive pinion, bearing cage, and new10. shim pack into the differential carrier.gear set is to be installed, or if the depth of the drive pinion has to be adjusted. You are checking the rolling resistance using a torque wrench.To check/adjust the shim pack thickness (Figure 24–56), do the following:With a micrometer, measure the thickness of 1. the old shim pack removed from under the pinion cage (Figure 24–57). Record the mea-surement for later use.Look at the pinion cone (PC) variation number 2. on the drive pinion being replaced (Figure 24–58). Record this number for later use also.If the old pinion cone number is a plus (+), 3. subtract the number from the old shim pack thickness that was recorded in step 1.If the old pinion cone number is a minus (–), 4. add the number to the old shim thickness that was measured in step 1.The value calculated in step 3 or 4 is the 5.t hickness of the standard shim pack without variation.Look at the PC variation number on the new 6. drive pinion that will be installed. Record the number for later use.If the new pinion cone number is a plus (+), 7. add the number to the standard shim packthickness that was calculated in step 3 or 4.FIGURE 24–56 Drive pinion depth controlled by shimpack thickness. (Courtesy of Arvin Meritor)FIGURE 24–57 Measuring the thickness of the old shim pack. Mike each shim individually then add tocalculate total thickness. (Courtesy of Arvin Meritor)FIGURE 24–58 Location of the pinion cone (PC)v ariation number. (Courtesy of Arvin Meritor)Adjust Differential Bearing PreloadOne of two methods can be used to check and adjust the preload of the differential bearings.Method One.Attach a dial indicator onto the mounting 1. flange of the carrier and adjust the indicator so that the plunger rides on the back surface of the crown ring gear (Figure 24–60).Loosen the bearing adjusting ring that is op-2. posite the ring gear so that a small amount of endplay is indicated on the dial indicator. To turn the adjusting rings, use a T-bar wrench that engages two or more opposite notches in the ring (Figure 24–61).Move the differential and crown gear to the 3. left and right using prybars as you read the dial indicator. Use two prybars that fit be-tween the bearing adjusting rings and the ends of the differential case (Figure 24–62). You also can use two prybars between the differential case or crown gear and the carrier at locations other than those just described. In either case, the prybars must not touch the differential bearings.EXAMPLES:Inchesmm 1.Old Shim Pack Thickness Old PC Number, PC +2Standard Shim Pack Thickness New PC Number, PC +5New Shim Pack Thickness .030.76–.002–.05.028.71+.005+.13.033.842.Old Shim Pack Thickness Old PC Number, PC –2Standard Shim Pack Thickness New PC Number, PC +5New Shim Pack Thickness .030.76+.002+.05.032.81+.005+.13.037.943.Old Shim Pack Thickness Old PC Number, PC +2Standard Shim Pack Thickness New PC Number, PC –5New Shim Pack Thickness .030.76–.002–.05.028.71–.005–.13.023.584.Old Shim Pack Thickness Old PC Number, PC –2Standard Shim Pack Thickness New PC Number, PC –5New Shim Pack Thickness.030.76+.002+.05.032.81–.005–.13.027.68FIGURE 24–59 Determining shim pack thickness.(Courtesy of ArvinMeritor Inc.)FIGURE 24–60 Dial indicator attached to carrier-mounted flange. (Courtesy of Arvin Meritor)FIGURE 24–61 Turning the adjusting ring using aT-bar wrench. (Courtesy of Arvin Meritor)FIGURE 24–62 Using pry bars to adjust play in the crown gear. (Courtesy of Arvin Meritor)Tighten the same bearing adjusting ring4.so that no endplay shows on the diali ndicator.Move the differential and crown gear to the5.left and right as needed. Repeat step 3 untilzero endplay is achieved.Tighten each bearing adjusting ring one6.notch from the zero endplay measured instep 4.Method Two.A second method of checking pre-load is to measure the expansion between the bearing caps after you tighten the adjusting rings. Use the following procedure:Turn both adjusting rings hand tight against1.the differential bearings.Measure the distance X or Y between oppo-2.site surfaces of the bearing caps (Figure24–63A) using a large micrometer of thec orrect size (Figure 24–63B). Make a note ofthe m easurement.Tighten each bearing adjusting ring one3.notch.Measure the distance X or Y again. Compare4.the dimension with the distance X or Y mea-sured in step 2. The difference between thetwo dimensions is the amount that the bear-ing caps have expanded.Example: Measurements of a carrier.Distance X or Y before tightening adjusting rings5 15.315 inches (389.00 mm)Distance X or Y after tightening adjusting rings5 15.324 inches (389.23 mm)15.324 inches minus 15.315 inches5 0.009 inch (0.23 mm) differenceIf the dimension is less than specification, repeat steps 3 and 4 as needed.Crown Gear Runout CheckTo check the runout of the crown/ring gear, do the f ollowing:Attach a dial indicator on the mounting flange1.of the differential carrier (Figure 24–64).Adjust the dial indicator so that the plunger or2.pointer is against the back surface of thecrown gear.FIGURE 24–63 (A) Location of distances measured to check expansion between bearing caps aftert ightening adjusting rings; (B) measuring this distance.(Courtesy of Arvin Meritor)FIGURE 24–64 Checking crown gear runout. (Courtesy of Arvin Meritor)Pinion and Crown Tooth ContactA djustment Correct tooth contact between the pinion and crown gear cannot be overemphasized, because improper tooth contact results in noisy operation and prema-ture failure. The tooth contact pattern consists of the lengthwise bearing (along the tooth of the ring gear) and the profile bearing (up and down the tooth). F igure 24–68 shows crown gear toothn omenclature.Adjust the dial of the indicator to zero.3. Rotate the differential and crown gear when4. reading the dial indicator. The runout of the crown gear must not exceed 0.008 inch (2 mm) (a typical value; refer to the applicable OEM service literature for the specificv alues).If runout of the crown gear exceeds the speci-5. fication, remove the differential and crown gear assembly from the carrier. Check the dif-ferential components, including the carrier, for the problem causing the runout of the gear to exceed specification. Repair or replace defec-tive components.After the components are repaired or re-6. placed, install the differential and crown gear into the carrier.Repeat the preload adjustment of the 7. differential bearings. Then repeat this runout procedure.Check/Adjust Crown Gear BacklashIf the used crown and pinion gear set is installed, ad-just the backlash to the setting that was measured before the carrier was disassembled. If a new gear set is to be installed, adjust backlash to the correct speci-fication for the new gear set.To check and adjust ring gear backlash, do thef ollowing: Attach a dial indicator onto the mounting1. flange of the carrier (see Figure 24–64).Adjust the dial indicator so that the plunger is 2. against the tooth surface at a right angle.Adjust the dial of the indicator to zero, making 3. sure that the plunger is loaded through at least one revolution.Hold the drive pinion in position.4. When reading the dial indicator, rotate the5. crown gear a small amount in both directions against the teeth of the drive pinion (Figure 24–65). If the backlash reading is not within specification (typically ranging from 0.010 to 0.020 inch or 254 to 508 mm), adjust backlash as outlined in steps 6 and 7.Loosen one bearing adjusting ring one notch 6. and then tighten the opposite ring the same amount. Backlash is increased by moving the crown gear away from the drive pinion (Figure 24–66). Backlash is decreased by moving the crown gear toward the drive pin-ion (Figure 24–67).Repeat steps 2 through 5 until the backlash is 7.within specifications.FIGURE 24–65 Check crown gear backlash. ( Courtesy of Arvin Meritor)FIGURE 24–66 Adjustments to increase backlash. (Courtesy of Arvin Meritor)the pattern in an unloaded condition (such as when you are performing this test) will be approximately one-half to two-thirds of the crown gear tooth in most models and ratios.Checking Tooth Contact Pattern on a Used Gear Set. Used gearing will not usually display the square, even contact pattern found in new gear sets. The gear will normally have a pocket at the toe-end of the gear tooth (Figure 24–71) that tails into a contact line along the root of the tooth. The more use a gear has had, the more the line becomes the dominant characteristic of the pattern.Adjusting Tooth Contact Pattern. When dis-assembling, make a drawing of the gear tooth con-tact pattern so that when reassembling it is possible to replicate approximately the same pattern. A cor-rect pattern should be clear of the toe and centers evenly along the face width between the top land and the root. Otherwise, the length and shape of the pattern can be highly variable and are usually con-sidered acceptable—providing the pattern does not run off the tooth at any time. If necessary, adjust the contact pattern by moving the crown gear and drive pinion.Checking Tooth Contact Pattern on a New Gear Set. Paint 12 crown gear teeth with a marking compound (Figure 24–69) and roll the gear to obtain a tooth contact pattern. A correct pattern should be well centered on the crown gear teeth with lengthwise contact clear of the toe (Figure 24–70). The length ofFIGURE 24–67 Adjustments to decrease backlash.(Courtesy of Arvin Meritor)FIGURE 24–68 Crown gear tooth nomenclature.(Courtesy of Dana Corporation)FIGURE 24–69 Application of a marking compoundto check tooth contact. (Courtesy of Dana Corporation)FIGURE 24–70 Correct tooth contact patternfor new gearing. (Courtesy of Dana Corporation)FIGURE 24–71 Correct tooth contact pattern for used gearing. (Courtesy of Dana Corporation)making adjustments, first adjust the pinion and then the backlash. Continue this sequence until the pattern is satisfactory.Thrust Screw AdjustmentFor those differential carriers equipped with a thrust screw, perform the following procedure. (If the carrier assembly does not have a thrust block, proceed to step 4 of this procedure.)Rotate the carrier in the repair stand until the 1. back surface of the crown gear is toward the top.Put the thrust block on the back surface of 2. the ring gear. The thrust block must be in the center between the outer diameter of the gear and the differential case.Rotate the crown gear until the thrust block 3. and hole for the thrust screw, in the carrier, are aligned.Install the jam nut on the thrust screw, one-4. half the distance between both ends (Figure 24–74).Install the thrust screw into the carrier until the 5. screw stops against the crown gear or thrust block.Loosen the thrust screw one-half turn, or 180 6. degrees.Tighten the jam nut to the correct torque value 7. against the carrier (typical values range from 150 to 295 lb-ft. or 200 to 400 N .m) (Figure 24–75).Axle TrackingAxle tracking can be measured using the older tram bar method or electronic alignment equipment. The procedures for setting axle alignment and tracking areexplained in Chapter 25.FIGURE 24–72 Two incorrect patterns when adjusting pinion position. (Courtesy of Dana Corporation)Crown gear position controls the backlash setting. This adjustment also moves the contact pattern along the face width of the gear tooth (Figure 24–72). Pinion position is determined by the size of the pinion bear-ing cage shim pack. It controls contact on the tooth depth of the gear tooth (Figure 24–73).These adjustments are interrelated. As a result, they must be considered together even though thepattern is altered by two distinct operations. WhenFIGURE 24–73 Two incorrect patterns when adjusting backlash. (Courtesy of Dana Corporation)• Most differential carriers are replaced as rebuilt/exchange units, so the role of the technician is, more often than not, to diagnose the problem and then, if necessary, to replace the defective assembly as a unit.• The technician who has disassembled and reas-sembled differential carriers should find trouble-shooting procedures easier to follow.• Follow the OEM procedure when disassem-bling differential carriers. Taking a few mo-ments to measure shim packs and gear tooth contact patterns on disassembly can save considerable time when reassembling thec arrier.• A crown and pinion gear set often can ber eused when rebuilding a differential carrier. Make sure that you inspect it properly ond isassembly.• Crown and pinion gear sets are always replaced as a matched pair during a rebuild.• When setting crown and pinion backlash, it is increased by moving the crown gear away from the drive pinion and decreased by moving the crown gear toward the drive pinion.• Adhering to OEM-recommended lubrication schedules is the key to ensuring the longest service life from both drive and dead axles.• Knowing the correct procedure to check lubricant level is essential. The level is correct when lubri-cant is exactly level with the bottom of the fill hole.• Because most OEMs approve of the use of syn-thetic lubricants in final drive carriers, lubrication drain schedules have been greatly increased in recent years. Drain schedules are determined by the actual lubricant used and the type of appli-cation to which the vehicle is subjected.• Servicing of axles on heavy-duty trucks consists of routine inspection, lubrication, cleaning, and, when required, troubleshooting and component overhaul.• Failure analysis is required to prevent recurrent failures.• Drive axle carrier components usually fail for one of the following reasons: Shock load Fatigue Spinout Lubrication problemsNormal wearFIGURE 24–74 Installing the jam nut on the thrust screw. (Courtesy of Arvin Meritor)FIGURE 24–75 Tighten the jam nut to the correct torque value. (Courtesy of Arvin Meritor)SUMMARY。
英语报告范文带翻译(实用

英语报告范文带翻译(实用英语报告范文格式篇一(一)date and placeminister of _____ (address) beijing,chinadear minister,i am writing this letter to thank you for youwarm hospitality accorded to me and my delegation during our recent visit to your beautiful country. i would also like to thank you for your interestingdiscussion with me which i have found very informative and the entire visit, my delegation and i wereoverwhelmed by the enthusiasm expressed by your businessrepresentatives on cooperation with china. i sincerelyhope we could have more exchanges like this one when wewould be able to continue our interesting discussion on possible ways to expand our bilateral economic and traderelations and bring our business people together.i am looking forward to your early visit to chinawhen i will be able to pay back some of the hospitalityi received during my memorable stay in yur beautifulcountry. with kind personal regards,faithfully yours,(signed)minister of economic cooperation(二)placedear mr/ms,thank you for your letter of june 4, enclosing an account of the organization and work of your chamber of merce and are very grateful for such a detailed account of your activities. this information is certain to help increase our future cooperation.yours faithfully英语报告类作文格式篇二一、实习岗位我被分配在翻译协会里任职,所以我们就在学校里拿到了老师发给我们的翻译材料。
《古代汉语》——《说文解字叙》原文+翻译 5000字

《说文解字叙》原文+翻译古者庖犧氏之王天下也,仰則觀象於天,俯則觀法於地,視鳥獸之文與地之宜,近取諸身,遠取諸物,於是始作《易》八卦,以垂憲象。
及神農氏結繩為治而統其事,庶業其繁,飾偽萌生。
黃帝之史倉頡,見鳥獸蹄迒之跡,知分理之可相別異也,初造書契。
“百工以乂,萬品以察,蓋取諸夬”,夬,“揚于王庭”。
言文者,宣教明化於王者朝廷,君子所以施祿及下,居德則忌也。
倉頡之初作書,蓋依類象形,故謂之文。
其後形聲相益,即謂之字。
文者,物象之本;字者,言孳乳而浸多也。
著於竹帛謂之書。
書者,如也。
以迄五帝三王之世,改易殊體。
封于泰山者七十有二代,靡有同焉。
《周禮》:八歲入小學,保氏教國子,先以六書。
一曰指事,指事者,視而可識,察而可見,上下是也;二曰象形,象形者,畫成其物,隨體詰詘,日月是也;三日形聲,形聲者,以事為名,取譬相成,江河是也;四日會意,會意者,比類合誼,以見指撝,武信是也;五日轉注,轉注者,建類一首,同意相受,考老是也;六日假借,假借者,本無其字,依聲託事,令長是也。
及宣王太史籀著《大篆》十五篇,與古文或異;至孔子書《六經》,左丘明述《春秋傳》,皆以古文,厥意可得而說。
其後,諸侯力政,不統於王,惡禮樂之害己,而皆去其典籍,分為七國,田疇異畮,車塗異軌,律令異法,衣冠異制,言語異聲,文字異形。
秦始皇初兼天下,丞相李斯乃奏同之,罷其不與秦文合者。
斯作《倉頡篇》,中車府令趙高作《爰曆篇》,太史令胡毋敬作《博學篇》,皆取史籀大篆,或頗省改,所謂小篆者也。
是時,秦燒滅經書,滌除舊典,大發隸卒,興役戍,官獄職務日繁,初有隸書,以趣約易,而古文由此絕矣。
自爾秦書有八體:一曰大篆,二曰小篆,三曰刻符,四曰蟲書,五曰摹印,六曰署書,七曰殳書,八曰隸書。
漢興,有艸書。
尉律:學僮十七已上,始試,諷籀書九千字乃得為吏,又以八體試之。
郡移太史並課,最者以為尚書史。
書或不正,輒舉劾之。
今雖有尉律,不課,小學不修,莫達其說久矣。
DeepL翻译真的比谷歌、有道、百度翻译都好用?来测评一波!

DeepL翻译真的比谷歌、有道、百度翻译都好用?来测评一波!DeepL翻译已经出来有一段时间了,官方网站被称为世界上最好的翻译机器,大大领先于其他竞争对手。
DeepL翻译图片所谓的”盲测”也就是说,当专业翻译评论员不知道哪个翻译版本是由哪个网站翻译的时候,翻译文本的评估一直是这样的DeepL测试方法之一。
DeepL由于精度极佳,也引爆了Reddit,有网友指出,DeepL不像谷歌翻译那样从单词上翻译,从Textractor可以在设置上看到,DeepL还支持以前的翻译作为上下文来改进翻译结果。
德国的硬核翻译工具DeepL体验DeepL这是一种来自德国的在线翻译工具,早在2017年就上线了(请原谅我的无知)。
它的外观与其他翻译工具相似,反应速度也很快OK!鼠标点击翻译时,左侧原文区会自动亮起,方便用户检查翻译结果。
DeepL界面不过DeepL并没有像Google像翻译这样的内置单词翻译在日常工作中仍然会显得有点不方便。
然而,我非常喜欢它的一键下载,它可以直接将翻译结果转换为TXT文档,保存,分享都很方便。
虽然第一印象还是不错的,但是对于一个翻译工具来说,翻译质量才是最重要的我们来看看。
但是真的像网友说的那样吗?今天我们请出来Google翻译,Baidu比较翻译、有道等主流翻译服务。
评测一:是骡子是马拉出来遛遛便知道了。
原句是骡子是马拉出来遛遛便知道了。
DeepLIt's a mule or a horse out for a walk, you'll see.谷歌It was the mule and the horse that came out and walked and knew.百度It's a mule or a horse that you know when you pull it out.搜狗It's a mule. It's a horse. Just pull it out for a walk.有道It's a mule or a horse that comes out for a walk.从五个翻译结果来看,很难区分胜负。
翻译服务收费标准

翻译服务收费标准一、笔译人民币元/千字中文( 加急加收30% —70% ,专业加收50% ) 语种中译外外译中外译外英语170 140 面议日语170 140韩语190 160德语220 180俄语220 180法语220 180意大利语280 250西班牙语280 250葡萄牙语290 260阿拉伯语350 320越南语430 400荷兰语510 460波兰语380-480 360-40塞尔维亚语370-470 420-530泰国语260-380 280-520老挝语320-420 370-480印度语320-420 370-480希腊语370-470 420-530哈萨克语280-380 300-410瑞典语300-400 340-450丹麦语320-420 370-470印度尼西亚语330-450 350-460蒙古语300-400 350-4601、字数计算:以中文版稿件在Windows word文档显示的字符数(不计空格)为基准。
也即包含了标点符号,因其为理解语义的必需。
2、图表计算:图表按每个A4页面,按页酌情计收排版费用。
3、外文互译:按照中文换算,即每个拉丁单词乘以二等于相应的中文字数。
4、日翻译量:正常翻译量3000-5000字/日/人,超过正常翻译量按专业难易受20%加急费.5、付款方式:按预算总价的20%收取定金,按译后准确字数计总价并交稿付款。
6、注意事项:出差在原价格上增加20%,客户负责翻译的交通、食宿和安全费用。
二、口译价格:(1) 交传报价(元/人/天,加小时按100-150元/小时加收费用)类型英语德、日、法、俄、韩小语种一般活动700 800 1500商务活动500-1200 500-1500 800-3000中小型会议1200-3000 1500-3000 2500-3000大型会议1200-4000 2500-6000 4000-9000(2) 同传报价(元/人/天)类别中-英互译日、韩、德、俄、法、韩-中互译小语种-中互译商务会议5000-8000 6000-10000 8000-10000中小型会议5500-8000 7000-12000 8000-12000大型国际会议6000-9000 8000-12000 12000-16000。
段落翻译(原文+译文)

段落翻译(原文+译文)1. 参与并取胜,这就是奥林匹克精神。
他表现于弱者敢于向强者挑战,也表现于强者力争取得更好的成绩。
胜而又胜,优而更优,这种理想一直鼓舞着运动员奋力前进。
他会尽其所能,争取优胜,永不松懈,永不罢休。
有人说竞技者终究逃脱不了失败,即使是最佳运动员也会被更强者所淘汰——这就是竞技运动的规律。
然而运动员却从不为这种不可避免的失败而气馁,仍然奋力拼搏争取最佳发挥。
并对自己在奥林匹克运动中为争取更好成绩已尽了一份力而心满意足。
他会自豪地说他的青春没有虚度。
(221字)【参考译文】To participate and win — that is the Olympic spirit. It finds expression in the weak daring to defy the strong, and the strong striving for ever better performance. “Ever better”— the ideal is always luring a sportsman forward. He will do everything he can for it, never relax, never give up. It is said that none of the competitors can avoid being defeated — even the best is to be surpassed by someone still stronger. This is rule of sports. However, undaunted by the inevitable failure, the sportsman is always striving to do the best he can and content with the fact that he has done his bit for the “ever better” records in the Olympic Games. He will say proudly that he has not lived his youth in vain.(陈艳粉供稿)2. 中国,一个值得自豪的文明古国,大约有5000年悠久和神秘的历史。
五分钟搞定5000字-外文文献翻译

五分钟搞定5000字-外文文献翻译在科研过程中阅读翻译外文文献是一个非常重要的环节,许多领域高水平的文献都是外文文献,借鉴一些外文文献翻译的经验是非常必要的。
由于特殊原因我翻译外文文献的机会比较多,慢慢地就发现了外文文献翻译过程中的三大利器:Google“翻译”频道、金山词霸(完整版本)和CNKI“翻译助手"。
具体操作过程如下:1.先打开金山词霸自动取词功能,然后阅读文献;2.遇到无法理解的长句时,可以交给Google处理,处理后的结果猛一看,不堪入目,可是经过大脑的再处理后句子的意思基本就明了了;3.如果通过Google仍然无法理解,感觉就是不同,那肯定是对其中某个“常用单词”理解有误,因为某些单词看似很简单,但是在文献中有特殊的意思,这时就可以通过CNKI的“翻译助手”来查询相关单词的意思,由于CNKI的单词意思都是来源与大量的文献,所以它的吻合率很高。
另外,在翻译过程中最好以“段落”或者“长句”作为翻译的基本单位,这样才不会造成“只见树木,不见森林”的误导。
注:1、Google翻译:/language_tools google,众所周知,谷歌里面的英文文献和资料还算是比较详实的。
我利用它是这样的。
一方面可以用它查询英文论文,当然这方面的帖子很多,大家可以搜索,在此不赘述。
回到我自己说的翻译上来。
下面给大家举个例子来说明如何用吧比如说“电磁感应透明效应”这个词汇你不知道他怎么翻译,首先你可以在CNKI里查中文的,根据它们的关键词中英文对照来做,一般比较准确。
在此主要是说在google里怎么知道这个翻译意思。
大家应该都有词典吧,按中国人的办法,把一个一个词分着查出来,敲到google里,你的这种翻译一般不太准,当然你需要验证是否准确了,这下看着吧,把你的那支离破碎的翻译在google里搜索,你能看到许多相关的文献或资料,大家都不是笨蛋,看看,也就能找到最精确的翻译了,纯西式的!我就是这么用的。
翻译服务收费标准

翻译服务收费标准一、笔译人民币元/千字中文( 加急加收30% —70% ,专业加收50% ) 语种中译外外译中外译外英语170 140 面议日语170 140韩语190 160德语220 180俄语220 180法语220 180意大利语280 250西班牙语280 250葡萄牙语290 260阿拉伯语350 320越南语430 400荷兰语510 460波兰语380-480 360-40塞尔维亚语370-470 420-530泰国语260-380 280-520老挝语320-420 370-480印度语320-420 370-480希腊语370-470 420-530哈萨克语280-380 300-410瑞典语300-400 340-450丹麦语320-420 370-470印度尼西亚语330-450 350-460蒙古语300-400 350-4601、字数计算:以中文版稿件在Windows word文档显示的字符数(不计空格)为基准。
也即包含了标点符号,因其为理解语义的必需。
2、图表计算:图表按每个A4页面,按页酌情计收排版费用。
3、外文互译:按照中文换算,即每个拉丁单词乘以二等于相应的中文字数。
4、日翻译量:正常翻译量3000-5000字/日/人,超过正常翻译量按专业难易受20%加急费.5、付款方式:按预算总价的20%收取定金,按译后准确字数计总价并交稿付款。
6、注意事项:出差在原价格上增加20%,客户负责翻译的交通、食宿和安全费用。
二、口译价格:(1) 交传报价(元/人/天,加小时按100-150元/小时加收费用)类型英语德、日、法、俄、韩小语种一般活动700 800 1500商务活动500-1200 500-1500 800-3000中小型会议1200-3000 1500-3000 2500-3000大型会议1200-4000 2500-6000 4000-9000(2) 同传报价(元/人/天)类别中-英互译日、韩、德、俄、法、韩-中互译小语种-中互译商务会议5000-8000 6000-10000 8000-10000中小型会议5500-8000 7000-12000 8000-12000大型国际会议6000-9000 8000-12000 12000-16000。
翻译报价一般标准
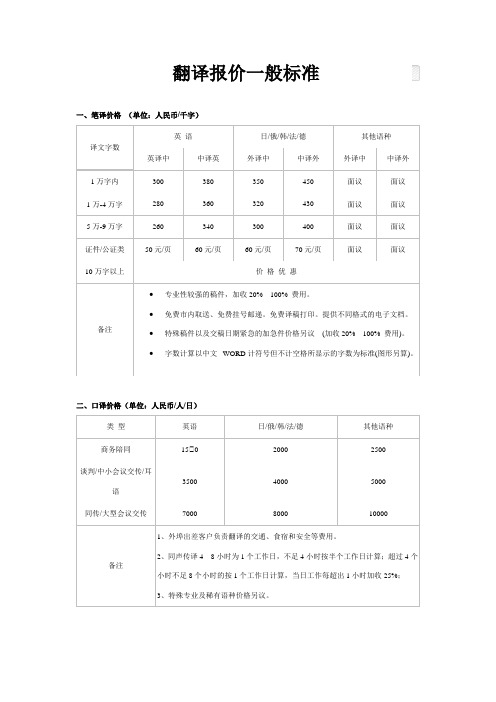
四、电影、电视剧本,录音带、VCD 等音频、视频翻译价格 语 种 英译中 中译英 其他语种 备注 价 格 100-200 元/分钟 150-300 元/分钟 200-300 元/分钟 提供非编、配音及各种后期处理。
翻译报价一般标准
一、笔译价格 (单位:人民币/千字) 英 语 译文字数 英译中 1 万字内 1 万-4 万字 5 万-9 万字 证件/公证类 10 万字以上 300 280 260 50 元/页 中译英 380 360 340 60 元/页 外译中 350 320 300 60 元/页 中译外 450 430 400 70 元/页 外译中 面议 面议 面议 面议 中译外 面议 面议 面议 面议 日/俄/韩/法/德 食宿和安全等费用。 2、同声传译 4—8 小时为 1 个工作日,不足 4 小时按半个工作日计算;超过 4 个 备注 小时不足 8 个小时的按 1 个工作日计算,当日工作每超出 1 小时加收 25%; 3、特殊专业及稀有语种价格另议。
三、网站翻译价格(由三部分组成,即页面翻译制作费用和文本、图形翻译费用) 翻译制作费用 文本部分 图形部分 以网页页面计,即一个 HTML、ASP、PHP 等类似文档,平均 300 元人民币/页面 文本部分与常规翻译收费相同,详细请查看翻译报价。 如客户无特殊要求则不收费,如有其它要求费用另议。
价 格 优 惠
• •
备注
专业性较强的稿件,加收 20%—100% 费用。 免费市内取送、免费挂号邮递。免费译稿打印。提供不同格式的电子文档。 特殊稿件以及交稿日期紧急的加急件价格另议 (加收 20%—100% 费用)。
• •
字数计算以中文 WORD 计符号但不计空格所显示的字数为标准(图形另算)。
二、口译价格(单位:人民币/人/日) 类 型 商务陪同 谈判/中小会议交传/耳 3500 语 同传/大型会议交传 7000 8000 10000 4000 5000 英语 15 0 日/俄/韩/法/德 2000 其他语种 2500
关于单片机的5000字英文翻译

英文资料翻译题目An overview of microcontroller系别电子工程学院.专业设备运行与管理.班级设备1101 .学生姓名姜凯凯.学号100110145 .指导教师袁惠娟2013年12 月An overview of microcontrollerDescriptionThe AT89C51 is a low-power, high-performance CMOS 8-bit microcomputer with 4K bytes of Flash programmable and erasable read only memory (PEROM). The device is manufactured using Atmel’s high-density nonvolatile memory technology and is compatible with the industry-standard MCS-51 instruction set and pinout. The on-chip Flash allows the program memory to be reprogrammed in-system or by a conventional nonvolatile memory programmer. By combining a versatile 8-bit CPU with Flash on a monolithic chip, the Atmel AT89C51 is a powerful microcomputer which provides a highly-flexible and cost-effective solution to many embedded control applications.Function characteristicThe AT89C51 provides the following standard features: 4K bytes of Flash, 128 bytes of RAM, 32 I/O lines, two 16-bit timer/counters, a five vector two-level interrupt architecture, a full duplex serial port, on-chip oscillator and clock circuitry. In addition, the AT89C51 is designed with static logic for operation down to zero frequency and supports two software selectable power saving modes. The Idle Mode stops the CPU while allowing the RAM, timer/counters, serial port and interrupt system to continue functioning. The Power-down Mode saves the RAM contents but freezes the oscillator disabling all other chip functions until the next hardware reset. Pin DescriptionVCC:Supply voltage.GND:Ground.Port 0:Port 0 is an 8-bit open-drain bi-directional I/O port. As an output port, each pin can sink eight TTL inputs. When 1s are written to port 0 pins, the pins can be used as highimpedance inputs.Port 0 may also be configured to be the multiplexed loworderaddress/data bus during accesses to external program and data memory. In this mode P0 has internal pullups.Port 0 also receives the code bytes during Flash programming,and outputs the code bytes during programverification. External pullups are required during programverification.Port 1:Port 1 is an 8-bit bi-directional I/O port with internal pullups.The Port 1 output buffers can sink/source four TTL inputs.When 1s are written to Port 1 pins they are pulled high by the internal pullups and can be used as inputs. As inputs,Port 1 pins that are externally being pulled low will source current (IIL) because of the internal pullups.Port 1 also receives the low-order address bytes during Flash programming and verification.Port 2:Port 2 is an 8-bit bi-directional I/O port with internal pullups.The Port 2 output buffers can sink/source four TTL inputs.When 1s are written to Port 2 pins they are pulled high by the internal pullups and can be used as inputs. As inputs,Port 2 pins that are externally being pulled low will source current, because of the internal pullups.Port 2 emits the high-order address byte during fetches from external program memory and during accesses to external data memory that use 16-bit addresses. In this application, it uses strong internal pullupswhen emitting 1s. During accesses to external data memory that use 8-bit addresses, Port 2 emits the contents of the P2 Special Function Register.Port 2 also receives the high-order address bits and some control signals during Flash programming and verification.Port 3:Port 3 is an 8-bit bi-directional I/O port with internal pullups.The Port 3 output buffers can sink/source four TTL inputs.When 1s are written to Port 3 pins they are pulled high by the internal pullups and can be used as inputs. As inputs,Port 3 pins that are externally being pulled low will source current (IIL) because of the pullups.Port 3 also serves the functions of various special features of the AT89C51 as listed below:Port 3 also receives some control signals for Flash programming and verification. RST Reset input. A high on this pin for two machine cycles while the oscillator is running resets the device.ALE/PROG Address Latch Enable output pulse for latching the low byte of the address during accesses to external memory. This pin is also the program pulse input (PROG) during Flash programming.In normal operation ALE is emitted at a constant rate of 1/6 the oscillator frequency, and may be used for external timing or clocking purposes. Note, however, that one ALE pulse is skipped during each access to external Data Memory.If desired, ALE operation can be disabled by setting bit 0 of SFR location 8EH. With the bit set, ALE is active only during a MOVX or MOVC instruction. Otherwise, the pin is weakly pulled high. Setting the ALE-disable bit has no effect if the microcontroller is in external execution mode.PSEN Program Store Enable is the read strobe to external program memory.When the AT89C51 is executing code from external program memory, PSEN is activated twice each machine cycle, except that two PSEN activations are skipped during each access to external data memory.EA/VPP External Access Enable. EA must be strapped to GND in order to enable the device to fetch code from external program memory locations starting at 0000H up to FFFFH. Note, however, that if lock bit 1 is programmed, EA will beinternally latched on reset.EA should be strapped to VCC for internal program executions.This pin also receives the 12-volt programming enable voltage(VPP) during Flash programming, for parts that require12-volt VPP.XTAL1Input to the inverting oscillator amplifier and input to the internal clock operating circuit.XTAL2Output from the inverting oscillator amplifier.Oscillator CharacteristicsXTAL1 and XTAL2 are the input and output, respectively,of an inverting amplifier which can be configured for use as an on-chip oscillator, as shown in Figure 1.Either a quartz crystal or ceramic resonator may be used. To drive the device from an external clock source, XTAL2 should be left unconnected while XTAL1 is driven as shown in Figure 2.There are no requirements on the duty cycle of the external clock signal, since the input to the internal clocking circuitry is through adivide-by-two flip-flop, but minimum and maximum voltage high and low time specifications must be observed.Figure 1. Oscillator Connections Figure 2. External Clock Drive ConfigurationIdle ModeIn idle mode, the CPU puts itself to sleep while all the onchip peripherals remain active. The mode is invoked by software. The content of the on-chip RAM and all the special functions registers remain unchanged during this mode. The idle mode can be terminated by any enabled interrupt or by a hardware reset.It should be noted that when idle is terminated by a hard ware reset, the device normally resumes programexecution,from where it left off, up to two machine cycles before the internal reset algorithm takes control. On-chip hardware inhibits access to internal RAM in this event, but access to the port pins is not inhibited. To eliminate the possibility of an unexpected write to a port pin when Idle is terminated by reset, the instruction following the one that invokes Idle should not be one that writes to a port pin or to external memory.Power-down ModeIn the power-down mode, the oscillator is stopped, and the instruction that invokes power-down is the last instruction executed. The on-chip RAM and Special Function Registers retain their values until the power-down mode is terminated. The only exit from power-down is a hardware reset. Reset redefines the SFRs but does not change the on-chip RAM. The reset should not be activated before VCC is restored to its normal operating level and must be held active long enough to allow the oscillator to restart and stabilize.Program Memory Lock BitsOn the chip are three lock bits which can be left unprogrammed (U) or can be programmed (P) to obtain the additional features listed in the table below.When lock bit 1 is programmed, the logic level at the EA pin is sampled andlatched during reset. If the device is powered up without a reset, the latch initializes to a random value, and holds that value until reset is activated. It is necessary that the latched value of EA be in agreement with the current logic level at that pin in order for the device to function properly.Structure and function of the MCS-51 seriesStructure and function of the MCS-51 series one-chip computer MCS-51 is a name of a piece of one-chip computer series which Intel Company produces. This company introduced 8 top-grade one-chip computers of MCS-51 series in 1980 after introducing 8 one-chip computers of MCS-48 series in 1976. It belong to a lot of kinds this line of one-chip computer the chips have,such as 8051, 8031, 8751,80C51BH, 80C31BH,etc., their basic composition, basic performance and instruction system are all the same. 8051 daily representatives- 51 serial one-chip computers .An one-chip computer system is made up of several following parts: ( 1) One microprocessor of 8 (CPU). ( 2) At slice data memory RAM (128B/256B),it use not depositting not can reading /data that write, such as result not middle of operation, final result and data wanted to show, etc. ( 3) Procedure memory ROM/EPROM(4KB/8KB ), is used to preserve the procedure , some initial data and form in slice. But does not take ROM/EPROM within some one-chip computers, such as 8031 , 8032, 80C ,etc.. ( 4) Four 8 run side by side I/O interface P0 four P3, each mouth can use as introduction , may use as exporting too. ( 5) Two timer / counter, each timer / counter may set up and count in the way, used to count to the external incident, can set up into a timing way too, and can according to count or result of timing realize the control of the computer. ( 6) Five cut off cutting off the control system of the source . ( 7) One all duplexing serial I/O mouth of UART (universal asynchronousreceiver/transmitter (UART) ), is it realize one-chip computer or one-chip computer and serial communication of computer to use for. ( 8) Stretch oscillator and clock produce circuit, quartz crystal finely tune electric capacity need outer. Allow oscillation frequency as 12 megahertas now at most. Every the above-mentioned part was joined through the inside data bus .Among them, CPU is a core of the one-chipcomputer, it is the control of the computer and command centre, made up of such parts as arithmetic unit and controller , etc.. The arithmetic unit can carry on 8 persons of arithmetic operation and unit ALU of logic operation while including one, the 1 storing device temporarilies of 8, storing device 2 temporarily, 8's accumulation device ACC, register B and procedure state register PSW, etc. Person who accumulate ACC count by 2 input ends entered of checking etc. temporarily as one operation often, come from person who store 1 operation is it is it make operation to go on to count temporarily , operation result and loopback ACC with another one. In addition, ACC is often regarded as the transfer station of data transmission on 8051 inside . The same as general microprocessor, it is the busiest register. Help remembering that agreeing with A expresses in the order. The controller includes the procedure counter , the order is depositted, the order decipher, the oscillator and timing circuit, etc. The procedure counter is made up of counter of 8 for two, amounts to 16. It is a byte address counter of the procedure in fact, the content is the next IA that will carried out in PC. The content which changes it can change the direction that the procedure carries out . Shake the circuit in 8051 one-chip computers, only need outer quartz crystal and frequency to finely tune the electric capacity, its frequency range is its12MHZ of 1.2MHZ. This pulse signal, as 8051 basic beats of working, namely the minimum unit of time. 8051 is the same as other computers, the work in harmony under the control of the basic beat, just like an orchestra according to the beat play that is commanded.There are ROM (procedure memory , can only read ) and RAM in 8051 slices (data memory, can is it can write ) two to read, they have each independent memory address space, dispose way to be the same with general memory of computer. Procedure 8051 memory and 8751 slice procedure memory capacity 4KB, address begin from 0000H, used for preserving the procedure and form constant. Data 8051- 8751 8031 of memory data memory 128B, address false 00FH, use for middle result to deposit operation, the data are stored temporarily and the data are buffered etc.. In RAM of this 128B, there is unit of 32 byteses that can be appointed as the job register, this and general microprocessor is different, 8051 slice RAM and job register rankone formation the same to arrange the location. It is not very the same that the memory of MCS-51 series one-chip computer and general computer disposes the way in addition. General computer for first address space, ROM and RAM can arrange in different space within the range of this address at will, namely the addresses of ROM and RAM, with distributing different address space in a formation. While visiting the memory, corresponding and only an address Memory unit, can ROM, it can be RAM too, and by visiting the order similarly. This kind of memory structure is called the structure of Princeton. 8051 memories are divided into procedure memory space and data memory space on the physics structure, there are four memory spaces in all: The procedure stores in one and data memory space outside data memory and one in procedure memory space and one outside one, the structure forms of this kind of procedure device and data memory separated form data memory, called Harvard structure. But use the angle from users, 8051 memory address space is divided into three kinds: (1) In the slice, arrange blocks of FFFFH , 0000H of location , in unison outside the slice (use 16 addresses). (2) The data memory address space outside one of 64KB, the address is arranged from 0000H 64KB FFFFH (with 16 addresses ) too to the location. (3) Data memory address space of 256B (use 8 addresses). Three above-mentioned memory space addresses overlap, for distinguishing and designing the order symbol of different data transmission in the instruction system of 8051: CPU visit slice, ROM order spend MOVC , visit block RAM order uses MOVX outside the slice, RAM order uses MOV to visit in slice.8051 one-chip computer have four 8 walk abreast I/O port, call P0, P1, P2 and P3. Each port is 8 accurate two-way mouths, accounts for 32 pins altogether. Every oneI/O line can be used as introduction and exported independently. Each port includes a latch (namely special function register ), one exports the driver and a introduction buffer . Make data can latch when outputting, data can buffer when making introduction , but four function of passway these self-same. Expand among the system of memory outside having slice, four port these may serve as accurate two-way mouth of I/O in common use. Expand among the system of memory outside having slice, P2 mouth see high 8 address off; P0 mouth is a two-way bus, send the introduction of 8low addresses and data / export in timesharingOutput grade , P3 of mouth , P1 of P1 , connect with inside have load resistance of drawing , every one of they can drive 4 Model LS TTL load to output. As while inputting the mouth, any TTL or NMOS circuit can drive P1 of 8051 one-chip computers as P3 mouth in a normal way . Because draw resistance on output grade of them have, can open a way collector too or drain-source resistance is it urge to open a way, do not need to have the resistance of drawing outerly . Mouths are all accurate two-way mouths too. When the conduct is input, must write the corresponding port latch with 1 first . As to 80C51 one-chip computer, port can only offer milliampere of output electric currents, is it output mouth go when urging one ordinary basing of transistor to regard as, should contact a resistance among the port and transistor base , in order to the electricity while restraining the high level from exporting P1~P3 Being restored to the throne is the operation of initializing of an one-chip computer. Its main function is to turn PC into 0000H initially , make the one-chip computer begin to hold the conduct procedure from unit 0000H. Except that the ones that enter the system are initialized normally,as because procedure operate it make mistakes or operate there aren't mistake, in order to extricate oneself from a predicament , need to be pressed and restored to the throne the key restarting too. It is an input end which is restored to the throne the signal in 8051 China RST pin. Restore to the throne signal high level effective , should sustain 24 shake cycle (namely 2 machine cycles ) the above its effective times. If 6 of frequency of utilization brilliant to shake, restore to the throne signal duration should exceed 4 delicate to finish restoring to the throne and operating. Produce the logic picture of circuit which is restored to the throne the signal: Restore to the throne the circuit and include two parts outside in the chip entirely. Outside that circuit produce to restore to the throne signal (RST ) hand over to Schmitt's trigger, restore to the throne circuit sample to output , Schmitt of trigger constantly in each S5P2 , machine of cycle in having one more , then just got and restored to the throne and operated the necessary signal insidly. Restore to the throne resistance of circuit generally, electric capacity parameter suitable for 6 brilliant to shake, can is it restore to the throne signal high level duration greater than 2machine cycles to guarantee. Being restored to the throne in the circuit is simple, its function is very important. Pieces of one-chip computer system could normal running,should first check it can restore to the throne not succeeding. Checking and can pop one's head and monitor the pin with the oscillograph tentatively, push and is restored to the throne the key, the wave form that observes and has enough range is exported (instantaneous), can also through is it restore to the throne circuit group holding value carry on the experiment to change.With the costant growing consumption of fossil energy, global energy crisis and environmental problems have become more and more acute. Among various green renewable energy resources, solar energy has drawn the attention from the scientific circles of various countries due to its unique advantages such as bountless storage content, cleaness and safety, and easiness to obtain. In particular, the application of solar photovoltaic technology has become a universal focus. China has relatively scarce fossil energy resources while a huge energy consumption. Therefore, the research and application of solar photovoltaic technology has important strategic meaning for the future economic development of China. A basic solar photovoltaic system is generally composed of solar panels, storage batteries, DC (direct current) control system and inverters, among which, DC control system is the central part of the solar photovoltaic system.The major content of this subject includes the development and application of the solar photovoltaic system, the classification of the solar photovoltaic system, solar photovoltaic cells, the design of DC (direct current) control system, settings of maximum power point tracking, circuit design and determination of the capacity of the inverter, and the settings of three-phase transformer and the AC (alternating current) distribution system.solar photovoltaic power, photovoltaic cells, DC (direct current) control system, AC (alternating current) distribution system.The 8051 microcontroller is an industry standard architecture that has broad acceptance, wide-ranging applications and development tools available. There are numerous commercial vendors that supply this controller or have it integrated intosome type of system-on-a-chip structure. Both MRC and IAμE chose this device to demonstrate two distinctly different technologies for hardening. The MRC example of this is to use temporal latches that require specific timing to ensure that single event effects are minimized. The IAμE technology uses ultra low power, and layout and architecture HBD design rules to achieve their results. These are fundamentally different than the approach by Aeroflex-United Technologies Microelectronics Center (UTMC), the commercial vendor of a radiation– hardened 8051, that built their 8051 microcontroller using radiation hardened processes. This broad range of technology within one device structure makes the 8051an ideal vehicle for performing this technology evaluation.The objective of this work is the technology evaluation of the CULPRiT process [3] from IAμE. The process has been baselined again st two other processes, the standard 8051 commercial device from Intel and a version using state-of-the-art processing from Dallas Semiconductor. By performing this side-by-side comparison, the cost benefit, performance, and reliability trade study can be done.In the performance of the technology evaluation, this task developed hardware and software for testing microcontrollers. A thorough process was done to optimize the test process to obtain as complete an evaluation as possible. This included taking advantage of the available hardware and writing software that exercised the microcontroller such that all substructures of the processor were evaluated. This process is also leading to a more complete understanding of how to test complex structures, such as microcontrollers, and how to more efficiently test these structures in the future.IV. TEST DEVICESThree devices were used in this test evaluation. The first is the NASA CULPRIT device, which is the primary device to be evaluated. The other two devices are two versions of a commercial 8051, manufactured by Intel and Dallas Semiconductor, respectively.The Intel devices are the ROM less, CMOS version of the classic 8052 MCS-51microcontroller. They are rated for operation at +5V, over a temperature range of 0 to 70 °C and at a clock speeds of 3.5 MHz to 24 MHz. They are manufactured in Intel’s P629.0 CHMOS III-E process.The Dallas Semiconductor devices are similar in that they are ROMless 8052 microcontrollers, but they are enhanced in various ways. They are rated for operation from 4.25 to 5.5 V olts over 0 to 70 °C at clock speeds up to 25 MHz. They have a second full serial port built in, seven additional interrupts, a watchdog timer, a power fail reset, dual data pointers and variable speed peripheral access. In addition, the core is redesigned so that the machine cycle is shortened for most instructions, resulting in an effective processing ability that is roughly 2.5 times greater (faster) than the standard 8052 device. None of these features, other than those inherent in the device operation, were utilized in order to maximize the similarity between the Dallas and Intel test codes.The CULPRiT technology device is a version of the MSC-51 family compatible C8051 HDL core licensed from the Ultra Low Power (ULP) process foundry. The CULPRiT technology C8051 device is designed to operate at a supply voltage of 500 mV and includes an on-chip input/output signal level-shifting interface with conventional higher voltage parts. The CULPRiT C8051 device requires two separate supply voltages; the 500 mV and the desired interface voltage. The CULPRiT C8051 is ROMless and is intended to be instruction set compatible with the MSC-51 family. V. TEST HARDWAREThe 8051 Device Under Test (DUT) was tested as a component of a functional computer. Aside from DUT itself, the other componentsof the DUT computer were removed from the immediate area of the irradiation beam.A small card (one per DUT package type) with a unique hard-wired identifier byte contained the DUT, its crystal, and bypass capacitors (and voltage level shifters for the CULPRiT DUTs). This "DUT Board" was connected to the "Main Board" by a short 60-conductor ribbon cable. The Main Board had all other components required to complete the DUT Computer, including some which nominally are not necessary insome designs (such as external RAM, external ROM and address latch).The DUT Computer and the Test Control Computer were connected via a serial cable and communications were established between the two by the Controller (that runs custom designed serial interface software). This Controller software allowed for commanding of the DUT, downloading DUT Code to the DUT, and real-time error collection from the DUT during and post irradiation. A 1 Hz signal source provided an external watchdog timing signal to the DUT, whose watchdog output was monitored via an oscilloscope. The power supply was monitored to provide indication of latchup.VI. TEST SOFTWAREThe 8051 test software concept is straightforward. It was designed to be a modular series of small test programs each exercising a specific part of the DUT. Since each test was stand alone, they were loaded independently of each other for execution on the DUT. This ensured that only the desired portion of the 8051 DUT was exercised during the test and helped pinpoint location of errors that occur during testing. All test programs resided on the controller PC until loaded via the serial interface to the DUT computer. In this way, individual tests could have been modified at any time without the necessity of burning PROMs. Additional tests could have also been developed and added without impacting the overall test design. The only permanent code, which was resident on the DUT, was the boot code and serial code loader routines that established communications between the controller PC and the DUT.All test programs implemented:•An external Universal Asynchronous Receive and Transmit device (UART) for transmission of error information and communication to controller computer.•An external real-time clock for data error tag.•A watchdog routine designed to provide visual verification of 8051 health and restart test code if necessary.•A "foul-up" routine to reset program counter if it wanders out of code space.•An external telemetry data storage memory to provide backup of data in the eventof an interruption in data transmission.The brief description of each of the software tests used is given below. It should be noted that for each test, the returned telemetry (including time tag) was sent to both the test controller and the telemetry memory, giving the highest reliability that all data is captured.Interrupt – This test used 4 of 6 available interrupt vectors (Serial, External, Timer0 Overflow, and Timer1 Overflow) to trigger routines that sequentially modified a value in the accumulator which was periodically compared to a known value. Unexpected values were transmitted with register information.Logic – This test performed a series of logic and math computations and provided three types of error identifications: 1) addition/subtraction, 2) logic and 3) multiplication/division. All miscompares of computations and expected results were transmitted with other relevant register information.Memory – This test loaded internal data memory at locations D:0x20 through D:0xff (or D:0x20 through D:0x080 for the CULPRiT DUT), indirectly, with an 0x55 pattern. Compares were performed continuously and miscompares were corrected while error information and register values were transmitted.Program Counter -The program counter was used to continuously fetch constants at various offsets in the code. Constants were compared with known values and miscompares were transmitted along with relevant register information.Registers – This test loaded each of four (0,1,2,3) banks of general-purpose registers with either 0xAA (for banks 0 and 2) or 0x55 (for banks 1 and 3). The pattern was alternated in order to test the Program Status Word (PSW) special function register, which controls general-purpose register bank selection.General-purpose register banks were then compared with their expected values. All miscompares were corrected and error information was transmitted.Special Function Registers (SFR) – This test used learned static values of 12 out 21 available SFRs and then constantly compared the learned value with the current one. Miscompares were reloaded with learned value and error information was transmitted.。
5000字英文论文

5000字英文论文篇一:论文用5000字中英文翻译MCU DescriptionSCM is also known as micro-controller (Microcontroller Unit), commonly used letters of the acronym MCU that it was first used in industrial control. Only a single chip by the CPU chip developed from a dedicated processor. The first design is by a large number of peripherals and CPU on a chip in the computer system, smaller, more easily integrated into a complex and demanding on the volume control device which. INTEL s Z80 is the first designed in accordance with this idea processor, then on the development of microcontroller and dedicated processors have parted ways.Are 8-bit microcontroller early or 4 bits. One of the most successful is the INTEL 8031, for a simple, reliable and good performance was a lot of praise. Then developed in 8031 out of MCS51 MCU Systems. SCM systems based on this system until now are still widely used. With the increased requirements of industrial control field, began a 16-bit microcontroller, because the cost is not satisfactory but have not been very widely used. After 90 years with the great development of consumer electronics, microcontroller technology has been a huge increase. With INTEL i960 series, especially the later series of widely used ARM, 32-bit microcontroller quickly replace high-end 16-bit MCU status and enter the mainstream market. The traditional 8-bit microcontroller performances have been the rapid increase capacity increase compared to 80 the number of times. Currently, high-end 32-bit microcontroller clocked over 300MHz, the performance catching the mid-90 s dedicated processor, while the average model prices fall to one U.S. dollars; the most high-end model only 10 dollars. Modern SCM systems are no longer only in the developmentand use of bare metal environment, a large number of proprietary embedded operating system is widely used in the full range of SCM. The handheld computers and cell phones as the core processing of high-end microcontroller can even use a dedicated Windows and Linux operating systems.SCM is more suitable than the specific processor used in embedded systems, so it was up to the application. In fact the number of SCM is the world s largest computer. Modern human life used in almost every piece of electronic and mechanical products will be integrated single chip. Phone, telephone, calculator, home appliances,electronic toys, handheld computers and computer accessories such as a mouse with a 1-2 in both the Department of SCM. Personal computer will have a large number of SCM in the work. General car with more than 40 SCM, complex industrial control systems may even have hundreds of SCM in the same time work! SCM is not only far exceeds the number of PC and other computing the sum, or even more than the number of human beingsSingle chip, also known as single-chip microcontroller, it is not complete a certain logic chips, but to a computer system integrated into a chip. Equivalent to a micro-computer, and computer than just the lack of a microcontroller I / O devices. General talk: a chip becomes a computer. Its small size, light weight, cheap, for the study, application and development of facilities provided. At the same time, learning to use the MCU is to understand the principle and structure of the computer the best choice. SCM and the computer functions internally with similar modules, such as CPU, memory, parallel bus, the same effect as well, and hard disk memory devices, and different is its performance of these components were relatively weak many of our home computer, but the price is low , usually not more than 10 yuan you can do with it ...... some control for a class is not very complicated electrical work is enough of. We are usingautomatic drum washing machine, smoke hood, VCD and so on appliances which could see its shadow! ...... It is primarily as a control section of the core componentsIt is an online real-time control computer, control-line is that the scene is needed is a stronger anti-jamming ability, low cost, and this is, and off-line computer (such as home PC), the main difference.Single chipMCU is through running, and can be modified. Through different procedures to achieve different functions, in particular special unique features, this is another device much effort needs to be done, some great efforts are very difficult to do. A not very complex functions if the 50 s with the United States developed 74 series, or the 60 s CD4000 series of these pure hardware buttoned, then the circuit must be a large PCB board! But if the United States if the 70 s with a series of successful SCM market, theresult will be a drastic change! Just because you are prepared by microcomputer programs can achieve high intelligence, high efficiency and high reliability!As the microcontroller on the cost-sensitive, so now the dominant software or the lowest level assembly language, which is the lowest level in addition to more than binary machine code language, and as so low why is the use? Many high-level language has reached the level of visual programming Why is not it? The reason is simply that there is no home computer as a single chip CPU, not as hard as a mass storage device. A visualization of small high-level language program which even if only one button, will reach tens of K of size! For the home PC s hard drive in terms of nothing, but in terms of the MCU is not acceptable. SCM in the utilization of hardware resources to be very high for the job so although the original is still in the compilation of a lot of use. The same token,if the giant computer operating system and applications run up to get home PC, home PC, also can not afford to.Can be said that the twentieth century across the three power era, that is, the age of electricity, the electronic age and has entered into the computer age. However, this computer, usually refers to the personal computer, referred to as PC. It consists of the host, keyboard, monitor and other components. Another type of computer, most people do not know how. This computer is to give all kinds of intelligent machines single chip (also known as micro-controller). As the name suggests, this computer system took only a minimal integrated circuit, can be a simple operation and control. Because it is small, usually hidden in the charged mechanical stomach in. It is in the device, like the human brain plays a role, it goes wrong, the whole plant was paralyzed. Now, this microcontroller has a very broad field of use, such as smart meters, real-time industrial control, communications equipment, navigation systems, and household appliances. Once all kinds of products were using SCM, can serve to upgrade the effectiveness of products, often in the product name preceded by the adjective - intelligent, such as intelligent washing machines. Now some technical personnel of factories or other amateur electronics developers to engage in out of certain products, not the circuit is too complicated, that function is too simple and can easily be copied. The reason may be stuck in the product did not use a microcontrolleror other programmable logic device.SCM historySCM was born in the late 20th century, 70, experienced SCM, MCU, SoC three stages.First model1.SCM the single chip microcomputer (Single Chip Microcomputer) stage, mainly seeking the best of the best single form of embedded systemsarchitecture. Innovation model success, laying the SCM and general computer completely different path of development. In the open road of independent development of embedded systems, Intel Corporation contributed.2.MCU the micro-controller (Micro Controller Unit) stage, the main direction of technology development: expanding to meet the embedded applications, the target system requirements for the various peripheral circuits and interface circuits, highlight the object of intelligent control. It involves the areas associated with the object system, therefore, the development of MCU s responsibility inevitably falls on electrical, electronics manufacturers. From this point of view, Intel faded MCU development has its objective factors. In the development of MCU, the most famous manufacturers as the number of Philips Corporation. Philips company in embedded applications, its great advantage, the MCS-51 single-chip micro-computer from the rapid development of the micro-controller. Therefore, when we look back at the path of development of embedded systems, do not forget Intel and Philips in History.Embedded SystemsEmbedded system microcontroller is an independent development path, the MCU important factor in the development stage, is seeking applications to maximize the solution on the chip; Therefore, the development of dedicated single chip SoC trend of the natural form. As the microelectronics, IC design, EDA tools development, application system based on MCU SOC design have greater development. Therefore, the understanding of the microcontroller chip microcomputer can be, extended to the single-chip micro-controller applications.MCU applicationsSCM now permeate all areas of our lives, which is almost difficult to find traces of the field without SCM. Missile navigation equipment,aircraft, all types of instrument control, computer network communications and data transmission, industrial automation, real-time process control and data processing, extensive use of various smart IC card, civilian luxury car security system, video recorder, camera, fully automatic washing machine control, and program-controlled toys, electronic pet, etc., which are inseparable from the microcontroller. Not to mention the area of robot control, intelligent instruments, medical equipment was. Therefore, the MCU learning, development and application of the large number of computer applications and intelligent control of the scientists, engineers.SCM is widely used in instruments and meters, household appliances, medical equipment, aerospace, specialized equipment, intelligent management and process control fields, roughly divided into the following several areas:1. In the application of Intelligent InstrumentsSCM has a small size, low power consumption, controlling function, expansion flexibility, the advantages of miniaturization and ease of use, widely used instrument, combining different types of sensors can be realized Zhuru voltage, power, frequency, humidity, temperature, flow, speed, thickness, angle, length, hardness, elemental, physical pressure measurement. SCM makes use of digital instruments, intelligence, miniaturization, and functionality than electronic or digital circuits more powerful. Such as precision measuring equipment (power meter, oscilloscope, various analytical instrument).2. In the industrial control applicationWith the MCU can constitute a variety of control systems, data acquisition system. Such as factory assembly line of intelligent control 3. In Household AppliancesCan be said that the appliances are basically using SCM, praise from the electric rice, washing machines, refrigerators, air conditioners, color TV, and other audio video equipment, to the electronic weighing equipment, varied, and omnipresent.篇二:毕业论文5000字英文文献翻译(c++)┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书英文翻译英语原文:. Introducing ClassesThe only remaining feature we need to understand before solving our bookstore problem is how to write a data structure to represent our transaction data. In C++ we define our own data structure by defining a class. The class mechanism is one of the most important features in C++. In fact, a primary focus of the design of C++ is to make it possible to define class types that behave as naturally as the built-in types themselves. The library types that we ve seen already, such as istream and ostream, are all defined as classesthat is,they are not strictly speaking part of the language.Complete understanding of the class mechanism requires mastering a lot of information. Fortunately, it is possible to use a class that someone else has written without knowing how to define a class ourselves. In this section, we ll describe a simple class that we canuse in solving our bookstore problem. We ll implement this class in the subsequent chapters as we learn more about types,expressions, statements, and functionsall of which are used in defining classes.To use a class we need to know three things:What is its name? Where is it defined?What operations does it support?For our bookstore problem, we ll assume that the class is named Sales_item and that it is defined in a header named Sales_item.h.The Sales_item ClassThe purpose of the Sales_item class is to store an ISBN and keep track of the number of copies sold, the revenue, and average sales price for that book. How these data are stored or computed is not our concern. To use a class, we need not know anything about how it is implemented. Instead, what we need to know is what operations the class provides.As we ve seen, when we use library facilities such as IO, we must include the associated headers. Similarly, for our own classes, we must make the definitions associated with the class available to the compiler. We do so in much the same way. Typically, we put the class definition into a file. Any program that wants to use our class must include that file. Conventionally, class types are stored in a file with a name that, like the name of a program source file, has two parts: a file name and a file suffix. Usually the file name is the same as the class defined in the header. The suffix usually is .h, but some programmers use .H, .hpp, or .hxx. Compilers usually aren t picky about header file names, but IDEs ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书sometimes are. We ll assume that our class is defined in a file named Sales_item.h.Operations on Sales_item ObjectsEvery class defines a type. The type name is the same as the name of the class. Hence, our Sales_item class defines a type namedSales_item. As with the built-in types, we can define a variable of a class type. When we write Sales_item item we are saying that item is an object of type Sales_item. We often contract the phrase an object of type Sales_item to aSales_ item object or even more simply to a Sales_item. In addition to being able to define variables of type Sales_item, we can perform the following operations on Sales_item objects:Use the addition operator, +, to add two Sales_items,Use the input operator, to read a Sales_item object,Use the output operator, to write a Sales_item object,Use the assignment operator, =, to assign one Sales_item object to another,Call the same_isbn function to determine if two Sales_items refer to the same book.Classes are central to most C++ programs: Classes let us define our own types that are customizedfor the problems we need to solve, resulting in applications that are easier to write andunderstand.Well-designed class types can be as easy to use as the built-in types.A class defines data and function members: The data members store the state associated with objectsof the class type, and the functions perform operations that give meaning to the data. Classeslet us separate implementation and interface. The interface specifies the operations that the classsupports. Only the implementor of the class need know or care about the details of the implementation. This separation reduces the bookkeeping aspects that make programming tedious anderror-prone.Class types often are referred to as abstract data types. An abstract data type treats the data(state) and operations on that state as a single unit. We can think abstractly about what the classd oes, rather than always having to be aware of how the class operates. Abstract data types arefundamental to both object-oriented and generic programming.Data abstraction is a programming (and design) technique that relies on the separation of interfaceand implementation. The class designer must worry about how a class is implemented, but programmersthat use the class need not know about these details. Instead, programmers who use a type need to know only the type s interface; they can think abstractly about what the type does rather than concretely about how the type works. Encapsulation is a term that describes the technique of combining lower-level elements to forma new, higher-level entity. A function is one form of encapsulation: The detailed actions performedby the function are encapsulated in the larger entity that is the function itself. Encapsulated elements hide the details of their implementationwe may call ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书a function but have no access to the statements that it executes. In the same way, a class is an encapsulated entity: It represents an aggregation of several members, and most (well-designed) class types hide the members that implement the type.If we think about the library vector type, it is an example of both data abstraction and encapsulation. It is abstract in that to use it, we think about its interfaceabout the operations that it can perform. It is encapsulated because we have no access to the details of how the type is representated nor to any of its implementation artifacts. An array, on the other hand, is similar in concept to a vector but is neither abstract nor encapsulated. We manipulate an array directly by accessing the memory in which the array is stored.Not all types need to be abstract. The library pair class is a good example of a useful, well-designed class that is concrete rather thanabstract. A concrete class is a class that exposes, rather than hides, its implementation.Some classes, such as pair, really have no abstract interface. The pair type exists to bundle two data members into a single object. There is no need or advantage to hiding the data members. Hiding the members in a class like pair would only complicate the use of the type.Even so, such types often have member functions. In particular, it is a good idea for any class that has data members of built-in or compound type to define constructor(s) to initialize those members. The user of the class could initialize or assign to the data members but it is less error-prone for the class to do so.Programmers tend to think about the people who will run their applications as users. Applicationsare designed for and evolve in response to feedback from those who ultimately use the applications. Classes are thought of in a similar way: A class designer designs and implements a class for users of that class. In this case, the user is a programmer, not the ultimate user of the application.Authors of successful applications do a good job of understanding and implementing the needs ofthe application s users. Similarly,well-designed, useful classes are designed with a close attention to the needs of the users of the class.In another way, the division between class designer and class user reflects the division betweenusers of an application and the designers and implementors of the application. Users care only if the application meets their needs in a cost-effective way. Similarly, users of a class care only about its interface. Good class designers define a class interface that is intuitive and easy to use. Users care about the implementation only in so far as the implementation affects their use of the class. If the implementation is too slow or puts burdens on users ofthe class, then the users must care. In well-designed classes, only the class designer worries about the implementation.In simple applications, the user of a class and the designer of the class might be one┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书and the same person. Even in such cases, it is useful to keep the roles distinct. When designing the interface to a class, the class designer should think about how easy it will be to use the class. When using the class, the designer shouldn t think about how the class works.When referring to a user, the context makes it clear which kind of user is meant. If we speak of user code or the user of the Sales_item class, we mean a programmer who is using a class in writing an application. If we speak of the user of the bookstore application, we mean the manager of the store who is running the application.Data abstraction and encapsulation provide two important advantages: 1.Class internals are protected from inadvertent user-level errors, which might corrupt the state of the object.2.The class implementation may evolve over time in response to changing requirements or bug reports without requiring change inuser-level code.By defining data members only in the private section of the class, the class author is free to make changes in the data. If the implementation changes, only the class code needs to be examined to see what affect the change may have. If data are public, then any function that directly accesses the data members of the old representation might be broken. Itwould be necessary to locate and rewrite all those portions of code that relied on the old pesentation before the program could be used again. Similarly, if the internal state of the class is private, then changes to the member data can happen in only a limited number of places. The data is protected from mistakes that users might introduce. If there is a bug that corrupts the object s state, the places to look for the bug are localized: When data are private, only a member function could be responsible for the error. The search for the mistake is limited, greatly easing the problems of maintenance and program correctness.If the data are private and if the interface to the member functions does not change, then user functions that manipulate class objects require no change.Because changing a class definition in a header file effectively changes the text of every source file that includes that header, code that uses a class must be recompiled when the class changes.Classes are the most fundamental feature in C++. Classes let us define new types that are tailored to our own applications, making our programs shorter and easier to modify.Data abstractionthe ability to define both data and function membersand encapsulationthe ability to protect class members from general accessare fundamental to classes. Member functions define the interface to the class. We encapsulate the class by making the data and functions used by the implementation of a class private.Classes may define constructors, which are special member functions that control how┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书objects of the class are initialized. Constructors may be verloaded. Every constructor should initialize every data member. Constructors should use a constructor initializer list to initialize the data members. Initializer lists are lists of namevalue pairs where the name is a member and the value is an initial value for that member.Classes may grant access to their nonpublic members to other classes or functions. A class grants access by making the class or function a friend.Classes may also define mutable or static members. A mutable member is a data member that is never const; its value may be changed inside a const member function. A static member can be either function or data; static members exist independently of the objects of the class type. Copy ControlEach type, whether a built-in or class type, defines the meaning of a (possibly empty) set of operations on objects of that type. We can add two int values, run size on a vector, and so on. These operations define what can be done with objects of the given type.Each type also defines what happens when objects of the type are created. Initialization of objects of class type is defined by constructors. Types also control what happens when objects of the type are copied, assigned, or destroyed. Classes control these actions through special member functions: the copy constructor, the assignment operator, and the destructor. This chapter covers these operations.When we define a new type, we specifyexplicitly or implicitlywhat happens when objects of that type are copied, assigned, and destroyed. We do so by defining special members: the copy constructor, the assignment operator, and the destructor. If we do not explicitly define the copy constructor or the assignment operator, the compiler will (usually) define them for us.The copy constructor is a special constructor that has a single parameter that is a (usually const) reference to the class type. The copy constructor is used explicitly when we define a new object and initialize it from an object of the same type. It is used implicitly when we pass or return objects of that type to or from functions.Collectively, the copy constructor, assignment operator, and destructor are referred to as copy control. The compiler automatically implements these operations, but the class may define its own versions. Copy control is an essential part of defining any C++ class. Programmers new to C++ are often confused by having to define what happens when objects arecopied, assigned, or destroyed. This confusion is compounded because if we do not explicitly define these operations, the compiler defines them for usalthough they might not behave as we intend.Often the compiler-synthesized copy-control functions are finethey do exactly the篇三:毕业设计的5000字英文文献翻译外文及翻译英语原文 Android Application FundamentalsAndroid applications are written in the Java programming language. The Android SDK tools compile the code—along with any data and resource files—into an Android package, an archive file with an .apk suffix. All the code in a single .apk file is considered to be one application and is the file that Android-powered devices use to install the application. Once installed on a device, each Android application lives in its own security sandbox: ? The Android operating system is a multi-user Linux system in which eachapplication is a different user.? By default, the system assigns each application a unique Linux user ID (the ID is used only by the system and is unknown to the application). The system setspermissions for all the files in an application so that only the user ID assigned to that application can access them.? Each process has its own virtual machine (VM), so an application s code runs in isolation from other applications.? By default, every application runs in its own Linux process. Android starts the process when any of the application s components need to be executed, then shuts down the process when it s no longer needed or when the system must recovermemory for other applications.In this way, the Android system implements the principle of least privilege. That is, each application, by default, has access only to the components that it requires to do its work and no more. This creates a very secure environment in which an application cannot access parts of the system for which it is not given permission.However, there are ways for an application to share data with other applications and for an application to access system services:? It s possible to arrange for two applications to share the same Linux user ID, in whichcase they are able to access each other s files. To conserve system resources,applications with the same user ID can also arrange to run in the same Linux processand share the same VM (the applications must also be signed with the samecertificate).。
5000字英文范文翻译类

In new network on 2 September Xinhua comprehensive report, the situation in Syria is currently in the United States of America in the teeth of the storm, President Obama issued a statement in August 31st, decided to take military action against the Syrian government target, the White House has formally asked Congress to authorize. But in the United States, Obama faces two trials of Congress and the public; in foreign countries, the multinational NATO would not send troops, many countries also oppose the United States plans. Analysis refers to the Syrian military command, Obama was "imminent", but his support for the difficulties, may "itself".The contradiction: the Congress attitude unknown Obama fears "riding a tiger"Local time on August 31st, the United States President Barack Obama issued a statement at the White House, said that "after careful consideration, I have decided that the United States should the regime in Syria to take military action against the target. It will not be indefinite intervention, we will not send ground troops, instead we aim to limit the action time and scale."But Obama said, he also made second decisions, is "to get authorization from Congress to", only the consent of Congress, I ordered the U.S. war on Syria. On the same day, the official White House to Congress a proposal, according to the United States Congress "War Powers Act" and the United Nations Security Council in 2004 passed a resolution, authorized the president to take military action in Syria.In the proposal, Obama asked Congress to use the authorization bill Syria, intended to deter, prevent and reduce blow, Syria continue to use chemical weapons and other weapons of mass destruction in the future. He also said, Syria internal conflict was resolved by political consultation.The analysis thinks, Obama remarks on the question of Syria to slam the brakes, to seek congressional approval for a military attack against Syria, is likely to lead to the United States at least 10 days delay action.However, Obama this "gambling" type decision will make it a tough fight. Obama broke the decades of practice, has announced that it will seek congressional approval Syria suspected use chemical weapons to act. But the United States senators would support Obama, will defeat him swallow bitter is still uncertain.Analysis pointed out that, Obama this bet is risky, he bet he could get Congress agreed to a limited attack Syria, defending against the international ban, the United States national security interests, and to protect Turkey, Jordan, Israel and other allies in the middle east.Obama had previously insisted, he retained ignore Congress decided to attack the right, White House officials said the change would give Obama more time to win internationalsupport. But for Obama, the most difficult and most threatening the authority of the president's war, or between members of Congress of political wrangling, because it cannot determine the Congress will support the attack on Syria.Observers caution, Obama could face the same fate with British Prime Minister Cameron. Cameron for the British Parliament authorized military action, but was rejected.Obama may be full of confidence, that he can win the vote in the Democratic controlled senate. The Senate also has many Republicans to take military action. However, he is in the house of Representatives won the support of the opportunity is not sure. The house has many conservative core people everywhere, to interfere with Obama's plan.In addition, the American people on the government military intervention plan highlights the ambivalence, and the Obama administration, Congress and the U.S. is unease shrouded. The Afghan war and the Iraq war, costly delay for a long time, the American people are unwilling to once again involved in the conflict in the middle east.The United States National Broadcasting Company (NBC) recently in a poll, half of Americans polled for the government of Syria military strikes do not support, only 35% behind Obama in the process encountered a time he was the most difficult questions of the 700 respondents.Only 1/5 of respondents said the military action, which is in the American national interest, and only 27% of the people think that the military can make the situation in Syria.If the United States to take action, 56% of people said that, the aim should be to prevent the use of chemical weapons. Only a small number of people (16% or less), military action to overthrow the Assad regime or stop Syria clashes between government forces and armed opposition.Outside the opposition: 12 NATO countries to the international community to anti war emotionWhen Obama published "on the Syrian military" statement on the same day, the United States anti war organizations held a protest outside the White House, shouting anti war slogans. People playing white banners and placards reading "not yellow, the Syrian war", "the Syrian military built on lies" etc.. The activities of the organization responsible person said, the day before and after the estimated 500 people have been involved in the protests, the organizers also prepared during the three day "Labor Day" long weekend continue to hold protest in front of the White House, where all over the United States would have to Washington to participate in.In August 31st, the British capital London is also the outbreak of large-scaledemonstrations, oppose aggression against Syria. According to the organization of this parade "anti war alliance", a total of 5000 people took part in the parade.The British Parliament in August 29th voted against Prime Minister Cameron to attack Syria's proposal, was named the greatest shame Cameron to be in power for three years "suffer". Although Obama assured Cameron that the relationship between them is still strong, but the British media will Cameron's the signs of failure as the so-called "special relationship" and "doomsday". They worry, support for military action.。
大学英语24篇翻译练习

作文号:375886题目:四级汉译英翻译:中国家庭文化原文:在传统的中国家庭文化中,同一祖先的几代后裔(descendants) 居住在一起,形成一个大家庭。
这种自治(autonomous)家族制度是中国传统社会的基本单位。
中国的孩子们跟随他们父亲的姓。
这和西方文化是一样的。
如今在中国,孩子跟父亲的姓或母亲的姓在法律上都是合法的。
除了那些因为结婚加入到家庭中的人以外,人们的姓氏都是一样的。
译文:In traditional Chinese family culture, descendants of several generations from the same ancestor lived together and formed a big family system. This kind of autonomous family system was the basic unit of traditional Chinese society. Chinese children follow their father’s family name. This is the same as w estern culture. Nowadays in China it is legally fine for a child to follow either father’s family name or mother’s family name. Within each family system, of course people except those who joined this family system through marriage all have the same family name.作文号:375887题目:四级汉译英翻译:法定假日原文:中国人民依法享受超过115天的假期,其中包括104天的周末和11天的节假日。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
人类闹剧,动物审判:中世纪的动物审判教我们如何公正的对待动物法律没有普遍保护动物的体系,而且另一点不足是没有正式的结构:在美国和加拿大的法律中动物不是法律上的“人”,没有受法律体系保护的独立权利。
有人呼吁扩大动物在法律上的地位,通过律师代表他们的权利或者通过其他的正式保护措施。
但是,在某种程度上,一些本已发生过。
很久以前,主要是中世纪和现代早期,动物们试图攻击人类并破坏庄稼。
这些动物被正式起诉,包括代表他们利益的律师。
历史上的动物审判表明,在人类创造的法律制度中,法律对动物的“权利”是为人类的目的服务的,很少有关于动物的利益。
这个历史表明动物正式的法律权利只是工具,而不是目的本身,并强调这重要性不仅仅是扩大正式保护,而是要人们通过换位思考(尽管人类的司法系统在这方面具有不可避免的局限性,)去体会动物自己的利益和观点。
一、引言:动物的客户,人权律师在一个1999年纽约的一个漫画中,两个实验室涂层的研究人员在猴子的笼子上看到一个文件。
标题是:“他说他需要一个律师。
”这很有趣,因为作为猴子,按照规则是不具有律师的。
猴子在动画片属于法律范畴的性质,其中人的权利方面的事情是行使;法律,猴子不是人,也就没有需要被保护的权利,所以它就不会拥有律师。
本文是关于动物的律师,动物审判和动物权利。
这是一个关于历史的实践,就像是遥不可及的小说,但牵涉一个非常当代辩论。
该辩论是关于动物的法律地位——他们是否应该被依法认定为法律上的人,这种改革的影响就是,从而使动物在实体上,拥有自己的合法权利。
目前,法律将动物视为物(或多或少的,也有一些例外的和次要的质疑)。
驯养的动物是财产,而不是人。
有些人认为动物的这种法律地位是我们的文化系统中虐待动物的基础。
例如,加里弗兰乔认为动物因为被虐待,所以不能被有意义的保护,除非废除他们只是财产的法律地位。
许多其他哲学家和法律思想家认为,在一种形式或者另一种形式下应该承认动物的法律人格。
关于律师,他的人格的本质是参加法律诉讼程序的一个实体。
从某种意义上说,一个人的法律意义上的人拥有法律地位,也可以有律师。
这是有道理的,那么一些动物权利的学者和倡导者侧重于扩大法律学说,给动物获得更多的法律机构,通过法院,动物宣传组织,或一个普通公民,申请强制执行动物保护法指定的监护人,来确保动物以自己的名义进行权利保护的可能性。
甚至有人建议,法律应该把动物作为法律某方面的一个主体,在某些情况下,调节其他动物损害的赔偿责任。
在辩论的另一方学者认为,这既是不现实的,也不能废除动物作为财产权益的法律地位,直到人们可以更好地影响动物而不是更差。
这些学者认为,我们的目标应该增量修改,而不是废除动物作为财产地位的状况,人格与财产问题上的焦点主要是一项学术活动分歧,并因此导致直接的法律改革工作,这将改善动物的生活。
这个关于取消动物的财产身份的必要性的辩论是在现代动物权利学术的“所有最激烈的辩论之一”。
但动物审判和法律主张代表的想法并不完全是新的。
这是一个很长的历史,主要是中世纪和现代早期,动物试图攻击人类和食用作物等罪行。
在这些审判中,动物作为被告对不法行为负责,允许最正当程序性保护,有社会团体向他们提供代理律师,并受到惩罚- 所有的方式,都模仿人类被告的对待方式。
有时他们就像披着人类的外衣。
现代动物的法律学者往往顺带一提动物审判,但相对较少的关注,也许因为某种原因,他们看到他们仅仅作为历史遗留,迷信的产物和仪式文化,与现今努力减轻动物的痛苦和剥削的相关性不大。
旧的动物审判中值得我们关注,是因为他们告诉我们一些有关承诺和一些限制使用的法律工具,如人格,独立,和法律权利,—人类的司法系统—进一步解放动物。
我用“动物解放”作为速记指减少动物的痛苦和剥削,灌输人类对待动物更好和更尊重的态度,以及发展更强有力的体制保护动物。
这可能对律师有一定的诱惑,认为改变动物的法律地位是动物解放的根本,其余的也将自然而然的改变,。
历史的旧动物审判应作为一个有益的提醒,事是比这复杂得多。
旧的动物审判表明,中世纪和早期现代法律文化,外国人在一次自己的和公认的前体,可容纳和重视辩论有关动物的思维能力,情感,和责任感,能认识到人类和动物的法律责任,可以容忍动物物种之间的运动的”事”和“人”。
然而,审判并没有为动物解放做多少事;他们在法律形式主义下荒谬的行为往往以恶劣的对待动物而结束。
历史上的动物审判是一种食物来源的思想——无论灵感还是警告——所带来的影响,就是在人类法律体系中将动物放置在人的角色上。
有许多不同的方式来看待动物试验,本文借用其中几个。
一些学者认为审判主要是作为一个社会或文化现象,本文也同意他们的观点。
其他人认为这些审判是解决动物权利和动物压迫问题的材料。
我们的大部分知识的动物试验(至少为讲英语的学者)来自欧洲议会,伊万斯的工作,《刑事诉讼和动物的死刑》,其中伊万斯收集有关审判的信息,并提出了他自己的意见,对那些在实践之后的文化,哲学、神学和背后的实践——意见受到伊万斯的惊人的“现代”亲动物权利观点的影响。
埃丝特科恩分析优秀的历史的审判中添加了大量的我们了解的背景。
动物审判也启发了一些富有想象力的文学和戏剧作品,指出他们的讽刺和颠覆性的方面。
本文所讨论的一些解释,也因为它们揭示了动物审判的文化意义和有关动物的法律地位的争论。
这些作品使我们认识到,法律的仪式可以是一种变相的运动的蛮力,但也给出了一个声音,在有限的方式内,让人保持沉默。
这些都是不同的,甚至是断开的方式在看待一个单一的现象,难以获得知识的掌握,但它们之间有共同的线索。
都是不同的方式回答将动物和人一样看待是什么意思,或把动物像人一样对待,不一定是相同的东西这个问题。
动物审判表明,给予动物正式的法律人格不一定对他们有好处。
比正式类别的财产或人格更重要的是对动物的法律方向——法律制度是否使用动物作为一种手段,处理本问题或是不能够完成的不寻常对待动物的方式,至少在一定程度上,试试从动物的视角来看事情。
这一见解出现由一个比较老的动物审判浮现,现代法律程序解决类似的问题,如出现动物攻击人类法律纠纷,或当野生动物消耗人类自己想要的资源。
今天我们决定做某些狗咬人事件处理之前,会举行听证会,,但我们并不把狗作为被告;然而,这些程序和旧的谋杀案审判猪可能真的是同样的关注,在执行过程之前,剥夺对动物的主人来说非常珍贵的东西。
当谈到与野生动物共存,我们不遵循中世纪主义,承认老鼠和蝗虫分享食物的“权利”,但有当代实例——一个是下面第五部分讨论的,——事实上我们其实也有无私方式的行为,比如自愿选择与动物共享资源,而不是摧毁他们。
实事求是的讲,这不是中世纪我们缺少技术的祖先的一种选择。
同时,赋予动物以人的法律地位,即使这一个空的形式,但这本身就是一种挑衅,颠覆了人与动物的正常层次结构。
一个关于动物权利的卓越的思想家,史提芬怀斯,谴责古代公理,他认为法律是为人服务的——“法律成是伟人的利益而建立的”——就像法律基础中对动物盲目的道德义务。
但它是真正的经验的事实,法律是由人创造并为人类服务的,无论人们可能认为法律是否或应表达基本自然正义原则,超越人类起源。
历史上的早期动物审判应提醒我们,我们的工作是改进法律保护动物,但我们应该明报,我们的法律体系并不是动物制定的,以及我自身代表能力的限制,甚至很难明白,动物的利益。
温迪亚当斯认为,如果动物被整合到人类的法律系统,一体化进程”应该是承认和尊重动物的利益,而不是代表人类的利益,为了自己的目的在使用动物。
”想想过去当我们将动物整合到法律制度里(尽管在有限的方式)可以给今天我们深入了解什么可以做,什么不该做。
从历史的动物审判得到的最重要的教训是在法庭上动物的存在(字面意思或表达方式),在最后,总是和永远居中的,动物经常被比喻穿上了衣服但这并不属于他们。
我们或许可以采用法律机构,通过从动物的角度倡导动物权益来减轻这种普遍存在的困难,最好我们可以理解他们。
但我们真正需要做的是对我们自身的局限保持敏感,——从来不要忘记我们是人,正如俗语所说,人之常情。
在第二部分,本文讨论的动物,律师,和参与了这些古老的动物审判的社区。
然后在第三部分第四和第五部分析了动物审判对动物权利潜在影响的争论,本文探讨了动物审判已在文学、戏剧提出并探讨现代动物审判解释了当前的动物和法律制度之间的关系。
在第六部分,本文提出了如何改进法律制度,以确保非人的动物利益在未来的动物审判中都得到充分体现。
二.动物审判伊万斯介绍了两类动物审判:第一,“资本主义的刑罚由世俗法庭对猪,牛,马,和其他牲畜作为惩罚杀人”案件中还具有兽性;其次,“由教会法院提起的对小鼠,大鼠,蝗虫,象甲,和其他害虫司法诉讼,为防止他们吞噬庄稼,并从果园,葡萄园,栽培领域的手段驱逐他们,是驱邪和惩罚。
”这些不同类型的程序被分别称为“世俗”和“教会”。
皮斯贝恩教授,犯罪学家和虐待动物的学者,认为教会诉讼不被审判,而是由”一个完全不同的过程,导致声明由教会逐出教会的法庭。
”代替。
然而,教会诉讼是公认在形式和功能类似现代民事审判,由抗辩双方提交程序性诉状,即使当事人之间解决。
伊万斯的例子二时,世俗类型的审判从十三世纪开始,第一次是一个1266年资本审判,猪被指控吃小孩。
通常情况下,被告在审批中是这些试验猪(虽然伊万斯报告审判也包括其他家养动物,如牛,绵羊,山羊,马,驴,骡,狗,和家禽)。
猪频繁的陷入法律麻烦可能是中世纪的做法,让他们自由地漫游在街头的一个后果,在那里他们更有机会机会吃掉无人看管的儿童——一个尴尬的提醒,猪就像部分年轻人,那些软弱的人会成为许多人的熏肉三明治。
因此,伊万斯描述,被告的动物在大多数情况下都是失败的。
伊万斯指出:“只有那些被指责的案例中被告被认定有罪,”虽然他也讲述一些例外。
例如,在一个案件中,“母驴”和她的主人的人都被判处死刑,但驴子因为性格两哈被宣告无罪。
社区的居民vanvres签署证书见证,驴在语言和行动上与她所有的生活习惯一样是最诚实的动物。
”另一个例子是,母猪和她的六猪仔试图杀死一个五岁的男孩;母猪被判处死刑,但由于仔猪缺乏确凿的证据证明他们参与了犯罪被宣告无罪。
当仔猪的主人拒绝为他们的未来负责的良好引导行为,他们被“宣布,作为空置财产,没收给贵族少女凯瑟琳德萨维尼女士。
”鉴于仔猪还在哺乳期和他们的母亲被杀,人们猜测,他们可能没有太多机会再以后出现在贵族女子的餐桌上。
伊万斯的很多公约的讨论和动物审判的理由的重点是教会的诉讼。
复杂的是,在某些方面,令人惊讶的现代的动物倡导者和反对者的有关辩论已经回落到我们的这种类型的审判。
这种开放的话语是符合教会的长期传统的内部争论神学观点。
这是教会法一个基本原则的,不能对一个没有得到听证的人作出决定,甚至是教会的地位制度化的霸王条款,“官员必须事先了解这些论点,撒旦本人可能应用于未来的圣人”的人和过程中。
