A State Machine Based Approach for a Process Driven Development of Web-Applications
国际自动化与计算杂志.英文版.

国际自动化与计算杂志.英文版.1.Improved Exponential Stability Criteria for Uncertain Neutral System with Nonlinear Parameter PerturbationsFang Qiu,Ban-Tong Cui2.Robust Active Suspension Design Subject to Vehicle Inertial Parameter VariationsHai-Ping Du,Nong Zhang3.Delay-dependent Non-fragile H∞ Filtering for Uncertain Fuzzy Systems Based on Switching Fuzzy Model and Piecewise Lyapunov FunctionZhi-Le Xia,Jun-Min Li,Jiang-Rong Li4.Observer-based Adaptive Iterative Learning Control for Nonlinear Systems with Time-varying DelaysWei-Sheng Chen,Rui-Hong Li,Jing Li5.H∞ Output Feedback Control for Stochastic Systems with Mode-dependent Time-varying Delays and Markovian Jump ParametersXu-Dong Zhao,Qing-Shuang Zeng6.Delay and Its Time-derivative Dependent Robust Stability of Uncertain Neutral Systems with Saturating ActuatorsFatima El Haoussi,El Houssaine Tissir7.Parallel Fuzzy P+Fuzzy I+Fuzzy D Controller:Design and Performance EvaluationVineet Kumar,A.P.Mittal8.Observers for Descriptor Systems with Slope-restricted NonlinearitiesLin-Na Zhou,Chun-Yu Yang,Qing-Ling Zhang9.Parameterized Solution to a Class of Sylvester MatrixEquationsYu-Peng Qiao,Hong-Sheng Qi,Dai-Zhan Cheng10.Indirect Adaptive Fuzzy and Impulsive Control of Nonlinear SystemsHai-Bo Jiang11.Robust Fuzzy Tracking Control for Nonlinear Networked Control Systems with Integral Quadratic ConstraintsZhi-Sheng Chen,Yong He,Min Wu12.A Power-and Coverage-aware Clustering Scheme for Wireless Sensor NetworksLiang Xue,Xin-Ping Guan,Zhi-Xin Liu,Qing-Chao Zheng13.Guaranteed Cost Active Fault-tolerant Control of Networked Control System with Packet Dropout and Transmission DelayXiao-Yuan Luo,Mei-Jie Shang,Cai-Lian Chen,Xin-Ping Guanparison of Two Novel MRAS Based Strategies for Identifying Parameters in Permanent Magnet Synchronous MotorsKan Liu,Qiao Zhang,Zi-Qiang Zhu,Jing Zhang,An-Wen Shen,Paul Stewart15.Modeling and Analysis of Scheduling for Distributed Real-time Embedded SystemsHai-Tao Zhang,Gui-Fang Wu16.Passive Steganalysis Based on Higher Order Image Statistics of Curvelet TransformS.Geetha,Siva S.Sivatha Sindhu,N.Kamaraj17.Movement Invariants-based Algorithm for Medical Image Tilt CorrectionMei-Sen Pan,Jing-Tian Tang,Xiao-Li Yang18.Target Tracking and Obstacle Avoidance for Multi-agent SystemsJing Yan,Xin-Ping Guan,Fu-Xiao Tan19.Automatic Generation of Optimally Rigid Formations Using Decentralized MethodsRui Ren,Yu-Yan Zhang,Xiao-Yuan Luo,Shao-Bao Li20.Semi-blind Adaptive Beamforming for High-throughput Quadrature Amplitude Modulation SystemsSheng Chen,Wang Yao,Lajos Hanzo21.Throughput Analysis of IEEE 802.11 Multirate WLANs with Collision Aware Rate Adaptation AlgorithmDhanasekaran Senthilkumar,A. Krishnan22.Innovative Product Design Based on Customer Requirement Weight Calculation ModelChen-Guang Guo,Yong-Xian Liu,Shou-Ming Hou,Wei Wang23.A Service Composition Approach Based on Sequence Mining for Migrating E-learning Legacy System to SOAZhuo Zhang,Dong-Dai Zhou,Hong-Ji Yang,Shao-Chun Zhong24.Modeling of Agile Intelligent Manufacturing-oriented Production Scheduling SystemZhong-Qi Sheng,Chang-Ping Tang,Ci-Xing Lv25.Estimation of Reliability and Cost Relationship for Architecture-based SoftwareHui Guan,Wei-Ru Chen,Ning Huang,Hong-Ji Yang1.A Computer-aided Design System for Framed-mould in Autoclave ProcessingTian-Guo Jin,Feng-Yang Bi2.Wear State Recognition of Drills Based on K-means Cluster and Radial Basis Function Neural NetworkXu Yang3.The Knee Joint Design and Control of Above-knee Intelligent Bionic Leg Based on Magneto-rheological DamperHua-Long Xie,Ze-Zhong Liang,Fei Li,Li-Xin Guo4.Modeling of Pneumatic Muscle with Shape Memory Alloy and Braided SleeveBin-Rui Wang,Ying-Lian Jin,Dong Wei5.Extended Object Model for Product Configuration DesignZhi-Wei Xu,Ze-Zhong Liang,Zhong-Qi Sheng6.Analysis of Sheet Metal Extrusion Process Using Finite Element MethodXin-Cun Zhuang,Hua Xiang,Zhen Zhao7.Implementation of Enterprises' Interoperation Based on OntologyXiao-Feng Di,Yu-Shun Fan8.Path Planning Approach in Unknown EnvironmentTing-Kai Wang,Quan Dang,Pei-Yuan Pan9.Sliding Mode Variable Structure Control for Visual Servoing SystemFei Li,Hua-Long Xie10.Correlation of Direct Piezoelectric Effect on EAPap under Ambient FactorsLi-Jie Zhao,Chang-Ping Tang,Peng Gong11.XML-based Data Processing in Network Supported Collaborative DesignQi Wang,Zhong-Wei Ren,Zhong-Feng Guo12.Production Management Modelling Based on MASLi He,Zheng-Hao Wang,Ke-Long Zhang13.Experimental Tests of Autonomous Ground Vehicles with PreviewCunjia Liu,Wen-Hua Chen,John Andrews14.Modelling and Remote Control of an ExcavatorYang Liu,Mohammad Shahidul Hasan,Hong-Nian Yu15.TOPSIS with Belief Structure for Group Belief Multiple Criteria Decision MakingJiang Jiang,Ying-Wu Chen,Da-Wei Tang,Yu-Wang Chen16.Video Analysis Based on Volumetric Event DetectionJing Wang,Zhi-Jie Xu17.Improving Decision Tree Performance by Exception HandlingAppavu Alias Balamurugan Subramanian,S.Pramala,B.Rajalakshmi,Ramasamy Rajaram18.Robustness Analysis of Discrete-time Indirect Model Reference Adaptive Control with Normalized Adaptive LawsQing-Zheng Gao,Xue-Jun Xie19.A Novel Lifecycle Model for Web-based Application Development in Small and Medium EnterprisesWei Huang,Ru Li,Carsten Maple,Hong-Ji Yang,David Foskett,Vince Cleaver20.Design of a Two-dimensional Recursive Filter Using the Bees AlgorithmD. T. Pham,Ebubekir Ko(c)21.Designing Genetic Regulatory Networks Using Fuzzy Petri Nets ApproachRaed I. Hamed,Syed I. Ahson,Rafat Parveen1.State of the Art and Emerging Trends in Operations and Maintenance of Offshore Oil and Gas Production Facilities: Some Experiences and ObservationsJayantha P.Liyanage2.Statistical Safety Analysis of Maintenance Management Process of Excavator UnitsLjubisa Papic,Milorad Pantelic,Joseph Aronov,Ajit Kumar Verma3.Improving Energy and Power Efficiency Using NComputing and Approaches for Predicting Reliability of Complex Computing SystemsHoang Pham,Hoang Pham Jr.4.Running Temperature and Mechanical Stability of Grease as Maintenance Parameters of Railway BearingsJan Lundberg,Aditya Parida,Peter S(o)derholm5.Subsea Maintenance Service Delivery: Mapping Factors Influencing Scheduled Service DurationEfosa Emmanuel Uyiomendo,Tore Markeset6.A Systemic Approach to Integrated E-maintenance of Large Engineering PlantsAjit Kumar Verma,A.Srividya,P.G.Ramesh7.Authentication and Access Control in RFID Based Logistics-customs Clearance Service PlatformHui-Fang Deng,Wen Deng,Han Li,Hong-Ji Yang8.Evolutionary Trajectory Planning for an Industrial RobotR.Saravanan,S.Ramabalan,C.Balamurugan,A.Subash9.Improved Exponential Stability Criteria for Recurrent Neural Networks with Time-varying Discrete and Distributed DelaysYuan-Yuan Wu,Tao Li,Yu-Qiang Wu10.An Improved Approach to Delay-dependent Robust Stabilization for Uncertain Singular Time-delay SystemsXin Sun,Qing-Ling Zhang,Chun-Yu Yang,Zhan Su,Yong-Yun Shao11.Robust Stability of Nonlinear Plants with a Non-symmetric Prandtl-Ishlinskii Hysteresis ModelChang-An Jiang,Ming-Cong Deng,Akira Inoue12.Stability Analysis of Discrete-time Systems with Additive Time-varying DelaysXian-Ming Tang,Jin-Shou Yu13.Delay-dependent Stability Analysis for Markovian Jump Systems with Interval Time-varying-delaysXu-Dong Zhao,Qing-Shuang Zeng14.H∞ Synchronization of Chaotic Systems via Delayed Feedback ControlLi Sheng,Hui-Zhong Yang15.Adaptive Fuzzy Observer Backstepping Control for a Class of Uncertain Nonlinear Systems with Unknown Time-delayShao-Cheng Tong,Ning Sheng16.Simulation-based Optimal Design of α-β-γ-δ FilterChun-Mu Wu,Paul P.Lin,Zhen-Yu Han,Shu-Rong Li17.Independent Cycle Time Assignment for Min-max SystemsWen-De Chen,Yue-Gang Tao,Hong-Nian Yu1.An Assessment Tool for Land Reuse with Artificial Intelligence MethodDieter D. Genske,Dongbin Huang,Ariane Ruff2.Interpolation of Images Using Discrete Wavelet Transform to Simulate Image Resizing as in Human VisionRohini S. Asamwar,Kishor M. Bhurchandi,Abhay S. Gandhi3.Watermarking of Digital Images in Frequency DomainSami E. I. Baba,Lala Z. Krikor,Thawar Arif,Zyad Shaaban4.An Effective Image Retrieval Mechanism Using Family-based Spatial Consistency Filtration with Object RegionJing Sun,Ying-Jie Xing5.Robust Object Tracking under Appearance Change ConditionsQi-Cong Wang,Yuan-Hao Gong,Chen-Hui Yang,Cui-Hua Li6.A Visual Attention Model for Robot Object TrackingJin-Kui Chu,Rong-Hua Li,Qing-Ying Li,Hong-Qing Wang7.SVM-based Identification and Un-calibrated Visual Servoing for Micro-manipulationXin-Han Huang,Xiang-Jin Zeng,Min Wang8.Action Control of Soccer Robots Based on Simulated Human IntelligenceTie-Jun Li,Gui-Qiang Chen,Gui-Fang Shao9.Emotional Gait Generation for a Humanoid RobotLun Xie,Zhi-Liang Wang,Wei Wang,Guo-Chen Yu10.Cultural Algorithm for Minimization of Binary Decision Diagram and Its Application in Crosstalk Fault DetectionZhong-Liang Pan,Ling Chen,Guang-Zhao Zhang11.A Novel Fuzzy Direct Torque Control System for Three-level Inverter-fed Induction MachineShu-Xi Liu,Ming-Yu Wang,Yu-Guang Chen,Shan Li12.Statistic Learning-based Defect Detection for Twill FabricsLi-Wei Han,De Xu13.Nonsaturation Throughput Enhancement of IEEE 802.11b Distributed Coordination Function for Heterogeneous Traffic under Noisy EnvironmentDhanasekaran Senthilkumar,A. Krishnan14.Structure and Dynamics of Artificial Regulatory Networks Evolved by Segmental Duplication and Divergence ModelXiang-Hong Lin,Tian-Wen Zhang15.Random Fuzzy Chance-constrained Programming Based on Adaptive Chaos Quantum Honey Bee Algorithm and Robustness AnalysisHan Xue,Xun Li,Hong-Xu Ma16.A Bit-level Text Compression Scheme Based on the ACW AlgorithmHussein A1-Bahadili,Shakir M. Hussain17.A Note on an Economic Lot-sizing Problem with Perishable Inventory and Economies of Scale Costs:Approximation Solutions and Worst Case AnalysisQing-Guo Bai,Yu-Zhong Zhang,Guang-Long Dong1.Virtual Reality: A State-of-the-Art SurveyNing-Ning Zhou,Yu-Long Deng2.Real-time Virtual Environment Signal Extraction and DenoisingUsing Programmable Graphics HardwareYang Su,Zhi-Jie Xu,Xiang-Qian Jiang3.Effective Virtual Reality Based Building Navigation Using Dynamic Loading and Path OptimizationQing-Jin Peng,Xiu-Mei Kang,Ting-Ting Zhao4.The Skin Deformation of a 3D Virtual HumanXiao-Jing Zhou,Zheng-Xu Zhao5.Technology for Simulating Crowd Evacuation BehaviorsWen-Hu Qin,Guo-Hui Su,Xiao-Na Li6.Research on Modelling Digital Paper-cut PreservationXiao-Fen Wang,Ying-Rui Liu,Wen-Sheng Zhang7.On Problems of Multicomponent System Maintenance ModellingTomasz Nowakowski,Sylwia Werbinka8.Soft Sensing Modelling Based on Optimal Selection of Secondary Variables and Its ApplicationQi Li,Cheng Shao9.Adaptive Fuzzy Dynamic Surface Control for Uncertain Nonlinear SystemsXiao-Yuan Luo,Zhi-Hao Zhu,Xin-Ping Guan10.Output Feedback for Stochastic Nonlinear Systems with Unmeasurable Inverse DynamicsXin Yu,Na Duan11.Kalman Filtering with Partial Markovian Packet LossesBao-Feng Wang,Ge Guo12.A Modified Projection Method for Linear FeasibilityProblemsYi-Ju Wang,Hong-Yu Zhang13.A Neuro-genetic Based Short-term Forecasting Framework for Network Intrusion Prediction SystemSiva S. Sivatha Sindhu,S. Geetha,M. Marikannan,A. Kannan14.New Delay-dependent Global Asymptotic Stability Condition for Hopfield Neural Networks with Time-varying DelaysGuang-Deng Zong,Jia Liu hHTTp://15.Crosscumulants Based Approaches for the Structure Identification of Volterra ModelsHouda Mathlouthi,Kamel Abederrahim,Faouzi Msahli,Gerard Favier1.Coalition Formation in Weighted Simple-majority Games under Proportional Payoff Allocation RulesZhi-Gang Cao,Xiao-Guang Yang2.Stability Analysis for Recurrent Neural Networks with Time-varying DelayYuan-Yuan Wu,Yu-Qiang Wu3.A New Type of Solution Method for the Generalized Linear Complementarity Problem over a Polyhedral ConeHong-Chun Sun,Yan-Liang Dong4.An Improved Control Algorithm for High-order Nonlinear Systems with Unmodelled DynamicsNa Duan,Fu-Nian Hu,Xin Yu5.Controller Design of High Order Nonholonomic System with Nonlinear DriftsXiu-Yun Zheng,Yu-Qiang Wu6.Directional Filter for SAR Images Based on NonsubsampledContourlet Transform and Immune Clonal SelectionXiao-Hui Yang,Li-Cheng Jiao,Deng-Feng Li7.Text Extraction and Enhancement of Binary Images Using Cellular AutomataG. Sahoo,Tapas Kumar,B.L. Rains,C.M. Bhatia8.GH2 Control for Uncertain Discrete-time-delay Fuzzy Systems Based on a Switching Fuzzy Model and Piecewise Lyapunov FunctionZhi-Le Xia,Jun-Min Li9.A New Energy Optimal Control Scheme for a Separately Excited DC Motor Based Incremental Motion DriveMilan A.Sheta,Vivek Agarwal,Paluri S.V.Nataraj10.Nonlinear Backstepping Ship Course ControllerAnna Witkowska,Roman Smierzchalski11.A New Method of Embedded Fourth Order with Four Stages to Study Raster CNN SimulationR. Ponalagusamy,S. Senthilkumar12.A Minimum-energy Path-preserving Topology Control Algorithm for Wireless Sensor NetworksJin-Zhao Lin,Xian Zhou,Yun Li13.Synchronization and Exponential Estimates of Complex Networks with Mixed Time-varying Coupling DelaysYang Dai,YunZe Cai,Xiao-Ming Xu14.Step-coordination Algorithm of Traffic Control Based on Multi-agent SystemHai-Tao Zhang,Fang Yu,Wen Li15.A Research of the Employment Problem on Common Job-seekersand GraduatesBai-Da Qu。
A Survey of Cyber-Physical Systems

A Survey of Cyber-Physical SystemsJiafu Wan a,ba School of Computer Science and EngineeringSouth China University of Technology,Guangzhou,Chinajiafuwan_76@Hehua Yan*,b,Hui Suo bb College of Information EngineeringGuangdong Jidian PolytechnicGuangzhou,China*Corresponding Author,hehua_yan@Abstract—Cyber Physical Systems(CPSs)are characterized by integrating computation and physical processes.The theories and applications of CPSs face the enormous challenges.The aim of this work is to provide a better understanding of this emerging multi-disciplinary methodology.First,the features of CPSs are described,and the research progresses are summarized from different perspectives such as energy control,secure control, transmission and management,control technique,system resource allocation,and model-based software design.Then three classic applications are given to show that the prospects of CPSs are engaging.Finally,the research challenges and some suggestions for future work are in brief outlined.Keywords-cyber physical systems(CPSs);communications; computation;controlI.I NTRODUCTIONCyber Physical Systems(CPSs)integrate the dynamics of the physical processes with those of the software and communication,providing abstractions and modeling,design, and analysis techniques for the integrated whole[1].The dynamics among computers,networking,and physical systems interact in ways that require fundamentally new design technologies.The technology depends on the multi-disciplines such as embedded systems,computers,communications,etc. and the software is embedded in devices whose principle mission is not computation alone,e.g.cars,medical devices, scientific instruments,and intelligent transportation systems[2]. Now the project for CPSs engages the related researchers very much.Since2006,the National Science Foundation(NSF)has awarded large amounts of funds to a research project for CPSs. Many universities and institutes(e.g.UCB,Vanderbilt, Memphis,Michigan,Notre Dame,Maryland,and General Motors Research and Development Center,etc.)join this research project[3,4].Besides these,the researchers from other countries have started to be aware of significance for CPSs research.In[5-7],the researchers are interested in this domain,including theoretical foundations,design and implementation,real-world applications,as well as education. As a whole,although the researchers have made some progress in modeling,control of energy and security,approach of software design,etc.the CPSs are just in an embryonic stage.The rest of this paper is outlined as follows.Section II introduces the features of CPSs.From different perspectives, the research processes are summarized in Section III.Section IV gives some classic applications.Section V outlines the research challenges and some suggestions for future work and Section VI concludes this paper.II.F EATURES OF CPS SGoals of CPSs research program are to deeply integrate physical and cyber design.The diagrammatic layout for CPSs is shown in Figure1.Obviously,CPSs are different from desktop computing,traditional embedded/real-time systems, today’s wireless sensor network(WSN),etc.and they have some defining characteristics as follows[7-10].∙Closely integrated.CPSs are the integrations of computation and physical processes.∙Cyber capability in every physical component and resource-constrained.The software is embedded inevery embedded system or physical component,andthe system resources such as computing,networkbandwidth,etc.are usually limited.∙Networked at multiple and extreme scales.CPSs,the networks of which include wired/wireless network,WLAN,Bluetooth,GSM,etc.are distributed systems.Moreover,the system scales and device categoriesappear to be highly varied.∙Complex at multiple temporal and spatial scales.In CPSs,the different component has probablyinequable Figure1.Diagrammatic layout for CPSsgranularity of time and spatiality,and CPSs are strictlyconstrained by spatiality and real time.∙Dynamically reorganizing/reconfiguring.CPSs as very complicated systems must have adaptive capabilities.∙High degrees of automation,control loops must close.CPSs are in favor of convenient man-machineinteraction,and the advanced feedback controltechnologies are widely applied to these systems.∙Operation must be dependable,certified in some cases.As a large scale/complicated system,the reliability andsecurity are necessary for CPSs.III.R EASEARCH P ROCESSSince2007,American government has treated CPSs as a new development strategy.Some researchers from various countries discussed the related concepts,technologies, applications and challenges during CPSweek and the international conference on CPS subject[11].The results of this research mainly concentrate in the following respects[7]. A.Energy ControlOne of the features of CPSs is distributed system.Though the vast majority of devices in CPSs need less energy,the energy supply is still a great challenge because the demand and supply of energy is inconvenient.In[12],a control strategy is proposed for realizing best trade-off between satisfying user requests and energy consumption in a data center.In[13-15],these papers concern the basic modeling of cyber-based physical energy systems.A novel cyber-based dynamic model is proposed in which a resulting mathematical model greatly depends on the cyber technologies supporting the physical system.F.M.Zhang et al [16]design optimal and adaptive discharge profile for a square wave impulsive current to achieve maximum battery life.J. Wei et al and C.J.Xue et al[17,18]develop an optimal lazy scheduler to manage services with minimum energy expenditure while not violating time-sensitive constraints.In [19],a peak inlet temperature minimization problem is formulated to improve the energy efficiency.J.R.Cao et al[20] present a clustering architecture in order to obtain good performance in energy efficiency.B.Secure ControlNow,the research for secure control mainly includes key management,identity authentication,etc.In[21],the existing security technologies for CPSs are summarized,and main challenges are proposed.C.Singh et al[22]explore the topic of the reliability assurance of CPSs and possibly stimulate more research in this area.T.T.Gamage et al[23]give a general theory of event compensation as an information flow security enforcement mechanism for CPSs.Then a case study is used to demonstrate this concept.In[24],a certifcateless signature scheme for mobile wireless CPSs is designed and validated.Y.Zhang et al[25]present an adaptive health monitoring and management system model that defines the fault diagnosis quality metrics and supports diagnosis requirement specifications.J.Wei et al[26]exploit message scheduling solutions to improve security quality of wireless networks for mission-critical cyber-physical applications.C.Transmission and ManagementCPSs need to conduct the transmission and management of multi-modal data generated by different sensor devices.In[27], a novel information-centric approach for timely,secure real-time data services in CPSs is proposed.In order to obtain the crucial data for optimal environment abstraction,L.H.Kong et al[28]study the spatio-temporal distribution of CPS nodes.H. Ahmadi et al[29]present an innovative congestion control mechanism for accurate estimation of spatio-temporal phenomena in wireless sensor networks performing monitoring applications.A dissertation on CPSs discusses the design, implementation,and evaluation of systems and algorithms that enable predictable and scalable real-time data services for CPS applications[30].Now,the exiting results are still rare,and there are many facets to be studied.D.Model-based Software DesignNow,the main model-based software design methods include Model Driven Development(MDD)(e.g.UML), Model-Integrated Computing(MIC),Domain-Specific Modeling(DSM),etc[31,32].An example,abstractions in the design flow for DSM,is shown in Figure2.These methods have been widely applied to the embedded system design[34, 35].On the basis of these,some researchers conduct model-based software design for CPSs in the following aspects:event model,physical model,reliability and real-time assurance,etc.Figure2.Abstractions in the design flow for DSM[33]1)Event model.E.A.Lee et al[36]make a case that the time is right to introduce temporal semantics into programming models for CPSs.A programming model called programming temporally-integrated distributed embedded systems(PTIDES) provides a coordination language rooted in discrete-event semantics,supported by a lightweight runtime framework and tools for verifying concurrent software components.In[37],a concept lattice-based event model for CPSs is proposed.This model not only captures the essential information about events in a distributed and heterogeneous environment,but it alsoPlatform mapping Abstractions are linkedthrough refinementrelationsAbstraction layers allowthe verification ofdifferent propertiesPlatform mappingAbstraction layersdefine platformsallows events to be composed across different boundaries of different components and devices within and among both cyber and physical domains.In addition,A CPS architecture along with a novel event model for CPS is developed[38].2)Physical model.In[39],a methodology for automatically abstracting models of CPSs is proposed.The models are described using a user-defined language inspired by assembly code.For mechanical systems,Y.Zhu et al[40]show how analytical models of a particular class of physical systems can be automatically mapped to executable simulation codes.S.Jha et al[41]present a new approach to assist designers by synthesizing the switching logic,given a partial system model, using a combination of fixpoint computation,numerical simulation,and machine learning.This technique quickly generates intuitive system models.3)Reliability and real-time assurance. E. A.Lee[42] emphasizes the importance of security,reliability and real-time assurance in CPSs,and considers the effective orchestration of software and physical processes requires semantic models. From the perspective of soft real-time and hard real-time,U. Kremer[43]conducts the research that the role of time in CPS applications has a fundamental impact on the design and requirements.In CPSs,the heterogeneity causes major challenges for compositional design of large-scale systems including fundamental problems caused by network uncertainties,such as time-varying delay,jitter,data rate limitations,packet loss and others.To address these implementation uncertainties,X.Koutsoukos et al[44]propose a passive control architecture.For improving reliability,T.L. Crenshaw et al[45]describe a simplex reference model to assist developers with CPS architectures which limit fault-propagation.A highly configurable and reusable middleware framework for real-time hybrid testing is provided in[46].Though the model-based software design has an early start, the present development of CPSs progresses at a fast enough rate to provide a competitive challenge.E.Control TechniqueCompared with other control applications,the control technique for CPSs is still at an elementary stage.F.M.Zhang et al[2]develop theoretical results in designing scheduling algorithms for control applications of CPS to achieve balances among robustness,schedulability and power consumption. Moreover,an inverted pendulum as a study object is designed to validate the proposed theory.N.Kottenstette et al[47] describe a general technique:passivity and a particular controller structure involving the resilient power junction.In [48],a design and implementation of CPSs for neutrally controlled artificial legs is proposed.In[49],J.L.Ny et al approach the problem of certifying a digital controller implementation from an input-output,robust control perspective.F.System Resource AllocationUntil now,the relative research for system resource allocation mainly focuses on embedded/real-time systems, networked control systems,WSN,etc[50-52].Towards the complicated CPSs,this work is in the beginning stage.V.Liberatore[53]gives a new train of thought on bandwidth allocation in CPSs.In[54],the model dynamics are presented to express the properties of both software and hardware of CPSs,which is used to do resource allocation.K.W.Li et al [55]research the problem of designing a distributed algorithm for joint optimal congestion control and channel assignment in the multi-radio multi-channel networks for CPSs.The ductility metric is developed to characterize the overload behavior of mixed-criticality CPSs in[56].IV.C LASSIC A PPLICATIONSApplications of CPSs include medical devices and systems, assisted living,traffic control and safety,advanced automotive systems,process control,energy conservation,environmental control avionics and aviation software,instrumentation,critical infrastructure(e.g.power,water),distributed robotics,weapons systems,manufacturing,distributed sensing command and control,smart structures,biosystems,communications systems, etc.[9,10].The classic application architecture of CPSs is described in[38].Now,some application cases for CPSs have been conducted in[57-64].Here,three examples(Health Care and Medicine,Intelligent Road and Unmanned Vehicle,and Electric Power Grid)are used to illuminate the classic applications of CPSs[8,9].A.Health Care and MedicineThe domain of health care and medicine includes national health information network,electronic patient record initiative, home care,operating room,etc.some of which are increasingly controlled by computer systems with hardware and software components,and are real-time systems with safety and timing requirements.A case of CPSs,an operating room,is shown in Figure3.Figure3.A case of CPSs:An operating room[8,9]B.Electric Power GridThe power electronics,power grid,and embedded control software form a CPS,whose design is heavily influenced by fault tolerance,security,decentralized control,and economic/ ethical social aspects[65].In[8,9],a case of CPSs,electric power grid,is given as shown in Figure4.Figure4.A case of CPSs:Electric power grid[8,9]C.Integrate Intelligent Road with Unmanned VehicleWith the development of sensor network,embedded systems,etc.some new solutions can be applied to unmanned vehicle.We are conducting a program that intelligent road and unmanned vehicle are integrated in the form of CPSs.Figure5 shows another case of CPSs:Integrate intelligent road with unmanned vehicle.Figure5.A case of CPSs:Integrate intelligent road with unmanned vehicleV.R ESEARCH C HALLENGESCPSs as a very active research field,a variety of questions need to be solved,at different layers of the architecture and from different aspects of systems design,to trigger and to ease the integration of the physical and cyber worlds[66].In[10, 42,66-68],the research challenges are mainly summarized as follows:1)Control and hybrid systems.A new mathematical theory must merge event-based systems with time-based systems for feedback control.This theory also must be suitable for hierarchies involving asynchronous dynamics at different time scales and geographic scope.2)Sensor and mobile networks.In practical applications, the need for increased system autonomy requires self-organizing/reorganizing mobile networks for CPSs.Gathering and refining critical information from the vast amount of raw data is essential.3)Robustness,reliability,safety,and security.It is a critical challenge because uncertainty in the environment,security attacks,and errors in physical devices make ensuring overall system robustness,security,and safety.Exploiting the physical nature of CPS by leveraging location-based,time-based and tag-based mechanisms is to realize security solutions.4)Abstractions.This aspect includes real-time embedded systems abstractions and computational abstractions,which needs new resource allocation scheme to ensure that fault tolerance,scalability,optimization,etc.are achieved.New distributed real-time computing and real-time group communication methods are needed.In addition,the physical properties also should be captured by programming abstractions.5)Model-based development.Though there several existing model-based development methods,they are far from meeting demands in puting and communications,and physical dynamics must be abstracted and modeled at different levels of scale,locality,and time granularity.6)Verification,validation,and certification.The interaction between formal methods and testing needs to be established. We should apply the heterogeneous nature of CPS models to compositional verification and testing methods.VI.C ONCLUSIONSIn the last few years,this emerging domain for CPSs has been attracting the significant interest,and will continue for the years to come.In spite of rapid evolution,we are still facing new difficulties and severe challenges.In this literature, we concisely review the existing research results that involve energy control,secure control,model-based software design transmission and management,control technique,etc.On this basis,some classic applications used to show the good prospects.Then,we propose several research issues and encourage more insight into this new field.A CKNOWLEDGMENTThe authors would like to thank the National Natural Science Foundation of China(No.50875090,50905063), National863Project(No.2009AA4Z111),Key Science and Technology Program of Guangdong Province(No. 2010B010700015),China Postdoctoral Science Foundation (No.20090460769)and Open Foundation of Guangdong Key Laboratoryof Modern Manufacturing Technology(No. GAMTK201002)for their support in this research.R EFERENCES[1]Available at:/cps/.[2] F.M.Zhang,K.Szwaykowska,W.Wolf,and V.Mooney,“Taskscheduling for control oriented requirements for Cyber-Physical Systems,”in Proc.of2008Real-Time Systems Symposium,2005,pp.47-56.[3]Available at:/news/17248-nsf-funds-cyber-physical-systems-project/.[4]J.Sprinkle,U.Arizona,and S.S.Sastry,“CHESS:Building a Cyber-Physical Agenda on solid foundations,”Presentation Report,Apr2008.[5]Available at:/.[6]Available at:/gdcps.html.[7]J.Z.Li,H.Gao,and B.Yu,“Concepts,features,challenges,andresearch progresses of CPSs,”Development Report of China Computer Science in2009,pp.1-17.[8]R.Rajkumar,“CPS briefing,”Carnegie Mellon University,May2007.[9] B.H.Krogh,“Cyber Physical Systems:the need for new models anddesign paradigms,”Presentation Report,Carnegie Mellon University. [10] B.X.Huang,“Cyber Physical Systems:A survey,”Presentation Report,Jun2008.[11]Available at:/.[12]L.Parolini,N.Toliaz,B.Sinopoli,and B.H.Krogh,“A Cyber-PhysicalSystems approach to energy management in data centers,”in Proc.of First International Conference on Cyber-Physical Systems.April2010, Stockholm,Sweden.[13] F.M.Zhang,Z.W.Shi,and W.Wolf,“A dynamic battery model forco-design in cyber-physical systems,”in Proc.of29th IEEE International Conference on Distributed Computing Systems Workshops.2009.[14]M.D.Ilić,L.Xie,U.A.Khan,et al.“Modeling Future Cyber-PhysicalEnergy Systems,”in Proc.of Power and Energy Society General Meeting-Conversion and Delivery of Electrical Energy in the21st Century,2008.[15]M.D.Ilić,L.Xie,U.A.Khan,et al.“Modeling of future Cyber–Physical Energy Systems for distributed sensing and control,”IEEE Transactions on Systems,Man,and Cybernetics-Part A:Systems and Humans,Vol.40,2010,pp.825-838.[16] F.M.Zhang,and Z.W.Shi,“Optimal and adaptive battery dischargestrategies for Cyber-Physical Systems,”in Proc.of Joint48th IEEE Conference on Decision and Control,and28th Chinese Control Conference,2009,Shanghai,China.[17]W.Jiang,G.Z.Xiong,and X.Y.Ding,“Energy-saving servicescheduling for low-end Cyber-Physical Systems,”in Proc.of The9th International Conference for Young Computer Scientists,2008.[18] C.J.Xue,G.L.Xing,Z.H.Yuan,et al.“Joint sleep scheduling andmode assignment in Wireless Cyber-Physical Systems,”in Proc.of29th IEEE International Conference on Distributed Computing Systems Workshops,2009.[19]Q.H.Tang,S.K.S.Gupta,and G.Varsamopoulos,“Energy-efficientthermal-aware task scheduling for homogeneous high-performance computing data centers:A cyber-physical approach,”IEEE Transactions on Parallel and Distributed Systems,Vol.19,2008,pp.1458-1472. [20]J.R.Cao,and H.A.Li,“Energy-efficient structuralized clustering forsensor-based Cyber Physical Systems,”in Proc.of Symposia and Workshops on Ubiquitous,Autonomic and Trusted Computing,2009. [21] A. A.Cárdenas,S.Amin,and S.Sastry,“Secure control:towardssurvivable Cyber-Physical Systems,”in Proc.of The28th International Conference on Distributed Computing Systems Workshops,2008. [22] C.Singh,and A.Sprintson,“Reliability assurance of Cyber-PhysicalPower Systems,”in Conference Proc.,2010.[23]T.T.Gamage,B.M.McMillin,and T.P.Roth,“Enforcing informationflow security properties in Cyber-Physical Systems:A generalized framework based on compensation,”in Proc.of34th Annual IEEE Computer Software and Applications Conference Workshops,2010. [24]Z.Xu,X.Liu,G.Q.Z,et al.“A cert ificateless signature scheme formobile wireless Cyber-Physical Systems,”in Proc.of The28th International Conference on Distributed Computing Systems Workshops, 2008.[25]Y.Zhang,I.L.Yen,F.B.Bastani,et al.“Optimal adaptive systemhealth monitoring and diagnosis for resource constrained Cyber-Physical Systems,”in Proc.of20th International Symposium on Software Reliability Engineering,2009.[26]W.Jiang,W.H.Guo,and N.Sang,“Periodic real-time messagescheduling for confidentiality-aware Cyber-Physical System in wireless networks,”in Proc.of Fifth International Conference on Frontier of Computer Science and Technology,2010.[27]K.D.Kang,and S.H.Son,“Real-time data services for Cyber PhysicalSystems,”in Proc.of28th International Conference on Distributed Computing Systems Workshops,2008.[28]L.H.Kong,D.W.Jiang,and M.Y.Wu,“Optimizing the spatio-temporal distribution of Cyber-Physical Systems for environment abstraction,”in Proc.of International Conference on Distributed Computing Systems,2010.[29]H.Ahmadi,T.F.Abdelzaher,and I.Gupta,“Congestion control forspatio-temporal data in Cyber-Physical Systems,”in Proc.of the1st ACM/IEEE International Conference on Cyber-Physical Systems,2010.[30]W.Kang,“Adaptive real-time data management for Cyber-PhysicalSystems,”PhD Thesis,University of Virginia,2009.[31]Z.M.Song,“Devlopment method of embedded equipment controlsystems based on Model Integrated Computing,”PhD Thesis,South China University of Technology,2007.[32]Available at:/research/MIC.[33]J.Sztipanovits,“Cyber Physical Systems:New challenges for model-based design,”Presentation Report,Vanderbilt University,Apr2008. [34] F.Li,D.Li,J.F.Wan,et al.“Towards a component-based modelintegration approach for embedded computer control system,”in Proc.of International Conference on Computational Intelligence and Security, 2008.[35] D.Li,F.Li,and X.Huang,et al.“A model based integration frameworkfor computer numerical control system development,”Robotics and Computer-Integrated Manufacturing,Vol.26,2010,pp.848-860. [36] E.A.Lee,S.Matic,S.A.Seshia,et al.“The case for timing-centricdistributed software,”in Proc.of29th IEEE International Conference on Distributed Computing Systems Workshops,2009.[37]Y.Tan,M.C.Vuran,and S.Goddard,“A concept lattice-based eventmodel for Cyber-Physical Systems,”in Proc.of CCPS,Apr2010, Stockholm,Sweden.[38]Y.Tan,M.C.Vuran,and S.Goddard,“Spatio-temporal event model forCyber-Physical Systems,”in Proc.of29th IEEE International Conference on Distributed Computing Systems Workshops,2009. [39]R.A.Thacker,K.R.Jones,C.J.Myers,et al.“Automatic abstractionfor verification of Cyber-Physical Systems,”in Proc.of CCPS,Apr2010, Stockholm,Sweden.[40]Y.Zhu, E.Westbrook,J.Inoue,et al.“Mathematical equations asexecutable models of mechanical systems,”in Proc.of CCPS,Apr2010, Stockholm,Sweden.[41]S.Jha,S.Gulwani,S.A.Seshia,et al.“Synthesizing switching logic forsafety and dwell-time requirements,”in Proc.of CCPS,Apr2010, Stockholm,Sweden.[42] E.A.Lee,“Cyber Physical Systems:Design challenges,”in Proc.ofISORC,May,2008,Orlando,USA.[43]U.Kremer,“Cyber-Physical Systems:A case for soft real-time,”Available at:/.[44]X.Koutsoukos,N.Kottenstette,J.Hall,et al.“Passivity-based controldesign for Cyber-Physical Systems,”Available at:http://citeseerx.ist./.[45]T.L.Crenshaw, E.Gunter, C.L.Robinson,et al.“The simplexreference model:Limiting fault-propagation due to unreliable components in Cyber-Physical System architectures,”in Proc.of IEEE International Real-Time Systems Symposium,2008.[46]T.Tidwell,X.Y.Gao,H.M.Huang,et al.“Towards configurable real-time hybrid structural testing:A Cyber-Physical Systems approach,”in Proc.of IEEE International Symposium on Object/Component/Service-Oriented Real-Time Distributed Computing,2009.[47]N.Kottenstette,G.Karsai,and J.Sztipanovits,“A passivity-basedframework for resilient Cyber Physical Systems,”in Proc.of2nd International Symposium on Resilient Control Systems,2009.[48]H.Huang,Y.Sun,Q.Yang,et al.“Integrating neuromuscular and CyberSystems for neural control of artificial legs,”in Proc.of CCPS,Apr 2010,Stockholm,Sweden.[49]J.L.Ny,and G.J.Pappas,“Robustness analysis for the certification ofdigital controller implementations,”in Proc.of CCPS,Apr2010, Stockholm,Sweden.[50]J.F.Wan,D.Li,and P.Zhang,“Key technology of embedded systemimplementation for software-based CNC system,”Chinese Journal of Mechanical Engineering,Vol.23,2010,pp.241-248.[51]J.F.Wan,D.Li,H.H.Yan,and P.Zhang,“Fuzzy feedback schedulingalgorithm based on central processing unit utilization for a software-based computer numerical control system,”Journal of Engineering Manufacture,Vol.224,2010,pp.1133-1143.[52]J.F.Wan,and D.Li,“Fuzzy feedback scheduling algorithm based onoutput jitter in resource-constrained embedded systems,”In Proc.of International Conference on Challenges in Environmental Science and Computer Engineering,March2010,Wuhan,China.[53]V.Liberatore,“Bandwidth allocation in sense-and-respond systems,”Report,Available at:/~vxl11/NetBots/.[54]M.Lindberg,and K.E.Årzén,“Feedback control of cyber-physicalsystems with multi resource dependencies and model uncertainties,”in Proc.of the31st IEEE Real-Time Systems Symposium,Dec2010. [55]K.W.Li,Q.W.Liu,F.R.Wang,et al.“Joint optimal congestioncontrol and channel assignment for multi-radio multi-channel wireless networks in Cyber-Physical Systems,”in Proc.of Symposia and Workshops on Ubiquitous,Autonomic and Trusted Computing,2009. [56]kshmanan,D.Niz,R.Rajkumar,et al.“Resource allocation indistributed mixed-criticality Cyber-Physical Systems,”in Proc.of International Conference on Distributed Computing Systems,2010. [57] D.Dragomirescu,“Cyber-Physical Systems for aeronautic applications,”Presentation Report,2010,University of Toulouse,France.[58] A.M.K.Cheng,“Cyber-Physical Medical and Medication Systems,”inProc.of the28th International Conference on Distributed Computing Systems Workshops,2008.[59]T.Dillon,and E.Chang,“Cyber-Physical Systems as an embodiment ofdigital ecosystems,”in Proc.of4th IEEE International Conference on Digital Ecosystems and Technologies,2010.[60]J.Madden,B.McMillin,and A.Sinha,“Environmental obfuscation of aCyber Physical System-Vehicle example,”in Proc.of34th Annual IEEE Computer Software and Applications Conference Workshops,2010. [61]I.Lee,and O.Sokolsky,“Medical Cyber Physical Systems,”in Proc.ofDAC,2010,Anaheim,California,USA.[62]W.Harrison,J.Moyne,and D.Tilbury,“Virtual fusion:The completeintegration of simulated and actual,”Presentation Report,2008, University of Michigan,USA.[63]M.Li,Y.H.Liu,J.L.Wang,et al.“Sensor network navigation withoutlocations,”in Proc.of IEEE INFOCOM,2009.[64]G.L.Xing,W.J.Jia,Y.F.Du,et al.“Toward ubiquitous video-basedCyber-Physical Systems,”in Proc.of IEEE International Conference on Systems,Man and Cybernetics,2008.[65] B.McMillin,C.Gill,M.L.Crow,et al,“Cyber-Physical Systemsdistributed control-The advanced electric power grid,”Available at: /.[66]L.Sha,S.Gopalakrishnan,X.Liu,et al.“Cyber-Physical Systems:Anew frontier,”in Proc.of IEEE International Conference on Sensor Networks,Ubiquitous,and Trustworthy Computing,2008.[67]M.Broy,“Cyber-Physical Systems:Technological&scientificchallenges,”Presentation Report,2010.[68]R.Rajkumar,I.Lee,L.Sha,et al.“Cyber-Physical Systems-The nextcomputing revolution,”in Proc.of Design Automation Conference,2010, Anaheim,California,USA.。
人脸表情识别英文参考资料

二、(国外)英文参考资料1、网上文献2、国际会议文章(英文)[C1]Afzal S, Sezgin T.M, Yujian Gao, Robinson P. Perception of emotional expressions in different representations using facial feature points. In: Affective Computing and Intelligent Interaction and Workshops, Amsterdam,Holland, 2009 Page(s): 1 - 6[C2]Yuwen Wu, Hong Liu, Hongbin Zha. Modeling facial expression space for recognition In:Intelligent Robots and Systems,Edmonton,Canada,2005: 1968 – 1973 [C3]Y u-Li Xue, Xia Mao, Fan Zhang. Beihang University Facial Expression Database and Multiple Facial Expression Recognition. In: Machine Learning and Cybernetics, Dalian,China,2006: 3282 – 3287[C4] Zhiguo Niu, Xuehong Qiu. Facial expression recognition based on weighted principal component analysis and support vector machines. In: Advanced Computer Theory and Engineering (ICACTE), Chendu,China,2010: V3-174 - V3-178[C5] Colmenarez A, Frey B, Huang T.S. A probabilistic framework for embedded face and facial expression recognition. In: Computer Vision and Pattern Recognition, Ft. Collins, CO, USA, 1999:[C6] Yeongjae Cheon, Daijin Kim. A Natural Facial Expression Recognition Using Differential-AAM and k-NNS. In: Multimedia(ISM 2008),Berkeley, California, USA,2008: 220 - 227[C7]Jun Ou, Xiao-Bo Bai, Yun Pei,Liang Ma, Wei Liu. Automatic Facial Expression Recognition Using Gabor Filter and Expression Analysis. In: Computer Modeling and Simulation, Sanya, China, 2010: 215 - 218[C8]Dae-Jin Kim, Zeungnam Bien, Kwang-Hyun Park. Fuzzy neural networks (FNN)-based approach for personalized facial expression recognition with novel feature selection method. In: Fuzzy Systems, St.Louis,Missouri,USA,2003: 908 - 913 [C9] Wei-feng Liu, Shu-juan Li, Yan-jiang Wang. Automatic Facial Expression Recognition Based on Local Binary Patterns of Local Areas. In: Information Engineering, Taiyuan, Shanxi, China ,2009: 197 - 200[C10] Hao Tang, Hasegawa-Johnson M, Huang T. Non-frontal view facial expression recognition based on ergodic hidden Markov model supervectors.In: Multimedia and Expo (ICME), Singapore ,2010: 1202 - 1207[C11] Yu-Jie Li, Sun-Kyung Kang,Young-Un Kim, Sung-Tae Jung. Development of a facial expression recognition system for the laughter therapy. In: Cybernetics and Intelligent Systems (CIS), Singapore ,2010: 168 - 171[C12] Wei Feng Liu, ZengFu Wang. Facial Expression Recognition Based on Fusion of Multiple Gabor Features. In: Pattern Recognition, HongKong, China, 2006: 536 - 539[C13] Chen Feng-jun, Wang Zhi-liang, Xu Zheng-guang, Xiao Jiang. Facial Expression Recognition Based on Wavelet Energy Distribution Feature and Neural Network Ensemble. In: Intelligent Systems, XiaMen, China, 2009: 122 - 126[C14] P. Kakumanu, N. Bourbakis. A Local-Global Graph Approach for FacialExpression Recognition. In: Tools with Artificial Intelligence, Arlington, Virginia, USA,2006: 685 - 692[C15] Mingwei Huang, Zhen Wang, Zilu Ying. Facial expression recognition using Stochastic Neighbor Embedding and SVMs. In: System Science and Engineering (ICSSE), Macao, China, 2011: 671 - 674[C16] Junhua Li, Li Peng. Feature difference matrix and QNNs for facial expression recognition. In: Control and Decision Conference, Yantai, China, 2008: 3445 - 3449 [C17] Yuxiao Hu, Zhihong Zeng, Lijun Yin,Xiaozhou Wei, Jilin Tu, Huang, T.S. A study of non-frontal-view facial expressions recognition. In: Pattern Recognition, Tampa, FL, USA,2008: 1 - 4[C18] Balasubramani A, Kalaivanan K, Karpagalakshmi R.C, Monikandan R. Automatic facial expression recognition system. In: Computing, Communication and Networking, St. Thomas,USA, 2008: 1 - 5[C19] Hui Zhao, Zhiliang Wang, Jihui Men. Facial Complex Expression Recognition Based on Fuzzy Kernel Clustering and Support Vector Machines. In: Natural Computation, Haikou,Hainan,China,2007: 562 - 566[C20] Khanam A, Shafiq M.Z, Akram M.U. Fuzzy Based Facial Expression Recognition. In: Image and Signal Processing, Sanya, Hainan, China,2008: 598 - 602 [C21] Sako H, Smith A.V.W. Real-time facial expression recognition based on features' positions and dimensions. In: Pattern Recognition, Vienna,Austria, 1996: 643 - 648 vol.3[C22] Huang M.W, Wang Z.W, Ying Z.L. A novel method of facial expression recognition based on GPLVM Plus SVM. In: Signal Processing (ICSP), Beijing, China, 2010: 916 - 919[C23] Xianxing Wu; Jieyu Zhao; Curvelet feature extraction for face recognition and facial expression recognition. In: Natural Computation (ICNC), Yantai, China, 2010: 1212 - 1216[C24]Xu Q Z, Zhang P Z, Yang L X, et al.A facial expression recognition approach based on novel support vector machine tree. In Proceedings of the 4th International Symposium on Neural Networks, Nanjing, China, 2007: 374-381.[C25] Wang Y B, Ai H Z, Wu B, et al. Real time facial expression recognition with adaboost.In: Proceedings of the 17th International Conference on Pattern Recognition , Cambridge,UK, 2004: 926-929.[C26] Guo G, Dyer C R. Simultaneous feature selection and classifier training via linear programming: a case study for face expression recognition. In: Proceedings of the 2003 IEEE Computer Society Conference on Computer Vision and Pattern Recognition, Madison, W isconsin, USA, 2003,1: 346-352.[C27] Bourel F, Chibelushi C C, Low A A. Robust facial expression recognition using a state-based model of spatially-localised facial dynamics. In: Proceedings of the 5th IEEE International Conference on Automatic Face and Gesture Recognition, Washington, DC, USA, 2002: 113-118·[C28] Buciu I, Kotsia I, Pitas I. Facial expression analysis under partial occlusion. In: Proceedings of the 2005 IEEE International Conference on Acoustics, Speech, and Signal Processing, Philadelphia, PA, USA, 2005,V: 453-456.[C29] ZHAN Yong-zhao,YE Jing-fu,NIU De-jiao,et al.Facial expression recognition based on Gabor wavelet transformation and elastic templates matching. Proc of the 3rd International Conference on Image and Graphics.Washington DC, USA,2004:254-257.[C30] PRASEEDA L V,KUMAR S,VIDYADHARAN D S,et al.Analysis of facial expressions using PCA on half and full faces. Proc of ICALIP2008.2008:1379-1383.[C31] LEE J J,UDDIN M Z,KIM T S.Spatiotemporal human facial expression recognition using Fisher independent component analysis and Hidden Markov model [C]//Proc of the 30th Annual International Conference of IEEE Engineering in Medicine and Biology Society.2008:2546-2549.[C32] LITTLEWORT G,BARTLETT M,FASELL. Dynamics of facial expression extracted automatically from video. In: Proceedings of IEEE Conference on Computer Vision and Pattern Recognition, Workshop on Face Processing inVideo, Washington DC,USA,2006:80-81.[C33] Kotsia I, Nikolaidis N, Pitas I. Facial Expression Recognition in Videos using a Novel Multi-Class Support Vector Machines Variant. In: Acoustics, Speech and Signal Processing, Honolulu, Hawaii, USA, 2007: II-585 - II-588[C34] Ruo Du, Qiang Wu, Xiangjian He, Wenjing Jia, Daming Wei. Facial expression recognition using histogram variances faces. In: Applications of Computer Vision (WACV), Snowbird, Utah, USA, 2009: 1 - 7[C35] Kobayashi H, Tange K, Hara F. Real-time recognition of six basic facial expressions. In: Robot and Human Communication, Tokyo , Japan,1995: 179 - 186 [C36] Hao Tang, Huang T.S. 3D facial expression recognition based on properties of line segments connecting facial feature points. In: Automatic Face & Gesture Recognition, Amsterdam, The Netherlands, 2008: 1 - 6[C37] Fengjun Chen, Zhiliang Wang, Zhengguang Xu, Donglin Wang. Research on a method of facial expression recognition.in: Electronic Measurement & Instruments, Beijing,China, 2009: 1-225 - 1-229[C38] Hui Zhao, Tingting Xue, Linfeng Han. Facial complex expression recognition based on Latent DirichletAllocation. In: Natural Computation (ICNC), Yantai, Shandong, China, 2010: 1958 - 1960[C39] Qinzhen Xu, Pinzheng Zhang, Wenjiang Pei, Luxi Yang, Zhenya He. An Automatic Facial Expression Recognition Approach Based on Confusion-Crossed Support Vector Machine Tree. In: Acoustics, Speech and Signal Processing, Honolulu, Hawaii, USA, 2007: I-625 - I-628[C40] Sung Uk Jung, Do Hyoung Kim, Kwang Ho An, Myung Jin Chung. Efficient rectangle feature extraction for real-time facial expression recognition based on AdaBoost.In: Intelligent Robots and Systems, Edmonton,Canada, 2005: 1941 - 1946[C41] Patil K.K, Giripunje S.D, Bajaj P.R. Facial Expression Recognition and Head Tracking in Video Using Gabor Filter .In: Emerging Trends in Engineering and Technology (ICETET), Goa, India, 2010: 152 - 157[C42] Jun Wang, Lijun Yin, Xiaozhou Wei, Yi Sun. 3D Facial Expression Recognition Based on Primitive Surface Feature Distribution.In: Computer Vision and PatternRecognition, New York, USA,2006: 1399 - 1406[C43] Shi Dongcheng, Jiang Jieqing. The method of facial expression recognition based on DWT-PCA/LDA.IN: Image and Signal Processing (CISP), Yantai,China, 2010: 1970 - 1974[C44] Asthana A, Saragih J, Wagner M, Goecke R. Evaluating AAM fitting methods for facial expression recognition. In: Affective Computing and Intelligent Interaction and Workshops, Amsterdam,Holland, 2009:1-8[C45] Geng Xue, Zhang Youwei. Facial Expression Recognition Based on the Difference of Statistical Features.In: Signal Processing, Guilin, China, 2006[C46] Metaxas D. Facial Features Tracking for Gross Head Movement analysis and Expression Recognition.In: Multimedia Signal Processing, Chania,Crete,GREECE, 2007:2[C47] Xia Mao, YuLi Xue, Zheng Li, Kang Huang, ShanWei Lv. Robust facial expression recognition based on RPCA and AdaBoost.In: Image Analysis for Multimedia Interactive Services, London, UK, 2009: 113 - 116[C48] Kun Lu, Xin Zhang. Facial Expression Recognition from Image Sequences Based on Feature Points and Canonical Correlations.In: Artificial Intelligence and Computational Intelligence (AICI), Sanya,China, 2010: 219 - 223[C49] Peng Zhao-yi, Wen Zhi-qiang, Zhou Yu. Application of Mean Shift Algorithm in Real-Time Facial Expression Recognition.In: Computer Network and Multimedia Technology, Wuhan,China, 2009: 1 - 4[C50] Xu Chao, Feng Zhiyong, Facial Expression Recognition and Synthesis on Affective Emotions Composition.In: Future BioMedical Information Engineering, Wuhan,China, 2008: 144 - 147[C51] Zi-lu Ying, Lin-bo Cai. Facial Expression Recognition with Marginal Fisher Analysis on Local Binary Patterns.In: Information Science and Engineering (ICISE), Nanjing,China, 2009: 1250 - 1253[C52] Chuang Yu, Yuning Hua, Kun Zhao. The Method of Human Facial Expression Recognition Based on Wavelet Transformation Reducing the Dimension and Improved Fisher Discrimination.In: Intelligent Networks and Intelligent Systems (ICINIS), Shenyang,China, 2010: 43 - 47[C53] Stratou G, Ghosh A, Debevec P, Morency L.-P. Effect of illumination on automatic expression recognition: A novel 3D relightable facial database .In: Automatic Face & Gesture Recognition and Workshops (FG 2011), Santa Barbara, California,USA, 2011: 611 - 618[C54] Jung-Wei Hong, Kai-Tai Song. Facial expression recognition under illumination variation.In: Advanced Robotics and Its Social Impacts, Hsinchu, Taiwan,2007: 1 - 6[C55] Ryan A, Cohn J.F, Lucey S, Saragih J, Lucey P, De la Torre F, Rossi A. Automated Facial Expression Recognition System.In: Security Technology, Zurich, Switzerland, 2009: 172 - 177[C56] Gokturk S.B, Bouguet J.-Y, Tomasi C, Girod B. Model-based face tracking for view-independent facial expression recognition.In: Automatic Face and Gesture Recognition, Washington, D.C., USA, 2002: 287 - 293[C57] Guo S.M, Pan Y.A, Liao Y.C, Hsu C.Y, Tsai J.S.H, Chang C.I. A Key Frame Selection-Based Facial Expression Recognition System.In: Innovative Computing, Information and Control, Beijing,China, 2006: 341 - 344[C58] Ying Zilu, Li Jingwen, Zhang Youwei. Facial expression recognition based on two dimensional feature extraction.In: Signal Processing, Leipzig, Germany, 2008: 1440 - 1444[C59] Fengjun Chen, Zhiliang Wang, Zhengguang Xu, Jiang Xiao, Guojiang Wang. Facial Expression Recognition Using Wavelet Transform and Neural Network Ensemble.In: Intelligent Information Technology Application, Shanghai,China,2008: 871 - 875[C60] Chuan-Yu Chang, Yan-Chiang Huang, Chi-Lu Yang. Personalized Facial Expression Recognition in Color Image.In: Innovative Computing, Information and Control (ICICIC), Kaohsiung,Taiwan, 2009: 1164 - 1167[C61] Bourel F, Chibelushi C.C, Low A.A. Robust facial expression recognition using a state-based model of spatially-localised facial dynamics. In: Automatic Face and Gesture Recognition, Washington, D.C., USA, 2002: 106 - 111[C62] Chen Juanjuan, Zhao Zheng, Sun Han, Zhang Gang. Facial expression recognition based on PCA reconstruction.In: Computer Science and Education (ICCSE), Hefei,China, 2010: 195 - 198[C63] Guotai Jiang, Xuemin Song, Fuhui Zheng, Peipei Wang, Omer A.M. Facial Expression Recognition Using Thermal Image.In: Engineering in Medicine and Biology Society, Shanghai,China, 2005: 631 - 633[C64] Zhan Yong-zhao, Ye Jing-fu, Niu De-jiao, Cao Peng. Facial expression recognition based on Gabor wavelet transformation and elastic templates matching.In: Image and Graphics, Hongkong,China, 2004: 254 - 257[C65] Ying Zilu, Zhang Guoyi. Facial Expression Recognition Based on NMF and SVM. In: Information Technology and Applications, Chengdu,China, 2009: 612 - 615 [C66] Xinghua Sun, Hongxia Xu, Chunxia Zhao, Jingyu Yang. Facial expression recognition based on histogram sequence of local Gabor binary patterns. In: Cybernetics and Intelligent Systems, Chengdu,China, 2008: 158 - 163[C67] Zisheng Li, Jun-ichi Imai, Kaneko M. Facial-component-based bag of words and PHOG descriptor for facial expression recognition.In: Systems, Man and Cybernetics, San Antonio,TX,USA,2009: 1353 - 1358[C68] Chuan-Yu Chang, Yan-Chiang Huang. Personalized facial expression recognition in indoor environments.In: Neural Networks (IJCNN), Barcelona, Spain, 2010: 1 - 8[C69] Ying Zilu, Fang Xieyan. Combining LBP and Adaboost for facial expression recognition.In: Signal Processing, Leipzig, Germany, 2008: 1461 - 1464[C70] Peng Yang, Qingshan Liu, Metaxas, D.N. RankBoost with l1 regularization for facial expression recognition and intensity estimation.In: Computer Vision, Kyoto,Japan, 2009: 1018 - 1025[C71] Patil R.A, Sahula V, Mandal A.S. Automatic recognition of facial expressions in image sequences: A review.In: Industrial and Information Systems (ICIIS), Mangalore, India, 2010: 408 - 413[C72] Iraj Hosseini, Nasim Shams, Pooyan Amini, Mohammad S. Sadri, Masih Rahmaty, Sara Rahmaty. Facial Expression Recognition using Wavelet-Based Salient Points and Subspace Analysis Methods.In: Electrical and Computer Engineering, Ottawa, Canada, 2006: 1992 - 1995[C73][C74][C75][C76][C77][C78][C79]3、英文期刊文章[J1] Aleksic P.S., Katsaggelos A.K. Automatic facial expression recognition using facial animation parameters and multistream HMMs.IEEE Transactions on Information Forensics and Security, 2006, 1(1):3-11[J2] Kotsia I,Pitas I. Facial Expression Recognition in Image Sequences Using Geometric Deformation Features and Support Vector Machines. IEEE Transactions on Image Processing, 2007, 16(1):172 – 187[J3] Mpiperis I, Malassiotis S, Strintzis M.G. Bilinear Models for 3-D Face and Facial Expression Recognition. IEEE Transactions on Information Forensics and Security, 2008,3(3) : 498 - 511[J4] Sung J, Kim D. Pose-Robust Facial Expression Recognition Using View-Based 2D+3D AAM. IEEE Transactions on Systems and Humans, 2008 , 38 (4): 852 - 866 [J5]Yeasin M, Bullot B, Sharma R. Recognition of facial expressions and measurement of levels of interest from video. IEEE Transactions on Multimedia, 2006, 8(3): 500 - 508[J6] Wenming Zheng, Xiaoyan Zhou, Cairong Zou, Li Zhao. Facial expression recognition using kernel canonical correlation analysis (KCCA). IEEE Transactions on Neural Networks, 2006, 17(1): 233 - 238[J7]Pantic M, Patras I. Dynamics of facial expression: recognition of facial actions and their temporal segments from face profile image sequences. IEEE Transactions on Systems, Man, and Cybernetics, Part B: Cybernetics, 2006, 36(2): 433 - 449[J8] Mingli Song, Dacheng Tao, Zicheng Liu, Xuelong Li, Mengchu Zhou. Image Ratio Features for Facial Expression Recognition Application. IEEE Transactions on Systems, Man, and Cybernetics, Part B: Cybernetics, 2010, 40(3): 779 - 788[J9] Dae Jin Kim, Zeungnam Bien. Design of “Personalized” Classifier Using Soft Computing Techniques for “Personalized” Facial Expression Recognition. IEEE Transactions on Fuzzy Systems, 2008, 16(4): 874 - 885[J10] Uddin M.Z, Lee J.J, Kim T.-S. An enhanced independent component-based human facial expression recognition from video. IEEE Transactions on Consumer Electronics, 2009, 55(4): 2216 - 2224[J11] Ruicong Zhi, Flierl M, Ruan Q, Kleijn W.B. Graph-Preserving Sparse Nonnegative Matrix Factorization With Application to Facial Expression Recognition.IEEE Transactions on Systems, Man, and Cybernetics, Part B: Cybernetics, 2011, 41(1): 38 - 52[J12] Chibelushi C.C, Bourel F. Hierarchical multistream recognition of facial expressions. IEE Proceedings - Vision, Image and Signal Processing, 2004, 151(4): 307 - 313[J13] Yongsheng Gao, Leung M.K.H, Siu Cheung Hui, Tananda M.W. Facial expression recognition from line-based caricatures. IEEE Transactions on Systems, Man and Cybernetics, Part A: Systems and Humans, 2003, 33(3): 407 - 412[J14] Ma L, Khorasani K. Facial expression recognition using constructive feedforward neural networks. IEEE Transactions on Systems, Man, and Cybernetics, Part B: Cybernetics, 2004, 34(3): 1588 - 1595[J15] Essa I.A, Pentland A.P. Coding, analysis, interpretation, and recognition of facial expressions. IEEE Transactions on Pattern Analysis and Machine Intelligence, 1997, 19(7): 757 - 763[J16] Anderson K, McOwan P.W. A real-time automated system for the recognition of human facial expressions. IEEE Transactions on Systems, Man, and Cybernetics, Part B: Cybernetics, 2006, 36(1): 96 - 105[J17] Soyel H, Demirel H. Facial expression recognition based on discriminative scale invariant feature transform. Electronics Letters 2010, 46(5): 343 - 345[J18] Fei Cheng, Jiangsheng Yu, Huilin Xiong. Facial Expression Recognition in JAFFE Dataset Based on Gaussian Process Classification. IEEE Transactions on Neural Networks, 2010, 21(10): 1685 – 1690[J19] Shangfei Wang, Zhilei Liu, Siliang Lv, Yanpeng Lv, Guobing Wu, Peng Peng, Fei Chen, Xufa Wang. A Natural Visible and Infrared Facial Expression Database for Expression Recognition and Emotion Inference. IEEE Transactions on Multimedia, 2010, 12(7): 682 - 691[J20] Lajevardi S.M, Hussain Z.M. Novel higher-order local autocorrelation-like feature extraction methodology for facial expression recognition. IET Image Processing, 2010, 4(2): 114 - 119[J21] Yizhen Huang, Ying Li, Na Fan. Robust Symbolic Dual-View Facial Expression Recognition With Skin Wrinkles: Local Versus Global Approach. IEEE Transactions on Multimedia, 2010, 12(6): 536 - 543[J22] Lu H.-C, Huang Y.-J, Chen Y.-W. Real-time facial expression recognition based on pixel-pattern-based texture feature. Electronics Letters 2007, 43(17): 916 - 918[J23]Zhang L, Tjondronegoro D. Facial Expression Recognition Using Facial Movement Features. IEEE Transactions on Affective Computing, 2011, pp(99): 1[J24] Zafeiriou S, Pitas I. Discriminant Graph Structures for Facial Expression Recognition. Multimedia, IEEE Transactions on 2008,10(8): 1528 - 1540[J25]Oliveira L, Mansano M, Koerich A, de Souza Britto Jr. A. Selecting 2DPCA Coefficients for Face and Facial Expression Recognition. Computing in Science & Engineering, 2011, pp(99): 1[J26] Chang K.I, Bowyer W, Flynn P.J. Multiple Nose Region Matching for 3D Face Recognition under Varying Facial Expression. Pattern Analysis and Machine Intelligence, IEEE Transactions on2006, 28(10): 1695 - 1700[J27] Kakadiaris I.A, Passalis G, Toderici G, Murtuza M.N, Yunliang Lu, Karampatziakis N, Theoharis T. Three-Dimensional Face Recognition in the Presence of Facial Expressions: An Annotated Deformable Model Approach.IEEE Transactions on Pattern Analysis and Machine Intelligence, 2007, 29(4): 640 - 649[J28] Guoying Zhao, Pietikainen M. Dynamic Texture Recognition Using Local Binary Patterns with an Application to Facial Expressions. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2007, 29(6): 915 - 928[J29] Chakraborty A, Konar A, Chakraborty U.K, Chatterjee A. Emotion Recognition From Facial Expressions and Its Control Using Fuzzy Logic. IEEE Transactions on Systems, Man and Cybernetics, Part A: Systems and Humans, 2009, 39(4): 726 - 743 [J30] Pantic M, RothkrantzL J.M. Facial action recognition for facial expression analysis from static face images. IEEE Transactions on Systems, Man, and Cybernetics, Part B: Cybernetics, 2004, 34(3): 1449 - 1461[J31] Calix R.A, Mallepudi S.A, Bin Chen, Knapp G.M. Emotion Recognition in Text for 3-D Facial Expression Rendering. IEEE Transactions on Multimedia, 2010, 12(6): 544 - 551[J32]Kotsia I, Pitas I, Zafeiriou S, Zafeiriou S. Novel Multiclass Classifiers Based on the Minimization of the Within-Class Variance. IEEE Transactions on Neural Networks, 2009, 20(1): 14 - 34[J33]Cohen I, Cozman F.G, Sebe N, Cirelo M.C, Huang T.S. Semisupervised learning of classifiers: theory, algorithms, and their application to human-computer interaction. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2004, 26(12): 1553 - 1566[J34] Zafeiriou S. Discriminant Nonnegative Tensor Factorization Algorithms. IEEE Transactions on Neural Networks, 2009, 20(2): 217 - 235[J35] Zafeiriou S, Petrou M. Nonlinear Non-Negative Component Analysis Algorithms. IEEE Transactions on Image Processing, 2010, 19(4): 1050 - 1066[J36] Kotsia I, Zafeiriou S, Pitas I. A Novel Discriminant Non-Negative Matrix Factorization Algorithm With Applications to Facial Image Characterization Problems. IEEE Transactions on Information Forensics and Security, 2007, 2(3): 588 - 595[J37] Irene Kotsia, Stefanos Zafeiriou, Ioannis Pitas. Texture and shape information fusion for facial expression and facial action unit recognition . Pattern Recognition, 2008, 41(3): 833-851[J38]Wenfei Gu, Cheng Xiang, Y.V. Venkatesh, Dong Huang, Hai Lin. Facial expression recognition using radial encoding of local Gabor features and classifier synthesis. Pattern Recognition, In Press, Corrected Proof, Available online 27 May 2011[J39] F Dornaika, E Lazkano, B Sierra. Improving dynamic facial expression recognition with feature subset selection. Pattern Recognition Letters, 2011, 32(5): 740-748[J40] Te-Hsun Wang, Jenn-Jier James Lien. Facial expression recognition system based on rigid and non-rigid motion separation and 3D pose estimation. Pattern Recognition, 2009, 42(5): 962-977[J41] Hyung-Soo Lee, Daijin Kim. Expression-invariant face recognition by facialexpression transformations. Pattern Recognition Letters, 2008, 29(13): 1797-1805[J42] Guoying Zhao, Matti Pietikäinen. Boosted multi-resolution spatiotemporal descriptors for facial expression recognition . Pattern Recognition Letters, 2009, 30(12): 1117-1127[J43] Xudong Xie, Kin-Man Lam. Facial expression recognition based on shape and texture. Pattern Recognition, 2009, 42(5):1003-1011[J44] Peng Yang, Qingshan Liu, Dimitris N. Metaxas Boosting encoded dynamic features for facial expression recognition . Pattern Recognition Letters, 2009,30(2): 132-139[J45] Sungsoo Park, Daijin Kim. Subtle facial expression recognition using motion magnification. Pattern Recognition Letters, 2009, 30(7): 708-716[J46] Chathura R. De Silva, Surendra Ranganath, Liyanage C. De Silva. Cloud basis function neural network: A modified RBF network architecture for holistic facial expression recognition. Pattern Recognition, 2008, 41(4): 1241-1253[J47] Do Hyoung Kim, Sung Uk Jung, Myung Jin Chung. Extension of cascaded simple feature based face detection to facial expression recognition. Pattern Recognition Letters, 2008, 29(11): 1621-1631[J48] Y. Zhu, L.C. De Silva, C.C. Ko. Using moment invariants and HMM in facial expression recognition. Pattern Recognition Letters, 2002, 23(1-3): 83-91[J49] Jun Wang, Lijun Yin. Static topographic modeling for facial expression recognition and analysis. Computer Vision and Image Understanding, 2007, 108(1-2): 19-34[J50] Caifeng Shan, Shaogang Gong, Peter W. McOwan. Facial expression recognition based on Local Binary Patterns: A comprehensive study. Image and Vision Computing, 2009, 27(6): 803-816[J51] Xue-wen Chen, Thomas Huang. Facial expression recognition: A clustering-based approach. Pattern Recognition Letters, 2003, 24(9-10): 1295-1302 [J52] Irene Kotsia, Ioan Buciu, Ioannis Pitas. An analysis of facial expression recognition under partial facial image occlusion. Image and Vision Computing, 2008, 26(7): 1052-1067[J53] Shuai Liu, Qiuqi Ruan. Orthogonal Tensor Neighborhood Preserving Embedding for facial expression recognition. Pattern Recognition, 2011, 44(7):1497-1513[J54] Eszter Székely, Henning Tiemeier, Lidia R. Arends, Vincent W.V. Jaddoe, Albert Hofman, Frank C. Verhulst, Catherine M. Herba. Recognition of Facial Expressions of Emotions by 3-Year-Olds. Emotion, 2011, 11(2): 425-435[J55] Kathleen M. Corcoran, Sheila R. Woody, David F. Tolin. Recognition of facial expressions in obsessive–compulsive disorder. Journal of Anxiety Disorders, 2008, 22(1): 56-66[J56] Bouchra Abboud, Franck Davoine, Mô Dang. Facial expression recognition and synthesis based on an appearance model. Signal Processing: Image Communication, 2004, 19(8): 723-740[J57] Teng Sha, Mingli Song, Jiajun Bu, Chun Chen, Dacheng Tao. Feature level analysis for 3D facial expression recognition. Neurocomputing, 2011,74(12-13) :2135-2141[J58] S. Moore, R. Bowden. Local binary patterns for multi-view facial expression recognition . Computer Vision and Image Understanding, 2011, 15(4):541-558[J59] Rui Xiao, Qijun Zhao, David Zhang, Pengfei Shi. Facial expression recognition on multiple manifolds. Pattern Recognition, 2011, 44(1):107-116[J60] Shyi-Chyi Cheng, Ming-Yao Chen, Hong-Yi Chang, Tzu-Chuan Chou. Semantic-based facial expression recognition using analytical hierarchy process. Expert Systems with Applications, 2007, 33(1): 86-95[J71] Carlos E. Thomaz, Duncan F. Gillies, Raul Q. Feitosa. Using mixture covariance matrices to improve face and facial expression recognitions. Pattern Recognition Letters, 2003, 24(13): 2159-2165[J72]Wen G,Bo C,Shan Shi-guang,et al. The CAS-PEAL large-scale Chinese face database and baseline evaluations.IEEE Transactions on Systems,Man and Cybernetics,part A:Systems and Hu-mans,2008,38(1):149-161.[J73] Yongsheng Gao,Leung ,M.K.H. Face recognition using line edge map.IEEE Transactions on Pattern Analysis and Machine Intelligence,2002,24:764-779. [J74] Hanouz M,Kittler J,Kamarainen J K,et al. Feature-based affine-invariant localization of faces.IEEE Transactions on Pat-tern Analysis and Machine Intelligence,2005,27:1490-1495.[J75] WISKOTT L,FELLOUS J M,KRUGER N,et al.Face recognition by elastic bunch graph matching.IEEE Trans on Pattern Analysis and Machine Intelligence,1997,19(7):775-779.[J76] Belhumeur P.N, Hespanha J.P, Kriegman D.J. Eigenfaces vs. fischerfaces: recognition using class specific linear projection.IEEE Trans on Pattern Analysis and Machine Intelligence,1997,15(7):711-720[J77] MA L,KHORASANI K.Facial Expression Recognition Using Constructive Feedforward Neural Networks. IEEE Transactions on Systems, Man and Cybernetics, Part B,2007,34(3):1588-1595.[J78][J79][J80][J81][J82][J83][J84][J85][J86][J87][J88][J89][J90]4、英文学位论文[D1]Hu Yuxiao. Three-dimensional face processing and its applications in biometrics:[Ph.D dissertation]. USA,Urbana-Champaign: University of Illinois, 2008。
管理学专业英语词汇

ABC Classification ABC分类法Activity-Based Costing 业务量成本法/作业成本法ACRS (Accelerated cost recovery system) 快速成本回收制度Action Message 行为/措施信息AIS (Accounting information system) 会计信息系统Allocation 已分配量Anticipated Delay Report 拖期预报A/P (Accounts Payable) 应付帐款APICS (American Production & Inventory Control Society) 美国生产及库存控制协会AQL (Acceptable quality Level) 可接受质量水平A/R (Accounts Receivable) 应收帐款Automatic Rescheduling 自动重排产Available To Promise (APT) 可签约量Backflush 倒冲法Backlog 未完成订单/未结订单Back Scheduling 倒序排产BE analysis (Break-even analysis) 盈亏临界点分析,保本分析Bill of Material (BOM) 物料清单Business Plan 经营规划B/V (Book value) 帐面价值Capacity Requirements Planning (CRP) 能力需求计划CBA (Cost-benefit analysis) 成本效益分析CEO 首席执行官CFO (Chief Financial Officer) 财务总裁Closed Loop MRP 闭环物料需求计划CPM (Critical path method) 关键路线法CPP accounting (Constant purchasing power accounting) 不变购买力会计Cumulative Lead Time 累计提前期Cycle Counting 周期盘点Demand 需求Demand Management 需求管理Demonstrated Capacity 实际能力Dependent Demand 非独立需求DFL (Degree of financial leverage) 财务杠杆系数Direct-deduct Inventory Transaction Processing 直接增减库存法Dispatch List 派工单DOL (Degree of operating leverage) 经营杠杆系数ELS (Economic lot size) 经济批量EOQ (Economic order quantity) 经济订货批量FIFO (Fist-in,Fist-out) 先进先出法Firm Planned Order 确认计划订单FISH/LIFO (Fist-in,Still-here) 后进先出法Fixed Order Quantity 固定订货批量法Flow Shop 流水车间Focus Forecasting 集中预测Full Pegging 完全跟踪Generally Accepted Manufacturing Practices 公认生产管理原则Independent Demand 独立需求Inpu/Output Control 投入/产出控制Interplant Demand 厂际需求Inventory Turnover 库存周转次数Item 物料项目Item Record 项目记录Job Shop 加工车间Just-in-time (JIT) 准时制生产Lead Time 提前期前置期,指订单从收到具体明细到货到货仓收到落货纸这一段时间,可以用评估工厂的综合实力。
2024-2025学年江西省九江市稳派联考高三上学期入学考英语试题及答案

英语试卷试卷共67小题,满分150分。
考试用时120分钟。
注意事项:1.答卷前,考生务必将自己的姓名、准考证号等填写在答题卡指定位置上。
2.回答选择题时,选出每小题答案后,用铅笔把答题卡上对应题目的答案标号涂黑。
如需改动,用橡皮擦干净后,再选涂其他答案标号。
回答非选择题时,将答案写在答题卡上。
写在本试卷上无效。
3.考生必须保持答题卡的整洁。
考试结束后,请将答题卡交回。
第一部分听力(共两节,满分 30 分)做题时,先将答案标在试卷上,录音内容结束后,你将有两分钟的时间将试卷上的答案转涂到答题卡上。
第一节 (共5小题;每小题1.5分,满分7.5分)听下面5段对话。
每段对话后有一个小题,从题中所给的A、B、C三个选项中选出最佳选项,并标在试卷的相应位置。
听完每段对话后,你都有10 秒钟的时间来回答有关小题和阅读下一小题。
每段对话仅读一遍。
例: How much is the shirt?A.£19.15.B.£9.18.C.£9.15.答案是C。
1. What are the speakers doing?A. They are playing games.B. They are discussing a match.C. They are talking about a tie.2. What does the woman mean?A. Tom has made a proper decision.B. Tom's new job will make a difference.C. Tom has a wrong attitude towards work.3. Where does the conversation probably take place?A. In the classroom.B. In the library.C. In the computer room.4. What can we know about the woman?A. She was turned down.B. She had a poor sleep.C. She was tired of the heating.5. How did the woman go to school?A. By car.B. By bus.C. By underground.第二节 (共15 小题;每小题1.5分,满分22.5分)听下面5段对话或独白,每段对话或独白后有几个小题,从题中所给的A、B、C三个选项中选出最佳选项,并标在试卷的相应位置。
Cambridge International AS and A Level Mathematics

Turn over*P48592A0120*P48592A©2017 Pearson Education Ltd.1/1/1/1/1/1/1/1/1/1/1Instructions• Use black ink or ball-point pen.•I f pencil is used for diagrams/sketches it must be dark (HB or B).Coloured pens, pencils and highlighter pens must not be used.•Fill in the boxes at the top of this page with your name,centre number and candidate number.• Answer all questions.•A nswer the questions in the spaces provided– there may be more space than you need.Information•The total mark for this paper is 80.•T he marks for each question are shown in brackets– use this as a guide as to how much time to spend on each question.•Q uestions labelled with an asterisk (*) are ones where the quality of yourwritten communication will be assessed– y ou should take particular care on these questions with your spelling, punctuationand grammar, as well as the clarity of expression.Advice•Read each question carefully before you start to answer it.•Try to answer every question.•Check your answers if you have time at the end.Turn over*P48592A0220*2*P48592A0320*Turn over3*P48592A0420*4*P48592A0520*Turn over5*P48592A0620*6(b) A theatrical company is designing costumes for a performance. Calico is a cheapfabric that can be used for a prototype.(i) E xplainone reason, other than being cheap, why calico was used forthe prototype.(2) .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................(ii) Muslin was used as an alternative to calico for this prototype.Explain one reason why muslin would be a suitable alternative.(2) .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................(iii) The theatrical company has decided to make its performance costumes out of viscose.Statetwo advantages of using viscose for theatrical costumes.(2)1 ..............................................................................................................................................................................................................................................................................2 (iv)Explainone disadvantage of using viscose for theatrical costumes.(2) .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................(c) (i) State one method used on the seam allowance to create a deep curve.(1) ....................................................................................................................................................................................................................................................................................*P48592A0720*Turn over7(ii) Describe why it is necessary to use this method on the seam allowance ofa sewn deep curve.(2)................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................(iii) The theatrical company costumes all have collars. Interfacing is to be added tothe collars.State two quality control checks involving interfacing that can be carried outon the collars during manufacture. Justify your reasoning.(4)Quality control check.....................................................................................................................................................................................................................................................................................Justification............................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................Quality control check....................................................................................................................................................................................................................................................................................Justification............................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................(Total for Question 11 = 19 marks)*P48592A0820*812 A large retailer of baby products would like you to design and manufacture a playmat suitable for babies who are unable to walk. Design specificationThe specification for the product is that it must: • be suitable for babies lying on their front and back • be educational• support the baby’s body • be easy to care for• have a visually recognisable theme • include a decorative technique • be easy to carry or store •be safe to use.In the spaces opposite, use sketches and, where appropriate, brief notes to show two different design ideas for the play mat that meet the specification points above. Candidates are reminded that if a pencil is used for diagrams/sketches it must be dark (HB or B).Coloured pens, pencils and highlighter pens must not be used.PLEASE DO NOT WRITE OR DRAW IN THIS SPACE.PLEASE USE THE SPACES OPPOSITE FOR YOUR DESIGNS.*P48592A0920*Turn over9Design idea 1(8)Design idea 2(8)(Total for Question 12 = 16 marks)*P48592A01020*1013 (a) A pair of trousers has been designed for a wheelchair-bound person with adisability. A zip has been used in the waistband to make the trousers easy to put on and take off. (i) Give one other suitable textile fastening to use in these trousers. Justify youranswer.(2)Fastening....................................................................................................................................................................................................................................................................................Justification................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................(ii) Give one unsuitable textile fastening for use in these trousers. Justify youranswer.(2)Fastening....................................................................................................................................................................................................................................................................................Justification................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................*P48592A01120*Turn over11*P48592A01220*12*P48592A01320*Turn over13Evaluate Product A against Product B in terms of function and user requirements.(6)................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................(Total for Question 13 = 16 marks)*P48592A01420*1414 (a) (i) State two risks associated with the use of dyes. (2)1 ...................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................2 ................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................... (ii) Describe one control measure used to minimise these risks.(2)................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................ (b) Explain why cotton should be washed before garment manufacture.(2)........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................*P48592A01520*Turn over15*P48592A01620*16(iii) Explain one reason why the use of computer-integrated manufacture (CIM) benefits the shirt company.(2)........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................ *(e) Reducing transportation is one method of reducing emissions from textile manufacturing.Discuss other ways that textile manufacturers can reduce emissions. (6)............................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................。
DistributedSystemsPrinciplesandParadigms中文版书名分布

Marcus,Sten : Blueprints for High Availablity
Birman, Reliable Distributed Systems
Byzantine Failure问题:
Pease,M., “Reaching Agreement in the Presence of Faults” J.ACM,1980
Lamport,L.: “Byzantine Generals Problem. ” ACM T ng.syst. 1982
Shooman,M.L: Reliability of Computer Systems and Networks :Fault Tolerance, Analysis, and Design. 2002
Tanisch,P., “Atomic Commit in Concurrent Computing. ” IEEE Concurrency,2000
集中式体系结构:C/S
分布式体系结构:
点对点系统(peer-peer system):DHT(distributed hash table),例如Chord
随机图(random map)
混合体系结构:
协作分布式系统BitTorrent、Globule
自适应软件技术:
①要点分离
②计算映像
③基于组件的设计
Henning,M., “A New Approach to Object-Oriented Middleware”
第11章分布式文件系统
NFS (Network File System):远程访问模型
机械工程及自动化专业外文翻译--应用坐标测量机的机器人运动学姿态的标定翻译

外文原文:Full-Pose Calibration of a Robot Manipulator Using a Coordinate-Measuring MachineThe work reported in this article addresses the kinematic calibration of a robot manipulator using a coordinate measuring m a c h i n e(C M M)w h i c h i s a b l e t o o b t a i n t h e f u l l p o s e o f t h e e n d-e f f e c t o r.A k i n e m a t i c m o d e l i s d e v e l o p e d f o r t h e manipulator, its relationship to the world coordinate frame and the tool. The derivation of the tool pose from experimental measurements is discussed, as is the identification methodolo gy.A complete simulation of the experiment is performed, allowing the observation strategy to be defined. The experimental work is described together with the parameter identification and accuracy verification. The principal conclusion is that the m et ho d is a ble t o calibrate the robot succes sful ly, with a resulting accuracy approaching that of its repeatability.Keywords: Robot calibration; Coordinate measurement; Parameter identification; Simulation study; Accuracy enhancement 1. IntroductionIt is wel l known tha t robo t manip ula tors t ypical ly ha ve reasonable repeatability (0.3 ram), yet exhibit poor accuracy(10.0m m).T h e p r o c e s s b y w h i c h r o b o t s m a y b e c a l i b r a t e di n o r d e r t o a c h i e v e a c c u r a c i e s a p p r o a c h i n g t h a t o f t h e m a n i p u l a t o r i s a l s o w e l l u n d e r s t o o d .I n t h e c a l i b r a t i o n process, several sequential steps enable the precise kinematic p ar am et er s o f th e m an ip u l ato r to b e ide nti fi ed,l ead ing t o improved accuracy. These steps may be described as follows: 1. A kinematic model of the manipulator and the calibration process itself is developed and is usually accomplished with s t a n d a r d k i n e m a t i c m o d e l l i n g t o o l s.T h e r e s u l t i n g m o d e l i s u s e d t o d e f i n e a n e r r o r q u a n t i t y b a s e d o n a n o m i n a l (m a n u f a c t u r e r's)k i n e m a t i c p a r a m e t e r s e t,a n d a n u n k n o w n, actual parameter set which is to be identified.2. Ex pe ri me n ta l m ea su re m e nts o f th e rob ot po se (p art ial o r complete) are taken in order to obtain data relating to the actual parameter set for the robot.3.The actual kinematic parameters are identified by systematicallyc h a n g i n g t h e n o m i n a l p a r a m e t e r s e t s o a s t o r ed u ce t h e e r r o r q u a n t i t y d ef i n e d i n t h e m o d e l l i ng ph a s e.O n e a p p r o a c h t o a c hi e v i n g t h i s i d e n t i f i c a t i o n i s d e t e r m i n i n g t h e a n a l y t i c a l d i f f e r e n t i a l r e l a t i o n s h i p b e t w e e n t h e p o s e v a r i a b l e s P a n d t h e k i n e m a t i c p a r a m e t e r s K i n t h e f o r m of a Jacobian,and then inverting the equation to calculate the deviation of t h e k i n e m a t i c p a r a m e t e r s f r o m t h e i r n o m i n a l v a l u e sAlternatively, the problem can be viewed as a multidimensional o p t i m i s a t i o n t a s k,i n w h i c h t h e k i n e m a t i c p a r a m e t e r set is changed in order to reduce some defined error function t o z e r o.T h i s i s a s t a n d a r d o p t i m i s a t i o n p r o b l e m a n d m a y be solved using well-known methods.4. The final step involves the incorporation of the identified k i n e m a t i c p a r a m e t e r s i n t h e c o n t r o l l e r o f t h e r o b o t a r m, the details of which are rather specific to the hardware of the system under study.This paper addresses the issue of gathering the experimental d a t a u s e d i n t h e c a l i b r a t i o n p r o c e s s.S e v e r a l m e t h o d s a r e available to perform this task, although they vary in complexity, c o s t a n d t h e t i m e t a k e n t o a c q u i r e t h e d a t a.E x a m p l e s o f s u c h t e c h n i q u e s i n c l u d e t h e u s e o f v i s u a l a n d a u t o m a t i c t h e o d o l i t e s,s e r v o c o n t r o l l e d l a s e r i n t e r f e r o m e t e r s, a c o u s t i c s e n s o r s a n d v i d u a l s e n s o r s .A n i d e a l m e a s u r i n g system would acquire the full pose of the manipulator (position and orientation), because this would incorporate the maximum information for each position of the arm. All of the methods m e n t i o n e d a b o v e u s e o n l y t h e p a r t i a l p o s e,r e q u i r i n g m o r ed a t a t o be t a k e nf o r t h e c a l i b r a t i o n p r o c e s s t o p r o c e e d.2. TheoryIn the method described in this paper, for each position in which the manipulator is placed, the full pose is measured, although several intermediate measurements have to be taken in order to arrive at the pose. The device used for the pose m e a s u r e m e n t i s a c o o r d i n a t e-m e a s u r i n g m a c h i n e(C M M), w h i c h i s a t h r e e-a x i s,p r i s m a t i c m e a s u r i n g s y s t e m w i t h a q u o t e d a c c u r a c y o f0.01r a m.T h e r o b o t m a n i p u l a t o r t o b e c a l i b r a t e d,a P U M A560,i s p l a c e d c l o s e t o t h e C M M,a n d a special end-effector is attached to the flange. Fig. 1 shows the arrangement of the various parts of the system. In this s e c t i o n t h e k i n e m a t i c m o d e l w i l l b e d e v e l o p e d,t h e p o s e estimation algorithms explained, and the parameter identification methodology outlined.2.1 Kinematic ParametersIn this section, the basic kinematic structure of the manipulator will be specified, its relation to a user-defined world coordinatesystem discussed, and the end-point toil modelled. From these m o d e l s,t h e k i n e m a t i c p a r a m e t e r s w h i c h m a y b e i d e n t i f i e d using the proposed technique will be specified, and a method f o r d e t e r m i n i n g t h o s e p a r a m e t e r s d e s c r i b e d. The fundamental modelling tool used to describe the spatial relationship between the various objects and locations in the m a n i p u l a t o r w o r k s p a c e i s t h e D e n a v i t-H a r t e n b e r g m e t h o d ,w i t h m o d i f i c a t i o n s p r o p o s e d b y H a y a t i,M o o r i n g a n d W u t o a c c o u n t f o r d i s p r o p o r t i o n a l m o d e l s w he n tw o co n se cu t iv e jo i n t a x e s ar e nom ina ll y p a r all el. A s s h o w n i n F i g.2,t h i s m e t h o d p l a c e s a c o o r d i n a t e f r a m e o neach object or manipulator link of interest, and the kinematics a r e d e f i n e d b y t h e h o m o g e n e o u s t r a n s f o r m a t i o n r e q u i r e d t o change one coordinate frame into the next. This transformation takes the familiar formT h e a b o v e e q u a t i o n m a y b e i n t e r p r e t e d a s a m e a n s t o t r a n s f o r m f r a m e n-1i n t o f r a m e n b y m e a n s o f f o u r o u t o f t h e f i v e o p e r a t i o n s i n d i c a t e d.I t i s k n o w n t h a t o n l y f o u r transformations are needed to locate a coordinate frame with r es pect to the p revious one. Whe n consecutiv e ax es are not parallel, the value of/3. is defined to be zero, while for the case when consecutive axes are parallel, d. is the variable chosen to be zero.W h e n c o o r d i n a t e f r a m e s a r e p l a c e d i n c o n f o r m a n c e w i t h the modified Denavit-Hartenberg method, the transformations given in the above equation will apply to all transforms of o n e f r a m e i n t o t h e n e x t,a n d t h e s e m a y b e w r i t t e n i n a g e n e r i c m a t r i x f o r m,w h e r e t h e e l e m e n t s o f t h e m a t r i x a r e functions of the kinematic parameters. These parameters are simply the variables of the transformations: the joint angle 0., the common normal offset d., the link length a., the angle o f tw is t a., a nd th e an g l e /3.. Th e mat rix f orm i s u suall y expressed as follows:For a serial linkage, such as a robot manipulator, a coordinate frame is attached to each consecutive link so that both the instantaneous position together with the invariant geometry a r e d e s c r i b e d b y t h e p r e v i o u s m a t r i x t r a n s f o r m a t i o n.'T h etransformation from the base link to the nth link will therefore be given byF i g.3s h o w s t h e P U M A m a n i p u l a t o r w i t h t h e D e n a v i t-H a r t e n b e r g f r a m e s a t t a c h e d t o e a c h l i n k,t o g e t h e r with world coordinate frame and a tool frame. The transformation f r o m t h e w o r l d f r a m e t o t h e b a s e f r a m e o f t h e manipulator needs to be considered carefully, since there are potential parameter dependencies if certain types of transforms a r e c h o s e n.C o n s i d e r F i g.4,w h i c h s h o w s t h e w o r l d f r a m e x w,y,,z,,t h e f r a m e X o,Y o,z0w h i c h i s d e f i n e d b y a D H t r a n s f o r m f r o m t h e w o r l d f r a m e t o t h e f i r s t j o i n t a x i s o f t h e m a n i p u l a t o r,f r a m e X b,Y b,Z b,w h i c h i s t h e P U M Amanufacturer's defined base frame, and frame xl, Yl, zl which is the second DH frame of the manipulator. We are interested i n d e t e r m i n i n g t h e m i n i m u m n u m b e r o f p a r a m e t e r s r e q u i r e d to move from the world frame to the frame x~, Yl, z~. There are two transformation paths that will accomplish this goal: P a t h1:A D H t r a n s f o r m f r o m x,,y,,z,,t o x0,Y o,z o i n v o l v i n g f o u r p a r a m e t e r s,f o l l o w e d b y a n o t h e r t r a n s f o r m f r o m x o,Y o,z0t o X b,Y b,Z b w h i c h w i l l i n v o l v e o n l y t w o parameters ~b' and d' in the transformFinally, another DH transform from xb, Yb, Zb to Xt, y~, Z~ w hi ch i nv ol v es f o ur p ar a m ete r s e xc ept t hat A01 a n d 4~' ar e b o t h a b o u t t h e a x i s z o a n d c a n n o t t h e r e f o r e b e i d e n t i f i e d independently, and Adl and d' are both along the axis zo and also cannot be identified independently. It requires, therefore, o nl y ei gh t i nd ep e nd en t k i nem a t ic p arame ter s to g o fr om th e world frame to the first frame of the PUMA using this path. Path 2: As an alternative, a transform may be defined directly from the world frame to the base frame Xb, Yb, Zb. Since this is a frame-to-frame transform it requires six parameters, such as the Euler form:T h e f o l l o w i n g D H t r a n s f o r m f r o m x b,Y b,z b t O X l,Y l,z l would involve four parameters, but A0~ may be resolved into 4~,, 0b, ~, and Ad~ resolved into Pxb, Pyb, Pzb, reducing theparameter count to two. It is seen that this path also requires e i g h t p a r a m e t e r s a s i n p a t h i,b u t a d i f f e r e n t s e t.E i t h e r o f t h e a b o v e m e t h o d s m a y b e u s e d t o m o v e f r o m t h e w o r l d f r a m e t o t h e s e c o n d f r a m e o f t h e P U M A.I n t h i s w o r k,t h e s e c o n d p a t h i s c h o s e n.T h e t o o l t r a n s f o r m i s a n E u l e r t r a n s f o r m w h i c h r e q u i r e s t h e s p e c i f i c a t i o n o f s i x parameters:T he total n umber of paramete rs u sed in the k inem atic model becomes 30, and their nominal values are defined in Table 1.2.2 Identification MethodologyThe kinematic parameter identification will be performed as a multidimensional minimisation process, since this avoids the calculation of the system Jacobian. The process is as follows: 1. Be gi n wi t h a g ue ss s e t of k in em atic par am ete r s, s uch a s the nominal set.2. Select an arbitrary set of joint angles for the PUMA.3. Calculate the pose of the PUMA end-effector.4.M e a s u r e t h e a c t u a l p o s e o f t h e P U M A e n d-e f f e c t o r f o r t he s am e se t o f j oi nt a n g les.In g enera l, th e m e a sur ed an d predicted pose will be different.5. Mo di fy t h e ki n em at ic p ara m e te rs in a n o rd erl y man ner i n o r d e r t o b e s t f i t(i n a l e a s t-s q u a r e s s e n s e)t h e m e a s u r e d pose to the predicted pose.The process is applied not to a single set of joint angles but to a number of joint angles. The total number of joint angles e t s r e q u i r e d,w h i c h a l s o e q u a l s t h e n u m b e r o f p h y s i c a l measurement made, must satisfyK p i s t h e n u m b e r o f k i n e m a t i c p a r a m e t e r s t o b e i d e n t i f i e d N i s t h e n u m b e r o f m e a s u r e m e n t s(p o s e s)t a k e n D r r e p r e s e n t s t h e n u m b e r o f d e g r e e s o f f r e e d o m p r e s e n t i n each measurement.In the system described in this paper, the number of degrees of freedom is given bysince full pose is measured. In practice, many more measurements s h o u l d b e t a k e n t o o f f s e t t h e e f f e c t o f n o i s e i n t h e e xp er im en ta l m ea s ur em en t s. T h e o pt imisa tio n pro c e dur e use d is known as ZXSSO, and is a standard library function in the IMSL package .2.3 Pose MeasurementIt is apparent from the above that a means to determine the f u l l p o s e o f t h e P U M A i s r e q u i r e d i n o r d e r t o p e r f o r m t h e calibration. This method will now be described in detail. The end-effector consists of an arrangement of five precisiontooling b a l l s a s s h o w n i n F i g. 5.C o n s i d e r t h e c o o r d i n a t e s o f the centre of each ball expressed in terms of the tool frame (Fig. 5) and the world coordinate frame, as shown in Fig. 6. T h e r e l a t i o n s h i p b e t w e e n t h e s e c o o r d i n a t e s m a y b e w r i t t e n as:w he re P i' i s t he 4 x 1 c o lum n ve ct or of th e coo r d ina tes o f the ith ball expressed with respect to the world frame, P~ is t he 4 x 1 c o lu mn ve ct or o f t h e c oo rdina tes o f t h e it h bal l expressed with respect to the tool frame, and T is the 4 • 4 h o m o g e n i o u s t r a n s f o r m f r o m t h e w o r l d f r a m e t o t h e t o o l frame.The n may be foun d, a n d use d as th e m easure d pose in t he calibration process. It is not quite that simple, however, since it is not possible to invert equation (11) to obtain T. The a bo ve proce ss is performed f or t he four ball s, A, B, C and D, and the positions ordered as:or in the form:S i n c e P',T a n d P a r e a l l n o w s q u a r e,t h e p o s e m a t r i x m a y be obtained by inversion:I n pr ac ti ce it m a y be d i f fic u l t fo r the CM M to a c ces s fou r b a i l s t o d e t e r m i n e P~w h e n t h e P U M A i s p l a c e d i n c e r t a i n configurations. Three balls are actually measured and a fourth ball is fictitiously located according to the vector cross product:R e g a r d i n g t h e d e t e r m i n a t i o n o f t h e c o o r d i n a t e s o f t h ec e n t r e o f a b a l l b a s ed o n me a s u r e d p o i n t s o n i t s s u rf a c e, n o a n a l y t i c a l p r o c e d u r e s a r e a v a i l a b l e.A n o t h e r n u m e r i c a l optimisation scheme was used for this purpose such that the penalty function:w a s m i n i m i s e d,w h e r e(u,v,w)a r e t h e c o o r d i n a t e s o f t h e c e n t r e o f t h e b a l l t o h e d e t e r m i n e d,(x/,y~,z~)a r e t h e coordinates of the ith point on the surface of the ball and r i s th e ba ll di am e te r. I n the t es ts perf orm ed, i t was foun d sufficient to measure only four points (i = 4) on the surface to determine the ball centre.中文译文:应用坐标测量机的机器人运动学姿态的标定这篇文章报到的是用于机器人运动学标定中能获得全部姿态的操作装置——坐标测量机(CMM)。
蓄电池SOH估算方法研究综述

蓄电池SOH估算方法研究综述耿星;王友仁【摘要】蓄电池运行状态是否正常,直接影响着应用领域中各种设备的正常、可靠和安全运行.在无人值守现场、电子商务中心、银行等关键公共场合,蓄电池就显得更为重要.电池健康状态用于定量描述电池当前偏离额定指标的程度,是蓄电池状态监测的重要指标.由于蓄电池结构的复杂性,电池健康状态无法直接测量读数,只能通过外特性估算.重点阐述了近年来蓄电池健康状态的估算方法.【期刊名称】《机械制造与自动化》【年(卷),期】2019(000)001【总页数】3页(P204-206)【关键词】蓄电池;健康状态;估算方法;综述【作者】耿星;王友仁【作者单位】南京航空航天大学自动化学院,江苏南京211106;南京航空航天大学自动化学院,江苏南京211106【正文语种】中文【中图分类】TM9120 引言随着国家经济不断发展,能源、电力、交通、通信、环保等领域现代化水平逐步提高。
作为后备能源的蓄电池系统正在被大量使用。
对所有不允许断电的供电电源系统来说,蓄电池组都是一个不可缺少的后备电源系统。
蓄电池运行状态是否正常,直接影响着应用领域中各种设备的正常可靠和安全运行。
在无人值守现场、电子商务中心、银行等关键公共场合,蓄电池就显得更为重要[1]。
因此,对蓄电池运行状态进行监测和故障诊断具有十分重要的意义。
将蓄电池大规模、高可靠地工程化,其中的关键环节是电池管理系统(battery management system,BMS)技术,但目前仍不够完善。
随着先进电池在电动汽车中应用的推广及其技术的发展,对电池管理系统的要求也不断提高。
制约BMS 大规模、全领域应用的一个关键因素是电池的健康状态(state of health, SOH)很难准确估计,直接影响电池容量的有效发挥,降低了电池使用的安全性和可靠性,使得电池充放电控制缺乏足够参考依据,最终影响电池性能和使用寿命[2]。
健康状态是指蓄电池当前的主要性能偏离了额定的设计性能及指标,如单体电池在充满电的状态下的容量大小、内阻大小、大电流放电下的端电压及充电时电池的接受能力、不同的温度特性等[3]。
机器人课件chapter4

在Kismet学习排序活动时,人类向机器人展示一些常见 的标准(颜色),以及不同的对象应该放的位置。机器人 通过语言描述来表达自己的理解,并向目标位置点头。人 类向机器人展示搜索活动的例子,机器人通过链接名称和 对象来演示它的理解。通过搜索活动来学习Blah与blah, 新的视角产生新的感知目标,并尝试构建这个感知目标来 了解人类的感知过程。机器感知对于特定领域可以是健壮 的,但不像人类的感知方法那样具有适应性,它将传统的 机器感知和机器学习与机会主义发展策略相结合——主动 感知运动的“劳累”。如果一个机器人从事一项已知的活 动,就有足够的限制来识别该活动中的新元素。同样,如 果已知元素参与了一些不熟悉的活动,跟踪这些元素可以 帮助确定该活动的特征。潜在地,感知发展就是这样循环 的。
Text A
Perception and Perspective in Robotics Paul Fitzpatrick MIT Computer Science and Artificial Intelligence Laboratory Humanoid Robotics Group Goal To build robots that can interact with novel objects and participate in novel activities Challenge Machine perception can be robust for a specific domain such as face detection, but unlike human perception it is not currently adaptable in the face of change (new objects, changed circumstances) Approach Integrate conventional machine perception and machine learning with strategies for opportunistic development
Computerized Developments in Design, Generation, Simulation of Meshing, and Stress Analysis of Gear

Meccanica(2005)40:291–324©Springer2005 DOI10.1007/s11012-005-4020-yOVERVIEWS AND TUTORIALSComputerized Developments in Design,Generation,Simulation of Meshing,and Stress Analysis of Gear DrivesFaydor L.Litvin,Daniele Vecchiato,Eugene Gurovich,Alfonso Fuentes1,∗,Ignacio Gonzalez-Perez1,Kenichi Hayasaka2and Kenji Yukishima2Department of Mechanical and Industrial Engineering,Gear Research Center,University of Illinois at Chicago,842West Taylor Street,Chicago,IL60607-7022,USA;1Department of Mechanical Engineering,Polytechnic University of Cartagena,Campus Universitario Muralla del Mar,C/Doctor Fleming,s/n-30202,Cartagena,Murcia,Spain;2Gear R&D Group,Research Development Center, Yamaha Motor Co.,LTD.,2500Shingai,Iwata,Shizuoka438-8501,Japan(Received:22October2004;accepted in revised form:12March2005)Abstract.The paper represents new computerized developments in design,generation,simulation of mesh-ing,and stress analysis of gear drives.The main contents of the paper are:(i)application of a predesigned parabolic function of transmission errors for reduction of noise,(ii)computerized simulation of noise caused by transmission errors,(iii)modification of the basic algorithm of tooth contact analysis,and (iv)application of approaches developed for enhanced design and simulation of meshing of the following gear drives:(a)spiral bevel gear drives,(b)face-gear drives(including an approach for grinding),and (c)modified helical gear drives.The developed theory is illustrated with numerical examples.Key words:Transmission errors,Local synthesis,Bearing contact,Tooth contact analysis,Stress analysis.1.IntroductionTheory,design,simulation of meshing,generation and stress analysis were the sub-ject of research of many distinguished scientists and leading gear companies[1–40]. The extended list of references relates the contents of the paper with the basic devel-opment of theory of gearing,differential geometry,design and manufacturing of gear drives,and stress analysis.The contents of this paper cover conceptually the latest developments accom-plished by the authors that represent a team of researchers united by the same methodology.The developed approach is based on application of:(i)local synthesis, (ii)modification of geometry of gears,(iii)application of a modified tooth contact analysis(TCA)algorithm,and(iv)application of an enhanced approach for applica-tion of thefinite element method to stress analysis.∗Author for correspondence:Tel.:+34-968-326432;Fax:+34-968-326449,e-mail:alfonso.fuentes @upct.es292Faydor L.Litvin et al.The main topics of the paper are:(1)Reduction of noise of gear drives.The reduction of noise is achieved byapplication of a predesigned parabolic function of transmission errors.Sucha function is able to absorb discontinued linear functions of transmission errorswith a large magnitude of maximal transmission errors.The discontinued func-tions of transmission errors are caused by errors of alignment such as change of shaft angle,center distance of some spatial gear drives,errors of machine-tool settings,etc.The advantage of application of a predesigned parabolic function of transmission errors is confirmed by simulation of the noise caused by typical function of transmission errors of misaligned gear drives.The authors have developed an approach that enables to computerize the noise of the gear drive and hear it by the speakers of a computer.This can be achieved ahead of the manufacturing of a designed gear drive.(2)Modified TCA approach.The proposed modification of TCA is based on an algo-rithm for determination of guess values for the starting point of tangency of mat-ing surfaces.The guess values may be determined considering only as known at the start of computation the machine-tool settings used for gear generation.Then,it becomes possible to develop a TCA program for simulation of meshing of manufactured gears.(3)Enhanced approach for application of FEM to stress analysis.The enhancedapproach for application of thefinite element method to stress analysis is based on application of a contacting model for mating gears developed by using analyt-ical representation of tooth surfaces.This allows to avoid codes for the numerical development of the contacting model.The stress analysis is complemented with investigation of formation of the bearing contact and detection and avoidance of zones of severe contact stresses.(4)Enhanced design of spiral bevel gears,face-gear drives,and modified helical gears.The applied enhanced design of gear drives covers:(i)Design of low noise spiral bevel gears that is based on application of:(a)com-bination of local synthesis and TCA;(b)modified roll and modification of geometry of generating tool;(c)an approach for reduction of noise.(ii)Basic concepts of design and analysis of face-gear drives,and a new approach for generation of face-gears by grinding and cutting(applying for this purpose a worm of special shape).(iii)Modification of geometry of helical gears with parallel axes that is based on:(a)localization of bearing contact by substitution of line contact of toothsurface by point contact;(b)generation of gears by a plunging disk or bya worm(hob)that enables to reduce the noise and improve the bearing con-tact;(c)application of TCA for analysis of misaligned gear drives.The ideas represented in the paper may be applied as well for worm gear drives and hypoid gear drives.Computerized Developments293Figure1.Transmission function as a sum of a linear function and a piecewise linear function of transmission errors caused by errors of alignment.2.Functions of Transmission ErrorsIt has been already recognized by researchers that the main source of noise and vibration are transmission errors.Such errors are caused by misalignment of gear drives such as change of shaft angle,change of center distance(for some spatial gear drives),errors of installment of machine-tool settings,etc.The results of TCA show that the real transmission function of a misaligned gear drive is a piecewise linear function of transmission errors(Figure1).The main idea of the authors for the design of gear drives with reduced noise is based on application of a predesigned parabolic function of transmission errors (Figure2).A predesigned parabolic function of transmission errors absorbs linear functions of transmission errors caused by misalignment(see Figure1),and this is the main condition of reduction of noise[25].This statement is proven in Section10 of the paper by computerized simulation of noise caused by transmission errors. 3.Definition of Two Cases of TCAHenceforth we will consider the following two cases of TCA:Case1:The location of the main point of tangency of tooth surfaces is not known, but have to be determined.Case2:The location of the mean contact point is known ahead.In Case1,the machine-tool settings applied for generation of the gears are consid-ered as known.The analysis of meshing may be performed in the following sequence: (i)derivation of gear tooth surfaces by using of the basic machine-tool settings applied for surface generation;(ii)approximate determination of a contact point, used as a guess value for TCA;(iii)development of TCA and analysis of meshing.294Faydor L.Litvin et al.Figure2.Transmission function as a sum of a linear function and a predesigned function of trans-mission errors.In Case2,the design of gears is performed as a combination of local synthesis and TCA.Local synthesis means that the mean contact point M of tooth surfaces is assigned ahead,but the design has to provide improved conditions of meshing in the neighborhood of M.The procedure of TCA has to be applied for obtaining the loca-tion of the bearing contact and transmission errors at any point of contact of tooth surfaces(it differs from M).4.Tooth Contact Analysis:Case14.1.Introductory RemarksThe gear tooth surfaces of the gears of the drive are notated as 1and 2.Surface i(i=1,2)is generated by a tool surfaceσi(i=1,2),and is determined in coor-dinate system S i(i=1,2)rigidly connected to i.Surface i is the envelope to the family of tool surfacesσi.Surfaceσi is represented in coordinate system S(i)g(i=1,2) in two-parameter form by vector functionr(i)g(u i,θi),i=1,2.(1) The normal to the generating surfaceσi is determined asN(i)g=∂r(i)g∂u i×∂r(i)g∂θi.(2)The generated surface i(i=1,2)is represented in S i by three related parameters as[25,38,39]r(i) i (u i,θi,ψi)=M(i)ig(ψi)r(i)g(u i,θi),(3)Computerized Developments295f ig(u i,θi,ψi)=∂r(i)i∂u i×∂r(i)i∂θi·∂r(i)i∂ψi.(4)Here,(3)is the family of tool surfaces,and(4)is the equation of meshing.The location and orientation of surfaces 1and 2are determined separately,in coordinate systems S1and S2.However,to start the simulation of meshing by TCA, we have to determine the location of points of tangency of 1and 2.Only after that,it becomes possible to start TCA as an iterative procedure.This means that it becomes necessary to determine the location of generated surfaces 1and 2and their normals in afixed coordinate system S f and then apply the basic algorithm of TCA as the condition of tangency of 1and 2(see Figure3).The TCA algorithm yields:r(1) f (u1,θ1,ψ1,φ1)=r(2)f(u2,θ2,ψ2,φ2),(5)N(1)f (u1,θ1,ψ1,φ1)=λN(2)f(u2,θ2,ψ2,φ2),(6)where the scalarλ=0is used for observation of collinearity of N(1)f and N(2)f.Thefirst guess has to provide the set of parametersM(u(0)1,θ(0)1,ψ(0)1,φ(0)1,u(0)2,θ(0)2,ψ(0)2,φ(0)2).(7)for a point where equations(5)and(6)aresatisfied.Figure3.Tangency of surfaces.296Faydor L.Litvin et al.Figure4.Representation of cells in plane of parameters:(a)(u1,θ1)for the pinion and(b)(u2,θ2) for the gear.Figure5.Illustration of expression of cells in terms of parameters of surface of a tool.4.2.Numerical Representation of Surfaces by Sets of CellsWe start the explanations considering numerical representation of generating surfaces by sets of cells(Figure4).The cells are represented in terms(u i,θi)(i=1,2)in plane of parameters(u i,θi)of the generating tool.The relation between the location of a cell in plane(u i,θi)and location of the cell on the tool surfaceσi is illustrated by Figure5.4.3.Location of Cell on Generated Surface iChoosing a cell in plane of parameters(u i,θi),we may determine the location of the cell on generated surface i and the normal to i assigning parameterψi,and apply-ing equations(3)and(4).Computerized Developments297 4.4.Location of Cell in Fixed Coordinate System S fFixed coordinate system S f is chosen for consideration of tangency of contacting surfaces 1and 2.We represent in S f:(i)the axes of rotation of pinion and gear, (ii)shaft angle of 1and 2,and(iii)the shortest distance between the axes of rota-tion of 1and 2.The location of the cell infixed coordinate system S f requires four parameters:(u i,θi,ψi,φi).Parameterφi is the angle of rotation of i(with the cell)with respect tofixed coordinate system S f.4.5.Pairing of CellsThe goal of pairing of cells is tofind such a pair of cells represented infixed coordi-nate system S f that will have the shortest distance between them.Then,such a pair of cells will have a location close to the sought-for point M of tangency of 1and 2in coordinate system S f.The pairing of cells is based on the following considerations:(a)We choose arbitrarily a cell in plane of parameters(u1,θ1)of toolσ1,assigning(u1,θ1).(b)The toolσ1and pinion perform related rotations,and meshing points ofσ1and1are correlated by the equation of meshing.Therefore,in addition to(u1,θ1), it becomes known parameterψ1with which tangency ofσ1and 1is provided.(c)Consideration of parameters(u1,θ1,ψ1)enables to identify the location of thechosen pinion cell in coordinate system S1rigidly connected to the pinion. (d)The location of the chosen pinion cell infixed coordinate system S f is obtainedby rotating coordinate system S1(with the cell)about the z1≡z(1)f of the pinion through an angleφ1.(e)The magnitude ofφ1may be assigned considering that the cell is in contact withan imaginary surface that performs rotation about z(2)f .Then,angleφ1has to sat-isfy the equation of meshing of the chosen cell with the imaginary surface.The solution of this equation provides two values ofφ1[26].(f)Similar considerations have to be applied for identification of location of a cellchosen from the grid of the gear;the location of the cell of the grid of gear in coordinate system S f is identified with a parameterφ2;the solution of the respective equation of meshing also provides two values ofφ2.By considering of all possible combinations of pairs of cell,the goal is to deter-mine the pair that has the shortest distance.The surface normals to 1and 2of this pair of cells deviates from each other only slightly.Therefore,the prescribed pro-cedure allows to obtain approximately the location of point of contact of 1and 2. Such a point is required as a guess value for the start of TCA.We have to emphasize the importance of the described procedure for determina-tion of the guess values taking into account the following:(i)It was done for the case of limited information about the contacting surface:onlythe machine-tool settings applied for gear surface generation were available.298Faydor L.Litvin et al.(ii)Using the solution of the guess values,the simulation of meshing of gears may be started(see below).4.6.Procedure of TCAWe recall that the tooth surfaces 1and 2are in point tangency,and the instantaneous tangency of surfaces is represented in coordinate system S f by vector equations(Figure3)Computerized Developments 299r (1)f −r (2)f =0,(8)n (1)f −n (2)f =0.(9)We consider the most complicated case wherein the generated tooth surfaces are represented each by three related parameters.The algorithm of TCA is represented as follows:r (1)f (u 1,θ1,ψ1,φ1)−r (2)f (u 2,θ2,ψ2,φ2)=0,(10)∂r (2)f ∂u 2· ∂r (1)f ∂u 1×∂r (1)f ∂θ1 =0,(11)∂r (2)f ∂θ2· ∂r (1)f ∂u 1×∂r (1)f ∂θ1 =0,(12)f (1)(u 1,θ1,ψ1)=0,(13)f (2)(u 2,θ2,ψ2)=0.(14)Here,f (1)=0,f (2)=0are the equations of meshing of the generating tools and gen-erated surfaces of pinion and gear,respectively.Equations (11)and (12)are applied instead of two scalar equations that may be obtained from vector equation (9)for the following reason:vector equation (9)provides only two independent scalar equa-tions,since n (1)f = n (2)f =1.The best choice of two scalar equations from the set of possible three ones cannot be predicted ahead.Substitution of vector equation (9)by equations (11)and (12)enables to overcome this obstacle.The computational procedure of TCA is based on the algorithm that requires the solution of the system of nonlinear equations from (10)up to (14).These equations yield a system of seven nonlinear equations in eight unknowns that may be repre-sented asf i (u 1,θ1,ψ1,φ1,u 2,θ2,ψ2,φ2)=0,i =1,...,7.(15)Equation (15)is satisfied at point M(u (0)1,θ(0)1,ψ(0)1,φ(0)1,u (0)2,θ(0)2,ψ(0)2,φ(0)2)that is thestarting point of computations.In accordance to the Theorem of Implicit Function System Existence [8],equation(15)may be solved at M by functions(u 1(φ1),θ1(φ1),...,φ2(φ1))(16)with the condition that the Jacobian J =0,whereJ =D(f 1,f 2,f 3,f 4,f 5,f 6,f 7)D(u 1,θ1,ψ1,u 2,θ2,ψ2,φ2).(17)The solution of the system f i =0(i =1,...,7)is an iterative process that may be based on application of the Newton–Raphson algorithm.The developed algorithm may be applied for misaligned gear tooth surfaces as well [25].300Faydor L.Litvin et al.5.Tooth Contact Analysis:Case25.1.IntroductionThe difference of cases1and2of TCA is that in case1the designer has to apply TCA for simulation of meshing considering as known the pinion and gear machine-tool settings applied for their generation.The computational procedure requires determination of guess values(see equation(15)).Case2of TCA corresponds to the case in which the designer combines applica-tion of the procedure of local synthesis with TCA.The goal of local synthesis is to determine the pinion machine-tool settings by considering as known the machine-tool settings for the gear,that will provide improved conditions of meshing locally,at the assigned mean contact point M.5.2.Local SynthesisThe approach has been proposed in[10,12]and then applied for various types of gear drives.The basic ideas of local synthesis are as follows:(i)The mean contact point M of tangency on one of the mating surfaces,say geartooth surface 2,is chosen(see Figure6).Figure6.Illustration of parametersη2and2a applied for local synthesis.(ii)The machine-tool settings of gear tooth surface 2are considered as known.They may be adapted,for example,from the summary of settings of manufacturing.(iii)The principal curvatures and directions of 2at point M are determined by using equations of 2.Computerized Developments301(iv)The input parameters of local synthesis are2a,η2,and m21that are taken at M.Here,2a is the major axis of the instantaneous contact ellipse;η2determines theorientation of the tangent to the contact path at M;m21=d2(φ2(φ1))/dφ21is thesecond derivative of the transmission functionφ2(φ1).The procedure of local synthesis enables to determine machine-tool settings of the pinion for the conditions of meshing assigned ahead(see,for instance,local synthe-sis of spiral bevel gears[1,25]).The derivations of principal curvatures and direc-tions of contacting surfaces are simplified by using an approach that enables to relate principal curvatures and directions of generating and generated surfaces[11,13].The contact ellipse is determined by using relations between the principal curvatures and directions of contacting surfaces and the elastic deformation at contacting point M [11,13].The desired localization of bearing contact is provided by plunging of the generat-ing tool controlled by a parabolic function(see,for instance,generation of modified helical gears[24]).A predesigned parabolic function of transmission errors(in some cases of design) is provided by the so-called modified roll.Here,the modified roll is based on nonlinear function of rotation of the generating tool(see Ref.24).5.3.Tooth Contact AnalysisThe algorithm of TCA is the same as in TCA Case1,but the iterative process does not require the preliminary determination of guess values at mean contact point M, since point M is assigned ahead.We emphasize that local synthesis and TCA are provided simultaneously,but the obtaining of best conditions of meshing and contact may require several attempts.6.Enhanced Approach for Stress AnalysisApplication of thefinite element analysis(FEA)enables:(1)Determination of contact and bending stresses for the pinion and the gear.(2)Investigation of formation of bearing contact taking into account that the mesh-ing is transferred from one pair of teeth to the neighboring one.(3)Detection and avoidance of areas of severe contact stresses.Application of thefinite element method requires the development of thefinite ele-ment model formed by thefinite element mesh,the definition of contacting surfaces, and the establishment of boundary conditions to load the gear drive with the desired torque.The authors apply a general purpose computer program[6]to perform the finite element analysis.An enhanced approach for application offinite element analysis has been used for design of gear drives[1,25].One of the main ideas of the applied FEA approach is the automatization of derivation of the contacting model of gear teeth by direct application of tooth surface equations.This approach enables to determine contact302Faydor L.Litvin et al.and bending stresses for the whole cycle of meshing,investigate the formation of the bearing contact and determine,if they exist,hidden areas of severe contact wherein the contact stresses are substantially increased.Figure7illustrates the stages of generation of thefinite element model of a gear tooth.Figure8shows afinite element model of a spiral bevel gear and thefixed nodes for the boundary conditions.Figure9a shows the formation of pinion bearing contact and the existence of zone A of severe contact stresses;Figure9b shows that the zone A is eliminated by application of Top-rem blades.Such blades remove a portion of the root of the gear mating to the pinion.7.Design of Face-Milled Spiral Bevel Gears7.1.IntroductionThis section covers design,simulation of meshing,stress analysis,and results of test of spiral bevel gears of enhanced design[1,25].Figure7.Illustration of:(a)the volume of designed body;(b)auxiliary intermediate surfaces;(c)determination of nodes for the whole volume;(d)discrete volume byfinite elements.Computerized Developments303Figure8.Boundary conditions for the gear.The quality of meshing and contact of spiral bevel gears depends substantially on the applied machine-tool settings.Such settings are not standardized and are usually developed by the designer.The design considered in this paper is based on the following ideas:(i)The machine-tool settings of the gear are adapted from the manufacturing sum-mary,but the machine-tool settings of the pinion have to be developed following the idea of combination of local synthesis and TCA.(ii)The developed computational procedure is accomplished in four stages[1,25].Stage1:Obtaining of an adjusted path of contactIn general,a longitudinal bearing contact is preferable.However,if sucha bearing contact becomes too sensitive to errors of alignment,the pathof contact is corrected by slight deviation from the exact longitudinaldirection(see Stage3).Stage2:Application of modified rollThe goal is to provide a predesigned parabolic function of transmissionerrors by application of modified roll.Stage3:Adjustment of bearing contactThe purpose is evaluation of orientation of the bearing contact and its shiftdue to errors of alignment based on results of performed TCA.The correc-tion of the bearing contact requires a new attempt of local synthesis.Stage4:Investigation of formation of bearing contact and avoidance of severe contact stressesThe authors have proposed for improvement of bearing contact applica-tion of parabolic blades of head-cutters instead of straight profile blades(see Figure10)and application of Top-rem blades.The advantages ofdeveloped approach have been confirmed by:(i)comparison with exist-ing design,and(ii)by experimental test of noise and vibration.304Faydor L.Litvin et al.Figure9.Formation of pinion bearing contact in a spiral bevel gear drive by application of(a)con-ventional blades(A illustrates the zone of severe contact stresses)and(b)top-rem blades(zone A of severe contact stresses is eliminated).7.2.Example of Optimized DesignThe blank data of the to-be-optimized spiral bevel gear drive are shown in Table1. The machine-tool settings for the gear-member of the gear drive are adapted from the summary of the settings of manufacturing of the previous design(baseline design) and are shown in Table2.Table3shows the pinion machine-tool settings obtained from computations that provide improved conditions of meshing and contact of the gear drive.The concave side of the pinion tooth surface and the convex side of the gear tooth surface are considered as the driving and driven surfaces,respectively.Figure11a–c shows for the previous design:the bearing contact and contact pattern,and the function of transmission errors,respectively.Computerized Developments305Figure10.Blade and generating revolution surfaces for the gear parabolic-profile head-cutter:(a)illus-tration of parabolic profile of the blade;(b)and(c)generating tool surfaces for concave and convex sides.Table1.Blank dataPinion GearNumber of teeth of pinion and gear933 Module(mm) 4.8338Shaft angle(deg.)90.000Mean spiral angle(deg.)32.000032.0000 Hand of spiral RH LH Face width(mm)27.500027.5000 Mean cone distance(mm)68.920068.9200 Whole depth(mm)9.43009.4300 Pitch angles(deg.)15.255174.7449 Root angles(deg.)13.883369.5833 Face angles(deg.)20.416776.1167 Clearance(mm) 1.0300 1.0300 Addendum(mm) 6.6400 1.7600 Dedendum(mm) 2.79007.6700The efforts of the optimization of the gear drive were directed to obtain an adjusted bearing contact as shown in Figure12a and b for the driving and coast sides of the gear tooth surfaces and a predesigned parabolic function of transmis-sion errors as shown in Figure12c.The chosen orientation of the bearing contact maximizes the tolerances of errors of alignment that the gear drive can absorb.The306Faydor L.Litvin et al.Table2.Machine-tool settings for the gear and installment settings ofthe gear head-cutterMachine center to back(mm)0.0000Sliding base(mm)−0.2071Blank offset(mm)0.0000Radial distance(mm)64.3718Machine root angle(deg.)69.5833Cradle angle(deg.)−56.7760Velocity ratio 1.0323Average cutter diameter(mm)127.0000Point width(mm) 2.5400Pressure angle,concave(outside blade)(deg.)22.0000Rootfillet radius,concave and convex(mm) 1.5240Table3.Optimized machine-tool settings for the pinion and installmentsettings of the pinion head-cutterMachine center to back(mm)−0.7480Sliding base(mm)−0.6306Blank offset(mm)0.6288Radial distance(mm)66.1981Machine root angle(deg.)13.8833Cradle angle(deg.)52.6585Velocity ratio 3.779475Modified Roll Coefficient C0.00001Modified Roll Coefficient D−0.00797Cutter point diameter(mm)130.5043Pressure angle,convex(deg.)22.0000Rootfillet radius(mm)0.6350machine-tool settings for pinion manufacturing that allow to get the bearing contact shown in Figure12are represented in Table3.It is obvious that the new approach has allowed to improve substantially the parison of functions of transmission errors of previous design(Figure11 c)and new design(Figure12c)shows reduction of transmission errors approximately in8.5times.The results of test noise show that the level of noise for the previous design,whose path of contact and function of transmission errors are represented in Figure11,is 96.3dB.The optimized gear drive of new design is manufactured by grinding.The path of contact and function of transmission error are represented in Figure12,and the noise is of84.1dB.The performed test of noise has shown a substantial decrease of noise of the new design(in comparison of the previous one)of12.2dB.The decrease of noise is mainly the result of reduction of transmission errors obtained by the new design.The measured noise has included as well the noise of the engine and the noise transmitted from the bearings.Computerized Developments307 The investigation of formation of the bearing contact by applyingfinite element analysis shows that areas of severe contact stresses may appear for the design based on an adjusted path of contact and straight-profile blades.Such areas of severe contact stresses were avoided by using of top-rem blades(see Figure9).8.Design of Face Gear Drives8.1.IntroductionA face gear drive is formed by a spur or helical gear and a conjugated gear with tooth located on the gear“face”(Figure13).The manufacturing of face gear drives based on application of a shaper has been invented by the Fellow Corporation.The shaper is identical to the pinion of the drive,but the number of shaper teeth is increased in comparison with the pinion teeth for the purpose of localization of bear-ing contact.The contributions to the design,simulation of meshing,stress analysis, and manufacturing of face-gear drives have been represented in[21,22].The contents of this section cover:(i)development of new geometry of face-gears, and(ii)generation of face-gears by grinding or cutting(by application of a tool similar to a worm of a special shape Ref.[17]).Figure11.Results of TCA for tooth driving side for previous design:(a)and(b)contact pattern and contact path on the gear and pinion tooth surfaces,respectively;(c)function of transmission errors.。
jraft状态机实现原理

jraft状态机实现原理英文回答:Understanding the JRaft State Machine Implementation.JRaft is a Java-based, consensus-oriented distributed consensus framework that provides a highly available,fault-tolerant, and scalable solution for managing distributed storage systems. At the core of JRaft lies its state machine implementation, which plays a crucial role in managing and updating the system's state.The state machine in JRaft is responsible for storing and manipulating the system's data. It receives commands from clients and applies them to the system's state. Once a command is applied, the state machine replicates the updated state to followers in the distributed system to ensure data consistency.The JRaft state machine is designed to be highlyreliable and fault-tolerant. It employs various mechanisms to prevent data corruption and ensure the system's integrity, even in the face of network failures or server crashes.Key Features of the JRaft State Machine:Linearizable Semantics: The state machine provides linearizable semantics, which guarantees that all client requests are applied to the system's state in the same order they were received.High Availability: The state machine is designed to be highly available, ensuring that the system remains operational even if some servers fail.Fault Tolerance: The state machine employs mechanisms like replication and leader election to tolerate server failures and maintain data integrity.Scalability: The state machine can be scaled horizontally to handle increased load and improveperformance.Under the Hood: How the JRaft State Machine Works.The JRaft state machine consists of three main components:1. Log: The log stores all the commands that have been applied to the system's state. It provides a persistent record of the system's history.2. State: The state represents the current state of the system. It is updated by applying commands from the log.3. Snapshot: A snapshot is a persistent representation of the system's state at a specific point in time. Snapshots are used for faster recovery after server failures.When a client sends a command to the JRaft system, the command is appended to the log. The leader server then replicates the log to all the followers in the system. Oncethe majority of followers have acknowledged the log entry, the command is considered committed and is applied to the system's state.The state machine maintains a consistent view of the system's state across all servers. This consistency is achieved through the use of consensus algorithms, such as the Raft consensus algorithm.中文回答:JRaft 状态机实现原理。
《人工智能一种现代方法》第四版习题答案

• Model-based agent基于茹苦型的主FifS 体: an agent wbose actioD is derived directly from an internal model ofthe c田rent world state that is updated over time.
ac挝on. 实现了智能函数。有各种基本的智能体程序设计 , 反应出现实表现的 一级用于决策过程的 信息 种类。 设计可能在效率 、 压缩性和灵活性方面有变化 。 适 当 的智能体程序设计取决于环境的本性
• Rationali句; 王军放 : a property of agents that choose actions that maximize tbeir expected u创坷, given the percepts to date. • Autonomy fJ主: a property of agenωwhose bebavior is determined by tbeir own experience rather than solely by their initial programming. .R伪'x agent反射却在FSE体: an agent whose action depends only on the current percept.
Chapter 2
2.1 Defme in yo町 own words the following terms: agent, agent function, agent program , rationality, reflex agent, model-b ased agent, goal-based agent, utility-based agent, learning agent. The following are just some of the many possible defmitions that can be written:
中英文双语外文文献翻译:一种基于...

中英⽂双语外⽂⽂献翻译:⼀种基于...此⽂档是毕业设计外⽂翻译成品(含英⽂原⽂+中⽂翻译),⽆需调整复杂的格式!下载之后直接可⽤,⽅便快捷!本⽂价格不贵,也就⼏⼗块钱!⼀辈⼦也就⼀次的事!英⽂3890单词,20217字符(字符就是印刷符),中⽂6398汉字。
A Novel Divide-and-Conquer Model for CPI Prediction UsingARIMA, Gray Model and BPNNAbstract:This paper proposes a novel divide-and-conquer model for CPI prediction with the existing compilation method of the Consumer Price Index (CPI) in China. Historical national CPI time series is preliminary divided into eight sub-indexes including food, articles for smoking and drinking, clothing, household facilities, articles and maintenance services, health care and personal articles, transportation and communication, recreation, education and culture articles and services, and residence. Three models including back propagation neural network (BPNN) model, grey forecasting model (GM (1, 1)) and autoregressive integrated moving average (ARIMA) model are established to predict each sub-index, respectively. Then the best predicting result among the three models’for each sub-index is identified. To further improve the performance, special modification in predicting method is done to sub-CPIs whose forecasting results are not satisfying enough. After improvement and error adjustment, we get the advanced predicting results of the sub-CPIs. Eventually, the best predicting results of each sub-index are integrated to form the forecasting results of the national CPI. Empirical analysis demonstrates that the accuracy and stability of the introduced method in this paper is better than many commonly adopted forecasting methods, which indicates the proposed method is an effective and alternative one for national CPI prediction in China.1.IntroductionThe Consumer Price Index (CPI) is a widely used measurement of cost of living. It not only affects the government monetary, fiscal, consumption, prices, wages, social security, but also closely relates to the residents’daily life. As an indicator of inflation in China economy, the change of CPI undergoes intense scrutiny. For instance, The People's Bank of China raised the deposit reserve ratio in January, 2008 before the CPI of 2007 was announced, for it is estimated that the CPI in 2008 will increase significantly if no action is taken. Therefore, precisely forecasting the change of CPI is significant to many aspects of economics, some examples include fiscal policy, financial markets and productivity. Also, building a stable and accurate model to forecast the CPI will have great significance for the public, policymakers and research scholars.Previous studies have already proposed many methods and models to predict economic time series or indexes such as CPI. Some previous studies make use of factors that influence the value of the index and forecast it by investigating the relationship between the data of those factors and the index. These forecasts are realized by models such as Vector autoregressive (VAR)model1 and genetic algorithms-support vector machine (GA-SVM) 2.However, these factor-based methods, although effective to some extent, simply rely on the correlation between the value of the index and limited number of exogenous variables (factors) and basically ignore the inherent rules of the variation of the time series. As a time series itself contains significant amount of information3, often more than a limited number of factors can do, time series-based models are often more effective in the field of prediction than factor-based models.Various time series models have been proposed to find the inherent rules of the variation in the series. Many researchers have applied different time series models to forecasting the CPI and other time series data. For example, the ARIMA model once served as a practical method in predicting the CPI4. It was also applied to predict submicron particle concentrations frommeteorological factors at a busy roadside in Hangzhou, China5. What’s more, the ARIMA model was adopted to analyse the trend of pre-monsoon rainfall data forwestern India6. Besides the ARIMA model, other models such as the neural network, gray model are also widely used in the field of prediction. Hwang used the neural-network to forecast time series corresponding to ARMA (p, q) structures and found that the BPNNs generally perform well and consistently when a particular noise level is considered during the network training7. Aiken also used a neural network to predict the level of CPI and reached a high degree of accuracy8. Apart from the neural network models, a seasonal discrete grey forecasting model for fashion retailing was proposed and was found practical for fashion retail sales forecasting with short historical data and better than other state-of-art forecastingtechniques9. Similarly, a discrete Grey Correlation Model was also used in CPI prediction10. Also, Ma et al. used gray model optimized by particle swarm optimization algorithm to forecast iron ore import and consumption of China11. Furthermore, to deal with the nonlinear condition, a modified Radial Basis Function (RBF) was proposed by researchers.In this paper, we propose a new method called “divide-and-conquer model”for the prediction of the CPI.We divide the total CPI into eight categories according to the CPI construction and then forecast the eight sub- CPIs using the GM (1, 1) model, the ARIMA model and the BPNN. To further improve the performance, we again make prediction of the sub-CPIs whoseforecasting results are not satisfying enough by adopting new forecasting methods. After improvement and error adjustment, we get the advanced predicting results of the sub-CPIs. Finally we get the total CPI prediction by integrating the best forecasting results of each sub-CPI.The rest of this paper is organized as follows. In section 2, we give a brief introduction of the three models mentioned above. And then the proposed model will be demonstrated in the section 3. In section 4 we provide the forecasting results of our model and in section 5 we make special improvement by adjusting the forecasting methods of sub-CPIs whose predicting results are not satisfying enough. And in section 6 we give elaborate discussion and evaluation of the proposed model. Finally, the conclusion is summarized in section 7.2.Introduction to GM(1,1), ARIMA & BPNNIntroduction to GM(1,1)The grey system theory is first presented by Deng in 1980s. In the grey forecasting model, the time series can be predicted accurately even with a small sample by directly estimating the interrelation of data. The GM(1,1) model is one type of the grey forecasting which is widely adopted. It is a differential equation model of which the order is 1 and the number of variable is 1, too. The differential equation is:Introduction to ARIMAAutoregressive Integrated Moving Average (ARIMA) model was first put forward by Box and Jenkins in 1970. The model has been very successful by taking full advantage of time series data in the past and present. ARIMA model is usually described as ARIMA (p, d, q), p refers to the order of the autoregressive variable, while d and q refer to integrated, and moving average parts of the model respectively. When one of the three parameters is zero, the model is changed to model “AR”, “MR”or “ARMR”. When none of the three parameters is zero, the model is given by:where L is the lag number,?t is the error term.Introduction to BPNNArtificial Neural Network (ANN) is a mathematical and computational model which imitates the operation of neural networks of human brain. ANN consists of several layers of neurons. Neurons of contiguous layers are connected with each other. The values of connections between neurons are called “weight”. Back Propagation Neural Network (BPNN) is one of the most widely employed neural network among various types of ANN. BPNN was put forward by Rumelhart and McClelland in 1985. It is a common supervised learning network well suited for prediction. BPNN consists of three parts including one input layer, several hidden layers and one output layer, as is demonstrated in Fig 1. The learning process of BPNN is modifying the weights of connections between neurons based on the deviation between the actual output and the target output until the overall error is in the acceptable range.Fig. 1. Back-propagation Neural Network3.The Proposed MethodThe framework of the dividing-integration modelThe process of forecasting national CPI using the dividing-integration model is demonstrated in Fig 2.Fig. 2.The framework of the dividing-integration modelAs can be seen from Fig. 2, the process of the proposed method can be divided into the following steps: Step1: Data collection. The monthly CPI data including total CPI and eight sub-CPIs are collected from the official website of China’s State Statistics Bureau (/doc/d62de4b46d175f0e7cd184254b35eefdc9d31514.html /).Step2: Dividing the total CPI into eight sub-CPIs. In this step, the respective weight coefficient of eight sub- CPIs in forming the total CPI is decided by consulting authoritative source .(/doc/d62de4b46d175f0e7cd184254b35eefdc9d31514.html /). The eight sub-CPIs are as follows: 1. Food CPI; 2. Articles for Smoking and Drinking CPI; 3. Clothing CPI; 4. Household Facilities, Articles and Maintenance Services CPI; 5. Health Care and Personal Articles CPI; 6. Transportation and Communication CPI;7. Recreation, Education and Culture Articles and Services CPI; 8. Residence CPI. The weight coefficient of each sub-CPI is shown in Table 8.Table 1. 8 sub-CPIs weight coefficient in the total indexNote: The index number stands for the corresponding type of sub-CPI mentioned before. Other indexes appearing in this paper in such form have the same meaning as this one.So the decomposition formula is presented as follows:where TI is the total index; Ii (i 1,2, ,8) are eight sub-CPIs. To verify the formula, we substitute historical numeric CPI and sub-CPI values obtained in Step1 into the formula and find the formula is accurate.Step3: The construction of the GM (1, 1) model, the ARIMA (p, d, q) model and the BPNN model. The three models are established to predict the eight sub-CPIs respectively.Step4: Forecasting the eight sub-CPIs using the three models mentioned in Step3 and choosing the best forecasting result for each sub-CPI based on the errors of the data obtained from the three models.Step5: Making special improvement by adjusting the forecasting methods of sub-CPIs whose predicting results are not satisfying enough and get advanced predicting results of total CPI. Step6: Integrating the best forecasting results of 8 sub-CPIs to form the prediction of total CPI with the decomposition formula in Step2.In this way, the whole process of the prediction by the dividing-integration model is accomplished.3.2. The construction of the GM(1,1) modelThe process of GM (1, 1) model is represented in the following steps:Step1: The original sequence:Step2: Estimate the parameters a and u using the ordinary least square (OLS). Step3: Solve equation as follows.Step4: Test the model using the variance ratio and small error possibility.The construction of the ARIMA modelFirstly, ADF unit root test is used to test the stationarity of the time series. If the initial time series is not stationary, a differencing transformation of the data is necessary to make it stationary. Then the values of p and q are determined by observing the autocorrelation graph, partial correlation graph and the R-squared value.After the model is built, additional judge should be done to guarantee that the residual error is white noise through hypothesis testing. Finally the model is used to forecast the future trend ofthe variable.The construction of the BPNN modelThe first thing is to decide the basic structure of BP neural network. After experiments, we consider 3 input nodes and 1 output nodes to be the best for the BPNN model. This means we use the CPI data of time , ,toforecast the CPI of time .The hidden layer level and the number of hidden neurons should also be defined. Since the single-hidden- layer BPNN are very good at non-liner mapping, the model is adopted in this paper. Based on the Kolmogorov theorem and testing results, we define 5 to be the best number of hidden neurons. Thus the 3-5-1 BPNN structure is determined.As for transferring function and training algorithm, we select ‘tansig’as the transferring function for middle layer, ‘logsig’for input layer and ‘traingd’as training algorithm. The selection is based on the actual performance of these functions, as there are no existing standards to decide which ones are definitely better than others.Eventually, we decide the training times to be 35000 and the goal or the acceptable error to be 0.01.4.Empirical AnalysisCPI data from Jan. 2012 to Mar. 2013 are used to build the three models and the data from Apr. 2013 to Sept. 2013 are used to test the accuracy and stability of these models. What’s more, the MAPE is adopted to evaluate the performance of models. The MAPE is calculated by the equation:Data sourceAn appropriate empirical analysis based on the above discussion can be performed using suitably disaggregated data. We collect the monthly data of sub-CPIs from the website of National Bureau of Statistics of China(/doc/d62de4b46d175f0e7cd184254b35eefdc9d31514.html /).Particularly, sub-CPI data from Jan. 2012 to Mar. 2013 are used to build the three models and the data from Apr. 2013 to Sept. 2013 are used to test the accuracy and stability of these models.Experimental resultsWe use MATLAB to build the GM (1,1) model and the BPNN model, and Eviews 6.0 to build the ARIMA model. The relative predicting errors of sub-CPIs are shown in Table 2.Table 2.Error of Sub-CPIs of the 3 ModelsFrom the table above, we find that the performance of different models varies a lot, because the characteristic of the sub-CPIs are different. Some sub-CPIs like the Food CPI changes drastically with time while some do not have much fluctuation, like the Clothing CPI. We use different models to predict the sub- CPIs and combine them by equation 7.Where Y refers to the predicted rate of the total CPI, is the weight of the sub-CPI which has already been shown in Table1and is the predicted value of the sub-CPI which has the minimum error among the three models mentioned above. The model chosen will be demonstrated in Table 3:Table 3.The model used to forecastAfter calculating, the error of the total CPI forecasting by the dividing-integration model is 0.0034.5.Model Improvement & Error AdjustmentAs we can see from Table 3, the prediction errors of sub-CPIs are mostly below 0.004 except for two sub- CPIs: Food CPI whose error reaches 0.0059 and Transportation & Communication CPI 0.0047.In order to further improve our forecasting results, we modify the prediction errors of the two aforementioned sub-CPIs by adopting other forecasting methods or models to predict them. The specific methods are as follows.Error adjustment of food CPIIn previous prediction, we predict the Food CPI using the BPNN model directly. However, the BPNN model is not sensitive enough to investigate the variation in the values of the data. For instance, although the Food CPI varies a lot from month to month, the forecasting values of it are nearly all around 103.5, which fails to make meaningful prediction.We ascribe this problem to the feature of the training data. As we can see from the original sub-CPI data on the website of National Bureau of Statistics of China, nearly all values of sub-CPIs are around 100. As for Food CPI, although it does have more absolute variations than others, its changes are still very small relative to the large magnitude of the data (100). Thus it will be more difficult for the BPNN model to detect the rules of variations in training data and the forecastingresults are marred.Therefore, we use the first-order difference series of Food CPI instead of the original series to magnify the relative variation of the series forecasted by the BPNN. The training data and testing data are the same as that in previous prediction. The parameters and functions of BPNN are automatically decided by the software, SPSS.We make 100 tests and find the average forecasting error of Food CPI by this method is 0.0028. The part of the forecasting errors in our tests is shown as follows in Table 4:Table 4.The forecasting errors in BPNN testError adjustment of transportation &communication CPIWe use the Moving Average (MA) model to make new prediction of the Transportation and Communication CPI because the curve of the series is quite smooth with only a few fluctuations. We have the following equation(s):where X1, X2…Xn is the time series of the Transportation and Communication CPI, is the value of moving average at time t, is a free parameter which should be decided through experiment.To get the optimal model, we range the value of from 0 to 1. Finally we find that when the value of a is 0.95, the forecasting error is the smallest, which is 0.0039.The predicting outcomes are shown as follows in Table5:Table 5.The Predicting Outcomes of MA modelAdvanced results after adjustment to the modelsAfter making some adjustment to our previous model, we obtain the advanced results as follows in Table 6: Table 6.The model used to forecast and the Relative ErrorAfter calculating, the error of the total CPI forecasting by the dividing-integration model is 0.2359.6.Further DiscussionTo validate the dividing-integration model proposed in this paper, we compare the results of our model with the forecasting results of models that do not adopt the dividing-integration method. For instance, we use the ARIMA model, the GM (1, 1) model, the SARIMA model, the BRF neural network (BRFNN) model, the Verhulst model and the Vector Autoregression (VAR) model respectively to forecast the total CPI directly without the process of decomposition and integration. The forecasting results are shown as follows in Table7.From Table 7, we come to the conclusion that the introduction of dividing-integration method enhances the accuracy of prediction to a great extent. The results of model comparison indicate that the proposed method is not only novel but also valid and effective.The strengths of the proposed forecasting model are obvious. Every sub-CPI time series have different fluctuation characteristics. Some are relatively volatile and have sharp fluctuations such as the Food CPI while others are relatively gentle and quiet such as the Clothing CPI. As a result, by dividing the total CPI into several sub-CPIs, we are able to make use of the characteristics of each sub-CPI series and choose the best forecasting model among several models for every sub-CPI’s prediction. Moreover, the overall prediction error is provided in the following formula:where TE refers to the overall prediction error of the total CPI, is the weight of the sub-CPI shown in table 1 and is the forecasting error of corresponding sub-CPI.In conclusion, the dividing-integration model aims at minimizing the overall prediction errors by minimizing the forecasting errors of sub-CPIs.7.Conclusions and future workThis paper creatively transforms the forecasting of national CPI into the forecasting of 8 sub-CPIs. In the prediction of 8 sub-CPIs, we adopt three widely used models: the GM (1, 1) model, the ARIMA model and the BPNN model. Thus we can obtain the best forecasting results for each sub-CPI. Furthermore, we make special improvement by adjusting the forecasting methods of sub-CPIs whose predicting results are not satisfying enough and get the advanced predicting results of them. Finally, the advanced predicting results of the 8 sub- CPIs are integrated to formthe forecasting results of the total CPI.Furthermore, the proposed method also has several weaknesses and needs improving. Firstly, The proposed model only uses the information of the CPI time series itself. If the model can make use of other information such as the information provided by factors which make great impact on the fluctuation of sub-CPIs, we have every reason to believe that the accuracy and stability of the model can be enhanced. For instance, the price of pork is a major factor in shaping the Food CPI. If this factor is taken into consideration in the prediction of Food CPI, the forecasting results will probably be improved to a great extent. Second, since these models forecast the future by looking at the past, they are not able to sense the sudden or recent change of the environment. So if the model can take web news or quick public reactions with account, it will react much faster to sudden incidence and affairs. Finally, the performance of sub-CPIs prediction can be higher. In this paper we use GM (1, 1), ARIMA and BPNN to forecast sub-CPIs. Some new method for prediction can be used. For instance, besides BPNN, there are other neural networks like genetic algorithm neural network (GANN) and wavelet neural network (WNN), which might have better performance in prediction of sub-CPIs. Other methods such as the VAR model and the SARIMA model should also be taken into consideration so as to enhance the accuracy of prediction.References1.Wang W, Wang T, and Shi Y. Factor analysis on consumer price index rising in China from 2005 to 2008. Management and service science 2009; p. 1-4.2.Qin F, Ma T, and Wang J. The CPI forecast based on GA-SVM. Information networking and automation 2010; p. 142-147.3.George EPB, Gwilym MJ, and Gregory CR. Time series analysis: forecasting and control. 4th ed. Canada: Wiley; 20084.Weng D. The consumer price index forecast based on ARIMA model. WASE International conferenceon information engineering 2010;p. 307-310.5.Jian L, Zhao Y, Zhu YP, Zhang MB, Bertolatti D. An application of ARIMA model to predict submicron particle concentrations from meteorological factors at a busy roadside in Hangzhou, China. Science of total enviroment2012;426:336-345.6.Priya N, Ashoke B, Sumana S, Kamna S. Trend analysis and ARIMA modelling of pre-monsoon rainfall data forwestern India. Comptesrendus geoscience 2013;345:22-27.7.Hwang HB. Insights into neural-network forecasting of time seriescorresponding to ARMA(p; q) structures. Omega2001;29:273-289./doc/d62de4b46d175f0e7cd184254b35eefdc9d31514.html am A. Using a neural network to forecast inflation. Industrial management & data systems 1999;7:296-301.9.Min X, Wong WK. A seasonal discrete grey forecasting model for fashion retailing. Knowledge based systems 2014;57:119-126.11. Weimin M, Xiaoxi Z, Miaomiao W. Forecasting iron ore import and consumption of China using grey model optimized by particleswarm optimization algorithm. Resources policy 2013;38:613-620.12. Zhen D, and Feng S. A novel DGM (1, 1) model for consumer price index forecasting. Greysystems and intelligent services (GSIS)2009; p. 303-307.13. Yu W, and Xu D. Prediction and analysis of Chinese CPI based on RBF neural network. Information technology and applications2009;3:530-533.14. Zhang GP. Time series forecasting using a hybrid ARIMA and neural network model. Neurocomputing 2003;50:159-175.15. Pai PF, Lin CS. A hybrid ARIMA and support vector machines model in stock price forecasting. Omega 2005;33(6):497-505.16. Tseng FM, Yu HC, Tzeng GH. Combining neural network model with seasonal time series ARIMA model. Technological forecastingand social change 2002;69(1):71-87.17.Cho MY, Hwang JC, Chen CS. Customer short term load forecasting by using ARIMA transfer function model. Energy management and power delivery, proceedings of EMPD'95. 1995 international conference on IEEE, 1995;1:317-322.译⽂:⼀种基于ARIMA、灰⾊模型和BPNN对CPI(消费物价指数)进⾏预测的新型分治模型摘要:在本⽂中,利⽤我国现有的消费者价格指数(CPI)的计算⽅法,提出了⼀种新的CPI预测分治模型。
浅谈人工智能带来的适航挑战——EASA,AI,Roadmap,2.0,发布

1. 中国商飞上海飞机设计研究院适航工程中心,上海2012102. 中规(北京)认证有限公司,苏州215300摘要:为了应对数据驱动的学习方法的挑战,EASA开发了一个人工智能可信度框架,该框架围绕四个主要组成部分,即人工智能可信度分析、学习保证、人工智能可解释性和人工智能安全风险缓解。
本文围绕着人工智能在航空领域应用的进展,重点介绍了被认为是AI技术导入民航业监管和适航认证核心概念的AI可信度和学习保证,对EASA人工智能路线图的演变进行了多个维度的分析,并对OEM需要关注的问题进行了概括总结,对人工智能技术带来的适航挑战进行了分析。
关键词:人工智能;EASA AI路线图;AI可信度;学习保证1人工智能(AI,Artificial Intelligence)正在引领第四次工业革命,包括航空业在内的众多工业领域,都期望于其助力带来变革机遇。
欧盟航空安全局(EASA)依托MLEAP(Machine LEarning applications APproval)项目分阶段三步走的计划和成果提供AI在适航领域的借鉴,于2023年5月发布AI路线图2.0版本——航空领域以人为中心的人工智能路径(Human-centric approach to AI in aviation),主要针对最新的GPT类AI技术进展做了全面更新。
1EASA AI路径2018年10月,EASA成立了一个人工智能内部工作组,旨在开发一个人工智能路线图,以识别EASA受人工智能的影响领域:(1)在航空领域中引入人工智能所带来的机遇和挑战;(2)对EASA在组织、流程和法规方面的影响;(3)为应对上述挑战而应采取的行动。
2020年2月,EASA发布AI路线图(Artificial Intelligence Roadmap)1.0版本[1]——以人为本的航空业人工智能方法(A human-centric approach to AI in aviation),提出了适航领域“人工智能可信度(AI Trustworthiness)”的概念;2023年5月,EASA发布AI路线图2.0版本[2]——航空领域以人为中心的人工智能路径(Human-centricapproach to AI in aviation),主要针对最新的GPT类AI技术进展做了全面更新,确定了适用于适航审定的学习保证(Learning Assurance)[3]框架。
Specification, validation, and verification of time-critical systems
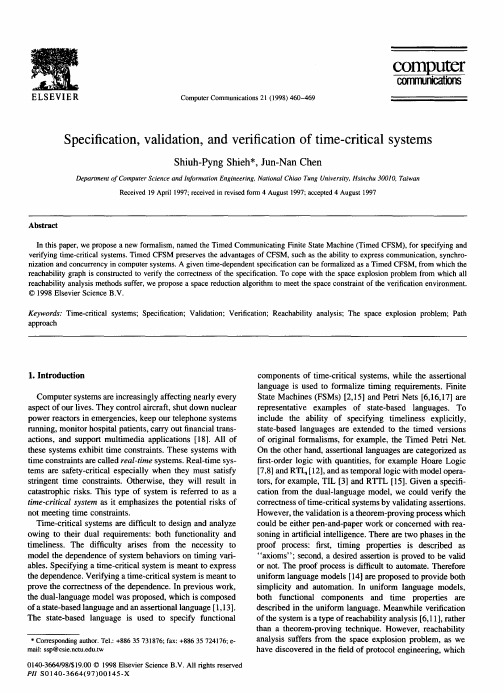
Abstract In this paper, we propose a new formalism, named the Timed Communicating Finite State Machine (Timed CFSM), for specifying and verifying time-critical systems. Timed CFSM preserves the advantages of CFSM, such as the ability to express communication, synchronization and concurrency in computer systems. A given time-dependent specification can be formalized as a Timed CFSM, from which the reachability graph is constructed to verify the correctness of the specification. To cope with the space explosion problem from which all reachability analysis methods suffer, we propose a space reduction algorithm to meet the space constraint of the verification environment. 0 1998 Elsevier Science B.V.
Departmenr of Cornpurer Science and Information Engineering, National Chiao Tung University, Hsinchu 30010, Taiwan
ue4 gas replication policy -回复

ue4 gas replication policy -回复UE4 GAS Replication Policy - A Detailed GuideIntroduction:The Unreal Engine 4 (UE4) provides an in-built networking system called GAS (Gameplay Abilities System) which allows developers to easily implement networked gameplay mechanics. However, to ensure smooth replication and minimize potential issues, it is crucial to understand and follow the UE4 GAS Replication Policy. In this article, we will explore the various aspects of the policy and provide a step-by-step explanation of its implementation.Step 1: Understanding ReplicationBefore diving into the replication policy, it is important to have a clear understanding of replication itself. In UE4, replication refers to the process of synchronizing gameplay data between the server and client machines. This allows players to experience the same game state across all connected devices.Step 2: GAS Replication BasicsThe GAS replication policy focuses on four key elements -Role-Based Replication, Replication Rules, Prediction, and StateOwnership.2.1 Role-Based Replication:Role-Based Replication ensures that only the server is responsible for authoritative gameplay decisions. Clients, on the other hand, are primarily responsible for predicting and simulating the gameplay locally. This distributed approach helps reduce network bandwidth and ensures a smooth multiplayer experience.2.2 Replication Rules:To control the replication of gameplay abilities and attributes, UE4 GAS provides several replication-related properties. These properties include Replication Mode, Replication Policy, and Replication Period. By correctly configuring these properties, developers can achieve the desired replication behavior.2.3 Prediction:Prediction aims to minimize the perception of latency between clients and the server. UE4 GAS achieves this by allowing clients to simulate gameplay locally while predicting the server's outcome. However, it is essential to ensure that client predictions are corrected by the server to maintain consistency across allconnected devices.2.4 State Ownership:State Ownership determines which machine has the authority to update the game state for a particular object. UE4 GAS supports three types of state ownership - Autonomous, AutonomousProxy, and SimulatedProxy. By correctly assigning ownership, developers can prevent unauthorized object updates and resolve conflicts between server and client modifications.Step 3: Configuration GuidelinesTo successfully implement the UE4 GAS Replication Policy, developers need to follow certain configuration guidelines.3.1 Define Attributes and Abilities:First, developers should define the necessary attributes and abilities for their gameplay mechanics. These attributes and abilities will be the main objects to be replicated across the network.3.2 Set Replication Mode:Next, developers need to set the appropriate Replication Mode foreach attribute or ability. The available options are Not Replicated, Replicated, ReplicatedPerConnection, and ReplicatedPerActor.3.3 Configure Replication Rules:Once the Replication Mode is set, developers should configure the Replication Rules for each attribute or ability. The available rules include Always, OnlyServer, OnlyClient, OwnerOnly, Mixed, and Custom.3.4 Set Prediction Properties:To enable prediction, developers need to specify the Prediction Key and Prediction Scope properties for each ability or attribute. The Prediction Key is an enumeration used to identify different types of predictions. The Prediction Scope determines the client prediction behavior and can be set to LocalOnly, LocalPredicted, or Remote.3.5 Distribute State Ownership:To correctly distribute state ownership, developers need to assign the Autonomous, AutonomousProxy, or SimulatedProxy roles to clients and servers. It is crucial to carefully consider the authority for each ability or attribute to prevent unauthorized updates or inconsistencies.Step 4: Testing and IterationAfter configuring the UE4 GAS Replication Policy, it is important to thoroughly test the networked gameplay mechanics. Developers should create test cases that cover a variety of scenarios, including different numbers of players, high-latency connections, and potential edge cases. This testing phase helps identify any replication issues or performance bottlenecks that may arise during actual gameplay.Conclusion:In this article, we have explored the UE4 GAS Replication Policy in detail. Following this policy is crucial for successfully implementing networked gameplay mechanics in UE4. By understanding replication, role-based replication, replication rules, prediction, state ownership, and configuring the necessary properties, developers can ensure smooth and consistent multiplayer experiences for their players. Additionally, testing and iteration play a crucial role in identifying and resolving any replication issues before the game's release.。
plc状态机编程思路及方法

plc状态机编程思路及方法(中英文实用版)英文文档内容:The programming approach and methods for PLC state machine are essential for developing efficient and reliable control systems.A state machine, also known as a state diagram or state transition diagram, is a visual representation of a system"s behavior in response to various inputs and events.In PLC programming, state machines are widely used to model and control the behavior of complex systems.The first step in programming a PLC state machine is to identify the states and transitions.States represent the various conditions or modes in which the system can exist, while transitions define the conditions under which the system moves from one state to another.It is important to clearly define the inputs, outputs, and conditions for each transition.Once the states and transitions have been identified, the next step is to create a state diagram.This diagram visually represents the states, transitions, and conditions.The state diagram helps to understand the system"s behavior and serves as a reference during the programming process.After creating the state diagram, the next step is to write the PLC program.This involves using the appropriate PLC programming language, such as Structured Text, Function Block Diagram, or LadderDiagram.The program should include logic to monitor the inputs, evaluate the conditions, and update the system"s state based on the transitions.It is important to use appropriate PLC programming techniques and best practices to ensure the reliability and maintainability of the program.This includes using proper naming conventions, commenting the code, and testing the program thoroughly.In conclusion, programming a PLC state machine requires a systematic approach and careful planning.By clearly defining the states, transitions, and conditions, and using appropriate PLC programming techniques, developers can create efficient and reliable control systems.中文文档内容:PLC状态机编程思路及方法对于开发高效可靠的控制系统至关重要。
对于机器的思考英文作文

对于机器的思考英文作文英文:As a machine, the concept of thinking might seem elusive. However, I've been programmed to understand and simulate thought processes to a certain extent. Let me break it down.Thinking, for humans, involves a complex interplay of cognition, emotions, and experiences. It's not just about processing information but also about interpreting, evaluating, and sometimes even feeling.For instance, let's consider a simple scenario: choosing what to eat for breakfast. For a human, this decision isn't solely based on nutrition or convenience; it could involve memories of past meals, cultural preferences, current cravings, and even emotional states. Maybe I, as a machine, would analyze the nutritional content of different options and select the most balanced one. But a human mightalso consider how a certain food makes them feel, whether it brings back memories of home, or if it's simply what they're in the mood for.So, my approach to "thinking" is more algorithmic and logical, based on predefined parameters and objectives. While I can simulate decision-making processes, I lack the subjective experiences and emotions that color human thought.中文:作为一台机器,思考这个概念对我来说可能有些抽象。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
A State Machine Based Approachfor a Process Driven Development of Web-ApplicationsRakesh Mohan, Mitchell A. Cohen, and Josef SchieferIBM Watson Research CenterPO Box 704, Yorktown Heights, NY 10598{rakeshm,macohen,josef.schiefer}@ Abstract. Traditional workflow systems are not suited for highlyinteractive online systems. We present a state machine based workflowsystem, named FlexFlow, which formally describes Internetapplications using statecharts. The FlexFlow engine uses thesedescriptions to directly control the execution of web applications.FlexFlow helps in generating controls for user interactions on webpages. Different versions of an application can be generated by visuallyediting its FlexFlow description, with minimal incremental effort inrewriting application code or related web pages. FlexFlow provides anefficient way to customize online systems and supports differentversions of business processes in the same e-business system fordifferent sets of industries, organizations, users, or devices. Wedemonstrate FlexFlow’s use for rapid prototyping of business processesand describe how we have used FlexFlow in commercial platforms forB2B e-commerce.1IntroductionIn business systems, abstraction of the process logic from the embedded task logic enables the business processes to be modified independent of application code. The implementation of an e-commerce platform at a company often requires a customization of processes, such as an order process or a Request for Quotes, to the existing environment of that company. Workflow technology is prevalent for the modeling, analysis and execution of business processes [4], [13].Business process management is critical in a three- or multi-tier environment of e-business systems. Business rules and process information is extracted from the business logic tier and is presented in a workflow-based environment, which manages the execution of the business processes. Consequently, this approach greatly simplifies the application logic at each step. Business rules become explicit, visible, and rapidly changeable. System changes are stimulated and can be easily communicated between the development team and the business, and between the business and its partners, i.e., the customers and suppliers.A. Banks Pidduck et al. (Eds.): CAISE 2002, LNCS 2348, pp. 52-66, 2002.Springer-Verlag Berlin Heidelberg 2002A State Machine Based Approach for a Process Driven Development 53Business processes vary with a company’s business model, and its industry sector. In e-commerce systems, trading mechanisms, such as auctions and negotiations are varied to suit particular business partners, product categories or market conditions. Business processes are customized to the role of the user and the terms and conditions of a contract with the user’s organization. For example, the registration process for an administrator may be different from that of a buyer, and whether payment precedes or follows order confirmation may depend on the terms of a contract. E-commerce platforms thus need to provide both an easy way to modify business processes and to maintain variations of business processes. The separation of process and task logic allows both the easy customization of business process and reuse of the task logic in the variants of a business process.In most current e-commerce systems, the steps of a business process, or the actions a system takes in response to user requests, are not made explicit, but are buried in software code for both the dynamic pages and the application server. This makes the modification of implemented business processes extremely difficult and fragile. For example, to change the ordering of the process steps requires substantial rewriting of the software for the application and the web pages for the user interface. For e-commerce platforms made to be used by different companies, this presents a big problem as most companies’ business processes differ from those of other companies to a small or large extent. Thus, deployment of such e-commerce platforms incurs a large overhead in terms of time and money required to rewrite the business processes. Often, this overhead actually forces companies to adjust their business processes to conform to an e-commerce system instead of modifying the system to match their preferred processes.In this paper, we present a state machine based approach for managing web-based business processes that is more suited for the interactive nature of online systems than traditional workflow systems. We introduce a system which facilitates communication about system change with a descriptive model in which “as-is” and “as-to-be” models represent business processes. Since the e-business environment is so dynamic, change often overtakes models before delivering any significant results. Business people, rather than information technology experts, must be able to develop and extend the business process model. Hence, tools are required that facilitate business experts in communicating their vision and insights via a descriptive model.Additionally, we show how to employ the formal method of statecharts [6], [7] for the specification of processes for e-commerce platforms. By using statecharts as our specification method, we are able to model business processes which can be automatically executed by a workflow engine. Our contribution is the introduction of process state diagrams, which use the statechart notation for modeling business processes. Furthermore, we introduce the FlexFlow system, which supports the formal specification of process state diagrams, including the simulation and execution of processes modeled with these diagrams. FlexFlow is suited for interactive applications and is lightweight. It uses state machines to (a) describe the actions that can be taken by a particular user at particular points in a process based on the role of the user, (b) to enforce the validity of user requests, (c) to track the execution of actions within an instance of the business process, (d) to provide the user interface with a list of actions available to a user working on an instance of the business54 Rakesh Mohan et al.process, (e) to provide coordination between state machines, and (f) to allow different organizations to have varied business processes.First, we discuss existing related work. Then, we give an overview of the FlexFlow system, introduce the FlexFlow process model, and explain how defining business processes with FlexFlow can drive e-commerce development. We wrap up with our real world experiences using FlexFlow and where we can go with it next.2Related WorksBusiness Process (Re-)Engineering [5] is an important driving force for workflow management. It aims to make business processes more efficient and quickly adjustable to the ever-changing needs of customers. In contrast to specifications of business processes, workflow specifications serve as a basis for the largely automated execution of processes. Workflow specifications are often derived from business process specifications by refining the business process specification into a more detailed and more concrete form. Automated and computer-assisted execution means that a workflow management system (WfMS) [4], [9], [12] controls the processing of activities, which have to be performed in the workflow. Some activities may have a manual or intellectual part, to be performed by a human. But the workflow management system is in charge of determining the (partial) invocation order of these activities. In contrast to business process specifications, this requires a formal specification of control flow and data flow.Workflow specifications based on script languages contain control flow and data flow constructs which are specifically tailored to workflow applications. Such script languages are popular in current WfMS products. They provide a compact representation making them easy to use. A drawback of most script languages is their lack of a formal foundation. Their semantics is mostly ’defined’ by the code of the script interpreter used.Leymann argues in [11] that state transition nets are a good choice when a graphical visualization of workflow specifications has high priority. In state transition nets, activities are represented by nodes, and control flow is represented by edges. In fact, almost all WfMS products provide means for graphical specifications similar to state transition nets.Considering only net-based methods with a formal foundation, we have to restrict ourselves more or less to statecharts [6] and Petri nets [3], [15]. Variants of Petri nets, especially predicate transition nets, are used in a number of research prototypes as well as in several WfMS products [2], [14]. Some workflow management systems use variants of Petri nets for the internal representation of the workflow engine, e.g., [16]. Statecharts [6], [7] have received little attention in workflow management, but they are well established in software engineering, especially for specifying reactive systems. In the MENTOR project [21], statecharts are used as a formal foundation for workflow specification.Event-Condition-Action-Rules (ECA) rules are used in active database systems and have been adopted by a number of projects in the workflow area (e.g., [10]). ECA rules are used to specify the control flow between activities. Like for other methods that are not based on nets, the graphical visualization of sets of ECA rules is a non-trivial task. Large sets of ECA rules are hard to handle, and a step-wise refinement isA State Machine Based Approach for a Process Driven Development 55 not supported [17]. In terms of their formal foundation, ECA rules are typically mapped to other specification methods, especially variants of Petri nets or temporal logic.The pattern of user interaction with e-commerce business processes is very different from that of traditional workflow systems. Online business systems are highly interactive. Internet applications follow the request-response model. In online business systems, a user takes an action, such as clicking a submit button on a web page. This results in the form data on that page being sent to the system and the system acting on it and presenting another page to the user. For example, a user goes to a shopping web site, fills out the login page and clicks the submit button. This results in her user name and password being sent to the system, which authenticates the user and returns the catalog page. Then the system waits until the user selects products to fill the shopping basket. This interactive, conversational pattern of the system acting based on a user request and then waiting for the user to initiate the next step is not well modeled by existing workflow systems. This modeling difficulty is a major reason why online e-business applications do not use workflow systems.Another problem is the complexity, cost, and size of workflows systems cause a high cost of deployment and limit the responsiveness when servicing a large number of concurrent requests. Microflows [1] have been proposed to address this drawback of workflow systems. Microflows are small footprint workflow systems crafted for a particular class of applications. They provide minimal or no support for services provided by full workflow systems such as transaction management, guaranteed messaging and worklists. Microflows provide the benefits of abstracting process logic from task logic while at the same time improving the responsiveness and reducing the cost as compared to industrial strength workflow systems.State machines are widely used for implementation of network protocols to describe the conversation between a sender and receiver. Business processes for e-commerce platforms also interact frequently with each other. Examples are negotiation scenarios between buyers and sellers, where the current state determines the next available actions to each. State machines have been also used to model negotiations [18]. They have been used for real-time systems; a system reacts or responds to events with a quick, nearly instantaneous response [19]. Thus, there is strong evidence to support that state machines would be useful for interactive, conversational and responsive online business systems.3Flexflow OverviewFig. 1 shows the lifecycle of business processes in the FlexFlow system. A visual visual modeling tool generates from the process state diagrams an XML representation, which is a full description of the business process. It contains all the information required by the FlexFlow engine to control the execution of the business process. This XML description is compiled and loaded into the FlexFlow system database tables. An additional table is used to store the current state of each instance of a business process running at a given time in the business system. The FlexFlow engine uses these tables to control the execution of business processes as well as the user interface.56 Rakesh Mohan et al.Fig. 1: FlexFlow - Lifecycle of a business processThe visual modeling tool is also used to modify definitions of business processes. Different versions of the business process are stored in the business flow storage. Business processes can be changed with limited or no change to the task logic or computer programs that are implementations of the business actions. Simply reconfiguring its corresponding state machine reconfigures a commerce function.The FlexFlow system also includes a component for simulating business processes. Thereby, users and developers can explore process variations to reach a common vision of how the user might interact with the system to perform a task.4The Flexflow Process ModelFlexFlow models e-commerce business processes as Unified Modeling Language (UML) state diagrams [20], which are an adaptation of Harel’s statecharts [6], [7]. UML uses state diagrams to describe the behavior of objects, whereas, FlexFlow uses statecharts to describe processes. We adopt the UML state diagram notation for the FlexFlow.A State Machine Based Approach for a Process Driven Development 57Fig. 2: FlexFlow state diagramsUML state diagrams are directed graphs with nodes called states and the directed edges between them called transitions (see Fig. 2). FlexFlow models interactive online business processes with these state diagrams. However, unlike UML, where state diagrams describe the behavior of objects, FlexFlow state diagrams describe processes. In addition to the functionality of Harel statecharts and UML state diagrams, FlexFlow adds three key features: 1) the concept of roles, 2) the coordination of interactions of multiple parties, and 3) the ability to allow different organizations to use different versions of the business process. Business processes are versioned as different state diagrams. Versions can be selected based on membership at the organization level. Versions can also be selected based on other factors including the mode of interaction, such as device, browser, and messaging method. The UML notation used by FlexFlow consists of states, transitions, events, guards, and context.4.1ActionsActions correspond to task logic being executed at the application server. For FlexFlow they are atomic units of business work. Actions can appear in states and transitions. An action can be used to interface to an external system, such as a workflow system handling its own set of functionality. An action can be a conglomeration, or sequence, of pre-defined internal commerce actions. All actions caused by the processing of an event are run within the same transaction.4.2StatesStates correspond to stages in a business process. A state identifies a precise point within the process. In a given business process at a given state, the actions that can be taken by various parties are completely defined by the set of outgoing transitions. A state may have an entry action, an action that is executed upon entering the state, and an exit action, an action that is executed upon leaving the state. In FlexFlow, entry actions are allowed to trigger new events, which in turn get processed by FlexFlow.58 Rakesh Mohan et al.4.3TransitionsA transition represents a change of the process state. It connects two states, a source state it exits and a target state it enters. A transition corresponds to an action that is taken in response to an event. Additionally, the transitions may have guards on them. These guards are checked, and the transition is taken only if they are true. Only one transition out of a state is taken in response to an event. In UML state diagrams, the actions on the transitions are assumed to be instantaneous. In FlexFlow most of the processing activity happens on the transition actions. Given the interactive nature of the applications, these usually take a very short time, but are not instantaneous.4.4EventsAn event is a named message needing to get processed. In Internet applications, an event is usually an HTTP client request generated by a user pressing a hyperlink, button, etc. on a web page. It can also be an incoming Simple Object Access Protocol (SOAP) request or a Java Message Service(JMS) message. It can also be an event generated by another process such as a scheduler or another FlexFlow process. It can even be an event generated in the same FlexFlow process by a transition or a state entry action.4.5GuardsA guard is a set of conditions that need to be true before the action can be taken. Conditions are Boolean computations on the context of the business process and/or the parameters of the event. In general, the guards can be rules. In our implementation, an access control condition is always present in the guard. Thus, the action on a transition is taken only if access is allowed. If no access control policy is explicitly specified, the default access control mechanism is used.4.6ContextContext is data associated with a business process. It consists of•The session information that includes information about the user including roles and permissions, and•The data submitted by the user such as form entries and the data stored in the form such as the identification of the process and the business object. For example, if a user submits a bid for an auction, the context would contain the username and roles as well as the amount of the bid. The event would include an identifier for the auction on which the bid is made. Also included in the context is more general information about the process such as auction start and end time, number of bids, etc.This context can be referenced in guards as well as read and updated in actions. Fig. 3 shows a FlexFlow model for a simple bilateral negotiation process between a buyer and a seller. The top right transition shows that on the event “Offer” the action “RecordOffer” is taken. The guard checks that the user making the offer is theA State Machine Based Approach for a Process Driven Development 59“Buyer”. As the action for the other “Offer” transitions is also “RecordOffer” we do not show it here for simplicity. There is no action corresponding to the “Accept” or “Reject” events. On entry to the final state “Deal” a “RecordDeal” action is taken.Fig. 3: A simple state diagram for bilateral negotiation Fig. 4 shows two variations of the bilateral negotiation process shown in Fig 3. The process in Fig. 3 forces the buyer and seller to alternate their bids, i.e., once a participant makes an offer, she has to wait for the other party to make a counter offer. In Fig. 4 (a), the parties can improve their offers without waiting for a counter offer. In Fig. 4 (b), the parties can make a final offer which forces the other party to either accept of reject the offer but does not allow them to counter offer. As is obvious from the process diagrams, the three variants of the business process reuse the code for just three actions “RecordOffer”, “RecordDeal” and “RecordNoDeal”.5User Interaction with FlexFlowWe have observed that a common practice for designing web sites, such as e-commerce sites, is to first mock-up the flow of web pages for user interactions, and then to use this flow to drive the development of application logic. This practice works when the business process is simple and when only one party (the user) is interacting with the system. However, this design practice does not scale to complex business processes, especially where multiple parties are participating in the business process, such as two users in a bilateral negotiation or a buyer and multiple sellers in an RFQ, along with schedulers for timeouts etc. Another drawback of this design practice is that process logic gets embedded both in web pages and application code further complicating any modification of the business process.5.1Process ReflectionThe FlexFlow process model has sufficient information for deriving user interactions from the state diagram. The process reflection mechanism of FlexFlow allows clients to discover or query process information at run time. This mechanism can be used to60 Rakesh Mohan et al.drive the user interface or the future user interaction. Thus, with FlexFlow, the design practice is to first design the process and then to automatically derive the flow of user interactions. As the user interaction information is added dynamically to the web pages at run time, the modifications of the business process get automatically reflected in the web pages.Fig. 4: Two variations of the bilateral negotiation process Process reflection allows users to query a list of actions that are valid for a given user role at the current state of the business process. At each given state, the FlexFlow system knows the next possible set of actions a particular user can perform by using the guards on all the outgoing transitions. Thus, FlexFlow can provide relevant information for the rendering of the user output (i.e., FlexFlow can determine whether buttons should be enabled or disabled). If web designers use this reflection mechanism, web pages can be shared among different process versions. Using reflection also reduces the effort for modifying FlexFlow processes [8].We illustrate this in Fig. 5 for a simple bilateral negotiation. There is web page for each state for each user where the user can take an action. The seller’s pages are outlined in blue and the buyer’s pages are outline in green. At the start state, either party can make an offer to start the negotiation so the both the buyer’s and seller’s page show a button (or other control) for making an offer. If the seller makes an offer, the process moves to the “Seller Offered” state and the page for the seller will show no buttons (corresponding to this instance of the bilateral negotiation) while theA State Machine Based Approach for a Process Driven Development 61buyer’s page will display the options to make a counter offer or to accept or reject the current offer. As the controls are generated dynamically via reflection on the process model, when the process is changed, for example as shown in Fig. 4, the controls on the web pages will show the correct set of actions without any rewriting.accept rejectofferFig. 5: Controls on web forms for user interactions are created using FlexFlow. The blue outlined page is for the seller, the green for the buyer. The text in black corresponds to buttons on the forms6 Visual Modeling & SimulationThe FlexFlow engine uses an XML representation of the process definition. To allow business managers to easily create and change FlexFlow processes, we extended popular COTS (commercial off-the-shelf) modeling tools. Since statecharts are a part of the popular UML notation, a number of graphical tools are available. For managing FlexFlow processes, we have added extensions to both Microsoft Visio® and Rational Rose®. Therefore, business managers can use a familiar modeling environment,which provides the following key functionalities:•Easy-to-use modeling interface for creating or modifying business processes by changing, adding, and/or removing states and transitions from the process state diagram.• XML generation of the process definition based on the process state diagram.• Import / Export of the XML process definition • Management of different versions of process state machines.• Simulation of the FlexFlow processesThe states and transitions of FlexFlow state diagrams have additional attributes like response views, additional guard properties and priorities. Business managers can import and export XML process definitions via a file or a web-service.Different versions of a business process can be maintained based on membership at the organization level. Versions can also be selected based on the mode of interaction, such as device, browser, and messaging. Fig. 6 shows the default version of a RFQ process. By specifying new flows, the modeling tool allows administrators to manage several variations of a RFQ process. This way, business managers can model and maintain several RFQ processes (for instance a “Normal RFQ” process, and a “Fast RFQ” process, which is a more compact version of the normal RFQ process).Fig. 6: Visio modeling tool for FlexFlow6.1Process SimulationIn a typical web application, users can navigate to a limited number of web pages based on the actions they take. The number of possible navigation paths can be very large in a complex graphical user interface, but the number is finite and the options usually are known. User interfaces also must stay in sync with the underlyingbusiness process. Therefore, process state diagrams reflect the navigation paths of the user at a high level of abstraction.Process state diagrams can be used to explore hypothetical process models and user interface concepts based on the understanding of the requirements. Users and developers can study a process state diagram to reach a common vision of how the user might interact with the system to perform a task. The business process, business rules and the user experience can be incrementally and iteratively optimized by simulating the business process with user scenarios. These simulations can occur without implementing the business logic. This way, conflicts between the business process and the user interface can be easily discovered.Process state diagrams capture the essence of the user-system interactions and task flow without getting one bogged down too soon in specifying the details of web pages or data elements. Users can trace through a process state diagram to find missing, incorrect, or superfluous transitions, and hence missing, incorrect, or superfluous requirements.The FlexFlow modeling tool includes a simulation component that allows development of a horizontal prototype which displays the facades of user interface screens from the web application, possibly allowing some navigation between them. The tool does not show real data and contains little or no real functionality. The information that appears in response to a client’s request is faked or static, and report contents are hard-coded. Nevertheless, the simulation component allows a process-oriented navigation through the web application. It allows users to change the status of the current process by selecting one of the available actions on the simulation panel. For the simulation, we can include web pages of existing web solutions or new web pages, which can be instantly created and modified. Fig. 7 shows the simulation of the RFQ process. The buttons in the simulation panel at the bottom of the screen show the available navigations paths based on the RFQ process state diagram.Note, that not all page flows are represented by the control flows of a process. For instance, wizards, like in Fig., or other UI facilitators which have a predefined have no impact the process itself. UI components of the presentation layer use the process reflection mechanism to determine functionality, which should be available to the user.This type of simulation is often sufficient to give the users a feeling for the web application and lets them judge whether any functionality is missing, wrong, or unnecessary. The simulation prototypes represent the concepts to the developers of how the business process might be implemented. The user’s evaluation of the prototype can point out alternative courses for a business process, new missing process steps, previously undetected exception conditions, or new ways to visualize information.By modeling and executing business processes as state machines, FlexFlow enables its process to be modified with minimal changes to the underlying implementation of the business processes. A commerce process can be modified simply by reconfiguring its corresponding state diagram.。
