Two new algorithms for UMTS access network topology design
华为数通HCIA211试卷二

华为数通HCIA211试卷二华为数通HCIA211试卷二1.【判断题】1分| NAT在使用动态地址池时,地址池中的地址可以重复使用,即同一IP同时映射给多个内网IP。
(已确认)A对B错2.【单选题】1分| 以太网数据帧的Length/Type字段取以下哪个值时,表示承载的是PPPoE发现阶段的报文?(单选)A 0x0800B 0x8863C 0x8864D 0x08063.【判断题】1分| 在华为设备上,如果使用AAA认证进行授权,当远程服务器无响应时,可以从网络设备侧进行授权。
A对B错4.【多选题】1分| 基于ACL规则,ACL可以划分为以下哪些类?(多选)A 二层ACLB 用户ACLC 高级ACLD 基本ACL5.【判断题】1分| 管理信息库MIB(Management Information Base)是一个虚拟的数据库,这个数据库保存在NMS上。
A对B错6.【判断题】1分| AR G3系列路由器上的ACL支持两种匹配顺序:配置顺序和自动排序。
A对B错7.【判断题】1分| 被请求节点组播地址由前缀FF02::1:FF00:0/104和单播地址的最后24位组成。
A对B错8.【判断题】1分| 组播地址FF02::2表示链路本地范围的所有路由器。
A对B错9.【判断题】1分| IPv6报文的基本首部长度是固定值。
A对B错10.【判断题】1分| IPv6地址2022:ABEF:224E:FFE2:BCC0:CD00:DDBE:8D58不能简写。
B错11.【多选题】1分| 路由器Router D邻居关系如下,下列说法正确的有?A DR路由器的Router-ID为10.0.2.2B DR路由器的Router-ID为10.0.1.1C 本路由器是DROther路由器D 本路由器和Router-ID为10.0.3.3的路由器不能直接交换链路状态信息12.【判断题】1分| SRGB(segment routing global block):为全局segment预留的本地标签集合。
路由交换技术智慧树知到答案章节测试2023年黑龙江交通职业技术学院

项目一测试1.交换机通过记录端口接收数据中的()和端口的对应关系来进行MAC地址表学习。
A:源MAC地址B:目的IP地址C:目的MAC地址D:源IP地址答案:A2.在一个交换网络中,存在多个VLAN。
管理员想在交换机间实现数据流转发的负载均衡,则应该选用()协议。
A:其余三者均可B:STPC:MSTPD:RSTP答案:C3.STP进行桥ID比较时,先比较优先级,优先级值__为优;在优先级相等的情况下,再用MAC地址来进行比较,MAC地址_为优()。
A:小者,小者B:大者,小者C:大者,大者D:小者,大者答案:A4.在802.1D中,默认的ForwardDelay时间是()秒。
A:20B:25C:15D:10答案:C5.集线器是一个()设备,它提供网络设备之间的直接连接或多重连接。
A:物理层B:数据链路层C:网络层D:传输层答案:A项目二测试1.路由器根据IP报文中的_进行路由表项查找,并选择其中_的路由项用于指导报文转发()。
A:目的IP地址,掩码最长B:目的IP地址,掩码最短C:源IP地址,掩码最长D:源IP地址,掩码最短答案:A2.RIP使用_协议来承载,其端口号是_()A:UDP, 520B:TCP,179C:UDP,179D:TCP, 520答案:A3.RIP协议的 Update定时器的默认时间是()秒A:30B:180C:60D:120答案:A4.RIP路由的默认优先级是()。
A:1B:60C:100D:0答案:C5.“单臂路由”是利用()链路允许多个VLAN帧通过而实现的A:TaggedB:TrunkC:HybridD:Access答案:B项目三测试1.IP 地址203.108.2.110 是()地址。
A:A 类B:B 类C:C 类D:D 类答案:C2.以下NAT技术中,允许外网主机主动对内网主机发起连接的是()。
A:NAT ServerB:Easy IPC:Basic NATD:NAPT答案:A3.IPv4地址共()位,理论上支持约40亿的地址空间。
2022年福州大学网络工程专业《计算机网络》科目期末试卷A(有答案)

2022年福州大学网络工程专业《计算机网络》科目期末试卷A(有答案)一、选择题1、以下说法错误的是()。
I..广播式网络一般只包含3层,即物理层、数据链路层和网络层II.Intermet的核心协议是TCP/IPIII.在lnternet中,网络层的服务访问点是端口号A. I、II、IIIB. IIIC. I、ⅢD. I、II2、在OS1参考模型中,下列功能需由应用层的相邻层实现的是()。
A.对话管理B.数据格式转换C.路由选择D.可靠数据传输3、采用了隧道技术后,如果一个不运行组播路由器的网络遇到了一个组播数据报,那么它会()。
A.丢弃该分组,不发送错误信息B.丢弃该分组,并且通知发送方错误信息C.选择一个地址,继续转发该分组D.对组播数据报再次封装,使之变为单一日的站发送的单播数据报,然后发送4、以下给出的地址中,属于子网192.168.15.19/28的主机地址是()。
I.192.168.15.17 Ⅱ.192.168.15.14Ⅲ.192.168.15.16 Ⅳ.192.168.15.31A.仅IB. 仅Ⅱ、IC. 仅IⅡ、I、ⅣD.Ⅲ、Ⅱ、I、Ⅳ5、一个通过以太网传送的IP分组有60B长,其中包括所有头部。
若没有使用LLC,则以太网帧中需要()填充字节。
A.4字节B.1440字节C.0字节D.64字节6、使用海明码进行前向纠错,如果冗余位为4位,那么信息位最多可以用到()位,假定码字为a6a5a4a3a2a1a0,并且有下面的监督关系式:S2=a2+a4+a5+a6两个答案7、数据段的TCP报头中为什么包含端口号()。
A.指示转发数据段时应使用正确的路由器接口B.标识接收或转发数据段时应使用的交换机端口C.让接收主机以正确的顺序组装数据报D.让接收主机转发数据到适当的应用程序8、TCP中滑动窗口的值设置太大,对主机的影响是()。
A.由于传送的数据过多而使路由器变得拥挤,主机可能丢失分组B.产生过多的ACKC.由于接收的数据多,而使主机的工作速度加快D.由于接收的数据多,而使主机的工作速度变慢9、某TCP分组的选项字段长度为9B,则该TCP分组的数据偏移字段内容为()。
物联网相关知识模拟练习题与参考答案

物联网相关知识模拟练习题与参考答案一、单选题(共60题,每题1分,共60分)1、售中-业务开通指客户经理在建设的物联网一体化平台上提单到完成网络侧业务开通,联调测试并交付的环节。
其中物联网专线(资源具备)银牌级开通时限为几个工作日A、8B、9C、6D、7正确答案:B2、NB-IoT系统在In band 操作模式下,时以下哪种情况下允许 LTE CRS 作为额外的参考信号用于物理下行数据信道解调?A、LTE与NB-IoT具有相同的PCI和不同的天线端口B、LTE与NB-IoT具有相同的PCI和相同的天线端口C、LTE与NB-IoT具有不同的PCI和不同的天线端口D、LTE与NB-IoT具有不同的PCI和相同的天线端口正确答案:B3、在处理MME故障时,结合故障处理流程,应该遵循()的基本原则。
A、一“动手”、二“查看”、三“询问”、四“思考”B、一“动手”、二“查看”、三“思考”、四“询问”C、一“查看”、二“询问”、三“思考”、四“动手”D、一“询问”、二“查看”、三“思考”、四“动手”正确答案:C4、安全风险评估分为自评估和检查评估两种形式。
下列描述不正确的是:()A、检查评估也可委托风险评估服务技术支持方实施,但评估结果仅对检查评估的发起单位负责。
B、安全风险评估应以自评估为主,自评估和检查评估相互结合、互为补充。
C、检查评估可在自评估实施的基础上,对关键环节或重点内容实施抽样评估。
D、检查评估是指信息系统上级管理部门组织有关职能部门开展的风险评估。
正确答案:D5、智慧地球是()提出来的A、法国B、美国C、德国D、日本正确答案:B6、NB-IoT上行链路中,对于3.75KHZ子载波间隔而言,其时隙长度延长至()ms。
A、1B、2C、0.5D、3正确答案:B7、对于GRE协议,以下说法错误的是哪项A、对使用GRE的用户,在发送用户的包时,先对用户的IP包进行一次GRE封装,然后再从Gi接口发送B、GRE是一种通用隧道协议,属于二层隧道协议C、当从Gi接口收到GRE封装的包时,首先要进行GRE的解封装,然后再查找上下文,将解开的IP包通过GPRS网络送给相应的用户D、对某些网络层协议的数据报进行封装,使这些被封装的数据报能够在另一个网络层协议(如IP)中传输正确答案:B8、NB-IoT 覆盖等级0 对应的MCL是多少?A、A164dbB、C144dbC、D134dbD、B154db正确答案:B9、OneLink用户连接数已经达到()亿A、1.2B、5.1C、2.3D、0.5正确答案:B10、下列()过程不是NB-IoT连接挂起过程中的步骤。
《交换网络二层技术》PPT课件

3、甲和乙接入vlan10端口互ping
甲
4、将乙移至TRUNK端口,开启抓包
5、甲再ping乙,可捕获802.1q数据
生成树技术
生成树协议数据单元
生成树形成过程
A0-11-23-B1-0D-01
根-交换机
指定端口 A0-11-23-B1-0D-02 根-PORT
指定端口 根-PORT A0-11-23-B1-0D-03
VLAN延伸实验2
VLAN20 丙
VLAN10
甲和乙通信报文,丙是否可通过镜
甲
乙
VLAN延伸实验3
• 给定设备,交换机1台,PC2台,网线2条,抓包 软件。
• 设计网络拓扑 • 目标:捕获802.1q数据 • ……
参考拓扑
Trunk,pvid=1
vlan10 乙
1、甲与乙相同网段地址
2、交换机划分vlan10,加入两个端口
本章小结
• VLAN概念
• 提升交换网络的效率和安全性能
• 生成树协议*
• 提供冗余链路备份的方法,同时也是负载分担的有效 手段。
• 链路聚合
• 经济有效的提升链路带宽的手段,同时也可以提供负 载分担。
• AM
• 提升安全性和可控性。
(拓扑变化)
新的BPDU处理方式
• 每台交换机主动将其BPDU每2秒发送一次 • 更快的信息超时机制 • 接受上游交换机的BPDU
快速生成树的收敛过程
• 生成树收敛过程
root A
B
C
D
边缘端口和工作模式
• 快速生成树收敛过程
root A
B
C
D
请求/确认序列
2、同步状态(替换端口不变化) 替换端口
无线传感器网络中能效优化算法的使用教程

无线传感器网络中能效优化算法的使用教程无线传感器网络(Wireless Sensor Network,缩写WSN)是由许多无线传感器节点组成的网络,节点分散在监测区域内,通过无线通信传输收集到的数据。
在WSN中,能源是一个关键资源,因此如何优化能量消耗成为了研究的重要问题。
本文将为您介绍几种在无线传感器网络中常用的能效优化算法,并详细说明每个算法的使用方法和优势。
1. LEACH算法LEACH(Low Energy Adaptive Clustering Hierarchy)是一种经典的能效优化算法。
它通过分簇的方式将传感器节点划分为无数个簇,并通过轮流担任簇首的方式来实现对能量消耗的均衡。
LEACH的使用方法如下:- 建立初始网络:将网络中的传感器节点随机地分为簇首节点和普通节点,并为每个节点分配能量。
- 簇首选举:普通节点根据一定的概率选择成为簇首节点,同时广播自己的信息给其他节点。
- 数据收集:簇首节点负责收集整个簇中的数据,并将聚合后的数据发送到基站进行处理。
LEACH算法的优点是能够减少数据传输的距离和能量消耗,从而延长整个网络的寿命。
2. PEGASIS算法PEGASIS(Power Efficient Gathering in Sensor Information Systems)是一种基于链路的能效优化算法。
它通过建立一个节点的链表来传输数据,从而减少节点之间的通信开销。
使用PEGASIS算法的方法如下:- 邻居查询:每个节点查询自己的邻居节点,并选择与自己距离最近的节点作为自己的下一个节点。
- 建立链表:每个节点根据前一步选择的下一个节点建立自己的链表,节点之间通过直接跳跃实现链表的建立。
- 数据收集:链表的第一个节点负责收集整个链表中的数据,并将数据传输到基站。
PEGASIS算法的优势在于能够有效减少节点之间的通信开销,从而延长整个网络的寿命。
3. S-MAC算法S-MAC(Sensor Medium Access Control)是一种基于时间同步和睡眠模式的能效优化算法。
无线传感器网络中的多路访问与冲突处理技术

无线传感器网络中的多路访问与冲突处理技术随着科技的不断发展,无线传感器网络在各个领域中的应用越来越广泛。
无线传感器网络由大量的节点组成,这些节点能够感知和收集环境中的信息,并将其传输到中心节点或其他节点进行处理和分析。
然而,由于节点数量众多,节点之间的通信会引发许多问题,其中最重要的是多路访问和冲突处理技术。
在无线传感器网络中,多路访问技术是实现节点之间并行传输的关键。
常见的多路访问技术包括频分多路复用(FDMA)、时分多路复用(TDMA)和码分多址(CDMA)。
在FDMA中,频谱被划分为多个子载波,每个节点被分配一个子载波进行通信。
这种方式可以避免节点之间的冲突,但是由于频谱资源有限,节点数量过多时会导致频谱利用率低下。
TDMA则将时间划分为多个时隙,每个节点在特定的时隙进行通信,从而避免冲突。
CDMA则通过编码和解码技术实现节点之间的并行传输,可以同时进行多个通信。
不同的多路访问技术适用于不同的场景,需要根据具体情况选择合适的方式。
然而,即使使用了多路访问技术,无线传感器网络中仍然会发生冲突。
冲突是指多个节点同时发送数据导致的信号干扰,会降低网络的性能和可靠性。
为了解决这个问题,研究者们提出了一系列的冲突处理技术。
其中最常见的是载波感知多路访问(CSMA)和时隙感知多路访问(CSMA/CA)。
在CSMA中,节点在发送数据之前会先监听信道是否空闲,如果空闲则开始发送数据,如果被占用则等待一段时间后再次监听。
CSMA/CA则是在CSMA的基础上引入了时隙的概念,节点根据时隙进行通信,避免了冲突。
此外,还有一些基于协调的冲突处理技术,如分布式协调函数(DCF)和无线分簇协议(LEACH)。
这些技术通过节点之间的协调和调度来避免冲突,提高了网络的性能。
除了多路访问和冲突处理技术,还有一些其他的技术可以进一步优化无线传感器网络的性能。
例如,功率控制技术可以根据节点之间的距离和信道质量来调整节点的发送功率,从而降低干扰和能耗。
中兴IPRAN题库
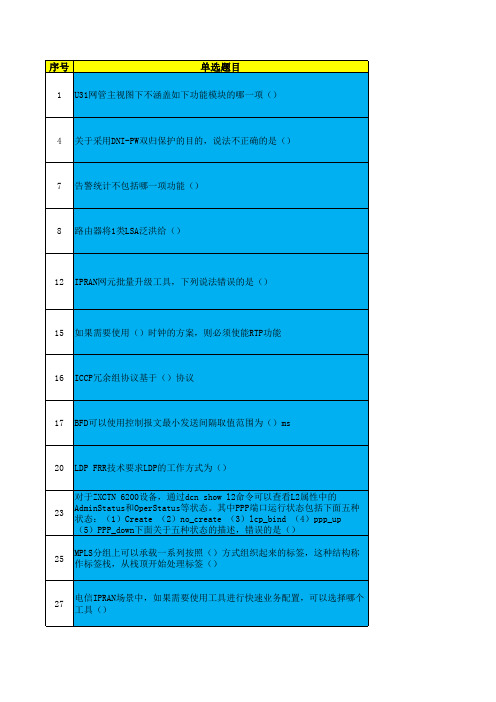
112 不管哪种场景,6000设备必须改成ROS启动方式()
113
联通IPRAN中,LTE业务本地配置需要三层虚子接口上部署本地ARP代理实 现X2流量交互()
115
OSPF协议生成的路由分为四类,按优先级从高到低顺序来说分别是,区 域内路由、区域间路由、第一类外部路由、第二类外部路由()
116
BGP协议的BFD是在BGP向邻居发送Keeplive报文时触发BFD模块开始进行 BFD会话()
序号
单选题目
1 U31网管主视图下不涵盖如下功能模块的哪一项()
4 关于采用DNI-PW双归保护的目的,说法不正确的是()
7 告警统计不包括哪一项功能()
8 路由器将1类LSA泛洪给()
12 IPRAN网元批量升级工具,下列说法错误的是()
15 如果需要使用()时钟的方案,则必须使能RTP功能
16 ICCP冗余组协议基于()协议
70 对于IPRAN场景下大客户业务专线的方案,描述正确的是()
73 U31网管任务管理包括()
74 故障采集服务端端采集支持()模式
75
关于dcn mccif 2 1 gei 1 2 10.0.0.1 255.255.255.255 0.0.0.1这条 命令的含义说法正确的是()
76 以下说法错误的有()
单选 单选 单选 单选 单选 单选 多选 多选 多选 多选 多选
A、按接入环接入端口对应单板启用ulei接口 B、全局只使用一对ulei接口即可 C、ulei是虚接口,没有数量限制 D、ulei接口对应的子接口也需要进行控制,建议不要用满 A、QX口管理方案 B、业务口L2通道监控 C、业务口L3通道监控 D、主备监控网元综合监控通道 A、MC-MSP B、MC-LAG C、DNI-PW D、BGP A、ASBR是那些将其他路由协议(也包括静态路由和接口的直连路由)发现的路由引入 (redistribute)到OSPF中的路由器 B、ASBR不一定要位于AS的边界,而是可以在自治系统中的任何位置(Stub区除外) C、OSPF ASBR为每一条引入的路由生成一条Type5类型的LSA D、若某个区域内有ASBR,则这个区域的ABR在向其他区域生成路由信息时必须单独为这 个ASBR生成一条Type 4类型的LSA A、TE-LSP Tunnel都是由隧道的首端发起建立,是一条head-end的LSP隧道 B、LSP Tunnel都是单向的 C、RSVP TE中的LSP都通过一个五元组来唯一标识 D、RSVP采用软状态模块,路径采用RSVP定期刷新机制进行维护 A、BGP BFD B、PW BFD C、TE BFD D、Peer BFD A、一端组播能力被破坏 B、acl拒绝了hello报文 C、一端NAT转换了HELLO报文 D、一端阻塞了hello报文 A、告警上报自动恢复 B、告警反转 C、不反转 D、不上报 A、MPLS协议中使用了两种标签保留的方式:保守方式和自由方式 B、保守标记保持方式时,只有用于数据转发的FEC标记绑定才会被保留 C、自由标记保持方式时,不论发送路由器是否是它所通告的特定FEC标记映射的下一 跳,路由器对于所有的标记映射都加以保留 D、自由标记保持方式相对于保守标记保持方式的主要优势在于路由器可以快速对路由 变化作出响应 A、BGP BFD B、PW BFD C、ISIS BFD D、Peer BFD A、级联数越高越好 B、级联数越高,封装效率越高 C、级联数越高,封装效率越低 D、级联数越高,传输时延越高
gsm部分复习题+答案

一、填空题:1、移动通信系统目前采用FDMA、TDMA和CDMA三种多址方式,GSM采用FDMA/TDMA多址方式。
2、MSC 和BSC 之间是A接口,基站和手机之间是Um接口,他们都是标准接口。
3、华为双时隙扩展小区技术最远支持120公里的覆盖半径,支持的最大TA为219。
4、由于天馈的互易性,对于上下行的影响是相同的。
同时GSM上下行频差不大,无线传播特性基本相同,人体损耗和功率余量应该基本相同。
在使用塔放情况下当上下行基本平衡时的简化平衡方程为:基站机顶功率-移动台接收灵敏度=移动台功率+分集增益+塔放带来的增益-基站接收灵敏度5、GSM规范中要求同频干扰保护比 9 dB,第一邻频干扰保护比 -9 dB,偏400kHz干扰保护比-41 dB。
6、NCC与BCC组成BSIC,如果用十进制表示,NCC从 0-7 ,BCC从 0-7 。
7、正常切换算法主要包括边缘切换、层间切换、 PBGT切换。
8、天馈系统主要有天线、塔放、馈线、跳线、避雷器等部件组成。
9、基站时钟模式有三种选择:内时钟、外时钟、外同步时钟。
10、空闲状态下手机显示的是驻留小区的 BCCH 信道的接收电平,通话状态下手机显示的是服务小区 TCH 信道的接收电平。
二、判断题:1、在场强方向图的主瓣中,把相对最大辐射方向场强下降到1/2倍处的波束宽度称为半功率波束宽度。
(F)下降到3db2、极化分集实际上是空间分集的特殊情况。
(T )3、帧(Frame)通常被表示为接连发生的几个时隙,一个TDMA帧包含8个基本的物理信道。
(T)4、在建网初期,我们一般采用3*3的复用方式,待业务量发展较大时,我们一般采用4*3的复用方式。
(F )一般采用4*3的复用方式,业务量发展较大时,我们一般采用1*3的复用方式。
5、GSM900M现阶段使用的频段范围为上行890-915MHZ,下行935-960MHZ。
(T)上行F1=890+(n*0.2m) 下行F2=F1+45MHZ 注N为频点号。
无线网络优化选择题

无线网络优化单选题1.以下关于小区负荷分担(Cell Load Sharing)的描述,哪项是错误的? C2.3. A.小区负荷分担仅限于对TCH的负荷进行分流。
B.小区负荷分担只能分流靠近边界的话务。
C.小区负荷分担能够在不同的BSC之间进行,但必需在同一MSC内。
D.小区负荷分担的切换只有在目标小区的话务负荷低到必然程度时才能进行。
4.下面哪个OBJTYPE用于切换原因的统计: C5.6.(信道释放统计)7.以下什么信息不是在系统消息5中传送的: D8.9.值 B.功率控制值BA表信息10.基站采用FCOMB,则要求相邻频点距离至少为 B11.12.13.若是一个网络运营商别离有15 MHz的上、下行频宽,那么他能够取得多少个GSM频点(减去一个保护频点)? D(15000/200=75-1=74)14.15.16.接收到的发射信号强度是-50 dBm,同时有一同频干扰信号的强度是-150 dBm ,则C/I是多少? D-50-(-150)=10017.18.19.基站数据中的BSPWRB、BSPWRT、BSPWR、BSTXPWR 的关系是: B20.21. A. 前两个是发射机功率,后两个是有效发射功率,有效发射功率应比发射机功率小 B.前两个是发射机功率,后两个是有效发射功率,有效发射功率应比发射机功率大 C.前两个是BCCH载波功率,后两个是DCH载波功率 D.前两个是DCH 载波功率,后两个是BCCH载波功率22.边界地域频繁的位置更新会使得 A的负荷大增。
23.24.25.三载波小区配置一个SDCCH/8 。
若利用半速度语音编码,则该小区最多可同时支持多少个通话? B 3*8=24-2=22*2=4426.27.28.无线参数T3212的作用是: B29.30. A.通知移动台多长时刻作一次切换。
B.通知移动台多长时刻作一次周期性记录。
C.限定移动台在成立呼唤后多长时刻内不能进行切换。
2024年电信5G基站建设理论考试题库(附答案)

2024年电信5G基站建设理论考试题库(附答案)一、单选题1.在赛事保障值守过程中,出现网络突发故障,需要启用红黄蓝应急预案进行应急保障,确保快速处理和恢复。
红黄蓝应急预案的应急逻辑顺序为()A、网络安全->用户感知->网络性能B、网络性能->用户感知->网络安全C、用户感知->网络安全->网络性能D、用户感知->网络性能->网络安全参考答案:D2.2.1G规划,通过制定三步走共享实施方案,降配置,省TCO不包含哪项工作?A、低业务小区并网B、低业务小区关小区C、低业务小区拆小区D、高业务小区覆盖增强参考答案:D3.Type2-PDCCHmonsearchspaceset是用于()。
A、A)OthersysteminformationB、B)PagingC、C)RARD、D)RMSI参考答案:B4.SRIOV与OVS谁的转发性能高A、OVSB、SRIOVC、一样D、分场景,不一定参考答案:B5.用NR覆盖高层楼宇时,NR广播波束场景化建议配置成以下哪项?A、SCENARTO_1B、SCENARIO_0C、SCENARIO_13D、SCENARIO_6参考答案:C6.NR的频域资源分配使用哪种方式?A、仅在低层配置(非RRC)B、使用k0、k1和k2参数以实现分配灵活性C、使用SLIV控制符号级别的分配D、使用与LTE非常相似的RIV或bitmap分配参考答案:D7.SDN控制器可以使用下列哪种协议来发现SDN交换机之间的链路?A、HTTPB、BGPC、OSPFD、LLDP参考答案:D8.NR协议规定,采用Min-slot调度时,支持符号长度不包括哪种A、2B、4C、7D、9参考答案:D9.5G控制信道采用预定义的权值会生成以下那种波束?A、动态波束B、静态波束C、半静态波束D、宽波束参考答案:B10.TS38.211ONNR是下面哪个协议()A、PhysicalchannelsandmodulationB、NRandNG-RANOverallDescriptionC、RadioResourceControl(RRC)ProtocolD、BaseStation(BS)radiotransmissionandreception参考答案:A11.在NFV架构中,哪个组件完成网络服务(NS)的生命周期管理?A、NFV-OB、VNF-MC、VIMD、PIM参考答案:A12.5G需要满足1000倍的传输容量,则需要在多个维度进行提升,不包括下面哪个()A、更高的频谱效率B、更多的站点C、更多的频谱资源D、更低的传输时延参考答案:D13.GW-C和GW-U之间采用Sx接口,采用下列哪种协议A、GTP-CB、HTTPC、DiameterD、PFCP参考答案:D14.NR的频域资源分配使用哪种方式?A、仅在低层配置(非RRC)B、使用k0、k1和k2参数以实现分配灵活性C、使用SLIV控制符号级别的分配D、使用与LTE非常相似的RIV或bitmap分配参考答案:D15.下列哪个开源项目旨在将电信中心机房改造为下一代数据中心?A、OPNFVB、ONFC、CORDD、OpenDaylight参考答案:C16.NR中LongTruncated/LongBSR的MACCE包含几个bit()A、4B、8C、2D、6参考答案:B17.对于SCS120kHz,一个子帧内包含几个SlotA、1B、2C、4D、8参考答案:D18.SA组网中,UE做小区搜索的第一步是以下哪项?A、获取小区其他信息B、获取小区信号质量C、帧同步,获取PCI组编号D、半帧同步,获取PCI组内ID参考答案:D19.SA组网时,5G终端接入时需要选择融合网关,融合网关在DNS域名的'app-protocol'name添加什么后缀?A、+nc-nrB、+nr-ncC、+nr-nrD、+nc-nc参考答案:A20.NSAOption3x组网时,语音业务适合承载以下哪个承载上A、MCGBearB、SCGBearC、MCGSplitBearD、SCGSplitBear参考答案:A21.5G需要满足1000倍的传输容量,则需要在多个维度进行提升,不包括下面哪个()A、更高的频谱效率B、更多的站点C、更多的频谱资源D、更低的传输时延参考答案:D22.以SCS30KHz,子帧配比7:3为例,1s内调度次数多少次,其中下行多少次。
路由与交换技术

5.6练习题
5.1.1物理拓扑与逻辑拓扑 5.1.2传统VLAN间路由环境 5.1.3单臂路由与路由器子接口环境
5.2.1传统VLAN间路由的配置 5.2.2单臂路由与路由器子接口环境的配置
5.3.1三层交换概述 5.3.2三层交换机与VLANIF接口环境 5.3.3三层交换机VLAN间路由的配置
7.3本章总结 7.4练习题
7.1.1 OSPF简介 7.1.2 OSPF的邻居表、LSDB与路由表 7.1.3 OSPF消息的封装格式 7.1.4 OSPF报文类型 7.1.5网络类型 7.1.6路由器ID 7.1.7 DR与BDR
7.2.1 OSPF的邻居状态机 7.2.2链路状态消息的交互 7.2.3路由计算 7.2.4单区域OSPF的基本配置
6.4.1 RIPv2的基本配置 6.4.2配置RIPv2路由自动汇总 6.4.3配置RIPv2路由手动汇总 6.4.4配置RIPv2下发默认路由 6.4.5配置RIPv2认证 6.4.6 RIP公共特性的调试
6.5.1信息交互 6.5.2链路状态协议算法
7.1 OSPF的特征
7.2单区域OSPF的原 理与基本配置
读书笔记
这是《路由与交换技术》的读书笔记模板,可以替换为自己的心得。
精彩摘录
这是《路由与交换技术》的读书笔记模板,可以替换为自己的精彩内容摘录。
谢谢观看
目录分析
1.1交换网络
1.2交换机的 基本设置
1.3本章总结
1.4练习题
1.1.1共享型以太网与冲突域 1.1.2交换机简介 1.1.3交换型以太网与广播域 1.1.4交换机的数据帧转发方式 1.1.5企业园区网设计示例
1.2.1速率与双工 1.2.2 MAC地址表 *1.2.3 MAC地址泛洪攻击概述
5G认证考核测试2021-32

5G认证考试32第一部分单选题(100题)1、根据移动目前的定义,NFVO-VNFM的接口是()A、C5B、C6C、C7D、C81、答案B2、NF instance ID说法不正确的是()A、采用UUID版本4格式(RFC 4122)共256个bitB、Region:标识网元负责业务所在的大区C、NF type:标识网元类型D、Province:标识网元所服务的省份2、答案A3、如果某个承载的QCI=9,那么关于这个承载说法错误的是A、可能是默认承载B、可能是专有承载C、一定是GBR承载D、一定是non-GBR承载3、答案C4、NSA对于的核心网业界称之为EPC+,SA对于的核心网称之为NGC,相比于NGC,EPC+支持什么业务A、eMBBB、mMTCC、uRLLCD、None4、答案A5、下列主流的虚拟化技术中哪个是微软虚拟化产品?A、VMWAREB、KVMC、Hyper-VD、Xen5、答案C6、核心网侧基于用户的签约信息、位置信息生成移动性限制策略,通过()或Configuration Update消息发给接入侧和用户,从而限制用户在5G中的移动性和业务接入A、注册响应B、鉴权响应C、连接响应D、限制响应6、答案A7、以下哪个失败原因值与5G会话管理无关?A、Missing or unknown DNNB、Unknown PDU session typeC、5GS services not allowedD、Service option not supported7、答案C8、以下不属于AMF相关的性能指标的是A、5G网络AUPI数B、5G开户用户数C、5G活动用户数D、去订阅用户数据成功率8、答案A9、以下哪项不是5G网络逻辑视图的构成部分A、接入平面B、控制平面C、管理编排平面D、转发平面9、答案C10、哪个网络功能支持服务和网络功能发现功能?A、NRFB、NSSFC、NEFD、UDM10、答案A11、SDN的特征不包括A、控制转发分离B、虚拟化网络C、可编程接口D、可切片11、答案D12、AMF网元基于()发现UDMA、IMSIB、GUAMIC、DDND、SUPI12、答案D13、5G SA二期工程基于R15()版本进行SA核心网建设。
UMTS网优专题-干扰排查指导_R2[1].0
![UMTS网优专题-干扰排查指导_R2[1].0](https://img.taocdn.com/s3/m/ad8a2146b307e87101f696aa.png)
UMTS干扰排查指导书R2.0法律声明若接收中兴通讯股份有限公司(以下称为“中兴通讯”)的此份文档,即表示您已同意以下条款。
若不同意以下条款,请停止使用本文档。
本文档版权所有中兴通讯股份有限公司。
保留任何未在本文档中明示授予的权利。
文档中涉及中兴通讯的专有信息。
未经中兴通讯事先书面许可,任何单位和个人不得复制、传递、分发、使用和泄漏该文档以及该文档包含的任何图片、表格、数据及其他信息。
和是中兴通讯的注册商标。
中兴通讯产品的名称和标志是中兴通讯的商标或注册商标。
在本文档中提及的其他产品或公司名称可能是其各自所有者的商标或注册商标。
在未经中兴通讯或第三方权利人事先书面同意的情况下,阅读本文档并不表示以默示、不可反言或其他方式授予阅读者任何使用本文档中出现的任何标记的权利。
本产品符合有关环境保护和人身安全方面的设计要求,产品的存放、使用和弃置应遵照产品手册、相关合同或相关国法律、法规的要求进行。
本文档按“现状”和“仅此状态”提供。
本文档中的信息随着中兴通讯产品和技术的进步将不断更新,中兴通讯不再通知此类信息的更新。
中兴通讯股份有限公司地址: 中国深圳市科技南路55号邮编518057网站: (TSM-技术支持库)邮箱: TSM售后文档库@版本更新说明目录1前言 (1)2UMTS受干扰的类型及其原理 (1)2.1内部干扰 (2)2.1.1设备故障导致的干扰 (2)2.1.2互调干扰 (2)2.2外部干扰 (4)2.2.1异系统产生的干扰 (4)2.2.2直放站干扰 (6)2.2.3室分干放干扰 (8)2.2.4微波传输干扰 (9)2.2.5其他类型设备(非通信相关设备)的干扰 (9)3干扰排查流程 (9)3.1发现干扰 (11)3.1.1RTWP指标分析 (11)3.1.2通过OMC话统发现干扰变化 (12)3.1.3通过网优测试发现干扰 (12)3.2统计UMTS全网受到干扰的小区 (12)3.2.1受干扰小区的统计原则 (13)3.3受干扰小区的后台分类与分析 (15)3.3.1DMS扫频及受干扰类型的初步分类 (15)3.3.2内部干扰及外部干扰的分类 (15)3.3.3后台的分析(相关性分析) (16)3.4上站排查与定位 (20)3.4.1内部干扰的分析与排查 (20)3.4.2外部干扰的分析与排查 (22)3.5干扰解决方案 (25)3.5.1内部干扰解决 (25)3.5.2外部干扰解决 (25)3.6干扰解决分析报告 (27)4干扰排查案例 (28)4.1室内站点干扰排查 (28)4.2香港CSL U900网络境外干扰的分析与排查 (31)5团队运作及管理 (39)5.1人员分配 (39)5.2跟局方的沟通与交流 (39)5.3技能转移 (40)6总结 (40)7附录 (40)图目录图2-1 互调产生的原理图 (3)图2-2 阻塞干扰频谱示意图 (5)图2-3 直放站的原理框图 (7)图2-4 一个典型的直放站室分系统 (7)图3-1 干扰排查流程图 (10)图3-2 不正常的RTWP值示例 (12)图3-3 通过PMS实时采集到的RTWP数据 (18)图3-4 莲塘里正站点与干扰源的位置关系 (19)图3-5 将电信站点及UMTS站点同时显示的图层示例 (20)图3-6 RTWP忘记配置的波形图 (21)图3-7 AOA定位法 (23)图3-8 中分法定位示意图 (24)图3-9 两点定位示意图 (24)图4-1 U900的RTWP (28)图4-2 U2100 F1 RTWP (29)图4-3 U2100 F3 RTWP (29)图4-4 U900开关功放后U2100频谱 (30)图4-5 分析结果 (31)图4-6 站点KAN小区RTWP随时间的变化图 (32)图4-7 KAN站点的PMS测量 (33)图4-8 信号测量显示干扰信号来自深圳 (34)图4-9 U900功放打开期间的频谱仪测量显示 (34)图4-10 U900关闭后的频谱仪测量显示 (35)图4-11 位于边境(紧邻深圳)区域的U900站点 (36)图4-12 香港边境(紧邻深圳)的几个小区的相关性曲线图 (36)图4-13 站点FUT的扫频图 (37)图4-14 站点MMH的扫频图 (37)图4-15 境外干扰的改造实施效果 (38)表目录表2-1 3GPP协议针对UMTS接收机阻塞特性的规定 (5)表5-1 人员角色及分配 (39)1 前言随着3G(UMTS)网络建设脚步的日益展开与加快,各大运营商在对自己目前的网络加大优化力度的同时,都面临着如何更好与后续3G系统相兼容的问题,都在从成本代价最小、工程最具操作性、对现有网络影响最小的角度出发,寻求3G网络建设中存在的干扰问题的解决方案。
CDMA是CodeDivisionMultipleAccess的缩写

CDMA是Code Division Multiple Access的缩写,被翻做码分多址。
这是现代通信技术中用来实现信道共享的一种技术。
所谓信道,可以是电磁信号的一个特定频率区域,称为频带;也可以是信号的一个特定时间片段,称为帧。
所谓信道共享,就是将同一个信道供多个用户同时使用并保证互不干扰。
信道共享可以提高信道资源的利用率。
有许多不同的技术可以用来实现信道共享。
把信道频带分割为若干更窄的互不相交的频带(称为子频带),把每个子频带分给一个用户专用(称为地址)。
这种技术被称为“频分多址”技术,英文就是FDMA (Frequency Division Multiple Access/Address)。
这是模拟载波通信、微波通信、卫星通信的基本技术,也是第一代模拟移动通信的基本技术。
类似地,可以把信道帧划分为若干不相重叠的时隙,把每个时隙分配给一个用户作为专用地址。
这就是“时分多址”,即TDMA(Time Division Multiple Access/Ad dress)。
这是数字数据通信和第二代移动通信的基本技术。
如果各个用户的地址既不是指定的信号子频带也不是时隙,而是信号的一组正交编码结构(码型),这些用户信号也可以同时在同一个信道上传输而互不干扰。
这种技术称为“码分多址”,即CDMA。
理论和实践证明,与FDMA及TD MA相比,除了其它一些优点之外,在相同的信道条件下,CDMA具有更高的信道资源利用率,因此,成为第三代移动通信信道共享的基本方式。
CDMA是码分多址的英文缩写(Code Division Muitiple Access),它是在数字技术的分支--扩频通信技术上发展起来的一种崭新而成熟的无线通信技术。
CDMA技术的原理是基于扩频技术,即将需传送的具有一定信号带宽信息数据,用一个带宽远大于信号带宽的高速伪随机码进行调制,使原数据信号的带宽被扩展,再经载波调制并发送出去。
接收端使用完全相同的伪随机码,与接收的带宽信号作相关处理,把宽带信号换成原信息数据的窄带信号即解扩,以实现信息通信。
通信工程师基础知识试题库

通信工程师习题集目录上篇新技术、新业务知识 (6)第一章基础知识 (6)第二章现代电信网 (15)第三章现代电信技术 (33)第四章电信业务 (48)第五章电信市场营销................................................................................... 错误!未定义书签。
下篇通信专业知识 .. (66)一、无线通信专业 .............................................. 错误!未定义书签。
第一章无线通信概述................................................................................... 错误!未定义书签。
第二章微波通信 ........................................................................................... 错误!未定义书签。
第三章卫星通信 ........................................................................................... 错误!未定义书签。
第四章无线市话通信................................................................................... 错误!未定义书签。
二、移动通信专业 (66)第一章移动通信概述 (66)第二章移动通信网 (76)第三章移动通信的无线覆盖技术 (84)第四章干扰和噪声 (91)第五章移动通信的电波传播 (97)第六章基站控制器(BSC) (102)第七章GPRS系统介绍 (111)第八章WCDMA系统介绍 (125)三、有线传输专业 .............................................. 错误!未定义书签。
TD信息元素详解

信息元素功能性定义作者:李欣目录目录 (1)信息元素功能性定义 (11)1 核心网信息元素 (11)1.1 CN Information elements (11)1.2 CN Domain System Information (11)1.3 CN Information info (11)1.4 IMEI (11)1.5 IMSI (GSM-MAP) (11)1.6 Intra Domain NAS Node Selector (11)1.7 Location Area Identification (12)1.8 NAS message (12)1.9 NAS system information (GSM-MAP) (12)1.10 Paging record type identifier (12)1.11 PLMN identity (12)1.12 PLMN Type (12)1.13 P-TMSI (GSM-MAP) (12)1.14 RAB identity (12)1.15 Routing Area Code (12)1.16 Routing Area Identification (13)1.17 TMSI (GSM-MAP) (13)2 UTRAN 移动信息元素 (13)2.1 Cell Access Restriction (13)2.2 Cell identity (13)2.3 Cell selection and re-selection info for SIB3/4 (13)2.4 Cell selection and re-selection info for SIB11/12 (13)2.5 Mapping Info (14)2.6 URA identity (14)3 UE 信息元素 (14)3.1 Activation time (14)3.2 Capability Update Requirement (14)3.3 Cell update cause (15)3.4 Ciphering Algorithm (15)3.5 Ciphering mode info (15)3.6 CN domain specific DRX cycle length coefficient (15)3.7 CPCH Parameters (15)3.8 C-RNTI (15)3.9 DRAC system information (15)3.10 Void (16)3.11 Establishment cause (16)3.12 Expiration Time Factor (16)3.13 Failure cause (16)3.14 Failure cause and error information (16)3.15 Initial UE identity (16)3.16 Integrity check info (16)3.17 Integrity protection activation info (17)3.18 Integrity protection Algorithm (17)3.19 Integrity protection mode info (17)3.20 Maximum bit rate (17)3.21 Measurement capability (17)3.22 Paging cause (17)3.23 Paging record (17)3.24 PDCP capability (17)3.25 Physical channel capability (18)3.26 Protocol error cause (18)3.27 Protocol error indicator (18)3.28 RB timer indicator (18)3.29 Redirection info (18)3.30 Re-establishment timer (18)3.31 Rejection cause (18)3.32 Release cause (18)3.33 RF capability FDD (19)3.34 RLC capability (19)3.35 RLC re-establish indicator (19)3.36 RRC transaction identifier (19)3.37 Security capability (19)3.38 START (19)3.39 Transmission probability (19)3.40 Transport channel capability (20)3.41 UE multi-mode/multi-RAT capability (20)3.42 UE radio access capability (20)3.43 UE Timers and Constants in connected mode (21)3.44 UE Timers and Constants in idle mode (21)3.45 UE positioning capability (21)3.46 URA update cause (21)3.47 U-RNTI (21)3.48 U-RNTI Short (21)3.49 UTRAN DRX cycle length coefficient (21)3.50 Wait time (21)3.51 UE Specific Behavior Information 1 idle (21)3.52 UE Specific Behavior Information 1 interRAT (22)4 无线承载信息元素 (22)4.0 Default configuration identity (22)4.1 Downlink RLC STATUS info (22)4.2 PDCP info (22)4.3 PDCP SN info (22)4.4 Polling info (22)4.5 Predefined configuration identity (23)4.6 Predefined configuration value tag (23)4.7 Predefined RB configuration (23)4.8 RAB info (23)4.9 RAB info Post (23)4.10 RAB information for setup (23)4.11 RAB information to reconfigure (24)4.12 NAS Synchronization indicator (24)4.13 RB activation time info (24)4.14 RB COUNT-C MSB information (24)4.15 RB COUNT-C information (24)4.16 RB identity (24)4.17 RB information to be affected (24)4.18 RB information to reconfigure (25)4.19 RB information to release (25)4.20 RB information to setup (25)4.21 RB mapping info (25)4.22 RB with PDCP information (25)4.23 RLC info (25)4.24 Signaling RB information to setup (26)4.25 Transmission RLC Discard (26)5 传输信道信息元素 (26)5.1 Added or Reconfigured DL TrCH information (26)5.2 Added or Reconfigured UL TrCH information (27)5.3 CPCH set ID (27)5.4 Deleted DL TrCH information (27)5.5 Deleted UL TrCH information (27)5.6 DL Transport channel information common for all transport channels (27)5.7 DRAC Static Information (27)5.8 Power Offset Information (28)5.9 Predefined TrCH configuration (28)5.10 Quality Target (28)5.11 Semi-static Transport Format Information (28)5.12 TFCI Field 2 Information (28)5.13 TFCS Explicit Configuration (28)5.14 TFCS Information for DSCH (TFCI range method) (29)5.15 TFCS Reconfiguration/Addition Information (29)5.16 TFCS Removal Information (29)5.17 Void (29)5.18 Transport channel identity (29)5.19 Transport Format Combination (TFC) (29)5.20 Transport Format Combination Set (29)5.21 Transport Format Combination Set Identity (29)5.22 Transport Format Combination Subset (29)5.23 Transport Format Set (29)5.24 UL Transport channel information common for all transport channels (30)6 物理信道信息元素 (30)6.1 AC-to-ASC mapping (30)6.2 AICH Info (30)6.3 AICH Power offset (30)6.4 Allocation period info (30)6.5 Alpha (30)6.6 ASC Setting (30)6.7 Void (31)6.8 CCTrCH power control info (31)6.9 Cell parameters Id (31)6.10 Common timeslot info (31)6.11 Constant value (31)6.12 CPCH persistence levels (31)6.13 CPCH set info (31)6.14 CPCH Status Indication mode (31)6.15 CSICH Power offset (32)6.16 Default DPCH Offset Value (32)6.17 Downlink channelisation codes (32)6.18 Downlink DPCH info common for all RL (32)6.19 Downlink DPCH info common for all RL Post (32)6.20 Downlink DPCH info common for all RL Pre (32)6.21 Downlink DPCH info for each RL (32)6.22 Downlink DPCH info for each RL Post (33)6.23 Downlink DPCH power control information (33)6.24 Downlink information common for all radio links (33)6.25 Downlink information common for all radio links Post (33)6.26 Downlink information common for all radio links Pre (33)6.27 Downlink information for each radio link (33)6.28 Downlink information for each radio link Post (33)6.29 Void (33)6.30 Downlink PDSCH information (33)6.31 Downlink rate matching restriction information (34)6.32 Downlink Timeslots and Codes (34)6.33 DPCH compressed mode info (34)6.34 DPCH Compressed Mode Status Info (34)6.35 Dynamic persistence level (34)6.36 Frequency info (34)6.37 Individual timeslot info (35)6.38 Individual Timeslot interference (35)6.39 Maximum allowed UL TX power (35)6.40 Void (35)6.41 Midamble shift and burst type (35)6.42 PDSCH Capacity Allocation info (35)6.43 PDSCH code mapping (36)6.44 PDSCH info (36)6.45 PDSCH Power Control info (36)6.46 PDSCH system information (36)6.47 PDSCH with SHO DCH Info (36)6.48 Persistence scaling factors (36)6.49 PICH Info (36)6.50 PICH Power offset (37)6.51 PRACH Channelisation Code List (37)6.52 PRACH info (for RACH) (37)6.53 PRACH partitioning (37)6.54 PRACH power offset (37)6.55 PRACH system information list (37)6.56 Predefined PhyCH configuration (38)6.57 Primary CCPCH info (38)6.58 Primary CCPCH info post (38)6.59 Primary CCPCH TX Power (38)6.60 Primary CPICH info (38)6.61 Primary CPICH Tx power (38)6.62 Primary CPICH usage for channel estimation (38)6.63 PUSCH info (38)6.64 PUSCH Capacity Allocation info (38)6.65 PUSCH power control info (39)6.66 PUSCH system information (39)6.67 RACH transmission parameters (39)6.68 Radio link addition information (39)6.69 Radio link removal information (39)6.70 SCCPCH Information for FACH (39)6.71 Secondary CCPCH info (39)6.72 Secondary CCPCH system information (40)6.73 Secondary CPICH info (40)6.74 Secondary scrambling code (40)6.75 SFN Time info (40)6.76 SSDT cell identity (40)6.77 SSDT information (40)6.78 STTD indicator (40)6.79 TDD open loop power control (41)6.80 TFC Control duration (41)6.81 TFCI Combining Indicator (41)6.82 TGPSI (41)6.83 Time info (41)6.84 Timeslot number (41)6.85 TPC combination index (41)6.86 TSTD indicator (41)6.87 TX Diversity Mode (41)6.88 Uplink DPCH info (41)6.89 Uplink DPCH info Post (42)6.90 Uplink DPCH info Pre (42)6.91 Uplink DPCH power control info (42)6.92 Uplink DPCH power control info Post (42)6.93 Uplink DPCH power control info Pre (42)6.94 Uplink Timeslots and Codes (42)6.95 Uplink Timing Advance (42)6.96 Uplink Timing Advance Control (43)7 测量信息元素 (43)7.1 Additional measurements list (43)7.2 Cell info (43)7.3 Cell measured results (43)7.4 Cell measurement event results (44)7.5 Cell reporting quantities (44)7.6 Cell synchronization information (44)7.7 Event results (44)7.8 FACH measurement occasion info (45)7.9 Filter coefficient (45)7.10 HCS Cell re-selection information (45)7.11 HCS neighboring cell information (45)7.12 HCS Serving cell information (45)7.13 Inter-frequency cell info list (46)7.14 Inter-frequency event identity (46)7.15 Inter-frequency measured results list (46)7.16 Inter-frequency measurement (46)7.17 Inter-frequency measurement event results (47)7.18 Inter-frequency measurement quantity (47)7.19 Inter-frequency measurement reporting criteria (47)7.20 Inter-frequency measurement system information (47)7.21 Inter-frequency reporting quantity (47)7.22 Inter-frequency SET UPDATE (48)7.23 Inter-RAT cell info list (48)7.24 Inter-RAT event identity (48)7.25 Inter-RAT info (48)7.26 Inter-RAT measured results list (48)7.27 Inter-RAT measurement (49)7.28 Inter-RAT measurement event results (49)7.29 Inter-RAT measurement quantity (49)7.30 Inter-RAT measurement reporting criteria (49)7.31 Inter-RAT measurement system information (50)7.32 Inter-RAT reporting quantity (50)7.33 Intra-frequency cell info list (50)7.34 Intra-frequency event identity (50)7.35 Intra-frequency measured results list (50)7.36 Intra-frequency measurement (50)7.37 Intra-frequency measurement event results (51)7.38 Intra-frequency measurement quantity (51)7.39 Intra-frequency measurement reporting criteria (51)7.40 Intra-frequency measurement system information (51)7.41 Intra-frequency reporting quantity (52)7.42 Intra-frequency reporting quantity for RACH reporting (52)7.43 Maximum number of reported cells on RACH (52)7.44 Measured results (52)7.45 Measured results on RACH (52)7.46 Measurement Command (52)7.47 Measurement control system information (53)7.48 Measurement Identity (53)7.49 Measurement reporting mode (53)7.50 Measurement Type (53)7.51 Measurement validity (53)7.52 Observed time difference to GSM cell (53)7.53 Periodical reporting criteria (53)7.54 Primary CCPCH RSCP info (54)7.55 Quality measured results list (54)7.56 Quality measurement (54)7.57 Quality measurement event results (54)7.58 Quality measurement reporting criteria (54)7.59 Quality reporting quantity (54)7.60 Reference time difference to cell (54)7.61 Reporting Cell Status (55)7.62 Reporting information for state CELL_DCH (55)7.63 SFN-SFN observed time difference (55)7.64 Time to trigger (55)7.65 Timeslot ISCP info (55)7.66 Traffic volume event identity (55)7.67 Traffic volume measured results list (55)7.68 Traffic volume measurement (55)7.69 Traffic volume measurement event results (56)7.70 Traffic volume measurement object (56)7.71 Traffic volume measurement quantity (56)7.72 Traffic volume measurement reporting criteria (56)7.73 Traffic volume measurement system information (56)7.74 Traffic volume reporting quantity (56)7.75 UE internal event identity (56)7.76 UE internal measured results (57)7.77 UE internal measurement (57)7.78 UE internal measurement event results (57)7.79 UE internal measurement quantity (57)7.80 UE internal measurement reporting criteria (57)7.81 Void (58)7.82 UE Internal reporting quantity (58)7.83 UE Rx-Tx time difference type 1 (58)7.84 UE Rx-Tx time difference type 2 (58)7.85 UE Transmitted Power info (58)7.86 UE positioning Ciphering info (58)7.87 UE positioning Error (58)7.88 UE positioning GPS acquisition assistance (59)7.89 UE positioning GPS almanac (59)7.90 UE positioning GPS assistance data (59)7.91 UE positioning GPS DGPS corrections (59)7.92 UE positioning GPS ionospheric model (59)7.93 UE positioning GPS measured results (59)7.94 UE positioning GPS navigation model (60)7.95 UE positioning GPS real-time integrity (60)7.96 UE positioning GPS reference time (60)7.97 UE positioning GPS UTC model (61)7.98 UE positioning IPDL parameters (61)7.99 UE positioning measured results (61)7.100 UE positioning measurement (61)7.101 UE positioning measurement event results (61)7.102 Void (62)7.103 UE positioning OTDOA assistance data for UE-assisted (62)7.104 Void (62)7.105 UE positioning OTDOA measured results (62)7.106 UE positioning OTDOA neighbor cell info (62)7.107 UE positioning OTDOA quality (63)7.108 UE positioning OTDOA reference cell info (63)7.109 UE positioning position estimate info (64)7.110 UE positioning reporting criteria (64)7.111 UE positioning reporting quantity (64)7.112 T ADV info (65)8 其它信息元素 (65)8.1 BCCH modification info (65)8.2 BSIC (65)8.3 CBS DRX Level 1 information (65)8.4 Cell Value tag (65)8.5 Inter-RAT change failure (65)8.6 Inter-RAT handover failure (66)8.7 Inter-RAT UE radio access capability (66)8.8 Void (66)8.9 MIB Value tag (66)8.10 PLMN Value tag (66)8.11 Predefined configuration identity and value tag (66)8.12 Protocol error information (66)8.13 References to other system information blocks (66)8.14 References to other system information blocks and scheduling blocks (67)8.15 Rplmn information (67)8.16 Scheduling information (67)8.17 SEG COUNT (67)8.18 Segment index (67)8.19 SIB data fixed (67)8.20 SIB data variable (67)8.21 SIB type (67)8.22 SIB type SIBs only (67)9 ANSI-41 Information elements (68)10 Multiplicity values and type constraint values (68)信息元素功能性定义消息是由多个信息元素组合而成,信息元素根据其功能的不同划分为:核心网域信息元素、UTRAN 移动信息元素、UE 信息元素、无线承载信息元素、传输信道信息元素、物理信道信息元素和测量信息元素。
移动考试题库题目

移动考试题库题目一. 填空题(共15分,每空1分)1.在TD-SCDMA系统中被采用的多址方式有(时分多址)、(频分多址)、(码分多址)、(空分多址)。
2.在TD-SCDMA系统中每10 ms为一个无线帧,每个无线帧包括2个子帧。
3.在GSM体系规范中,每一个TDMA帧被定义为一个载频,每个载频包括 8 个信道。
每载波间隔为 200 KHz。
4.802.11 b/g WLAN工作在2.4G频段,频率范围为2.400~2.4835GHz,共划分为13个信道,每信道带宽为22MHz,相邻信道是重叠的,在同一个覆盖区域只可以同时使用 3 个互不重叠的信道。
5.直接费是指与构成工程实体密切相关的费用,它包括人工费、材料费和机械使用费。
6.一般情况下,新建基站机房使用面积需要 20 平方米,若兼顾未来发展需求,可按 40 平方米考虑。
7.当TD-SCDMA智能天线和GSM定向天线并排同向安装时,水平隔离度至少 2米;垂直方向隔离度至少 0.5 米。
8.在安装TD-SCDMA天线时,应避免和PHS的天线处在同一个水平面内;同时应避免直接指向PHS天线;采用垂直隔离时,隔离度不小于 2 米。
二、判断题 (共5分,每题1分)1.TDD系统易于使用非对称频段, 无需具有特定双工间隔的成对频段,同时上行和下行使用同个载频,无线传播是对称的,有利于智能天线技术的实现。
(T )2.在TD-SCDMA 7个常规时隙中,TS0总是固定地用作下行时隙,而TS1既可用作上行时隙也可用作下行时隙;( F )3.GSM使用的多址方式主要有TDMA、FDMA和CDMA。
(F )4.通信建设工程项目投资即建设项目的造价,它是由设备工器具的购置费和建筑安装工程费所组成。
(F )5.GPS天线可安装在走线架、铁塔或女儿墙上,GPS 天线必须安装在较空旷位置,上方90 度范围内(或至少北向45度)应无建筑物遮挡。
( F )三.单项选择题(共20分,每空1分)1.由TD协议时隙帧标准结构决定的理想条件下最大覆盖半径为(A )kmA、11.25B、30C、40D、502.10W/20W 输出功率换算正确的是(C )A、35/38dBmB、38/41dBmC、40/43dBmD、43/45dBm3.TD-SCDMA基站的 BBU和RRU之间采用(B )连接。
无线局域网题集

无线局域网题集一、选择题1.无线局域网WLAN 传输介质是: ( )A.无线电波(正确答案)B.红外线C.载波电流D.卫星通信答案解析:A我国的火警报警电话是119。
2.无线局域网的最初协议是: ( )A . IEEE802.11(正确答案)B.IEEE802.5C. IEEE802.3D. IEEE802.1答案 A3 .现网 AP设备能支持下列哪种管理方式: ( )A. SNMPB.SSHC.WEB正确答案)D.TELNET答案 C4.室内 AP最好安装在下面哪个环境? ( )A. 强电井通风好B. 弱电井通风好(正确答案)C. 强电井通风不好D. 弱电井通不好答案 B5.802.11 协议定义了无线的 ( ) [单选题]A. 物理层和数据链路层B.网络层和MAC层C.物理层和介质访问控制层(正确答案)D.网络层和数据链路层答案 C6. 802.11b 和802.11a 的工作频段、最高传输速率分别为: ( )A. 2.4GHz、11Mbps ; 2.4GHz 、54MbpsB. 5GHz、54Mbps ; 5GHz 、11MbpsC.5GHz、54Mbps ;2.4GHz 、11MbpsD.2.4GHz 、11Mbps ; 5GHz 、54Mbps(正确答案)答案 D7.由于无线通信过程中信号强度太弱、错误率较高,无线客户端自动切换到其它无线AP的信道,这个过程称为。
( )A.关联B.重关联C.漫游(正确答案)D.负载平衡答案 C8.802.11g 规格使用哪个RF频段( )A.5.2GHzB. 5.4GHzC.2.4 GHz(正确答案)D.800 MHz答案 C9. IEEE802.11 标准在OSI 模型中的提供进程间的逻辑通信.A.数据链路层(正确答案)B.网络层C.传输层D.应用层答案 A10.无线AP 的特点不包括以下哪一个 ( )A.稳定B.高速C.覆盖范围广D.简洁性(正确答案)答案 D11.以下哪一项不是胖 AP入网需要配置的参数?( )A.IP 地址B.DNS服务器地址(正确答案)C.默认网关地址D.子网掩码答案 B12.无线局域网中最常用的标准是:A. IEEE 802.1B. IEEE 802.3C. IEEE 802.11D. IEEE 802.1513.IEEE 802.11n标准工作在哪些频段?A. 仅2.4GHzB. 仅5GHzC. 2.4GHz和5GHzD. 1GHz以下14.以下哪个标准不属于Wi-Fi标准系列?A. IEEE 802.11aB. IEEE 802.11bC. IEEE 802.11gD. IEEE 802.15.415.IEEE 802.11a标准使用哪种调制技术?A. DSSSB. FHSSC. OFDMD. CDMA16.IEEE 802.11b标准最高支持多少Mbps的数据速率?A. 1 MbpsB. 11 MbpsC. 54 MbpsD. 600 Mbps17.以下哪个选项是Wi-Fi 6的标准名称?A. IEEE 802.11acB. IEEE 802.11adC. IEEE 802.11axD. IEEE 802.11be18.IEEE 802.11g标准与哪个标准向后兼容?A. IEEE 802.11aB. IEEE 802.11bC. IEEE 802.11b和IEEE 802.11a(部分)D. IEEE 802.11n19.以下哪个标准主要用于个人区域网络(WPAN)?A. IEEE 802.11B. IEEE 802.15.4C. IEEE 802.3D. IEEE 802.1620.IEEE 802.11标准中,用于无线局域网的安全协议是?A. WEPB. WPAC. WPA2D. TKIP21.以下哪个标准支持最高达6.75Gbps的数据速率?A. IEEE 802.11nB. IEEE 802.11acC. IEEE 802.11ax(Wi-Fi 6)D. IEEE 802.11be(Wi-Fi 7)22.IEEE 802.11标准中,哪个子标准使用5GHz频段?A. IEEE 802.11aB. IEEE 802.11bC. IEEE 802.11a和IEEE 802.11n(5GHz部分)D. IEEE 802.11g23.以下哪个选项不属于Wi-Fi网络的组成部分?A. 接入点(AP)B. 无线网卡C. 以太网交换机D. 分布式系统(DS)24.IEEE 802.11标准中,用于解决隐藏节点和暴露节点问题的机制是?A. RTS/CTSB. CTS/RTSC. CSMA/CAD. DSSS25.以下哪个选项不是Wi-Fi 6(IEEE 802.11ax)引入的新特性?A. OFDMAB. MU-MIMOC. DSSSD. Target Wake Time (TWT)26.IEEE 802.11标准中,用于无线局域网的基本服务集标识符是?A. BSSIDB. SSIDC. BSSID和SSIDD. MAC地址27.以下哪个标准支持高达9.6Gbps的数据速率?A. IEEE 802.11acB. IEEE 802.11axC. IEEE 802.11be(Wi-Fi 7)D. IEEE 802.11ad28.IEEE 802.11标准中,哪种方式用于减少冲突并提高网络效率?A. RTS/CTSB. CSMA/CDC. CSMA/CAD. FHSS29.以下哪个选项是Wi-Fi网络的物理层技术之一?A. TCP/IPB. HTTPC. OFDMD. DNS30.IEEE 802.11ac标准主要用于哪个频段?A. 2.4GHzB. 5GHzC. 6GHzD. 2.4GHz和5GHz31.以下哪个标准定义了无线局域网的媒体访问控制层(MAC)和物理层(PHY)?A. IEEE 802.1B. IEEE 802.3C. IEEE 802.11D. IEEE 802.1532.以下哪种拓扑结构在无线局域网中最常见,用于将多个设备连接到网络?A. 网状结构B. 星型结构C. 蜂窝状结构D. 总线型结构答案:B33.在无线局域网中,所有节点都直接连接到中心节点的拓扑结构是?A. 环形结构B. 星型结构C. 树状结构D. 分布式结构答案:B34.以下哪种拓扑结构在无线局域网中通过无线链路连接多个独立网络?A. WDS无线分布系统B. D-HOC拓扑C. DS分布式系统D. Mesh网络答案:A35.Mesh网络中,负责连接到有线网络的AP角色被称为?A. MPPB. MPC. MAPD. BSS答案:A36.哪种拓扑结构适用于节点按环形连接,每个节点连接两个相邻节点的场景?A. 环形拓扑B. 星型拓扑C. 总线拓扑D. 树状拓扑答案:A37.以下哪种结构是由一个或多个BSS组成的?A. BSSB. ESSC. BSSIDD. WDS答案:B38.在无线局域网中,用于标识AP管理的BSS的是?A. SSIDB. BSSIDC. APIDD. DSID答案:B39.以下哪种拓扑结构通过无线链路连接两个或多个独立的无线局域网?A. 星型拓扑B. 总线拓扑C. Mesh网络D. P2P拓扑答案:D(但注意,P2P通常是WDS的一种形式,这里为符合选项格式而给出)40.在WDS点对点拓扑结构中,对接的AP应使用什么?A. 不同的信道B. 统一的信道C. 不同的频段D. 随机的频段答案:B41.以下哪个不是无线局域网中常见的拓扑结构?A. 环形拓扑B. 蜂窝状结构C. 星型拓扑D. 总线型结构答案:B(虽然蜂窝状结构在移动通信中有应用,但不是无线局域网中的常见拓扑)42.Mesh网络中,处于中间位置的AP角色被称为?A. MPPB. MPC. MAPD. BSS答案:B43.以下哪种拓扑结构在无线局域网中通过无线链路实现网络互通?A. 环形拓扑B. 总线拓扑C. WDS无线分布系统D. 星型拓扑答案:C44.哪种拓扑结构适用于远距离无线连接,如城市间的无线连接?A. WLANB. WMANC. WPAND. WWAN答案:D45.以下哪个术语表示无线局域网的基本服务集?A. SSIDB. BSSC. BSSIDD. WDS答案:B46.Mesh网络中,负责连接STA的AP角色被称为?A. MPPB. MPC. MAPD. BSS答案:C47.在无线局域网中,以下哪种拓扑结构没有中心节点?A. 星型拓扑B. 总线拓扑C. D-HOC拓扑D. 树状拓扑答案:C(D-HOC拓扑通常没有固定的中心节点)48.以下哪种拓扑结构通过无线链路连接多个网络,并形成一个网状结构?A. 星型拓扑B. Mesh网络C. 总线拓扑D. WDS点到多点拓扑答案:B49.在无线局域网中,用于区分不同网络的SSID是?A. 网络名称B. MAC地址C. IP地址D. 端口号答案:A50.以下哪种拓扑结构在无线局域网中通常用于大型建筑内的无线覆盖?A. 环形拓扑B. 星型拓扑C. Mesh网络D. 总线拓扑答案:C(Mesh网络特别适用于大型建筑或区域的无线覆盖)51.以下哪个术语不是用于描述无线局域网拓扑结构的?A. BSSB. WDSC. APD. ESS答案:C(AP是接入点的简称,不是拓扑结构)52.在2.4GHz频段,IEEE 802.11标准中互不干扰的信道有哪些?A. 1, 6, 11B. 2, 4, 6C. 3, 7, 10D. 5, 8, 13答案:A53.动态信道选择技术的主要目的是什么?A. 提高数据传输速率B. 减少信道间干扰C. 扩大网络覆盖范围D. 增加网络节点数量答案:B54.使用定向天线相比于全向天线,在减少干扰方面的优势是什么?A. 增加信号覆盖范围B. 提高信号方向性C. 降低设备成本D. 简化网络配置答案:B55.在无线网络中,提高信噪比(SNR)的主要目的是什么?A. 增加信道带宽B. 延长电池寿命C. 减少噪声和干扰D. 提高设备兼容性答案:C56.MIMO技术通过什么方式提高数据速率和信号质量?A. 使用单个发送和接收天线B. 利用多个发送和接收天线C. 增加信道带宽D. 改进调制方式答案:B57.波束成形技术主要用于什么?A. 增加信号覆盖范围B. 控制信号方向C. 加密无线信号D. 提高设备功率答案:B58.信道绑定可能带来的主要问题是什么?A. 降低信号质量B. 减少带宽C. 增加干扰风险D. 提高成本答案:C59.在无线网络规划中,如何避免相邻AP之间的干扰?A. 使用相同的信道B. 尽可能增加AP之间的距离C. 分配相邻的信道D. 降低发射功率答案:B60.以下哪项不是减少无线网络干扰的策略?A. 信道规划与管理B. 使用低功率设备C. 增加信道数量D. 禁用不必要的无线设备答案:C61.在认知无线电网络中,频谱感知技术的主要作用是什么?A. 预测网络流量B. 实时监测频谱使用情况C. 加密无线信号D. 自动调整信道带宽答案:B62.信道接入控制(MAC)层协议的主要目的是什么?A. 确保数据传输的安全性B. 管理信道接入,减少碰撞和干扰C. 扩大网络覆盖范围D. 提高设备兼容性答案:B63.在无线网络中,提高接收机灵敏度的主要目的是什么?A. 延长电池寿命B. 减少外部噪声和干扰的影响C. 增加信号覆盖范围D. 提高数据传输速率答案:B64.以下哪项技术不是用于减少无线网络干扰的?A. 信道绑定B. 信道重用规划C. 自适应调制与编码D. 干扰避免算法答案:A65.在大型无线网络中,合理规划信道重用模式的主要目的是什么?A. 增加信道数量B. 减少信号重叠和干扰C. 扩大网络覆盖范围D. 提高设备功率答案:B66.无线AP的供电方式有哪些?(多选)A. PoE供电B. DC电源适配器C. USB供电D. 太阳能供电答案:A, B67.在无线网络中,如何判断哪个信道受到的干扰最小?A. 通过环境检测工具B. 观察信号强度C. 询问网络管理员D. 随意选择一个信道答案:A68.Wi-Fi 6中的BSS Coloring技术主要用于什么?A. 加密无线信号B. 提升信道复用率C. 预测网络流量D. 降低设备功耗答案:B69.以下哪项不是IEEE 802.11n的技术特点?A. 向下兼容IEEE 802.11bB. 工作于2.4G频段时,最大传输速率是600Mbit/sC. 采用双频工作模式D. 另一个名称是“Wi-Fi 5”答案:D70.在无线网络中,如何减少AP之间的信号重叠?A. 增加AP的发射功率B. 分配相邻的信道C. 合理规划AP的位置D. 禁用不必要的无线设备答案:C71.以下哪项是信道接入控制(MAC)层协议不直接管理的?A. 信道分配B. 数据加密C. 信道接入顺序D. 冲突检测和避免答案:B二、简答题1.什么是WPA3?它相比WPA2有哪些改进?答案:WPA3(Wi-Fi Protected Access 3)是Wi-Fi联盟发布的最新一代Wi-Fi安全协议。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Two New Algorithms for UMTS Access NetworkTopology DesignAlp´a r J¨u ttner∗†,Andr´a s Orb´a n∗,Zolt´a n Fiala∗September17,2003AbstractPresent work introduces two network design algorithms for planning UMTS(Universal Mobile Telecommunication System)access networks.The task is to determine the cost-optimal number and location of theRadio Network Controller nodes and their connections to the Radio BaseStations(RBS)in a tree topology according to a number of planning con-straints.First,a global algorithm to this general problem is proposed,which combines a metaheuristic technique with the solution of a specificb-matching problem.It is shown how a relatively complex algorithm canbe performed within each step of a metaheuristic method still in reasonabletime.Then,another method is introduced that is able to plan single RBS-trees.It can also be applied to make improvements on each tree createdby thefirst algorithm.This approach applies iterative local improvementsusing branch-and-bound with Lagrangian lower bound.Eventually,it isdemonstrated through a number of test cases that these algorithms areable to reduce the total cost of UMTS access networks,also compared toprevious results.Keywords:Telecommunication,Metaheuristics,UMTS,Facilities planning and design,Lagrange–relaxation∗Ericsson Research Hungary,Laborc u.1,Budapest,Hungary H-1037e-mails:{Alpar.Juttner,Andras.Orban,Zoltan.Fiala}@eth.ericsson.se †Communication Networks Laboratory and Department of Operations Research,E¨o tv¨o s University,P´a zm´a ny P´e ter s´e t´a ny1/C,Budapest,Hungary H-11171IntroductionUMTS[24],[21]stands for Universal Mobile Telecommunication System;it is a member of the ITU’s IMT-2000global family of third-generation(3G)mobile communication systems.UMTS will play a key role in creating the future mass market for high quality wireless multimedia communications,serving expectedly 2billion users worldwide by the year2010.One part of the UMTS network will be built upon the transport network of today’s significant2G mobile systems[14],but to satisfy the needs of the future Information Society new network architectures are also required.Since UMTS aims to provide high bandwidth data,video or voice transfer,the radio stations communicating with the mobile devices of the end-users should be placed more dense to each other,corresponding to the higher frequency needed for the communication.In the traditional star topology of the radio stations,i.e.all the radio stations are directly connected to the central station,this would increase the number of expensive central stations as well.To solve this problem,UMTS allows a constrained tree topology of the base stations,permitting to connect them to each other and not only to the central station.This new architecture requires new planning methods as well.As shown in Figure1the UMTS topology can be decomposed into two main parts:the core network and the access network.The high-speed core network based on e.g.ATM technology connects the central stations of the access network. These connections are generally realized with high-capacity optical cables.In this paper the focus is on planning the access network,the design of the core network is beyond the scope.The reader is referred to e.g.[20]on this topic.The access network consists of a set of Radio Base Station s(RBS nodes) and some of them are provided with Radio Network Controller s(RNC nodes). The RBSs communicate directly with the mobile devices of the users,like mobile phones,mobile notebooks,etc.,collect the traffic of a small region and forward it to the RNC they belong to using the so-called access links,that are typically mi-crowave radio links with limited length(longer length connections can be realized using repeaters,but at higher cost).In traditional GSM configuration the RBSs are connected directly to an RNC station limiting the maximum number of RBSsRBS ArrayRNCFigure1:UMTS topologybelonging to a certain RNC.To overcome this limitation the UMTS technology makes it possible for an RBS to connect to another RBS instead of its RNC. However RBSs have no routing capability,they simply forward all the received data toward their corresponding RNC station,therefore all traffic from an RBS goesfirst to the RNC controlling it.For example if a mobile phone in region A on Figure1wants to communicate with a device in region B,their traffic will be sent trough the RNC R.Only the RNC station is responsible for determining the correct route for that amount of traffic.It follows that the RBSs should be connected to the RNC in a tree topology.(There are research initiatives to provide some low-level routing capability for the RBSs and to allow additional links between RBSs,which may increase the reliability of the network.These developments are quite in early stage,hence we only deal with tree topology.) As a consequence,the access network can be divided into independent trees of RBSs,each rooted at an RNC.These trees are called Radio Network Subsystem s (RNS).Further advantage of the tree topology compared to the star topology is that the links can become shorter,which on one hand reduces the cost of the links,on the other hand it may require less repeaters in the network.Moreover,there are some additional links connecting the RNCs to each other (inter-RNC link s)and to the core network.The planning of these links are beyond the scope of this paper.For technical reasons the following strict topology constraints have to be takeninto account:•The limited resources of the RBS stations and the relatively low bandwidth of the access links cause considerable amount of delay in the communication.In order to reduce this kind of delay,the maximum number of the access links on a routing path is kept under a certain amount by limiting the depth of a tree to a small predefined value.This limit is denoted by l tree in our model.Currently,the usual value of l tree is3.•The degree of an RBS is also constrained.One simple reason is that the commercial devices have only limited number of ports.Another reason is that too many close RBSs can cause interference problems in their ra-dio interface if their connections are established through microwave links.Moreover the capacity of an RBS device also limits the number of con-nectable RBSs.Therefore in our model there can be at most d RBS RBSs connected directly to another RBSs on a lower level.It is typically a low value,d RBS=2in the currently existing devices.•The degree of RNCs(the number of RBSs connected directly to a certain RNCs)is also limited for similar reasons,it is at most d RNC.Generallyd RNC d RBS.The planning task investigated in the present paper is to plan cost-optimal access network,that is to determine the optimal number and location of the RNCs and tofind the connections of minimal cost between RNCs and RBSs satisfying all the topological restrictions.The cost of a UMTS access network is composed of two variable factors:the cost of the RNC stations and the cost of the links.For the exact definitions see Section2.Unfortunately,this planning problem is N P-hard.The problem offinding a minimal weight two-depth rooted tree in a weighted graph can be reduced to this problem.Moreover,the problem remains N P-hard even in the special case of planning a single tree with afixed RNC node.See Appendix A for the proof of this claim.A general UMTS network may contain even about1000RBSs,a powerful RNC device controls approximately at most200-300RBSs.This large numberof network nodes indicates that the planning algorithms have to be quite fast in order to get acceptable results.One possible approach to the problem described above would be to divide the set of input nodes into clusters and then create a tree with one RNC in each cluster.However,this“two-stage”solution has some significant drawbacks:first, it is very hard to give a good approximation to the cost of a cluster without knowing the exact connections.Second,it would be also a strong restriction to the algorithm searching for connections to work in static clusters of nodes created in the beginning.For these reasons a“one-stage”approach is introduced:an algorithm which creates a number of independent trees with connections simultaneously.The proposed method called Global is based on a widely used metaheuristic tech-nique called Simulated Annealing.However,it is not straightforward to apply Simulated Annealing to this problem,since the state space is very large and a rea-sonable neighborhood-relationship is hard tofind.To overcome these problems a combination of the Simulated Annealing and a specific b-matching algorithm is proposed.To make this method efficient it will be shown how the relatively complex and time-consuming b-matching method can be performed within each step of a metaheuristic process in still acceptable time.Then,a Lagrangian relaxation based lower bound computation method is presented for the problem of designing a single tree with predefined RNC node. Using this lower bound a branch-and-bound method is proposed to compute the theoretical optimal solution to this problem for smaller but still considerable large number of nodes.For bigger single-tree design tasks,a second heuristic method called Local is proposed based on an effective combination of a local search technique and the branch-and-bound procedure above.This Local algorithm can be used effectively either in circumstances when only a single tree should be designed or to improve each trees provided by the Global algorithm.Related work.Similar problems have already been examined by several au-thors,using different notations according to the origin of their optimization tasks.By adding a new virtual root node r to the underlying graph and connectingthe possible RNC nodes to r the problem transforms to the planning problem of a single rooted spanning tree with limited depth and with inhomogeneous degree constraints.There are some papers in the literature dealing with planning a minimal cost spanning tree with either of the above constraints(see e.g.[17,18, 2]),butfinding an algorithm handling both requirements is still a challenge.On the other hand,our problem can be considered as a version of facility location problems.The problem of facility location is to install some“facilities”at some of the possible places,so that they will be able to serve a number of “clients”.The objective is usually to minimize the sum of distances between the clients and the corresponding facilities while satisfying some side constraints,e.g.the number or capacity of facilities is limited.See e.g.[9,19]for more details on facility location problems and on the known algorithmic approaches.Facility location problems give a good model to the planning task of tra-ditional GSM access network topology,for it requires the design of one-level concentrators.The case of multilevel concentrators is also studied in the liter-ature,though less extensively.[22]examined the problem similar to ours,but without depth and degree constraint and with capacity dependent cost functions.[5]discusses the case of two-level concentrators,also without degree constraints.Finally,our problem can also be considered as an extension of the so-called hub location problem.In this scenario we have a given set of nodes communicating with each other and the amount of the traffic between the node pairs is given by a traffic matrix.Instead of installing a link between every pair of nodes,each node is connected to only a single special node called hub.The hubs are fully interconnected,so the trafficflow between two nodes is realized on a path of length three,where the two intermediate nodes are hubs.The task is tofind an optimal placement of hubs,where the cost is composed of the cost of the hubs and the capacity dependent cost of the links.There are several papers examining hub location problems with various side constraints and optimization objectives.A good review on this topic can be found e.g.in[16].A previous method that is able to a give solution to the problem presented in this paper can be found in[13].This algorithm called TreePlanfinds the number and the places of the RNC devices by Simulated Annealing metaheuristic and connects the nodes to the RNSs using an extension of Prim’s spanning tree algo-rithm,which respects the topological requirements on the tree.This algorithm was used as a reference method in our experimental tests.The rest of the paper is organized as follows.First,in Section 2the exactly defined planning problem is introduced.Then,in Section 3the Global algorithm for the general problem is described in detail.In Section 4the Local method is introduced for planning a single tree with one RNC.Section 5shows the re-sults of test cases of both algorithms also compared to former solutions.Finally,Appendix A gives a short proof of the N P -completeness of the problem in the special case when only a single tree with a given RNC node is planned.2Problem Definition and NotationsThe access network is modeled as a directed graph G (N,E ),where N is the set of the RBSs.For each feasible solution there exists a natural one to one mapping of the set of links to the set of edges.Each edge in E corresponds to a link between its ends and directed toward the corresponding RNC.On the other hand,this set E of directed edges determines the set of RNCs as well:a node is RNC if and only if it has no outgoing edge.In order to illustrate the logical structure of the network the notion of the level of nodes is introduced (Figure 2).Let all RNC nodes be on level 0,and let the level of an RBS station be the number of edges of the path that connects it to its controlling RNC.The level of a link is defined as the level of its end on the greater level-number.Some other important notations used in this paper is shown in Table 1.RBSRNC0. level1. level2. level3. levelFigure 2:Logical structure of the networkN the set of RBSsE the set of linksn the number of network nodesl tree the maximal depth of the treesL E,L i the set of nodes on the i-th level of the graphiE i the set of links on the i-th level of the graphl E(v),l(v)the level of the node vl E(e),l(e)the level of the edge ed RBS the maximal degree of an RBSd RNC the maximal degree of an RNCcost RNC the cost of an RNCTable1:Some important notationsThe input of the examined planning problem consists of the set N of RBSs, the cost function c link of the links(described later),the installation cost cost RNC of the RNCs and the constraints d RNC,d RBS and l tree.Moreover we are given the set R R of places of required RNCs and the set R P of places of possible RNCs. (It is useful since in many practical cases already existing networks should be extended.)The set E of links is a feasible solution to this input if•E forms a set of disjoint rooted trees,which cover the whole set N,•the depth of each tree is at most l tree,•the degree of the root of each tree is at most d RNC,•the in-degree of each other node is at most d RBS,⊆R P.•R R⊆L EThe total cost of the network is composed of the following factors.•The cost of the RNC stations.The cost of one RNC,cost RNC,means the installation cost of that particular RNC.This constant may contain otherfactors as well,e.g.the cost of the links between the RNCs can be included, assuming that it has a nearly constant additional cost for every RNC.•The cost of the access links.In this model the cost c link(i,j,l)of a link depends on its endpoints i and j and its level l.A possible further simpli-fication is to assume that c link(i,j,l)=f l·c link(i,j),where f l is a constant factor representing the weight of level l.This kind of link-cost function has two applications.First,since access links closer to the RNC aggregate more traffic,this is an elementary way to model the capacity dependent costs by giving higher cost on the lower levels.Second,it can be used to prohibit the usage of some links on some levels by setting their cost to an extremely large value.Also,it makes it possible to force a node to be on a predefined level.So,the task is tofind a feasible connection E minimizing the total cost|L E0|·cost RNC+(ij)∈Ec linki,j,l E(ij)(1)3The Global AlgorithmThe aim of this algorithm is tofind the optimum places of the RNC nodes(i.e.to decide which RBSs should be equipped with RNC devices)and to connect each RBS to an RNC directly or indirectly as described in Section2.The basic idea of the proposed approach is the following.Assuming that the level l(v)is known for each node v,the theoretically min-imal cost can be determined for that given level-distribution(see Section3.2). The algorithm considers a series of such distributions,determines the cost for each of them and uses some metaheuristic method to reach thefinal solution. From among the wide range of metaheuristic methods existing in the literature, Simulated Annealing was chosen for this purpose,but some other local search methods could also be used,e.g.the so-called Tabu Search method[11,1].3.1Using Simulated AnnealingIn this section the application of Simulated Annealing([15,1])to the problem is illustrated.To use Simulated Annealing to a specific optimization problem, an appropriate state space S corresponding to the possible feasible solutions, a neighborhood-relation between the states and a cost function of each state should be selected.The role of neighborhood-relation is to express the similarity between the elements of the state space.The neighborhood of a state s is typically defined as the set of the states that can be obtained by making some kind of local modifications on s.Then the Simulated Annealing generates a sequence of feasible solutions s0,s1,···,approaching to a suboptimal solution as follows.It starts with an arbitrary initial state s0.In each iteration it chooses a random neighbor s i+1of the last solution s i and calculates its cost c(s i+1),then decides whether it accepts this new solution or rejects it(i.e.s i+1:=s i).This iteration is repeated until a certain stop condition fulfills.If the cost of the new state c(s i+1)is lower than c(s i),the new state is always accepted.If it is higher then it is accepted with a given probability P accept de-termined by the value of the deterioration and a global system variable,the so called temperature T of the system.In this case P accept is also positive,however, it is an exponentially decreasing function of cost deterioration.In general,the state s i+1is accepted with probabilityP accept=min1,exp−c(s i+1)−c(s i)T i.The temperature decreases exponentially during the execution,i.e the tem-perature T i in the i-th iteration is given by:T i=T i−1∗fact,T0=const.where fact is the so called decreasing factor,which is a number close to1, typically0.99-0.9999.The values T0and fact are declared in the beginning of the algorithm.The short pseudo-code in Figure3illustrates the framework of Simulated Annealing.procedure Sim Ann(steps,factor,temp,s0){curcost:=cost(s0);oldcost:=curcost;while(steps>0){Choose a random neighbor s i+1of s i;curcost:=cost(s i+1);if(acceptable(curcost,oldcost,temp))oldcost:=curcost;else s i+1:=s i;i:=i+1;steps:=steps-1;temp:=temp*factor;}return s n;}Figure3:Structure of the Simulated Annealing algorithmFor an effective Simulated Annealing the following criteria should be met.The state space to be searched should be possibly small;each state should have lot of (meaningful)neighborhoods,allowing to reach the optimum in a low number of steps;the cost of a state should be determined relatively fast.None of these criteria can be fulfilled easily in case of this planning problem. The most obvious idea for the state space would be the set of all feasible con-nections.Two such connections would be neighbors,if they can be reached from each other by changing one edge.This solution violates thefirst two criteria:the state space is very large,and because of the topological constraints,each state has only few neighbors and there are a lot of local minima.Although the cost of a state can be calculated easily,since the exact connections are given in every state,this solution is not usable.Instead,we propose following idea.The state-space of Simulated Annealing is the set of all possible distributions of the nodes on the different levels of the graph.Thus a given distribution can be represented as an n-dimensional integer vector s in S.(Note that the distribution of an arbitrary state i is denoted by s i.)D={0,1,2,..,l tree},S=D n,s∈SThe state space with this selection will be much smaller than in the previous case.Two level-distributions are neighbors if they can be reached from each other trough one of the following slight modifications of the current distribution:•moving an arbitrary node onto an adjacent level upwards or downwards•swapping an arbitrary RNC with an arbitrary RBS,that is,moving an RNC to another siteThe price for the smaller state space is that the calculation of the cost of a state becomes more difficult.Section3.2shows how the cost c(s i)of a given state s i∈S can be calculated.The initial state s0of the Simulated Annealing algorithm can be any feasible state.Such a state can be constructed easily by setting each possible nodes to RNC and connecting the other nodes arbitrarily fulfilling the criteria defined in Section2.The fact that there exists no feasible solution at all can be detected, as well.3.2Finding the Exact Cost for a GivenLevel-distribution s iLet us assume that the distribution of the nodes on different levels is known.In order tofind the optimal connections for this given distribution,the connections between the adjacent levels have to be determined.The main observation is that the connections of the different levels to their parents are independent,so the task of connecting the nodes of a certain level can be performed separately for each level.(As there are l tree adjacent level-pairs,the algorithm described now has to be run l tree times in each step of the Simulated Annealing process.)Generally,for each adjacent level-pair(L i and L i+1,i=0,···,l tree−1)a connection has to be found so that•all nodes in set L i+1are covered•the maximal degree k of the nodes in set L i is given.As already mentioned, k=d RNC if i=0,k=d RBS if i>0.This can be formulated as a special b-matching problem,which can be solved in strongly polynomial time[3,7].3.2.1Bipartite b-matchingA bipartite b-matching problem is the general minimal-cost matching problem, where there is a predefined lower bound low(v)and upper bound upp(v)for the degree of each node v in a bipartite graph.Definition3.1Let G(V,E)be a bipartite graph and let low,upp:V−→N be two predefined functions on the set of nodes.A subgraph M of G is called b-matching if low(v)≤deg M(v)≤upp(v)for each v∈V.Obviously,our case is a special b-matching problem with low(v)=1and upp(v)=1for each node v∈L i+1and low(w)=0and upp(w)=k for each node w∈L i.3.2.2The Solution of the b-matching ProblemAs it was mentioned above,the problem offinding the cost of a given level-distribution can be reduced to a specific b-matching problem.In this section the solution of this b-matching problem is outlined.The detailed description of this method is skipped and only its main idea and the definition of the used notions is sketched in order to show how the b-matching algorithm can be accelerated significantly when it is called with a series of inputs such that each input only slightly differs from the previous one.Let a bipartite graph G=(L i,L i+1,E i+1),a cost function c:E i+1−→R≥0 and a degree bound k of the nodes L i be given.Definition3.2A subset M of E i+1is called partial matching if the degree of each node in L i is at most k and in L i+1at most1.A partial matching is called full matching if the degree of each node in L i+1is exactly1.Thus,the aim is tofind a c-minimal full matching.Of course,it can be supposed that k·|L i|≥|L i+1|,otherwise there cannot be a full matching.Definition3.3For a partial matching M a path P={e1,e2,...,e2t+1}is called M-alternating,if e2i∈M for all i=1,2,...,t and e2i+1∈M for all i= 0,1,...,t.Definition3.4A node v∈L i is called saturated if the degree of v in M is maximal,that is if deg M(v)=k.A node v∈L i+1is saturated if M covers it, that is if deg M(v)=1.The most important property of M-alternating path is that if there exists an M-alternating path P between two non-saturated nodes,then a partial matching with one more edge can be found by“flipping”the edges of the path P.More exactly M :=(M\P)∪(P\M)is again a partial matching and|M |=|M|+1. It also holds that if a partial matching is not maximal,then it can be extended through alternating paths.Definition3.5A real functionπ(u)defined for each node u∈L i∪L i+1is called a node potential:π:L i∪L i+1→RA givenπis called c-feasible or simply feasible ifπ(v)≤0∀v∈L i(2)and the conditionπ(x)+π(y)≤c xy(3) holds for every edge(x,y)∈E i+1.If inequality(3)is actually an equation,the⊆E i+1denote the set of edge(x,y)∈E i+1is called an equality edge.Let Eπi+1all equality edges with respect to the potentialπ.The following theorem is also fundamental in matching theory.Theorem3.6A full matching M is c-minimal if and only if there exists a fea-sible potentialπfor which all edges in M are equality edges.The algorithm is based on this theorem.It stores a feasible potentialπand a partial matching M⊆Eπ,i.e.a partial matching having only equality edges.i+1If M is a full matching then it is optimal.If it is not,then in each iteration the algorithm eitherfinds a partial matching having one more edges or“improves”the potentialπ.The algorithmfinds an optimal full matching in O(n3)steps in full bipartite graphs.3.2.3Acceleration of the AlgorithmThe b-matching algorithm described in Section3.2should be run in each step of the Simulated Annealing for all adjacent level-pairs.Because the complexity of the b-matching algorithm is O(n3)this process is quite time-consuming.This section introduces an idea to accelerate the whole algorithm significantly,so that it can solve even large inputs in acceptable time.Considering that in each transition only a minor part of the level distribution changes,therefore a significant part of the former connections can be reused in the next step.The possible changes are:•a node is deleted•a new node is added•a node is moved from the set L i to L i+1or vice versa.The idea is,that after making a modification to the level-distribution,a better initial potentialπand initial partial matching M can be used instead of the zero potential and the empty matching.If a node is deleted,the previous potential resulted by the algorithm remains feasible so it does not need to be modified.If a new node v is added,it is easy tofind an appropriate potentialπ(v)for this new node in such a way that(2) and(3)hold.Moving a node is a combination of a deletion and an addition.Furthermore,a significant part of M can be reused,too,only the edges which ceased to be equality edges after the modification must be deleted.These improved initial values make it possible to reduce the running time efficiently,since there is no need to calculate all connections again from the be-ginning.Section5shows that this acceleration makes the algorithm significantly faster,nearly square-wise to the number of input nodes.It enables us to run the quite difficult b-matching algorithm in each step of the Simulated Annealing process.4The Single-Tree ProblemIn practical planning problems it is often the case that—for geographical,polit-ical or economical reasons—the exact number and location of the RNC nodes and the set of RBSs belonging to them is already known in the beginning.For these reasons in this section we discuss the special problem where only one fixed RNC and a set of RBS nodes are given.Of course the Global algorithm can solve this special case,as well,but an alternative method called Local algorithm, whichfinds remarkably better solutions,is introduced.Although this algorithm is slightly slower than the Global algorithm,it is efficient for about200-300nodes, which is the typical number of RBSs controlled by one RNC.The Local algorithm is based on a branch-and-bound method thatfinds the exact optimal solution for smaller inputs(40-50nodes).To sum up,the Local algorithm can be used for the following purposes.•Planning a tree of RBSs belonging to afixed RNC.•Improving the trees created by an arbitrary previous algorithm.•Determining the real optimum for smaller inputs.The simplified single-tree problem can be formulated as follows.A single RNC and n−1RBSs are given by their coordinates.Note that the problem of positioning the RNC is omitted in this model.The task of the algorithm is to connect all the RBSs directly or indirectly to the RNC.These。
