Specification and Enforcement of Access Control in Heterogeneous Distributed Applications
电位器3296

Specifications are subject to change without notice.Customers should verify actual device performance in their specific applications.Electrical Characteristics Standard Resistance Range........................10 ohms to 2 megohms(see standard resistance table)Resistance Tolerance............±10 % std.(tighter tolerance available)Absolute Minimum Resistance..............................1 % or 2 ohms max.(whichever is greater)Contact Resistance Variation...........................1.0 % or 3 ohms max.(whichever is greater)AdjustabilityVoltage.....................................±0.01 %Resistance...............................±0.05 %Resolution.....................................Infinite Insulation Resistance................500 vdc.1,000 megohms min.Dielectric StrengthSea Level..................................900 vac 70,000 Feet...............................350 vac Effective Travel..................25 turns nom.Environmental Characteristics Power Rating (300 volts max.)70 °C ........................................0.5 watt 125 °C .........................................0 watt Temperature Range..................................-55 °C to +150 °C Temperature Coefficient....±100 ppm/°C Seal Test.......................85 °C Fluorinert*-STD-202 Method 10396 hours(2 % ∆TR, 10 Megohms IR)Vibration.........20 G (1 % ∆TR; 1 % ∆VR)Shock...........100 G (1 % ∆TR; 1 % ∆VR)Load Life...............1,000 hours 0.5 watt @ 70 °C(3 % ∆TR; 3 % or 3 ohms,whichever is greater, CRV)Rotational Life........................200 cycles(4 % ∆TR; 3 % or 3 ohms,whichever is greater, CRV)Physical CharacteristicsTorque .............................3.0 oz-in. max.Mechanical Stops..................Wiper idles Terminals........................Solderable pins Weight ........................................0.03 oz.Marking...........................Manufacturer’strademark, resistance code,wiring diagram, date code,manufacturer’s modelnumber and styleWiper..................................50 % ±10 %Flammability ..........................U.L. 94V-0Standard Packaging.....50 pcs. per tube Adjustment Tool..............................H-90Common Dimensions3296X3296Z (Commercial Only)Resistance Resistance (Ohms)Code 1010020200505001001012002015005011,0001022,0002025,00050210,00010320,00020325,00025350,000503100,000104200,000204250,000254500,0005041,000,0001052,000,000205Standard Resistance TableA V A I L AB L E T H R O U G H D I S T R I B U T I O N*”FLUORINERT” IS A REGISTERED TRADEMARK OF 3M CO.Popular values listed in boldface. Special resistances available.How to Order3296 W - 1 - 103 __ LFModel StyleStandard or Modified Product Indicator-1 = Standard Product Resistance CodePackaging DesignatorBlank =Tube (Standard)R =T ape and Reel (X and W Pin StylesOnly)A =Ammo Pack (X and W Pin Styles Only)TerminationsLF =100 % Tin-plated (lead free)Blank =90 % Tin / 10 % Lead-plated Consult factory for other available options.Specifications are subject to change without notice.Customers should verify actual device performance in their specific applications.SIDE ADJUST 3296X-1TOP ADJUST 3296W-11000/REEL/BOXPackaging SpecificationsMeets EIA Specification 468.REV. 06/04。
USP药典的验证中英文对照

VALIDATION OF COMPENDIAL PROCEDURES 药典方法的验证Test procedures for assessment of the quality levels of pharmaceutical articles are subject to various requirements. According to Section 501 of the Federal Food, Drug, and Cosmetic Act, assays and specifications in monographs of the United States Pharmacopeia and the National Formulary constitute legal standards. The Current Good Manufacturing Practice regulations [21 CFR 211.194(a)] require that test methods, which are used for assessing compliance of pharmaceutical articles with established specifications, must meet proper standards of accuracy and reliability. Also, according to these regulations [21 CFR 211.194(a)(2)], users of analytical methods describedin USP–NF are not required to validate the accuracy and reliability of these methods, but merely verify their suitability under actual conditions of use. Recognizing the legal status of USP and NF standards, it is essential, therefore, that proposals for adoption of new or revised compendial analytical procedures be supported by sufficient laboratory data to document their validity.用于评估药品质量的检验方法需要满足不同的要求。
ep15-a3verificationofprecisionandestimationofbias

CLSI EP15-A3: verification of precision and estimation of biasWe are pleased to have a guest essay explaining the latest in Method Verification, specifically the newest version of the CLSI guideline EP15 on Method Verification. For labs seeking a qui ck check to insure their methods are meeting manufacturer specifications, EP15 may be the r ight choiceWhat's New in CLSI EP15-A3: User Verification of Precision and Estimation of Bias; Ap proved Guideline -Third Edition R. Neill Carey, Ph.D. July 2015IntroductionCLSI EP15 was released as an A3 document in September 2014. This is its fourth iteration, and alt hough it retains much of its original approach, there were some significant changes in the A3 vers ion.The most significant change is the creation of a relatively simple experiment that gives reliable es timates of a measurement procedure's imprecision and its bias. The essentials to accomplish this were present in EP15 through all of its previous versions, but they are refined and combined in EP 15-A3 to make a single experiment. Here's a brief description of the protocol.Specification of Acceptable PerformanceBefore doing anything else, the user should specify total allowable error, and derive from it the all owable standard deviation (or %CV), and the allowable bias. The user should ascertain that the i mprecision of the candidate measurement procedure meets the criterion for allowable imprecisi on before beginning the evaluation. If the measurement procedure's imprecision reported in publ ications, such as the manufacturer's stated imprecision, does not meet the criterion, the precisio n verification procedure described in EP15-A3 is not appropriate. Being a limited experiment, it is less rigorous than the experiment described in CLSI EP5-A3, which would be mor e appropriate.Verification of PrecisionEP15 first describes a precision verification experiment. If the user is evaluating a procedure for w hich there are manufacturer's precision claims, or published precision results, that were developed using CLSI EP5, the user can verify the published precision in an experiment lasting as few as five days.Patient samples, reference materials, proficiency testing samples, or control materials may be use d as the test samples, provided there is sufficient sample material for testing each sample five tim es per run for five to seven runs. Precision should be tested with two or more sample materials at different medical decision pointconcentrations. The experiment produces at least 25 replicates collected over at least 5 days for e ach sample material.The repeatability (previously termed "within-run") and the within-laboratory (previously termed "total") standard deviations are calculated by an analysis of variance technique (ANOVA) that pro perly accounts for the within-run andbetween-run contributions to the overall imprecision of the measurement procedure. The user n eeds access to software to do the ANOVA calculations, but they areavailable in Excel, Minitab, Analyze-it, and other software packages that do statistical calculations . The repeatability and within-laboratory standard deviations are then compared to the claimed o r published standard deviations. If the calculated standard deviations are less than the published values, the user has verified the claim. Sometimes the calculated standard deviations may exceed the published values, and yet the true standard deviations are less than the published values. For example, if the true standard deviations were actually exactly equal to their claimed counterpart s, the calculated standard deviations would exceed their published counterparts fifty percent of t he time in verification experiments. To allow for this possibility, the user calculates a "verification limit" based on the published standard deviation and the size of the user's experiment. If the calc ulated standard deviation is less than the verification limit, it is not statistically significantly larger than the published standard deviation, and the user has verified the published precision. If the ca lculated precision exceeds the verification limit, the calculated standard deviation is statistically si gnificantly larger than the published standard deviation, and the user has failed to verify the publ ished imprecision. The document includes tables to simplify the calculation of the verification limi t.Estimation of BiasBecause the precision experiment has so many replicate measurements, collected over several da ys, results from the precision experiment may be used to make a reliable estimate of the bias of t he measurement procedure relative to the assigned (target) values of the sample materials used i n the experiment. The only requirement is that the assigned value must be available. The choice of material depends on the purpose of the user in estimating the bias. Two or more appropriate materials should be tested in the precision experiment.If the user is interested in estimating bias relative to the peer group for proficiency testing, and w ants to estimate how the measurement procedure will perform well on proficiency testing, profici ency testing materials with peer group values for the measurement procedure being evaluated ar e appropriate.For bias relative to the quality control peer group, quality control materials with peer group value s for the measurement procedure are appropriate. "Assayed" quality control materials are not ap propriate, unless peer group information is available. Typically, there is no way to estimate the un certainty of the "assayed" values, which is needed to determine if the calculated bias is statisticall y significant.Internationally recognized high order reference materials, such as a material from the U.S. Nation al Institute of Standards and Technology, or from the Joint Committee for Traceability in Laborato ry Medicine, or from similar organizations may be appropriate if the user wishes to estimate the bias relative to the assignedconcentrations of such materials. Use of these materials is important in establishing the traceabili ty of measurement procedures.Patient samples or control materials which have been repeatedly assayed with a measurement pr ocedure felt to be substantially equivalent to the measurementprocedure being evaluated may be appropriate if the user is interested in estimating bias relativeto that measurement procedure. This could be useful, for example, if the intent of the experimen t was to estimate the bias of one laboratory in a system relative to another, or to the mean of the laboratories in a system.If the sample materials are appropriate, and target concentrations are available, the user can esti mate the bias between the mean concentration calculated in the precision experiment relative to the target concentration of each of the materials.To determine whether there is any statistically significant bias between the mean concentration c alculated from the experiment and the target concentration, the user calculates a “v erification int erval” around the target concentration. The width of the verification interval depends on the unc ertainty of the target value of the reference material and the standard error of the calculated me an concentration from the experiment. Calculation of the verification interval would be complicat ed, but the committee simplified it greatly by providing tables for the difficult-to-calculate quantities based on the number of replicate measurements per run, the number of runs, and the uncertainty of the target value.If the mean concentration from the user's experiment is within the verification interval, there is n o statistically significant bias.。
灭火器设置法律要求和标准规范文件

英文回答:In accordance with the Law of the People ' s Republic of Chinaon Fire Protection and the relevant regulations, all units and individuals are required to set up fire extinguishers in strictpliance with national regulations and to ensure that fire—fighting facilities are fully and fully equipped and that inspections and maintenance are carried out on a regular basis。
Documents such as the building design fire code and the building design code fire technical regulations set out fire extinguisher specifications for different types of buildings in the design and construction process and must be implemented in accordance with strict requirements。
The policy is directed towards ensuring fire safety and the safety of people ' s livesand property, with the active cooperation of any unit or individual and the effective implementation of the relevant obligations。
FDA 21 CFR QSR820 中英文对照版本

820.198 Complaint files.
客户抱怨文件
Subpart N—Servicing
820.200 Servicing.
Subpart O—Statistical Techniques
820.250 Statistical techniques.
Authority: Secs. 501, 502, 510, 513, 514, 515, 518, 519, 520, 522, 701, 704, 801, 803 of the Federal Food, Drug, and Cosmetic Act (21 U.S.C. 351, 352, 360, 360c, 360d, 360e, 360h, 360i, 360j, 360l, 371, 374, 381, 383).
产品包装
Subpart L—Handling, Storage, Distribution, and Installation
L部分——操作、存储、分配以及安装
820.140 Handling.
操作
820.150 Storage.
存储
820.160 Distribution.
分配
820.170 Installation.
设计控制
Subpart D—Document Controls
D部分——文件控制
820.40 Document controls.
文件控制
Subpart E—Purchasing Controls
E部分——采购控制
820.50 Purchasing controls.
采购控制
Subpart F—Identification and Traceability
美国药品生产质量管理规范-中英文对照

GOOD MANUFACTURE PRACTICE 美国药品生产质量管理规范(CGMP)二○○三年十二月目录210.1 cGMP法规的地位 (2)210.2 cGMP法规的适用性 (2)210.3 定义 (2)211-A- 总则 (4)211-B- 组织与人员 (4)211-C- 厂房和设施 (5)211-D- 设备 (7)211-E- 成份、药品容器和密封件的控制 (8)211-F- 生产和加工控制 (10)211-G- 包装和标签控制 (11)211-H- 贮存和销售 (13)211-I- 实验室控制 (14)211-J- 记录和报告 (16)211-K- 退回的药品和回收处理 (20)210部分—人用及兽用药品的生产、加工、包装或贮存的CGMPPart 210 - CURRENT GOOD MANUFACTURING PRACTICE IN MANUFACTURING, PROCESSING, PACKING, OR HOLDING OF DRUGS; GENERAL210.1 cGMP法规的地位§ 210.1 Status of current good manufacturing practice regulations.(a) 在本部分及21CFR 211—226部分中陈述的法规是在药品生产、加工、包装或贮存中使用的现行生产质量管理规范及使用的设施或控制的最低标准,以保证该药品符合联邦食品、药品及化妆品法对安全性的要求,具有均一性和效价(或含量)并符合或代表其生产过程的质量及纯度等特征。
(a) The regulations set forth in this part and in Parts 211 through 226 of this chapter contain the minimum current good manufacturing practice for methods to be used in, and the facilities or controls to be used for, the manufacture, processing, packing, or holding of a drug to assure that such drug meets the requirements of the act as to safety, and has the identity and strength and meets the quality and purity characteristics that it purports or is represented to possess.(b) 凡是在药品生产、加工、包装或贮存过程中存在任何不符合本部分及21CFR 211—226部分中陈述的法规的药品,依据联邦食品、药品及化妆品法501 (a)(2)-(B),该药应被视为劣药,同时导致该事故发生的负责人应受相应的法规的制裁。
Law Enforcement, Malfeasance, andCompensation of Enforcers

Law Enforcement, Malfeasance, and Compensation of EnforcersAuthor(s): Gary S. Becker and George J. StiglerSource: The Journal of Legal Studies, Vol. 3, No. 1 (Jan., 1974), pp. 1-18Published by: The University of Chicago PressStable URL: /stable/724119Accessed: 18/11/2010 00:18Your use of the JSTOR archive indicates your acceptance of JSTOR's Terms and Conditions of Use, available at/page/info/about/policies/terms.jsp. JSTOR's Terms and Conditions of Use provides, in part, that unless you have obtained prior permission, you may not download an entire issue of a journal or multiple copies of articles, and you may use content in the JSTOR archive only for your personal, non-commercial use.Please contact the publisher regarding any further use of this work. Publisher contact information may be obtained at/action/showPublisher?publisherCode=ucpress.Each copy of any part of a JSTOR transmission must contain the same copyright notice that appears on the screen or printed page of such transmission.JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact support@.The University of Chicago Press is collaborating with JSTOR to digitize, preserve and extend access to TheJournal of Legal Studies.。
世界海关组织海关专业词汇汉译表
《国际道路运输公约》知识产权知识产权《伊斯坦布尔公约》转移定价知识产权知识产权知识产权知识产权廉政转移定价原产地转移定价《国际道路运输公约》《伊斯坦布尔公约》转移定价转移定价廉政《伊斯坦布尔公约》《濒危野生动植物种国际贸易公约》转移定价《国际道路运输公约》转移定价原产地《伊斯坦布尔公约》协调制度《濒危野生动植物种国际贸易公约》转移定价转移定价知识产权《濒危野生动植物种国际贸易公约》知识产权知识产权知识产权《濒危野生动植物种国际贸易公约》原产地原产地原产地原产地知识产权转移定价原产地《国际道路运输公约》《濒危野生动植物种国际贸易公约》《伊斯坦布尔公约》《伊斯坦布尔公约》知识产权《伊斯坦布尔公约》《伊斯坦布尔公约》转移定价转移定价转移定价《国际道路运输公约》, 《世界海关组织贸易安全与便利标准框架》,《国际道路运输公约》知识产权知识产权转移定价知识产权协调制度协调制度《濒危野生动植物种国际贸易公约》知识产权知识产权《国际道路运输公约》转移定价原产地《伊斯坦布尔公约》《伊斯坦布尔公约》《伊斯坦布尔公约》, 《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》《国际道路运输公约》转移定价转移定价转移定价转移定价转移定价《国际道路运输公约》《伊斯坦布尔公约》《伊斯坦布尔公约》, 《国际道路运输公约》《伊斯坦布尔公约》知识产权《国际道路运输公约》《濒危野生动植物种国际贸易公约》《世界海关组织贸易安全与便利标准框架》《世界海关组织贸易安全与便利标准框架》廉政, 《世界海关组织贸易安全与便利标准框架》《国际道路运输公约》廉政《伊斯坦布尔公约》《伊斯坦布尔公约》知识产权转移定价《伊斯坦布尔公约》转移定价。
联合国国际货物销售合同公约(CISG)逐句中英文对照

合国国际货物销售合同公约(逐句中英文对照)联合国国际货物销售合同公约(United Nations Convention on Contractsfor the International Sale of Goods (1980) )PreambleThe States Parties to this Convention Bearing in Mind the broad objectives in the resolutions adopted by the sixth special session of the General Assembly of the United Nations on the establishment of a New International Economic Order. Considering that the development of international trade on the basis of equality and mutual benefit is an important element in promoting friendly relations among States, Being of the Opinion that the adoption of uniform rules which govern contracts for the international sale of goods and take into account the different social, economic and legal systems would contribute to the removal of legal barriers in international trade and promote the development of international trade, have decreed as follows:本公约个缔约国: 铭记联合国大会第六界特别会议通过的关于建立新的国际经济次序的各项决议的广泛目标, 考虑到在平等互利基础上发展国际贸易, 是促进各国间友好关系的一个重要因素, 认为采用照顾到不同的社会, 经济和法律制度的国际货物销售合同统一规则,将有助于减少国际贸易的法律障碍, 促进国际贸易的发展 .兹协议如下 .PART ISphere of Application and General ProvisionsChapter ISphere of ApplicationArticle 1(1) This Convention applies to contracts of sale of goods between parties whose places of business are in different States: ( 本公约适用于营业地在不同国家的当事人之间所订立的货物销售合同,)(a) when the States are Contracting States; or ( 如果这些国家是缔约国, 或)(b) when the rules of private international law lead to the application of the law of a Contracting State. ( 如果国际私法规则导致适用某一缔约国的法律,)(2) The fact that the parties have their places of business in different States is to be disregarded whenever this fact does not appear either from the contract or from any dealings between, or from information disclosed by, the parties at any time before or at the conclusion of the contract. ( 当事人营业地在不同国家的事实,如果从合同或从订立合同前任何时候或订立合同时, 当事人之间的任何交易或当事人透露的情报均看不出, 应不予考虑)(3) Neither the nationality of the parties nor the civil or commercial character of the parties or of the contract is to be taken into consideration in determining the application of this Convention. ( 在确定本公约的适用时, 当事人的国籍和当事人或合同的民事或商业性质,应不予考虑)Article 2This Convention does not apply to sales: ( 本公约不适用以下的销售)(a) of goods bought for personal, family or household use, unless the seller, at any time before or at the conclusion of the contract, neither knew nor ought to have known that the goods were bought for any such use; ( 购供私人, 家人或家庭使用的货物销售, 除非卖方再订立合同前任何时候或订立合同时不知道而且没有理由知道这些货物是购供任何这种使用)(b) by auction; ( 经由拍卖销售的)(c) on execution or otherwise by authority of law; ( 根据法律执行令状或其他领状的销售)(d) of stocks, shares, investment securities, negotiable (可通过谈判解决的)instruments (手段)or money;( 公债,股票,投资证券, 流通票据或是货币的销售)(e) of ships, vessels (船只), hovercraft (水翼船)or aircraft;( 船舶船只,气垫船或是飞机的销售)(f) of electricity. ( 电力的销售)Article 3(1) Contracts for the supply of goods to be manufactured or produced are to be considered sales unless the party who orders the goods undertakes to supply a substantial part of the materials necessary for such manufacture or production.( 供应尚待制造或生产的货物的合同应视为销售合同, 除非订购货物的当事人保证供应这种制造或生产所需的大部分重要材料 .)(2) This Convention does not apply to contracts in which the preponderant( 优势的) part of the obligations of the party (当事人)who furnishes the goods consists in the supply of labour or other services.( 本公约不适用于供应货物一方的绝大部分义务在于供应劳力或其它服务的合同)Article 4This Convention governs only the formation (形成)of the contract of sale and the rights and obligations of the seller and the buyer arising from (产生)such a contract. In particular, except as otherwise expressly (明确地)provided in this Convention, it is not concerned with: ( 本公约只适用于销售合同的订立和卖方和买方因此种合同而产生的权利和义务. 特别是本公约除非另有明文规定, 与以下事项无关:)(a) the validity (效力)of the contract or of any of its provisions(供应)or of any usage;( 合同的效力,或其任何条款的效力,或任何惯例的效力)(b) the effect which the contract may have on the property in the goods sold. (合同对所销售物所有权可能产生的影响。
符合计量制度和合同要求

符合计量制度和合同要求Ensuring compliance with measurement standards and contract requirements is crucial in any business operation. It not only demonstrates professionalism and integrity but also plays a vital role in maintaining the trust of customers and upholding the reputation of the company. 保证符合计量标准和合同要求对于任何企业运营都至关重要。
这不仅表明专业精神和诚信,而且在维护客户的信任和实践公司的声誉方面发挥着至关重要的作用。
From a legal perspective, adherence to measurement standards and contract requirements is necessary to avoid any potential disputes or legal issues that may arise from inaccuracies or discrepancies. Therefore, it is essential for businesses to have clear and well-defined policies and procedures in place to ensure that all measurements and contractual obligations are met. 从法律的角度来看,遵守计量标准和合同要求是必要的,以避免由于不准确或不一致而可能产生的任何潜在争议或法律问题。
因此,企业有必要确立明确和定义清晰的政策和程序,以确保满足所有的计量和合同义务。
最新21CFRPART11企业指南中英对照

最新21CFRPART11企业指南中英对照Guidance for IndustryPart11,Electronic Records;Electronic Signatures —Scope and ApplicationAugust2003Pharmaceutical CGMPsFDA工业指南联邦法规11部分电子记录和电子签名—范围和应用2003年8月药物CGMPsTABLE OF CONTENTS目录I.Introduction (2)II.Background (3)III.Discussion (5)A.Overall Approach to Part11Requirements (5)B.Details of Approach-Scope of Part11 (6)1.Narrow Interpretation of Scope (6)2.Definition of Part11Records (7)C.Approach to Specific Part11Requirements (9)1.Validation (9)2.Audit Trail (9)3.Legacy Systems (10)4.Copies of Records (11)5.Record Retention (12)IV.REFERENCES (13)This guidance represents the Food and Drug Administration's(FDA's)current thinking on this topic.It does not create or confer any rights for or on any person and does notoperate to bind FDA or the public.You can use an alternative approach if the approach satisfies the requirements of the applicable statutes and regulations.If you want to discuss an alternative approach,contact the FDA staff responsible for implementing this guidance.If you cannot identify the appropriate FDA staff,call the appropriate number listed on the title page of this guidance.I.IntroductionThis guidance is intended to describe the Food and Drug Administration's(FDA’s)current thinking regarding the scope and application of part11of Title 21of the Code of Federal Regulations;Electronic Records;Electronic Signatures(21CFR Part11).This document provides guidance to persons who,in fulfillment of a requirement in a statute or another part of FDA's regulations to maintain records or submit information to FDA,have chosen to maintain the records or submit designated information electronically and,as a result,have become subject to part11.Part11applies to records in electronic form that are created,modified,maintained,archived, retrieved,or transmitted under any records requirements set forth in Agency regulations.Part11 also applies to electronic records submitted to the Agency under the Federal Food,Drug,and Cosmetic Act(the Act)and the Public Health Service Act(the PHS Act),even if such records are not specifically identified in Agency regulations(§11.1).The underlying requirements set forth in the Act,PHS Act, and FDA regulations(other than part11)are referred to in this guidance document as predicate rules.As an outgrowth of its current good manufacturing practice(CGMP)initiative for human and animal drugs andbiologics,FDA is re-examining part11as it applies to all FDA regulated products.We anticipate initiating rulemaking to change part11as a result of that re-examination.This guidance explains that we 本指南代表了FDA在此领域的当前思路,它不赋予任何人任何权利,也并非用于约束FDA或公众。
reach附件17使用范围

reach附件17使用范围From a legal perspective, the reach附件17使用范围must be interpreted in accordance with the REACHlegislation and any relevant case law. This requires a thorough understanding of the legal framework surrounding reach附件17, including its objectives, scope, and specific restrictions. Legal experts and practitioners mustcarefully analyze the language of the regulation, as well as any guidance provided by the European Chemicals Agency (ECHA) or other relevant authorities. It is essential to ensure compliance with reach附件17 in order to avoid potential legal consequences and protect public and environmental health.From a business perspective, reach附件17使用范围presents challenges and opportunities for companies operating within the EU. Businesses must carefully assess the impact of reach附件17 on their operations, supply chains, and product offerings. This may involve conducting thorough risk assessments, engaging with suppliers andmanufacturers, and implementing appropriate risk management measures. Compliance with reach附件17 is not only a legal requirement but also a business imperative, as failure to adhere to the regulation can result in reputational damage and loss of market access.From a scientific and technical perspective, reach附件17使用范围 requires a deep understanding of the properties and potential hazards of the substances and mixtures covered by the regulation. This involves conducting comprehensive chemical safety assessments, toxicological studies, and exposure evaluations. Scientists and technical experts play a crucial role in providing the necessary data and expertise to support compliance with reach附件17. They must also stay abreast of any developments in the field of chemical safety and regulatory requirements to ensure that their knowledge remains current and relevant.From a public health and environmental perspective, reach附件17使用范围 is aimed at protecting human health and the environment from the risks posed by certain hazardous substances. It is essential to consider thepotential benefits of reach附件17 in terms of reducing exposure to harmful chemicals and preventing adverse health effects. At the same time, it is important to address any potential challenges or unintended consequences that may arise from the implementation of the regulation. Public health officials, environmental advocates, and community stakeholders all have a vested interest in ensuring that reach附件17 effectively fulfills its protective objectives.From a global perspective, reach附件17使用范围 has implications beyond the borders of the EU. As a major regulatory framework for chemicals management, REACH has a significant impact on global supply chains and trade. Companies operating outside the EU must also take reach附件17 into account if they wish to access the European market. This requires collaboration and coordination between regulatory authorities, industry stakeholders, and international organizations to promote harmonization and mutual recognition of chemical safety standards. The global reach of reach附件17 underscores the importance of a coordinated and cooperative approach to chemicals management on a worldwide scale.In conclusion, reach附件17使用范围 is a multifaceted issue that requires careful consideration from legal, business, scientific, public health, environmental, and global perspectives. By approaching this problem from multiple angles, it is possible to gain a comprehensive understanding of the challenges and opportunities associated with the regulation. Collaboration and dialogue between stakeholders from diverse backgrounds are essential to ensure that reach附件17 effectively achieves its objectives while minimizing any potential adverse effects.。
gmp对销售合同内容具体要求

gmp对销售合同内容具体要求英文回答:A sales contract is a legally binding agreement between a buyer and a seller that outlines the terms and conditions of a sale. The content of a sales contract can vary depending on the specific transaction and the parties involved. However, there are some common requirements that are typically included in a sales contract.Firstly, a sales contract should clearly state the identities of the buyer and the seller. This includes their names, addresses, and contact information. This is important to establish the parties involved in the transaction and to ensure that there is clear communication throughout the process.Secondly, a sales contract should specify the details of the goods or services being sold. This includes a description of the products or services, the quantity,quality, and any specifications or requirements. It is important to be specific and detailed in this section to avoid any misunderstandings or disputes in the future.Thirdly, a sales contract should outline the terms of payment. This includes the total purchase price, any applicable taxes or fees, and the payment method and schedule. It is important to clearly state the payment terms to ensure that both parties are aware of their obligations and responsibilities.Furthermore, a sales contract should include the terms and conditions of delivery. This includes the mode of transportation, the delivery date or timeline, and any additional costs or responsibilities related to delivery. It is important to specify these details to avoid any confusion or disputes regarding the delivery of the goods or services.Additionally, a sales contract should address any warranties or guarantees. This includes any warranties provided by the seller regarding the quality, performance,or durability of the goods or services. It is important to clearly state the terms and conditions of any warranties to protect the rights and interests of both parties.Moreover, a sales contract should include provisionsfor dispute resolution. This can include a clause specifying the jurisdiction and venue for any legal proceedings, as well as any alternative dispute resolution methods such as mediation or arbitration. Including these provisions can help to resolve any potential disputes in a fair and efficient manner.In conclusion, a sales contract should include the identities of the parties, a description of the goods or services, payment terms, delivery terms, warranties or guarantees, and provisions for dispute resolution. These requirements ensure that both the buyer and the seller are protected and that there is clarity and transparency in the transaction.中文回答:销售合同是买卖双方之间的一份具有法律约束力的协议,详细规定了销售的条款和条件。
捕捉和控制河狸和水獭的规定说明书

REGUL ATION Sbeaver damage. Damage Control Permits issued dur-ing the open beaver trapping season may be awarded to applicants that did not received a zone wide permit during the open lottery and who reside near the damage site. All beaver harvested on Damage Con-trol Permits issued during the open season must be registered at an official beaver/otter check station. Beaver taken on Damage Control Permits issued outside of the open beaver trapping season may not be possessed or sold by the damage permit holder.Other beaver/otter rules and regulations:• Holders of a river otter trapping permit may use a maximum of three traps daily.• Trappers may only possess one Special River Otter Trapping Permit per season.• All beaver and otter trap tags must be clearly vis-ible above the water or ice.• Holders of both a Special Beaver Permit anda Beaver Damage Control Permit may use fiveadditional traps daily on the property listed inthe Damage Control Permit.• A Fish and Wildlife-issued Beaver Transporta-tion Tag or Otter Transportation Tag must beaffixed to the beaver or otter carcass immediatelyupon taking possession of the animal .• All otters harvested incidentally by beaver trap-pers (i.e., trappers possessing a beaver permit butnot an otter permit) must be fully surrenderedto the Division of Fish and Wildlife. The entirecarcass, including the pelt, must be surrendered.• All successful trappers (or their agents) must pres-ent their beaver and/or otter pelts at a designatedcheck station for examination where pelt tags willbe affixed. All otter carcasses must be surren-dered when pelts are registered, as required bythe Game Code. Failure to submit your carcasswill result in the issuance of a citation by theBureau of Law Enforcement.• Trappers are requested to properly flesh and stretch all pelts for examination. Additional information on check stations will be provided to all permit holders.• Fish and Wildlife will staff check-in stations at the Assunpink, Clinton, Flatbrook, Tucka-hoe and Winslow WMAs and the Newfound-land Fire Company on Saturday, Feb. 20, 2016 (9 a.m.–noon). Successful trappers who cannot attend the scheduled dates should contact eitherJoseph Garris at (908) 735-7040 or Andrew Bur-nett at (609) 748-2047 prior to Feb. 13 to make alternate arrangements.• Permit holders will be notified via email, telephone or U.S. mail in the event the beaver and otter trap-ping season is extended for any reason, and notified of any change in the pelt registration date.Bobcat and FisherBobcats are classified as endangered in New Jersey; they are distributed widely across the northern part of the state. Fishers are returning, naturally and through reintroduction efforts in New York and Pennsylvania, to most of their historic range in the northeastern United States. Fishers have been documented in several north-ern and southern New Jersey counties.Regulations in red are new this year.• A trapping license is required and a Trapper Edu-cation course must be passed. See pages 1 and 8 for license information.• All traps set or used must bear a legible tag of durable material with the name and address of the person setting, using and maintaining the traps. Trap tags with Fish and Wildlife-issued trap identification number or the trapper’s Con-servation Identification Number (CID#) may be used in lieu of name and address to mark each trap. • No traps or trap stakes are to be set prior to times indicated in this section.• All traps must be checked and tended at least once every 24 hours, preferably in the morning.• No trap shall be permitted to remain set on any property at the close of the trapping season.• No person shall steal or attempt to take traps of another, or remove a trapped animal without permission of the trap owner.• There is a mandatory reporting requirement for trappers who incidentally capture a bobcat to call (877) WARNDEP before releasing the bobcat. A Fish and Wildlife Trapper Response Team technician will go to the site for data collection and the safe release of the bobcat.• Any person (including a farmer) who traps a coy-ote must report their harvest via the Automated Harvest Reporting System no later than 8 p.m. on the day of harvest.• Licensed trappers in possession of a valid rifle permit may carry a .22 caliber rifle and use only .22 caliber short rimfire cartridges to kill legally trapped animals other than muskrat. Licensed trappers may carry an air gun and use ammuni-tion no smaller than .177 caliber and no larger than .22 caliber to dispatch legally trapped ani-mals other than muskrat. Firearms may not be loaded with more than three rounds.Beaver and River OtterBeaver may be taken only by properly licensed trap-pers in possession of a special beaver trapping permit valid for an entire management zone, or a special site-specific beaver permit valid as designated on the permit. River otter may only be taken by prop-erly licensed trappers in possession of a special river otter trapping permit valid for an entire management zone. Application can be made at license agents or via Fish and Wildlife’s Internet license sales site . Applicants must have a current and valid trapping license to apply. Zone maps, boundary descriptions and per-mit quotas are available on our website or call (609) 292-1473. Applicants must have a current and valid trapping license to apply. The application period is October 1–31. Applicants may apply for only one beaver trapping permit and/or one otter trapping permit. If the number of applications exceeds the permit quota, a random lottery drawing will be held to determine permit holders. Successful beaver permit applicants will be given first oppor-tunity for otter permits in their respective zone. The Director may issue Beaver Damage Control Permits to owners or lessees of any land to control There is no open trapping season for either bobcat or fisher. It is now mandatory for trap-pers and farmers to report any incidental bobcat capture within 24 hours of discovery by calling 1-877-WarnDEP (1-877-927-6336). Possession of New Jersey bobcats or fishers is prohibited but those legally harvested in other U.S. states or Canadian provinces may be possessed if properly documented. Call the same number for a dead bobcat or fisher on your trapline; a Fish and Wildlife technician will arrange to pick up the animal. Biological sam-ples will be taken from all bobcat and fisher car-casses. The data collected will be instrumental tounderstand the status of the species populations.Traps, Live-capture Foot EncapsulatingEnclosed or foot encapsulating (also known asenclosed foothold or dog-proof traps) traps arenow legal for trapping. These traps have been spe-cifically designed to capture species such as raccoonand opossum (which possess a degree of manualdexterity) while minimizing the capture of non-target animals especially domestic dogs and cats.Enclosed foothold traps are a live-restraint trapwhich do not result in the death of the capturedanimal or in the potential for significant injury.These traps are subject to the following requirements:• All triggering and restraining mechanisms shallbe enclosed by a housing.• The triggering and restraining mechanism is acces-sible only by a single opening when the trap is set.• The access opening does not exceed 2 inches indiameter or when measured diagonally.• The triggering mechanism can be activated onlyby a pulling force.• The trap has a swivel-mounted anchoring system.Traps, Live-capture Cable Restraints (Snares)• No person shall set, use or maintain any type ofsnare unless they have first passed a Fish and Wild-life-approved trapper education course and carryon their person appropriate certification thereof. • All live capture cable restraints must include a relax-ing-type lock, except when submerged underwater or when set for mink, muskrat, nutria or weasel.• All natural baits consisting of fish, bird or mam-mal carcasses or flesh used in trapping with live-capture cable restraints must be covered or concealed from view except when placed at least30 feet from any trap set.Live-capture cable restraints set for mink, muskrat, nutria and weasel are subject to the following requirements:• All such traps must be constructed of aircraft cable or crucible wire measuring 1/32, 3/64 or 1/16 inches in diameter, equipped with a swivel;• Mink, muskrat and nutria cable restraints must be set within 50 feet of the mean high water line.• All such traps must be equipped with a stop to prevent the average loop diameter from exceeding 4 inches; and,| New Jersey Hunting & Trapping Digest2015 Issue66North Zone:Nov. 15–Mar. 15South Zone:Dec. 1–Mar. 15WMAs:Jan. 1–Mar. 15No daily or seasonal bag limit for these species.Traps may not be set prior to 6 a.m. on the respective opening day.Del. Water Gap Nat’l Rec. Area closed to trappingReport any nutria harvest to a Division of Fish and Wildlife Office.Mink, Muskrat and Nutria Trapping ZonesBeaver and River Otter Trapping ZonesSeason Dates:Dec. 26–Feb. 9 exceptJan. 1–Feb. 9 on select WMAs *(See WMA list this page, above.) Number of Traps Allowed:Beaver—5 per zone per day Otter—3 per day Bag Limits:Beaver—8 per permit Otter—1 per season Traps may not be set prior to 6 a.m. on the respective opening day.Del. Water Gap Nat’l Rec. Area closed to trappingAll otter carcasses must be surrendered to the Division of Fish and Wildlife.Mandatory pelt registration:Feb. 20 (9 a.m.–noon)Traps, Body-gripping or Killer-typeNo body-gripping or killer-type trap shall be used in non-tidal waters unless completely submergedunderwater when the water is at the normal level. In tidal water, such traps must be completely covered at normal high tide. It is illegal to use, set or maintain a body-gripping or killer-type trap having a jaw spread greater than Greenwood (incl. Howardsville), Heislerville, MacNamara (Tuckahoe), Mad Horse, Mana-hawkin, Manasquan River, Medford, Nantuxent, Peaslee, Pequest, Port Republic, Stafford Forge, Walpack, Winslow and Whittingham. Trap-ping is prohibited at all times on the Delaware Water Gap Nat’l Recreation Area.• Bag Limits: No daily bag limit for any of these species.• No open fisher season. Call (877) 927-6337 to report any fisher capture.*The following wildlife management areas (WMAs) are closed to trapping until Jan. 1: Assunpink, Berkshire Valley, Bevans (Millville), Black River, Clinton, Colliers Mills, Flatbrook-Roy, Glassboro, Greenwood (incl. Howardsville),H eislerville, MacNamara (Tuckahoe), Mad Horse, Manahawkin, Manasquan River, Med-ford, Nantuxent, Peaslee, Pequest, Port Republic,Stafford Forge, Walpack, Winslow and Whit-tingham. Trapping is prohibited at all times on the Delaware Water Gap Nat’l Recreation Area.2015 Issue New Jersey Hunting & Trapping Digest |67。
中英对照《萨班斯-奥克斯利法案》与内部审计师相关的关键条款

中英对照《萨班斯-奥克斯利法案》与内部审计师相关的关键条款中英对照《萨班斯-奥克斯利法案》与内部审计师相关的关键条款sec. 2 definitions定义defines terms used in the bill, including the following:法案中对以下名词定义为:●'audit' means an examination of the financial statements of any issuer by an independentpublic accounting firm in accordance with the rules of the board or the commission for thepurpose of expressing an opinion on such statements.审计:为了对财务报表出具意见而由独立的会计师事务所根据本委员会的规则对某个报表发布者提供的财务报表进行的审查。
●'audit committee' means: (a) a committee established by and amongst the board of directors of an issuer for the purpose of overseeing the accounting and financial reporting processes of the issuer and audits of the financial statements of the issuer; or (b) the entire board of directors if nosuch committee exists.审计委员会:(a)由发布者的董事会组建并由董事会成员组成的一个委员会,对其会计和财务报告过程以及财务报表的审计过程进行监管;或(2)如果不存在这样的委员会,则整个董事会即为审计委员会。
欧盟GMP中英文对照

实用文档European Union药品生产质量管理规范GUIDE TO GOOD MANUFACTURING PRACTICE FOR MEDICINAL PRODUCTS目录第一章质量管理CHAPTER 1: QUALITY MANAGEMENT原则............................................................ ..................................................... ............ (5)Principle (5)质量保证................................................................... .............. . (5)Quality Assurance (5)药品生产质量管理规范(GMP) (7)Good Manufacturing Practice for Medicinal Products (7)质量控制(QC) (9)Quality Control....................... . (9)产品质量回顾....................... ....................... (10)第二章人员CHAPTER 2: PERSONNEL...................................................................................... .. (11)原则 (11)Principle (11)通则 (12)General...................................................................................................................... . (12)关键人员................................................................................................................... . (12)Key Personnel (12)培训 (12)Training..................................................................................................................... . (15)人员卫生 (16)Personnel Hygiene (16)第三章厂房和设备CHAPTER 3: PREMISES AND EQUIPMENT................................................................ .. (18)原则 (18)Principle (18)厂房 (18)Premises (18)通则 (18)General (18)生产区 (19)Production Area (19)贮存区 (21)Storage Area (21)Quality Control Area (22)附助区 (22)Ancillary Areas (22)设备 (23)Equipment (23)第四章文件CHAPTER 4: DOCUMENTATION (24)原则 (24)Principle (24)通则 (25)General (25)文件要求 (27)Documents Required (27)Specifications (27)Specifications for starting and packaging materials (27)Specifications for Intermediate and Bulk Products (27)Specifications for Finished Products (28)Manufacturing Formulae and Processing Instructions (28)Packaging Instructions (30)Batch Processing Records (31)Batch Packaging Records. (32)Procedures and Records........................................................................................ .. (33)Receipt (34)Sampling (34)Testing (35)Other (35)第五章生产CHAPTER 5: PRODUCTION......................................... ........ (36)原则........................................ . (36)Principle (36)通则........................................ . (36)General (36)生产过程中对交叉污染的预防 (39)Prevention of Cross-contamination in Production (39)Validation................................. . (40)原料........................................ . (41)Starting Materials..................... . (41)生产操作:中间产品和待包装产品 (42)Processing Operations: Intermediate and Bulk Products (42)包装材料........................................ . (43)Packaging Materials.......................... . (43)包装操作........................................ . (44)Packaging Operations........................ . (44)成品........................................ . (46)Finished Products..................... . (46)不合格、回收料和退货物料 (46)Rejected, Recovered and Returned Materials (46)第六章质量控制CHAPTER 6: QUALITY CONTROL (48)原则........................................ . (48)Principle................................... . (48)通则........................................ . (48)General... .. (48)质量控制实验室规范 (49)Good Quality Control Laboratory Practice (49)Documentation (49)Sampling................................... (50)Testing... .. (52)销售产品的稳定性考察 (54)第七章委托生产与委托检验CHAPTER 7: CONTRACT MANUFACTURE AND ANALYSIS (55)原则........................................ . (55)Principle................................... . (55)通则........................................ . (56)General..................................... . (56)委托方.................................... . (56)受托方.................................... (57)The Contract Acceptor.............. (57)合同........................................ . (58)The Contract............................. (58)第八章投诉与召回CHAPTER 8: COMPLAINTS AND PRODUCT RECALL (59)原则........................................ . (59)Principle.................................... . (59)投诉........................................ . (59)Complaints................................ . (59)召回 (60)Recalls (60)第九章自查CHAPTER 9: SELF INSPECTION (61)原则 (61)Principle (61)附件8 原辅料和包装材料的取样ANNEX8 SAMPLING OF STARTING AND PACKAGING MATERIALS (63)原则 (63)Principle (63)人员 (63)Personnel (63)原辅料 (63)Starting materials (64)包装材料 (65)Packaging material (65)第一章质量管理CHAPTER 1 QUALITY MANAGEMENTPrinciple原则生产许可证持有厂家只能生产医药产品,以确保药品符合其预期的使用目的,符合销售许可证的要求,并不因药品安全性、质量或药效方面的问题而给患者带来风险。
TRIPS与贸易有关地的知识产权协定中英文对照

TRIPS: TEXT OF THE AGREEMENTAgreement on Trade-Related Aspects of Intellectual Property Rights与贸易有关的知识产权协定(TRIPS协定是1994年4月15日在摩洛哥马拉喀什签署的《成立世界贸易组织马拉喀什协定》中的附件1C。
)The TRIPS Agreement is Annex 1C of the Marrakesh Agreement Establishing the World Trade Organization, signed in Marrakesh, Morocco on 15 April 1994.与贸易有关的知识产权协定的前言PREAMBLE to the Agreement on Trade-Related Aspects of Intellectual Property Rights第一部分总则和基本原则PART I General Provisions and Basic Principles第二部分关于知识产权的效力、范畴和应用时的规范PART II Standards Concerning the Availability, Scope and Use of Intellectual Property Rights1. 著作权和相关的权利Copyright and Related Rights2. 商标Trademarks3. 地理标识Geographical Indications4. 工业品外观设计Industrial Designs5. 专利Patents6. 集成电路布局设计(拓扑图)Layout-Designs (Topographies) of Integrated Circuits7. 对未公开信息的保护Protection of Undisclosed Information8.对许可契约中限制竞争行为的抑制Control of Anti-Competitive Practices in Contractual Licences 第三部分知识产权的实施PART III Enforcement of Intellectual Property Rights1. 基本责任General Obligations2. 民事和行政程序及其救济措施Civil and Administrative Procedures and Remedies3. 临时措施Provisional Measures4. 与边境措施相关的专门要求Special Requirements Related to Border Measures5.刑事程序Criminal Procedures第四部分知识产权的取得和维持以及当事人之间的相关程序PART IVAcquisition and Maintenance of Intellectual Property Rights and RelatedInter-Partes Procedures第五部分争端的防止和解决PART V Dispute Prevention and Settlement第六部分过渡性安排PART VI Transitional Arrangements第七部分机构安排;最后条款PART VIIInstitutional Arrangements; Final Provisions全体成员,Members,因渴望减少国际贸易中的被扭曲与障碍,认为必须提高知识产权有效和充分的保护,并应同时确保知识产权行施中的措施和程序其本身不成为合法贸易中的障碍;所以确认需要下列方面的新规则和自律准则:Desiring to reduce distortions and impediments to international trade, and taking into account the need to promote effective and adequate protection of intellectual property rights, and to ensure that measures and procedures to enforce intellectual property rights do not themselves become barriers to legitimate trade;Recognizing, to this end, the need for new rules and disciplines concerning:(a)关于《1994年关贸总协定(GATT)》和有关国际知识产权协定或公约基本原则的应用;the applicability of the basic principles of GATT 1994 and of relevant international intellectual property agreements or conventions;(b) 关于涉及贸易的知识产权的效力、范畴和应用的适用规范和原则性规定;the provision of adequate standards and principles concerning the availability, scope and use of trade-related intellectual property rights;(c) 关于在考虑各国法律制度之间差异的前提下,实施涉及贸易的知识产权时有效与适宜方式的规定;the provision of effective and appropriate means for the enforcement of trade-related intellectual property rights, taking into account differences in national legal systems;(d) 关于多边参与防止和解决政府间争端的有效与迅速的反应程序的规定;以及the provision of effective and expeditious procedures for the multilateral prevention and settlement of disputes between governments; and(e) 关于为充分分享国际谈判的成果所进行的过渡性安排;transitional arrangements aiming at the fullest participation in the results of the negotiations;且确认,需要拥有一个关于处理国际贸易中假冒商品问题的原则、规则和纪律的多边框架;Recognizing the need for a multilateral framework of principles, rules and disciplines dealing with international trade in counterfeit goods;且确认,知识产权属于私权;Recognizing that intellectual property rights are private rights;且确认,知识产权国家保护制度中基本的政府政策目标,包括开发保护的目标和技术保护的目标;Recognizing the underlying public policy objectives of national systems for the protection of intellectual property, including developmental and technological objectives;且确认,最不发达国家成员国内法律法规实施时关于最高灵活性的特殊需求,从而使其在本协定实施时能具备健全可行的技术性基础;Recognizing also the special needs of the least-developed country Members in respect ofmaximum flexibility in the domestic implementation of laws and regulations in order to enable them to create a sound and viable technological base;需要强调,通过多边程序解决与贸易有关的知识产权争端,重视承诺,从而减少紧张关系的重要性;Emphasizing the importance of reducing tensions by reaching strengthened commitments to resolve disputes on trade-related intellectual property issues through multilateral procedures;期望在WTO与世界知识产权组织(本协定中简称“WIPO”)以及其他有关国际组织之间建立一种相互支持的关系;Desiring to establish a mutually supportive relationship between the WTO and the World Intellectual Property Organization (referred to in this Agreement as “WIPO”) as well as other relevant international organizations;因此通过协定如下:Hereby agree as follows:第一部分总则和基本原则Part I — General Provisions and Basic Principles第1条责任的性质和范围Article 1Nature and Scope of Obligations1. 各成员均必须实行本协定中的规定,各成员可以但并无义务,在其法律中实施比本协定要求更广泛的保护,只要此种保护不违反本协定的规定。
美国《联邦规章典集》(CFR)第21篇“食品与药品”总目
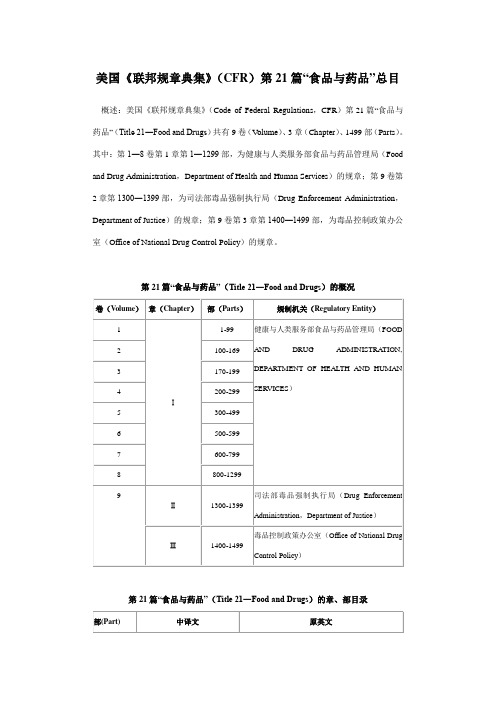
美国《联邦规章典集》(CFR)第21篇“食品与药品”总目概述:美国《联邦规章典集》(Code of Federal Regulations,CFR)第21篇“食品与药品”(Title 21―Food and Drugs)共有9卷(V olume)、3章(Chapter)、1499部(Parts)。
其中:第1―8卷第1章第1―1299部,为健康与人类服务部食品与药品管理局(Food and Drug Administration,Department of Health and Human Services)的规章;第9卷第2章第1300―1399部,为司法部毒品强制执行局(Drug Enforcement Administration,Department of Justice)的规章;第9卷第3章第1400―1499部,为毒品控制政策办公室(Office of National Drug Control Policy)的规章。
第21篇“食品与药品”(Title 21―Food and Drugs)的概况卷(Volume)章(Chapter)部(Parts)规制机关(Regulatory Entity)1Ⅰ1-99健康与人类服务部食品与药品管理局(FOODAND DRUG ADMINISTRA TION,DEPARTMENT OF HEALTH AND HUMANSERVICES)2100-1693170-1994200-2995300-4996500-5997600-7998800-12999Ⅱ1300-1399司法部毒品强制执行局(Drug EnforcementAdministration,Department of Justice)Ⅲ1400-1499毒品控制政策办公室(Office of National DrugControl Policy)第21篇“食品与药品”(Title 21―Food and Drugs)的章、部目录部(Part)中译文原英文第Ⅰ章―健康与人类服务部食品与药品管理局(CHAPTERADMINISTRATION, DEPARTMENT OF HEALTH AND HUMAN SERVICES)第A分章―总则(SUBCHAPTER A―GENERAL)1一般强制执行规章GENERAL ENFORCEMENT REGULA TIONS2一般行政规则与决定GENERAL ADMINISTRA TIVE RULINGS ANDDECISIONS3产品管辖权PRODUCT JURISDICTION5组织ORGANIZA TION7强制执行政策ENFORCEMENT POLICY10行政规范与程序ADMINISTRA TIVE PRACTICES ANDPROCEDURES11电子化记录;电子化签名ELECTRONIC RECORDS; ELECTRONICSIGNA TURES12正式证据的公众听证FORMAL EVIDENTIARY PUBLIC HEARING13在公众质询委员会前的公众听证PUBLIC HEARING BEFORE A PUBLIC BOARD OF INQUIRY14在公众咨询委员会前的公众听证PUBLIC HEARING BEFORE A PUBLIC ADVISORY COMMITTEE15在FDA局长前的公众听证PUBLIC HEARING BEFORE THECOMMISSIONER16在FDA前的规制性听证REGULA TORY HEARING BEFORE THE FOODAND DRUG ADMINISTRA TION17行政罚款听证CIVIL MONEY PENALTIES HEARINGS19行为标准与利益冲突STANDARDS OF CONDUCT AND CONFLICTSOF INTEREST20公共信息PUBLIC INFORMA TION21隐私保护PROTECTION OF PRIVACY25环境影响考虑ENVIRONMENTAL IMPACT CONSIDERA TIONS26药品良好制造规范报告、医疗器械质量体系核查报告以及某些医疗器械产品评价报告的互认:美国与欧共体MUTUAL RECOGNITION OFPHARMACEUTICAL GOOD MANUFACTURINGPRACTICE REPORTS, MEDICAL DEVICEQUALITY SYSTEM AUDIT REPORTS, ANDCERTAIN MEDICAL DEVICE PRODUCTEV ALUA TION REPORTS: UNITED STA TES ANDTHE EUROPEAN COMMUNITY50人类受试者的保护PROTECTION OF HUMAN SUBJECTS54临床试验者的财务公开FINANCIAL DISCLOSURE BY CLINICALINVESTIGA TORS56机构审查委员会INSTITUTIONAL REVIEW BOARDS58对非临床实验室研究的良好实验室规范GOOD LABORA TORY PRACTICE FOR NONCLINICAL LABORA TORY STUDIES60专利期恢复PA TENT TERM RESTORA TION70色素添加剂COLOR ADDITIVES71色素添加剂申请COLOR ADDITIVE PETITIONS73免除认证的色素添加剂的列表LISTING OF COLOR ADDITIVES EXEMPTFROM CERTIFICA TION74适用认证的色素添加剂的列表LISTING OF COLOR ADDITIVES SUBJECT TOCERTIFICA TION80色素添加剂认证COLOR ADDITIVE CERTIFICA TION81用于食品、药品和化妆品的临时性色素添加剂的一般规范和一般限制GENERAL SPECIFICA TIONS AND GENERALRESTRICTIONS FOR PROVISIONAL COLORADDITIVES FOR USE IN FOODS, DRUGS, ANDCOSMETICS82经认证的临时性列表的色素和规范的列表LISTING OF CERTIFIED PROVISIONALL Y LISTED COLORS AND SPECIFICA TIONS83-98[预留的][Reserved]99已上市的药品、生物制品和器械的未经批准的/新的用途的信息的发布DISSEMINA TION OF INFORMA TION ONUNAPPROVED/NEW USES FOR MARKETEDDRUGS, BIOLOGICS, AND DEVICES第B分章―用于人类消费的食品(SUBCHAPTER B―FOOD FOR HUMAN CONSUMPTION)100总则GENERAL101食品标识FOOD LABELING102非标准化食品的普通的或者通常的名称COMMON OR USUAL NAME FOR NONSTANDARDIZED FOODS104食品的营养质量指南NUTRITIONAL QUALITY GUIDELINES FORFOODS105特殊膳食用途的食品FOODS FOR SPECIAL DIETARY USE106婴儿配方母乳替代食品质量控制程序INFANT FORMULA QUALITY CONTROL PROCEDURES107婴儿配方母乳替代食品INFANT FORMULA108紧急许可控制EMERGENCY PERMIT CONTROL109在人类食品与食品-包装材料中的不可避免的污染物UNA VOIDABLE CONTAMINANTS IN FOODFOR HUMAN CONSUMPTION ANDFOOD-PACKAGING MA TERIAL110在制造、包装或者保存人类食品中的现行良好制造规范CURRENT GOOD MANUFACTURINGPRACTICE IN MANUFACTURING, PACKING, ORHOLDING HUMAN FOOD113装在密封容器中的热加工低酸食品THERMALL Y PROCESSED LOW-ACID FOODSPACKAGED IN HERMETICALL Y SEALEDCONTAINERS114酸化食品ACIDIFIED FOODS 115带壳蛋SHELL EGGS119存在显著或者不合理风险的膳食补充剂DIETARY SUPPLEMENTS THA T PRESENT A SIGNIFICANT OR UNREASONABLE RISK120危害分析与关键控制点(HACCP)体系HAZARD ANALYSIS AND CRITICAL CONTROL POINT (HACCP) SYSTEMS123鱼与渔业产品FISH AND FISHERY PRODUCTS129饮用水加工与装瓶PROCESSING AND BOTTLING OF BOTTLEDDRINKING WA TER130食品标准:总则FOOD STANDARDS: GENERAL131乳与奶油MILK AND CREAM133乳酪与相关乳酪产品CHEESES AND RELA TED CHEESE PRODUCTS 135冷冻点心FROZEN DESSERTS136烘焙产品BAKERY PRODUCTS137谷物粉与相关产品CEREAL FLOURS AND RELA TED PRODUCTS 139通心粉与面条产品MACARONI AND NOODLE PRODUCTS145罐装水果CANNED FRUITS146罐装水果汁CANNED FRUIT JUICES150水果黄油、果冻、防腐剂以及相关产品FRUIT BUTTERS, JELLIES, PRESERVES, AND RELA TED PRODUCTS152水果馅饼FRUIT PIES155罐装蔬菜CANNED VEGETABLES156蔬菜汁VEGETABLE JUICES158冷冻蔬菜FROZEN VEGETABLES160蛋与蛋制品EGGS AND EGG PRODUCTS161鱼与有壳的水生动物FISH AND SHELLFISH163可可制品CACAO PRODUCTS164树坚果与花生制品TREE NUT AND PEANUT PRODUCTS 165饮料BEVERAGES166人造黄油MARGARINE168增甜剂与餐桌糖浆SWEETENERS AND TABLE SIRUPS169食品敷料与调味料FOOD DRESSINGS AND FLA VORINGS 170食品添加剂FOOD ADDITIVES171食品添加剂申请FOOD ADDITIVE PETITIONS172允许直接加入用于人类消费食品的食品添加剂FOOD ADDITIVES PERMITTED FOR DIRECTADDITION TO FOOD FOR HUMANCONSUMPTION173在用于人类消费的食品中允许的次直接的食品添加剂SECONDARY DIRECT FOOD ADDITIVESPERMITTED IN FOOD FOR HUMANCONSUMPTION174间接食品添加剂:总则INDIRECT FOOD ADDITIVES: GENERAL175间接食品添加剂:胶粘剂与涂层的组分INDIRECT FOOD ADDITIVES: ADHESIVES AND COMPONENTS OF COA TINGS176间接食品添加剂:纸与纸板组分INDIRECT FOOD ADDITIVES: PAPER ANDPAPERBOARD COMPONENTS177间接食品添加剂:聚合体INDIRECT FOOD ADDITIVES: POL YMERS178间接食品添加剂:辅剂、生产助剂和消毒剂INDIRECT FOOD ADDITIVES: ADJUVANTS, PRODUCTION AIDS, AND SANITIZERS179在食品生产、加工和处理中的辐照IRRADIA TION IN THE PRODUCTION, PROCESSING AND HANDLING OF FOOD180在额外试验期间临时在食品或者在与食品接触中被允许的食品添加剂FOOD ADDITIVES PERMITTED IN FOOD OR INCONTACT WITH FOOD ON AN INTERIM BASISPENDING ADDITIONAL STUDY181先前核准的食品配料PRIOR-SANCTIONED FOOD INGREDIENTS182一般认为安全的物质SUBSTANCES GENERALL Y RECOGNIZED ASSAFE184被确认为一般认为安全的直接食品物质DIRECT FOOD SUBSTANCES AFFIRMED AS GENERALL Y RECOGNIZED AS SAFE186被确认为一般认为安全的间接INDIRECT FOOD SUBSTANCES AFFIRMED AS食品物质GENERALL Y RECOGNIZED AS SAFE 189禁止用于人类食品的物质SUBSTANCES PROHIBITED FROM USE INHUMAN FOOD190膳食补充剂DIETARY SUPPLEMENTS191-199[预留的][Reserved]第C分章―药品:总则(SUBCHAPTER C―DRUGS: GENERAL)200总则GENERAL201标识LABELING202处方药广告PRESCRIPTION DRUG ADVERTISING203处方药销售PRESCRIPTION DRUG MARKETING205对批发处方药销售商颁发州执照的指南GUIDELINES FOR STA TE LICENSING OFWHOLESALE PRESCRIPTION DRUGDISTRIBUTORS206人用固体口服剂型药品的印码IMPRINTING OF SOLID ORAL DOSAGE FORMDRUG PRODUCTS FOR HUMAN USE207药品生产者的登记与商业销售的药品的列表REGISTRA TION OF PRODUCERS OF DRUGSAND LISTING OF DRUGS IN COMMERCIALDISTRIBUTION208处方药的药物治疗指导MEDICA TION GUIDES FOR PRESCRIPTIONDRUG PRODUCTS210制造、加工、包装或者保存药品的现行良好制造规范;总则CURRENT GOOD MANUFACTURINGPRACTICE IN MANUFACTURING, PROCESSING,PACKING, OR HOLDING OF DRUGS; GENERAL211对完成的药品的现行良好制造规范CURRENT GOOD MANUFACTURINGPRACTICE FOR FINISHEDPHARMACEUTICALS216药房配药PHARMACY COMPOUNDING225对含药饲料的现行良好制造规CURRENT GOOD MANUFACTURING范PRACTICE FOR MEDICA TED FEEDS226对A型含药物品的现行良好制造规范CURRENT GOOD MANUFACTURINGPRACTICE FOR TYPE A MEDICA TEDARTICLES250对特殊人用药品的特殊要求SPECIAL REQUIREMENTS FOR SPECIFICHUMAN DRUGS290管制的药品CONTROLLED DRUGS299药品;正式名称与已确定的名称DRUGS; OFFICIAL NAMES AND ESTABLISHEDNAMES第D分章―人用药品(SUBCHAPTER D―DRUGS FOR HUMAN USE)300总则GENERAL310新药NEW DRUGS312试验用新药申请INVESTIGA TIONAL NEW DRUG APPLICA TION 314为FDA批准上市新药的申请APPLICA TIONS FOR FDA APPROV AL TOMARKET A NEW DRUG315诊断用放射性药品DIAGNOSTIC RADIOPHARMACEUTICALS316罕见病药ORPHAN DRUGS320生物利用度与生物等效性要求BIOA VAILABILITY AND BIOEQUIVALENCEREQUIREMENTS328含有酒精的预期用于口部摄入的非处方药品OVER-THE-COUNTER DRUG PRODUCTSINTENDED FOR ORAL INGESTION THA TCONTAIN ALCOHOL330一般认为安全与有效以及不错误标识的非处方人用药品OVER-THE-COUNTER (OTC) HUMAN DRUGSWHICH ARE GENERALL Y RECOGNIZED ASSAFE AND EFFECTIVE AND NOTMISBRANDED331用于非处方的人类使用的抗酸产品ANTACID PRODUCTS FOR OVER-THE-COUNTER (OTC) HUMAN USE332用于非处方的人类使用的抗胃肠气胀产品ANTIFLA TULENT PRODUCTS FOR OVER-THE-COUNTER HUMAN USE333用于非处方的人类使用的局部抗菌药品TOPICAL ANTIMICROBIAL DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE335用于非处方的人类使用的止泻药品ANTIDIARRHEAL DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE336用于非处方的人类使用的止吐药品ANTIEMETIC DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE338用于非处方的人类使用的帮助夜间睡眠的药品NIGHTTIME SLEEP-AID DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE340用于非处方的人类使用的兴奋药品STIMULANT DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE341用于非处方的人类使用的感冒、咳嗽、过敏症药、支气管扩张以及平喘药品COLD, COUGH, ALLERGY, BRONCHODILA TOR,AND ANTIASTHMA TIC DRUG PRODUCTS FOROVER-THE-COUNTER HUMAN USE343用于非处方的人类使用的内服的止痛、退热以及抗风湿药品INTERNAL ANALGESIC, ANTIPYRETIC, ANDANTIRHEUMA TIC DRUG PRODUCTS FOROVER-THE-COUNTER HUMAN USE344用于非处方的人类使用的局部的耳部药品TOPICAL OTIC DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE346用于非处方的人类使用的肛肠药品ANORECTAL DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE347用于非处方的人类使用的皮肤保护药品SKIN PROTECTANT DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE348用于非处方的人类使用的外部的止痛药品EXTERNAL ANALGESIC DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE349用于非处方的人类使用的眼科药品OPHTHALMIC DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE350用于非处方的人类使用的止汗药品ANTIPERSPIRANT DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE352用于非处方的人类使用的遮光药品SUNSCREEN DRUG PRODUCTS FOROVER-THE-COUNTER HUMAN USE [STAYEDINDEFINITEL Y]355用于非处方的人类使用的防龋药品ANTICARIES DRUG PRODUCTS FOR OVER-THE-COUNTER HUMAN USE357用于非处方的人类使用的其他内服药品MISCELLANEOUS INTERNAL DRUGPRODUCTS FOR OVER-THE-COUNTERHUMAN USE358用于非处方的人类使用的其他外用药品MISCELLANEOUS EXTERNAL DRUGPRODUCTS FOR OVER-THE-COUNTERHUMAN USE361一般认为安全与有效以及不错误标识的处方人用药品:用于研究的药品PRESCRIPTION DRUGS FOR HUMAN USEGENERALL Y RECOGNIZED AS SAFE ANDEFFECTIVE AND NOT MISBRANDED: DRUGSUSED IN RESEARCH369在用于非处方销售的药品与器械上关于警告的解释性声明INTERPRETA TIVE STA TEMENTS REW ARNINGS ON DRUGS AND DEVICES FOROVER-THE-COUNTER SALE370-499[预留的][Reserved]第E分章―动物药品、饮料和相关产品(SUBCHAPTER E―ANIMAL DRUGS, FEEDS, AND RELA TED PRODUCTS)500总则GENERAL501动物食品标识ANIMAL FOOD LABELING502非标准化的动物食品的普通的或通常的名称COMMON OR USUAL NAMES FOR NONSTANDARDIZED ANIMAL FOODS509在动物食品与食品-包装材料中UNA VOIDABLE CONTAMINANTS IN ANIMAL的不可避免的污染物FOOD AND FOOD-PACKAGING MA TERIAL510新动物药NEW ANIMAL DRUGS511作为试验用途的新动物药NEW ANIMAL DRUGS FOR INVESTIGA TIONALUSE514新动物药申请NEW ANIMAL DRUG APPLICA TIONS515含药饲料厂执照MEDICA TED FEED MILL LICENSE520口服剂型的新动物药ORAL DOSAGE FORM NEW ANIMAL DRUGS 522植入或者注射剂型的新动物药IMPLANTA TION OR INJECTABLE DOSAGEFORM NEW ANIMAL DRUGS524眼科和局部剂型的新动物药OPHTHALMIC AND TOPICAL DOSAGE FORMNEW ANIMAL DRUGS526乳房内的剂型INTRAMAMMARY DOSAGE FORMS529某些其他剂型的新动物药CERTAIN OTHER DOSAGE FORM NEWANIMAL DRUGS530在动物中的特别标签药品使用EXTRALABEL DRUG USE IN ANIMALS556在食品中新动物药残留的容许量TOLERANCES FOR RESIDUES OF NEW ANIMAL DRUGS IN FOOD558用于动物饲料的新动物药NEW ANIMAL DRUGS FOR USE IN ANIMALFEEDS564[预留的][Reserved]570食品添加剂FOOD ADDITIVES571食品添加剂申请FOOD ADDITIVE PETITIONS573在动物饲料与饮用水中允许的食品添加剂FOOD ADDITIVES PERMITTED IN FEED AND DRINKING WA TER OF ANIMALS579在动物饲料和宠物食品的生产、加工和处理中的辐照IRRADIA TION IN THE PRODUCTION,PROCESSING, AND HANDLING OF ANIMALFEED AND PET FOOD582一般认为安全的物质SUBSTANCES GENERALL Y RECOGNIZED ASSAFE584在动物饲料与饮用水中被确认为一般认为安全的食品物质FOOD SUBSTANCES AFFIRMED ASGENERALL Y RECOGNIZED AS SAFE IN FEEDAND DRINKING WA TER OF ANIMALS589禁止用于动物食品或者饲料的物质SUBSTANCES PROHIBITED FROM USE IN ANIMAL FOOD OR FEED590-599[预留的][Reserved]第F分章―生物制品(SUBCHAPTER F―BIOLOGICS)600生物制品:总则BIOLOGICAL PRODUCTS: GENERAL 601颁发执照LICENSING606对血液与血液组分的现行良好制造规范CURRENT GOOD MANUFACTURINGPRACTICE FOR BLOOD AND BLOODCOMPONENTS607对人类血液与血液制品的制造者的机构登记与产品列表ESTABLISHMENT REGISTRA TION ANDPRODUCT LISTING FOR MANUFACTURERS OFHUMAN BLOOD AND BLOOD PRODUCTS610普通生物制品标准GENERAL BIOLOGICAL PRODUCTSSTANDARDS630对血液、血液组分和血液衍生物的一般要求GENERAL REQUIREMENTS FOR BLOOD,BLOOD COMPONENTS, AND BLOODDERIVA TIVES640对人类血液和血液制品的附加标准ADDITIONAL STANDARDS FOR HUMAN BLOOD AND BLOOD PRODUCTS660对用于实验室检测的诊断物质的附加标准ADDITIONAL STANDARDS FOR DIAGNOSTIC SUBSTANCES FOR LABORATORY TESTS680对其他产品的附加标准ADDITIONAL STANDARDS FORMISCELLANEOUS PRODUCTS第G分章―化妆品(SUBCHAPTER G―COSMETICS)700总则GENERAL701化妆品标识COSMETIC LABELING710化妆品机构的自愿登记VOLUNTARY REGISTRA TION OF COSMETICPRODUCT ESTABLISHMENTS720化妆品配料构成声明的自愿存档VOLUNTARY FILING OF COSMETIC PRODUCT INGREDIENT COMPOSITION STA TEMENTS740化妆品警告声明COSMETIC PRODUCT WARNINGSTA TEMENTS741-799[预留的][Reserved]第H分章―医疗器械(SUBCHAPTER H―MEDICAL DEVICES)800总则GENERAL801标识LABELING803医疗器械报告MEDICAL DEVICE REPORTING806医疗器械;改正与移动的报告MEDICAL DEVICES; REPORTS OFCORRECTIONS AND REMOV ALS807对器械的制造者与首次进口者的机构登记与器械列表ESTABLISHMENT REGISTRA TION ANDDEVICE LISTING FOR MANUFACTURERS ANDINITIAL IMPORTERS OF DEVICES808对州和地方医疗器械要求的联邦优先权的豁免EXEMPTIONS FROM FEDERAL PREEMPTIONOF STA TE AND LOCAL MEDICAL DEVICEREQUIREMENTS809人用体外诊断产品IN VITRO DIAGNOSTIC PRODUCTS FORHUMAN USE810医疗器械召回权MEDICAL DEVICE RECALL AUTHORITY812试验用器械豁免INVESTIGA TIONAL DEVICE EXEMPTIONS813[预留的][Reserved]814医疗器械的上市前批准PREMARKET APPROVAL OF MEDICALDEVICES820质量体系规章QUALITY SYSTEM REGULA TION医疗器械跟踪要求MEDICAL DEVICE TRACKING 821REQUIREMENTS822上市后监视POSTMARKET SURVEILLANCE医疗器械分类程序MEDICAL DEVICE CLASSIFICA TION 860PROCEDURES性能标准制定程序PROCEDURES FOR PERFORMANCE 861STANDARDS DEVELOPMENT临床化学与临床毒理学器械CLINICAL CHEMISTRY AND CLINICAL862TOXICOLOGY DEVICES864血液学与病理学器械HEMA TOLOGY AND PA THOLOGY DEVICES 免疫学与微生物学器械IMMUNOLOGY AND MICROBIOLOGY866DEVICES868麻醉学器械ANESTHESIOLOGY DEVICES870心血管器械CARDIOVASCULAR DEVICES872牙科器械DENTAL DEVICES874耳、鼻和咽器械EAR, NOSE, AND THROA T DEVICES876胃肠病学-泌尿学器械GASTROENTEROLOGY-UROLOGY DEVICES878普通与整形外科器械GENERAL AND PLASTIC SURGERY DEVICES普通医院与个人使用器械GENERAL HOSPITAL AND PERSONAL USE880DEVICES882神经学器械NEUROLOGICAL DEVICES产科与妇科学器械OBSTETRICAL AND GYNECOLOGICAL 884DEVICES886眼科器械OPHTHALMIC DEVICES888矫形外科器械ORTHOPEDIC DEVICES890内科学器械PHYSICAL MEDICINE DEVICES892放射学器械RADIOLOGY DEVICES895禁止的器械BANNED DEVICES898电极铅线与患者电缆的性能标准PERFORMANCE STANDARD FOR ELECTRODE LEAD WIRES AND PA TIENT CABLES第I分章―乳房造影质量标准法(SUBCHAPTER I―MAMMOGRAPHY QUALITY STANDARDS ACT)900乳房造影法MAMMOGRAPHY第J分章―放射学的健康(SUBCHA PTER J―RADIOLOGICAL HEALTH)1000总则GENERAL1002记录与报告RECORDS AND REPORTS1003缺陷与未能守法的通报NOTIFICA TION OF DEFECTS OR FAILURE TOCOMPL Y1004电子产品的回购、修理或者置换REPURCHASE, REPAIRS, OR REPLACEMENTOF ELECTRONIC PRODUCTS1005电子产品的进口IMPORTA TION OF ELECTRONIC PRODUCTS1010电子产品的性能标准:总则PERFORMANCE STANDARDS FORELECTRONIC PRODUCTS: GENERAL 1020电离辐射发生产品的性能标准PERFORMANCE STANDARDS FOR IONIZINGRADIA TION EMITTING PRODUCTS1030微波与射电频率发生产品的性能标准PERFORMANCE STANDARDS FORMICROWA VE AND RADIO FREQUENCYEMITTING PRODUCTS1040发光产品的性能标准PERFORMANCE STANDARDS FORLIGHT-EMITTING PRODUCTS1050声波、次声波和超声波发生产品的性能标准PERFORMANCE STANDARDS FOR SONIC,INFRASONIC, AND ULTRASONICRADIA TION-EMITTING PRODUCTS第K分章―[预留的](SUBCHAPTER K―[RESERVED])第L分章―根据由食品与药品管理局行政执行的某些其他法的规章(SUBCHAPTERL―REGULA TIONS UNDER CERTAIN OTHER ACTS ADMINISTERED BY THE FOOD AND DRUG ADMINISTRA TION)1210根据《联邦进口乳法》的规章REGULA TIONS UNDER THE FEDERAL IMPORTMILK ACT1230根据《联邦腐蚀性毒物法》的规章REGULA TIONS UNDER THE FEDERAL CAUSTIC POISON ACT1240传染病的控制CONTROL OF COMMUNICABLE DISEASES1250州际运输卫生INTERSTA TE CONVEYANCE SANITA TION1251-1269[预留的][Reserved]1270预期用于移植的人体组织HUMAN TISSUE INTENDED FORTRANSPLANTA TION1271人体细胞、组织以及细胞的和基于组织的产品HUMAN CELLS, TISSUES, AND CELLULAR AND TISSUE-BASED PRODUCTS1272-1299[预留的][Reserved]第Ⅱ章―司法部毒品强制执行局(CHAPTER ADMINISTRATION, DEPARTMENT OF JUSTICE)1300定义DEFINITIONS1301管制物质的制造者、分销者和调剂者的登记REGISTRA TION OF MANUFACTURERS,DISTRIBUTORS, AND DISPENSERS OFCONTROLLED SUBSTANCES1302对管制物质的标识与包装要求LABELING AND PACKAGING REQUIREMENTSFOR CONTROLLED SUBSTANCES1303定额QUOTAS1304登记者的记录与报告RECORDS AND REPORTS OF REGISTRANTS 1305令的格式ORDER FORMS1306处方PRESCRIPTIONS1307杂项MISCELLANEOUS1308管制物质的表SCHEDULES OF CONTROLLED SUBSTANCES1309表I化学品的制造者、分销者、进口者和出口者的登记REGISTRA TION OF MANUFACTURERS,DISTRIBUTORS, IMPORTERS AND EXPORTERSOF LIST I CHEMICALS1310列入表的化学品和某些机器的记录与报告RECORDS AND REPORTS OF LISTED CHEMICALS AND CERTAIN MACHINES1311[预留的][Reserved]1312管制物质的进口与出口IMPORTA TION AND EXPORTA TION OFCONTROLLED SUBSTANCES1313前体与必要化学品的进口与出口IMPORTA TION AND EXPORTA TION OF PRECURSORS AND ESSENTIAL CHEMICALS1314-1315[预留的][Reserved]1316行政职能、规范和程序ADMINISTRA TIVE FUNCTIONS, PRACTICES,AND PROCEDURES第Ⅲ章―毒品控制政策办公室(CHAPTER Ⅲ―Off)1400[预留的][Reserved]1401信息的公众可及性PUBLIC A VAILABILITY OF INFORMA TION 1402强制性解密审查MANDATORY DECLASSIFICA TION REVIEW1403对给予州和地方政府资金和合作协议的统一行政要求UNIFORM ADMINISTRA TIVE REQUIREMENTSFOR GRANTS AND COOPERA TIVEAGREEMENTS TO STA TE AND LOCALGOVERNMENTS1404政府范围的排除与暂停(非获得)GOVERNMENTWIDE DEBARMENT AND SUSPENSION (NONPROCUREMENT)1405对无毒品工作场所的政府范围的要求(财政援助)GOVERNMENTWIDE REQUIREMENTS FORDRUG-FREE WORKPLACE (FINANCIALASSISTANCE)1406-1499[预留的][Reserved]。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Specification and Enforcement of Access Control in Heterogeneous Distributed Applications Torsten Fink,Manuel Koch,and Cristian OanceaInstitut f¨u r InformatikFreie Universit¨a t Berlin,14195Berlin,Germany{tnfink,mkoch,oancea}@inf.fu-berlin.deAbstract.Security is a crucial aspect in any modern software system.We consider in this article the specification and the management of ac-cess control in in-house business applications which are coupled over theInternet using Web services.In-house business applications are usuallybuilt on a middleware in which security is an established aspect andsecurity management tools are available.The integration of security inSOAP,however,is still an ongoing activity.Therefore,we propose an access control model for Web services whichoriginates from CORBA-based applications.This integration has theadvantage of a unique access control policy for both the CORBA-basedin-house application and the Web services.We implemented an infras-tructure to enforce the access control policy and a comprehensive set ofpowerful XML based management tools.Keywords:SOAP-based web services,access control,RBAC,CORBA,security management,interoperability.1IntroductionSecurity is an integral part of most modern software systems that are not used in completely trusted environments.We consider in this article in-house business applications that are integrated over the Internet by SOAP-based Web services. There is an established support for security in the middleware,e.g.CORBA[15] or Java RMI,used in in-house business applications,but there is still an ongoing effort in establishing standards for Web service security.Nowadays,due to the lack of a Web security standard and corresponding implementations,Web security is mostly delegated to the security mechanisms of the Web server which acts as application server.For example,the Tomcat Web server[2]provides a security manager for the administration of users,groups, roles,and permissions to access Java-Web applications.The authorization in Tomcat,however,is coarse-grained,in the sense,that it is not possible to restrict the access on single operations of Web services.Moreover,delegation of accessdecision is as well a problem as the reuse of access control policies in different frameworks,[11].There are emerging XML-based security standards from W3C and OASIS for Web security.The Web Services Security(WSS)specification[13]from OASIS M.Jeckle and L.-J.Zhang(Eds.):ICWS-Europe2003,LNCS2853,pp.88–100,2003.c Springer-Verlag Berlin Heidelberg2003Specification and Enforcement of Access Control89 describes a mechanism for securely exchanging SOAP messages.It provides the following three main security features:the ability to send security tokens(e.g., user name,certificates)as part of a SOAP message to authenticate users,to provide message integrity,and message confidentiality.The Security Assertion Markup Language(SAML)[12]from OASIS is an XML framework for exchanging authentication and authorization information, whereas the eXtensible Access Control Markup Language(XACML)[14]pre-sented by OASIS lets you express authorization and access control policies in XML.XACML defines a vocabulary to specify subjects,rights,objects,and conditions.Implementations of the XACML standard already exist,for example Sun’s XACML implementation[19]written in Java or the access control en-gine jiffyXACML by Jiffy Software[10].To our knowledge,however,there is no implementation which enforces a given XACML policy in an application.Unlike all approaches mentioned above which concentrate on developing new approaches for security in Web services,we propose to integrate a well-established security model from a different domain into Web service applications. This security model is called View-based Access Control(VBAC)[6]which orig-inates from CORBA-based applications.VBAC is a variant of role-based access control[16]and provides a specification language,View Policy Language(VPL), in which access control policies can be specified.Authorizations can be speci-fiedfine-grained on the level of single Web service operations and authorization rights can change dynamically,triggered by operation calls.The VBAC model is implemented in the CORBA-based infrastructure Raccoon[5]accompanied with a comprehensive set of powerful XML based management tools.Raccoon enforces a VPL policy for CORBA-based systems.We identified the features needed to describe access control for Web services, extended the VPL accordingly and applied the VPL to the specification of access control requirements in Web services.We use the Raccoon infrastructure to enforce a Web service security policy.Therefore we developed a proxy which intercepts SOAP messages.This proxy extracts the authentication and service information and delegates access decision to the Raccoon infrastructure.The Raccoon infrastructure decides if the request is rejected or if the Web service is executed.The advantages of an integration of a well-established security model into Web services are:–A unique access control model and access control language for both in-house applications and Web services.This reduces the expert security knowledge required by system designers and administrators.–A powerful access control language in which dynamic right changes can be expressed and authorization can be explicitly granted or denied on the level of Web service operations.For example,XACML does not provide a possi-bility for dynamic right changes,Tomcat specifies access control on the level of entire Web applications only.–The VPL was especially designed for readability and an easy use by develop-ers and system administrators.XACML is mainly designed to describe access90T.Fink,M.Koch,and C.Oanceacontrol policies in a format that allows for an efficient machine evaluation of access requests against access requirements.So,the VPL is more suitable for system designers and administrators and reduces design and administration errors.–VPL supports automatic type and consistency checks.For example,contra-dicting authorization assignments can be statically detected.–VBAC and VPL are accompanied by an infrastructure which enforces access control policies written in VPL.There are XML based graphical management tools for policy deployment and policy administration.These tools can be used without any new implementation.The VPL access control specification and the XACML specification,however,do not mutually exclude,since the VPL specification can be transformed in a XACML specification by an XSL stylesheet.Therefore,the proposed specifica-tion language VPL can be also used as a manageable front-end for a XACML specification.Moreover,the VPL is independent of Raccoon and can be used also with other access control enforcement engines.The remainder of this paper is organized as follows:Section2introduces a video rental example which is used throughout the paper.In section 3we identify the access control requirements of the video rental example and introduce the VPL and the VBAC model.Section 4presents a brief overview of the Raccoon infrastructure and shows how it can be used to enforce a VPL access control policy for Web services.Section 5concerns related work and section 6concludes the paper and points to future work.2Example –Video CentralVideo Central is a Web service sample application provided by IBM [9].The Video Central contains a central data repository that can be accessed by regis-tered Web-based applications (see fig.1).There is one business-related Web service,the business registration ,that allows a business (a video store)to register with the Video Central.Once a video store registered with Video Central,it is able to use the following customer-related Web services:customer Acustomer BFig.1.Video Central architecture.Specification and Enforcement of Access Control 91–Customer Registration :Enables the registered video store to register their own customers with Video Central.–Customer Infraction :Enables the registered video store to add and query infraction information to and from the central repository.–Customer Rented List :Enables the registered video store to add and query rented videos for each customer.–Customer Wish List :Enables the registered video store to add and query the titles of videos the customer has expressed an interest in watching.–Movie Search :Enables the registered video store to search for movie titles.This Web Service can be used by the staffor customers of the store.The UML design of Video Central is given in[9].Figure 2shows the part of the class diagram needed for the paper.Fig.2.Video Central class diagram.It shows the classes for the six Web services and their operations.The op-eration parameters for the operations of the classes BusinessRegistration and MovieSearch are not shown,since we will not need them later in the paper.The operation parameters of the remaining classes are relevant and are depicted in the class diagram.The arrows between actors and Web services show in which Web services the actors participate.92T.Fink,M.Koch,and C.Oancea3Access ControlWe identify in this section the access control requirements in the Video Central application and introduce afterwards the View Policy Language and the View-based Access Control model in which we express the Video Central access control requirements.3.1Access Control in Video CentralIn the Video Central application,the accesses on the services are performed by video store staffmembers and video store customers.We get the following access control requirements for the above Web services:–Business Registration:Can be used by a video store staffmember(this will be in general a video store manager).The business registration is a prerequisite for all remaining Web services.–Customer Registration,Customer Infraction:Staffmembers can use these Web services,but only if their video store is registered with Video Central.Staffmembers can use the Web services only with respect to their customers.For example,a staffmember of video store A is denied to register a customer for video store B.–Customer Rented List,Wish List:Staffmembers can use these Web services (again only for their customers).Customers can check the list of videos rented by themselves,but they cannot add requests to the list.Customers can add,remove,and query their wish list.–Movie Search:This Web service can be used by staffmembers and customers.3.2View-Based Access ControlView-based access control(VBAC)is an access control model specifically de-signed to support the design and management of access control policies in dis-tributed systems.VBAC is an extension of role-based access control(RBAC)[16, 17]by the concept of views and schemas.A view groups permissions or denials to access objects(e.g.,afile,a method,printer)and views are assigned to roles.A subject(e.g.,a user,a process)can access an object if the subject has a role to which a view with the required permissions is assigned.If such a view does not exist for the role,the subject cannot access the object.A schema specifies dynamic assignments or removals of views to and from roles.These assignments are performed automatically whenever a given operation is executed.The View Policy Language(VPL)is a declarative language to specify VBAC policies[6,4].The VPL is used to specify roles,views,and schemas.Roles are defined in a role declaration(after the keyword roles),the views in several view definitions(introduced by the keyword view)and the schemas in several schema definitions(introduced by the keyword schema).The role clause defines the available roles in the policy together with their initial views.Figure3depicts the role definition for the Video Central applicationSpecification and Enforcement of Access Control93 in which we have two roles,namely customer and staff.The role staff has initially the view BusinessRegistration(keyword holds),the role customer does not have an initial view.A VPL view defines the authorization for a subset of operations of a single Web service,which is referenced in the controls clause.For example,the view BusinessRegistration gives the permission to call the operation processRegis-terRequest of Web service BusinessRegistration.A VPL view can be statically restricted to certain roles listed after a restricted to clause,so that it can only be assigned to these roles.For example,the view BusinessRegistration can be assigned only to the role staff,but not to customer.The view CustomerRegistration gives the permission for the operations getCustomerGUID and processRegisterRequest.Since a video store can only reg-ister its own customers(see requirements in Sec3.1),the operation can be called only with a subset of the possible operation parameters.In our example,get-CustomerGUID can be called only with the loginBusinessID of the calling video store(a video store gets its loginBusinessID after registering with Video Central by the Web service BusinessRegistration).Analog,the operation processRegis-terRequest can only be called with the loginBusinessID of the calling video store.This restriction of parameters is not necessary in the VPL originating from CORBA-based applications.An operation can be granted so that it can be called with all possible operation parameters or it is denied.This is due to the fact that in CORBA-based applications a common design pattern is used that creates an object on the server side for each client.The client communicates with this object and thus no identification is necessary.For example,in a Video rental CORBA application each client would get its own CustomerRegistration object on the role customerstaffholds BusinessRegistrationview BusinessRegistration controls BusinessRegistration restricted to staff{ processRegisterRequest}view CustomerRegistration controls CustomerRegistration restricted to staff{getCustomerGUID(loginBusinessID,,,)if caller=loginBusinessIDprocessRegisterRequest(loginBusinessID,,,)if caller=loginBusinessID }view CustomerInfraction controls CustomerInfraction restricted to staff{ processAddRequest(loginBusinessID,,)if caller=loginBusinessIDprocessQueryRequest(loginBusinessID,,,,)if caller=loginBusinessID }Fig.3.The VPL role and view declaration.94T.Fink,M.Koch,and C.Oanceaserver side.SOAP,however,does not support these object-oriented concepts[21].Instead a general function is used where the loginBusinessID is explicitly givenas a parameter.We extended the VPL with the possibility to specify conditions of the formif caller=param,where the keyword caller represents the ID of the callerof a Web service and param is an operation parameter.The caller of a Webservice is identified by an integer,i.e.,only parameters of type integer can beused in the condition if caller=param.This is afirst attempt sufficient for theVideo Central example.If a parameter x i of an operation op(x1,..,x i,...,x n)is not restricted(i.e.,all values are allowed in an operation call),we denote thisby op(x1,...,,...,x n).If there is no condition for the parameters of op(x1,..,x n) in a view,the operation can be called with all possible parameter values.In this case we simply write the operation name op without parameter list(e.g., processRegisterProcess in view BusinessRegistration).The view CustomerInfraction gives the permission to call the Web ser-vice operations processAddRequest and processQueryRequest,again only for thecustomers of the video store.view CustomerRentedListFull controls CustomerRentedListrestricted to staff{processAddRequest(loginBusinessID,,,)if caller=loginBusinessIDprocessQueryRequest(loginBusinessID,,)if caller=loginBusinessID}view CustomerRentedListRestricted controls CustomerRentedList{processQueryRequest(,,customerGUID)if caller=customerID}Fig.4.The VPL view declaration.There are different access requirements for the roles staff and customerwith respect to the Web service CustomerRentedList.A staffmember can callboth operations processAddRequest and processQueryRequest,but a customer cancall processQueryRequest only.The view CustomerRentedListFull is restrictedto the role staff and gives the permission to call both operations.The viewCustomerRentedListRestricted permits only to call processQueryRequest and is not restricted to a certain role,but to certain parameters.The operation can be called only if the caller is the customer for which the rented list shall be checked.For the Web service WishList,we have again different views for customersand staffmembers.Staffmembers can add,remove,and query the wish list ofall their customers.A customer can add,remove and query only his/her ownwish list.This is reflected in the view WishListFull for the role staff and viewWishListRestricted for the role customer.The Web service MovieSearch can be used by staffmembers and customers without any restriction(seefig.5).Specification and Enforcement of Access Control95 view WishListFull controls WishList restricted to staff{processAddRequest(businessGuid,,,)if caller=businessGuidprocessQueryRequest(businessGuid,,,)if caller=businessGuidprocessRemoveRequest(businessGuid,,,)if caller=businessGuid}view WishListRestricted controls WishList restricted to customer{processAddRequest(,,customerGuid,)if caller=customerGuidprocessQueryRequest(,,customerGuid,)if caller=customerGuidprocessRemoveRequest(,,customerGuid,)if caller=customerGuid}view MovieSearch controls MovieSearch{processRequest}Fig.5.The VPL view declaration.Initially only the view BusinessRegistration is assigned to a role,namelyto staff.Therefore,users in role staff can access the Web service Business-Registration but they cannot access any other Web service.Customers can notaccess any Web service.Customer-specific Web services become available notbefore a video store has registered with Video Central.After the video storeregistered with Video Central,the views to access the Web services are assignedto the roles.The dynamic assignment and removal of views(and so of autho-rizations)to/from roles is specified in VPL schemas introduced by the keywordschema followed by the schema name and an observes clause that specifies theWeb service for which the schema is defined.The assignment(removal)of viewsis triggered by the execution of an operation of a Web service.After the oper-ation name op,we specify by assign V1,...,V N to R that the views V1,...,V N are assigned to role R after calling the operation op.We specify by remove V1,...,V N from R that the views V1,...,V N are removed from R after calling op. Fig.6depicts the schema of the Video Central example,which specifies the viewassignment after a video store has registered with Video Central.4Implementation–Enforcing the PolicyWe show in this section the infrastructure to enforce an access control policyspecified in VPL.This infrastructure is integrated into the Raccoon infrastruc-ture[5]which enforces VPL policies in CORBA environments.We start withan introduction of Raccoon and show afterwards how we have integrated SOAPmessages.96T.Fink,M.Koch,and C.Oanceaschema BusinsessRegistration controls BusinessRegistration{processRegisterRequestassigns CustomerRegistration,CustomerInfraction,CustomerRentedListFull,WishListFull,MovieSearch to staffassigns CustomerRentedListRestricted,WishListRestricted,MovieSearch to customer}Fig.6.The VPL schema declaration.4.1Raccoon InfrastructureThe Raccoon infrastructure consists of a deployment tool which processes VPL policies and stores view and role definitions in repositories(role and policy server) that can be managed using graphical management tools.Access decisions are made on the basis of policy information that is supplied by these repositories.Fig.7.Security infrastructure.Figure7shows the main parts of the Raccoon infrastructure.A role server contains all the role certificates of a user.When a client authenticates at the system,he/she gets all their role certificates.The role certificates are transmitted when a client calls a server operation.This call is intercepted by a CORBA interceptor which forwards the client information to an access decision object. This access decision object decides on the basis of the given roles and the policy if the client is permitted to call the operation.The current policy can be requested on the policy server.If the policy permits to call the operation for the client,the interceptor forwards the request to the servant.If the client is not permitted to call the operation,the request is denied.Specification and Enforcement of Access Control 97Graphical management tools support the management of access control.There is a tool for the definition of roles and the user role assignment,a tool for the definition of views and a tool for the definition of policies,i.e.,the relation of views to roles.Modifications made in these tools become immediately valid and are enforced in the distributed system.4.2Access Control Enforcement in Web ServicesWe use Raccoon for the management and the enforcement of VPL policies in Web service environments.The idea is to intercept SOAP messages and to delegate the access control decision to Raccoon.Depending on the Raccoon decision,the SOAP message is forwarded or rejected.Figure8shows the integrated architec-ture.We use HTTPS as communication protocol,since messages are encrypted and client certificates are transported on the server side.Fig.8.Security infrastructure.Deployment of Web ServicesThe Web services are deployed on the Web server.We use the Apache Tomcat Web Server [2]together with the Axis SOAP implementation [1]in order to take advantage of the concept of Axis handlers .A handler is a component that acts on a specific part of a SOAP message;for example,a handler can be in charge of performing authentication on the message’s sender before allowing it to be processed by the service provider.Policy DeploymentThe VPL policy for the Web services is deployed in the Raccoon infrastructure.Raccoon is a CORBA-based application and the deployment of the VPL policy needs the CORBA interface repository.The interfaces defined in the Interface Definition Language (IDL)are derived from the WSDL document of the Web services.This transformation in IDL can be done by an XSL stylesheet.For example,WSDL portTypes are IDL interfaces,WSDL operations are IDL op-erations,WSDL <input >elements for operations are IDL in parameters and WSDL <output >elements are IDL out parameters.98T.Fink,M.Koch,and C.OanceaAxis Handler for Access DecisionWe implemented a handler on the server side which is located before the Web service,i.e.,the SOAP message must pass this handler before it reaches the service.The handler serves as CORBA client to communicate with the CORBA-based Raccoon infrastructure,i.e.,the Raccoon role and policy server.When a SOAP message passes the handler,the handler extracts the user information (e.g.,certificates)and the requested method name and the parameters from the SOAP message.This certificates are used to get the role certificates of the user from the Raccoon role server.The role server stores the relation between user certificates and roles.The policy server contains the views and the view-role association,so that the handler can determine,on the basis of the client roles, if the access to the requested Web service operation is permitted or denied. If access is denied,an exception is thrown.Otherwise,the SOAP message is transmitted to the Web service.5Related WorkIn[3]role-based access control(RBAC)is applied to Web applications.RBAC is implemented as a CGI script for the use with a Web server.The creation of users,roles and authorizations are created by an Admin Tool.Thus,in some aspects this work constitutes a predecessor of our work.Damiani et.al present in[8,7]an approach for the definition of authorizations at the level of individual XML elements and attributes.On the basis of such an authorization policy,a tool produces a view on an XML document for each requester,showing the XML elements and attributes for which the requester has a permission.In contrast to our approach,where a client can see all Web services but get an exception if a denied service is called,Damiani et.al hide the denied services.Moreover,their approach misses a complete management environment, the underlying access control model does not provide dynamic right changes nor the concept of roles and group definition.Sirer and Wang present in[18]an approach for formal specification and enforcement of security policies on Web services.The specification language is based on temporal logic.A policy is processed by an enforcement engine which produces platform-specific code that is integrated into the Web server.This approach,however,is difficult to handle in dynamic environments(e.g.,changing access control requirements).An authorization change requires to write a new policy,to generate new code,and to integrate it in the Web server.In our approach dynamic right changes can be done by graphical management tools and policy modifications are immediately enforced without changing the web application.Moreover,the policy language in[18]focus more on the specification of sequencing actions by inserting predicates and implications.Actions are URL invocations initiated by clients and server-side script executions.The IONA Security Framework(iSF)[20]provides security service adapters for Web Services,J2EE and CORBA applications allowing interoperable security enforcement.In contrast to our appraoch,however,the iSF does not support theSpecification and Enforcement of Access Control99 designer or administrator with a declarative description language as the VPL. Dynamic right changes specified in VPL schemas and a permission management by views are not possible,either.6Conclusion and Future WorkWe used the View Policy Language(VPL)to specify access control requirements in Web services.The VPL and the corresponding access control model originate from CORBA-based applications.Extensions of the VPL were necessary to cover all requirements occurring in Web services.We implemented an infrastructure to enforce an access control policy in Web-based applications.We also provide deployment and management tools for Web service security management.The VPL can be used as a front-end for XACML specifications.We have to investigate the mapping from VPL to XACML in more detail to see if all VPL features can be mapped and if so,how this mapping should look like. Future work will concern also the mapping of the Raccoon infrastructure to the XACML model.This would provide interoperability with other systems,such as jiffyXACML or Sun’s XACML implementation.References1.Apache.Axis./axis/.2.Apache.Tomcat./tomcat/index.html.3.J.Barkley,A.Cincotta,D.Ferraiolo,S.Gavrila,and D.Kuhn.Role-based AccessControl for the World Wide Web.In Proc.of the20th National Information System Security Conference,1997.4.G.Brose.Access Control Management in Distributed Object Systems.PhD thesis,Freie Universit¨a t Berlin,2001.5.G.Brose.Raccoon–An infrastructure for managing access control in CORBA.In Proc.Int.Conference on Distributed Applications and Interoperable Systems (DAIS).Kluwer,2001.6.G.Brose.Manageable Access Control for CORBA.Journal of Computer Security,4:301–337,2002.7. E.Damiani,S.De Capitani di Vimercati,S.Paraboschi,and P.Samarati.FineGrained Access Control for SOAP E-Services.In Proc.of10th WWW Conference, 2001.8. E.Damiani,S.De Capitani di Vimercati,S.Paraboschi,and P.Samarati.AFine-Grained Access Control System for XML Documents.ACM Transactions on Information and System Security(TISSEC),5(2),2002.9.IBM.IBM Video Central for e-business tutorial,Version7.2,2002./developerworks/webservices/demos/videocentral/.10.jiffySoftware.jiffyXACML./xacml/index.html,April2003. Framework./net/.12.OASIS.Security Assertion Markup Language(SAML)v1.0Specification,Novem-ber2002.。
