路由器-IPSec-Over-GRE典型配置
GRE OVER IPSEC配置(第五组3月25日)

GRE over IPSEC配置一、技术简介GRE over IPSec的外层ip就是公网的路由IP,GRE over IPSec,是将整个已经封装过的GRE数据包进行加密。
由于IPSec不支持对多播和广播数据包的加密,这样的话,使用IPSec的隧道中,动态路由协议等依靠多播和广播的协议就不能进行正常通告,所以,这时候要配合GRE隧道,GRE隧道会将多播和广播数据包封装到单播包中,再经过IPSec 加密。
此外由于GRE建立的是简单的,不进行加密的VPN隧道,他通过在物理链路中使用ip地址和路由穿越普通网络。
所以很常见的方法就是使用IPSec对GRE 进行加密,提供数据安全保证。
二、设备简介在总部与两个分部的出口路由器之间实施GRE over IPSec技术。
三、基本配置总部配置:Router#conf tRouter(config)#no ip do loRouter(config)#line con 0Router(config-line)#logg syRouter(config-line)#exec-t 0 0Router(config)#ho BJ-R-001BJ-R-001(config)#int lo 0BJ-R-001(config-if)#ip add 192.168.1.1 255.255.255.0 配置loopback口地址BJ-R-001(config-if)#int s0/0BJ-R-001(config-if)#ip add 12.12.12.1 255.255.255.0 配置接口地址BJ-R-001(config-if)#no shBJ-R-001(config-if)#exitBJ-R-001(config)#ip route 0.0.0.0 0.0.0.0 12.12.12.2 配置静态路由BJ-R-001(config)#crypto isakmp policy 10 定义isakmp策略BJ-R-001(config-isakmp)#hash md5BJ-R-001(config-isakmp)#encryption desBJ-R-001(config-isakmp)#group 2BJ-R-001(config-isakmp)#authentication pre-shareBJ-R-001(config-isakmp)#exitBJ-R-001(config)#crypto isakmp key 0 cisco address 23.23.23.3BJ-R-001(config)#crypto isakmp key 0 cisco address 24.24.24.4BJ-R-001(config)#crypto ipsec transform-set beijing esp-des esp-md5-hmac 设置转换集BJ-R-001(cfg-crypto-trans)#exitBJ-R-001(config)#crypto ipsec profile cisco 定义配置文件BJ-R-001(ipsec-profile)#set transform-set beijingBJ-R-001(ipsec-profile)#exitBJ-R-001(config)#int tunnel 0 配置tunnelBJ-R-001(config-if)#ip add 172.16.1.1 255.255.255.0BJ-R-001(config-if)#tunnel source s0/0BJ-R-001(config-if)#tunnel destination 23.23.23.3BJ-R-001(config-if)#tunnel mode ipsec ipv4BJ-R-001(config-if)#tunnel protection ipsec profile ciscoBJ-R-001(config-if)#no shBJ-R-001(config)#int tunnel 1BJ-R-001(config-if)#ip add 172.16.2.1 255.255.255.0 BJ-R-001(config-if)#tunnel source s0/0BJ-R-001(config-if)#tunnel destination 24.24.24.4BJ-R-001(config-if)#tunnel mode ipsec ipv4BJ-R-001(config-if)#tunnel protection ipsec profile cisco BJ-R-001(config-if)#no shBJ-R-001(config-if)#exitBJ-R-001(config)#router ospf 1BJ-R-001(config-router)#net 172.16.1.1 0.0.0.0 a 0BJ-R-001(config-router)#net 192.168.1.1 0.0.0.0 a 0BJ-R-001(config-router)#net 172.16.2.1 0.0.0.0 a 0BJ-R-001(config-router)#exit分部配置:Router>enRouter#conf tRouter(config)#no ip do loRouter(config)#line con 0Router(config-line)#logg synRouter(config-line)#exec-t 0 0Router(config-line)#exitRouter(config)#ho DL-R-001DL-R-001(config)#int s0/1DL-R-001(config-if)#ip add 23.23.23.3 255.255.255.0 DL-R-001(config-if)#no shDL-R-001(config-if)#ip add 192.168.2.1 255.255.255.0 DL-R-001(config-if)#exitDL-R-001(config)#ip route 0.0.0.0 0.0.0.0 23.23.23.2 DL-R-001(config)#crypto isakmp policy 10DL-R-001(config-isakmp)#hash md5DL-R-001(config-isakmp)#encryption desDL-R-001(config-isakmp)#group 2DL-R-001(config-isakmp)#authentication pre-shareDL-R-001(config-isakmp)#exitDL-R-001(config)#crypto isakmp key 0 cisco address 12.12.12.1DL-R-001(config)#crypto ipsec transform-set dalian esp-des esp-md5-hmac DL-R-001(cfg-crypto-trans)#exitDL-R-001(config)#crypto ipsec profile ciscoDL-R-001(ipsec-profile)#set transform-set dalianDL-R-001(ipsec-profile)#exitDL-R-001(config)#int tunnel 0DL-R-001(config-if)#ip add 172.16.1.2 255.255.255.0DL-R-001(config-if)#no shDL-R-001(config-if)#tunnel source s0/1DL-R-001(config-if)#tunnel destination 12.12.12.1DL-R-001(config-if)#tunnel mode ipsec ipv4DL-R-001(config-if)#tunnel protection ipsec profile ciscoDL-R-001(config-if)#exitDL-R-001(config)#router ospf 1DL-R-001(config-router)#net 192.168.2.1 0.0.0.0 a 0DL-R-001(config-router)#net 172.16.1.2 0.0.0.0 a 0DL-R-001(config-router)#exitRouter>enRouter#conf tRouter(config)#no ip do loRouter(config)#line con 0Router(config-line)#logg synRouter(config-line)#exec-t 0 0Router(config-line)#exitRouter(config)#ho KS-R-001KS-R-001(config-if)#ip add 192.168.3.1 255.255.255.0KS-R-001(config-if)#int s0/2KS-R-001(config-if)#ip add 24.24.24.4 255.255.255.0KS-R-001(config-if)#no shKS-R-001(config-if)#exitKS-R-001(config)#ip route 0.0.0.0 0.0.0.0 24.24.24.2KS-R-001(config)#crypto isakmp policy 10KS-R-001(config-isakmp)#hash md5KS-R-001(config-isakmp)#encryption desKS-R-001(config-isakmp)#group 2KS-R-001(config-isakmp)#authentication pre-shareKS-R-001(config-isakmp)#exitKS-R-001(config)#crypto isakmp key 0 cisco address 12.12.12.1KS-R-001(config)#crypto ipsec transform-set kunshan esp-des esp-md5-hmac KS-R-001(cfg-crypto-trans)#exitKS-R-001(config)#cry ipsec profile ciscoKS-R-001(ipsec-profile)#set transform-set kunshanKS-R-001(ipsec-profile)#exitKS-R-001(config)#int tunnel 0KS-R-001(config-if)#ip add 172.16.2.2 255.255.255.0KS-R-001(config-if)#no shKS-R-001(config-if)#tunnel source s0/2KS-R-001(config-if)#tunnel destination 12.12.12.1KS-R-001(config-if)#tunnel mode ipsec ipv4KS-R-001(config-if)#tunnel protection ipsec profile ciscoKS-R-001(config-if)#exitKS-R-001(config)#router ospf 1KS-R-001(config-router)#net 172.16.2.2 0.0.0.0 a 0 KS-R-001(config-router)#net 192.168.3.1 0.0.0.0 a 0 KS-R-001(config-router)#exit四、验证配置。
H3C MSR系列路由器IPsec典型配置举例(V7)

7 相关资料1 简介本文档介绍IPsec的典型配置举例。
2 配置前提本文档适用于使用Comware V7软件版本的MSR系列路由器,如果使用过程中与产品实际情况有差异,请参考相关产品手册,或以设备实际情况为准。
本文档中的配置均是在实验室环境下进行的配置和验证,配置前设备的所有参数均采用出厂时的缺省配置。
如果您已经对设备进行了配置,为了保证配置效果,请确认现有配置和以下举例中的配置不冲突。
本文档假设您已了解IPsec特性。
3 使用iNode客户端基于证书认证的L2TP over IPsec功能配置举例3.1 组网需求如图1所示,PPP用户Host与Device建立L2TP隧道,Windows server 2003作为CA服务器,要求:•通过L2TP隧道访问Corporate network。
•用IPsec对L2TP隧道进行数据加密。
•采用RSA证书认证方式建立IPsec隧道。
图1 基于证书认证的L2TP over IPsec配置组网图3.2 配置思路由于使用证书认证方式建立IPsec隧道,所以需要在ike profile中配置local-identity 为dn,指定从本端证书中的主题字段取得本端身份。
3.3 使用版本本举例是在R0106版本上进行配置和验证的。
3.4 配置步骤3.4.1 Device的配置(1) 配置各接口IP地址# 配置接口GigabitEthernet2/0/1的IP地址。
<Device> system-view[Device] interface gigabitethernet 2/0/1[Device-GigabitEthernet2/0/1] ip address 192.168.100.50 24[Device-GigabitEthernet2/0/1] quit# 配置接口GigabitEthernet2/0/2的IP地址。
[Device] interface gigabitethernet 2/0/2[Device-GigabitEthernet2/0/2] ip address 102.168.1.11 24[Device-GigabitEthernet2/0/2] quit# 配置接口GigabitEthernet2/0/3的IP地址。
H3C v7版本 ipsec over gre配置指导
Ipsec over gre配置RT1和RT3用环回口来模拟私网上的接口。
它们的封装方式是先封装ipsec,然后在进行gre的封装,所以在ipsec的ACL中要匹配的事两端私网的地址。
报文的封装格式:指定Tunnel口源接口地址[H3C-Tunnel0]source 10.1.1.1指定Tunnel口目的端地址[H3C-Tunnel0]destination 20.1.1.2[H3C-Tunnel0] quit创建访问控制列表[H3C]acl advanced 3000[H3C-acl-ipv4-adv-3000]rule 0 permit ip source 192.168.1.1 0.0.0.0 destination 1 92.168.2.1 0.0.0.0[H3C-acl-ipv4-adv-3000]quit创建ipsec安全提议tran1[H3C]ipsec transform-set tran1指定安全协议的工作模式为隧道模式[H3C]ike profile profile1绑定ike keychain[H3C-ike-profile-profile1]keychain ike1配置本地封装的IP地址[H3C-ike-profile-profile1]local-identity address 100.1.1.1配置对端封装的IP地址[H3C-ike-profile-profile1]match remote identity address 100.1.1.2 24 [H3C-ike-profile-profile1]quit创建一条ike协商方式的ipsec安全策略,序列号为1,名字为policy1 [H3C]ipsec policy policy1 1 isakmp指定引用ACL3000[H3C-ipsec-policy-isakmp-policy1-1]security acl 3000[H3C-rip-1]network 10.1.1.1RT2的主要配置:<H3C>system-view[H3C]interface GigabitEthernet 0/0[H3C-GigabitEthernet0/0]ip address 10.1.1.2 24[H3C-GigabitEthernet0/0]quit[H3C]interface GigabitEthernet 0/1[H3C-GigabitEthernet0/1] ip address 20.1.1.1 24 [H3C-GigabitEthernet0/1]quit配置rip路由协议[H3C]rip[H3C-rip-1]version 2[H3C-rip-1]undo summary[H3C-rip-1]network 10.1.1.2指定Tunnel口源接口地址[H3C-Tunnel0]source 20.1.1.2指定Tunnel口目的端地址[H3C-Tunnel0]destination 10.1.1.1[H3C-Tunnel0] quit创建访问控制列表[H3C]acl advanced 3000[H3C-acl-ipv4-adv-3000]rule 0 permit ip source 192.168.2.1 0.0.0.0 destination 192.168.1.1 0.0.0.0[H3C-acl-ipv4-adv-3000]quit创建ipsec安全提议tran1[H3C]ipsec transform-set tran1指定安全协议的工作模式为隧道模式[H3C]ike profile profile1绑定ike keychain[H3C-ike-profile-profile1]keychain ike1配置本地封装的IP地址[H3C-ike-profile-profile1]local-identity address 100.1.1.2配置对端封装的IP地址[H3C-ike-profile-profile1]match remote identity address 100.1.1.1 24[H3C-ike-profile-profile1]quit创建一条ike协商方式的ipsec安全策略,序列号为1,名字为policy1[H3C]ipsec policy policy1 1 isakmp指定引用ACL3000[H3C-ipsec-policy-isakmp-policy1-1]security acl 3000[H3C-rip-1]network 20.1.1.2测试从RT1的环回口来ping RT3的环回口[H3C]ping -a 192.168.1.1 192.168.2.1Ping 192.168.2.1 (192.168.2.1) from 192.168.1.1: 56 data bytes, press CTRL_C to breakRequest time out56 bytes from 192.168.2.1: icmp_seq=1 ttl=255 time=2.000 ms56 bytes from 192.168.2.1: icmp_seq=2 ttl=255 time=2.000 ms 56 bytes from 192.168.2.1: icmp_seq=3 ttl=255 time=2.000 ms 56 bytes from 192.168.2.1: icmp_seq=4 ttl=255 time=1.000 ms 说明VPN建立成功。
IPsec over GRE 和GRE over IPsec

IPsec over GRE 和GRE over IPsec比较和区别与配置GRE over IPsec & IPsec over GREI PSec -Over-GRE是先ipsec后gre,这种我没用过。
GRE -Over-IPSec 是先gre后ipsec,也就是说ipsec是最后的承载方式。
一般常用的就是这种,解决了ipsec不支持多播的问题。
另外在mtu上也有一些相关,gre是先分段后封装,而ipsec则是先封装再分段。
个人理解。
IPsec over GRE 和GRE over IPsec在配置上的区别:GRE over IPsec IPsec over GREACL定义:GRE数据流内网数据流IKE Peer中指定的remote-address 对方公网地址对方GRE Tunnel 地址应用端口:公网出口 GRE Tunnel上GRE over IPSEC(传输模式)IPSEC封装GRE好处:可以利用GRE封装组播或广播了以及非IP流量,因为如果不使用GRE的话,IPSEC 是传不了组播或广播IP流量的IPSEC over GRE(里外)(tunel模式)IPSEC over GRE:GRE在IPSEC外面,由GRE来封装IPSEC注意!!!IPSEC over GRE的时候,路由协议流量是明文的注意!!!当指的peer是对等体物理接口地址的时候不是IPSEC over GRE,只有当peer是对等体的lookback是才是真正的IPSEC over GREipsec over gre配置:crypto isakmp policy 10authentication pre-sharecrypto isakmp key cisco address 10.1.1.2!crypto ipsec transform-set myset esp-des esp-sha-hmac!crypto map mymap 10 ipsec-isakmpset peer 10.1.1.2set transform-set mysetmatch address 102!interface Serial0ip address 10.1.1.1 255.255.255.0clockrate 64000crypto map mymap!ip route 0.0.0.0 0.0.0.0 20.1.1.2ip route 40.1.1.0 255.255.255.0 Tunnel0!access-list 102 permit ip 1.1.1.0 0.0.0.255 1.1.2.0 0.0.0.255!interface Tunnel0ip address 100.1.1.1 255.255.255.0tunnel source Serial0tunnel destination 30.1.1.2crypto map mymapGRE OVER IPSEC的配置拓朴结构:R1 F0/0(172.16.1.1/24)->R2 F0/0(172.16.1.2/24) 模拟外网连接R1 F1/0(192.168.1.1/24)模拟内网1R2 F1/0(192.168.2.1/24)模拟内网2R1://定义IKE策略,用于阶段1的SA建立,系统会按对端协商的参数去查找我们定义的policy,直到找到一个各项参数都匹配的policy并使用之,如果没找到会在阶段1失败crypto isakmp policy 10hash md5authentication pre-sharelifetime 3600crypto isakmp key qhtest address 172.16.1.2!//这里定义阶段2所使用的SA,其所使用的加密密钥为随机,并使用阶段1所建立的SA来交换crypto ipsec transform-set myset esp-3des!//定义密码映射crypto map qh 10 ipsec-isakmpset peer 172.16.1.2set transform-set mysetmatch address 102//这里注意引用了访问列表102,这里对gre包进行加密,而不是如上一篇所做的那样是对内网地址段,实际上是去往内网2的数据包先被封装到GRE包里,再从外网接口出去,并被IPSET加密!//下面在接口上应用密码映射interface FastEthernet0/0ip address 172.16.1.1 255.255.255.0duplex fullcrypto map qh!//这里定义GRE隧道接口interface Tunnel0ip address 192.168.100.1 255.255.255.0tunnel source 172.16.1.1tunnel destination 172.16.1.2//由于GRE可以传路由协议,所有我们在隧道接口上启用了路由协议router ospf 100log-adjacency-changesredistribute connected subnetsnetwork 192.168.100.0 0.0.0.255 area 0//这里的访问列表我们定义了针对GRE的包施行IPSEC加密access-list 102 permit gre host 172.16.1.1 host 172.16.1.2R2:crypto isakmp policy 10hash md5authentication pre-sharelifetime 3600crypto isakmp key qhtest address 172.16.1.1!!crypto ipsec transform-set myset esp-3des!crypto map qh 10 ipsec-isakmpset peer 172.16.1.1set transform-set mysetmatch address 102!interface Tunnel0ip address 192.168.100.2 255.255.255.0tunnel source 172.16.1.2tunnel destination 172.16.1.1!interface FastEthernet0/0ip address 172.16.1.2 255.255.255.0duplex fullcrypto map qh!router ospf 100log-adjacency-changesredistribute connected subnetsnetwork 192.168.100.0 0.0.0.255 area 0!access-list 102 permit gre host 172.16.1.2 host 172.16.1.1IPSEC Over GRE与GRE Over IPSEC的区别和好处到底是IPSEC Over GRE好呢,还是GRE Over IPSEC好?以前一直是出于一个模糊的状态,能通就行了么。
工程应用之方案二 IPSEC over GRE
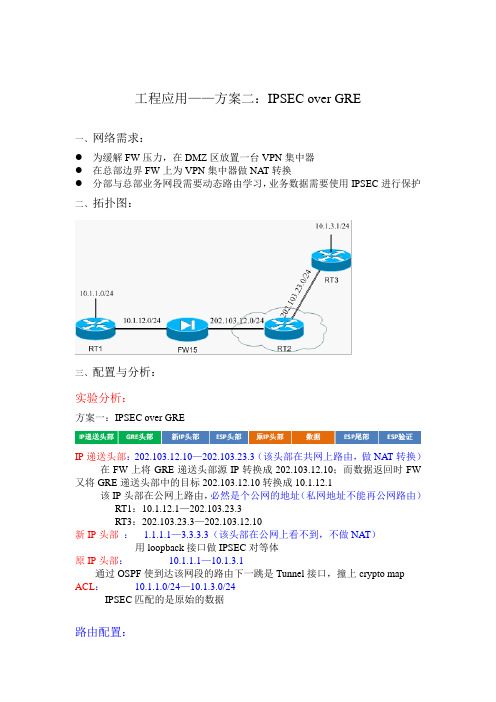
工程应用——方案二:IPSEC over GRE一、网络需求:●为缓解FW压力,在DMZ区放置一台VPN集中器●在总部边界FW上为VPN集中器做NAT转换●分部与总部业务网段需要动态路由学习,业务数据需要使用IPSEC进行保护二、拓扑图:三、配置与分析:实验分析:方案一:IPSEC over GREIP递送头部:202.103.12.10—202.103.23.3(该头部在共网上路由,做NAT转换)在FW上将GRE递送头部源IP转换成202.103.12.10;而数据返回时FW 又将GRE递送头部中的目标202.103.12.10转换成10.1.12.1该IP头部在公网上路由,必然是个公网的地址(私网地址不能再公网路由)RT1:10.1.12.1—202.103.23.3RT3:202.103.23.3—202.103.12.10新IP头部: 1.1.1.1—3.3.3.3(该头部在公网上看不到,不做NAT)用loopback接口做IPSEC对等体原IP头部:10.1.1.1—10.1.3.1通过OSPF使到达该网段的路由下一跳是Tunnel接口,撞上crypto map ACL:10.1.1.0/24—10.1.3.0/24IPSEC匹配的是原始的数据路由配置:RT1(config)#ip route 0.0.0.0 0.0.0.0 10.1.12.2RT3(config)#ip route 0.0.0.0 0.0.0.0 202.103.23.2FW(config)# route outside 0.0.0.0 0.0.0.0 202.103.12.2 1FW配置NAT,放行GRE流量:FW(config)#access-list 100 permit gre host 202.103.23.3 host 202.103.12.10 GRE流量access-group 100 in interface outsideStatic (inside,outside) 202.103.12.10 10.1.12.1 netmask 255.255.255.255GRE配置:RT1(config)#interface Tunnel0ip address 10.1.13.1 255.255.255.0tunnel source Ethernet1/0 RT1GER源,10.1.12.1tunnel destination 202.103.23.3 RT1GRE目标,公网地址RT3(config)#interface Tunnel0ip address 10.1.13.3 255.255.255.0tunnel source Serial0/0tunnel destination 202.103.12.10 RT3GRE目标,对方NAT转换后的IPRT1#ping 10.1.3.1 source 10.1.1.1 测试GRE隧道是否建立成功Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 10.1.3.1, timeout is 2 seconds:Packet sent with a source address of 10.1.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 28/63/152 msOSPF配置:●公布Tunnel接口网段,通过Tunnel接口建立OSPF邻居●公布业务网段,通过OSPF实现到达对端业务网段的下一跳是Tunnel接口,以便撞上crypto map●公布IPSEC对等体网段,下一跳是Tunnel接口,以便进行GRE封装RT1(config)#router ospf 1router-id 1.1.1.1network 1.1.1.0 0.0.0.255 area 0 IPSEC对等体network 10.1.1.0 0.0.0.255 area 0 业务网段network 10.1.13.0 0.0.0.255 area 0 Tunnel接口RT3(config)#router ospf 1router-id 3.3.3.3network 3.3.3.0 0.0.0.255 area 0network 10.1.3.0 0.0.0.255 area 0network 10.1.13.0 0.0.0.255 area 0RT1#show ip route1.0.0.0/24 is subnetted, 1 subnetsC 1.1.1.0 is directly connected, Loopback13.0.0.0/32 is subnetted, 1 subnetsO 3.3.3.3 [110/11112] via 10.1.13.3, 01:09:55, Tunnel0 IPSEC对等体路由10.0.0.0/8 is variably subnetted, 4 subnets, 2 masksC 10.1.13.0/24 is directly connected, Tunnel0C 10.1.12.0/24 is directly connected, Ethernet1/0O 10.1.3.1/32 [110/11112] via 10.1.13.3, 01:09:55, Tunnel0 业务网段路由C 10.1.1.0/24 is directly connected, Loopback0S* 0.0.0.0/0 [1/0] via 10.1.12.2RT3#show ip routeC 202.103.23.0/24 is directly connected, Serial0/01.0.0.0/32 is subnetted, 1 subnetsO 1.1.1.1 [110/11112] via 10.1.13.1, 01:10:26, Tunnel03.0.0.0/24 is subnetted, 1 subnetsC 3.3.3.0 is directly connected, Loopback110.0.0.0/8 is variably subnetted, 3 subnets, 2 masksC 10.1.13.0/24 is directly connected, Tunnel0C 10.1.3.0/24 is directly connected, Loopback0O 10.1.1.1/32 [110/11112] via 10.1.13.1, 01:10:26, Tunnel0S* 0.0.0.0/0 [1/0] via 202.103.23.2RT1#ping 3.3.3.3 source 1.1.1.1 测试IPSEC对等体路由可达Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:Packet sent with a source address of 1.1.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 24/61/100 msIPSEC配置RT1(config)#crypto isakmp policy 10 IKE阶段传输集encryption deshash md5authentication pre-sharegroup 2crypto isakmp key 6 allen address 3.3.3.3 共享密钥crypto ipsec transform-set laodong esp-des esp-md5-hmac IPSEC阶段传输集access-list 100 permit ip host 10.1.1.1 host 10.1.3.1 IPSEC流量crypto map bluefox local-address Loopback1 loopback接口作为IPSEC源crypto map bluefox 10 ipsec-isakmpset peer 3.3.3.3 对等体IP为对端的loopback接口set transform-set laodongmatch address 100interface Tunnel0crypto map bluefox crypto map应用于Tunnel接口RT3(config)#crypto isakmp policy 10encryption deshash md5authentication pre-sharegroup 2crypto isakmp key 6 allen address 1.1.1.1crypto ipsec transform-set laodong esp-des esp-md5-hmacaccess-list 100 permit ip host 10.1.3.1 host 10.1.1.1crypto map bluefox local-address Loopback1crypto map bluefox 10 ipsec-isakmpset peer 1.1.1.1set transform-set laodongmatch address 100interface Tunnel0crypto map bluefox测试:RT1#ping 10.1.3.1 source 10.1.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 10.1.3.1, timeout is 2 seconds:Packet sent with a source address of 10.1.1.1.!!!!Success rate is 80 percent (4/5), round-trip min/avg/max = 68/93/128 msFW# show xlate1 in use,2 most usedPAT Global 202.103.12.10(1024) Local 10.1.12.1(4500)RT1#show crypto isakmp sadst src state conn-id slot status3.3.3.3 1.1.1.1 QM_IDLE 1 0 ACTIVE RT1#show crypto ipsec sainterface: Tunnel0Crypto map tag: bluefox, local addr 1.1.1.1protected vrf: (none)local ident (addr/mask/prot/port): (10.1.1.1/255.255.255.255/0/0)remote ident (addr/mask/prot/port): (10.1.3.1/255.255.255.255/0/0)current_peer 3.3.3.3 port 500PERMIT, flags={origin_is_acl,}#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 1, #recv errors 0local crypto endpt.: 1.1.1.1, remote crypto endpt.: 3.3.3.3path mtu 1476, ip mtu 1476, ip mtu idb Tunnel0current outbound spi: 0x2043C509(541312265)inbound esp sas:spi: 0x1B1667DD(454453213)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }conn id: 2002, flow_id: SW:2, crypto map: bluefoxsa timing: remaining key lifetime (k/sec): (4417317/2393)IV size: 8 bytesreplay detection support: YStatus: ACTIVEoutbound esp sas:spi: 0x2043C509(541312265)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }conn id: 2001, flow_id: SW:1, crypto map: bluefoxsa timing: remaining key lifetime (k/sec): (4417317/2392)IV size: 8 bytesreplay detection support: YStatus: ACTIVE四、总结:由数据包的封装结构分析,IPSEC对等体,GRE源目,IPSEC流量是什么CRYPTO-6-IKMP_MODE_FAILURE: Processing of Quick mode failed with peer at 3.3.3.3快速模式协商失败可能的原因:set peer 对等体错误已经建立数据连接后再次建立,SPI可能错误。
思科GRE over IPSec VPN配置

一、隧道技术主机配置:1.vpc1set pcname VPC1 //更改主机名ip 10.1.1.1/24 10.1.1.100 //配置主机IP地址和网关2.vpc2set pcname VPC2 //更改主机名ip 20.1.1.1/24 20.1.1.100 //配置主机IP地址和网关配置路由协议(RIP):1.R1:/*基础配置*/R1(config )#int e0/0R1(config-if)#ip add 10.1.1.100 255.255.255.0R1(config-if)#no shutdownR1(config-if)#int e0/1R1(config-if)#ip add 12.1.1.1 255.255.255.0R1(config-if)#no shutdown/*路由协议配置*/R1(config)#router ripR1(config-router)#ver 2//版本2R1(config-router)#no au//关闭自动汇总R1(config-router)#net 12.0.0.0//宣告网段2.R2:/*基础配置*/R2(config )#int e0/0R2(config-if)#ip add 12.1.1.2 255.255.255.0R2(config-if)#no shutdownR2(config-if)#int e0/1R2(config-if)#ip add 23.1.1.2 255.255.255.0R2(config-if)#no shutdown/*路由协议配置*/R2(config)#router ripR2(config-router)#ver 2R2(config-router)#no auR2(config-router)#net 12.0.0.0R2(config-router)#net 23.0.0.03.R3:/*基础配置*/R3(config )#int e0/0R3(config-if)#ip add 23.1.1.3 255.255.255.0R3(config-if)#no shutdownR3(config-if)#int e0/1R3(config-if)#ip add 20.1.1.100 255.255.255.0R3(config-if)#no shutdown/*路由协议配置*/R3(config)#router ripR3(config-router)#ver 2R3(config-router)#no auR3(config-router)#net 23.0.0.0配置隧道:1.R1:R1(config)#interface tun 100//创建隧道R1(config-if)#ip add 13.1.1.1 255.255.255.0R1(config-if)#no shutdownR1(config-if)#tunnel source 12.1.1.1//指定隧道源地址R1(config-if)#tunnel destination 23.1.1.3//指定隧道目的地址R1(config)#ip route 0.0.0.0 0.0.0.0 13.1.1.3 //配置默认路由指向隧道2.R3:R3(config)#interface tun 1R3(config-if)#ip add 13.1.1.3 255.255.255.0R3(config-if)#no shutdownR3(config-if)#tunnel source 23.1.1.3R3(config-if)#tunnel destination 12.1.1.1R3(config)#ip route 0.0.0.0 0.0.0.0 13.1.1.1OSPF:Router ospf 1Net 13.1.1.1 0.0.0.0 area 0Net 10.1.1.100 0.0.0.0 ar0Net 20.1.1.100 0.0.0.0 ar0Router ospf 1Net 13.1.1.3 0.0.0.0 area 0Net 30.1.1.100 0.0.0.0 area0Net 40.1.1.100 0.0.0.0 area0第二大阶段:使用VPN保护隧道1.配置VPN,保护隧道:1)第一阶段配置:1 IPSec VPN的第一阶段策略R1(config)#crypto isakmp policy 10//创建策略集,优先级为10R1(config-isakmp)#encryption 3des//定义加密算法为3desR1(config-isakmp)#hash md5//定义HASH算法为MD5R1(config-isakmp)#authentication pre-share//认证方式选择预共享密钥R1(config-isakmp)#group 2//非对称加密算法长度,2表示1024的长度R1(config-isakmp)#exitR1(config)#crypto isakmp key cisco add 0.0.0.02)第二阶段配置:R1(config)#crypto ipsec transform-set 123 esp-3des esp-md5-hmacR1(cfg-crypto-trans)#mode transport //使用传输模式来保护隧道R1(config)#crypto ipsec profile vpn//创建第二阶段配置文件R1(ipsec-profile)#set transform-set 123//设置转换机R1(config-if)#int tunnel 1R1(config-if)#tunnel protection ipsec profile vpn//使用配置文件对隧道进行加密查看加密传输次数R1#show crypto engine connections active动态多点VPN:1、基础环境搭建1.)配置所有设备的IP地址2.)配置RIP协议R1-R2-R3-R4验证:R1 ping 23.1.1.3 和24.1.1.4 均可以通R4 ping 23.1.1.3 可以通2、MGRE的配置方式1.依然是隧道的配置R1:Int tunnel 123Ip add 123.1.1.1 255.255.255.0No shutTunnel source 12.1.1.1Tunnel mode gre multipointIp nhrp network-id 123R3:Int tunnel 123Ip add 123.1.1.3 255.255.255.0No shutTunnel source 23.1.1.3Tunnel mode gre multipointIp nhrp network-id 123R4:Int tunnel 123Ip add 123.1.1.4 255.255.255.0No shutTunnel source 24.1.1.4Tunnel mode gre multipointIp nhrp network-id 1233、NHRP(下一条解析协议)的配置中心点站配置R1:Ip nhrp map multicast dynamic //会把物理接口地址和隧道地址进行动态映射分支站点配置://物理借口地址为真实地址,隧道接口地址为虚拟地址虚真真虚R3:Ip nhrp map 123.1.1.1 12.1.1.1 //我将123.1.1.1映射到12.1.1.1Ip nhrp map multicast 12.1.1.1 //我们会从12.1.1.。
ipsec over gre原理及配置

ipsec over gre步骤:1.创建tunnel口,配置ip,source,destination2.默认路由指向出口下一跳3.使用路由协议,把路由ping通(环回口,要加密的数据的ip)4.建立vpn,并在tunnel口上绑定map废话不多说,直接上配置:R1配置:hostname R1!crypto isakmp policy 10hash md5authentication pre-sharegroup 2crypto isakmp key zhang address 3.3.3.3!!crypto ipsec transform-set mytrans esp-3des esp-md5-hmac !crypto map mymap local-address Loopback0crypto map mymap 10 ipsec-isakmpset peer 3.3.3.3set transform-set mytransmatch address VPN!interface Tunnel0ip address 172.16.1.1 255.255.255.0tunnel source FastEthernet0/0tunnel destination 23.1.1.2tunnel key 123crypto map mymap!interface Loopback0ip address 1.1.1.1 255.255.255.0!interface Loopback10ip address 192.168.1.1 255.255.255.0!interface FastEthernet0/0ip address 12.1.1.1 255.255.255.0duplex autospeed auto!router ospf 1router-id 1.1.1.1log-adjacency-changesnetwork 1.1.1.0 0.0.0.255 area 0network 172.16.1.0 0.0.0.255 area 0network 192.168.1.0 0.0.0.255 area 0neighbor 3.3.3.3!no ip http serverno ip http secure-serverip route 0.0.0.0 0.0.0.0 12.1.1.2!ip access-list extended VPNpermit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255 !endR2配置:hostname R2interface FastEthernet0/0ip address 12.1.1.2 255.255.255.0 duplex autospeed auto!interface FastEthernet1/0ip address 23.1.1.1 255.255.255.0 duplex autospeed auto!endR3配置:hostname R3!crypto isakmp policy 10hash md5authentication pre-sharegroup 2crypto isakmp key zhang address 1.1.1.1!crypto ipsec transform-set mytrans esp-3des esp-md5-hmac !crypto map mymap local-address Loopback0crypto map mymap 10 ipsec-isakmpset peer 1.1.1.1set transform-set mytransmatch address VPN!interface Tunnel0ip address 172.16.1.2 255.255.255.0tunnel source FastEthernet0/0tunnel destination 12.1.1.1tunnel key 123crypto map mymap!interface Loopback0ip address 3.3.3.3 255.255.255.0!interface Loopback10ip address 192.168.3.1 255.255.255.0!interface FastEthernet0/0ip address 23.1.1.2 255.255.255.0duplex autospeed auto!router ospf 1router-id 3.3.3.3log-adjacency-changesnetwork 3.3.3.0 0.0.0.255 area 0network 172.16.1.0 0.0.0.255 area 0network 192.168.3.0 0.0.0.255 area 0neighbor 1.1.1.1!ip route 0.0.0.0 0.0.0.0 23.1.1.1!ip access-list extended VPNpermit ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255 !end实验效果:IPSec Over GRE 路由原理下图是R1的路由表当我们ping 192.168.3.1 source loopback 10,其实就是从192.168.1.1 Ping 192.168.3.11.要从192.168.1.1到192.168.3.1,看到是通过ospf通过tunnel0学到的,因此路由发往tunnel0.2.由于tunnel0上存在mymap,mymap上有ip access-list,判断是否满足。
GRE over IPSEC路由配置

GRE over IPSEC路由配置GRE over IPSEC路由配置r1(0/0)——r2——(1/1)r3GRE over IPSEC先ipsec在gre解决了ipsec无法传递多播流量问题,即可以在ipsec中跑路由协议,而且协议是通过加密的!!R1:crypto isakmp policy 10 hash md5 authentication pre-share crypto isakmp key zaq address 2.3.0.1!crypto ipsec transform-set vpn esp-des!crypto map vpn 10 ipsec-isakmp set peer 2.3.0.1 set transform-set vpn match address 101!interface Tunnel0 ip address 1.3.0.1 255.255.255.0 tunnel source FastEthernet0/0 tunnel destination 2.3.0.1!interface Loopback0 ip address 1.1.1.1 255.255.255.255!interface Loopback1 ip address 10.0.0.1 255.255.255.0!interface FastEthernet0/0 ip address 1.2.0.1 255.255.255.0 duplex full crypto map vpn!router ospf 1 log-adjacency-changes!ip route 0.0.0.0 0.0.0.0 1.2.0.2!access-list 101 permit gre host 1.2.0.1 host 2.3.0.1R2:interface FastEthernet0/0 ip address 1.2.0.2 255.255.255.0 duplex full!interface FastEthernet1/1 ip address 2.3.0.2 255.255.255.0 duplex full speed autoR3:crypto isakmp policy 10 hash md5 authentication pre-share crypto isakmp key zaq address 1.2.0.1!crypto ipsec transform-set vpn esp-des!crypto map vpn 10 ipsec-isakmp set peer 1.2.0.1 set transform-set vpn match address 101!interface Tunnel0 ip address 1.3.0.2 255.255.255.0 tunnel source FastEthernet1/1 tunnel destination 1.2.0.1!interface Loopback0 ip address 3.3.3.3 255.255.255.255!interface Loopback1 ip address 30.0.0.1 255.255.255.0!interface FastEthernet1/1 ip address 2.3.0.1 255.255.255.0 duplex full speed auto crypto map vpn!ip route 0.0.0.0 0.0.0.0 2.3.0.2!access-list 101 permit gre host 2.3.0.1 host 1.2.0.1Router#show crypto engine connections active IDInterface IP-Address State Algorithm Encrypt Decrypt 1FastEthernet1/1 2.3.0.1 set HMAC_MD5+DES_56_CB 0 0 2001FastEthernet1/1 2.3.0.1 set DES 0 27 2002FastEthernet1/1 2.3.0.1 set DES 27 0 Router#show crypto isakmp sadst src state conn-id slot status 1.2.0.1 2.3.0.1 QM_IDLE 1 0 ACTIVE Router#show crypto isakmp peers Peer:1.2.0.1 Port:500 Local:2.3.0.1 Phase1 id:1.2.0.1 Router#show crypto ipsec sa interface:FastEthernet1/1 Crypto map tag:vpn,local addr 2.3.0.1 protected vrf:(none)local ident (addr/mask/prot/port):(2.3.0.1/255.255.255.255/47/0)remote ident (addr/mask/prot/port):(1.2.0.1/255.255.255.255/47/0)current_peer 1.2.0.1 port 500 PERMIT,flags={origin_is_acl,} #pkts encaps:44,#pkts encrypt:44,#pkts digest:44 #pkts decaps:44,#pkts decrypt:44,#pkts verify:44 #pkts compressed:0,#pkts decompressed:0 #pkts not compressed:0,#pkts compr. failed:0 #pkts not decompressed:0,#pkts decompress failed:0 #send errors 1,#recv errors 0 local crypto endpt.:2.3.0.1,remote crypto endpt.:1.2.0.1 path mtu 1500,ip mtu 1500,ip mtu idb FastEthernet1/1 current outbound spi:0xEAA8551D(3936900381)inbound esp sas:spi:0x323BE771(842786673)transform:esp-des ,in use settings ={Tunnel,} conn id:2001,flow_id:1,crypto map:vpn sa timing:remaining key lifetime (k/sec):(4493451/2885)IV size:8 bytes replay detection support:N Status:ACTIVE inbound ah sas:inbound pcp sas:outbound esp sas:spi:0xEAA8551D(3936900381)transform:esp-des ,in use settings ={Tunnel,} conn id:2002,flow_id:2,crypto map:vpn sa timing:remaining key lifetime (k/sec):(4493451/2884)IV size:8 bytes replay detection support:N Status:ACTIVE outbound ah sas:outbound pcp sas:还有一种是ipsec over gre 个人认为没有意义,因为虽然解决了多播问题,但是多播是明文传输,所以ipsec就没有意义了,还不如直接用gre就好了!!。
IPSEC over GRE

IPSEC over GRE Configuration技术特点:利用tunnel跑动态路由协议实验 1 :R2(config)#interface tunnel 23R2(config-if)#ip address 23.1.1.2 255.255.255.0 <===起tunnel地址R2(config-if)#tunnel source 12.1.1.2R2(config-if)#tunnel destination 13.1.1.3R2(config-if)#tunnel key 12345 <=== "tunnel key" 只是用于标识Tunnel,两端要对称,不是用于加密,在这可以不输入这条命令R2(config-if)# router eigrp 90 <===不用宣告连接Internet的接口R2(config-router)#no auto-summaryR2(config-router)#network 2.2.2.0 0.0.0.255 <====宣告环回口网络R2(config-router)#network 100.2.2.0 0.0.0.255 <====宣告内部网络R2(config-router)#network 23.1.1.0 0.0.0.255 <====宣告tunnel地址---------------------------------------------------R3(config)#interface tunnel 23R3(config-if)#ip address 23.1.1.3 255.255.255.0R3(config-if)#tunnel source 13.1.1.3R3(config-if)#tunnel destination 12.1.1.2R3(config-if)#tunnel key 12345R3(config-if)#router eigrp 90R3(config-router)#no auto-summaryR3(config-router)#network 3.3.3.0 0.0.0.255R3(config-router)#network 100.3.3.0 0.0.0.255R3(config-router)#network 23.1.1.0 0.0.0.255IKE Phase I Policy:R2(config)#crypto isakmp policy 1R2(config-isakmp)#authentication pre-shareR2(config-isakmp)#hash md5R2(config-isakmp)#encryption 3desR2(config-isakmp)#group 2R2(config)#crypto isakmp key 0 togogo address 3.3.3.3 <===一定要用环回口地址-----------------------------------------------------R3(config)#crypto isakmp policy 1R3(config-isakmp)#authentication pre-shareR3(config-isakmp)#hash md5R3(config-isakmp)#encryption 3desR3(config-isakmp)#group 2R3(config)#crypto isakmp key 0 togogo address 2.2.2.2IPSec Phase II Policy:R2(config)#crypto ipsec transform-set cisco esp-des esp-sha-hmacR2(config)#access-list 101 permit ip 100.2.2.0 0.0.0.255 100.3.3.0 0.0.0.255R2(config)#crypto map huawei local-address Loopback0 <===将"peer"改用"Loopback0"协商建立IPSEC通道(默认以物理口协商建立IPSEC通道)R2(config)#crypto map huawei 10 ipsec-isakmpR2(config-crypto-map)#set peer 3.3.3.3 <===可用公网接口地址,也可用环回口地址(与第一阶段设置无关)以下四种情况每一次封装,先查路由表,再决定封装什么:Peer设置为物理口,Map应用到公网接口时:包结构: ...|tunnel source tunnel destination |GRE|source:100.2.2.2 destination:100.3.3.3|icmp...由于应用到公网接口的Map,没有匹配到感兴趣流,所以没有加密直接发出. Peer设置为物理口,Map应用到tunnel接口时:包结构: ...|peer source peer destination |ESP|source:100.2.2.2 destination:100.3.3.3|icmp...由于应用到tunnel接口的Map,匹配到感兴趣流,根据PEER的目标地址发出.(不经过tunnel,就出去了)Peer设置为环回口,Map应用到公网接口时:包结构: ...|tunnel source tunnel destination |GRE|source:100.2.2.2 destination:100.3.3.3|icmp...由于应用到公网接口的Map,没有匹配到感兴趣流,所以没有加密直接发出. Peer设置为环回口,Map应用到tunnel接口时:包结构: ...|tunnel source tunnel destination |GRE|peer source peer destination |ESP|source:100.2.2.2 destination:100.3.3.3|icmp...由于应用到tunnel接口的Map,匹配到感兴趣流,然后加密,根据PEER的目标地址,继续查路由表,得出下一跳为Tunnel...(经过tunnel,从物理接口发出)R2(config-crypto-map)#set transform-set ciscoR2(config-crypto-map)#set pfsR2(config-crypto-map)#match address 101-----------------------------------------------------------------------------R3(config)#crypto ipsec transform-set cisco esp-des esp-sha-hmacR3(config)#access-list 101 permit ip 100.3.3.0 0.0.0.255 100.2.2.00.0.0.255R3(config)#crypto map huawei local-address Loopback0R3(config)#crypto map huawei 10 ipsec-isakmpR3(config-crypto-map)#set peer 2.2.2.2R3(config-crypto-map)#set transform-set ciscoR3(config-crypto-map)#set pfsR3(config-crypto-map)#match address 101Apply VPN ConfigurationR2(config)#interface ethernet 0/0R2(config-if)#crypto map huaweiR2(config-if)#interface tunnel 23R2(config-if)#crypto map huawei---------------------------------------------R3(config)#interface tunnel 23R3(config-if)#crypto map huaweiR3#show crypto engine connections activeID Interface IP-Address State Algorithm Encrypt Decrypt1 Tunnel23 23.1.1.3 set HMAC_MD5+3DES_56_C 0 02001 Tunnel23 3.3.3.3 set DES+SHA 0 82002 Tunnel23 3.3.3.3 set DES+SHA 8 0------------------------------------------------------------R2#show crypto isakmp sadst src state conn-id slot status1.1.1.12.2.2.2 QM_IDLE 1 0 ACTIVE------------------------------------R2#show crypto isakmp peersPeer: 1.1.1.1 Port: 500 Local: 2.2.2.2Phase1 id: 1.1.1.1--------------------------------R2#show crypto ipsec sainterface: Ethernet0/0Crypto map tag: cisco, local addr 2.2.2.2protected vrf: (none)local ident (addr/mask/prot/port): (10.1.2.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0) current_peer 1.1.1.1 port 500PERMIT, flags={origin_is_acl,}#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 1, #recv errors 0local crypto endpt.: 2.2.2.2, remote crypto endpt.: 1.1.1.1path mtu 1500, ip mtu 1500current outbound spi: 0x12D1DDFE(315743742)inbound esp sas:spi: 0xC2686DB7(3261623735)transform: esp-des esp-sha-hmac ,in use settings ={Tunnel, }conn id: 2001, flow_id: 1, crypto map: ciscosa timing: remaining key lifetime (k/sec): (4386784/3492) IV size: 8 bytesreplay detection support: YStatus: ACTIVEinbound ah sas:inbound pcp sas:outbound esp sas:spi: 0x12D1DDFE(315743742)transform: esp-des esp-sha-hmac ,in use settings ={Tunnel, }conn id: 2002, flow_id: 2, crypto map: ciscosa timing: remaining key lifetime (k/sec): (4386784/3490) IV size: 8 bytesreplay detection support: YStatus: ACTIVEoutbound ah sas:outbound pcp sas:interface: Tunnel21Crypto map tag: cisco, local addr 2.2.2.2protected vrf: (none)local ident (addr/mask/prot/port): (10.1.2.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0) current_peer 1.1.1.1 port 500PERMIT, flags={origin_is_acl,}#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 1, #recv errors 0local crypto endpt.: 2.2.2.2, remote crypto endpt.: 1.1.1.1path mtu 1500, ip mtu 1500current outbound spi: 0x12D1DDFE(315743742)inbound esp sas:spi: 0xC2686DB7(3261623735)transform: esp-des esp-sha-hmac ,in use settings ={Tunnel, }conn id: 2001, flow_id: 1, crypto map: ciscosa timing: remaining key lifetime (k/sec): (4386784/3488) IV size: 8 bytesreplay detection support: YStatus: ACTIVEinbound ah sas:inbound pcp sas:outbound esp sas:spi: 0x12D1DDFE(315743742)transform: esp-des esp-sha-hmac ,in use settings ={Tunnel, }conn id: 2002, flow_id: 2, crypto map: ciscosa timing: remaining key lifetime (k/sec): (4386784/3487) IV size: 8 bytesreplay detection support: YStatus: ACTIVEoutbound ah sas:outbound pcp sas:IPSEC over GRE Configuration技术特点利用tunnel跑动态路由协议,ipsec over gretopology1.1.1.12.2.2.2| |Lo0 Lo0| |10.1.1.0/24-router1-172.16.171.10--------------172.16.171.20-router2-10.1.2.0/24| || tunnel |----------------------------------------------------------Basic configurationRouter1:Interface tunnel 12ip add 192.168.100.1 255.255.255.0tunnel source 172.16.171.10tunnel dest 172.16.171.20router eigrp 100no aunet 1.1.1.0 0.0.0.255net 10.1.1.0 0.0.0.255net 192.168.100.0 0.0.0.255Router2:Interface tunnel 21ip add 192.168.100.2 255.255.255.0tunnel source 172.16.171.20tunnel dest 172.16.171.10router eigrp 100no aunet 2.2.2.0 0.0.0.255net 10.1.2.0 0.0.0.255net 192.168.100.0 0.0.0.255IKE Phase I policyRouter1:crypto isakmp policy 1authentication per-sharedhash md5encr 3desgroup 2crypto isakmp key cisco address 2.2.2.2 or 172.16.171.20Router2:crypto isakmp policy 1authentication per-sharedhash md5encr 3desgroup 2crypto isakmp key cisco address 1.1.1.1 or 172.16.171.10IPSec Phase II policyRouter1:crypto ipsec transform-set cisco esp-des esp-sha-hmac access-list 101 permit ip 10.1.1.0 0.0.0.255 10.1.2.0 0.0.0.255 crypto map cisco 10 ipsec-isakmpset peer 2.2.2.2 or 172.16.171.20set transform-set ciscoset pfsmatch address 101Router2:crypto ipsec transform-set cisco esp-des esp-sha-hmac access-list 101 permit ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255 crypto map cisco 10 ipsec-isakmpset peer 1.1.1.1 or 172.16.171.10set transform-set ciscoset pfsmatch address 101Apply VPN ConfigurationRouter1:interface s0crypto map ciscointerface tu 12crypto map ciscoRouter2:interface s0crypto map ciscointerface tu 21crypto map cisconote:peer 设置为 1.1.1.1 or 2.2.2.2 时封装格式如下ip –gre –ip - esp –ip –datapeer 设置为 172.16.171.10 or 172.16.171.20 时封装格式如下ip –esp –ip –data。
H3C路由器两种ipsec-gre配置总结

H3C路由器gre over ipsec和ipsec over gre的差别与配置方法概念区分IPSEC Over GRE即IPSEC在里,GRE在外。
先把需要加密的数据包封装成IPSEC包,然后再扔到GRE隧道里。
作法是把IPSEC的加密图作用在Tunnel口上的,即在Tunnel口上监控(访问控制列表监控本地ip网段-源ip和远端ip 网段-目的地),是否有需要加密的数据流,有则先加密封装为IPSEC包,然后封装成GRE包进入隧道(这里显而易见的是,GRE隧道始终无论如何都是存在的,即GRE隧道的建立过程并没有被加密),同时,未在访问控制列表里的数据流将以不加密的状态直接走GRE隧道,即存在有些数据可能被不安全地传递的状况。
GRE Over IPSEC是指,先把数据分装成GRE包,然后再分装成IPSEC包。
做法是在物理接口上监控,是否有需要加密的GRE流量(访问控制列表针对GRE 两端的设备ip),所有的这两个端点的GRE数据流将被加密分装为IPSEC包再进行传递,这样保证的是所有的数据包都会被加密,包括隧道的建立和路由的建立和传递。
无论是哪种数据流,若一方进行了加密,而另一方没有配,则无法通讯,对于GRE则,路由邻居都无法建立。
另一个概念是隧道模式和传输模式。
所谓的隧道模式还是传输模式,是针对如ESP如何封装数据包的,前提是ESP在最外面,如果都被Over到了GRE里,自然谈不上什么隧道模式和传输模式(都为隧道模式)。
只有当GRE Over IPSEC 的时候,才可以将模式改为传输模式。
IPSEC不支持组播,即不能传递路由协议,而GRE支持。
配置方法两者配置方法上差别不大,注意定义访问控制列表的流量、配置过程中的对端地址以及策略应用位置即可。
总结一下就是:gre ove ipsec在配置访问控制列表时应配置为物理端口地址,而IPSEC Over GRE中则应配置为兴趣流量网段地址。
在gre ove ipsec配置对端地址过程中全都配置为相应物理地址,而IPSEC Over GRE中则全都配置为对端tunnel口虚拟地址。
RSR系列路由器GRE over IPSEC配置案例

network 172.16.1.0 0.0.0.255 area 0
�
如果此时用动态路由协议时【以 OSPF 路由协议为例】 ,千万不能将路由器互联的接口 IP 地址宣告进 OSPF【本案例中是 202.100.1.1】 ,否则会导致 OSPF 邻居关系抖动。 步骤三: 创建ISAKMP 策略
crypto isakmp policy 10 authentication pre-share crypto isakmp key 0 ruijie address 202.100.1.2
密级:受控
配置案例
! interface Loopback 1 ip address 2.2.2.2 255.255.255.255 ! interface Loopback 2 ip address 3.3.3.3 255.255.255.255 ! interface Tunnel 0 ip ref ip address 172.16.1.1 255.255.255.0 tunnel source 202.100.1.1 tunnel destination 202.100.1.2 ! ! ! ! ! ! ! ! ! router ospf 1 router-id 1.1.1.1 network 1.1.1.1 0.0.0.0 area 0 network 2.2.2.2 0.0.0.0 area 0 network 3.3.3.3 0.0.0.0 area 0 network 172.16.1.1 0.0.0.0 area 0 ! ! ! ! ! ! ! ref parameter 50 140 line con 0 line aux 0 line vty 0 4 login ! ! end Ruijie# 记录保存期限:2 年 锐捷网络机密,未经许可不得散 第 9页, 共 12页
神州数码IPSEC OVER GRE

IPSEC over GRE是将数据流封装在IPSEC中,然后将IPSEC包扔到GRE隧道中,应用在GRE隧道,针对的是本地内网和外部私网的数据流定义ACL:ip access-list <> <name> //ACLpermit ip <local-address> <remote-address> //在IPSEC OVER GRE中是将本地内网和外部网络的内网数据流匹配定义IKE1:crypto isakmp policy 1 //定义IKE第一阶段加密,encryption {des | 3des | ..|} //定义加密算法hash {md5 | sha} //设置完整性算法lifetime <0-86400> //设置IKE的生命周期配置对端预共享密钥:crypto isakmp key <WORD> //定义预共享密钥值,关联对端IP地址\主机域名配置IPS:crypto ipsec transform-set <WORD> //定义IPS名transform-type {esp-..| ah-.. | ...} //定义变换类型mode tunnel //注意改为隧道传输模式配置加密映射表:crypto map <map-name> <id> ipsec-isakmp //IPSEC/通过ISAKMP协商set peer <ip-address> //允许加密的对端地址set transform-set <transform_name> //指定变换集合名match address <acl> //匹配感兴趣流量应用映射表:interface tunnel <id> //进入隧道接口crypto map <map_name> //应用加密图定义路由ip route <Remote-address> 物理接口//定义路由,下一跳地址为目的地址的物理接口对端相同,注意配置IPS的顺序最好是先定义好感兴趣流量,隧道接口,一步一步有序的执行当网络因为IPS发生不通畅时,要关闭掉IPS查找问题举例:首先RA,与RC间一定是有路由的RA:定义ACL:#ip acce ex ipsec_over_gre#per ip 192.168.10.0 255.255.255.0 192.168.49.0 255.255.255.0配置接口:#int g0/3#ip add 10.0.0.1 255.255.255.252#int g0/4#ip add 192.168.10.1 255.255.255.0 //这里可以使用loopbank接口做测试#int t1#ip add 1.1.1.1 255.255.255.0#tun so g0/3#tun de 20.0.0.2配置路由:#ip route 20.0.0.0 255.255.255.252 10.0.0.2 //这里也可以使用动态路由基本接口,路由连接好之后,可以配置IPSEC OVER GRE了定义第一阶段:#cry is po 1#enc 3des#ha md#gr 2#authen pre配置对端预共享密钥:#cry is key 123456 20.0.0.2 255.255.255.252定义第二阶段:#cry ip tr myset#mode tunn //传输模式为隧道模式定义映射表:#cry map mymap 1 ipsec-is#set peer 20.0.0.2#set tr myset#mat add ipsec_over_gre配置路由:#ip route 192.168.49.0 255.255.255.0 t1将映射表应用在隧道接口中:#int t1#cry map mymapRB:定义ACL:#ip acce ex ipsec_over_gre#per ip 192.168.49.0 255.255.255.0 192.168.10.0 255.255.255.0配置接口:#int g0/3#ip add 192.168.49.1 255.255.255.0 //这里可以使用loopbank接口做测试#int g0/4#ip add 20.0.0.2 255.255.255.252#int t1#ip add 1.1.1.2 255.255.255.0#tun so g0/4#tun de 10.0.0.1配置路由:#ip route 10.0.0.0 255.255.255.252 20.0.0.1 //这里也可以使用动态路由基本接口,路由连接好之后,可以配置IPSEC OVER GRE了定义第一阶段:#cry is po 1#enc 3des#ha md#gr 2#authen pre配置对端预共享密钥:#cry is key 123456 10.0.0.1 255.255.255.252定义第二阶段:#cry ip tr myset#mode tunn //传输模式为隧道模式定义映射表:#cry map mymap 1 ipsec-is#set peer 10.0.0.1#set tr myset#mat add ipsec_over_gre配置路由:#ip route 192.168.10.0 255.255.255.0 t1 将映射表应用在隧道接口中:#int t1#cry map mymap写的很简单如有问题加QQ:1195918199可以咨询。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
路由器-IPSec-Over-GRE典型配置路由器-IPSec-Over-GRE典型配置【需求】分部1和分部2通过野蛮IPSec的方式连接到中心,采用IPSec-Over-GRE的方式,在tunnel 上运行OSPF协议来实现总部和分部之间的互通。
【组网图】【配置脚本】中心配置脚本#sysname Center#ike local-name center /中心ike的local-name为:center/#router id 1.1.1.1#radius scheme system#domain system##ip route-static 0.0.0.0 0.0.0.0 202.101.1.1 preference 60#user-interface con 0user-interface vty 0 4#return分部1配置脚本#sysname Branch1#ike local-name branch1 /分部1的ike的local-name为:branch1/#radius scheme system#domain system#ike peer center /配置到中心的ike peer/exchange-mode aggressive /设置IPSec为野蛮方式/pre-shared-key abc /预共享密钥为abc/id-type name /选择名字作为ike协商过程中使用的ID/remote-name center /对端的名字为center/remote-address 10.0.0.1 /对端的地址为10.0.0.1(中心的tunnel地址)/#ipsec proposal 1 /定义ipsec proposal/#ipsec policy branch1 10 isakmp /配置到中心的ipsec policy/security acl 3001 /指定安全策略所引用的访问控制列表号/ike-peer center /引用ike peer/proposal 1 /引用ipsec proposal/#acl number 3001 /定义从分部1到中心的内网数据流/rule 0 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 #interface Serial2/0link-protocol pppip address 202.101.2.2 255.255.255.252#interface Tunnel0 /配置分部1和中心之间的GRE tunnel/ip address 10.0.0.2 255.255.255.252source 202.101.2.2destination 202.101.1.2ipsec policy branch1 /在tunnel 0上应用IPSec policy branch1/#interface NULL0#interface LoopBack0ip address 2.2.2.2 255.255.255.255#interface Ethernet0/0 /配置分部1的内网地址/ip address 192.168.2.1 255.255.255.0#ospf 1area 0.0.0.10 /分部1属于area 10/network 2.2.2.2 0.0.0.0network 10.0.0.0 0.0.0.3network 192.168.2.0 0.0.0.255#ip route-static 0.0.0.0 0.0.0.0 202.101.2.1 preference 60#user-interface con 0user-interface vty 0 4#return分部2配置脚本#sysname Branch2#ike local-name branch1 /分部2的ike的local-name为:branch2/#radius scheme system#domain system#ike peer center /配置到中心的ike peer/exchange-mode aggressive /设置IPSec为野蛮方式/pre-shared-key abc /预共享密钥为abc/id-type name /选择名字作为ike协商过程中使用的ID/remote-name center /对端的名字为center/remote-address 10.0.0.5 /对端的地址为10.0.0.5(中心的tunnel地址)/#ipsec proposal 1 /定义ipsec proposal/#ipsec policy branch1 10 isakmp /配置到中心的ipsec policy/security acl 3001 /指定安全策略所引用的访问控制列表号/ike-peer center /引用ike peer/proposal 1 /引用ipsec proposal/#acl number 3001 /定义从分部2到中心的GRE数据流/rule 0 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 #interface Serial2/0link-protocol pppip address 202.101.3.2 255.255.255.252#interface Tunnel0 /配置分部1和中心之间的GRE tunnel/ip address 10.0.0.6 255.255.255.252source 202.101.3.2destination 202.101.1.2ipsec policy branch2 /在tunnel 0上应用IPSec policy branch2/#interface NULL0#interface LoopBack0ip address 3.3.3.3 255.255.255.255#interface Ethernet0/0 /配置分部1的内网地址/ip address 192.168.3.1 255.255.255.0#ospf 1area 0.0.0.20 /分部2属于area 20/network 3.3.3.3 0.0.0.0network 10.0.0.4 0.0.0.3network 192.168.3.0 0.0.0.255#ip route-static 0.0.0.0 0.0.0.0 202.101.3.1 preference 60#user-interface con 0user-interface vty 0 4#return【验证】1、中心上的ike sa 状态:disp ike saconnection-id peer flag phase doi----------------------------------------------------------44 10.0.0.2 RD 1 IPSEC48 10.0.0.6 RD 2 IPSEC47 10.0.0.6 RD 1 IPSEC45 10.0.0.2 RD 2 IPSECflag meaningRD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO—TIMEOUT 2、中心上的IPSec sa状态:disp ipsec sa=============================== Interface: Tunnel0path MTU: 64000===============================-----------------------------IPsec policy name: "branch1"sequence number: 10mode: isakmp-----------------------------connection id: 8encapsulation mode: tunnelperfect forward secrecy: None tunnel:local address: 10.0.0.1remote address: 10.0.0.2flow: (4 times matched)sour addr: 192.168.1.0/255.255.255.0 port: 0 protocol: IPdest addr: 192.168.2.0/255.255.255.0 port: 0 protocol: IP[inbound ESP SAs]spi: 2701983530 (0xa10cff2a) proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5sa remaining key duration (bytes/sec): 1887436664/2136max received sequence-number: 2udp encapsulation used for nat traversal: N[outbound ESP SAs]spi: 2132567950 (0x7f1c678e) proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5sa remaining key duration (bytes/sec): 1887436632/2136max sent sequence-number: 3 udp encapsulation used for nat traversal: N=============================== Interface: Tunnel1path MTU: 64000===============================-----------------------------IPsec policy name: "branch2"sequence number: 10mode: isakmp-----------------------------connection id: 9encapsulation mode: tunnelperfect forward secrecy: None tunnel:local address: 10.0.0.5remote address: 10.0.0.6flow: (18 times matched)sour addr: 192.168.1.0/255.255.255.0 port: 0 protocol: IPdest addr: 192.168.3.0/255.255.255.0 port: 0 protocol: IP[inbound ESP SAs]spi: 1612204948 (0x60184b94) proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5sa remaining key duration (bytes/sec): 1887436188/2886max received sequence-number: 9udp encapsulation used for nat traversal: N[outbound ESP SAs]spi: 3432409622 (0xcc966a16) proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5sa remaining key duration (bytes/sec): 1887436044/2886max sent sequence-number: 10 udp encapsulation used for nat traversal: N3、中心路由表disp ip routRouting Table: public net Destination/Mask ProtocolPre Cost Nexthop Interfa ce0.0.0.0/0 STATIC 60 0 202.101.1.1 Serial2/0/0 1.1.1.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0 2.2.2.2/32 OSPF 10 1563 10.0.0.2 Tunnel03.3.3.3/32 OSPF 10 1563 10.0.0.6 Tunnel110.0.0.0/30 DIRECT 0 0 10.0.0.1 Tunnel010.0.0.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0 10.0.0.4/30 DIRECT 0 0 10.0.0.5 Tunnel110.0.0.5/32 DIRECT 0 0 127.0.0.1 InLoopBack0 127.0.0.0/8 DIRECT 0 0 127.0.0.1 InLoopBack0 127.0.0.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0 192.168.1.0/24 DIRECT 0 0 192.168.1.1 LoopBack10 192.168.1.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0 192.168.2.0/24 OSPF 10 1563 10.0.0.2 Tunnel0192.168.3.0/24 OSPF 10 1563 10.0.0.6 Tunnel1202.101.1.0/30 DIRECT 0 0 202.101.1.2 Serial2/0/0 202.101.1.1/32 DIRECT 0 0 202.101.1.1 Serial2/0/0 202.101.1.2/32 DIRECT 0 0 127.0.0.1 InLoopBack04、分部1的ike sa状态:disp ike saconnection-id peer flag phase doi----------------------------------------------------------27 10.0.0.1 RD|ST 1 IPSEC28 10.0.0.1 RD|ST 2 IPSECflag meaningRD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO—TIMEOUT 5、分部1的ipsec sa状态:disp ipsec sa=============================== Interface: Tunnel0path MTU: 64000===============================-----------------------------IPsec policy name: "branch1"sequence number: 10mode: isakmp-----------------------------connection id: 6encapsulation mode: tunnelperfect forward secrecy: None tunnel:local address: 10.0.0.2remote address: 10.0.0.1flow: (4 times matched)sour addr: 192.168.2.0/255.255.255.0 port: 0 protocol: IPdest addr: 192.168.1.0/255.255.255.0 port: 0 protocol: IP[inbound ESP SAs]spi: 2132567950 (0x7f1c678e) proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5sa remaining key duration (bytes/sec): 1887436664/2054max received sequence-number: 2udp encapsulation used for nat traversal: N[outbound ESP SAs]spi: 2701983530 (0xa10cff2a) proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5sa remaining key duration (bytes/sec): 1887436632/2054max sent sequence-number: 3 udp encapsulation used for nat traversal: N6、分部1的路由表:disp ip routRouting Table: public net Destination/Mask ProtocolPre Cost Nexthop Inter face0.0.0.0/0 STATIC 60 0 202.101.2.1 Serial2/0/01.1.1.1/32 OSPF 10 1563 10.0.0.1 Tunnel02.2.2.2/32 DIRECT 0 0 127.0.0.1 InLoopBack03.3.3.3/32 OSPF 10 3125 10.0.0.1 Tunnel010.0.0.0/30 DIRECT 0 0 10.0.0.2 Tunnel010.0.0.2/32 DIRECT 0 0 127.0.0.1 InLoopBack010.0.0.4/30 OSPF 10 3124 10.0.0.1 Tunnel0127.0.0.0/8 DIRECT 0 0 127.0.0.1 InLoopBack0 127.0.0.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0 192.168.1.0/24 OSPF 10 1563 10.0.0.1 Tunnel0192.168.2.0/24 DIRECT 0 0 192.168.2.1 LoopBack10 192.168.2.1/32 DIRECT 0 0 127.0.0.1 InLoopBack0 192.168.3.0/24 OSPF 10 3125 10.0.0.1 Tunnel0202.101.2.0/30 DIRECT 0 0 202.101.2.2 Serial2/0/0 202.101.2.1/32 DIRECT 0 0 202.101.2.1 Serial2/0/0 202.101.2.2/32 DIRECT 0 0 127.0.0.1 InLoopBack0【提示】1、IPSec-Over-GRE和GRE-Over-IPSec方式配置上的区别为:GRE-Over-IPS ec IPSec-Over-G REACL定义GRE数据流内网数据流Ike peer中指对方公网地址对方GRE定的tunnel地址remote-address应用端口公网出口GRE tunnel上2、各个分部和总部之间通过OSPF路由来实现互访,如果没有运行OSPF则必需在分部和总部配置静态路由。
