计算机网络-chapter3
计算机网络:自顶向下方法-课本课后习题答案(1-3)

课后习题答案:Chapter 1:Review questions: 1,4,11,13,15,16,18,19,23,25,261没有不同,在本文书中,“主机”和“终端系统”可以互换使用。
终端系统包括PCs ,工作站,Web 服务器,电子邮件服务器,连接Internet 的PDA ,WebTV 等。
41 通过电话线拨号调制解调器:住宅2 通过电话线的DSL :住宅或小型办公室3 光纤电缆:住宅4 100 Mbps 交换以太网:公司5 无线LAN :移动电话6 蜂窝移动接入(例如WAP ):移动电话11电路交换网络可以为一个通话保证特定数量的端到端带宽。
大多数现在分组交换网络(包括Internet )可以提供所有端到端带宽保证。
13在时间t0发送主机开始传输。
在t1 = L/R1时,发送主机完成传输并且整个分组到达路由器(没有传播延迟)。
因为路由器在时间t1拥有整个分组,所以它在时间t1开始向接收主机传输此分组。
在时间t2 = t1 + L/R2,路由器完成传输并且接收主机接收整个分组(也没有传播延迟)。
因此端到端延迟是L/R1 + L/R2。
15a) 可以支持两个用户因为每个用户需要一半的链路带宽。
b) 因为在传输过程中每个用户需要1Mbps ,如果两个或更上用户同时传输,那么最大需要2Mbs 。
因为共享的链路的可用带宽是2Mbps ,所以在链接之前没有排队延迟。
然而,如果三个用户同时传输,那么需要的带宽将是3Mbps ,它大于共享链路的可用带宽,在这种情况下在链接前存在排队延迟。
c) 给定用户传输的概率是0.2。
d) 所有三个用户同时传输的概率是()333133--⎪⎪⎭⎫ ⎝⎛p p = (0.2)3 = 0.008。
因为当所有用户都传输时,队列增加,所以在队列增加的分数(它等于所有三个用户同时传输的概率)是0.008。
16延迟组件是处理延迟,传输延迟,传播延迟和排队延迟。
除了排队延迟是变化的,其它所有延迟都是固定的。
计算机网络 Chapter_3_V6.0

3.6 principles of congestion control 3.7 TCP congestion control
Transport Layer 3-7
DatagramSocket mySocket2 = new DatagramSocket (9157);
application
DatagramSocket serverSocket = new DatagramSocket (6428);
Chapter 3 Transport Layer
A note on the use of these ppt slides:
We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) If you post any slides on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Thanks and enjoy! JFK/KWR All material copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved Transport Layer 3-1
计算机网络英文题库(附答案)chapter

Chapter 1 Computer Networks and the Internet1.The ( ) is a worldwide computer network, that is, a network that interconnects millions of computing devices throughout the world. ppt3A public InternetB IntranetC switch netD television net2.Which kind of media is not a guided media? ( )A twisted-pair copper wireB a coaxial cableC fiber opticsD digital satellite channel3.Which kind of media is a guided media? ( )A geostationary satelliteB low-altitude satelliteC fiber opticsD wireless LAN4.The units of data exchanged by a link-layer protocol are called ( ).A FramesB SegmentsC DatagramsD bit streams5.Which of the following option belongs to the circuit-switched networks? ( )A FDMB TDMC VC networksD both A and B6.( )makes sure that neither side of a connection overwhelms the other side by sending too many packets too fast.A Reliable data transferB Flow controlC Congestion controlD Handshaking procedure7.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Store-and-forward transmissionB FDMC End-to-end connectionD TDM8.Datagram networks and virtual-circuit networks differ in that ( ).A datagram networks are circuit-switchednetworks, and virtual-circuit networks arepacket-switched networks.B datagram networks are packet-switchednetworks, and virtual-circuit networks arecircuit-switched networks.C datagram networks use destinationaddresses and virtual-circuit networks useVC. numbers to forward packets toward theirdestination.D datagram networks use VC. numbers andvirtual-circuit networks use destinationaddresses to forward packets toward theirdestination.9.In the following options, which one is not a guided media? ( )A twisted-pair wireB fiber opticsC coaxial cableD satellite10.Processing delay does not include the time to ( ).A examine the packet’s headerB wait to transmit the packet onto the linkC determine where to direct the packetD check bit-error in the packet11.In the following four descriptions, which one is correct? ( )A The traffic intensity must be greater than1.B The fraction of lost packets increases asthe traffic intensity decreases.C If the traffic intensity is close to zero,the average queuing delay will be close tozero.D If the traffic intensity is close to one,the average queuing delay will be close toone.12.The Internet’s network layer is responsible for moving network-layer packets known as ( ) from one host to another.A frameB datagramC segmentD message13.The protocols of various layers are called ( ).A the protocol stackB TCP/IPC ISPD network protocol14.There are two classes of packet-switched networks: ( ) networks and virtual-circuit networks.A datagramB circuit-switchedC televisionD telephone15.Access networks can be loosely classified into three categories: residential access, company access and ( ) access.A cabledB wirelessC campusD city areaQuestion 16~17Suppose, a is the average rate at which packets arrive at the queue, R is the transmission rate, and all packets consist of L bits, then the traffic intensity is ( 16 ), and it should no greater than ( 17 ).16. A LR/aB La/RC Ra/LD LR/a17.A 2B 1C 0D -118.In the Internet, the equivalent concept to end systems is ( ).A hostsB serversC clientsD routers19.In the Internet, end systems are connected together by ( ).A copper wireB coaxial cableC communication linksD fiber optics20.End systems access to the Internet through its ( ).A modemsB protocolsC ISPD sockets21.End systems, packet switches, and other pieces of the Internet, run ( ) that control thesending and receiving of information within the Internet.A programsB processesC applicationsD protocols22.There are many private networks, such as many corporate and government networks, whose hosts cannot exchange messages with hosts outside of the private network. These private networks are often referred to as ( ).A internetsB LANC intranetsD WAN23.The internet allows ( ) running on its end systems to exchange data with each other.A clients applicationsB server applicationsC P2P applicationsD distributed applications24.The Internet provides two services to its distributed applications: a connectionlessunreliable service and () service.A flow controlB connection-oriented reliableC congestion controlD TCP25.It defines the format and the order of messagesexchanged between two or more communicatingentities, as well as the actions taken on the transmission and/or receipt of a message orother event. The sentence describes ( ).A InternetB protocolC intranetD network26.In the following options, which does not define in protocol? ( )A the format of messages exchanged betweentwo or more communicating entitiesB the order of messages exchanged betweentwo or more communicating entitiesC the actions taken on the transmission ofa message or other eventD the transmission signals are digitalsignals or analog signals27.In the following options, which is defined in protocol? ( )A the actions taken on the transmission and/orreceipt of a message or other eventB the objects exchanged between communicating entitiesC the content in the exchanged messagesD the location of the hosts28.In the following options, which does not belong to the network edge? ( )A end systemsB routersC clientsD servers29.In the following options, which belongs to the network core? ( )A end systemsB routersC clientsD servers30.In the following options, which is not the bundled with the Internet’sconnection-oriented service? ( )A reliable data transferB guarantee of the transmission timeC flow controlD congestion-control31.An application can rely on the connection to deliver all of its data without error and in the proper order. The sentence describes ( ).A flow controlB congestion-controlC reliable data transferD connection-oriented service32.It makes sure that neither side of a connection overwhelms the other side by sending too many packets too fast. The sentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer33.It helps prevent the Internet from entering a state of gridlock. When a packet switch becomes congested, its buffers can overflow and packet loss can occur. The sentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer34.The Internet’s connection-oriented service has a name, it is ( ).A TCPB UDPC TCP/IPD IP35.In the following options, which service does not be provided to an application by TCP?( )A reliable transportB flow controlC video conferencingD congestion control36.The Internet’s connectionless service is called ( ).A TCPB UDPC TCP/IPD IP37.In the following options, which does not use TCP?( )A SMTPB internet telephoneC FTPD HTTP38.In the following options, which does not use UDP?( )A Internet phoneB video conferencingC streaming multimediaD telnet39.There are two fundamental approaches to buildinga network core, ( ) and packet switching.A electrical current switchingB circuit switchingC data switchingD message switching40.In ( ) networks, the resources needed along a path to provide for communication between the end system are reserved for the duration of the communication session.A packet-switchedB data-switchedC circuit-switchedD message-switched41.In ( ) networks, the resources are not reserved;a session’s messages use the resources ondemand, and as a consequence, may have to wait for access to communication link.A packet-switchedB data-switchedC circuit-switchedD message-switched42.In a circuit-switched network, if each link has n circuits, for each link used by the end-to-end connection, the connection gets ( ) of thelink’s bandwidth for the duration of theconnection.A a fraction 1/nB allC 1/2D n times43.For ( ), the transmission rate of a circuit is equal to the frame rate multiplied by the number of bits in a slot.A CDMAB packet-switched networkC TDMD FDM44.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Queuing delayB Store-and-forward transmissionC Packet lossD Propagation45.The network that forwards packets according to host destination addresses is called ( )network.A circuit-switchedB packet-switchedC virtual-circuitD datagram46.The network that forwards packets according to virtual-circuit numbers is called ( ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram47.In the following entries, which is not a kind of access network?( )A residential accessB company accessC wireless accessD local access48.Suppose there is exactly one packet switch between a sending host and a receiving host. The transmission rates between the sending host and the switch and between the switch and thereceiving host are R1 and R2, respectively.Assuming that the switch uses store-and-forward packet switching, what is the total end-to-end delay to send a packet of length L? (Ignorequeuing delay, propagation delay, andprocessing delay.) ( )A L/R1+L/R2B L/R1C L/R2D none of the above49.The time required to examine the packet’s headerand determine where to direct the packet is part of the ( ).A queuing delayB processing delayC propagation delayD transmission delay50.The time required to propagate from the beginning of the link to the next router is ( ).A queuing delayB processing delayC propagation delayD transmission delay51.Consider sending a packet of 3000bits over a path of 5 links. Each link transmits at 1000bps. Queuing delays, propagation delay and processing delay are negligible. (6 points)(1).Suppose the network is a packet-switched virtual circuit network. VC setup time is 0.1 seconds. Suppose the sending layers add a total of 500 bits of header to each packet. How long does it take to send the file from source to destination?(2).Suppose the network is a packet-switched datagram network and a connectionless service is used. Now suppose each packet has 200 bits of header. How long does it take to send the file?(3).Suppose that the network is a circuit-switched network. Further suppose that the transmission rate of the circuit between source and destination is 200bps. Assuming 0.02s setup time and 200 bits of header appended to the packet, how long does it take to send the packet?Solution:?(1) .?t=5*(3000+500)/1000+0.1=17.6s?(2). t=5*(3000+200)/1000=16s(3). t=(3000+200)/200+0.02=16.02s。
计算机网络英文题库(附答案)chapter3解析

Chapter 3 Transport Layer1. A transport-layer protocol provides for logical munication between ____.A Application processesB HostsC RoutersD End systems2. Transport-layer protocols run in ____.A ServersBClientsCRoutersDEnd systems3. In transport layer, the send side breaks application messages into ____, passes to network layer.A FramesB SegmentsC Data-gramsD bit streams4. Services provided by transport layer include ____.A HTTP and FTPB TCP and IPC TCP and UDPD SMTP5. Which of the following services is not provided by TCP"A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers6. These two minimal transport-layer services----____ and ____----are the only two services that UDP provides!A process-to-process data delivery, error checkingB congestion control, reliable data transferC flow control, congestion controlD In-order data transfer, error checking7. Port number’s scope is ____ to ____.A 0, 1023B 0, 65535C 0, 127D 0,2558. The port numbers ranging from ____to ____ are called well-known port number and are restricted.A 0, 1023B 0, 65535C 0, 127D 0,2559. UDP socket identified by two ponents, they are____.A source IP addresses and source port numbersB source IP addresses and destination IP addressesC destination IP address and destination port numbersD destination port numbers and source port numbers10. TCP socket identified by a (an) ____.A 1-tupleB 2-tupleC 3-tupleD 4-tuple11. Which of the following applications normally uses UDP services"A SMTPB Streaming multimediaC FTPD HTTP12.Reliable data transfer protocol over a perfectly reliable channel is____.A rdt1.0B rdt2.0C rdt3.0D rdt2.113.Reliable data transfer protocol over a channel with bit errors and packet losses is_ ___.A rdt1.0B rdt2.0C rdt3.0D rdt2.114.Which of the following about reliable data transfer over a channel with bit errors is not correct"A RDT2.0:assuming ACK and NAK will not be corruptedB RDT2.1:assuming ACK and NAK can be corruptedC RDT2.2:only use ACK-sD RDT2.2:use both ACK-s and NAK-s15.Which of the following protocols is not pipelining protocols"A TCPB rdt3.0C GO-BACK-ND selective repeat16.Which of the following is not correct about GBN protocol"A Only using ACK-sB Using cumulative ACK-sC Receiver discards all out-of-order packetsD It is not pipelined protocol17.Which of the following is not correct about SR protocol"A receiver individually acknowledges all correctly received packetsB sender only resends packets for which ACK not receivedC It limits sequence number of sent but un-ACK-ed packetsD It is not a pipelined protocol18. Which of the following about TCP connection is not correct"A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection19. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection20. The FIN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection21.How does TCP sender perceive congestion"A Through a timeout eventB Through a receiving duplicate ACK-s eventC Both A and BD Either A or B22. Extending host-to-host delivery to process-to-process delivery is called transport-layer____ and .A multiplexing and de-multiplexingB storing and forwardingC forwarding and filteringD switching and routing23. UDP is a ____ service while TCP is a connection-oriented service.A ConnectionlessB ReliableC Connection-orientedD In-order24. The UDP header has only four fields, they are____.A Source port number, destination port number, length and checksumB Source port number, destination port number, source IP and destination IPC source IP, destination IP, source MAC address and destination MAC addressD source IP, destination IP, sequence number and ACK sequence number25. There are two 16-bit integers: 1110 0110 0110 0110, 1101 0101 0101 0101. Their checksum is____.A 00011B 11100C 11111D 0000026.The maximum amount of data that can be grabbed and placed in a segment is limited by the____.A Maximum segment size (MSS)B MTUC ChecksumD Sequence number27.The MSS is typically set by first determining the length of the largest link-layerframe that can be sent by the local sending host----the so-called____.A Maximum transmission unit (MTU)B MSSC ChecksumD Sequence number28. A File size of 500,000bytes, MSS equals 1000bytes. When we want to transmit this file with TCP, the sequence number of the first segment is 0, and the sequence number of the second segment is ____.A 1000B 999C 1001D 50000029.Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide____.A Cumulative acknowledgementsB Selective acknowledgementsC 3 duplicate ACKsD positive ACKs30. Provided α=0.125, current value of Estimated-RTT is 0.4s, Sample-RTT is 0.8s, then the new value of Estimated-RTT is ____s.A 0.45B 0.6C 0.7D 0.831.Provided RcvBuffer=20,LastByteRcvd=20,LastByteRead=15, thenRcvWindow=____.A 14B 15C 16D 1032. TCP service does not provide____.A Reliable data transferB Flow controlC Delay guaranteeD Congestion control33. There are two states in TCP congestion control, which are ____.A slow start and congestion avoidanceB safe start and congestion avoidanceC slow start and congestion abandonD safe start and congestion abandon34. The transport-layer protocol provides logical munication between ____, and the network-layer protocol provides logical munication ____.A hosts, processesB processes, hostsC threads, processesD processes, threads35.To implement the multicast services the Internet employs the____protocol.A FTPB TCPC IGMPD UDP36. If an application developer chooses ____ protocol, then the application process is almost directly talking with IP.A HTTPB RIPC CSMA/CDD UDP37. ____ maintains connection-state in the end systems. This connection state includes receive and send buffers, congestion-control parameters, and sequence and acknowledgment number parameters.A UDPB TCPC DNSD HTTP38. The host that initiates the session in the Internet is labeled as ____.A serverB user agentC clientD router39. With TCP there is no _____ between sending and receiving transport-layer entities.A flow controlB handshakingC.congestion control D VC setup40. The Internet’s ____ service helps prevent the Internet from entering a state of gridlock.A datagramB congestion controlC sliding windowD timeout event41. Connection setup at the transport layer involves ____.A serverB only the two end systemsC clientD router42. A ____layer protocol provides for logical munication between applications.A transportB applicationC networkingD MAC43. In static congestion window, if it satisfies W*S/R > RTT + S/R, the Latency is ____.A W*S/R – ( RTT+ S/R)B 2RTT + O/RC 2RTT + O/R + (k-1)[W* S/R- (RTT + S/R)]D 2RTT + S/R44. The receive side of transport layer reassembles segments into messages, passes to ____layer.A ApplicationB NetworkingC PhysicalD MAC45. In the following four options, which one is correct"A The variations in the SampleRTT are smoothed out in the putation of the EstimatedRTTB The timeout should be less than the connection’s RTTC Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≥1 secD Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≤1 sec46. The port number used by HTTP is ____.A 80B 25C 110D 5347. The port number used by SMTP is ____.A 80B 25C 110D 5348. The port number used by pop3 is ____.A 80B 25C 110D 5349. The port number used by DNS is ____.A 80B 25C 110D 5350. The port number used by FTP is ____.A 20 and 21B 20C 21D 5351. A UDP socket identified by a ____ tuple(s).A 2B 4C 1D 352. A TCP socket identified by a ____ tuple(s).A 2B 4C 1D 353. A TCP socket does not include____.A Source MAC addressB Source port numberC Destination IP addressD Destination port number54. Which of following about UDP is not correct.A It is a reliable data transfer protocolB It is connectionlessC no handshaking between UDP sender, receiverD it is a best effort service protocol55. DNS uses ____ service.A TCPB UDPC Both TCP and UDPD None of above56. Which of following about UDP is correct"A Finer application-level control over what data is sent, and whenB No connection establishment (which can add delay), so no delay for establish a connectionC No connection state (so, UDP can typically support many active clients)D Large packet header overhead (16-B)57. Streaming media uses a ____ service normally.A TCPB UDPC Both TCP and UDPD None of above58. The UDP header has only ____ fields.A 2B 4C 1D 359. Which of the following does not included in UDP header.A Source port numberB Destination port numberC ChecksumD Sequence number60. Which of the following is not a pipelining protocol.A Rdt1.0B Go-Back-NC Selective repeatD TCP61. In the following four descriptions about MSS and MTU, which one is not correct"A The MSS is the maximum amount of application-layer data in the segmentB The MSS is the maximum size of the TCP segment including headersC The MSS is typically set by MTUD The MTU means the largest link-layer frame62. The job of gathering data chunks, encapsulating each data chunk with header information to create segments and passing the segments to the network is called ____.A multiplexingB de-multiplexingC forwardingD routing63. In the following four descriptions about the relationship between the transport layer and the network layer, which one is not correct"A The transport-layer protocol provides logical munication between hostsB The transport-layer protocol provides logical munication between processesC The services that a transport-layer protocol can provide are often constrained by the service model of the network-layer protocolD A puter network may make available multiple transport protocols64. Suppose the following three 8-bit bytes: 01010101, 01110000, 01001100. What’s the 1s plement of the sum of these 8-bit bytes"A 00010001B 11101101C 00010010D 1000100065. The following four descriptions about multiplexing and de-multiplexing, which one is correct"A A UDP socket is identified by a two-tuples consisting of a source port number and a destination port number.B If two UDP segment have different source port number, they may be directed to thesame destination process.C If two TCP segments with different source port number, they may be directed to the same destination process.D If two TCP segments with same destination IP address and destination port number, they must be the same TCP connection.66. UDP and TCP both have the fields except ____.A source port numberB destination port numberC checksumD receive window67. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [nextseqnum,base+N-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged68. Which of the following about TCP is not correct"A It is a connectionless protocolB Point-to-point protocolC Reliable, in-order byte steam protocolD Pipelined protocol69. Which of the following about TCP is not correct"A It is a connectionless protocolB full duplex data transfer protocolC connection-oriented protocolD flow controlled protocol70. The maximum amount of data that can be grabbed and placed in a segment is limited by the ____.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum71. The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host (the so-called____), and then will fit into a single link-layer frame.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum72. The MSS is the maximum amount of ____layer data in the segment, not the maximum size of the TCP segment including headers.A ApplicationB TransportD Link73. Which of the following field is not used for connection setup and teardown"A Sequence numberB TSTC SYND FIN74. ____ is the byte stream number of first byte in the segment.A Sequence numberB ACK numberC ChecksumD port number75. ____ is the byte sequence numbers of next byte expected from other side.A Sequence numberB ACK numberC ChecksumD port number76. Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide ____ acknowledgements.A CumulativeB SelectiveC Single77. Fast retransmit means in the case that ____ duplicate ACK-s are received, the TCP sender resend segment before timer expires.A 3B 4C 5D 678. TCP____ means sender won’t overflow receiver’s buffer by transmitting too much, too fast.A Flow controlB Congestion controlC Reliable data transferD Connection-oriented service79. TCP provides flow control by having the sender maintain a variable called the ____.A Receive windowB Congestion windowC Sliding windowD buffer80. How does TCP sender perceive congestion"A TimeoutB 3 duplicate ACK-sC Both A and BD None of above81. Transport protocols run in ____.A ServersB ClientsC RoutersD End systems82. Which of the following services is not provided by TCP"A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers83. Which service does UDP not provide"A multiplexingB de-multiplexingC error-detectionDerror-correction84. There are three major events related to data transmission and retransmission in the TCP sender, which one is not in it"A data received from application aboveB de-multiplexing segmentC timer timeoutD ACK receipt85. Which of the following applications normally uses UDP services"A SMTPB Streaming multimediaC FTPD HTTP86. Which of the following about TCP connection is not correct"A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection87. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection88. Which service helps prevent the internet from entering a state of gridlock"A reliable data transferB flow controlC congestion controlD handshaking procedure89. The Internet’s _____is responsible for moving packets from one host to another.A application layerB transport layerC network layerD link layer90.In the following applications, which one is a bandwidth-sensitive application"AB web applicationC real-time audioD file transfer91. In the following applications, which one uses UDP"AB web applicationC file transferD DNS92. In the following four descriptions, which one is correct"A If one host’s transport layer uses TCP, then its network layer must use virtual-circuit network.B Datagram network provides connection serviceC The transport-layer connection service is implemented in the routerD The network-layer connection service is implemented in the router as well as in the end system.93.____ is a speeding-matching service---matching the rate which the sender is sending against the rate at which the receiving application is reading.A congestion controlB flow controlC sliding-window controlD variable control94. In the following four descriptions about Rcv-Window, which one is correct"A The size of the TCP RcvWindow never changes throughout the duration of the connectionB The size of the TCP RcvWindow will change with the size of the TCP RcvBufferC The size of the TCP RcvWindow must be less than or equal to the size of the TCP RcvBufferD Suppose host A sends a file to host B over a TCP connection, the number of unacknowledged bytes that A sends cannot exceed the size of the size of the RcvWindow.95. There are 6 flag fields. Which one is to indicate that the receiver should pass the data to the upper layer immediately"A PSHB URGC ACKD RST96. Suppose the TCP receiver receives the segment that partially or pletely fills in gap in received data, it will ____.A immediately send ACKB immediately send duplicate ACKC wait some time for arrival of another in-order segmentD send single cumulative97. _____ imposes constrain on the rate at which a TCP sender can send traffic into the network.A sliding windowB congestion windowC receive windowD variable window98. Flow control and congestion control are same at that they all limit the rate of the sender, but differ in that ____.A flow control limits its rate by the size of RcvWindow, but congestion control by the traffic on the linkB congestion control limits its rate by the size of RcvWindow, but flow control by the traffic on the linkC flow control mainly is acplished by the sender, but congestion control by the receiver.D flow control mainly is acplished by the receiver, but congestion control by the link.99. This job of delivering the data in a transport-layer segment to the correct socket is called ____.A multiplexingB de-multiplexingC forwardingD routing100. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [base, nextseqnum-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged101. ____ are the two types of transport services that the Internet provides to the applications.A TCP and UDPB connection-oriented and connectionless serviceC TCP and IPD reliable data transfer and flow control102. In the following descriptions about persistent connection, which one is not correct"A The server leaves the TCP connection open after sending a responseB Each TCP connection is closed after the server sending one objectC There are two versions of persistent connection: without pipelining and with pipeliningD The default mode of HTTP uses persistent connection with pipelining103. The field of Length in UDP segment specifies the length of ____.A the UDP segment, not including the headerB the UDP segment, including the headerC the UDP segment’s headerD the Length field104. In TCP segment header, which field can implement the reliable data transfer"A source port number and destination port numberB sequence number and ACK numberC urgent data pointerD Receive window105. In the following four descriptions about TCP connection management, which one is not correct"A Either of the two processes participating in a TCP connection can end the connectionB If the FIN bit is set to 1, it means that it wants to close the connectionC In the first two step of the three-way handshake, the client and server randomly choose an initial sequence numberD In the three segments of the three-way handshake, the SYN bit must be set to 1 106. Suppose host A sends two TCP segments back to back to host B over a TCP connection. The first segment has sequence number 42, and the second has sequence number 110. If the 1st is lost and 2nd arrives at host B. What will be the acknowledgment number"A 43B ACK42C 109D ACK1101.Consider sending an object of size O=500,000bytes from server to client. Let S=500bytes and RTT=0.2s. Suppose the transport protocol uses static windows with window size 5. For a transmission rate of 100Kbps, determine the latency for sending the whole object. Recall the number of windows K=O/ WS), and there is K-1 stalled state (that is idle time gaps).2.Consider the following plot of TCP congestion window size as a function of time.Fill in the blanks as follow:a) The initial value of Threshold at the first transmission round is ____. b) The value of Threshold at the 11st transmission round is ____. c) The value of Threshold at the 21st transmission round is ____. d) After the 9th transmission round, segment loss detected by ____.(A) Timeout (B) Triple duplicate ACKe) After the 19th transmission round, segment loss detected by ____.(A) Timeout (B) Triple duplicate ACKf) During ____ transmission round, the 18th segment is sent.0 00 Congestion window size Transmission round3.Consider the TCP reliable data transfer in the given graph. If in Segment 1’s Sequence number =10,data=“AC〞, please fill in the following blanks.a)In Segment 2, ACK number=____;b)In Segment 3, Sequence number =____; data=“0123456789”c)If there are some bits corrupted in segment 3 when it arrives Host B, then the ACKnumber in Segment 5 is ____; and the ACK number in Segment 6 is ____.12345674. The client A wants to request a Web page from Server B. Suppose the URL of the page is 172.16.0.200/experiment, and also it wants to receive French version of object.The time-sequence diagram is shown below, please fill in the blanks.12345Packet① to Packet③ are TCP connection’s segment, then:Packet ①: SYN flag bit= aACK flag bit= bSequence number= 92Packet ②: SYN flag bit=1ACK flag bit= cSequence number=100Packet ③: SYN flag bit= dACK flag bit=1Sequence number= e5. Consider sending an object of size O=100 Kbytes from server to client. Let S=536 bytes and RTT=100msec. Suppose the transport protocol uses static windows withwindow size W.(1) For a transmission rate of 25 kbps, determine the minimum possible latency. Determine the minimum window size that achieves this latency. (2) Repeat (1) for 100 kbps.6. Consider the following plot of TCP congestion window size as a function of time. Please fill in the blanks as below.a) The initial value of Threshold at the first transmission round is____.b) The value of Threshold at the 11th transmission round is_____.c) The value of Threshold at the 21st transmission round is_____.d) After the 9th transmission round, _____ occurs. 14 18 26 30 0 2 6 4 8 10 12 16 20 22 24 28 32 Congestion window size Transmission round 4 8 12 16e) After the 19th transmission round, ____ are detected.。
计算机网络专业词汇中英对照

《计算机网络》中英文对照Chapter 1End system P28 端系统Modem P29 调制解调器(俗称:猫)Base station P29 基站Communication link P30 通信链路Physical media P30 物理介质Coaxial cable P30 同轴电缆Fiber optics P30 光纤Radio spectrum P30 射频频谱Transmission rate P30 传输速率Packets P30 (数据)包,或分组Routers P30 路由器Link-layer switches P30 链路层交换机Path P30 路径ISP (Internet Service Provider) P30 网络服务提供商TCP (Transmission Control Protocol) P31 传输控制协议IP ( Internet Protocol) P31 网际协议Intranets P31 内网API (Application Programming Interface) P32 应用程序编程接口Network edge P35 网络边缘Access Networks P38 接入网Ethernet P42 以太网Network core P48 网络核心Circuit Switching P50 电路转换Packet Switching 分组交换FDM (frequency-division multiplexing) P50 频分多路复用TDM (time-division multiplexing) P50 时分多路复用Statistical Multiplexing 统计复用Store-and-forward 存储转发Queuing delays P53 排队延迟Transmission delay P60 传输延迟,或发送延迟Propagation delay P60 传播延迟Throughput P59 吞吐量Internet backbone P57 骨干网Delay P59 延迟,或时延Loss P59 丢包Packet-Switched Network P59 分组交换网络Nodal processing delay P60 节点处理延迟End-to-end delay P66 端到端延迟Instantaneous throughput P68 瞬时吞吐量Network interface card P74 网络接口卡(即网卡)Message P75 消息,或报文Segment P75 (报文)段Datagram P75 数据报Frames P75 帧Packet sniffer P82 数据包监听器Protocol Stack 协议栈Peer entities 对等实体Chapter 2 应用层Server farm P110 服务器集群Infrastructure P110 基础设施,或基础架构Self-scalability P111 自扩展性Timing P114 实时性Bandwidth-sensitive applications P115带宽敏感应用Connection-oriented service P117 面向连接的服务Directory service P121 目录服务Base HTML 基本HTML文件Stateless protocol P124 无状态协议RTT (round-trip time ) P126 往返时间Web proxy caches P128 网页代理缓存Status line P130 状态行Out-of-band P141 (频)带外(的)In-band P141 带内(的)User agents P144 用户代理Mail servers P144 邮件服务器Pull protocol P148 拉式协议Push protocol p148 推式协议Host aliasing P158 主机别名Canonical hostname P158 规范主机名Mail server aliasing P158 邮件服务器别名Load distribution P158 负载分配Top-level domain (TLD) servers P161 顶级域名服务器Authoritative DNS servers P161 权威域名服务器Iterative queries P168 迭代查询Resource records (RRs) P165 资源记录Overlay network P179 覆盖网Nonpersistent HTTP 非持久HTTP,或非坚持HTTP Persistent HTTP 持久性HTTP,或坚持的HTTP Peer-to-Peer (P2P) Network 对等网络Socket programming 套接字编程Chapter 3 传输层Multiplexing and demultiplexing P226 复用与分用Unidirectional data transfer P241 单向数据传送Finite-state machine (FSM) P242 有限状态机Positive acknowledgments P243 肯定确认Negative acknowledgments P243 否定确认Countdown timer P250 (倒数)计时器Cumulative acknowledgment P258 累积确认Receive buffer P269 接收缓冲区,或接收缓存Resource-management cells 资源管理单元Source (port number) 源端口号Destination (port number) 目的端口号Checksum 校验与Pipelined protocols 流水线(型)协议Go-back-N 回退NSelective Repeat 选择重传Timeout (定时器)超时Fast Retransmit 快速重传Flow Control 流量控制Three way handshake 三次握手sequence number 序列号(简写为seq)acknowledgement number 确认号(简写为ack;注意与大小的ACK不同)Congestion Control 拥塞控制additive increase, multiplicative decrease 加性增乘性减Slow Start 慢启动congestion-avoidance 拥塞避免fast recovery 快速恢复duplicate (ACK) 冗余(ACK)Random Early Detection 随机早期检测Chapter 4 网络层Forwarding table P338 转发表Virtual-circuit networks P343 虚电路网络Datagram networks P343 数据报网络Signaling message P346 信令报文Content Addressable Memory P354 内容可寻址存储器Crossbar switch P356 纵横开关Active queue management 主动队列管理Head-of-the-line (HOL) 队头Classless interdomain routing (CIDR) P371 无类域间路由Plug-and-play P376 即插即用Anycast P386 任播Interior gateway protocols P414 内部网关协议Routing information Protocol P414 路由信息协议(RIP)Open shortest Path First OSPF P414 开放最短路径优先Area border routers P419 区域边界路由器Sequence-number-controlled flooding P430 序列号控制的洪泛,或带序列号的受控洪泛Reverse path forwarding (RPF) P431 逆向路径转发Rendezvous point P433 汇聚点Longest prefix matching 最长前缀匹配Scheduling 调度Fragmentation 分片,或分段Fragment Offset 报文段偏移量Network Address Translation (NAT) 网络地址转换NAT traversal NAT穿越Multicast 组播,或多播Unicast 单播Tunneling 隧道技术Link-State Routing Algorithm 链路状态路由算法Distance Vector Routing Algorithm 距离向量路由算法Count to Infinity Problem 无穷计数问题Hierarchical Routing 分层路由autonomous systems 自治系统BGP (Border Gateway Protocol) 边界网关协议in-network duplication 网内复制broadcast storm 广播风暴spanning tree 生成树redundant packets 冗余数据包Chapter 5 数据链路层,或链路层Broadcast channels P461 广播信道Trailer fields P464 尾部字段Link access P464 链路接入,或链路访问Network interface card P466 网络接口卡(即网卡)Parity checks P469 奇偶校验Forward error correction (FEC) P471 前向纠错Cyclic Redundancy Check 循环冗余校验Polynomial code P472 多项式码(即CRC码)Multiple access P475 多路接入Random access protocols P477 随机接入协议CSMA/CD P484 带冲突检测的载波侦听多路访问CSMA/CA 带冲突避免的载波侦听多路访问Token passing protocol P487 令牌传递协议ARP P491 地址解析协议Preamble P497 前导(字段)Exponential backoff P502 指数回退,或指数退避Repeater P504 中继器Virtual-channel identifier P520 虚拟信道标识Cell-loss priority P520 信元丢失优先权Label-switched router P524 标签交换路由器Framing (封装)成帧error detection 误差检测,或检错Channel Partitioning 信道分割式(MAC协议)Taking turns MAC protocol 轮流式MAC协议Collision 冲突,或碰撞Time Slot 时隙Slotted ALOHA 时隙ALOHAUnslotted ALOHA 无时隙ALOHA Nonpersistent CSMA 非坚持CSMA1-persistent CSMA 1坚持CSMAp-persistent CSMA p坚持CSMAToken Ring 令牌环(Wireless) LAN (无线)局域网Hub 集线器Collision domain 冲突域Bridge 网桥。
chapter3-计算机网络技术基础(第3版)-田庚林-清华大学出版社

地址分配:
路由器A的E0端口:202.3.5.1 255.255.255.224
pca1:
202.3.5.2 255.255.255.224
pca2:
202.3.5.3 255.255.255.224
…
pca15:
202.3.5.16 255.255.255.224
路由器A的E1端口:202.3.5.33 255.255.255.224
第3章 计算机网络中的通信地址与路由
3.1 计算机网络中的地址种类
3.1.1 物理地址
物理地址是标识网络内计算机的唯一地址 是集成在网卡上的48位二进制数编号 使用16进制数书写,如:00:5b:03:5e:3f: 0b 或:005b.035e.3f0b MAC地址
以太网卡为TCP/IP协议网络传输IP报文 时使用MAC地址的示意图
0011000000000001 0000000001110011 0000000000000000 0010111100111100 0000001010111011 0000000000011111 1111000000101000 0001110001011011
➢冒分十六进制格式为:
3001:0073:0000:2F3C:02BB:001F:F028:1C5B ➢去除前导无效0位后可写成:
3.3 子网与子网掩码Mask
3.3.1 子网的概念
在一个网络地址内划分出的网络 划分子网时需要占用原来的主机编号字段
3.3.2 IPv4子网掩码Mask
使用子网之后用来计算网络地址的工具 在Mask中,二进制位为“1”的位表示网络编 号部分;二进制位为“0”的位表示主机编号 部分 网络地址计算:
Mask表示方法: 200.100.120.28 255.255.255.224 200.100.120.28/27
计算机网络_中英文名词术语对照表
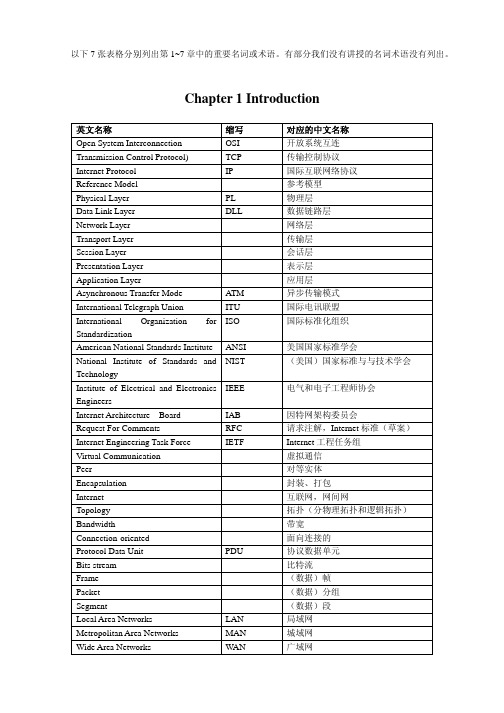
Advanced Data Communication Control
Procedure
High-level Data Link Control
Point-to-Point Protocol
Link Control Protocol
Network Control Protocol
缩写 CRC
PAR ARQ
LAN
Metropolitan Area Networks
MAN
Wide Area Networks
WAN
对应的中文名称 开放系统互连 传输控制协议 国际互联网络协议 参考模型 物理层 数据链路层 网络层 传输层 会话层 表示层 应用层 异步传输模式 国际电讯联盟 国际标准化组织
美国国家标准学会 (美国)国家标准与与技术学会
Physical layer coding violations
Hamming Code
Hamming Distance
Even
Odd
Parity bit
Codeword
Finite state machine models
Petri net models
Synchronous Data Link Control
缩写 MAC CSMA CSMA/CD MACA
TDR
FE FDDI GE LLC
VLAN NIC
对应的中文名称 多路访问协议 介质访问控制 纯 ALOHA 协议 分槽 ALOHA 协议 载波侦听多路访问 带冲突检测的载波侦听多路访问 避免冲突的多路访问 冲突窗口 位图协议 二进制倒计数 适应树搜索协议 时域反射计 曼侧斯特编码 差分曼侧斯特编码 以太帧格式 二进制指数回退算法 快速以太网(100M) 光纤分布式数据接口 吉比特以太网(1G,1000M) 逻辑链路控制 透明网桥 交换机 逆向地址学习 泛洪/广播 转发 丢弃 过滤 冲突域 生成树 虚拟局域网 网络接口卡(网卡) 存储转发交换 直通交换 无分片交换
计算机网络(第四版)课后习题(英文)+习题答案(中英文)

ANDREW S. TANENBAUM 秒,约533 msec.----- COMPUTER NETWORKS FOURTH EDITION PROBLEM SOLUTIONS 8. A collection of five routers is to be conn ected in a poi nt-to-poi nt sub net.Collected and Modified By Yan Zhe nXing, Mail To: Betwee n each pair of routers, the desig ners may put a high-speed line, aClassify: E aEasy, M ^Middle, H Hard , DaDeleteGree n: Importa nt Red: Master Blue: VI Others:Know Grey:—Unnecessary ----------------------------------------------------------------------------------------------ML V Chapter 1 In troductio nProblems2. An alter native to a LAN is simply a big timeshari ng system with termi nals forall users. Give two adva ntages of a clie nt-server system using a LAN.(M)使用局域网模型可以容易地增加节点。
如果局域网只是一条长的电缆,且不会因个别的失效而崩溃(例如采用镜像服务-------------------------------------------器)的情况下,使用局域网模型会更便宜。
计算机网络第三章作业参考答案

Chapter3 THE DATA LINK LAYER2.The following data fragment occurs in the middle of a data stream for which thebyte-stuffing algorithm described in the text is used: A B ESC C ESC FLAG FLAG D. What is the output after stuffing?Answer:A B ESC C ESC FLAG FLAG D ==> A B ESC ESC C ESC ESC ESC FLAG ESC FLAG D3.What is the maximum overhead in byte-stuffing algorithm?Answer :This a frame delimited by flag bytes. (Ignore the header and trailer)Suppose that there is x bytes in payload field, and the worst case is that all of them are flag bytes or ESC, there should be 2x bytes in total. So the max overhead in byte-stuffing should be: 2+x x+1+111111lim=lim =lim +=+lim =2+2x 2x+122x+122x+12x x x x →∞→∞→∞→∞()()()() Or: (from 袁子超)if it has n bytes to send, and has m ESC. So the overhead is :.If the n bytes are all ESC, the overhead is maximum as :FLAG FLAG Payload field4.When bit stuffing is used, is it possible for the loss, insertion, or modification of a single bit to cause an error not detected by the checksum? If not, why not? If so, how? Does the checksum length play a role here?Answer:It is possible. Suppose that the original text contains the bit sequence 01111110 as data. After bit stuffing, this sequence will be rendered as 011111010. If the second 0 is lost due to a transmission error, what is received is 01111110, which the receiver sees as end of frame. It then looks just before the end of the frame for the checksum and verifies it. If the checksum is 16 bits, there is 1 chance in 216 that it will accidentally be correct, leading to an incorrect frame being accepted. The longer the checksum, the lower the probability of an error getting through undetected, but the probability is never zero.6.To provide more reliability than a single parity bit can give, an error-detecting coding scheme uses one parity bit for checking all the odd-numbered bits and a second parity bit for all the even-numbered bits. What is the Hamming distance of this code?Answer:Any single-bit error in the odd-numbered bits could change parity bit. It’s the same as the even-numbered bits. And both two errors occur in the odd-numbered bits or in the even-numbered bits will not change the parity bit. That is to say , this code could only detect single-bit errors, which means the Hamming distance is 2.7.An 8-bit byte with binary value 10101111 is to be encoded using an even-parity Hamming code. What is the binary value after encoding?According to rr m 2)1(≤++,m=8 r=4P1=B1⊕B3⊕B5⊕B7⊕B9⊕B11 =∑(0,1,0,0,1,1)=1P2=B2⊕B3⊕B6⊕B7⊕B10⊕B11=∑(0,1,1,0,1,1)=0P3=B4⊕B5⊕B6⊕B7 ⊕B12 =∑(0,0,1,0,1)=0P4=B8⊕B9⊕B10⊕B11⊕B12 =∑(0,1,1,1,1)=0So, Hamming code is: 10100100111113.Suppose that a message 1001 1100 1010 0011 is transmitted using Internet Checksum (4-bit word). What is the value of the checksum?Solution:100111001010+ 0011---------------------------------0010 (have 2 added bit),so:+1+1----------------------------------0100So, the Internet checksum is the ones complemnet of 0100, or 1011.14.What is the remainder obtained by dividing 751x x ++by the generator polynomial 31x +?42375745452424211111x x xx x x x x x x x x x x x xx x ++++++++++++++The remainder is 21x x ++.15.A bit stream 10011101 is transmitted using the standard CRC method described in the text. Thegenerator polynomial is ,. Show the actual bit string transmitted. Suppose that the third bit from the left is inverted during transmission. Show that this error is detected at the receiv er’s end. Give an example of bit errors in the bit string transmitted that will not be detected by the receiver.Solution:(1)→100110011101000 mod 1001 = 100The actual bit string transmitted: 10011101000+100=10011101100(2) The bit string receiver receives :10011101100→10111101100 10111101100 mod 1001 = 100 ≠ 0 →error!(3)example: 10011101100→1001111010110011110101 mod 1001 = 0So the receiver may think that the received bit string is right while it ’s wrong in fact.Data link protocols almost always put the CRC in a trailer than in a header. Why? Answer:CRC is calculated during sending. It could be appended to the data bit string as soon as the last data bit is send to the path. If it is put in the header, it must scan the whole frame in order to calculate CRC. It means that we should dispose the code 2 times. And CRC in the trailer could help to drop the half time.Or: (from 袁子超)CRC calculate during transmission. Once the last data sent out line, immediately put CRC code attached to the output stream from the back. If put CRC on the head of the frame, then we should check the frame to calculate CRC before sending. So that each byte has to deal with two times, the first is to calculate the check code, second times to send. Put CRC in the tail of the processing time can be halved.20.A 3000-km-long T1 trunk is used to transmit 64-byte frames using protocol 5. If the propagat ion speed is 6 μsec/km, how many bits should the sequence numbers be? Solution:delay= 3000-km* 6 μsec/km=18msBecause the bandwidth of T1 trunk = 1.544Mbps ,so:send time=64*8bits/1.544Mbps=0.33msthe time of send a frame and receive the acknowledge frame=18ms+0.33ms+18ms=36.33msthe number of frames: 36.33ms/0.33ms=11064=≤110≤=128sequence number should be 7 bitsFrames of 1000 bits are sent over a 1-Mbps channel using a geostationary satellite whose propagation time from the earth is 270 msec. Acknowledgements are always piggybacked onto data frames. The headers are very short. Three-bit sequence numbers are used. What is the maximum achievable channel utilization for(a) Stop-and-wait?(b) Protocol 5?(c) Protocol 6?Solution:Time for send a frame is: 1000bits/(1Mbps)=1msRound trip time: R=270ms*2=540msIt takes R+2=542ms to send a frame (be acknowledged).Therefore, a transmission cycle is 542ms. If the 542ms can send w frame, as a result of each frame transmission time is 1ms, the channel utilization rate is w/542.Three-bit sequence numbers are used, so the max window for (a),(b),(c) are :(a):W=1(b)1<W≤-1=7 →W=7(c)W≤=4→W=4So line utilization rate is: (a) 1*1ms/542ms * 100%=0.184%(b)7*1ms/542ms * 100%=1.292%(c)4*1ms/542ms*100%=0.738%30.Consider an error-free 64-kbps satellite channel used to send 512-byte data frames in one direction, with very short acknowledgements coming back the other way. What is the maximum throughput for window sizes of 1, 7, 15, and 127? The earth-satellite propagation time is 270 msec.Solution:Time for send a frame: 512*8bits/64kbps=64msSo, a transmission cycle: T=270ms*2+64ms=604ms and transmission window is:604ms/64ms=9.4,that’s mean: if w>9 the channel is full, the throughput cannot rise,(1)W=1: throughout=512*8b/604ms=6781bps=6.78kbps(2)W=7: throughout=7*512*8b/604ms=47.47kbps(3)(4) 15>9&&127>9, so throughout= 64kbps32.Give at least one reason why PPP uses byte stuffing instead of bit stuffing to prevent accidental flag bytes within the payload from causing confusion.Answer:(1) PPP was clearly designed to be implemented in software, not in hardware as HDLC nearly always is. With a software implementation, working entirely with bytes is muc h simpler than working with individual bits.(2) PPP was designed to be used with modems, and modems accept and transmit data in units of 1 byte, not 1 bit.33. What is the minimum overhead to send an IP packet using PPP? Count only the overhead introduced by PPP itself, not the IP header overhead. What is the maximum overhead?Solution:the PPP full frame format for unnumbered mode is:And Address and control could be ignored if sender and receiver have approve it.The minimum overhead=1+1+2+1=5bytesThe maximum overhead=1+1+1+2+4+1=10bytes。
计算机网络教程自顶向下方法选择题及答案Chapt3TransportLayer-QUIZZ

Chapter 3 Transport Layer1.One of the main duties of the transport layer is to provide ____________ communication.A) node-to-nodeB) host-to-hostC) process-to-processD) None of the choices are correct2.A client program normally uses ____________ port number. A server program normally uses __________ port number.A) a well-known; an ephemeralB) an ephemeral; a well-knownC) a private; a well-knownD) None of the choices are correct3.A socket address is a combination of __________.A) A MAC address and a logical addressB) A MAC address and a port numberC) a user-specific address and a logical addressD) None of the choices are correct4.______________ means accepting items from more than one source. ______________ means delivering items to more than one source.A) Demultiplexing; MultiplexingB) Multiplexing; DemultiplexingC) Encapsulation; DecapsulationD) Pulling; Pushing5.________ means the producer delivers the items when they are produced. _______ means the consumer takes the items when it is ready to do so.A) Pushing; pullingB) Pulling; pushingC) Forwarding; acceptingD) None of the choices are correct6.In the stop-and-wait protocol, the maximum send window size is ______ and the maximum receive window size is _______ where m is the number of bits in the sequence.A) 1; 1B) 2m; – 1C) 1; 2mD) 2m; 2m7.In the Go-Back-N protocol, the maximum send window size is ______ and the maximum receivewindow size is _______, where m is related to the number of bits in the sequence. number.A) 1; 1B) 1; 2mC) 2m – 1; 1D) 2m – 1; 2m – 18.In the selective-repeat protocol, the maximum send window size is ______ and the maximum receive window size is _______, where m is the number of bits in the sequence.A) 1; 1B) 1; 2m – 1C) 2m – 1; 1D) 2m – 1; 2m – 19.UDP is a ________________ transport protocol.A) connectionless, reliableB) connection-oriented, unreliableC) connectionless, unreliableD) None of the choices are correct10.UDP is an acronym for _______.A) User Delivery ProtocolB) User Datagram ProcedureC) User Datagram ProtocolD) None of the choices are correct11.At the transport layer, to define the processes, we need two identifiers called ____________.A) logical addressesB) physical addressesC) port addressesD) None of the choices are correct12.The ports ranging from 0 to 1,023 are called the ___________ ports. The ports ranging from 1,024 to 49,151 are called ___________ ports. The ports ranging from 49,152 to 65,535 are called the ___________ ports.A) well-known; registered; dynamic or privateB) registered; dynamic or private; well-knownC) private or dynamic; well-known; registeredD) private or dynamic; registered; well-known13.UDP and TCP are two protocols at the ___________ layer.A) data linkB) networkC) transportD) application14.Which of the following functions are performed by UDP?A) process-to-process communicationB) host-to-host communicationC) node-to-node communicationD) None of the choices are correct15.A port number is _______ bits long.A) 8B) 16C) 32D) 6416.Which of the following does UDP provide?A) flow controlB) connection-oriented deliveryC) error controlD) None of the choices are correct17.The source port number on the UDP user datagram header defines _______.A) the sending computerB) the receiving computerC) the process running on the sending computerD) None of the choices are correct18.To use the services of UDP, we need ________ socket addresses.A) fourB) twoC) threeD) None of the choices are correct19.UDP packets are called __________ .A) user datagramsB) segmentsC) framesD) None of the choices are correct20.UDP packets have a fixed-size header of _______ bytes.A) 16B) 8C) 40D) 3221.TCP is a __________ protocol.A) byte-orientedB) message-orientedC) block-orientedD) None of the choices are correct22.TCP groups a number of bytes together into a packet called a ___________.A) user datagramB) segmentC) datagramD) None of the choices are correct23.TCP is a(n) ___________ protocol.A) connection-orientedB) connectionlessC) both connection-oriented and connectionlessD) None of the choices are correct24.TCP is a(n) _______ transport protocol.A) unreliableB) best-effort deliveryC) reliableD) None of the choices are correct25.TCP uses _________________ to check the safe and sound arrival of data.A) an acknowledgment mechanismB) out-of-band signalingC) the services of another protocolD) None of the choices are correct26.The bytes of data being transferred in each connection are numbered by TCP. The numbering starts with a __________________.A) 0B) 1C) randomly generated numberD) None of the choices are correct27.In TCP, the sequence number for each segment is the number of the _______ byte (virtual byte) carried in that segment.A) firstB) lastC) middleD) None of the choices are correct28.Communication in TCP is ___________.A) simplexB) half-duplexC) full-duplexD) None of the choices are correct29.In TCP, the value of the acknowledgment field in a sent segment defines the sequence number related to the ______ byte a party expects to receive next.A) firstB) lastC) nextD) None of the choices are correct30.The inclusion of the checksum in the TCP segment is ________.A) optionalB) mandatoryC) depends on the type of dataD) None of the choices are correct31.In TCP, a SYN segment consumes _____ sequence number(s).A) noB) oneC) twoD) None of the choices are correct32.In TCP, a SYN + ACK segment consumes _____ sequence numbers.A) noB) threeC) twoD) one33.In TCP, an ACK segment, if carrying no data, consumes ______ sequence number(s).A) noB) oneC) twoD) None of the choices are correct34.The connection establishment procedure in TCP is susceptible to a serious security problem called the _________ attack.A) ACK floodingB) FIN floodingC) SYN floodingD) None of the choices are correct35.The SYN flooding attack belongs to a group of security attacks known as a _____ attack.A) denial of serviceB) replayC) man-in-the middleD) None of the choices are correct36.In TCP, a FIN segment consumes ____ sequence numbers if it does not carry data.A) twoB) threeC) noD) one37.In TCP, a FIN + ACK segment consumes _____ sequence number(s) if it does not carry data.A) twoB) threeC) oneD) no38.In TCP, one end can stop sending data while still receiving data. This is called a ______ termination.A) half-closeB) half-openC) full-closeD) None of the choices are correct39.TCP sliding windows are __________ oriented.A) packetB) segmentC) byteD) None of the choices are correct40.In TCP, the size of the send window is the ________ of rwnd and cwnd.A) maximumB) sum ofC) minimumD) None of the choices are correct41.In TCP, the window should not be _________.A) openedB) closedC) shrunkD) slide42.In TCP, the receiver can temporarily shut down the window; the sender, however, can always send a segment of _____ byte(s) after the window is shut down.A) tenB) zeroC) oneD) None of the choices are correct43.A serious problem can arise in the sliding window operation when either the sending application program creates data slowly or the receiving application program consumes data slowly, or both. This problem is called the ______.A) silly window syndromeB) unexpected syndromeC) window bugD) None of the choices are correct44.Nagle's algorithm can solve the silly window syndrome created by the _________.A) senderB) receiverC) both sender and receiverD) None of the choices are correct45.Clark's solution can solve the silly window syndrome created by the _________.A) senderB) receiverC) both sender and receiverD) None of the choices are correct46.Delayed acknowledgment can solve the silly window syndrome created by the _________.A) senderB) receiverC) both sender and receiverD) None of the choices are correct47.In TCP, an ACK segments that carry no data consumes _______ sequence number(s).A) noB) oneC) twoD) None of the choices are correct48.In modern implementations of TCP, a retransmission occurs if the retransmission timer expires or ________ duplicate ACK segments have arrived.A) oneB) twoC) threeD) None of the choices are correct49.In TCP, ________ retransmission timer is set for an ACK segment.A) oneB) a previousC) noD) None of the choices are correct50.In TCP, there can be ______ RTT measurement(s) in progress at any time.A) twoB) only oneC) severalD) None of the choices are correct51.We need to multiply the header length field by _______ to find the total number of bytes in the TCP header.A) 2B) 4C) 6D) None of the choices are correct52.In TCP, urgent data requires the urgent pointer field as well as the URG bit (to be set) in the _______ field.A) controlB) offsetC) sequence numberD) None of the choices are correct53.In TCP, if the ACK value is 200, then byte _______ has been received successfully.A) 199B) 200C) 201D) None of the choices are correct54.In TCP, the _______ timer prevents a long idle connection between two TCPs.A) retransmissionB) persistenceC) keepaliveD) None of the choices are correct55.In TCP, the _______ timer is needed to handle the zero window-size advertisement.A) retransmissionB) persistenceC) keepaliveD) None of the choices are correct56.In TCP, Karn's algorithm is used in calculations by the _______ timer.A) retransmissionB) persistenceC) keepaliveD) None of the choices are correct57.In TCP, a special segment called a probe is sent by a sending TCP when the _______ timer goes off.A) transmissionB) persistenceC) keepaliveD) None of the choices are correct58.__________ control refers to the mechanisms and techniques to keep the load below the capacity.A) flowB) errorC) congestionD) None of the choices are correct59.In TCP's ________ algorithm the size of the congestion window increases exponentially until it reaches a threshold.A) congestion avoidanceB) congestion detectionC) slow startD) None of the choices are correct60.In TCP's __________ algorithm the size of the congestion window increases additively until congestion is detected.A) congestion avoidanceB) congestion detectionC) slow startD) None of the choices are correct61.________ treats the two signs of congestion detections, timeout and three duplicate ACKs, in the same way.A) Taho TCPB) Reno TCPC) new Reno TCPD) None of the choices are correct62.In ______ TCP, when the connection is established, TCP starts the slow start algorithms and sets the ssthresh variable to a pre-agreed value (normally 64 or 128 kilobytes) and the cwnd variable to 1 MSS.A) Taho TCPB) Reno TCPC) new Reno TCPD) None of the choices are correct63.The ___________ added a new state to the congestion control FSM, called the fast recovery state.A) Taho TCPB) Reno TCPC) new Reno TCPD) None of the choices are correct64.The ___________ treated the two signals of congestion, timeout and arrival of three duplicate ACKs, differently.A) Taho TCPB) Reno TCPC) new Reno TCPD) None of the choices are correct65.The __________ state in Reno TCP is a state somehow between the slow start and the congestion avoidance states.A) congestion avoidanceB) congestion detectionC) slow recoveryD) None of the choices are correct66.In the Reno TCP, when TCP enters the fast recovery, if duplicate ACKs continue to come, TCP ____________________________________.A) stays in this state, but the cwnd grows additivelyB) stays in this state, but the cwnd grows exponentiallyC) moves to slow start stateD) moves to the congestion avoidance state but deflate the size of the cwnd to ssthresh value67.In the Reno TCP, when TCP enters the fast recovery, if a timeout occurs, TCP ____________________________________.A) stays in this state, but the cwnd grows additivelyB) stays in this state, but the cwnd grows exponentiallyC) moves to slow start stateD) moves to the congestion avoidance state but deflate the size of the cwnd to ssthresh value68.In the Reno TCP, when TCP enters the fast recovery, if a new (non duplicate) ACK arrives TCP.____________________________________.A) stays in this state, but the cwnd grows additivelyB) stays in this state, but the cwnd grows exponentiallyC) moves to slow start stateD) moves to the congestion avoidance state but deflate the size of the cwnd to ssthresh value69.A later version of TCP, called ______ TCP, made an extra optimization on the _______ TCP.A) New Reno; RenoB) New Taho; TahoC) New Reno; TahoD) New Taho; Reno70.In the slow start algorithm, the size of the congestion window grows ______________ until ___________________.A) exponentially; it reaches a thresholdB) exponentially; congestion is detectedC) additively; it reaches a thresholdD) additively; congestion is detected71.In the congestion avoidance algorithm, the size of the congestion window grows ______________ congestion is detected.A) exponentially; it reaches a thresholdB) exponentially; congestion is detectedC) additively; it reaches a thresholdD) additively; congestion is detected72.The congestion window size, after it passes the initial slow start state, follows a saw tooth pattern called _________________________________.A) exponential increase, additive decreaseB) additive increase, exponential decreaseC) multiplicative increase, additive decreaseD) additive increase, multiplicative decreaseCBDBA ACDCC CACAB DCBAB ABACA CACCB BDACA DCACC CCAAB BACCB BAACB ABCCA AABBD BCDAA DD.。
计算机网络英文题库附答案chapter定稿版

计算机网络英文题库附答案c h a p t e r精编W O R D版IBM system office room 【A0816H-A0912AAAHH-GX8Q8-GNTHHJ8】Chapter 1 Computer Networks and the Internet 1.The ( ) is a worldwide computer network, that is, a network that interconnects millions of computing devices throughout the world.ppt3A public InternetB IntranetC switch netD television net2.Which kind of media is not a guided media ( )A twisted-pair copper wireB a coaxial cableC fiber opticsD digital satellite channel3.Which kind of media is a guided media ( )A geostationary satelliteB low-altitude satelliteC fiber opticsD wireless LAN4.The units of data exchanged by a link-layer protocol are called ( ).A FramesB SegmentsC DatagramsD bit streams5.Which of the following option belongs to the circuit-switched networks ( )A FDMB TDMC VC networksD both A and B6.( )makes sure that neither side of aconnection overwhelms the other side bysending too many packets too fast.A Reliable data transferB Flow controlC Congestion controlD Handshaking procedure7.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Store-and-forward transmissionB FDMC End-to-end connectionD TDM8.Datagram networks and virtual-circuit networks differ in that ( ).A datagram networks are circuit-switchednetworks, and virtual-circuit networks arepacket-switched networks.B datagram networks are packet-switchednetworks, and virtual-circuit networks arecircuit-switched networks.C datagram networks use destinationaddresses and virtual-circuit networks useVC. numbers to forward packets towardtheir destination.D datagram networks use VC. numbersand virtual-circuit networks use destinationaddresses to forward packets toward theirdestination.9.In the following options, which one is not a guided media ( )A twisted-pair wireB fiber opticsC coaxial cableD satellite10.Processing delay does not include the time to ( ).A examine the packet’s headerB wait to transmit the packet onto the linkC determine where to direct the packetD check bit-error in the packet11.In the following four descriptions, which one is correct ( )A The traffic intensity must be greaterthan 1.B The fraction of lost packets increases asthe traffic intensity decreases.C If the traffic intensity is close to zero,the average queuing delay will be close tozero.D If the traffic intensity is close to one, theaverage queuing delay will be close to one.12.The Internet’s network layer isresponsible for moving network-layerpackets known as ( ) from one host toanother.A frameB datagramC segmentD message13.The protocols of various layers are called ( ).A the protocol stackB TCP/IPC ISPD network protocol14.There are two classes of packet-switched networks: ( ) networks and virtual-circuitnetworks.A datagramB circuit-switchedC televisionD telephone15.Access networks can be loosely classified into three categories: residential access,company access and ( ) access.A cabledB wirelessC campusD city areaQuestion 16~17Suppose, a is the average rate at which packets arrive at the queue, R is the transmission rate, and all packets consist of L bits, then the traffic intensity is ( 16 ), and it should no greater than ( 17 ).16.A LR/aB La/RC Ra/LD LR/a 17.A 2B 1C 0D -118.In the Internet, the equivalent concept to end systems is ( ).A hostsB serversC clientsD routers19.In the Internet, end systems are connected together by ( ).A copper wireB coaxial cableC communication linksD fiber optics20.End systems access to the Internet through its ( ).A modemsB protocolsC ISPD sockets21.End systems, packet switches, and other pieces of the Internet, run ( ) that controlthe sending and receiving of informationwithin the Internet.A programsB processesC applicationsD protocols22.There are many private networks, such as many corporate and government networks,whose hosts cannot exchange messageswith hosts outside of the private network.These private networks are often referredto as ( ).A internetsB LANC intranetsD WAN23.The internet allows ( ) running on its end systems to exchange data with each other.A clients applicationsB server applicationsC P2P applicationsD distributed applications24.The Internet provides two services to its distributed applications: a connectionlessunreliable service and () service.A flow controlB connection-oriented reliableC congestion controlD TCP25.It defines the format and the order of messages exchanged between two or morecommunicating entities, as well as theactions taken on the transmission and/orreceipt of a message or other event. Thesentence describes ( ).A InternetB protocolC intranetD network26.In the following options, which does not define in protocol ( )A the format of messages exchangedbetween two or more communicatingentitiesB the order of messages exchangedbetween two or more communicatingentitiesC the actions taken on the transmission ofa message or other eventD the transmission signals are digitalsignals or analog signals27.In the following options, which is defined in protocol ( )A the actions taken on the transmissionand/or receipt of a message or othereventB the objects exchanged between communicating entitiesC the content in the exchanged messagesD the location of the hosts28.In the following options, which does not belong to the network edge ( )A end systemsB routersC clientsD servers29.In the following options, which belongs to the network core ( )A end systemsB routersC clientsD servers30.In the following options, which is not the bundled with the Internet’s connection-oriented service( )A reliable data transferB guarantee of the transmission timeC flow controlD congestion-control31.An application can rely on the connection to deliver all of its data without error andin the proper order. The sentencedescribes ( ).A flow controlB congestion-controlC reliable data transferD connection-oriented service32.It makes sure that neither side of aconnection overwhelms the other side bysending too many packets too fast. Thesentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer33.It helps prevent the Internet from enteringa state of gridlock. When a packet switchbecomes congested, its buffers canoverflow and packet loss can occur. Thesentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer34.The Internet’s connection-oriented service has a name, it is ( ).A TCPB UDPC TCP/IPD IP 35.In the following options, which service does not be provided to an application by TCP( )A reliable transportB flow controlC video conferencingD congestion control36.The Internet’s connectionless service is called ( ).A TCPB UDPC TCP/IPD IP37.In the following options, which does not use TCP()A SMTPB internet telephoneC FTPD HTTP38.In the following options, which does not use UDP( )A Internet phoneB video conferencingC streaming multimediaD telnet39.There are two fundamental approaches to building a network core, ( ) and packetswitching.A electrical current switchingB circuit switchingC data switchingD message switching40.In ( ) networks, the resources needed along a path to provide forcommunication between the end systemare reserved for the duration of thecommunication session.A packet-switchedB data-switchedC circuit-switchedD message-switched41.In ( ) networks, the resources are not reserved; a session’s messages use theresources on demand, and as aconsequence, may have to wait for accessto communication link.A packet-switchedB data-switchedC circuit-switchedD message-switched42.In a circuit-switched network, if each link has n circuits, for each link used by theend-to-end connection, the connectiongets ( ) of the link’s bandwidth for theduration of the connection.A a fraction 1/nB allC 1/2D n times43.For ( ), the transmission rate of a circuit is equal to the frame rate multiplied by thenumber of bits in a slot.A CDMAB packet-switched networkC TDMD FDM 44.( ) means that the switch must receive the entire packet before it can begin totransmit the first bit of the packet onto theoutbound link.A Queuing delayB Store-and-forward transmissionC Packet lossD Propagation45.The network that forwards packetsaccording to host destination addresses iscalled ( ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram46.The network that forwards packetsaccording to virtual-circuit numbers iscalled ( ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram47.In the following entries, which is not a kind of access network()A residential accessB company accessC wireless accessD local access48.Suppose there is exactly one packet switch between a sending host and a receivinghost. The transmission rates between thesending host and the switch and betweenthe switch and the receiving host are R1and R2, respectively. Assuming that theswitch uses store-and-forward packetswitching, what is the total end-to-enddelay to send a packet of length L (Ignorequeuing delay, propagation delay, andprocessing delay.) ( )A L/R1+L/R2B L/R1C L/R2D none of the above49.The time required to examine thepacket’s header and determine where todirect the packet is part of the ( ).A queuing delayB processing delayC propagation delayD transmission delay50.The time required to propagate from the beginning of the link to the next router is( ).A queuing delayB processing delayC propagation delayD transmission delay51.Consider sending a packet of 3000bits over a path of 5 links. Each link transmits at 1000bps. Queuing delays, propagation delay and processing delay are negligible. (6 points) (1).Suppose the network is a packet-switched virtual circuit network. VC setup time is 0.1 seconds. Suppose the sending layers add a total of 500 bits of header to each packet. How long does it take to send the file from source to destination?(2).Suppose the network is a packet-switched datagram network and a connectionless serviceis used. Now suppose each packet has 200 bitsof header. How long does it take to send the file?(3).Suppose that the network is a circuit-switched network. Further suppose that the transmission rate of the circuit between sourceand destination is 200bps. Assuming 0.02s setuptime and 200 bits of header appended to the packet, how long does it take to send the packet?So lution:(1).t=5*(3000+500)/1000+0.1=17.6s( 2).t=5*(3000+200)/1000=16s( 3).t=(3000+200)/200+0.02=16.02s。
计算机网络复习资料(杨庚_胡素君)

Chapter 1 概论1.计算机网络提供的主要功能?数据通信、资源共享、负载均衡、提高可靠性2.计算机网络的分类?覆盖范围分类:LAN、WAN、MAN按照数据通信和数据处理的功能分为:通信子网、资源子网3.常用的物理拓扑结构?总线型、星型、环型、树型、分布式结构1.OSI七层模型及各层功能?物理层、数据链路层、网络层、传输层、会话层、表示层、应用层1.在PH可采用防窃听技术来加强通信线路安全。
2.实现端到端应答,提供分组排序和流控。
在DL可采用通信保密机进行链路加密。
3.提供点对点的数据链路,在N可采用防火墙建立安全。
4.在T提供主机之间端到端的数据传送。
2.TCP/IP层次模型?网络接入层、互连网络层、传输层、应用层1.OSI七层模型及各层功能?在ISO的OSI模型中,实现端到端的应答、提供分组排序和流量控制功能的层是(1)。
提供建立、维护和拆除端到端连接的层是(2)。
为数据分组提供在网络中路由功能的是(3)。
传输层提供(4)的数据传送。
为网络层实体提供数据发送和接收功能与过程的是(5)。
(1)A. 1,2,3层 B. 2,3,4层 C. 3,4,5层 D. 4,5,6层(2)A. 物理层 B. 数据链路层 C. 会话层 D. 传输层(3)A. 物理层 B. 数据链路层 C. 网络层 D. 传输层(4)A. 主机之间 B. 网络之间 C. 数据链路之间 D. 物理链路之间(5)A. 物理层 B. 数据链路层 C. 网络层 D. 传输层2.TCP/IP层次模型?Chapter 2 物理层1.通信3个基本要素信源、信宿、信道2.编码、调制、解调、解码编码:数据→适合传输的数字信号调制:数字信号→适合传输的形式解调:接收波形→数字信号解码:数字信号→原始数据3.数字信道、模拟信道数字信道:数字传输,ADSL、ISDN、DDN、ATM、局域网模拟信道:模拟传输,CATV、无线电广播、电话拨号线路4.调制解调器数据:模拟数据数字数据信号:模拟信号数字信号信道:模拟信道数字信道5.PCM编码传输速度计算?模拟数据-量化-采样-编码-数字信号量化级别数*频率*采样次数6.RS-232CRS232C通信方式是Com接口RS232C的零调制解调器(采用交叉跳接信号线的链接电缆7.画比特流0011011001的差分曼彻斯特编码8.100baseT的物理层使用的编码方式?P120,4B/5B5.奈科斯特定理任意一个信号如果通过带宽为W(Hz)的理想低通滤波器,当每秒传输2W码元,就可实现无码元间干扰传输在理想的条件下,即无噪声有限带宽为W的信道,其最大的数据传输速率C(即信道容量)为: C = 2W log2 M,其中M是信号状态的个数。
计算机网络第四版(课后练习+答案)

计算机网络第四版(课后练习+答案)计算机网络第四版(课后练习+答案)Introduction:计算机网络是现代信息技术的基础,它涉及到计算机与计算机之间如何进行数据交换和通信。
《计算机网络第四版》是一本权威指南,提供了大量的课后练习和答案,帮助读者加强对计算机网络的理解。
本文将对《计算机网络第四版》课后练习和答案进行综述,以便读者更好地掌握网络通信的关键概念和原理。
Chapter 1: Introduction to Networking在第一章中,课后练习的内容涵盖了计算机网络的基本概念和发展历程。
学习者可以通过这些练习加深对网络通信的了解,例如描述计算机网络的基本组成部分、定义OSI模型的七层结构以及解释分组交换和电路交换的区别。
Chapter 2: Network Models第二章课后练习着重介绍了计算机网络的各种模型,包括OSI模型和TCP/IP模型。
练习题目涵盖了每个模型的层次结构和功能,同时还要求学习者能够比较这两个模型之间的异同点。
Chapter 3: Physical Layer and Media物理层和传输介质是计算机网络的基础,第三章课后练习起到了巩固和扩展这些概念的作用。
学习者将通过回答问题和解决实际情况的案例,深入理解诸如数据信号的调制和解调、传输介质的特性以及常见的物理层设备等内容。
Chapter 4: Data Link Layer数据链路层构建在物理层之上,并处理节点到节点之间的数据传输。
第四章的课后练习要求学习者熟练掌握数据链路层的基本概念,包括帧的封装和解封装、错误检测和纠正技术以及介绍局域网和广域网等。
Chapter 5: Network Layer网络层负责数据包的转发和路由选择,在第五章的练习题中,学习者需要回答关于IP地址的分配和路由表的设计的问题,深入理解网络层的功能和特性。
还会涉及到IP协议的各种细节,例如子网划分、地址转换和网络控制协议等。
Chapter 6: Transport Layer传输层提供端到端的可靠数据传输服务,第六章的课后练习通过设计案例和讨论问题的方式,帮助学习者掌握TCP和UDP协议的细节和应用场景。
(最新)思科网络第一学期1-5章中文测试题及答案

ENetwork Chapter 2 - CCNA Exploration: 网络基础知识(版本 4.0) 1在封装过程中,数据链路层执行什么操作?不添加地址。
添加逻辑地址。
添加物理地址。
添加进程的端口号。
2TCP/IP 网络接入层有何作用?路径确定和数据包交换数据表、编码和控制可靠性、流量控制和错误检测详细规定构成物理链路的组件及其接入方法将数据段划分为数据包3数据链路层封装添加的报尾信息有何主要功能?支持差错校验确保数据按照顺序到达确保送达正确目的标识本地网络中的设备帮助中间设备进行处理和路径选择4请参见图。
下列哪组设备仅包含终端设备?A、C、DB、E、G、HC、D、G、H、I、JD、E、F、H、I、JE、F、H、I J5OSI 模型各层从最高层到最低层的正确顺序如何?物理层、网络层、应用层、数据链路层、表示层、会话层、传输层应用层、物理层、会话层、传输层网络层、数据链路层、表示层应用层、表示层、物理层、会话层、数据链路层、传输层、网络层应用层、表示层、会话层、传输层、网络层、数据链路层、物理层表示层、数据链路层、会话层、传输层、网络层、物理层、应用层6下列哪三项陈述是对局域网(LAN) 最准确的描述?(选择三项)LAN 通常位于一个地域内。
此类网络由由一个组织管理。
LAN 中的不同网段之间一般通过租用连接的方式连接。
此类网络的安全和访问控制由服务提供商控制。
LAN 为同一个组织内的用户提供网络服务和应用程序访问。
此类网络的每个终端通常都连接到电信服务提供商(TSP)。
7第4 层端口指定的主要作用是什么?标识本地介质中的设备标识源设备和目的设备之间的跳数向中间设备标识过该网络的最佳路径标识正在通信的源终端设备和目的终端设备标识终端设备内正在通信的进程或服务8以下哪种特征正确代表了网络中的终端设备?管理数据流发送数据流重新定时和重新传输数据信号确定数据传输路径9请参见图示。
哪个术语正确判断出了包含于绿色区域中的设备类型?源终端传输中间10OSI 模型哪两层的功能与TCP/IP 模型的网络接入层相同?(选择两项)网络层传输层物理层数据链路层会话层11请参见图示。
Chapter 3 Foundation of Computer Network(计算机网络基础)

Key words: networking(网络技术),spreadsheet(电子 表格),share(共享),network(网络),message(信息), graphics(图形),fax machine(传真机),modem(调制解调 器),CD-ROM(只读光盘),data storage equipment(数据存储 设备),Wide Area Network(广域网),Local Area Network (局域网),Metropolitan Area Network(城域网)
教学内容:
计算机网络英语;各相关硬件设备品牌、主要生 产厂商;常用的专业术语。
教学提示:
到学校机房或有关网络公司参观,感受本章内容, 以学到更多的专业知识和词汇。
3.1
Network Concepts(网络基础)
计算机网络的建立是为了满足人们 以即时方式共享数据的需求。个人计 算机在处理数据、电子表格、图形以 及其他类型的信息方面是理想的办公 设备,但却不支持快速(用户输出的) 数据共享。 如果用户能把他的计算机与其他 计算机联系在一起的话,他就可以共 享其他计算机上的数据,包括高性能 的打印机。一组计算机和其他的设备 连接在一起构成的系统叫作网络,互 连的计算机共享资源的技术(概念) 叫作网络技术。 联网的计算机可以共享数据、消息、 图形、打印机、传真机、调制解调器、 只读光盘、硬盘以及其他数据存储设 备。 按照网络作用的范围与计算机相互 连接的距离分,有广域网、局域网和 城域网3种类型的网络。
A computer network is a communication system connecting some computers that work together to exchange and share resources. Generally it is made up of two parts: network operation system (NOS) and hardware or nodes, referring to any devices that are connected to a network. Take LAN for example, the hardware system includes a microcomputer, which is used as file server and workstation, net interface card, Tshape juncture, BNC joint, terminator, and cables etc. File Server is the soul of a whole network, so it must be the best. All the input and output of data are under control of the File Server on the network. A network must have a computer as the network File Server, and it provides the workstation its data on the hard disk. Workstation actually is a set of PC. When it has been connected with File Server and been logged on, it can access data from the File Server, and operates on the workstation with the documents needed. Net card (network interface card: NIC) is the interface between File Server and Workstation.
计算机专业英语-计算机网络基础-Chapter 3 Foundation of Computer Network(计算机网络基础)

on, it can access data from the File Server, and 需文件后就可以在工作站上运行。
operates on the workstation with the documents 网卡(network interface card: NIC)
needed.
是服务器与工作站之间的接口。
BNC joint, terminator, and cables etc.
服务器( file server )是整个网络的
File Server is the soul of a whole network, so it 灵魂,所以它必须是最好的。网络上所
must be the best. All the input and output of data 有数据的进出都须通过服务器来控制。
configurations or Network are star, bus, ring, 星形、总线形、环形和树形。
and tree.
星形网络
Star Network
星形网络由一台中央处理器、
A star network contains a central unit, a 多台个人计算机、终端或外围设
wonderful business tools for producing data, 算机在处理数据、电子表格、图形以
spreadsheets, graphics, and other types of 及其他类型的信息方面是理想的办公
information, but do not allow you to quickly 设备,但却不支持快速(用户输出的)
Ø 教学提示:
到学校机房或有关网络公司参观,感受本章内容, 以学到更多的专业知识和词汇。
(完整版)计算机网络英文题库(附答案)chapter3

Chapter 3 Transport Layer1. A transport-layer protocol provides for logical communication between ____.A Application processesB HostsC RoutersD End systems2. Transport-layer protocols run in ____.A ServersB ClientsC RoutersD End systems3. In transport layer, the send side breaks application messages into ____, passes to network layer.A FramesB SegmentsC Data-gramsD bit streams4. Services provided by transport layer include ____.A HTTP and FTPB TCP and IPC TCP and UDPD SMTP5. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers6. These two minimal transport-layer services----____ and ____----are the only two services that UDP provides!A process-to-process data delivery, error checkingB congestion control, reliable data transferC flow control, congestion controlD In-order data transfer, error checking7. Port number’s scop e is ____ to ____.A 0, 1023B 0, 65535C 0, 127D 0,2558. The port numbers ranging from ____to ____ are called well-known port number and are restricted.A 0, 1023B 0, 65535C 0, 127D 0,2559. UDP socket identified by two components, they are ____.A source IP addresses and source port numbersB source IP addresses and destination IP addressesC destination IP address and destination port numbersD destination port numbers and source port numbers10. TCP socket identified by a (an) ____.A 1-tupleB 2-tupleC 3-tupleD 4-tuple11. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP12. Reliable data transfer protocol over a perfectly reliable channel is____.A rdt1.0B rdt2.0C rdt3.0D rdt2.113. Reliable data transfer protocol over a channel with bit errors and packet losses is _ ___.A rdt1.0B rdt2.0C rdt3.0D rdt2.114. Which of the following about reliable data transfer over a channel with bit errors i s not correct?A RDT2.0: assuming ACK and NAK will not be corruptedB RDT2.1: assuming ACK and NAK can be corruptedC RDT2.2: only use ACK-sD RDT2.2: use both ACK-s and NAK-s15. Which of the following protocols is not pipelining protocols?A TCPB rdt3.0C GO-BACK-ND selective repeat16. Which of the following is not correct about GBN protocol?A Only using ACK-sB Using cumulative ACK-sC Receiver discards all out-of-order packetsD It is not pipelined protocol17. Which of the following is not correct about SR protocol?A receiver individually acknowledges all correctly received packetsB sender only resends packets for which ACK not receivedC It limits sequence number of sent but un-ACK-ed packetsD It is not a pipelined protocol18. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection19. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection20. The FIN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection21.How does TCP sender perceive congestion?A Through a timeout eventB Through a receiving duplicate ACK-s eventC Both A and BD Either A or B22. Extending host-to-host delivery to process-to-process delivery is called transport-layer ____ and .A multiplexing and de-multiplexingB storing and forwardingC forwarding and filteringD switching and routing23. UDP is a ____ service while TCP is a connection-oriented service.A ConnectionlessB ReliableC Connection-orientedD In-order24. The UDP header has only four fields, they are____.A Source port number, destination port number, length and checksumB Source port number, destination port number, source IP and destination IPC source IP, destination IP, source MAC address and destination MAC addressD source IP, destination IP, sequence number and ACK sequence number25. There are two 16-bit integers: 1110 0110 0110 0110, 1101 0101 0101 0101. Their checksum is____.A 0100010001000011B 1011101110111100C 1111111111111111D 100000000000000026.The maximum amount of data that can be grabbed and placed in a segment is limited by the____.A Maximum segment size (MSS)B MTUC ChecksumD Sequence number27.The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host----the so-called____.A Maximum transmission unit (MTU)B MSSC ChecksumD Sequence number28. A File size of 500,000bytes, MSS equals 1000bytes. When we want to transmit this file with TCP, the sequence number of the first segment is 0, and the sequence number of the second segment is ____.A 1000B 999C 1001D 50000029.Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide____.A Cumulative acknowledgementsB Selective acknowledgementsC 3 duplicate ACKsD positive ACKs30. Provided α=0.125, current value of Estimated-RTT is 0.4s, Sample-RTT is 0.8s, then the new value of Estimated-RTT is ____s.A 0.45B 0.6C 0.7D 0.831.Provided RcvBuffer=20,LastByteRcvd=20,LastByteRead=15, thenRcvWindow=____.A 14B 15C 16D 1032. TCP service does not provide____.A Reliable data transferB Flow controlC Delay guaranteeD Congestion control33. There are two states in TCP congestion control, which are ____.A slow start and congestion avoidanceB safe start and congestion avoidanceC slow start and congestion abandonD safe start and congestion abandon34. The transport-layer protocol provides logical communication between ____, and the network-layer protocol provides logical communication ____.A hosts, processesB processes, hostsC threads, processesD processes, threads35. To implement the multicast services the Internet employs the ____ protocol.A FTPB TCPC IGMPD UDP36. If an application developer chooses ____ protocol, then the application process is almost directly talking with IP.A HTTPB RIPC CSMA/CDD UDP37. ____ maintains connection-state in the end systems. This connection state includes receive and send buffers, congestion-control parameters, and sequence and acknowledgment number parameters.A UDPB TCPC DNSD HTTP38. The host that initiates the session in the Internet is labeled as ____.A serverB user agentC clientD router39. With TCP there is no _____ between sending and receiving transport-layer entities.A flow controlB handshakingC. congestion control D VC setup40. The Internet’s ____service helps prevent the Internet from entering a state of gridlock.A datagramB congestion controlC sliding windowD timeout event41. Connection setup at the transport layer involves ____.A serverB only the two end systemsC clientD router42. A ____layer protocol provides for logical communication between applications.A transportB applicationC networkingD MAC43. In static congestion window, if it satisfies W*S/R > RTT + S/R, the Latency is ____.A W*S/R – ( RTT+ S/R)B 2RTT + O/RC 2RTT + O/R + (k-1)[W* S/R- (RTT + S/R)]D 2RTT + S/R44. The receive side of transport layer reassembles segments into messages, passes to ____layer.A ApplicationB NetworkingC PhysicalD MAC45. In the following four options, which one is correct?A The variations in the SampleRTT are smoothed out in the computation of the EstimatedRTTB The timeout should be less than the connection’s RTTC Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≥1 secD Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≤1 sec46. The port number used by HTTP is ____.A 80B 25C 110D 5347. The port number used by SMTP is ____.A 80B 25C 110D 5348. The port number used by pop3 is ____.A 80B 25C 110D 5349. The port number used by DNS is ____.A 80B 25C 110D 5350. The port number used by FTP is ____.A 20 and 21B 20C 21D 5351. A UDP socket identified by a ____ tuple(s).A 2B 4C 1D 352. A TCP socket identified by a ____ tuple(s).A 2B 4C 1D 353. A TCP socket does not include____.A Source MAC addressB Source port numberC Destination IP addressD Destination port number54. Which of following about UDP is not correct.A It is a reliable data transfer protocolB It is connectionlessC no handshaking between UDP sender, receiverD it is a best effort service protocol55. DNS uses ____ service.A TCPB UDPC Both TCP and UDPD None of above56. Which of following about UDP is correct?A Finer application-level control over what data is sent, and whenB No connection establishment (which can add delay), so no delay for establish a connectionC No connection state (so, UDP can typically support many active clients)D Large packet header overhead (16-B)57. Streaming media uses a ____ service normally.A TCPB UDPC Both TCP and UDPD None of above58. The UDP header has only ____ fields.A 2B 4C 1D 359. Which of the following does not included in UDP header.A Source port numberB Destination port numberC ChecksumD Sequence number60. Which of the following is not a pipelining protocol.A Rdt1.0B Go-Back-NC Selective repeatD TCP61. In the following four descriptions about MSS and MTU, which one is not correct?A The MSS is the maximum amount of application-layer data in the segmentB The MSS is the maximum size of the TCP segment including headersC The MSS is typically set by MTUD The MTU means the largest link-layer frame62. The job of gathering data chunks, encapsulating each data chunk with header information to create segments and passing the segments to the network is called ____.A multiplexingB de-multiplexingC forwardingD routing63. In the following four descriptions about the relationship between the transport layer and the network layer, which one is not correct?A The transport-layer protocol provides logical communication between hostsB The transport-layer protocol provides logical communication between processesC The services that a transport-layer protocol can provide are often constrained by the service model of the network-layer protocolD A computer network may make available multiple transport protocols64. Suppose the following three 8-bit bytes: 01010101, 01110000, 01001100. What’s the 1s complement of the sum of these 8-bit bytes?A 00010001B 11101101C 00010010D 1000100065. The following four descriptions about multiplexing and de-multiplexing, which one is correct?A A UDP socket is identified by a two-tuples consisting of a source port number and a destination port number.B If two UDP segment have different source port number, they may be directed to the same destination process.C If two TCP segments with different source port number, they may be directed to the same destination process.D If two TCP segments with same destination IP address and destination port number, they must be the same TCP connection.66. UDP and TCP both have the fields except ____.A source port numberB destination port numberC checksumD receive window67. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [nextseqnum,base+N-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged68. Which of the following about TCP is not correct?A It is a connectionless protocolB Point-to-point protocolC Reliable, in-order byte steam protocolD Pipelined protocol69. Which of the following about TCP is not correct?A It is a connectionless protocolB full duplex data transfer protocolC connection-oriented protocolD flow controlled protocol70. The maximum amount of data that can be grabbed and placed in a segment is limited by the ____.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum71. The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host (the so-called____), and then will fit into a single link-layer frame.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum72. The MSS is the maximum amount of ____layer data in the segment, not the maximum size of the TCP segment including headers.A ApplicationB TransportC NetworkingD Link73. Which of the following field is not used for connection setup and teardown?A Sequence numberB TSTC SYND FIN74. ____ is the byte stream number of first byte in the segment.A Sequence numberB ACK numberC ChecksumD port number75. ____ is the byte sequence numbers of next byte expected from other side.A Sequence numberB ACK numberC ChecksumD port number76. Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide ____ acknowledgements.A CumulativeB SelectiveC SingleD Negative77. Fast retransmit means in the case that ____ duplicate ACK-s are received, the TCP sender resend segment before timer expires.A 3B 4C 5D 678. TCP____ means sender won’t overflow receiver’s buffer by tran smitting too much, too fast.A Flow controlB Congestion controlC Reliable data transferD Connection-oriented service79. TCP provides flow control by having the sender maintain a variable called the ____.A Receive windowB Congestion windowC Sliding windowD buffer80. How does TCP sender perceive congestion?A TimeoutB 3 duplicate ACK-sC Both A and BD None of above81. Transport protocols run in ____.A ServersB ClientsC RoutersD End systems82. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers83. Which service does UDP not provide?A multiplexingB de-multiplexingC error-detectionD error-correction84. There are three major events related to data transmission and retransmission in the TCP sender, which one is not in it?A data received from application aboveB de-multiplexing segmentC timer timeoutD ACK receipt85. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP86. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection87. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection88. Which service helps prevent the internet from entering a state of gridlock?A reliable data transferB flow controlC congestion controlD handshaking procedure89. The Internet’s _____is responsible for moving packets from one host to another.A application layerB transport layerC network layerD link layer90.In the following applications, which one is a bandwidth-sensitive application?A E-mailB web applicationC real-time audioD file transfer91. In the following applications, which one uses UDP?A E-mailB web applicationC file transferD DNS92. In the following four descriptions, which one is correct?A If one host’s transport layer uses TCP, then its network layer must use virtual-circuit network.B Datagram network provides connection serviceC The transport-layer connection service is implemented in the routerD The network-layer connection service is implemented in the router as well as in the end system.93.____ is a speeding-matching service---matching the rate which the sender is sending against the rate at which the receiving application is reading.A congestion controlB flow controlC sliding-window controlD variable control94. In the following four descriptions about Rcv-Window, which one is correct?A The size of the TCP RcvWindow never changes throughout the duration of the connectionB The size of the TCP RcvWindow will change with the size of the TCP RcvBufferC The size of the TCP RcvWindow must be less than or equal to the size of the TCP RcvBufferD Suppose host A sends a file to host B over a TCP connection, the number of unacknowledged bytes that A sends cannot exceed the size of the size of the RcvWindow.95. There are 6 flag fields. Which one is to indicate that the receiver should pass the data to the upper layer immediately?A PSHB URGC ACKD RST96. Suppose the TCP receiver receives the segment that partially or completely fills in gap in received data, it will ____.A immediately send ACKB immediately send duplicate ACKC wait some time for arrival of another in-order segmentD send single cumulative97. _____ imposes constrain on the rate at which a TCP sender can send traffic into the network.A sliding windowB congestion windowC receive windowD variable window98. Flow control and congestion control are same at that they all limit the rate of the sender, but differ in that ____.A flow control limits its rate by the size of RcvWindow, but congestion control by the traffic on the linkB congestion control limits its rate by the size of RcvWindow, but flow control by the traffic on the linkC flow control mainly is accomplished by the sender, but congestion control by the receiver.D flow control mainly is accomplished by the receiver, but congestion control bythe link.99. This job of delivering the data in a transport-layer segment to the correct socket is called ____.A multiplexingB de-multiplexingC forwardingD routing100. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [base, nextseqnum-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged101. ____ are the two types of transport services that the Internet provides to the applications.A TCP and UDPB connection-oriented and connectionless serviceC TCP and IPD reliable data transfer and flow control102. In the following descriptions about persistent connection, which one is not correct?A The server leaves the TCP connection open after sending a responseB Each TCP connection is closed after the server sending one objectC There are two versions of persistent connection: without pipelining and with pipeliningD The default mode of HTTP uses persistent connection with pipelining103. The field of Length in UDP segment specifies the length of ____.A the UDP segment, not including the headerB the UDP segment, including the headerC the UDP segment’s headerD the Length field104. In TCP segment header, which field can implement the reliable data transfer?A source port number and destination port numberB sequence number and ACK numberC urgent data pointerD Receive window105. In the following four descriptions about TCP connection management, which one is not correct?A Either of the two processes participating in a TCP connection can end the connectionB If the FIN bit is set to 1, it means that it wants to close the connectionC In the first two step of the three-way handshake, the client and server randomly choose an initial sequence numberD In the three segments of the three-way handshake, the SYN bit must be set to 1 106. Suppose host A sends two TCP segments back to back to host B over a TCP connection. The first segment has sequence number 42, and the second has sequence number 110. If the 1st is lost and 2nd arrives at host B. What will be the acknowledgment number?A 43B ACK42C 109D ACK1101.Consider sending an object of size O=500,000bytes from server to client. LetS=500 bytes and RTT=0.2s. Suppose the transport protocol uses static windows with window size 5. For a transmission rate of 100Kbps, determine the latency for sending the whole object. Recall the number of windows K=O/ WS), and there is K-1 stalled state (that is idle time gaps).2.Consider the following plot of TCP congestion window size as a function of time.Fill in the blanks as follow:a) The initial value of Threshold at the first transmission round is ____. b) The value of Threshold at the 11st transmission round is ____. c) The value of Threshold at the 21st transmission round is ____. d) After the 9th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKe) After the 19th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKf) During ____ transmission round, the 18th segment is sent.3.Consider the TCP reliable data transfer in the given graph. If in Segment 1’s Sequence number =10,data=“AC”, please fill in the following blanks. a) In Segment 2, ACK number=____;b) In Segment 3, Sequence number =____; data=“0123456789”c) If there are some bits corrupted in segment 3 when it arrives Host B, then the ACK number in Segment 5 is ____; and the ACK number in Segment 6 is ____.14 180 26 3000 2 6 4 8 10 12 16 20 22 240 28 32Congestion window sizeTransmission round48121612345674. The client A wants to request a Web page from Server B. Suppose the URL of the page is 172.16.0.200/experiment, and also it wants to receive French version of object. The time-sequence diagram is shown below, please fill in the blanks.12345Packet① to Packet③are TCP connection’s segment, then:Packet ①: SYN flag bit= aACK flag bit= bSequence number= 92Packet ②: SYN flag bit=1ACK flag bit= c Sequence number=100 Packet ③: SYN flag bit= d ACK flag bit=1Sequence number= e5. Consider sending an object of size O=100 Kbytes from server to client. Let S=536 bytes and RTT=100msec. Suppose the transport protocol uses static windows with window size W.(1) For a transmission rate of 25 kbps, determine the minimum possible latency. Determine the minimum window size that achieves this latency. (2) Repeat (1) for 100 kbps.6. Consider the following plot of TCP congestion window size as a function of time. Please fill in the blanks as below.a) The initial value of Threshold at the first transmission round is____. b) The value of Threshold at the 11th transmission round is_____. c) The value of Threshold at the 21st transmission round is_____.14 18 26 30 0 2 6 4 8 10 12 16 20 22 24 28 32 Congestion window sizeTransmission round481216d) After the 9th transmission round, _____ occurs.e) After the 19th transmission round, ____ are detected.。
计算机网络第三的名词解释

计算机网络第三的名词解释计算机网络第三层的名词解释引言:计算机网络是当今信息技术领域的重要组成部分,它架起了全球通信的桥梁。
网络是由一系列不同层次组成的,每一层都有其特定的功能和任务。
本文将重点解释计算机网络中第三层的相关名词和概念。
一、第三层简介在计算机网络中,第三层通常又被称为网络层。
它位于OSI(开放式系统互联)模型和TCP/IP(传输控制协议/互联网协议)模型中的中间层次。
网络层主要负责控制数据在不同网络之间的传输和路由。
二、IP协议IP(互联网协议)是网络层中最重要的协议之一。
它给予每个连接到网络的设备一个独特的IP地址,类似于一个房子的门牌号码,使其能够在全球范围内与其他设备进行通信。
IP协议为数据包提供了寻址和传输的主要机制,并且负责将数据包从源节点传送到目的节点。
三、IP地址IP地址是网络层中非常重要的一个概念。
它由32位二进制数字组成,通常用点分十进制表示法来表示。
IP地址的作用是唯一标识网络上的每个设备,使得数据能够准确地被发送和接收。
IP地址分为IPv4和IPv6两种格式,目前IPv4是最常用的,但IPv6由于提供了更大的地址空间,正在逐渐普及。
四、路由协议路由协议是网络层中用于确定数据包传输路径的重要工具。
当一个数据包从源节点发送到目的节点时,它需要经过多个中间节点,而每个节点通过路由协议来决定下一跳节点的路径。
常见的路由协议包括RIP(路由信息协议)、OSPF(开放式最短路径优先)和BGP(边界网关协议)等。
不同的路由协议有不同的工作原理和适用场景。
五、路由器路由器是网络层中常用的设备类型。
它是一种能够根据IP地址和路由表决定数据包的路径的网络设备。
路由器通常连接多个网络和子网络,并根据网络层的信息将数据包传送到正确的目的地。
路由器在互联网中扮演着重要的角色,是全球网络通信的关键组成部分。
六、IP数据包IP数据包是网络层中传输的基本单位。
它包含了源IP地址、目的IP地址以及其他与网络层相关的控制信息和数据内容。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Introduction Two Basic Internet Communication Paradigms Connection-Oriented Communication The Client-Server Model of Interaction Characteristics of Clients and Servers Server Programs and Server-Class Computers Requests, Responses, and Direction of Data Multiple Clients and Multiple Servers Server Identification and Demultiplexing Concurrent Servers Circular Dependencies Among Servers Peer-to-Peer Interactions Network Programming and the Socket API
3.2.1
Stream Transport in the Internet
Stream denotes a paradigm in which a sequence of bytes flows from one application program to another Internet's mechanism arranges two streams between a pair of communicating applications, one in each direction The network accepts input from either application, and delivers the data to the other application The stream mechanism transfers a sequence of bytes without attaching meaning to the bytes and without inserting boundaries A sending application can choose to generate one byte at a time, or can generate blocks of bytes The network chooses the number of bytes to deliver at any time
It is possible to devise new services without changing the Internet Chapter covers two key concepts of Internet applications:
describes the conceptual paradigm that applications follow when they communicate over the Internet presents the details of the socket Application Programming Interface (socket API) that Internet applications use
Later parts of the text provide the necessary information by explaining data communications and protocols used to form the Internet
7
3.2 Two Basic Internet Communication Paradigms
Topics Covered
3.14 Sockets, Descriptors, and Network I/O 3.15 Parameters and the Socket API 3.16 Socket Calls in a Client and Server 3.17 Socket Functions Used by Both Client and Server 3.18 The Connection Function Used Only by a Client 3.19 Socket Functions Used Only by a Server 3.20 Socket Functions Used with the Message Paradigm 3.21 Other Socket Functions 3.22 Sockets, Threads, and Inheritance
However, understanding network protocols and technologies allows them to write efficient and reliable code that enables applications to scale across many sites
Multicast
a message can be multicast to some of the computers on a network, 1-to-many
Broadcast
a message can be broadcast to all computers on a given network, 1-to-all
3.1
Introduction
Internet application programmers can get started easily It is possible to create Internet applications without knowing how networks operate
Internet provides a general purpose mechanism on which
all services are built and individual services are supplied by application programs that run on computers attached to the Internet
2013-7-13 2 暨南大学计算中心
Chapter 3
Internet Applications and Network Programming
Topics Covered
3.1 3.2 3.3 3.4 3.5 3.6 3.7 Flow 3.8 3.9 3.10 3.11 3.12 3.13
A programmer who uses the message paradigm must insure that the application operates correctly
even if packets are lost or reordered
Most applications require delivery guarantees Programmers tend to use the stream service except in special situations
such as video, where multicast is needed and the application provides support to handle packet reordering and loss
Thus, we will focus on the stream paradigm
3.1
Introduction
The Internet offers users a rich diversity of services
none of the services is part of the underlying communication infrastructure
The Internet supports two basic communication paradigms:
3.2.1 Stream Transport in the Internet 3.2.2 Message Transport in the Internet
Figure 3.1 summarizes the differences
9
3.2.2
Message Transport in the Internet
In a message paradigm, the network accepts and delivers messages Each message delivered to a receiver corresponds to a message that was transmitted by a sender
the network can choose to combine smaller blocks into one large block or can divide a large block into smaller blocks
© 2009 Pearson Education Inc., Upper Saddle River, NJ. All rights reserved.
计算机网络及应用技术
计算中心 林龙新
2013-7-13
暨南大学计算中心
1
主要参考书目
1. 计算机网络与因特网(第五版)机械工业出版社 2. 计算机网络与因特网(第四版)机械工业出版社 3. Internetworking with TCP/IP Volume I (Principles,Protocols and Architecture ) er 清华大学出版社 4. Interconnections Second Edition Bridges, routers,Switches and Internetworking Protocols Radia Perlman 清华大学出版社 5. computer networks (the fourth edition) Andrew S.Tanenbaum 清华大学出版社
