S7506E三层交换机配置资料讲解
H3C_S7506E维护操作管理守则

精心整理H3C_S7506E维护操作手册配置举例:1、配置设备主机名如:sysnameH3C_S7506E2、3如:4如:5如:6如:7如:authorization-attributelevel38、配置将用户名admin及密码abc应用于telnet登录验证如:service-typetelnet9、开启telnet如:telnetserverenable10、配置E0/0接口描述如:descriptionto_G1/0/1_1.1.1.111、配置E0/0接口IP地址(广域网口IP地址)如:ipaddress2.2.2.212、配置E0/0接口为全双工状态如:13如:14如:15如:16如:17如:18如:19、配置环回地址如:ipaddress3.3.3.25520、配置VLAN端口如:interfaceVlan-interface121、配置VLAN接口的描述如:descriptionServer22、配置VLAN端口IP地址如:ipaddress3.3.3.1.023创建备份组并配置虚拟IP地址如:vrrpvrid1virtual-ip3.3.3.3 24、配置交换机在备份组中的优先级如:25如:26如:27如:2829如:30如:area 0.0.0.1network0.0.0.3network1.1.1.00.0.0.25531、设置OSPF链路开销参考值10000 bandwidth-reference1000032、将该OSPF区域设置为完全末梢区如:stubno-summary33、OSPF的开销如:ospfcost2034、开启SNMP代理如:35如:36如:37如:38如:39如:40如:snmp-agenttrapqueue-size500 41、配置SNMP陷阱报文生存时间如:snmp-agenttraplife60042、配置远程登录接口如:user-interfacevty0443、配置远程登录使用用户名及密码验证。
S7506E设备参数
支持流量整形和流量监管
MPLS特性
支持L3VPN:支持跨域MPLS VPN(Option1/2/3)、嵌套MPLS VPN、支持分层PE(HoPE)、CE双归属、MCE、多角色主机、GRE隧道等;支持L2VPN:Martini、Kompella、CCC和SVC方式;支持MPLS TE、RSVP TE
安全特性
支持IP+MAC+PORT任意组合的绑定,支持非法帧报文过滤,用户分级管理和口令保护,支持端口隔离,支持SSH,支持SNMPv3网管
★可靠性
支持VRRP,RRPP,Ethernet OAM(802.3ah),支持Graceful Restart for OSPF/BGP/IS-IS
设备管理
SNMP V1/V2/V3;RMON1/2/3/9;支持sFlow流量统计,Syslog;支持WEB网管,支持MIB-II;中文图形化管理
QOS
优先级队列调度:每端口支持8个优先级队列,3个丢弃优先级,支持SP、WRR、CBWFQ队列调度算法,支持WRED拥塞避免算法,支持流量整形,支持802.1P,DSCP/TOS优先级和重新标记能力,支持基于时间段的流分类和QoS控制能力;支持标准和扩展ACL,基于VLAN的ACL;支持VLAN ACL和IPv6 ACL;每板ACL条目数>=4000条
★虚拟化特性
支持H3C IRF2技术或Cisco VSS技术,将多台物理设备虚拟化为一台逻辑设备,虚拟组内可以实现一致的转发表项,统一的管理,跨物理设备的链路聚合
支持4台设备的虚拟化
支持至少三种以上分裂检测功能
支持远距离虚拟化,距离可达70km
7506E-S配置

MANUFACTURING_DATE : 2014-01-12
VENDOR_NAME : H3C
Slot 5:
DEVICE_NAME : LSQ1FWBSC0
DEVICE_SERIAL_NUMBER : 210231A832B125000018
MAC_ADDRESS : NONE
Only new chassis support this command.
The operation is not supported on the specified power.
Fan 1:
Only new chassis support this command.
The operation is not supported on the specified fan.
<WX3024>reboot
Start to check configuration with next startup configuration file, please wait.........DONE!
This command will reboot the device. Current configuration will be lost, save current configuration? [Y/N]:n
MANUFACTURING_DATE : 2014-01-11
VENDOR_NAME : H3C
Power 1:
Only new chassis support this command.
The operation is not supported on the specified power.
三层交换机详细配置实例(图)
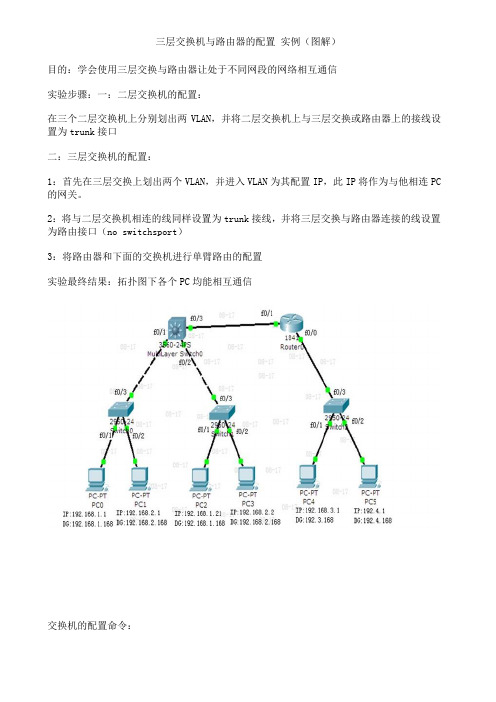
三层交换机与路由器的配置实例(图解)目的:学会使用三层交换与路由器让处于不同网段的网络相互通信实验步骤:一:二层交换机的配置:在三个二层交换机上分别划出两VLAN,并将二层交换机上与三层交换或路由器上的接线设置为trunk接口二:三层交换机的配置:1:首先在三层交换上划出两个VLAN,并进入VLAN为其配置IP,此IP将作为与他相连PC 的网关。
2:将与二层交换机相连的线同样设置为trunk接线,并将三层交换与路由器连接的线设置为路由接口(no switchsport)3:将路由器和下面的交换机进行单臂路由的配置实验最终结果:拓扑图下各个PC均能相互通信交换机的配置命令:SW 0:Switch>Switch>enSwitch#confConfiguring from terminal, memory, or network [terminal]?Enter configuration commands, one per line. End with CNTL/Z.Switch(config)#vlan 2Switch(config-vlan)#exitSwitch(config)#int f0/2Switch(config-if)#switchport access vlan 2Switch(config-if)#no shutSwitch(config-if)#int f0/3Switch(config-if)#switchport mode trunk%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/3, changed state to down%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/3, changed state to upSwitch(config-if)#exitSwitch(config)#SW 1:Switch>enSwitch#confConfiguring from terminal, memory, or network [terminal]?Enter configuration commands, one per line. End with CNTL/Z.Switch(config)#int f0/2Switch(config-if)#switchport access vlan 2% Access VLAN does not exist. Creating vlan 2Switch(config-if)#no shutSwitch(config-if)#exitSwitch(config)#int f0/3Switch(config-if)#switchport mode trunk%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/3, changed state to down%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/3, changed state to upSwitch(config-if)#SW 2:Switch>enSwitch#confConfiguring from terminal, memory, or network [terminal]?Enter configuration commands, one per line. End with CNTL/Z.Switch(config)#int f0/2Switch(config-if)#switchport access vlan 2% Access VLAN does not exist. Creating vlan 2Switch(config-if)#exitSwitch(config)#int f0/3Switch(config-if)#switchport mode trunkSwitch(config-if)#三层交换的配置命令:Switch>enSwitch#confConfiguring from terminal, memory, or network [terminal]?Enter configuration commands, one per line. End with CNTL/Z.Switch(config)#int f0/1Switch(config-if)#switchport mode trunk%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/2, changed state to downSwitch(config-if)#exitSwitch(config)#int f0/2Switch(config-if)#switchport mode trunkSwitch(config-if)#exitSwitch(config)#vlan 2Switch(config-vlan)#exitSwitch(config)#int vlan 1Switch(config-if)#no shut%LINK-5-CHANGED: Interface Vlan1, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to up Switch(config-if)#ip address 192.168.1.168 255.255.255.0Switch(config-if)#exitSwitch(config)#int vlan 2%LINK-5-CHANGED: Interface Vlan2, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan2, changed state to upSwitch(config-if)#ip addSwitch(config-if)#ip address 192.168.2.168 255.255.255.0Switch(config-if)#%LINK-5-CHANGED: Interface FastEthernet0/3, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/3, changed state to upSwitch(config-if)#exitSwitch(config)#int f0/3Switch(config-if)#no switchport%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/3, changed state to down%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/3, changed state to upSwitch(config-if)#Switch(config-if)#ip address 192.168.10.1 255.255.255.0Switch(config-if)#no shutSwitch(config-if)#exitSwitch(config)#ip routingSwitch(config-if)#exitSwitch(config)#ip route 0.0.0.0 0.0.0.0 192.168.10.2Switch(config)#路由器的配置:Router>enRouter#confConfiguring from terminal, memory, or network [terminal]?Enter configuration commands, one per line. End with CNTL/Z.Router(config)#int f0/0Router(config-if)#no shut%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to upRouter(config-if)#exitRouter(config)#int f0/1Router(config-if)#no shut%LINK-5-CHANGED: Interface FastEthernet0/1, changed state to up%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to upRouter(config-if)#exitRouter(config)#int f0/0Router(config-if)#no shutRouter(config-if)#exitRouter(config)#int f0/0.1Router(config-subif)#encapsulation dot1Q 1Router(config-subif)#ip address 192.168.3.168 255.255.255.0Router(config-subif)#exitRouter(config)#int f0/0.2Router(config-subif)#encapsulation dot1Q 2Router(config-subif)#ip addRouter(config-subif)#ip address 192.168.4.168 255.255.255.0Router(config-subif)#exitRouter(config)#ip route 0.0.0.0 0.0.0.0 192.168.10.1Router(config)#exit%SYS-5-CONFIG_I: Configured from console by consoleRouter#confConfiguring from terminal, memory, or network [terminal]?Enter configuration commands, one per line. End with CNTL/Z.Router(config)#int f0/1Router(config-if)#ip addRouter(config-if)#ip address 192.168.10.2 255.255.255.0 Router(config-if)#。
三层交换机基本配置

详细描述
三层交换机的主要功能包括路由,即根据IP地址或网络 层协议(如IPX或AppleTalk)将数据包从一个网络接口 转发到另一个网络接口。此外,它还可以实现访问控制 列表(ACL),这是一种安全功能,用于过滤和限制对 网络资源的访问。另外,三层交换机还可以在不同的 VLAN(虚拟局域网)之间进行路由,这对于大型企业 网络尤其重要,因为它们通常需要将不同的部门或用户 组划分为不同的VLAN。
详细描述
通过配置流量控制,可以限制网络中 数据包的流量,防止网络拥堵和数据 丢失。常见的流量控制技术包括基于 端口的流量控制和基于IP的流量控制。
端口汇聚配置
总结词
实现端口汇聚,提高网络带宽和可靠性
详细描述
端口汇聚可以将多个物理端口绑定为一个逻辑端口,从而提高网络带宽和可靠性。通过配置端口汇聚 ,可以实现负载均衡、备份和故障恢复等功能。
2. 创建ACL规则,指定允许或拒绝的IP地址和端口号。
详细描述:通过定义访问控制规则,ACL可以限制网络 流量,只允许符合规则的数据包通过交换机,从而保护 网络免受恶意攻击和非法访问。 1. 进入交换机的配置模式。
3. 将ACL应用到相应的接口上,以过滤进出的网络流量 。
IP源防护(IP Source Guard)配置
总结词:IP Source Guard用于防止IP地址欺骗攻击, 确保网络的安全性。
配置步骤
详细描述:IP Source Guard可以防止非法用户通过伪 造IP地址来攻击网络,通过绑定IP地址和MAC地址, 确保只有合法的用户能够通过交换机访问网络。
1. 进入交换机的配置模式。
2. 启用IP Source Guard功能。
动态路由配置(RIP)
总结词
三层交换机的连接和配置

课堂小结
例:
vlan 2 //建立编号为2的VLAN,并进入VLAN配置模式
port 0/0 untagged //加入接口0
exit
ห้องสมุดไป่ตู้
port 0/0 //进入设置接口模式
pvid 2 //设置接口0/0默认VLAN为VLAN2
exit
interface sw2 //进入sw2的接口配置模式
ip address 10.0.0.1 255.0.0.0 //配置VLAN网关地址
9.2三层交换机的连接和配置
三层交换机的接口
三层交换机的外观与普通交换机相似,有多种接口。 常用的接口有以下两种: ·以太网接口——一般为R45J接口,用双绞线与以太 网连接。一般有24个接口,通常标记为 “ETHERNET0/0”、“ETHERNET0/1”、…… “ETHERNET0/23”。 ·配置端口——又称为Console接口或控制台接口。大 多数三层交换机的Console接口同样为RJ45,少数使用 串口、IEEE1394接口。
VLAN接口配置命令需在全局配置模式下使用。 ①配置VLAN接口
interface VLAN接口(如sw0;sw1;sw3……) ②配置IP地址和子网掩码
ip address IP地址 子网掩码 例如: ③VLAN接口分配到VLAN。VLAN接口必须关联一个VLAN,此 VLAN必须提前配置好。 vlan-id 虚拟局域网号 vlan-id 1
port——向虚拟局域网中添加接口。
例:①vlan 2
建立编号为2的vlan,并进入vlan配置模式
②port 0/1 untagged 加入端口1
③exit
退出当前VLAN模式,返回上一级模式
S7506E三层交换机配置上课讲义

***************************************************************** ************** Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. ** Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ****************************************************************** *************Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33#vlan 3988description wirelesssupervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250#vlan 3991subvlan 1200 to 1225#vlan 3992supervlansubvlan 100 to 111#vlan 3993supervlansubvlan 1032 to 1150#vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#description to UTM200#vlan 4000 to 4001#ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator and if-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan #dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0 gateway-list 192.168.36.254expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0 gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3990network 192.168.138.0 mask 255.255.254.0 gateway-list 192.168.138.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!!service-type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1##interface Vlan-interface1ip address 192.168.39.2 255.255.255.0 #interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #interface Vlan-interface3986 (分配网关)ip address 192.168.160.1 255.255.224.0local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0#interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0#interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3990ip address 192.168.138.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227qos apply policy kefang inboundmirroring-group 2 monitor-port#interface GigabitEthernet3/0/5port access vlan 3901qos apply policy kefang inbound#interface GigabitEthernet3/0/6port access vlan 8#interface GigabitEthernet3/0/7port access vlan 3999description to UTM-200_G 0/0qos apply policy kefang inbound#interface GigabitEthernet3/0/8port access vlan 8qos apply policy kefang inbound#interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan 34stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/25 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/26 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/27 port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/31port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/32port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/33port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/34port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound#interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet3/0/45 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/46 port access vlan 35qos apply policy kefang inbound #interface GigabitEthernet3/0/47 port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound #interface GigabitEthernet3/0/48 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/13port link-type trunkqos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/38port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunk#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunk#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253 ip route-static 10.0.18.0 255.255.255.0 192.168.30.253 ip route-static 10.0.24.0 255.255.255.0 192.168.30.253 ip route-static 10.0.25.0 255.255.255.0 192.168.30.253 ip route-static 10.0.29.0 255.255.255.0 192.168.30.253 ip route-static 10.0.97.0 255.255.255.0 192.168.30.253 ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253 ip route-static 10.11.30.0 255.255.255.0 192.168.30.253 ip route-static 10.11.70.0 255.255.255.0 192.168.30.253 ip route-static 10.11.72.0 255.255.255.0 192.168.30.253 ip route-static 10.12.41.0 255.255.255.0 192.168.30.253 ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2。
三层交换机的基本配置方法

三层交换机的基本配置方法一、前言三层交换机是一种高级网络设备,它能够实现数据包的转发和路由功能。
在企业网络中,三层交换机的应用非常广泛,因为它可以提高网络性能和安全性。
本文将介绍三层交换机的基本配置方法,帮助读者了解如何正确地配置和管理这种设备。
二、基础知识在进行三层交换机的配置之前,需要了解一些基础知识:1. VLAN(Virtual Local Area Network):虚拟局域网,是一种将物理上分散的计算机连接起来形成逻辑上的局域网的技术。
2. STP(Spanning Tree Protocol):生成树协议,用于避免网络中出现环路。
3. OSPF(Open Shortest Path First):开放式最短路径优先协议,用于计算网络中最短路径。
4. ACL(Access Control List):访问控制列表,用于限制对网络资源的访问。
5. DHCP(Dynamic Host Configuration Protocol):动态主机配置协议,用于自动分配IP地址和其他网络参数。
6. NAT(Network Address Translation):网络地址转换,用于将内部IP地址映射为外部IP地址。
7. QoS(Quality of Service):服务质量,用于优化数据流量传输并确保网络性能。
三、配置步骤下面是三层交换机的基本配置步骤:1. 连接设备首先,需要将三层交换机与其他设备连接起来。
可以使用网线或光纤连接,然后通过串口或SSH等方式进行管理。
2. 设置管理IP地址设置管理IP地址是非常重要的一步,它允许管理员通过网络访问交换机进行配置和管理。
可以使用命令行界面或Web界面设置IP地址。
3. 配置VLANVLAN是将不同的网络设备划分为逻辑上的不同区域,从而提高网络安全性和性能。
可以使用命令行界面或Web界面创建和配置VLAN。
4. 配置STPSTP用于避免网络中出现环路,从而保证网络稳定性和可靠性。
H3C S7506E上配置策略路由
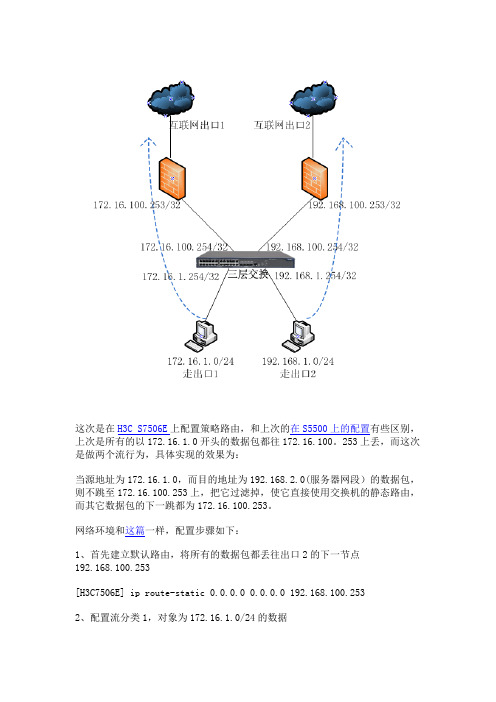
这次是在H3C S7506E上配置策略路由,和上次的在S5500上的配置有些区别,上次是所有的以172.16.1.0开头的数据包都往172.16.100。
253上丢,而这次是做两个流行为,具体实现的效果为:当源地址为172.16.1.0,而目的地址为192.168.2.0(服务器网段)的数据包,则不跳至172.16.100.253上,把它过滤掉,使它直接使用交换机的静态路由,而其它数据包的下一跳都为172.16.100.253。
网络环境和这篇一样,配置步骤如下:1、首先建立默认路由,将所有的数据包都丢往出口2的下一节点192.168.100.253[H3C7506E] ip route-static 0.0.0.0 0.0.0.0 192.168.100.2532、配置流分类1,对象为172.16.1.0/24的数据[H3C7506E]acl number 3001[H3C7506E-acl-adv-3001] rule 0 deny ip source 172.16.1.0 0.0.0.255 dest 192.168.2.0 0.0.0.255[H3C7506E] quit[H3C7506E] traffic classifier 1[H3C7506E-classifier-1] if-match acl 3001[H3C7506E-classifier-1] quit3、配置刚才定义的流分类的行为,定义如果匹配则允许[H3C7506E] traffic behavior 1[H3C7506E-behavior-1] filter permit[H3C7506E-behavior-1] quit4、配置流分类2,对象仍为172.16.1.0、24[H3C7506E]acl number 3002[H3C7506E-acl-adv-3002] rule 0 permit ip source 172.16.1.0 0.0.0.255 [H3C7506E] quit[H3C7506E] traffic classifier 2[H3C7506E-classifier-2] if-match acl 3002[H3C7506E-classifier-2] quit5、配置刚才定义的流分类的行为,定义如果匹配就下一跳至出口1即172.16.100.253[H3C7506E] traffic behavior 2[H3C7506E-behavior-2] redirect next-hop 172.16.100.253[H3C7506E-behavior-2] quit6、将刚才设置的应用至QOS策略中,定义policy 1[H3C7506E] qos policy 1[H3C7506E-qospolicy-2] classifier 1 behavior 1[H3C7506E-qospolicy-2] classifier 2 behavior 2[H3C7506E-qospolicy-2] quit7、在接口上应用定义的QOS策略policy 1[H3C7506E] interface GigabitEthernet 1/0/15[H3C7506E-GigabitEthernet1/0/15] qos apply policy 1 inbound[H3C7506E-GigabitEthernet1/0/15] quit至此,配置已完成。
S7506E 系列交换机IRF2 功能配置案例

在本次项目中,两台7506E核心交换机之间是用IRF技术,使用这种虚拟化技术可以集合多台设备的硬件资源和软件处理能力,实现多台设备的协同工作、统一管理和不间断维护。
以下为配置模板:# 设置RG-SP-HX-S7506E的成员编号为1,成员优先级为20,创建IRF端口2,并将它与物理端口Ten-GigabitEthernet2/0/7 Ten-GigabitEthernet2/0/8绑定。
(形成聚合IRF链路)独立运行模式配置:< RG-SP-HX-S7506E> system-view[RG-SP-HX-S7506E] irf member 1[RG-SP-HX-S7506E] irf priority 20[RG-SP-HX-S7506E] irf-port 2[RG-SP-HX-S7506E-irf-port 2] port group interface Ten-Gigabitethernet 2/0/7[RG-SP-HX-S7506E-irf-port 2] port group interface Ten-Gigabitethernet 2/0/8[RG-SP-HX-S7506E-irf-port 2] quit将当前配置保存到下次启动配置文件。
[RG-SP-HX-S7506E] quit< RG-SP-HX-S7506E> save将设备的运行模式切换到IRF模式。
< RG-SP-HX-S7506E> system-view[RG-SP-HX-S7506E] chassis convert mode irfThe device will switch to IRF mode and reboot. You are recommended to save the current running configuration and specify the configuration file for the next startup. Continue? [Y/N]:yDo you want to convert the content of the next startup configuration file flash:/startup.cfg to make it available in IRF mode? [Y/N]:yPlease wait...Saving the converted configuration file to the main board succeeded.Slot 1:Saving the converted configuration file succeeded.Now rebooting, please wait...设备重启后7506E-01组成了只有一台成员设备的IRF。
S7506E三层交换机配置

****************************************************************************** * Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. * * Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ******************************************************************************* Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33vlan 3988description wireless supervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250 #vlan 3991supervlansubvlan 1200 to 1225 #vlan 3992supervlansubvlan 100 to 111 #vlan 3993supervlansubvlan 1032 to 1150vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator and if-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan #dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0 gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0 gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3990network 192.168..0 mask 255.255.254.0gateway-list 192.168..1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!! -type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0#interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #ip address 192.168.160.1 255.255.224.0 local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0 #interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0 #interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3990ip address 192.168..1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0 local-proxy-arp enableinterface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128 local-proxy-arp enable#description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundport link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundport link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227qos apply policy kefang inboundmirroring-group 2 monitor-port#interface GigabitEthernet3/0/5port access vlan 3901qos apply policy kefang inbound#interface GigabitEthernet3/0/6port access vlan 8#interface GigabitEthernet3/0/7description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2#interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2#interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2#interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan 34stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/25 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/26 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/27 port link-type trunkmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/31port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/32port access vlan 2qos apply policy kefang inbound#port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39qos apply policy kefang inbound #interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/46port access vlan 35qos apply policy kefang inbound#interface GigabitEthernet3/0/47port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound#interface GigabitEthernet3/0/48port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/13port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunk#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunk#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253ip route-static 10.0.18.0 255.255.255.0 192.168.30.253ip route-static 10.0.24.0 255.255.255.0 192.168.30.253ip route-static 10.0.25.0 255.255.255.0 192.168.30.253ip route-static 10.0.29.0 255.255.255.0 192.168.30.253ip route-static 10.0.97.0 255.255.255.0 192.168.30.253ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253ip route-static 10.11.30.0 255.255.255.0 192.168.30.253ip route-static 10.11.70.0 255.255.255.0 192.168.30.253ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2#snmp-agentsnmp-agent local-engineid 800063A203000FE22EDA1Csnmp-agent community write q-ideasnmp-agent sys-info version allsnmp-agent target-host trap address udp-domain 192.168.34.120 udp-port 5000 params securityname q-idea#dhcp server detect#dhcp enable#user-interface aux 0idle-timeout 0 0user-interface vty 0 4acl 3011 inboundauthentication-mode schemeuser privilege level 3#return<7506E>。
7506E与CISCO交换机MSTP协议对接配置
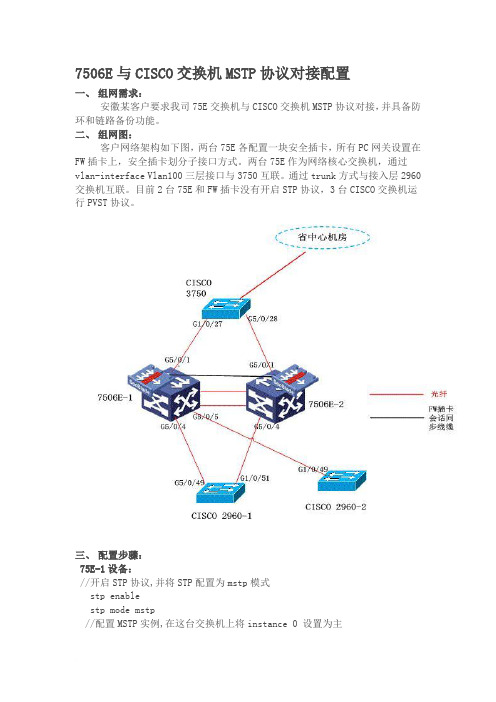
7506E与CISCO交换机MSTP协议对接配置一、组网需求:安徽某客户要求我司75E交换机与CISCO交换机MSTP协议对接,并具备防环和链路备份功能。
二、组网图:客户网络架构如下图,两台75E各配置一块安全插卡,所有PC网关设置在FW插卡上,安全插卡划分子接口方式。
两台75E作为网络核心交换机,通过vlan-interface Vlan100三层接口与3750互联。
通过trunk方式与接入层2960交换机互联。
目前2台75E和FW插卡没有开启STP协议,3台CISCO交换机运行PVST协议。
三、配置步骤:75E-1设备://开启STP协议,并将STP配置为mstp模式stp enablestp mode mstp//配置MSTP实例,在这台交换机上将instance 0 设置为主stp region-configurationregion-name h3crevision-level 1instance 0 vlan 1 to 4094active region-configuration#stp instance 0 root primary//配置与CISCO设备对接时需要修改的参数stp bpdu-protectionstp pathcost-standard dot1tstp timer-factor 1stp no-agreement-check#stp config-digest-snooping#//接口基本配置,并开启摘要侦听功能interface GigabitEthernet5/0/1port link-mode bridgeport access vlan 100stp config-digest-snooping#interface GigabitEthernet5/0/4port link-mode bridgeport link-type trunkport trunk permit vlan allstp config-digest-snooping#interface GigabitEthernet5/0/5port link-mode bridgeport link-type trunkport trunk permit vlan allspeed 1000duplex fullstp config-digest-snooping75E-2设备://开启STP协议,并将STP配置为mstp模式stp enablestp mode mstp//配置MSTP实例,在这台交换机上将instance 0 设置为备stp region-configurationregion-name h3crevision-level 1instance 0 vlan 1 to 4094active region-configuration#stp instance 0 root secondary//配置与CISCO设备对接时需要修改的参数stp bpdu-protectionstp pathcost-standard dot1tstp timer-factor 1stp no-agreement-check#stp config-digest-snooping#//接口基本配置,并开启摘要侦听功能interface GigabitEthernet5/0/1port link-mode bridgeport access vlan 100stp config-digest-snooping#interface GigabitEthernet5/0/4port link-mode bridgeport link-type trunkport trunk permit vlan allstp config-digest-snooping#interface GigabitEthernet5/0/5port link-mode bridgeport link-type trunkport trunk permit vlan allspeed 1000duplex fullstp config-digest-snooping安全插卡:因为安全插卡运行在三层模式,所以不需要开启STP协议。
H3C_7506交换机主主模式_配置
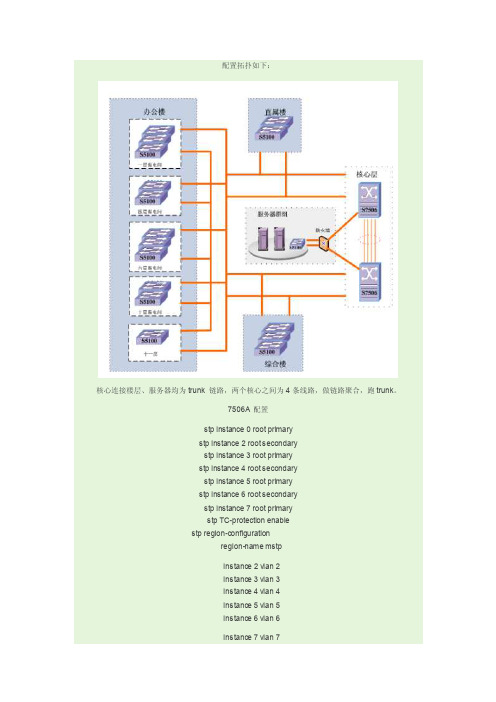
配置拓扑如下:核心连接楼层、服务器均为trunk 链路,两个核心之间为4条线路,做链路聚合,跑trunk。
7506A 配置stp instance 0 root primarystp instance 2 root secondarystp instance 3 root primarystp instance 4 root secondarystp instance 5 root primarystp instance 6 root secondarystp instance 7 root primarystp TC-protection enablestp region-configurationregion-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configurationstp enablevlan 2vlan 3vlan 4vlan 5vlan 6vlan 7interface Vlan-interface2ip address 192.168.2.251 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.2.254interface Vlan-interface3ip address 192.168.3.251 255.255.255.0 vrrp vrid 3 virtual-ip 192.168.3.254vrrp vrid 3 priority 110interface Vlan-interface4ip address 192.168.4.251 255.255.255.0 vrrp vrid 4 virtual-ip 192.168.4.254interface Vlan-interface5ip address 192.168.5.251 255.255.255.0 vrrp vrid 5 virtual-ip 192.168.5.254vrrp vrid 5 priority 110interface Vlan-interface6ip address 192.168.6.251 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.6.254interface Vlan-interface7ip address 192.168.7.251 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.7.254vrrp vrid 6 priority 110link-aggregation group 1 mode manualvrrp ping-enableinterface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan allport link-aggregation group 17506B 配置stp instance 0 root primarystp instance 2 root primary stp instance 3 root secondarystp instance 4 root primary stp instance 5 root secondarystp instance 6 root primary stp instance 7 root secondary stp TC-protection enablestp region-configuration region-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configurationstp enablevlan 2vlan 3vlan 4vlan 5vlan 6vlan 7interface Vlan-interface2ip address 192.168.2.252 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.2.254vrrp vrid 2 priority 110interface Vlan-interface3ip address 192.168.3.252 255.255.255.0 vrrp vrid 3 virtual-ip 192.168.3.254interface Vlan-interface4ip address 192.168.4.252 255.255.255.0 vrrp vrid 4 virtual-ip 192.168.4.254vrrp vrid 4 priority 110interface Vlan-interface5ip address 192.168.5.252 255.255.255.0 vrrp vrid 5 virtual-ip 192.168.5.254interface Vlan-interface6ip address 192.168.6.252 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.6.254vrrp vrid 6 priority 110interface Vlan-interface7ip address 192.168.7.252 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.7.254link-aggregation group 1 mode manualvrrp ping-enableinterface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan allport link-aggregation group 1楼层交换机配置(S5100)vlan 2 to 7stp bpdu-protectionstp enablestp region-configurationregion-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configuration所有连接PC机的端口,全部配置边缘端口(stp edged-port enable)楼层连接核心的两条上行链路配置为trunk,这两个端口不能配置边缘端口注:双机做完后,可以用dis stp brief 查看状态1、两个核心上所有连接楼层接入的端口都应该为fordowing状态2、楼层接入交换机主核心线路端口应该为fordowing,从核心线路端口应该为discard核心间的链路聚合,随后有相关日志描述。
火箭林克 ES7506 工业6口 PoE 交换机用户指南说明书

ROCKET LINX ES7506Industrial 6-Port Managed PoE Switch QUICK INSTALLATION GUIDE 2000528 Rev D | Release Date - January, 2014INTRODUCTIONThe RocketLinx 7506 is designed for industrial PoE applications where the power source is not conveniently located, such as IP surveillance or wireless access points.See t he Comtrol website for complete product specifications. INSTALLATION OVERVIEWYou can use the following overview to install the ES7506. If you need more detailed installation and configuration information, you can refer to the RocketLinx ES7506 User Guide, which is available on the RocketLinx CD or you can download the latest version.Wiring the Power InputsThe ES7506 provides redundant power, reverse polarity protection, and accepts a positive or negative power source but PW1 and PW2 must apply to the same mode. The power supplies should be UL Listed with a minimumoutput rating of 24-55VDC and at 2.5A.1. Insert the positive and negative wires into PW+ and PW- contacts (PW1 and PW2). You can connect a single power supply or two power supplies depending on your requirements.2. If both power inputs are connected, the ES7506 is powered from the highest connected voltage. The unit can be configured to signal an alarm for loss of power in either PW1 or PW2.3.Tighten the wire-clamp screws to prevent the wires from being loosened.Power should be disconnected from the power supply before connecting it to the switch. Otherwise, your screwdriver blade can inadvertently short your terminalconnections to the grounded enclosure.Wiring the Alarm Relay Outputterminal block connector on the side of the ES7506. The power supply should be UL Listed with a minimum output rating of 2.5A at 24-55VDC.The relay contacts are energized (open) for normal operation and closeunder faulty conditions. Faulty conditions can include power failure, Ethernet port link break, or other predefined events configurable in the ES7506 user interface. To activate the alarm relay output function, refer to the RocketLinx ES7506 User Guide .Power SupplyAC Power Input24-55VDC/2.5A (UL Listed)V-DC Power InputGrounding the E7506Wire the earth ground to ensure the system is not damaged by noise or any electrical shock, we recommend that you make a direct connection between the ES7506 and earth ground.Using a screw driver, loosen the earth ground screw on the side of theES7506 and then tighten the screw after the earth ground wire is connected.Mounting the ES7506Use the appropriate procedure to mount the ES7506 on the wall or a DIN rail.Connecting RJ45 PortsConnect one end of an Ethernet cable into the Ethernet port of the ES7506 and the other end to the attached networking device. The Ethernet ports support 10/100Mbps half/full-duplex. All ports auto-detect the signal from connected devices to negotiate the link speed and duplex mode. Auto MDI/MDIX allows users to connect another switch, hub, or workstation without changing straight through or crossover cable.Link/Act LEDs are lit to indicate traffic and link status, see the LEDs subsection for more information.Attaching the ES7506 to the WallUse the hook holes located at the corners ofthe wall-mount plate to mount the ES7506.DIN Rail MountingTwo DIN rail clips and four screws were shipped with the ES7506. Use the screws to attach theDIN rail clip to the wall-mount plate.Always make sure that the cables between the Array switches and attached devices (for example,switch, hub, or workstation) are less than 100meters (328 feet).• 10BASE-T: Category 3, 4, or 5 cable• 100BASE-TX: Category 5 cable• IEEE 802.3af: Category 5 cablePROGRAMMING THE IPADDRESSConfigure the IP address using one of thefollowing methods:• PortVision DX (available on the RocketLinx CD shipped with the product)• Web browser• Telnet• Command Line Interface (CLI) using the RS-232 console cableThe easiest way to configure a static IP address for your network in theES7506 is to use a Windows host and PortVision DX (see below). For information about using other configuration methods, refer to the RocketLinx ES7506 User Guide.Note: Optionally, you can use NetVision if you are accustomed to using NetVision. PortVision DX is replacing NetVision. NetVision is not documented in the RocketLinx ES7506 User Guide.The following procedure uses PortVision DX to program network settings. 1. Install PortVision DX on a host system with a Windows operatingsystem. If you need assistance installing PortVision DX, see the RocketLinx ES7506 User Guide.2. Start PortVision DX. PortVision DX can be started from Start --> AllPrograms --> Comtrol --> PortVision DX.3. Click the Scan button.4. Select the Comtrol product families that you want to locate and click theScan button.(cont. on page 5)(cont. from page 4)5. Right-click the ES7506 in the Device List pane (lower) that you want toconfigure and click Properties.6. Enter a user-friendly Device Name.7. Optionally, enter the ES7506 serial number, which displays a friendlydevice name in the Device List pane on the main page.8. Select DHCP IP or Static IP for the IP Mode.• If you select DHCP IP, go to Step 9.• If you select Static IP, enter an IP address, Subnet Mask, and Default Gateway value for your network.9. Optionally, select the appropriate Network Topology, which is aninformational field.10. Click the Apply Changes button.11. Click Close to return to the main screen.You are now ready to configure the ES7506 features.LED INDICATORSYou can also view the LEDs for the ES7506 through the web interface usingpage.the Device Front PanelFEATURE CONFIGURATIONThe ES7506 provides both in-band and out-band configuration methods:Out-band management means that you configure the ES7506 using the RS-232 console cable and the Command Line Interface (CLI) to access the ES7506 without attaching an admin PC to the network. You can also use out-band management, if you lost the network connection to the ES7506.In-band management means that you connect remotely using the ES7506 IP address through the network. You can remotely connect with the ES7506 Java applet web interface or a Telnet console and the CLI.The following procedure uses a web browser to configure ES7506 features. Refer to the RocketLinx ES7506 User Guide for other configuration methods.1. If necessary, install the latest version of the Java Runtime Environment,which is required to run the web management interface.2. Open a web browser and enter the IP address of the ES7506.3. Click Run when Java prompts you to run the applet.4. Enter admin for both the user name and the password when prompted.5. Use the web interface to configure your device as needed for yournetwork.You can use the help system or the RocketLinx ES7506 User Guide for information about configuring ES7506 features.You can use one of the following methods to contact Comtrol.。
三层交换机配置

学院:计算机学院班级:网络112班学号:201100824205 姓名:单海丽三层交换机的配置1、实验目的(1)、掌握三层交换机的工作原理。
(2)、掌握三层交换机上路由的配置命令和步骤。
(3)、学习配置三层交换机的命令和步骤。
2、实验内容利用三层交换机和二层交换机进行VLAN间的通信,以及三层交换机与路由器之间的路由共享情况,给出通信测试。
3、实验原理三层交换机就是具有理由器功能的交换机。
三层交换机的最重要的目的是加快大型局域网内部的数据交换,所具有的路由功能也是为这一目的服务的,能够做到一次路由,多次转发。
对于数据包转发等规律的过程由硬件高速实现,而像路由信息更新、路由表维护、路由确定等功能由软件实现。
出于安全和管理方便考虑,只要是为了减小广播风暴的危害,必须把大型局域网按功能或因素划分成一个个小的局域网,这就使VLAN技术在网络中得以大量应用。
而各个不同VLAN间的通信都要经过路由器来完成转发,随着网间互访的不断增加,单纯使用路由器来实现网间访问,不但因为端口数量有限,而且路由速度慢,从而限制了网络的规模和访问速度。
基于这种情况,三层交换机便应运而生。
三成交换机是为IP设计的,接口类型简单,拥有很强的二层帧处理能力,非常适用于大型局域网内的数据路由与交换,它既可以工作在协议的第三层替代或部分完成传统路由器的功能,同时又具有几乎第二层交换的速度,而价格相对便宜些4、实验环境与网络拓扑5、实验步骤(1)、三层交换机VLAN的基本配置(2)、三层交换机上VLAN的IP地址配置(4)、交换机和路由器的路由协议配置(5)、查看三层交换机的路由表6、实验故障与调试三层交换机和路由器的路由表应该是一样的,而且是具有全网络的路由信息。
拓扑中的任何两台设备之间都可以进行通信。
如果出现问题,要查看VLAN是否配置正确,VLAN 的IP地址是否有误,Trunk链路是否正确,路由协议是否配置正确。
7、实验心得通过对三层交换机的配置,我们了解到了大型局域网内的网络通信情况,对实际的网络由了更深的了解。
三层交换机怎么设置

三层交换机怎么设置三层交换机怎么设置三层交换机怎么设置三层交换机确实具有一定的路由功能,它可以实现不同的子网连接功能,但是特别注意的问题是,它的路由功能相对路由器来说还是要弱许多的,而且三层交换机只能使用一个网络。
而且通常只是局域网子网之间的互联,并不能把局域网与广域网,或者互联网连接起来,因为三层交换机所支持的路由协议非常有限,毕竟这不是它的主要功能。
我们知道,在局域网上,二层的交换机通过源MAC 地址来标识数据包的发送者,根据目的MAC 地址来转发数据包。
对于一个目的地址不在本局域网上的数据包,二层交换机不可能直接把它送到目的地,需要通过路由设备(比如传统的路由器)来转发,这时就要把交换机连接到路由设备上。
如果把交换机的缺省网关设置为路由设备的IP 地址,交换机会把需要经过路由转发的包送到路由设备上。
路由设备检查数据包的目的地址和自己的路由表,如果在路由表中找到转发路径,路由设备把该数据包转发到其它的网段上,否则,丢弃该数据包。
专用路由器昂贵、复杂、速度慢、易成为网络瓶颈,因为它要分析所有的广播包并转发其中的一部分,还要和其它的路由器交换路由信息,而且这些处理过程都是由CPU 来处理的(不是专用的ASIC )。
第三层交换机既能像二层交换机那样通过MAC 地址来标识转发数据包,也能像传统路由器那样在两个网段之间进行路由转发。
传统路由器采用软件来维护路由表,而三层交换机是通过专用的ASIC芯片来处理路由转发的。
与传统路由器相比,第三层交换机的路由速度一般要快十倍或数十倍。
大家都知道,路由器可以连接企业局域网和广域网(如因特网),但却忽略了一路由器的另一个应用,那就是它的局域网连接功能。
路由器的广域网连接可参见拓扑图图和三层交换机的路由连接图。
路由器的作用因不同的路由器类型而定,我们常说的路由器通常是指边界路由器,就是位于不同类型网络的边界,如拓扑图图和三层交换机的路由连接图所示。
还有一种路由器。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
***************************************************************** ************** Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. ** Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ****************************************************************** *************Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meetingsupervlansubvlan 36#vlan 3986description dianxin wireless supervlansubvlan 3901#vlan 3987description huisuo vlan 33 supervlansubvlan 33#vlan 3988description wirelesssupervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250#vlan 3991supervlansubvlan 1200 to 1225#vlan 3992supervlansubvlan 100 to 111#vlan 3993supervlansubvlan 1032 to 1150#vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790#vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001#ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator andif-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan#dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3990network 192.168.138.0 mask 255.255.254.0gateway-list 192.168.138.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!!service-type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0 #interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 ##interface Vlan-interface3986 (分配网关)ip address 192.168.160.1 255.255.224.0local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0#interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0#interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3990ip address 192.168.138.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39#interface GigabitEthernet3/0/3 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/4 port access vlan 1227qos apply policy kefang inbound mirroring-group 2 monitor-port #interface GigabitEthernet3/0/5 port access vlan 3901qos apply policy kefang inbound #interface GigabitEthernet3/0/6 port access vlan 8#interface GigabitEthernet3/0/7 port access vlan 3999description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10qos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inboundstp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/25port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/26port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundqos apply policy kefang inbound #interface GigabitEthernet3/0/32 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/33 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39#interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet3/0/45 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/46 port access vlan 35qos apply policy kefang inbound #interface GigabitEthernet3/0/47port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253 ip route-static 10.0.18.0 255.255.255.0 192.168.30.253 ip route-static 10.0.24.0 255.255.255.0 192.168.30.253 ip route-static 10.0.25.0 255.255.255.0 192.168.30.253 ip route-static 10.0.29.0 255.255.255.0 192.168.30.253 ip route-static 10.0.97.0 255.255.255.0 192.168.30.253 ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253 ip route-static 10.11.30.0 255.255.255.0 192.168.30.253 ip route-static 10.11.70.0 255.255.255.0 192.168.30.253 ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2 #snmp-agentsnmp-agent local-engineid 800063A203000FE22EDA1Csnmp-agent community write q-ideasnmp-agent sys-info version allsnmp-agent target-host trap address udp-domain 192.168.34.120 udp-port 5000 params securityname q-idea#dhcp server detect#dhcp enable#user-interface aux 0idle-timeout 0 0user-interface vty 0 4acl 3011 inboundauthentication-mode schemeuser privilege level 3#return<7506E>。
