Cisco PPPoE Server和Cisco PPPoE Client
Cisco ADSL WAN接口卡说明书

Corporate Headquarters:Copyright © 2004 Cisco Systems, Inc. All rights reserved.Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706USA WIC-1ADSL, WIC-1ADSL-DG, and WIC-1ADSL-I-DG Documentation Roadmap Updated 9/21/2004This document provides links to resources for understanding, installing, and configuring ADSL WAN interface cards (WICs). Use this document in HTML format on .Products:Note This is a platform-independent document. To see which routers support these products, refer to thedocuments in the following section.Product Information and Supported Hardware and Software•ADSL WAN Interface Cards for the Cisco 1700, 2600, and 3700 Series Modular Access Routers ,data sheet •Cisco 1700/2600/3600 ADSL WIC Frequently Asked Questions , FAQs •ADSL WAN Interface Card (WIC) for Cisco 1700/2600/3600 Series Routers , Q & A •Cisco DSL Router Configuration and Troubleshooting Guide—ADSL WIC , how-to Service Categories•Understanding the CBR Service Category for ATM VCs , tech note •Understanding the Variable Bit Rate Real Time (VBR-rt) Service Category for ATM VCs , tech note •Understanding the VBR-nrt Service Category and Traffic Shaping for ATM VCs , tech note WIC-1ADSL1-port ADSL-over-POTS WAN interface card WIC-1ADSL-DG1-port ADSL-over-POTS with dying gasp WAN interface card WIC-1ADSL-I-DG 1-port ADSL-over-ISDN with dying gasp WAN interface cardWIC-1ADSL, WIC-1ADSL-DG, and WIC-1ADSL-I-DG Documentation Roadmap2OL-5592-01 Rev. A0Regulatory Compliance and Safety Information•Cisco Network Modules and Interface Cards Regulatory Compliance and Safety Information Hardware InstallationSee the following chapters of the Cisco Interface Cards Hardware Installation Guide:•Installing Cisco Interface Cards in Cisco Access Routers•Connecting DSL WAN Interface Cards to a NetworkSee also:•DSL Modem/Router Interface Pinouts and Status LED Descriptions, tech noteInterface Numbering•Overview in the hardware installation documentation for your routerSoftware Configuration•Configuring an ADSL WAN Interface Card on Cisco 1700 Series Routers, configuration note•1-Port ADSL WAN Interface Card, Cisco IOS Releases 12.2(13)ZH, 12.2(15)ZJ, and 12.3(4)T feature module•1-Port ADSL WAN Interface Card for Cisco2600Series and Cisco3600Series Routers,Cisco IOS Release 12.2(4)T feature module•1-Port ADSL WAN Interface Card, Cisco IOS Releases 12.1(3)XJ and 12.2(2)T feature module•1-Port ADSL WAN Interface Card, Cisco IOS Release 12.1(5)YB feature module•Cisco DSL Router Configuration and Troubleshooting Guide, how-toVoice and QoS Features•Enhanced Voice and QoS for ADSL and G.SHDSL, Cisco IOS Release 12.3(2)T feature module•Enhanced Voice and QoS for ADSL and G.SHDSL on Cisco 1700 Series, Cisco 2600 Series,Cisco3600 Series, and Cisco 3700 Series Routers, Cisco IOS Releases 12.2(8)YN and 12.2(13)Tfeature module•Voice and Quality of Service Features for ADSL and G.SHDSL on Cisco 1700, Cisco 2600, and Cisco 3600 Series Routers, Cisco IOS Releases 12.2(4)XL and 12.2(13)T feature module Troubleshooting•Troubleshooting Layer 1 on a Cisco 1700/2600/3600 ADSL WIC, tech note•Cisco DSL Router Configuration and Troubleshooting Guide, how-toWIC-1ADSL, WIC-1ADSL-DG, and WIC-1ADSL-I-DG Documentation RoadmapConfiguration Examples•Configuring IPSec Over ADSL on a Cisco 2600/3600 With ADSL-WIC and Hardware Encryption Modules, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC With a Single IP Address, DHCP, PPPoA, and PPP-PAP, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC With IP Unnumbered E0, DHCP, PPPoA, and PPP-PAP, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC With IP Unnumbered E0, PPPoA, PPP-PAP, and Manually Configured Local LAN Devices, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC (Unnumbered Interface) With RFC1483 Routing Using AAL5SNAP Protocol IP, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC With RFC1483 Routing Using AAL5SNAPProtocol IP, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC Using PPPoA With CHAP and PAP, sampleconfiguration•Configuring a Cisco 1700/2600/3600 ADSL WIC With IRB and NAT Using RFC1483 Bridging, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC With NAT, a DHCP Server, and Easy IP Using PPPoA (aal5mux ppp), sample configuration•Configuring a Cisco1700/2600/3600ADSL WIC as a PPPoE Client With NAT,sample configuration•Configuring Network Address Translation and Static Port Address Translation to Support anInternal Web Server, sample configuration•Configuring a Cisco1700/2600/3600ADSL WIC With AAL5MUX IP Routing,Multiple PVCs,and Terminating on a Cisco 6400 UAC-NRP, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC to Support PPPoE Clients, Terminating on aCisco6400 UAC, sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC and a Cisco 6400 Configured With IRB Using RFC1483 Bridging (aal5snap), sample configuration•Configuring a Cisco 1700/2600/3600 ADSL WIC and a Cisco 6400 in RBE Mode Using RFC1483 Bridging, sample configurationOL-5592-01 Rev. A03WIC-1ADSL, WIC-1ADSL-DG, and WIC-1ADSL-I-DG Documentation Roadmap4OL-5592-01 Rev. A0Copyright © 2004 Cisco Systems, Inc. All rights reserved.CCSP, the Cisco Square Bridge logo, Cisco Unity, Follow Me Browsing, FormShare, and StackWise are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live, Play, and Learn, and iQuick Study are service marks of Cisco Systems, Inc.; and Aironet, ASIST, BPX, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Empowering the Internet Generation, Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step, GigaDrive, GigaStack, HomeLink, Internet Quotient, IOS, IP/TV, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, LightStream, Linksys, MeetingPlace, MGX, theNetworkers logo, Networking Academy, Network Registrar, Packet, PIX, Post-Routing, Pre-Routing, ProConnect, RateMUX, Registrar, ScriptShare, SlideCast, SMARTnet, StrataView Plus, SwitchProbe, TeleRouter, The Fastest Way to Increase Your Internet Quotient, TransPath, and VCO areregistered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (0406R)。
PPPOE拨号系列之一:Cisco-路由器-防火墙-PPPOE拨号配置

PPPOE拨号系列之一:Cisco-路由器-防火墙-PPPOE拨号配置一、拓扑一二、Cisco 路由器 PPPOE client 拨号配置1、接口下调用 PPPOE-clientpppoe_client(config)#interface e0/0pppoe_client(config-if)#pppoe-client dial-pool-number 1pppoe_client(config-if)#no shutdown2、PPPOE-client 接口的配置pppoe_client(config)#interface dialer 1pppoe_client(config-if)#encapsulation ppp 【在思科上面默认为 HDLC】pppoe_client(config-if)#ip address negotiated 【地址通过协商获取】如果运营商那边认证方式为 PAP 则配置如下pppoe_client(config-if)#ppp authentication pap calin 【开启 PAP 认证,注意这里是单向的】pppoe_client(config-if)#ppp pap sent-username username password xxx如果运营商那边认证方式为 CHAP 则配置如下PPPOE_client(config-if)#ppp authentication chap callinPPPOE_client(config-if)#ppp chap hostname usernamePPPOE_client(config-if)#ppp chap password xxx如果不确定运营商那边是什么方式的话,还有一种办法PPPOE_client(config-if)#ppp authentication chap pap callin然后输入 pap 跟 chap 两种方式,这样无论运营商是哪种都可以成功。
思科、华为、神州数码PPPOE拨号实验

方法一:PPPoE配置命令dcr路由器实现了pppoe client功能,pppoe配置命令:1 pppoe-client dialer2 show pppoe3 debug pppoe3.2.2.1 pppoe-client dialer命令:pppoe-client dialer [dialer-number]no pppoe-client dialer功能:启动以太网接口的pppoe client功能,同时指定对应的拨号口;本命令的no操作为关闭pppoe client功能。
参数:[dialer-number]为pppoe client建立session时使用的拨号口,取值范围为0~255。
缺省情况:以太网不打开pppoe client功能。
命令模式:以太网接口配置模式使用指南:本命令在打开以太网接口的pppoe client功能的同时,还指定了对应的拨号口,其中拨号口的号码为命令interface dialer [number]中设置的号码之一。
举例:配置以太网接口0为pppoe client,并且对应拨号口1。
router(config)#interface dialer 1router(config-dialer1)#en ppprouter(config-dialer1)#exitrouter(config)#interface ethernet 0router(config-ethernet0)#pppoe-client dialer 1相关命令:interface dialer3.2.2.2 show pppoe命令:show pppoe功能:显示pppoe两端的mac地址、session id、连接建立时间、持续时间等。
命令模式:特权用户配置模式举例:router#show pppoeethernet0 pppoe information:sid locmac remmac intf status oinft0x0061 0003.0f00.8012 0050.baf2.8b46 ethernet0 4 dialer1create session time : 0:03:31 duration : 00:56:173.2.2.3 debug pppoe命令:debug pppoe { event| packet }no debug pppoe { event| packet }功能:打开pppoe的调试开关。
cisco路由器ADSL拨号配置上网

PPP-C#conf tPPP-C(config)#vpdn enable //启用路由器的虚拟专用拨号网络---vpnd 由于ADSL的PPPoE应用是通过虚拟拨号来实现的所以在路由器中需要使用VPDN的功能PPP-C(config)#int e1/0 // 路由器内网接口PPP-C(config-if)#no shutPPP-C(config-if)#ip add 192.168.0.1 255.255.255.0PPP-C(config-if)#ip nat insidePPP-C(config)#int f0/0 //与ADSL model连接的端口PPP-C(config-if)#no ip addPPP-C(config-if)#no shutPPP-C(config-if)#pppoe enablePPP-C(config-if)#pppoe-client dial-pool-number 100 // 将以太接口的pppoe拨号客户端加入拨号池100虚拟拨号接口PPP-C(config)#int dialer 0 //配置虚拟拨号接口0 ,类似于xp中建立的拨号连接PPP-C(config-if)#ip address negotiated //协商获得ip地址PPP-C(config-if)#ip mtu 1492 //适用于ADSL线路,原始大小是1500 ,1492=1500-pppoe header PPP-C(config-if)#no shutPPP-C(config-if)#encapsulation ppp //协议类型为pppPPP-C(config-if)#ppp authentication chap pap callin //验证方式采用chap和pap,方式取决于服务器方,二者前后位置可以调换PPP-C(config-if)#ppp chap hostname cisco //设置chap 账号PPP-C(config-if)#ppp chap password cisco //设置chap 密码PPP-C(config-if)#ppp pap sent-username cisco password cisco //只是是采用pap验证,上面关于chap的不需要设置PPP-C(config-if)#dialer pool 100 // 该接口使用100号拨号池进行拨号,应该与上面理接口f0/0 pppoe-client dial-pool-nuber 号码一致PPP-C(config-if)#ppp ipcp dns request //客户端dns采用服务器上预先设置的,也可以手动设置固定ip地址:202.98.96.68PPP-C(config-if)#ip nat outside //设置内部接口和dialer 0 的PATPPP-C(config)#access-list 1 permit 192.168.0.0 0.0.0.255PPP-C(config)#ip nat inside source list 1 interface dialer 0 overloadPPP-C(config)#service dhcpPPP-C(config)#ip dhcp pool nat-ip //配置作用域PPP-C(dhcp-config)#network 192.168.0.0 255.255.255.0 //地址范围PPP-C(dhcp-config)#default-router 192.168.0.1 // 默认网关PPP-C(dhcp-config)#dns-server 10.0.0.2 //DNS服务器PPP-C(dhcp-config)#lease 1 //租期1天PPP-C(config)#ip dhcp excluded-address 192.168.0.2 192.168.0.15 //指定保留的ip地址PPP-C(config)#ip route 0.0.0.0 0.0.0.0 dialer 0 //配置内部到远端的缺省路由远程接入专题的最后我们介绍时下在个人用户和小企业中非常流行的ADSL拨号方式的配置方法。
PPPoE的几种配置

4.
*** Client ***
interface Ethernet0/1
pppoe enable
pppoe-client dial-pool-number 1
!
interface Dialer1
ip address dhcp
encapsulation ppp
dialer pool 1
accept-dialin
protocol pppoe
virtual-template 1
!
interface Ethernet0/0
pppoe enable
!
interface Virtual-Template1
ip address 142.1.35.3 255.255.255.0
ip address dhcp
encapsulation ppp
dialer pool 1
dialer idle-timeout 0
dialer persistent
SERVER
vpdn enable
ip dhcp exclude-address YY.YY.12.1
ip dhcp pool PPP-Pool
ip mtu 1492
ip address 28.28.34.3 255.255.255.0 \\1500=1492pppoe+8ether
peer default ip address pool cisco \\直接配置IP
encapsulation ppp
username Rack28R4 password cisco
!
interface Dialer1
双线路Cisco路由器配置pppoe拨号上网

公司原有的20M城域网光纤不能满足现在的需求了,公司决定购买中国电信的ADSL 100M光纤线路,所以路由器变成了,双线连接互联,有某些业务需要使用20M线路固定公网IP,公司内部员工默认使用100M光纤上网。
此配置适合两条ADSL线路上网,只需要把固定IP的换成ADSL配置
ip nat inside
exit
#固定IP地址
interface GigabitEthernet0/1
ip address 113.106.x.x 255.255.255.240 secondary
ip address 113.106.x.y 255.255.255.240 secondary
match interface g0/1
exit
#NAT上网(PAT配置)
ip nat inside source route-map LANTo100Nat int dia 1 overload
ip nat inside source route-map LANTo20Nat int g0/1 overload
route-map lantointernetacl permit 10
match ip address lanto100adsl-acl
set ip next-hop verify-availability #因为不是固定IP,所以用这个参数
exit
route-map lantointernetacl permit 20
match ip add adsl100-nat-acl
match interface dia 1
exit
no route-map LANTo20Nat permit 20
PPPOE

实验环境:IOS版本:c7200-jk9s-mz.123-8.T11.bin和c7200-jk9o3s-mz.124-10a.binCCO下文档的位置:SUPPORT→PRODUCT SUPPORT→ CISCO IOS SOFTWARE12.4 MAINLINE→CONFIGURE→CONFIGURATION GUILDxDSL→Cisco IOS Broadband Access Aggregation and DSL Configuration Guide, Release 12.4拓扑IOS 12.4之前版本的配置[编辑]A.B.C.D 是静态指定地址。
Dhcp 是通过dhcp协商获得。
Negotiated 是通过PPP的ipcp获得。
Pool 是通过本地的dhcp地址池获得。
Slarp 通过串行链路ARP分配地址,即通过SLARP查询对端地址+1作为本地址。
IOS 12.4之前的配置:1.在R1上show ip int bri看到地址是manual的配置dialer pool配置错了,那么这个接口不会发起PPPOE会话。
显示结果如果是NVRAM则是从设备的NVRAM中读取的配置,NVRAM的内容在路由器断电后仍然保持。
dialer-list 1 protocol ip permit:该命令配上,则做成按需拨号方式,不配置该命令,则为持续型连接。
此外还有一种配置方法:参考网页/2008/07/06/the-mystery-of-ppp-ipcp-mask-request-command/给出关键配置大致解释一下:PPPOE CLIENT端设置获得的地址是本地的DHCP地址池,但在DHCP里面配置了DHCP 的参数来自于IPCP。
PPPOE SERVER通过IPCP分配IP 地址和网络掩码并传给PPPOE CLIENT。
2.在R1上show ip int bri看到地址是ipcp的配置这种情况下R2无论如何配置,PPPOE CLIENT获得的地址永远是32位的。
CISCO 路由器 作 PPPOE SERVER 服务器的配置

CISCO 路由器作 PPPOE SERVER 服务器的配置时间:2010-08-03 10:00来源:未知作者:admin 点击:215次Cisco PPPOE server配置笔记 1.首先在自己的电脑上创建一个宽带连接,用户名:test 密码:cisco 2.然后进入路由器全局配置模式: ! #定义一个PPPOE RADIUS SERVER组 Router(config)# radius-server host 10.72.253.16auth-port 1645 acct-port 1646 key 88----99 # 配置Radius服务器的IP地址和**端口号 Router(config)# rCisco PPPOE server配置笔记1.首先在自己的电脑上创建一个宽带连接,用户名:test 密码:cisco2.然后进入路由器全局配置模式:!#定义一个PPPOE RADIUS SERVER组Router(config)# radius-server host 10.72.253.16 auth-port 1645acct-port 1646 key 88----99 # 配置Radius服务器的IP地址和**端口号Router(config)# radius-server retransmit 3Router(config)# aaa group server radius pppoeRouter(config-sg-radius)# server 10.72.253.16 auth-port 1645 acct-port 1646#创建一个VPDN session group 并链接到一个虚拟模版Router(config)#vpdn enable #开启虚拟拨号网VPDNRouter (config)#no vpdn logging #关闭连接中提示!Router (config)#vpdn-group pppoe #配置一个VPND 组,组名为pppoeRouter (config-vpdn)#accept-dialin #允许拨入(将路由器当PPPOE server用accept-dialin允许客户端拨入命令;若是将路由器当PPPOE client用request-dialin向服务器发出请求接入信息。
Ensp做PPPoE实验
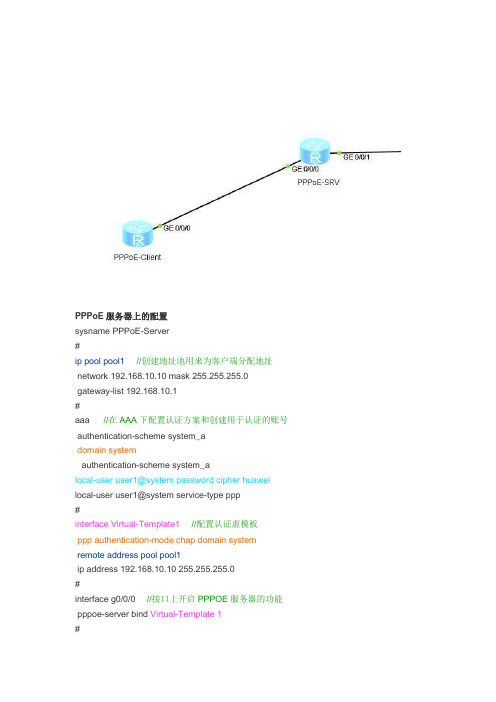
PPPoE服务器上的配置sysname PPPoE-Server#ip pool pool1//创建地址池用来为客户端分配地址network 192.168.10.10 mask 255.255.255.0gateway-list 192.168.10.1#aaa //在AAA下配置认证方案和创建用于认证的账号 authentication-scheme system_adomain systemauthentication-scheme system_alocal-user user1@system password cipher huawei local-user user1@system service-type ppp#interface Virtual-Template1//配置认证虚模板ppp authentication-mode chap domain system remote address pool pool1ip address 192.168.10.10 255.255.255.0#interface g0/0/0 //接口上开启PPPOE服务器的功能 pppoe-server bind Virtual-Template 1#interface LoopBack100 //模拟公网的地址ip address 100.100.100.100 255.255.255.0PPPoE客户端的配置#sysname PPPoE-Client#dialer-rule //配置拨号规则,IP流量触发PPP拨号dialer-rule 1 ip permit#interface Dialer0 //配置拨号接口0link-protocol ppp //协议是PPPppp chap user user1@system //配置被认证方的chap账号ppp chap password simple huawei //配置chap密码mtu 1492 //修改MTU为1500-8=1492 ,1500是以太网最大传输单元,8是PPP头部长度ip address ppp-negotiate //配置IP地址采用PPP协商方式获取,即通过服务器的地址池分配dialer user user1@system //配置拨号用户,这个是非按需拨号时要配置dialer bundle 1//配置拨号捆绑的编号1,1要和下面接口的的配置对应#interface g0/0/0pppoe-client dial-bundle-number 1#ip route-static 0.0.0.0 0.0.0.0 Dialer0 //配置用于上网的默认路由,注意出口是拨号接口Dialer0,不用也没法指定下一跳IPreturn如果路由器下面还有PC要上网,还要配置NATacl 3000rule permit ipinter dialer 0nat outbound 3000在客户端测试PPPoE的配置[PPPoE-Client]dis ip inter briInterface IP Address/Mask Physical ProtocolDialer0 192.168.10.254/32 up up(s)GigabitEthernet0/0/0 unassigned up down GigabitEthernet0/0/1 unassigned down downNULL0 unassigned up up(s)[PPPoE-Client]ping 100.100.100.100PING 100.100.100.100: 56 data bytes, press CTRL_C to breakReply from 100.100.100.100: bytes=56 Sequence=1 ttl=255 time=100 ms Reply from 100.100.100.100: bytes=56 Sequence=2 ttl=255 time=10 msReply from 100.100.100.100: bytes=56 Sequence=3 ttl=255 time=10 msReply from 100.100.100.100: bytes=56 Sequence=4 ttl=255 time=10 msReply from 100.100.100.100: bytes=56 Sequence=5 ttl=255 time=10 ms--- 100.100.100.100 ping statistics ---5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 10/28/100 ms[PPPoE-Client]dis pppoe-client session summaryPPPoE Client Session:ID Bundle Dialer Intf Client-MAC Server-MAC State1 1 0 GE0/0/0 00e0fc03c38b 00e0fc033c76 UP在服务器上测试PPPoE的配置<PPPoE-Server>dis ip routing-tableRoute Flags: R - relay, D - download to fib------------------------------------------------------------------------------Routing Tables: PublicDestinations : 11 Routes : 11Destination/Mask Proto Pre Cost Flags NextHop Interface100.100.100.0/24 Direct 0 0 D 100.100.100.100 LoopBack100 100.100.100.100/32 Direct 0 0 D 127.0.0.1 LoopBack100 100.100.100.255/32 Direct 0 0 D 127.0.0.1 LoopBack100 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0 192.168.10.0/24 Direct 0 0 D 192.168.10.10 Virtual-Template1 192.168.10.10/32 Direct 0 0 D 127.0.0.1 Virtual-Template1 192.168.10.254/32 Direct 0 0 D 192.168.10.254 Virtual-Template1 192.168.10.255/32 Direct 0 0 D 127.0.0.1 Virtual-Template1 255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0<PPPoE-Server>dis pppoe-server session allSID Intf State OIntf RemMAC LocMAC1 Virtual-Template1:0 UP GE0/0/0 00e0.fc03.c38b 00e0.fc03.3c76<PPPoE-Server>dis access-user------------------------------------------------------------------------------UserID Username IP address MAC------------------------------------------------------------------------------145 user1@system - 00e0-fc03-c38b------------------------------------------------------------------------------Total 1,1 printed<PPPoE-Server>。
实验14 pppoe服务器和客户机的互联
1server(config-vpdn)#accept-dialin 允许拨入server(config-vpdn-acc-in)#protocol ? 发现可支持很多的二层协议 any Use any protocol l2f Use L2F l2tp Use L2TP pppoe Use PPPoE pptp Use PPTPserver(config-vpdn-acc-in)#protocol pppoe 我们打算启动pppoe 协议 % PPPoE config from vpdn-group is converted to pppoe-profile based config. % Continue PPPoE configuration under 'bba-group pppoe global'注意这里提示,有关pppoe 协议的配置已经转移到了bba-group pppoe global 命令下了。
你需要在此命令下配置相关的选项。
per-vlan Per-VLAN session configuration 每个vlan可连接的pppoe链路的数量server(config-bba-group)#sessions per-mac limit ?<1-800> Per-MAC session limitserver(config-bba-group)#sessions per-mac limit 5 如配置成每个mac地址可发起5个数据链路层会话。
server(config-bba-group)#exitserver(config)#int e0/0server(config-if)#no sh*Mar 1 00:09:28.987: %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to up*Mar 1 00:09:29.987: %LINEPROTO-5-UPDOWN: Line protocol on Interface Ethernet0/0, changed state to upeserver(config-if)#pppoe en 在以太网端口中启动pppoe协议。
cisco+pppoe拨号配置教程

CISCO上配置 PPPOE拨号r1(config)#vpdn enable 开启虚拟拨号VPDNr1(config)#vpdn-group pppoe 定义组名(pppoe)r1(config-vpdn)#request-dialin 这里是请求拨入r1(config-vpdn-req-in)#protocol pppoe 设置拨号协议为PPPOEr1(config)#in ethernet 0 进入E0端口r1(config-if)#half-duplex 半双工r1(config-if)#pppoe enable 使用PPPOEr1(config-if)#pppoe-client dial-pool-number 1 把该物理端口加入到拨号池1中r1(config-if)#bandwidth 640 宽带640r1(config-if)#no cdp enable 关闭CDP协议r1(config-if)#no shr1(config)#interface dialer 1 建立一个虚拟拨号端口r1(config-if)#bandwidth 640 宽带640r1(config-if)#ip address negotiated 由于局端提供动态地址r1(config-if)#ip mtu 1492 修改MTU值适用于ADSL网络,默认为1500,我们要修改为1452 r1(config-if)#ip tcp adjust-mss 1452 IP 的TCP调整r1(config-if)#ip nat outside 启用NAT转换,设置外网端口为外部网r1(config-if)#dialer pool 1 使用拨号池,因为ETH0加入到拨号池,实际使用ETH0 r1(config-if)#dialer idle-timeout 0 拨号闲置-超时0(保持连接)r1(config-if)#dialer hold-queue 100 断线了可以保持100个封包r1(config-if)#dialer persistent 拨号持久(上不了网就连线)r1(config-if)#dialer-group 1r1(config-if)#encapsulation PPp 使用PPP的帧格式r1(config-if)#PPp authentication pap chap callin 设置拨号的验证方式为PAP 和CHAPr1(config-if)#ppp pap sent-username sz123@163gd password 123 用户帐号和密码r1(config-if)#no cdp enable 不走CDPr1(config-if)#no ip mroute-cache 是关闭快速交换。
PPPoE完整版

PPPoE完整版PPPOE:纯二层技术~客户端和服务器端中间肯定是没有路由设备的。
拨号分为两个阶段:1、discovery:客户端查找有哪些可拨入的设备2、PPP Session phase:客户端拨入这个设备注意:当Client和Server之间有透明防火墙时~防火墙需要放行0X8863,第一阶段,和0X8864,第二阶段,.测试过程:先在PPPOE.GW上使用本地认证,成功拨号后,再使用3A认证,授权,审计。
PPPOE.GW基本配置部份:先使用本地认证version 12.4!hostname PPPOE.GW!no aaa new-model !vpdn enable 虚拟私有拔号网络开启!username cisco password 0 cisco !bba-group pppoe globalvirtual-template 1! 由于我用的是12.4的IOS,因此,原来的VPDN相关的配置已经不再使用,转而用bba-group pppoe global更为合理。
同时要说明下,VPDN不是这个概念,而是运营商提供的一种基于gre和l2tp的VPN解决方案,只不过cisco之前在指令运用上有所借贷。
因此,不要过多确定网上的那些vpdn就是拨号设置的必备参数,了解其真实成因才是要紧的interface FastEthernet1/0no ip addresspppoe enable!interface FastEthernet2/0ip address 172.17.11.1 255.255.255.0!interface FastEthernet3/0ip address 202.100.1.1 255.255.255.0!interface Virtual-Template1 虚拟接口模板ip unnumbered FastEthernet2/0 借用F2/0的接口地址若这里没有F2/0,那么可以设置loopback是为了将loopback的ip绑在VT上。
cisco设置方法步骤

cisco设置方法步骤思科(Cisco)路由器是一个集成多业务路由器,福利综合服务网络路由器,以及获得回报的网络路由器。
cisco路由器怎么设置??有网友提到自己不会设置思科的设备,该怎么办?店铺在网上找了一些教程及命令,需要的朋友可以参考下。
以下是cisco路由器设置具体命令一、 host到router1、实验网络拓扑:pc( client 4.01)---switch---router1720 ( access server)pc配置:ip:10.130.23.242/28gw:10.130.23.2461720接口ip:f0:10.130.23.246/28lo0:172.16.1.1/241720的ios为c1700-k93sy7-mz.122-8.T5.bin2、步骤:1、配置isakmp policy:crypto isakmp policy 1encr 3desauthen pre-sharegroup 22、配置 client地址池cry isa client conf address-pool local pool192ip local pool pool192 192.168.1.1 192.168.1.2543、配置 client有关参数cry isa client conf group vclient-group####vclient-group就是在client的连接配置中需要输入的group authentication name。
key vclient-key####vclient-key就是在client的连接配置中需要输入的group authentication password。
pool pool192 ####client的ip地址从这里选取####以上两个参数必须配置,其他参数还包括domain、dns、wins等,根据情况进行配置。
4、配置ipsec transform-setcry ipsec trans vclient-tfs esp-3des esp-sha-hmac5、配置map模板cry dynamic-map template-map 1set transform-set vclient-tfs ####和第四步对应6、配置mapcry map map 1 ipsec-isakmp dynamic template-map#### 使用第?*脚渲玫?map 模板cry map map isakmp author list vclient-group ####使用第三步配置的参数authorizationcry map map client conf address respond ####响应client分配地址的请求7、配置静态路由ip route 192.168.1.0 255.255.255.0 fastethernet03、说明几点:(1)因为1720只有一个fastethernet口,所以用router1720上的lo0地址来模拟router内部网络。
思科PPPOE方式上网怎么配置

思科PPPOE方式上网怎么配置cisco思科公司制造的路由器、交换机和其他设备承载了全球80%的互联网通信,成为了网络应用的成功实践者之一,那么你知道思科PPPOE方式上网怎么配置吗?下面是店铺整理的一些关于思科PPPOE 方式上网怎么配置的相关资料,供你参考。
思科PPPOE方式上网配置的方法现有客户需要使用思科的2600路由器上网,用户为10M光纤,申请了16个固定IP,ip为61.161.xxx.2-61.161.xxx.14,默认网关是61.161.xxx.1.内网ip段192.168.1.0,客户要实现192.168.1.50-192.168.1.60之间的ip可以上网,其余的不可以。
路由器e0/0接口为外网接口,e0/1为内网接口interface e0/0ip address 61.161.xxx.2 255.255.255.240 //这里可以使用61.161.xxx.2-14个地址中的任意一个,这里就用2ip nat outsidefull-duplexinterface e0/1ip address 192.168.1.1 255.255.255.0ip nat insidefull-duplexaccess-list 1 permit host 192.168.1.50access-list 1 permit host 192.168.1.51access-list 1 permit host 192.168.1.52access-list 1 permit host 192.168.1.53access-list 1 permit host 192.168.1.54access-list 1 permit host 192.168.1.55access-list 1 permit host 192.168.1.56access-list 1 permit host 192.168.1.57access-list 1 permit host 192.168.1.58access-list 1 permit host 192.168.1.59access-list 1 permit host 192.168.1.60ip nat pool intoout 61.161.xxx.2 61.161.xxx.2 netmask 255.255.255.240 //这里复用61.161.xxx.2的地址,也可以这样写:ip nat pool intoout 61.161.xxx.2 61.161.xxx.14 netmask 255.255.255.252 这样写之后,从地址池里选择任意可用的外网ip 转换。
PPPOE 相关知识点学习

PPP协议中的IPCP报文
IPCP request packet:该报文用于发起协商网 络参数。 IPCP ACK packet:该报文用于确认所协商的参 数。 IPCP NAK:用于回应IPCP request packet 的 报文
PPPOE 连接建立的过程
TDM
Source 00 11 25 81 29 26
Notice: Code:该域用0x19来标识该报文为PADR Tag:该域中的主机标识会发生改变
PADS报文格式
目的MAC 地址 00 18 8b 11 e3 17 代码(1byte) 6 5 源MAC地址 00 ad 01 cd 02 bd 会话ID(2byte) 0 0 d 9 Ethernet类型域 88 63 长度域 00 24 版本号(4bit) 0x01 Tag 类型(4bit) 0x01
LCP协议工作原理
LCP协议主要是负责数据链路的建立和协 商。 当主机协商PPP连接时,协商双方交换 LCP分组。 LCP分组能够使链路两端能够动态的协商 参数,其中包括了认证 压缩和MLP。在 LCP分组中的协议域是用来定义不同的三 层协议。
NCP协议工作原理
NCP(network control protocol)协议是在 二层连接建立后用来协商网络层的网络 参数。 每种第3层协议都有自己的NCP。例如 IP的IPCP,IPX的IPXCP NCP还有在一条链路上建立和中断多种 第三层协议会话的功能
在该阶段PPPOE以unicast的方式发送给它识别到的client,并确认client所请求的服务。
PADR(PPPOE Active Discovery Request)
在该阶段 PPPOE client通过该报文来选择接入的PPPOE server
怎么设置cisco路由器串口IP

怎么设置cisco路由器串口IP为了帮助网友解决“关于cisco路由器串口IP的设置”相关的问题,小编特意去找了一些资料。
下面跟大家分享下。
解决方案1:0 0.1 255.1.1.1.0.1配置NAT.1.255,)protocol pppoe(vpdn子组使用pppoe建立会话隧道)配置路由器连接adsl modem的接口interface Ethernet1no ip addresspppoe enable允许以太接口运行pppoepppoe-client dial-pool-number 1将以太接口的pppoe拨号客户端加入拨号池1配置逻辑拨号接口假设E0接内网.1ip dhcp pool ABCimport all(导入dns和wins server)network 10;0接ADSL上外网配置vpdnvpdn enable(启用虚拟专用拨号网络---d)vpdn-group office(建立一个vpdn组.1.0default-router 10.1.255,)request-dialin(初始化d tunnel.255.0 255.1.0.1.0ip nat inside为该接口启用NAT配置路由器为内部网络主机提供dhcp服务ip dhcp excluded-address 10.0.0:interface Dialer1ip address negotiated从adsl服务商动态协商得到ip地址ip nat outside为该接口启用NATencapsulation ppp为该接口封装ppp协议dialer pool 1该接口使用1号拨号池进行拨号dialer-group 1该命令对于pppoe是意义不大的ppp authentication pap callin启用ppp pap验证ppp pap sent-username xxxxxxx password 0 yyyyyyy使用已经申请的用户名和口令配置内部网络接口interface Ethernet0(内部网络接口)ip address 10,建立请求拨入的vpdn子组,S0/.255.0 0.255ip nat inside source list 1 interface Dialer1 overload配置缺省路由ip route 0.1:access-list 1 permit 10.1.0.0解决方案2:是的int s0/0ipaddress mask.......(ISP供应商IP)no shutdownclock rate 72000之后路由表怎么写都可以了。
ciscoclient设置

cisco client设置CISCO 是CISCO PIX防火墙提供的功能,用户通过CISCO CLIENT软件连接到CISCO PIX防火墙,利用IPSEC协议建立加密的安全隧道。
那么在cisco 中如何配置client客户端?店铺整理了相关资料,供大家参考。
cisco client设置教程如下:1、安装CISCO IPSEC 客户端解压下载的安装包后,点击-client-2.2.2-release.exe启动安装程序,只需在第二步时把默认的professional改为standard,其它部分只需一直按next即可.包里一共有三个文件,sites目录包含卓越配置文件,bat结尾的为脚本文件,用来启动ipsec客户端的,可以把它拷到桌面便于启用。
2、输入用户名和密码右击bat结尾的脚本文件,选择编辑。
可用记事本或其它文本编辑器打开该文件。
3、填入信息输入你的用户名和密码,切记不要编辑未提及的其它参数。
4、开始连接保存修改好的配置文件后,直接双击卓越-ipsec.bat即可开始通过CISCO IPSEC连接。
5、更换服务器地址如果服务器无法连接或因为别的原因需要更换服务器。
【实例验证】试验说明;R1为SKY公司的网关,其F1/0接口连接互联网,用户现在出差在外,通过拨号连接到互联网上,现在希望实现用户通过internet拨号进入SKY公司的R1路由器上,拨号使用easy ,并能连接到SKY公司的内网,192.168.0.0/24 网段需求拓扑:实验要求;1,通过cisco client 拨上R1,需要ping通R1的网关的地址,2,拨入成功之后,可以ping通 192.168.0.2,能访问内网服务器上的共享资源实验过程:第一步 R1预配置R1(config)#int f0/0R1(config-if)#ip add 192.168.0.1 255.255.255.0R1(config-if)#no shR1(config-if)#int e1/0R1(config-if)#ip add 192.168.1.200 255.255.255.0R1(config-if)#no shR1(config-if)#endR1#ping 192.168.1.101// 在本实验中PC机的IP地址是192.168.1.101Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.101, timeout is 2 seconds:.Success rate is 80 percent (4/5), round-trip min/avg/max = 8/50/168 msR1#第二步配置认证策略R1#conf tR1(config)#aaa new-model// 激活AAAR1(config)#aaa authorization network -client-user local// 配置对远程接入IPSec连接的授权,组名为-client-user第三步定义用户的组策略R1(config)#ip local pool DHCP 192.168.0.100 192.168.0.150 // 配置一个内部地址池,用于分配IP地址到远程接入的客户端,在本实验中地址池的起始地址为192.168.0.100,终止的IP地址为192.168.0.150,在后面的组策略中会引用改地址池R1(config)#crypto isakmp client configuration group -client-user// 配置远程接入组,组名为-client-user,此组名与aaa authorization network命令中的名称一致R1(config-isakmp-group)#key // 配置IKE阶段1使用预共享密钥,密钥为R1(config-isakmp-group)#pool DHCP// 配置在客户端连接的Easy client所分配的IP地址池R1(config-isakmp-group)#dns 221.11.1.67// 给客户端分配DNS地址R1(config-isakmp-group)#domain // 配置分配给客户端的DNS域名R1(config-isakmp-group)#exitR1(config)#第四步配置IKE阶段1策略R1(config)#crypto isakmp policy 10R1(config-isakmp)#authentication pre-shareR1(config-isakmp)#encryption 3desR1(config-isakmp)#group 2R1(config-isakmp)#hash shaR1(config-isakmp)#exitR1(config)#endR1#show crypto isakmp policyGlobal IKE policyProtection suite of priority 10encryption algorithm: Three key triple DEShash algorithm: Secure Hash Standardauthentication method: Pre-Shared KeyDiffie-Hellman group: #2 (1024 bit)lifetime: 86400 seconds, no volume limitDefault protection suiteencryption algorithm: DES - Data Encryption Standard (56 bit keys).hash algorithm: Secure Hash Standardauthentication method: Rivest-Shamir-Adleman SignatureDiffie-Hellman group: #1 (768 bit)lifetime: 86400 seconds, no volume limit第五步配置动态加密映射R1#conf tR1(config)#crypto ipsec transform-set R1 esp-sha-hmac esp-3des// 配置名为R1的转换集R1(cfg-crypto-trans)#exitR1(config)#crypto dynamic-map dy 10// 配置名为dy的动态加密映射R1(config-crypto-map)#set transform-set R1R1(config-crypto-map)#reverse-route//Reverse-route 生成的两条路由,不配置这条命令,是无法ping 内网的设备192.168.0.2R1(config-crypto-map)#exit第六步配置静态加密映射R1(config)#crypto map dy isakmp authorization list -client-user// 指定应该为远程接入连接执行的授权,这里的-client-user名称必须与aaa authorization network命令中的相同R1(config)#crypto map dy client configuration address respond// 配置允许路由器将信息分配给远程接入客户端,respond参数使路由器等待客户端提示发送这些信息,然后路由器使用策略信息来回应R1(config)#crypto map dy 1 ipsec-isakmp dynamic dy// 配置在静态映射条目中关联动态加密映射第七步在接口上激活静态加密映射R1(config)#int e1/0R1(config-if)#crypto map dyR1(config-if)# ^Z第八步在PC机上打开Cisco Client进行配置,点击New创建一个新的连接第九步在连接中进行配置,连接名填写easy,主机填写Server 192.168.1.200,name填写-client-user,密码填写 第十步测试连接,选中easy,点击Connect第十一步连接成功后查看连接的统计信息第十二步在 R1上查看相关信息R1#show crypto ipsec sainterface: Ethernet1/0Crypto map tag: dy, local addr 192.168.1.200protected vrf: (none)local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)remote ident (addr/mask/prot/port): (192.168.0.100/255.255.255.255/0/0)current_peer 192.168.1.101 port 1141PERMIT, flags={}#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 0, #recv errors 0local crypto endpt.: 192.168.1.200, remote crypto endpt.: 192.168.1.101path mtu 1500, ip mtu 1500, ip mtu idb Ethernet1/0current outbound spi: 0x1E9D1DD2(513613266)inbound esp sas:spi: 0x469FD498(1184879768)transform: esp-3des esp-sha-hmac ,in use settings ={Tunnel, }conn id: 1, flow_id: SW:1, crypto map: dysa timing: remaining key lifetime (k/sec): (4462636/3584)IV size: 8 bytesreplay detection support: YStatus: ACTIVEinbound ah sas:inbound pcp sas:outbound esp sas:spi: 0x1E9D1DD2(513613266)transform: esp-3des esp-sha-hmac ,in use settings ={Tunnel, }conn id: 2, flow_id: SW:2, crypto map: dysa timing: remaining key lifetime (k/sec): (4462636/3540)IV size: 8 bytesreplay detection support: YStatus: ACTIVEoutbound ah sas:outbound pcp sas:R1#以上就是小编为大家带来的cisco client设置方法介绍,都是些简单的配置,适合新手学习,希望可以帮到大家哦!cisco client设置 CISCO 是CISCO PIX防火墙提供的功能,用户通过CISCO CLIENT软件连接到CISCO PIX防火墙,利用IPSEC协议建立加密的安全隧道。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
第五步
在 R1 上进行 PPPoE 和 PPP 信息的调试
R1#debug ppp authentication PPP authentication debugging is on R1#debug pppoe events PPPoE protocol events debugging is on R1# *Jun 16 20:35:37.319: *Jun 16 20:35:37.319: R1# padi timer expired Sending PADI: Interface = FastEthernet0/0
R1(config-if)#dialer pool 1 R1(config-if)#ppp chap hostname cisco 度 配置拨号上去加密方式和密钥 0 代表为加密强
R1(config-if)#ppp chap password 0 cisco R1(cห้องสมุดไป่ตู้nfig-if)#exit R1(config)# R1(config)#ip route 0.0.0.0 0.0.0.0 Dialer0 指定一条默认路由,下一跳为 dialer0
第四步
配置 ATM2
ATM2(config)#no ip routing ATM2(config)# ATM2(config)#int f0/0 ATM2(config-if)#no ip add
ATM2(config-if)#no sh ATM2(config-if)#bridge-group 1 ATM2(config-if)# ATM2(config-if)#int atm1/0 ATM2(config-if)#no ip add ATM2(config-if)#no sh ATM2(config-if)#bridge-group 1 ATM2(config-if)#pvc 2/200 ATM2(config-if-atm-vc)#encapsulation aal5snap ATM2(config-if-atm-vc)# ATM2(config-if-atm-vc)#bridge 1 protocol ieee ATM2(config)#
Bridge Group 1 is running the IEEE compatible Spanning Tree protocol
Port 4 (FastEthernet0/0) of bridge group 1 is down Port 5 (ATM1/0 RFC 1483) of bridge group 1 is down
R1# *Jun 16 21:00:15.147: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to up R1#show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route
第二步
配置 R2 为 Aggregation 路由
R2(config)#username cisco password cisco R2(config)# R2(config)#vpdn enable R2(config)#vpdn-group 1 R2(config-vpdn)#accept-dialin R2(config-vpdn-acc-in)#protocol pppoe % PPPoE config from vpdn-group is converted to pppoe-profile based config. % Continue PPPoE configuration under 'bba-group pppoe global' % PPPoE config from vpdn-group is converted to pppoe-profile based config. % Continue PPPoE configuration under 'bba-group pppoe global'
R1(config-if)#exit R1(config)# R1(config)#interface Dialer0 虚拟接口 Dialer0
R1(config-if)#ip address negotiated R1(config-if)# R1(config-if)#encapsulation ppp 封装 PPP
*Jun 16 20:41:34.331:
PPPOE: we've got our pado and the pado timer went off
*Jun 16 20:41:34.331: OUT PADR from PPPoE Session *Jun 16 20:41:34.451: PPPoE 1: I PADS R:ca02.0a14.0000 L:ca01.0a20.0000 Fa0/0
配置 Cisco PPPoE Server 和 Cisco PPPoE Client
试验拓扑介绍:两台路由器,通过 ATM1 和 ATM2 桥接,左边为 R1,右边为 R2。 R1 配置为 PPPOE SERVER ,R2 配置为 PPPOE CLIENT。
试验要求:通过 ATM1 和 ATM2,二层桥接,R2 发送拨号请求,经过 ATM2--DSLAM-AMT1 从 R1 处获得 IP 地址
*Jun 16 20:41:34.451: IN PADS from PPPoE Session *Jun 16 20:41:34.483: %DIALER-6-BIND: Interface Vi2 bound to profile Di0 *Jun 16 20:41:34.483: PPPoE: Virtual Access interface obtained. *Jun 16 20:41:34.487: PPPoE : encap string prepared *Jun 16 20:41:34.487: [0]PPPoE 1: data path set to Virtual Acess *Jun 16 20:41:34.491: Vi2 PPP: Using dialer call direction *Jun 16 20:41:34.491: Vi2 PPP: Treating connection as a callout *Jun 16 20:41:34.495: Vi2 PPP: Session handle[A1000004] Session id[0] *Jun 16 20:41:34.495: Vi2 PPP: Authorization required *Jun 16 20:41:34.495: Vi2 PPP: No remote authentication for call-out *Jun 16 20:41:34.623: %LINK-3-UPDOWN: Interface Virtual-Access2, changed state to up R1# *Jun 16 20:41:34.807: Vi2 PPP: No authorization without authentication *Jun 16 20:41:34.831: Vi2 CHAP: I CHALLENGE id 1 len 23 from "R2" *Jun 16 20:41:34.903: Vi2 CHAP: Using hostname from interface CHAP *Jun 16 20:41:34.903: Vi2 CHAP: Using password from interface CHAP *Jun 16 20:41:34.903: Vi2 CHAP: O RESPONSE id 1 len 26 from "cisco" *Jun 16 20:41:35.471: Vi2 CHAP: I SUCCESS id 1 len 4
实验过程:
第一步
配置 R1 为 PPPoE 客户端
R1(config)#int f0/0 R1(config-if)#pppoe enable 接口下开启 pppoe 协议
R1(config-if)#no sh R1(config-if)# R1(config-if)#pppoe-client dial-pool-number 1 定义组名
ATM1(config-if)# ATM1(config-if)#int atm1/0 ATM1(config-if)#no ip add ATM1(config-if)#no sh ATM1(config-if)#bridge-group 1 ATM1(config-if)#pvc 1/100 ATM1(config-if-atm-vc)#encapsulation aal5snap ATM1(config-if-atm-vc)# ATM1(config-if-atm-vc)#bridge 1 protocol ieee ATM1(config)#end ATM1# ATM1#show bridge group
