Toward a parallel implementation of Concurrent ML
项目报告模板 英文

项目报告模板英文1. IntroductionThe purpose of this project report is to provide an overview of the project's objectives, scope, and outcomes. The report will also discuss the methodology used, the challenges encountered, and the lessons learned throughout the project. This project aimed to [state the project's objectives].2. ObjectivesThe main objectives of this project were as follows:- Objective 1: [Provide a brief description of the first objective] - Objective 2: [Provide a brief description of the second objective]- Objective 3: [Provide a brief description of the third objective] 3. MethodologyThe project followed a [describe the methodology used, such as Agile, Waterfall, etc.] approach. The project team consisted of [mention the team size and roles]. The project plan was divided into various phases, including planning, analysis, design,implementation, testing, and deployment.During the planning phase, the team conducted a thorough analysis of the project requirements and developed a detailed project plan. The analysis phase involved gathering and documenting the stakeholders' requirements and identifying any potential risks and constraints.In the design phase, the team created a system architecture and designed the various components of the project. The implementation phase focused on coding and integrating the different modules. Testing was carried out in parallel with implementation to ensure the quality and reliability of the system.4. ChallengesThroughout the project, several challenges were encountered, including:- Challenge 1: [Describe the first challenge faced]- Challenge 2: [Describe the second challenge faced]- Challenge 3: [Describe the third challenge faced]These challenges were successfully addressed by [mention thestrategies or solutions implemented].5. Lessons LearnedThe project provided several valuable lessons, including:- Lesson 1: [Highlight the first lesson learned]- Lesson 2: [Highlight the second lesson learned]- Lesson 3: [Highlight the third lesson learned]These lessons will be applied to future projects to improve the overall project management and outcomes.6. ConclusionIn conclusion, this project report has provided an overview of the project's objectives, methodology, challenges, and lessons learned. The project has successfully achieved its objectives, and the outcomes have met the stakeholders' requirements. The project team has gained valuable experience and knowledge throughout the project, which will be beneficial for future initiatives.7. RecommendationsBased on the project's experience, the followingrecommendations are provided for future projects:- Recommendation 1: [Suggest the first recommendation]- Recommendation 2: [Suggest the second recommendation] - Recommendation 3: [Suggest the third recommendation]These recommendations aim to improve the project management and ensure the successful delivery of future projects.8. References[List any references used in the project report]。
常用线性代数程序库简单介绍
BLAS(Basic Linear Algebra Subprograms 基础线性代数程序集)是一个应用程序接口(API)标准,用以规范发布基础线性代数操作的数值库(如矢量或矩阵乘法)。
该程序集最初发布于1979年,并用于建立更大的数值程序包(如LAPACK)。
在高性能计算领域,BLAS被广泛使用。
例如,LINPACK的运算成绩则很大程度上取决于BLAS中子程序DGEMM的表现。
为提高性能,各硬件厂商(如Intel)则针对其硬件对BLAS接口实现进行高度优化。
BLAS按照功能被分为三个级别:Level 1:矢量-矢量运算Level 2:矩阵-矢量运算Level 3:矩阵-矩阵运算实现Parallel Basic Linear Algebra Subprograms (PBLAS) is an implementation of Level 2 and3 BLAS intended for distributed memory architectures. It provides a computational backbonefor ScaLAPACK, a parallel implementation of LAPACK. It depends on Level 1 sequential BLAS operations for local computation and BLACS for communication between nodes.PLAPACK (Parallel Linear Algebra Package) is an infrastructure for coding parallel linear algebra algorithms at a high level of abstraction.The ScaLAPACK (or Scalable LAPACK) library includes a subset of LAPACK routines redesigned for distributed memory MIMD parallel computers. It is currently written in a Single-Program-Multiple-Data style using explicit message passing for interprocessor communication. It assumes matrices are laid out in a two-dimensional block cyclic decomposition.ScaLAPACK is designed for heterogeneous computing and is portable on any computer that supports MPI or PVM.ScaLAPACK depends on PBLAS operations in the same way LAPACK depends on BLAS.。
系统集成项目管理工程师模拟试题与参考答案

系统集成项目管理工程师模拟试题与参考答案一、单选题(共100题,每题1分,共100分)1、在大数据相关技术中,()是一个分布的、面向列的开源数据库,是一个适合于非结构化数据存储的数据库。
A、ChukwaB、HDFSC、MapReduceD、HBase正确答案:D2、以下关于项目整体变更控制过程的叙述中,不正确的是()A、会议是实施整体变更控制的工具与技术之一B、实施整体变更控制过程的目的是为了降低项目风险C、实施整体变更控制过程贯穿项目始终,并且应用于项目的各个阶段D、变更控制委员会对整体变更控制过程负最终责任正确答案:D3、关于信息系统设计的描述,正确的是:()。
A、设备选型与法律制度无关B、人机界面设计是系统概要设计的任务之一C、系统架构设计对设备选型起决定作用D、确定系统架构时,要对整个系统进行“纵向”分解而不是“横向”分解正确答案:C4、()不属于信息系统审计的主要内容A、灾难恢复与业务持续计划B、信息化战略C、资产的保护D、信息系统的管理、规划与组织正确答案:B5、电子商务不仅包括信息技术,还包括交易原则、法律法规和各种技术规范等内容,其中电子商务的信用管理,收费及隐私保护等问题属于()方面的内容。
A、技术规范B、交易规则C、信息技术D、法律法规正确答案:D6、某制造商面临大量产品退货,产品经理怀疑是采购和货物分类流程存在问题,此时应该采用()进行分析。
A、直方图B、质量控制图C、流程图D、鱼骨图正确答案:D7、()将质量控制扩展到产品生命周期全过程。
A、全面质量管理B、统计质量控制C、抽验检验方法D、检验技术正确答案:A8、对MAC地址进行变更属于()。
A、链路层交换B、网络层交换C、传输层交换D、物理层交换正确答案:A9、信息技术服务标准(ITSS)定义了IT服务的核心要素由人员、过程、技术和资源组成。
()要素关注“正确做事”。
A、过程B、技术C、人员D、资源正确答案:A10、In a project plan, when the project manager scheouies activities, he(or sha) oftenuses ()method, precedence relationships between acticities are represented by cireles connected by one or more arrows.The length of the arrow represents the duration of the relevant activity.A、histogramB、causality diagramC、Gantt chartD、arrow djgram正确答案:D11、风险识别的输出是()A、风险概率B、风险因素C、已识别风险清单D、风险损失正确答案:C12、在重点领域试点建设智能工厂、数字化车间,加快人工智能交互、工业机器人、智能物能管理等技术在生产过程中的应用。
使用并行结构的英文作文

使用并行结构的英文作文Title: The Beauty of Parallel Structures in English Composition.In the realm of English composition, parallelstructures offer a powerful tool to enhance clarity, rhythm, and impact. They are the architectural pillars of well-constructed sentences, creating a balance and harmony that draw readers into the flow of thought. In this essay, wewill explore the elegance and effectiveness of parallel structures, discussing how they can elevate the quality of our writing.To understand parallel structures, we must first appreciate their basic form. At its core, a parallel structure involves the repetition of grammatical elementsin a sentence, creating a sense of balance and symmetry. This repetition can take various forms, such as the use of similar phrases, clauses, or sentence structures. By repeating these elements, writers can establish a rhythmicpattern that guides readers through their ideas.The benefits of parallel structures are numerous. Firstly, they promote clarity by ensuring that ideas are presented in a consistent and logical manner. When writers use parallel structures, they are effectively mapping out their thoughts, allowing readers to follow the path with ease. This clarity is especially important in complex arguments or detailed descriptions, where it can help to organize information and maintain focus.Moreover, parallel structures add a rhythmic beauty to writing. Just as music relies on melody and harmony to create a captivating experience, so does English composition rely on parallel structures to create a flow that draws readers in. This rhythm not only makes the writing more enjoyable to read but also helps to convey the writer's enthusiasm and conviction.Additionally, parallel structures can enhance the impact of writing by emphasizing key points. By repeating certain grammatical elements, writers can draw attention toparticular ideas or phrases, highlighting their importance. This emphasis can be particularly effective in persuasive writing, where it can help to convince readers of thewriter's position.However, it is important to note that while parallel structures can greatly enhance the quality of writing, they should not be used excessively. Overreliance on parallel structures can lead to a stilted and unnatural feel, robbing the writing of its vitality and authenticity. Instead, writers should use parallel structures sparingly, employing them only when they add value to the sentence or paragraph.In conclusion, parallel structures are an essential component of effective English composition. They promote clarity, add rhythmic beauty, and enhance the impact of writing. By mastering the art of parallel structures, writers can transform their ideas into a captivating narrative that draws readers in and leaves a lasting impression. Therefore, as we craft our words, let usremember the power of parallel structures and harness their beauty to elevate our writing to new heights.。
y and

Keywords: Torus, routing, placement, bisection, interconnection network, edge separator, congestion.
1 Introduction
Meshes and torus based interconnection networks have been utilized extensively in the design of parallel computers in recent years 5]. This is mainly due to the fact that these families of networks have topologies which re ect the communication pattern of a wide
1
variety of natural problems, and at the same time they are scalable, and highly suitable for hardware implementation. An important factor determining the e ciency of a parallel algorithm on a network is the e ciency of communication itself among processors. The network should be able to handle \large" number of messages without exhibiting degradation in performance. Throughput, the maximum amount of tra c which can be handled by the network, is an important measure of network performance 3]. The throughput of an interconnection network is in turn bounded by its bisection width, the minimum number of edges that must be removed in order to split the network into two parts each with about equal number of processors 8]. Here, following Blaum, Bruck, Pifarre, and Sanz 3, 4], we consider the behavior of torus networks with bidirectional links under heavy communication load. We assume that the communication latency is kept minimum by routing the messages through only shortest (minimal length) paths. In particular, we are interested in the scenario where every processor in the network is sending a message to every other processor (also known as complete exchange or all-to-all personalized communication). This type of communication pattern is central to numerous parallel algorithms such as matrix transposition, fast Fourier transform, distributed table-lookup, etc. 6], and central to e cient implementation of high-level computing models such as the PRAM and Bulk-Synchronous Parallel (BSP). In Valiant's BSP-model for parallel computation 14] for example, routing of h-relations, in which every processor in the network is the source and destination of at most h packets, forms the main communication primitive. Complete-exchange scenario that we investigate in this paper has been studied and shown to be useful for e cient routing of both random and arbitrary h-relations 7, 12, 13]. The network of d-dimensional k-torus is modeled as a directed graph where each node represents either a router or a processor-router pair, depending on whether or not a processor is attached at this node, and each edge represents a communication link between two adjacent nodes. Hence, every node in the network is capable of message routing, i.e. directly receiving from and sending to its neighboring nodes. A fully-populated d-dimensional k-torus where each node has a processor attached, contains kd processors. Its bisection width is 4kd? (k even), which gives kd=2 processors on each component of the bisection. Under the complete-exchange scenario, the number of messages passing through the bisection in both directions is 2(kd =2)(kd=2). Dividing by the bisection bandwidth, we nd that there must exist an edge in the bisection with a load kd =8. This means that unlike multistage networks, the maximum load on a link is not linear in the number of processors injecting messages into the network. To alleviate this problem, Blaum et al. 3, 4] have proposed partially-populated tori . In this model, the underlying network is torodial, but the nodes do not all inject messages into the network. We think of the processors as attached to a (relatively small) subset of nodes (called a placement), while the other nodes are left as routing nodes. This is similar to the case of a
科研实验室-Rebuttal经验总结

Review和Rebuttal介绍
➢ Review和Rebuttal
1. 审稿意见 (Review):会议论文投稿之后一般3个月之内会出
Review,其中包含3-4个审稿人的评审意见。
Table 1. ICLR2018 Scores & Decisions
Oral Poster Workshop Reject
需要对比审稿人描述 的方法
3. How sensitive would the method be to the number of nearest neighbors used for local coordinate coding?
需要对某个超参数进 行敏感度分析
4. Inception score (IS) cannot evaluate the generalization ability as simply memorizing all data gives highest score.
共性问题要形 成共性回答
Response to Reviewer 1 (R1): Q1. Training complexity of xxx: The complexity of xxx… Q2. Advantage of xxx: Our method provides an effective way…
计算机期刊大全

计算机期刊大全【前言】随着计算机技术的快速发展,越来越多的人开始关注计算机期刊,以获取最新的科研成果和技术进展。
本文旨在介绍全球范围内主要的计算机期刊,帮助读者了解各期刊的主题范围、影响因子、最新收录论文等信息,以提高论文发表效率和科研成果的质量。
【一、计算机科学顶级期刊】计算机领域的顶级期刊,对于任何一位计算机科学家来说,都是非常重要的。
这些期刊的文章水平高、质量优,其发表文章往往具有一定的权威性和影响力。
以下是全球最著名的计算机科学顶级期刊:1.《ACM Transactions on Computer Systems》(ACM TOCS)主题范围:该期刊关注计算机系统的设计、分析、实现和评估等方面,特别是操作系统、网络、分布式系统、数据库管理系统和存储系统等方面的最新研究成果。
影响因子:3.612发行周期:每年4期最新收录论文:Content-Based Data Placement for Efficient Query Processing on Heterogeneous Storage Systems, A Framework for Evaluating Kernel-Level Detectors, etc.2.《IEEE Transactions on Computers》(IEEE TC)主题范围:该期刊刊登计算机科学领域的创新性研究成果,重点关注计算机系统、组件和软件的设计、分析、实现和评估等方面的最新进展。
影响因子:4.804发行周期:每月1期最新收录论文:A Comprehensive View of Datacenter Network Architecture, Design, and Operations, An Efficient GPU Implementation of Imperfect Hash Tables, etc.3.《IEEE Transactions on Software Engineering》(IEEE TSE)主题范围:该期刊涉及软件工程领域的各个方面,包括软件开发、可靠性、维护、测试等方面的最新研究成果。
JVM for a Heterogeneous Shared Memory System
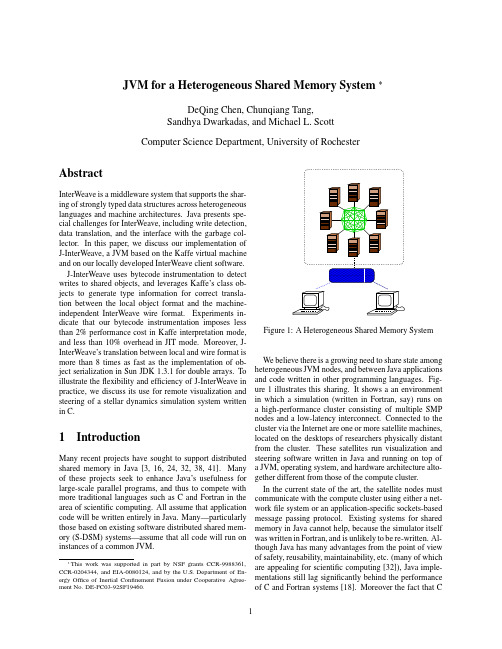
JVM for a Heterogeneous Shared Memory SystemDeQing Chen,Chunqiang Tang,Sandhya Dwarkadas,and Michael L.ScottComputer Science Department,University of Rochester AbstractInterWeave is a middleware system that supports the shar-ing of strongly typed data structures across heterogeneouslanguages and machine architectures.Java presents spe-cial challenges for InterWeave,including write detection,data translation,and the interface with the garbage col-lector.In this paper,we discuss our implementation ofJ-InterWeave,a JVM based on the Kaffe virtual machineand on our locally developed InterWeave client software.J-InterWeave uses bytecode instrumentation to detectwrites to shared objects,and leverages Kaffe’s class ob-jects to generate type information for correct transla-tion between the local object format and the machine-independent InterWeave wire format.Experiments in-dicate that our bytecode instrumentation imposes lessthan2%performance cost in Kaffe interpretation mode,and less than10%overhead in JIT mode.Moreover,J-InterWeave’s translation between local and wire format ismore than8times as fast as the implementation of ob-ject serialization in Sun JDK1.3.1for double arrays.Toillustrate theflexibility and efficiency of J-InterWeave inpractice,we discuss its use for remote visualization andsteering of a stellar dynamics simulation system writtenin C.1IntroductionMany recent projects have sought to support distributedshared memory in Java[3,16,24,32,38,41].Manyof these projects seek to enhance Java’s usefulness forlarge-scale parallel programs,and thus to compete withmore traditional languages such as C and Fortran in thearea of scientific computing.All assume that applicationcode will be written entirely in Java.Many—particularlythose based on existing software distributed shared mem-ory(S-DSM)systems—assume that all code will run oninstances of a common JVM.has yet to displace Fortran for scientific computing sug-gests that Java will be unlikely to do so soon.Even for systems written entirely in Java,it is appealing to be able to share objects across heterogeneous JVMs. This is possible,of course,using RMI and object serial-ization,but the resulting performance is poor[6].The ability to share state across different languages and heterogeneous platforms can also help build scalable dis-tributed services in general.Previous research on var-ious RPC(remote procedure call)systems[21,29]in-dicate that caching at the client side is an efficient way to improve service scalability.However,in those sys-tems,caching is mostly implemented in an ad-hoc man-ner,lacking a generalized translation semantics and co-herence model.Our on-going research project,InterWeave[9,37],aims to facilitate state sharing among distributed programs written in multiple languages(Java among them)and run-ning on heterogeneous machine architectures.InterWeave applications share strongly-typed data structures located in InterWeave segments.Data in a segment is defined using a machine and platform-independent interface de-scription language(IDL),and can be mapped into the ap-plication’s local memory assuming proper InterWeave li-brary calls.Once mapped,the data can be accessed as ordinary local objects.In this paper,we focus on the implementation of In-terWeave support in a Java Virtual Machine.We call our system J-InterWeave.The implementation is based on an existing implementation of InterWeave for C,and on the Kaffe virtual machine,version1.0.6[27].Our decision to implement InterWeave support directly in the JVM clearly reduces the generality of our work.A more portable approach would implement InterWeave support for segment management and wire-format trans-lation in Java libraries.This portability would come,how-ever,at what we consider an unacceptable price in perfor-mance.Because InterWeave employs a clearly defined internal wire format and communication protocol,it is at least possible in principle for support to be incorporated into other JVMs.We review related work in Java distributed shared state in Section2and provide a brief overview of the Inter-Weave system in Section3.A more detailed description is available elsewhere[8,37].Section4describes the J-InterWeave implementation.Section5presents the results of performance experiments,and describes the use of J-InterWeave for remote visualization and steering.Sec-tion6summarizes our results and suggests topics for fu-ture research.2Related WorkMany recent projects have sought to provide distributed data sharing in Java,either by building customized JVMs[2,3,24,38,41];by using pure Java implementa-tions(some of them with compiler support)[10,16,32]; or by using Java RMI[7,10,15,28].However,in all of these projects,sharing is limited to Java applications. To communicate with applications on heterogeneous plat-forms,today’s Java programmers can use network sock-ets,files,or RPC-like systems such as CORBA[39].What they lack is a general solution for distributed shared state. Breg and Polychronopoulos[6]have developed an al-ternative object serialization implementation in native code,which they show to be as much as eight times faster than the standard implementation.The direct compari-son between their results and ours is difficult.Our exper-iments suggest that J-Interweave is at least equally fast in the worst case scenario,in which an entire object is mod-ified.In cases where only part of an object is modified, InterWeave’s translation cost and communication band-width scale down proportionally,and can be expected to produce a significant performance advantage.Jaguar[40]modifies the JVM’s JIT(just-in-time com-piler)to map certain bytecode sequences directly to na-tive machine codes and shows that such bytecode rewrit-ing can improve the performance of object serialization. However the benefit is limited to certain types of objects and comes with an increasing price for accessing object fields.MOSS[12]facilitates the monitoring and steering of scientific applications with a CORBA-based distributed object system.InterWeave instead allows an application and its steerer to share their common state directly,and in-tegrates that sharing with the more tightly coupled sharing available in SMP clusters.Platform and language heterogeneity can be supported on virtual machine-based systems such as Sun JVM[23] and [25].The Common Language Run-time[20](CLR)under framework promises sup-port for multi-language application development.In com-parison to CLR,InterWeave’s goal is relatively modest: we map strongly typed state across languages.CLR seeks to map all high-level language features to a common type system and intermediate language,which in turn implies more semantic compromises for specific languages than are required with InterWeave.The transfer of abstract data structures wasfirst pro-posed by Herlihy and Liskov[17].Shasta[31]rewrites bi-nary code with instrumentation for access checks forfine-grained S-DSM.Midway[4]relies on compiler support to instrument writes to shared data items,much as we do in the J-InterWeave JVM.Various software shared memory systems[4,19,30]have been designed to explicitly asso-ciate synchronization operations with the shared data they protect in order to reduce coherence costs.Mermaid[42] and Agora[5]support data sharing across heterogeneous platforms,but only for restricted data types.3InterWeave OverviewIn this section,we provide a brief introduction to the design and implementation of InterWeave.A more de-tailed description can be found in an earlier paper[8]. For programs written in C,InterWeave is currently avail-able on a variety of Unix platforms and on Windows NT. J-InterWeave is a compatible implementation of the In-terWeave programming model,built on the Kaffe JVM. J-InterWeave allows a Java program to share data across heterogeneous architectures,and with programs in C and Fortran.The InterWeave programming model assumes a dis-tributed collection of servers and clients.Servers maintain persistent copies of InterWeave segments,and coordinate sharing of those segments by clients.To avail themselves of this support,clients must be linked with a special In-terWeave library,which serves to map a cached copy of needed segments into local memory.The servers are the same regardless of the programming language used by clients,but the client libraries may be different for differ-ent programming languages.In this paper we will focus on the client side.In the subsections below we describe the application programming interface for InterWeave programs written in Java.3.1Data Allocation and AddressingThe unit of sharing in InterWeave is a self-descriptive data segment within which programs allocate strongly typed blocks of memory.A block is a contiguous section of memory allocated in a segment.Every segment is specified by an Internet URL and managed by an InterWeave server running at the host indi-cated in the URL.Different segments may be managed by different servers.The blocks within a segment are num-bered and optionally named.By concatenating the seg-ment URL with a block number/name and offset(delim-ited by pound signs),we obtain a machine-independent pointer(MIP):“/path#block#offset”. To create and initialize a segment in Java,one can ex-ecute the following calls,each of which is elaborated on below or in the following subsections:IWSegment seg=new IWSegment(url);seg.wl_acquire();MyType myobj=new MyType(seg,blkname);myobj.field=......seg.wl_release();In Java,an InterWeave segment is captured as an IWSegment object.Assuming appropriate access rights, the new operation of the IWSegment object communi-cates with the appropriate server to initialize an empty segment.Blocks are allocated and modified after acquir-ing a write lock on the segment,described in more detail in Section3.3.The IWSegment object returned can be passed to the constructor of a particular block class to al-locate a block of that particular type in the segment. Once a segment is initialized,a process can convert be-tween the MIP of a particular data item in the segment and its local pointer by using mip ptr and ptr mip where appropriate.It should be emphasized that mip ptr is primar-ily a bootstrapping mechanism.Once a process has one pointer into a data structure(e.g.the root pointer in a lat-tice structure),any data reachable from that pointer can be directly accessed in the same way as local data,even if embedded pointers refer to data in other segments.In-terWeave’s pointer-swizzling and data-conversion mech-anisms ensure that such pointers will be valid local ma-chine addresses or references.It remains the program-mer’s responsibility to ensure that segments are accessed only under the protection of reader-writer locks.3.2HeterogeneityTo accommodate a variety of machine architectures,In-terWeave requires the programmer to use a language-and machine-independent notation(specifically,Sun’s XDR[36])to describe the data types inside an InterWeave segment.The InterWeave XDR compiler then translates this notation into type declarations and descriptors appro-priate to a particular programming language.When pro-gramming in C,the InterWeave XDR compiler generates twofiles:a.hfile containing type declarations and a.c file containing type descriptors.For Java,we generate a set of Java class declarationfiles.The type declarations generated by the XDR compiler are used by the programmer when writing the application. The type descriptors allow the InterWeave library to un-derstand the structure of types and to translate correctly between local and wire-format representations.The lo-cal representation is whatever the compiler normally em-ploys.In C,it takes the form of a pre-initialized data struc-ture;in Java,it is a class object.3.2.1Type Descriptors for JavaA special challenge in implementing Java for InterWeave is that the InterWeave XDR compiler needs to gener-ate correct type descriptors and ensure a one-to-one cor-respondence between the generated Java classes and C structures.In many cases mappings are straight forward: an XDR struct is mapped to a class in Java and a struct in C,primitivefields to primitivefields both in Java andC,pointersfields to object references in Java and pointers in C,and primitive arrays to primitive arrays. However,certain“semantics gaps”between Java and C force us to make some compromises.For example,a C pointer can point to any place inside a data block;while Java prohibits such liberties for any object reference. Thus,in our current design,we make the following compromises:An InterWeave block of a single primitive data item is translated into the corresponding wrapped class for the primitive type in Java(such as Integer,Float, etc.).Embedded structfields in an XDR struct definition areflattened out in Java and mapped asfields in its parent class.In C,they are translated naturally into embeddedfields.Array types are mapped into a wrapped IWObject(including the IWacquire,wl acquire, and rlpublic class IWSegment{public IWSegment(String URL,Boolean iscreate);public native staticint RegisterClass(Class type);public native staticObject mip_to_ptr(String mip);public native staticString ptr_to_mip(IWObject Ob-ject obj);......public native int wl_acquire();public native int wl_release();public native int rl_acquire();public native int rl_release();......}Figure2:IWSegment Class4.1.1JNI Library for IWSegment ClassThe native library for the IWSegment class serves as an intermediary between Kaffe and the C InterWeave library. Programmer-visible objects that reside within the IWSeg-ment library are managed in such a way that they look like ordinary Java objects.As in any JNI implementation,each native method has a corresponding C function that implements its function-ality.Most of these C functions simply translate their pa-rameters into C format and call corresponding functions in the C InterWeave API.However,the creation of an In-terWeave object and the method RegisterClass need special explanation.Mapping Blocks to Java Objects Like ordinary Java objects,InterWeave objects in Java are created by“new”operators.In Kaffe,the“new”operator is implemented directly by the bytecode execution engine.We modi-fied this implementation to call an internal function new-Block in the JNI library and newBlock calls the Inter-Weave C library to allocate an InterWeave block from the segment heap instead of the Kaffe object heap.Before returning the allocated block back to the“new”operator, newBlock initializes the block to be manipulated cor-rectly by Kaffe.In Kaffe,each Java object allocated from the Kaffe heap has an object header.This header contains a pointer to the object class and a pointer to its own monitor.Since C InterWeave already assumes that every block has a header (it makes no assumption about the contiguity of separate blocks),we put the Kaffe header at the beginning of what C InterWeave considers the body of the block.A correctly initialized J-InterWeave object is shown in Figure3.Figure3:Block structure in J-InterWeaveAfter returning from newBlock,the Kaffe engine calls the class constructor and executes any user cus-tomized operations.Java Class to C Type Descriptor Before any use of a class in a J-InterWeave segment,including the creation of an InterWeave object of the type,the class object must befirst registered with RegisterClass.Register-Class uses the reflection mechanism provided by the Java runtime system to determine the following informa-tion needed to generate the C type descriptor and passes it to the registration function in the C library.1.type of the block,whether it is a structure,array orpointer.2.total size of the block.3.for structures,the number offields,eachfield’s off-set in the structure,and a pointer to eachfield’s type descriptor.4.for arrays,the number of elements and a pointer tothe element’s type descriptor.5.for pointers,a type descriptor for the pointed-to data.The registered class objects and their corresponding C type descriptors are placed in a hashtable.The new-Block later uses this hashtable to convert a class object into the C type descriptor.The type descriptor is required by the C library to allocate an InterWeave block so that it has the information to translate back and forth between local and wire format(see Section3).4.2KaffeJ-InterWeave requires modifications to the byte code in-terpreter and the JIT compiler to implementfine-grained write detection via instrumentation.It also requires changes to the garbage collector to ensure that InterWeave blocks are not accidentally collected.Figure4:Extended Kaffe object header forfine-grained write detection4.2.1Write DetectionTo support diff-based transmission of InterWeave segment updates,we must identify changes made to InterWeave objects over a given span of time.The current C ver-sion of InterWeave,like most S-DSM systems,uses vir-tual memory traps to identify modified pages,for which it creates pristine copies(twins)that can be compared with the working copy later in order to create a diff.J-InterWeave could use this same technique,but only on machines that implement virtual memory.To enable our code to run on handheld and embedded devices,we pursue an alternative approach,in which we instrument the interpretation of store bytecodes in the JVM and JIT. In our implementation,only writes to InterWeave block objects need be monitored.In each Kaffe header,there is a pointer to the object method dispatch table.On most architectures,pointers are aligned on a word boundary so that the least significant bit is always zero.Thus,we use this bit as theflag for InterWeave objects.We also place two32-bit words just before the Kaffe object header,as shown in Figure4.The second word—modification status—records which parts of the object have been modified.A block’s body is logically divided into32parts,each of which corresponds to one bit in the modification status word.Thefirst extended word is pre-computed when initializing an object.It is the shift value used by the instrumented store bytecode code to quickly determine which bit in the modification status word to set(in other words,the granularity of the write detection).These two words are only needed for In-terWeave blocks,and cause no extra overhead for normal Kaffe objects.4.2.2Garbage CollectionLike distributedfile systems and databases(and unlike systems such as PerDiS[13])InterWeave requires man-ual deletion of data;there is no garbage collection.More-over the semantics of InterWeave segments ensure that an object reference(pointer)in an InterWeave object(block) can never point to a non-InterWeave object.As a result, InterWeave objects should never prevent the collection of unreachable Java objects.To prevent Kaffe from acci-dentally collecting InterWeave memory,we modify the garbage collector to traverse only the Kaffe heap.4.3InterWeave C libraryThe InterWeave C library needs little in the way of changes to be used by J-InterWeave.When an existing segment is mapped into local memory and its blocks are translated from wire format to local format,the library must call functions in the IWSegment native library to initialize the Kaffe object header for each block.When generating a description of modified data in the write lock release operation,the library must inspect the modifi-cation bits in Kaffe headers,rather than creating diffs from the pristine and working copies of the segment’s pages.4.4DiscussionAs Java is supposed to be“Write Once,Run Anywhere”, our design choice of implementing InterWeave support at the virtual machine level can pose the concern of the portability of Java InterWeave applications.Our current implementation requires direct JVM support for the fol-lowing requirements:1.Mapping from InterWeave type descriptors to Javaobject classes.2.Managing local segments and the translation be-tween InterWeave wire format and local Java objects.3.Supporting efficient write detection for objects in In-terWeave segments.We can use class reflection mechanisms along with pure Java libraries for InterWeave memory management and wire-format translation to meet thefirst two require-ments and implement J-InterWeave totally in pure Java. Write detection could be solved using bytecode rewrit-ing techniques as reported in BIT[22],but the resulting system would most likely incur significantly higher over-heads than our current implementation.We didn’t do this mainly because we wanted to leverage the existing C ver-sion of the code and pursue better performance.In J-InterWeave,accesses to mapped InterWeave blocks(objects)by different Java threads on a single VM need to be correctly synchronized via Java object monitors and appropriate InterWeave locks.Since J-InterWeave is not an S-DSM system for Java virtual machines,the Java memory model(JMM)[26]poses no particular problems. 5Performance EvaluationIn this section,we present performance results for the J-InterWeave implementation.All experiments employ a J-InterWeave client running on a1.7GHz Pentium-4Linux machine with768MB of RAM.In experiments involving20406080100120_201_co mp r e s s _202_j e s s _205_ra y t r a c e _209_db _213_j a va c _222_m p e g a u d i o _227_m t r t _228_j a c kJVM98 BenchmarksT i m e (s e c .)Figure 5:Overhead of write-detect instrumentation in Kaffe’s interpreter mode01234567_201_c o mp r e s s _202_j e s s _205_r a y t r a c e _209_d b _213_j a v a c _222_m p e g a u d i o _227_m t r t _228_j a c k JVM98 Benchmarks T i m e (s e c .)Figure 6:Overhead of write-detect instrumentation inKaffe’s JIT3modedata sharing,the InterWeave segment server is running on a 400MHz Sun Ultra-5workstation.5.1Cost of write detectionWe have used SPEC JVM98[33]to quantify the perfor-mance overhead of write detection via bytecode instru-mentation.Specifically,we compare the performance of benchmarks from JVM98(medium configuration)run-ning on top of the unmodified Kaffe system to the per-formance obtained when all objects are treated as if they resided in an InterWeave segment.The results appear in Figures 5and 6.Overall,the performance loss is small.In Kaffe’s inter-preter mode there is less than 2%performance degrada-tion;in JIT3mode,the performance loss is about 9.1%.The difference can be explained by the fact that in inter-preter mode,the per-bytecode execution time is already quite high,so extra checking time has much less impact than it does in JIT3mode.The Kaffe JIT3compiler does not incorporate more re-cent and sophisticated technologies to optimize the gener-ated code,such as those employed in IBM Jalepeno [35]and Jackal [38]to eliminate redundant object referenceand array boundary checks.By applying similar tech-niques in J-InterWeave to eliminate redundant instrumen-tation,we believe that the overhead could be further re-duced.5.2Translation costAs described in Sections 3,a J-InterWeave application must acquire a lock on a segment before reading or writ-ing it.The acquire operation will,if necessary,ob-tain a new version of the segment from the InterWeaveserver,and translate it from wire format into local Kaffeobject format.Similarly,after modifying an InterWeavesegment,a J-InterWeave application must invoke a write lock release operation,which translates modified por-tions of objects into wire format and sends the changes back to the server.From a high level point of view this translation re-sembles object serialization ,widely used to create per-sistent copies of objects,and to exchange objects between Java applications on heterogeneous machines.In this sub-section,we compare the performance of J-InterWeave’stranslation mechanism to that of object serialization in Sun’s JDK v.1.3.1.We compare against the Sun im-plementation because it is significantly faster than Kaffe v.1.0.6,and because Kaffe was unable to successfully se-rialize large arrays in our experiments.We first compare the cost of translating a large array of primitive double variables in both systems.Under Sun JDK we create a Java program to serialize double arrays into byte arrays and to de-serialize the byte arrays backagain.We measure the time for the serialization and de-serialization.Under J-InterWeave we create a programthat allocates double arrays of the same size,releases (un-maps)the segment,and exits.We measure the releasetime and subtract the time spent on communication with the server.We then run a program that acquires (maps)the segment,and measure the time to translate the byte arrays back into doubles in Kaffe.Results are shown in Figure 7,for arrays ranging in size from 25000to 250000elements.Overall,J-InterWeave is about twenty-three times faster than JDK 1.3.1in serialization,and 8times faster in dese-rialization.5.3Bandwidth reduction To evaluate the impact of InterWeave’s diff-based wire format,which transmits an encoding of only those bytes that have changed since the previous communication,we modify the previous experiment to modify between 10and 100%of a 200,000element double array.Results appear in Figures 8and 9.The former indicates translation time,the latter bytes transmitted.20406080100120140250005000075000100000125000150000175000200000225000250000Size of double array (in elements)T i m e (m s e c .)Figure 7:Comparison of double array translation betweenSun JDK 1.3.1and J-InterWeave102030405060708090100100908070605040302010Percentage of changesT i m e (m s e c .)Figure 8:Time needed to translate a partly modified dou-ble arrayIt is clear from the graph that as we reduce the per-centage of the array that is modified,both the translationtime and the required communication bandwidth go down by linear amounts.By comparison,object serialization is oblivious to the fraction of the data that has changed.5.4J-InterWeave Applications In this section,we describe the Astroflow application,developed by colleagues in the department of Physics andAstronomy,and modified by our group to take advan-tage of InterWeave’s ability to share data across hetero-geneous platforms.Other applications completed or cur-rently in development include interactive and incremental data mining,a distributed calendar system,and a multi-player game.Due to space limitations,we do not present these here.The Astroflow [11][14]application is a visualization tool for a hydrodynamics simulation actively used in the astrophysics domain.It is written in Java,but employs data from a series of binary files that are generated sepa-rately by a computational fluid dynamics simulation sys-00.20.40.60.811.21.41.61.8100908070605040302010Percentage of changesT r a n s mi s s i o n s i z e (M B )Figure 9:Bandwidth needed to transmit a partly modified double array2040608010012014012416Number of CPUsT i m e (s e c .)Figure 10:Simulator performance using InterWeave in-stead of file I/Otem.The simulator,in our case,is written in C,and runs on a cluster of 4AlphaServer 41005/600nodes under the Cashmere [34]S-DSM system.(Cashmere is a two-level system,exploiting hardware shared memory within SMP nodes and software shared memory among nodes.InterWeave provides a third level of sharing,based on dis-tributed versioned segments.We elaborate on this three-level structure in previous papers [8].)J-InterWeave makes it easy to connect the Astroflow vi-sualization front end directly to the simulator,to create an interactive system for visualization and steering.The ar-chitecture of the system is illustrated in Figure 1(page 1).Astroflow and the simulator share a segment with one header block specifying general configuration parameters and six arrays of doubles.The changes required to the two existing programs are small and limited.We wrote an XDR specification to describe the data structures we are sharing and replaced the original file operations with shared segment operations.No special care is re-quired to support multiple visualization clients or to con-trol the frequency of updates.While the simulation data。
44 Defect-Oriented Testing in the Deep-Submicron Era High Defect Coverage with Low-Power Te

Automatic Parallelization of Scripting Languages Toward Transparent Desktop Parallel Comput
Xiaosong Ma¢¡ £ , Jiangtian Li¢¡ £ , and Nagiza F. Samatova£
facturers such as Intel and AMD have directed their development efforts to multi-core processors. These processors bring unprecedented hardware parallelism to ordinary desktop machines. As exploiting parallelism in traditional personal applications may often be limited by the inherently sequential processing manner of the human brain, it is natural to explore aggregating idle hardware for running demanding scientific computing jobs as a secondary workload.
North Carolina State University Department of Computer Engineering
Raleigh, NC 27695-8206 USA ma@
£ Oak Ridge National Laboratory Computer Science and Mathematics Division
使用并行结构的英文作文

使用并行结构的英文作文英文回答:In the realm of language, the art of parallelism holds a place of prominence. This literary device harnesses the power of repetition to create rhythm, emphasis, and clarity in prose and poetry alike. Employed skillfully, parallel structures can elevate ordinary sentences into passages of exceptional beauty and impact.Parallelism manifests in two primary forms: grammatical parallelism and syntactic parallelism. Grammatical parallelism entails the use of similar grammatical structures within a sentence, such as a series of nouns, verbs, or prepositional phrases. This repetition of form fosters a sense of balance and symmetry, guiding thereader's attention through the text. For example, consider the opening lines of Abraham Lincoln's Gettysburg Address: "Fourscore and seven years ago our fathers brought forth on this continent, a new nation, conceived in liberty, anddedicated to the proposition that all men are created equal." The parallel structure of these three phrases lends an air of solemnity and reverence to Lincoln's words, underscoring the profound significance of the nation's founding principles.Syntactic parallelism, on the other hand, involves the repetition of syntactical patterns within a sentence or passage. This technique can create a sense of rhythm and momentum, propelling the reader forward through the text. A classic example of syntactic parallelism can be found in the opening paragraph of Martin Luther King Jr.'s "I Have a Dream" speech: "I have a dream that one day this nationwill rise up and live out the true meaning of its creed:'We hold these truths to be self-evident, that all men are created equal.'" The repeated use of the phrase "I have a dream" establishes a steady cadence that buildsanticipation and reinforces the speaker's unwavering belief in the possibility of a better future.Beyond its aesthetic appeal, parallelism serves several important functions in language. It can enhance clarity byensuring that ideas are expressed in a logical and consistent manner. By highlighting similarities and contrasts, parallelism can also aid in the development of arguments and the elucidation of complex concepts. Furthermore, parallelism can create a sense of momentum and urgency, motivating the reader to engage with the text on a deeper level.In addition to its value in written language, parallelism also plays a crucial role in spoken communication. Effective public speakers often employ parallel structures to deliver memorable and impactful speeches. By repeating key phrases or ideas, speakers can reinforce their messages and create a lasting impression on their audience. Consider the famous "I Have a Dream" speech by Martin Luther King Jr., which is replete with instances of parallelism: "I have a dream that my four littlechildren will one day live in a nation where they will not be judged by the color of their skin but by the content of their character." The repetition of the phrase "I have a dream" serves to emphasize the speaker's unwavering belief in a better future and to inspire his listeners to join himin the pursuit of racial equality.The effective use of parallelism is a hallmark of skilled writers and speakers. By harnessing the power of repetition, parallelism can elevate language from the mundane to the extraordinary, captivating readers and listeners alike.中文回答:并行结构在英文中的运用。
六西格玛入门课程系列005:改进阶段简介(双语教材)(专业经典系统,新手必备,建议收藏)

Cost Ease to Implement
Effectiveness
Counteractions Fax from Master Contact List
Send Supplier E-Mail version of the PO file
Auto-fax: Modify Access Database to fax and e- mail confirm.
Data entry errors cause extra rework time.
数据录入错误导致了额外的返工时间。
Team’s Ideas for Counteracting this Cause解决这个原因的团队意见: • Fax from master contact list.来自主联系列表的传真。 • Send supplier e-mail version of the PO file.将PO文件译文邮件发送给供应商。 • Auto-fax: Modify Access Database to fax and e-mail confirm
2. Understand what is meant by “output response”, “factors” and a “designed experiment (DOE)”.了解什么是“输出响应”,“因 子”和“设计试验”。
3. Understand what is meant by a counteraction. 了解什么是解决方案。
Johnson Controls, Inc. ©
5
Improve_Mod_E_1-28-04
Methods for Determining Solutions
确定解决方案的方法
Implementation_Plan_of_International_Trade_Classro

Journal of International Education and Development2022, VOL. 6, NO. 10, 96-99DOI: 10.47297/wspiedWSP2516-250017.20220610Implementation Plan of International Trade Classroom Teaching Reform in the New Media EnvironmentAiqin WangTaishan University, Taian, ShandongABSTRACTNew media technology has become a necessary means of classroomteaching in colleges and universities. In the process of educatingstudents, strengthening the use of new media resources and promotingclassroom teaching to keep pace with the times will help to achieve themutual penetration of new media resources and various disciplines, sothat they can go together and form a synergistic effect. This paper putsforward the implementation plan of the classroom teaching reform ofinternational trade under the new media environment from threeaspects: optimizing the classroom teaching content, building thecurriculum platform, and reforming the classroom teaching methods,which is conducive to improving the enthusiasm of students and thequality of classroom teaching.KEYWORDSNew media; International trade; Teaching reform1 Optimizing Classroom Teaching Content(1) Guiding principlesIn teaching, the guiding ideology of "teaching is integrated and production, teaching and research are conducted in parallel" not only enables students to master the basic theory of international trade, but also enables students to carry out the training of "production, learning and research are conducted in parallel" by linking knowledge points together, so as to improve their practical operation ability. In the course of lectures, the basic theoretical knowledge of international trade is presented to students through systematic and perfect chapter design, so that students can learn the basic knowledge of international trade step by step from simple to deep, from easy to difficult, and form a relatively complete basic framework system of international trade.The curriculum content design is carried out around one key point and three key links. One key point is to find an effective way to integrate ideological and political elements, and to cultivate students' patriotism, integrity awareness and contract spirit by explaining the background, national policies, and professional ethics of foreign trade industry contained in the knowledge points. The three key links are: first, pay close attention to and accurately find hot and difficult issues in the field of international trade, guide students to find problems, and cultivate the ability to actively think about problems; Second, interdisciplinary, multi perspective, scientific analysis of the dynamic international trade system, through case discussions, thematic design and other ways to improve students' ability to use theory to analyze international trade issues; Third, through heuristic teaching, inquiry based teaching, problem oriented teaching, in combination with professional skills competition, special simulation practice, off campus practice and other ways, students' innovationJournal of International Education and Development97 awareness is cultivated and their ability to solve problems is improved.(2) Teaching design of international trade theoryThe course of international trade mainly includes two parts: international trade theory and international trade policy. The theoretical knowledge of international trade is abstract, obscure and boring. How to explain the part of international trade theory well is the key and difficult point in this course. To solve this problem, we need to build a systematic curriculum teaching system so that students can flexibly use theoretical knowledge to explain new international trade phenomena. The development system of international trade theory is very perfect, from classical international trade theory to neo classical international trade theory, and then to contemporary new international trade theory; From the theory of trade protection to the theory of free trade, these theories are not independent of each other, but are closely related. Only by building a systematic and perfect theoretical system of international trade can students truly understand the theoretical connotation.In the teaching process, follow the teaching idea of "leading out the theory - introducing the historical background - explaining the theoretical content - students commenting on the theory". When introducing the new trade theory, first of all, review the previous trade theory related to it to introduce the new theory to be explained; Secondly, introduce the historical background of the theory; Then, the main content of the theory is introduced in detail, and the explanation of the theoretical content is interspersed with cases to enhance the ability of the theory to solve practical problems; Finally, we will comment on the historical progress and limitations of the theory, actively guide students to participate widely, let students comment on the theory according to their own understanding, and teachers will summarize[1].(3) Integration of ideological and political elementsUnder the new media environment, the smooth implementation of classroom teaching reform is inseparable from the cultivation of students' moral quality. Actively integrate ideological and political elements into the teaching, always put the cultivation of students' ideological and moral quality in the first place, integrate patriotism into the teaching. In the process of teaching the professional knowledge of international trade, professional quality and patriotism are integrated into it, which is suitable for the needs of the educational reform of colleges and universities, students can not only learn the subject, but also improve their comprehensive quality. In classroom teaching, we always integrate excellent traditional Chinese culture and advanced socialist culture into the classroom at the right time, and guide students to make use of their knowledge to contribute to the cause of socialism with Chinese characteristics.2 Building a Course Platform(1) Building a perfect online teaching systemThe teaching reform of courses cannot be separated from the support of a perfect online teaching system. The course of international trade has been jointly built and shared by the Shandong Higher Education Curriculum Alliance, and has reached the Online Review Standards for Platform Courses. At present, it has been run simultaneously on the Smart Tree platform and offline courses. There are 764 minute learning videos on the Smart Tree platform, which cover all the contents of the ten chapters of the international trade course. Each learning video is designed with pop-up questions. Each chapter has 2-5 open chapter discussion questions, 10 chapter testAiqin Wang 98questions, and 150 final test questions.(2) Use self-compiled textbooksThe textbook has distinctive features, closely follows the hot spots of the industry. The teaching materials are rich in supporting resources and guidance cases and exercises. Instead of simply teaching students to learn theoretical knowledge, it focus on the basic operating skills and practical application abilities of international trade, so that students can have the basic skills to engage in international trade and adapt to the requirements of their posts as soon as possible after work. It pays attention to the combination with China's foreign trade practice, and each important knowledge point is accompanied by the latest international trade related cases in recent years. By integrating the latest cases into the teaching of knowledge points in the textbook, students can use the theoretical knowledge of the textbook to solve specific problems in practical business, which not only improves students' interest, but also enhances students' sense of achievement and cultivates their comprehensive quality[2].(3) Organic combination of online and offlineUnder the new media environment, advanced technical means have greatly promoted the smooth progress of classroom teaching reform. The online teaching tool Learning Connect is mainly used to achieve the organic combination of online and offline. In the classroom teaching process, we use Learning Connect to upload courseware, teaching plan and other materials to the Learning Connect platform, and upload the pre class preview content, homework after class, group discussion and other content to the Learning Connect in time. In the classroom, we use the signing in, random questions, classroom discussion, homework and other functions of the Learning Connect platform to achieve an organic combination of online and offline, and improve students' interest in learning.3 Reforming Classroom Teaching Methods(1) Adopt online and offline hybrid teaching methodUnder the new media environment, both online and offline teaching methods are indispensable, online and offline hybrid teaching methods must be adopted. In the teaching of international trade, the online wisdom tree teaching platform is mainly used for self-study, preview and review. In class, the relevant functions of the learning through teaching platform help to explain the basic content of the classroom, so as to improve students' participation in the classroom.(2) Use case teaching methodBased on the actual needs of international trade posts, adhere to the principle of close integration of theory and practice, introduce the latest cases related to international trade theory and policy in classroom teaching, reform and design the teaching content. Following the teaching mode of "case derivation - theoretical knowledge explanation - practical case analysis - knowledge point review", by inserting the latest international trade cases into the teaching of knowledge points, students have not only deepened their grasp of theoretical knowledge, but also improved their ability to solve practical problems, and fully solved the problem that the classroom teaching is dominated by single knowledge transfer and the communication between teachers and students is seriously insufficient, to truly improve students' sense of participation and initiative and return the99 Journal of International Education and Developmentclassroom to students[3].(3) Adopt methods such as "heuristic teaching, research-based learning and ability training"We should pay attention to the use of "heuristic teaching, research learning, ability training" and other methods to cultivate students' innovative consciousness, thinking mode and knowledge application ability; Change from "teaching centered" to "learning centered". In the explanation of knowledge points closely related to the practical problems of international trade, such as tariff policy, trade protection policy, non-tariff measures and other knowledge points, the teaching method of "arranging problems in advance - students looking for information before class - class group discussion - teachers' comments" is adopted to give full play to students' subjective initiative and ability to participate in the class.FundingFund projects: The special project of Tai'an City's teaching science planning "Research on the practical path of integrating curriculum ideology and politics into professional teaching under the new media environment (TJK202106ZX046)".About the AuthorAiqin Wang (1982-02), Female, Taishan University, Associate Professor, Research Field: Human Resource Management, International Trade.References[1] Li Ling, Xu Yuqin. Analysis of the Teaching Reform Path of Ideological and Political Courses in Colleges andUniversities under the New Media Environment, New West [J], 2019, (35).[2] Li Fen. Teaching Reform of Ideological and Political Theory Course in Colleges and Universities under the New MediaEnvironment, Western Quality Education [J], 2018, (24).[3] Li Mingwen, Yu Shuya. Research on the Reform of College Teaching Methods in the New Media Environment,Western Radio and Television [J], 2018, (04).。
悲伤和美丽的英语作文

悲伤和美丽的英语作文Title: The Dichotomy of Sadness and Beauty。
In the vast tapestry of human experience, sadness and beauty often intertwine, creating a complex and profound narrative of existence. Despite their seemingly disparate nature, they share a common thread that binds them together in the fabric of life.Sadness, like a heavy cloak, can envelop us in its somber embrace, weighing down our spirits with its burdensome presence. It manifests in moments of loss, disappointment, and despair, casting a shadow over our hearts and minds. Yet, within the depths of sorrow, there lies a poignant beauty—a beauty born out of resilience, empathy, and introspection.In times of sadness, we are reminded of our shared humanity, our capacity to feel deeply, to empathize with others, and to find solace in the embrace of those whounderstand our pain. It is in these moments ofvulnerability that the beauty of human connection shines brightest, illuminating the darkness with its gentle glow.Moreover, sadness serves as a catalyst for growth and transformation. It prompts us to confront our innermostfears and insecurities, to reevaluate our priorities, andto chart a new course forward. In the midst of our struggles, we discover hidden reserves of strength and courage, propelling us toward a brighter tomorrow.But alongside sadness, there exists a parallel realm of beauty—a beauty that transcends the confines of sorrow and elevates the human spirit. It reveals itself in thefleeting moments of joy, in the tender embrace of loved ones, and in the awe-inspiring wonders of the natural world.The beauty of a sunset painting the sky in hues of gold and crimson, the laughter of children echoing through the air, the gentle touch of a loved one's hand—these are the moments that remind us of the inherent goodness and beauty that permeate our world. They serve as beacons of hope,guiding us through the darkest of nights and inspiring usto persevere in the face of adversity.Yet, perhaps it is in the fusion of sadness and beauty that the true essence of life is revealed. For it is in the bittersweet symphony of joy and sorrow that we find meaning, purpose, and ultimately, redemption. Like a masterpiece painted upon the canvas of existence, each brushstroke of sadness is juxtaposed by a stroke of beauty, creating a tableau of unparalleled richness and depth.In conclusion, the interplay between sadness and beauty is a fundamental aspect of the human experience. While sadness may cast its shadow upon our lives, it is throughits juxtaposition with beauty that we discover the true richness and complexity of our existence. In embracing both the sorrow and the splendor of life, we embark on a journey of self-discovery, growth, and ultimately, transcendence.。
并行的英文作文模板

并行的英文作文模板英文:When it comes to writing a parallel essay, there are a few things to keep in mind. First and foremost, it's important to have a clear understanding of what the topicis and what the main points are that you want to make. Once you have that, you can start to think about how you want to structure your essay.One approach is to use a block structure, where you discuss one point in one paragraph and then move on to the next point in the next paragraph. Another approach is to use a point-by-point structure, where you discuss each point in each paragraph and then compare and contrast them in the conclusion.Personally, I prefer the point-by-point structure because it allows for a more in-depth analysis of each point and makes it easier to draw connections between them.For example, if I were writing an essay about the benefits of exercise, I might discuss the physical benefits in one paragraph, the mental benefits in another paragraph, and the social benefits in a third paragraph. Then, in the conclusion, I could compare and contrast these benefits and argue that exercise is an important part of a healthy lifestyle.Overall, the key to writing a successful parallel essay is to have a clear structure and to make sure that each point is well-supported with evidence and examples.中文:写并行的文章时,有几个要点需要注意。
A Parallel Implementation of Job Shop Scheduling Heuristics

U. Der
1
and K. Steinhofel
1;2
2
GMD - Research Center for Information Technology, 12489 Berlin, Germany. ETH Zurich, Institute of Theoretical Computer Science, 8092 Zurich, Switzerland.
1
Abstract. In the paper we present rst experimental results of a parallel implementation of simulated annealing-based heuristics. The heuristics are developed for the classical job shop scheduling problem that consists of l jobs where each job has to process exactly one task on each of the m machines. We utilize the disjunctive graph representation and the objective is to minimize the length of longest paths, i.e., the overall completion time of tasks. A theoretical parallelization employs O(n3 ) processors, where n = l m is the total number of tasks. Since O(n3 ) is an extremely large number of processors for real world applications, the heuristics were implemented in a distributed computing environment. The implementation is running on a cluster of 12 processors and has been applied to several benchmark problems. We compare our computational experiments to sequential results and show that stable results equal or close to optimum solutions are calculated by the parallel implementation with a high speed up. Keywords: distributed computing, job shop scheduling, simulated annealing, communication strategies, benchmark problems.
电力线路载波通道应用(POWER LINE CARRIER CHANNEL application and consideration)

Pulsar Technologies, Inc. 4050 NW 121 Avenue Coral Springs, FL 954-344-9822
Pulsar Document Number C045–P0597
POWER LINE CARRIER CHANNEL & APPLICATION CONSIDERATIONS FOR TRANSMISSION LINE RELAYING
by Miriam P. Sanders & Roger E. Ray
troduction
While the application of Power-Line Carrier is not new to the power utility industry, the people who have historically worked on this type of equipment are leaving the industry, thereby creating a tremendous void in the expertise available. This paper is a tutorial that will present the basic principles of Power-Line Carrier to assist engineers who are new to this field as well as provide some good reference material for those experienced individuals who desire refresher information. It will focus on the application of carrier in Protective Relaying schemes. History of PLC Power Line Carrier (PLC) has been around longer than you think. For example, at the turn of the 20th century, a 500 Hz signal on the power line was used to control the street lights in New York City. The transmitters and receivers were originally powered with M-G (motor-generator) sets with a tuning coil 3 feet in diameter. As technology progressed, so did the PLC equipment. There are still many transmitters and receiver sets in use today that utilize vacuum tubes, or discrete transistor logic but these are being replaced with state of the art components such as digital signal processors and other VLSI components. Today’s Usage 100 years later, the power industry still uses PLC. Although its use is expanding into the distribution area for load control and even into households for control of lighting, alarming and a/c and heating, the major application is on Transmission Lines in Protective relaying. A channel is used in line relaying so that both ends of a circuit are cleared at high speed for all faults, including end zone faults. A PLC channel can also be used to provide remote tripping functions for transformer protection, shunt reactor protection and remote breaker failure relaying. The typical application in the United States is with dedicated power line carrier, which means that one channel is used for protective relaying only. Single-sideband is used extensively in Europe and in “emerging growth countries” where many functions (relaying, voice, data, etc.) are multiplexed at the audio level (1200 to 3000 Hz) over a single RF channel (30 to 500 kHz). The trend in Europe is now changing towards dedicated carrier for relaying because fiber is taking over for generalized communications. Goals Many factors will affect the reliability of a power line carrier (PLC) channel. The goal is to get a signal level to the remote terminal that is above the sensitivity of the receiver, and with a signal-to-noise ratio (SNR) well above the minimum, so that the receiver can make a correct decision based on the information transmitted. If both of these requirements are met then the PLC channel will be reliable. The factors affecting reliability are:
parallel四级真题例句

parallel四级真题例句1.Parallel lines indicates a break in continuity.平行线表示连续的中断。
2.In plain language,China and the United States agreed on the need for parallel policies toward the world balance of power.讲得明白些,就是中国和美国同意有必要执行并行不悖的政策维持世界的均衡。
3.We may begin with an analysis exactly parallel to that of our utility theory.我们或许可从与我们的效用理论完全相似的分析开始。
4.The rapid development of numerical taxonomy over the past fifteen years has contributed to the development of parallel methods in plant ecology.数值分类学的迅速发展,虽是近十五年的事,但它对植物生态学中相应方法的发展作出了贡献。
5.For the better convenience of beholding him,I lay on my side,so that my face was parallel to his,and he stood but three yards off.为了更方便地看他,我侧身躺着,脸对着他的脸,他站在离开我只有三码远的地方。
6.Because of the increase in size,there are more myofibrilsparallel to each other and more mitochondria to supply energy.由于体积增大,就有较多的互相并联的肌原纤维,又有较多的线粒体来供应能量。
科研实验室-Rebuttal经验总结

Review中的问题整理
第二步:总结需要补的实验,第一时间跑实验
1. Inference time (frame per second, FPS) and model size are 需要补充FPS和model also very important criterions, which should be considered. size的对比结果
实际上是denser 而不是sharper
问题案例分析
实验结果类问题:
1. 可以得到的结果:直接展示,说明方法有效性 2. 无法得到的结果:简单说明原因
案例(可以得到的结果):
Q: Inference time (frame per second, FPS) and model size are also very important criterions, which should be considered.
Review和Rebuttal介绍
➢ Review和Rebuttal
1. 审稿意见 (Review):会议论文投稿之后一般3个月之内会出
Review,其中包含3-4个审稿人的评审意见。
Table 1. ICLR2018 Scores & Decisions
Oral Poster Workshop Reject
2. A simple baseline that the authors could compare with is to learn a latent representation using VAE, and then use its decoder as an initialization point for GANs.
共性问题要形 成共性回答
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Toward a parallel implementation of Concurrent MLJohn Reppy and Yingqi XiaoUniversity of ChicagoAbstract.Concurrent ML(CML)is a high-level message-passing language thatsupports the construction offirst-class synchronous abstractions called events.This mechanism has proven quite effective over the years and has been incorpo-rated in a number of other languages.While CML provides a concurrent pro-gramming model,its implementation has always been limited to uniprocessors.This limitation is exploited in the implementation of the synchronization pro-tocol that underlies the event mechanism,but with the advent of cheap parallelprocessing on the desktop(and laptop),it is time for Parallel CML.We are pursuing such an implementation as part of the Manticore project.Inthis paper,we describe a parallel implementation of Asymmetric CML(ACML),which is a subset of CML that does not support output guards.We describe anoptimistic concurrency protocol for implementing CML synchronization.Thisprotocol has been implemented as part of the Manticore system.1IntroductionConcurrent ML(CML)[1,2]is a statically-typed higher-order concurrent language that is embedded in Standard ML[3].CML extends SML with synchronous message passing over typed channels and a powerful abstraction mechanism,calledfirst-class synchronous operations,for building synchronization and communication abstractions. This mechanism allows programmers to encapsulate complicated communication and synchronization protocols asfirst-class abstractions,which encourages a modular style of programming where the actual underlying channels used to communicate with a given thread are hidden behind data and type abstraction.CML has been used success-fully in a number of systems,including a multithreaded GUI toolkit[4],a distributed tuple-space implementation[2],and a system for implementing partitioned applications in a distributed setting[5].The design of CML has inspired many implementations of CML-style concurrency primitives in other languages.These include other imple-mentations of SML[6],other dialects of ML[7],other functional languages,such as H ASKELL[8],S CHEME[9],and our own M OBY language[10],and other high-level languages,such as J AVA[11].One major limitation of CML is that its implementation is single-threaded and can-not take advantage of multicore or multiprocessor systems.1We are incorporating the CML concurrency primitives into the functional parallel-programming language Man-ticore[12,13],so this limitation must be addressed.In this paper,we take a major step in that direction by describing a parallel implementation of a subset of CML,which 1In fact,almost all of the existing implementations of events have this limitation.type’a eventval choose:(’a event*’a event)->’a eventval wrap:’a event*(’a->’b)->’b eventval guard:(unit->’a event)->’a eventval withNack:(unit event->’a event)->’a eventval sync:’a event->’aval never:’a eventval always:’a->’a eventtype’a chanval recvEvt:’a chan->’a eventval sendEvt:(’a chan*’a)->unit eventFig.1.The core features of CMLwe call Asymmetric Concurrent ML(ACML).This subset of CML includes the full set of CML combinators,but does not support output guards(i.e.,send operations in a choice).We try to provide both an intuitive explanation of the synchronization protocol that underlies ACML,as well as enough of the nitty-gritty details to help other imple-mentors.Because of space constraints,much of the implementation is omitted,but an extended version of this paper will be available as technical report[14].2A CML overviewConcurrent ML is a higher-order concurrent language that is embedded into Standard ML[1,2].It supports a rich set of concurrency mechanisms,but for purposes of this paper we focus on the core mechanisms of communication and events,which are shown in munication in CML is based on synchronous message passing on typed channels.Because channels are synchronous,both the send and receive operations are blocking.To support more complicated interactions,CML provides event values,which are first-class synchronous abstractions.Base events constructed by sendEvt and recvEvt describe simple communications on channels.There are also two special base-events: never,which is never enabled and always,which is always enabled for synchro-nization.These events can be combined into more complicated event values using the event combinators:–Event wrappers(wrap)for post-synchronization actions.–Event generators(guard and withNack)for pre-synchronization actions and cancellation(withNack).–Choice(choose)for managing multiple communications.In CML,this combi-nator takes a list of events as its argument,but we restrict it to be a binary operator here.Choice of a list of events can be constructed using choose as a“cons”oper-ator and never as“nil.”type’a queueval queue:unit->’a queueval isEmptyQ:’a queue->boolval enqueue:(’a queue*’a)->unitval dequeue:’a queue->’a optionFig.2.Specification of queue operationsTo use an event value for synchronization,we apply the sync operator to it.Event values are pure values similar to function values.When the sync operation is applied to an event value,a dynamic instance of the event is created,which we call a synchronization event.A single event value can be synchronized on many times,but each time involves a unique synchronization event.In this paper,we describe an implementation ACML,which differs from the in-terface in Figure1in that it does not have the sendEvt event constructor.Instead, sending a message is supported using the functionval send:(’a chan*’a)->unitThis function is still blocking,but does not support sending a message in a choice context.3PreliminariesWe present our implementation using SML syntax with a few extensions.To streamline the presentation,we elide several aspects of the actual implementation,such as thread IDs and processor affinity.3.1QueuesOur implementation uses queues to track pending messages and waiting threads in chan-nels.We omit the implementation details here,but give the interface to the queue oper-ations that we use in Figure2.These operations have the expected semantics.3.2Threads and thread schedulingAs in the uniprocessor implementation of CML,we usefirst-class continuations to im-plement threads and thread-scheduling.The continuation operations have the following specification:type’a contval callcc:(’a cont->’a)->’aval throw:’a cont->’a->’bWe represent the state of a suspended thread as a unit continuationtype thread=unit contThe interface to the scheduling system is represented by two atomic operations:val enqueueRdy:thread->unitval dispatch:unit->’aThefirst enqueues a ready thread in the scheduling queue and the second transfers control to the next ready thread in the scheduler queue.3.3Compare and swapOur implementation also relies on the atomic compare-and-swap instruction.We use the following SML specification for this operation:val cas:(’a ref*’a*’a)->’aNote that cas does not follow the SML equality semantics in that it performs pointer equality.With this operation,we build spinlocks:val spinLock:bool ref->unitval spinUnlock:bool ref->unitFor purposes of this paper,we assume that threads are not preempted,so spinlocks are a reasonable locking mechanism.4A parallel implementation of PCMLOur parallel implementation is based on a core subset of the CML event operations, called Primitive CML(PCML).This subset has an event type with a minimal set of combinators,a condition-variable type used for signaling,and support for channels with input events.The signature of PCML is given in Figure3.Note that unlike full CML(see Figure1),there are no guard or withNack combinators.As we discuss in Section5,these can be implemented on top of PCML.4.1The synchronization protocolThe heart of the implementation is the protocol for synchronization on a choice of events.This protocol is split between the sync operator and the base-event construc-tors(e.g.,waitEvt and recvEvt).Each base event is represented by a record of three functions:pollFn,which tests to see if the base-event is enabled(e.g.,there is a mes-sage waiting);doFn,which is used to synchronize on an enabled event;and blockFn, which is used to block the calling thread on the base event.In the single-threaded im-plementation of CML[15,2],we rely heavily on the fact that sync is executed as an atomic operation.The single-threaded protocol is as follows:1.Poll the base events in the choice to see if any of them are enabled.This phase iscalled the polling phase.signature PRIM_CML=sig(*events*)type’a evtval never:’a evtval always:’a->’a evtval choose:(’a evt*’a evt)->’a evtval wrap:’a evt*(’a->’b)->’b evtval sync:’a evt->’a(*condition variables*)type cvarval new:unit->cvarval set:cvar->unitval waitEvt:cvar->unit evt(*channels*)type’a chanval channel:unit->’a chanval recvEvt:’a chan->’a evtval send:(’a chan*’a)->unitendFig.3.Primitive CML2.If one or more base events are enabled,pick one and synchronize on it using itsdoFn.This phase is called the commit phase.3.If no base events are enabled we execute the blocking phase,which has the follow-ing steps:(a)Enqueue a continuation for the calling thread on each of the base events usingits blockFn.(b)Switch to some other thread.(c)Eventually,some other thread will complete the synchronization.We use the term synchronization setup for steps1,2,and3(a)of this protocol.Because the implementation of sync is atomic,the single-threaded implementa-tion does not have to worry about the state of a base event changing between when we poll it and when we invoke the doFn or blockFn on it.In a parallel implementation, however,the global lock would be a bottleneck,so we must design a more complicated protocol.This design is further constrained by the fact that a given event may involve multiple occurrences of the same event.For example,the following code nondetermin-isticly tags the message received from ch with either1or2:sync(choose(wrap(recvEvt ch,fn x=>(1,x)),wrap(recvEvt ch,fn y=>(2,y))))We must also avoid deadlock when multiple threads are simultaneously attempting communication on the same channel.For example,if thread P is executingsync(choose(recvEvt ch1,recvEvt ch2))at the same time that thread Q is executingsync(choose(recvEvt ch2,recvEvt ch1))we have a potential deadlock if the implementation of sync attempts to hold a lock on both channels simultaneously(i.e.,where P holds the lock on ch1and attempts to lock ch2,while Q holds the lock on ch2and attempts to lock ch1).Our approach to avoiding these pitfalls is to use an optimistic protocol that does not hold a lock on more than one channel at a time and avoids locking whenever possible. The basic protocol has a similar structure to the sequential one described above,but it must deal with the fact that the state of a base event can change before the synchro-nization setup is complete.This fact means that the commit phase may fail and that the blocking phase may commit.The parallel synchronization protocol is as follows:–The protocol starts with the polling phase,which is done in a lock-free way.–The If one or more base events are enabled,pick one and attempt to synchronize on it using its doFn.This attempt may fail because of changes in the base-event state since the polling was done.–If there are no enabled base events(or all attempts to synchronize failed),we en-queue a continuation for the calling thread on each of the base events using its blockFn.When blocking the thread on a particular base event,we may discover that synchronization is now possible,in which case we can synchronize immedi-ately.This design is guided by the goal of minimizing synchronization overhead and maxi-mizing concurrency.4.2The PCML event typeA primitive-event value is represented as a binary tree,where the internal nodes rep-resent choice and the leaves represent single synchronous operations.This canonical representation of events relies on the following equivalences:wrap(wrap(ev,g),f)=wrap(ev,f◦g)wrap(choose(ev1,ev2),f1)=choose(wrap(ev1,f),wrap(ev2,f))We use this equivalence to maintain a canonical representation of events as trees in which the leaves are wrapped base-event values and the interior nodes are choice opera-tors.Figure4illustrates the mapping from a nesting of wrap and choose combinators to its canonical representation.Another issue that we must deal with is that another thread may attempt to complete the synchronization before setup isfinished.We solve this problem by piggybacking on the mechanism used in the single-threaded implementation to do“garbage collection”of completed events.For each synchronization event,we allocate an event-state refer-ence to hold the state of the synchronization.choose choose wrap wrap wrapwrap recvrecv recv choose choose wrap wrapwrap wraprecv recv recv wrapFig.4.The canonical-event transformationdatatype event_status =INIT |WAITING |SYNCHEDtype event_state =event_status refThe INIT state denotes that event setup is in progress,WAITING denotes that setup is complete and the event is available for synchronization,and SYNCHED denotes that the event has been synchronized on.The canonical-event representation is implemented by the following datatype:datatype ’a evt=BEVT of {pollFn :unit ->bool,doFn :’a cont ->unit,blockFn :(event_state *’a cont)->unit}|CHOOSE of ’a evt *’a evtIn this type,wrapped base events are represented by three functions:the pollFn is used to poll an event to test for its availability,the doFn is used to synchronize on an enabled event,and the blockFn is used to enqueue a suspended thread on the event.Both doFn and blockFn take resumption continuations as arguments.These continuations are used to return from the invoking sync operation.Note also that the blockFn takes a state flag as an argument.This flag is enqueued along with the resume continuation in the waiting queue maintained by the underlying communication object.4.3The PCML sync operationThe implementation of the sync operation is given in Figure 5.It is structured as three functions that correspond to the items in the protocol description above.Each of these functions does a walk over the tree representation of the event value to ap-ply its operation to the base events at the leaves.The poll function polls each base event and returns a list of doFn functions for the base events that were enabled.The doEvt function,which is applied to this list,attempts to complete the synchronizationfun sync ev=callcc(fn resumeK=>let(*optimistically poll the base events*)fun poll(BEVT{pollFn,doFn,blockFn},enabled)=if pollFn()then doFn::enabledelse enabled|poll(CHOOSE(ev1,ev2),enabled)=poll(ev2,poll(ev1,enabled))(*attempt to complete an enabled communication*)fun doEvt[]=blockThd()|doEvt(doFn::r)=(doFn resumeK;(*if we get here,that means that the*attempt failed,so try the next one*)doEvt r)(*record the calling thread’s continuation in the*event waiting queues*)and blockThd()=letval flg=ref INITfun block(BEVT{blockFn,...})=blockFn(flg,resumeK)|block(CHOOSE(ev1,ev2))=(block ev1;block ev2)inblock ev;(*if we get here,then setup is complete*)flg:=WAITING;dispatch()endindoEvt(poll(ev,[]))end)Fig.5.The primitive sync operationon one of the base event’s using its doFn function.Since the state of the base event might have changed since it was polled,it possible for the doFn to fail,in which case it returns.Otherwise,it will transfer control to the resume continuation.If doEvt is unable to complete the synchronization of any of the enabled events(or there were no enabled events),then it calls blockThd.This function allocates the stateflag and then calls the blockFn of each of the base events to enqueue the resumption continuation. If the state of the base event has changed since polling(i.e.,it has become enabled), then the blockFn will complete the synchronization,otherwise it returns.If all of the blockFn s return,then the event’s state is changed to WAITING and some other thread is dispatched.INIT WAITINGSYNCHEDevent owner finishessetupanother threadsynchronizes on the eventowner synchronizesduring setup Fig.6.The state-transitions of a synchronization event.Because sync does not hold locks on the underlying communication objects,it is possible that some other thread may attempt to synchronize on one of the base events before blockThd has completed its work.Our policy is to only allow the owner thread of a synchronization event (i.e.,the caller of the sync operation)to change its state from INIT ,as is shown in Figure 6.To implement this policy,non-owners use the following utility function to change the state:fun claimEvent flg =(case cas(flg,WAITING,SYNCHED)of WAITING =>true|INIT =>claimEvent flg|SYNCHED =>false(*end case *))This function forces its caller to wait until setup is complete before being allowed to synchronize on the event.If the state is already SYNCHED ,then it returns false.An obvious simplification of this design would be to combine pollFn and doFn into a single function.There is a disadvantage of merging these two functions,however,which is that by polling all of the base events first,it is possible to impose an ordering on enabled events,such as priorities or to support fairness [2].4.4The PCML event combinatorsThe implementation of the primitive-event combinators is largely straightfoward,with the exception of wrap ,which involves both the continuation hacking needed to hook in the wrapper function and event canonicalization.The implementation of wrap is given in Figure 7.When applied to a base-event value,we need to arrange for the wrapper function (f )to be applied to the values thrown to the resumption continuation by doFn and pollFn .When applied to a CHOOSE value,it pushes the wrapper down into both branches as described by the equivalence in Section 4.2.4.5PCML channelsThe other half of the synchronization protocol is implemented in the base-event values for the communication objects.The representation of a channel consists of a spinlock,afun wrap(BEVT{pollFn,doFn,blockFn},f)=BEVT{pollFn=pollFn,doFn=fn k=>callcc(fn retK=>throw k(f(callcc(fn k’=>(doFn k’;throw retK()))))), blockFn=fn(flg,k)=>callcc(fn retK=>throw k(f(callcc(fn k’=>(blockFn(flg,k’);throw retK()))))) }|wrap(CHOOSE(ev1,ev2),f)=CHOOSE(wrap(ev1,f),wrap(ev2,f))Fig.7.The primitive wrap combinatorqueue of blocked senders(with messages),and a queue of blocked receivers(with their owner’s event state).datatype’a chan=Ch of{lock:bool ref,sendq:(’a*unit cont)queue,recvq:(event_state*’a cont)queue}The code for recvEvt is a non-trivial example of a base-event implementation and is given in Figure8.The pollFn checks to see if the channel’s sendq is empty. Since this operation only involves reading the state of the queue,it can be done without locking.Even if the results are erroneous because of conflicts with other threads,the fallback code in the doFn and blockFn will ensure correct behavior.The doFn is called when the sendq is expected to be nonempty.It locks the channel,removes an item from the sendq and then releases the lock.If the queue was empty(i.e.,NONE was returned),then the doFn returns.Otherwise,it enqueues the blocked sender and throws the message to the resume continuation of the sync operation.The blockFn is called when the sendq is expected to be empty.It also locks the channel and then checks the sendq in case its state has changed since polling.If there is an item available, then it is used to complete the synchronization.Otherwise,the resume continuation and event-stateflag are enqueued in the channel’s recvq.The send operation on channels is given in Figure9.The body of this function is a loop that examines the recvq for waiting events.If itfinds one,then it completes the synchronization,otherwise it enqueues its resume continuation and message on the sendq.5Implementing full CMLIn this section,we sketch how to build an implementation of the full set of CML event combinators from the PRIM_CML interface that we implemented in the previous sec-tion.The basic idea,which was suggested by Matthew Fluet[16],is to move the book-keeping used to track negative acknowledgments out of the implementation of sync andfun recvEvt(Ch{lock,sendq,recvq})=letfun pollFn()=not(isEmptyQ(sendq))fun doFn k=letval_=spinLock lockval item=dequeue sendqinspinUnlock lock;case itemof NONE=>()|SOME(msg,sendK)=>(enqueueRdy sendK;throw k msg)(*end case*)endfun blockFn(flg:event_state,k)=(spinLock lock;(*if we are lucky,a sender may have arrived*on the channel since we polled it.*)case dequeue sendqof SOME(msg,sendK)=>((*there is a matching send*)spinUnlock lock;flg:=SYNCHED;enqueueRdy sendK;throw k msg)|NONE=>(enqueue(recvq,(flg,k));spinUnlock lock)(*end case*))inBEVT{pollFn=pollFn,doFn=doFn,blockFn=blockFn} endFig.8.The recvEvt event constructorinto guards and wrappers.Space does not permit a complete description of this layer, but we cover the highlights.In this implementation,negative acknowledgments are signaled using the condition variables(cvars)provided by PCML.Since we must create these variables at synchro-nization time,we represent events as suspended computations(or thunks).The event type has the following definition:datatype’a event=E of(cvar list*(cvar list*’a thunk)PCML.evt)thunk where the thunk type istype’a thunk=unit->’afun send(Ch{lock,sendq,recvq},msg)=callcc(fn sendK=>let val_=spinLock lockfun tryLp()=(case dequeue recvqof SOME(flg,recvK)=>(*there is a matching recv,but we must*check to make sure that some other*thread has not already claimed the event.*)if claimEvent flgthen((*we got it*)spinUnlock lock;enqueueRdy sendK;throw recvK msg)else(*someone else got the event*)tryLp()|NONE=>(enqueue(sendq,(msg,sendK));spinUnlock lock;dispatch())(*end case*))intryLp()end)Fig.9.The send operationThe outermost thunk is a suspension used to delay the evaluation of guards until syn-chronization time.When evaluated,it produces a list of cvars and a primitive event. The cvars are used to signal the negative acknowledgments for the event.The primitive event,when synchronized,will yield a list of those cvars that need to be signaled and a thunk that is the suspended wrapper action for the event.With this representation,the sync operation is straightforward.fun sync(E thunk)=letval(_,ev)=thunk()val(cvs,act)=PCML.sync evinList.app PCML.set cvs;act()endWe start by evaluating the top-level thunk to get the primitive event value,which we then synchronize on.The result of synchronization will be a list of cvars that need tobe signaled and the wrapper thunk.We signal the nacks by setting the cvars and then evaluate the wrapper thunk.The two combinators that are at the heart of the bookkeeping for negative acknowl-edgments are withNack and choose.The former creates a new cvar when its thunkis evaluated.This cvar is passed as an argument to withNack’s argument and is addedto the list of cvars for its result.fun withNack f=letfun thunk()=letval nack=PCML.new()val E thunk’=f(baseEvt(PCML.waitEvt nack))val(cvs,ev)=thunk’()in(nack::cvs,ev)endinE thunkendThe purpose of negative acknowledgments is to signal that some other event in a choice was chosen,which means that the choose combinator must associate the cvars of its left side with the synchronization result of its right side(and vice versa).fun choose(E thunk1,E thunk2)=letfun thunk()=letval(cvs1,ev1)=thunk1()val(cvs2,ev2)=thunk2()in(cvs1@cvs2,PCML.choose(PCML.wrap(ev1,fn(cvs,th)=>(cvs@cvs2,th)),PCML.wrap(ev2,fn(cvs,th)=>(cvs@cvs1,th))) )endinE thunkendSpace does not permit a description of the other mechanisms,but they can be found in a forthcoming technical report[14].6Related workVarious authors have described implementations of choice protocols using message passing as the underlying mechanism[17–20].While these protocols could,in prin-ciple,be mapped to a shared-memory implementation,we believe that our approach is both simpler and more efficient.Russell described a monadic implementation of CML-style events on top of Con-current Haskell[8].His implementation uses Concurrent Haskell’s M-vars for concur-rency control and he uses an ordered two-phase locking scheme to commit to commu-nications.A key difference in his implementation is that choice is biased to the left, which means that he can commit immediately to an enabled event during the polling phase.This feature greatly simplifies his implementation,since it does not have to han-dle changes in event status between the polling phase and the commit phase.Russell’s implementation did not support multiprocessors(because Concurrent Haskell did not support them at the time),but presumably would work on a parallel implementation ofConcurrent Haskell.Donnelly and Fluet have implemented a version of events that sup-port transactions on top of Haskell’s STM mechanism[16].Their mechanism is quite powerful and,thus,their implementation is quite complicated.In earlier work,we reported on specialized implementations of CML’s channel op-erations that can be used when program analysis determines that it is safe[21].Those specialized implementationsfit into our framework and can be regarded as complemen-tary.7ConclusionWe have described a new protocol for implementing Asymmetric CML on multiproces-sors.This implementation consists of a primitive layer that provides basic synchronous operations,non-deterministic choice,and post-synchronization wrappers.This layer is implemented using a new optimistic-concurrency protocol.The full set of CML event combinators is then constructed on top of this primitive layer.One advantage of this ar-chitecture is that the more complicated upper layer does not directly use locks or thread scheduling operations.We have implemented the primitive layer in the Manticore system using the Manti-core compiler’s BOM intermediate representation[13].This implementation must also deal with preemption,which we do by locally masking preemption.Unfortunately, Manticore is not yet stable enough to be able to run meaningful performance tests, although we have been able to test the correctness of the implementation on an8-way parallel system.We expect that the basic performance of the primitives will be good when channels are used to implement point-to-point communications(as is common), but the interesting question will be how they perform in a situation with many senders or receivers sharing a single channel.We plan to provide preliminary performance results in a forthcoming technical report[14].In the longer term,we want to extend the PCML layer to support output guards(i.e., sendEvt).In our protocol,adding this event constructor complicates the implemen-tation in a couple of significant ways.First,it becomes possible to write code that has matching communications in a single choice,as in the following example:sync(choose(recvEvt ch,wrap(sendEvt(ch,1),fn()=>2)))The implementation must detect such cases and avoid having a thread communicate with itself.The second problem is that committing to a synchronization will require atomically updating the states of two different synchronization events.Two-phase lock-ing is one possible solution,but it requires introducing a linear order on synchronization events to avoid deadlock.Instead,we are exploring the use of implementation tech-niques from STM[22],but we have not worked out the details.References1.Reppy,J.H.:CML:A higher-order concurrent language.In:PLDI’91,New York,NY,ACM(June1991)293–305。
