NLOS Error Mitigation for Mobile Location Estimation in Wireless Networks
illegal instruction 的解决方法
Illegal instruction 的解决方法最新解决方法:把/usr/local/arm/compiler/arm-none-linux-gnueabi/libc/armv4t/lib 目录(也就是你的编译器的库目录)下的所有文件拷贝到目标板子的根目录的lib目录下就好了。
这样无论你的hello是动态编译还是静态编译,跑起来都不会有Illegal instruction的问题。
////////////////////////////////老的解决方法:开发板配置: ARM9 + linux-3.6.30编译器:arm-linux-4.3.2在移植好jffs2文件系统以后,当然想写个hello world 来验证一下自己的成果了。
好,开始:1.编辑编译#vi hello.c#include <stdio.h>int main(void){printf("welcome to my rootfs!/n");return 0;}#arm-linux-gcc –o hello hello.c2.把hello复制到用来制作文件系统的文件夹,制作文件系统rootfs.jffs2,下载运行,开发板能够成功启动,能够出现shell交互界面。
这点肯定地说明busybox是没有问题的。
运行hello./hello 出现:Illegal instruction从网上找了很多资料,大部分把责任归于EABI,但我想想,既然kernel和busybox都能正常启动,那它们都应该是eabi编译的了,hello也肯定是eabi的,因为他们都是用arm-linux-4.3.2编译的(编译内核的时候make menuconfig要选山EABI选项).所以网上大部分资料都不适合解决我遇到的问题。
但最终还是找到了一边能够帮我解决问题的文章:sysV是UNIX的两大分支之一,现在的UNIX和类UNIX系统根据其发展分支可以分为sysV 分支和BSD分支,这两个分支是最初的UNIX分化出来的最初的AT&T实验室的UNIX系统到了第5版,也是就system V (sysV) 后就分化成了BSD分支和sysV分支, 两者的最大区别就是启动过程的运行等级机制有很大区别. linux是sysV风格的UNIX系统,freeBSD是BSD 风格的UNIX系统, 但是现在这个界限也在慢慢模糊掉, 两种分支的系统取长补短,相互渗透.还有一种可能性:maemo下自带的编译器支持新的嵌入式应用程序二进制接口标准EABI,而kernel,首先并未打开对eabi的支持,其次,kernel编绎使用的是非EABI的编译器。
clgetplatformids returned unknown error code

您遇到的问题与OpenCL环境的配置有关。
clGetPlatformIDs()函数返回的错误代码-1001对应于状态宏CL_PLATFORM_NOT_FOUND_KHR,这通常意味着系统上没有找到可用的OpenCL平台。
以下是可能的解决方案:
安装OpenCL驱动和库:确保您的系统上安装了正确的OpenCL驱动和库。
这通常包括与您的GPU或CPU兼容的驱动和库。
检查环境变量:确保OpenCL相关的环境变量(如PATH或LD_LIBRARY_PATH)已正确设置,以便系统可以找到OpenCL库。
检查设备支持:使用clinfo工具检查系统上的OpenCL设备是否被正确识别。
确保您的硬件支持OpenCL,并且驱动程序已正确安装。
更新驱动程序和固件:确保您的GPU驱动程序和固件是最新的,有时候这可以解决兼容性问题。
检查文档和社区支持:查阅特定硬件或软件的官方文档,或在相关社区和论坛中搜索类似的问题。
可能有人遇到了相同的问题,并找到了解决方案。
联系技术支持:如果上述方法都不能解决问题,可能需要联系您的硬件供应商或OpenCL软件供应商的技术支持寻求帮助。
在处理此类问题时,请注意查阅相关的技术文档和社区论坛,以获得最准确和最新的解决方案。
NLOS identification and mitigation for localization based on UWB experimental data

NLOS Identification and Mitigation for Localization Based on UWB Experimental Data Stefano Maran`o,Student Member,IEEE,Wesley M.Gifford,Student Member,IEEE,Henk Wymeersch,Member,IEEE,Moe Z.Win,Fellow,IEEEAbstract—Sensor networks can benefit greatly from location-awareness,since it allows information gathered by the sensors to be tied to their physical locations.Ultra-wide bandwidth(UWB) transmission is a promising technology for location-aware sensor networks,due to its power efficiency,fine delay resolution,and robust operation in harsh environments.However,the presence of walls and other obstacles presents a significant challenge in terms of localization,as they can result in positively biased distance estimates.We have performed an extensive indoor measurement campaign with FCC-compliant UWB radios to quantify the effect of non-line-of-sight(NLOS)propagation.From these channel pulse responses,we extract features that are representative of the propagation conditions.We then develop classification and regression algorithms based on machine learning techniques, which are capable of:(i)assessing whether a signal was trans-mitted in LOS or NLOS conditions;and(ii)reducing ranging error caused by NLOS conditions.We evaluate the resulting performance through Monte Carlo simulations and compare with existing techniques.In contrast to common probabilistic approaches that require statistical models of the features,the proposed optimization-based approach is more robust against modeling errors.Index Terms—Localization,UWB,NLOS Identification,NLOS Mitigation,Support Vector Machine.I.I NTRODUCTIONL OCATION-AW ARENESS is fast becoming an essential aspect of wireless sensor networks and will enable a myr-iad of applications,in both the commercial and the military sectors[1],[2].Ultra-wide bandwidth(UWB)transmission [3]–[8]provides robust signaling[8],[9],as well as through-wall propagation and high-resolution ranging capabilities[10], [11].Therefore,UWB represents a promising technology for localization applications in harsh environments and accuracy-critical applications[10]–[15].In practical scenarios,however, a number of challenges remain before UWB localization and communication can be deployed.These include signal Manuscript received15May2009;revised15February2010.This research was supported,in part,by the National Science Foundation under grant ECCS-0901034,the Office of Naval Research Presidential Early Career Award for Scientists and Engineers(PECASE)N00014-09-1-0435,the Defense University Research Instrumentation Program under grant N00014-08-1-0826, and the MIT Institute for Soldier Nanotechnologies.S.Maran`o was with Laboratory for Information and Decision Systems (LIDS),Massachusetts Institute of Technology(MIT),and is now with the Swiss Seismological Service,ETH Z¨u rich,Z¨u rich,Switzerland(e-mail: stefano.marano@sed.ethz.ch).H.Wymeersch was with LIDS,MIT,and is now with Chalmers University of Technology,G¨o teborg,Sweden(e-mail:henkw@chalmers.se).Wesley M.Gifford and Moe Z.Win are with LIDS,MIT,Cambridge,MA 02139USA(e-mail:wgifford@,moewin@).Digital Object Identifier10.1109/JSAC.2010.100907.acquisition[16],multi-user interference[17],[18],multipath effects[19],[20],and non-line-of-sight(NLOS)propagation [10],[11].The latter issue is especially critical[10]–[15]for high-resolution localization systems,since NLOS propagation introduces positive biases in distance estimation algorithms, thus seriously affecting the localization performance.Typical harsh environments such as enclosed areas,urban canyons, or under tree canopies inherently have a high occurrence of NLOS situations.It is therefore critical to understand the impact of NLOS conditions on localization systems and to develop techniques that mitigate their effects.There are several ways to deal with ranging bias in NLOS conditions,which we classify as identification and mitigation. NLOS identification attempts to distinguish between LOS and NLOS conditions,and is commonly based on range estimates[21]–[23]or on the channel pulse response(CPR) [24],[25].Recent,detailed overviews of NLOS identification techniques can be found in[22],[26].NLOS mitigation goes beyond identification and attempts to counter the positive bias introduced in NLOS signals.Several techniques[27]–[31]rely on a number of redundant range estimates,both LOS and NLOS,in order to reduce the impact of NLOS range estimates on the estimated agent position.In[32]–[34]the geometry of the environment is explicitly taken into account to cope with NLOS situations.Other approaches,such as[35],attempt to detect the earliest path in the CPR in order to better estimate the TOA in NLOS prehensive overviews of NLOS mitigation techniques can be found in[26],[36]. The main drawbacks of existing NLOS identification and mitigation techniques are:(i)loss of information due to the direct use of ranges instead of the CPRs;(ii)latency incurred during the collection of range estimates to establish a history; and(iii)difficulty in determining the joint probability distribu-tions of the features required by many statistical approaches. In this paper,we consider an optimization-based approach. In particular,we propose the use of non-parametric ma-chine learning techniques to perform NLOS identification and NLOS mitigation.Hence,they do not require a statistical characterization of LOS and NLOS channels,and can perform identification and mitigation under a common framework.The main contributions of this paper are as follows:•characterization of differences in the CPRs under LOS and NLOS conditions based on an extensive indoor mea-surement campaign with FCC-compliant UWB radios;•determination of novel features extracted from the CPR that capture the salient properties in LOS and NLOS conditions;0733-8716/10/$25.00c 2010IEEE•demonstration that a support vector machine (SVM)clas-si fier can be used to distinguish between LOS and NLOS conditions,without the need for statistical modeling of the features under either condition;and•development of SVM regressor-based techniques to mit-igate the ranging bias in NLOS situations,again without the need for statistical modeling of the features under either condition.The remainder of the paper is organized as follows.In Section II,we introduce the system model,problem statement,and describe the effect of NLOS conditions on ranging.In Section III,we describe the equipment and methodologies of the LOS/NLOS measurement campaign and its contribu-tion to this work.The proposed techniques for identi fication and mitigation are described in Section IV,while different strategies for incorporating the proposed techniques within any localization system are discussed in Section V.Numerical performance results are provided in Section VI,and we draw our conclusions in Section VII.II.P ROBLEM S TATEMENT AND S YSTEM M ODEL In this section,we describe the ranging and localization algorithm,and demonstrate the need for NLOS identi fication and mitigation.A.Single-node LocalizationA network consists of two types of nodes:anchors are nodes with known positions,while agents are nodes with unknown positions.For notational convenience,we consider the point of view of a single agent,with unknown position p ,surrounded by N b anchors,with positions,p i ,i =1,...,N b .The distance between the agent and anchor i is d i = p −p i .The agent estimates the distance between itself and the anchors,using a ranging protocol.We denote the estimateddistance between the agent and anchor i by ˆdi ,the ranging error by εi =ˆdi −d i ,the estimate of the ranging error by ˆεi ,the channel condition between the agent and anchor i by λi ∈{LOS ,NLOS },and the estimate of the channelcondition by ˆλi .The mitigated distance estimate of d i is ˆd m i=ˆd i −ˆεi .The residual ranging error after mitigation is de fined as εm i =ˆd m i −d i .Given a set of at least three distance estimates,the agent will then determine its position.While there are numerous positioning algorithms,we focus on the least squares (LS)criterion,due to its simplicity and because it makes no assumptions regarding ranging errors.The agent can infer its position by minimizing the LS cost functionˆp=arg min p(p i ,ˆdi )∈Sˆd i − p −p i 2.(1)Note that we have introduced the concept of the set of useful neighbors S ,consisting of couplesp i ,ˆdi .The optimization problem (1)can be solved numerically using steepest descent.B.Sources of ErrorThe localization algorithm will lead to erroneous results when the ranging errors are large.In practice the estimated distances are not equal to the true distances,because of a number of effects including thermal noise,multipath propa-gation,interference,and ranging algorithm inaccuracies.Ad-ditionally,the direct path between requester and responder may be obstructed,leading to NLOS propagation.In NLOS conditions,the direct path is either attenuated due to through-material propagation,or completely blocked.In the former case,the distance estimates will be positively biased due to the reduced propagation speed (i.e.,less than the expected speed of light,c ).In the latter case the distance estimate is also positively biased,as it corresponds to a re flected path.These bias effects can be accounted for in either the ranging or localization phase.In the remainder of this paper,we focus on techniques that identify and mitigate the effects of NLOS signals during the ranging phase.In NLOS identi fication,the terms in (1)corre-sponding to NLOS distance estimates are omitted.In NLOS mitigation,the distance estimates corresponding to NLOS signals are corrected for improved accuracy.The localization algorithm can then adopt different strategies,depending on the quality and the quantity of available range estimates.III.E XPERIMENTAL A CTIVITIESThis section describes the UWB LOS/NLOS measurement campaign performed at the Massachusetts Institute of Tech-nology by the Wireless Communication and Network Sciences Laboratory during Fall 2007.A.OverviewThe aim of this experimental effort is to build a large database containing a variety of propagation conditions in the indoor of fice environment.The measurements were made using two FCC-compliant UWB radios.These radios repre-sent off-the-shelf transceivers and therefore an appropriate benchmark for developing techniques using currently available technology.The primary focus is to characterize the effects of obstructions.Thus,measurement positions (see Fig.1)were chosen such that half of the collected waveforms were cap-tured in NLOS conditions.The distance between transmitter and receiver varies widely,from roughly 0.6m up to 18m,to capture a variety of operating conditions.Several of fices,hallways,one laboratory,and a large lobby constitute the physical setting of this campaign.While the campaign was conducted in one particular indoor of fice envi-ronment,because of the large number of measurements and the variety of propagation scenarios encountered,we expect that our results are applicable in other of fice environments.The physical arrangement of the campaign is depicted in Fig.1.In each measurement location,the received waveform and the associated range estimate,as well as the actual distance are recorded.The waveforms are then post-processed in order to reduce dependencies on the speci fic algorithm and hardware,e.g.,on the leading edge detection (LED)algorithm embedded in the radios.Fig.1.Measurements were taken in clusters over several different rooms and hallways to capture different propagation conditions.B.Experimental ApparatusThe commercially-available radios used during the data collection process are capable of performing communications and ranging using UWB signals.The radio complies with the emission limit set forth by the FCC[37].Specifically, the10dB bandwidth spans from3.1GHz to6.3GHz.The radio is equipped with a bottom fed planar elliptical antenna. This type of dipole antenna is reported to be well matched and radiation efficient.Most importantly,it is omni-directional and thus suited for ad-hoc networks with arbitrary azimuthal orientation[38].Each radio is mounted on the top of a plastic cart at a height of90cm above the ground.The radios perform a round-trip time-of-arrival(RTOA)ranging protocol1and are capable of capturing waveforms while performing the ranging procedure.Each waveform r(t)captured at the receiving radio is sampled at41.3ps over an observation window of190ns.C.Measurement ArrangementMeasurements were taken at more than one hundred points in the considered area.A map,depicting the topological organization of the clusters within the building,is shown 1RTOA allows ranging between two radios without a common time reference;and thus alleviates the need for networksynchronization.Fig.2.The measurement setup for collecting waveforms between D675CA and H6around the corner of the WCNS Laboratory.in Fig.1,and a typical measurement scenario is shown in Fig.2.Points are placed randomly,but are restricted to areas which are accessible by the carts.The measurement points are grouped into non-overlapping clusters,i.e.,each point only belongs to a single cluster.Typically,a cluster corresponds to a room or a region of a hallway.Within each cluster,measurements between every possible pair of points were captured.When two clusters were within transmission range, every inter-cluster measurement was collected as well.Overall, more than one thousand unique point-to-point measurements were performed.For each pair of points,several received waveforms and distance estimates are recorded,along with the actual distance.During each measurement the radios remain stationary and care is taken to limit movement of other objects in the nearby surroundings.D.DatabaseUsing the measurements collected during the measurement phase,a database was created and used to develop and evaluate the proposed identification and mitigation techniques. It includes1024measurements consisting of512waveforms captured in the LOS condition and512waveforms captured in the NLOS condition.The term LOS is used to denote the existence of a visual path between transmitter and receiver,i.e., a measurement is labeled as LOS when the straight line be-tween the transmitting and receiving antenna is unobstructed. The ranging estimate was obtained by an RTOA algorithm embedded on the radio.The actual position of the radio during each measurement was manually recorded,and the ranging error was calculated with the aid of computer-aided design(CAD)software.The collected waveforms were then processed to align thefirst path in the delay domain using a simple threshold-based method.The alignment process creates a time reference independent of the LED algorithm embedded on the radio.IV.NLOS I DENTIFICATION AND M ITIGATIONThe collected measurement data illustrates that NLOS prop-agation conditions significantly impact ranging performance. For example,Fig.3shows the empirical CDFs of the ranging error over the ensemble of all measurements collected under the two different channel conditions.In LOS conditions a ranging error below one meter occurs in more than95%of the measurements.On the other hand,in NLOS conditions a ranging error below one meter occurs in less than30%of the measurements.Clearly,LOS and NLOS range estimates have very dif-ferent characteristics.In this section,we develop techniques to distinguish between LOS and NLOS situations,and to mitigate the positive biases present in NLOS range estimates. Our techniques are non-parametric,and rely on least-squares support-vector machines(LS-SVM)[39],[40].Wefirst de-scribe the features for distinguishing LOS and NLOS situa-tions,followed by a brief introduction to LS-SVM.We then describe how LS-SVM can be used for NLOS identification and mitigation in localization applications,without needing to determine parametric joint distributions of the features for both the LOS and NLOS conditions.A.Feature Selection for NLOS ClassificationWe have extracted a number of features,which we expect to capture the salient differences between LOS and NLOS signals,from every received waveform r(t).These featuresFig.3.CDF of the ranging error for the LOS and NLOS condition. were selected based on the following observations:(i)in NLOS conditions,signals are considerably more attenuated and have smaller energy and amplitude due to reflections or obstructions;(ii)in LOS conditions,the strongest path of the signal typically corresponds to thefirst path,while in NLOS conditions weak components typically precede the strongest path,resulting in a longer rise time;and(iii)the root-mean-square(RMS)delay spread,which captures the temporal dispersion of the signal’s energy,is larger for NLOS signals. Fig.4depicts two waveforms received in the LOS and NLOS condition supporting our observations.We also include some features that have been presented in the literature.Taking these considerations into account,the features we will consider are as follows:1)Energy of the received signal:E r=+∞−∞|r(t)|2dt(2) 2)Maximum amplitude of the received signal:r max=maxt|r(t)|(3) 3)Rise time:t rise=t H−t L(4) wheret L=min{t:|r(t)|≥ασn}t H=min{t:|r(t)|≥βr max},andσn is the standard deviation of the thermal noise.The values ofα>0and0<β≤1are chosen empirically in order to capture the rise time;in our case, we usedα=6andβ=0.6.4)Mean excess delay:τMED=+∞−∞tψ(t)dt(5) whereψ(t)=|r(t)|2/E r.Fig.4.In some situations there is a clear difference between LOS(upper waveform)and NLOS(lower waveform)signals.5)RMS delay spread:τRMS=+∞−∞(t−τMED)2ψ(t)dt(6)6)Kurtosis:κ=1σ4|r|TT|r(t)|−μ|r|4dt(7)whereμ|r|=1TT|r(t)|dtσ2|r|=1TT|r(t)|−μ|r|2dt.B.Least Squares SVMThe SVM is a supervised learning technique used both for classification and regression problems[41].It represents one of the most widely used classification techniques because of its robustness,its rigorous underpinning,the fact that it requires few user-defined parameters,and its superior performance compared to other techniques such as neural networks.LS-SVM is a low-complexity variation of the standard SVM, which has been applied successfully to classification and regression problems[39],[40].1)Classification:A linear classifier is a function R n→{−1,+1}of the forml(x)=sign[y(x)](8) withy(x)=w Tϕ(x)+b(9) whereϕ(·)is a predetermined function,and w and b are unknown parameters of the classifier.These parameters are de-termined based on the training set{x k,l k}N k=1,where x k∈R n and l k∈{−1,+1}are the inputs and labels,respectively.In the case where the two classes can be separated the SVM determines the separating hyperplane which maximizes the margin between the two classes.2Typically,most practical problems involve classes which are not separable.In this case,the SVM classifier is obtained by solving the following optimization problem:arg minw,b,ξ12w 2+γNk=1ξk(10)s.t.l k y(x k)≥1−ξk,∀k(11)ξk≥0,∀k,(12) where theξk are slack variables that allow the SVM to tolerate misclassifications andγcontrols the trade-off between minimizing training errors and model complexity.It can be shown that the Lagrangian dual is a quadratic program(QP) [40,eqn.2.26].To further simplify the problem,the LS-SVM replaces the inequality(11)by an equality:arg minw,b,e12w 2+γ12Nk=1e2k(13)s.t.l k y(x k)=1−e k,∀k.(14) Now,the Lagrangian dual is a linear program(LP)[40,eqn.3.5],which can be solved efficiently by standard optimization toolboxes.The resulting classifier can be written asl(x)=signNk=1αk l k K(x,x k)+b,(15)whereαk,the Lagrange multipliers,and b are found from the solution of the Lagrangian dual.The function K(x k,x l)=ϕ(x k)Tϕ(x l)is known as the kernel which enables the SVM to perform nonlinear classification.2)Regression:A linear regressor is a function R n→R of the formy(x)=w Tϕ(x)+b(16) whereϕ(·)is a predetermined function,and w and b are unknown parameters of the regressor.These parameters are determined based on the training set{x k,y k}N k=1,where x k∈R n and y k∈R are the inputs and outputs,respectively. The LS-SVM regressor is obtained by solving the following optimization problem:arg minw,b,e12w 2+γ12e 2(17)s.t.y k=y(x k)+e k,∀k,(18) whereγcontrols the trade-off between minimizing training errors and model complexity.Again,the Lagrangian dual is an LP[40,eqn.3.32],whose solution results in the following LS-SVM regressory(x)=Nk=1αk K(x,x k)+b.(19)2The margin is given by1/ w ,and is defined as the smallest distance between the decision boundary w Tϕ(x)+b=0and any of the training examplesϕ(x k).C.LS-SVM for NLOS Identi fication and MitigationWe now apply the non-parametric LS-SVM classi fier to NLOS identi fication,and the LS-SVM regressor to NLOS mitigation.We use 10-fold cross-validation 3to assess the performance of our features and the SVM.Not only are we interested in the performance of LS-SVM for certain features,but we are also interested in which subsets of the available features give the best performance.1)Classi fication:To distinguish between LOS and NLOS signals,we train an LS-SVM classi fier with inputs x k and corresponding labels l k =+1when λk =LOS and l k =−1when λk =NLOS .The input x k is composed of a subset of the features given in Section IV-A.A trade-off between classi fier complexity and performance can be made by using a different size feature subset.2)Regression:To mitigate the effect of NLOS propagation,we train an LS-SVM regressor with inputs x k and corre-sponding outputs y k =εk associated with the NLOS signals.Similar to the classi fication case,x k is composed of a subset of features,selected from those given in Section IV-A and therange estimate ˆdk .Again,the performance achieved by the regressor will depend on the size of the feature subset and the combination of features used.V.L OCALIZATION S TRATEGIESBased on the LS-SVM classi fier and regressor,we can develop the following localization strategies:(i)localization via identi fication ,where only classi fication is employed;(ii)localization via identi fication and mitigation ,where the re-ceived waveform is first classi fied and error mitigation is performed only on the range estimates from those signals identi fied as NLOS;and (iii)a hybrid approach which discards mitigated NLOS range estimates when a suf ficient number of LOS range estimates are present.A.Strategy 1:StandardIn the standard strategy,all the range estimates ˆdi from neighboring anchor nodes are used by the LS algorithm (1)for localization.In other words,S S =p i ,ˆd i :1≤i ≤N b .(20)B.Strategy 2:Identi ficationIn the second strategy,waveforms are classi fied as LOS or NLOS using the LS-SVM classi fier.Range estimates are used by the localization algorithm only if the associated waveform was classi fied as LOS,while range estimates from waveforms classi fied as NLOS are discarded:S I = p i ,ˆd i:1≤i ≤N b ,ˆλi =LOS .(21)Whenever the cardinality of S I is less than three,the agent isunable to localize.4In this case,we set the localization error to +∞.3InK -fold cross-validation,the dataset is randomly partitioned into K parts of approximately equal size,each containing 50%LOS and 50%NLOS waveforms.The SVM is trained on K −1parts and the performance is evaluated on the remaining part.This is done a total of K times,using each of the K parts exactly once for evaluation and K −1times for training.4Note that three is the minimum number of anchor nodes needed to localize in two-dimensions.TABLE IF ALSE ALARM PROBABILITY (P F ),MISSED DETECTION PROBABILITY (P M ),AND OVERALL ERROR PROBABILITY (P E )FOR DIFFERENT NLOSIDENTIFICATION TECHNIQUES .T HE SET F i IDENOTES THE SET OF i FEATURES WITH THE SMALLEST P E USING THE LS-SVM TECHNIQUE .Identi fication Technique P F P M P E Parametric technique given in [42]0.1840.1430.164LS-SVM using features from [42]0.1290.1520.141F 1I ={r max }0.1370.1230.130F 2I ={r max ,t rise }0.0920.1090.100F 3I ={E r ,t rise ,κ}0.0820.0900.086F 4I={E r ,r max ,t rise ,κ}0.0820.0900.086F 5I ={E r ,r max ,t rise ,τMED ,κ}0.0860.0900.088F 6I={E r ,r max ,t rise ,τMED ,τRMS ,κ}0.0920.0900.091C.Strategy 3:Identi fication and MitigationThis strategy is an extension to the previous strategy,wherethe received waveform is first classi fied as LOS or NLOS,and then the mitigation algorithm is applied to those signals with ˆλi =NLOS .For this case S IM =S I ∪S M ,where S M = p i ,ˆd m i :1≤i ≤N b ,ˆλi =NLOS ,(22)and the mitigated range estimate ˆd m iis described in Sec.II.This approach is motivated by the observation that mitigation is not necessary for range estimates associated with LOS waveforms,since their accuracy is suf ficiently high.D.Strategy 4:Hybrid Identi fication and Mitigation In the hybrid approach,range estimates are mitigated as in the previous strategy.However,mitigated range estimates are only used when less than three LOS anchors are available:5S H =S I if |S I |≥3S IMotherwise(23)This approach is motivated by the fact that mitigated range es-timates are often still less accurate than LOS range estimates.Hence,only LOS range estimates should be used,unless there is an insuf ficient number of them to make an unambiguous location estimate.VI.P ERFORMANCE E VALUATION AND D ISCUSSION In this section,we quantify the performance of the LS-SVM classi fier and regressor from Section IV,as well as the four localization strategies from Section V.We will first consider identi fication,then mitigation,and finally localization.For every technique,we will provide the relevant performance measures as well as the quantitative details of how the results were obtained.5Inpractice the angular separation of the anchors should be suf ficiently large to obtain an accurate estimate.If this is not the case,more than three anchors may be needed.TABLE IIM EAN AND RMS VALUES OF RRE FOR LS-SVM REGRESSION -BASEDMITIGATION .T HE SET F i MDENOTES THE SET OF i FEATURES WHICH ACHIEVES THE MINIMUM RMS RRE.Mitigation Technique with LS-SVM RegressionMean [m]RMS [m ]No Mitigation2.63223.589F 1M={ˆd}-0.0004 1.718F 2M ={κ,ˆd }-0.0042 1.572F 3M ={t rise ,κ,ˆd }0.0005 1.457F 4M ={t rise ,τMED ,κ,ˆd }0.0029 1.433F 5M={E r ,t rise ,τMED ,κ,ˆd }0.0131 1.425F 6M ={E r ,t rise ,τMED ,τRMS ,κ,ˆd }0.0181 1.419F 7M={E r ,r max ,t rise ,τMED ,τRMS ,κ,ˆd}0.01801.425A.LOS/NLOS Identi ficationIdenti fication results,showing the performance 6for eachfeature set size,are given in Table I.For the sake of compari-son,we also evaluate the performance of the parametric identi-fication technique from [42],which relies on three features:the mean excess delay,the RMS delay spread,and the kurtosis of the waveform.For fair comparison,these features are extracted from our database.The performance is measured in terms of the misclassi fication rate:P E =(P F +P M )/2,where P F is the false alarm probability (i.e.,deciding NLOS when the signal was LOS),and P M is the missed detection probability (i.e.,deciding LOS when the signal was NLOS).The table only lists the feature sets which achieved the minimum misclassi fication rate for each feature set size.We observe that the LS-SVM,using the three features from [42],reduces the false alarm probability compared to the parametric technique.It was shown in [43]that the features from [42],in fact,give rise to the worst performance among all possible sets of size three considered ing the features from Section IV-A and considering all feature set sizes,our results indicate that the feature set of size three,F 3I ={E r ,t rise ,κ},provides the best pared to the parametric technique,this set reduces both the false alarm and missed detection probabilities and achieves a correct classi fication rate of above 91%.In particular,among all feature sets of size three (results not shown,see [43]),there are seven sets that yield a P E of roughly 10%.All seven of these sets have t rise in common,while four have r max in common,indicating that these two features play an important role.Their importance is also corroborated by the presence of r max and t rise in the selected sets listed in Table I.For the remainder of this paper we will use the feature set F 3I for identi fication.B.NLOS MitigationMitigation results,showing the performance 7for different feature set sizes are given in Table II.The performance is measured in terms of the root mean square residual ranging6Wehave used an RBF kernel of the form K (x ,x k )=exp “− x −x k 2”and set γ=0.1.Features are first converted to the log domain in order to reduce the dynamic range.7Here we used a kernel given by K (x ,x k )=exp “− x −x k2/162”and set γ=10.Again,features are first converted to the log domain.Fig.5.CDF of the ranging error for the NLOS case,before and after mitigation.error (RMS RRE): 1/N N i =1(εm i )2.A detailed analysis ofthe experimental data indicates that large range estimates are likely to exhibit large positive ranging errors.This means that ˆditself is a useful feature,as con firmed by the presence of ˆdin all of the best feature sets listed in the table.Increasing the feature set size can further improve the RMS RRE.Thefeature set of size six,F 6M={E r ,t rise ,τMED ,τRMS ,κ,ˆd },offers the best performance.For the remainder of this paper,we will use this feature set for NLOS mitigation.Fig.5shows the CDF of the ranging error before and after mitigation using this feature set.We observe that without mitigation around 30%of the NLOS waveforms achieved an accuracy of less than one meter (|ε|<1).Whereas,after the mitigation process,60%of the cases have an accuracy less than 1m.C.Localization Performance1)Simulation Setup:We evaluate the localization perfor-mance for fixed number of anchors (N b )and a varying prob-ability of NLOS condition 0≤P NLOS ≤1.We place an agent at a position p =(0,0).For every anchor i (1≤i ≤N b ),we draw a waveform from the database:with probability P NLOS we draw from the NLOS database and with probability 1−P NLOS from the LOS database.The true distance d i corre-sponding to that waveform is then used to place the i th anchor at position p i =(d i sin(2π(i −1)/N b ),d i cos(2π(i −1)/N b )),while the estimated distance ˆdi is provided to the agent.This creates a scenario where the anchors are located at different distances from the agent with equal angular spacing.The agent estimates its position,based on a set of useful neighbors S ,using the LS algorithm from Section II.The arithmetic mean 8of the anchor positions is used as the initial estimate of the agent’s position.2)Performance Measure:To capture the accuracy and availability of localization,we introduce the notion of outage probability .For a certain scenario (N b and P NLOS )and a8Thisis a fair setting for the simulation,as all the strategies are initialized inthe same way.Indeed,despite the identical initialization,strategies converge to signi ficantly different final position estimates.In addition,we note that such an initial position estimate is always available to the agent.。
National Instruments TestStand序列编辑器用户手册说明书
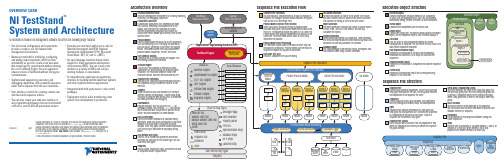
Execution Object StructureExecution ObjectContains information TestStand needs to run a sequence, its steps, and any subsequences it calls. You can suspend,interactively debug, resume, terminate, or abort executions.Thread ObjectRepresents an independent path of control flow.Report ObjectContains the report text. The process model updates the Report object, and the sequence editor or user interface displays it.Call StackLists the chain of active sequences waiting for nestedsubsequences to complete. The first item in the call stack is the most-nested sequence invocation.Root SequenceContext ObjectRepresents the execution of the least-nested sequence invocation that contains a list of steps and calls to other sequences.SequenceContext ObjectRepresents the execution of a sequence that another sequence called.Current StepRepresents the executing step of the currently executingsequence in the call stack.Architecture OverviewTestStand Sequence EditorTestStand development environment for creating, modifying,executing, and debugging sequences.Custom User InterfacesCustomizable applications that, depending on mode,edit, execute, and debug test sequences on a test station. User interfaces are available in several different programming languages and include fullsource code, which allows you to modify them to meet specific needs.Process ModelsDefine the operations that occur for all test sequences,such as identifying the UUT, notifying the operator of pass/fail status, generating a test report, and logging results. TestStand includes three fully customizable process models: Sequential, Parallel, and er Interface ControlsA powerful set of ActiveX controls and support APIs for creating custom user interfaces.TestStand EngineA set of DLLs that provides an extensive ActiveX Automation API for controlling and interacting with TestStand. The TestStand Sequence Editor, User Interface Controls, and user interfaces use this API.Sequence File ExecutionsCreated by the TestStand Engine when you execute a test sequence using the sequence editor or a user interface.AdaptersAllow TestStand to call code modules in a variety of different formats and languages. Adapters also allow TestStand to integrate with various ADEs to streamline test code generation and debugging.Code ModulesProgram modules, such as LabVIEW VIs (.vi ) or Windows Dynamic Link Libraries (.dll ), that contain one or more functions that perform a specific test or action. TestStand adapters call code modules. Built-In Step TypesDefine the standard behaviors for common testing operations. Some step types use adapters to call code modules that return data to TestStand for furtheranalysis. Other step types perform standard operations,such as calling an executable or displaying dialog boxes.User-Defined Step TypesDefine a set of custom step properties and default behaviors for each step of that custom type. You can also define data types.TemplatesCreate custom sequences, steps, and variables to use as templates to build sequence files.OVERVIEW CARDNI TestStandTMSystem and ArchitectureNI TestStand is flexible test management software that offers the following major features:•Out-of-the-box configuration and components provide a ready-to-run, full-featured test management environment.•Numerous methods for modifying, configuring,and adding new components, which provide extensibility so you can create a test executive that meets specific requirements without altering the core TestStand Engine. You can upgrade to newer versions of TestStand without losing your customizations.•Sophisticated sequencing, execution, anddebugging capabilities, and a powerful sequence editor that is separate from the user interfaces.•User interface controls for creating custom user interfaces and sequence editors.•You can also create your own user interface in any programming language that can host ActiveX controls or control ActiveX automation servers.•Example user interfaces with source code for National Instruments LabVIEW, National Instruments LabWindows ™/CVI ™, Microsoft Visual Basic .NET, C#, and C++ (MFC).•An open language interface that provides support for many application development environments (ADEs). You can create code modules in a variety of ADEs and call pre-existing modules or executables.• A comprehensive application programminginterface for building multithreaded test systems and other sophisticated test applications.•Integration with third-party source code control packages.•Deployment tools to aid in transferring a test system from development to production.TestStand Sequence EditorCode ModulesResultsResultsResultsResultsResultsResultsResultsResultsCustom User InterfacesUser Interface (UI)ControlsApplication Programming Interface (API) TestStand EngineSequence File ExecutionsUser-Defined Step TypesSequence File ExecutionsNo ModelTest Socket 0Execution UUTUUTUUTTest Socket 1Execution UUTUUT TestSocket nExecution UUTUUTUUT UUT UUTUUTUUTUUTProcess Model Result ProcessingSchema DefinitionsDatabase LoggerReport GeneratorADO/ODBCThread Object 0Thread Object n Sequence File GlobalsStepsMain Step GroupStepsCleanup Step GroupParametersSequencesLocal VariablesAdapters.VI.DLL, .OBJ, .LIB, .C.DLL .DLL, .EXE .DLL, .EXE.PRG .SEQLabVIEW Adapter LabWindows/CVI Adapter C/C++ DLL Adapter .NET Adapter ActiveX/COM Adapter HTBasic Adapter Sequence AdapterTypesSequence FileParallel Process ModelBatch Process ModelSequential Process ModelProcess Model Sequence File ExecutionTestSocket nExecution Test Socket 1Execution TestSocket 0Execution Oracle . . .SQL ServerReport ObjectExecution ObjectCall StackRootSequenceContextObject 0SequenceContextObject 1SequenceContextObject nStep Object 0Step Object n. . .Current StepMicrosoft Access Process Models. ... ..XMLHTMLASCII-Text. . .Sequence File Execution FlowSequence File ExecutionsYou can execute a sequence directly, or you can execute a sequence file through a process model Execution entry point,such as Test UUTs and Single Pass.Process Model Sequence File ExecutionWhen you start an execution through a process modelExecution entry point, the process model defines how to test the UUTs. The Sequential model tests one UUT at a time. The Parallel model tests multiple independent test sockets at the same time. The Batch model tests a batch of UUTs using dependent test sockets.Process Model Result ProcessingThe TestStand Engine collects the results of each step that executes into a result list. Process models use the result list to generate reports and log data to databases. Unit Under Test (UUT)Device or component that you are testing.Test Socket ExecutionFor each test socket, or fixture, in the system, the Parallel and Batch models launch a separate test socket execution that controls the testing of UUTs in that test socket.Report GeneratorThe report generator traverses test results to create reports in XML, HTML, and ASCII-text formats. You can fully customize the reports.Schema DefinitionsSchema definitions define SQL statements, table definitions,and TestStand expressions that define how to log results to a database. You can fully customize the schemas.Database LoggerThe database logger traverses test results and exports data into database tables using schema definitions.Sequence File StructureSequence FileContains any number of sequences, a set of data types and step types the sequence file uses, and any global variables that sequences in the sequence file share.SequencesContain groups of steps, local variables, and parameters used for passing data between steps and subsequences.TypesSequence files contain definitions of all data types and step types that its sequences use. Variables and properties in a sequence are instances of data types. Steps in a sequence are instances of step types.Sequence File GlobalsStore data you want to access from any sequence or step within the sequence file in which you define the sequence file global variable.Setup, Main, Cleanup Step GroupsTestStand executes the steps in the Setup step group first,the Main step group next, and the Cleanup step group last.By default, a sequence moves to the Cleanup step group when a step generates an error in the Setup or Main step group.Local VariablesStore data relevant to the execution of the sequence. You can access local variables from within steps and code modules defined in a sequence.ParametersUse parameters to exchange data between calling and called sequences.StepsPerform built-in operations or call code modules. A step is an instance of a step type, which defines a set of step properties and default behaviors for each step.373457B-01 Apr07. . .. . .. . .National Instruments, NI, , NI TestStand, and LabVIEW are trademarks of National Instruments Corporation. Refer to the Terms of Use section on /legal for more information aboutNational Instruments trademarks. Other product and company names mentioned herein are trademarks or trade names of their respective companies. For patents covering National Instruments products,refer to the appropriate location: Help»Patents in your software, the patents.txt file on your CD, or /patents .© 2003–2007 National Instruments Corporation. All rights reserved.Printed in Ireland.StepsSetup Step GroupTemplatesFlow Control Sequence Call Statement LabelMessage Popup Call Executable Property Loader FTP FilesSynchronization Steps Database Steps IVI-C Steps LabVIEW UtilityPass/Fail Test Numeric Limit Test Multiple Numeric Limit Test String Value Test Action Built-In Step TypesYou can use the fully customizable TestStand developmentenvironment to create, modify, execute, and debug sequences. You can also use the sequence editor to modify step types and process models. You can customize the environment by docking, auto-hiding, and floating panes to optimize your development tasks. TheDevelopment EnvironmentOVERVIEW CARD NI TestStand TMSystem and ArchitectureTestStand includes separate user interface applications developed in LabVIEW, LabWindows/CVI, Microsoft Visual Basic .NET,C#, and C++ (MFC). Because TestStand includes the source code for each user interface, you can fully customize the userinterfaces. You can also create your own user interface using any programming language that can host ActiveX controls orcontrol ActiveX automation servers. With the user interfaces in operator mode, you can start multiple concurrent executions, set breakpoints, and single-step. In editor mode, you can modify sequences, display sequence variables, sequence parameters,step properties, and so on.TestStand Sequence Editor Overview User Interface OverviewPrinted DocumentationNI TestStand Quick Start GuideUse this document for system requirements andinstallation instructions. This document also contains information about the different TestStand licensing options.NI TestStand Release NotesUse this document to learn about new features and upgrade information.Using TestStandUse this manual to familiarize yourself with the TestStand environment and the basic features you use to build and run test sequences.Using LabVIEW with TestStandUse this manual in conjunction with the Using TestStand manual to learn how to use LabVIEW with ing LabWindows/CVI with TestStandUse this manual in conjunction with the Using TestStand manual to learn how to use LabWindows/CVI with TestStand.NI TestStand Reference ManualUse this manual to learn about TestStand concepts,architecture, and features.Online HelpNI TestStand HelpUse this help file to learn more about the TestStand environment and the TestStand User Interface Controls and Engine APIs. The NI TestStand Help also includes basic information about using an ActiveX automation server.NI TestStand VIs and Functions HelpUse this help file to learn more about TestStand-specific VIs and functions. This help file is accessible only from LabVIEW.Cards and PostersNI TestStand User Interface Controls Reference Poster Use this poster to learn about the controls available for writing custom user interfaces for TestStand.NI TestStand API Reference PosterUse this poster as an overview of the TestStand API. This poster lists the properties, objects, methods, and APIinheritance of the TestStand API.L i s t B a r Lists the currentlyopen sequence files and executions.S e q u e n c e F i l e W i n d o wE x e c u t i o n V i e wR e p o r t V i e wS e q u e n c e V i e wLists steps in the sequence and step group for the sequence file you select in the list bar.Displays the threads,call stack, and steps for the execution you select.Displays the report for the execution you select.Displays sequences and other items in a sequence Displays the threads,call stack, and stepsthat an execution runs.When executioncompletes, displays thereport for theexecution.User Manager WindowAdministers groups, users,login names, pass-words, and privi-leges.UsersDisplays users for the test station. Output Pane Displays output messages that expressions and code modules post to theTestStand Engine.Call Stack Pane Displays the nested sequence invocations for the thread you select.sequence editor provides familiar LabVIEW, LabWindows/CVI, and Microsoft Visual Studio .NET debugging tools, including breakpoints, single-stepping, stepping into or over function calls, tracing, a Variables pane, and a Watch View pane. In the TestStand Sequence Editor, you can start multiple concurrent executions, execute multiple instances of the same sequence, and execute different sequences at the same time. Separate Execution windows display each execution. In trace mode, the Execution window displays the steps in the currently executing sequence. When you suspend an execution, the Execution window displays the next step to execute and provides single-stepping options.Templates List Organizes custom sequences, steps,and variables you can use as templates for building sequence files.Step Settings PaneSpecifies the settings for the step, such as code module parameters, switching, flow control, and post actions.Variables Pane Displays the variables andproperties, including the values, that steps can access at run time.StepPerforms built-in operations or calls code modules.ProjectOrganizes sequence files and code module files in folders.Workspace PaneManages projects for source code control (SCC) integration and deployment. TestStand inte-grates with third-party SCC pack-ages to add files, obtain the lat-est versions of files, and check files in and out.Watch View Pane Monitors the values of specifiedvariables, properties,and expressions during an execution.Threads Pane Contains a list of threads in the current execution.Insertion Palette Displays step types and templates you can insert into sequence files.GroupsDisplays groups that users belong to.。
Skyworks Si53159 EVALUATION BOARD 用户指南说明书

Si53159-EVB Si53159 E VALUATION B OARD U SER’S G UIDEDescriptionThe Si53159 is a nine port PCIe clock buffer compliant to the PCIe Gen1, Gen2 and Gen3 standards. The Si53159 is a 48-pin QFN device that operates on a 3.3V power supply and can be controlled using SMBus signals along with hardware control input pins. The device is spread aware and accepts frequency spread differential clock frequency range from 100 to 210MHz. The connections are described in this document.EVB FeaturesThis document is intended to be used in conjunction with the Si53159 device and data sheet for the following tests:⏹PCIe Gen1, Gen2, Gen3 compliancy⏹Power consumption test⏹Jitter performance⏹Testing out I2C code for signal tuning⏹In-system validation where SMA connectors arepresent2SkyworksSolutions,Inc.•Phone[781]376-3000•Fax[781]376-3100•*********************•1. Front PanelFigure 1.Evaluation Module Front PanelTable 1. Input Jumper SettingsJumper LabelTypeDescriptionOE0I OE0, 3.3V Input for Enabling DIFF0 Clock Output .1 = DIFF0 enabled, 0 = DIFF0 disabled.OE1I OE1, 3.3V Input for Enabling DIFF1 Clock Output .1 = DIFF1 enabled, 0 = DIFF1 disabled.OE2I OE2, 3.3V Input for Enabling DIFF2 Clock Output .1 = DIFF2 enabled, 0 = DIFF2 disabled.OE3I OE3, 3.3V Input for Enabling DIFF3 Clock Output .1 = DIFF3 enabled, 0 = DIFF3 disabled.OE4/5I OE4/5, 3.3V Input for Enabling DIFF4 and DIFF5 Clock Outputs.1 = DIFF4 & DIFF5 enabled, 0 = DIFF4 & DIFF5 disabled.OE6/8I OE6/8, 3.3V Input for Enabling DIFF6, DIFF7 and DIFF8 Clock Outputs.1 = DIFF6, DIFF7 & DIFF8 enabled, 0 = DIFF6, DIFF7 & DIFF8 disabled.CLKPWGD/PDI3.3V LVTTL Input.After CLKPWGD (active high) assertion, this pin becomes a real-time input for asserting power down (active low).SDATA I/O SMBus-Compatible SDATA .SCLKISMBus-Compatible SCLOCK .SkyworksSolutions,Inc.•Phone[781]376-3000•Fax[781]376-3100•*********************• 31.1. Generating DIFF Outputs from the Si53159Upon power-on of the device if the differential input is applied and input pins are left floating, by default all DIFF outputs DIFF[0:8] are ON. The input pin headers have clear indication of jumper settings for setting logic low (0)and high (1) as shown in the figure below, the jumper placed on the middle and left pin will set input OE0 to low;and jumper placed on the middle and right pin will set input OE0 to high.The output enable pins can be changed on the fly to observe outputs stopped cleanly. Input functionality is explained in detail below. 1.1.1. OE [0:8] InputsThe output enable pins can change on the fly when the device is on. Deasserting (valid low) results in corresponding DIFF output to be stopped after their next transition with final state low/low. Asserting (valid high)results in corresponding output that was stopped are to resume normal operation in a glitch-free manner. Each of the hardware OE [0:8] pins are mapped via I 2C to control bit in Control register. The hardware pin and the Register Control Bit both need to be high to enable the output. Both of these form an “AND” function to disable or enable the DIFF output. The DIFF outputs and their corresponding I 2C control bits and hardware pins are listed in Table 2.Table 2. Output Enable ControlI2C Control BitOutput Hardware Control InputByte1 [bit 4]DIFF0OE0 Byte1 [bit 2]DIFF1OE1 Byte2 [bit 1]DIFF2OE2 Byte2 [bit 0]DIFF3OE3 Byte1 [bit 7]DIFF4OE4/5Byte1 [bit 6]DIFF5OE4/5Byte2 [bit 5]DIFF6OE6/8Byte2 [bit 4]DIFF7OE6/8Byte2 [bit 3]DIFF8OE6/82. SchematicsFigure4.Clock and Control Signals Figure5.Differential Clock Signals SCLK/SDATASkyworksSolutions,Inc.•Phone[781]376-3000•Fax[781]376-3100•*********************•5Copyright © 2021 Skyworks Solutions, Inc. All Rights Reserved.Information in this document is provided in connection with Skyworks Solutions, Inc. (“Skyworks”) products or services. These materials, including the information contained herein, are provided by Skyworks as a service to its customers and may be used for informational purposes only by the customer. Skyworks assumes no responsibility for errors or omissions in these materials or the information contained herein. Skyworks may change its documentation, products, services, specifications or product descriptions at any time, without notice. Skyworks makes no commitment to update the materials or information and shall have no responsibility whatsoever for conflicts, incompatibilities, or other difficulties arising from any future changes.No license, whether express, implied, by estoppel or otherwise, is granted to any intellectual property rights by this document. Skyworks assumes no liability for any materials, products or information provided hereunder, including the sale, distribution, reproduction or use of Skyworks products, information or materials, except as may be provided in Skyworks’ Terms and Conditions of Sale.THE MATERIALS, PRODUCTS AND INFORMATION ARE PROVIDED “AS IS” WITHOUT WARRANTY OF ANY KIND, WHETHER EXPRESS, IMPLIED, STATUTORY, OR OTHERWISE, INCLUDING FITNESS FOR A PARTICULAR PURPOSE OR USE, MERCHANTABILITY, PERFORMANCE, QUALITY OR NON-INFRINGEMENT OF ANY INTELLECTUAL PROPERTY RIGHT; ALL SUCH WARRANTIES ARE HEREBY EXPRESSLY DISCLAIMED. SKYWORKS DOES NOT WARRANT THE ACCURACY OR COMPLETENESS OF THE INFORMATION, TEXT, GRAPHICS OR OTHER ITEMS CONTAINED WITHIN THESE MATERIALS. SKYWORKS SHALL NOT BE LIABLE FOR ANY DAMAGES, INCLUDING BUT NOT LIMITED TO ANY SPECIAL, INDIRECT, INCIDENTAL, STATUTORY, OR CONSEQUENTIAL DAMAGES, INCLUDING WITHOUT LIMITATION, LOST REVENUES OR LOST PROFITS THAT MAY RESULT FROM THE USE OF THE MATERIALS OR INFORMATION, WHETHER OR NOT THE RECIPIENT OF MATERIALS HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.Skyworks products are not intended for use in medical, lifesaving or life-sustaining applications, or other equipment in which the failure of the Skyworks products could lead to personal injury, death, physical or environmental damage. Skyworks customers using or selling Skyworks products for use in such applications do so at their own risk and agree to fully indemnify Skyworks for any damages resulting from such improper use or sale.Customers are responsible for their products and applications using Skyworks products, which may deviate from published specifications as a result of design defects, errors, or operation of products outside of published parameters or design specifications. Customers should include design and operating safeguards to minimize these and other risks. Skyworks assumes no liability for applications assistance, customer product design, or damage to any equipment resulting from the use of Skyworks products outside of Skyworks’ published specifications or parameters.Skyworks, the Skyworks symbol, Sky5®, SkyOne ®, SkyBlue™, Skyworks Green™, Clockbuilder ®, DSPLL ®, ISOmodem ®, ProSLIC ®, and SiPHY ® are trademarks or registered trademarks of Skyworks Solutions, Inc. or its subsidiaries in the United States and other countries. Third-party brands and names are for identification purposes only and are the property of their respective owners. Additional information, including relevant terms and conditions, posted at , are incorporated by reference.Portfolio/ia/timingSW/HW/CBProQuality/qualitySupport & Resources/supportSkyworksSolutions,Inc.|Nasdaq:SWKS|*********************| USA: 781-376-3000 | Asia: 886-2-2735 0399 | Europe: 33 (0)1 43548540 |。
物联网中英文词汇对照表

扩大器
Amplitude-Shift Keyi ng
ASK
幅移键控
Antenna
天线
An ti-Collisio n
防碰撞
Application Family Identifier
AFI
应用系列产品识别码
Application Identifier
应用识别码
Applicati on Level Events
物联网词汇中英对照表
英文名称
英文缩与
中文翻译
The Internet of Things
IOT
物联网
1-Bit Transpon der
1位询答器
2D Matrix Code
矩阵式二维条形码
2D Sea nner
二维条形码扫描枪
2D Stacked Code
堆栈式二维条形码
Abstract Data Model Layer
GSMP
全球标准管理程序
Global Tag
GTAG
全球标准标签
Global Trade Item Number
GTIN
全球交易品项识别代码
Han dheld Reader
手持式读取器
Hash Lock
杂凑锁
Hash-cha in
杂凑链
Header
标头
Health&Life Scie nce
HLS
健康医疗产业
EPCglobal
EPCglobal Chi na
EPCglobal中国
EPCglobal Network
EPCglobal网络
Erasure Correction
《城市轨道交通供电系统工程施工质量验收规范》标准全文

量安全监督总站负责技术内容的解释。执行过程中,请各有关单位结合实际,不断总结经验,
并将发现的问题、意见和建议函告杭州市建设工程质量安全监督总站[地址:莫干山路 100 号耀江国际大厦 A 座 12 楼,邮政编码:311005],以供修订时参考。
本规范主编单位、参编单位、主要起草人和主要审查人: 本规范主编单位:杭州市建设工程质量安全监督总站
本规范共分 10 章,主要技术内容包括:1 总则;2 术语;3 基本规定;4 牵引及降压变 电所;5 刚性架空接触网;6 柔性架空接触网;7 接触轨;8 杂散电流腐蚀防护系统;9 可视 化接地系统;10 电力监控与电能质量管理系统。
本规范由浙江省住房和城乡建设厅负责管理和对强制条文的解释,由杭州市建设工程质
浙江省工程建设标准
城市轨道交通供电系统施工质量验收规范
Code for acceptance of construction quality of power supply system engineering of urban rail transit
DB33/T ××/××××-201×
主编单位:杭州市建设工程质量安全监督总站 中铁电气化局集团有限公司 中铁二局集团有限公司
中铁电气化局集团有限公司 中铁二局集团有限公司 本规范参编单位:中国电建集团华东勘测设计研究院有限公司 杭州市地铁集团有限责任公司 宁波市轨道交通集团有限公司 中铁十一局集团电务工程有限公司 中铁一局集团电务工程有限公司 浙江丽水宏瑜建设有限公司 浙江德光建筑工程有限公司 浙江瓯立园林建设有限公司 纳琦绿能工程有限公司 浙江鸿旭园林建设有限公司 浙江罗邦建设有限公司 丽水市金丰建筑工程有限公司 丽水市鼎旺建设工程有限公司 浙江瓯业园林建设有限公司 丽水市汇桦市政园林有限公司 浙江屹立建设有限公司 浙江华歌建设有限公司 本规范主要起草人:史文杰 周静增 肖国军 雷 鸣 蔡佳旻 周 军 施云琼 王祥涛 于镇川 郭润桥 唐兆军 孙海东 王海涛 左传文 郭 忠 叶波涛 徐 俊 吴赟胤 王存建 王 波 朱智文 赵加建 范 卿 韩明学 陈俊卿 周洪波 何贵龙 黄美香 潘国平 蒋 真 本规范主要审查人:石西全 赵宇宏 戴新国 游劲秋 张 燕 袁 林 刘 伟 洪秀敏
DS2208数字扫描器产品参考指南说明书

-05 Rev. A
6/2018
Rev. B Software Updates Added: - New Feedback email address. - Grid Matrix parameters - Febraban parameter - USB HID POS (formerly known as Microsoft UWP USB) - Product ID (PID) Type - Product ID (PID) Value - ECLevel
-06 Rev. A
10/2018 - Added Grid Matrix sample bar code. - Moved 123Scan chapter.
-07 Rev. A
11/2019
Added: - SITA and ARINC parameters. - IBM-485 Specification Version.
No part of this publication may be reproduced or used in any form, or by any electrical or mechanical means, without permission in writing from Zebra. This includes electronic or mechanical means, such as photocopying, recording, or information storage and retrieval systems. The material in this manual is subject to change without notice.
NI ELVIS II系列产品规格说明说明书

Arbitrary Waveform Generator/Analog Output
Number of channels.........................2
DAC resolution................................16 bits
DNL.................................................±1 LSB
Maximum working voltage for analog inputs (signal + common mode) ................ ±11 V of AIGND
CMRR (DC to 60 Hz) ..................... 90 dB
Source..............................................AI<0..15>, ScopeCH0, ScopeCH1
Small signal bandwidth (–3 dB)......1.2 MHz
Input FIFO size................................4095 samples
Scanlist memory ..............................4095 entries
Data B signal stream, programmed I/O
定位失败代码

120
CP 无第三方能力
123
124
USER REJECTION
125
MS OUT SERVICE UNSURPPORT SEVICE FORBIDDEN ORIGINATOR LOCATION UNAVIALABLE
OF
126
127
128
129
REQUEST PLATFORM ERROR MS POWER OFF LOCATION ACTIVATING FAILURE REQUEST ROAMCITY ERROR
130 131
132
无法获得在服务质量中说明的被请求时间要求 基础网络中出现故障 用户余额不足 用户欠费 移动台挂失
CP 在用户列表中完全拒绝
111 112 113 114 115
116
LCS Client Time Restricted User Pass Error Calling Time
CP 该时间段不允许
117 118
主叫用户密码错 主叫用户该时间段不允许
Restricted 119 NONE LCS Client ACCOUNT UNAUTHORIZED Third Party LCS CLIENT 121 122 SYSTEM ERROR MS FORBIDEDN IN ICP REPLY OVERTIME 系统错误 (系统内部出错) 被查手机在 ICP 的配置中禁止 被查手机在行业 ICP 的黑名单 等待用户回应超时 (查询需要用户确认时,用户超 时,未返回应答) 用户确认为拒绝查询(查询需要用户确认时,用户返 回拒绝) 用户不在服务区内(手机无信号) 不支持的服务 禁止定位 (用户查询的隐私鉴权未通过,在被查用户 的黑名单或者被查用户禁止查询) 位置服务器无法计算位置 (用户所在 CELLID 在系统 基站数据中查不出来) 请求定位平台错误 用户手机关机 定位激活失败,一般用于手机欠费或者手机隐私设置 没有设置为 不限制 获取用户所在城市信息失败
隐蔽空间下超宽带TDOA定位算法研究

隐蔽空间下超宽带 TDOA定位算法研究王佰亮,刘江波(国家粮食和物资储备局,北京 100038)摘要:针对隧道等隐蔽空间环境复杂,干扰严重,最小二乘位置解算方法定位精度低的情况,研究一种结合最小二乘(Least Square,LS)位置求解方法的BP(Back Propagation)神经网络定位算法。
首先基于超宽带(Ultra Wide Band,UWB)系统到达时间差(Time Difference Of Arrival,TDOA)利用最小二乘法进行位置解算,然后根据解算得到的初始位置进行TDOA 测量值修正,BP神经网络基于修正后的TDOA对LS定位结果进行优化。
仿真结果表明,该方法可以有效克服非视距误差影响,定位精度大幅提高,且在不同误差环境下具有一定通用性。
关键词:UWB定位;TDOA;最小二乘;BP神经网络中图分类号:TN929.5 文献标志码:A 文章编号:1673-4440(2021)03-0078-05Research on UWB TDOA Location Algorithm for Indoor,Underground and Tunnel EnvironmentsWang Bailiang, Liu Jiangbo(National Food and Strategic Reserves Administration, Beijing 100038, China)Abstract: In a complex environment with serious interference, e.g. in a tunnel, the positioning accuracy of the least square method (LS) is low. In this paper, a BP neural network location algorithm combined with least square is studied. Firstly, the least square method is used to determine the position based on the time difference of arrival (TDOA) in UWB system, and then the measured value of TDOA is modifi ed according to the initial position obtained by the LS method. The modifi ed TDOA is used by the BP neural network to get fi nal location results. The simulation results show that the infl uence of NLOS (non-line-of-sight) is reduced and the accuracy of the proposed LS-BP method is greatly improved compared with that of the LS method. The proposed LS-BP method can be applied to handle errors in certain diff erent environments.Keywords: UWB positioning; TDOA; least square; BP neural networkDOI: 10.3969/j.issn.1673-4440.2021.03.0161 概述随着国内城市化和机动化的加快,具有节能、快捷和大运量特征的城市轨道交通建设越来越受到众多城市的关注,轨道交通路网建设进程不断发展。
ipmitool relocation error

ipmitool relocation error
“ipmitool relocation error”这个错误通常意味着在尝试使用ipmitool时,系统无法找到或者正确加载所需的库或模块。
这可能是由于以下原因:
1. 所需的库或模块没有被正确安装或者加载。
在这种情况下,你需要确认所有必需的库和模块都已经被正确安装并且在系统中可用。
2. 你可能正在使用的ipmitool版本与你的系统不兼容。
你需要检查你的ipmitool版本是否与你的操作系统版本兼容。
3. 如果你在一个虚拟环境中运行这个命令,可能会因为虚拟环境不支持某些硬件级别的功能而出现这个错误。
在这种情况下,你可能需要在物理机上运行你的命令。
为了解决这个问题,你可以尝试以下步骤:
1. 确认所有必需的库和模块都已经被正确安装并且在系统中可用。
你可以使用如lsmod | grep ipmi这样的命令来检查所需的IPMI模块是否已经被加载。
2. 确保你正在使用的ipmitool版本与你的操作系统版本兼容。
你可以通过执行ipmitool -V来查看你的ipmitool版本。
3. 如果可能,尝试在物理机上而不是在虚拟环境中运行你的命令。
EACM非正常操作

MENU 非正常操作
4/38
To begin we will look at what happens when
one我or们b从oth了F解lig两ht台W飞ar行nin警g 告Co计m算pu机ter发s 生fa故il.
F障o后r a会si出ng现le什FW么C情fa况ult开a始ca。ut一ion台m计es算sa机ge故w障ill
can be cleared.
不,按压清除No键. C以le取ar 消th状e S态TA页TUS page
ECAM
MENU 非正常操作
33/38
巡航页返回到了下部ECAM屏幕显示 ,并且在E/WD上有状态字样。
在剩下的飞行中,ECAM将不会每次 都提醒你探测到的 NhomakorabeaLS1故障。
现在我们看看你如何调出被取消的警 戒。
飞机系统传感器
MENU 非正常操作
3/38
我们从了解两台飞行警告计算机发生故障 后会出现什么情况开始。一台计算机故障后 会在E/WD上显示警戒信息。注意没有兰色 的动作行,所以不需要机组采取措施。因为 不存在EIS的系统页面,所以没有系统页面 调出。
清除飞行警告系统
FWS FWC 1 FAULT
ECAM
MENU 非正常操作
13/38
ECAM
顶板上的任何警告都应该检查。可以通过 单独地选择或使用ALL按键挨个地选择以检 查系统页的非正常指示。我们按住ALL键让 你看看将出现什么情况。
注:如果ALL松开,在顺序显示过程中,
。 巡航页会被显示出来
MENU 非正常操作
14/38
ECAM
MENU 非正常操作
the STATUS page.
不,调出状态页
CMS Error codes

Send SMS with GSM Modem - CMS Error codesIf you are trying to send an SMS messages with a GSM modem, the modem can return an error code in case there is a problem. The following table lists the most common error codes.IntroductionThe error codes listed in this table are called CMS ERROR codes. Please note that CMS errors are modem specific errors, which means, the best you can do to find out what an error code means is to check your modem's manual. Of course we know, that sometimes it is hard to find the modem manual, this is why have published this information.The most common errors you will face when you want to send an SMS message are discussed in the following document: Send SMS Error Reasons. If this document does not help, take a look at the following table:CMS ERROR 1 "Unassigned (unallocated) number" This cause indicates thatthe destination requested by the Mobile Station cannot bereached because, although the number is in a valid format, it isnot currently assigned (allocated).CMS ERROR 8 "Operator determined barring" This cause indicates that theMS has tried to send a mobile originating short message whenthe MS's network operator or service provider has forbiddensuch transactions.CMS ERROR 10 "Call barred" This cause indicates that the outgoing call barredservice applies to the short message service for the calleddestination.CMS ERROR 17 "Network failure". This cause is sent to the MS if the MSCcannot service an MS generated request because of PLMNfailures, e.g. problems in MAP.CMS ERROR 21 "Short message transfer rejected" This cause indicates thatthe equipment sending this cause does not wish to accept thisshort message, although it could have accepted the shortmessage since the equipment sending this cause is neitherbusy nor incompatible.CMS ERROR 22 "Congestion". This cause is sent if the service request cannotbe actioned because of congestion (e.g. no channel, facilitybusy/congested etc.).CMS ERROR 27 "Destination out of service" This cause indicates that thedestination indicated by the Mobile Station cannot be reachedbecause the interface to the destination is not functioningcorrectly. The term "not functioning correctly" indicates that asignaling message was unable to be delivered to the remoteuser; e.g., a physical layer or data link layer failure at theremote user, user equipment off line, etc.CMS ERROR 28 "Unidentified subscriber" This cause indicates that thesubscriber is not registered in the PLMN (i.e. IMSI not known). CMS ERROR 29 "Facility rejected" This cause indicates that the facilityrequested by the Mobile Station is not supported by the PLMN. CMS ERROR 30 "Unknown subscriber" This cause indicates that the subscriberis not registered in the HLR (i.e. IMSI or directory number isnot allocated to a subscriber).CMS ERROR 38 "Network out of order" This cause indicates that the network isnot functioning correctly and that the condition is likely to lasta relatively long period of time; e.g., immediatelyreattempting the short message transfer is not likely to besuccessful.CMS ERROR 41 "Temporary failure" This cause indicates that the network isnot functioning correctly and that the condition is not likely tolast a long period of time; e.g., the Mobile Station may wish totry another short message transfer attempt almostimmediately.CMS ERROR 42 "Congestion" This cause indicates that the short messageservice cannot be serviced because of high traffic.CMS ERROR 47 "Resources unavailable, unspecified" This cause is used toreport a resource unavailable event only when no other causeapplies.CMS ERROR 50 "Requested facility not subscribed" This cause indicates thatthe requested short message service could not be provided bythe network because the user has not completed thenecessary administrative arrangem ents with its supportingnetworks.CMS ERROR 69 "Requested facility not implemented" This cause indicates thatthe network is unable to provide the requested short messageservice.CMS ERROR 81 "Invalid short message transfer reference value" This causeindicates that the equipm ent sending this cause has received amessage with a short message reference which is not currentlyin use on the MS network interface.CMS ERROR 95 "Invalid message, unspecified" This cause is used to report aninvalid message event only when no other cause in the invalidmessage class applies.CMS ERROR 96 "Invalid mandatory information" This cause indicates that theequipment sending this cause has received a message where amandatory information element is missing and/or has acontent error (the two cases are indistinguishable).CMS ERROR 97 "Message type non existent or not implemented" This causeindicates that the equipm ent sending this cause has received amessage with a message type it does not recognize eitherbecause this is a message not defined or defined but notimplemented by the equipment sending this cause.CMS ERROR 98 "Message not compatible with short message protocol state"This cause indicates that the equipment sending this cause hasreceived a message such that the procedures do not indicatethat this is a permissible message to receive while in the shortmessage transfer state.CMS ERROR 99 "Information element non existent or not implemented" Thiscause indicates that the equipment sending this cause hasreceived a message which includes information elements notrecognized because the information elem ent identifier is notdefined or it is defined but not implemented by the equipmentsending the cause. However, the information element is notrequired to be present in the message in order for theequipment sending the cause to process the message.CMS ERROR 111 "Protocol error, unspecified" This cause is used to report aprotocol error event only when no other cause applies.CMS ERROR 127 "Interworking, unspecified" This cause indicates that there hasbeen interworking with a network which does not providecauses for actions it takes; thus, the precise cause for amessage which is being send cannot be ascertained.CMS ERROR 128 Telematic interworking not supported xCMS ERROR 129 Short message Type 0 not supported x xCMS ERROR 130 Cannot replace short message x xCMS ERROR 143 Unspecified TP PID error x xCMS ERROR 144 Data coding scheme (alphabet) not supported xCMS ERROR 145 Message class not supported xCMS ERROR 159 Unspecified TP DCS error x xCMS ERROR 160 Command cannot be actioned xCMS ERROR 161 Command unsupported xCMS ERROR 175 Unspecified TP Command error xCMS ERROR 176 TPDU not supported x xCMS ERROR 192 SC busy xCMS ERROR 193 No SC subscription xCMS ERROR 194 SC system failure xCMS ERROR 195 Invalid SME address xCMS ERROR 196 Destination SME barred xCMS ERROR 197 SM Rejected Duplicate SM xCMS ERROR 198 TP VPF not supported XCMS ERROR 199 TP VP not supported XCMS ERROR 208 SIM SMS storage full xCMS ERROR 209 No SMS storage capability in SIM xCMS ERROR 210 Error in MS xCMS ERROR 211 Memory Capacity Exceeded XCMS ERROR 212 SIM Application Toolkit Busy x xCMS ERROR 255 Unspecified error cause128...255 Other values in this range are reserved, defined by GSM 03.40subclause 9.2.3.22 valuesCMS ERROR 300 ME failureCMS ERROR 301 SMS service of ME reservedCMS ERROR 302 operation not allowedCMS ERROR 303 operation not supportedCMS ERROR 304 invalid PDU mode parameterCMS ERROR 305 invalid text mode parameterCMS ERROR 310 SIM not insertedCMS ERROR 311 SIM PIN requiredCMS ERROR 312 PH SIM PIN requiredCMS ERROR 313 SIM failureCMS ERROR 314 SIM busyCMS ERROR 315 SIM wrongCMS ERROR 316 SIM PUK requiredCMS ERROR 317 SIM PIN2 requiredCMS ERROR 318 SIM PUK2 requiredCMS ERROR 320 memory failureCMS ERROR 321 invalid memory indexCMS ERROR 330 SMSC address unknownCMS ERROR 331 no network serviceCMS ERROR 332 network timeoutCMS ERROR 340 no +CNMA acknowledgement expectedCMS ERROR 500 unknown error256...511 Other values in this range are reserved 512... manufacturer specificHere are the m ost common CMS errors:CMS ERROR: 1 Unassigned numberCMS ERROR: 8 Operator determined barringCMS ERROR: 10 Call baredCMS ERROR: 21 Short m essage transfer rejectedCMS ERROR: 27 Destination out of serviceCMS ERROR: 28 Unindentified subscriberCMS ERROR: 29 Facility rejectedCMS ERROR: 30 Unknown subscriberCMS ERROR: 38 Network out of orderCMS ERROR: 41 Temporary failureCMS ERROR: 42 CongestionCMS ERROR: 47 Recources unavailableCMS ERROR: 50 Requested facility not subscribedCMS ERROR: 69 Requested facility not im plementedCMS ERROR: 81 Invalid short m essage transfer reference valueCMS ERROR: 95 Invalid m essage unspecifiedCMS ERROR: 96 Invalid m andatory informationCMS ERROR: 97 Message type non existent or not im plementedCMS ERROR: 98 Message not com patible with short m essage protocol CMS ERROR: 99 Information element non-existent or not im plemente CMS ERROR: 111 Protocol error, unspecifiedCMS ERROR: 127 Internetworking , unspecifiedCMS ERROR: 128 Telem atic internetworking not supportedCMS ERROR: 129 Short m essage type 0 not supportedCMS ERROR: 130 Cannot replac e short m essageCMS ERROR: 143 Unspecified TP-PID errorCMS ERROR: 144 Data code schem e not supportedCMS ERROR: 145 Message class not supportedCMS ERROR: 159 Unspecified TP-DCS errorCMS ERROR: 160 Command cannot be actionedCMS ERROR: 161 Command unsupportedCMS ERROR: 175 Unspecified TP-Command errorCMS ERROR: 176 TPDU not supportedCMS ERROR: 192 SC busyCMS ERROR: 193 No SC subscriptionCMS ERROR: 194 SC System failureCMS ERROR: 195 Invalid SME addressCMS ERROR: 196 Destination SME barredCMS ERROR: 197 SM Rejected-Duplicate SMCMS ERROR: 198 TP-VPF not supportedCMS ERROR: 199 TP-VP not supportedCMS ERROR: 208 D0 SIM SMS Storage fullCMS ERROR: 209 No SMS Storage capability in SIMCMS ERROR: 210 Error in MSCMS ERROR: 211 Memory capacity exceededCMS ERROR: 212 Sim application toolkit busyCMS ERROR: 213 SIM data download errorCMS ERROR: 255 Unspecified error causeCMS ERROR: 300 ME FailureCMS ERROR: 301 SMS service of ME reservedCMS ERROR: 302 Operation not allowedCMS ERROR: 303 Operation not supportedCMS ERROR: 304 Invalid PDU mode parameterCMS ERROR: 305 Invalid Text mode parameterCMS ERROR: 310 SIM not insertedCMS ERROR: 311 SIM PIN requiredCMS ERROR: 312 PH-SIM PIN requiredCMS ERROR: 313 SIM failureCMS ERROR: 314 SIM busyCMS ERROR: 315 SIM wrongCMS ERROR: 316 SIM PUK requiredCMS ERROR: 317 SIM PIN2 requiredCMS ERROR: 318 SIM PUK2 requiredCMS ERROR: 320 Memory failureCMS ERROR: 321 Invalid memory indexCMS ERROR: 322 Memory fullCMS ERROR: 330 SMSC address unknownCMS ERROR: 331 No network serviceCMS ERROR: 332 Network tim eoutCMS ERROR: 340 No +CNMA expectedCMS ERROR: 500 Unknown errorCMS ERROR: 512 User abortCMS ERROR: 513 Unable to storeCMS ERROR: 514 Invalid StatusCMS ERROR: 515 Device busy or Invalid Character in string CMS ERROR: 516 Invalid lengthCMS ERROR: 517 Invalid character in PDUCMS ERROR: 518 Invalid parameterCMS ERROR: 519 Invalid length or characterCMS ERROR: 520 Invalid character in textCMS ERROR: 521 Timer expiredCMS ERROR: 522 Operation tem porary not allowedCMS ERROR: 532 SIM not readyCMS ERROR: 534 Cell Broadcast error unknownCMS ERROR: 535 Protocol stack busyCMS ERROR: 538 Invalid parameterCME (GSM Equipment Related) errorsHere are the m ost common CME errors:CME ERROR: 0 Phone failureCME ERROR: 1 No connection to phoneCME ERROR: 2 Phone adapter link reservedCME ERROR: 3 Operation not allowedCME ERROR: 4 Operation not supportedCME ERROR: 5 PH_SIM PIN requiredCME ERROR: 6 PH_FSIM PIN requiredCME ERROR: 7 PH_FSIM PUK requiredCME ERROR: 10 SIM not insertedCME ERROR: 11 SIM PIN requiredCME ERROR: 12 SIM PUK requiredCME ERROR: 13 SIM failureCME ERROR: 14 SIM busyCME ERROR: 15 SIM wrongCME ERROR: 16 Incorrect passwordCME ERROR: 17 SIM PIN2 requiredCME ERROR: 18 SIM PUK2 requiredCME ERROR: 20 Memory fullCME ERROR: 21 Invalid indexCME ERROR: 22 Not foundCME ERROR: 23 Memory failureCME ERROR: 24 Text string too longCME ERROR: 25 Invalid characters in text stringCME ERROR: 26 Dial string too longCME ERROR: 27 Invalid characters in dial stringCME ERROR: 30 No network serviceCME ERROR: 31 Network tim eoutCME ERROR: 32 Network not allowed, emergency calls only CME ERROR: 40 Network personalization PIN requiredCME ERROR: 41 Network personalization PUK requiredCME ERROR: 42 Network subset personalization PIN required CME ERROR: 43 Network subset personalization PUK requiredCME ERROR: 44 Service provider personalization PIN required CME ERROR: 45 Service provider personalization PUK required CME ERROR: 46 Corporate personalization PIN requiredCME ERROR: 47 Corporate personalization PUK requiredCME ERROR: 48 PH-SIM PUK requiredCME ERROR: 100 Unknown errorCME ERROR: 103 Illegal MSCME ERROR: 106 Illegal MECME ERROR: 107 GPRS services not allowedCME ERROR: 111 PLMN not allowedCME ERROR: 112 Location area not allowedCME ERROR: 113 Roaming not allowed in this location area CME ERROR: 126 Operation tem porary not allowedCME ERROR: 132 Service operation not supportedCME ERROR: 133 Requested service option not subscribed CME ERROR: 134 Service option tem porary out of order CME ERROR: 148 Unspecified GPRS errorCME ERROR: 149 PDP authentication failureCME ERROR: 150 Invalid m obile classCME ERROR: 256 Operation tem porarily not allowedCME ERROR: 257 Call barredCME ERROR: 258 Phone is busyCME ERROR: 259 User abortCME ERROR: 260 Invalid dial stringCME ERROR: 261 SS not executedCME ERROR: 262 SIM BlockedCME ERROR: 263 Invalid blockCME ERROR: 772 SIM powered down。
拒绝手机垃圾的英语作文

In the modern era, smartphones have become an integral part of our daily lives, providing us with a wealth of information and convenience. However, they also come with a significant downside: the proliferation of mobile phone spam. This essay aims to discuss the reasons behind the prevalence of mobile phone spam and suggest some strategies to combat it.Firstly, the widespread use of smartphones has made it easier for spammers to reach a large audience. With billions of users worldwide, mobile phones have become a prime target for advertisers and scammers alike. The anonymity provided by the internet also allows spammers to send out unsolicited messages without fear of immediate consequences.Secondly, the low cost of sending spam messages contributes to the problem. Unlike traditional advertising methods, which can be expensive, sending a spam message via SMS or email is relatively cheap. This low cost encourages spammers to send out a large volume of messages, hoping that a small percentage of recipients will respond.Moreover, the lack of effective regulation and enforcement against mobile phone spam exacerbates the issue. In many countries, there are either no laws or weak regulations in place to combat spam. This lack of legal framework allows spammers to operate with impunity.To address the problem of mobile phone spam, several measures can be taken. Firstly, users should be educated on how to identify and avoid spam messages. This includes not clicking on suspicious links, not providing personal information to unknown sources, and using spam filters on their devices.Secondly, mobile service providers should take a more proactive role in combating spam. They can implement stricter policies on the sending of unsolicited messages and collaborate with law enforcement agencies to identify and prosecute spammers. Thirdly, governments should establish and enforce strong antispam laws. These laws should include penalties for spammers, as well as provisions for compensation for victims of spam. By creating a legal deterrent, governments can discourage potential spammers from engaging in this activity.In conclusion, mobile phone spam is a growing problem that affects millions of users worldwide. By understanding the reasons behind its prevalence and taking appropriate measures, we can work towards a cleaner and safer mobile communication environment.It is essential for individuals, service providers, and governments to join forces in the fight against mobile phone spam.。
GSM未接通代码

GSM未接通代码GSM未接通代码解释1 Normal class1.1 Cause No. 1 "unassigned (unallocated) number"(未分配的号码)This cause indicates that the destination requested by the mobile station cannot be reached because, although the number is in a valid format, it is not currently assigned (allocated).1.2 Cause No. 3 "no route to destination"(目的地无路由)This cause indicates that the called user cannot be reached because the network through which the call has been routed does not serve the destination desired.1.3 Cause No. 6 "channel unacceptable"(信道无法接受)This cause indicates the channel most recently identified is not acceptable to the sending entity for use in this call.1.4 Cause No. 8 "operator determined barring"(操作者定义禁止)This cause indicates that the MS has tried to access a service that the MS's network operator or service provider is not prepared to allow.1.5 Cause No.16 "normal call clearing"(正常的呼叫清除)This cause indicates that the call is being cleared because one of the users involved in the call has requested that the call be cleared.Under normal situations, the source of this cause is not the network.1.6 Cause No.17 "user busy"(用户忙)This cause is used when the called user has indicated the inability to accept another call.It is noted that the user equipment is compatible with the call.1.7 Cause No. 18 "no user responding"(用户无响应)This cause is used when a user does not respond to a call establishment message with either an alerting or connect indication within the prescribed period of time allocated (defined by the expiry of either timer T303 or T310).1.8 Cause No. 19 "user alerting, no answer"(用户振铃,无应答)This cause is used when a user has provided an alerting indication but has not provided a connect indication within a prescribed period of time.1.9 Cause No. 21 "call rejected"(呼叫拒绝)This cause indicates that the equipment sending this cause does not wish to accept this call, although it could have accepted the call because the equipment sending this cause is neither busy nor incompatible.1.10 Cause No. 22 "number changed"(号码变换)This cause is returned to a calling mobile station when the called party number indicated by the calling mobile station is no longer assigned. The new called party number may optionally be included in the diagnostic field. If a network does not support this capability, cause No. 1 "unassigned (unallocated) number" shall be used.1.11 Cause No. 26 "non-selected user clearing"(未选择的用户清除)Not supported. Treated as cause no. 31.1.12 Cause No. 27 "destination out of order"(目的端命令超出)This cause indicates that the destination indicated by themobile station cannot be reachedbecause the interface to the destination is not functioning correctly. The term "not functioning correctly" indicates that a signalling message was unable to be delivered to the remote u ser; e.g.,a physical layer or data link layer failure at the remote user, user equipment off-line, etc.1.13 Cause No. 28 "invalid number format (incomplete number)"(非法的号码格式(不完整的号码)This cause indicates that the called user cannot be reached because the called party number is not a valid format or is not complete.1.14 Cause No. 29 "facility rejected"(设备拒绝)This cause is returned when a facility requested by user can not be provided by the network.1.15 Cause No. 30 "response to STATUS ENQUIRY"(响应STATUS ENQUIRY)This cause is included in STATUS messages if the message is sent in response to a STATUS ENQUIRY message. See also section 5.5.3.1.16 Cause No. 31 "normal, unspecified"(一般,未定义)This cause is used to report a normal event only when no other cause in the normal class applies.2 Resource unavailable class2.1 Cause No. 34 "no circuit/channel available"(无电路/信道可用)This cause indicates that there is no appropriate circuit/channel presently available to handle the call.2.2 Cause No. 38 "network out of order"(网络命令超出)This cause indicates that the network is not functioningcorrectly and that the condition is likely to last a relatively long period of time; e.g., immediately re-attempting the call is not likely to be successful.2.3 Cause No. 41 "temporary failure"(临时失败)This cause indicates that the network is not functioning correctly and that the condition is not likely to last a long period of time; e.g., the mobile station may wish to try another call attempt almost immediately.2.4 Cause No. 42 "switching equipment congestion"(交换设备拥塞)This cause indicates that the switching equipment generating this cause is experiencing a period of high traffic.2.5 Cause No. 43 "access information discarded"(接入信息丢弃)This cause indicates that the network could not deliver access information to the remote user as requested; i.e., a user-to-user information, low layer compatibility, high layer compatibility, or sub-address as indicated in the diagnostic.It is noted that the particular type of access information discarded is optionally included in the diagnostic.2.6 Cause No. 44 "requested circuit/channel not available"(请求的电路/信道不可用)This cause is returned when the circuit or channel indicated by the requesting entity cannot be provided by the other side of the interface.2.7 Cause No. 47 "resource unavailable, unspecified"(资源不可用,未定义)This cause is used to report a resource unavailable event only when no other cause in the resource unavailable class applies.3 Service or option not available class3.1 Cause No. 49 "quality of service unavailable"(业务质量(QOS)不可用)This cause indicates to the mobile station that the requested quality of service, as defined inCCITT Recommendation X.213, cannot be provided.3.2 Cause No. 50 "Requested facility not subscribed"(请求的设备未预定)This cause indicates that the requested supplementary service could not be provided by the network because the user has no completed the necessary administrative arrangements with its supporting networks.3.3 Cause No. 55 "Incoming calls barred within the CUG"(在CUG中来话禁止)This cause indicates that although the called party is a member of the CUG for the incoming CUG call, incoming calls are not allowed within this CUG.3.4 Cause No. 57 "bearer capability not authorized"(承载能力未授权)This cause indicates that the mobile station has requested a bearer capability which is implemented by the equipment which generated this cause but the mobile station is not authorized to use.3.5 Cause No. 58 "bearer capability not presently available"(承载能力当前不可用)This cause indicates that the mobile station has requested a bearer capability which is implemented by the equipment which generated this cause but which is not available at this time.3.6 Cause No. 63 "service or option not available, unspecified"(业务或选件不可用,未定义)This cause is used to report a service or option not available event only when no othercause in the service or option not available class applies.3.7 Cause No. 68 "ACM equal to or greater than ACMmax"(ACM大于等于ACM最大值)This cause is used by the mobile to indicate that call clearing is due to ACM (累计呼叫次数)being greater than or equal to ACMmax.4 Service or option not implemented class4.1 Cause No. 65 "bearer service not implemented"(承载业务无法实现)This cause indicates that the equipment sending this cause does not support the bearer capability requested.4.2 Cause No. 69 "Requested facility not implemented"(请求的设备不可执行)This cause indicates that the equipment sending this cause does not support the requested supplementary service.4.3 Cause No. 70 "only restricted digital information bearer capability is available"(有限的数字承载能力可用)This cause indicates that one equipment has requested an unrestricted bearer service, but that the equipment sending this cause only supports the restricted version of the requested bearer capability.4.4 Cause No. 79 "service or option not implemented, unspecified"(业务或选项不可执行,未定义)This cause is used to report a service or option not implemented event only when no other cause in the service or option not implemented class applies.5 Invalid message (e.g., parameter out of range) class5.1 Cause No. 81 "invalid transaction identifier value"(无效的传送标识符)This cause indicates that the equipment sending this cause has received a message with a transaction identifier which is notcurrently in use on the MS-network interface.5.2 Cause No. 87 "user not member of CUG"(用户非CUG成员)This cause indicates that the called user for the incoming CUG call is not a member of the specified CUG.5.3 Cause No. 88 "incompatible destination"(矛盾的目的地)This cause indicates that the equipment sending this cause has received a request to establish a call which has low layer compatibility, high layer compatibility, or other compatibility attributes(e.g., data rate) which cannot be accommodated.5.4 Cause No. 91 "invalid transit network selection"(无效的传输网络选择)For further study. Treated as cause no. 95.5.5 Cause No. 95 "semantically incorrect message"(语义错误消息)This cause is used to report receipt of a message with semantically incorrect contents (see section 8.8).6 Protocol error (e.g., unknown message) class6.1 Cause No. 96 "invalid mandatory information"(无效的强制消息)This cause indicates that the equipment sending this cause has received a message with a non-semantical mandatory IE error (see section 8.5).6.2 Cause No. 97 "message type non-existent or not implemented"(消息类型不存在或不可实现)This cause indicates that the equipment sending this cause has received a message with a message type it does not recognize either because this is a message not defined, or defined but not implemented by the equipment sending this6.3 Cause No. 98 "message type not compatible with protocol state"(消息类型与协议状态不一致)This cause indicates that the equipment sending this cause has received a message not compatible with the protocol state (section 8.4).6.4 Cause No. 99 "information element non-existent or not implemented"(消息元素不存在或不可执行)This cause indicates that the equipment sending this cause has received a message which includes information elements not recognized because the information element identifier is not defined or it is defined but not implemented by the equipment sending the cause. However, the information element is not required to be present in the message in order for the equipment sending the cause to process the message.6.5 Cause No. 100 "conditional IE error"(有条件的IE错)This cause indicates that the equipment sending this cause has received a message with conditional IE errors (see section 8.7.2).6.6 Cause No. 101 "message not compatible with protocol state"(消息与协议状态不兼容)This cause indicates that a message has been received which is incompatible with the protocol state or that a STATUS message has been received indicating an incompatible call state.6.7 Cause No. 102 "recovery on timer expiry"(定时器超时恢复)This cause indicates that a procedure has been initiated by the expiry of a timer in association with TS 04.08 error handling procedures.6.8 Cause No. 111 "protocol error, unspecified"(协议错误,This cause is used to report a protocol error event only when no other cause in the protocol error class applies.7 Interworking class7.1 Cause No. 127 "interworking, unspecified"(互联,未定义)This cause indicates that there has been interworking with a network which does not providecauses for actions it takes; thus, the precise cause for a message which is being sent cannot be ascertained.。
eterm常见错误代码

希望大家一起参与写下自己遇见的错误代码谢谢!!ETRY电子票重出票指令,适用于各种原因(比如系统传输等问题)导致电子票出票失败时,在出票当天重新出票。
希望大家一起参与写下自己遇见的错误代码谢谢!!有些情况下,是无法使用该指令的。
典型的几种错误提示如下:●CAN NOT RETRY THIS PNR. ETDZ FIRST说明:该PNR没有执行ETDZ指令● RMK CA/XXXXX NOT FOU ND. PNR MISMATCH说明:没有返回ICS PNR(航空公司大编码)● PNR TICKETED说明:该PNR已被出票● CAN NOT RETRAY THIS ET, TICKET IS OUT OF DATE说明:该ET票不是当天销售的● ACTION说明:行动代码不正确● AIRLINE说明:航空公司代码不正确● AMOUNT 说明:数量,通常指FC、FN中的票价输入不正确● AUTHORITY说明:权限问题● CASH COLLECTION 说明:FN中缺少SCNY项● CONTACT ELEMENT MISSING说明:缺少联系组,将旅客的联系电话输入到PNR中● CURRENCY说明:货币代码不正确● DATE说明:输入的日期不正确.● DEVICE说明:打票机序号不正确● DUP ID说明:PNR中某项重复,或缺少旅客标识14● ELE NBR说明:序号不正确● FLT NUMBER说明:航班号不正确● FORMAT说明:输入格式不正确● ILLEGAL说明:不合法● INACTIVE说明:检查打票机各项状态,一般体现在没有进工作号● INFANT说明:缺少婴儿标识● INPUT说明:打票机的输入状态● INVALID CHAR说明:存在非法字符,或终端参数设置有误● ITINERARY DOES NOT MATCH FC说明:FC与PNR中的航程不符● MANUAL说明:手工出票● MAX TIM E FOR EOT - IGNORE PNR AND RESTART说明:建立了航段组,但未封口的时间超过5分钟,这时系统内部已经做了IG,将座位还原,营业员应做IG,并重新建立PNR● NAME LENGTH说明:姓名超长或姓氏少于两个字符● NAMES说明:PNR中缺少姓名项● NO DISPLAY说明:没有显示● NO NAME CHANGE FOR MU/Y说明:某航空公司不允许修改姓名● NO QUEUE说明:说明该部门此类信箱不存在● OFFICE说明:部门代号不正确● OUTPUT说明:打票机的输出状态18● PENDING说明:表示有未完成的旅客订座PNR,在退号前必须完成或放弃它。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
II.
MEASUREMENT MODEL
The network considered consists of N fixed stations (FSs) whose locations are known as ( xi , yi , zi ), i = 1, 2, ..., N , and a number of mobile stations (MSs) whose locations are to be determined. The unknown three dimensional coordinates of the MS of interest are denoted by ( x, y , z ) . The Euclidean distance between FS i and the MS is given by
NLOS Error Mitigation for Mobile Location Estimation in Wireless Networks
Kegen Yu
Wireless Technologies Laboratory CSIRO ICT Centre Marsfield NSW 2122, Australia Email: Kegen.Yu@csiro.au
ቤተ መጻሕፍቲ ባይዱY. Jay Guo
Wireless Technologies Laboratory CSIRO ICT Centre Marsfield NSW 2122, Australia Email: Jay.Guo@csiro.au either directly employs the existing propagation models or empirically develops a model based on experimental results. Then, statistical estimation/detection theory is applied. Similarly, the error statistics based method [13]-[16] assumes that the NLOS error has certain distribution. On the other hand, the database based method [9], [17], [18] makes use of a signature database established a priori through an extensive survey. When the MS is to be located, some measurements are performed and results are forwarded to the location server in which the MS location is estimated by comparing the measured data with the recorded fingerprints. In this paper we first propose an efficient method to reduce the NLOS effect in the event that both the LOS and NLOS measurements are required to produce a position estimate. By assuming the knowledge of the NLOS measurements, a simple Taylor series (TS) based least-square (LS) algorithm is developed. Compared to the constrained optimization method, the proposed TS-LS algorithm has a substantially reduced complexity [19] even accounting for the extra complexity incurred due to the NLOS identification, and achieves a better location accuracy on average. Although the NLOS identification is not dealt with in the paper, several existing techniques [1], [2], [4] may be employed. Additionally, the optimal location estimator is derived when the measurement noise is Gaussian and the NLOS error is Rayleigh distributed. The optimal estimator produces an excellent performance reference. The remainder of the paper is organized as follows. In section II the measurement model is defined. In section III the proposed TS-LS algorithm is described. In section IV the maximum log likelihood estimator is studied, which serves as a performance benchmark. In section V some simulation results are presented for performance evaluation and comparisons.
Abstract—Most radio positioning methods are based on the measurements of distance between different wireless nodes. Owing to the existence of non-line-of-sight (NLOS) radio propagation, unfortunately, not all the measured distances are reliable. One way to tackle the problem of positioning is therefore to take two-steps: (i) identifying the NLOS measurements; (ii) smart signal processing of the mixed LOS and NLOS measurements. This paper is focused on the second issue. Under the assumption that the NLOS measurements have been identified, we first propose a simple method to suppress the effect of the NLOS error. Simulation results demonstrate that the proposed method achieves similar or better accuracy than several other known methods and the computational complexity is reduced considerably. We also present an optimal location estimator under the assumption of Gaussian distributed measurement noise and Rayleigh distributed NLOS error. Although it is difficult to achieve the optimal performance in practice due to modeling uncertainties, the optimal estimator provides a performance benchmark. Keywords---mobile location; NLOS error mitigation; Taylorseries LS estimator; optimal estimator; wireless networks.
I. INTRODUCTION Position location and tracking is an important issue for many applications and services. Police and other personnel need the location information to provide emergency assistance. When a vehicle is stolen or even a pet is lost, it can be readily found if its location can be determined. In healthcare, doctors and nurses need to know where their patients are so that services can be given in time. In factories, construction fields, hospitals and offices, it is often necessary to know the location of the tools, material and assets in general. One main error source in radio positioning is the NLOS signal propagation, which makes a signal travels an extra time/distance from a transmitter to a receiver. Complete removal of the NLOS impact may be impractical; however, various methods have been proposed to mitigate the impact. The residual based approach [1]-[4] basically relies on a large number of measurements which are grouped into subsets. Location estimates from each subset of measurements are evaluated by its residual. The final location estimate is obtained either by weighting the different results or by only using some selected measurements. The constrained optimization method [5-7] exploits optimization techniques [8] and geometrical constraints. The propagation model based method [9]-[12]
