android安全-Hotmobile 2012 Demo L4Android Security Framework
《自主代客泊车系统总体技术要求》(征求意见稿)

6.1 停车场场地规范 ................................................................ 19 6.1.1 场地分级规范 .............................................................. 19 6.1.2 车场匹配 .................................................................. 21 6.1.3 场地标识规范 .............................................................. 22 6.1.3.1 位置标识 ................................................................ 22 6.1.3.2 跨层标识 ................................................................ 23 6.1.3.3 十字路口处标识 .......................................................... 24 6.1.3.4 丁字路口处标识 .......................................................... 24 6.1.3.5 闸口/收费口标识.......................................................... 25 6.1.3.6 上下车点标识 ............................................................ 25
IEC60601-1第三版(中文版)

国际标准 IEC60601-1 医用电气设备—— 第一部分:安全通用要求和基本准则
MEDICAL ELECTRICAL EQUIPMENT – Part 1: General requirements for basic safety and essential pe.......................................................................................................................8 1.1 范围 ........................................................................................................................................8 1.2 目标 ........................................................................................................................................8 1.3 * 并列标准 ................................................................................................................................8 1.4 * 专用标准 ................................................................................................................................8
华为SecoManager安全控制器产品介绍说明书

Huawei SecoManager Security ControllerIn the face of differentiated tenant services and frequent service changes, how to implementautomatic analysis, visualization, and management of security services, security policy optimization,and compliance analysis are issues that require immediate attention. Conventional O&M relies onmanual management and configuration of security services and is therefore inefficient. Securitypolicy compliance check requires dedicated personnel for analysis. Therefore, the approval is usuallynot timely enough, and risky policies may be omitted. The impact of security policy delivery onservices is unpredictable. That is, the impact of policies on user services cannot be evaluated beforepolicy deployment. In addition, as the number of security policies continuously increases, it becomesdifficult for security O&M personnel to focus on key risky policies. The industry is in urgent needof intelligent and automated security policy management across the entire lifecycle of securitypolicies to help users quickly and efficiently complete policy changes and ensure policy deliverysecurity and accuracy, thereby effectively improving O&M efficiency and reducing O&M costs.The SecoManager Security Controller is a unified security controller provided by Huawei for differentscenarios such as DCs, campus networks, Branch. It provides security service orchestration andunified policy management, supports service-based and visualized security functions, and forms aproactive network-wide security protection system together with network devices, security devices,and Big Data intelligent analysis system for comprehensive threat detection, analysis, and response.Product AppearancesProduct HighlightsMulti-dimensional and automatic policy orchestration, security service deployment within minutes• Application mutual access mapping and application-based policy management: Policymanagement transitions from the IP address-based perspective to the application mutual access relationship-based perspective. Mutual-access relationships of applications on the network are abstracted with applications at the core to visualize your application services so that you can gain full visibility into the services, effectively reducing the number of security policies. The model-based application policy model aims to reduce your configuration workload and simplify network-wide policy management.• Policy management based on service partitions: Policy management transitions from thesecurity zone-based perspective to the service partition-based perspective. Conventional network zones are divided into security zones, such as the Trust, Untrust, DMZ, and Local zones. In a scenario with a large number of security devices and a large network scale, factors of security zone, device, policy, service rollout, and service change are intertwined, making it difficult to visualize services and to effectively guide the design of security policies. However, if security policies are managed, controlled, and maintained from the perspective of service partitions, users need to pay attention only to service partitions and security services but not the mapping among security zones, devices, and services, which effectively reduces the complexity of security policy design.Service partition-based FW1untrusttrustDMZ XXX FW2untrust trustDMZ XXX FW3untrust trust DMZ XXX InternetGuest partition R&D partition Data storage partitionExternal service partition Internal service partition• Management scope of devices and policies defined by protected network segments to facilitate policy orchestration: A protected network segment is a basic model of security service orchestration and can be considered as a range of user network segments protected by a firewall.It can be configured manually or through network topology learning. The SecoManager Security Controller detects the mapping between a user service IP address and a firewall. During automatic policy orchestration, the SecoManager Security Controller automatically finds the firewall that carries a policy based on the source and destination addresses of the policy.• Automatic security service deployment: Diversified security services bring security assurance for data center operations. Technologies such as protected network segment, automatic policy orchestration, and automatic traffic diversion based on service function chains (SFCs) enable differentiated tenant security policies. Policies can be automatically tiered, split, and combined so that you can gain visibility into policies.Intelligent policy O&M to reduce O&M costs by 80%• Policy compliance check: Security policy compliance check needs to be confirmed by the security approval owner. The average number of policies to be approved per day ranges from several to hundreds. Because the tool does not support all rules, the policies need to be manually analyzed one by one, resulting in a heavy approval workload and requiring a dedicated owner to spend hours in doing so. The SecoManager Security Controller supports defining whitelists, risk rules, and hybrid rules for compliance check. After a policy is submitted to the SecoManager Security Controller, the SecoManager Security Controller checks the policy based on the defined check rules and reports the check result and security level to the security approval owner in a timely manner.In this way, low-risk policies can be automatically approved, and the security approval owner needs to pay attention only to non-compliant policy items, improving the approval efficiency and avoiding the issues that the approval is not timely and that a risky policy is omitted.• Policy simulation: Based on the learning result of service mutual access relationships, the policies to be deployed are compared, and their deployment is simulated to assess the impact of the deployment, effectively reducing the risks brought by policy deployment to services.• Redundant policy deletion: After a policy is deployed, redundancy analysis and hit analysis are performed for policies on the entire network, and the policy tuning algorithm is used, deleting redundant policies and helping you focus on policies closely relevant to services.Network collaboration and security association for closed-loop threat handling within minutes • Collaboration with network for threat handling: In a conventional data center, application deployment often takes a long time. The application service team relies on the network team to deploy the network; the network team needs to understand the requirements of the application service team to deploy a network that is suitable for the application service team. The SecoManager Security Controller learns mappings between service policies and security policies based on the network topology, and collaborates with the data center SDN management and control system (IMaster NCE-Fabric) or campus SDN management and control system to divert tenant traffic to corresponding security devices based on SFCs on demand. The SecoManager Security Controller automatically synchronizes information about the tenants, VPCs, network topology (including logical routers, logical switches, logical firewalls, and subnets), EPGs, and SFCs from the SDN management and control system and combines the learned application service mutual access relationships to automatically orchestrate and deliver security policies, implementing security-network synergy.• Collaboration with security: Advanced persistent threats (APTs) threaten national infrastructure of the finance, energy, government, and other sectors. Attackers exploit 0-day vulnerabilities, use advanced evasion techniques, combine multiple attack means such as worm and ransomware, and may remain latent for a long period of time before they actually initiate attacks. The Big Data security product HiSec Insight can effectively identify unknown threats based on network behavior analysis and correlation analysis technologies. The threat handling method, namely isolation or blocking, is determined based on the threat severity. For north-south threats, the SecoManager Security Controller delivers quintuple blocking policies to security devices. For east-west threats, isolation requests are delivered to the network SDN management and control system to control switches or routers to isolate threatened hosts.Product Deployment• Independent deployment: The SecoManager Security Controller is deployed on a server or VM as independent software.• Integrated deployment: The SecoManager Security Controller and SDN management and control system are deployed on the same physical server and same VM.Database• Collaboration with the SDN management and control system to detect network topology changes and implement tenant-based automatic security service deployment.• North-south threat blocking, east-west threat isolation, and refined SDN network security control through SFC-based traffic diversion.• Interworking with the cloud platform to automatically convert service policies to security policies. Product SpecificationsOrdering InformationNote: This product ordering list is for reference only. For product subscription, please consult Huawei representatives. GENERAL DISCLAIMERThe information in this document may contain predictive statement including, without limitation, statements regarding the future financial and operating results, future product portfolios, new technologies, etc. There are a number of factors that could cause actual results and developments to differ materially from those expressed or implied in the predictive statements. Therefore, such information is provided for reference purpose only and constitutes neither an offer nor an acceptance. Huawei may change the information at any time without notice.Copyright © 2020 HUAWEI TECHNOLOGIES CO., LTD. All Rights Reserved.。
腾讯移动安全实验室2012年手机安全报告

文章来源: /dirs/1497.htm腾讯移动安全实验室2012年手机安全报告第一章手机安全报告摘要2012年,随着Android智能手机的大热与普及,手机病毒也发展迅猛。
在Android平台,2012年的手机病毒增长呈现直线上升的趋势,安全形势堪忧。
2012年,腾讯移动安全实验室共检测截获手机病毒总量达到177407个,超过90%的病毒包集中在Android平台,Android已经成为手机病毒肆虐的主战场。
2012年,在被病毒感染最多的前十款软件中,神庙逃亡、水果忍者、植物大战僵尸OL和捕鱼达人这四款最热门游戏无一幸免。
2012年,腾讯手机管家共为手机用户查出了5699万次手机病毒。
广东省2012年连续12个月手机中毒用户数均位居第一位,全年手机中毒用户比例达到1 4.7%,广东、江苏、浙江、北京市、辽宁四省一市位居前五,中毒手机用户比例分别为:14.7%、7.53%、6.5%、6.25%、5.23%。
感染比例共占据了全国的40.21%的比例。
2012年,腾讯手机管家用户主动举报垃圾短信总量达到3.04亿条,其中,广告类垃圾短信占据79.1%的比例,位居所有垃圾短信类型之首。
2012年,各种恶意广告进一步泛滥,截至2012年12月,腾讯手机管家已检测出含恶意广告的软件包共467026个,占已发现所有软件包比例13.31%。
自2012年9月份腾讯手机管家上线广告拦截功能以来,截至12月底,在客户端已经为用户一共拦截了240386 56次恶意广告。
2012年二维码大热的背后,安全风险暗藏。
据腾讯移动安全实验室监测,腾讯手机管家从2012年7月为灵动快拍提供二维码安全检测以来,7月~12月共为灵动快拍检测网址达9 56万条以上,拦截恶意网址达20.6万条。
报告正文第二章2012年全年手机安全现状2012年,随着国内Android系统的设备的持续大幅增长,Android系统市场占有率占据主流地位,而Android系统的手机病毒包也呈现爆发式增长态势,手机病毒的技术日渐成熟,在2012年,手机病毒包全年呈现前所未有的高速增长。
Android应用安全专利技术综述

Android应用安全专利技术综述摘要Android操作系统已成为全球第一大操作系统,其安全性关乎海量用户的信息和财产安全。
本文对Android应用安全技术领域专利技术进行分析和整理,以Android应用安全检测技术和安全加固技术为主线,重点关注了本领域的全球专利申请趋势、技术发展走向以及主要技术方案,有助于全面了解Android应用安全技术领域的发展态势。
关键词Android系统;安全技术;专利1 Android系统简介及其安全性分析Android(中文俗称“安卓”),是一个基于Linux内核的开源移动操作系统,由Google成立的开放手机联盟(Open Handset Alliance)持续领导与开发,主要设计用于智能手机等移动终端。
2017年3月,Android全球网络流量和设备超越了Windows,成为全球第一大操作系统。
Android操作系统架构自底向上分为4个层次:Linux内核层、系统库层、应用框架层、应用层[1]。
其中应用层为用户提供各式各样的应用程序,是Android 系统面临的安全风险和威胁的“重灾区”。
Android应用层安全研究和相关技术聚焦于Android应用本身的安全,包括了2个主要技术分支:一是针对应用是否存在恶意行为、漏洞等进行安全检测,规避安全风险,保证系统及其他应用不受恶意行为、漏洞的影响;二是针对应用进行安全加固,保护应用安全[2-5]。
2 Android应用安全技术专利申请情况2.1 国内外相关专利申请趋势分析Android应用安全技术的专利申请趋势总体上可以分为二个阶段,其中:2008-2010年为萌芽期:在该阶段,国外由于先发技术优势在申请量上领先于国内,国内起步时间相对略有滞后。
2011-2016年为增长期:自2011年开始Android 应用安全领域专利申请量开始明显地快速增长并在2016年达到峰值。
2.2 全球专利申请来源国/地区分布截至2018年5月,Android应用安全技术全球专利申请的来源国/地区主要为中国、美国、韩国。
AndroidO限制系统全屏进一步遏制手机勒索

Android O限制系统全屏进一步遏制手机勒索引言近期谷歌发布了最新手机操作系统Android O的开发者预览版,一如往常,Android O又带来了多项新功能与优化升级,其中一项有关系统窗口管理的优化给Android手机勒索软件带来了严重冲击。
简述Android系统与勒索软件对抗史手机勒索软件是一种特殊的恶意软件,其通常将自身伪装为看似无害的软件或是利用社会工程学诱导受害者下载安装,随后通过恶意利用操作系统正常功能或者缺陷强制锁住用户桌面使得用户无法正常使用设备,并几乎都会要求受害者缴纳赎金以解锁设备。
手机勒索的解锁费用通常为20、30或50元不等,通常情况下当用户设备感染勒索软件后,出于设备被锁定的焦急心理与不高的赎金金额,用户一般都会通过勒索软件锁屏界面提供的联系方式联系制马人以尝试解锁设备,因此这种“薄利多销”且制作成本低廉的点对点式直接性敲诈软件颇受制马人的青睐。
此外,这类软件通常具有很高的可变性,制马人只需简单调整软件代码或锁屏样式便可生成新的勒索软件。
360烽火实验室一直密切关注国内外手机勒索软件动向,先后发布了多篇对手机勒索软件的研究成果。
纵观Android系统尤其是高版本系统史,每一版都在遏制勒索软件方面做出了积极的应对:♦Android L(Android 5.0-5.1)在早期Android版本中,通过getRunningTasks 方法可获取当前运行栈顶程序,但自Android 5.0起该方法被弃用,同时getRunningAppProcesses与get AppTasks方法的使用也受到了限制,由此抑制了劫持Activity类勒索软件的出现。
♦Android M(Android 6.0)大部分手机勒索软件的惯用伎俩是通过SYSTEM_ALERT_WINDOW权限来打开特定系统类型窗口并将其显示在所有其他应用程序和窗口之上,以此达到锁定用户设备的目的。
Android M的出现使得勒索软件制马人在实施手机勒索时遇到了一大瓶颈——动态权限申请,由于自Android M起,SYSTE M_ALERT_WINDOW开始被列为一种危险程度较高的权限而被特殊处理——即需要用户动态授权。
Android平台网络连接架构分析-connectivityservice框架流程word版本
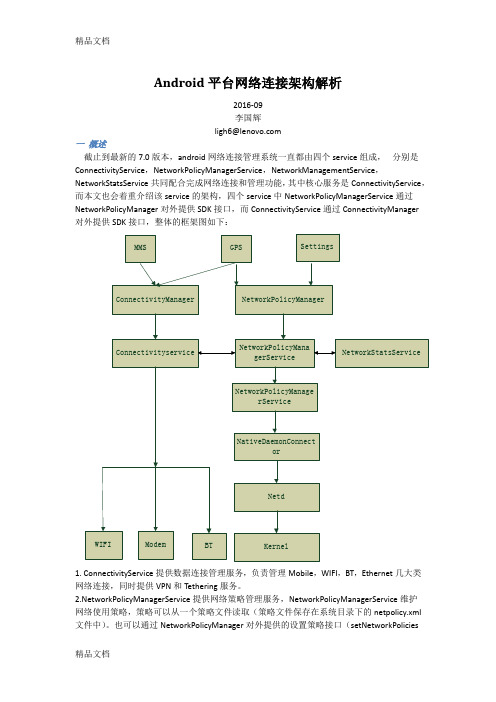
Android平台网络连接架构解析2016-09李国辉ligh6@一概述截止到最新的7.0版本,android网络连接管理系统一直都由四个service组成,分别是ConnectivityService,NetworkPolicyManagerService,NetworkManagementService,NetworkStatsService共同配合完成网络连接和管理功能,其中核心服务是ConnectivityService,而本文也会着重介绍该service的架构,四个service中NetworkPolicyManagerService通过NetworkPolicyManager对外提供SDK接口,而ConnectivityService通过ConnectivityManager对外提供SDK接口,整体的框架图如下:1. ConnectivityService提供数据连接管理服务,负责管理Mobile,WIFI,BT,Ethernet几大类网络连接,同时提供VPN和Tethering服务。
workPolicyManagerService提供网络策略管理服务,NetworkPolicyManagerService维护网络使用策略,策略可以从一个策略文件读取(策略文件保存在系统目录下的netpolicy.xml 文件中)。
也可以通过NetworkPolicyManager对外提供的设置策略接口(setNetworkPolicies及setUidPolicy)进行设置,NetworkPolicyManagerService能够根据这些设置或从策略文件中读取的策略控制网络连接。
另外NetworkPolicyManagerService还具有动态调节网络连接限额及动态设置网络连接的功能,动态调节网络连接限额机制是通过INetworkStatsService访问NetworkStatsService服务获得上面设置或读取的策略匹配的网络连接类型的传输统计信息(NetworkPolicyManagerService采用NetworkTemplate进行网络连接类型的匹配),并根据这些信息生成有效的规则,并提交给ConnectivityService服务,并调用NetworkManagementService 的setInterfaceQuota函数对网络连接的带宽限额。
SOTI 移动安全解决方案

目前,摩托罗拉的Windows Mobile,CE和Android设备正在 陆续预装MobiControl Stage
谢谢!
MobiControl
中兴
华为
MobiControl
通过了超过70家OEM厂商的支持
基Байду номын сангаас标准的跨平台框架
构建一个通用的模块化框架
全生命周期的移动管理
为您提供完整的安全策略
安全保障移动设备管理生命周期的每一步
• 安全的设备注册
•
• • • • • • •
应用管理
内容管理 系统加密,防病毒 设备功能管理 屏幕应用锁定 证书管理 失联策略 应用沙箱,Samsung Knox, Google AFW, Graphite Software
移动安全管理解决方案
为您提供端到端的移动安全管理解决方案
全生命周期的移动设备管理
• 业界独有的安卓加技术,大量专利内核级API, 对设备进行内核级的管控。 • 与硬件厂家深度合作,真正多种厂家设备兼容,满足安全管理的需求。 • 一个平台可以管理几乎所有的智能移动设备,统一的功能模块化设计。 • 高可扩展性,与第三方应用的结合,支持自定义数据,自定义属性,功能脚本等。 • 实用的功能设计,切实解决用户碰到的问题。
MobiControl 移动设备安全及管理功能
设备监控和报告
能够随时查看设备当前信
息,通过报表查看设备使 用状况,在线情况分组状
况等。便于企业对设备进
行资产管理。
真正的远程控制和实时 远程查看,实时支持
Mobicontrol的远程控制是Android和Windows 设备最快的和最可靠的交互式远程控制,能够提 供最优秀的远程控制和故障排除,还可以为iOS设 备提供远程查看和先进的设备管理。 这些一流的远程桌面功能使管理员毫不费力的支
Landesk桌面管理与安全解决方案

3
定期维护与更新
定期对客户的系统进行维护和更新,确保系统的 稳定性和安全性,提高客户的使用满意度。
THANKS
谢谢您的观看
VS
详细描述
客户C是一家政府机构,由于监管合规要 求严格,需要确保员工桌面环境的合规性 。通过部署Landesk解决方案,客户C实 现了对员工桌面环境的精细化管理,满足 了各项监管要求,同时提高了IT服务响应 速度和工作效率,为政府机构的业务运营 提供了有力支持。
05
合作伙伴与认证
合作伙伴网络
广泛的合作伙伴网络
商务谈判与合作
与客户进行商务谈判,就合作方式、合同条款等达成一致,促成双 方的合作。
技术支持与服务
1 2
技术咨询与支持
为客户提供Landesk桌面管理与安全解决方案的 技术咨询和支持服务,解决客户在使用产品过程 中遇到的技术问题。
培训与指导
为客户提供产品使用的培训和指导服务,帮助客 户更好地使用产品,提高使用体验和工作效率。
根据客户的具体需求和行业特点,Landesk可提供定制化的 桌面管理与安全解决方案,确保解决方案的针对性和有效
性。
06
联系我们
销售咨询
了解产品详情
为客户提供Landesk桌面管理与安全解决方案的详细信息,解答客 户关于产品功能、特点、价格等方面的疑问。
定制化推荐
根据客户的实际需求和场景,为客户提供定制化的产品推荐,帮助 客户选择最适合自己需求的解决方案。
培训和教育
提供安全培训和的安全风险。
数据加密与备份
数据加密
采用强加密算法对敏感数据进行加密,确保数据 在传输和存储时的安全性。
数据备份
定期备份所有数据,以防数据丢失或损坏,同时 确保数据的可恢复性。
Kaspersky Security for Mobile 用户手册说明书

Kaspersky Security for Mobile © 2022 AO Kaspersky Lab目录Kaspersky Security for Mobile 帮助新增功能取决于管理工具的应用程序功能的比较分发包在 Kaspersky Security Center Web Console 和 Kaspersky Security Center 云控制台中工作关于 Kaspersky Security Center Web Console 和云控制台中的移动设备管理Kaspersky Security Center Web Console 和云控制台中的移动设备管理的主要功能关于 Kaspersky Endpoint Security for Android 应用程序关于 Kaspersky Security for Mobile 插件关于 Kaspersky Endpoint Security for Android 插件硬件和软件要求已知问题和注意事项在 Kaspersky Security Center Web Console 或云控制台中部署移动设备管理解决方案部署方案准备 Kaspersky Security Center Web Console 和云控制台以进行部署配置管理服务器以连接移动设备创建管理组创建自动将设备分配至管理组的规则部署管理插件从可用分发包列表安装管理插件从分发包安装管理插件部署 Kaspersky Endpoint Security for Android 应用程序使用 Kaspersky Security Center Web Console 或云控制台部署 Kaspersky Endpoint Security for Android 应用程序激活 Kaspersky Endpoint Security for Android 应用程序提供 Kaspersky Endpoint Security for Android 应用程序所需的权限管理证书查看证书列表定义证书设置创建证书续订证书删除证书与 Firebase Cloud Messaging 交换信息在 Kaspersky Security Center Web Console 和云控制台中管理移动设备将移动设备连接到 Kaspersky Security Center将未分配的移动设备移至管理组向移动设备发送命令从 Kaspersky Security Center 移除移动设备管理组策略用于管理移动设备的组策略查看组策略列表查看策略分发结果创建组策略修改组策略复制组策略将策略移动到另一个管理组删除组策略定义策略设置配置反病毒保护配置实时保护配置移动设备上的病毒扫描自动运行配置反病毒数据库更新定义设备解锁设置配置对被盗或丢失设备的数据的保护配置应用程序控制配置使移动设备符合公司安全要求的合规性控制启用和禁用合规性规则编辑合规性规则添加合规性规则删除合规性规则不合规标准列表不合规时的操作列表配置用户对网站的访问配置功能限制防止 Kaspersky Endpoint Security for Android 被删除配置移动设备与 Kaspersky Security Center 的同步卡巴斯基安全网络与卡巴斯基安全网络交换信息启用和禁用卡巴斯基安全网络与 Google Analytics for Firebase、SafetyNet Attestation、Firebase Performance Monitoring 和 Crashlytics 交换信息配置移动设备上的通知检测设备入侵(根权限)定义授权许可设置配置事件配置有关在用户设备上安装、更新和删除应用程序的事件网络负载在基于 MMC 的管理控制台中工作关键用例关于 Kaspersky Security for Mobile基于 MMC 的管理控制台中的移动设备管理的主要功能关于 Kaspersky Endpoint Security for Android关于 Kaspersky Device Management for iOS关于 Exchange 邮箱关于 Kaspersky Endpoint Security for Android 管理插件关于 Kaspersky Device Management for iOS 管理插件硬件和软件要求已知问题和注意事项部署解决方案架构常见集成解决方案部署方案Kaspersky Endpoint Security for Android 的部署方案iOS MDM 配置文件的部署方案准备管理控制台以便部署集成解决方案配置连接移动设备的管理服务器设置在管理控制台中显示“移动设备管理”文件夹创建管理组为设备自动分配至管理组创建规则创建常规证书安装 Kaspersky Endpoint Security for Android权限使用 Google Play 链接安装 Kaspersky Endpoint Security for Android Kaspersky Endpoint Security for Android 的其他安装方法从 Google Play 或华为应用市场手动安装创建和配置安装包创建独立安装包配置同步设置激活 Kaspersky Endpoint Security for Android 应用程序安装 iOS MDM 配置文件关于 iOS 设备管理模式通过 Kaspersky Security Center 安装安装管理插件更新先前版本的应用程序升级先前版本的 Kaspersky Endpoint Security for Android安装先前版本的 Kaspersky Endpoint Security for Android升级先前版本的管理插件删除 Kaspersky Endpoint Security for Android远程删除应用程序允许用户删除应用程序由用户删除应用程序配置和管理开始使用启动和停止应用程序创建管理组用于管理移动设备的组策略创建组策略配置同步设置管理对组策略的修订删除组策略限制配置组策略的权限保护在安卓设备上配置防病毒保护在互联网上保护 Android 设备保护被盗或丢失设备的数据向移动设备发送命令解锁移动设备数据加密配置设备解锁密码强度为安卓设备配置强解锁密码为 iOS MDM 设备配置强解锁密码为 EAS 设备配置强解锁密码配置虚拟专用网 (VPN)在安卓设备上配置 VPN(仅限三星)在 iOS MDM 设备上配置 VPN在安卓设备上配置防火墙(仅限三星)防止 Kaspersky Endpoint Security for Android 被删除检测设备入侵(根权限)在 iOS MDM 设备上配置全局 HTTP 代理向 iOS MDM 设备添加安全证书向 iOS MDM 设备添加 SCEP 配置文件控制配置限制运行 Android 10 及更高版本的设备的特殊注意事项配置安卓设备的限制配置 iOS MDM 设备功能限制配置 EAS 设备功能限制配置用户对网站的访问在安卓设备上配置网站访问在 iOS MDM 设备上配置网站访问使用公司安全要求控制安卓设备的合规性应用程序启动控制安卓设备上的应用程序启动控制为应用程序配置 EAS 设备限制安卓设备上的软件清单在 Kaspersky Security Center 中配置安卓设备的显示管理配置与 Wi-Fi 网络的连接将安卓设备连接至 Wi-Fi 网络将 iOS MDM 设备连接至 Wi-Fi 网络配置电子邮件在 iOS MDM 设备上配置邮箱在 iOS MDM 设备上配置 Exchange 邮箱在安卓设备上配置 Exchange 邮箱(仅限三星)管理第三方移动应用程序配置 Kaspersky Endpoint Security for Android 的通知将 iOS MDM 设备连接到 AirPlay将 iOS MDM 设备连接到 AirPrint配置访问点名称 (APN)在安卓设备上配置 APN(仅限三星)在 iOS MDM 设备上配置 APN配置安卓工作配置文件关于安卓工作配置文件配置工作配置文件添加 LDAP 帐户添加日历帐户添加联系人帐户配置日历订阅添加网络收藏夹添加字体使用第三方 EMM 系统管理应用程序(仅限 Android)开始使用如何安装应用程序如何激活应用程序如何连接设备到 Kaspersky Security CenterAppCon g 文件网络负载加入卡巴斯基安全网络与卡巴斯基安全网络交换信息启用和禁用使用卡巴斯基安全网络使用卡巴斯基私有安全网络对第三方服务的数据提供与 Firebase Cloud Messaging 交换信息与 Google Analytics for Firebase、SafetyNet Attestation、Firebase Performance Monitoring 和 Crashlytics 交换信息全局接受附加声明三星 KNOX通过 KNOX Mobile Enrollment 安装 Kaspersky Endpoint Security for Android 应用程序创建 KNOX MDM 配置文件在 KNOX Mobile Enrollment 中添加设备安装应用程序配置 KNOX 容器关于 KNOX 容器激活 Samsung KNOX在 KNOX 中配置防火墙在 KNOX 中配置 Exchange 邮箱附录配置组策略的权限应用程序类别使用 Kaspersky Endpoint Security for Android 应用程序程序功能主界面概览设备扫描运行计划扫描更改保护模式反病毒数据库更新计划的数据库更新设备丢失或被盗时如何操作Web 保护应用程序控制获取证书与 Kaspersky Security Center 同步不使用 Kaspersky Security Center 激活 Kaspersky Endpoint Security for Android 应用程序更新应用程序卸载应用程序带有手提箱图标的应用程序KNOX 应用程序程序授权许可关于最终用户许可协议关于授权许可关于订阅关于密钥数据提供联系技术支持如何获得技术支持通过“Kaspersky CompanyAccount”获得技术支持有关应用程序的其他信息源术语Apple 推送通知服务 (APNs) 证书EAS 设备Exchange Mobile Devices ServerIMAPiOS MDM 服务器iOS MDM 设备iOS MDM 配置文件Kaspersky Security Center Web Server Kaspersky Security Center 管理员Kaspersky 更新服务器Kaspersky 类别POP3SSL代理服务器供给配置文件最终用户授权许可协议卡巴斯基安全网络 (KSN)卡巴斯基私有安全网络(私有 KSN)反病毒数据库合规性控制安卓工作配置文件安装包密钥文件应用程序管理插件授权许可授权许可的有效期清单文件激活码激活程序独立安装包病毒监控设备策略管理员工作站管理服务器管理组组任务网络钓鱼解锁码订阅隔离有关第三方代码的信息商标声明Kaspersky Security for Mobile 帮助Kaspersky Security for Mobile 旨在保护和管理公司移动设备以及公司员工用于公司用途的个人移动设备。
android基础知识题库100道及答案(完整版)

android基础知识题库100道及答案(完整版)1. Android 操作系统基于以下哪种内核?A. LinuxB. WindowsC. UnixD. Mac OS答案:A2. Android 应用程序主要使用哪种编程语言?A. JavaB. C++C. PythonD. Ruby答案:A3. AndroidManifest.xml 文件的作用是什么?A. 存储应用的资源B. 定义应用的组件和权限C. 保存应用的数据D. 处理应用的逻辑答案:B4. 在Android 中,用于存储少量键值对数据的存储方式是?A. SharedPreferencesB. SQLiteC. ContentProviderD. File答案:A5. Android 中的Activity 生命周期方法中,在Activity 可见但不可交互时调用的是?A. onStart()B. onResume()C. onPause()D. onStop()答案:C6. 以下哪个不是Android 中的布局管理器?A. LinearLayoutB. RelativeLayoutC. AbsoluteLayoutD. GridLayout答案:C7. Android 中用于在后台执行耗时操作的是?A. AsyncTaskB. HandlerC. ThreadD. Service答案:A8. 以下哪个不是Android 中的广播类型?A. 普通广播B. 有序广播C. 无序广播D. 本地广播答案:C9. Android 中用于发送短信的权限是?A. android.permission.SEND_SMSB. android.permission.RECEIVE_SMSC. android.permission.READ_SMSD. android.permission.WRITE_SMS答案:A10. 在Android 中,用于获取网络数据的类是?A. HttpURLConnectionB. SocketC. ServerSocketD. DatagramSocket答案:A11. Android 中用于实现页面跳转的类是?A. IntentB. BundleC. ContextD. ActivityManager答案:A12. 以下哪个不是Android 中的存储方式?A. 内部存储B. 外部存储C. 网络存储D. 数据库存储答案:C13. Android 中用于显示图片的控件是?A. ImageViewB. TextViewC. ButtonD. EditText答案:A14. 以下哪个不是Android 中的触摸事件?A. onClickB. onTouchC. onLongClickD. onScroll答案:A15. Android 中用于创建菜单的方法是?A. onCreateOptionsMenuB. onPrepareOptionsMenuC. onOptionsItemSelectedD. onContextItemSelected答案:A16. 以下哪个不是Android 中的动画类型?A. 帧动画B. 补间动画C. 属性动画D. 3D 动画答案:D17. Android 中用于获取系统服务的类是?A. SystemServiceB. ContextC. ServiceManagerD. ActivityManager答案:B18. 以下哪个不是Android 中的传感器类型?A. 加速度传感器B. 陀螺仪传感器C. 光线传感器D. 压力传感器答案:D19. Android 中用于实现碎片(Fragment)的类是?A. FragmentB. FragmentManagerC. FragmentTransactionD. FragmentActivity答案:A20. 以下哪个不是Android 中的进程类型?A. 前台进程B. 后台进程C. 空进程D. 服务进程答案:C21. Android 中用于处理音频的类是?A. AudioRecordB. AudioTrackC. MediaPlayerD. SoundPool答案:C22. 以下哪个不是Android 中的图形绘制方式?A. CanvasB. OpenGL ESC. SVGD. Bitmap答案:C23. Android 中用于实现定位功能的类是?A. LocationManagerB. LocationProviderC. GeocoderD. MapView答案:A24. 以下哪个不是Android 中的通知类型?A. 普通通知B. 大视图通知C. 悬挂式通知D. 弹窗通知答案:D25. Android 中用于实现自定义视图的方法是?A. onDrawB. onMeasureC. onLayoutD. onCreate答案:A26. 以下哪个不是Android 中的数据传递方式?A. Intent 传递B. 共享文件传递C. 数据库传递D. 网络传递答案:C27. Android 中用于实现多线程下载的类是?A. DownloadManagerB. AsyncTaskC. ThreadPoolExecutorD. HttpClient答案:A28. 以下哪个不是Android 中的网络请求方式?A. GETB. POSTC. PUTD. DELETE答案:C29. Android 中用于实现蓝牙通信的类是?A. BluetoothAdapterB. BluetoothSocketC. BluetoothServerSocketD. BluetoothDevice答案:A30. 以下哪个不是Android 中的权限组?A. 危险权限组B. 正常权限组C. 特殊权限组D. 签名权限组答案:D31. Android 中用于实现语音识别的类是?A. SpeechRecognizerB. TextToSpeechC. AudioManagerD. Vibrator答案:A32. 以下哪个不是Android 中的视图组(ViewGroup)?A. FrameLayoutB. LinearLayoutC. RelativeLayoutD. ListView答案:D33. Android 中用于实现推送通知的服务是?A. GCMB. FCMC. C2DMD. MQTT答案:B34. 以下哪个不是Android 中的数据存储格式?A. JSONB. XMLC. CSVD. YAML答案:D35. Android 中用于实现进程间通信的方式是?A. IntentB. MessengerC. AIDLD. ContentProvider答案:C36. 以下哪个不是Android 中的UI 线程操作限制?A. 网络操作B. 耗时计算C. 文件读写D. 界面更新答案:D37. Android 中用于实现图片加载的开源框架是?A. PicassoB. GlideC. FrescoD. Volley答案:B38. 以下哪个不是Android 中的资源类型?A. 字符串资源C. 布局资源D. 服务资源答案:D39. Android 中用于实现数据库升级的方法是?A. onUpgradeB. onCreateC. onOpenD. onDowngrade答案:A40. 以下哪个不是Android 中的意图过滤器(IntentFilter)的动作?A. ACTION_CALLB. ACTION_EDITC. ACTION_SENDD. ACTION_DELETE答案:D41. Android 中用于实现视频播放的类是?A. VideoViewB. MediaControllerC. SurfaceViewD. TextureView答案:A42. 以下哪个不是Android 中的布局属性?A. layout_widthB. layout_heightC. paddingD. margin答案:C43. Android 中用于实现应用内购买的服务是?A. In-app BillingB. Google Play BillingC. Amazon Appstore BillingD. Apple App Store Billing答案:B44. 以下哪个不是Android 中的触摸模式?A. 单点触摸B. 多点触摸C. 滑动触摸答案:C45. Android 中用于实现动画插值器(Interpolator)的类是?A. AccelerateInterpolatorB. DecelerateInterpolatorC. LinearInterpolatorD. CycleInterpolator答案:A46. 以下哪个不是Android 中的消息机制?A. HandlerB. LooperC. MessageQueueD. ThreadPool答案:D47. Android 中用于实现文件上传的类是?A. HttpPostB. MultipartEntityC. FileUploadD. HttpPut答案:B48. 以下哪个不是Android 中的屏幕方向?A. 竖屏B. 横屏C. 自动旋转D. 反向横屏答案:D49. Android 中用于实现手势识别的类是?A. GestureDetectorB. ScaleGestureDetectorC. OnGestureListenerD. OnDoubleTapListener答案:A50. 以下哪个不是Android 中的日志级别?A. VERBOSEB. DEBUGC. INFOD. WARNING答案:C51. Android 中用于实现应用签名的工具是?A. KeytoolB. JarsignerC. ApktoolD. Dex2jar答案:B52. 以下哪个不是Android 中的进程优先级?A. 前台优先级B. 可见优先级C. 服务优先级D. 后台优先级答案:C53. Android 中用于实现地图功能的类是?A. MapViewB. GoogleMapC. LocationViewD. MapFragment答案:B54. 以下哪个不是Android 中的图片压缩格式?A. JPEGB. PNGC. GIFD. BMP答案:D55. Android 中用于实现应用内搜索的类是?A. SearchViewB. SearchManagerC. ContentSearcherD. QueryBuilder答案:B56. 以下哪个不是Android 中的传感器事件类型?A. SENSOR_TYPE_ACCELEROMETERB. SENSOR_TYPE_GYROSCOPEC. SENSOR_TYPE_LIGHTD. SENSOR_TYPE_TEMPERATURE答案:D57. Android 中用于实现应用更新的方式是?A. Google Play 自动更新B. 应用内检测更新C. 手动下载更新D. 以上都是答案:D58. 以下哪个不是Android 中的资源目录?A. drawableB. layoutC. valuesD. assets答案:D59. Android 中用于实现进程保活的方法是?A. 前台服务B. 广播接收器C. 工作线程D. 以上都是答案:D60. 以下哪个不是Android 中的动画帧间隔时间单位?A. 毫秒B. 秒C. 微秒D. 纳秒答案:D61. Android 中用于实现应用主题的方式是?A. 在styles.xml 中定义B. 在AndroidManifest.xml 中指定C. 在代码中设置D. 以上都是答案:D62. 以下哪个不是Android 中的布局测量模式?A. EXACTLYB. AT_MOSTC. UNSPECIFIEDD. AUTO答案:D63. Android 中用于实现音频录制的类是?A. MediaRecorderB. AudioRecordC. SoundRecorderD. VoiceRecorder答案:A64. 以下哪个不是Android 中的视图状态保存方法?A. onSaveInstanceStateB. onRestoreInstanceStateC. onPauseD. onResume答案:C65. Android 中用于实现应用国际化的方式是?A. 使用资源文件B. 在代码中判断语言C. 使用第三方库D. 以上都是答案:D66. 以下哪个不是Android 中的触摸事件分发机制?A. dispatchTouchEventB. onInterceptTouchEventC. onTouchEventD. onTouchDispatchEvent答案:D67. Android 中用于实现应用加密的方式是?A. 对称加密B. 非对称加密C. 哈希加密D. 以上都是答案:D68. 以下哪个不是Android 中的应用组件?A. ActivityB. ServiceC. BroadcastReceiverD. Adapter答案:D69. Android 中用于实现应用权限管理的类是?A. PermissionManagerB. PermissionCheckerC. PackageManagerD. ActivityManager答案:C70. 以下哪个不是Android 中的应用启动模式?A. standardB. singleTopC. singleTaskD. singleInstance答案:A71. Android 中用于实现应用崩溃捕获的工具是?A. ACRAB. BuglyC. CrashlyticsD. 以上都是答案:D72. 以下哪个不是Android 中的数据绑定方式?A. 双向数据绑定B. 单向数据绑定C. 无数据绑定D. 自动数据绑定答案:D73. Android 中用于实现应用性能优化的工具是?A. Android ProfilerB. LeakCanaryC. SystraceD. 以上都是答案:D74. 以下哪个不是Android 中的应用架构模式?A. MVPB. MVVMC. MVCD. MVVMC答案:D75. Android 中用于实现应用热修复的技术是?A. DexposedB. AndFixC. TinkerD. 以上都是答案:D76. 以下哪个不是Android 中的应用混淆工具?A. ProGuardB. R8C. DexGuardD.混淆不是必需的答案:D77. Android 中用于实现应用签名的密钥类型是?A. 调试密钥B. 发布密钥C. 临时密钥D. 以上都是答案:D78. 以下哪个不是Android 中的应用测试类型?A. 单元测试B. 集成测试C. 系统测试D. 压力测试答案:D79. Android 中用于实现应用多语言支持的资源文件后缀是?A. xmlB. stringsC. valuesD. 语言代码答案:D80. 以下哪个不是Android 中的应用资源目录?A. mipmapB. rawC. animD. class答案:D81. Android 中用于实现应用数据备份的类是?A. BackupManagerB. RestoreManagerC. DataManagerD. FileManager答案:A82. 以下哪个不是Android 中的应用权限分类?A. 危险权限C. 特殊权限D. 自定义权限答案:C83. Android 中用于实现应用动态权限申请的方法是?A. requestPermissionsB. checkSelfPermissionC. shouldShowRequestPermissionRationaleD. 以上都是答案:D84. 以下哪个不是Android 中的应用缓存策略?A. 内存缓存B. 磁盘缓存C. 网络缓存D. 无缓存答案:C85. Android 中用于实现应用数据加密存储的类是?A. CipherB. SecretKeyC. EncryptedFileD. EncryptedSharedPreferences答案:D86. 以下哪个不是Android 中的应用版本控制方式?A. 版本号B. 版本名C. 构建号D. 发布日期答案:D87. Android 中用于实现应用日志输出到文件的类是?A. FileWriterB. BufferedWriterC. PrintWriterD. LogWriter答案:A88. 以下哪个不是Android 中的应用性能指标?A. CPU 使用率B. 内存使用率C. 电量消耗答案:D89. Android 中用于实现应用资源压缩的工具是?A. aaptB. apktoolC. dex2jarD. jd-gui答案:A90. 以下哪个不是Android 中的应用发布渠道?A. Google PlayB. 应用宝C. 豌豆荚D. 开发工具答案:D91. Android 中用于实现应用版本回退的方法是?A. 安装旧版本的APKB. 恢复应用数据C. 没有直接的版本回退方法D. 使用系统的备份功能答案:C92. 以下哪个不是Android 中的应用图标尺寸?A. 48x48 dpB. 72x72 dpC. 96x96 dpD. 128x128 dp答案:D93. Android 中用于实现应用推送通知图标定制的方法是?A. 在NotificationCompat.Builder 中设置B. 在AndroidManifest.xml 中设置C. 在资源文件中设置D. 无法定制答案:A94. 以下哪个不是Android 中的应用启动画面类型?A. 静态图片B. 动态图片C. 视频D. 文本答案:D95. Android 中用于实现应用数据迁移的方法是?A. 手动复制数据B. 使用数据库迁移工具C. 利用系统提供的备份和恢复机制D. 以上都是答案:D96. 以下哪个不是Android 中的应用架构组件?A. LiveDataB. ViewModelC. RepositoryD. AdapterView答案:D97. 以下哪个不是Android 中获取设备唯一标识的可靠方法?A. IMEIB. Android IDC. UUIDD. 以上都不是可靠方法答案:D98. Android 中用于实现应用在后台运行时保持网络连接的方式是?A. 使用前台服务B. 使用唤醒锁C. 使用JobSchedulerD. 以上都是答案:D99. 以下哪个不是Android 中处理图片加载时的优化策略?A. 图片压缩B. 图片缓存C. 图片懒加载D. 图片加密答案:D100. Android 中用于实现应用在不同屏幕尺寸上自适应布局的方式是?A. 使用百分比布局B. 使用约束布局C. 使用多种布局文件D. 以上都是答案:D。
Kaspersky Embedded Systems Security 安卓安全全面解决方案说明书

KasperskyEmbedded Systems SecurityAll-in-one security designed for embedded systemsThe embedded systems market is growing steadily. And cybercriminals are taking note.While the number of attacked devices in the first 10 months of 2019 was slightly lower than the previous year, the numberof ATM/POS infections had already exceeded those for all of 2018.Embedded systems are all around us and impact on every part of our daily lives – we depend on them for everything from PoS systems and ATMs to medical devices and telecommunications. This means more attack vectors than ever before.As support for Windows 7 winds down – ending on 12 January 2020 – there is still time for companies to update the OS in their embedded systems, and take any additional protection measures necessary. However, older Windows XP - still an extremely popular OS for embedded systems – is still being overlooked, even though support for that OS ended in 2016. This is an open invitation to hackers.Cybercriminals are increasingly turning their attention to these embedded devices as a door into the corporate network, and businesses need to be smarter than ever to keep their systems and data safe. Featuring powerful threat intelligence, real-time malware detection, comprehensive application and device controls and flexible management, Kaspersky Embedded Systems Security is all-in-one security designed specifically for embedded systems.HighlightsEfficient Design for even Low-End HardwareKaspersky Embedded Systems Security has been built specifically to operate effectively even on low-end hardware. Efficient design delivers powerful security with no risk of systems overload. Requirements start from only 256MB RAM for the Windows XP family, with around 50MB space required on the system hard drive when operating in ‘Default Deny only’ mode. Memory ProtectionPowerful Exploit Prevention technology watches over critical processes to prevent exploits from attacking unpatchedand even zero-day vulnerabilities in applications and system components. This is especially important for protection against widespread ransomware attacks such as WannaCry and ExPetr. Windows XP OptimizedMost embedded systems still run on the now-unsupported Windows® XP OS. Kaspersky Embedded Systems Security has been optimized to run with full functionally on the Windows XP platform as well as the Windows 7, Windows 8 and Windows 10 families.Kaspersky Embedded Systems Security is committed to providing 100% support for the Windows XP family for the foreseeable future, giving enough time for gradual upgrade. ComplianceThe unique, comprehensive set of protection components (anti-malware, application and device control, firewall management, File Integrity Monitoring and log audit) within Kaspersky Embedded Systems Security identifies and blocks malicious actions against your system, and detects different indicators of a security breach, in compliance with regulations (including PCI/DSS, SWIFT, etc.).ATMs POS Ticketingmachines Cashier Old PCs Medicalequipment2019 AO Kaspersky Lab. All rights reserved.Registered trademarks and service marks are the property of their respective owners.Cyber Threats News: IT Security News: IT Security for SMB: /businessIT Security for Enterprise: /enterpriseWe are proven. We are independent. We aretransparent. We are committed to building a safer world, where technology improves our lives. Which is why we secure it, so everyone everywhere has the endless opportunities it brings. Bring on cybersecurity for a safer tommorow.Know more at /transparencyFeaturesPowerful Anti-MalwareProactive, cloud-assisted threat detection and analysis work with traditional technologies to provide protection from known, unknown and advanced threats. An optional (but strongly recommended) anti-malware component can be disabled in scenarios with low-end hardware or slow communications channels.Real-time Malware Detection with Kaspersky Security Network (KSN)KSN is Kaspersky cloud-assisted, global threat intelligencenetwork. Millions of globally distributed nodes constantly feed real-world threat intelligence to our systems, ensuring rapid response to even the newest, emerging and evolving threats, including mass attacks.This constant flow of new data about attempted malware attacks and suspicious behavior creates instant file verdicts, delivering real-time protection against the latest threats.Application ControlAdopting a Default Deny scenario using Application Launch Control optimizes your system’s resilience to data breaches. By prohibiting the running of any applications other than specified programs, services, and trusted system components, you can automatically block most forms of malware completely.Software distribution control uses a ‘trusted installer’ approach, eliminating the need for time-consuming, manual whitelisting of files created or changed during a software update or installation. Just specify the installer as trusted and carry out the update in the usual way.Device Monitoring and ControlDevice Control from Kaspersky gives you the ability to control USB storage devices connected or trying to connect physically to systems hardware. Preventing access by unauthorized devices means you block a common point of entry used by cybercriminals as the first step in a malware attack.All USB device connections are monitored and logged so that inappropriate USB use can be identified as a possible attack source during the incident investigation and response process.Windows Firewall ManagementWindows Firewall can be configured directly from Kaspersky Security Center, giving you the convenience of local firewall management through a single unified console. This is essential when embedded systems are not in domain and Windows firewall settings can’t be configured centrally.File Integrity Monitoring*File Integrity Monitoring tracks actions performed on specified files and folders within scope. You can also configure file changes to be tracked during periods when monitoring is interrupted.Log Audit*Kaspersky Embedded Systems Security monitors possible protection violations based on inspecting Windows Event Logs. The application notifies the administrator when it detects abnormal behavior that may indicate an attempted cyberattack.SIEM IntegrationKaspersky Embedded Systems Security can convert events in application logs into formats supported by the syslog server, so these can be transmitted to, and successfully recognized by, all SIEM systems. Events can be exported directly from Kaspersky Embedded System Security to SIEM or centrally via Kaspersky Security Center.Flexible ManagementKaspersky Embedded Systems Security can be managed from the command line, local GUI, or the centralized policy-based management via Kaspersky Security Center. Security policies, signature updates, anti-malware scans and results collection are easily managed through a single centralized management console – Kaspersky Security Center. In addition, clients in a local network can be managed through any local console – particularly useful when working in the isolated, segmented networks typical of embedded systems.* Requires Kaspersky Embedded Systems Security Compliance Edition licenseSystem integrity monitoring • File integrity monitor • Log InspectionAnti-malware protection • Optional• Real-time/on-demand • Exploit prevention against ransomware and other threats Optimized system requirements • RAM 256MB and more • OS: Windows XP and laterSystem control• Application launch control • Software distribution control • Device controlNetwork protection • Firewall management。
Native Instruments MASCHINE MIKRO MK3用户手册说明书

The information in this document is subject to change without notice and does not represent a commitment on the part of Native Instruments GmbH. The software described by this docu-ment is subject to a License Agreement and may not be copied to other media. No part of this publication may be copied, reproduced or otherwise transmitted or recorded, for any purpose, without prior written permission by Native Instruments GmbH, hereinafter referred to as Native Instruments.“Native Instruments”, “NI” and associated logos are (registered) trademarks of Native Instru-ments GmbH.ASIO, VST, HALion and Cubase are registered trademarks of Steinberg Media Technologies GmbH.All other product and company names are trademarks™ or registered® trademarks of their re-spective holders. Use of them does not imply any affiliation with or endorsement by them.Document authored by: David Gover and Nico Sidi.Software version: 2.8 (02/2019)Hardware version: MASCHINE MIKRO MK3Special thanks to the Beta Test Team, who were invaluable not just in tracking down bugs, but in making this a better product.NATIVE INSTRUMENTS GmbH Schlesische Str. 29-30D-10997 Berlin Germanywww.native-instruments.de NATIVE INSTRUMENTS North America, Inc. 6725 Sunset Boulevard5th FloorLos Angeles, CA 90028USANATIVE INSTRUMENTS K.K.YO Building 3FJingumae 6-7-15, Shibuya-ku, Tokyo 150-0001Japanwww.native-instruments.co.jp NATIVE INSTRUMENTS UK Limited 18 Phipp StreetLondon EC2A 4NUUKNATIVE INSTRUMENTS FRANCE SARL 113 Rue Saint-Maur75011 ParisFrance SHENZHEN NATIVE INSTRUMENTS COMPANY Limited 5F, Shenzhen Zimao Center111 Taizi Road, Nanshan District, Shenzhen, GuangdongChina© NATIVE INSTRUMENTS GmbH, 2019. All rights reserved.Table of Contents1Welcome to MASCHINE (23)1.1MASCHINE Documentation (24)1.2Document Conventions (25)1.3New Features in MASCHINE 2.8 (26)1.4New Features in MASCHINE 2.7.10 (28)1.5New Features in MASCHINE 2.7.8 (29)1.6New Features in MASCHINE 2.7.7 (29)1.7New Features in MASCHINE 2.7.4 (31)1.8New Features in MASCHINE 2.7.3 (33)2Quick Reference (35)2.1MASCHINE Project Overview (35)2.1.1Sound Content (35)2.1.2Arrangement (37)2.2MASCHINE Hardware Overview (40)2.2.1MASCHINE MIKRO Hardware Overview (40)2.2.1.1Browser Section (41)2.2.1.2Edit Section (42)2.2.1.3Performance Section (43)2.2.1.4Transport Section (45)2.2.1.5Pad Section (46)2.2.1.6Rear Panel (50)2.3MASCHINE Software Overview (51)2.3.1Header (52)2.3.2Browser (54)2.3.3Arranger (56)2.3.4Control Area (59)2.3.5Pattern Editor (60)3Basic Concepts (62)3.1Important Names and Concepts (62)3.2Adjusting the MASCHINE User Interface (65)3.2.1Adjusting the Size of the Interface (65)3.2.2Switching between Ideas View and Song View (66)3.2.3Showing/Hiding the Browser (67)3.2.4Showing/Hiding the Control Lane (67)3.3Common Operations (68)3.3.1Adjusting Volume, Swing, and Tempo (68)3.3.2Undo/Redo (71)3.3.3Focusing on a Group or a Sound (73)3.3.4Switching Between the Master, Group, and Sound Level (77)3.3.5Navigating Channel Properties, Plug-ins, and Parameter Pages in the Control Area.773.3.6Navigating the Software Using the Controller (82)3.3.7Using Two or More Hardware Controllers (82)3.3.8Loading a Recent Project from the Controller (84)3.4Native Kontrol Standard (85)3.5Stand-Alone and Plug-in Mode (86)3.5.1Differences between Stand-Alone and Plug-in Mode (86)3.5.2Switching Instances (88)3.6Preferences (88)3.6.1Preferences – General Page (89)3.6.2Preferences – Audio Page (93)3.6.3Preferences – MIDI Page (95)3.6.4Preferences – Default Page (97)3.6.5Preferences – Library Page (101)3.6.6Preferences – Plug-ins Page (109)3.6.7Preferences – Hardware Page (114)3.6.8Preferences – Colors Page (114)3.7Integrating MASCHINE into a MIDI Setup (117)3.7.1Connecting External MIDI Equipment (117)3.7.2Sync to External MIDI Clock (117)3.7.3Send MIDI Clock (118)3.7.4Using MIDI Mode (119)3.8Syncing MASCHINE using Ableton Link (120)3.8.1Connecting to a Network (121)3.8.2Joining and Leaving a Link Session (121)4Browser (123)4.1Browser Basics (123)4.1.1The MASCHINE Library (123)4.1.2Browsing the Library vs. Browsing Your Hard Disks (124)4.2Searching and Loading Files from the Library (125)4.2.1Overview of the Library Pane (125)4.2.2Selecting or Loading a Product and Selecting a Bank from the Browser (128)4.2.3Selecting a Product Category, a Product, a Bank, and a Sub-Bank (133)4.2.3.1Selecting a Product Category, a Product, a Bank, and a Sub-Bank on theController (137)4.2.4Selecting a File Type (137)4.2.5Choosing Between Factory and User Content (138)4.2.6Selecting Type and Character Tags (138)4.2.7Performing a Text Search (142)4.2.8Loading a File from the Result List (143)4.3Additional Browsing Tools (148)4.3.1Loading the Selected Files Automatically (148)4.3.2Auditioning Instrument Presets (149)4.3.3Auditioning Samples (150)4.3.4Loading Groups with Patterns (150)4.3.5Loading Groups with Routing (151)4.3.6Displaying File Information (151)4.4Using Favorites in the Browser (152)4.5Editing the Files’ Tags and Properties (155)4.5.1Attribute Editor Basics (155)4.5.2The Bank Page (157)4.5.3The Types and Characters Pages (157)4.5.4The Properties Page (160)4.6Loading and Importing Files from Your File System (161)4.6.1Overview of the FILES Pane (161)4.6.2Using Favorites (163)4.6.3Using the Location Bar (164)4.6.4Navigating to Recent Locations (165)4.6.5Using the Result List (166)4.6.6Importing Files to the MASCHINE Library (169)4.7Locating Missing Samples (171)4.8Using Quick Browse (173)5Managing Sounds, Groups, and Your Project (175)5.1Overview of the Sounds, Groups, and Master (175)5.1.1The Sound, Group, and Master Channels (176)5.1.2Similarities and Differences in Handling Sounds and Groups (177)5.1.3Selecting Multiple Sounds or Groups (178)5.2Managing Sounds (181)5.2.1Loading Sounds (183)5.2.2Pre-listening to Sounds (184)5.2.3Renaming Sound Slots (185)5.2.4Changing the Sound’s Color (186)5.2.5Saving Sounds (187)5.2.6Copying and Pasting Sounds (189)5.2.7Moving Sounds (192)5.2.8Resetting Sound Slots (193)5.3Managing Groups (194)5.3.1Creating Groups (196)5.3.2Loading Groups (197)5.3.3Renaming Groups (198)5.3.4Changing the Group’s Color (199)5.3.5Saving Groups (200)5.3.6Copying and Pasting Groups (202)5.3.7Reordering Groups (206)5.3.8Deleting Groups (207)5.4Exporting MASCHINE Objects and Audio (208)5.4.1Saving a Group with its Samples (208)5.4.2Saving a Project with its Samples (210)5.4.3Exporting Audio (212)5.5Importing Third-Party File Formats (218)5.5.1Loading REX Files into Sound Slots (218)5.5.2Importing MPC Programs to Groups (219)6Playing on the Controller (223)6.1Adjusting the Pads (223)6.1.1The Pad View in the Software (223)6.1.2Choosing a Pad Input Mode (225)6.1.3Adjusting the Base Key (226)6.2Adjusting the Key, Choke, and Link Parameters for Multiple Sounds (227)6.3Playing Tools (229)6.3.1Mute and Solo (229)6.3.2Choke All Notes (233)6.3.3Groove (233)6.3.4Level, Tempo, Tune, and Groove Shortcuts on Your Controller (235)6.3.5Tap Tempo (235)6.4Performance Features (236)6.4.1Overview of the Perform Features (236)6.4.2Selecting a Scale and Creating Chords (239)6.4.3Scale and Chord Parameters (240)6.4.4Creating Arpeggios and Repeated Notes (253)6.4.5Swing on Note Repeat / Arp Output (257)6.5Using Lock Snapshots (257)6.5.1Creating a Lock Snapshot (257)7Working with Plug-ins (259)7.1Plug-in Overview (259)7.1.1Plug-in Basics (259)7.1.2First Plug-in Slot of Sounds: Choosing the Sound’s Role (263)7.1.3Loading, Removing, and Replacing a Plug-in (264)7.1.4Adjusting the Plug-in Parameters (270)7.1.5Bypassing Plug-in Slots (270)7.1.6Using Side-Chain (272)7.1.7Moving Plug-ins (272)7.1.8Alternative: the Plug-in Strip (273)7.1.9Saving and Recalling Plug-in Presets (273)7.1.9.1Saving Plug-in Presets (274)7.1.9.2Recalling Plug-in Presets (275)7.1.9.3Removing a Default Plug-in Preset (276)7.2The Sampler Plug-in (277)7.2.1Page 1: Voice Settings / Engine (279)7.2.2Page 2: Pitch / Envelope (281)7.2.3Page 3: FX / Filter (283)7.2.4Page 4: Modulation (285)7.2.5Page 5: LFO (286)7.2.6Page 6: Velocity / Modwheel (288)7.3Using Native Instruments and External Plug-ins (289)7.3.1Opening/Closing Plug-in Windows (289)7.3.2Using the VST/AU Plug-in Parameters (292)7.3.3Setting Up Your Own Parameter Pages (293)7.3.4Using VST/AU Plug-in Presets (298)7.3.5Multiple-Output Plug-ins and Multitimbral Plug-ins (300)8Using the Audio Plug-in (302)8.1Loading a Loop into the Audio Plug-in (306)8.2Editing Audio in the Audio Plug-in (307)8.3Using Loop Mode (308)8.4Using Gate Mode (310)9Using the Drumsynths (312)9.1Drumsynths – General Handling (313)9.1.1Engines: Many Different Drums per Drumsynth (313)9.1.2Common Parameter Organization (313)9.1.3Shared Parameters (316)9.1.4Various Velocity Responses (316)9.1.5Pitch Range, Tuning, and MIDI Notes (316)9.2The Kicks (317)9.2.1Kick – Sub (319)9.2.2Kick – Tronic (321)9.2.3Kick – Dusty (324)9.2.4Kick – Grit (325)9.2.5Kick – Rasper (328)9.2.6Kick – Snappy (329)9.2.7Kick – Bold (331)9.2.8Kick – Maple (333)9.2.9Kick – Push (334)9.3The Snares (336)9.3.1Snare – Volt (338)9.3.2Snare – Bit (340)9.3.3Snare – Pow (342)9.3.4Snare – Sharp (343)9.3.5Snare – Airy (345)9.3.6Snare – Vintage (347)9.3.7Snare – Chrome (349)9.3.8Snare – Iron (351)9.3.9Snare – Clap (353)9.3.10Snare – Breaker (355)9.4The Hi-hats (357)9.4.1Hi-hat – Silver (358)9.4.2Hi-hat – Circuit (360)9.4.3Hi-hat – Memory (362)9.4.4Hi-hat – Hybrid (364)9.4.5Creating a Pattern with Closed and Open Hi-hats (366)9.5The Toms (367)9.5.1Tom – Tronic (369)9.5.2Tom – Fractal (371)9.5.3Tom – Floor (375)9.5.4Tom – High (377)9.6The Percussions (378)9.6.1Percussion – Fractal (380)9.6.2Percussion – Kettle (383)9.6.3Percussion – Shaker (385)9.7The Cymbals (389)9.7.1Cymbal – Crash (391)9.7.2Cymbal – Ride (393)10Using the Bass Synth (396)10.1Bass Synth – General Handling (397)10.1.1Parameter Organization (397)10.1.2Bass Synth Parameters (399)11Working with Patterns (401)11.1Pattern Basics (401)11.1.1Pattern Editor Overview (402)11.1.2Navigating the Event Area (404)11.1.3Following the Playback Position in the Pattern (406)11.1.4Jumping to Another Playback Position in the Pattern (407)11.1.5Group View and Keyboard View (408)11.1.6Adjusting the Arrange Grid and the Pattern Length (410)11.1.7Adjusting the Step Grid and the Nudge Grid (413)11.2Recording Patterns in Real Time (416)11.2.1Recording Your Patterns Live (417)11.2.2Using the Metronome (419)11.2.3Recording with Count-in (420)11.3Recording Patterns with the Step Sequencer (422)11.3.1Step Mode Basics (422)11.3.2Editing Events in Step Mode (424)11.4Editing Events (425)11.4.1Editing Events with the Mouse: an Overview (425)11.4.2Creating Events/Notes (428)11.4.3Selecting Events/Notes (429)11.4.4Editing Selected Events/Notes (431)11.4.5Deleting Events/Notes (434)11.4.6Cut, Copy, and Paste Events/Notes (436)11.4.7Quantizing Events/Notes (439)11.4.8Quantization While Playing (441)11.4.9Doubling a Pattern (442)11.4.10Adding Variation to Patterns (442)11.5Recording and Editing Modulation (443)11.5.1Which Parameters Are Modulatable? (444)11.5.2Recording Modulation (446)11.5.3Creating and Editing Modulation in the Control Lane (447)11.6Creating MIDI Tracks from Scratch in MASCHINE (452)11.7Managing Patterns (454)11.7.1The Pattern Manager and Pattern Mode (455)11.7.2Selecting Patterns and Pattern Banks (456)11.7.3Creating Patterns (459)11.7.4Deleting Patterns (460)11.7.5Creating and Deleting Pattern Banks (461)11.7.6Naming Patterns (463)11.7.7Changing the Pattern’s Color (465)11.7.8Duplicating, Copying, and Pasting Patterns (466)11.7.9Moving Patterns (469)11.8Importing/Exporting Audio and MIDI to/from Patterns (470)11.8.1Exporting Audio from Patterns (470)11.8.2Exporting MIDI from Patterns (472)11.8.3Importing MIDI to Patterns (474)12Audio Routing, Remote Control, and Macro Controls (483)12.1Audio Routing in MASCHINE (484)12.1.1Sending External Audio to Sounds (485)12.1.2Configuring the Main Output of Sounds and Groups (489)12.1.3Setting Up Auxiliary Outputs for Sounds and Groups (494)12.1.4Configuring the Master and Cue Outputs of MASCHINE (497)12.1.5Mono Audio Inputs (502)12.1.5.1Configuring External Inputs for Sounds in Mix View (503)12.2Using MIDI Control and Host Automation (506)12.2.1Triggering Sounds via MIDI Notes (507)12.2.2Triggering Scenes via MIDI (513)12.2.3Controlling Parameters via MIDI and Host Automation (514)12.2.4Selecting VST/AU Plug-in Presets via MIDI Program Change (522)12.2.5Sending MIDI from Sounds (523)12.3Creating Custom Sets of Parameters with the Macro Controls (527)12.3.1Macro Control Overview (527)12.3.2Assigning Macro Controls Using the Software (528)13Controlling Your Mix (535)13.1Mix View Basics (535)13.1.1Switching between Arrange View and Mix View (535)13.1.2Mix View Elements (536)13.2The Mixer (537)13.2.1Displaying Groups vs. Displaying Sounds (539)13.2.2Adjusting the Mixer Layout (541)13.2.3Selecting Channel Strips (542)13.2.4Managing Your Channels in the Mixer (543)13.2.5Adjusting Settings in the Channel Strips (545)13.2.6Using the Cue Bus (549)13.3The Plug-in Chain (551)13.4The Plug-in Strip (552)13.4.1The Plug-in Header (554)13.4.2Panels for Drumsynths and Internal Effects (556)13.4.3Panel for the Sampler (557)13.4.4Custom Panels for Native Instruments Plug-ins (560)13.4.5Undocking a Plug-in Panel (Native Instruments and External Plug-ins Only) (564)14Using Effects (567)14.1Applying Effects to a Sound, a Group or the Master (567)14.1.1Adding an Effect (567)14.1.2Other Operations on Effects (574)14.1.3Using the Side-Chain Input (575)14.2Applying Effects to External Audio (578)14.2.1Step 1: Configure MASCHINE Audio Inputs (578)14.2.2Step 2: Set up a Sound to Receive the External Input (579)14.2.3Step 3: Load an Effect to Process an Input (579)14.3Creating a Send Effect (580)14.3.1Step 1: Set Up a Sound or Group as Send Effect (581)14.3.2Step 2: Route Audio to the Send Effect (583)14.3.3 A Few Notes on Send Effects (583)14.4Creating Multi-Effects (584)15Effect Reference (587)15.1Dynamics (588)15.1.1Compressor (588)15.1.2Gate (591)15.1.3Transient Master (594)15.1.4Limiter (596)15.1.5Maximizer (600)15.2Filtering Effects (603)15.2.1EQ (603)15.2.2Filter (605)15.2.3Cabinet (609)15.3Modulation Effects (611)15.3.1Chorus (611)15.3.2Flanger (612)15.3.3FM (613)15.3.4Freq Shifter (615)15.3.5Phaser (616)15.4Spatial and Reverb Effects (617)15.4.1Ice (617)15.4.2Metaverb (619)15.4.3Reflex (620)15.4.4Reverb (Legacy) (621)15.4.5Reverb (623)15.4.5.1Reverb Room (623)15.4.5.2Reverb Hall (626)15.4.5.3Plate Reverb (629)15.5Delays (630)15.5.1Beat Delay (630)15.5.2Grain Delay (632)15.5.3Grain Stretch (634)15.5.4Resochord (636)15.6Distortion Effects (638)15.6.1Distortion (638)15.6.2Lofi (640)15.6.3Saturator (641)15.7Perform FX (645)15.7.1Filter (646)15.7.2Flanger (648)15.7.3Burst Echo (650)15.7.4Reso Echo (653)15.7.5Ring (656)15.7.6Stutter (658)15.7.7Tremolo (661)15.7.8Scratcher (664)16Working with the Arranger (667)16.1Arranger Basics (667)16.1.1Navigating Song View (670)16.1.2Following the Playback Position in Your Project (672)16.1.3Performing with Scenes and Sections using the Pads (673)16.2Using Ideas View (677)16.2.1Scene Overview (677)16.2.2Creating Scenes (679)16.2.3Assigning and Removing Patterns (679)16.2.4Selecting Scenes (682)16.2.5Deleting Scenes (684)16.2.6Creating and Deleting Scene Banks (685)16.2.7Clearing Scenes (685)16.2.8Duplicating Scenes (685)16.2.9Reordering Scenes (687)16.2.10Making Scenes Unique (688)16.2.11Appending Scenes to Arrangement (689)16.2.12Naming Scenes (689)16.2.13Changing the Color of a Scene (690)16.3Using Song View (692)16.3.1Section Management Overview (692)16.3.2Creating Sections (694)16.3.3Assigning a Scene to a Section (695)16.3.4Selecting Sections and Section Banks (696)16.3.5Reorganizing Sections (700)16.3.6Adjusting the Length of a Section (702)16.3.6.1Adjusting the Length of a Section Using the Software (703)16.3.6.2Adjusting the Length of a Section Using the Controller (705)16.3.7Clearing a Pattern in Song View (705)16.3.8Duplicating Sections (705)16.3.8.1Making Sections Unique (707)16.3.9Removing Sections (707)16.3.10Renaming Scenes (708)16.3.11Clearing Sections (710)16.3.12Creating and Deleting Section Banks (710)16.3.13Working with Patterns in Song view (710)16.3.13.1Creating a Pattern in Song View (711)16.3.13.2Selecting a Pattern in Song View (711)16.3.13.3Clearing a Pattern in Song View (711)16.3.13.4Renaming a Pattern in Song View (711)16.3.13.5Coloring a Pattern in Song View (712)16.3.13.6Removing a Pattern in Song View (712)16.3.13.7Duplicating a Pattern in Song View (712)16.3.14Enabling Auto Length (713)16.3.15Looping (714)16.3.15.1Setting the Loop Range in the Software (714)16.3.15.2Activating or Deactivating a Loop Using the Controller (715)16.4Playing with Sections (715)16.4.1Jumping to another Playback Position in Your Project (716)16.5Triggering Sections or Scenes via MIDI (717)16.6The Arrange Grid (719)16.7Quick Grid (720)17Sampling and Sample Mapping (722)17.1Opening the Sample Editor (722)17.2Recording Audio (724)17.2.1Opening the Record Page (724)17.2.2Selecting the Source and the Recording Mode (725)17.2.3Arming, Starting, and Stopping the Recording (729)17.2.5Checking Your Recordings (731)17.2.6Location and Name of Your Recorded Samples (734)17.3Editing a Sample (735)17.3.1Using the Edit Page (735)17.3.2Audio Editing Functions (739)17.4Slicing a Sample (743)17.4.1Opening the Slice Page (743)17.4.2Adjusting the Slicing Settings (744)17.4.3Manually Adjusting Your Slices (746)17.4.4Applying the Slicing (750)17.5Mapping Samples to Zones (754)17.5.1Opening the Zone Page (754)17.5.2Zone Page Overview (755)17.5.3Selecting and Managing Zones in the Zone List (756)17.5.4Selecting and Editing Zones in the Map View (761)17.5.5Editing Zones in the Sample View (765)17.5.6Adjusting the Zone Settings (767)17.5.7Adding Samples to the Sample Map (770)18Appendix: Tips for Playing Live (772)18.1Preparations (772)18.1.1Focus on the Hardware (772)18.1.2Customize the Pads of the Hardware (772)18.1.3Check Your CPU Power Before Playing (772)18.1.4Name and Color Your Groups, Patterns, Sounds and Scenes (773)18.1.5Consider Using a Limiter on Your Master (773)18.1.6Hook Up Your Other Gear and Sync It with MIDI Clock (773)18.1.7Improvise (773)18.2Basic Techniques (773)18.2.1Use Mute and Solo (773)18.2.2Create Variations of Your Drum Patterns in the Step Sequencer (774)18.2.3Use Note Repeat (774)18.2.4Set Up Your Own Multi-effect Groups and Automate Them (774)18.3Special Tricks (774)18.3.1Changing Pattern Length for Variation (774)18.3.2Using Loops to Cycle Through Samples (775)18.3.3Load Long Audio Files and Play with the Start Point (775)19Troubleshooting (776)19.1Knowledge Base (776)19.2Technical Support (776)19.3Registration Support (777)19.4User Forum (777)20Glossary (778)Index (786)1Welcome to MASCHINEThank you for buying MASCHINE!MASCHINE is a groove production studio that implements the familiar working style of classi-cal groove boxes along with the advantages of a computer based system. MASCHINE is ideal for making music live, as well as in the studio. It’s the hands-on aspect of a dedicated instru-ment, the MASCHINE hardware controller, united with the advanced editing features of the MASCHINE software.Creating beats is often not very intuitive with a computer, but using the MASCHINE hardware controller to do it makes it easy and fun. You can tap in freely with the pads or use Note Re-peat to jam along. Alternatively, build your beats using the step sequencer just as in classic drum machines.Patterns can be intuitively combined and rearranged on the fly to form larger ideas. You can try out several different versions of a song without ever having to stop the music.Since you can integrate it into any sequencer that supports VST, AU, or AAX plug-ins, you can reap the benefits in almost any software setup, or use it as a stand-alone application. You can sample your own material, slice loops and rearrange them easily.However, MASCHINE is a lot more than an ordinary groovebox or sampler: it comes with an inspiring 7-gigabyte library, and a sophisticated, yet easy to use tag-based Browser to give you instant access to the sounds you are looking for.What’s more, MASCHINE provides lots of options for manipulating your sounds via internal ef-fects and other sound-shaping possibilities. You can also control external MIDI hardware and 3rd-party software with the MASCHINE hardware controller, while customizing the functions of the pads, knobs and buttons according to your needs utilizing the included Controller Editor application. We hope you enjoy this fantastic instrument as much as we do. Now let’s get go-ing!—The MASCHINE team at Native Instruments.MASCHINE Documentation1.1MASCHINE DocumentationNative Instruments provide many information sources regarding MASCHINE. The main docu-ments should be read in the following sequence:1.MASCHINE MIKRO Quick Start Guide: This animated online guide provides a practical ap-proach to help you learn the basic of MASCHINE MIKRO. The guide is available from theNative Instruments website: https:///maschine-mikro-quick-start/2.MASCHINE Manual (this document): The MASCHINE Manual provides you with a compre-hensive description of all MASCHINE software and hardware features.Additional documentation sources provide you with details on more specific topics:►Online Support Videos: You can find a number of support videos on The Official Native In-struments Support Channel under the following URL: https:///NIsupport-EN. We recommend that you follow along with these instructions while the respective ap-plication is running on your computer.Other Online Resources:If you are experiencing problems related to your Native Instruments product that the supplied documentation does not cover, there are several ways of getting help:▪Knowledge Base▪User Forum▪Technical Support▪Registration SupportYou will find more information on these subjects in the chapter Troubleshooting.Document Conventions1.2Document ConventionsThis section introduces you to the signage and text highlighting used in this manual. This man-ual uses particular formatting to point out special facts and to warn you of potential issues.The icons introducing these notes let you see what kind of information is to be expected:This document uses particular formatting to point out special facts and to warn you of poten-tial issues. The icons introducing the following notes let you see what kind of information canbe expected:Furthermore, the following formatting is used:▪Text appearing in (drop-down) menus (such as Open…, Save as… etc.) in the software andpaths to locations on your hard disk or other storage devices is printed in italics.▪Text appearing elsewhere (labels of buttons, controls, text next to checkboxes etc.) in thesoftware is printed in blue. Whenever you see this formatting applied, you will find thesame text appearing somewhere on the screen.▪Text appearing on the displays of the controller is printed in light grey. Whenever you seethis formatting applied, you will find the same text on a controller display.▪Text appearing on labels of the hardware controller is printed in orange. Whenever you seethis formatting applied, you will find the same text on the controller.▪Important names and concepts are printed in bold.▪References to keys on your computer’s keyboard you’ll find put in square brackets (e.g.,“Press [Shift] + [Enter]”).►Single instructions are introduced by this play button type arrow.→Results of actions are introduced by this smaller arrow.Naming ConventionThroughout the documentation we will refer to MASCHINE controller (or just controller) as the hardware controller and MASCHINE software as the software installed on your computer.The term “effect” will sometimes be abbreviated as “FX” when referring to elements in the MA-SCHINE software and hardware. These terms have the same meaning.Button Combinations and Shortcuts on Your ControllerMost instructions will use the “+” sign to indicate buttons (or buttons and pads) that must be pressed simultaneously, starting with the button indicated first. E.g., an instruction such as:“Press SHIFT + PLAY”means:1.Press and hold SHIFT.2.While holding SHIFT, press PLAY and release it.3.Release SHIFT.1.3New Features in MASCHINE2.8The following new features have been added to MASCHINE: Integration▪Browse on , create your own collections of loops and one-shots and send them directly to the MASCHINE browser.Improvements to the Browser▪Samples are now cataloged in separate Loops and One-shots tabs in the Browser.▪Previews of loops selected in the Browser will be played in sync with the current project.When a loop is selected with Prehear turned on, it will begin playing immediately in-sync with the project if transport is running. If a loop preview starts part-way through the loop, the loop will play once more for its full length to ensure you get to hear the entire loop once in context with your project.▪Filters and product selections will be remembered when switching between content types and Factory/User Libraries in the Browser.▪Browser content synchronization between multiple running instances. When running multi-ple instances of MASCHINE, either as Standalone and/or as a plug-in, updates to the Li-brary will be synced across the instances. For example, if you delete a sample from your User Library in one instance, the sample will no longer be present in the other instances.Similarly, if you save a preset in one instance, that preset will then be available in the oth-er instances, too.▪Edits made to samples in the Factory Libraries will be saved to the Standard User Directo-ry.For more information on these new features, refer to the following chapter ↑4, Browser. Improvements to the MASCHINE MIKRO MK3 Controller▪You can now set sample Start and End points using the controller. For more information refer to ↑17.3.1, Using the Edit Page.Improved Support for A-Series Keyboards▪When Browsing with A-Series keyboards, you can now jump quickly to the results list by holding SHIFT and pushing right on the 4D Encoder.▪When Browsing with A-Series keyboards, you can fast scroll through the Browser results list by holding SHIFT and twisting the 4D Encoder.▪Mute and Solo Sounds and Groups from A-Series keyboards. Sounds are muted in TRACK mode while Groups are muted in IDEAS.。
Android应用安全防护和逆向分析

7.1 dex文件格式 7.2构造dex文件 7.3解析数据结构 7.4解析代码 7.5本章小结
第8章 Android应用
1
安全防护的基
本策略
第9章
2
Android中常
用权限分析
3 第10章
Android中的 run-as命令
4
第11章 Android中的
allowBackup
属性
5 第12章
Android中的 签名机制
第20章静态方 1
式逆向应用
第21章动态调 2
试smali源码
3 第22章 IDA工
具调试so源码
4 第23章逆向加
固应用
5 第24章逆向应
用经典案例分 析
第25章 Android中常
见漏洞分析
第26章文件 加密病毒 Wannacry样 本分析
20.1 smali语法 20.2手动注入smali语句 20.3 ARM指令 20.4用IDA静态分析so文件 20.5案例分析 20.6本章小结
21.1动态调试步骤 21.2案例分析 21.3本章小结
22.1 IDA中的常用快捷键 22.2构造so案例 22.3逆向so文件 22.4用IDA解决反调试问题 22.5本章小结
23.1逆向加固应用的思路 23.2获取解密之后的dex文件 23.3分析解密之后的dex文件内容 23.4逆向方法 23.5逆向测试 23.6逆向加固应用的方法总结 23.7本章小结
第13章 Android应用
加固原理
第14章 Android中的 so加固原理
8.1混淆机制 8.2签名保护 8.3手动注册native方法 8.4反调试检测 8.5本章小结
9.1辅助功能权限 9.2设备管理权限 9.3通知栏管理权限 9.4 VPN开发权限 9.5本章小结
海思Android安全方案 使用指南

文档版本 发布日期
02 2014-03-12
版权所有 © 深圳市海思半导体有限公司 2014。保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本文档内容的部分或全部,并不得以任 何形式传播。
商标声明
、
、海思和其他海思商标均为深圳市海思半导体有限公司的商标。
2013-09-29
2013-07-22 2013-03-29 2013-01-22
版本 02
01
00B05
00B04
00B03 00B02 00B01
修订说明
修改 1.3 编译配置章节,增加 4.7 维修方案章节,删除第 四章,修改第一章安全启动的描述。
增加 1.4 小节编译配置说明和 2.0 章节升级说明,修改安 全 boot 开发说明和补充中国电信开发提示。
文档版本 02 (2014-03-12)
海思 Android 安全方案 使用指南
目录
目录
前 言................................................................................................................................................iii 1 安全启动.......................................................................................................................................1-1
表示能帮助您解决某个问题或节省您的时间。
您需要知道的 11 大 Android 秘密安全代码

您需要知道的11 大Android 秘密安全代码寻找最好的Android 密码和黑客?以下是增强智能手机安全性和隐私性的顶级USSD 代码。
Android 是当今世界上最流行的移动操作系统,为超过25 亿台设备提供支持。
而且,如果您使用Android 设备已有一段时间,您可能已经知道USSD 代码。
USSD 代码,也通俗地称为“秘密代码”,只是用于解锁智能手机中隐藏操作的代码。
非结构化补充服务数据(USSD) 是一种用户界面协议,可用于访问智能手机中的隐藏功能。
要运行任何Android 安全代码,您必须直接在拨号器中输入。
如果输入正确,代码将自动返回响应,或者您可能必须按拨号。
那么最常见的安卓安全码有哪些呢?“秘密代码”实际上是做什么的?1. *2767*3855#(擦除设备并重新安装固件)这是最有效的Android 安全代码之一,可用于快速擦除设备上的所有信息。
把它想象成恢复出厂设置——在你的拨号器中添加这个代码并运行它,它会有效地删除你手机中的所有数据,并将其擦除干净。
此代码在重新安装固件时更进一步,因此它与新的软件一样好。
注意:这是一个硬重置,并且会擦除所有内容,因此只能在绝对紧急情况下使用。
2. *#*#7780#*#*(恢复出厂设置)如果您不想运行硬重置,这是下一个最佳选择。
与恢复出厂设置类似,此代码将简单地从您的设备中删除所有应用程序数据以及任何应用程序。
然后,它会将您的设备恢复到出厂状态。
如果您不想花费额外的精力来重置和重新安装固件,而只想从您的设备中删除任何个人数据、应用程序和应用程序数据,那么这是最佳选择。
如果您要出售手机,这对您的隐私很有好处。
3. *#06#(查看设备的IMEI)这是另一个重要的代码,您可以使用它来检查设备的IMEI是否与包装盒上提到的相同。
大多数现代智能手机的背面都印有IMEI,但如果您想确定,可以使用此代码进行检查。
只需打开拨号器,添加代码,它就会返回IMEI。
安卓4.0,你知道多少

Android 4.0Android 4.0Android 系统4.0 命名为 Ice Cream Sandwich(简称ICS,冰淇淋三明治),是谷歌发布新一代操作系统。
Android4.0 拥有十大重点新特性。
集成谷歌电视和Chrome OS的智能停放,运行速度得到进一步提升。
2011年10月19日上午十点,谷歌与三星联手在中国香港举办发布会,公布有关Android 4.0系统信息。
目录系统概述系统命名最新消息十大特性全新的UI速度提升新特性机型曝光展开系统概述Android 4.0每当谷歌发布新一代操作系统之后,各家手机厂商升级上一代操作便会提上日程,同时也会有下一代操作系统的消息在互联网流出,这样的形式渐渐成为谷歌推广Android操作系统的一种惯用方式。
在Android2.3姜饼即将发布,Android3.0系统蜂巢被曝光,各家手机厂商都正在忙于将自己的Android手机升级至Android2.2操作系统的时候,国外媒体有消息指出Android下一代系统名称已经确定,爆料者为ARM公司的总裁Tudor Brown,该系列产品代号Ice Cream Sandwich,简称ICS,中文直译过来便是“冰激凌三明治。
谷歌方面已经非常明确的告诉大家:Android4.0是各手机与平板电脑系统融合的产品,并没有最低硬件要求,理论上来讲,现有的Android2.2/2.3均可升级Android4.0。
在硬件上不设限的同时,谷歌公布Android 4.0系统后,很快就将SDK公之于众。
Google同时公布了Android 3.0, 4.0源代码,最新版本为4.0.1。
Nexus机型上系统简介最新 Android 系统4.0 命名为 Ice Cream Sandwich(以下简称ICS,冰淇淋三明治),对于Google公司旗下最新一代Android Ice Cream Sandwich操作系统,相信很多玩家都已经有所耳闻了,而且恐怕相思之情已经难以慰藉。
2012datacenter密钥

2012年,美国国家安全局(NSA)的前雇员爱德华·斯诺登爆料,揭露了美国政府秘密监控计划Prism,其中泄露了一份对被监控数据中心的密钥。
这一事件引发了全球范围内的轰动,也引发了对数据安全和隐私保护的深刻思考。
在这篇文章中,我们将对2012datacenter密钥这一事件进行分析和解读。
一、事件背景1.斯诺登爆料2012年,爱德华·斯诺登向《卫报》和《华盛顿邮报》提供了大量的证据,揭露了美国政府秘密监控计划Prism。
Prism被揭露后,人们发现美国政府通过此计划可以对全球范围内的通讯数据进行监控和窃取。
这一事件引起了全球范围内的关注和愤怒,亦引发了对数据安全和隐私保护的广泛讨论。
二、事件影响1.全球关注2012年,Prism事件成为全球关注的焦点,并引发了关于政府监控行为和个人隐私保护权利的激烈讨论。
人们开始对政府的监控行为提出质疑,并加大了对数据安全和隐私保护的关注程度。
2.数据中心密钥泄露在Prism事件中,斯诺登泄露了一份对被监控数据中心的密钥,这一行为引发了对数据中心安全性的质疑。
数据中心一直被视为各个行业的重要基础设施,而其安全性更是备受重视。
密钥的泄露给数据中心的安全性带来了严重的挑战和危机。
三、事件启示1.数据中心安全性问题Prism事件中密钥的泄露凸显了数据中心的安全性问题。
数据中心的安全性一直备受关注,而此次事件的发生引发了对数据中心安全性的深刻思考。
数据中心在承载着各种重要信息和数据的也面临着来自外部的安全威胁和挑战。
数据中心安全性的加强势在必行。
2.数据隐私保护Prism事件引发了对数据隐私保护的讨论。
人们开始重新审视自己的个人隐私权利,并对政府和企业在数据收集和利用方面的行为进行了持续关注和监督。
数据隐私保护成为了社会的热点话题,也催生了相关法律法规的出台和完善。
四、对策建议1.加强数据中心安全管理对于数据中心来说,加强安全管理是至关重要的。
数据中心需要采取一系列有效的措施,包括加密技术、权限管理、入侵检测等,以保障数据的安全性和完整性。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Hotmobile2012Demo:L4Android Security Framework
on the Samsung Galaxy S2
Matthias Lange a Steffen Liebergeld a
Adam Lackorzynski b Alexander Warg b
Janis Danisevskis a Jan C.Nordholz a
a Security in Telecommunications,TU Berlin,Germany
b Chair of Operating Systems,TU Dresden,Germany
There is a recent trend to use privately owned mobile devices in corporate environments. This poses serious threats on the security of corporate data.In this demo we show how we applied an efficient sandboxing mechanism to the Android software stack.This allows us to run multiple instances of Android securely isolated side-by-side on one device.We implemented a prototype on the Samsung Galaxy S2.
I.Introduction
Virtualization,a technology well known from server and desktop computers,gained interest in the mobile handset market to employ multiple personalities on one device.As described by[1,2]virtualization also allows for high-assurance isolation between secure and insecure components which is required by emerg-ing applications such as micro payment via NFC or mobile banking.
As smartphones are heavily used in today’s busi-nesses they are usually provisioned by the corporate’s IT department to prevent unsolicited data revelation. This often makes these devices cumbersome to use and consequently many carry an additional private phone with them.Running both tasks on one device is highly desirable.
In this demo we show how we leveraged the fea-tures of the L4Android[3]security framework on the Samsung Galaxy S2to implement two virtual ma-chines running on the device.
II.System Architecture
Our system architecture is depicted in Figure1.The system is based on a modern third-generation micro-kernel.The system does not require hardware-assisted virtualization capabilities.Instead the Android ker-nel has been modified to run as an userspace appli-cation on the microkernel.We run two instances of L4Android where one is for private and the other for business purposes.Access to the graphics hardware and input devices is multiplexed by a secure GUI. The board support package provides a generic in-terface to device drivers.Android implements this generic interface in its hardware abstraction layer.
Figure1:Two instances of Android running in paral-lel on one device.
While still providing the same interface the board sup-port package can be changed without the need to adapt Android.
III.Demo Setup
We implemented our demo on the Samsung Galaxy S2 smartphone.It features a dual core ARM Cortex-A9 CPU with1GB of RAM.We ported the microkernel to the Exynos4SoC of the Galaxy S2and implemented the board support package(BSP).The BSP contains various drivers for devices such as display,input de-vices,real time clock and accelerometer.Our proto-type is capable of connecting to the mobile network
for sending and receiving SMS as well as data con-nectivity.
We run two instances of Android concurrently.The Android version is the latest Gingerbread release from the Android open source project.The L4Android ker-nel version is Linux3.1.
References
[1]G UDETH,K.,P IRRETTI,M.,H OEPER,K.,AND
B USKEY,R.Delivering secure applications on
commercial mobile devices:the case for bare metal hypervisors.In Proceedings of the1st ACM workshop on Security and privacy in smartphones and mobile devices(2011),SPSM’11,ACM. [2]L ANGE,M.,L IEBERGELD,S.,L ACKORZYN-
SKI, A.,W ARG, A.,AND P ETER,M.
L4Android:A Generic Operating System Frame-work for Secure Smartphones.In Proceedings of the1st ACM workshop on Security and privacy in smartphones and mobile devices(2011),SPSM ’11,ACM.
[3]L ANGE,M.,L IEBERGELD,S.L4Android:An-
droid on top of L4.http://www.l4android.o rg,January2012.。
