ob-mba_05
的国际性专业鉴定毕家驹

MBA 的国际性专业鉴定毕家驹关键词工商管理硕士专业鉴定教育评估高等教育作者毕家驹同济大学研究生院教授(上海 200092, jiajubi@)本文浏览了国际性MBA专业鉴定的概况,着重对MBA协会的性质和宗旨,及其鉴定的要素和特点作了述评,以供全国MBA专业点及评估工作者参考。
一、 MBA 国际性专业鉴定概况工商管理硕士学位(MBA)是一个在国际上众所周知的、后工作经历的研究生学位。
许多人把它奉为进入管理事业殿堂的入场券。
在中国,MBA也早已是脍炙人口的了。
美国在20世纪初设立MBA学位,现在每年有9万名毕业生。
欧洲从20世纪60年代引入MBA学位教育,目前英国每年有1万名毕业生。
中国大陆的MBA专业创办于上世纪90年代初,现在共有62所院校设有MBA专业点。
截止2000年10月,总共授予了8千名MBA。
近年来学生人数增加得很快,在读人数已达16000名。
2001年的招生人数逾万名。
世界上现在有多种类型和形式的MBA专业。
MBA的学制,在欧洲多为1年、在美国则多为2年;教学方式,有全日制的、业余制的、弹性制的、模块制的、开放的、远程的和网络的等等;除了一地、一校办学外,还有跨国的和国际合作的;培养目标,有一般通用的、偏重国际工商的、或侧重某一行业的,如金融、保险、工程、科技等。
国际人才市场对MBA的要求日高,各管理学院或商学院之间的质量竞争十分激烈。
国际性的MBA专业鉴定成了MBA的优质保证和标志。
在英国注册的MBA协会( Association of MBAs,简称AMBA)是专门从事国际性MBA专业鉴定的一家组织。
它成立于1967年,其主要任务是鉴定MBA专业质量是否符合培养专业经理的高标准,并促进MBA专业的发展。
为此,AMBA制订了专门的鉴定准则,并不断予以改善。
1997年,AMBA又推出新的国际性鉴定方案,旨在为全球各地的MBA专业作独立的确认,以应对日益国际化的MBA市场的挑战。
现在,全球,主要是欧洲,经过AMBA鉴定的共有13个国家的65所管理学院或商学院的一百几十个MBA专业点,其统计数见表-1。
ASCO 产品说明书:单稳态阀门

FEATURES• The monostable spool valves in conformity with IEC 61508 Standard (2010 route 2H version) have TÜV certified with integraty levels: SIL 2 for HFT = 0 / SIL 3 for HFT = 1• All the exhaust ports of the spool valve are connectable, providing betterenvironmental protection. Particularly recommended for sensitive areas, such as clean rooms, and applications in the pharmaceutical and food processing sectors • The valves offer environmental protection against the ingress of liquids, dusts or other foreign matter (environmentally-protected construction)• Can be externally piloted (external air pilot supply) to convert valve to zero minimum operation by flipping a gasket• The solenoid valves satisfy all relevant EU directivesGENERALDifferential pressure 2 - 10,4 bar [1 bar =100 kPa]Flow (Qv at 6 bar)860 l/min (ANR)fluids (✶)temperature range (TS)seal materials (✶)air, inert gas, filtered-40°C to +60°CVMQ (silicone) + PUR (polyurethane)MATERIALS IN CONTACT WITH FLUID(✶) Ensure that the compatibility of the fluids in contact with the materials is verified Body, end covers Brass Spool valve internal parts Brass, stainless steel, POM Core tube Stainless steel Core and plugnut Stainless steel Core spring Stainless steelSeals & discs NBR Top disc P A Disc holder POM Cartridge (low power) Welded, packless AISI 430Seat Brass Seat insert POM Shading coil CopperRider rings (low power) PTFE (NF/WSNF solenoids only)SPECIFICATIONSpipe size orifice size flow coefficientKv operating pressure differential (bar)powerlevel prefix optional solenoidsbasic catalogue numbermin.(2)max. (PS)NEMA ATEX / IECExIP65air (✶)7 & 9Ex db Ex eb mb Ex mb Ex ia-( )(mm)(m 3/h)(l/min)~=~/=EF LPKF NF EM PV (WS)LI -SC Solenoid air pilot operated - spring return (monostable)1/460,7512,50 / 21010BP --l l l --l 551A407 (1)1/460,7512,50 / 21010BP l ------- 551G407 (1)1/460,7512,50 / 21010LP -l l l m m -l 551A307 (1)1/460,7512,50 / 21010LP m ------- 551G307 (1)Solenoid air pilot operated and return (bistable)1/460,7512,50 / 21010BP --l l l --l 551A4081/460,7512,50 / 21010BP l ------- 551G4081/460,7512,50 / 21010LP -l l l m m -l 551A3081/460,7512,50 / 21010LPm-------551G308Select 8 for NPT ANSI 1.20.3 or select G for ISO G (228/1) ● Available feature m Available feature in DC only. - Not available (1) Certified IEC 61508 Functional Safety data, use suffix "SL". (2)Zero minimum is only achieved if external pressure is applied.SOLENOID VALVESpilot operated, spool typesingle/dual solenoid (mono/bistable function )brass body, 1/4NC3/2Series55118/R 01POWER LEVELS - cold electrical holding values (watt)PREFIX TABLEprefixdescription power level1234567LP RP MP BP E F Explosionproof - NEMA 7, 9 - Zinc plated steel conduit m--l E V Explosionproof - NEMA 7, 9 - 316 SS conduit m--l E M Waterproof IP66/67 - Metal enclosure (EN/IEC 60079-7,-18 and -31)*l--lE T Threaded conduit/hole (M20 x 1,5)l--l L P KF Flameproof - Aluminium (EN/IEC 60079-1, 60079-31)*l---N F Flameproof - Aluminium (EN/IEC 60079-1, 60079-31)*l--l P V Encapsulated epoxy moulded (EN/IEC 60079-18)*m--l S C Solenoid with spade plug connector (EN/IEC 60730)l--l W P Waterproof IP67 - Metal enclosure l--l L I I.S. with Aluminium IP66/IP67 enclosure (EN/IEC 60079-11+31)*m---W S Waterproof IP67 - 316 SS enclosure l--l W S L P K F Flameproof 316L SS (EN/IEC 60079-1, 60079-31)*l---W S E M Waterproof IP66/67 - 316 SS enclosure (EN/IEC 60079-0+7+18+31)*l--l W S L I I.S. with 316L SS IP66/IP67 enclosure (EN/IEC 60079-11+31)*m---W S N F Flameproof 316L SS (EN/IEC 60079-1, 60079-31)*l--l T Threaded conduit (1/2" NPT)l--lH T Class H - High temperature, +80°C ambient temp.---lX Other special constructions l--l SUFFIX TABLEsuffixdescription power level1234567LP RP MP BP M O Push type manual operator m/l--l S L Certified IEC 61508 Functional Safety data (2)m/l--l OPTIONS & ACCESSORIESseries pipe size exhaust protector (stainless steel)551G 1/834600418(1) NPT 1/834600482(1) G 1/434600419(1) NPT 1/434600483(1) M534600484(1)l Available featurem Available feature in DC only- Not available* A TEX/IECEx valves using these solenoids are approved according to EN 13463-1 (non electrical)(1)Provided with "SL" suffix(2)Not to use with MO suffixPRODUCT SELECTION GUIDESTEP 1Select basic catalogue number,including pipe thread indentificationletter. Refer to the specifications tableon page: 1Example: G551A407STEP 2Select prefix (combination). Refer tothe specifications table and the prefixtable, respect the indicated powerlevel.Example: EMSTEP 3Select suffix (combination) if required.Refer to the suffix table, respect theindicated power level.Example: MOSTEP 4Select voltage. Refer to standardvoltages on page: 3Example: 230V / 50HzSTEP 5Final catalogue / ordering number.Example:EM G551A407MO 230 V / 50 HzORDERING EXAMPLES VALVES:SC G551 A 407230V/50 HzSC G551 A 407SL230V/50 HzSC G551 A 408MO230V/50 HzSCHT8551 A 408MO230V/50 HzWSLPKF G551 A 307MO24V/DCLPKF G551 A 307MO24V/DCLPKF G551 A 307MO230V/50 HzLI G551 A 30724V/DCWSLI G551 A 308MO24V/DCEM8551 A 407MO230V/50 HzEF G551 H 407MS240V/60 Hzprefix(3)pipe thread voltage basic number(3)suffix(3)P refix EF and EV should always be used in conjunction with change letter Hin the basic number18/R1EXPLANATION OF TEMPERATURE RANGES OF SOLENOID VALVESValve temperature rangeThe valve temperature range (TS) is determined by the selected seal material, the temperature range for proper operation of the valve and sometimes by the fluid (e.g. steam)Operator ambient temperature range The operator ambient temperature range is determined by the selected power level and the safety codeT otal temperature rangeThe temperature range of the complete solenoid valve is determined by the limitations of both temperature ranges aboveELECTRICAL CHARACTERISTICSCoil insulation class FElectrical safety IEC 335Standard voltagesDC (=) 24V - 48VAC (~) 24V - 48V - 115V - 230V (5)/50Hz; other voltages and 60Hz are available on requestprefix optionpower ratings operator ambient temperature range (TS)safety codeelectrical enclosure protection (EN 60529)replacement coil / kit type(2)inrush holding hot/cold ~~=~=(VA)(VA)(W)(W)(C°)(1)230 V/50 Hz 24V/DC Basic power (BP)SC552310,59/11,2-40 to +75EN 60730IP65, moulded 400425-117400425-14201WP/WS 552310,59/11,2-40 to +75EN 60730IP67, steel /SS 400405-117400405-14204NF/WSNF 552310,5--60 to +25/40/60II2G Ex db IIC Gb T6/T5/T4, II2D Ex tb IIIC Db IP66/67, alu./SS 400405-117-02NF/WSNF ---9/11,2-60 to +40/60/75II2G Ex db IIC Gb T6/T5/T4, II2D Ex tb IIIC Db IP66/67, alu./SS -400405-14202EM/WSEM 552310,59/11,2-40 to +40II2G Ex eb mb IIC Gb T3, II2D Ex tb IIIC Db IP66/67, steel /SS 400909-117400913-14204PV 552310,59/11,2-40 to +65II2G Ex mb IIC Gb T3(~)/T4(=), II2D Ex mb IIIC DbIP67, moulded -(4)-(4)05EF/EV552310,59/11,2-40 to +52/40NEMA type 7 and 9NEMA 4X 238614-058238714-00606Low Power (LP)SC 1,51,51,51,7/1,7-40 to +60EN 60730IP65, moulded 400925-097400925-04207WP/WS 1,51,51,51,7/1,7-40 to +60EN 60730IP67, steel /SS 400926-097400926-04209LPKF/WSLPKF(7)2,42,42,4 (8)--40 to +40/65/80II2G Ex db IIB+H2 Gb T6/T5/T4, II2D Ex tb IIIC Db IP66/67, alu./SS - (4)- (4)13LPKF/WSLPKF---0,5/0,5 (7)-40 to +60II2G Ex db IIB+H2 Gb T6, II2D Ex tb IIIC Db IP66/67, alu./SS - (4)- (4)13LPKF/WSLPKF ---2,1 (8)-40 to +40/80II2G Ex db IIB+H2 Gb T6/T4, II2D Ex tb IIIC Db IP66/67, alu./SS - (4)- (4)13NF/WSNF 1,851,851,851,5/1,8-60 to +75/80II2G Ex db IIC Gb T6/T5, II2D Ex tb IIIC Db IP66/67, alu./SS - (4) (5)- (4)08EM/WSEM 1,51,51,51,7/1,7-40 to +40/55II2G Ex eb mb IIC Gb T6/T5, II2D Ex tb IIIC Db IP66/67, steel /SS - (4)- (4)09PV ---1,7/1,7-40 to +65II2G Ex mb IIC Gb T6, II2D Ex mb IIIC DbIP67, moulded -- (4)10EF/EV ---1,7/1,7-40 to +60NEMA type 7 and 9NEMA 4X -- (4)11LI (3) (6)---0,5/0,5-40 to +60II1G Ex ia IIC T6 Ga, II2D Ex tb IIIC Db (6)IP66/67, alu.-- (4)14WSLI (3) (6)---0,5/0,5-40 to +60II1G Ex ia IIC T6 Ga, II2D Ex tb IIIC Db (6)IP66/67, SS-- (4)14prefix optionsafety parameters (1) Temperature range can be limited by sealings(2)Refer to the dimensional drawings on pages: 4 to 7(3) L I/WSLI: Check the electrical characteristics in the corresponding catalogue pages (4) Multiple coil kits are available under A TEX/IECEx, contact us (5) Only available in 24, 48 and 110V/DC (6) L I/WSLI: Low Power, 24 V DC only (LI: For use in zone 0 locations, see the installation conditions given in the I&M instructions )(7)LPKF/WSLPKF: 24 V DC, max. ambient temp. +80°C, contact us (48 V DC = 2,1 W)(8)Max. power ratings values: 115 V AC (2,4 W), 48 V DC (2,1 W)- Not availableU I = (DC)I I P I L I C I (V)(mA)(W)(H)(µF)Low Power (LP)LI/WSLI325001,5ELECTRICAL CONNECTIONSprefixconnectionSCSpade plug connector with cable gland EN175301-803A (ISO 4400) for cables with an outer diameter from 6 to 10 mm WP , WS, EM, WSEMM20 plastics cable gland for cables with an outer diameter from 7 to 12 mm.NF , WSNF , LPKF , WSLPKF 1/2" NPT threaded cable entry. Enclosures are supplied without cable gland PVMoulded-in cable, standard length 2 mLI, WSLI 1/2" NPT threaded cable entry. Enclosures are supplied without cable gland EF , EV1/2" NPT conduits, standard length 35 cmADDITIONAL OPTIONS• Valves configured for external pilot air supply, TPL 20547• Other pipe threads are available on request• Ex mb/mD (prefix "PV") solenoid can be supplied with various cable lengths •Compliance with "UL", "CSA" and other local approvals available on requestINSTALLATION• Multi language installation/maintenance instructions are included with each valve • The solenoid valves can be mounted in any position without affecting operation• Do not connect the pressure supply to the exhaust port 3. The “environmentally-protected” construction is not adapted for a “distributing” function or use in NO function. Contact us for functions available in specific versions• IEC 61508 Functional Safety (suffix SL). Check temperature range of valve body and solenoid for suitability. For probability of failure, contact us• It is necessary to connect pipes or fittings to the exhaust ports to protect the internal parts of the spool valve and its pneumatic operator if used outside or in harsh environments (dusts, liquids etc.)• Threaded pipe connection identifier is 8 = NPT (ANSI 1.20.3); G = G (ISO 228/1)18/R 01DIMENSIONS (mm), WEIGHT (kg)2 mounting holes: 5,3 mm dia.; Spotfacing: 9 mm dia., depth 5 mmTYPE 01:Epoxy mouldedSC: IEC 335 / ISO 4400551A407 / 551A408TYPE 02:Aluminium, epoxy coated / AISI 316L SSNF / WSNF: EN/IEC 60079-1, 60079-31551A407 / 551A408TYPE 04:Metal, epoxy coated / AISI 316L SSWP / WS: IEC 335EM / WSEM: EN/IEC 60079-7+18+31551A407 / 551A408All types18/R1TYPE 05:Epoxy encapsulatedPV: EN/IEC 60079-18551A407 / 551A408TYPE 06:Epoxy encapsulatedEF and EV: NEMA type 7, 9 / ICS-6 ANSI551G407 / 551G408TYPE 07:Epoxy mouldedSC: IEC 335 / ISO 4400TYPE 08:Aluminium, epoxy coated / AISI 316L SSNF / WSNF: EN/IEC 60079-1, 60079-31551A307 / 551A308TYPE 09:Metal, epoxy coated / AISI 316L SSWP / WS: IEC 335EM / WSEM: EN/IEC 60079-7+18+31TYPE 10:Epoxy encapsulatedPV: EN/IEC 60079-1818/R1TYPE 11:Epoxy encapsulatedEF and EV: NEMA type 7, 9 / ICS-6 ANSI551G307 / 551G308TYPE 13:Aluminium, cataphorese black painting / AISI 316L SSLPKF/WSLPKF: EN/IEC 60079-1, 60079-31TYPE 14:Aluminium, cataphorese black painting / AISI 316L SSLI / WSLI: EN/IEC 60079-11, 60079-31551A307 / A308 / A307MO / A308MO551A307 / A308 / A307MO / A308MO18/R1type prefix/option power level A B C D E weight (1)monostable bistable 01SC BP132170102,722,586,50,761,34 02NF BP158224141,8--1,853,51 02WSNF BP158224141,8--3,154,81 04WP / WS / EM / WSEM BP148204103--1,622,22 05PV BP1321728822,567,50,821,45 06EF / EV BP132,517385,522,574,50,641,29 07SC LP132,5173101,522,587,50,971,55 08NF LP158224141,8--1,853,51 08WSNF LP158224141,8--3,154,81 09WP / WS / EM / WSEM LP148204102,2--1,051,70 10PV LP132172100,522,567,51,031,67 11EF/EV LP132,5173100,522,574,50,851,50 13LPKF LP141192113--0,901,62 13WSLPKF LP141192113--1,512,82 14LI LP141192113--0,911,63 14WSLI LP141192113--1,522,83 (1)Incl. coil(s) and connector(s).2Ex d certified cable gland (on request)3Three-core cable, length 2 m4Cable gland for unarmoured cable with 7 to 12 mm dia. sheath6Connector rotatable by 90° increments (cable Ø 6 - 10 mm)8Manual operator location, suffix MO9External pilot air supply, 1/8 pipe sizeConnectable pilot exhaust portNon-connectable pilot exhaust portACCESSORIESø14ø14201/8NPTpilot exhaust protector part number276405-0011/81/41011exhaust protector18/R1e s i g n a n d s p e c i fi c a t i o n s a r e s u b j e c t t o c h a n g e w i t h o u t n o t i c e . A l l r i g h t s r e s e r v e d .18/R 01。
MBA组织行为学实战指南

MBA组织行为学实战指南组织行为学(Organizational Behavior,简称OB)是管理学中的重要分支,研究员工个体和群体在组织中的行为与互动。
MBA学习者在实际的工作场景中,需要灵活应用组织行为学的理论和原则,以帮助他们更好地管理团队和组织。
本文将为MBA学习者提供一份实战指南,介绍如何运用组织行为学的知识来提升领导力、优化团队效能,并建立积极的组织文化。
第一部分:领导力的实战运用1.1 了解不同领导风格的特点与适应性在实际工作中,一位优秀的领导者需要具备适应不同情境的能力。
不同领导风格适用于不同的情境和员工群体,了解每种领导风格的特点和优缺点,有助于MBA学习者在实战中选择合适的领导方式。
1.2 建立有效的沟通渠道作为领导者,良好的沟通技巧至关重要。
通过有效的沟通,可以明确目标、激发团队士气,并解决潜在的冲突和问题。
MBA学习者可以学习和运用沟通技巧,如倾听、表达和非语言沟通,以提升领导力,促进团队合作。
1.3 培养人际关系管理能力组织行为学强调团队合作和有效的人际关系管理。
作为领导者,MBA学习者应该学会建立积极的人际关系,包括发展信任、建立合作关系,并处理潜在的冲突。
通过培养人际关系管理能力,可以改善团队氛围,提高团队绩效。
第二部分:团队效能的优化2.1 设定明确的目标和角色在组织中,明确的目标和角色分工对于团队的高效运作至关重要。
通过设定明确的目标,团队成员可以聚焦于共同的目标,提高工作效率。
同时,明确的角色分工可以消除团队内部的不确定性和冲突。
2.2 建立有效的团队沟通机制团队内部的沟通是保证工作顺利进行的关键环节。
MBA学习者可以引入有效的团队沟通机制,如定期团队会议、使用共享工具和技术平台等,以促进信息的流动和团队之间的互动。
2.3 培养团队合作精神和文化团队合作和共享文化是促进团队效能的重要因素。
MBA学习者可以通过培养团队合作精神和塑造积极的组织文化,激发团队成员之间的互信与合作,提高工作效能。
OB--名词解释-及知识点(word文档物超所值)

第一章什么是组织行为学1、组织:是对完成特定使命的人的系统性安排2、管理:就是在特定的环境下,对组织所拥有的的资源进行有效地计划、组织、激励、领导和控制,以达到既定组织目标的过程。
3、管理:指同别人一起、或通过别人使活动完成得更有效的过程。
4、组织:是一种有意协调的社会单元,由两个以上的人组成,在一个连续的基础上运作,以达到共同的目标。
5、管理的四种职能①计划:设定目标,制定实现目标的方案。
②组织:实施计划制定的行动方案。
③领导:影响成员,营造氛围,提升士气。
④控制:对组织的各项活动进行检查,纠正偏差。
6、任何组织的安排都必须具备以下三个条件:(1)组织是人组成的集合2)组织是适应于目标的需要3)组织通过专业分工和协调来是实现目标。
7、管理人员应具备的管理技能:1)技术技能是指某一专业领域内有关的工作程序、技术和知识完成组织任务的能力。
2)概念技能是指综观全局,洞察组织与环境相互影响的复杂性的能力,具体包括理解事物的相互关联性从而找出关键影响因素的能力等。
3)人际技能是指与处理人事关系有关的技能,及理解、激励他人并与他人共事的能力。
4)诊断技能:管理者面对问题时把握因果关系和找出最优方案的能力。
8、管理者角色(名茨伯格):1)人际关系角色是指所有的管理者都要履行礼仪和象征性的义务。
(头面人物、领导者、联络者)2)信息传递角色是指所有的管理者在某种程度上,都从外部的组织机构接受和收集信息(监控者、传播者、发言人)3)决策制定角色(创业者、混乱处理者、资源分配者、谈判者)9、组织行为学OB定义:OB是一个研究领域,它探讨个体、群体以及结构对组织内部行为的影响,以便应用这些知识来改善组织的有效性。
第二章个体行为的基础1、人格:个体所有的反应方式和与他人交往方式的总和。
2、人格特质:个体所具有的一些持久的、稳定的特点。
个体在不同的情境下均表现出这些特点。
3、人格特质的五维度模型:①外倾性:指个体喜好社交的倾向性②随和性:描述一个人随和、合作、信任方面的特点③责任心:描述一个人的责任感、可靠性、持久性、成就倾向方面的人各维度。
3.2.2双曲线的简单几何性质(第二课时)课件-高二上学期数学人教A版选择性【05】

| PF2 | a,| PF1 | 3a,
a2 (3a)2 (2c)2, e c 10 10 . a42
(法2)e c 2c | F1F2 | 10x 10 a 2a | PF2 | | PF1 | 3x x 2
注:题目中有焦点三角形时,
[变式1]P为C上一点且 PF1 3 PF2 , F1PF2 60. 用定义法求离心率.
一条渐近线交于M , N两点,若MAN 60,则该双曲线的离心率为_____.
(法1)AM OA MOA 30 k b 3 e 2 3
a3
3
B
(法2) AM AN b, MAN 60,取MN中点B,
则 AB 3b , 2
tan BOA AB | OB |
3b 2
b
a2 3 b2 a
y2 b2
1.
②若常数 c a
1,即c
a
0,则点M的轨迹是双曲线,方程为
x2 a2
y2 b2
1.
③若常数 c 1,则点M的轨迹是抛物线. a
对比发现:
推论1.
若点A,
B是椭圆C: x2 a2
y2 b2
1(a
b
点P是椭圆C上除A, B以外任意一点,则 kPA
0)上任意关于椭圆中心对称的两点,
4
a2 3b2, e
b2 2 3 1 a2 3 .
(2015浙江)椭圆
x a
2 2
y2 b2
1(a
b
0)的右焦点F (c,0)关于直线
l
:
y
b c
x
的对称点Q在椭圆上,则椭圆的离心率是 _______.
析 : 设QF的中点为P, 则OP QF ,
Mason-a Java multiagent simulation library

MASON:A JAVA MULTI-AGENT SIMULATION LIBRARYG. C. BALAN, Department of Computer ScienceC. CIOFFI-REVILLA, Center for Social Complexity*S. LUKE, Department of Computer Science∗L. PANAIT, Department of Computer ScienceS. PAUS, Department of Computer ScienceGeorge Mason University, Fairfax, VAABSTRACTAgent-based modeling (ABM) has transformed social science research by allowingresearchers to replicate or generate the emergence of empirically complex socialphenomena from a set of relatively simple agent-based rules at the micro-level.Swarm, RePast, Ascape, and others currently provide simulation environments forABM social science research. After Swarm — arguably the first widely used ABMsimulator employed in the social sciences — subsequent simulators have sought toenhance available simulation tools and computational capabilities by providingadditional functionalities and formal modeling facilities. Here we present MASON(Multi-Agent Simulator Of Neighborhoods), following in a similar tradition that seeksto enhance the power and diversity of the available scientific toolkit in computationalsocial science. MASON is intended to provide a core of facilities useful not only tosocial science but to other agent-based modeling fields such as artificial intelligenceand robotics. We believe this can foster useful “cross-pollination” between suchdiverse disciplines, and further that MASON's additional facilities will becomeincreasing important as social complexity simulation matures and grows into newapproaches. We illustrate the new MASON simulation library with a replication ofHeatBugs and a demonstration of MASON applied to two challenging case studies:ant-like foragers and micro-aerial agents. Other applications are also beingdeveloped. The HeatBugs replication and the two new applications provide an idea ofMASON’s potential for computational social science and artificial societies.Keywords: MASON, agent-based modeling, multi-agent social simulation, ant foraging, aerial-vehicle flightINTRODUCTIONAgent-based modeling (ABM) in the social sciences is a productive and innovative frontier for understanding complex social systems (Berry, Kiel, and Elliott 2002), because object-oriented programming from computer science allows social scientists to model social phenomena directly in terms of social entities and their interactions, in ways that are inaccessible either through statistical or mathematical modeling in closed form (Axelrod 1997; Axtell and Epstein 1996; Gilbert and Troitzsch 1999). The multi-agent simulation environments that have been∗Corresponding authors’ address: Sean Luke, Department of Computer Science, George Mason University, 4400 University Drive MSN 4A5, Fairfax, VA 22030; e-mail: sean@. Claudio Cioffi-Revilla, Center for Social Complexity, George Mason University, 4400 University Drive MSN 3F4, Fairfax, VA 22030; e-mail: ccioffi@. All authors are listed alphabetically.developed in recent years are designed to meet the needs of a particular discipline; for example, simulators such as TeamBots () (Balch 1998) and Player/Stage () (Gerkey, Vaughan, and Howard 2003) emphasize robotics, StarLogo (/starlogo) is geared towards education, breve (Klein 2002) () aims at physics and a-life, and RePast (), Ascape (/dybdocroot/es/dynamics/models/ascape), a n d Swarm () have traditionally emphasized social complexity scenarios with discrete or network-based environments. Social science ABM applications based environments in this final category are well-documented in earlier Proceedings of this conference (Macal and Sallach 2000; Sallach and Wolsko 2001) and have contributed substantial new knowledge in numerous domains of the social sciences, including anthropology (hunter-gatherer societies and prehistory), economics (finance), sociology (organizations and collective behavior), political science (government and conflict), and linguistics (emergence of language) — to name a few examples.In this paper we present MASON, a new “Multi-Agent Simulator Of Neighborhoods”developed at George Mason University as a joint collaborative project between the Department of Computer Science's Evolutionary Computation Laboratory (Luke) and the Center for Social Complexity (Cioffi-Revilla). MASON seeks to continue the tradition of improvements and innovations initiated by Swarm, but as a more general system it can also support core simulation computations outside the human and social domain in a strict sense. More specifically, MASON is a general-purpose, single-process, discrete-event simulation library intended to support diverse multiagent models across the social and other sciences, artificial intelligence, and robotics, ranging from 3D continuous models, to social complexity networks, to discretized foraging algorithms based on evolutionary computation (EC). MASON is of special interest to the social sciences and social insect algorithm community because one of its primary design goals is to support very large numbers of agents efficiently. As such, MASON is faster than scripted systems such as StarLogo or breve, while still remaining portable and producing guaranteed replicable results. Another MASON design goal is to make it easy to build a wide variety of multi-agent simulation environments (for example, to test machine learning and artificial intelligence algorithms, or to cross-implement for validation purposes), rather than provide a domain-specific framework.This paper contains three general sections. The first section describes the new MASON environment in greater detail, including its motivation, main features, and modules. The second section argues for MASON's applicability to social complexity simulation, including a comparison with RePast and a simple case-study replication of HeatBugs (a common Swarm-inspired ABM widely familiar to computational social scientists. The third section presents two further case studies of MASON applied to areas somewhat outside of the computational social science realm, but which point, we think, in directions which will be of interest to the field in the future. We conclude with a brief summary.MASONMotivation: Why MASON? History and JustificationMASON originated as a small library for a very wide range of multi-agent simulation needs ranging from robotics to game agents to social and physical models. The impetus for this stemmed from the needs of the original architects of the system (S. Luke , G. C. Balan, and L.MASON Model Library, Utilities(Optional)MASON GUI Tools(Optional)Domain-Specific Simulation Library,ToolsApplicationsFIGURES 1 and 2 MASON Layers and Checkpointing ArchitecturePanait) being computer scientists specializing in artificial intelligence, machine learning, and multi-agent behaviors. We needed a system in which to apply these methods to a wide variety of multi-agent problems. Previously various robotics and social agent simulators were used for this purpose (notably TeamBots); but domain-specific simulators tend to be complex, and can lead to unexpected bugs if modified for use in domains for which they are not designed.Our approach in MASON is to provide the intersection of features needed for most multiagent problem domains, rather than the union of them, and to make it as easy as possible for the designer to add additional domain functionality. We think this “additive” approach to simulation development is less prone to problems than the “subtractive” method of modifying an existing domain-specific simulation environment. As such, MASON is intentionally simple but highly flexible.Machine learning methods, optimization, and other techniques are also expensive,requiring a large number of simulation runs to achieve good results. Thus we needed a system that ran efficiently on back-end machines (such as beowulf clusters), while the results were visualized, often in the middle of a run, on a front-end workstation. As simulations might take a long time, we further needed built-in checkpointing to disk so we could stop a simulation at any point and restart it later.Last, our needs tended towards parallelism in the form of many simultaneous simulationruns, rather than one large simulation spread across multiple machines. Thus MASON is a single-process library intended to run on one machine at a time.While MASON was not conceived originally for the social agents community, we believe it will prove a useful tool for social agent simulation designers, especially as computational social science matures and grows into new approaches that require functionalities such as those implemented by the MASON environment. MASON's basic functionality has considerable overlap with Ascape and RePast partially to facilitate new applications as well as replications of earlier models in Swarm, Repast or Ascape; indeed we think that developers used to these simulators will find MASON's architecture strikingly familiar. Finally, MASON is motivated by simulation results replicability as an essential tool in advancing computationally-based claims (Cioffi-Revilla 2002), similar to the role of replication in empirical studies (Altman et al. 2001).Visualization Tools Model Running on Back-End PlatformDiskCheckpointedModel Running under Visualization on User's PlatformRecoveredDiskCheckpointedRecoveredFeaturesMASON was conceived as a core library around which one might build a domain-specific custom simulation library, rather than as a full-fledged simulation environment. Such custom simulation library “flavors” might include robotics simulation library tools, graphics and physical modeling tools, or interactive simulator environments. However, MASON provides enough simulation tools that it is quite usable as a basic “vanilla” flavor library in and of itself; indeed, the applications described later in this paper use plain MASON rather than any particular simulator flavor wrapped around it.In order to achieve the flavors concept, MASON is highly modular, with an explicit layered architecture: inner layers have no ties to outer layers whatsoever, and outer layers may be completely removed. In some cases, outer layers can be removed or added to the simulation dynamically during a simulation run. We envision at least five layers: a set of basic utilities, the core model library, provided visualization toolkits, additional custom simulation layers (flavors), and the simulation applications using the library. These layers are shown in Figure 1.Two other MASON design goals are portability and guaranteed replicability. By replicability we mean that for a given initial setting, the system should produce identical results regardless of the platform on which it is running, and whether or not it is being visualized. We believe that replicability and portability are crucial features of a high-quality scientific simulation system because they guarantee the ability to disseminate simulation results not only in publication form but also in repeatable code form. To meet these goals, MASON is written in 100% Java.Java's serialization facilities, and MASON's complete divorcing of model from visualization, permit it to easily perform checkpointing: at any time the model may be serialized to the disk and reloaded later. As shown in Figure 2, models may be checkpointed and loaded with or without visualization. Additionally, serialized data can be reused on any Java platform: for example, one can freely checkpoint a model from a back-end Intel platform running Linux, then load and visualize its current running state on MacOS X.Despite its Java roots, MASON is also intended to be fast, particularly when running without visualization. The core model library encourages direct manipulation of model data, is designed to avoid thread synchronization wherever possible, has carefully tuned visualization facilities, and is built on top of a set of utility classes optimized for modern Java virtual machines.1Additionally, while MASON is a single-process, discrete-event library, it still permits multithreaded execution in certain circumstances, primarily to parallelize expensive operations in a given simulation.1 One efficiency optimization not settled yet is whether to use Java-standard multidimensional arrays or to use so-called ``linearized'' array classes (such as used in RePast). MASON has been implemented with both of them for testing purposes. In tight-loop microbenchmarks. linearized arrays are somewhat faster; but in full MASON simulation applications, Java arrays appear to be significantly faster. This is likely due to a loss in cache and basic-block optimization in real applications as opposed to simple microbenchmarks. We are still investigating this issue.FIGURE 3 MASON Utilities, Model, and Visualization LayersThe Model and Utilities LayersMASON's model layer, shown in Figure 3, consists of two parts: fields and a discrete-event schedule. Fields store arbitrary objects and relate them to locations in some spatial neighborhood. Objects are free to belong to multiple fields or, in some cases, the same field multiple times. The schedule represents time, and permits agents to perform actions in the future.A basic simulation model typically consists of one or more fields, a schedule, and user-defined auxiliary objects. There is some discrepancy in the use of the term agents between the social sciences and computer science fields. When we speak of agents , we refer to entities that can manipulate the world in some way: they are brains rather than bodies. Agents are very often embodied — physically located in fields along with other objects — but are not required to be so.The model layer comes with fields providing the following spatial relationships, butothers can be created easily.•Bounded and toroidal discrete grids in 2D and in 3D for integers, doubles, and arbitrary Objects (one integer/double/Object per grid location)•Bounded and toroidal hexagonal grids in 2D for integers, doubles, and arbitrary Objects (one integer/double/Object per grid location)• Efficient sparse bounded, unbounded, and toroidal discrete grids in 2D and 3D(mapping zero or more Objects to a given grid location)• Efficient sparse bounded, unbounded, and toroidal continuous space in 2D and 3D(mapping zero or more Objects to a real-valued location in space)• Binary directed graphs or networks (a set of Objects plus an arbitrary binary relation)Simulation ModelDiscrete Event Schedule (Representation of Time)Fields(Representations of Space)Holds AgentsAny ObjectHoldUtilitiesVisualization and GUI ToolsControllers(Manipulate the Schedule)2D and 3D Displays2D and 3D Portrayals(Draw Fields and the Objects they hold)DiskHoldThe model layer does not contain any visualization or GUI code at all, and it can be run all by itself, plus certain classes in the utilities layer. The utilities layer consists of Java classes free of simulation-specific function. Such classes include bags (highly optimized Java Collection subclasses designed to permit direct access to int, double, and Object array data), immutable 2D and 3D vectors, and a highly efficient implementation of the Mersenne Twister random number generator.The Visualization LayerAs noted earlier, MASON simulations may operate with or without a GUI, and can switch between the two modes in the middle of a simulation run. To achieve this, the model layer is kept completely separate from the visualization layer. When operated without a GUI the model layer runs in the main Java thread as an ordinary Java application. When run with a GUI, the model layer is kept essentially in its own “sandbox”: it runs in its own thread, with no relationship to the GUI, and can be swapped in and out at any time. Besides the checkpointing advantages described earlier, another important and desirable benefit of MASON's separation of model from visualization is that the same model objects may be visualized in radically different ways at the same time (in both 2D and 3D, for example). The visualization layer, and its relationship to the Model layer, is shown in Figure 3.To perform the feat of separation, the GUI manages its own separate auxiliary schedule tied to the underlying schedule, to queue visualization-agents that update the GUI displays. The schedule and auxiliary schedule are stepped through a controller in charge of the running of the simulation. The GUI also displays and manipulates the model not directly but through portrayals which act as proxies for the objects and fields in the model layer. Objects in the model proper may act as their own portrayals but do not have to.The portrayal architecture is divided into field portrayals, which portray fields in the model, and various simple portrayals stored in a field portrayal and used to portray various objects in the field portrayals' underlying field. Field portrayals are, in turn, attached to a display, which provides a GUI environment for them to draw and manipulate their fields and field objects. Portrayals can also provide auxiliary objects known as inspectors (approximately equivalent to “probes” in RePast and Swarm) that permit the examination and manipulation of basic model data. MASON provides displays and portrayals for both 2D and 3D space, and can display all of its provided fields in 2D and 3D, including displaying certain 2D fields in 3D. 2D portrayals are displayed using AWT and Java2D graphics primitives. 3D portrayals are displayed using the Java3D scene graph library. Examples of these portrayals are shown in Figure 4.APPLICABILITY TO SOCIAL COMPLEXITY ENVIRONMENTS MASON was designed with an eye towards social agent models, and we think that social science experimenters will find it valuable. MASON shares many core features with social agent simulators such as Swarm, Ascape, and RePast. In this section we specify the primary differences between MASON and RePast, followed by a simple example of MASON used to simulate the well-known HeatBugs model.a. b. c.d. e. f.FIGURE 4 Sample Field Portrayals (Applications in Parentheses). a. Discrete 2D Grids (Ant Foraging). b. Hexagonal 2D Grids (Hexagonal HeatBugs). c. Continuous2D Space (“Woims”: Flocking Worms). d. Networks in 2D (A Network Test). e. Continuous 3D Space (3D “Woims”).f. Discrete 2D Grids in 3D Space (HeatBugs)Comparison with RePastHere we provide a brief enumeration of most of the differences between the facilities provided by MASON and those of RePast, the latter of which evolved from Swarm to model situated social agents.Differences•MASON provides a full division between model and visualization. One consequenceof this key difference is that MASON can separate or join the two at any time andprovide cross-platform checkpointing in an easy fashion. Another consequence isthat MASON objects and fields can be portrayed in very different ways at the sametime, and visualization methods may change even during an expensive simulation run.•MASON has facilities for 3D models and other visualization capabilities that remainlargely unexplored in the social science realm, but which are potentially insightful forsocial science ABM simulations.•In our experience, MASON has generally faster models and visualization than RePast,especially on Mac OS X, and has more memory-efficient sparse and continuousfields. MASON's model data structures also have computational complexityadvantages.•MASON has a clean, unified way of handling network and continuous fieldvisualization.•RePast provides many facilities, notably: GIS, Excel import/export, charts and graphs,and SimBuilder and related tools. Due to its design philosophy, MASON does notinclude these facilities. We believe they are better provided as separate packagesrather than bundled. Further, we believe that many of these tools can be easily portedto MASON.Differences in Flux: MASON Will Likely Change These Features in its Final Version •RePast uses linearized array classes for multidimensional arrays. MASON presentlyhas facilities for both linearized arrays and true Java arrays, but may reduce to usingone or the other.•RePast's schedule uses doubles, while MASON's schedule presently uses longs.•RePast allows objects to be selected and moved by the mouse.•RePast allows deep-inspection of objects; MASON's inspection is presently shallow.Replicating HeatBugsHeatBugs is arguably the best known ABM simulation introduced by Swarm, and is a standard demonstration application in RePast as well. It contains basic features common to a great many social agent simulations: for example, a discrete environment defining neighborhood relationships among agents, residual effects (heat) of agents, and interactions among them. We feel that the ability to replicate models like HeatBugs, Sugarscape, Conway’s Game of Life (or other cellular automata), and Schelling’s segregation model in a new computational ABM environment should be as essential as the ability to implement regression, factor analysis, ANOVA, and similar basic data facilities in a statistical analysis environment.Indeed, a 100x100 toroidal world, 100-agent HeatBugs model was MASON's very first application. In addition to this classical HeatBugs model, we have implemented several other HeatBugs examples. Figure 4 includes partial screenshots of two of them: Figure 4B shows HeatBugs on a hexagonal grid (fittingly called “HexaBugs” in RePast), and Figure 4f shows 2D HeatBugs visualized in 3D space, where vertical scale indicates temperature, and HeatBugs onthe same square are shown stacked vertically as well. Whereas the original HeatBugs is based on a 2D grid of interacting square cells (connected by Moore or von Neumann neighborhoods), HexaBugs is more relevant in some areas of computational social science where hexagonal cells are more natural (e.g., computational political science, especially international relations) and four-corner situations are rare or nonexistent (Cioffi-Revilla and Gotts 2003).CASE STUDIESAlthough MASON has existed for only six months, we have already used it in a variety of research and educational contexts. Additionally, we are conducing tests to port RePast, Swarm, and Ascape models to MASON, ported by modelers not immediately familiar with MASON. These ports include a model of warfare among countries, a model of land use in a geographic region, and a model of the spread of anthrax in the human body).In this section we describe the implementation and results of two research projects that used the MASON simulation library. The first case study used MASON to discover new ant-colony foraging and optimization algorithms. The second case study applied MASON to the development of evolved micro-aerial vehicle flight behaviors. These are not computational social science models per se: but they are relevant enough to prove illuminating. The first case study uses a model that is similar to the discrete ABM models presently used, but it is applied to an automated learning method, demonstrating the automated application of large numbers of simulations in parallel. The second case study uses a continuous 2D domain environment and interaction, which we think points to one future area of ABM research. Neither of these more advanced applications is implemented in Swarm, RePast, or Ascape at present, and both take advantage of features special to MASON. In both cases experiments were conducted running MASON on the command-line in several back-end machines, and the progress was analyzed by attaching the simulators to visualization tools on a front-end workstation. Additionally, the second case involves a continuous field that is scalable and both memory- and time-efficient (both O(#agents), rather than O(spatial area)).Both of the projects described below have an evolutionary computation (EC) component: to save repetition, we give a quick explanation of evolutionary computation here. EC is family of stochastic search and optimization techniques for “hard” problems for which there is no known procedural optimization or solution-discovery method. EC is of special interest to certain multiagent fields because it is agent-oriented: it operates not by modifying a single candidate solution, but by testing a “population” of such solutions all at one time. Such candidate solutions are known as “individuals”, and each individual's assessed quality is known as its “fitness”. The general EC algorithm is as follows. First, an initial population of randomly-generated individuals is created and each individual's fitness is assessed. Then a new population of individuals (the next generation) is assembled through an iterative process of stochastically selecting individuals (tending to select the fitter ones), copying them, then breeding the copies (mixing and matching individuals' components and mutating them), and placing the results into the next generation. The new generation replaces the old generation; its individuals' fitnesses are in turn assessed, and the cycle continues. EC ends when a sufficiently fit individual is discovered, or when resources (notably time) expire. The most famous example of EC is the genetic algorithm (GA) (Holland 1975), but other versions exist as well; we will discuss genetic programming (GP) (Koza 1992) as one alternative EC method below.Ant ForagingAnt foraging models attempt to explain how ant colonies discover food sources, then communicate those discoveries to other ants through the use of pheromone trails — leaving proverbial “bread crumbs” to mark the way. This area has become popular not just in biology but curiously in artificial intelligence and machine learning as well, because pheromone-based communication has proven an effective abstract notion for new optimization algorithms (known collectively as ant colony optimization) and for cooperative robotics.Previous ant foraging models have to date relied to some degree on a priori knowledge of the environment, in the form of explicit gradients generated by the nest, by hard-coding the nest location in an easily-discoverable place, or by imbuing the ants with the knowledge of the nest direction. In contrast, the case study presented here solves ant foraging problems using two pheromones, one applied when leaving the nest and one applied when returning to the nest. The resulting algorithm is orthogonal and simple, and biologically plausible, yet ants are able to establish increasingly efficient trails from the nest to the food even in the presence of obstacles.Ants are sensitive to one of the two pheromones at any given time; the sensitivity depends on whether they are foraging or carrying food. While foraging, an ant will stochastically move in the direction of increasing food pheromone concentration, and will deposit some amount of nest pheromone. If there is already more nest pheromone than the desired level, the ant deposits nothing. Otherwise, the ant “tops off” the pheromone value in the area to the desired level. As the ant wanders from the nest, its desired level of nest pheromone drops. This decrease in deposited pheromone establishes an effective gradient. When the ant is instead carrying food, the movement and pheromone-laying procedures use the opposite pheromones than those used during foraging.The model assumes a maximum number of ants per location in space. At each time step, an ant will move to its best choice among non-full, non-obstacle locations; the decision is made stochastically with probabilities correlated to the amounts of pheromones in the nearby locations. Ants move in random order. Ants live for 500 time steps; a new ant is born at the nest each time step unless the total number of ants is at its limit. Pheromones both evaporate and diffuse in the environment.Figure 4a shows a partial screenshot of a small portion of the ant colony foraging environment. The ants have laid down a path from the nest to the food and back again. Part of the ground is colored with pheromones. The large oval regions are obstacles. The MASON implementation was done with two discrete grids of doubles (two pheromone values), discrete grids of obstacles, food sources, and ant nests, and a sparse discrete grid holding the ants proper. Each ant is also an agent (and so is scheduled at each time step to move itself). Additional agents are responsible for the evaporation and diffusion of pheromones in the environment, and also for creating new ants when necessary.In addition to the successful design of hard-coded ant foraging behaviors, we also experimented with letting the computer search for and optimize those behaviors on its own. For this purpose, we connected MASON to the ECJ evolutionary computation system (Luke 2002) (/~eclab). ECJ handled the main evolutionary loop: an individual took the form of a set of ant behaviors that was applied to each ant in the colony. To evaluate an individual, ECJ spawned a MASON simulation with the specified ant behaviors. The simulation was run。
西门子S7-300系列产品数据参数表说明书

24 V 240 mA 60 mA 3W 4 Yes 25 mA 18 V Yes Yes Yes
03/05/2013
subject to modifications © Copyright Siemens AG 2013
0 to 20 mA -20 to +20 mA 4 to 20 mA Load impedance (in rated range of output) with voltage outputs, min. with voltage outputs, capacitive load, max. with current outputs, max. with current outputs, inductive load, max. Cable length Cable length, shielded, max. Analog value creation Integrations and conversion time/ resolution per channel Resolution with overrange (bit including sign), max.
Analog outputs Number of analog outputs Voltage output, short-circuit protection Voltage output, short-circuit current, max. Current output, no-load voltage, max. Output ranges, voltage 0 to 10 V 1 to 5 V -10 to +10 V Output ranges, current
OB教学大纲(2010-2012)

《组织行为学》课程教学大纲(MBA适用)编著:夏清华一、教学目的和要求有效地领导个体和群体是管理卓越的关键。
然而,它也是作为一个管理者最困难的挑战。
组织行为学这门课程旨在帮助管理者和未来管理者首先获取和理解组织中与人类行为相关的概念和理论知识,然后学会怎样在实践中运用这些知识。
具体来说,这门课程能够: 帮助你理解和管理组织中的个人和人与人之间的行为。
通过提供群体动力学和团队建立方面的理论和经验知识,帮助你管理群体去实现高绩效。
帮助你理解领导和变革组织所面临的挑战。
新的OB体系以“领导力开发与组织行为”为逻辑,属于品格塑造与软技能培养课程,新的课程体系融合了组织行为理论、领导力理论二方面的内容。
在以往的MBA课程中,组织行为与领导力开发这两方面往往是分离的,并又有很多重合。
新的课程体系力求精简,让两部分内容互相强化,并以领导力开发为主线,强调对人格塑造、自我认识和自我管理的操练。
这门课的另一个亮点是教练式学习方法的引入,要求教师组在必要时候多个教师同时进入课堂,保证对学生的有效指导。
同时,将以前组织行为学中较为原理性和综合性知识、抽象的软技能变得更具有可操作性,更贴近于商业现实。
为了学好这门课程,要求学生具有很好的管理学基础知识,积极参与课堂的讨论和团队学习,认真完成案例分析和专题讨论。
通过这门课的学习,学生能够很好地理解管理学和组织行为学之间的密切关系,进而较完整地理解组织行为和管理实践的完整内容和理论框架。
二、课程内容与学时分配组织行为学课程的核心内容包括:理论框架,个体行为分析,动机与激励,群体行为与工作团队,管理沟通与冲突,领导艺术,组织结构,组织文化与组织变革。
课程内容与学时分配表讲授内容 学 时案例分析领导力与OB 4 苹果系列领导风格与模式 4 人生历练的历程领导如何对个体实施管理 4 BEHAVIOR MODIFICATION领导如何实施激励 4 联想和华为的接班人领导如何授权与组建团队 4 华为的职业化领导如何管理沟通与冲突 4 创业领袖退场与继任冲突领导如何创建企业文化 4 绩效主义毁了索尼领导如何实施变革 4 黄海液压系统公司三、教材与阅读材料教材:[1] Stephen P.Robbins:《组织行为学》(第12版),中国人民大学出版社2008 阅读材料:(1)乔治.曼宁(George Manning)等:领导的艺术,电子工业出版社,2011(2 James Kouzes, Barry Posner, 领导力(Leadership Challenge),电子工业出版社,2011(3) 彼得. 德鲁克(Peter Drucker):卓有成效的管理者,机械工业出版社,2005(4) 金杰.拉皮德.伯格达: 九型人格与领导力,中信出版社,2010(5) 吴建国冀勇庆:《华为的世界》,中信出版社,2006(6)凌志军:联想风云,中信出版社,2005(7)南怀瑾:南怀瑾演讲录,上海人民出版社,2008(8)曾国藩:曾国藩家书精选,中央编译出版社,2008(9) (10) (11) (12)组织行为学案例,夏清华编辑,2011版四、作业和考核方式作业可见于每章课件(PPT)或教材中中的思考题。
AOB508经济型数字指示控制仪说明书
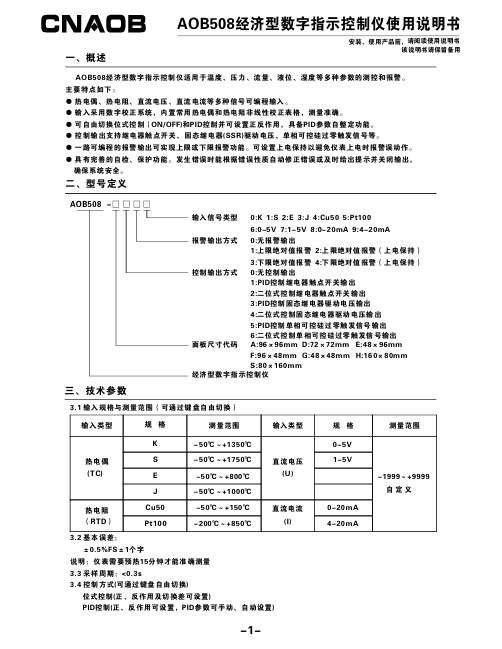
AOB508经济型数字指示控制仪使用说明书安装、使用产品前,请阅读使用说明书该说明书请保留备用AOB508经济型数字指示控制仪适用于温度、压力、流量、液位、湿度等多种参数的测控和报警。
主要特点如下:●热电偶、热电阻、直流电压、直流电流等多种信号可编程输入。
●输入采用数字校正系统,内置常用热电偶和热电阻非线性校正表格,测量准确。
●可自由切换位式控制(ON/OFF)和PID 控制并可设置正反作用,具备PID 参数自整定功能。
●控制输出支持继电器触点开关、固态继电器(SSR)驱动电压、单相可控硅过零触发信号等。
●一路可编程的报警输出可实现上限或下限报警功能。
可设置上电保持以避免仪表上电时报警误动作。
●具有完善的自检、保护功能。
发生错误时能根据错误性质自动修正错误或及时给出提示并关闭输出,确保系统安全。
一、概述二、型号定义1:PID 控制继电器触点开关输出2:二位式控制继电器触点开关输出3:PID 控制固态继电器驱动电压输出4:二位式控制固态继电器驱动电压输出5:PID 控制单相可控硅过零触发信号输出6:二位式控制单相可控硅过零触发信号输出D:72×72mm E:48×96mmG:48×48mm H:160×80mm AOB508-□□□□输入信号类型报警输出方式0:无报警输出1:上限绝对值报警2:上限绝对值报警(上电保持)3:下限绝对值报警4:下限绝对值报警(上电保持)控制输出方式0:无控制输出面板尺寸代码A:96×96mm F:96×48mm S:80×160mm经济型数字指示控制仪0:K 1:S 2:E 3:J 4:Cu505:Pt1006:0-5V 7:1-5V 8:0-20mA 9:4-20mA 三、技术参数3.1输入规格与测量范围(可通过键盘自由切换)输入类型输入类型-1999~+9999自定义规格规格KS E J热电偶(T C)直流电压(U)Cu50测量范围测量范围-50℃~+1350℃-50℃~+1750℃-50℃~+800℃-50℃~+1000℃-50℃~+150℃-200℃~+850℃Pt100热电阻(RTD )0-5V1-5V0-20mA 4-20mA直流电流(I)3.2基本误差:±0.5%FS ±1个字3.3采样周期:<0.3s3.4控制方式(可通过键盘自由切换)位式控制(正、反作用及切换差可设置)PID 控制(正、反作用可设置,PID 参数可手动、自动设置)说明:仪表需要预热15分钟才能准确测量单位:mm四、外形尺寸及开孔尺寸A D E F G H S宽967248964816080高967296484880160宽926845924515276高926892454576152安装开孔尺寸面板尺寸代码高916744904415075深916790444475150宽100100100100100壳体尺寸面板尺寸1001003.5报警方式(可通过键盘自由切换)一路可编程的报警输出可实现上限或下限报警功能(继电器输出)。
20216275_经皮椎间孔镜对复发性腰椎间盘突出症合并腰椎后凸畸形患者的疗效及对患者细胞因子的影响

peng,SHEN Dan
p
ZHOU Yi
zha
i,DUAN L
i
u*
peng,MA Guo
j
(
Depar
tmentof Or
t
hopaedi
c
s,t
heSe
c
ondCent
ra
lHo
spi
t
a
lof Baodi
ng,
Hebe
iPr
ov
i
nc
e,Baodi
ng 072750,Ch
i
na)
[
Ab
(
2.
6±0.
2)年。2 组 年 龄、性 别、病 程 差 异 均 无 统 计
学意义,具有可比性(
P >0
.05)。
本研 究 经 医 院 伦 理 委 员 会 批 准;患 者 均 签 署 知
情同意书。
1.
2 纳入标准和排除标准 纳入标准:① 满足复发
性腰椎间盘突出症 合 并 腰 椎 后 凸 畸 形 的 临 床 诊 断,
病时间 3 个月 ~6 年 3 个月,平均(
2.
5±0.
3)年。研
术切口,确认无误 后 置 入 引 流 装 置,缝 合 切 口,手 术
女性 13 例;年龄 25~67 岁,平均(
45.
6±3.
2)岁;发
究组男 性 20 例,女 性 12 例;年 龄 23~65 岁,平 均
(
45.
3±2.
3)岁;发病时间 4 个月 ~6 年 5 个月,平均
2019-07-26
[作者简介]郑义朋(
1983- ),男,河北曲阳人,河北省保定市第
ob-mba_02

能力测验示例——标准瑞文推理测验 能力测验示例 标准瑞文推理测验
1
2
3
4
5
6
7
8
2-7
能力测验示例——高级瑞文测验 高级瑞文测验 能力测验示例
1
2
3
4
5
6
7
8 2-8
态
度
• 对人、物或者事件的评价性陈述 – 喜欢或者 不喜欢 • 态度反映个体对某人、物或者事件的感受。
2-9
态度的三要素( 成分) 态度的三要素(ABC成分) 成分
2-21
管理中的实践
• • • • 赞美、奖励远比惩罚有效 重视规则的传授与掌握 体验式学习(experienced learning) 教练技巧(coaching skill)
2-22
2-19
行为塑造( 行为塑造( Shaping Behavior) )
1. 2. 3. 4. 正强化(Positive reinforcement) 负强化(Negative reinforcement) 惩罚(Punishment) 消退(Extinction)
2-20
强化程序
• 连续强化Continuous reinforcement • 间歇强化Intermittent reinforcement
组织行为学
龚 文 北京工商大学商学院
2-1
第二章 个体行为的基础
1. 2. 3. 4. 5. 解释能力与工作业绩的关系 比较态度的三大要素 讨论工作满意度及相关问题 理解如何塑造他人的行为 讨论四种强化程序
2-2
能
力
• 能力( ability )、智力( intellectual ability )、职业性向(aptitude)认知能力 (cognitive ability ) • 能力的测量与评价 • 能力与工作业绩之间存在正相关 • 能力与工作满意度之间存在零相关 • 能力与职业匹配,工作业绩会提高
基于DBOGSVM_的学生成绩三分类预测模型

第38卷第2期2024年3月兰州文理学院学报(自然科学版)J o u r n a l o fL a n z h o uU n i v e r s i t y ofA r t s a n dS c i e n c e (N a t u r a l S c i e n c e s )V o l .38N o .2M a r .2024收稿日期:2023G05G04基金项目:安徽省高等学校自然科学研究项目(K J 2021A 1221)作者简介:张广海(1988G),男,安徽阜阳人,讲师,硕士,研究方向为智能优化算法应用㊁数据挖掘与可视化分析.E Gm a i l :Z h a n g _G u a n gh a i @163.c o m.㊀㊀文章编号:2095G6991(2024)02G0056G06基于D B O GS VM 的学生成绩三分类预测模型张广海1,祖㊀璇2,王㊀杨1,3(1安徽师范大学皖江学院大数据与人工智能系,安徽芜湖241003;2.安徽师范大学皖江学院经济系,安徽芜湖241003;3.安徽师范大学计算机与信息学院,安徽芜湖241000)摘要:为提高学生学习效率和教师教学管理水平,提出基于D B O GS VM 的学生成绩三分类预测模型.首先根据皮尔逊相关系数筛选特征属性;然后针对数据不均衡问题,经对比实验选用A D A S Y N 技术;之后由螳螂优化算法通过迭代寻优支持向量机的参数;最后由支持向量机建立学生成绩三分类预测模型.在学生成绩数据集上进行测试,实验结果表明:本文方法预测准确率比S S A GS VM 提高了2.09%,达到了91.67%;F 1分数的加权平均值为0.92,证明了模型的稳定性.关键词:螳螂优化算法;支持向量机;A D A S Y N 技术;学生成绩预测中图分类号:T P 391㊀㊀㊀文献标志码:AT h r e e Gc l a s sP r e d i c t i o n M o d e l o f S t u d e n tG r a d eB a s e do nD B O GS V MZ HA N GG u a n g Gh a i 1,Z U X u a n 2,WA N GY a n g1,3(1.D e p a r t m e n t o fB i g D a t a a n dA r t i f i c i a l I n t e l l i ge n c e ,W a n j i a n g C o l l e g e o fA n h u iN o r m a lU n i v e r s i t y,W u h u241003,A n h u i ,C h i n a ;2.D e p a r t m e n t o fE c o n o m i c s ,W a n j i a n g C o l l e g e o fA n h u iN o r m a lU n i v e r s i t y,W u h u241003,A n h u i ,C h i n a ;3.S c h o o l o fC o m p u t e r a n d I n f o r m a t i o n ,A n h u iN o r m a lU n i v e r s i t y,W u h u241000,A n h u i ,C h i n a )A b s t r a c t :T oi m p r o v es t u d e n t l e a r n i n g e f f i c i e n c y a n de n h a n c et e a c h e rt e a c h i n g m a n a ge m e n t l e v e l ,ef f e c t i v e f e a t u r e s a r em a i n l y e x t r a c t e d f r o ms t u d e n t p e r f o r m a n c e d a t a ,a n d a t h r e e Gc l a s Gs i f i c a t i o n p r e d i c t i o nm o d e l f o r s t u d e n t p e r f o r m a n c e b a s e do nD B O GS VMi s p r o p o s e d .F i r s t l y ,t h e f e a t u r e s a t t r i b u t e s a r e s e l e c t e da c c o r d i ng to t h eP e a r s o nc o r r e l a t i o nc o e f f i c i e n t ,a n d t h e n t h eA D A S Y Nt e c h n i q u e i s u s e d t o s o l v e t h e p r o b l e mo f d a t a i m b a l a n c e ,a f t e r t h a t ,t h ed u n gb e e t l e o p t i m i z e i su s e dt od e t e r m i n e t h e p a r a m e t e r so f t h es u p p o r tv ec t o rm a c h i n e ,a n dt h e s u p p o r t v e c t o rm a c h i n e i s u s ed t ob u i l d a t h re e Gc l a s s p r e d i c t i n g mo d e l f o r s t u d e n t g r a d e .T h e e x p e r i m e n t a l r e s u l t s s h o wt h a t t h e p r e d i c t i o n a c c u r a c y o f t h e p r o p o s e dm e t h o d i s 2.09%h i gh Ge r t h a nt h a to fS S A GS VM ,r e a c h i n g 91.67%.T h e w e i g h t e da v e r a g eo fF 1Gs c o r e i s0.92,w h i c h p r o v e s t h e s t a b i l i t y of t h em o d e l .K e y wo r d s :d u n g b e e t l eo p t i m i z e ra l g o r i t h m ;s u p p o r tv e c t o r m a c h i n e ;A D A S Y Nt e c h n i q u e ;s t u d e n t g r a d e p r e d i c t i o n0㊀引言随着信息技术的快速发展,与教育相关的数据在内容和数量上都有了极大的提高.如果合理利用这些数据信息,可以有效提高学生的学习成绩和教师的教学质量.因此,教育数据挖掘作为一个新兴的研究领域,开始被越来越多的学者关注.预测学生成绩的能力是提高学生学习成绩的解决方案之一[1],有助于探索学生或教师在教学过程中遇到的各种问题和困难.目前,基于机器学习模型的研究在预测学生学习成绩方面证明了其可靠性[2G3].文献[4]利用注意力机制方法,采用C N N和L S T M技术构建了学生成绩预测模型,该模型充分解决了手动方法对特征提取不全㊁模型融合效果不理想等情况,提高了预测准确率.文献[5]在预测学生成绩时利用了密度全局KGm e a n s算法,从实验结果可以看出成长中的陪伴㊁双亲学历㊁学习时的激励和引导对孩子的学习成绩至关重要.然而,随着学生成绩数据集的扩大和复杂,不平衡分布对分类预测的影响越来越高,这直接降低了预测模型的性能.神经网络和机器学习中面临的重要挑战之一是分类不平衡问题,因此了解不平衡分类方法对于建立有效的预测模型㊁提高学生的学习成绩和课题表现非常重要[6].螳螂优化算法(D u n g B e e t l e O p t i m i z e r, D B O)[7]是一种新型智能算法,具有收敛速度快㊁计算精度高等特点.因此,本文提出了一种基于D B OGS VM的学生成绩三分类预测模型.为验证所提模型的优越性和稳定性,在阿里云天池平台学生成绩数据集上与3种预测算法进行对比实验.结果显示了该方法的模型稳定性最好,预测准确率最高.1㊀相关概念1.1㊀DBO算法原理螳螂优化算法由X U E等[7]于2022年11月提出,该算法以螳螂为研究对象,模拟了螳螂的滚球㊁跳舞㊁觅食㊁偷窃和繁殖行为.1.1.1滚球行为为模拟滚球行为,螳螂需要在整个搜索空间中朝着预设的目标方位移动,假设光源的强度会影响螳螂的路径.在滚动过程中,滚球螳螂的位置可以表示为:x i(t+1)=x i(t)+αˑkˑx i(t-1)+bˑәx,әx=x i(t)-X w,(1)式中:t表示当前的迭代次数;x i(t)表示第i只螳螂在第t次迭代的位置信息;kɪ(0,0.2],是一个常数值,表示偏转系数;bɪ(0,1),是一个常量;α是一个取值为-1或1的自然系数;X w表示全局最差位置;әx模拟光照强度的变化.1.1.2㊀跳舞行为跳舞行为在螳螂滚粪球时起着重要的作用.当螳螂遇到障碍无法前进时,它需要通过跳舞进行重新定位来改变线路.一旦成功确定了一个新的方向,就会继续前进.跳舞行为的更新公式为:x i(t+1)=x i(t)+t a n(θ)x i(t)-x i(t-1),(2)式中:θɪ(0,π],表示偏转角.1.1.3㊀繁殖行为选择一个安全环境产卵对螳螂至关重要,因此提出了一种边界选择策略来模拟雌性螳螂产卵的区域.繁殖行为更新公式为:L b∗=m a x X∗ˑ1-R(),L b(),U b∗=m i n X∗ˑ1+R(),U b(),(3)式中:X∗表示当前局部最优位置;L b∗和U b∗分别表示产卵区的下界和上界;R=1-t/T m a x, T m a x表示最大迭代次数;L b和U b分别表示优化问题的下界和上界.一旦确定了产卵区,雌性螳螂就会在这个区域选择孵卵球产卵.D B O算法约定:每只雌性螳螂在每次迭代中只产生一个卵.此外,由公式(3)可知,产卵区的边界范围是动态变化的,且由R 值决定.因此,迭代过程中的孵化球位置也是动态的,计算公式为:B i(t+1)=X∗+b1ˑB i(t)-L b∗()+b2ˑB i(t)-U b∗(),(4)式中:B i(t)为第i个卵球在第t次迭代时的位置信息;b1和b2分别表示大小为1ˑD维的随机向量,D为优化问题的维数.1.1.4㊀觅食行为成年螳螂需要从地面出来寻找食物,因此建立最佳的觅食区域来指导觅食是有必要的.最佳觅食区域的更新公式为:L b b=m a x X bˑ1-R(),L b(),U b b=m i n X bˑ1+R(),U b(),(5)式中:X b表示全局最优位置;L b b和U b b分别表示最优觅食区域的下界和上界.因此,螳螂的位置更新公式为:x i(t+1)=x i(t)+C1ˑx i(t)-L b b()+C2ˑx i(t)-U b b(),(6)式中:x i(t)表示第i个螳螂在第t次迭代时的位75第2期张广海等:基于D B OGS VM的学生成绩三分类预测模型置信息;C 1为服从正态分布的随机数;C 2为(0,1)范围内的随机向量.1.1.5㊀偷窃行为螳螂中也存在偷窃行为,从其他螳螂身上偷粪球者称之为小偷.由公式(5)可知,X b 是最优食物来源.因此,假设X b 附近为争夺食物的最佳地点.在迭代过程中,小偷的位置信息更新公式为:x i (t +1)=X b+S ˑg ˑx i (t )-X ∗+x i (t )-X b(),(7)式中:x i (t )表示第i 个小偷在第t 次迭代时的位置信息;g 的大小为1ˑD ,是随机向量,且服从正态分布;S 表示常数值.1.2㊀支持向量机算法支持向量机(S u p p o r tV e c t o r M a c h i n e ,S V M )是一类有监督的分类器[8],其优势在于学习高维数据的能力及实践能力.线性可分的目标是找到边际最大的分离超平面,使用内核函数生成线性可分的转换特征数据.线性分类器函数可表示为:f X ()=w TX +b ,(8)式中:w 和b 是未知的,并从训练数据集中确定.具体实现公式为m i n J w ,ξ()=12 w 2+C ðNi =1ξi ,s .t .y i f X i ()ȡ1-ξi ,i =1,2, ,N .(9)式中:ξi 是一个松弛变量,用于控制训练误差并保持约束;参数C 用于控制模型复杂度(第1项)和经验风险(第2项)之间的权衡.根据公式(8),输入向量x 通过非线性映射函数Φ(x )首先映射到一个高维空间,然后根据公式(9)在此映射空间里由线性分类器分类.使用内核概念K X i ,X j ()=ΦT(X i )Φ(X j )重写S VM 分类器函数,公式可表示为:f X i ()=ðN sk =1y kαk K (X i ,S k )+b ,(10)式中:S k ,k =1,2, ,N s 是支持向量,它对应分类器的决策边缘内或在决策边缘上的训练样本,其值在训练步骤中确定.核函数起着将输入向量隐式映射到高维特征空间的核心作用,在该空间中实现了更好的可分性.由于高斯核函数可以映射到无限维,且决策边界多样,因此本文采用高斯核函数,其定义式为:K X i ,X j ()=e x p - X i ,X j 22σ2æèçöø÷,(11)其中,σ为核宽度,是一个为大于零的常数.2㊀DBO GSVM 学生成绩预测模型多分类学生成绩预测模型框架如图1所示.该框架包含数据准备㊁数据预处理㊁模型构建和数据可视化4部分.图1㊀多分类学生成绩预测模型框架2.1㊀实验数据本文使用的数据集来自阿里云天池平台,包含305个男生和175个女生的基本情况以及课堂课外表现的量化数据,数据集包含共480条用户行为记录,每个记录都包含性别㊁国籍㊁出生地等17个字段属性.数据集中的原始数据特征包含字符型与整型,需要将所有特征数值化处理.本文经分析选择pa n d a s 独热编码的方式将所有的分类型特征转换为数字.2.2㊀数据预处理2.2.1㊀特征筛选学生学习成绩数据集中共有17个特征属性,每一个特征属性对学生的学习成绩都有一定的影响,但是不同的特征影响强度不同.合理选择特征属性将有效节省优化时间,提高预测准确率.为反映特征属性间的关联程度,采用了皮尔逊相关系数.相关系数r ɪ[-1,1],|r |越接近于1,表明关联程度越显著;反之,表明关联程度越弱.一般认为|r |<0.2时为弱相关,可以忽略.本文利用皮尔逊相关系数分析了所有属性后,保留了10个特征属性用于构建预测模型,具体数据如表1所列.2.2.2㊀A D A S Y N 技术平衡数据集数据集中成绩分类的情况如图2所示.由图2可知样本数量存在类别不平衡问题.不平衡数据将在很大程度上影响预测结果,因此需要合成少数类样本来平衡数据集.通过不同过采样方法后的学生成绩预测准确率,选择A D A S Y N 技术平衡少数类,预测准确率结果如表2所列,预处理后的结果分布如图3所示.85㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀兰州文理学院学报(自然科学版)㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀第38卷表1㊀保留特征属性的数据特征描述序号特征属性解释说明1G e n d e r性别2R e l a t i o n孩子家庭教育负责人(父亲,母亲)3R a i s e d H a n d s学生该学期上课举手的次数4V i s i t e d R e s o u r c e s学生浏览在线课件的次数5A n n o u c e m e n t s V i e w 学生浏览学校公告的次数6D i s c u s s i o n学生参与课堂讨论的次数7P a r e n t A n s w e r i n g S u r v e y 家长是否填写了关于学校的问卷调查(是,否)8P a r e n t S c h o o l S a t i s f a c t i o n家长对于学校的满意度(好,不好)9S t u d e n t A b s e n c e D a ys 学生缺勤天数(大于7天,小于7天)10C l a s s L :分数区间在0~59;M :分数区间在60~89;H :分数区间在90~100图2㊀成绩分类统计结果表2㊀不同过采样方法学生成绩预测准确率过采样技术S MO T ES MO T E N C B o r d e r l i n e S MO T E A D A S Y N 准确率/%89.5887.587.591.67运行时间/s 28.7131.7628.6326.43图3㊀经过A D A S Y N 平衡之后的成绩分类统计结果2.3㊀模型构建S VM 分类器的性能直接取决于核函数参数c 和惩罚因子g ,因此提高学生成绩的预测率就需要合理选择参数.本文使用D B O 优化S VM ,即找到S VM 参数的最优解.D B O GS VM 学生成绩预测流程如图4所示,主要包含数据读取㊁数据预处理㊁D B O 优化S VM 参数和预测等模块.螳螂优化算法的流程如图5所示,具体算法实现过程如下:图4㊀D B O GS V M 学生成绩预测流程㊀㊀(1)设定最大迭代次数T m a x 和种群数量p o p ,按照要求划分滚球螳螂㊁孵化球㊁小螳螂和小偷的个数,并初始化D B O 算法的参数;(2)目标函数计算所有因子的适应度值;(3)更新所有螳螂的位置;(4)判断每个因子是否超出边界.若未出界,继续执行步骤(2)和(3);否则执行步骤(5);(5)更新当前最优解及其适应度值;(6)重复上述步骤,直到迭代次数t 满足终止95第2期张广海等:基于D B O GS VM 的学生成绩三分类预测模型准则,输出全局最优解及其适应度值.求得种群中适应度值的最优位置即为最优的核函数参数c 和惩罚因子g.图5㊀螳螂优化算法流程3㊀实验结果与分析学生成绩数据集中训练集和测试集的划分比例为9:1.设定螳螂总群数量为35,其中滚球螳螂㊁孵化球㊁小螳螂和小偷的个数分别为7㊁7㊁10和11,迭代20次.计算机配置为I n t e l (R )C o r e (T M )i 5G10210U C P U @1.60G H z ,内存为16.00G ,采用P y t h o n 编程环境,对基于D B O GS VM 的学生成绩预测模型进行预测测试分析,测试的分类结果如图6所示.由图6可知,L 类别的预测准确率为100%.在全部48组测试分类样本数据中,测试分类正确样本有44组,故模型分类预测准确率达到了91.67%,测试分析结果如表3所列.表3㊀测试分析结果类别测试分类总样本测试分类正确样本准确率/%样本484491.67为验证本文算法的性能,将D B O GS VM 模型与S S A GS VM [9]㊁S VM 和随机森林[10]3种模型进行对比实验,结果如表4所列.4种分类模型精确率㊁召回率和F 1分数的性能对比如图7所示.图6㊀测试集分类结果表4㊀4种分类模型性能比较模型成绩类别精确率召回率F 1分数准确率/%D B O GS VML1.001.001.00M0.960.880.92H 0.790.920.85加权平均0.920.920.9291.67S S A GS VML1.000.900.95M0.830.960.89H 0.890.670.76加权平均0.880.880.8789.58S VML0.560.710.63M0.700.760.73H 0.880.700.78加权平均0.750.730.7372.92随机森林L1.001.001.00M0.830.770.80H 0.570.670.62加权平均0.800.790.8079.17㊀㊀通过对表4和图7分析可以得到:①除了S VM 模型外,其他3种分类模型在L 类别上的性能都很好;②召回率是指被正确分类的正样本占实际正样本的比值.由图7(b )观察可知除了基于S S A GS VM 分类模型在M 类别上略高外,D B O GS VM 模型在L 类别和H 类别都具有较明显的优势;③F 1分数的值为[0,1],值越大说明模型越稳定.由图7(c )可知,D B O GS VM 模型性能最为稳定,因为其在3个类别上的F 1分数均最高;④S VM 模型的准确率只有72.92%,预测效果最差;⑤D B O GS VM 模型的准确率比S S A GS VM 模型提高了2.09%,达到了91.67%.D B O 与S S A 寻优时间对比如表5所列.由06㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀兰州文理学院学报(自然科学版)㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀第38卷(a)精确率(b)召回率(c )F 1分数图7㊀4种分类模型的性能对比表5可以看出,D B O GS VM 模型不仅预测准确度高,寻优速度也较快,在学生成绩分类中表现出了良好的性能.表5㊀D B O 与S S A 寻优时间对比算法D B O GS VM S S A GS VM 寻优时间/s26.4327.924㊀结语预测学生的学习成绩是监测学生学业表现的关键指标之一,同时可以使教育者精准帮扶学生完成学习内容.为提高学生学习预测准确率,研究了D B O GS VM 的学生成绩三分类预测模型.利用A D A S Y N 技术平衡少数类,再通过D B O 优化算法寻优S VM 核心参数,从而有效地提高了预测准确率.与麻雀搜索算法相比,寻优时间更短.今后,将继续改进D B O 算法,以期提高其寻优能力和学生成绩分类预测准确率.参考文献:[1]A L Y A H Y A NE ,D U S T E G O RD.P r e d i c t i n g ac ade m i c s u c c e s s i nh i gh e r e d u c a t i o n :l i t e r a t u r e r e v i e wa n db e s t p r a c t i c e s [J ].I n tJ E d u c .T e c h n o l .H i gh e r E d u c .,2020,10(5):1G21.[2]A L B R E I K IB ,Z A K IN ,A L A S HWA L H.As ys t e m Ga t i c l i t e r a t u r e r e v i e wo f s t u d e n t pe rf o r m a n c e p r e d i c Gt i o nu s i ng m a chi n e l e a r n i n g t e c h n i q u e s [J ].E d u cS c i ,2021,11(9):552G559.[3]吕品,于文兵,汪鑫,等.基于机器学习的学生成绩预测及教学启示[J ].计算机技术与发展,2019,29(4):200G203.[4]梅玉丽.基于校园大数据的学生成绩预测研究[D ].兰州:兰州理工大学,2021.[5]谢娟英,张宜,陈恩红.学生成绩关键因素挖掘与成绩预测[J ].南京信息工程大学学报(自然科学版),2019,11(3):316G325.[6]赵喆梅.基于过采样的不平衡数据分类方法研究[D ].兰州:兰州交通大学,2023.[7]X U EJK ,S H E NB .D u n g b e e t l e o pt i m i z e r :a n e w m e Gt a Gh e u r i s t i c a l g o r i t h mf o r g l o b a l o p t i m i z a t i o n [J ].T h e J o u r n a l o f S u p e r c o m p u t i n g,2022,35:1G32.[8]K A B B A D JY ,R E G R A G U IF ,H I MM IM M.M i c r o Gc a l c i f i c a t i o nde t e c t i o nu s i n g af u z z y i n f e r e n c es y s t e m a n d s u p p o r t v e c t o rm a c h i n e s [J ]I E E E ,2012,15:312G315.[9]张广海,祖璇.基于麻雀搜索算法和S VM 的学生成绩预测研究[J ].池州学院学报,2023,37(3):11G15.[10]庄巧蕙.基于改进随机森林算法的研究与应用[D ].厦门:华侨大学,2019.[责任编辑:李㊀岚]16第2期张广海等:基于D B O GS VM 的学生成绩三分类预测模型。
OBO外部防雷技术

Copyright OBO BETTERMANN 2010
04.10.2023
9
OBO isCon®-System
isolated Conductor
Copyright OBO BETTERMANN 2010
04.10.2023
10
Construction of isCon-conductor
Copyright OBO BETTERMANN 2010
Copyright OBO BETTERMANN 2010
04.10.2023
34
isCon线制作步骤
1.
2.
3.
4.
5.
6.
Copyright OBO BETTERMANN 2010
04.10.2023
35
isCon线接头制作
7.
8.
9.
10.
11.
12.
Copyright OBO BETTERMANN 2010
04.10.2023
36
快速组合
thread-ed rod
Fang-Fix concrete blocks
Copyright OBO BETTERMANN 2010
04.10.2023
12
IEC62305中电气绝缘距离计算公式
Copyright OBO BETTERMANN 2010
04.10.2023
13
s
ki
kc km
L
isolated lightning protection
公式中的参数说明
ki 雷区
s
04.10.2023
30
1.有效保护外部重要设备及人身安全 2. 释放天面空间 3. 专用切割工具,快速切割,全现场制作 4. 多种的连接备件,安装无须焊接,
组织行为学核心主题全系列(MBA研修班学生版4日)

(2) 群体行为(OB的中观层面)
群体动力学、群体动态发展、群体间动力 学等。 工作团队研究 领导行为研究
12 2020/3/3
(3) 组织行为(OB的宏观层面)
组织结构和组织设计、组织文化、组织变 革等。
13 2020/3/3
引论 思考题: 1、定义组织行为学, 并与管理学进行比较。 2、管理者为什么要学习和研究组织行为
(三)态度的作用
“态度决定一切” 态度对人的生活方式、工作或行为方式、
工作绩效等有很大的影响。在组织管理 中,每个职工对组织目标、政策、管理 制度和本职工作的态度,直接关系到组 织目标的能否实现。在管理者对下属的 绩效评价中,工作态度一直都是决定评 价结果的重要因素。
33 2020/3/3
31 2020/3/3
(二) 态度的结构成分
态度有内在的心理结构,是由认知、情感 与行为倾向三种心理成分构成的。 认知成分 指个体对态度对象的认识、理解和
评价。
情感成分 指个体对态度对象的喜爱或厌恶的
情感体 验。
行为倾向成分, 也叫意向, 指个体对态度对
象的反应倾向,是行 为的准备状态。
32 2020/3/3
“社会人”假设与“人际关系理论” “自我实现人”假设(非理性“性善观”)
与“Y理论” “复杂人”假设与“超Y理论” “理念人”假设(“文化”“信念”观, 强
调运用“文化”的非理性软手段来统驭 理性硬管理手段)与“企业文化论”
20 2020/3/3
(三)本我、自我、超我
1. 弗洛伊德的动力理论
学? 3、组织行为学模型中的三种(或四种)分析
水平是什么? 它们有关系吗? 为什么? 4、你认为今天的管理者所面对的有关
组织行为学ob

理论原理:
个人努力
期望理论
维克多 弗鲁姆 Victor H Vroom;1964
Valence
E1
E2
E3
个人绩效
组织奖励
个人目标
个人需要
M:动机motivation;是直接推动或使人们采取某行动的内驱力 V:目标效价valence;指达成目标后对于满足个人需要其价值的大小;它
第二讲 当代动机理论
期望理论
维克多 弗鲁姆 Victor H Vroom;1964
期望理论前提假设: 1人们会主观地决定各种行动结果的价值;所以每个人对结果各有
偏好; 2任何对行为的激励;不但要考虑人们所要完成的目标;也要考虑目
标实现的可能性
理论原理: 动机motivation取决于行动结果的价值评价即效价valence和其对应的 期望值expectancy的乘积:
反映个人对某奖酬的重视与渴望程度; E:期望值expectancy;这是指根据以往经验;个人对某一行为导致特定
成果的可能性或概率的估计与判断
理论原理:
个人努力
期望理论
维克多 弗鲁姆 Victor Vroom
E1
E2
E3
个人绩效
组织奖励
个人目标
1. E1努力绩效关系:个人感到通过一定程度的努力可以达到某种绩 效水平的可能性
期望理论
启示: 1提高期望:与员工的个性乐观vs悲观 个人能力 客观
环境良好的办公环境 设备 文化制度 快捷方式 任务工 具等因素有关 2提高效价:与员工的需求 兴趣 愿望 知识 能力和生 活经验等因素有关
自我效能感理论
艾伯特 班杜拉 Bandura
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
需要、 需要、动机与行为的关系
挫折
个人需求 产生心理 紧张
未满足需求
动机
紧张消除
行为
结果
满足需求
5-4
马斯洛需求层次理论
自我实 现需求
自尊 社会需求 社会需求 安全需求 生理需求 生理需求
5-5
评价马斯洛需求层次理论
缺乏理论支持 实际需求并不完全符合马斯洛划分的类型 需求的变化比马斯洛描述得更为迅速 主导需求并不总是处于需求层次的最底层 价值观影响需求 结论:需求层次理论人与人之间存在差异(并不 是固有的或者普遍的)
• 个体对自己能胜任某项任务的自信 • 提高自我效能的途径
直接经验 他人榜样 言语说服 唤醒(Arousal)
5-14
公平理论( 公平理论(Equity Theory) )
组织成员的激励程度不仅受到自己经过努力 所得报酬绝对量的影响, 所得报酬绝对量的影响,而且受到报酬相对 量比较的影响。 量比较的影响。
5-6
X 理论和 Y 理论
• 麦格雷戈(Douglas McGregor)提出人性假 设 • X理论--“性恶”说 • Y理论--“性善”说
5-7
X理论(父母型) 理论(父母型) 理论
• • • • • • • • • 不愿在工作中尽全力,尽可能少工作 避免承担责任 对能否在工作中有所成就不感兴趣 不能约束自身的行为 对于组织需要漠不关心 尽可能避免做决策 不能为人所信赖或依靠 在工作中需要被人严密监督和控制 激励工作的动力来自于金钱和其它收益
• • • • • 培训员工 选择有合适能力的员工 提供清晰的角色要求 提供充分的资源 提供培训和反馈
5-21
增加绩效-结果期望 增加绩效 结果期望
• 准确衡量绩效 • 描述优差绩效的结果 • 解释奖励是如何与过去绩效相联系的
5-22
增加结果效价
• 确保奖励是有价值的 • 个性化奖励 • 减少负效价
5-8
Y理论(成人型) 理论(成人型) 理论
• • • • • • • 为完成预定目标而努力工作 在职责范围内勇于承担责任 强烈希望在工作中有所成就 ห้องสมุดไป่ตู้够约束自身行为 工作积极,喜欢决策而不盲从 工作动力来自其对工作本身的兴趣和任务挑战性 乐于接收变化并不断进步
5-9
图解人性假设
我对
X理论
你不对 父母
5-12
其它相关的激励理论
• 认知评价理论( Cognitive Evaluation Theory ) • 目标设定理论( Goal-Setting Theory ) • 目标管理( Management by Objectives - MBO)
5-13
自我效能理论 (Self-Efficacy Theory) )
5-17
减少不公平感
减少不公平感的行为 例子
减少投入 增加产出 增加其他人的投入 减少其他人的产出 改变我们的认知 改变比较对象 离开该领域
更少的组织公民行为 要求增加报酬 要求同事更加努力的工作 要求老板停止给予其他人更加优 厚的待遇 认为其他人的额外津贴并不是那 么有价值 与跟自己情景更加相似的人比 辞职
5-23
帕特- 帕特-劳勒激励模型
个人 目标 环境 限制 能 力 个人 努力 个人 绩效 公平 比较 组织 奖赏 内在 奖励 满意 感
绩效 管理
角色概念 的理解
绩效激 励效价
5-24
激励理论的文化局限
• 大部分激励理论来自于美国的研究 • 文化的差异可能会弱化上述理论的意义
5-25
组织行为学
龚 文 北京工商大学商学院
5-1
第五章 激励理论
1. 2. 3. 4. 概括激励的过程 马斯洛需要层次分析 其他相关激励理论 提高自我效能的方法
5-2
动机( 动机( Motivation)? )
• 动机指个体在实现目标的过 程中的努力程度、努力方向 和毅力。
强度(Intensity) – how hard Intensity a person tries 方向(Direction) – one that benefits the organization 毅力(Persistence) – how long the effort is maintained
Y理论
成人 你对
病态
儿童 我不对
5-10
激励-保健双因素理论 激励-
双因素理论-赫茨伯格(Herzberg) 双因素理论-赫茨伯格(Herzberg) 保健因素: 保健因素:不满意 没有不满意 激励因素: 激励因素:没有满意 满意
5-11
麦克莱兰需要理论
麦克莱兰(McClelland): 麦克莱兰(McClelland): 成就需求(nAch) 偏爱适度风险、 成就需求(nAch) :偏爱适度风险、喜欢个 人负责、关注绩效反馈; 人负责、关注绩效反馈; 权力需求(nPow) 偏爱控制他人、 权力需求(nPow) :偏爱控制他人、掌握关 键信息、偏爱竞争性任务、喜欢做领导; 键信息、偏爱竞争性任务、喜欢做领导; 亲和需求(nAff) 偏爱团队任务、 亲和需求(nAff) :偏爱团队任务、渴望友 谊和亲密关系、注重人际技能。 谊和亲密关系、注重人际技能。
5-18
公平理论的实践意义
公平是心理量 下属认为公平更重要 结果公平,程序也要公平
5-19
动机的期望理论
努力-绩效期望 努力 绩效期望 绩效-结果期望 绩效 结果期望 结果&效价 结果 效价
结果1 结果1
+或-
努力
绩效
结果 2
+或-
结果 3
+或-
激励力= 激励力=效价 × 期望率
5-20
增加努力-绩效期望 增加努力 绩效期望
5-15
公平理论的要素
• 投入产出比
投入——员工贡献的(比如:技能) 产出——员工得到的(比如:薪酬)
• 与其他人比
将自己的投入产出比与其他人的投入产出比相比较 不容易辨别
• 公平的评价
将自己的投入产出比与其他人比较之后,对公平形成的 评价
5-16
公平理论与工资制度
员工感到 报酬不足 计时制 计件制 产量↓ 质量↓ 产量↓,质量↓ 产量↑ 质量↓ 产量↑,质量↓ 员工感到 报酬过高 产量↑ 质量↑ 产量↑,质量↑ 产量↓ 质量↑ 产量↓,质量↑
