Dynamic Memory Allocation for Multiple-Query Workloads
operating system《操作系统》ch08-main memory

Operating system maintains information about: a) allocated partitions b) free partitions (hole)
8.12
Dynamic Linking
Linking postponed until execution time Small piece of code, stub, used to locate the appropriate memory-resident library routine Stub replaces itself with the address of the routine, and executes the routine Operating system needed to check if routine is in processes’ memory address Dynamic linking is particularly useful for libraries System also known as shared libraries
8.16
Contiguous Allocation (Cont.)
Multiple-partition allocation
Hole – block of available memory; holes of various size are scattered throughout memory
8.6
Binding of Instructions and Data to Memory
出现MAF(memoryallocationfailure)的解决方法

出現MAF(memo ry al locat ion f ailur e)的解決方法.玩超大型MOD,內存至少3G,而且需要輸入指令,打開電腦內存使用權限,才能發揮內存效果,我也經常玩32文明的Carte r地球192*120(地圖比G EM 210*90還大).以前不懂內存使用超過2G,需另外下指令擴增權限(32位元系統預設系統與其它程式共同使用內存上限2G),常常玩超大MOD到1500年超就出現"m emory allo catio nfai lure"內存配置失敗(XP好像是出現藍屏),重開遊戲玩個10回合,又發生MAF失敗,後來查資料,才知道除了內存硬體需擴充到3G(32位元系統,安裝4G內存效果和3G一樣), 還需要輸入指令,才能打開內存權限給程式使用,正常18Civ遊戲,內存2G綽綽有餘,但是文明4超大型MO D,玩到1500年後很容易使用超出2G內存,所以請依以下方式操作.(分Vista,XP與W in7三種32位元系統)一:先講Vi sta 32位元系統1:到C:\Win dows\Syste m32 目錄下,找出"cmd.exe"執行檔2:在cdm.exe上點滑鼠右鍵,選"以管理員身分運行",執行c md.ex e3:然後可以看到cmd視窗,直接輸入 bcde dit /set I ncrea seUse rVA 3072 再按Ente r4:然後可以看到"操作成功完成",最後重開機,就可以享受無MAF樂趣.請注意,如果輸入指令後,看到"无法打开启动配置数据存储。
memory allocation policy 内存分配策略 -回复

memory allocation policy 内存分配策略-回复【内存分配策略】内存分配策略是操作系统中的重要概念之一,用于决定如何有效地管理和分配计算机内存资源。
通过合理的内存分配策略,可以提高系统的性能和资源利用率,从而为用户提供更好的使用体验。
本文将一步一步回答关于内存分配策略的问题,深入探讨其原理、分类和应用。
一、什么是内存分配策略?内存分配策略是操作系统中用于管理计算机内存的方法和流程,它决定了如何将计算机内存划分为不同的区域,并按照一定的规则分配给进程或程序。
内存分配策略可以根据不同的需求和应用场景进行调整,以满足系统性能和资源管理的要求。
二、内存分配策略的原理和分类1. 首次适应(First Fit):这是最常见的内存分配策略之一。
首次适应策略从内存的起始位置开始搜索,找到第一个能满足进程内存需求的空闲区域,并进行分配。
这种策略简单高效,但可能会造成内存碎片的问题。
2. 最佳适应(Best Fit):最佳适应策略选择最小而又能满足进程需求的空闲分区进行分配。
它可以减少内存碎片的数量,但可能会增加搜索的时间和开销。
3. 最坏适应(Worst Fit):最坏适应策略选择最大的空闲分区进行分配。
这种策略可以使得分配后剩余的空闲区域更大,但可能会增加内存碎片的数量。
4. 快速适应(Quick Fit):快速适应策略是对首次适应策略的改进,通过将内存划分为多个大小不同的区域,根据进程的需要分配合适的区域。
这种策略可以减少搜索的时间和开销,并且在一定程度上解决了内存碎片的问题。
5. 分区固定(Fixed Partitioning):分区固定策略将内存分成固定大小的区域,每个区域只能分配给一个进程。
这种策略简单且适用于特定场景,但会导致内存利用率较低。
6. 动态分区(Dynamic Partitioning):动态分区策略按需划分内存,每个分区可分配给不同大小的进程。
这种策略可以灵活利用内存资源,但可能会增加内存碎片的问题。
Dynamic slot allocation and tracking of multiple m
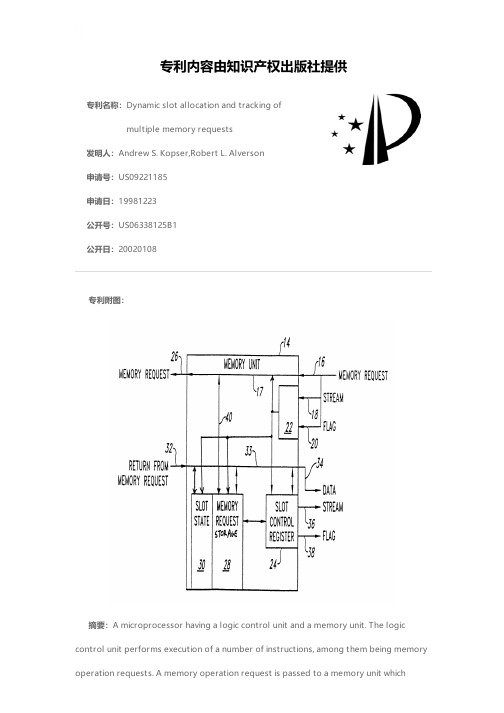
专利名称:Dynamic slot allocation and tracking ofmultiple memory requests发明人:Andrew S. Kopser,Robert L. Alverson申请号:US09221185申请日:19981223公开号:US06338125B1公开日:20020108专利内容由知识产权出版社提供专利附图:摘要:A microprocessor having a logic control unit and a memory unit. The logiccontrol unit performs execution of a number of instructions, among them being memory operation requests. A memory operation request is passed to a memory unit whichbegins to fulfill the memory request immediately. Simultaneously with the memory request being made, a copy of the full memory request is made and stored in a storage device within the memory unit. In addition, an identification of the request which was the origin of the memory operation is also stored. In the event the memory request is fulfilled immediately, whether it be the retrieval of data or the storing of data, the results of the memory request are provided to the microprocessor. On the other hand, in the event the memory is busy and cannot fulfill the request immediately, the memory unit performs a retry of the memory request on future memory request cycles. The microprocessor is able to perform the execution of additional instructions and other operations without having to be concerned about the memory request because the memory unit contains a duplicate of the memory request and will continue to perform and retry the memory request until it is successfully completed. This significantly increases overall microprocessor operation and throughput of instruction sets.申请人:CRAY INC.代理机构:Seed IP Law Group PLLC代理人:David V. Carlson更多信息请下载全文后查看。
formal parameter形式参数actual parameter 实际参数 assign 赋值 direct recursion 直接递归i单词

•formal parameter形式参数actual parameter 实际参数assign 赋值direct recursion 直接递归indirect recursi间接递归dynamic memory allocation 动态存储分配(run-time or dynamic allocation of memory)operator 操作符pointer 指针compile编译address 访问exception异常throw 引发catching 捕获block 语句块abnormal program termination 异常程序终结mechanism机制Instance 实例Component 成员Public 共有类Private 私有类Method方法Interact 交互Softwareengineering软件工程Construtor functio构造函数Default value 缺省值Initialization 初始值Null function 空函数Reuse 重用Constant function 常元函数Reserved word 保留关键字Derived class 派生类Base class 基类program test 程序测试test data 测试数据test set 测试集black box method 黑盒法white box method 白盒法I/O partitioning I/O分类cause-effect graphin 因果图statement coverage 语句覆盖decision coverage分支覆盖clause coverage 从句覆盖boolean expression 布尔表达式execution path 执行路径data representation 数据描述formula based representation 公式化描述linked representation 链接描述indirect addressing间接寻址simulated pointer 模拟指针linear list 线性表abstract data type抽象数据类型chains 链表circular lists 循环链表doubly linked lists双向链表primitive 原语atomic 原子element 元素Template class模板类Link field 链接域Data field 数据域Singly linked list 单向链表Row-major representation 行主描述形式Column-major representation 列主描述形式Multidimensional array多维数组Diagonal matrices 对角矩阵Tridiagonal matrices 三对角矩阵Triangular 三角矩阵Symmetric matrices 对称矩阵The Abstract Data Type抽象数据类型Dictionaries字典binary search method 折半搜索法random access随机访问sequential access 顺序访问ambiguity 歧义hash function 哈希函数hash table哈希表collision 冲突overflow 溢出compressor 压缩器decompressor 解压缩器hierarchical data 层次数据sibling 兄弟grandchild 孙子grandparent 祖父ancestor 祖先descendent后代degree of an element 元素的度full binary tree 满二叉树complete binary tree 完全二叉树Preorder 前序遍历Inorder中序遍历Postorder后序遍历Level order 层次遍历priority queue 优先队列min priority queue最小优先队列max priority queue 最大优先队列schedule 调度approximation algorithms 近似算法•••••••。
浙大操作系统试题-2003-2004_PncipleExam6
浙江大学2003 —2004 学年第一学期期终考试《操作系统》课程试卷考试时间:120 分钟开课学院: 计算机学院专业:___________姓名:____________ 学号:_____________ 任课教师:_____________题序一二三(1)三(2)三(3)三(4)三(5)总分评分评阅人PART I Operating System Principle Exam一、C hoose True(T) or False(F) for each of following statements and fill your answer infollowing blanks, (20 marks)1. ( )2. ( )3. ( )4. ( )5. ( )6. ( )7. ( )8. ( )9. ( ) 10. ( )11. ( ) 12. ( ) 13. ( ) 14. ( ) 15. ( )16. ( ) 17. ( ) 18. ( ) 19. ( ) 20. ( )1.Process is an entity that can be scheduled.2.In the producer-consumer problem, the order of wait operations cannot be reversed, while theorder of signal operations can be reversed.3.As to semaphores, we can think an execution of signal operation as applying for a resource.4.Mutual exclusion is a special synchronization relationship.5.Paging is a virtual memory-management scheme.6.If the size of disk space is large enough in the virtual memory-management system, then aprocess can have unlimited address space.7.Priority-scheduling algorithm must be preemptive.8.In the virtual memory-management system, the running program can be larger thanphysical memory.9.File directory is stored in a fixed zone in main memory.10.While searching a file, the searching must begin at the root directory.11.Thread can be a basic scheduling unit, but it is not a basic unit of resourceallocation.12. A process will be changed to waiting state when the process can not be satisfiedits applying for CPU.13.If there is a loop in the resource-allocation graph, it shows the system is ina deadlock state.14.The size of address space of a virtual memory is equal to the sum of main memoryand secondary memory.15.Virtual address is the memory address that a running program want to access.16.If a file is accessed in direct access and the file length is not fixed, thenit is suitable to use indexed file structure.17.SPOOLing system means Simultaneous Peripheral Operation Off Line.18.Shortest-seek-time-first(SSTF) algorithm select the request with the minimumhead move distance and seek time. It may cause starvation.19.The main purpose to introduce buffer technology is to improve the I/O efficiency.20.RAID level 5 stores data in N disks and parity in one disk.二、Choose the CORRECT and BEST answer for each of following questions and fill your answer in following blanks, (30 marks)1. ( )2. ( )3. ( )4. ( )5. ( )6. ( )7. ( )8. ( )9. ( ) 10. ( )11. ( ) 12. ( ) 13. ( ) 14. ( ) 15. ( )16. ( ) 17. ( ) 18. ( ) 19. ( ) 20. ( )21. ( ) 22. ( ) 23. ( ) 24. ( ) 25. ( )26. ( ) 27. ( ) 28. ( ) 29. ( ) 30. ( )1. A system call is 。
SSD6名词解释(个人完善版)

SSD6名词解释1. alignment(对齐)Compilers often try to align data word boundaries or even double-word or even double-word boundaries.(计算机系统对基本数据类型的可允许地址做出的限制,要求某种类型的对象地址必须是某个值K(2,4,8)的倍数。
2. activation record(活动记录)The chunk of memory allocated for each function invocation .大块的内存分配为每个函数调用3. buffer overflow(缓存溢出)Place more than the buffer can hold, so overwrite the boundary .4. static memory allocation(静态内存分配)Static memory allocation is the allocation of memory storage during the compile time and link time (在程序编译和链接时分配内存)5. dynamic memory allocation(动态内存分配)Dynamic memory allocation is the allocation of memory storage during the runtime of program. (在程序运行时分配内存)6. garbage collection (垃圾回收)Automatic reclamation of heap-allocated storage .自动回收堆存储的过程叫做垃圾回收。
垃圾收集器是一种动态存储分配器,它自动释放程序不再需要的已分配块。
7. timer(计时器)A component in computer system/CS, as a hardware or software, which can provide the ability of measure time in some degree.计算机系统的组件,可以是硬件或者软件,能够提供某种精度上的时间的测量。
内存报错解决方法(Memory error resolution)

内存报错解决方法(Memory error resolution)然后关闭并停止Windows管理规范服务。
删除WINNT \ System32 \ WBEM \库文件夹中的所有文件。
(在删除前请创建这些文件的备份副本。
)打开”服务和应用程序”,单击服务,然后打开并启动Windows 管理规范服务。
当服务重新启动时,将基于以下注册表项中所提供的信息重新创建这些文件:hkey_local_machine \软件\微软\ \\”MOFs CIMOM WBEM下面搜集几个例子给大家分析:例一:即浏览器出现”0x0a8ba9ef”指令引用的”0x03713644”内存,或者”0x70dcf39f”指令引用的”0x00000000”内存。
该内存不能为“读”。
要终止程序,请单击”确定”的信息框,单击”确定”后,又出现”发生内部错误,您正在使用的其中一个窗口即将关闭”的信息框,关闭该提示信息后,即解决方法浏览器也被关闭:1、开始-运行窗口,输入“regsvr32 actxprxy .dll”回车,接着会出现一个信息对话框”中的DllRegisterServer actxprxy.dll中成功”,确定。
再依次运行以下命令。
(这个方法有人说没必要,但重新注册一下那些。
DLL对系统也没有坏处,反正多方下手,能解决问题就行。
)regsvr32 Shdocvw.dllregsvr32 OLEAUT32.DLLregsvr32 actxprxy.dll中regsvr32 mshtml.dllmsjava.dll regsvr32regsvr32 browseui.dllregsvr32 urlmon.dll2、修复或升级IE浏览器,同时打上系统补丁。
看过其中一个修复方法是,把系统还原到系统初始的状态下升级到了建议将IE 6。
例二:有些应用程序错误:“0x7cd64998”指令参考的”0x14c96730”内存。
该内存不能为“读”。
17-allocation-basic
Will discuss simple explicit memory allocation today
4
Carnegie Mellon
The mallocPackage
#include <stdlib.h> void *malloc(size_t size) Successful: Returns a pointer to a memory block of at least sizebytes (typically) aligned to 8-byte boundary If size == 0, returns NULL Unsuccessful: returns NULL (0) and sets errno void free(void *p) Returns the block pointed at by p to pool of available memory p must come from a previous call to mallocor realloc Other functions calloc: Version of malloc that initializes allocated block to zero. realloc: Changes the size of a previously allocated block. sbrk: Used internally by allocators to grow or shrink the heap
Uk= ( maxi<k Pi ) / Hk
11
Carnegie Mellon
Fragmentation
Poor memory utilization caused by fragmentation
c语言英文试卷

c语言英文试卷C语言英文试卷的主要内容包括:基础知识、数据结构与算法、操作系统、网络编程等方面。
以下是一些建议的英文试题:1. Choose the correct answer:Which of the following is NOT a basic data type in C language?A. intB. floatC. stringD. character2. Fill in the blank:The prototype of the function `void swap(int *a, int *b)` is______.3. Write the correct syntax for declaring a 2D array of size 3x4 and initializing it with default values.4. Choose the correct answer:Which of the following is the correct syntax for calling a function na med `sum` that takes two integers as arguments and returns an integer?A. int sum(int a, int b);B. int sum(int, int);C. int sum(a, b);D. int sum(int b, int a);5. Fill in the blank:The return statement in C language is______.6. Write a C program to find the factorial of a given number.7. Write a C program to sort an array of 10 elements using bubble s ort.8. Choose the correct answer:Which of the following is the correct way to declare a function with a pointer parameter?A. void fun(int *p);B. void fun(int &p);C. void fun(int p);D. void fun(int *&p);9. Fill in the blank:In the following code, the purpose of the `malloc` function is to allo cate______.10. Write a C program to demonstrate the use of file I/O operations.11. Write a C program to implement a simple dynamic memory alloc ation using `malloc` and `free`.12. Choose the correct answer:Which of the following is NOT a valid operator in C language?A. %B. &C. |D. <<13. Fill in the blank:The precedence of the following arithmetic operators is______.14. Write a C program to find the sum of all even numbers from 1 to 100.15. Write a C program to implement a function that takes a string as input and reverses it.Remember to provide solutions for each problem, and use appropriate English vocabulary and grammar. This will help you practice your C lan guage programming skills and prepare for an English-based exam or interv iew.。
CHAPTER 9 MEMORY MANAGEMENT (内存管理) 《操作系统概念》英文版课件

Background: Overlays(覆盖 )
Keep in memory only those instructions and data that are needed at any given time.
Needed when process is larger than amount of memory allocated to it.
Contiguous Memory Allocation: Fixed-Sized Contiguous Partitions
Main memory is divided into a number of fixed partitions at system generation time. A process may be ded into a partition of equal or greater size. Equal-size partitions Unequal-size partions
Swapping: Schematic View
Swapping: Backing store
Swap file Swap device Swap device and swap file
Swapping: Performance
Major part of swap time is transfer time; total transfer time is directly proportional to the amount of memory swapped. 1000KB/5000KBS = 1/5 seconds = 200ms
Why to protect memory? To protect the OS from user processes And to protect user process from each other.
介入中c的组件和用法

在软件开发中,特别是在使用C语言进行编程时,组件通常是指可以重用并且能够执行特定功能的代码模块。
在C语言中,组件可以是函数、结构体、联合体、枚举类型、宏定义等。
这些组件可以通过函数调用、指针、引用或者导入的头文件等方式被其他代码文件使用。
以下是一些C语言中常用的组件和它们的用法:1. **函数(Function)**:- 定义:函数是一段可以被多次调用的代码块,它执行一个特定的任务。
- 用法:函数必须先被声明,然后定义。
声明包括函数名、返回类型和参数列表。
2. **结构体(Structure)**:- 定义:结构体是一种复合数据类型,允许开发者将不同类型的数据项组合成一个单一的实体。
- 用法:定义结构体类型,然后声明并初始化结构体变量。
3. **联合体(Union)**:- 定义:联合体是一种特殊的数据类型,它允许在相同的内存位置存储不同类型的数据。
- 用法:定义联合体类型,然后声明并初始化联合体变量。
4. **枚举(Enum)**:- 定义:枚举是一种命名的整数类型,允许开发者定义一组命名的常量。
- 用法:定义枚举类型,然后使用枚举常量。
5. **宏定义(Macro)**:- 定义:宏定义是在预处理器阶段替换为指定字符串的文本。
- 用法:使用`#define`关键字定义宏,并在代码中使用`#include`来包含头文件。
6. **动态内存分配(Dynamic Memory Allocation)**:- 定义:动态内存分配是在程序运行时分配内存,与静态内存分配相对。
- 用法:使用`malloc()`, `calloc()`, `realloc()`和`free()`函数进行动态内存的管理。
7. **指针(Pointer)**:- 定义:指针是一个变量,其值为另一个变量的地址。
- 用法:通过指针访问和修改内存中的数据。
8. **引用(Reference)**:- 定义:引用是一个变量的别名,它和原变量共享同一个内存地址。
应用程序初始化失败问题(Applicationinitializationfailed)

应用程序初始化失败问题(Application initialization failed)The application failed to initialize _~ ~!Application initialization failed (oxc0000005) reasons and Solutions1, Microsoft IE buffer overflow vulnerability caused2, memory or virtual memory address conflict program needs to be allocated to address certain procedures to use, when new procedures for the use of space to release at the end of the program, win is a multi tasking system before the program does not end sometimesThere is a new task to how much memory or virtual memory to ensure that we run at the same time the task? Perhaps win on this issue is not ready, so the errors often occur, the general operation of the large-scale software or multimedia3, poor memory will appear this problem in general, memory problems are not likely, the main aspect is: bad memory, memory quality problems, there are 2 different brands of different memory mixed interpolation, are more prone to incompatible situation, but also pay attention to the heat problem, especially after overclocking. You can use the MemTest software to check memory, which can thoroughly detect the stability of memory. If you are dual memory, and the memory of different brands, mixed in, or bought a secondary memory, this problem occurs, then you have to check whether the memory problems, or incompatible with other hardware.4, Microsoft WINDOWS system vulnerabilities, windows memory address 0X00000000 to 0X0000ffff designated as assigned null pointer address range, if the program attempts to access this address, is considered to be wrong. Programs written by c/c++ usually do not undergo rigorous error checking and return null pointers when malloc is used to allocate memory and the assigned address space is insufficient. However, the code does not check this error, considers that the address assignment has been successful, so it accesses the address of the 0X00000000, so memory violation access occurs, and the process is terminated. The following ASCII character fill consisting of PIF file: an illegal PIF file (filled with a ASCII character \''x\'') at least 369 bytes, the system was considered to be a valid PIF file, 0] will display to the PIF icon, [pifmgr.dll, will have a program, font, memory, screen etc. the contents in the attributes. And when a non PIF file is 369 bytes in size, the program's error is not detected even if it is 370 bytes. When a PIF file is larger than 369 bytes for illegal property "program" page, Explorer will go wrong, that \''***\''Command Reference \''***\'' memory. This memory cannot be \''read\''The problem is in the 16 hexadecimal address of the PIF file: 0x00000181[0x87]0x00000182[0x01] and0x00000231[0xC3]0x00000232[0x02] even if it's a legitimate PIF file, it can cause program errors whenever you change any of these places. As long as the value of 0x00000181 and 0x00000182 is changed to [0xFF][0xFF], any change of other addresses will not cause errors.5, there may not be a Apache service is installed correctly,and started its service in the cause; OracleOraHomeXXHTTPServer to stop6, the application does not check the memory allocation failure procedure requires a memory to save the data, you need to call the operating system to provide a "function" to apply, if successful memory allocation, memory area function will be the new return to the application, the application can use this memory via this address. This is the "dynamic memory allocation", the memory address, that is, "pointer" in programming". Memory is not always available, endless, and sometimes memory allocation will fail.When the allocation fails, the system function returns a 0 value, when the return value "0" does not represent the newly enabled pointer, but rather a notification issued by the system to the application informing the error. As an application, in the memory after each application should check whether the return value is 0, if it is, it means that there is a fault, some measures should be taken to save, which enhances the robustness of the program "". If the application does not check the error, it will continue to use this memory in subsequent operations, in accordance with the thinking inertia that the value is the pointer that is allocated to it. The real 0 address memory area holds the most important "interrupt descriptor table" in the computer system and absolutely does not allow the application to use. In the operating system without protection mechanism under (such as DOS), write data to this address will lead to crash immediately, and in the robust operating system, such as Windows, this operation will be immediately captured the protection mechanism of the system, the result is forciblyclosed by the operating system application error, in order to prevent the error expansion. At this point, the above "write memory" error occurs and indicates that the referenced memory address is "0x00000000"". Memory allocation failure, many reasons, memory is insufficient, the version of the system function mismatch, and so may have an impact. Therefore, the distribution of failure in the operating system to use for a long time, the installation of a variety of applications (including accidentally "Install" virus program), after the change of system parameters and system of a large number of documents.7, the application due to its unusual BUG quoted the memory pointer in the application using dynamic allocation, sometimes there will be such a situation: the program attempts to write a "should be available" in memory, but I do not know why, it is expected that can be a pointer has been a failure. There may be "forget" to the operating system requirements distribution, or it may be the program itself at some point has canceled the memory, and "no attention" and so on. Off the system memory to be recycled, the access does not belong to the application, read and write operations can also trigger a mechanism to protect the system, trying to "end" illegal procedures only termination of the operation is to be run, all resource recovery. The laws of the computer world are still much more effective and harsher than human beings! A situation like this belongs to the BUG of the program itself, and you can often reproduce errors in a particular order of operations. The invalid pointer is not always 0, so the memory address in the error is not necessarily "0x00000000", but rather the other random numbers.If the system often mentions errors, the following suggestions might help:1. check whether there is a Trojan horse or virus in the system. In order to control the system, such programs often change the system without responsibility, resulting in abnormal operating systems. Generally, we should strengthen the awareness of information security and not be curious about the executable programs of unknown sources.2. update the operating system so that the operating system's installer re copies the correct version of the system file and changes the system parameters. Sometimes, the operating system itself will have BUG, pay attention to install the official release of the upgrade program.3. try out a new version of the application.4, delete, and then recreate the WINDOWS\Wbem\RepositoryFile in the folder: right click on my computer on the desktop, and then click manage. Under services and applications, click service, then close and stop Windows ManagementInstrumentation service. DeleteWINDOWS\System32\Wbem\RepositoryAll files in the folder. (create a backup copy of these files before deleting.) Open the service and application, click service, and then open and start Windows ManagementInstrumentation service. When the service restarts, these files are recreated based on the information provided in the following registry key:hkey_local_machine \软件\微软\ \ \”MOFs CIMOM WBEM下面我从几个例子给大家分析:例一:打开IE浏览器或者没过几分钟就会出现”0x70dcf39f”指令引用的”0x00000000”内存。
memory allocation policy 内存分配策略

memory allocation policy 内存分配策略Memory allocation policy refers to the strategy and set of rules followed by a computer system to manage and allocate memory resources. It determines how memory is assigned, utilized, and released by programs and processes running on the system. This article aims to provide a comprehensive understanding of memory allocation policies, their types, and their impact on overall system performance.To begin with, memory allocation policies are essential for efficient memory management in any computer system. The main objective of these policies is to maximize the utilization of limited memory resources while minimizing fragmentation and conflicts among different processes. Additionally, memory allocation policies play a crucial role in determining the fairness and responsiveness of a system to different tasks and user demands.There are several types of memory allocation policies commonly used in modern operating systems. The most fundamental policy is called fixed partition allocation. In this policy, the memory is divided into fixed-sized partitions, and each process is allocated a partition that best fits its memory requirements. However, thispolicy suffers from the limitation of fixed-sized partitions, resulting in internal fragmentation, where memory inside the partition remains unutilized.To address the limitations of fixed partition allocation, dynamic partition allocation was introduced. This policy overcomes the fixed-sized partition problem by allocating memory dynamically according to the process's actual memory requirements. It uses data structures like linked lists or binary trees to keep track of the free and allocated memory blocks. Dynamic partition allocation reduces internal fragmentation but can lead to external fragmentation, where free memory blocks become scattered and fragmented over time.To combat external fragmentation, another approach known as compaction is often used in memory allocation policies. Compaction involves moving the allocated blocks of memory together, leaving a large contiguous free memory space. However, compaction can be computationally expensive and may result in a significant delay in memory allocation operations.Another important memory allocation policy is called paging. Inthis policy, memory is divided into fixed-sized blocks called pages, and processes are divided into fixed-sized units called pages or page frames. The primary advantage of paging is that it can eliminate both external and internal fragmentation. However, it introduces overhead due to the need for page tables and additional memory accesses.A variation of the paging policy is known as virtual memory. Virtual memory is an abstraction that allows processes to access more memory than physically available in the system. It uses a combination of RAM and disk storage to swap pages in and out of memory as needed. Virtual memory greatly enhances the system's ability to run multiple processes simultaneously, as it provides an illusion of a larger memory space to each process.Apart from the aforementioned policies, there are other memory allocation strategies like buddy allocation, slab allocation, and first-fit, best-fit, and worst-fit allocation algorithms. These policies offer different trade-offs between memory utilization, fragmentation, and allocation speed, depending on the specific requirements of the system.In conclusion, memory allocation policies are vital for efficient memory management in computer systems. They determine how memory resources are assigned, utilized, and released. Various policies like fixed partition allocation, dynamic partition allocation, paging, compaction, and virtual memory have been developed to address different challenges and trade-offs. The selection of the appropriate memory allocation policy depends on factors such as the system's requirements, performance goals, and available hardware resources.。
dmalloc用法

dmalloc用法【原创实用版】目录1.dmalloc 简介2.dmalloc 基本用法3.dmalloc 的优缺点4.使用 dmalloc 的注意事项正文【1.dmalloc 简介】dmalloc 是一个用于分配内存的 C 语言库函数,它的全称是“dynamic memory allocation”,即动态内存分配。
与传统的 malloc 和calloc 函数相比,dmalloc 提供了更多的灵活性和控制能力,使得程序员可以在运行时动态地分配和释放内存。
【2.dmalloc 基本用法】使用 dmalloc 的基本步骤如下:(1)包含头文件:在使用 dmalloc 之前,需要包含头文件<stdlib.h>。
(2)分配内存:使用 dmalloc 函数分配内存,其基本语法为:```void *dmalloc(size_t size);```其中,`size`表示要分配的内存空间的大小,单位为字节。
如果分配成功,dmalloc 返回一个指向分配内存的指针;如果分配失败,则返回NULL。
(3)释放内存:使用 dfree 函数释放已分配的内存,其基本语法为:```void dfree(void *ptr);```其中,`ptr`表示要释放的内存空间的指针。
【3.dmalloc 的优缺点】优点:(1)灵活性高:dmalloc 允许程序员在运行时动态地分配和释放内存,适应性强。
(2)控制能力好:dmalloc 提供了一些附加的控制参数,如分配内存的位置、是否初始化为 0 等,方便程序员进行精细化控制。
缺点:(1)易错性高:由于 dmalloc 需要手动分配和释放内存,程序员容易忘记或错误地进行内存管理,导致内存泄漏等问题。
(2)性能较差:相较于 malloc 和 calloc 函数,dmalloc 的性能较差,因为其需要更多的控制参数和函数调用。
【4.使用 dmalloc 的注意事项】(1)避免内存泄漏:在使用 dmalloc 时,务必记得在不再需要内存时使用 dfree 函数释放,以免造成内存泄漏。
编程英文面试题及答案高中

编程英文面试题及答案高中1. What is the difference between a 'function' and a'procedure' in programming?Answer:A 'function' in programming is a block of code that performs a specific task and returns a value. It can be called multiple times within a program. A 'procedure', on the other hand, is a block of code that performs a task but does not return a value. Procedures are used for their side effects.2. Explain the concept of 'encapsulation' in object-oriented programming (OOP).Answer:Encapsulation in OOP is the mechanism of bundling the data (attributes) and the methods (functions) that operate on the data into a single unit or class. It restricts direct access to some of an object's components, which can prevent the accidental modification of data.3. What is the purpose of 'inheritance' in OOP?Answer:Inheritance in OOP allows a class (child class) to inherit properties and methods from another class (parent class). This promotes code reusability and can create a hierarchical relationship between classes.4. Describe the 'call stack' in programming.Answer:The call stack is a data structure used by a program to keep track of function calls. When a function is called, its return address and local variables are pushed onto the stack. When the function returns, the information is popped from the stack, and the program continues from the return address.5. What is the difference between 'static' and 'dynamic' memory allocation in programming?Answer:Static memory allocation is when memory is allocated at compile time and the size is fixed. It is typically used for global variables and static variables. Dynamic memory allocation, on the other hand, occurs at runtime, and the size can change. It is typically managed through pointers and requires manual allocation and deallocation using functions like `malloc` and `free` in C.6. What is 'recursion' in programming?Answer:Recursion is a programming technique where a function calls itself directly or indirectly to solve a problem. It is often used to solve problems that can be broken down into smaller, similar subproblems.7. Explain the 'Big O' notation and its importance inalgorithm analysis.Answer:Big O notation is a mathematical notation that describes the limiting behavior of a function when the argument tends towards a particular value or infinity. In computer science, it is used to classify algorithms according to how their running time or space requirements grow as the input size grows.8. What is a 'hash table' and how does it work?Answer:A hash table is a data structure that stores data in an associative manner. It uses a hash function to compute an index into an array of buckets or slots, from which the desired value can be found. Ideally, the hash function assigns each key to a unique bucket, but most hash table designs employ an imperfect hash function, which might cause hash collisions.9. What is 'polymorphism' in OOP?Answer:Polymorphism in OOP is the ability of different objects to respond, each in their own way, to the same message or method call. It allows objects of different classes to be treated as objects of a common superclass.10. What is 'exception handling' in programming?Answer:Exception handling is a programming language feature to handle the occurrence of errors during program execution. It allows the program to 'catch' an error, decide how to handle it, and then continue executing the program.结束语:Understanding these fundamental concepts is crucial for anyone looking to excel in programming. Whether you are preparing for a high school programming interview or simply looking to deepen your knowledge, these questions and answers should provide a solid foundation for further exploration in the field of computer science.。
【总结】Spark任务的core,executor,memory资源配置方法

【总结】Spark任务的core,executor,memory资源配置⽅法执⾏Spark任务,资源分配是很重要的⼀⽅⾯。
如果配置不准确,Spark任务将耗费整个集群的机缘导致其他应⽤程序得不到资源。
怎么去配置Spark任务的executors,cores,memory,有如下⼏个因素需要考虑:数据量任务完成时间点静态或者动态的资源分配上下游应⽤Spark应⽤当中术语的基本定义:Partitions : 分区是⼤型分布式数据集的⼀⼩部分。
Spark使⽤分区来管理数据,这些分区有助于并⾏化数据处理,并且使executor之间的数据交换最⼩化Task:任务是⼀个⼯作单元,可以在分布式数据集的分区上运⾏,并在单个Excutor上执⾏。
并⾏执⾏的单位是任务级别。
单个Stage 中的Tasks可以并⾏执⾏Executor:在⼀个worker节点上为应⽤程序创建的JVM,Executor将巡⾏task的数据保存在内存或者磁盘中。
每个应⽤都有⾃⼰的⼀些executors,单个节点可以运⾏多个Executor,并且⼀个应⽤可以跨多节点。
Executor始终伴随Spark应⽤执⾏过程,并且以多线程⽅式运⾏任务。
spark应⽤的executor个数可以通过SparkConf或者命令⾏ –num-executor进⾏配置Cores:CPU最基本的计算单元,⼀个CPU可以有⼀个或者多个core执⾏task任务,更多的core带来更⾼的计算效率,Spark中,cores决定了⼀个executor中并⾏task的个数Cluster Manager:cluster manager负责从集群中请求资源cluster模式执⾏的Spark任务包含了如下步骤:1. driver端,SparkContext连接cluster manager(Standalone/Mesos/Yarn)2. Cluster Manager在其他应⽤之间定位资源,只要executor执⾏并且能够相互通信,可以使⽤任何Cluster Manager3. Spark获取集群中节点的Executor,每个应⽤都能够有⾃⼰的executor处理进程4. 发送应⽤程序代码到executor中5. SparkContext将Tasks发送到executors以上步骤可以清晰看到executors个数和内存设置在spark中的重要作⽤。
内存不能为read的解决办法-电脑知识-360百科(Memorycannotbeas..

内存不能为read的解决办法 - 电脑知识 - 360百科(Memory can not be a solution for read - computer knowledge - 360encyclopedias)Memory can not be read solutions - computer knowledge - Encyclopedia of 360 log | registered | complaints and suggestions | area Kaba activated the official website of 360 | Zhuanshagongju | 360 | ForumWikipedia home pageSoftware classificationSearch for posts, search WikipediaReturn home essence, Wikipedia school task, receive Gold Exchange* 360 security guards V4.1Beta version release, please download the trial! You drive to stop "the new AV variant (javqhc) and terminator"* this week popular Trojan warning, remind you to prevent 360 (20080326). Who is the "king of the task? Latest task list!* [new] gift vote cast your favorite gift. Encyclopedia assistant to help you friends, please help![*] tricky Carnival: April Fool's Day activities and being the whole share experience! '[produced] user task Raiders, to help you do a better job!* [produced] Wikipedia users ashes users taught you: "360 new upgrade guide"! * 360 security guards V4.1Beta version release, please download the trial!You drive to stop "the new AV variant (javqhc) and terminator". This week popular Trojan warning, remind you to prevent 360 (20080326)* who is the "task king"? The latest task list! * [new] gift vote cast your favorite gift. Encyclopedia assistant to help you friends, please help![*] tricky Carnival: April Fool's Day activities and being the whole share experience! '[produced] user task Raiders, to help you do a better job!* [produced] Wikipedia users ashes users taught you: "360 new upgrade guide"!Current position: 360 Encyclopaedia computer knowledge > memory cannot be read solutionQuick answer, new topic, I want to ask for help, a total of 325 posts, <12345... 17> memory can not be read solutionLisongshunSend a noteGold coin: 678Experience value: 393Level: grade five in primary schoolReference reported 1 floor memory can not be read solution published at 10:15 2008-03-27Recently, many users have encountered the memory can not be "read" error prompt. I hope that the following articles can help you.When you run certain programs, there are hints of memory errors, and then the program closes."0x" the directive quoted as "0x?" memory. The memory cannot be "read""."0x", the directive quoted as "0x" memory, and this memory cannot be "written"".The above situation is believed that everyone should have seen, and even said that some users because of this error often does not occur repeatedly reinstall the system. Believe that ordinary users should not understand those complex sixteen hexadecimal code.There are aspects of this phenomenon, one is hardware, that is, memory problems, and the two is software, which there are many problems.One: first about hardware:Generally speaking, computer hardware is not easy to bad. Memory problems are not likely (unless your memory is really a Hodge only to collapse), the main areas are: 1. Memory bad (secondary memory is mostly), 2. Using quality memory, 3. Memory inserted on the motherboard is too dusty in the gold fingers section. 4. The use of different brands, different capacities of memory, resulting in incompatibility. 5. Overclocking brings heat problems. You can use the MemTest software to check memory, which can thoroughly detect the stability of memory.Two, if not, then the software from the troubleshooting.The first principle: the memory has a place called the storage of data buffer, when the program on the data buffer, need to provide the operating system "function" to apply, if successful memory allocation, memory area function will be the new return to the application, applications can use this memory through this address. This is the "dynamic memory allocation", the memory address, that is, "cursor" in programming".Memory is not always available, endless, and sometimes memory allocation will fail. When the allocation fails, the system function returns a 0 value, when the return value "0" does not represent the newly enabled cursor, but rather a notification issued by the system to the application informing the error. As an application, in the memory after each application should check whether the return value is 0, if it is, it means that there is a fault, some measures should be taken to save, whichenhances the robustness of the program "". If the application does not check the error, it will continue to use this memory in subsequent execution, in accordance with the idea that the value is the available cursor assigned to it. The real 0 address memory area stores the most important "interrupt descriptor table" in the computer system and absolutely does not allow the application to use. In the operating system without protection mechanism under (such as DOS), write data to this address will lead to crash immediately, and in the robust operating system, such as Windows, this operation will be immediately captured the protection mechanism of the system, the result is forcibly closed by the operating system application error, in order to prevent the error expansion. At this point, the memory is not "read", and the referenced memory address is "0x00000000"". Memory allocation failure, many reasons, memory is insufficient, the version of the system function mismatch, and so may have an impact. Therefore, the distribution of failure in the operating system to use for a long time, the installation of a variety of applications (including accidentally "Install" virus program), after the change of system parameters and system of archives.In applications using dynamic allocation, sometimes there will be such a situation: the program attempts to write a "should be available" in memory, but I do not know why, the expected available cursor has expired. There may be "forget" to the operating system requirements distribution, or it may be the program itself at some point has canceled the memory, and "no attention" and so on. Off the system memory to be recycled, the access does not belong to the application, read and write operations can also trigger a mechanism to protect the system,trying to "end" illegal procedures only termination of the operation is to be performed, all resource recovery. The laws of the computer world are still much more effective and harsher than human beings! A situation like this belongs to the BUG of the program itself, and you can often reproduce errors in a particular order of operations. The invalid cursor is not always 0, so the memory address in the error is not necessarily 0x00000000, but other random numbers.First suggest:1, check whether there is a Trojan horse or virus in the system>2, update the operating system, let the operating system's installer re copy the correct version of the system files and correct the system parameters. Sometimes, the operating system itself will have BUG, pay attention to install the official release of the upgrade program.3, try to use the latest official version of the application, Beta version, trial version, there will be BUG.4, delete, and then recreate the files in theWinntSystem32WbemRepository folder: right click on my computer on the desktop, and then click management. Under services and applications, click service, and then close and stop the WindowsManagementInstrumentation service. Delete all files in the WinntSystem32WbemRepository folder. (create a backup copy of these files before deleting.) Open the service and application, click service, and then open and start the WindowsManagementInstrumentation service. When the servicerestarts, these files are recreated based on the information provided in the following registry key:HKEY_LOCAL_MACHINESOFTWAREMicrosoftWBEMCIMOMAutorecoverMOFsDada edited the post at 2008-03-28 13:40:30WohuifadaSend a noteGold coin: 110Experience value: 139Level: grade two in primary schoolCited report 2 floor reply: memory can not be read solution published at 10:55 2008-03-27I also have such a problem you ~ ~, but just bought the computer soon, out of warranty, as usual, we haven't tried the above method, so you can do it, hope ~ ~ thanksShrimp Yang GuoSend a noteGold coin: 250Experience value: 276Level: Grade Four in primary schoolCited report 3 floor reply: memory can not be read solution published at 13:29 2008-03-27I have a collection of absolute good, until now are not dealt with...Add requirements...Shrimp Yang GuoSend a noteGold coin: 250Experience value: 276Level: Grade Four in primary schoolCited report 4 floor reply: memory can not be read solution published at 13:30 2008-03-27Haha, look, have addedSijiali0Send a noteGold coin: 55Experience value: 60Level: KindergartenCited report 5 floor reply: memory can not be read solution published at 13:34 2008-03-27goodSijiali0Send a noteGold coin: 55Experience value: 60Level: KindergartenCited report 6 floor reply: memory can not be read solution published at 13:35 2008-03-27Earn pointsJia7856280Send a noteGold coin: 415Experience value: 338Level: grade five in primary schoolCited report 7 floor reply: memory can not be read solution published at 13:38 2008-03-27Very handsome!Jia7856280Send a noteGold coin: 415Experience value: 338Level: grade five in primary schoolCited report 8 floor reply: memory can not be read solution published at 13:38 2008-03-27very goodJia7856280Send a noteGold coin: 415Experience value: 338Level: grade five in primary schoolCited report 9 floor reply: memory can not be read solution published at 13:39 2008-03-27Very goodYigirlSend a noteGold coin: 165Experience value: 336Level: grade five in primary schoolCited report 10 floor reply: memory can not be read solution published at 14:05 2008-03-27Download and go home to see....Your name has been usedSend a noteGold coin: 75Experience value: 80Level: KindergartenCited report 11 floor reply: memory can not be read solution published at 14:21 2008-03-27Drunk and wine richSend a noteGold coin: 157Experience value: 283Level: Grade Four in primary schoolCited report 12 floor reply: memory can not be read solution published at 14:24 2008-03-27Ff44333Send a noteGold coin: 195Experience value: 273Level: Grade Four in primary schoolCited report 13 floor reply: memory can not be read solution published at 14:35 2008-03-27I don't seem to understandDong111222999Send a noteGold coin: 75Experience value: 100Level: PreschoolCited report 14 floor reply: memory can not be read solution published at 15:15 2008-03-27Ha-ha! It's worth seeingIt snows in the NorthSend a noteGold coin: 170Experience value: 477Level: grade five in primary schoolCited report 15 Floor reply: memory can not be read solution published at 15:28 2008-03-27You handsomeExpert moderatorSend a noteGold coin: 460Experience value: 1432Grade: junior grade oneCited report 16 floor reply: memory can not be read solution published at 16:05 2008-03-27Luanshi518123Send a noteGold coin: 200Experience value: 305Level: grade five in primary schoolCited report 17 floor reply: memory can not be read solution published at 16:45 2008-03-27The front is full of crap! No problem has been solved at the backIloveulovemeSend a noteGold coin: 170Experience value: 258Level: Grade Four in primary schoolCited report 18 floor reply: memory can not be read solution published at 17:16 2008-03-27Water does not understand, willing to learnFox confused 00Send a noteGold coin: 165Experience value: 391Level: grade five in primary schoolCited report 19 floor reply: memory can not be read solution published at 17:38 2008-03-27I often encounter this is something, but.MuguniangSend a noteGold coin: 95Experience value: 118Class: Grade 1Cited report 20 floor reply: memory can not be read solution published at 18:17 2008-03-27Quick answer, new topic, I want to ask for help, a total of 325 posts, <12345... 17> quick reply themeTitle:Content: automatic typesettingUpload pictures:[after completion, press Ctrl+Enter release]Latest discussion[this link] needs publicity[important] new sign in is not waterSimple quick solution. Unable to delete filesSerious violation of ID blacklist open! In March 6The computer starts the black frequency. What's the matter?Full speed: elaborate construction! Do for XPThe "start" and "run" magicalNine break Windows XP login password22 classic fun computer skillsDouble click the U disk, and the computer prompts the disk to be out of orderRelated EncyclopediaCategory: computer learning moreComputer knowledgeCheck the computerComputerWhat is wuauclt.exe?idiomHot recommendationAntivirus software, whole network, lowest priceWho is the task King waiting for you?Trojan horse can not kill, use stubborn Trojan to kill specially360 robot dog virus killed the latest download!360 intercepted pornographic door peeping back door360 remind Blizzard video users to upgrade soon!Teach you to use the 360 safe deposit box to protect the online accountDownload + popular science: what is an ARP attack?Detection and elimination of latent viruses in local area networksBeginners must read! IE common troubleshooting guideExcel's 10 tricks that are often overlookedTell me about any QQ games you've playedCopyright? 2008 All Rights Reserved 360 security center。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Dynamic Memory Allocation for Multiple-Query WorkloadsManish Mehta1David J.DeWittComputer Science DepartmentUniversity of Wisconsin-Madison{mmehta,dewitt}@AbstractThis paper studies the problem of memory allocation and scheduling in a multiple query workloadwith widely varying resource requirements.Several memory allocation and scheduling schemesare presented and their performance is compared using a detailed simulation study.The resultsdemonstrate the inadequacies of static schemes withfixed scheduling and memory allocationpolicies.A dynamic adaptive scheme which integrates scheduling and memory allocation isdeveloped and is shown to perform effectively under widely varying workloads.1.IntroductionAn important reason for the popularity of relational database systems is their ability to process ad-hoc queries posed by the users.Past research on query processing has dealt with issues of query optimization,scheduling,and resource allocation.Unfortunately,most of the work in this area has concentrated on processing single queries and does not consider multi-user issues.A particularly important issue that has largely been ignored is memory allocation for multiple-query workloads.In the past,the majority of the memory allocation policies proposed have concentrated on allocating the ’proper amount’of memory to a single operator or query and have ignored the presence of other concurrently executing queries.Such’localized’allocation techniques,which ignore global system behavior,can lead to poor performance and reduced throughput as the appropriate memory allocation for a query cannot be determined in isolation.Another drawback is that the memory allocation policy is largely independent of the query scheduling policy.To the best of our knowledge each of these schemes schedules queries in afirst-come,first-served manner, delaying the actual execution only until sufficient memory becomes available(e.g.DBMIN[Chou85]).As we will demonstrate,this decoupling of query scheduling from memory allocation can have disastrous effects on the overall performance of the system.The problem of processing multiple-query workloads becomes even more complex when the workload consists of different types of queries,each with widely varying memory requirements.As we will demonstrate,1This research was supported by the IBM Corporation through a Research Initiation Grant and through a dona-tion by NCR.An abridged version of this paper is to appear in the Proceedings of the19th VLDB Conference,Dublin,Ireland,1993.each type of query has a different sensitivity to how memory is allocated,and an effective memory allocation policy must carefully consider these differences if the overall performance of the system is to be maximized.In this paper,we study the relative performance of various query scheduling and memory allocation policies. We compare schemes that perform scheduling and memory allocation independently to a new dynamic algorithm that integrates the two decisions.The performance of all the policies is compared using a detailed simulation model.The rest of the paper is organized as follows.Section2discusses related work.The workloads studied in the paper are presented in Section3followed by a discussion of the metric used to compare the various policies in Section4.Sections5and6describe the various scheduling and memory allocation policies,respectively.Section7 presents the simulation model.The performance of the policies under various workloads is presented in Section8 which is followed by our conclusions and future work in Section9.2.Related WorkThe subject of memory allocation in database systems has been studied extensively.A significant portion of this work is related to allocating buffers to queries in order to minimize the number of disk accesses.The hot set model[Sacc86]defines the notion of a hot set for nested-loop join operations and tries to pre-allocate a join’s hot-set prior to its execution.The DBMIN algorithm[Chou85]extends the idea of a hot-set by estimating the buffer allocation perfile based on the expected pattern of usage.The DBMIN algorithm was further extended in Marginal Gains allocation[Ng91]and later it was employed to perform predictive load control based on disk utilization [Falo91].Each of these schemes,with the exception of[Falo91],ignore the effects of other concurrently executing queries and thus make localized decisions for each query.In addition,none of these algorithms handle the allocation of memory to hash joins.The only work,to our knowledge,that directly handles memory allocation among concurrently executing hash-join queries is[Corn89,Yu93].The authors introduce the concepts of memory consumption and return on consumption which are used to study the overall reduction in response times due to additional memory allocation.A heuristic algorithm based on these ideas is proposed for memory allocation.The algorithm’s performance is determined by three runtime parameters.The problem with the heuristic is that the performance of the algorithm is very sensitive to the value of these parameters and the authors do not discuss how to set their parameter values. Also,the performance is based on average response times which,as discussed in Section4,is not an appropriate metric for multiple class workloads.All these schemes use afirst-comefirst-served policy to service the arriving queries.As will be shown later, this can lead to bad performance for a multi-query workload.Query scheduling algorithms proposed in[Chen92a,Schn90]handle scheduling of only single complex join queries and do not consider multiple queries.The batch scheduling algorithms studied in[Meht93]cannot be directly applied as batch scheduling algorithms attempt only to maximize overall throughput and do not consider the impact on query response times.Adaptive hash join algorithms,which can adapt to changing memory requirements have been proposed by [Zell90].The implications of adapting to memory changes have not been investigated in the context of a multiple query workload.It is not very evident as to when taking memory from an executing query and giving it to some other query benefits the overall performance of the system.The same drawback lies in other schemes which dynamically change query plans at run-time[Grae89a].3.Workload DescriptionIn this study we consider only queries involving a single join and two selections.This simple workload allowed us to study the effects of memory allocation and load control without considering other complex query scheduling issues like pipelining and intra-query parallelism.For example,while there are several different execution strategies for complex queries such as left-deep,right-deep,and bushy scheduling[Schn90],nothing is known about their relative performance in a multiuser environment.Including queries with multiple joins would have made it impossible to separate the effects of memory allocation from other query scheduling issues.In addition most database systems(with the exception of Gamma[DeWi90]and Volcano[Grae89b]),execute multiple-query joins as a series of binary joins and do not pipeline tuples between adjacent joins in the query tree. Such simplified workloads have also been used previously in[Falo91,Ng91,Yu93].Another simplification in the workload is that the selections were executed by scanning the datafile and do not use indices.Also,the same join selectivity is used for each query—the number of output tuples produced by the join is one half of the number of the tuples in the outer relation.Inclusion of indices and varying join selectivity changes only the overall response time of the query and not the memory requirements of the queries.As a result, ignoring these simplifications does not affect the results qualitatively.All joins were executed using the hybrid-hash join algorithm2[DeWi84,Shap86].This algorithm operates in two phases.In thefirst phase,called the build phase,the inner relation is partitioned into n buckets I1,I1,...I n. The tuples that hash into bucket I1are kept in an in-memory hash table.Tuples that hash to one of the remaining buckets are written back to disk,with a separatefile being used for each bucket.The number of buckets,n,is2In the conclusions,we discuss the application of our techniques when other join algorithms are used.selected to be the minimum value such that each bucket I i willfit into the memory space allocated to it at run time.In the second phase,called the probe phase,the outer relation is also partitioned into n buckets O1,O1,...O n. Tuples that hash into bucket O1,are joined immediately with the tuples in I1.The other tuples are written to their corresponding bucketfile on disk.If n=1,the algorithm terminates.Otherwise,the algorithms proceeds to join I i and O i for i=2,...,n.As the tuples from bucket I i are read,an in-memory hash table is constructed.Then,O i is scanned and its tuples are used to probe the hash table constructed from I i looking for matching join attribute values. Results tuples are written back to disk.If the size of the inner relation is K pages,then the amount of memory available for the join must be at least√ K(also n is proportional to√ K).In a multiquery environment(composed of join queries from a number of different users or even perhaps join operations from a complex query composed of multiple joins),the memory requirements of each query can vary widely.To facilitate our study,we decided to classify each join as one of three different types:small,medium,or large.The idea is simple.Small queries are ones whose operands willfit in memory in most workloads.Medium queries are those which could always run in one pass(i.e.n=1)if they are alone in the rge queries are those whose execution always require multiple buckets.The workloads studied in this paper consist of mixes of queries from these three classes.As we will show later,in order to maximize the throughput of a system executing such a workload,it is necessary to carefully control the allocation of memory to queries from each of these different classes of queries.The following sections describe the classes in more detail.3.1.Small Query ClassThefirst query class represents join queries with minimal memory requirements.As such,this class of queries can always be expected to execute in one pass of the hybrid hash algorithm(i.e.no disk buckets are created during the build phase of the algorithm).For our experiments,we set the average memory requirement for this class to be5%of the size of main memory with the actual requirement varying from1to10%of the memory.3.2.Medium Query ClassThe second class represents join queries whose operands are about the same size as main memory.For our experiments we assumed that medium queries range from10%to95%of memory so an average of two such queries canfit into memory simultaneously.Thus,the memory requirements of this class of queries are nearly an order of magnitude larger than the small class.However,since the memory requirements of these queries are substantial compared to the total amount of main memory available,in the presence of other concurrently executing queries,medium queries will frequently require multiple join passes(depending on the actual scheduling and memory allocation policy employed).rge Query ClassThe last class represents queries whose operands are larger than the amount of physical memory available and thus always require multiple buckets for their execution.The large query sizes varied from the size of the memory upto four times the memory size.4.Performance Objective and MetricThis section describes the performance metric used to compare the various memory allocation and scheduling policies examined in this paper.The metric is presented here in order to simplify the presentation of the algorithms described in the following section.We spent a significant amount of time and effort trying tofind a reasonable goal for a multi-class workload. The performance goals that are typically used for single class workloads are not adequate as they are biased towards one class or another.For example,combining the different query types into a single class and maximizing overall throughput biases the metric towards the smaller queries which have a higher throughput;algorithms that maximize the throughput of the smaller queries at the expense of the other classes will fare better.Similarly,minimizing the average response time is inadequate as the value of the metric is determined mainly by the large queries with long execution time and hence high response times.In the absence of any universally accepted relative importance of the three workload classes(such as might be defined by an organization like the TPC council),we wanted a performance goal that weights the relative priority of the different classes equally.The performance goal chosen for this study is fairness.Thefirst step in measuring fairness is to obtain,for each class,the ratio of the observed average response time to average response time of the class when instances of the class are executed alone in the system.This normalizes the effect on the metric of the actual values of the response times of the different query types,which may differ by orders of magnitude.3Fairness is then defined as the standard deviation in the ratios obtained for each of the three classes in thefirst step.A higher standard deviation means a larger difference in the response time changes.This implies that the performance of some class was disproportionately worse when compared to other classes in the system and that the system was unfair towards that class.In addition,we also measured the mean percentage change in response time across all three classes;a lower mean implies that,overall,the classes had better performance and that their observed response times were closer to3Normalization can also be done using expected response times(as in[Ferg93])or the optimizer estimate of the query response time.Since we did not want to invent arbitrary expected response times for the queries we did not choose thefirst ap-proach and the absence of a real optimizer prevented us from using the second.their stand-alone response times.Whenever necessary,the response times for each individual class are shown along with the Fairness metric.5.Memory Allocation PoliciesWe begin this section by describing three different ways of allocating memory to a hash join operation: minimum,maximum,and available.Next,we discuss how these alternatives can be applied to each of the three query classes:small,medium,and large.The resulting combinations provide a wide range of alternatives for controlling the allocation of memory to queries in a multiuser environment.5.1.Join Memory AllocationThe amount of memory allocated to a hybrid hash join can range from the square root of the size of the inner relation to the actual size of the relation[DeWi84].In a multi-query environment,allocating more memory to a join reduces not only the execution time of the operation but also disk and CPU contention as the query performs fewer I/O operations.The drawback of allocating more memory is that it may cause other queries to wait longer for memory to become available.Allocating less memory has the opposite effect.It increases execution time and disk contention but it may reduce the waiting time of other queries.Also,the overall multi-programming level in the system may be higher as the memory requirement of each individual query is reduced and more of them can be executed in parallel.We studied the effect of three allocation schemes on query performance.MinimumIn this scheme,the join is always allocated the minimum memory required to process the join(i.e.the square root of the size of the inner relation).Hence a partitioning phase and a joining phase are always required.In effect,except for buckets I1and O1,both relations get read twice and written once.This scheme is the least memory intensive but causes the most disk/CPU contention.MaximumIn the maximum scheme(which only works for small and medium queries),each join is allocated enough memory so that its inner relation(i.e.the temporary relation resulting from the selection)willfit in memory.No tuples from the inner or outer relations get written back to bucketfiles on disk and the join is processed by reading each relation once.This allocation scheme minimizes the response time of the query but is also the most memory intensive.Also,since enough memory may not be available when the query enters the system, it may have to wait longer to begin rge queries cannot use this scheme as the size of their inner relations is much greater than the amount of main memory available.AvailableThe previous two schemes ignore how much memory is actually available at run-time.The Available scheme determines a query’s allocation at run-time by examining available memory when the query is ready for execution.The query is given whatever memory is available subject to the constraint that the amount of memory allocated is at least the minimum required by the query(i.e.the square root of the size of the inner relation)and no more than the maximum.An allocation between two these extremes is interesting because it increases the number of tuples in bucket I1and O1and hence reduces the number of tuples that have to be read twice from disk(and written back once).5.2.Impact of Memory Allocation on Each ClassCombining these schemes in all possible ways for each of the three query classes gives us18possible allocation schemes(3small schemes*3medium schemes*2large schemes).As studying all possible combinations was not feasible,the number of combinations was reduced by removing some schemes for the small and large queries that are either redundant or that we expected to perform badly.Queries in the small class require small amounts of memory to execute.From some preliminary experiments, we observed that in most cases the queries always got the maximum memory required.Also,as the memory needed by these queries is quite small(on the average1/20th the size of physical memory),the queries did not wait long for memory to become available.As a result,the Maximum allocation scheme was always superior to the other schemes for this class of queries.Hence,we elected to only use this scheme for small queries.Similarly,using Available for queries in the large class is a very bad idea as these queries can consume all of the memory,blocking out all other queries.Thus,only Minimum was used for these queries.6.Scheduling PoliciesThe response time of a single query is determined not only by the execution time of the query but also by how queries are scheduled for execution.The scheduling decision gains added significance if the response times of the queries vary significantly.We considered three schedule policies,FCFS,Responsible,and Adaptive,which are described below.6.1.FCFSThis simple scheduling policy is illustrated in Figure1.Queries from all classes are directly sent to the memory queue as they arrive into the system.The memory queue is served infirst-comefirst-served(FCFS)order and queries execute whenever sufficient memory is available.We present results for this scheduling policy incombination with all three medium-query memory allocation schemes -Maximum ,Available and Minimum .The FCFS-Maximum combination can be particularly bad for small queries as they may need to wait behind large queries with much higher response times.The medium queries also suffer as the policy tends to restrict the multi-programming level (MPL)of medium queries.On the other hand,the FCFS-Minimum combination may cause very high system contention as a lot of queries can fit into the system if minimum memory is allocated to each.Moreover,all three schemes are inherently biased towards larger queries.The larger queries take up more memory and block out the smaller queries.In addition,the larger queries take longer to execute and thus are present in the system longer.This means that the average MPL of the larger queries could become disproportionately higher compared to the smaller queries as time progresses and larger queries tend to consume an increasing fraction of the system resources.6.2.ResponsibleWe term the second scheduling policy Responsible as it is biased in favor of the smaller queries.As shown in Figure 2,small queries are sent directly to the Memory queue as in the FCFS scheduling policy.Medium and large queries on the other hand are queued in separate queues to prevent them from blocking small queries.These scheduler calculates the average amount of memory consumed by the small queries and leave that amount of memory for use by the small queries.The leftover memory is divided among the medium and large queries according to their memory allocation policy (e.g.minimum for the large queries and available for the medium queries).In order to prevent starvation,each class has a minimum MPL of one.The amount of memory being used by small queries is calculated by multiplying the average MPL of the small queries by their average memory requirement.Responsible is thus biased towards the small queries as the small queries are sent directly to the memory queue while the medium and large queries wait in separate queues for execution.LARGE MEMORY QUEUE SMALLLARGEMEMORY QUEUEFigure 1.-FCFS Scheduling Figure 2.-Responsible Scheduling6.2.1.AdaptiveFCFS scheduling lets the scheduling decision be determined by memory availability and is biased towards larger queries.Responsible is biased in favor of small queries.As we will demonstrate later,both schemes can exhibit very poor performance.The Adaptive scheduling scheme,on the other hand,tries to allocate resources such that the overall goal of fairness is achieved to the maximum extent possible.The basic mechanism used by Adaptive is the control of the MPL of each class of queries.For each class,an MPL queue is maintained in which incoming queries wait if the current MPL of the class is above a dynamically determined level(this level will fluctuate over time under the control of the Fairness Metric).Each MPL queue is serviced independently in FIFO order.When a query belonging to a particular class completes,the next waiting query in the queue is moved from the class’s MPL queue to the memory queue.Figure3illustrates the various queues managed by the Adaptive scheduling algorithm.As mentioned before,small queries always execute at maximum memory and large queries always execute at their ing these two properties,the algorithm calculates the average amount of memory consumed by queries from both classes.The remainder is then distributed among the medium queries.As an example,assume that there is32MB of memory available,that maximum MPL of the small class is10and that the small queries consume,on the average,0.5MB of memory.Similarly,assume that the large query MPL is2and that they require 3MB on the average.Thus,the memory available to the medium queries is21MB(32-10*0.5-2*3).If the current maximum medium MPL is5,then each medium query receives4.2MB of memory.Dividing the memory in this manner ensures that the smaller queries are not blocked out by the medium and large queries.Also,note that the memory allocated to a query is related directly to the MPL of its class.The adaptive algorithm thus integrates query scheduling and memory allocation.MEMORY QUEUEMPLQUEUESSMALL MEDIUM LARGEFigure3-Adaptive SchedulingThe adaptiveness of the algorithm arises from the fact that the MPLs of the query classes are determined dynamically based on system parameters.Periodically,the algorithm checks the average response times for each of the query classes and evaluates the Fairness Metric(Section4).If the variance is high,implying that some class is doing much better than the other two,the algorithm takes a compensating action so that the offending class is throttled back.The decision may mean increasing the MPL of the class that is doing worst so that it receives more resources or decreasing the MPL of the offending class to reduce its resource consumption.The actual algorithm is presented in more detail in Figure4.We followed a few general principles in deciding the action to be taken in response to the state the system is in.The increase and decrease of MPLs was done under the constraints that the MPL for a class can never be zero and that the corresponding memory associated with the class cannot exceed the total memory size.Also,when the algorithm must decide what class should have its maximum MPL adjusted,the algorithm always tries to change the if(Activate){calculate the average response times for each classcalculate Fairness Metric(Dev)and mean Response Time change(MRT)calculate difference of percentage change from the meanSP=difference in percentage change for small classMP=difference in percentage change for medium classLP=difference in percentage change for large classif(Dev>DevThreshold){sort SP,MP and LP(a higher value means the correspondingclass has poorer performance)switch{SP>MP>LP—>increase small MPL||decrease large MPL||decrease medium MPLMP>SP>LP—>increase medium MPL||decrease large MPL||decrease small MPLLP>SP>MP—>decrease medium MPL||increase large MPL||decrease small MPLLP>MP>SP—>decrease small MPL||increase large MPL||decrease medium MPLSP>LP>MP—>increase small MPL||decrease medium MPL||decrease large MPLMP>LP>SP—>decrease small MPL||increase medium MPL||decrease large MPL}}}Figure4:Pseudo Code of the Adaptive AlgorithmMPL of the smaller query classfirst.This is because the smaller queries have shorter response times and changing their MPL makes the system respond to the change faster.As can be seen in Figure4,there are two parameters that control how often the adaptive algorithm adjusts the query workload.The algorithm is invoked every time the variable,Activate,is set to TRUE.If invoked too frequently,the algorithm is susceptible to transients in the workload;on the other hand infrequent activation makes the algorithm slow to respond to workload changes.For the purposes of this paper,Activate was set to TRUE at the completion of each medium query.The second parameter,DevThreshold,controls how much of a deviation the algorithm tolerates before making a compensating action.A low threshold means that the system will respond to even very low changes in the deviation and thus may react too quickly to a transient change.A very high threshold means that the algorithm does not change the runtime parameters even if the deviation is very high and some class is performing relatively worse. The threshold value was set to0.75for the purposes of the performance study.A sensitivity analysis of the algorithm towards these two parameters can be found in Section8.5.During execution,the adaptive algorithm needs to compute the average observed response times for each of the three query classes in order to calculate the percentage change from the ideal case.This requires that the algorithm be provided with the response time of a representative query from each class,run with the MPL set to1. Also,if the activation frequency of the algorithm is such that an activation can occur before a single query of some class has completed execution,the algorithm needs a way of calculating the expected response time of the class. The solution used in this study is to require as input two numbers for each class when the queries are run in a multi-user mode:Response Time and the observed Disk Read Response Time.If the system is I/O bound,the response time is in most cases proportional to the disk response time so that we can compare the current Disk Read Response Time to the above number and estimate the expected response time accordingly.This technique could be replaced by another estimation technique without changing the algorithm.Even if the estimate is quite inaccurate,the penalty is not severe as the estimate is no longer needed once a single query from the class has completed.7.Simulation ModelThe simulator used for this work was derived from a simulation model of the Gamma parallel database machine which had been validated against the actual Gamma implementation.The simulator is written in the CSIM/C++process-oriented simulation language[Schw90].The simulator models a centralized database system as shown in Figure5.The system consists of a single processing node,composed of one CPU,memory,one or more disk drives,and a set of external terminals from。
