第三学期第四章VTP
cisco第三学期final_stu
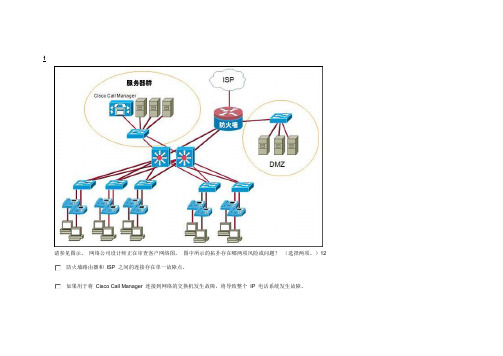
1请参见图示。
网络公司设计师正在审查客户网络图。
图中所示的拓扑存在哪两项风险或问题?(选择两项。
)12防火墙路由器和ISP 之间的连接存在单一故障点。
如果用于将Cisco Call Manager 连接到网络的交换机发生故障,将导致整个IP 电话系统发生故障。
使用第 3 层交换机将数据中心服务器与IP 电话机相连会导致延时过大。
需要采用冗余方式将IP 电话机连接到交换机,以防止接入层形成故障点。
如果一台第 3 层交换机发生故障,Cisco Call Manager 将不可达。
2网络工程师正在客户现场。
解决网络中的技术问题后,工程师为支持人员提供培训课程。
以下哪项工作职能与此类网络工程师的活动最相符?4网络设计师客户经理售前工程师售后现场工程师3下列哪个值是IPv6 地址2001:DB80:0000:0000:0C41:3EFF:FE00:0000 的另一种表达方式?32001:DB8::C41:3EFF:FE:2001:DB80::C41:3EFF:FE00::2001:DB80::C41:3EFF:FE00:02001:DB80:0:0:0:C41:3EFF:FE::4请参见图示。
SW11 上已启用的所有接口的生成树角色是什么?3 备用备份指定根5某公司的帮助台员工不太熟悉VPN。
为了使帮助台能够支持远程工作人员进行安全的远程访问,网络设计师必须将以下哪两项功能或技术定为培训内容?(选择两项)35QoS 工作原理VLAN 配置隧道协议IPv6 和IPv4 双协议栈加密算法帧中继配置6可在无线网络中广播什么信息来帮助用户连接网络并使用无线服务?1SSIDWEP 密钥VLAN 参数WPA 加密密钥VPN 身份验证信息7需要将一个配置文件从TFTP 服务器加载到路由器的RAM 中。
管理员在完成此任务前应该了解什么信息?2 路由器的IP 地址和TFTP 服务器所用的操作系统TFTP 服务器的IP 地址服务器上的配置文件的名称路由器的IP 地址和NVRAM 中路由器配置文件的名称TFTP 服务器的IP 地址和路由器上的配置寄存器的值8配置帧中继时,是什么标识WAN 交换机的虚电路?4LMICPEPVCDLCI9在实施安全策略时,安全检查列表中应当包括下列哪两项操作?(选择两项)45禁用所有日志。
(2021年整理)思科网络第三学期期末考试试题1
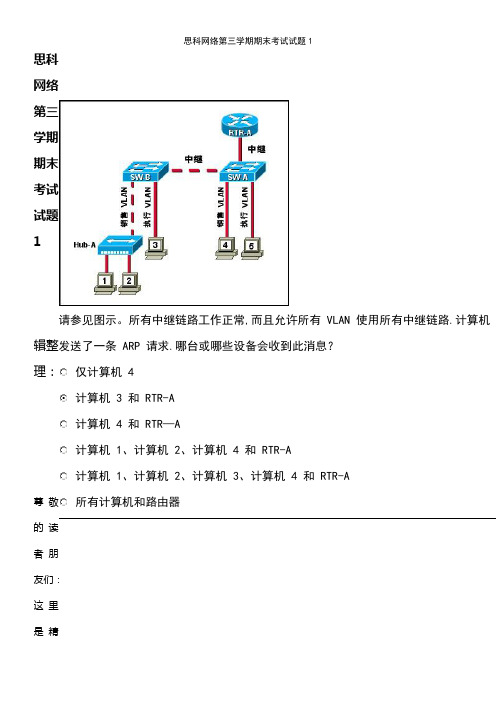
网络第三学期期末考试试题1辑整理:尊敬的读者朋友们: 这里是精请参见图示。
所有中继链路工作正常,而且允许所有 VLAN 使用所有中继链路.计算机发送了一条 ARP 请求.哪台或哪些设备会收到此消息?仅计算机 4计算机 3 和 RTR-A计算机 4 和 RTR —A计算机 1、计算机 2、计算机 4 和 RTR-A计算机 1、计算机 2、计算机 3、计算机 4 和 RTR-A所有计算机和路由器档编辑中心,本文档内容是由我和我的同事精心编辑整理后发布的,发布之前我们对文中内容进行仔细校是难免会有疏漏的地方,但是任然希望(思科网络第三学期期末考试试题1)的内容能够给您的工作和学来便利。
同时也真诚的希望收到您的建议和反馈,这将是我们进步的源泉,前进的动力。
本文可编辑可修改,觉得对您有帮助请收藏以便随时查阅,最后祝您生活愉快业绩进步,以下为思科网络第三学期期末考试试的全部内容。
下列关于在接入点上启用开放式身份验证的陈述,哪一项是正确的?不需要身份验证使用 64 位加密算法需要使用身份验证服务器需要共同商定的密码请参见图示。
该交换机用于让图中所示部门的成员实现连接,但不存在路由。
连接到 Fa0/2的一位用户应该能够与 accounting VLAN 中的用户通信.下列哪项更改可实现所需通信?将该用户连接到 Gi0/1。
将该用户连接到 Fa0/6。
将该用户添加到本征 VLAN。
将该用户添加到默认 VLAN。
分层网络模型具有哪三项优点?(选择三项.)Option 1,36带宽争用现象减少物理布局范围减小网络的容错能力提高无需配线间无需第三层功能管理和故障排除工作简化下列关于新交换机默认配置的说法中哪三项正确?(选择三项。
)Option 3,46禁用了生成树协议.使能口令被配置为 cisco。
所有交换机端口都被分配给 VLAN1。
闪存目录中包含 IOS 映像。
VLAN1 配置有管理 IP 地址.所有接口均设置为自动协商速度和双工模式。
visual pc在高职网络安全实训课程中的应用

关键 词 : sap ; 拟机 ; Vi l c虚 u 网络 安 全 ; 实训课 程 ; 用 应
中 图分 类 号 : 3 30 TP 9 . 8
文献标识码 : A
拟 机 软 件 利 用 某 台 真 实 的计 算 机 上 的物 理 硬 件 虚 拟 出来 的 , 用 方 法 与 真 实 计 算 机 一 样 , 可 以 自行 设 置 的 条 件 使 且 更 多 。 由 于直 接 使 用 了 X8 6的 保 护 模 式 , 供 了 对 系 统 提
硬 件 的 访 问 能 力 , 拟 机 在 性 能 上 有 十 分 出 色 的 表 现 。 它 虚
文 章 编 号 : 6 27 0 ( 0 1 0 — 1 30 l 7 ~ 8 0 2 1 ) 20 2 —2
文件 , 拟 机 在 硬 盘 上 的操 作 只在 这 个 文 件 上 进 行 ; 可 虚 ②
1 计 算 机 实训 室 的现 状 与 问题 的提 出
学 校 学 生 越 来越 多 , 上 经 费 不 足 , 致 实 训 室 的 建 加 导 设 远 根 不 上 课 程 开设 的需 要 。某 些 网络 安 全 实 验 , 木 马 如 入侵 、 站攻击 , 网 病毒 测试 等 破 坏 性 实 验 , 一 般 的机 房 中 在 无 法 进 行 。一 些跨 系 统 的 网站 攻 防原 理 及 技 巧 , 法 在 课 无 堂 上 演 示 , 生 也无 法通 过 普 通 实 验 更 进 一 步 加 深 理 解 。 学 高 职 学 院 在 国家 投 资 较 少 的情 况 下 , 投 资 大 量 资 金 要 新 建计 算 机 网 络安 全 实 验 室 是 不 现 实 的 , 何 要 解 决 上 述 如 矛 盾 呢 ?应 用 虚拟 计 算 机 ( 以下 简 称 虚 拟 机 ) 能 使 矛 盾 就
大英unit4 a virtual life

Unit 4 warming up-1
• • • • • 1 check the listening task on P.89 Key: 1 An employee 2 Surfing the net 3 He acted all surprised, as if he didn’t know why the computer had died suddenly
Warm up-3/Advantages and disadvantages of internet-5
• Disadvantages • Theft of Personal information • If you use the Internet, you may be facing grave danger as your personal information such as name, address, credit card number etc. can be accessed by hackers, or even cyber criminals to make your problems worse. • Spamming • Spamming refers to sending unwanted e-mails in bulk, which needlessly obstruct the entire system. Such illegal activities can be very damaging, so instead of just ignoring it, you should make an effort to try and stop these activities so that using the Internet can become that much safer.
1带翻译

1、1、金融用语:受取手形:应收票据;外貨ポジジョン:外汇头寸;公定歩合:法定贴现率;最割引率:再贴现率;つなぎ融資:过渡性融资;変動為替レート:浮动汇率2、股市用语:上げ幅:升幅;先安:看跌;そこを割る:跌破最低大关;持ち合い:暂告平息;軟調:疲软3、缩略语:ADBゕジゕ開発銀行(亚洲开发银行);CIEC 国際経済協力会議(国际经济合作会议);GA TT関税貿易一般協定(国际关税和贸易总协定);FAO 国連食料農業機構(联合国粮农组织);IMF 国際通貨基金(国际货币基金组织);JICA国際協力事業団(日本国际事业协力团)OPEC石油輸出国機構(石油输出国组织);UNDP国連開発計画(联合国开发计划署)一、经济类文章○円の国際化変動相場制の第二の不均衡は、日本の貿易収支の大幅な黒字である。
確かに第二次石油ショックの直後こそ貿易収支は赤字またはわずかな黒字だったが、数年後には大幅黒字が復活している。
79年の第二次石油ショックの後も、79-80年こそ、貿易収支は20億ドル前後の赤字、経常収支は大幅の赤字だったが、81年以降再び黒字を増やし、83年には経常収支も黒字となった。
85年、86年は貿易収支各461億ドル、828億ドル、経常収支は各350億ドル、492億ドルの黒字である。
普通ならとっくに円高となってよさそうだが、そうならなかったのは、日本からゕメリカへ莫大な金利稼ぎの長期資本が流出したからである。
この時期の貿易黒字の急増は、日本の輸出努力とともに、ゕメリカのドル高のあおりを受けたと見るのが正しいだろう。
かつては通貨レートは貿易の動きに依存していたが、現在では、資本収支の動きが大きな影響を持つようになっている。
それだけに、貿易摩擦問題が通貨レート調整によって解決する見通しは少ない。
むしろ日本側は、経常収支の黒字を対外投資の推進に振り向け、円高を避けてきた。
实行浮动汇率制度的第二个不均衡问题是日本的贸易收支顺差大幅度。
CCNA第三学期官方章节考试题之四、《VTP》(附答案)46 doc

VTP
VTP
一台配置了
VTP
VTP
2
如果将此交换机添加到已收敛的网络中,则同一个
告的
此交换机未显示配置修订版的错误。
此交换机已经与相邻设备建立了双向通信。
此交换机被配置为向同一个
此交换机被配置为允许网络管理员通过限制通向特定网络设备的流量来尽量提高带宽。
模式
域口令
版本号
4
所有交换机均会收到更新并同步
仅交换机
SW3
仅交换机
该交换机会以
该交换机会以
该交换机会以
该交换机会以6
S2
S2
S2
当电缆重新接好时,
无法在处于透明模式的交换机上创建
服务器模式交换机既不会侦听透明模式交换机发出的
在透明模式交换机上创建的
其它交换机上没有为新的
透明模式中的交换机不会转发8
交换机必须通过接入链路互连。
必须将交换机
必须将该两台交换机配置为
必须采用同一个
必须采用同一个
只能接受
可以创建并接受更新后的
只能传递
可以向域中添加
无法添加
10
Switch1
Switch1
Switch2
Switch1
Switch1 12在
14下
它检验了已配置的它检验了
它检验了是否在交换它检验了。
思科网络第三学期期末试题及答案

1 窗体顶端请参见图示。
下列哪三种说法描述了Host1 和Host2 无法通信的原因?(选择三项。
)交换机端口处于不同的VLAN 中。
交换机的IP 地址在错误的子网中。
主机被配置在不同的逻辑网络中。
需要路由器在Host1 与Host2 之间转发流量。
每个VLAN 中的VLAN 端口必须连续分配。
主机的默认网关地址必须处于同一个逻辑网络中。
2 窗体顶端请参见图示。
主机PC_A 和主机PC_B 同时发送流量,来自这两台发送站的帧发生了冲突。
最后收到冲突台设备?集线器HB1交换机SW1路由器R1交换机SW2路由器R2交换机SW43 窗体顶端请参见图示。
在生成树协议中,“学习”表示什么意思?交换机正在发送并接收数据帧。
交换机并未接收BPDU,但正在发送并接收数据。
交换机正在通过转发收到的BPDU 参与选举过程。
交换机正在接收BPDU 并填充MAC 地址表,但并未发送数据。
4 窗体顶端请参见图示。
RTB 被配置为进行传统的VLAN 间路由。
RTB 可以ping 通计算机 A 但无法ping 通计算障的原因可能是什么?Fa0/11 端口处于错误的VLAN 中。
RTB 上没有有效的路由协议。
计算机B 的IP 地址在错误的逻辑网络中。
路由器的Fa0/1 接口上配置了错误的中继封装类型。
窗体底端5 窗体顶端请参见图示。
网络管理员已将网络划分为两个VLAN,R1 和S1 的配置如图所示。
但是,PC1 无法访问P 可能出在哪里?R1 上未配置路由协议。
S1 的Fa0/1 端口不是中继端口。
S1 上未设置默认网关地址。
S1 和R1 之间只配置了一条物理链路用于VLAN 间路由。
6 窗体顶端单臂路由器VLAN 间路由有哪三项特征?(选择三项。
)需要使用VTP需要使用子接口减少广播域的数量使用过多VLAN 时会影响性能需要在路由器和至少一台交换机之间采用接入链路比用于VLAN 间路由的其它方法更加经济规定至少要在路由器和交换机之间使用两个交换机端口7 窗体顶端请参见图示。
《学生成绩信息管理系统程序设计》说明书

《VC++程序设计》课程卷二实践考核方案VC++程序设计设计说明书设计题目:学生学习成绩管理程序姓名:郭达学号:20090450110班级:09计本指导教师:苏秀芝完成日期:2010-6-22VC++程序设计设计要求内容要求VC++程序设计1、项目数据库的设计说明2、项目使用框架的说明3、项目实践中的心得体会目录第一章系统分析 (3)第二章系统设计 (4)2.1系统功能分析 (4)第三章数据库设计 (4)3.1数据库需求分析 (4)3.2数据库的建立 (3)3.3创建数据源 (3)3.4使用MFC AppWizard选择数据源 (3)3.5设计浏览记录界面 (3)3.6ODBC数据表绑定更新 (3)3.7添加“查询、添加、编辑、删除”功能 (3)3.8菜单栏编辑 (3)3.9状态栏设置 (3)3.10编译并运行 (3)第四章总结 (5)参考文献 (6)学生成绩信息管理系统设计说明书第一章系统分析当今时代是飞速发展的信息时代,在各行各业中都离不开信息处理,这正是计算机被广泛应用于管理信息系统的环境。
计算机的最大好处在于利用它能够进行信息管理。
使用计算机进行信息控制,不仅提高了工作效率,而且大大的提高了其安全性。
尤其对于复杂的信息管理,计算机能够充分发挥它的优越性。
而且只要系统的设计合理,就可以为老师们提供更简单的操作平台来管理复杂的学生成绩,借助数据库管理技术,实现学生管理的规范化和人性化。
相比传统书面记录,网络管理有着以下优点:◎降低成本:由于管理系统是通过互联网将学生的信息记录到一起,加强各系部与总部的信息交流,大大降低了人力成本、管理成本,使老师能够及时对学生学习中出现的问题进行解决。
◎提高控制力度:管理系统可以加强成绩记录控制,减少人为错误,使每一个学生都可以记录正确,使管理更完善。
◎减少操作误差:记录的自动化管理,可以在业务操作时录入,保证数据的真实性。
多种业务单据自动生成和权限控制,减少操作上的人为误差。
乐写数位板操作指南

目 录目 录 (1)第一章 产品概述 (2)第二章 基本说明 (2)2.1 产品示意图 (2)2.2 系统要求 (3)2.3 数位板说明 (3)2.3.1指针功能 (3)2.3.2按键功能 (3)2.3.3压力感应 (3)2.4数位笔说明 (4)2.4.1笔尖双击 (4)2.4.2按键功能 (4)2.4.3笔的卷页功能 (4)2.4.4数位笔的置放 (4)2.4.5数位笔充电 (5)2.4.6数位笔睡眠 (5)2.4.7校准方法 (5)2.4.8更换笔芯 (6)第三章 驱动安装 (6)3.1 下载及安装驱动程序 (6)3.2 卸载驱动 (6)3.2.1通过开始菜单卸载 (6)3.2.2通过控制面板卸载 (6)第四章 在Windows操作系统下使用 (7)4.1 数位板连接 (7)4.2设备连接提示 (7)4.3数位板指示灯状态指示 (8)4.4 工作区域设置 (9)4.4.1使用多个显示器 (9)4.4.2设置工作区域 (10)4.4.3旋转工作区域 (10)4.5 数位板快捷键功能设置 (11)4.6 数位笔设置 (13)4.6.1笔按键设置 (13)4.6.2笔尖感应设置 (14)4.6.3当前压力感应测试 (14)4.6.4双击时笔尖间距 (14)4.6.5启用Windows Ink功能 (14)4.7关于数据导出和导入 (15)第五章 规格参数 (16)第六章 常见问题 (17)第一章 产品概述本产品具有压力感应功能,使用本产品绘图时,笔迹会随着您控制压感笔按施压力的大小而产生粗细或浓或淡变化,即所谓压感功能。
如果配合适当的绘图软件,例如Photoshop,Painter,SketchBook等,可以让您模拟铅笔、马克笔、水彩笔、毛笔、油画笔等笔触,效果就同如在纸上或画布上绘图所展现的真实感。
本产品适用于签名、绘图及计算机等多项应用。
为了是您更好的了解和使用您的数位板,请务必在使用前仔细阅读本说明书。
粤沪版物理九年级上册第十二章第4节热机与社会发展同步练习

粤沪版物理九年级上册第十二章第四节热机与社会发展同步练习一、选择题1、下列过程中,将内能转化为机械能的是A.汽油机的压缩冲程B.水蒸气顶起水壶盖的过程C.小孩沿滑梯下滑的过程D.流星在大气层中穿行的过程答案:B知识点:能量的转化解析:解答:汽油机的压缩冲程中机械能转化为内能,故A错误;水蒸气顶起水壶盖的过程,内能转化为机械能,故B正确;小孩沿滑梯下滑的过程,机械能转化为内能,故C错误;流星在大气层中穿行的过程机械能转化为内能,故D错误。
选B。
分析:本题的易错点是压缩冲程的能量转化,从该冲程压缩发热出发便于理解它的能量转化过程。
本题考查的是能量的转化。
2、在进行下列实验或有关装置工作时,能量转化由机械能转化为内能的是()A.空气压缩引火仪的活塞压燃硝化棉B.柴油机的做功冲程C.弯折铁丝D.太阳能热水器加热水答案:AC知识点:能量的转化解析:解答:空气压缩引火仪的活塞压燃硝化棉是机械能转化为内能,故A正确;柴油机的做功冲程,内能转化为机械能,故B错误;弯折铁丝,机械能转化为内能,故C正确;太阳能热水器加热水时太阳能转化为内能,故D错误。
选AC。
分析:掌握各种形式的能之间的转化是本题的解题关键,本题考查的是能量的转化。
3、在内燃机的四个冲程中,其中把机械能转化为内能的是( )A.吸气冲程B.压缩冲程C.做功冲程D.排气冲程答案:B知识点:内燃机的四个冲程解析:解答:机械能与内能之间的能量转化主要发生压缩冲程与做功冲程,故AD错误;做功冲程,内能转化为机械能,故C错误;压缩冲程内能转化为机械能,选B。
分析:掌握各冲程能量之间的转化是本题的解题关键,本题考查的是内燃机的四个冲程。
4、关于热机,下列说法错误的是( )A.热机性能好坏的重要标志之一是热机效率B.在四冲程内燃机中减少废气带走的大量热量可以大大提高热机效率C.柴油机的效率比汽油机的高,这是因为柴油的热值比汽油的大D.在压缩冲程中内燃机将机械能转化为内能答案:C知识点:热机的效率;能量的转化解析:解答:热机效率反映了燃料完全燃烧放出能量的利用率,是热机性能好坏的的重要标志,A正确;内燃机能量损耗的主要原因之一就是废气带走的热量,所以减少废气带走的热量可以提高热机的效率,故B正确;柴油机的效率高于汽油机是因为柴油机的压缩比大,燃料燃烧更充分,而不是柴油机的热值高,故C错误;压缩冲程是机械能转化为内能,故D 正确。
ccna第三学期1-7套练习题答案(最新)

ESwitching Chapter 1 - CCNA Exploration: LAN 交换和无线(版本4.0)1、分层网络设计模型中的哪一层称为互连网络的高速主干层,其中高可用性和冗余性是该层的关键?A.接入层B. 核心层C. 数据链路层D. 分布层E. 网络层F. 物理层2、分层网络设计模型中的哪一层提供了将设备接入网络的途径并控制允许那些设备通过网络进行通信?A. 应用层B. 接入层C. 分布层D. 网络层E. 核心层3、分层设计模型中的哪一层使用策略来控制网络流量的流动并通过在虚拟局域网 (VLAN) 之间执行路由功能来划定广播域的边界?A. 应用层B. 接入层C. 分布层D. 网络层E. 核心层4、从传统的公司网络架构迁移到完全融合网络后,很可能产生什么影响?A. 可将本地模拟电话服务完全外包给收费更低的提供商B. 以太网 VLAN 结构会简化C. 会形成共享的基础架构,因此只需管理一个网络。
D. QoS 问题会大大减轻5、语音数据流和视频数据流争夺带宽的问题会减轻。
应该在分层网络的哪一层或哪几层实现链路聚合?A. 仅核心层B. 分布层和核心层C. 接入层和分布层D. 接入层、分布层和核心层6、下列哪种说法正确描述了模块化交换机?A. 外形纤细B. 允许通过冗余背板进行交换机互连C. 物理特性固定D. 特性灵活多变7、下列哪项功能可在交换网络中通过合并多个交换机端口来支持更高的吞吐量?A. 收敛B. 冗余链路C. 链路聚合D. 网络直径8、在处于不同的 VLAN 中的设备间配置通信需要使用 OSI 模型中的哪个层?A. 第 1 层B. 第 3 层C. 第 4 层D. 第 5 层9、企业级交换机有哪两项特点?(选择两项。
)A. 端口密度低B. 转发速度高C. 延时水平高D. 支持链路聚合E.端口数量预先确定10、Cisco 三层式分层模型中的三层都支持哪两项功能?(选择两项。
)A. 以太网供电B. 在冗余中继链路之间进行负载均衡C. 冗余组件D. 服务质量E. 链路聚合11、网络管理员选择的交换机将在网络核心层工作。
pink stick luv

omou dakede shiawase na no honto wa chotto setsunai
口を出る强がり 见抜いて寂しがり
kuchi wo deru tsuyogari mimeite samishigari
実はもう限界越えてんの だけど言えるはずない 言えるわけない
Say yeah手を繋ぎたいキスをしたい
Say yeah te wo tsunagitai kisu wo shitai
君と半径10メートル以内
kimi to hankei juu meetoru inai
でも叶わないだから妄想で
demo kanawanai dakara mousou de
Ye Yo! Sunday Monday ちゅーして ぎゅーして
Ye Yo! Sunday Monday chuushite gyuushite
毎日 クリンチ 射抜いてけ穷地
mainichi kurinchi imeiteke kyuuchi
健気さCutey
kenagesa Cutey
神様お愿い ちょっとでいいから 勇気をください 「カジキマグロ」
kamisama onegai chotto de ii kara yuuki wo kudasai "kajiki maguro"
すれ违ったり
sure chigattari
ふと目と目が交わるだけで
futo me to me ga majiwaru dakede
宙に浮いてる気分になる
chuu ni uiteru kibun ni naru
A communication virtual machine

A Communication Virtual MachineYi Deng, S. Masoud Sadjadi, Peter J. Clarke, Chi Zhang, Vagelis Hristidis, Raju Rangaswami, and Nagarajan Prabakar Technical Report: FIU-SCIS-2006-02 School of Computing and Information Sciences Florida International UniversityAbstractThe convergence of data, voice and multimedia communication over digital networks, coupled with continuous improvement in network capacity and reliability has significantly enriched the ways we communicate. However, the stovepipe approach used to develop today’s communication applications and tools results in rigid technology, limited utility, lengthy and costly development cycle, difficulty in integration, and hinders innovation. In this paper, we present a fundamentally different approach, which we call Communication Virtual Machine (CVM) to address these problems. CVM provides a user-centric, modeldriven approach for conceiving, synthesizing and delivering communication solutions across application domains. We argue that CVM represents a far more effective paradigm for engineering communication solutions. The concept, architecture, modeling language, prototypical design and implementation of CVM are discussed. Keywords: Model driven, communication application, multimedia, middleware, telemedicine.1. IntroductionCommunication is the most fundamental function of business, government and society at large. In recent years, the convergence of data, voice, and multimedia over digital networks coupled with the continuous improvement in network capacity and reliability has enabled a wide range of communication applications. Examples range from general-purpose communication applications such as VoIP telephony, voice, video or multimedia conferencing to specialized applications such as disaster management and telemedicine. The pace of innovation of new communication applications will undoubtedly accelerate further as both capacity and demand increase. When we exam this trend a little further, however, it reveals several major issues. First, today’s communication tools are developed in stovepipe fashion with limited separation between application needs and logic, device types and underlying networks.The combined complexity of these aspects results in high cost and a lengthy development cycle. Second, such vertically developed systems typically have fixed functionality and interface and do not interoperate with each other (because of differences in design, architecture, API, and network/device assumptions). It is difficult to adapt the systems to fit changing user needs, the dynamics of underlying networks, and new device and network technologies [17]. Users, particularly sophisticated domain specific users, are forced to hop between tools to satisfy their communication needs. Third, the fragmented development approach poses major challenges in integration and in providing integrated communication solutions. Last but not the least, it hinders the development of new communication tools, particularly for domain specific applications (e.g., telemedicine), because of the complexity, cost, and lengthy cycle required of vertical development. In this paper, we present a fundamentally different approach for engineering communication solutions. This approach, which we call Communication Virtual Machine (CVM), represents a paradigm shift on how a communication application is conceived and delivered. We argue that the CVM approach provides the basis to effectively address the problems discussed above. The design of CVM draws from the concepts of model-driven engineering [1,25], communication middleware [23] and middleware-based architecture [24]. However, by focusing on the communication domain only, CVM achieves high degree of automation and effectiveness, and avoids the pitfalls of many general purpose methods and techniques for modeldriven engineering that are overreaching and consequently ineffective. Furthermore, the CVM approach goes far beyond the goals of communication middleware towards end-to-end communication solutions. (See Section 7 for more in depth discussion of related work.) As opposed to stovepipe development, which will inevitably leads to repetitive and incompatible designs, and costly, lengthy and error-prone developments, CVM provides a model-driven process for conceiving, structuring, synthesizing and delivering1communications that are tailor-made for user or application needs. In CVM, general purpose or domain specific communication needs are specified in a model, called communication schema, independent of device types and underlying network configuration. Such a model is instantiated, negotiated, synthesized and executed, by a fully automated process, to satisfy the users’ communication needs. Since even a sophisticated communication model can be built in terms of hours or days, rather than months or years needed for designing and implementing a major communication application (e.g., telemedicine) CVM provides an effective way to support user-centric ondemand communications. (As discussed later, the ondemand feature of the CVM is also reflected by its ability to change the communication model at runtime.) This model-driven communication is supported by the CVM layered architecture (Section 3). These layers are common to and shared by different communication applications. This architecture separates and encapsulates major concerns of communication modeling, synthesis, coordination, and the actual delivery of the communication by the underlying network and devices, into self-contained compartments with clear interface and responsibility. We will show that this architectural principle of separation of concerns employed in CVM is the basis for its automation and flexibility. This is because system components and communication protocols common to different applications can be identified and shared without having to be hard coded into a stovepipe system. This will also enable the CVM architecture to be independent of the underlying networking infrastructure and communication devices. Coupled with the CVM architecture are several major components, together forming the CVM system (Section 4): A communication modeling language providing an intuitive graphic form for users (or user organizations) to model declaratively their communication requirements; a synthesis engine responsible for negotiating and synthesizing user communication sessions; a communication engine for executing user communication logic; and network communication broker to interfacing with the underlying network infrastructure. A prototypical design of the CVM is implemented and fully functional (Section 5 and 6). In addition to supporting general purpose communication functions (e.g., multimedia conferencing), we have worked with physicians and technical staff at the Miami Children’s Hospital (MCH) and the Teges Corporation, which supplies MCH with its patient medical information system called i-Rounds©. We have conducted case studies of using the CVM to support communicationbetween doctors involved in cardiovascular operations based on scenarios and criteria formulated by the doctors. We have demonstrated that it took less than a day to discuss, formulate and structure the telemedicine scenarios into CVM communication schemas; and it took two graduate students in a week to integrate the CVM system with the i-Rounds patient information systems, which transforms a general purpose CVM into a communication platform capable of supporting a variety of telemedicine communications with structured exchange of patient medical information.2. A Motivating ExampleLet us consider the following scenario: Eric is a general practitioner who is examining one of his patients. He observes an unusual symptom and decides to call Mary, who is a specialist. During their conversation, Mary calls John, who is a researcher working in a medical laboratory, and asks him to join the call. This turns the two-way call into a conference call. Eric then decides to share parts of his patient’s record with Mary and John and show them some related images. This turns the voice conference into a multimedia telemedicine application. Clearly, carrying out this scenario is possible with today’s technology. For instance, Eric would first place a phone call to reach Mary. Next, assuming Mary’s phone has conferencing capability, she switches to a conference call to include John in a three-way conversation. Otherwise, they have to use a conferencing application such as Yahoo! Messenger. Eric would then use a separate custom developed telemedicine application for sharing the patient’s record with Mary and John. In case either Mary or John does not have access to such a custom application, Eric may need to send the images via email or a file sharing application. In general, although such scenarios can be accommodated with today’s technology, the users would either have to jump between different tools (e.g., phone, email, file-sharing, and messenger application), or to rely on custom-developed applications, which are typically expensive and rigidly designed. In the following sections, we show how this scenario, as well as any other similar scenarios, can be satisfied on-demand and with ease under the CVM approach.3. Communication Virtual MachineTo better understand CVM, let’s first look to the data management area. Figure 1 captures the parallelism between the CVM paradigm and the one for managing heterogeneous data sources. As the use of computers and databases increases, we reach to a point where data is dispersed to a large number of sources2with different data models (e.g., relational, XML, text, and so on), data schemas and querying interfaces (e.g., SQL, XQuery, and keyword search). However, applications require access to multiple of these data sources and it became clear that developing specialized access mechanisms for each data source is cumbersome and inflexible since, if a legacy database is replaced by a newer one, the application has to be changed. Hence, the logical data abstraction paradigm was proposed, to hide the specifics of the underlying sources and export a uniform interface to the applications for querying data. The right part of Figure 1 shows a popular mediator architecture [7], where XQuery (See /XML/Query/) is used as the common data extraction language.(2) Transform the user communication requirements into a sequence of commands or actions, which when executed will control the flow of user communication as dictated by the requirements. (3) Provide a platform or environment in which the said sequence of commands can be executed to regulate the flow of communication. (4) Deliver the media or data among the communicating parties through a communication network or networks. Today, these tasks are typically hard coded in a communication system or tool, which predefines the way that user will use the system. Such a stovepipe design is the root cause of the problems discussed in Section 1. At the heart of CVM is a layered architecture, which provides a clean separation and compartmentalization of these major concerns in the spirit of [4], as illustrated in Figure 2. The CVM architecture divides the major communication tasks into four major levels of abstraction, which correspond to the four key components of CVM: (1) user communication interface (UCI), which provides a language environment for users to specify their communication requirements in the form of a user communication schema or schema instance1. (2) synthesis engine (SE), which is a suite of algorithms to automatically synthesize a user communication schema instance to an executable form called communication control script; (3) user-centric communication middleware (UCM), which executes the communication control script to manage and coordinate the delivery of communication services to users, independent of the underlying network configuration; and (4) network communication broker (NCB), which provides a network-independent API to UCM and works with the underlying network protocols to deliver the communication services. This layered division of responsibility is reminiscent of the OSI layered stack model for network communication [10]. Each layer has a specific role in the stack and communicates logically with the peerlayer at a remote site during communication sessions. Each layer builds on the upper layers in the stack to finally realize the user communication schema. UCI is responsible for providing users with means to define and manage their communication schema, which describes the role of communicating parties and the communication logic (e.g., participants, flow of1 A schema is a generic model of communication; an instance is an instantiation of the schema for a particular communication session. We will use the terms interchangeably until Section 4, where communication modeling is discussed.Figure 1: Analogy between CVM and Data Mediator.In the communication domain there is a similar need to hide the underlying device and network infrastructure and provide a unified communication abstraction layer. The CVM plays the role of the mediator and it handles the execution of communication requests specified in CML (which corresponds to XQuery. The wrappers on the left and right side of Figure 1 play the role of abstracting the network/device and data specifics, respectively. Finally, the SIP messages (See ) play the same role as break-down XQuery queries. Notice that the arrows between the left and right parts depict the correspondences between the two paradigms. In this section, we present a CVM architectural model for achieving the vision discussed earlier. There are four major tasks need to be performed to serve the users’ communication needs: (1) Conceive and describe the users’ communication requirements. In the case of a multimedia conferencing, it is to specify who the participants of the conference are and what kind of media or data are to be exchanged. In the case of the telemedicine application, it also includes the policy that governs who can access which part(s) of the patient’s medical record.3data or information). For this purpose, a communication modeling language is needed [8]. Such a language (see Section 5) should be intuitive enough to support on-the-fly communication modeling without requiring knowledge of underlying networks and yet rich enough to describe a variety of communication tasks. The language design poses many interesting research issues in its own right. In addition, it is responsible for maintaining consistency between the views of participants, and for serving as the runtime interface for user to manage his session.User/ Application (Initiator) User/ Application (Initiator)CVMUser Communication Interface (UCI) User CommunicationCVMUser Communication Interface (UCI)These changes (received in the form of signals from the NCB layer) may include: (1) session invitation, (2) receive media, (3) end media transmission, and (4) connection failed. Furthermore, UCM is responsible for providing a safe state transition between the running and updated communication control scripts. For example, when a session participant changes the communication schema by switching from a person-toperson call to a multi-way conference, SE will generate a new communication control script that reflects the change. Once the new communication control script is deployed to UCM, it should transfer the state of the old control script to the new one seamlessly and safely [29].Table 1: Summary of high-level tasks of CVM layers.CVM Layer User Communication Interface Tasks 1. Create/modify the communication schema instance based on user input. 2. Check the correctness and validity of the user communication schema. 3. Maintain consistency between participants’ instances. 1. Ensure the consistency of user communication schema through schema negotiation. 2. Perform schema synthesis to obtain the communication control script. 3. Deploy the script to the user-centric communication middleware. 1. Execute the communication control script. 2. Update the user communication schema based on changes made by other participants. 3. Perform a safe state transition from an older schema to an updated one. 1. Provide a high-level communication API, which is independent of the platform. 2. Utilize and coordinate the available, lowlevel network and hardware services. 3. Provide self-management in response to dynamics of the underlying infrastructure.Synthesis Engine (SE)Schema Instance Negotiation Communication LogicSynthesis Engine (SE)User-centric Communication Middleware (UCM) Network Communication Broker (NCB)User-centric Communication Middleware (UCM) Network Communication Broker (NCB)Communication DataCommunication NetworkCommunication NetworkFigure 2: Layered CVM architecture.Synthesis EngineSE performs two major tasks. The first is schema negotiation among participants of communication to ensure that all parties agree to a consistent schema. Second, SE automatically transforms the schema to an executable communication control script. This script represents the network-independent control logic for user-level communication session specified in the schema. A basic requirement for SE is that the synthesis process must be fully automated. SE uses a repository of pre-defined components for common as well as domain-specific communication functions. SE puts together the communication control script by combining pre-defined components (e.g., communication session establishment or transmission of text message) based on the user-defined schema. Consequently, the capability of a schema synthesizer can be improved incrementally as more “middleware” components are developed. The design of automated and efficient synthesis techniques and the middleware components represents another class of interesting research issues. UCM is the execution engine for communication control scripts. Based on the communication logic defined in the script, UCM invokes the common services provided by the NCB layer to perform tasks including: (1) session creation, (2) adding a participant to the session, (3) adding a media to the session, (4) transmitting media, and (5) adjusting media QoS. UCM is also responsible for updating the user communication schema resulted from runtime changes.User-centric Communication MiddlewareNetwork Communication BrokerNCB is responsible for providing a uniform API of high-level and network-independent communication services to diverse communication applications [31], in such a way to shield user applications from the underlying network/device heterogeneity and dynamics. It utilizes and coordinates networking functions (e.g., signaling, encoding & decoding, and transmitting & receiving) provided by the underlying networks, systems, and libraries. Given the variety and complexity of network configurations, it must exhibit a self-managing behavior that can respond to dynamics of the underlying device and network infrastructure. The concept of NCB offers a novel approach to simplify application development and interoperation, and introduces many important research issues4including self-management, dynamic configuration, definition of application independent communication API, and software framework for hiding network heterogeneity. These layers collectively fulfill the promise of CVM − that of generating communication applications that are reconfigurable, adaptive, and flexible based only on a high-level description of communication requirements. A summary of the high-level responsibilities assigned to each of these layers is presented in Table 1.default action that is performed on a medium. Actions “send” and “doNotSend” mean transfer automatically the medium or wait for the user to choose respectively, while “startApplication” orders the system to open the suggested application of the medium once transferred.4. Communication Modeling LanguageWe present an intuitive communication modeling language (CML) for modeling user communication requirements. We developed two equivalent variants of CML: the XML-based (X-CML) and the graphical (GCML), which are documented formally and in detail in [8]. The former is the version that CVM understands and processes, while the later is the user-friendly graphical form. G-XML is analogous to the E-R diagram [5] in the database domain. In [8], we show how these two variants can be automatically converted to each other. Figure 3 shows the (instantiated) X-CML and G-CML representations for the scenario of Section 2. A connection in CML is a user session, and is defined as a communication among a group of participants, where exchanged data is by default broadcasted to all participants. In addition to the local side, a connection contains a set of media (mediaAttached) currently transferred in the connections (user communication session) and a set of remote participants (remote). Both local and remote participants are associated with a communication device (e.g., PC, cell phone), which is associated by a set of capabilities (deviceCapability). Notice that the specific characteristics of a device, such as its type (e.g., PC or cell phone) or its connection type to the network (e.g., IP or cellular), are not defined nor required. The reason is that CML operates on an abstraction of the underlying network and devices as mentioned above. We assume there is a single virtual device per person, which has the union of the capabilities of all physical devices attached to the user. A medium is a data piece or data stream, like a Word document or a live video feed respectively. A medium has a type which is one of the predefined types supported by the system, a mediumURL that contains the location of the medium (a file location for a data piece or a port for a data stream), a suggestedApplication which defines the application that can be used to view or process a medium (e.g., Powerpoint for ppt files), and an action which defines a(a) G-CML<?xml version="1.0" encoding="ISO-8859-1"?> <userSchema> <connection connectionID = "connection1"> <device deviceID = "001" isVirtual = "false"> <deviceCapability>LiveAudio</deviceCapability> <deviceCapability>NonStreamFile</deviceCapability> </device> <device deviceID = "002" isVirtual = "true"> <deviceCapability>LiveAudio</deviceCapability> <deviceCapability>NonStreamFile</deviceCapability> </device> <device deviceID = "003" isVirtual = "true"> <deviceCapability>LiveAudio</deviceCapability> <deviceCapability>NonStreamFile</deviceCapability> </device> </connection> <person personName = "Mary Smith" personID = "007" personRole = ""/> <person personName = "Eric Goldberg" personID = "011" personRole = ""/> <person personName = "John Johnson" personID = "012" personRole = ""/> <isAttached personID = "007" deviceID = "001"></isAttached> <isAttached personID = "011" deviceID = "002"></isAttached> <isAttached personID = "012" deviceID = "003"></isAttached> <data connectionID="connection2"> <medium mediumDataType = "NonStreamFile" mediumName = "Heart_Scan.jpg" mediumURL = "/Heart_Scan.jpg"/> <medium mediumDataType = "NonStreamFile" mediumName = "X_Ray1.jpg" mediumURL = "/X_Ray1.jpg"/> </data> </userSchema>(b) X-CML Figure 3: CML example for our scenario.Finally, composite data are represented using forms in CML, which are nested structures that contain media as well as user-defined attributes (e.g., media with common suggestedApplication or action settings can be grouped together in a form). For example, it is common in medical scenarios to require transferring complex medical data consisting of multiple simple media (e.g., a page in a patient medical record).5. A Prototypical Design of CVMWe present a prototypical design of CVM, which closely follows the CVM architecture. The notation of Figure 4 (adopted by [12]) is used to describe the interfaces between the prototype components, which are summarized in Table 2. Notice that each layer uses5(resp. handles) what the lower level provides (resp. signals). UCI Component. The architecture design of UCI, which is detailed in [8], consists of four major components: (1) the communication modeling environment – provides the user with an environment to develop communication schemas and instances in GCML which are then automatically transformed to XCML, (2) the schema transformation environment – transforms an X-CML instance into a synthesis-ready X-CML instance or stores the X-CML model in the repository, (3) the repository – stores artifacts (e.g., grammar rules and CML schemas) to support the creation of CML schemas/instances, and (4) the UCIto-synthesis engine interface – provides a conduit for interaction with the synthesis engine.Provides Signalsthe UCI signals the User/Application (initiator) of the problem. This status update allows Eric, the sender of the image, to send text describing the images.Table 2. Interface between CVM components.CVM Layer UCI provides msg invoke(SchemaInst) msg invoke(SchemaData) msg store(SchemaInst) signals -Altered Instance (after negotiation by SE) -medium transmission status -ExceptionsSEmsg invoke(SchemaInst) msg invoke(SchemaData)UCMexecuteScript(XML)NCBcreateSession(sessionID) addParty(userID); addMedia(mediaURI), applyPolicy(xmlString);notifyMediaStatus notifyParticipantStatus notifyException notifySIStatus notifyMediaStatus notifyParticipantStatus notifyException notifySessionStatus notifySessionInvitation notifyNetworkFailureUsesHandlesFigure 4: Generic layer architecture[12].UCIprovidestheinterfacefunctionsinvoke(SchemaInst), invoke(SchemaData) and store(SchemaInst), shown in Table 2, to theUser/Application (initiator) (Figure 2), where SchemaInst and SchemaData are a communication schema instance and the data to be sent, respectively, and are both represented in X-CML. The functions return an acknowledgement or error message in the form of a message (msg). For example, in the scenario describe in Section 2 Mary builds the communication instance in a client application and submits the X-CML shown in Figure 3(b) via the invoke functions to UCI. Furthermore, UCI checks the syntactic and semantic correctness of a communication schema instance by building an abstract syntax tree of the X-CML representation and traversing the tree to check type compatibility of the media types and the values of the fields of the attributes. Some schema instances require that their abstract syntax trees be annotated with metadata associated with a communication schema (a template for a class of communication schema instances). This meta-data is defined using the communication modeling environment and stored in the repository. UCI also stores the current state of the schema instance. The state is required during communication with the synthesis engine and is updated based on the signals from the synthesis engine (see Table 2). For example, if there is a problem in transmitting the images of the patient record (scenario from Section 2) to Mary (e.g., bandwidth of the connection is too small)SE Component. The role of the synthesis engine is to convert the user schema in CML representation to an executable communication control script. It is invoked by UCI via its provides interface functions, invoke(SchemaInst) and invoke(SchemaData). SE performs the following tasks in sequence. First, SE determines if the invocation from the UCI requires a negotiation with the other session participants. If yes, it establishes an initial communication session with the other participants and performs schema negotiation to obtain an agreed schema in CML notation. SE then carries out the actual synthesis process. It parses the CML representation to obtain the logical components, which are the relationships along with associated media. For each logical component of the schema instance, the SE appends the appropriate script invocation (detailed below) to the communication control script. Finally, it dispatches the communication control script to the UCM layer. In CVM, each participant of a communication session has a local copy of their schema, which maybe changed at runtime. Any change to the schema will result in an update to the schemas of all participants. If two users in a session are simultaneously altering their schemas, concurrency problems arise. The SE component uses a modified 3-phase handshake protocol [26] for schema synchronization. As an example, the script for the scenario of Section 2 created by Mary’s local synthesizer is as follows:createSession(“ID”); addParty("ID", "ericgoldberg"); addParty("ID", "johnjohnson");6。
二(下)第一单元基础达标卷

二(下)第一单元基础达标卷班级:________ 姓名:___________一、填一填。
(每空1分,共26分)1.24里面有()个8。
2.从27里面连续减去7,最多能减()次,还余()。
3.25÷4=6……1,在这道除法算式中,25是(),4是(),商是(),余数是()。
4.÷6=5……2,被除数是()。
5.△÷8=8……○,○最大是(),△最大是()。
6.4月份有30天,合()个星期余()天。
7.括号里最大能填几?()×7<60 6×()<23 ()×8<549×()<51 ()×9<64 5×()<428.看图写算式。
÷=(盒)……(个)÷=(个)……(个)二、判一判。
(对的画“√”,错的画“×”)(每题1分,共5分)1.27÷6=5……3 ()2.÷4=7……,余数不可能是7。
()3.56里面最多有6个9。
()4.被除数一定比除数和商大。
()5.60天最多有7个星期天。
() 三、算一算。
(1题9分,2题18分,共27分)1.直接写得数。
36÷9=72÷8=42÷7=25÷5=63÷7=81÷9=20÷7=21÷5=29÷9=2.用竖式计算。
26÷6=62÷8=60÷7=70÷8=49÷6=52÷9=四、你能帮助信鸽送信吗?(填一填)(9分)五、解决问题。
(3题9分,其余每题8分,共33分) 1.装糖果。
糖的颗数9 18 27 36 45 54 63袋数 1 2可以装几袋?还剩几颗?2.把下面的面包和苹果平均分给6个同学。
(1)每个同学分几个面包?(2)每个同学分几个苹果?还剩几个苹果?3.动物园里有26只小兔。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
当包含VLAN 的交换网络中配置了VTP 时,下列哪种说法正确?Option 4
VTP 仅与802.1Q 标准兼容。
VTP 增大了管理交换网络的复杂性。
通过VTP 可将交换机配置为多个VTP 域的成员。
VTP 会向同一VTP 域内的所有交换机动态通知VLAN 更改情况。
2
VTP 以客户端模式工作具有哪两项特点?(选择两项。
)Option 15
无法添加VLAN
可添加在本地有效的VLAN
无论VLAN 信息如何,将广播从所有端口转发出去
只能传递VLAN 管理信息而无法接受更改
可向同一VTP 域中的其它交换机转发VLAN 信息
3
请参见图示。
交换机S1 处于VTP 服务器模式。
交换机S2 和S3 处于客户端模式。
管理员意外断开了S2 的F0/1 接口上的电缆。
这会对S2 产生什么后果?Option3
S2 会自动转换到VTP 透明模式。
S2 会将所有VLAN 从VLAN 数据库中删除,直到重新接好电缆为止。
S2 会保存已知的最新修订版本的VLAN ,但如果它重新加载,就会丢失这些VLAN。
当电缆重新接好时,S2 会自动向172.17.99.11 发送一个VTP 通告请求。
4
下列关于实施VTP 的说法中哪两项正确?(选择两项。
)Option12
交换机必须通过中继链路来连接。
VTP 域名区分大小写。
透明模式下的交换机不能配置新VLAN。
必须使用VTP 口令且区分大小写。
使用VTP 的交换机必须具有相同的交换机名称。
5
请参见图示。
VTP 域内的所有交换机均是新的。
交换机SW1 被配置为VTP 服务器,交换机SW2 和SW4 被配置为VTP 客户端,交换机SW3 被配置为VTP 透明模式。
哪台或哪些交换机会收到VTP 更
新并根据更新来同步VLAN 配置?Option 4
所有交换机均会收到更新并同步VLAN 信息。
仅交换机SW2 会收到更新并同步VLAN 信息。
仅交换机SW3 和SW4 会收到更新并同步VLAN 信息。
SW3 和SW4 会收到更新,但仅交换机SW4 会同步VLAN 信息。
6
请参见图示。
S2 之前用在实验环境中,现在以服务器模式添加到生产网络中。
实验网络和生产网络使用同一个VTP 域名,因此网络管理员未更改S2 的配置就将其添加到生产网络中。
实验域具有更高的修订版号。
将S2 添加到生产网络中后,很多计算机无法连接网络。
哪些命令可以解决此问题?Option2 通过下面两种方法之一重置S2 的修订版号:使用delete VTP 命令;或更改域名然后恢复原有的域名。
在S1 上手动重新输入除VLAN 1 外的所有适当的VLAN,使它们在网络中传播。
将S1 更改为透明VTP 模式以恢复vlan.dat 中的所有VLAN,然后改回服务器模式。
将S2 更改为客户端模式,这样VLAN 会自动传播。
7
在VTP 管理域内,当客户端模式交换机收到的总结通告的修订版号比交换机当前的修订版号高时,会进
行什么操作?Option 2
它会暂停转发,直到收到子集通告更新为止。
它会发出一个通告请求,以获取新的VLAN 信息。
它会增大其修订版号并将通告转发给其它交换机。
它会删除总结通告中未包含的VLAN。
它会发出总结通告以向其它交换机告知状态变化。
8
下列哪种情况会导致配置了VTP 的交换机发出总结通告?Option1
五分钟的更新计时器到期。
该交换机上的某个端口关闭。
该交换机更改为透明模式。
该管理域内的一台交换机连接了一台新主机。
9
请参见图示。
图中所示的交换机通过同一个VTP 管理域内的中继链路相连。
每台交换机标有其VTP 模式。
向Switch3 添加了一个新的VLAN。
此VLAN 未出现在其它交换机中。
此问题的原因是什么?Option
3
无法在处于透明模式的交换机上创建VLAN。
透明模式中的交换机不会转发VTP 通告。
在透明模式交换机上创建的VLAN 不会包含在VTP 通告中。
服务器模式交换机既不会侦听透明模式交换机发出的VTP 消息,也不会向其转发VTP 消息。
10
同一个域中的交换机之间通过何种方式发送VTP 消息?Option 2
第 2 层广播
第 2 层组播
第 2 层单播
第 3 层广播
第 3 层组播
第 3 层单播
11
请参见图示。
网络中的所有交换机均属于同一个VTP 域。
新交换机SW2 具有默认配置且修订版号为0,将该新交换机插入现有的VTP 域Lab_Network 中会发生什么情况?Option 4
该交换机会以VTP 客户端模式工作。
该交换机会以VTP 透明模式工作。
该交换机会以VTP 服务器模式工作,并会删除域内的现有VLAN 配置。
该交换机会以VTP 服务器模式工作,但不会删除域内的现有VLAN 配置。
该交换机会以VTP 服务器模式在默认VTP 域内工作,但不会影响现有VTP 域内的配置。
12
请参见图示。
交换机SW1 和SW2 通过中继链路互连,但无法交换VLAN 信息。
网络管理员发出show vtp status 命令来排查问题所在。
根据所提供的命令输出,可采取什么措施来纠正该问题?
Option 3
必须将交换机SW2 配置为VTP 客户端。
交换机必须通过接入链路互连。
必须采用同一个VTP 域名来配置交换机。
必须采用同一个VTP 修订版号来配置该两台交换机。
13
请参见图示。
Switch1 未与图中所示的其它交换机一起参与VTP 管理过程。
此问题可能有哪两种解释?
(选择两项。
)Option 4 6
Switch1 处于客户端模式。
Switch2 处于服务器模式。
Switch2 处于透明模式。
Switch1 处于另一个管理域内。
Switch1 有连接到端口的终端设备。
Switch1 所使用的是VTP 第1 版,而Switch2 所使用的是VTP 第2 版。
14
请参见图示。
根据图中所示的输出可确认哪两项事实?(选择两项。
)Option1 4
如果将此交换机添加到已收敛的网络中,则同一个VTP 域内的其它启用了VTP 的交换机会认为自己的
VLAN 信息比此交换机通告的VLAN 信息新。
此交换机未显示配置修订版的错误。
此交换机已经与相邻设备建立了双向通信。
此交换机被配置为向同一个VTP 域内启用了VTP 的其它交换机通告VLAN 配置。
此交换机被配置为允许网络管理员通过限制通向特定网络设备的流量来尽量提高带宽。
15
Option
请参见图示。
从所提供的输出可以获得什么信息?Option3
它检验了已配置的VTP 口令。
它检验了VTP 域是否被配置为使用VTP 第 2 版。
它检验了是否在交换VTP 通告。
它检验了VTP 域名是否是V1。
参加考试- ESwitching Chapter 4 - CCNA Exploration: LAN 交换和无线(版本 4.0)
剩余时间: 20:18:43
16
下列哪两种说法正确描述了VTP 透明模式的工作情况?(选择两项。
)Option 23
透明模式交换机可以创建VLAN 管理信息。
透明模式交换机添加的VLAN 只在本地有效。
透明模式下,交换机会将收到的所有VLAN 管理信息传递给其它交换机。
透明模式下,交换机可以接受其它交换机发来的VLAN 管理更改。
透明模式下,交换机会发出有关其VLAN 状态的更新,将该状态通知给其它交换机。
17
同一个VTP 域内的所有交换机上的哪三个VTP 参数必须相同?(选择三项。
)Option2 56
修订版号
域名
修剪
模式
域口令
版本号
18
在某台交换机发生故障后,网络管理员用之前就位于网络中的另一台交换机更换了故障交换机。
为了避免不正确的VLAN 信息通过网络传播,管理员应该对新更换的交换机采取什么预防措施?Option2
启用VTP 修剪。
更改VTP 域名。
将VTP 模式改为客户端。
将该交换机上的所有接口都改为接入端口。
19
以下哪项说法正确描述了中继链路上默认传播哪些VLAN?Option 2
仅VLAN 1
所有的VLAN
不传播任何VLAN
本征VLAN
20
下列关于VTP 修剪的说法中哪两项正确?(选择两项。
)Option 25
修剪功能默认为启用。
只能在VTP 服务器上配置修剪功能。
