Alteon配置手册V2
Alteon 实验操作手册

Alteon 实验操作手册LAB 1Alteon Web Switch 基本操作实验环境:alteon web switch 交换机1台。
1、准备工作用console线连接PC机串口到alteon web switch交换机管理口打开超级终端软件设置为以下参数打开switch电源,按回车键进入如下提示:输入缺省管理密码:admin输入N 跳过初始化配置,直接进入命令行配置界面2、更改密码在主菜单输入:Main#/cfg 进入配置菜单输入:>> Configuration#sys 进入系统菜单输入:System# user/admpw 更改系统密码Changing ADMINISTRATOR password; validation required... Enter current administrator password:输入当前密码Enter new administrator password:输入新密码Re-enter new administrator password:重复密码System# apply 应用配置System# save 保存配置3、配置VLAN,端口等L2信息。
创建VLAN进入配置菜单输入:>> Configuration#vlan (2-1024)进入vlan配置菜单>> vlan 2# ena (打开vlan 2)>> vlan 2# add 2 (把端口2加到 vlan 2)4、配置IP 接口地址、路由、网关等L3信息。
配置Interface 信息在配置菜单输入:>> Configuration#ip进入ip选项菜单输入:>> IP#if 1进入interface配置输入:>> IP Interface 1#addr 192.168.0.252>> IP Interface 1#mask 255.255.255.0>> IP Interface 1#ena>> IP Interface 1#..(返回IP配置菜单)配置路由信息输入:>> IP#route 进入路由配置>> IP Static Route#add (添加静态路由记录)>> IP Static Route#..(返回IP配置菜单)配置缺省网关输入:>> IP#gw 配置网关信息>> Default gateway 1#addr 192.168.0.254 (网关地址) >> Default gateway 1#ena>> Default gateway 1#apply>> Default gateway 1#save5、升级image系统软件、boot image 、bin文件。
北电Alteon应用层交换机技术手册_SSL session ID based persistence

T e c h n i c a l T i pTT-0412406a -- Information -- 20-Dec-2004SSL session ID based persistenceContents: Introduction: (1)Associated Products: (1)Overview (1)Sample configuration (4)Setup (4)Configuring PC (4)Configuring Server1 (4)Configuring network parameters (4)Configuring CA (5)Requesting server certificate (7)Signing server certificate request (7)Configuring apache for HTTPS (7)Configuring Server2 (12)Configuring network parameters (12)Requesting the certificate (12)Configuring apache for HTTPS (15)Configuring Alteon (15)Configuring interfaces (16)Configuring real servers (16)Assigning real servers to a group (17)Configuring virtual server (17)Enabling client/server processing on ports (18)Enabling direct access mode (18)Enabling SLB globally (18)Testing the configuration (19)Appendix A: Alteon configuration file (33)Introduction:This document illustrates the operation and sample configuration of SSL session ID based persistence on Nortel Web and Application switches (formerly Alteon WebOS and Application switches).Associated Products:The information in this document is intended to be used with the following product(s) with the indicated software or hardware revisions:Revision InformationProduct Name or Order Number Potentially Affected Corrected Nortel (formerly Alteon) Web and Application switches: 180e, 180All N/A Plus, 184, AD2, AD3, AD4, 2224, 2424, 2208, 2216, 3408OverviewSSL is the industry-standard method for protecting web communications developed by Netscape Communications Corporation. The SSL security protocol provides data encryption, server authentication, message integrity, and optional client authentication for a TCP/IP connection. Because SSL is built into all major browsers and web servers, simply installing a digital certificate turns on their SSL capabilities.The primary goal of the SSL Protocol is to provide privacy and reliability between two communicating applications. The protocol is composed of two layers – SSL Handshake Protocol and SSL Record Layer Protocol (see Figure 1). Figure 1. . . . Application LayerAt the lowest level, layered on top of reliable transport protocol (TCP) is the SSL Record Protocol. The SSL Record Protocol is used for encapsulation of various higher-level protocols. One such encapsulated protocol is the SSL Handshake Protocol that allows the server and client to authenticate each other and to negotiate an encryption algorithm and cryptographic keys before the application protocol transmits or receives its first byte of data. One advantage of SSL is that it is application protocol independent. A higher-level protocol can layer on top of the SSL Protocol transparently.The SSL handshake has two major phases. The first phase is used to established private communication; the second phase is used for client authentication.The first phase starts with the client sending a Client-Hello message to the server. The server receives the message, processes it and responds with a Server-Hello message. The Server-Hello message contains server’s certificate, bulk cipher specifications, and a randomly generated session ID. During this stage parameters are passed in clear text, in other words they are not encrypted yet. Once Client and Server agreed on a cipher and generated session keys, all the messages are encrypted using the selected cipher.During the second phase client authenticates itself to the server if server was configured to verify client’s identity. Nortel Web and Application switches, when configured for server load balancing, can use SSL session ID retrieved during clear text SSL handshake to maintain persistence between clients and real servers.Using SSL session ID, switch forwards the client’s requests to the same real servers that were selected to serve the requests originally.When the client sends an initial SSL Client-Hello message (Figure 2), no session ID is set and the switch forwards client request to the next available real server based on the configured load balancing metric. The real server receives the request, processes it and responds with SSL Server-Hello that contains session ID randomly generated by the real server. The switch notes the session ID and the real server that processed the request and forwards request to the client. When the client makes a subsequent request, it inserts the received session ID in SSL Client-Hello message. The switch receives a subsequent Client-Hello, looks up the session ID and associated with that ID real server and forwards the subsequent request to the real server that initially severed the request:Figure 2Client sends SSL Client-HelloSwitch forwards the request tothe selected real server (forexample, Server 1)Real server responds withSSL Server-Hello withsession ID setSwitch records session ID value and real serveraddress and forwards SSL Server-Hello to ClientClient uses the received session ID for subsequentrequestsSwitch forwards thesubsequent request to thereal server based on thesession ID informationSample configurationSetupPC – Windows 2000 professional with Mozilla 1.6 installed, IP address 192.168.10.77/24;Alteon – Nortel Web switch AD3, code version 10.0.30.7, interface 1 IP 192.168.10.100/24, interface 2 IP 192.168.20.200/24, Virtual IP 192.168.10.150, port 1 – client port, port 8 – server port;Server1/CA – Linux RedHat 9.0 with apache software 2.0.49 and openssl 0.9.7a installed, IP address 192.168.20.10/24. Server1 will also be used as a Certificate Authority (CA) for both servers;Server2 – Linux RedHat 9.0 with apache software 2.0.49 and openssl 0.9.7a installed, IP address 192.168.20.20/24.The goal of the configuration is to configure HTTPS load balancing with session persistence based on SSL session ID.Configuring PCConfigure IP address (192.168.10.77/24) on PC:C:\>ipconfigWindows 2000 IP ConfigurationEthernet adapter Local Area Connection:Connection-specific DNS Suffix . :IP Address. . . . . . . . . . . . : 192.168.10.77 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . :Configuring Server1Root privileges are required for configuration:[user@Server1 user]$ suPassword:[root@Server1 user]#Configuring network parameters1. Configure IP address (192.168.20.10/24) on WebServer1:GW: 192.168.20.200[root@Server1 user]# /sbin/ifconfig eth0 192.168.20.10 netmask 255.255.255.0 2. Configure static route to 192.168.10.0/24 network (PC’s network) via Alteon interface 2 (192.168.20.200):[root@Server1 user]# /sbin/route add –net 192.168.10.0/24 gw 192.168.20.200 Configuring CAting as a Certificate Authority (CA) for both Server1 and Server2. he ssl.ca scripts are used in this example to configure CA and sign the server certificates. Scripts are available atServer1 will be ac Configure CA on Server1.T /contrib/Obtain the archived scripts from the web site mentioned above.1. Open the archive: [root@Server1 user]# tar -xzf ssl.ca-0.1.tar.gz2. Change directory to ssl.ca-0.1:[root@Server1 user]# cd ssl.ca-0.1 [root@Server1 ssl.ca-0.1]#3. Run a ./new-root-ca.sh script to create a self signed CA certificate.a) When prompted enter the pass phrase for the CA key – any combination of letters and digits (linuxwas used as a pass phrase in this example). Make sure to remember the phrase as it’ll be used tosign certificates.b) Fill out the appropriate fields for the certificate (some fields can be left blank). In this example,Country Name (US), State or Province Name (MA), Locality Name (Billerica), OrganizationName (Nortel), Organizational Unit Name (Support), Common Name (LinuxCA) were filled andEmail Address was left blank:[root@Server1 ssl.ca-0.1]# ./new-root-ca.shNo Root CA key round. Generating oneGenerating RSA private key, 1024 bit long modulus..++++++ ....................................................++++++e is 65537 (0x10001)Enter pass phrase for ca.key: ÅEnter pass phraseVerifying - Enter pass phrase for ca.key: ÅEnter pass phraseSelf-sign the root CA...Enter pass phrase for ca.key: ÅEnter pass phraseYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [MY]:USState or Province Name (full name) [Perak]:MALocality Name (eg, city) [Sitiawan]:BillericaOrganization Name (eg, company) [My Directory Sdn Bhd]:NortelOrganizational Unit Name (eg, section) [Certification Services Division]:Support Common Name (eg, MD Root CA) []:LinuxCAEmail Address []:The script creates CA key (ca.key) and certificate (ca.crt) files.Requesting server certificateRun ./new-server-cert.sh<name to be given to request> script to create server certificate request file.When prompted, fill out appropriate fields of certificate request. In this example, Country (US), State (MA), Locality (Billerica), Organization (Nortel) and Common Name (Server1) were filled out, the remainder were left blank. [root@Server1 ssl.ca-0.1]# ./new-server-cert.sh server1No server1.key round. Generating oneGenerating RSA private key, 1024 bit long modulus............++++++..................................++++++e is 65537 (0x10001)Fill in certificate dataYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [MY]:USState or Province Name (full name) [Perak]:MALocality Name (eg, city) [Sitiawan]:BillericaOrganization Name (eg, company) [My Directory Sdn Bhd]:NortelOrganizational Unit Name (eg, section) [Secure Web Server]:Common Name (eg, ) []:Server1Email Address []:You may now run ./sign-server-cert.sh to get it signedThe script creates certificate request (server1.csr) file.Signing server certificate requestOnce certificate request has been created, sign the request using ./sign-server-cert.sh <name of the created request> script. When prompted, enter the pass phrase selected for the CA (linux in this example). Enter y (yes) to sign the certificate and commit:[root@Server1 ssl.ca-0.1]# ./sign-server-cert.sh server1CA signing: server1.csr -> server1.crt:Using configuration from ca.configphraseEnter pass phrase for ./ca.key: (EnterpassCheck that the request matches the signatureSignature okThe Subject's Distinguished Name is as followscountryName :PRINTABLE:'US'stateOrProvinceName :PRINTABLE:'MA'localityName :PRINTABLE:'Billerica'organizationName :PRINTABLE:'Nortel'organizationalUnitName:PRINTABLE:'Secure Web Server'commonName :PRINTABLE:'Server1'Certificate is to be certified until Jun 25 02:41:29 2005 GMT (365 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base UpdatedCA verifying: server1.crt <-> CA certserver1.crt: OKThe server certificate request (server1.crt) is created.Configuring Apache for HTTPSNote: In this configuration Server1 and Server2 are configured for HTTPS only, no clear HTTP requests will be processed. For more information on the Apache server please consult Apache documentation available at HYPERLINK "/" /This configuration assumes that Apache 2.0.49 has been compiled with SSL module enabled and has been successfully installed. It is also assumed that the default prefix /usr/local/apache2 was used for installation.1. Verify SSL module is installed:[root@Server1 ssl.ca-0.1]# /usr/local/apache2/bin/httpd -lCompiled in modules:core.cmod_access.cmod_auth.cmod_include.cmod_log_config.cmod_env.cmod_usertrack.cmod_setenvif.cmod_ssl.cprefork.chttp_core.cmod_mime.cmod_status.cmod_autoindex.cmod_asis.cmod_cgi.cmod_negotiation.cmod_dir.cmod_imap.cmod_actions.cmod_userdir.cmod_alias.cmod_so.c2. To simplify the configuration, move the created certificate and key file to the httpd’s default directories.Note: This step can be omitted.a) Create directory (ssl.crt) for server certificate under the apache conf directory:[root@Server1 ssl.ca-0.1]# mkdir /usr/local/apache2/conf/ssl.crtb) Create directory (ssl.key) for server certificate key under[root@Server1 ssl.ca-0.1]# mkdir /usr/local/apache2/conf/ssl.keyc) Move the created server (server1.crt) certificate to ssl.crt directory:[root@Server1 ssl.ca-0.1]# mv server1.crt /usr/local/apache2/conf/ssl.crt/d) Move the certificate key file (server1.key) to ssl.key directory:[root@Server1 ssl.ca-0.1]# mv server1.key /usr/local/apache2/conf/ssl.crt/3. Modify the default httpd configuration file (httpd.conf) to enable SSL. Sample directives for httpd with SSLcan be taken from the default ssl.conf configuration file.The following modifications are made to httpd.conf file based on the example in the default ssl.conf file:a) Change the port httpd listens on to HTTPS port 443:Listen 443b) Enter server name (Server1) and associated port (443):ServerName Server1:443c) Enable SSL engine:SSLEngine ond) Specify the cipher suites to be used for communication with clients (the default setting was taken): SSLCipherSuite ALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+EXP:+eNULLe) Specify the location of the server certificate created earlier:SSLCertificateFile /usr/local/apache2/conf/ssl.crt/server1.crtf) Specify the location of the server certificate key file:SSLCertificateKeyFile /usr/local/apache2/conf/ssl.key/server1.keyg) Configure custom log for the SSL sessions:CustomLog /usr/local/apache2/logs/ssl_request_log \"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"h) Configure the existing internal seeding source to be used at startup and for each new SSLconnection as a pseudo random number generator:SSLRandomSeed startup builtinSSLRandomSeed connect builtini) Configure the storage type for the global/interprocess SSL session cache (this speeds up parallelrequest processing), ssl_scache file is used as a cache in this example:SSLSessionCache dbm:/usr/local/apache2/logs/ssl_scachej) Set the session cache timeout to default 300 seconds:SSLSessionCacheTimeout 300k) Leave the rest of the fields at their defaults.[root@Server1 ssl.ca-0.1]# tail -n 14 /usr/local/apache2/conf/httpd.confSSLEngine onSSLCipherSuite ALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+EXP:+eNULL SSLCertificateFile /usr/local/apache2/conf/ssl.crt/server1.crtSSLCertificateKeyFile /usr/local/apache2/conf/ssl.key/server1.keyCustomLog /usr/local/apache2/logs/ssl_request_log \"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"SSLRandomSeed startup builtinSSLRandomSeed connect builtinSSLSessionCache dbm:/usr/local/apache2/logs/ssl_scacheSSLSessionCacheTimeout 300SetEnvIf User-Agent ".*MSIE.*" \nokeepalive ssl-unclean-shutdown \downgrade-1.0 force-response-1.04. Start httpd:[root@Server1 ssl.ca-0.1]# /usr/local/apache2/bin/apachectl start5. Verify Apache is listening on HTTPS port 443:[root@Server1 ssl.ca-0.1]# netstat -ltActive Internet connections (only servers)Proto Recv-Q Send-Q Local Address Foreign Address Statetcp 0 0 *:1024 *:* LISTENtcp 0 0 *:sunrpc *:* LISTENtcp 0 0 *:ftp *:* LISTENtcp 0 0 *:ssh *:* LISTENtcp 0 0 *:telnet *:* LISTENtcp 0 0 *:https *:* LISTEN6. Verify server process HTTPS requests by connecting to the HTTPS (443) port via openssl client simulation:[root@Server1 ssl.ca-0.1]# /usr/bin/openssl s_client -connect 192.168.20.10:443 CONNECTED(00000003)depth=0 /C=US/ST=MA/L=Billerica/O=Nortel/OU=Secure Web Server/CN=Server1verify error:num=20:unable to get local issuer certificateverify return:1depth=0 /C=US/ST=MA/L=Billerica/O=Nortel/OU=Secure Web Server/CN=Server1verify error:num=27:certificate not trustedverify return:1depth=0 /C=US/ST=MA/L=Billerica/O=Nortel/OU=Secure Web Server/CN=Server1verify error:num=21:unable to verify the first certificateverify return:1---Certificate chain0 s:/C=US/ST=MA/L=Billerica/O=Nortel/OU=Secure Web Server/CN=Server1i:/C=US/ST=MA/L=Billerica/O=Nortel/OU=Support/CN=LinuxCA---Server certificate-----BEGIN CERTIFICATE-----MIICrTCCAhagAwIBAgIBATANBgkqhkiG9w0BAQQFADBjMQswCQYDVQQGEwJVUzELMAkGA1UECBMCTUExEjAQBgNVBAcTCUJpbGxlcmljYTEPMA0GA1UEChMGTm9ydGVs MRAwDgYDVQQLEwdTdXBwb3J0MRAwDgYDVQQDEwdMaW51eENBMB4XDTA0MDYyNTAyNDEyOVoXDTA1MDYyNTAyNDEyOVowbTELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAk1B MRIwEAYDVQQHEwlCaWxsZXJpY2ExDzANBgNVBAoTBk5vcnRlbDEaMBgGA1UECxMRU2VjdXJlIFdlYiBTZXJ2ZXIxEDAOBgNVBAMTB1NlcnZlcjEwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMzeEuQxbJoFsH+RZAV8rQKgmPdEHIeg4Rev/jtkpSWwru8pGsQit/fgt7Ky4eDPCqj3Fu4dRZrbl4S5raboZT1+ZV4XbI1sBtMJELlv+XVoYVU2a/Q/fqZs386Rv8T85yPaqG98flV/l/uGsRBa4KkUAwg7UPUcVDhupUiKNWTdAgMBAAGjZzBlMB8GA1UdIwQYMBaAFK1L+WCjrCgo7hzGhEnr13DovvnaMDQGA1Ud JQQtMCsGCCsGAQUFBwMBBggrBgEFBQcDAgYKKwYBBAGCNwoDAwYJYIZIAYb4QgQBMAwGA1UdEwEB/wQCMAAwDQYJKoZIhvcNAQEEBQADgYEAG57na5KTbybNf4YVr2DjrwJia0YY4VAUmtWBcD60e+I7UETKvyJvKgxxdb31CH7eeXVtEASXGX1fRosiE6r9lDRVdhsgL6t67QCljWP1MWAuBSqca9sQTgVTncOlFHL15lvVuqMw1V5TRyae31STWdKTPtYtcPKXjn5eaMRsfiU=-----END CERTIFICATE-----subject=/C=US/ST=MA/L=Billerica/O=Nortel/OU=Secure Web Server/CN=Server1issuer=/C=US/ST=MA/L=Billerica/O=Nortel/OU=Support/CN=LinuxCA---No client certificate CA names sent---SSL handshake has read 1253 bytes and written 340 bytes---New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-SHAServer public key is 1024 bitSSL-Session:Protocol : TLSv1Cipher : DHE-RSA-AES256-SHASession-ID: 67DF401536C7A2C6A0C336A26D455CDA783418772D1A89058B040F36CB424203Session-ID-ctx:Master-Key:6F23DFF11CB1C7E01D5EA3DE0A0EB4D1DD9A8CB1323EB862221BC473C792FE427ACB7A5E039C0233E58FD7 95612EAC98Key-Arg : NoneKrb5 Principal: NoneStart Time: 1088207925Timeout : 300 (sec)Verify return code: 21 (unable to verify the first certificate)---7. An SSL connection is successfully opened.8. Close connection by entering any symbol followed by Enter:?<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"><html><head><title>501 Method Not Implemented</title></head><body><h1>Method Not Implemented</h1><p>? to /index.html.en not supported.<br /></p><hr /><address>Apache/2.0.49 (Unix) mod_ssl/2.0.49 OpenSSL/0.9.7c Server at Server1 Port 443</address></body></html>closedConfiguring Server2Root privileges are required for configuration:[user@Server1 user]$ suPassword:[root@Server1 user]#Configuring network parameters1. Configure IP address (192.168.20.20/24) on WebServer1:[root@Server1 user]# /sbin/ifconfig eth0 192.168.20.20 netmask 255.255.255.02. Configure static route to 192.168.10.0/24 network (PC’s network) via Alteon interface 2 (192.168.20.200): [root@Server1 user]# /sbin/route add –net 192.168.10.0/24 gw 192.168.20.200Requesting the certificate1. The ssl.ca scripts are used to create a certificate request. Obtain ssl.ca scripts, open the archive andchange directory to ssl.ca-0.1:[root@Server2 user]# tar -xzf ssl.ca-0.1.tar.gz[root@Server2 user]# cd ssl.ca-0.1[root@Server2 ssl.ca-0.1]#2. Run the ./new-server-cert.sh <request name> script to create a new certificate request. Fill out theappropriate fields of the request:[root@Server2 ssl.ca-0.1]# ./new-server-cert.sh server2No server2.key round. Generating oneGenerating RSA private key, 1024 bit long modulus ..................................................................++++++ ...............................++++++e is 65537 (0x10001)Fill in certificate dataYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [MY]:USState or Province Name (full name) [Perak]:MALocality Name (eg, city) [Sitiawan]:BillericaOrganization Name (eg, company) [My Directory Sdn Bhd]:NortelOrganizational Unit Name (eg, section) [Secure Web Server]:Common Name (eg, ) []:Server2Email Address []:You may now run ./sign-server-cert.sh to get it signedThe script creates certificate request (server2.csr) and server certificate private key (server2.key).3. Transfer the created request to Server1 acting as a CA via FTP. Make sure to use binary mode:[root@Server2 ssl.ca-0.1]# ftp 192.168.20.10Connected to 192.168.20.10 (192.168.20.10).220 (vsFTPd 1.1.3)Name (192.168.20.10:user): username331 Please specify the password.Password: password230 Login successful. Have fun.Remote system type is UNIX.Using binary mode to transfer files.ftp> bin200 Switching to Binary mode.ftp> put server2.csrlocal: server2.csr remote: server2.csr227 Entering Passive Mode (192,168,20,10,162,141)150 Ok to send data.226 File receive OK.725 bytes sent in 0.000677 secs (1e+03 Kbytes/sec)ftp> quit221 Goodbye.4. Once certificate request has been transferred, run ./sign-server-cert.sh <request name> script on theServer1. Note: during transfer, certificate request can be saved into a different directory, enter theappropriate path to the request file. When prompted enter the selected CA pass phrase (linux in thisexample) and enter y(yes) to sign certificate and commit:[root@Server1 ssl.ca-0.1]# ./sign-server-cert.sh ../server2CA signing: ../server2.csr -> ../server2.crt:Using configuration from ca.configEnter pass phrase for ./ca.key: Åenter pass phraseCheck that the request matches the signatureSignature okThe Subject's Distinguished Name is as followscountryName :PRINTABLE:'US'stateOrProvinceName :PRINTABLE:'MA'localityName :PRINTABLE:'Billerica'organizationName :PRINTABLE:'Nortel'organizationalUnitName:PRINTABLE:'Secure Web Server'commonName :PRINTABLE:'Server2'Certificate is to be certified until Jun 25 04:00:49 2005 GMT (365 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base UpdatedCA verifying: ../server2.crt <-> CA cert../server2.crt: OKThe script creates server certificate (server2/crt) in the same directory from which the request was taken.5. Transfer the signed certificate back to Server2 using FTP:[root@Server2 ssl.ca-0.1]# ftp 192.168.20.10Connected to 192.168.20.10 (192.168.20.10).220 (vsFTPd 1.1.3)Name (192.168.20.10:user): username331 Please specify the password.Password: password230 Login successful. Have fun.Remote system type is UNIX.Using binary mode to transfer files.ftp> bin200 Switching to Binary mode.ftp> get server2.crtlocal: server2.crt remote: server2.crt227 Entering Passive Mode (192,168,20,10,110,36)150 Opening BINARY mode data connection for server2.crt (3062 bytes). 226 File send OK.3062 bytes received in 0.00072 secs (4.2e+03 Kbytes/sec)ftp> quit221 Goodbye.Configuring apache for HTTPS1. Configure httpd configuration file (httpd.conf) file in the same manner it was configured for Server1. Refer tohttpd.conf configuration for Server1.[root@Server2 ssl.ca-0.1]# tail -n 13 /usr/local/apache2/conf/httpd.confListen 443ServerName Server2:443SSLEngine onSSLCipherSuite ALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLV2:+EXP:+eNULL SSLCertificateFile /usr/local/apache2/conf/ssl.crt/server2.crtSSLCertificateKeyFile /usr/local/apache2/conf/ssl.key/server2.keyCustomLog /usr/local/apache2/logs/ssl_request_log \"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"SSLRandomSeed startup builtinSSLRandomSeed connect builtinSSLSessionCache dbm:/usr/local/apache2/logs/ssl_scacheSSLSessionCacheTimeout 300SetEnvIf User-Agent ".*MSIE.*" \nokeepalive ssl-unclean-shutdown \downgrade-1.0 force-response-1.02. Start httpd:[root@Server2 ssl.ca-0.1]# /usr/local/apache2/bin/apachectl start3. Verify httpd is listening on HTTPS port (443):[root@Server2 ssl.ca-0.1]# netstat -ltActive Internet connections (only servers)Proto Recv-Q Send-Q Local Address Foreign Address Statetcp 0 0 *:1024 *:* LISTENtcp 0 0 *:sunrpc *:* LISTENtcp 0 0 *:ftp *:* LISTENtcp 0 0 *:ssh *:* LISTENtcp 0 0 *:telnet *:* LISTENtcp 0 0 *:https *:* LISTENConfiguring AlteonNote: Configuration of Alteon has been started from factory default settings.1. Log on to the switch:Enter password:System Information at 11:05:11 Wed Apr 21, 2004Alteon AD3sysName:sysLocation:. . .2. Select n to not run the setup script:The switch is booted with factory default configuration.To ease the configuration of the switch, a "Set Up" facility whichwill prompt you with those configuration items that are essentialto the operation of the switch is provided.Would you like to run "Set Up" to configure the switch? [y/n] nConfiguring interfaces1. Configure IP address (192.168.10.100/24) for interface 1 and enable interface:>> Main# /cfg/ip/if 1/mask 255.255.255.0/addr 192.168.10.100/enaCurrent subnet mask: 0.0.0.0New pending subnet mask: 255.255.255.0Current IP address: 0.0.0.0New pending IP address: 192.168.10.100Pending new broadcast address: 192.168.10.255Current status: disabledNew status: enabled2. Configure IP address (192.168.20.200/24) for interface 2 and enable interface:>> IP Interface 1# /cfg/ip/if 2/mask 255.255.255.0/addr 192.168.20.200/enaCurrent subnet mask: 0.0.0.0New pending subnet mask: 255.255.255.0Current IP address: 0.0.0.0New pending IP address: 192.168.20.200Pending new broadcast address: 192.168.20.255Current status: disabledNew status: enabled3. Apply and save the changes:>> IP Interface 2# apply/save------------------------------------------------------------------Apply complete; don't forget to "save" updated configuration.Request will first copy the FLASH "active" config to "backup",then overlay FLASH "active" with new config.Confirm saving to FLASH [y/n]: yNew config successfully saved to FLASH.Switch is currently set to use factory default config block on next boot.Do you want to change that to the active config block? [y/n] yNext boot will use active config block.Configuring real servers1. Configure real server 1. Enter real server 1 configuration menu, set real server 1 IP address (192.168.20.10)and enable the real server:>> IP Interface 2# /cfg/slb/real 1/rip 192.168.20.10/enaCurrent real server IP address: 0.0.0.0New pending real server IP address: 192.168.20.10Current status: disabledNew status: enabled。
阿尔卡特用户配置手册

ALCATEL交换机用户配置手册2019-7-202019年7月20日目录1 设备管理 (6)1.1 交换机登录 (6)1.2 打开其它访问权限 (6)1.3 恢复到出厂设置 (6)1.4 文件系统操作 (7)1.5 上传系统软件到交换机 (7)1.6 重启交换机 (8)1.7 保存交换机配置 (9)1.8 显示交换机所有配置 (9)2 配置以太网端口 (10)2.1 配置以太网端口指南 (10)2.3 启用和关闭一个端口 (10)2.4 启用和关闭流控 (11)2.5 验证以太网端口配置 (11)3 管理源学习(Managing Sourcing learning) (12)3.1 MAC 地址表项配置例子 (12)3.2 显示MAC 地址表信息 (13)4 配置 VLAN(Configure VLAN) (13)4.1 VLAN 配置举例 (13)4.2 创建/修改VLAN (14)4.3 定义 VLAN 端口分配 (15)4.4 修改端口的缺省 VLAN 配置 (15)4.5 打开/关闭一个 VLAN 生成树 (15)4.6 配置 VLAN 路由网关地址(Ip interface) (16)4.7、配置端口隔离 (16)5 配置802.1Q (18)5.1 打开端口的标记(tag) (18)5.2 打开链路聚合的标记(tagging) (18)5.3 配置端口数据帧类型 (18)5.4 显示802.1Q 信息 (19)5.5 802.1Q 配置实例 (19)6 配置静态链路聚合 (21)6.1 创建静态聚合 (21)6.2 删除静态链路聚合 (22)6.3 添加/删除静态链路聚合中的端口 (22)6.4 激活/关闭静态链路聚合状态 (22)6.5 显示静态链路聚合配置和统计信息 (22)7 配置动态链路聚合 (23)7.1 创建动态聚合 (23)7.2 删除动态链路聚合组 (24)7.3 添加/删除动态链路聚合中的端口 (24)7.4 激活/关闭动态链路聚合状态 (25)7.5 显示动态链路聚合配置和统计信息 (25)7.6 LACP 配置实例 (26)8 配置IP (27)8.1 IP 转发快速配置 (27)8.2 创建静态路由 (28)8.3 创建缺省路由 (29)8.4 创建 ARP (29)8.5 使用PING 命令 (29)8.6 使用Trceroute 命令 (30)8.7 查看IP 配置 (30)9 配置RIP (31)9.1、RIP简介 (31)9.2、RIP 默认配置 (31)9.3、RIP 典型配置 (31)9.4、RIP具体配置 (32)9.4.1、启用RIP (32)9.4.2、创建RIP 端口 (33)9.4.3、启用RIP 端口 (33)9.4.4、配置RIP 端口的发送版本 (33)9.4.5、配置RIP 端口的接收版本 (33)9.4.6、配置RIP 端口Metric (34)9.5、RIP选项 (34)9.5.1、配置RIP 抑制时间 (34)9.5.2、配置RIP主机路由 (35)9.5.3、RIP 路由再分配 (35)9.6、RIP安全 (36)9.6.1、配置认证类型 (36)9.6.2、配置密码 (36)9.7、查看RIP 配置 (37)10配置VRRP (38)10.1、VRRP 默认配置 (38)10.2、VRRP 典型配置 (38)10.3、VRRP具本配置 (39)10.3.1、基本虚拟路由器配置 (39)10.3.2、创建虚拟路由器 (39)10.3.3、给虚拟路由器分配IP地址 (39)10.3.4、配置虚拟路由器的优先级 (40)10.3.5、设置虚拟路由器的占先 (40)10.3.6、设置VRRP 认证 (40)10.3.7、禁用和启用虚拟路由器 (41)10.3.8、查看VRRP 配置 (41)11、配置OSPF (42)11.1、OSPF默认配置 (42)11.3、OSPF具体配置 (44)11.3.1、加载OSPF (44)11.3.2、启用OSPF (44)11.3.3、创建OSPF 端口 (44)11.3.4、启用OSPF 端口 (44)11.3.5、配置OSPF 端口进入OSPF域 (45)11.3.6、OSPF路由再分配 (45)11.3.7、OSPF安全 (46)11.3.8、查看OSPF 配置 (47)12 配置IP组播 (47)12.1 IP组播简介 (47)12.1、IP 组播默认配置 (48)12.2、配置IPMS (48)12.2.1、在交换机上启用和禁用IPMS (48)12.2.2、配置和恢复IGMP版本 (49)12.2.3、配置和删除静态邻居 (49)12.3、更改IPMS 配置 (50)12.3.1、更改IGMP询问时间间隔 (50)12.3.2、更改IGMP最后成员询问时间间隔 (50)12.3.3、更改IGMP询问响应时间间隔 (51)12.2.4、启用和禁用IGMP询问 (51)12.4、查看IPMS 配置和状态 (51)13 配置DHCP 中继(Relay) (52)13.1 Per-VLAN DHCP (53)13.2 查看DHCP 中继配置 (53)14 配置QoS (53)14.1 配置总体QoS 参数 (54)14.2 配置QoS 端口参数 (54)14.3 创建策略 (55)14.4 查看策略配置 (57)15 配置访问控制列表(ACLs) (57)15.1 ACL 快速配置 (57)15.2 ACL 配置步骤 (58)15.3查看ACL 配置 (59)15.4 ACL 配置实例 (59)16、设置服务器负载均衡SLB (61)17、sFlow配置 (62)18、配置端口镜像 (63)19、配置802.1X (63)19.1、802.1X 典型配置 (63)19.2、802.1x再认证 (64)19.3、设置802.1X 交换机参数 (64)20、阿尔卡特网络管理软件 (66)20.2 网络管理软件快速使用 (67)21阿尔卡特OmniStack 6200 操作命令 (67)21.1 交换机管理登录 (67)21.2 打开其它访问权限 (67)21.3 Vlan 配置 (68)21.4 802.1Q配置 (68)21.5 具体案例配置 (69)21.6 访问控制列表(ACL) (70)21.7 开启交换机网管功能 (70)121.8 OmniStack 6200保存配置 (70)21.9 OmniStack 6200堆叠功能 (71)1 设备管理1.1 交换机登录OmniSwitch支持多种登录方式,包括console, telnet, http等,在缺省情况下,交换机只开放console 管理。
Radware Alteon负载均衡器指导书 v1.0

第 2 章 Alteon 组网和配置流程 .....................................................................................................2
2.1 直连组网 .................................................................................................................................2 2.2 双臂组网 .................................................................................................................................3 2.3 单臂组网 .................................................................................................................................4 2.4 三角传输-DSR ........................................................................................................................5 2.5 配置负载均衡的基本流程 .......................................................................................................6 2.6 负载均衡的地址规划 ..............................................................................................................7 2.7 服务器地址规划 ......................................................................................................................8
Alteon基本配置示例

Alteon基本配置示例目录1. 设备基本配置 (2)设备连接示意图 (2)配置步骤 (3)2. 设备配置备份及升级 (5)设备连接示意图 (5)配置步骤 (6)3. SLB/RSTP SLB配置 (10)设备连接示意图 (10)配置步骤 (10)4. SYN Attack Detection (13)设备连接示意图 (13)配置步骤 (14)5. TCP Rate Limiting (16)此功能需要license (16)设备连接示意图 (17)配置步骤 (17)6. WAN Link Load Balancing (21)设备连接示意图 (21)配置步骤 (21)出线路负载均衡 (21)入线路负载均衡 (25)7. Alteon双机模式Active/Standby (31)设备连接示意图 (31)配置步骤 (31)1. 设备基本配置设备连接示意图Client #1I P=10.1.11.31/24Clien t #2I P=10.1.11.35/24I F 1=10.1.11.1/24I F 2=10.1.1.1/24I P=10.1.1.32/24I P=10.1.1.33/24配置要求:端口1、2配置为外部client 端,端口7、8配置为内部服务器端,地址如上图所示。
配置步骤1、配置超级终端:Baud rate = 9600Data bits = 8Parity = noneStop bits = 12、登录到设备上:缺省密码为:admin3、恢复配置成出厂默认值a、 /boot/conf factory:Boot Options# confCurrently set to use active config block on next boot.Specify new block to use ["active"/"backup"/"factory"]: facNext boot will use factory default config block instead of active. Confirm : Do you want to keep management port connectivity? [y/n]: y (如果选n的话,网管端口的配置也会被清空)Nov 3 11:22:05 NOTICE mgmt: boot config block changedb、 /boot/reset重启设备c、按Enter确认重启4、配置IP接口a、/cfg/L3/if 1b、mask 255.255.255.0c、addr 10.1.11.1d、en 将此ip接口激活e、同上可以配置第二个IP接口:/cfg/l3/if 2/mask 255.255.255.0/addr 10.1.1.1/en5、将IP转发打开,如果是关闭的,也就是不能做IP转发a、/cfg/L3/frwdb、on6、将端口关联到具体的VLAN/cfg/L2Layer 2# vlan 1 创建VLAN 1VLAN 1# name vlan-1 命名为:vlan-1VLAN 1# add 1 将端口1加到VLAN 1上VLAN 1# en 将该VLAN激活/cfg/L2Layer 2# vlan 2 创建VLAN 2VLAN 2# name vlan-1 命名为:vlan-2VLAN 2# add 8 将端口8加到VLAN 2上VLAN 2# en 将该VLAN激活7、将VLAN关联到具体的interface上/cfg/l3/if 1Vlan 1 将VLAN 1关联到interface 1上/cfg/l3/if 2Vlan 2 将VLAN 2关联到interface 2上8、配置VLAN的缺省网关Alteon可以配置最多255个缺省网关,每个VLAN都可以有单独的缺省网关,其中1-4编号是系统自用的,配置每个VLAN的网关是,gateway编号不一定是与vlan id 相对应的。
戴尔易安信快速配置系列指南说明书

Planning and Preparation Guide Rapid EqualLogic Configuration SeriesSwitch: Cisco 3750XArray: PS4100, PS6100, or PS6500Host: VMware ESXi, Windows or Red Hat Enterprise Linux April 2014RevisionsTHIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL INACCURACIES. THE CONTENT IS PROVIDED AS IS, WITHOUT EXPRESS OR IMPLIED WARRANTIES OF ANY KIND.© 2013 Dell Inc. All rights reserved. Reproduction of this material in any manner whatsoever without the express written permission of Dell Inc. is strictly forbidden. For more information, contact Dell.Dell, the DELL logo, the DELL badge, EqualLogic, Dell Networking and Force10 are trademarks of Dell Inc. VMware®, ESXi® and vSphere® are registered trademarks or trademarks of VMware, Inc. in the United States or other countries. Red Hat® and Red Hat® Enterprise Linux® are registered trademarks of Red Hat, Inc. in the United States and/or other countries. Windows® and Windows Server® are registered trademarks of Microsoft Corporation in the United States and/or other countries. Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products. Dell disclaims any proprietary interest in the marks and names of others.1Introduction1.1Document useKeyboard keys are shown in brackets with the actual key bolded.Example: [Enter]Commands that are to be typed are bolded and shown after the appropriate prompt.Example:console>enable1.2Intended audienceThis document series has been written for system or storage administrators with experience deployingWindows®, VMware®vSphere ESXi™ or Red Hat Enterprise Linux® servers, storage systems, and Ethernetnetworking. If you are unsure about completing the installation, Dell support is available and ready to assist you.1.3List of references∙TR1050 – Monitoring Your PS Series SAN with SAN HeadQuartershttps:///WorkArea/DownloadAsset.aspx?id=8749∙SAN HQ User Guide, available for download on ∙Dell EqualLogic Configuration Guide, available for download at:/dell-groups/dtcmedia/m/mediagallery/19852516/download.aspx ∙Dell EqualLogic Compatibility Matrix, available for download at:/techcenter/storage/w/wiki/2661.equallogic-compatibility-matrix-07262013.aspx2Prerequisites2.1Equipment∙A null-modem DB9 serial cable (included with the array)∙A switch serial console management cable (included with the switch)2.2Software2.2.1VMware host operating system∙Latest EqualLogic Multipathing Extension Module for VMware® vSphere installation package(/support).∙The VMware vSphere® Command-Line Interface (vCLI) environment must be installed on themanagement server (/downloads).∙Latest network device driver update (/downloads).2.2.2Windows host operating system∙Latest network adapter device driver update ()∙Latest Host Integration Tools (HIT) kit installation package (/support)∙Latest SAN HeadQuarters installation package (/support)2.2.3Red Hat Enterprise Linux operating system∙Latest network adapter device driver update ()∙Latest Host Integration Tools (HIT) kit installation package (/support)2.3Configuration settings2.3.1VMware host operating systemThis document assumes that you have already installed VMware ESXi and have applied the latest criticalpatches available through VMware Update Manager.To properly configure your vSphere ESXi system, you must also have a management system available. Thissystem must be running Windows (2008, Windows 7, etc.)2.3.2Windows host operating systemThis document assumes that you have already installed Windows 2008 R2 with Service Pack 1 or later andhave applied the latest critical security updates available through Windows Update.2.3.3Red Hat Enterprise Linux operating systemThis document assumes that you have already installed RHEL 6.5 or later and have applied the latestcritical security updates available through Linux.2.3.4SwitchReference the EqualLogic Compatibility Matrix at /dell-groups/dtcmedia/m/mediagallery/19856862/download.aspx to determine the recommended switchfirmware version. To get the latest update, visit /techsupport Installationinstructions are provided as part of the download. The switch user manual is also available to downloadfor reference.2.3.5ArrayReference the EqualLogic Compatibility Matrix at /dell-groups/dtcmedia/m/mediagallery/19856862/download.aspx to determine the recommended arrayfirmware version. To get the latest update, visit /support. Update instructionsand release notes are available with the latest downloads.2.4Configuration informationYour iSCSI SAN configuration requires several static IP addresses. Complete this form and have it availablefor reference during the configuration.Switch Admin password: _________________________Array Group Admin password: __________________________*Array Membership password: ___________________________**These may be the same password – see the PS Series Group Administration guide for more information.3Connectivity DiagramsUse the appropriate diagram and point-to-point table when cabling the SAN.Figure 1Cisco 3750X and the PS41003.1Point to Point connection tables11Cisco 3750X | Configuration Introduction | Rapid EqualLogic Configuration Series。
Alteon_证书链配置

2.2 双向认证模式
在双向认证模式下,除客户端验证服务器端是否合法外,服务器端也需要验证客户端 是否为合法用户。服务器端需要安装颁发客户端证书的CA 的根证书和中间证书,要求 客户端提交客户端证书,并通过已经安装的根证书和中间证书对客户端证书进行逐级验 证。以确定客户端是否为合法用户。当客户端连接一个双向认证模式的 应用时,除了 客户端验证服务器端是否安全外,还需要进行以下步骤:
3
2.SSL 的认证模式
2.1 单向认证模式
在采用单向认证时,主要是客户端验证服务器端是否合法。在建立 SSL 握手的时候, 服务器将其证书传送给客户端进行验证。客户端主要验证有三个方面:
1、服务器证书是否在有效时间内即服务器证书的有效时间与当前时间相比较,如果 过期,则认为该证书已经失效。
2、服务器证书中的域名是否与用户访问的域名一致,即客户端访问的域名,如在浏 览器中填入:https://,则访问的域名为。服 务器的证书中的域名必须与此域名一致。
WEB方式选择SLB→SSL→Certificate Repository→Import CLI方式 /cfg/slb/ssl/certs/import
5
ID中输入序号,该ID会在SSL Policy中调用。 Type 选择KEY。 Passphrase中输入申请证书时的密码。 对于KEY可以选择在Text中直接拷入文本或在File中选择相应的KEY文件进行导 入。
首先需导入客户端证书
12
WEB方式选择SLB→SSL→Certificate Repository→Import CLI方式 /cfg/slb/ssl/certs/import
ID中输入序号,这里的ID与之前根证书和KEY的ID可以不一样。 Type 选择Trusted CA Text中贴入客户端证书。 其次,配置Client Authentication Policies WEB方式选择SLB→SSL→Client Authentication Policies→Add CLI方式 /cfg/slb/ssl/authpol 1/
Alteon简易配置手册

ALTEON 2216简易手册Index1.简介 (2)2.ALTEON 2216 的基本配置 (2)2.1系统管理 (2)2.1.1设置系统时间 (2)2.1.2设置 NTP 时钟同步 (3)2.1.3修改管理员口令 (3)2.1.4配置允许访问管理端口的网段 (4)2.2端口设置 (4)2.2.1设置端口名字 (4)2.2.2禁用和启用端口 (4)2.3与上联交换机互联配置 (4)2.3.1配置流程说明 (4)2.3.2VLAN 配置 (5)2.3.3互联地址配置 (5)2.3.4配置网关 (5)2.4 2 台交换机的 HA 配置 (5)2.4.1配置流程说明 (5)2.4.2启用路由转发功能 (6)2.4.3配置本地路由转发 (6)2.4.4给 2 台交换机的互联端口打 tag (6)2.4.5配置 VLAN (6)2.4.6将端口划入 VLAN (6)2.4.7在下联网段中为 2 台交换机配置 IP 地址 (7)2.4.8启用 VRRP 机制 (7)2.4.9配置 VRRP (7)2.4.10配置 slb sync switch (8)2.5路由配置 (8)2.6SLB 配置 (8)2.6.1ALTEON 的 SLB 基本概念 (8)2.6.2SLB 配置基本步骤 (以广告引擎为例 ) (8)3ALTEON的日常维护 (9)3.1INFO 命令 (9)3.1.1检查链路状态 (9)3.1.2检查 SLB 真实服务器的工作情况 (10)3.1.3检查 SLB 虚拟服务器的工作情况 (10)3.1.4检查 Alteon 系统情况 (10)3.1.5检查系统日志 (11)3.1.6检查 VLAN 配置 (12)3.1.7检查端口的配置 (12)3.1.8检查系统的 IP 配置 (12)3.2S命令 (13)TAT3.2.1检查 CPU 状态 (13)3.2.2检查内存使用状态 (13)3.2.3检查端口错误计数器 (14)3.2.4检查各个接口的 IP 流量情况 (15)3.2.5检查系统的 IP 流量情况 (15)1.简介Alteon WebSystems的万维网操作系统(WebOS)为Alteon万维网交换机产品提供一系列增值服务,包括本地及全球服务器负载均衡、应用重新定向、非服务器(例如防火墙、路由器等)负载均衡、多层的全激活高可用性、带宽管理、服务等级和服务器安全服务,让管理员对其IP 网络获得前所未有的控制。
Alteon典型配置案例

Alteon典型配置目录1项目概览 (2)2实施结构阐述 (2)3用户目前的业务范围 (3)4系统变动 (3)5IP地址分配 (4)6具体配置过程 (5)6.1配置设备的基本的参数 (5)6.2原有业务层配置 (6)6.3新加业务层配置 (10)6.3.1Outbound方向防火墙负载均衡(内部Alteon实现) (10)6.3.2Oubound方向链路负载均衡: (11)6.3.3Inbound方向链路负载均衡 (13)6.3.4Outbound 流量返回时的防火墙负载均衡 (14)7需要修改的相关设备 (15)标准的三明治结构,包括了多链路、防火墙及服务器的负载均衡的所有配置,在今后类似的项目上可以直接套用此配置。
1 项目概览某电力企业目前有两条链路分别接入互联网,内网有两台防火墙做安全的网关,核心交换机采用北电的Passport交换机。
并且为下联的二级地市提供互联网接入。
根据用户要求,采用两台Alteon四-七交换机做两条链路和两台防火墙及后台服务器的负载均衡,提供高可靠性和高可用性。
2 实施结构阐述将两台Alteon应用交换机分别部署在出口路由器和防火墙、核心交换机和防火墙之间,组成一个“三明志“结构。
3 用户目前的业务范围某电力企业目前在网上承载业务在将来的网络优化改造后全部平滑过渡到新的网络环境中使用,主要的业务包括:外部:●供外部用户访问的Web站点●供外部用户访问的FTP站点●供外部用户访问的邮件站点●供外部用户访问的电费系统●供外部用户访问的电网系统新加业务:●服务器的负载均衡●链路负载均衡●防火墙负载均衡4 系统变动1.防火墙要求启用路由模式。
防火墙的网关地址,该为指向外部Alteon的interface ip ;核心交换机的网关地址,该为指向内部Alteon的interface ip ;2.Alteon2的3、4端口做Trunk,同时连接两台核心交换机。
3.为两台Alteon设备分配IP地址,具体如下表:4.修改用于Inbound方向的公网DNS服务器的纪录指向。
埃图桑 GFX 安装与操作手册说明书

2GFX ManualEATON GFX Installation and Operation Manual April 2020 CAN Controller Area Network EMC Electromagnetic Compatibility FCC Federal Communications Commission GNSS Global Navigation Satellite System GPS Global Positioning System IMU Inertial Measurement Unit IP Ingress ProtectionNMEA National Marine Electronics Association RED Radio Equipment Directive SAE Society of Automotive Engineers PWMPulse Width ModulationKey acronyms and abbreviations:Weight 160 gram Mounting torque 1.8Nm±0.2Nm Mounting size 5.35mm hole 2 locations ColorRAL 9005 Jet blackPotted assemblyTechnical specifications:Accuracy4.77m CEPCircular Error Probability (radius of a circle centered on the true value)Acquisition timeHot start 4 Sec Warm start 38 Sec Cold start 60 SecSensitivity Tracking -160dBm Acquisition -145dBm GPS data update rate5HzAngular rate ±245 dps Magnetic field ±4 gauss IMU data update rate50HzNominal voltage 12VDC and 24VDCInput currentUp to 120mAAt full operating voltage rangeOverview:The GFX sensor is a high-performance GPS and dynamic motion sensor for use in on/off-highway vehicle applications. The unitfeatures an embedded GPS receiver and inertial measurement unit (IMU) sensor with configurable outputs to meet the needs of a variety of demanding applications. Model Part No. 6044572-001•GPS receiver provides positioning and velocity estimates at 5Hz •NMEA 2000 (CAN) and NMEA 0183 (RS232) output messaging •Provides ISOBUS ground speed message•Available true ground speed PWM output (available on request)•IMU provides 3-axis: linear acceleration, angular rate and magnetic field•Low current consumption (up to 120mA)•Wide operating temperature range (-40°C to 85°C)•Dustproof and waterproof design, suitable for open-cab environments•Compact and rugged package allows for flexible vehicle mounting•Easy to install and useX, Y & Z axisDirection of detectable accelerations Direction of detectable angular ratesCircular arrow direction indicates positive angular ratePWM frequency 36Hz to 1.85KHz for 1kph to 50kph speed Linearly varyingSignal amplitude Equal to supply input Accuracy ± 5% Source impedance 100Ω ± 10ΩLoad impedance>3kΩotee:N 1. Digital speed output is disabled at speed less than 1Kph2. When digital speed output is disabled, output will be equal to supply input(100% duty cycle).Cautione: Pay attention to Digital Output Pin Wiring. This pin should not be short circuit with ground terminal.Key features:3GFX ManualEATONGFX Installation and Operation Manual April 2020 input to GNDCANH & CANL pins: Up to 36V TX & RX pins: Up to 32V Reverse polarity Yes Up to -36VHot plugYesLive connection and disconnection topower supplyMating connector Deutsch DTM06-08SAFemale type (8 pin)GPS antenna connectorSMA Female Board/bulkhead mount connectorFemale type Storage temperature -40°C to +85°C Humidity 90% RH Altitude 40000 ft Air shipment , Device off state Mechanical shock50Grms, 11mSec 30Grms, 18mSec6 pulses at each axis, Total: 36 pulses10 pulses at each axis, Total: 60 pulsesIngress protection IP67ISO 20653 (Road vehicles - Degrees of protection (IP code)Protection of electrical equipment against foreign objects, water and accessSalt spray 96 hrs. in salt fog atmosphere Chemical resistanceCab mountingAlcohol, Detergents, Diesel fuel, Waxes, Spray paint, Hydraulic fluid etc.Free fall <1mVibration Sine sweepRandom vibration10Hz to 2000Hz, 3.5Grms10Hz to 2000Hz, 2.18GrmsSerialRS232Default : 115200 bpsConfigurable baud rate9600/19200/38400/57600/115200 bpsDiagnostic / health monitoringRedContinuous ON when faults persist• Overvoltage (>36V) & under voltage (<5V)• GPS antenna open & short • Over temperature fault (95°C)•GPS and IMU faultEN ISO 14982:2009Agriculture and Forestry machineryConducted Electrical Transient Pulses ISO7637:2004Level: IV for 12V & 24V (all pulses)Radiated EmissionCISPR 25:201630MHz to 1000MHz Bulk Current Injection ISO11452-4:2011Functional Class A 20MHZ-200MHZ, 60mA Radiated Immunity ISO11452-2:2004Functional Class A200MHZ to 1GHZ, 30V/m ESDISO 10605:2008Functional Class A - Contact & Air discharge (Powered and Unpowered)Direct discharge (3 pulses with > 1s interval)Contact: ±4kV Air: ±4kVIndirect Discharge: (50 pulses with > 50ms interval) ±4kVRadio Equipment Directive (RED) 2014/53/EU ETSI EN 301 489-19 V2.1.0:2017EMC for Radio Equipment and ServicesConducted Electrical Transient Pulses ISO7637:2004Level: IV for 12V & 24V (all pulses)Conducted ImmunityIEC 61000 4-6:2013Functional Class A 150KHZ- 80MHZ, 3VrmsConducted Emission ReferenceClause 8.3CISPR 32:2015 / EN 55032:2015Quasi-peak: Product Class A 0.15-0.5MHZ: 79dB(uV) 0.5-30MHZ: 73dB(uV) Average: Product Class A 0.15-0.5MHZ: 66dB(uV) 0.5-30MHZ: 60dB(uV) Radiated Immunity IEC 61000 4-3:200680MHZ to 6GHZ, 3V/m, Class A Radiated EmissionEN 5503230MHz to 6GHzETSI EN 303 413 V1.1.1 (2017-06)Harmonised EU standard for GNSS essential requirementSpurious EmissionReference:Clause No 4.2.230MHz-8.3GHz (Radiated & Conducted Method)Adjacent Frequency band Reference:Clause No 4.2.1 Δ C/N0 ≤ 1 dB Conducted MethodLow Voltage (LVD) Directive 2014/35/EU2014/53/EUIEC 62368-1:2014Safety: Audio/video, information and communication technologyequipment - Part 1: Safety requirements (Hazard Based Safety Standard)EN 62479:2010Health: Assessment of the compliance of low-power electronic and electrical equipment with the basic restrictions related to human exposure to electromagnetic fields (10 MHz to 300 GHz)RoHS 2 Directive 2011/65/EURestriction of the Use of Certain Hazardous Substancesin Electronic and Electrical Equipment(Suppliers Declaration of Conformity)Radiated Emissions Section 15.109 (30MHz to 1GHz)GFX ManualCAN output messagesGFX provides GPS, IMU, ISO bus PGN 65097 and proprietary PGN 65281 on CAN bus. Default source address of CAN message is 75 (0x4B).CAN message data switches between unsigned integer (UINT) and signed integer (INT) based on the parameter.1. GPS message informationGFX provides following NMEA 2000 PGNs at 5Hz transmission rate over CAN bus.PGN 126992This PGN provides a regular transmission of UTC time and date.PGN 129025This PGN provides latitude and longitude referenced to WGS84.PGN 129033This PGN provides time, date and local offset time information.PGN 129026This PGN provides Course Over Ground (COG) and Speed Over Ground (SOG).PGN 127250This PGN provides Heading sensor angle, Deviation, Variation information.PGN 127258This PGN provides Age of service, Variation information.PGN 129539This PGN provides GNSS status and dilution of precision components (DOP).PGN 129029This PGN conveys a comprehensive set of Global Navigation Satellite System (GNSS)parameters, including position information.N The PGN 129029 transmits more than 8 bytes of data. So, to transmit this PGN NMEA 2000 Fast Packetotee:protocol is used.4EATON GFX Installation and Operation Manual April 2020 5GFX ManualEATONGFX Installation and Operation Manual April 2020 Field Acceleration X Acceleration Y Acceleration Z Who I AM Reg Status reg Datatype Int 16Int 16Int 16Unit 8Uint 8Resolution 0.0010.0010.001--Unit g ggNANAByte Sequence Accl Byte 0Accl Byte 1Accl Byte 0 Accl Byte 1Accl Byte 0Accl Byte 1 Bit SequenceBit 7 Bit 0Bit 15 Bit 8Bit 7 Bit 0Bit 15 Bit 8Bit 7 Bit 0Bit 15 Bit 8Default value of Who I AM register of Acceleration and Gyroscope is 0x68, it indicates Accelerometer and Gyroscope are responding.Field Angular Rate X Angular Rate Y Angular Rate Z Who I AM Reg Status reg Datatype Int 16Int 16Int 16Unit 8Uint 8Resolution 0.010.010.01--Unit dps dpsdpsNANAByte Sequence Gyro Byte 0Gyro Byte 1Gyro Byte 0 Gyro Byte 1 Gyro Byte 0Gyro Byte 1Bit SequenceBit 7 Bit 0Bit 15 Bit 8Bit 7 Bit 0Bit 15 Bit 8Bit 7 Bit 0Bit 15 Bit 8Default value of Who I AM register of Acceleration and Gyroscope is 0x68, it indicates Accelerometer and Gyroscope are responding.Field Magnetic Field X Magnetic Field Y Magnetic Field Z Who I AM Reg Status reg Datatype Int 16Int 16Int 16Unit 8Uint 8Resolution 0.0010.0010.001--Unit gauss gaussgaussNANAByte Sequence Mag Byte 0Mag Byte 1Mag Byte 0Mag Byte 1Mag Byte 0Mag Byte 1Bit SequenceBit 7 Bit 0Bit 15 Bit 8Bit 7 Bit 0Bit 15 Bit 8Bit 7 Bit 0Bit 15 Bit 8Default value of Who I AM register of Magnetometer is 0x3D, it indicates Magnetometer is responding.2. IMU message informationGFX transmits IMU data over CAN bus at 50Hz transmission rate in below defined format.PGN 65429This PGN provides IMU X, Y and Z Axis Acceleration data.PGN 65430This PGN provides IMU X, Y and Z Axis Gyroscope data.PGN 65431This PGN provides IMU X, Y and Z Axis Magnetometer data.6GFX ManualEATONGFX Installation and Operation Manual April 2020 Datatype NA NA Int 16Uint 16NA Uint 8Resolution NA NA 0.010.01--Unit NA NA °C VoltsNANA Byte Sequence NA NA Temp Byte 0Temp Byte 0Voltage Byte 0Voltage Byte 0Bit SequenceNANABit 7 Bit 0Bit 15 Bit 8Bit 7 Bit 0Bit 15 Bit 8NANADatatype Uint 16NANA NA NAResolution 0.001Unit mps Byte Sequence SoG Byte 0SoG Byte 1Bit SequenceBit 7 Bit 0Bit 15 Bit 821Over temp fault 0x02Temperature > 100 deg c 32GPS Antenna Open 0x04GPS Antenna not connected 43GPS Antenna Short0x08Antenna Short54GPS message not received 0x10Not receiving any message from GPS module 65All Axis data of Accl are zero 0x20Value of all Axis of Acceleration are zero 76Reserved-87All Axis data of Mag are zero 0x80Values of all Axis of Magnetometer are zero4. PGN 65281 informationThis PGN provides supply voltage, temperature, status code.Status code (Byte 7 in PGN 65281)Status word indicate various fault conditions, supply voltage fault, over temperate fault, GPS Antenna fault, GPS message not received fault, IMU acceleration and magnetometer fault.3. ISO Bus PGN 65097 message informationThis PGNs provides speed over ground at transmission rate of 10Hz over CAN bus.7GFX ManualEATONGFX Installation and Operation Manual April 2020 1UTC of position fix2, 3Direction of latitude, N (North) or S (South)4, 5Direction of longitude, E (East) or W (West)6GPS Quality indicator: 0 - Fix not valid, 1 - GPS fix, 2 - Differential GPS fix 7Number of satellites in use, range from 00 through to 24+8Horizontal Dilution of Precision (HDOP)9, 10 Antenna altitude in Meters (MSL reference) , M = Meters11, 12"Geoidal Separation in Meters, M=Meters. Geoidal separation is the difference between the WGS-84 earth ellipsoid and mean-sea-level."13Age of differential GPS data record. Time in seconds since last Type 1 or Type 9 update. Null field when DGPS is not used.14Reference station ID, range 0000-4095. A null field when any reference station ID is selected and no corrections are received.hhThe checksum data, always begins with *1UTC (When UTC offset has been decoded by the receiver)2Day, ranging between 01 and 313Month, ranging between 01 and 124Year5Local time zone offset from GMT, ranging from 00 through ±13 hours 6Local time zone offset from GMT, ranging from 00 through 59 minutes hhThe checksum data, always begins with *10 - Sleep (Disable NMEA 0183 output)1 - Wake (Enable NMEA 0183 output)1"Baudrate setting: 9600 19200 38400 57600 115200"NMEA 0183 configuration messagesGFX NMEA0183 output can be enabled or disabled using PMTK_SLEEP_CLT serial command. NMEA0183 output is enabled by default.Baudrate of NMEA0183 messages can be configured using PMTK_SET_NMEA_BAUDRATE serail command. Default baud rate is 115200 bpsNMEA 0183 output messages8GFX ManualEATONGFX Installation and Operation Manual April 2020 1"Mode: M = Manual, A = Automatic. In manual mode, the receiver is forced to operate in either 2D or 3D mode. In automatic mode,the receiver is allowed to switch between 2D and 3D modes subject to the PDOP and satellite masks."2Mode 2, Fix type, 1 = not available, 2 = 2D, 3 = 3D 3 - 14"PRN numbers of the satellites used in the position solution. When less than 12 satellites are used, the unused fields are null"15Position dilution of precision: 0.5 through 99.916Horizontal dilution of precision: 0.5 through 99.917Vertical dilution of precision: 0.5 through 99.9hhThe checksum data, always begins with *1, 2Track made good relative to true north 3, 4Track made good relative to magnetic north 5, 6Speed over ground (SOG) in knots 7, 8Speed over ground in kilometers/hour (kph)9Mode indicator:A=Autonomous mode D=Differential modeE=Estimated (dead reckoning) mode M=Manual input mode S=Simulated mode N=Data not validhhThe checksum data, always begins with *0Message ID $GPRMC 1UTC of Position Fix (when UTC offset has been decoded by the receiver).2Status:A - ValidV - Navigation receiver warning3, 4Latitude, N (North) or S (South).5, 6Longitude, E (East) or W (West).7Speed over the ground (SOG) in knots 8Track angle in degrees true 9Date: dd/mm/yy 10, 11Magnetic variation in degrees, E = East / W= West 12"Position System Mode Indicator:A = Autonomous D = Differential E = Estimated M = Manual input S = Simulation mode N = Data not valid"hh The checksum data, always begins with *9GFX ManualEATON GFX Installation and Operation Manual April 2020 Product dimensionsALL DIMENSIONS ARE IN MMPin out detailsotee:NUse supply ground for RS232 GND.2CAN High 3RS232 RX4Digital Out- Speed signal 5Not used 6RS232 TX 7CAN Low 8Ground1"N (antenna status) 0 = Open 1 = Normal 2 = Short"GFX ManualInstalling the GFXMounting considerations•The GFX shall be fixed using two mounting holes provided diagonally across the enclosed assembly.•Use the standard threaded M5 size screws to affix the GFX. (Note: Customer shall choose length of the screws as per mounting base)•Mounting torque shall be 1.8±0.2Nm.Mating antenna detailsUse 3V external Active AntennaRecommended Active AntennaPart Number: 66800-52, Manufacturer: Trimble Inc.otee:N Antenna interface SMA connector recommended mating torque - 4-5 inch-pounds.Antenna interface SMA connector durability- 500 Cycles. Cautione: Supply voltage provision is 3V for external active antenna. Ensure appropriate antenna is chosen forfunctioning of GPS.Recommended wiring practices•Confirm the CAN cable is properly terminated using 120 ohm resistor.•Use twisted or twisted shielded pair cable for CAN as per the applicable standard.•Verify that the harness is constructed to meet the needs of the application environment (e.g. shock, vibration, moisture, temperature, chemicals, and impact).•Ensure that the harness is designed and constructedto minimize induced interference resulting from EMI coupling between signal wires.•Separate power circuits from low-level signals.•Provide sufficient clearance from moving parts.•Wires routed through holes in the vehicle body/chassis should use grommets.•Avoid sharp metal edges, fasteners, and other abrasive surfaces or use protective shielding when routing harness assembly.•Route wires to avoid exhaust system components or other high temperature areas, use appropriate heat shielding or other insulation where routing is a problem.•Avoid routing near wheel wells or provide adequate mechanical protection to the assembly•Use a protective fuse sized appropriately for the GFX supply current.Device troubleshootingThe following is a check list, if there is any problem inthe device.•Make sure the Power indication Green LED is ONIf Red LED is ON, check the following:•Power input is within 5-36V.•External Antenna interface- Antenna is not properly connected or antenna is shorted. Short alert is triggered if external active antenna draws approximately morethan 19mA.•Operating temperature is not exceeding >85Degrees Celsius.•GPS information is not available in corresponding PGNs.•IMU Accelerometer and Magnetometer three axis information is not available in corresponding PGNs.WarningsWhen installing this component, all requirements of the outlined standard must be fulfilled.•This component is designed to be affixed in the application, and a suitable enclosure should be provided in the end system.Declaration of conformityHereby, Eaton Corp. declares that this GFX is in compliance with the essential requirements and other relevant provisions of the following directives:1. Electromagnetic Compatibility (EMC) Directive2014/30/EU2. Radio Equipment Directive (RED) 2014/53/EU3. Low Voltage (LVD) Directive 2014/35/EU4. RoHS 2 Directive 2011/65/EUManufacturer DetailsEaton Corporation Hydraulics Operations,14615 Lone Oak Road, Eden Prairie MN 55344,United States.10EATON GFX Installation and Operation Manual April 2020 Eaton1000 Eaton Boulevard Cleveland, OH 44122 United States © 2020 EatonAll Rights Reserved Printed in USA April 2020Eaton is a registered trademark. All trademarks are propertyof their respective owners.。
北电Alteon应用层交换机技术手册_Element Manager 4.0.2 Users Guide

4655 Great America ParkwaySanta Clara, CA 95054Phone 1-800-4NortelNortel Application Switch Element Manager 4.0.2User’s Guidepart number: 320512-A, January 2006Nortel Application Switch Element Manager 4.0.2 User’s GuideCopyright © Nortel Networks Limited 2006. All rights reserved. Part Number: 320512-A.This document is protected by copyright and distributed under licenses restricting its use, copying,distribution, and decompilation. No part of this document may be reproduced in any form by any meanswithout prior written authorization of Nortel Networks, Inc. Documentation is provided “as is” withoutwarranty of any kind, either express or implied, including any kind of implied or express warranty ofnon-infringement or the implied warranties of merchantability or fitness for a particular purpose.U.S. Government End Users: This document is provided with a “commercial item” as defined by FAR2.101 (Oct. 1995) and contains “commercial technical data” and “commercial software documentation” asthose terms are used in FAR 12.211-12.212 (Oct. 1995). Government End Users are authorized to use thisdocumentation only in accordance with those rights and restrictions set forth herein, consistent with FAR12.211- 12.212 (Oct. 1995), DFARS 227.7202 (JUN 1995) and DFARS 252.227-7015 (Nov. 1995).Nortel Networks, Inc. reserves the right to change any products described herein at any time, and withoutnotice. Nortel Networks, Inc. assumes no responsibility or liability arising from the use of productsdescribed herein, except as expressly agreed to in writing by Nortel Networks, Inc. The use and purchase ofthis product does not convey a license under any patent rights, trademark rights, or any other intellectualproperty rights of Nortel Networks, Inc.Nortel Application Switch Element Manager 4.0.2 is a trademark of Nortel Networks, Inc. in the UnitedStates and certain other countries.Any other trademarks appearing in this manual are owned by their respective companies.Originated in the USA.ExportThis product, software and related technology is subject to U.S. export control and may be subject to exportor import regulations in other countries. Purchaser must strictly comply with all such laws and regulations.A license to export or reexport may be required by the U.S. Department of Commerce.2320512-A, January 2006Nortel Application Switch Element Manager 4.0.2 User’s Guide3320512-A, January 2006ContentsContents. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3Figures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7Using the Nortel Application Switch Element Manager. . . . . . . . . . . . . . . . 9Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9Setting ASEM Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9Opening a Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12Opening a Switch Using SNMP versions 1 or 2 . . . . . . . . . . . . . . . . . . . . . . . . . . .12Opening a Switch using SNMPv3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14Previously Opened Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15Troubleshooting the Opening of a Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15Connecting to a ASEM Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17The ASEM Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18Summary View . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19GUI Front Panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20ASEM Interface Elements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21ASEM Menubar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21ASEM Toolbar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28ASEM Screen and Tab Buttons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31ASEM Tree Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33ASEM Context Menus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .34Working with Switch Screens . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .41Viewing a Switch Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .41Undocking a Switch Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .42Docking a Switch Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .43Closing a Switch Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .43Switch Configuration Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45Configuration Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45Working with Tables and Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46Working with Edit Tables and Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46Nortel Application Switch Element Manager 4.0.2 User’s GuideFiltering Table Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48Sorting T able Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49 Monitoring Performance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .50 Working with Polling Tables and Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .50 Exporting Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .50Printing Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .50 Working with Graphing Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51 Altering the Graph Display . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52 Customizing the ASEM Display . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53 Modifying Label Appearance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53Modifying the list of well-known ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .54Modifying or adding Well-known Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .54Altering the Default Browser . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55Localization of ASEM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56Changing the MIB Default Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56 Server Load Balancing Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57Link Load Balancing Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 714320512-A, January 2006Nortel Application Switch Element Manager 4.0.2 User’s Guide FiguresFigure 1Properties Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10Figure 2Open Device screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13Figure 3Connection Error Message . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15Figure 4Open Device screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17Figure 5ASEM Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18Figure 6Summary View screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19Figure 7GUI Front Panel screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20Figure 8Tree Preferences screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33Figure 9Application Root Context Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35Figure 10Switch Root Context Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36Figure 11Switch Tree Context Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37Figure 12Port Context Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39Figure 13Screen Context Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40Figure 14Undocked Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .43Figure 15Table Filter screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48Figure 16Selected graphing data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51Figure 17Graphing T able - Bar Graph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52Figure 18SLB Wizard - Introductory Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58Figure 19SLB Wizard - Physical Configuration Screen . . . . . . . . . . . . . . . . . . . . . .59Figure 20SLB Wizard - Virtual Service Configuration Screen . . . . . . . . . . . . . . . . .60Figure 21SLB Wizard - L2/L3 Configuration Options Screen . . . . . . . . . . . . . . . . . .61Figure 22SLB Wizard - Add an IP Interface Screen . . . . . . . . . . . . . . . . . . . . . . . . .61Figure 23SLB Wizard - Real Server Configuration Screen . . . . . . . . . . . . . . . . . . .62Figure 24L2/L3 Configuration options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62Figure 25Add an IP Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63Figure 26SLB Wizard - Real Group Configuration Screen . . . . . . . . . . . . . . . . . . . .64Figure 27LLB Wizard - Introductory Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .65Figure 28LLB - ISP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .66Figure 29LLB - ISP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .67Figure 30LLB - Outbound Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .68Figure 31LLB - Inbound Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69Figure 32LLB - Inbound Configuration - Add an IP Interface . . . . . . . . . . . . . . . . . .705 320512-A, January 2006Nortel Application Switch Element Manager 4.0.2 User’s Guide6320512-A, January 2006Nortel Application Switch Element Manager 4.0.2 User’s Guide TablesTable 1Property screen fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11Table 2Main menubar items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21Table 3Nortel, Actions, and Help menus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22Table 4 Toolbar items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28Table 5ASEM Screen and Tab Buttons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31Table 6Application Root Context Menu items . . . . . . . . . . . . . . . . . . . . . . . . . . . .35Table 7Switch Root Context Menu items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36Table 8Switch Tree Context Menu items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37Table 9Port Context Menu items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39Table 10Screen Context Menu items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40Table 11Configuration Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45Table 12Graph sub-types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .527 320512-A, January 2006Nortel Application Switch Element Manager 4.0.2 User’s Guide8320512-A, January 2006Using the Nortel Application Switch Element ManagerOverviewThe Nortel Application Switch Element Manager (ASEM) provides a graphical userinterface (GUI) for remotely managing a Nortel Application Switch through the SimpleNetwork Management Protocol (SNMP). This document provides an overview of howto use the ASEM.The following topics are covered by this book:•“Setting ASEM Properties”on page 9•“Opening a Switch”on page 12•“The ASEM Interface”on page 18•“Switch Configuration T ools”on page 45•“Monitoring Performance”on page 50•“Customizing the ASEM Display”on page 53Setting ASEM PropertiesASEM uses the Simple Network Management Protocol (SNMP) to configure andmanage a Nortel Application Switch. The ASEM Properties screen is used toconfigure parameters used to communicate with a switch. These parameters includepolling interval, time-out, and retry count. These parameters can be set at any timebefore or after a device is opened.To set the properties in the ASEM Properties screen, follow this procedure:1From the ASEM menu, choose Nortel ASEM > Properties. This screen isillustrated in Figure1on page 10.9 320512-A, January 2006Nortel Application Switch Element Manager 4.0.2 User’s Guide10320512-A, January 2006Figure 1 Properties Screen2Select the properties to change and set their values.3Click the Save button.Table1 The following table outlines the fields present on this screen.Table 1 Property screen fieldsField DescriptionPolling FieldsStatus Interval The interval at which statistics and status information are gathered.(If T raps, Status Interval)If the Register for Traps check box is selected, the interval, in seconds, at which statistics and status information are gathered.Hotswap Detect The multiples of polling intervals between hotswap checks.Enable If checked, ASEM will poll the switch according to the settings listedabove the Enable check box.SNMP FieldsRetry Count The number of times ASEM will retransmit any SNMP messagebefore reporting a timeout message.Timeout The length of time between each retry of each SNMP waiting period,from 3 to 30 seconds.If the retry count is set to 2 and the time-out value to 5 seconds,ASEM will report a timeout (no response from the switch) after 10seconds.T race If checked, ASEM sends detailed SNMP information to the log. Register for Traps If checked, ASEM will attempt to register the client’s IP address to one of the trap hosts’ IP fields.Listen for Traps If checked, ASEM will listen for traps and will attempt to hook to thetrap port 162.Max Traps in Log The specified number of traps that may exist in the trap log. Thedefault is 500.T rap Port The number of the port on which trap messages will be captured. The default is 162.General FieldsListen for Syslogs If checked, ASEM will listen for syslogs and will attempt to hook to the syslog port 514.Confirm row deletion If checked, ASEM will request for confirmation each time a row in the application is deleted.See also:•“Opening a Switch” on page 12•“The ASEM Interface” on page 18Opening a SwitchASEM provides two options for opening a switch for configuration and management. A switch can either be opened using SNMP versions 1 or 2 or SNMP version 3. The following sections detail how to open a switch through either of these methods.Opening a Switch Using SNMP versions 1 or 2To open a switch using SNMP versions 1 or 2, follow this procedure:Synchronize VRRPPeers on Apply If checked, the switch will synchronize the SLB, filter, and VRRP configuration on a peer switch on Apply . To take effect, peers mustbe configured on the switches and the administrator password on theswitches must be identical.ASEM Server Notifications Fields Enable Enable or disable ASEM Server e-mail notifications.From The e-mail address used to send the notification.T o The e-mail address that will receive the notification.Note: This field supports only a single e-mail address. To send ane-mail notification to multiple addresses, create a mail list for thoseaddresses.Server The e-mail server used to send the notification.User The user name used to log into the e-mail server.PasswordThe password used to log into the e-mail server.Table 1 Property screen fields (Continued)FieldDescription1From the menu, select Nortel ASEM > Open. The Open Device screen opens.This screen is illustrated in Figure2.Figure 2 Open Device screenThe Open Device screen can also be opened through the toolbar or byright-clicking on the ASEM tree control. Refer to “ASEM Toolbar”on page28 and “ASEM Tree Control”on page33 for more information on these options.2Identify the device to be opened by typing the Domain Naming Services (DNS) name or Internet Protocol (IP) address of the device in the Device Name field.3Type the appropriate community strings in the Read Community and Write Community fields. The default strings are public and private respectively.These settings apply to SNMP version 1 or 2 access. For access using SNMP version 3, refer to “Opening a Switch using SNMPv3”on page 14.4Click the Open button.Optionally, click the Ping button to check if the switch is reachable on the network before attempting to open it.To connect to the switch through the Telnet protocol, click the Telnet button.See also:•“Opening a Switch using SNMPv3”•“Previously Opened Switches”on page 15•“Troubleshooting the Opening of a Switch”on page 15Opening a Switch using SNMPv3Before opening a switch using SNMP version 3, SNMP version 3 must be enabled on the switch. Refer to the Nortel Application Switch Operating System 23.0.2 Command Reference (Part Number 320506-A) for information on enabling SNMP version 3.To open a switch using SNMP version 3, follow this procedure:1From the menu, select Nortel ASEM > Open. The Open Device screen opens.This screen is illustrated in Figure2on page 13.The Open Device screen can also be opened through the toolbar or byright-clicking on the ASEM tree control. Refer to “ASEM Toolbar”on page28 and“ASEM Tree Control”on page33 for more information on these options.2Identify the device to be opened by typing the Domain Naming Services (DNS) name or Internet Protocol (IP) address of the device in the Device Name field.3Click the v3 Enabled check box.4Enter the user name in the User Name field.5If applicable, select the appropriate authentication protocol in the Authentication Protocol drop-down list. The options in the list are None, MD5, and SHA-96. IfNone is selected, no further configuration is required. Steps 6 to 8 assume that anauthentication protocol was selected.6Enter the authentication password in the Authentication Password field.7If applicable, select the appropriate privacy protocol in the Privacy Protocol drop-down list. The options are None and DES.8Enter the privacy password in the Privacy Password field.9Click Open.See also:•“Opening a Switch Using SNMP versions 1 or 2” on page 12•“Previously Opened Switches”•“Troubleshooting the Opening of a Switch”on page 15Previously Opened SwitchesAny switch that was opened during past sessions will appear as a folder in theleft-hand tree control navigation pane. This folder will be labelled with the IP address or DNS name of the switch. Click on the desired folder to initiate a new connection to the switch.See also:•“Opening a Switch Using SNMP versions 1 or 2” on page 12•“Opening a Switch using SNMPv3” on page 14•“Troubleshooting the Opening of a Switch”on page 15Troubleshooting the Opening of a SwitchErrors can occur during the opening of a switch. Should an error occur, ASEM willdisplay an error message. This message is illustrated in Figure3.Figure 3 Connection Error MessageIf this message is displayed, the following items should be checked:•In slower networks, increase the Retry Count and Timeout values on the Properties screen. Refer to “Setting ASEM Properties”on page 9 for informationon performing this task.•In the Open Device screen, ensure that the correct read and write community strings have been entered for SNMP version 1 and 2 connections. Refer to“Opening a Switch Using SNMP versions 1 or 2”on page 12 for more informationon performing this task.•In the Open Device screen, ensure that the correct SNMP version 3 information has been entered for SNMP version 3 connections. Refer to “Opening a Switchusing SNMPv3”on page 14 for more information on performing this task.•Ensure that the switch is physically connected to the network.•Ensure that the switch is turned on and receiving power.•Ensure that the switch has been assigned a correct IP address.•Ensure that the correct IP address is being used in the Open Device screen.•Ensure that the problem does not exist because of an unrelated network misconfiguration.•Ensure that SNMP access is enabled on the switch. Refer to the Nortel Application Switch Operating System 23.0.2 Command Reference (Part Number 320506-A) for information on enabling SNMP access.•Ensure that switch is not blocking access from the client IP address.See also:•“Opening a Switch Using SNMP versions 1 or 2”on page 12•“Opening a Switch using SNMPv3”on page 14•“Previously Opened Switches”on page 15Connecting to a ASEM ServerWhen connecting to a switch through the ASEM, the user also has the option ofconnecting to an ASEM Server. T o connect to a ASEM Server, follow this procedure: 1From the Open Device screen, select the ASEM Server Enabled checkbox.Figure4 illustrates this screen. For information on accessing and using thisscreen, refer to “Opening a Switch”on page 12.Figure 4 Open Device screen2Enter the IP address or DNS name of the server in the ASEM Server Address field.3Enter the server user name in the ASEM Server User field. By default, this user name is root.4Enter the server password in the ASEM Server Password field.5Click Open.The ASEM InterfaceThe ASEM interface consists of two framed windows with menu and tool bars. Theleft-hand tree control frame is used to display a list of switches that were connected toduring previous sessions. The right-hand frame display changes with the differentfunctions performed throughout the application. An example of the ASEM interface isillustrated in Figure5.Figure 5 ASEM InterfaceThe following topics are covered in this section:•“Summary View”on page 19•“GUI Front Panel”on page 20•“ASEM Interface Elements”on page 21•“Working with Switch Screens”on page 41Summary ViewThe ASEM Summary View screen provides a quick view of various switch functions.The information presented on this screen is read-only. Figure6 illustrates an example of the Summary View screen.Figure 6 Summary View screenThis screen is displayed when a connection is initially established with a switch orwhen the root switch folder is selected in the left-hand navigation frame.GUI Front PanelThe GUI Front Panel screen displays a graphical representation of the switchcurrently being configured. From this screen a user can select ports for configuration and maintenance. Selection of ports is accomplished by clicking on the graphic for a single port or holding down the CTRL key and clicking multiple port graphics. Anexample of this screen is illustrated in Figure7.Figure 7 GUI Front Panel screenASEM Interface ElementsThe following section outlines the common interface elements that make up the Nortel Application Switch Element Manager. These common elements are found throughout the application.See also:•“ASEM Menubar”on page 21•“ASEM Toolbar”•“ASEM Screen and Tab Buttons”on page 31•“ASEM Tree Control”on page 33•“ASEM Context Menus”on page 34ASEM MenubarThe ASEM menubar provides the commands used to monitor and configure theswitch. Table2 The following table provides a brief outline of the main menubar items.Table 2 Main menubar itemsMenu DescriptionNortel The Nortel menu provides commands for:•Opening a switch.•Refreshing the switch view.•Setting polling and SNMP properties.•Setting tree control preferences.•Refreshing switch status.•Switch rediscovery.•Log viewing.•Telnetting to a switch.•Import, export, and clearing of preferences.•Closing ASEM.Configure The Configure menu contains commands for switch configuration. Formore information on this menu, refer to the ASEM online help.Detailed Menu DescriptionsTable 3 The following table outlines the options available in the Nortel , Actions , and Help menus in detail. For a detailed description of the Configure and Monitor menus, consult the ASEM online help.MonitorThe Monitor menu provides commands for switch performancemonitoring. For more information on this menu, refer to the ASEM online help.WizardsThe Wizards menu differs depending on the type of switch being managed:In Nortel Link Optimizer switches, the Wizardsmenu opens the initial configuration wizard. This wizard steps the user through the initialconfiguration. This wizard is a one-time action performed while installing a new switch. This wizard cannot be used to modify an existing switch configuration.In Nortel Application Switches the Wizards menu provides access to the Server Load Balancing Wizard. This wizard can be used at any time to provide a simplified interface for the configuration of server load balancing through ASEM. The Link Load Balancing Wizard is only accessible when the LLB key is enabled. The Traffic Management Wizard is only accessible when the ITM key is enabled and the ASEM client is connected to an ASEM Server ActionsThe Actions menu provides commands for:•Opening the browser-based interface.•Applying switch configuration changes.•Saving switch configuration changes.HelpThe Help menu provides commands for accessing the online help and support options for the ASEM.Table 3 Nortel, Actions, and Help menusIcon TextDescriptionNortel MenuOpenOpens a screen that enables the user to connect to a switch. The user can connect to a switch through this window by entering the appropriate SNMP information. The four buttons at the bottom of this window allows the user to open, ping, or telnet to thedesired switch or close the window without connecting.Table 2 Main menubar items (Continued)Menu Description。
Alteon设备用户使用手册

Alteon设备调试管理使用手册目录目录 (3)Alten四层交换机的配置 (4)一、网络拓扑 (4)二、登录设备 (5)2.1 使用console连接设备 (5)2.2 远程telnet (5)三、设备配置及说明 (6)3.1 系统配置 (6)3.2 二层配置 (7)3.2 三层配置 (8)3.3 VRRP配置 (9)3.4 Server LB配置 (10)Alten四层交换机的维护 (13)一. 检查设备运行的状态的方法. (13)二. 检查设备硬件是否有故障或是否起作用的方法. (15)三. 出现故障时的处理流程. (16)Alten四层交换机的配置一、网络拓扑网络拓扑图如下:(标准架构)整个网络由防火墙、路由交换机、二层交换机和两台负载均衡交换机组成。
路由交换机连接防火墙的DMZ区,负载均衡交换机通过二层交换机连接路由交换机。
Alteon交换机划分两个Vlan,分别连接服务器和交换机。
两台alteon交换机工作于主备模式,平时一台设备为active状态,另一台为backup状态,当active设备出现故障的时候,backup设备会变为active状态。
二、登录设备2.1 使用console连接设备按照如下连接参数配置ternimal终端:Baud rate = 9600Data bits = 8Parity = noneStop bits = 1Flow control = none输入密码就可以登录管理界面默认的密码是admin2.2 远程telnettelnet <设备ip地址>输入密码,就可以登录管理界面三、设备配置及说明Alteon交换机的管理分为命令行和图形界面两种方式,图形界面需要EMS 软件或者Optivity网管软件实现,命令行则可以通过超级终端、telnet等方式,最常用的就是超级终端的方式本说明主要针对命令行的方式来说明实现对Alteon交换机的管理维护,命令行方式是推荐的使用方式。
alteon常用命令

修改系统时间>> Main# /cfg/sys/ time修改密码>> Main# /cfg/sys/access/user/admpw启用和禁用端口>> Main# /cfg/port 8/dis>> Main# /cfg/port 8/ena配置vlan>> Main# /cfg/l2/vlan 20/name "VLAN 20 upto_3552" >> Main# /cfg/l2/vlan 20/ena1.将上联端口划分到VLAN上去>> Main# /cfg/l2/vlan 20/add 162.将端口从VLAN配置中去掉>> Main# /cfg/l2/vlan 20/rem 16配置vlan IP地址也就是SVI接口IP地址:1.配置IP地址:>> Main# /cfg/l3/if 20/addr 59.37.52.32.配置掩码:>> Main# /cfg/ip/if 20/mask 255.255.255.2403.配置广播地址:>> Main# /cfg/ip/if 20/broad 59.37.52.154.配置VLAN:把这个接口ip和vlan id绑定到一起>> Main# /cfg/ip/if 20/vlan 205.启用接口:>> Main# /cfg/ip/if 20/ena配置网关:Main# /c/l3/gw 1/ena>> Main# /c/l3/gw 1/addr 59.37.52.1启用路由转发功能:缺省情况下,alteon的路由转发功能是启用的,也可以使用下列命令来启用>> Main# /c/l3/frwd/on配置本地路由转发:>> Main# /c/l3/frwd/local/add 59.37.52.160 255.255.255.224>> Main# /c/l3/frwd/local/add 59.37.52.0 255.255.255.240SLB方面的配置:1.配置real server:/c/slb/real 165enarip 59.37.52.165name "AD-ENGINE-01"2.配置group :为了方便标识,将VIP的最后一位作为group和virt的id/c/slb/group 164health http --指定以http端口作为健康检测基准add 165 --增加real serveradd 1663.配置vip:/c/slb/virt 164enavip 59.37.52.164/c/slb/virt 164/service httpgroup 164dbind ena维护命令:察看借口双工之类的状态:>> Main# /info/link------------------------------------------------------------------Port Speed Duplex Flow Ctrl Link----- ----- -------- --TX-----RX-- ------1 100 full yes yes up2 100 full yes yes up3 100 full yes yes up察看某个真实server的状态:>> Server Load Balancing Information# /info/slb/real 172172: AD-IMAGE-01, 00:15:c5:e5:8d:c5, vlan 32, port 14, health 4, up rport 80, up, current察看slb内server的状态:>> Server Load Balancing Information# /info/slb/virt 171171: 59.37.52.171, 00:00:5e:00:01:abvirtual ports:http: rport http, group 171, ad-image-http, backup none, dbindreal servers:172: AD-IMAGE-01, backup none, 0 ms, group ena, up173: AD-IMAGE-02, backup none, 1 ms, group ena, up174: AD-IMAGE-03, backup none, 0 ms, group ena, up175: AD-IMAGE-04, backup none, 0 ms, group ena, up176: AD-IMAGE-05, backup none, 0 ms, group ena, FAILED察看系统日志:>> Information# /info/logAug 13 1:28:48 INFO vrrp: Synchronization connection early RCLOSE in RX. Aug 13 1:28:49 NOTICE slb: real service 59.37.52.173:80 operationalAug 13 1:28:49 NOTICE slb: Services are available for Virtual Server171:59.37.52.171Aug 13 1:28:49 NOTICE vrrp: virtual router 59.37.52.171 is now BACKUP察看vlan配置:>> Information# /info/l2/vlanVLAN Name Status Jumbo BWC Learn Ports ---- -------------------------------- ------ ----- ---- ----- ----------------1 Default VLAN ena n 256 ena 14 17 18 20 VLAN 20 upto_3550 ena n 256 ena 14 16 32 VLAN 32 ads ena n 256 ena 1-15察看ip地址配置:>> Information# /info/l3/ipIP information:AS number 0Interface information:20: 59.37.52.4 255.255.255.240 59.37.52.15 , vlan 20, up 32: 59.37.52.163 255.255.255.224 59.37.52.191 , vlan 32, upDefault gateway information: metric strict1: 59.37.52.1, vlan any, up2: 59.37.52.2, vlan any, upCurrent IP forwarding settings: ON, dirbr disabledCurrent local networks:Network Address Mask--------------- ---------------59.37.52.160 255.255.255.22459.37.52.0 255.255.255.240Current IP port settings:All other ports have forwarding ONCurrent network filter settings:noneCurrent route map settings:察看cpu状态:>> Main# /stats/mp/cpu------------------------------------------------------------------ CPU utilization:cpuUtil1Second: 4%cpuUtil4Seconds: 3%cpuUtil64Seconds: 2%察看内存状态:>> Main# /stats/mp/mem------------------------------------------------------------------Memory stats:Total: 130121728 bytesUsed: 86953984 bytesFree: 43167744 bytesLowFree: 43167744 bytes 察看接口统计:system inf-statice命令相同:>> Port 2 Statistics# /stats/port 2/dump------------------------------------------------------------------Bridging statistics for port 2:dot1PortInFrames: 0dot1PortOutFrames: 15649048dot1PortInDiscards: 4dot1TpLearnedEntryDiscards: 0dot1BasePortDelayExceededDiscards: NA dot1BasePortMtuExceededDiscards: NA dot1StpPortForwardTransitions: 4------------------------------------------------------------------。
维克ト恩能源生产力系统配置助手说明书
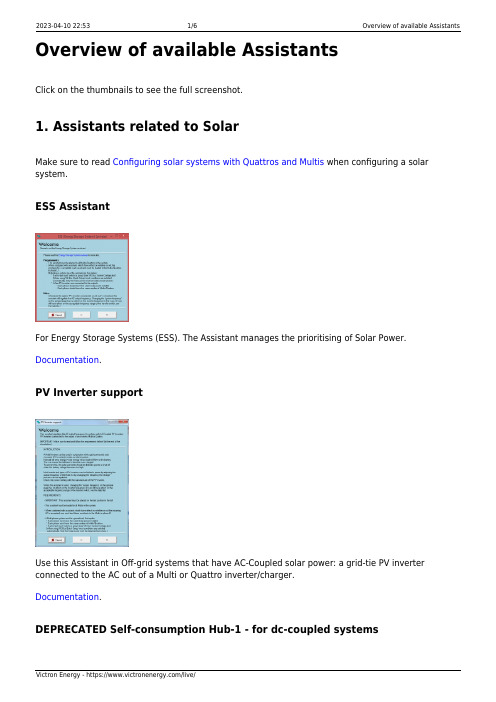
Overview of available AssistantsClick on the thumbnails to see the full screenshot.1. Assistants related to SolarMake sure to read Configuring solar systems with Quattros and Multis when configuring a solar system.ESS AssistantFor Energy Storage Systems (ESS). The Assistant manages the prioritising of Solar Power. Documentation.PV Inverter supportUse this Assistant in Off-grid systems that have AC-Coupled solar power: a grid-tie PV inverter connected to the AC out of a Multi or Quattro inverter/charger.Documentation.DEPRECATED Self-consumption Hub-1 - for dc-coupled systems2022-06-01assistants:overview_of_available_assistants https:///live/assistants:overview_of_available_assistants 13:41Note that Hub-1 is deprecated in favor of ESS.Hub-1 Assistant documentation.Hub-1 is only for hardware with new microprocessor (26 or 27).Hub-1 and Hub-2 Assistant notesDEPRECATED Self-consumption Hub-2 v3 - for ac-coupled systemsTake note of the factor 1.0 rule.Deprecated in favor of ESS.Only for hardware with new microprocessor (26 or 27).Hub-1 and Hub-2 Assistant notesDEPRECATED Self-consumption Hub-2 v2 - for ac-coupled systemsUse only on hardware with old microprocessor (19 or 20). On newer systems, use the version 3 instead, see above.Take note of the factor 1.0 rule.Note that all Hub-2 Assistant versions have been deprecated in favor of ESS.Hub-1 and Hub-2 Assistant notesDEPRECATED Self-consumption Hub-4Do not use Hub-4 for new installs. It is deprecated in favor of ESS.Hub-4 manual.Only for hardware with new microprocessor (26 or 27).2. Functional AssistantsGenerator start and stopAutomatically start and stop a generator based on battery state of charge andactual load of a system. Note that automatic genset start/stop functionality isalso available on the Virtual switch tab in VEConfigure, which is easier to workwith.This is one of the available options to automatically start and stop a generator using Victron equipment. See the auto-generator-start-stop document for an overview of all options. More general information about using a generator in combination with Victron is available here.This Generator start and stop Assistant is also the one to use to configure Ignore AC Input using Assistants.AC Current sensor2022-06-01assistants:overview_of_available_assistants https:///live/assistants:overview_of_available_assistants 13:41Reads PV Inverter current, using an AC Current sensor (CSE000100000),connected to a VE.Bus product. More information available in the AC Currentsensor manual.Silence fanDisable the fans at night with a simple external switch, to ensure a quiet night.Very useful for boats and motorhomes.Input current limit controlAutomatically set the input current limit to a predefined value based on thestate of an aux input or rpm measured with the 1140 interface. Used in thefollowing systems:1.A variable speed generator, flywheel generator or waterturbine, where the available AC powerdepends on the rpm. See the Interface 1140 (ASS030510000) manual for more information.Vehicles or boats that have two different types of shore plugs. One high power plug and one low 2.power plug. Use the assistant to automatically set the input current limiter based on the used plug.And there are more situations that can come to mind, for example a Multi connected behind a 3.transfer switch.Charge current controlSets the charge current to a predefined setpoint, based on the active AC Input(for Quattros) or the state of an aux input.Safety switchUsed to wire an emergency stop button to a VE.Bus system. DEPRECATED VE.Bus BMS supportDeprecated: per VE.Bus firmware version 489, this Assistant is no longer required. When installing a system with VE.Bus BMS, our advice is to first update the firmware of the inverter, using VictronConnect, and thereafter do the configuration. No Assistant needed.Required in combination with a VE.Bus BMS, used with our 12.8 V Lithium batteries. This Assistant communicates with the BMS and controls the Multi based on the BMS measurements.Two-Signal BMS support (previously called Lynx Ion BMS support)Required in combination with a Lynx Ion BMS, used with our 24 V 180 AhLithium system. This Assistant can also be used to control the Multi with a thirdparty Lithium system including BMS. See our PDF Connecting other lithiumbattery systems to Multis and Quattros for more information.3. Advanced AssistantsProgrammable relay2022-06-01assistants:overview_of_available_assistants https:///live/assistants:overview_of_available_assistants 13:41Relay lockerGeneral flag userDISQUSView the discussion thread.。
Ergotron 移动工作站配置指南说明书

E-03-005 rev. 02/13/13 • Ergotron Mounting Solutions Orderguide • 45Mobile WorkStandConfigure a mobile mounting solution that works for you No matter how demanding the mobile computingapplication, or what type of computing equipment you need to mobilize, Ergotron has a computer cart to get the job done. The Mobile WorkStand integrates technology and convenience, allowing the user to move a computer system from room to room. It quickly adjusts to a sitting or standing user height, providing an ergonomically-correct work environment at all times.Mobile WorkStand with 400 Series LCD and Keyboard Arms offer vertical adjustment range of 22"-24" (56-61 cm) for sit-to-stand flexibilityeasy attachment of many Ergotron mounts, placed at any point along the poleErgotron's Uni-versal CPU Holder attaches to the base and accom-modates a wide range of CPU/UPS sizes46 • Ergotron Mounting Solutions Orderguide • rev. 02/13/13 E-03-005Part Description Dimensions Shipping Number H x W x D Weight 99-068-100*, grey Wire Storage Basket 6-1/8" x 13-1/8" x 4-1/8" 3 lbs(156 x 333 x 105 mm)(1.4 kg)* Requires separately ordered Pole Mount Bracket. May be mounted to Bracket shared by another component.Two Brackets for mounting LX, 200, 400 Series, Extenders, on vertical 2" Round PoleShipping Weight: 2 lbs (.9 kg)Pole-Mount Bracketsand Wire Storage Basket on vertical 2" Round PoleShipping Weight: 2 lbs (.9 kg)Pole to mount 100 Series pivots.Shipping Weight: 2 lbs (.9 kg)Pole-Mount Bracket Kit。
艾洛终端参数设置说明书

艾洛终端参数设置说明书艾洛终端参数设置说明书艾洛终端是一款功能强大的设备,可以通过参数设置来满足不同用户的需求。
本文将详细介绍艾洛终端的参数设置,并提供一些指导,帮助用户正确设置终端。
1. 艾洛终端参数设置的重要性艾洛终端的参数设置直接影响到设备的性能和功能。
正确的参数设置可以提升设备的效率、减少故障发生的概率,同时还能提供更好的用户体验。
因此,了解并正确设置终端参数非常重要。
2. 基本参数设置基本参数设置包括设备的名称、IP地址、子网掩码等。
用户可以根据实际需要对这些参数进行设置。
确保设备的名称和IP地址设置正确,可以方便用户管理和识别设备。
设置正确的子网掩码可以确保设备和其他设备之间的通讯正常、稳定。
3. 网络参数设置网络参数设置包括网络类型、网络频率、WIFI设置等。
用户可以根据实际情况选择合适的网络类型(如2G、3G、4G等),并设置相应的网络频率,以实现设备与服务器的正常通讯。
此外,用户还可以设置WIFI连接,使设备可以通过无线网络进行通信。
4. 安全参数设置安全参数设置是保障设备和数据安全的重要措施。
用户可以设置设备的密码、限制登录次数、开启数据加密等措施,以防止未经授权的访问和数据泄露。
此外,用户还可以根据需要设置设备的远程访问权限,确保设备的安全性。
5. 传感器参数设置艾洛终端配备有多种传感器,可以测量温度、湿度、光照等参数。
用户可以根据实际需要对传感器参数进行设置,如设置温度范围、湿度报警阈值等。
这些设置可以提供实时监测和报警功能,保障设备的正常运行。
6. 数据上传参数设置数据上传参数设置包括上传间隔、上传量级、上传方式等。
用户可以根据需要设置数据上传的间隔时间和量级,以及上传的方式(如FTP、HTTP等)。
合理的数据上传设置可以提高数据的及时性和准确性。
7. 参数设置的注意事项在进行参数设置时,用户需要注意以下几点:- 确保参数设置正确,尤其是设备的名称、IP地址等基本参数。
Alcatel OneTouch 3G X602D 移动网络 USB 模块配置手册说明书

MANUAL DE INSTALACIÓN ALCATEL ONETOUCH3G X602DMANUAL DE INSTALACIÓN DE INTERNET MÓVILPEPEPHONE CON EL MÓDEM USBALCATEL ONETOUCH 3G X602DINTRODUCCIÓN¡Bienvenido a Pepephone!Con esta guía de configuración podrás configurar paso a paso tu acceso a Internetmóvil Pepephone con el módem USB Alcatel Onetouch 3G X602D. Para ello,solamente tienes que realizar dos simples tareas:1º Instalar el software del módem en tu ordenador2º Búsqueda de red3º Conectarte a InternetPARA EMPEZAR ANAVEGAR∙ Introduce la SIM en el módem USB∙ Introduce el módem, con la tarjeta SIM de Pepephone insertada, en un puertoUSB de tu portátil. Se iniciará un programa automático para la instalación delgestor de conexión 3G. Sigue las instrucciones que te indicamos a continuaciónpara su configuración.1/Al introducir el módem en un puerto USB 2.0 se inicia la instalación automática de la aplicación My Connection. En la ventana “Reproducción automática” escogemos la opción “Ejecutar autorun.exe”. A continuación aceptamos que el programa realice cambios en nuestro equipo y escogeremos el idioma que se utilizará durante la instalación.2/Se iniciará entonces el asistente de instalación de My Connection. Tras hacer clic en “Siguiente”, escogeremos la ubicación en la que se instalará el programa.3/ Una vez escogida la carpeta en la que se instalará el programa, el asistente nos preguntará si deseamos crear un icono de escritorio, para a continuación iniciarse la instalación. Cuando se complete la instalación de My Connection haremos clic en “Finalizar ” para salir del asistente y abrir la aplicación de acceso a Internet.4/ Una vez instalada la aplicación, la abriremos. El “Nombre perfil” aparecerá vacío durante unos segundos hasta que el módem USB se registre en la red de Pepephone.5/ Completada la búsqueda y registro en la red (si hay cobertura disponible), se mostrará “Nombre Perfil: Pepephone ” y pulsaremos en “Conectar ” para iniciar la sesión de conexión a Internet móv il con Pepephone. Una vez estemos conectados el botón conmutará a “Desconectar”.1/Asegúrate de encontrarte en una zona con cobertura Pepephone.2/El módem USB Alcatel OneTouch 3G X602D está pre configurado con los parámetros de Pepephone. Esto significa, que no es necesario configurar ningún valor en el “Perfil de conexión”. No obstante, puedes comprobarlo en el menú “Configuración” (en el menú superior: tercer icono por la der echa).A continuación escoge “Perfil de conexión” en el menú de la izquierda y en la Lista de perfiles verifica queúnicamente figura el perfil de “Pepephone”. Si haces clic en “Ver” podrás comprobar que el APN correcto que figura y que permite conectarse a la red de Pepephone es 。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Alteon中文配置手册版本V1版本V2二、连接Alteon (5)三、设备维护配置 (6)四、物理层配置 (8)五、链路层配置 (8)VLAN划分 (8)端口汇聚 (8)802.1q Trunk端口配置 (9)六、网络层配置 (9)IP接口地址配置 (9)网关配置 (9)静态路由配置 (10)动态路由配置 (10)冗余配置 (10)Active-standby传统模式 (11)新的floating IP的配置方式 (11)冗余状态检测 (12)七、负载均衡配置 (12)配置服务器 (12)服务器组Group配置 (14)配置虚拟服务器virtual service (15)配置源地址翻译 (15)会话保持配置 (16)Delay binding (19)八、基本四层负载均衡配置 (20)案例网络场景 (20)配置步骤 (20)九、HTTP服务器负载均衡 (22)十、FTP负载均衡 (22)十一、基于URL的7层负载均衡 (22)十三、链路负载均衡 (27)出向流量链路负载均衡配置 (28)入向流量负载均衡配置 (32)DNS解析相关配置 (33)十四、全局负载均衡 (35)独立模式的全局负载均衡配置 (35) (35)多站点协同的负载均衡算法配置 (36)A站点配置 (37)B站点配置 (38)C站点配置 (40)其他全局负载均衡优化配置 (42)十五、排错纠错 (42)系统信息 (43)网络层排错 (44)负载均衡相关排错纠错 (44)一、Alteon设备简单介绍目前市场上主要销售的Alteon产品包括了,Alteon 4408、Alteon 5208、Alteon 6024、Alteon6420。
当然还有基于各种虚拟化平台的Alteon VA。
Alteon 4408Alteon 4408提供了8个接口,其中2个是SFP插槽,用户可以根据自己的需要选择插入千兆光口或者千兆电口。
其中固化在上面的第六个电口已经被设置为管理口,所以实际可用的业务口为7个。
除此外,Alteon 4408还有一个RJ-45的Console口。
Alteon 5208Alteon 5208提供了10个接口,其中2个是SFP插槽,用户可以根据自己的需要选择插入万兆借口、千兆光口或者千兆电口。
其中固化在上面的第八个电口已经被设置为管理口,所以实际可用的业务口为9个。
除此外,Alteon 5208还有一个RJ-45的Console口。
Alteon 6420Alteon 6420提供了24个接口,其中4个是40G端口,可插入QSFP模块。
另外有20个SFP插槽,可插入10G或者千兆模块。
除此外,Alteon 6420还有一个RJ-45的Console口和两个管理端口。
二、连接Alteon从30.2开始,Alteon支持Console、HTTPS和SSH、telnet管理模式,HTTP模式的管理不再支持。
另外,图形化的管理界面支持中文化管理。
Alteon 终端的设置是9600/n/8/1,及波特率为9600、无流控、数据位为8,停止位为1。
另外Alteon的终端控制线和Cisco等其他设备一样。
图形界面的默认语言类型为english,如果要改成中文,只需要输入下面的命令即可。
/cfg/sys/lanague chinese配置设备管理接口以及管理段网关/cfg/sys/mmgmt/addr x.x.x.x/mask 255.255.255.0/gw x.x.x.x/ena三、设备维护配置如果在一个项目中涉及很多设备,如果没有一个合理的命名规范可能最后会导致管理者也无法明确了解自己在管理哪个设备。
另外,终端的过快超时等都会带来烦恼。
因此Alteon 提供了命令来帮助解决这些问题。
1、设置设备终端名字显示/cfg/sys/hprompt e/cfg/sys/ssnmp/sysname “DEMO-ALTEON”apply2、终端超时时间长度修改/cfg/sys/idle 600 #minutes3、日志服务器设置,Alteon默认可以设置5个syslog服务器/cfg/sys/syslogHst1 x.x.x.xAudit # enable configuration audit4、用户认证服务器设置/cfg/sys/radiusPrisrv x.x.x.xSecsrv x.x.x.x5、Ntp服务器配置/cfg/sys/ntpOnprisvr6、修改默认的管理信息发送的端口/cfg/sys/mmgmt/dns [mgmt. data]/cfg/sys/mmgmt/smtp [mgmt data]/cfg/sys/mmgmt/snmp [mgmt. data]/cfg/sys/mmgmt/syslog [mgmt. data]/cfg/sys/mmgmt/tftp [mgmt. data]/cfg//sys/mmgmt/ntp [mgmt. data]另外Alteon支持各种历史命令查询,通过上下箭头来查询历史命令通过Cur 命令来查询当前的配置/cfg/dump命令来查询当前整个配置Diff来看内存中当前还没有apply的命令Revert可以返回到上次apply的配置7、升级设备/boot/gtimg–m #-m 的意思是从管理口升级设备准备好要升级的软件,准备好升级的密码放到FTP服务器的目录中确保管理口和ftp服务器之间网络可达,并且ftp服务是起来的Alteon硬件设备中可以放置4个img,10个vADC的image,如果软件代码太大,可能需要删除flash中原有不再用的image。
软件下载完成后/boot/image 新的image的位置重启设备/boot/reset8、恢复出厂设置/boot/conf factoryAlteon在flash保存了三个配置文件,当前active的配置文件,上一次save前的配置文件保存在backup配置中,还有一个就是factory配置文件。
/boot/reset设备重启后就是默认的配置了。
9、下载配置/cfg/ptcfg10、上传配置/cfg/gtcfg11、四、物理层配置物理层的配置相对比较简单。
目前大部分的主机和交换机都支持端口速率的自动协商和适应,包括了直连线和交叉线的自动协商。
因此很少有机会发生Alteon根周边设备的端口协商出现问题,需要强制的场合。
一旦发生这种情况,则可以通过/info/link来查看各端口的协商情况。
然后通过/cfg/port n/来进行调整。
五、链路层配置链路层的配置主要包括下面几点。
VLAN划分Alteon默认情况是一台标准的二层交换机,所有端口都在默认的vlan 1中。
根据实际网络中实施的需要,需要把不同的端口划分到不同的vlan中。
/cfg/l2/vlan nnn/ena/def x同一VLAN中的所有端口二层就是通的。
端口汇聚如果需要把多个端口捆绑起来作为一个逻辑端口使用,则需要配置端口汇聚,端口汇聚有两种模式。
一种是静态static模式,即上下游的设备之间没有协商,根据自身设定的hash 算法把流量分配到不同的端口。
另外一种模式是lacp,lacp又有两种模式,一种是active模式,一种是passive模式。
首先静态端口汇聚和lacp动态模式的区别在于动态模式能主动发包检测链路,如果在两台形成端口汇聚设备之间有端口转换设备的时候,lacp协议比较有优势,能主动检测到对端故障,而非中间设备故障。
Active模式中设备会主动发送检测包,而passive模式中的设备则不会主动发送检测包,而是被动接受。
配置静态的端口汇聚,把端口2,3加入到port channel 1/cfg/l2/trunk 1Add 2Add 3Ena/cfg/l2/lacp/port 1/mode active/cfg/l2/lacp/port 1/adminkey 100/cfg/l2/lacp/port 2/mode active/cfg/l2/lacp/port 2/adminkey 100只有adminkey相同的端口才能形成端口汇聚。
802.1q Trunk端口配置如果Alteon和周边设备之间通过vlan trunk相连,则需要enable 802.1q的tag。
/cfg/port x/tag e然后可以把相同的端口加入到多个vlan中。
/cfg/l2/vlan 10/def 1/cfg/l2/vlan 20/def 1六、网络层配置IP接口地址配置Alteon的接口地址是基于VLAN进行配置的,根据网络设计对每个网段都是需要配置一个接口地址。
接口地址配置的时候需要指定vlan号码,IP地址和掩码。
/cfg/l3/if nAddr x.x.x.xMask 255.255.255.0Vlan xxEna根据网络设计为每个接口指定IP地址。
其中值得一提的地方是建议为每个接口地址配置对端设备的peer地址,这个在以后的冗余配置和配置同步时都会发挥巨大作用。
/cfg/l3/if nPeer x.x.x.x网关配置Alteon有两类网关,一类是系统默认网关,序号是从1-4。
5开始后的网关是per vlan 的,这个是用于隔离不同vlan的流量的。
对于在链路负载均衡场景中,对接口地址的访问需要通过gateway per vlan来确保访问每个接口IP地址的流量从各自的网关回去。
1-4之间的网关有两种选择模式,一种是严格模式,即首先选择Gateway 1,只有当gateway 1失效的时候才选择gateway 2,依此类推。
另外一种模式是轮询模式,在设置的默认网关中轮询,这种模式很少采用。
建议采用模式1。
从上面可以看出,Alteon对于网关也是有健康检查的,检查网关是否可用,来觉得是否需要选择第二个网关。
健康检查有两种模式,一种是ICMP,即通过ping网关,根据网关的响应来判断网关是否可用,这种模式在网关禁止ping的时候会失效。
所以Alteon提供了第二种模式即Arp模式,只要网关响应ARP就认为网关可用。
而网关只要健康是必然会响应ARP的,所以我们怎么理解为什么还会保留第一种模式。
网关1-4的配置如下:/cfg/l3/gw 1Addr x.x.x.xEnaHealth [icmp arp]Gateway per vlan的配置如下/cfg/l3/gw 5Addr x.x.x.xEnaVlan nnnHealth [icmp arp]有关gateway per vlan怎么来隔离不同vlan的流量,留待后续。
静态路由配置如果服务器或者某些客户端需要跨网段进行访问,那么就需要配置静态路由。
/cfg/l3/route/ipv4/add destination mask nexthop interface number动态路由配置Alteon默认支持RIP/OSPF/BGP等动态路由,但是我的建议是最好不要用。
