2009年全国硕士研究生入学考试计算机统考真题参考答案
2009研究生入学考试计算机网络试题及答案

研究生入学考试计算机网络试题及答案一、是非题(请在括号内,正确的划√,错误的划×)(每个2分,共20分)1.所有以太网交换机端口既支持10BASE-T标准,又支持100BASE-T标准。
()2.Ethernet、Token Ring与FDDI是构成虚拟局域网的基础。
()3.ATM既可以用于广域网,又可以用于局域网,这是因为它的工作原理与Ethernet基本上是相同的。
()4.Windows操作系统各种版本均适合作网络服务器的基本平台。
()5.局域网的安全措施首选防火墙技术。
()6.帧中继的设计主要是以广域网互连为目标。
()7.应用网关是在应用层实现网络互连的设备。
()8.双绞线是目前带宽最宽、信号传输衰减最小、抗干扰能力最强的一类传输介质。
()9.PPP(Point-to-Point Protocol,点到点协议)是一种在同步或异步线路上对数据包进行封装的数据链路层协议,早期的家庭拨号上网主要采用SLIP协议,而现在更多的是用PPP协议。
()10.如果多台计算机之间存在着明确的主/从关系,其中一台中心控制计算机可以控制其它连接计算机的开启与关闭,那么这样的多台计算机就构成了一个计算机网络。
()参考答案:1、× 2、√ 3、× 4、× 5、√ 6、√ 7、√ 8、× 9、√ 10、×二、单选题和多选题(除题目特殊说明是多选题外,其他均为单选题。
每空2分,共40分)1.(4选2)网络按通信方式分类,可分为()和()。
A. 点对点传输网络B. 广播式传输网络C. 数据传输网络D. 对等式网络2.能实现不同的网络层协议转换功能的互联设备是()。
A. 集线器B. 交换机C. 路由器D. 网桥3.路由器(Router)是用于联接逻辑上分开的()网络。
4.(4选2)计算机网络完成的基本功能是()和()。
A. 数据处理B. 数据传输C. 报文发送D. 报文存储5. (4选2)计算机网络的安全目标要求网络保证其信息系统资源的完整性、准确性和有限的传播范围,还必须保障网络信息的()、(),以及网络服务的保密性。
2009年计算机科学与技术学科联考计算机学科专业基础综合考研真题

则该排序 算法只 能是______ 。
A.起泡排序
B. 插入排 序
C.选择 排序
D .二路 归并排 序
11. 冯•诺依曼计算机中指令和数据均以二进制形式存放在存储器中, CPU 区分它们的依据是
。
A .指令操作 码的译 码结果
B.指 令和数 据的寻 址方式
C. 指令周 期的不 同阶段
D.指 令和数 据所在 的存储 单元
。
A.1
B. 2
C. 3
D.4
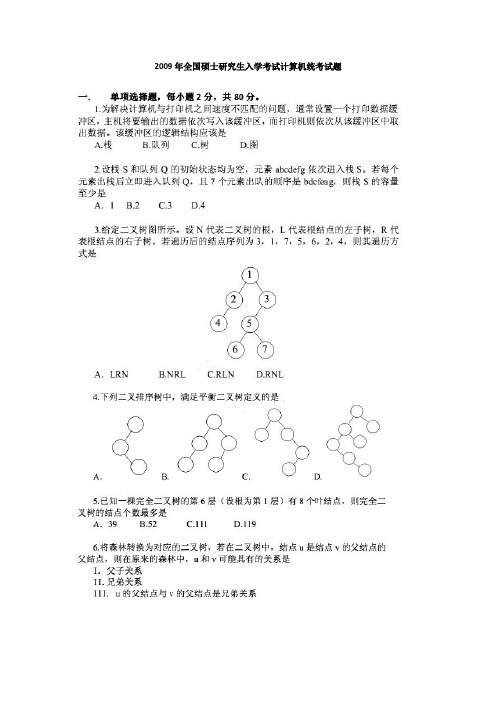
3. 给定二叉树如右图所示。设 N 代表二叉树的根,L 代表根结点的左子树,R 代表根结
点的右子树。若遍历后的结点序列是 3,1,7,5,6,2,4,则其遍历方式是
。
A.LRN
B.NRL
C . RLN
D . RN L
4. 下列二叉排序树中,满足平衡二叉树定义的是______。
Ⅰ.父子 关系
Ⅱ. 兄弟关 系
Ⅲ.u 的父结点与 v 的父结点是兄弟关系
A. 只有Ⅱ
B.Ⅰ和 Ⅱ
C. Ⅰ和Ⅲ
D.Ⅰ 、Ⅱ和 Ⅲ
7. 下列关于无向连通图特性的叙述中,正确的是______。
I. 所有顶点的度之和为偶数
II. 边数大于顶点个数减 1
III. 至少有一个顶点的度为 1
A. 只有Ⅰ B.只有Ⅱ C.Ⅰ和Ⅱ
12. 一个 C 语言程序在一台 32 位机器上运行。程序中定义了三个变量 x、y 和 z,其中 x 和 z 为 int 型,y 为 short
型。当 x=127,y=-9 时,执行赋值语句 z=x+y 后,x、y 和 z 的值分别是
。
A . x= 0000007F H,y= FF F9 H, z=00000076H
2009年408真题及答案解析

。
A.0
B.1
C. 4
D. 6
15. 某计算机主存容量为 64KB,其中 ROM 区为 4KB,其余为 RAM 区,按字节编址。现要用 2K×8 位的 ROM
芯片和 4K×4 位的 RAM 芯片来设计该存储器,则需要上述规格的 ROM 芯片数和 RAM 芯片数分别
是
。
A .1、 15
B.2、15
C.1、30
30. 文件系统中,文件访问控制信息存储的合理位置是______。
A.文件控制块 B.文件分配表
C.用户口令表 D.系统注册表
31. 设文件 F1 的当前引用计数值为 1,先建立 F1 的符号链接(软链接)文件 F2,再建立 F1 的硬链接文件 F3,
然后删除 F1。此时,F2 和 F3 的引用计数值分别是______。
24. 下列进程调度算法中,综合考虑进程等待时间和执行时间的是______。
A .时间片轮 转调度 算法
B. 短进程 优先调 度算法
C. 先来先 服务调 度算法
D.高 响应比 优先调 度算法
25. 某计算机系统中有 8 台打印机,由 K 个进程竞争使用,每个进程最多需要 3 台打印机。该系统可能会发生
播速度是 200 000km/s 。若最小数据帧长度减少 800 比特,则最远的两个站点之间的距离至少需要______。
A.增加 160m
B.增加 80m
C.减少 160m
D.减少 80m
38. 主机甲与主机乙之间已建立一个 TCP 连接,主机甲向主机乙发送了两个连续的 TCP 段,分别包含 300 字 节和 500 字节的有效载荷,第一个段的序列号为 200,主机乙正确接收到两个段后,发送给主机甲的确认 序列号是______。
2009统考计算机考研试题【3】

2009统考计算机考研试题【3】(1) 依次访问上述三个虚地址,各需多少时间?给出计算过程。
(2) 基于上述访问序列,虚地址1565H的物理地址是多少?请说明理由。
47.(9分)某公司网络拓扑图如下图所示,路由器R1通过接口E1、E2分别连接局域网1、局域网2,通过接口L0连接路由器R2,并通过路由器R2连接域名服务器与互联网。
R1的L0接口的IP地址是202.118.2.1;R2的L0接口的IP地址是202.118.2.2,L1接口的IP地址是130.11.120.1,E0接口的IP地址是202.118.3.1;域名服务器的IP地址是202.118.3.2。
将IP地址空间202.118.1.0/24划分为两个子网,分配给局域网1、局域网2,每个局域网分配的地址数不少于120个,请给出子网划分结果。
说明理由或给出必要的计算过程。
请给出R1的路由表,使其明确包括到局域网1的路由、局域网2的路由、域名服务器的主机路由和互联网的路由。
请采用路由聚合技术,给出R2到局域网1和局域网2的路由。
2009年计算机统考真题参考答案一. 选择题1 2 3 4 5 6 7 8 9 10B C D B C B A D A B11 12 13 14 15 16 17 18 19 20C D D C D C A A D B21 22 23 24 25 26 27 28 29 30D A D D C A C B A A31 32 33 34 35 36 37 38 39 40B A B BC AD D C A1.为解决计算机与打印机之间速度不匹配的问题,通常设置一个打印数据缓冲区,该缓冲区的逻辑结构应该是(队列)栈的定义:栈是只准在表尾进行插入和删除的线性表,称为LIOFO(即后进先出表)。
允许插入和删除的一端叫栈顶,另一端叫栈底。
队列的定义:队列是允许在一端进行插入而在另一端进行删除的线性表。
允许插入的一端称为队尾,允许删除的一端称为队头。
2009年全国硕士研究生入学统一考试真题加答案

2009年全国硕士研究生入学统一考试英语试题Section I Use of EnglishDirections:Read the following text. Choose the best word(s) for each numbered blank and mark A, B, C or D on ANSWER SHEET 1. (10 points)Research on animal intelligence always makes me wonder just how smart humans are.1 the fruit-fly experiments described in Carl Zimmer‘s piece in the Science Times on Tuesday. Fruit flies who were taught to be smarter than the average fruit fly 2 to live shorter lives. This suggests that 3 bulbs burn longer, that there is an 4 in not being too terrifically bright.Intelligence, it 5 out, is a high-priced option. It takes more upkeep, burns more fuel and is slow 6 the starting line because it depends on learning — a gradual 7 — instead of instinct. Plenty of other species are able to learn, and one of the things they‘ve apparently learned is when to 8 .Is there an adaptive value to 9 intelligence? That‘s the question behind this new research. I like it. Instead of casting a wistful glance 10 at all the species we‘ve left in the dust I.Q.-wise, it implicitly asks what the real11 of our own intelligence might be. This is 12 the mind of every animal I‘ve ever met.Research on animal intelligence also makes me wonder what experiments animals would 13 on humans if they had the chance. Every cat with an owner, 14 , is running a small-scale study in operant conditioning. we believe that 15 animals ran the labs, they would test us to 16 the limits of our patience, our faithfulness, our memory for terrain. They would try to decide what intelligence in humans is really 17 , not merely how much of it there is. 18 , they would hope to study a 19 question: Are humans actually aware of the world they live in? 20 the results are inconclusive.1. [A] Suppose [B] Consider [C] Observe [D] Imagine2. [A] tended [B] feared [C] happened [D] threatened3. [A] thinner [B] stabler [C] lighter [D] dimmer4. [A] tendency [B] advantage [C] inclination [D] priority5. [A] insists on [B] sums up [C] turns out [D] puts forward6. [A] off [B] behind [C] over [D] along7. [A] incredible [B] spontaneous [C]inevitable [D] gradual8. [A] fight [B] doubt [C] stop [D] think19. [A] invisible [B] limited [C] indefinite [D] different10. [A] upward [B] forward [C] afterward [D] backward11. [A] features [B] influences [C] results [D] costs12. [A] outside [B] on [C] by [D] across13. [A] deliver [B] carry [C] perform [D] apply14. [A] by chance [B] in contrast [C] as usual [D] for instance15. [A] if [B] unless [C] as [D] lest16. [A] moderate [B] overcome [C] determine [D] reach17. [A] at [B] for [C] after [D] with18. [A] Above all [B] After all [C] However [D] Otherwise19. [A] fundamental [B] comprehensive [C] equivalent [D] hostile20. [A] By accident [B] In time [C] So far [D] Better stillSection II Reading ComprehensionPart ADirections:Read the following four texts. Answer the questions below each text by choosing A, B, C or D. Mark your answers on ANSWER SHEET 1. (40 points)Text1Habits are a funny thing. We reach for them mindlessly, setting our brains on auto-pilot and relaxing into the unconscious comfort of familiar routine. ―Not choice, but habit rules the unreflecting herd,‖ William Wordsworth said in the 19th century. In the ever-changing 21st century, even the word ―habit‖ carries a ne gative connotation.So it seems antithetical to talk about habits in the same context as creativity and innovation. But brain researchers have discovered that when we consciously develop new habits, we create parallel synaptic paths, and even entirely new brain cells, that can jump our trains of thought onto new, innovative tracks.But don‘t bother trying to kill off old habits; once those ruts of procedure are worn into the hippocampus, they‘re there to stay. Instead, the new habits we deliberately ingrain into ourselves create parallel pathways that can bypass those old roads.―The first thing needed for innovation is a fascination with wonder,‖ says Dawna Markova, author of ―The Open Mind‖ and an executive change consultant for Professional Thinking Part ners. ―But we are taught instead to ‗decide,‘ just as our president calls himself ‗the Decider.‘‖ She adds, however, that ―to decide is to kill off all possibilities but one. A good innovational thinker is always exploring the many other possibilities.‖A ll of us work through problems in ways of which we‘re unaware, she says. Researchers in the late 1960 covered that humans are born with the capacity to2approach challenges in four primary ways: analytically, procedurally, relationally (or collaboratively) and innovatively. At puberty, however, the brain shuts down half of that capacity, preserving only those modes of thought that have seemed most valuable during the first decade or so of life.The current emphasis on standardized testing highlights analysis and procedure, meaning that few of us inherently use our innovative and collaborative modes of thought. ―This breaks the major rule in the American belief system — that anyone can do anything,‖ explains M. J. Ryan, author of the 2006 book ―This Year I Will...‖ and Ms. Markova‘s business partner. ―That‘s a lie that we have perpetuated, and it fosters commonness. Knowing what you‘re good at and doing even more of it creates excellence.‖ This is where developing new habits comes in.21. The view of Wordsworth habit is claimed by beingA. casualB. familiarC. mechanicalD. changeable.22. The researchers have discovered that the formation of habit can beA. predictedB. regulatedC. tracedD. guided23.‖ ruts‖(in li ne one, paragraph 3) has closest meaning toA. tracksB. seriesC. characteristicsD. connections24. Ms. Markova‘s comments suggest that the practice of standard testing ? A, prevents new habits form being formedB, no longer emphasizes commonnessC, maintains the inherent American thinking modelD, complies with the American belief system25. Ryan most probably agree thatA. ideas are born of a relaxing mindB. innovativeness could be taughtC. decisiveness derives from fantastic ideasD. curiosity activates creative mindsText 2It is a wise father that knows his own child, but today a man can boost his paternal (fatherly) wisdom –or at least confirm that he‘s the kid‘s dad. All he needs to do is shell our $30 for paternity testing kit (PTK) at his local drugstore – and another $120 to get the results.More than 60,000 people have purchased the PTKs since they first become available without prescriptions last years, according to Doug Fog, chief operating officer of Identigene, which makes the over-the-counter kits. More than two dozen companies sell DNA tests Directly to the public , ranging in price from a few hundred dollars to more than $2500.3Among the most popular : paternity and kinship testing , which adopted children can use to find their biological relatives and latest rage a many passionate genealogists-and supports businesses that offer to search for a family‘s geographic roots .Most tests require collecting cells by webbing saliva in the mouth and sending it to the company for testing. All tests require a potential candidate with whom to compare DNA.But some observers are skeptical, ―There is a kind of false precision being hawked by people claiming they are doing ancestry testing,‖ says Trey Duster, a New York University sociologist. He notes that each individual has many ancestors-numbering in the hundreds just a few centuries back. Yet most ancestry testing only considers a single lineage, either the Y chromosome inherited through men in a father‘s line or mito chondrial DNA, which a passed down only from mothers. This DNA can reveal genetic information about only one or two ancestors, even though, for example, just three generations back people also have six other great-grandparents or, four generations back, 14 other great-great-grandparents.Critics also argue that commercial genetic testing is only as good as the reference collections to which a sample is compared. Databases used by some companies don‘t rely on data collected systematically but rather lump together information from different research projects. This means that a DNA database may differ depending on the company that processes the results. In addition, the computer programs a company uses to estimate relationships may be patented and not subject to peer review or outside evaluation.26.In paragraphs 1 and 2 , the text shows PTK‘s ___________.[A]easy availability[B]flexibility in pricing[C] successful promotion[D] popularity with households27. PTK is used to __________.[A]locate one‘s b irth place[B]promote genetic research[C] identify parent-child kinship[D] choose children for adoption28. Skeptical observers believe that ancestry testing fails to__________.[A]trace distant ancestors[B] rebuild reliable bloodlines[C] fully use genetic information[D] achieve the claimed accuracy29. In the last paragraph ,a problem commercial genetic testing faces is __________.4[A]disorganized data collection[B] overlapping database building30. An appropriate title for the text is most likely to be__________.[A]Fors and Againsts of DNA testing[B] DNA testing and It‘s problems[C]DNA testing outside the lab[D] lies behind DNA testingText 3The relationship between formal education and economic growth in poor countries is widely misunderstood by economists and politicians alike progress in both area is undoubtedly necessary for the social, political and intellectual development of these and all other societies; however, the conventional view that education should be one of the very highest priorities for promoting rapid economic development in poor countries is wrong. We are fortunate that is it, because new educational systems there and putting enough people through them to improve economic performance would require two or three generations. The findings of a research institution have consistently shown that workers in all countries can be trained on the job to achieve radical higher productivity and, as a result, radically higher standards of living.Ironically, the first evidence for this idea appeared in the United States. Not long ago, with the country entering a recessing and Japan at its pre-bubble peak. The U.S. workforce was derided as poorly educated and one of primary cause of the poor U.S. economic performance. Japan was, and remains, the global leader in automotive-assembly productivity. Yet the research revealed that the U.S. factories of Honda Nissan, and Toyota achieved about 95 percent of the productivity of their Japanese countere pants a result of the training that U.S. workers received on the job.More recently, while examing housing construction, the researchers discovered that illiterate, non-English- speaking Mexican workers in Houston, Texas, consistently met best-practice labor productivity standards despite the complexity of the building industry‘s work.What is the real relationship between education and economic development? We have to suspect that continuing economic growth promotes the development of education even when governments don‘t force it. After all, that‘s how education got started. When our ancestors were hunters and gatherers 10,000 years ago, they didn‘t have time to wonder much about anything besides finding food. Only when humanity began to get its food in a more productive way was there time for other things.As education improved, humanity‘s productivity potential, they could in turn afford more education. This increasingly high level of education is probably a necessary, but not a sufficient, condition for the complex political systems required by advanced5economic performance. Thus poor countries might not be able to escape their poverty traps without political changes that may be possible only with broader formal education. A lack of formal education, however, doesn‘t const rain the ability of the developing world‘s workforce to substantially improve productivity for the forested future. On the contrary, constraints on improving productivity explain why education isn‘t developing more quickly there than it is.31. The author holds in paragraph 1 that the important of education in poor countries ___________.[A] is subject groundless doubts[B] has fallen victim of bias[C] is conventional downgraded[D] has been overestimated32. It is stated in paragraph 1 that construction of a new education system __________.[A]challenges economists and politicians[B]takes efforts of generations[C] demands priority from the government[D] requires sufficient labor force33.A major difference between the Japanese and U.S workforces is that __________.[A] the Japanese workforce is better disciplined[B] the Japanese workforce is more productive[C]the U.S workforce has a better education[D] ]the U.S workforce is more organize34. The author quotes the example of our ancestors to show that education emerged __________.[A] when people had enough time[B] prior to better ways of finding food[C] when people on longer went hung[D] as a result of pressure on government35. According to the last paragraph , development of education __________.[A] results directly from competitive environments[B] does not depend on economic performance[C] follows improved productivity[D] cannot afford political changesText 4The most thoroughly studied in the history of the new world are the ministers and political leaders of seventeenth-century New England. According to the standard history of American philosophy, nowhere else in colonial America was ―So much6important attached to intellectual pursuits ‖ Accord ing to many books and articles, New England‘s leaders established the basic themes and preoccupations of an unfolding, dominant Puritan tradition in American intellectual life.To take this approach to the New Englanders normally mean to start with the Puritans‘ theological innovations and their distinctive ideas about the church-important subjects that we may not neglect. But in keeping with our examination of southern intellectual life, we may consider the original Puritans as carriers of European culture adjusting to New world circumstances. The New England colonies were the scenes of important episodes in the pursuit of widely understood ideals of civility and virtuosity.The early settlers of Massachusetts Bay included men of impressive education and influence in England. `Besides the ninety or so learned ministers who came to Massachusetts church in the decade after 1629,There were political leaders like John Winthrop, an educated gentleman, lawyer, and official of the Crown before he journeyed to Boston. There men wrote and published extensively, reaching both New World and Old World audiences, and giving New England an atmosphere of intellectual earnestness.We should not forget , however, that most New Englanders were less well educated. While few crafts men or farmers, let alone dependents and servants, left literary compositions to be analyzed, The in thinking often had a traditional superstitions quality. A tailor named John Dane, who emigrated in the late 1630s, left an account of his reasons for leaving England that is filled with signs. sexual confusion, economic frustrations , and religious hope-all name together in a decisive moment when he opened the Bible, told his father the first line he saw would settle his fate, and read th e magical words: ―come out from among them, touch no unclean thing , and I will be your God and you shall be my people.‖ One wonders what Dane thought of the careful sermons explaining the Bible that he heard in puritan churched.Mean while , many se ttles had slighter religious commitments than Dane‘s, as one clergyman learned in confronting folk along the coast who mocked that they had not come to the New world for religion . ―Our main end was to catch fish. ‖36. The author notes that in the seventeenth-century New England___________.[A] Puritan tradition dominated political life.[B] intellectual interests were encouraged.[C] Politics benefited much from intellectual endeavors.[D] intellectual pursuits enjoyed a liberal environment.37. It is suggested in paragraph 2 that New Englanders__________.[A] experienced a comparatively peaceful early history.[B] brought with them the culture of the Old World[C] paid little attention to southern intellectual life[D] were obsessed with religious innovations738. The early ministers and political leaders in Massachusetts Bay__________.[A] were famous in the New World for their writings[B] gained increasing importance in religious affairs[C] abandoned high positions before coming to the New World[D] created a new intellectual atmosphere in New England39. The story of John Dane shows that less well-educated New Englanders were often __________.[A] influenced by superstitions[B] troubled with religious beliefs[C] puzzled by church sermons[D] frustrated with family earnings40. The text suggests that early settlers in New England__________.[A] were mostly engaged in political activities[B] were motivated by an illusory prospect[C] came from different backgrounds.[D] left few formal records for later referencePart BDirections:Directions: In the following text, some sentences have been removed. For Questions (41-45), choose the most suitable one from the list A-G to fit into each of the numbered blank. There are two extra choices, which do not fit in any of the gaps. Mark your answers on ANSWER SHEET 1. (10 points)Coinciding with the groundbreaking theory of biological evolution proposed by British naturalist Charles Darwin in the 1860s, British social philosopher Herbert Spencer put forward his own theory of biological and cultural evolution. Spencer argued that all worldly phenomena, including human societies, changed over time, advancing toward perfection. 41.____________.American social scientist Lewis Henry Morgan introduced another theory of cultural evolution in the late 1800s. Morgan, along with Tylor, was one of the founders of modern anthropology. In his work, he attempted to show how all aspects of culture changed together in the evolution of societies.42._____________.In the early 1900s in North America, German-born American anthropologist Franz Boas developed a new theory of culture known as historical particularism. Historical particularism, which emphasized the uniqueness of all cultures, gave new direction to anthropology. 43._____________ .8Boas felt that the culture of any society must be understood as the result of a unique history and not as one of many cultures belonging to a broader evolutionary stage or type of culture. 44._______________.Historical particularism became a dominant approach to the study of culture in American anthropology, largely through the influence of many students of Boas. But a number of anthropologists in the early 1900s also rejected the particularist theory of culture in favor of diffusionism. Some attributed virtually every important cultural achievement to the inventions of a few, especially gifted peoples that, according to diffusionists, then spread to other cultures. 45.________________.Also in the early 1900s, French sociologist Émile Durkheim developed a theory of culture that would greatly influence anthropology. Durkheim proposed that religious beliefs functioned to reinforce social solidarity. An interest in the relationship between the function of society and culture—known as functionalism—became a major theme in European, and especially British, anthropology.[A] Other anthropologists believed that cultural innovations, such as inventions, had a single origin and passed from society to society. This theory was known as diffusionism.[B] In order to study particular cultures as completely as possible, Boas became skilled in linguistics, the study of languages, and in physical anthropology, the study of human biology and anatomy.[C] He argued that human evolution was characterized by a struggle he called the ―survival of the fittest,‖ in which weaker races and societies must eventu ally be replaced by stronger, more advanced races and societies.[D] They also focused on important rituals that appeared to preserve a people‘s social structure, such as initiation ceremonies that formally signify children‘s entrance into adulthood.[E] Thus, in his view, diverse aspects of culture, such as the structure of families, forms of marriage, categories of kinship, ownership of property, forms of government, technology, and systems of food production, all changed as societies evolved.[F]Supporters of the theory viewed as a collection of integrated parts that work together to keep a society functioning.[G] For example, British anthropologists Grafton Elliot Smith and W. J. Perry incorrectly suggested, on the basis of inadequate information, that farming, pottery9making, and metallurgy all originated in ancient Egypt and diffused throughout the world. In fact, all of these cultural developments occurred separately at different times in many parts of the world.Part CDirections:Read the following text carefully and then translate the underlined segments into Chinese. Your translation should be written carefully on ANSWER SHEET 2. (10 points)There is a marked difference between the education which every one gets from living with others, and the deliberate educating of the young. In the former case the education is incidental; it is natural and important, but it is not the express reason of the association.46It may be said that the measure of the worth of any social institution is its effect in enlarging and improving experience; but this effect is not a part of its original motive. Religious associations began, for example, in the desire to secure the favor of overruling powers and to ward off evil influences; family life in the desire to gratify appetites and secure family perpetuity; systematic labor, for the most part, because of enslavement to others, etc. 47Only gradually was the by-product of the institution noted, and only more gradually still was this effect considered as a directive factor in the conduct of the institution. Even today, in our industrial life, apart from certain values of industriousness and thrift, the intellectual and emotional reaction of the forms of human association under which the world's work is carried on receives little attention as compared with physical output.But in dealing with the young, the fact of association itself as an immediate human fact, gains in importance.48 While it is easy to ignore in our contact with them the effect of our acts upon their disposition, it is not so easy as in dealing with adults. The need of training is too evident; the pressure to accomplish a change in their attitude and habits is too urgent to leave these consequences wholly out of account. 49Since our chief business with them is to enable them to share in a common life we cannot help considering whether or no we are forming the powers which will secure this ability.If humanity has made some headway in realizing that the ultimate value of every institution is its distinctively human effect we may well believe that this lesson has been learned largely through dealings with the young.50 We are thus led to distinguish, within the broad educational process which we have been so far considering, a more formal kind of education -- that of direct tuition or schooling. In undeveloped social groups, we find very little formal teaching and training. These groups mainly rely for instilling needed dispositions into the young upon the same sort of association which keeps the adults loyal to their group.Section & Writing10Part A51. Directions:Restrictions on the use of plastic bags have not been so successful in some regions. ―White pollution ‖is still going on. Write a letter to the editor(s) of your local newspaper to1)give your opinions briefly and2)make two or three suggestionsYou should write about 100 words. Do not sign your own name at the end of the letter. Use "Li Ming" instead. You do not need to write the address.Part B52. Directions:In your essay, you should1) describe the drawing briefly,2) explain its intended meaning, and then3) give your comments.You should write neatly on ANSHWER SHEET 2. (20 points)11。
09-10年计算机考研真题及答案
2009年全国硕士研究生入学考试计算机统考试题2010年硕士研究生入学考试计算机专业基础综合试题一、单项选择题:1-40题,每题20分共80分。
在每个小题给出的四个选项中选正确答案。
1、若元素a、b、c、d、e、f依次进栈,允许进栈、退栈操作交替进行,但不允许连续三次进行退栈工作,则不可能得到的出栈序列是()A、dcebfaB、cbdaefC、bcaefdD、afedcb2、某队列允许在其两端进行入队操作,但仅允许在一端进行出队操作,则不可能得到的顺顺序是()A、bacdeB、dbaceC、dbcaeD、ecbad3、下列线索二叉树中(用虚线表示线索),符合后序线索树定义的是()4、在下列所示的平衡二叉树中插入关键字48后得到一棵新平衡二叉树,在新平衡二叉树中,关键字37所在结点的左、右子结点中保存的关键字分别是()A、13,48B、24,48C、24,53D、24,905、在一棵度数为4的树T中,若有20个度为4的结点,10个度为3的结点,1个度为2的结点,10个度为1的结点,则树T的叶结点个数是()A、41B、82C、113D、1226、对n(n>=2)个权值均不相同的字符构成哈弗曼树,关于该树的叙述中,错误的是()A、该树一定是一棵完全二交叉B、树中一定没有度为1的结点C、树中两个权值最小的结点一定是兄弟结点D、树中任一非叶结点的权值一定不小于下一层任一结点的权值7、若无向图G=(V.E)中含7个顶点,则保证图G在任何情况下都是连通的,则需要的边数最少是()A、6B、15C、16D、218、对下图进行拓扑排序,可以得到不同的拓扑序列的个数是()A、4B、3C、2D、19、已知一个长度为16的顺序表L,其元素按关键字有序排列,若采用折半查找法查找一个不存在的元素,则比较次数最多的是()A、4B、5C、6D、710、采用递归方式对顺序表进行快速排序,下列关于递归次数的叙述中,正确的是()A、递归次数于初始数据的排列次数无关B、每次划分后,先处理较长的分区可以减少递归次数C、每次划分后,先处理较短的分区可以减少递归次数D、递归次数与每次划分后得到的分区处理顺序无关11、对一组数据(2,12,16,88,5,10)进行排序,若前三趟排序结果如下:()第一趟:2,12,16,5,10,88第二趟:2,12,5,10,16,88第三趟:2,5,10,12,16,88则采用的排序方法可能是A.冒泡排序法B.希尔排序法C.归并排序法D.基数排序法12.下列选项中,能缩短程序执行时间的措施是()1.提高CPU时钟频率2.优化通过数据结构3.优化通过程序A.仅1和2B.仅1和3C,仅2和3D.1,2,313.假定有4个整数用8位补码分别表示r1=FEH,r2=F2H,r3=90H,r4=F8H,若将运算结果存放在一个8位寄存器中,则下列运算会发生益处的是()A. r1 x r2B. r2 x r3C. r1 x r4D. r2 x r414.假定变量i,f,d数据类型分别为int, float, double(int用补码表示,float和double用IEEE754单精度和双精度浮点数据格式表示),已知i=785,f=1.5678e3,d=1.5e100,若在32位机器中执行下列关系表达式,则结果为真的是()(I) i==(int)(float)I(II)f==(float)(int)f(III)f==(float)(double)f(IV)(d+f)-d==fA. 仅I和IIB. 仅I和IIIC. 仅II和IIID. 仅III和IV15.假定用若干个2K x 4位芯片组成一个8K x 8为存储器,则0B1FH所在芯片的最小地址是()A.0000HB.0600HC.0700HD.0800H16.下列有关RAM和ROM得叙述中正确的是()I RAM是易失性存储器,ROM是非易失性存储器II RAM和ROM都是采用随机存取方式进行信息访问III RAM和ROM都可用做CacheIV RAM和ROM都需要进行刷新A. 仅I和IIB. 仅II和IIIC. 仅I ,II,IIID. 仅II,III,IV17.下列命令组合情况,一次访存过程中,不可能发生的是()A.TLB未命中,Cache未命中,Page未命中B.TLB未命中,Cache命中,Page命中C.TLB命中,Cache未命中,Page命中D.TLB命中,Cache命中,Page未命中18.下列寄存器中,反汇编语言程序员可见的是()A.存储器地址寄存器(MAR)B.程序计数器(PC)C.存储区数据寄存器(MDR)D.指令寄存器(IR)19.下列不会引起指令流水阻塞的是()A.数据旁路B.数据相关C.条件转移D.资源冲突20.下列选项中的英文缩写均为总线标准的是()A. PCI、CRT、USB、EISAB. ISA、CPI、VESA、EISAC. ISA、SCSI、RAM、MIPSD. ISA、EISA、PCI、PCI-Express21、单级中断系统中,中断服务程序执行顺序是()I保护现场II开中断III关中断IV保存断点V中断事件处理VI恢复现场VII中断返回A、I->V->VI->II->VIIB、III->I->V->VIIC、III->IV->V->VI->VIID、IV->I->V->VI->VII22、假定一台计算机的显示存储器用DRAM芯片实现,若要求显示分辨率为1600*1200,颜色深度为24位,帧频为85HZ,现实总带宽的50%用来刷新屏幕,则需要的显存总带宽至少约为()A、245MbpsB、979MbpsC、1958MbpsD、7834Mbps23、下列选项中,操作S提供的给应程序的接口是()A、系统调用B、中断C、库函数D、原语24、下列选项中,导制创进新进程的操作是()I用户登陆成功II设备分配III启动程序执行A、仅I和IIB、仅II和IIIC、仅I和IIID、I、II、III25、设与某资源相关联的信号量初值为3,当前值为1,若M表示该资源的可用个数,N表示等待该资源的进程数,则M,N分别是()A、0,1B、1,0C、1,2D、2,026、下列选项中,降低进程优先权级的合理时机是()A、进程的时间片用完B、进程刚完成I/O,进入就绪列队C、进程长期处于就绪列队D、进程从就绪状态转为运行状态27、进行PO和P1的共享变量定义及其初值为()booleam flag[2];int turn=0;flag[0]=false; flag[1]=false;若进行P0和P1访问临界资源的类C代码实现如下:void p0() // 进程p0 void p1 () // 进程p1{ {while (TRUE){ while (TRUE){flag[0]=TRUE; turn=1; flag[0]=TRUE; turn=0;While (flag[1]&&(turn==1)) While (flag[0]&&(turn==0));临界区;临界区;flag[0]=FALSE; flag[1]=FALSE;} }} }则并发执行进程PO和P1时产生的情况是()A、不能保证进程互斥进入临界区,会出现“饥饿”现象B、不能保证进程互斥进入临界区,不会出现“饥饿”现象C、能保证进程互斥进入临界区,会出现“饥饿”现象D、能保证进程互斥进入临界区,不会出现“饥饿”现象28、某基于动态分区存储管理的计算机,其主存容量为55Mb(初始为空),采用最佳适配(Best Fit)算法,分配和释放的顺序为:分配15Mb,分配30Mb,释放15Mb,分配6Mb,此时主存中最大空闲分区的大小是()A、7MbB、9MbC、10MbD、15Mb29、某计算机采用二级页表的分页存储管理方式,按字节编制,页大小为2(10)【2的10次方,下同】字节,页表项大小为2字节,逻辑地址结构为页目录号页号页内偏移量逻辑地址空间大小为2(10)页,则表示整个逻辑地址空间的页目录表中包含表项的个数至少是()A、64B、128C、256D、51230.设文件索引节点中有7个地址项,其中4个地址为直接地址索引,1个地址项是二级间接地址索引,每个地址项的大小为4字节,若磁盘索引块和磁盘数据块大小均为256字节,则可表示的单个文件最大长度是()A. 33KBB. 519KBC. 1057KBD. 16513KB31. 设当前工作目录的主要目的是()A. 节省外存空间B. 节省内存空间C. 加快文件的检索速度D. 加快文件的读写速度32.本地用户通过键盘登陆系统是,首先获得键盘输入信息的程序时()A. 命令解释程序B. 中断处理程序C. 系统调用程序D. 用户登录程序33. 下列选项中,不属于网络体系结构中所描述的内容是()A.网络的层次B.每一层使用的协议C.协议的内部实现细节D.每一层必须完成的功能34.在下图所表示的采用”存储-转发”方式分组的交换网络中所有的链路的数据传输速度为100Mbps,分组大小为1000B,其中分组头大小为20B若主机H1向主机H2发送一个大小为980000的文件,则在不考虑分组拆装时间和传播延迟的情况下,从H1发送到H2接受完为止,需要的时间至少是()A.80msB. 80.08msC. 80.16msD. 80.24ms35.某自治系统采用RIP协议,若该自治系统内的路由器R1收到其邻居路由器R2的距离矢量中包含的信息<net1,16>,则可能得出的结论是()A. R2可以经过R1到达net1,跳数为17B. R2可以到达net1,跳数为16C. R1可以经过R2到达net1,跳数为17D.R1不能经过R2到达net136.若路由器R因为拥塞丢弃IP分组,则此时R可向发出该IP分组的源主机的ICMP报文件的类型是()A. 路由重定向B. 目的不可达C. 源抑制D. 超时37、某网络的IP地址空间为192.168.5.0/24采用长子网划分,子网掩码为255.255.255.248,则该网络的最大子网个数、每个子网内的最大可分配地址个数为()A、32,8B、32,6C、8,32D、8,3038、下列网络设备中,能够抑制网络风暴的是()I中断器II集线器III网桥IV路由器A、仅I和IIB、仅IIIC、仅III和IVD、仅IV39、主机甲和主机乙之间建立一个TCP连接,TCP最大段长度为1000字节,若主机甲的当前拥塞窗口为4000字节,在主机甲向主机乙连续发送2个最大段后,成功收到主机乙发送的第一段的确认段,确认段中通告的接收窗口大小为2000字节,则此时主机甲还可以向主机乙发送的最大字节数是()A、1000B、2000C、3000D、400040、如果本地域名服务无缓存,当采用递归方法解析另一网络某主机域名时,用户主机本地域名服务器发送的域名请求条数分别为()A、1条,1条B、1条,多条C、多条,1条D、多条,多条二、综合应用题:41-47小题,共70分41.(10分)将关键字序列(7、8、30、11、18、9、14)散列存储到散列表中,散列表的存储空间是一个下标从0开始的一个一维数组散列,函数为:H(key)=(key x 3)MODT,处理冲突采用线性探测再散列法,要求装载因子为0.7问题:(1).请画出所构造的散列表。
2009年考研计算机统考真题及答案解析

12. 一个 C 语言程序在一台 32 位机器上运行。 程序中定义了三个变量 x、 y 和 z, 其中 x 和 z 为 int 型, y 为 short 型。当 x=127,y =- 9 时,执行赋值语句 z=x+y 后, x、y 和 z 的值分别是 A . x=0000007FH,y=FFF9H, z=00000076H B. x=0000007FH,y=FFF9H, z=FFFF0076H C. x=0000007FH,y=FFF7H, z=FFFF0076H D. x=0000007FH,y=FFF7H, z=00000076H 13. 浮点数加、减运算过程一般包括对阶、尾数运算、规格化、舍入和判溢出等步骤。设浮点数的阶码和尾数 均采用补码表示,且位数分别为 5 位和 7 位(均含 2 位符号位)。若有两个数 X=27 ×29/ 32 , Y=25 ×5/8 ,则 用浮点加法计算 X+Y 的最终结果是 A .00111 1100010 C. 01000 0010001 。
40. FTP 客户和服务器间传递 FTP 命令时,使用的连接是______ 。 A .建立在 TCP 之上的控制连接 C.建立在 UDP 之上的控制连接 二、综合应用题:第 41~47 题,共 70 分。 41. (10 分)带权图(权值非负,表示边连接的两顶点间的距离)的最短路径问题是找出从初始顶点到目标顶 点之间的一条最短路径。假设从初始顶点到目标顶点之间存在路径,现有一种解决该问题的方法:
28. 下列文件物理结构中,适合随机访问且易于文件扩展的是______ 。 A .连续结构 C.链式结构且磁盘块定长 B.索引结构 D.链式结构且磁盘块变长
29. 假设磁头当前位于第 105 道,正在向磁道序号增加的方向移动。现有一个磁道访问请求序列为 35,45,12 , 68 ,110 ,180, 170, 195 ,采用 SCA N 调度 (电梯调度) 算法得到的磁道访问序列是 ______ 。 A .110,170,180,195,68,45,35,12 C.110,170,180,195,12,35,45,68 B.110,68,45,35,12,170,180,195 D. 12,35,45,68,110下列二叉排序树中,满足平衡二叉树定义的是______ 。
2009-计算机考研408真题及答案
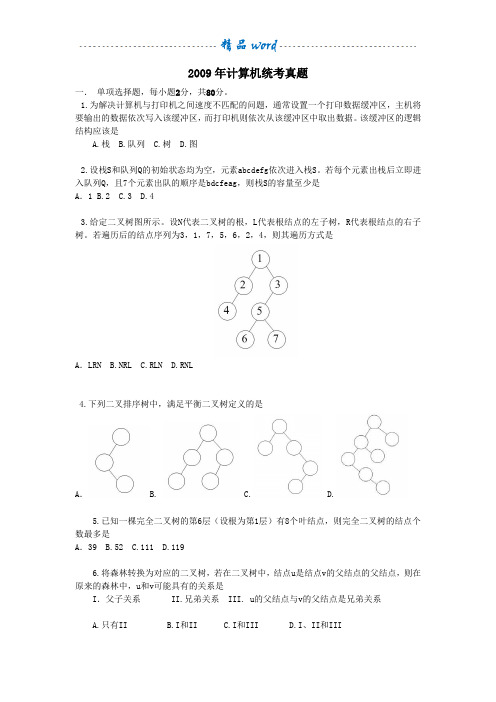
2009年计算机统考真题一.单项选择题,每小题2分,共80分。
1.为解决计算机与打印机之间速度不匹配的问题,通常设置一个打印数据缓冲区,主机将要输出的数据依次写入该缓冲区,而打印机则依次从该缓冲区中取出数据。
该缓冲区的逻辑结构应该是A.栈B.队列C.树D.图2.设栈S和队列Q的初始状态均为空,元素abcdefg依次进入栈S。
若每个元素出栈后立即进入队列Q,且7个元素出队的顺序是bdcfeag,则栈S的容量至少是A.1 B.2 C.3 D.43.给定二叉树图所示。
设N代表二叉树的根,L代表根结点的左子树,R代表根结点的右子树。
若遍历后的结点序列为3,1,7,5,6,2,4,则其遍历方式是A.LRN B.NRL C.RLN D.RNL4.下列二叉排序树中,满足平衡二叉树定义的是A. B. C. D.5.已知一棵完全二叉树的第6层(设根为第1层)有8个叶结点,则完全二叉树的结点个数最多是A.39 B.52 C.111 D.1196.将森林转换为对应的二叉树,若在二叉树中,结点u是结点v的父结点的父结点,则在原来的森林中,u和v可能具有的关系是I.父子关系 II.兄弟关系 III. u的父结点与v的父结点是兄弟关系A.只有IIB.I和IIC.I和IIID.I、II和III7.下列关于无向连通图特性的叙述中,正确的是I.所有顶点的度之和为偶数 II.边数大于顶点个数减1III.至少有一个顶点的度为1A.只有IB. 只有IIC.I和IID.I和III8.下列叙述中,不符合m阶B树定义要求的是A.根节点最多有m棵子树 B.所有叶结点都在同一层上C.各结点内关键字均升序或降序排列 D.叶结点之间通过指针链接9.已知关键序列5,8,12,19,28,20,15,22是小根堆(最小堆),插入关键字3,调整后得到的小根堆是A.3,5,12,8,28,20,15,22,19B. 3,5,12,19,20,15,22,8,28C.3,8,12,5,20,15,22,28,19D. 3,12,5,8,28,20,15,22,1910.若数据元素序列11,12,13,7,8,9,23,4,5是采用下列排序方法之一得到的第二趟排序后的结果,则该排序算法只能是A.起泡排序 B.插入排序 C.选择排序 D.二路归并排序11.冯·诺依曼计算机中指令和数据均以二进制形式存放在存储器中,CPU区分它们的依据是A.指令操作码的译码结果 B.指令和数据的寻址方式C.指令周期的不同阶段D.指令和数据所在的存储单元12.一个C语言程序在一台32位机器上运行。
2009-计算机考研408真题及答案
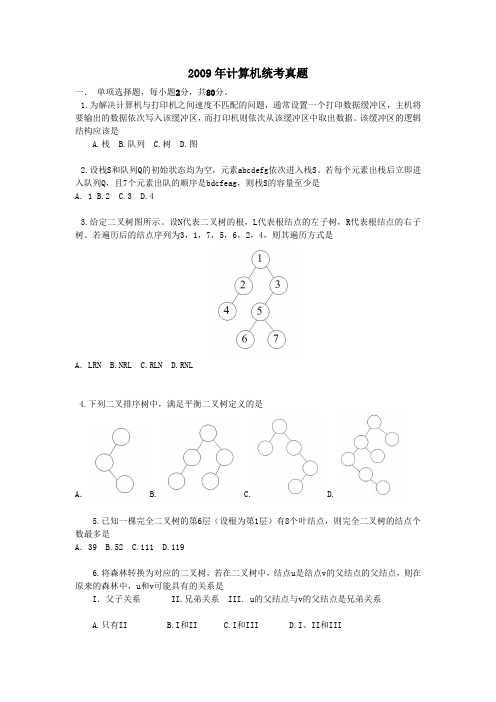
2009年计算机统考真题一.单项选择题,每小题2分,共80分。
1.为解决计算机与打印机之间速度不匹配的问题,通常设置一个打印数据缓冲区,主机将要输出的数据依次写入该缓冲区,而打印机则依次从该缓冲区中取出数据。
该缓冲区的逻辑结构应该是A.栈B.队列C.树D.图2.设栈S和队列Q的初始状态均为空,元素abcdefg依次进入栈S。
若每个元素出栈后立即进入队列Q,且7个元素出队的顺序是bdcfeag,则栈S的容量至少是A.1 B.2 C.3 D.43.给定二叉树图所示。
设N代表二叉树的根,L代表根结点的左子树,R代表根结点的右子树。
若遍历后的结点序列为3,1,7,5,6,2,4,则其遍历方式是A.LRN B.NRL C.RLN D.RNL4.下列二叉排序树中,满足平衡二叉树定义的是A. B. C. D.5.已知一棵完全二叉树的第6层(设根为第1层)有8个叶结点,则完全二叉树的结点个数最多是A.39 B.52 C.111 D.1196.将森林转换为对应的二叉树,若在二叉树中,结点u是结点v的父结点的父结点,则在原来的森林中,u和v可能具有的关系是I.父子关系 II.兄弟关系 III. u的父结点与v的父结点是兄弟关系A.只有IIB.I和IIC.I和IIID.I、II和III7.下列关于无向连通图特性的叙述中,正确的是I.所有顶点的度之和为偶数 II.边数大于顶点个数减1III.至少有一个顶点的度为1A.只有IB. 只有IIC.I和IID.I和III8.下列叙述中,不符合m阶B树定义要求的是A.根节点最多有m棵子树 B.所有叶结点都在同一层上C.各结点内关键字均升序或降序排列 D.叶结点之间通过指针链接9.已知关键序列5,8,12,19,28,20,15,22是小根堆(最小堆),插入关键字3,调整后得到的小根堆是A.3,5,12,8,28,20,15,22,19B. 3,5,12,19,20,15,22,8,28C.3,8,12,5,20,15,22,28,19D. 3,12,5,8,28,20,15,22,1910.若数据元素序列11,12,13,7,8,9,23,4,5是采用下列排序方法之一得到的第二趟排序后的结果,则该排序算法只能是A.起泡排序 B.插入排序 C.选择排序 D.二路归并排序11.冯·诺依曼计算机中指令和数据均以二进制形式存放在存储器中,CPU区分它们的依据是A.指令操作码的译码结果 B.指令和数据的寻址方式C.指令周期的不同阶段D.指令和数据所在的存储单元12.一个C语言程序在一台32位机器上运行。
09和10年全国研究生考试计算机统考真题

子为0.7, 问题:
(1)请画出所构造的散列表; (2)分别计算等概率情况下,查找成功和查找不成功 的平均查找长度。
14
解答:(1) 因为装填因子为0.7,数据总数为7,所以
存储空间长度为L = 7/0.7 = 10
因此可选T=7,构造的散列函数为
H(key) = (key*3) MOD 7 线性探测再散列函数为: Hi = ( H(key)+ di ) MOD 10 , (di = 1,2,3...9)
栈和队列 2010年
1、若元素a,b,c,d,e,f依次进栈,允许进栈、退栈操作交 替进行。但不允许连续三次进行退栈工作,则不可能得
到的出栈序列是( )
A:dcebfa B:cbdaef C:bcaefd D:afedcb
3
树与二叉树 2009
3、给定二叉树图所示。设 N 代表二叉树的根,L 代表 根结点的左子树,R 代 表根结点的右子树。若遍历后的 结点序列为 3,1,7,5,6,2,4,则其遍历方 式是
前6层满二叉树的结点数为26-1=63 第7层上的结点数为:26-1-8=24 答案:63+2*24=111
6
树与二叉树 2010年
3、下列线索二叉树中(用虚线表示线索),符合中序线索树定义的是( )
NULL
7
树与二叉树 2009年
6.将森林转换为对应的二叉树,若在二叉树中,结点 u 是 结点 v 的父结点的 父结点,则在原来的森林中,u 和 v 可能具有的关系是 I.父子关系 II.兄弟关系 III. u 的父结点与 v 的父结点是 兄弟关系 A.只有 II B.I 和 II C.I 和 III D.I、II 和 III
A.LRN
B.NRL
2009统考计算机考研试题【5】

2009统考计算机考研试题【5】38.主机甲和主机乙之间建立一个TCP连接,主机甲向主机乙发送了两个连续的TCP段,分别含300字节和500字节的有效载荷,第一个段的序列号为200,主机乙正确接收到两个段后,发送给主机甲的确认序列号是(1000)。
例如,序列号等于前一个报文段的序列号与前一个报文段中数据字节的数量之和。
例如,假设源主机发送3个报文段,每个报文段有100字节的数据,且第一个报文段的序列号是1000,那么接收到第一个报文段后,目的主机返回含确认号1100的报头。
接收到第二个报文段(其序号为1100)后,目的主机返回确认号1200。
接收到第三个报文段后,目的主机返回确认号1300。
39.确定拥塞窗口的大小的过程:在刚建立连接时,将拥塞窗口的大小初始化为该连接所需的最大连接数据段的长度值,并发送一个最大长度的数据段(当然必须是接收窗口允许的)。
如果在定时器超时前得到确认,将拥塞窗口的大小增加一个数据段的字节数,并发送两个数据段,如果每个数据段在定时器超时前都得到确认,就再在原基础上增加一倍,即为4个数据段的大小,如此反复,每次都在前一次的基础上加倍。
当定时器超时或达到发送窗口设定值,停止拥塞窗口尺寸的增加。
这种反复称为慢速启动,所有的TCP协议都支持这种方法。
一个TCP连接总是以1KB的最大段发送TCP段,发送方有足够多的数据要发送。
当拥塞窗口为16KB时发生了超时,如果接下来的4个RTT(往返时间)时间内的TCP段的传输都是成功的,那么当第4个RTT 时间内发送的所有TCP段都得到肯定应答时,拥塞窗口大小是(9KB)。
40.FTP客户和服务器间传递FTP时,使用的连接是(建立在TCP 之上的控制连接)。
二. 综合应用题41.该方法求得的路径不一定是最短路径。
例如,对于下图所示的带权图,如果按照题中的原则,从A到C的最短路径为A→B→C,事实上其最短路径为A→D→C。
42. (1)算法基本思想如下:从头至尾遍历单链表,并用指针P指向当前节点的前K个节点。
2009年统考计算机考研真题及答案(word版)

2009年计算机统考真题(完整版)一.单项选择题,每小题 2 分,共80 分。
1.为解决计算机与打印机之间速度不匹配的问题,通常设置一个打印数据缓冲区,主机将要输出的数据依次写入该缓冲区,而打印机则依次从该缓冲区中取出数据。
该缓冲区的逻辑结构应该是 A.栈 B.队列 C.树 D.图2.设栈S 和队列Q 的初始状态均为空,元素abcdefg 依次进入栈S。
若每个元素出栈后立即进入队列Q,且7 个元素出队的顺序是bdcfeag,则栈S 的容量至少是A.1 B.2 C.3 D.43.给定二叉树图所示。
设N 代表二叉树的根,L 代表根结点的左子树,R 代表根结点的右子树。
4.若遍历后的结点序列为3,1,7,5,6,2,4,则其遍历方式是A.LRN B.NRL C.RLN D.RNL5.下列二叉排序树中,满足平衡二叉树定义的是6.已知一棵完全二叉树的第 6 层(设根为第 1 层)有8 个叶结点,则完全二叉树的结点个数最多是A.39 B.52 C.111 D.1197.将森林转换为对应的二叉树,若在二叉树中,结点u 是结点v 的父结点的父结点,则在原来1的森林中,u 和v 可能具有的关系是I.父子关系II.兄弟关系III. u 的父结点与v 的父结点是兄弟关系A.只有IIB.I 和IIC.I 和IIID.I、II 和III8.下列关于无向连通图特性的叙述中,正确的是I.所有顶点的度之和为偶数II.边数大于顶点个数减 1 III. 至少有一个顶点的度为 1A.只有IB. 只有IIC.I 和IID.I 和III9.下列叙述中,不符合m 阶B 树定义要求的是A.根节点最多有m 棵子树 B.所有叶结点都在同一层上C.各结点内关键字均升序或降序排列 D.叶结点之间通过指针链接10.已知关键序列5,8,12,19,28,20,15,22 是小根堆(最小堆),插入关键字3,调整后得到的小根堆是A. 3,5,12,8,28,20,15,22,19B. 3,5,12,19,20,15,22,8,28C. 3,8,12,5,20,15,22,28,19D. 3,12,5,8,28,20,15,22,1911.若数据元素序列11,12,13,7,8,9,23,4,5 是采用下列排序方法之一得到的第二趟排序后的结果,则该排序算法只能是A.起泡排序 B.插入排序 C.选择排序 D.二路归并排序12.冯·诺依曼计算机中指令和数据均以二进制形式存放在存储器中,CPU 区分它们的依据是A.指令操作码的译码结果 B.指令和数据的寻址方式C.指令周期的不同阶段D.指令和数据所在的存储单元13.一个 C 语言程序在一台32 位机器上运行。
2009年全国硕士研究生入学统一考试408计算机学科专业基础综合真题

2009年全国硕士研究生入学统一考试408计算机学科专业基础综合真题一、单项选择题:1~40小题,每小题2分,共80分。
下列每题给出的四个选项中。
只有一个选项是最符合题目要求的。
1.为解决计算机主机与打印机之间速度不匹配问题,通常设置一个打印数据缓冲区,主机将要输出的数据依次写入该缓冲区,而打印机则依次从该缓冲区中取出数据。
该缓冲区的逻辑结构应该是()。
A.栈B.队列C.树D.图2.设栈S和队列Q的初始状态均为空,元素a,b,c,d,e,f,g依次进入栈S。
若每个元素出栈后立即进入队列Q,且7个元素出队的顺序是b,d,c,f,e,a,g,则栈S的容量至少是()。
A.1B.2C.3D.43.给定二叉树如下图所示。
设N代表二叉树的根,L代表根结点的左子树,R代表根结点的右子树。
若遍历后的结点序列为3,1,7,5,6,2,4,则其遍历方式是()。
A.LRNB.NRLC.RLND.RNL4.下列二叉排序树中,满足平衡二叉树定义的是()。
5.已知一棵完全二叉树的第6层(设根为第1层)有8个叶结点,则该完全二叉树的结点个数最多是()。
A.39B.52C.111D.1196.将森林转换为对应的二叉树,若在二叉树中,结点u是结点v的父结点的父结点,则在原来的森林中,u和v可能具有的关系是()。
Ⅰ.父子关系Ⅱ.兄弟关系Ⅲ.u的父结点与v的父结点是兄弟关系A.只有ⅠB.Ⅰ和ⅡC.Ⅰ和ⅢD.Ⅰ、Ⅱ和Ⅲ7.下列关于无向连通图特性的叙述中,正确的是()。
Ⅰ.所有的顶点的度之和为偶数Ⅱ.边数大于顶点个数减1Ⅲ.至少有一个顶点的度为1A.只有ⅠB.只有ⅡC.Ⅰ和ⅡD.Ⅰ和Ⅲ8.下列叙述中,不符合m阶B树定义要求的是()。
A.根结点最多有m棵子树B.所有叶结点都在同一层上C.各结点内关键字均升序或降序排列D.叶结点之间通过指针链接9.已知关键字序列5,8,12,19,28,20,15,22是小根堆(最小堆),插入关键字3,调整后的小根堆是()。
全国硕士研究生考试2009-2012年计算机学科专业基础综合试题

16.某机器字长为 16 位,主存按字节编址,转移指令采用相对寻址,由两个字节组成,第一字节为
操作码字段,第二字节为相对位移量字段。假定取指令时,每取一个字节 PC 自动加 1。若某转移指令所
在主存地址为 2000H,相对位移量字段的内容为 06H,则该转移指令成功转移后的目标地址是
。
A.2006H
到的小根堆是
。
A.3,5,12,8,28,20,15,22,19
B.3,5,12,19,20,15,22,8,28
C.3,8,12,5,20,15,22,28,19
D.3,12,5,8,28,20,15,22,19
10.若数据元素序列 11,12,13,7,8,9,23,4,5 是采用下列排序方法之一得到的第二趟排序
的确认序列号是
。
A.500
B.700
C.800
D.1000
39.一个 TCP 连接总是以 1KB 的最大段长发送 TCP 段,发送方有足够多的数据要发送。当拥塞窗
口为 16KB 时发生了超时,如果接下来的 4 个 RTT(往返时间)时间内的 TCP 段的传输都是成功的,那
么当第 4 个 RTT 时间内发送的所有 TCP 段都得到肯定应答时,拥塞窗口大小是
Y=25×5/8,则用浮点加法计算 X+Y 的最终结果是
。
A.00111 1100010
B.00111 0100010
C.01000 0010001
D.发生溢出
14.某计算机的 Cache 共有 16 块,采用 2 路组相联映射方式(即每组 2 块)。每个主存块大小为 32B,
按字节编址。主存 129 号单元所在主存块应装入到的 Cache 组号是
2009统考计算机考研试题【2】

2009统考计算机考研试题【2】29.假设磁头当前位于第105道,正在向磁道序号增加的方向移动。
现有一个磁道访问请求序列为35,45,12,68,110,180,170,195,采用SCAN调度(电梯调度)算法得到的磁道访问序列是A.110,170,180,195,68,45,35,12B.110,68,45,35,12,170,180,195C.110,170,180,195,12,35,45,68D.12,35,45,68,110,170,180,19530.文件系统中,文件访问控制信息存储的合理位置是A.文件控制块B.文件分配表C.用户口令表D.系统注册表31.设文件F1的当前引用计数值为1,先建立F1的符号链接(软链接)文件F2,再建立F1的硬链接文件F3,然后删除F1。
此时,F2和F3的引用计数值分别是A.0、1B.1、1C.1、2D.2、132.程序员利用系统调用打开I/O设备时,通常使用的设备标识是A.逻辑设备名B.物理设备名C.主设备号D.从设备号33.在OSI参考模型中,自下而上第一个提供端到端服务的层次是A.数据链路层B.传输层C.会话层D.应用层34.在无噪声情况下,若某通信链路的带宽为3kHz,采用4个相位,每个相位具有4种振幅的QAM调制技术,则该通信链路的最大数据传输速率是A.12kbpsB.24 kbpsC.48 kbpsD.96 kbps35.数据链路层采用了后退N帧(GBN)协议,发送方已经发送了编号为0~7的帧。
当计时器超时时,若发送方只收到0、2、3号帧的确认,则发送方需要重发的帧数是A.2B.3C.4D.536.以太网交换机进行转发决策时使用的PDU地址是A.目的物理地址B.目的IP地址C.源物理地址D.源IP地址37.在一个采用CSMA/CD协议的网络中,传输介质是一根完整的电缆,传输速率为1Gbps,电缆中的信号传播速度是200 000km/s。
若最小数据帧长度减少800比特,则最远的两个站点之间的距离至少需要A.增加160mB.增加80mC.减少160mD.减少80m38.主机甲和主机乙间已建立一个TCP连接,主机甲向主机乙发送了两个连续的TCP段,分别包含300字节和500字节的有效载荷,第一个段的序列号为200,主机乙正确接收到两个段后,发送给主机甲的确认序列号是 A.500 B.700 C.800 D.100039.一个TCP连接总是以1KB的最大段发送TCP段,发送方有足够多的数据要发送。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
2009年计算机统考真题参考答案感谢会员ysb手工录入了这份真题,任何组织和个人无权将其用于任何商业赢利为目的的活动!予人玫瑰,手有余香,王道论坛伴你一路同行!一. 选择题1 2 3 4 5 6 7 8 9 10B C D B C B A D A B11 12 13 14 15 16 17 18 19 20C D D C D C A A D B21 22 23 24 25 26 27 28 29 30D A D D C A C B A A31 32 33 34 35 36 37 38 39 40B A B BC AD D C A二. 综合应用题41.该方法求得的路径不一定是最短路径。
例如,对于下图所示的带权图,如果按照题中的原则,从A到C的最短路径为A→B→C,事实上其最短路径为A→D→C。
42.(1)算法基本思想如下:从头至尾遍历单链表,并用指针p指向当前结点的前k个结点。
当遍历到链表的最后一个结点时,指针p所指向的结点即为所查找的结点。
(2)详细实现步骤:增加两个指针变量和一个整型变量,从链表头向后遍历,其中指针p1指向当前遍历的结点,指针p指向p1所指向结点的前k个结点,如果p1之前没有k个结点,那么p指向表头结点。
用整型变量i表示当前遍历了多少个结点,当i>k时,指针p随着每次遍历,也向前移动一个结点。
当遍历完成时,p或者指向表头结点,或者指向链表中倒数第k个位置上的结点。
(3)算法描述:int LocateElement(Linklist list,int k){p1=list->link;p=list;i=1;while(p1){p1=p1->link;i++;if(i>k)p=p->next; //如果i>k,则p也往后移}if(p==list)return 0; //说明链表没有k个结点else{printf(“%d\n“,p->data);return 1;}}43.(1)在中断方式下,每32位(4B)被中断一次,故每秒中断0.5MB/4B=0.5×106/4=12.5×104次要注意的是,这里是数据传输率,所以1MB=106B。
因为中断服务程序包含18条指令,中断服务的其他开销相当于2条指令的执行时间,且执行每条指令平均需5个时钟周期,所以,1秒内用于中断的时钟周期数为(18+2)×5×12.5×104=12.5×106(2)在DMA方式下,每秒进行DMA操作5MB/5000B=5×106/5000=1×103 次因为DMA预处理和后处理的总开销为500个时钟周期,所以1秒钟之内用于DMA操作的时钟周期数为500×1×103=5×105故在DMA方式下,占整个CPU时间的百分比是((5×105)/(500×106))×100%=0.1%44.指令执行阶段每个节拍的功能和有效控制信号如下所示时钟 功能 有效控制信号C5 MAR←(R1) PCout,MARinC6 MDR←M(MAR) MemR,MDRinEC7 A←(R0) R0out,AinC8 AC←(MDR)+(A) MDRout,Addr,ACinC9 MDR←(AC) ACout,MDRinC10 M(MAR) ←MDR MDRoutE,MemW45.定义信号量S1控制P1与P2之间的同步;S2控制P1与P3之间的同步;empty 控制生产者与消费者之间的同步;mutex控制进程间互斥使用缓冲区。
程序如下:Var s1=0,s2=0,empty=N,mutex=1;ParbeginP1:beginX=produce(); /*生成一个数*/P(empty); /*判断缓冲区是否有空单元*/P(mutex); /*缓冲区是否被占用*/Put();If x%2==0V(s2); /*如果是偶数,向P3发出信号*/elseV(s1); /*如果是奇数,向P2发出信号*/V(mutex); /*使用完缓冲区,释放*/end.P2:beginP(s1); /*收到P1发来的信号,已产生一个奇数*/P(mutex); /*缓冲区是否被占用*/Getodd();Countodd():=countodd()+1;V(mutex); /*释放缓冲区*/V(empty); /*向P1发信号,多出一个空单元*/end.P3:beginP(s2) /*收到P1发来的信号,已产生一个偶数*/P(mutex); /*缓冲区是否被占用*/Geteven();Counteven():=counteven()+1;V(mutex); /*释放缓冲区*/V(empty); /*向P1发信号,多出一个空单元*/end.Parend.46.(1)根据页式管理的工作原理,应先考虑页面大小,以便将页号和页内位移分解出来。
页面大小为4KB,即212,则得到页内位移占虚地址的低12位,页号占剩余高位。
可得三个虚地址的页号P如下(十六进制的一位数字转换成4位二进制,因此,十六进制的低三位正好为页内位移,最高位为页号): 2362H:P=2,访问快表10ns,因初始为空,访问页表100ns得到页框号,合成物理地址后访问主存100ns,共计10ns+100ns+100ns=210ns。
1565H:P=1,访问快表10ns,落空,访问页表100ns落空,进行缺页中断处理108ns,合成物理地址后访问主存100ns,共计10ns+100ns+108ns+100ns≈108ns。
25A5H:P=2,访问快表,因第一次访问已将该页号放入快表,因此花费10ns 便可合成物理地址,访问主存100ns,共计10ns+100ns=110ns。
(2)当访问虚地址1565H时,产生缺页中断,合法驻留集为2,必须从页表中淘汰一个页面,根据题目的置换算法,应淘汰0号页面,因此1565H的对应页框号为101H。
由此可得1565H的物理地址为101565H。
47.(1)无类IP地址的核心是采用不定长的网络号和主机号,并通过相应的子网掩码来表示(即网络号部分为1,主机号部分为0)。
本题中网络地址位数是24,由于IP地址是32位,因此其主机号部分就是8位。
因此,子网掩码就是11111111 11111111 11111111 00000000,即255.255.255.0。
根据无类IP地址的规则,每个网段中有两个地址是不分配的:主机号全0表示网络地址,主机号全1表示广播地址。
因此8位主机号所能表示的主机数就是28-2,即254台。
该网络要划分为两个子网,每个子网要120台主机,因此主机位数X应该满足下面三个条件:X<8,因为是在主机号位长为8位的网络进行划分,所以X一定要小于8位。
2x>120,因为根据题意需要容纳120台主机。
X是整数。
解上述方程,得到X=7.子网掩码就是11111111 11111111 11111111 10000000,即255.255.255.128。
所以划分的两个网段是:202.118.1.0/25与202.118.1.128/25。
(2)填写R1的路由表填写到局域网1的路由。
局域网1的网络地址和掩码在问题(1)已经求出来了,为202.118.1.0/25。
则R1路由表应填入的网络地址为202.118.1.0,掩码为255.255.255.128。
由于局域网1是直接连接到路由器R1的E1口上的,因此,下一跳地址填写直接路由(Direct)。
接口填写E1.填写到局域网2的路由表1。
局域网2的网络地址和掩码在问题(1)中已经求出来了,为202.118.1.128/25。
则R1路由表应该填入的网络地址为202.118.1.128,掩码为255.255.255.128.由于局域网2是直接连接到路由器R1的E2口上的,因此,下一跳地址填写直接路由。
接口填写E2。
填写到域名服务器的路由。
由于域名服务器的IP地址为202.118.3.2,而该地址为主机地址,因此掩码为255.255.255.255。
同时,路由器R1要到DNS服务器,就需要通过路由器R2的接口L0才能到达,因此下一跳地址填写L0的IP 地址(202.118.2.2)。
填写互联网路由。
本题实质是编写默认路由。
默认路由是一种特殊的静态路由,指的是当路由表中与包的目的地址之间没有匹配的表项时路由器能够做出的选择。
如果没有默认路由器,那么目的地址在路由表中没有匹配表项的包将被丢弃。
默认路由在某些时候非常有效,当存在末梢网络时,默认路由会大大简化路由器的配置,减轻管理员的工作负担,提高网络性能。
默认路由叫做“0/0”路由,因为路由的IP地址0.0.0.0,而子网掩码也是0.0.0.0。
同时路由器R1连接的网络需要通过路由器R2的L0口才能到达互联网络,因此下一跳地址填写L0的IP为202.118.2.2。
综上,填写的路由表如下:R1路由表目的网络IP地址 子网掩码 下一跳IP地址 接口202.118.1.0 255.255.255.128 Direct E1202.118.1.128 255.255.255.128 Direct E2202.118.3.2 255.255.255.255 202.118.2.2 L00.0.0.0 0.0.0.0 202.118.2.2 L0(3)填写R2到局域网1和局域网2的路由表2。
局域网1和局域网2的地址可以聚合为202.118.1.0/24,而R2去往局域网1和局域网2都是同一条路径。
因此,路由表里面只需要填写到202.118.1.0/24网络的路由即可,如下表所示R2路由表目的网络IP地址 子网掩码 下一跳IP地址 接口202.118.1.0 255.255.255.0 202.118.2.1 L0。
