22-09-0140-03-0000-meeting-minutes-of-the-security-and-management-plane-procedures-ad-hocs
MeetingMinutes概要

Three sections
Opening statement----the background Points in discussion Conclusions----resolutions or
recommendations or decisions reached
Sample
Labor Grievances Committee of the Slate and Johnson Luggage Company
meeting 3) Time, date and place of the meeting 4) The name of the presiding officer and minutes
recorder 5) List of people attending 6) List of absent member of the group
It may record review of the past activities, new decisions and polices, and provide the decisionmaking process.
key information
1) Where and when the meeting took place 2) Who was there and who was not 3) What has been decided for the group 4) Who has agreed to do that
It was agreed that the next meeting would be held on October 22, at 4 p.m. in employees’ cafeteria.
Minutes of Meeting.ppt
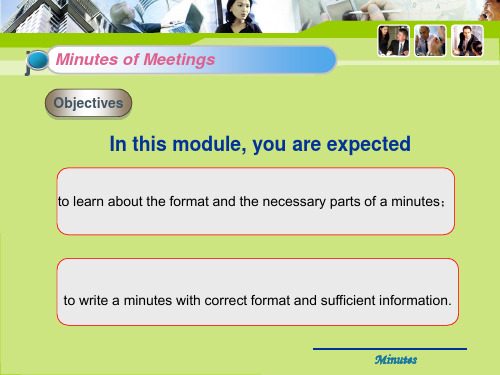
Objectives
In this module, you are expected
to learn about the format and the necessary parts of a minutes;
to write a minutes with correct format and sufficient information. Minutes
1) Do you think it is an effective meeting? Why? Yes it is an effective meeting. Chair of the meeting controlled the meeting very well and everyone attended the meeting stated out their opinions clearly at the meeting.
Minutes
2 Communicative Activity
3) What should we take down in a meeting minutes? Although there are different styles of minutes, they have the key information in common. All should cover four basic things: (1) where and when the meeting took place; (2) who was there and who was not; (3) what has been decided for the group; (4) who has agreed to be this or that. Therefore, most minutes can be divided into four parts: heading, body, adjournment time, and signature of the minute’s recorder.
Minutes of Meeting

Minutes
Sample Analysis
Body
4. Mr. Chen’s opinion: He agreed with the new working system but disagreed with Ms. Li’s new proposal on “core times”. 5. Mr. Zhao’s opinion: Because of the time difference, it’s very hard for Mr. Zhao’s department to carry out flextime system. Adjournment The meeting adjourned at 9:45 a.m. Qiu Xiaoyun Business Assistant
Signature
Minutes
Summary
The definition of meeting minutes Minutes of meetings keep permanent and formal records of discussions and decisions at meetings. Minute is the written record of a meeting and serves to provide an accurate record of what has been said, discussed and legible to someone who was not present at the meeting. It is an accurate and concise summary of all decision and main points for future reference.
minutes--of--meeting(会议纪要)

EXAMPLE
Main Body
• Agenda Discussed • Decisions Reached
CREATE AN OUTLINE ACCORDING TO THE
AGENDA OF THE MEETING FIRST
Approval of minutes: Motion: Approve minutes from 14 January 2013 board meeting Vote: Motion carried Resolved: Minutes from the meeting on 14 January 2013 approved without modification
contents
INTRODUCTION EXAMPLE TIPS QUESTIONS
INTRODUCTION
HOW
WHY
WHO
WHAT
WHY WE NEED MEETING MINTUES?
•to create a record of what took place in the meeting •to remind those at the meeting of the actions they need to take after the meeting.
Meeting called to order at 12:00 p.m. on 13 February 2013 at Room 1211 by CEO Taylor Cooper
Members present: Taylor Cooper, CEO Logan Shafter, CFO Morgan Ely, Senior Vice President, Marketing Elyse Chan, Senior Vice President, Engineering Joyce Comer, Senior Vice President, Consulting Lindsay Rogan, Communication Strategist
商务英语写作 第15次课

Practical Writing
撰写电邮替香港Hamilton Hotel 的Room Service Supervisor撰写致Mr. Lee的电邮: 1)感谢Mr. Lee近期在香港旅游时选择该酒店, 希望 对服务满意。 2)发现一件Giorgio Armani 衬衫和一瓶Cologne香 水遗落, 现在放在失物招领处, 问是否要寄回(有 mailing charge)。 3)希望尽快回电答复, 期望能再次光临Hamilton Hotel。
Sample e-mails
Dear Mr. Solomon: Thank you very much for sending us your AST application. Enclosed is your hotel confirmation slip along with directions on how to get to the hotel. Due to a computer error, however, you might receive the confirmation slip twice. If this happens, would you please let us know? We are sorry to trouble you and look forward to seeing you in Shanghai. Sincerely yours, Elements
Time—the beginning and ending time and date of the meeting; Chairperson—the name of the person or the group holding the meeting; Participants—the people who attend the meeting; Content—problems for discussion, opinions of the speakers, decisions in the meeting, etc; Minute Keeper—the person who makes the minute.
22-10-0114-00-0000-802-22-motions-at-the-july-plenary-executive-committee-meeting

statement "IEEE standards may include the known use of patent(s), including patent applications, provided the IEEE receives assurance from the patent holder or applicant with respect to patents essential for compliance with both mandatory and optional portions of the standard." Early disclosure to the Working Group of patent information that might be relevant to the standard is essential to reduce the possibility for delays in the development process and increase the likelihood that the draft publication will be approved for publication. Please notify the Chair Apurva N. Mody < apurva.mody@ > as early as possible, in written or electronic form, if patented technology (or technology under patent application) might be incorporated into a draft standard being developed within the IEEE 802.22 Working Group. If you have questions, contact the IEEE Patent Committee Administrator at patcom@. >
商务英语之(8. MEETINGS)会议-1229

c. 促请再考虑 Could you reconsider that? (请你再考虑一下好吗?) Could you think over that matter one more time. (你能再好好的考虑这件事情吗?) d. 说明反对的依据 I don’t agree this will not be of benefit to us. (我不同意,这对我们都没有好处.) That’s just not feasible. / not really practical. (那是行不通的/ 不切实际的.) I have to oppose the plan because of the shortage of manpower. (我必须反对因为人手不足.) e. 拒绝 I’m afraid that I can’t accept your proposal. (我恐怕无法接受你的提议.) We’re sorry, but we can not meet your requirement. (非常抱歉, 我们无法照办.)
7
步骤三、询问及确认 a. 开口询问 I’d like to ask you a question. (我想问你一个问题.) I have a question to put to you. (我想个问题想问你. ) b. 再确认一次议题 I’d like to confirm the purpose of this meeting. (我想再确认一下这次会议的目的.) Let me confirm whether or not the news is true. (让我再确认一下这个消息是真还是假.) I’d like to briefly go over the situation. (我想再确认一下大致情况. ) c. 确认发言的内容 I beg your pardon? (请你再说一遍好吗?) I don’t understand what you’re saying. (我不明白你说什么? )
meeting minutes

The Body 正文
As the first purpose of a minutes is to set out the conclusions reached so that those who have to take action will know precisely what they have to do; the second is to give the reasons why the conclusions were reached. The body part falls clearly into three sections:
(1) The minutes begin by recording certain document under discussion, giving the name and date of each. It goes like these:
“The president noted a letter dated … from… stating that…” “The president noted the following information concerning…”
缺席人员
会议记录的内容
主持人 记录人 休会时间
Layout
会议讨论的问题
Title Presiding Present Absent Items of Discussion And Business
Adjournment Recorder
Notes for the various Sections
Notes and explanation
1) 2) 3) 4)
Although there are different styles of minutes, they have the key information in common. All should cover four basic things: What When & where Where and when the meeting took place Who Who was there and who was not What (textbook) What has been decided for the group Who has agreed to do that
Unit10 Minutes of Meetings

Keep main points: The ones that will be written down are
Remain the same from the beginning to the end:
How many types of meeting minutes and what are they?
(3) The dean said, “School dental programs will teach children proper dental care.” (announce) The dean announced that school dental programs would teach children proper dental care.
The format of minutes of a meeting
The format of minutes of a meeting is uncomplicated and usually includes four parts:
The heading of the meeting The basic situation of the meeting
3.New business (A) A survey will be completed to collect data on spending habits in these areas. (B) The results of this survey will be delivered to the sales teams. (C) Considering specific data mining procedures to help deepen understanding.
Minutes of the meeting 会议摘要

Minutes of the meeting on Tuesday, 6th of December 2011 Present: Luo Baoshan (The chair person)Mo Minyi&Lin Shanshan (The H&R Manager)Guo Ziyi&Zhang Huiqin (The Finance Director)Xu Xinrun&Zheng Danna (The Trade Union Representative)Li Chujun& Rao Yijuan (The Production Manager)The chairperson opened the meeting with the follow point:● A short introduction about the proposed alliance●Explain the 35-hour week situation●Ask for advices about the situationThe H&R manager’s opinion can be listed as follow:●Disagree with the 35-hour week●Believe the company will not survive without alliance●Suggestion of training seminars●Open to other suggestions and want a compromiseThe Finance Director’s opinion can be listed as follow:●Agree with the 35-hour week●35-hour week save money; alliance will bring a new customer base and improvefinancial healthy●Suggest to think about long term profit, concerned more about the company andtry to see the advantage of this situation●Only agree with a compromiseThe Trade Union Representative’s opinion can be listed as follow:●Disagree with the 35-hour week●Salaries are low and loss of overtime is a problem●Reluctantly accept performance related bonuses and other perks●Won’t accept 35-hour week unless obtain some of the compromisesThe Production Manager’s opinion can be listed as follow:●Disagree with the 35-hour week●Worry about meeting production deadlines and the morale of the workers●Reluctantly accept the present worker earn overtime on training the new parttimers●Support any reasonable suggestionAfter a long discussion, it turned out without any solution towards this situation, so we decide to hold another meeting.Date of next meeting ----- 16th December 2011。
有关开会时间与自己约定时间不符的英语作文

Meeting Time Mismatch: A Dilemma inProfessional CoordinationIn the fast-paced world of professional life, scheduling meetings can often be a challenging task. Imagine being in a situation where the proposed meeting time does not align with your pre-arranged plans. Such scenarios are not uncommon and can lead to a significant dilemma, especially when the stakes are high and the consequences of a missed meeting are severe.Recently, I faced such a predicament. I had scheduled a personal appointment with a friend, a long-awaited catch-up that we had been looking forward to for weeks. The plans were finalized, and the date and time were set in stone. Little did I know that a crucial work meeting would be scheduled for the exact same time.The situation left me in a predicament. On one hand, the work meeting was important, involving a key projectthat I was leading. Missing it could have serious implications on the progress of the project and my professional reputation. On the other hand, the personal appointment was equally significant. It was a chance toreconnect with a friend, share updates, and catch up onlost time.As I weighed the pros and cons of each option, I realized that a decision had to be made. I knew that I couldn't be in two places at once, and the clock was ticking. I quickly began exploring possible solutions, considering all angles.I first attempted to reschedule the work meeting. I approached my colleagues and explained the situation, hoping for some flexibility. Unfortunately, the meeting was already part of a larger schedule, and rescheduling was not an option. I then turned to my personal appointment, gently suggesting to my friend if we could push the meeting to a later date. Thankfully, my friend understood my predicament and was willing to accommodate.While the solution was not ideal, it was the best I could manage given the circumstances. It taught me a valuable lesson about the importance of planning and communication in professional life.In conclusion, when faced with a meeting time mismatch, it is crucial to act promptly and communicate effectively.Weighing the importance of each commitment and exploring all possible solutions is key. While it may not always be possible to avoid such dilemmas, being prepared and proactive can help minimize their impact on our professional and personal lives.**会议时间不符:专业协调的两难境地**在快节奏的职业生活中,安排会议往往是一项具有挑战性的任务。
会议时间管理英语作文

会议时间管理英语作文英文回答:Time Management in Meetings.Effective time management is crucial for successful meetings. By adhering to certain strategies, participants can maximize productivity and achieve desired outcomes.1. Establish a Clear Agenda:Before the meeting, create a detailed agenda outlining the topics to be discussed and the allotted time for each. This provides a roadmap for the meeting and keeps it on track.2. Start and End on Time:Respecting the scheduled start and end times is essential. Punctuality ensures that everyone's time isvalued and allows for efficient use of the meeting space.3. Delegate Responsibilities:Assign specific roles to participants, such as note-taking, timekeeping, or leading discussions. This distributes the workload and promotes accountability.4. Encourage Active Participation:Engage attendees by soliciting input, asking questions, and fostering a collaborative environment. Active participation ensures that all voices are heard and the meeting progresses smoothly.5. Minimize Distractions:Create a distraction-free zone by eliminating unnecessary interruptions, such as phone calls or email notifications. Encourage attendees to focus on the meeting objectives.6. Use Technology Wisely:Utilize technology to enhance productivity, such as video conferencing for remote participants or digital tools for note-taking and collaboration. However, avoid relying solely on technology and ensure it complements themeeting's purpose.7. Allow for Flexibility:While adhering to the agenda is important, be prepared to adjust the schedule as needed to accommodate unforeseen circumstances or productive discussions. Flexibility allows for unexpected opportunities and ensures the meeting remains effective.8. Summarize and Follow Up:At the conclusion of the meeting, summarize key decisions and assign action items. Distribute meeting minutes promptly to provide attendees with a record of the discussion. Follow up regularly to ensure progress onagreed-upon tasks.中文回答:会议时间管理。
会议记录怎么写minutes

Agenda
Name & topic of the meeting Time, date and place of meeting Chair/Host/Owner of the meeting List of people attending List of absent members of the group Record of the principle points discussed and decisions taken • Task list • Whom will perform the tasks • deadlines • • • • • •
Agenda
• Time, date and place of next meeting • Name of person taking the minutes
Assignment
• • • • • • • • title of minutes venue date time present chairperson apologies for absence notes on the meeting
• • •
· Finance Committee report provided by Chair, Elizabeth Drucker: - Drucker explained that consultant, Susan Johns, reviewed the organization's bookkeeping procedures and found them to be satisfactory, in preparation for the upcoming yearly financial audit. Funds recommends that our company ensure the auditor provides a management letter along with the audit financial report. · - Drucker reviewed highlights, trends and issues from the balance sheet, income statement and cash flow statement. Issues include that high accounts receivables require Finance Committee attention to policies and procedures to ensure our organization receives more payments on time. After brief discussion of the issues and suggestions about how to ensure receiving payments on time, MOTION to accept financial statements; seconded and passed. · Board Development Committee's report provided by Chair, Douglas Carver: - Carver reminded the Board of the scheduled retreat coming up in three months, and provided a drafted retreat schedule for board review. MOTION to accept the retreat agenda; seconded and passed. - Carver presented members with a draft of the reworded By-laws paragraph that would allow members to conduct actions over electronic mail. Carver suggested review and a resolution to change the By-laws accordingly. Kyumoto suggested that Swanson first seek legal counsel to verify if the proposed change is consistent with state statute. Swanson agreed to accept this action and notify members of the outcome in the next Board meeting.
【免费下载】大学商务英语会议纪要

Meeting Minutes一.Brief Introduction:Minutes are written as an accurate record of a group's meetings, and a record decision taken. They are useful because people can forget what was decided at a meeting if there is no written record of the proceedings. Minutes can also inform people who were not at the meeting about what took place.Before each meeting an agenda should be drawn up, detailing the matters to be discussed at the meeting. A set of minutes should normally include the following information:·Name and topic of the meeting·Time, date and place of meeting;·Chair/Host/Owner of the meeting·List of people attending;·List of absent members of the group;·For each item in the agenda, a record of the principal points discussed and decisions taken;·Task List·Whom will perform the tasks·Deadlines·Time, date and place of next meeting·Name of person taking the minutes / Minutes Taker·Topic for Discussion·Voting Results·Resolutions二.8 Tips for meeting minutes writing会议纪要的8建议1. 根据会议议程表制定会议纪要大纲,并根据议题的讨论顺序做记录。
Minutes of Meetings2

会议记录
Sample 1
UNIVERSITY OF WALES, CARDIFF DEPARTMENT FOR CONTINUING EDUCATION ___________________________________________________ Minutes of Staff Meeting held on Friday, 11 February 1999
4. ANY OTHER BUSINESS 1) Library Funds £40,000 is available to spend on books this year. Staff members were recommended to submit as many orders as possible. 2) Staff Changes Susan Walker has resigned her post and will be leaving the department at the end of February. A post to replace Susan has been advertised internally throughout the College. 5. NEXT MEETING Staff will be notified in due course of the date of the next staff meeting, if it should be changed from the schedule date, March 25th.
Present: Mr. J. W. Perkins (Director), Dr. G. Awbery, Mrs. S. Chadha Mrs. H. Eckart, Mr. D. Evans, Dr. M. S. C. Havard Apologies for absence were received from: Ms. G. Boden, Mr. M. J. Chiles, Ms. S. Ediwards, Ms. R. Elt. 1. MINUTES OF MEETING HELD ON 21 JANUARY 1999 The minutes of meeting held on 21 January 1999 were agreed and signed, subject to the following amendments: 2.5 Programme Planning 1998-99 Para.2, Line 3, should read: Nominations for the team were Terry Evans and Peter Webster. 6. Amend heading to read: Progress with contacts in other departments and Parttime Degrees.
会议流程英语

I —IntroductionsOpening the MeetingWelcoming and Introducing ParticipantsStating the Principal Objectives of a MeetingGiving Apologies for Someone Who is AbsentII - Reviewing Past BusinessReading the Minutes (notes)of the Last MeetingDealing with Recent DevelopmentsIII —Beginning the MeetingIntroducing the AgendaAllocating Roles (secretary,participants)Agreeing on the Ground Rules for the Meeting (contributions, timing,decision-making,etc。
)IV - Discussing ItemsIntroducing the First Item on the AgendaClosing an ItemNext ItemGiving Control to the Next ParticipantV - Finishing the MeetingSummarizingFinishing UpSuggesting and Agreeing on Time,Date and Place for the Next MeetingThanking Participants for AttendingClosing the MeetingThe following pages focus on each part of the meeting and the appropriate language fo r each situation.用英语主持会议(2):主持会议Opening 宣布会议开始Good morning/afternoon, everyone.If we are all here,let’s get started / start the meeting / start。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
IEEE P802.22Wireless RANsAbstractThis document provides the minutes of the Security Ad-Hoc conference calls held on, Year 2009– August 3rd, August 10th, August 17th, August 24th 20091. August 3rd 2009 – Security Ad-Hoc Conference Call Meeting Minutes Meeting Minutes1. AttendanceApurva Mody – BAE SystemsGerald Chouinard - CRCRanga Reddy – US ArmyWinston Caldwell – Fox2.1 Agenda∙Attendance∙Chair asked if everyone attending was familiar with the IEEE patent policy -/board/pat/pat-slideset.pdf - Everyone was familiar.∙Minutes of all the Security Ad-Hoc Conference Calls previously held can be found at –https:///802.22/dcn/08/22-08-0163-22-0000-meeting-minutes-of-the-security-ad-hoc-group-in-802-22.doc∙Discussion on Protection Mechanisms for Co-existence Beaconing Packets – led by Ranga Reddy. https:///802.22/dcn/08/22-08-0296-03-0000-cbp-security-protection-mechanisms.doc∙Recommended Text for Section 7 on Security in 802.22 – included in Draft v 2.0 can be found at https:///802.22/dcn/08/22-08-0174-18-0000-recommended-text-for-section-7-on-security-in-802-22.doc∙Reference Document - Table of Contents for Section 7. The reference document for the proposed text can be found athttps:///802.22/file/08/22-08-0165-00-0000-table-of-content-for-the-security-section-in-802-22.doc∙Reference Document - Scope and the Workplan for the Security Ad-Hoc Group –https:///802.22/file/08/22-08-0159-00-0000-scope-agenda-workplan-and-timeline-for-the-security-ad-hoc-in-802-22.doc∙Reference Document - Presentation on the PRM and Security Enhancements in 802.22 – 802.22 Threat Analysishttps:///802.22/dcn/08/22-08-0083-08-0000-security-and-prm-enhancements-in-80222-v3.ppt∙Proposed Reference Architecture for 802.22 - https:///802.22/dcn/08/22-08-0121-10-0000-text-on-protocol-reference-model-enhancements-in-802-22.doc∙802.22 Database Interface Architecture and Security Mechanisms -https:///802.22/dcn/09/22-09-0111-02-0000-database-interface-architecture-and-security-mechanisms.ppt∙Whitespace Database Service - https:///802.19/dcn/09/19-09-0047-00-tvws-white-spaces-database.pptMinutes and Discussions∙Comments 667, 668, 673, 674, 675, 676, 679 and 680 were resolved. The proposed resolutions can be found in the Document https:///802.22/dcn/09/22-09-0120-03-0000-wran-draft-2-0-ballot-comment-database.xls∙Comment #662 – Gerald Chouinard. Th ere were some discussions on this comment. Gerald’ s comment is to keep the complexity of the security suites in 802.22 low so that there is not a high barrier to the market∙Ranga Reddy suggested that when the security ad-hoc started exploring the architecture for the security in 802.22, we found the 802.16 model most appropriate. Many things from the 802.16 security architecture have been streamlined. There is also an option, that if a user does not have a capability to perform security related functions such as encryption / authentication, it may tell the BS and the BS may either choose to serve the user with no security features or it may decide to de-authorize the user from the network.∙Apurva Mody suggested that the security ad-hoc will consider providing some 802.11 type of mechanisms so that it may facilitate quicker adoption of the standard.∙Ranga Reddy suggested that security ad-hoc is already considering adding Extensivle Authentication Protocol (EAP) which will allow the service providers to automatically generate the certificates and keys.∙Ranga Reddy suggested that we wait until all the comments are resolved and then re-visti this comment to see if something can be done to reduce the complexity.∙Winston – We need to keep in mind the market where 802.22 is likely to be deployed more – not Africa but the US∙Apurva Mody suggested that looking at the trends in 802.16 / WiMAX, it looked like 802.22 may be adopted more quickly in other countries with lesser broadband penetration as compared to the US.2. August 10th 2009 – Security Ad-Hoc Conference Call Meeting Minutes Meeting Minutes1. AttendanceApurva Mody – BAE SystemsGerald Chouinard - CRCRanga Reddy – US ArmyWinston Caldwell – Fox2.1 Agenda∙Attendance∙Chair asked if everyone attending was familiar with the IEEE patent policy -/board/pat/pat-slideset.pdf - Everyone was familiar.∙Minutes of all the Security Ad-Hoc Conference Calls previously held can be found at –https:///802.22/dcn/08/22-08-0163-22-0000-meeting-minutes-of-the-security-ad-hoc-group-in-802-22.doc∙Discussion on Protection Mechanisms for Co-existence Beaconing Packets – led by Ranga Reddy. https:///802.22/dcn/08/22-08-0296-03-0000-cbp-security-protection-mechanisms.doc∙Recommended Text for Section 7 on Security in 802.22 – included in Draft v 2.0 can be found at https:///802.22/dcn/08/22-08-0174-18-0000-recommended-text-for-section-7-on-security-in-802-22.doc∙Reference Document - Table of Contents for Section 7. The reference document for the proposed text can be found athttps:///802.22/file/08/22-08-0165-00-0000-table-of-content-for-the-security-section-in-802-22.doc∙Reference Document - Scope and the Workplan for the Security Ad-Hoc Group –https:///802.22/file/08/22-08-0159-00-0000-scope-agenda-workplan-and-timeline-for-the-security-ad-hoc-in-802-22.doc∙Reference Document - Presentation on the PRM and Security Enhancements in 802.22 – 802.22 Threat Analysishttps:///802.22/dcn/08/22-08-0083-08-0000-security-and-prm-enhancements-in-80222-v3.ppt∙Proposed Reference Architecture for 802.22 - https:///802.22/dcn/08/22-08-0121-10-0000-text-on-protocol-reference-model-enhancements-in-802-22.doc∙802.22 Database Interface Architecture and Security Mechanisms -https:///802.22/dcn/09/22-09-0111-02-0000-database-interface-architecture-and-security-mechanisms.ppt∙Whitespace Database Service - https:///802.19/dcn/09/19-09-0047-00-tvws-white-spaces-database.pptMinutes and Discussions∙Discussions on security aspects with the external Whitespace database was carried out.∙Ranga Reddy brought to the attention of the group that the Whitespaces Databases Group has started talking about the security issues of the database with the Whitespace Device. This document includes Public Key Infrastructure (PKI), Transport Security and Device Security.∙PKI - For PKI, X.509 based use of certificates is suggested for key exchange. These X.509 certificates will hold an entity name in the SubjectAltName field, following the convention of the World Wide Web. A 2048-bit RSA key for initial deployment is suggested with forward compatibility for key size increases.U se key rollover procedures based on pre-published supersession to ensure long-term stability of the security architecture is proposed. The OSCP protocol (RFC2560) may be used by WSDs to verify that WSSP certificates have not been revoked by the Repository.∙Transport Security –Transport Layer Security or TLS (RFC4346, though it is sometimes better known by its old name, Secure Sockets Layer or SSL) is suggested. TLS provides authentication, integrity, and confidentiality properties at the transport layer below HTTP.∙Device Security – It is proposed that the device security be carried out using enrollment process with mutual authentication.∙Some discussions based on this proposed document were as follows:∙Winston – Database will be designed such that it will be able to shut down a particular device with a particular FCC ID∙Gerald – complexity needs to be taken into account∙Gerald – Path for 802.22 is clear since we go through a proxy server sucha as NCMS.∙Winston – Take a step back from complexity, implement it and then worry about 802.22 CPEs acting as the Whitespace access points for other Whitespaces network.∙Winston –we are inserting NCMS, Whitespaces Database group is inserting White Space Service Provider.∙Apurva Mody – Based on the proposed document it appears as if the Whitespace database group is thinking about an 802.11 type of a model which is not based on an Internet Service Provider concept. It is proposed that the White Space Device (WSD) will be able to access the Whitespace Service Provider / Repository directly.∙Apurva Mody –suggested that for an 802.11 type of a device, accessing the repository is relatively easy, since the user can easily access the 802.11 MIBs using internet browser application and configure the 802.11 hardware (provide it with the URL) such that the device will transparently access the repository and validate the channels.∙Apurva Mody –802.22 model is not that simple. We chose to follow the Internet Service Provider route where typically, and ISP is likely to maintain an external server such as the NCMS to manage the network.∙Towards the end of the call, the ad-hoc tried to resolve some comments. However, due to lack of time, not much progress was made on comment resolution.3. August 17th 2009 – Security Ad-Hoc Conference Call Meeting Minutes Meeting Minutes1. AttendanceApurva Mody – BAE SystemsGerald Chouinard - CRCRanga Reddy – US ArmyWinston Caldwell – Fox2.1 Agenda∙Attendance∙Chair asked if everyone attending was familiar with the IEEE patent policy -/board/pat/pat-slideset.pdf - Everyone was familiar.∙Minutes of all the Security Ad-Hoc Conference Calls previously held can be found at –https:///802.22/dcn/08/22-08-0163-22-0000-meeting-minutes-of-the-security-ad-hoc-group-in-802-22.doc∙Discussion on Protection Mechanisms for Co-existence Beaconing Packets – led by Ranga Reddy. https:///802.22/dcn/08/22-08-0296-03-0000-cbp-security-protection-mechanisms.doc∙Recommended Text for Section 7 on Security in 802.22 – included in Draft v 2.0 can be found at https:///802.22/dcn/08/22-08-0174-18-0000-recommended-text-for-section-7-on-security-in-802-22.doc∙Reference Document - Table of Contents for Section 7. The reference document for the proposed text can be found athttps:///802.22/file/08/22-08-0165-00-0000-table-of-content-for-the-security-section-in-802-22.doc∙Reference Document - Scope and the Workplan for the Security Ad-Hoc Group –https:///802.22/file/08/22-08-0159-00-0000-scope-agenda-workplan-and-timeline-for-the-security-ad-hoc-in-802-22.doc∙Reference Document - Presentation on the PRM and Security Enhancements in 802.22 – 802.22 Threat Analysishttps:///802.22/dcn/08/22-08-0083-08-0000-security-and-prm-enhancements-in-80222-v3.ppt∙Proposed Reference Architecture for 802.22 - https:///802.22/dcn/08/22-08-0121-10-0000-text-on-protocol-reference-model-enhancements-in-802-22.doc∙802.22 Database Interface Architecture and Security Mechanisms -https:///802.22/dcn/09/22-09-0111-02-0000-database-interface-architecture-and-security-mechanisms.ppt∙Whitespace Database Service - https:///802.19/dcn/09/19-09-0047-00-tvws-white-spaces-database.pptMinutes and Discussions∙Ranga Reddy talked about some of the privacy concerns in current 802.22 security architecture - Multi-cast management messages are protected, however, multicast transport security is complex and it is left upto the service provider / higher layer to provide IPSec.∙Document 114 was reviewed.∙Ranga presented two approaches – pros and cons of both were discussed∙Gerald brought to the attention the fact that FCC requires MAC Address of the device to be sent in the clear.∙Gerald – The trick we found to reduce the overhead was that instead of sending MAC address in every US burst, 802.22 transmits it in the CBP burst every 2 minutes.∙Ranga Reddy - The main issue is the concern about privacy – malicious user should not be able to link MAC address with the CID.∙Winston Caldwell – FCC Report and Order Section 15.711 Part E – Fixed TVBD shall transmit identifying information. The ID information must confirm to a standard. ID should contain sufficient information to identify the device and its geolocation information.∙Apurva Mody - FCC says that the identification and geolocation information needs to be transmitted but does not say that it is in the clear – that is un-encrypted. MAC address may or may not qualify as the identifying information.∙Apurva Mody – Based on document 09-0114 it looks like Approach 1 is more suitable since the MAC address needs to be protected and the FCC does not require that the MAC address is required to be in the clear.∙Apurva Mody - Decision needs to be made in the coming weeks on whether Approach 1 or 2 should be adopted since the Privacy concerns are valid.∙Gerlad Chouinard – prefers Approach 2.∙Apurva Mody – prefers an approach that does not require major modifications to the standard and still overcomes the concerns.∙Winston Caldwell – Wants to provide utmost security that 802.22 can – leave complexity aside.3. August 24th 2009 – Security Ad-Hoc Conference Call Meeting Minutes Meeting Minutes1. AttendanceApurva Mody – BAE SystemsRanga Reddy – US ArmyWinston Caldwell – Fox2.1 Agenda∙Attendance∙Chair asked if everyone attending was familiar with the IEEE patent policy -/board/pat/pat-slideset.pdf - Everyone was familiar.∙Minutes of all the Security Ad-Hoc Conference Calls previously held can be found at –https:///802.22/dcn/08/22-08-0163-22-0000-meeting-minutes-of-the-security-ad-hoc-group-in-802-22.doc∙Discussion on Protection Mechanisms for Co-existence Beaconing Packets – led by Ranga Reddy. https:///802.22/dcn/08/22-08-0296-03-0000-cbp-security-protection-mechanisms.doc∙Recommended Text for Section 7 on Security in 802.22 – included in Draft v 2.0 can be found at https:///802.22/dcn/08/22-08-0174-18-0000-recommended-text-for-section-7-on-security-in-802-22.doc∙Reference Document - Table of Contents for Section 7. The reference document for the proposed text can be found athttps:///802.22/file/08/22-08-0165-00-0000-table-of-content-for-the-security-section-in-802-22.doc∙Reference Document - Scope and the Workplan for the Security Ad-Hoc Group –https:///802.22/file/08/22-08-0159-00-0000-scope-agenda-workplan-and-timeline-for-the-security-ad-hoc-in-802-22.doc∙Reference Document - Presentation on the PRM and Security Enhancements in 802.22 – 802.22 Threat Analysishttps:///802.22/dcn/08/22-08-0083-08-0000-security-and-prm-enhancements-in-80222-v3.ppt∙Proposed Reference Architecture for 802.22 - https:///802.22/dcn/08/22-08-0121-10-0000-text-on-protocol-reference-model-enhancements-in-802-22.doc∙802.22 Database Interface Architecture and Security Mechanisms -https:///802.22/dcn/09/22-09-0111-02-0000-database-interface-architecture-and-security-mechanisms.ppt∙Whitespace Database Service - https:///802.19/dcn/09/19-09-0047-00-tvws-white-spaces-database.pptMinutes and Discussions∙Comments 693, 694, 695, 696 and 697 were discussed.∙Ranga Reddy - is proposing to drop RSA –since supporting a certificate based methods are onerous, especially for small service providers∙Ranga Reddy – RSA is an older technology. Huge overhead since they are not strong and long key sizes are required. Going forward, longer and longer keys will be needed.∙Ranga Reddy – ECC is still present for CPE authentication. You can also use EAP. You can also do both. In case of both, you would first do ECC based authentication. Then EAP exchange happens. Information is used from both ECC and EAP for key generation.∙Ranga Reddy - Section 7.2.2.5 needs to be updated. Ranga will provide update to the second paragraph in this section with regards to how the cryptographic suits are selected. Relation between primary, secondary and GSA will be explained.。
