Integrating Concurrency and Object-Oriented Programming An Evaluation of Hybrid
Optimizations for parallel object-oriented frameworks

1 Introduction
Application codes increasingly fail to realize the potential performance of modern parallel architectures; compilers have only limited mechanisms with which to e ect sophisticated transformations to arrest this trend. Compilers must must perform optimizations in the context of the semantics of a complete language speci cation and thus cannot perform more sophisticated transformations. Object-oriented frameworks provide a level of tailoring of the C++ language to speci c restricted contexts, but compilers are still relied upon for most performance optimization. No mechanism exists to express the restricted semantics of a class library such that a compiler could perform more sophisticated optimizations. In this paper we explore a family of optimizing transformations appropriate to objectoriented frameworks for scienti c computing, and present a preprocessing mechanism, ROSE, which delivers the more sophisticated transformations automatically from the use of abstractions represented within high level object-oriented frameworks. We have found that these optimizations permit improved performance over FORTRAN 77 by factors of three to four, su ciently interesting to suggest that higher level abstractions can contain greater semantics and that the greater semantics can be used to drive more sophisticated optimizations than are possible with lower level languages.
methods of numerical integration

methods of numerical integrationIntroductionNumerical integration is a process commonly used in mathematics and scientific computations to find the approximate value of a definite integral. Integrals are fundamental in calculus and often used to calculate areas, volumes, and probabilities. Numerical integration methodscome in handy when analytical solutions are either difficultor impossible to find. In this article, we will explore different numerical integration methods and their applications, step by step.Step 1: Riemann SumsRiemann sums use rectangles to approximate integrals. Suppose we need to find the integral of a function f(x) fromx = a to b. We divide the interval [a, b] into n subintervals, each of width Δx = (b - a) / n, and evaluate the function at the left or right endpoint of each subinterval. For instance, if we are using the left endpoint rule, we calculate Δx [ f(a) + f(a + Δx) + f(a + 2Δx) + ... + f(a + (n-1)Δx) ]In this way, we obtain a finite sum that approximatesthe integral. As n increases, the approximation improves, and we approach the exact value of the integral.Step 2: Trapezoidal RuleThe trapezoidal rule is another numerical integration method that uses trapezoids to approximate integrals. Again, we divide the interval [a, b] into n subintervals, but now we approximate f as a straight line within each subinterval. Thearea of each trapezoid is (Δx/2)[f(x_i) + f(xi+1)], where xi and xi+1 are the endpoints of the subinterval. The sum ofthese areas yields an approximation to the integral.Step 3: Simpson's RuleSimpson's rule is a more accurate numerical integration method that uses quadratic polynomials to approximate fwithin each subinterval. Suppose we divide [a, b] into aneven number of subintervals, n = 2m, where m is an integer. Then, for each subinterval [xi, xi+2], we can find aquadratic polynomial that passes through the endpoints andthe midpoint xi+1. The area under each parabolic arch is(Δx/6)[f(xi) + 4f(xi+1) + f(xi+2)]. Summing these areas overall the subintervals gives a more accurate approximation tothe integral than either Riemann sums or the trapezoidal rule.Step 4: Monte Carlo IntegrationMonte Carlo integration is a stochastic method that approximates integrals using random numbers. Suppose we wantto find the integral of a function f(x) over a domain D. We generate N random points (x,y) uniformly within D andcalculate what fraction of them fall below the graph of f.This fraction is roughly equal to the area below the graph divided by the area of D. Hence, the approximate value of the integral is the area of D times the fraction of points below the graph.ConclusionIn conclusion, numerical integration is an essentialtool for approximating integrals in mathematics andscientific computing. Riemann sums, the trapezoidal rule, Simpson's rule, and Monte Carlo methods are some of the most commonly used methods. The choice of the method depends onthe properties of the function, the interval, and the desiredlevel of accuracy. Numerical integration has countless applications in physics, engineering, economics, and other fields where integrals arise.。
工作分析和工作计划英文版

Definition of Work Analysis
Work Analysis is a process of studying the nature, characteristics, and requirements of work tasks.
It involves breaking down work into its constituent elements and analyzing them to understand their relationships and dependencies.
Identifies the human, technical, and material resources required for project execution.
Identifies potential risks and how they will be mitigated or managed.
Case Study 2: Work Plan in a Software Development Project
总结词
需求分析、时间管理、团队协作
详细描述
在软件开发项目中,制定详细的工作计划至关重要。首先,进行需求分析,明确软件的 功能和性能要求,为后续开发提供依据。其次,做好时间管理,根据项目复杂度和团队 能力,合理安排开发进度,确保项目按时交付。此外,加强团队协作,通过有效的沟通
Analyze work: Break down the project into smaller, manageable tasks and analyze the effort required for each task.
Prioritize tasks:
two-stage stochastic programming

two-stage stochastic programmingTwo-stage stochastic programming is a mathematical optimization approach used to solve decision-making problems under uncertainty. It is commonly applied in various fields such as operations research, finance, energy planning, and supply chain management. In this approach, decisions are made in two stages: the first stage involves decisions made before uncertainty is realized, and the second stage involves decisions made after observing the uncertain events.In two-stage stochastic programming, the decision-maker aims to optimize their decisions by considering both the expected value and the risk associated with different outcomes. The problem is typically formulated as a mathematical program with constraints and objective functions that capture the decision variables, uncertain parameters, and their probabilistic distributions.The first stage decisions are typically made with theknowledge of the uncertain parameters, but without knowing their actual realization. These decisions are usually strategic and long-term in nature, such as investment decisions, capacity planning, or resource allocation. The objective in the first stage is to minimize the expected cost or maximize the expected profit.The second stage decisions are made after observing the actual realization of the uncertain events. These decisions are typically tactical or operational in nature, such as production planning, inventory management, or scheduling. The objective in the second stage is to minimize the cost or maximize the profit given the realized values of the uncertain parameters.To solve two-stage stochastic programming problems, various solution methods can be employed. One common approach is to use scenario-based methods, where a set of scenarios representing different realizations of the uncertain events is generated. Each scenario is associated with a probability weight, and the problem is then transformed into a deterministic equivalent problem byreplacing the uncertain parameters with their corresponding scenario values. The deterministic problem can be solved using traditional optimization techniques such as linear programming or mixed-integer programming.Another approach is to use sample average approximation, where the expected value in the objective function is approximated by averaging the objective function valuesover a large number of randomly generated scenarios. This method can be computationally efficient but may introduce some approximation errors.Furthermore, there are also robust optimization techniques that aim to find solutions that are robust against the uncertainty, regardless of the actualrealization of the uncertain events. These methods focus on minimizing the worst-case cost or maximizing the worst-case profit.In summary, two-stage stochastic programming is a powerful approach for decision-making under uncertainty. It allows decision-makers to consider both the expected valueand the risk associated with uncertain events. By formulating the problem as a mathematical program and employing various solution methods, optimal or near-optimal solutions can be obtained to guide decision-making in a wide range of applications.。
遍历性源和混合源总结

遍历性源和混合源总结
遍历性和混合源(什么是遍历性,如何证明遍历性,什么是混合源)上面提到的离散源,就是离散马尔科夫过程。
这些马尔科夫过程的一个子集在通信理论中非常重要。
这个子集叫做遍历的马尔科夫过程,我们叫对应的源叫遍历源(ergodic source)。
遍历过程的正式定义有点复杂,想法还是比较简单的,就是过程产生的每个序列有相同的统计特性。
也可以把遍历性叫做统计同质性。
所有4中的过程都是ergodic的。
证明一个马尔科夫过程是ergodic的充分条件是它的图表示满足两个特性(1)不存在两个孤立的子图。
(2)所有闭序列长度的最大公约数是1。
混合源就是不满足(1)的源,但是它的孤立子图是ergodic的。
散信息源(怎样用数学形式表示信源,给定信息源的生成信息的速度是多少呢,为什么要研究信息源)我们可以看到上文中求解信道的C的时候只用到了信号的持续时间,而没有过分关注信源。
所以信道相对独立,我们可以通过研究信号源的特性,然后通过适当的编码来降低对信道capacity的要求(研究信源的原因)。
信源传输的序列往往是有规律的,这个规律的数学模型就是随机过程,离散信息源是一个随机过程,任何从有限符号集合中选择符号产生符号序列的随机过程就是离散信源。
常见的离散源有(A)比如英语、德语、汉语等自然语言。
(B)通过量化过程的连续源,比如经过了PCM发送器的量化语音等。
(C)数学定义的随机过程,它能够生成一个符号序列。
最general的case就是n-gram模型,它的统计结构由p(i1,i2,...,in)
或者pi1,i2,...,in−1(in)确定。
Uncertainty principles and ideal atomic decomposition

1 Introduction
Recently, workers in the computational harmonic analysis community have developed a number of interesting new signal representations; see [8, 18, 23]. In addition to sinusoids and wavelets, we now have Wilson bases [9], wavelet packets, and cosine packets [7]. Moreover, the list of such representations is expanding all the time; recent additions include ridgelets, curvelets, and chirplets [4, 2, 3]. In each of these cases we have a transform which has been designed to be e ective at representing objects of a speci c type, where \e ective" means requiring very few signi cant coecients. The transforms turn out to be complementary in the sense that the type of objects for which one transform is well-suited are unlike the objects for which another transform is well-suited. For example, wavelets perform relatively poorly on high-frequency sinusoids, for which sinusoids are (naturally) very e ective. On the other hand, sinusoids perform poorly on impulsive events, for which wavelets are very e ective. In dimension 2, wavelets do poorly with discontinuities on edges, for which ridgelets are e ective [4], while ridgelets do poorly on impulsive events. It is natural in such a setting to consider combining signal representations, using terms from each of several di erent bases. One supposes that the object of interest is a superposition of two phenomena, one of which by itself can be e ectively represented in Basis 1 and the other of which by itself can be e ectively represented in Basis 2, and one hopes that by allowing a representation built from terms in both bases, one might obtain an e ective representation { far more e ective than what one could obtain using either basis alone. Speci cally, one hopes to represent an object containing two phenomena in superposition with the eciency one would expect in analyzing each phenomenon separately in its own appropriate basis. Such speculation leads one to propose the use of dictionaries = 1 [ 2 [ : : : [ D made from a concatenation of several orthonormal bases d = f'd;i g, and to seek representations of a signal S (t) as
基于不确定性量化分析的超低能耗建筑空调系统运行能耗研究

学术探讨暖通空调HV&AC2021年第51卷第5期67 [引用本文]赵德印,徐强.基于不确定性量化分析的超低能耗建筑空调系统运行能耗研究[J].暖通空调,2021,51(5) :67-74基于不确定性量化分析的超低能耗建筑空调系统运行能耗研究X上海市建筑科学研究院有限公司赵德印☆徐强摘要由于实际建筑运行条件复杂多变,单一工况点下的建筑空调系统运行能耗模拟 计算结果往往与实测数据偏差较大。
为准确评估上海一栋超低能耗建筑空调系统的运行能 耗,应用不确定性量化分析方法对其进行了分析研究,使用累积概率对建筑空调系统运行能 耗进行了概率估计。
对影响空调系统运行能耗的参数进行了不确定性辨析,确定了参数概 率分布及取值范围;在此基础上,使用DesignBuilder对空调系统运行能耗进行了不确定性量 化分析。
经计算可知,在95%的概率下,该建筑空调系统全年单位面积运行能耗约为25 kW•h/( m2 •a)。
关键词不确定性量化分析超低能耗建筑空调系统敏感性分析累积概率Energy consumption of air conditioning systems in ultra-lowenergy buildings based on uncertainty quantitative analysisBy Zhoo Deyin^ and Xu QiongAbstract Due to the complicated operating conditions o f actual buildings, the simulation results of energy consumption of building air conditioning systems under a single working condition often deviategreatly from the measured data. In order to accurately assess the air conditioning system energyconsumption of an ultra-low energy building in Shanghai, takes the cumulative probability to estimate theenergy consumption of air conditioning system based on the uncertainty quantitative analysis. Analyses theuncertainty o f parameters affecting the energy consumption of air conditioning system and determines theprobability distribution and value range. On this basis,analyses the uncertainty distribution o f energyconsumption using the DesignBuilder software. According to the analysis, the annual energy consumptionper unit area of the building air conditioning system is about 25 kW h/(m2• a) with a probability of 95%.Keywords uncertainty quantitative analysis, ultra-low energy building,air conditioning system,sensitivity analysis,cumulative probability★Shanghai Research Institute of Building Sciences Co., Ltd., Shanghai, China〇引言受内部和外部各种复杂因素的影响,在工程 实践中存在着大量的随机不确定性和认知不确定性,因此如何通过一定的技术手段来提高工程 系统的稳健性显得尤为重要。
java英文参考文献

java英⽂参考⽂献java英⽂参考⽂献汇编 导语:Java是⼀门⾯向对象编程语⾔,不仅吸收了C++语⾔的各种优点,还摒弃了C++⾥难以理解的多继承、指针等概念,因此Java语⾔具有功能强⼤和简单易⽤两个特征。
下⾯⼩编为⼤家带来java英⽂参考⽂献,供各位阅读和参考。
java英⽂参考⽂献⼀: [1]Irene Córdoba-Sánchez,Juan de Lara. Ann: A domain-specific language for the effective design and validation of Java annotations[J]. Computer Languages, Systems & Structures,2016,:. [2]Marcelo M. Eler,Andre T. Endo,Vinicius H.S. Durelli. An Empirical Study to Quantify the Characteristics of Java Programs that May Influence Symbolic Execution from a Unit Testing Perspective[J]. The Journal of Systems & Software,2016,:. [3]Kebo Zhang,Hailing Xiong. A new version of code Java for 3D simulation of the CCA model[J]. Computer Physics Communications,2016,:. [4]S. Vidal,A. Bergel,J.A. Díaz-Pace,C. Marcos. Over-exposed classes in Java: An empirical study[J]. Computer Languages, Systems & Structures,2016,:. [5]Zeinab Iranmanesh,Mehran S. Fallah. Specification and Static Enforcement of Scheduler-Independent Noninterference in a Middleweight Java[J]. Computer Languages, Systems & Structures,2016,:. [6]George Gabriel Mendes Dourado,Paulo S Lopes De Souza,Rafael R. Prado,Raphael Negrisoli Batista,Simone R.S. Souza,Julio C. Estrella,Sarita M. Bruschi,Joao Lourenco. A Suite of Java Message-Passing Benchmarks to Support the Validation of Testing Models, Criteria and Tools[J]. Procedia Computer Science,2016,80:. [7]Kebo Zhang,Junsen Zuo,Yifeng Dou,Chao Li,Hailing Xiong. Version 3.0 of code Java for 3D simulation of the CCA model[J]. Computer Physics Communications,2016,:. [8]Simone Hanazumi,Ana C.~V. de Melo. A Formal Approach to Implement Java Exceptions in Cooperative Systems[J]. The Journal of Systems & Software,2016,:. [9]Lorenzo Bettini,Ferruccio Damiani. Xtraitj : Traits for the Java Platform[J]. The Journal of Systems & Software,2016,:. [10]Oscar Vega-Gisbert,Jose E. Roman,Jeffrey M. Squyres. Design and implementation of Java bindings in OpenMPI[J]. Parallel Computing,2016,:. [11]Stefan Bosse. Structural Monitoring with Distributed-Regional and Event-based NN-Decision Tree Learning Using Mobile Multi-Agent Systems and Common Java Script Platforms[J]. Procedia Technology,2016,26:. [12]Pablo Piedrahita-Quintero,Carlos Trujillo,Jorge Garcia-Sucerquia. JDiffraction : A GPGPU-accelerated JAVA library for numerical propagation of scalar wave fields[J]. Computer Physics Communications,2016,:. [13]Abdelhak Mesbah,Jean-Louis Lanet,Mohamed Mezghiche. Reverse engineering a Java Card memory management algorithm[J]. Computers & Security,2017,66:. [14]G. Bacci,M. Bazzicalupo,A. Benedetti,A. Mengoni. StreamingTrim 1.0: a Java software for dynamic trimming of 16S rRNA sequence data from metagenetic studies[J]. Mol Ecol Resour,2014,14(2):. [15]Qing‐Wei Xu,Johannes Griss,Rui Wang,Andrew R. Jones,Henning Hermjakob,Juan Antonio Vizcaíno. jmzTab: A Java interface to the mzTab data standard[J]. Proteomics,2014,14(11):. [16]Rody W. J. Kersten,Bernard E. Gastel,Olha Shkaravska,Manuel Montenegro,Marko C. J. D. Eekelen. ResAna: a resource analysis toolset for (real‐time) JAVA[J]. Concurrency Computat.: Pract. Exper.,2014,26(14):. [17]Stephan E. Korsholm,Hans S?ndergaard,Anders P. Ravn. A real‐time Java tool chain for resource constrained platforms[J]. Concurrency Computat.: Pract. Exper.,2014,26(14):. [18]M. Teresa Higuera‐Toledano,Andy Wellings. Introduction to the Special Issue on Java Technologies for Real‐Time and Embedded Systems: JTRES 2012[J]. Concurrency Computat.: Pract. Exper.,2014,26(14):. [19]Mostafa Mohammadpourfard,Mohammad Ali Doostari,Mohammad Bagher Ghaznavi Ghoushchi,Nafiseh Shakiba. Anew secure Internet voting protocol using Java Card 3 technology and Java information flow concept[J]. Security Comm. Networks,2015,8(2):. [20]Cédric Teyton,Jean‐Rémy Falleri,Marc Palyart,Xavier Blanc. A study of library migrations in Java[J]. J. Softw. Evol. and Proc.,2014,26(11):. [21]Sabela Ramos,Guillermo L. Taboada,Roberto R. Expósito,Juan Touri?o. Nonblocking collectives for scalable Java communications[J]. Concurrency Computat.: Pract. Exper.,2015,27(5):. [22]Dusan Jovanovic,Slobodan Jovanovic. An adaptive e‐learning system for Java programming course, based on Dokeos LE[J]. Comput Appl Eng Educ,2015,23(3):. [23]Yu Lin,Danny Dig. A study and toolkit of CHECK‐THEN‐ACT idioms of Java concurrent collections[J]. Softw. Test. Verif. Reliab.,2015,25(4):. [24]Jonathan Passerat?Palmbach,Claude Mazel,David R. C. Hill. TaskLocalRandom: a statistically sound substitute to pseudorandom number generation in parallel java tasks frameworks[J]. Concurrency Computat.: Pract.Exper.,2015,27(13):. [25]Da Qi,Huaizhong Zhang,Jun Fan,Simon Perkins,Addolorata Pisconti,Deborah M. Simpson,Conrad Bessant,Simon Hubbard,Andrew R. Jones. The mzqLibrary – An open source Java library supporting the HUPO‐PSI quantitative proteomics standard[J]. Proteomics,2015,15(18):. [26]Xiaoyan Zhu,E. James Whitehead,Caitlin Sadowski,Qinbao Song. An analysis of programming language statement frequency in C, C++, and Java source code[J]. Softw. Pract. Exper.,2015,45(11):. [27]Roberto R. Expósito,Guillermo L. Taboada,Sabela Ramos,Juan Touri?o,Ramón Doallo. Low‐latency Java communication devices on RDMA‐enabled networks[J]. Concurrency Computat.: Pract. Exper.,2015,27(17):. [28]V. Serbanescu,K. Azadbakht,F. Boer,C. Nagarajagowda,B. Nobakht. A design pattern for optimizations in data intensive applications using ABS and JAVA 8[J]. Concurrency Computat.: Pract. Exper.,2016,28(2):. [29]E. Tsakalos,J. Christodoulakis,L. Charalambous. The Dose Rate Calculator (DRc) for Luminescence and ESR Dating-a Java Application for Dose Rate and Age Determination[J]. Archaeometry,2016,58(2):. [30]Ronald A. Olsson,Todd Williamson. RJ: a Java package providing JR‐like concurrent programming[J]. Softw. Pract. Exper.,2016,46(5):. java英⽂参考⽂献⼆: [31]Seong‐Won Lee,Soo‐Mook Moon,Seong‐Moo Kim. Flow‐sensitive runtime estimation: an enhanced hot spot detection heuristics for embedded Java just‐in‐time compilers [J]. Softw. Pract. Exper.,2016,46(6):. [32]Davy Landman,Alexander Serebrenik,Eric Bouwers,Jurgen J. Vinju. Empirical analysis of the relationship between CC and SLOC in a large corpus of Java methods and C functions[J]. J. Softw. Evol. and Proc.,2016,28(7):. [33]Renaud Pawlak,Martin Monperrus,Nicolas Petitprez,Carlos Noguera,Lionel Seinturier. SPOON : A library for implementing analyses and transformations of Java source code[J]. Softw. Pract. Exper.,2016,46(9):. [34]Musa Ata?. Open Cezeri Library: A novel java based matrix and computer vision framework[J]. Comput Appl Eng Educ,2016,24(5):. [35]A. Omar Portillo‐Dominguez,Philip Perry,Damien Magoni,Miao Wang,John Murphy. TRINI: an adaptive load balancing strategy based on garbage collection for clustered Java systems[J]. Softw. Pract. Exper.,2016,46(12):. [36]Kim T. Briggs,Baoguo Zhou,Gerhard W. Dueck. Cold object identification in the Java virtual machine[J]. Softw. Pract. Exper.,2017,47(1):. [37]S. Jayaraman,B. Jayaraman,D. Lessa. Compact visualization of Java program execution[J]. Softw. Pract. Exper.,2017,47(2):. [38]Geoffrey Fox. Java Technologies for Real‐Time and Embedded Systems (JTRES2013)[J]. Concurrency Computat.: Pract. Exper.,2017,29(6):. [39]Tórur Biskopst? Str?m,Wolfgang Puffitsch,Martin Schoeberl. Hardware locks for a real‐time Java chip multiprocessor[J]. Concurrency Computat.: Pract. Exper.,2017,29(6):. [40]Serdar Yegulalp. JetBrains' Kotlin JVM language appeals to the Java faithful[J]. ,2016,:. [41]Ortin, Francisco,Conde, Patricia,Fernandez-Lanvin, Daniel,Izquierdo, Raul. The Runtime Performance of invokedynamic: An Evaluation with a Java Library[J]. IEEE Software,2014,31(4):. [42]Johnson, Richard A. JAVA DATABASE CONNECTIVITY USING SQLITE: A TUTORIAL[J]. Allied Academies International Conference. Academy of Information and Management Sciences. Proceedings,2014,18(1):. [43]Trent, Rod. SQL Server Gets PHP Support, Java Support on the Way[J]. SQL Server Pro,2014,:. [44]Foket, C,De Sutter, B,De Bosschere, K. Pushing Java Type Obfuscation to the Limit[J]. IEEE Transactions on Dependable and Secure Computing,2014,11(6):. [45]Parshall, Jon. Rising Sun, Falling Skies: The Disastrous Java Sea Campaign of World War II[J]. United States Naval Institute. Proceedings,2015,141(1):. [46]Brunner, Grant. Java now pollutes your Mac with adware - here's how to uninstall it[J]. ,2015,:. [47]Bell, Jonathan,Melski, Eric,Dattatreya, Mohan,Kaiser, Gail E. Vroom: Faster Build Processes for Java[J]. IEEE Software,2015,32(2):. [48]Chaikalis, T,Chatzigeorgiou, A. Forecasting Java Software Evolution Trends Employing Network Models[J]. IEEE Transactions on Software Engineering,2015,41(6):. [49]Lu, Quan,Liu, Gao,Chen, Jing. Integrating PDF interface into Java application[J]. Library Hi Tech,2014,32(3):. [50]Rashid, Fahmida Y. Oracle fixes critical flaws in Database Server, MySQL, Java[J]. ,2015,:. [51]Rashid, Fahmida Y. Library misuse exposes leading Java platforms to attack[J]. ,2015,:. [52]Rashid, Fahmida Y. Serious bug in widely used Java app library patched[J]. ,2015,:. [53]Odeghero, P,Liu, C,McBurney, PW,McMillan, C. An Eye-Tracking Study of Java Programmers and Application to Source Code Summarization[J]. IEEE Transactions on Software Engineering,2015,41(11):. [54]Greene, Tim. Oracle settles FTC dispute over Java updates[J]. Network World (Online) [55]Rashid, Fahmida Y. FTC ruling against Oracle shows why it's time to dump Java[J]. ,2015,:. [56]Whitwam, Ryan. Google plans to remove Oracle's Java APIs from Android N[J]. ,2015,:. [57]Saher Manaseer,Warif Manasir,Mohammad Alshraideh,Nabil Abu Hashish,Omar Adwan. Automatic Test Data Generation for Java Card Applications Using Genetic Algorithm[J]. Journal of Software Engineering andApplications,2015,8(12):. [58]Paul Venezia. Prepare now for the death of Flash and Java plug-ins[J]. ,2016,:. [59]PW McBurney,C McMillan. Automatic Source Code Summarization of Context for Java Methods[J]. IEEE Transactions on Software Engineering,2016,42(2):. java英⽂参考⽂献三: [61]Serdar Yegulalp,Serdar Yegulalp. Sputnik automates code review for Java projects on GitHub[J].,2016,:. [62]Fahmida Y Rashid,Fahmida Y Rashid. Oracle security includes Java, MySQL, Oracle Database fixes[J]. ,2016,:. [63]H M Chavez,W Shen,R B France,B A Mechling. An Approach to Checking Consistency between UML Class Model and Its Java Implementation[J]. IEEE Transactions on Software Engineering,2016,42(4):. [64]Serdar Yegulalp,Serdar Yegulalp. Unikernel power comes to Java, Node.js, Go, and Python apps[J]. ,2016,:. [65]Yudi Zheng,Stephen Kell,Lubomír Bulej,Haiyang Sun. Comprehensive Multiplatform Dynamic Program Analysis for Java and Android[J]. IEEE Software,2016,33(4):. [66]Fahmida Y Rashid,Fahmida Y Rashid. Oracle's monster security fixes Java, database bugs[J]. ,2016,:. [67]Damian Wolf,Damian Wolf. The top 5 Java 8 features for developers[J]. ,2016,:. [68]Jifeng Xuan,Matias Martinez,Favio DeMarco,Maxime Clément,Sebastian Lamelas Marcote,Thomas Durieux,Daniel LeBerre. Nopol: Automatic Repair of Conditional Statement Bugs in Java Programs[J]. IEEE Transactions on Software Engineering,2017,43(1):. [69]Loo Kang Wee,Hwee Tiang Ning. Vernier caliper and micrometer computer models using Easy Java Simulation and its pedagogical design features-ideas for augmenting learning with real instruments[J]. Physics Education,2014,49(5):. [70]Loo Kang Wee,Tat Leong Lee,Charles Chew,Darren Wong,Samuel Tan. Understanding resonance graphs using Easy Java Simulations (EJS) and why we use EJS[J]. Physics Education,2015,50(2):.【java英⽂参考⽂献汇编】相关⽂章:1.2.3.4.5.6.7.8.。
Reactive Objects

Reactive ObjectsJohan Nordlander,Mark P.Jones,Magnus Carlsson,Richard B.Kieburtz,and Andrew Black∗OGI School of Science&Engineering at OHSU,20000NW Walker Road,Beaverton,OR97006.AbstractObject-oriented,concurrent,and event-based program-ming models provide a natural framework in which to ex-press the behavior of distributed and embedded software sys-tems.However,contemporary programming languages stillbase their I/O primitives on a model in which the environ-ment is assumed to be centrally controlled and synchronous,and interactions with the environment carried out throughblocking subroutine calls.The gap between this view and thenatural asynchrony of the real world has made event-basedprogramming a complex and error-prone activity,despite re-cent focus on event-based frameworks and middleware.In this paper we present a consistent model of event-basedconcurrency,centered around the notion of reactive objects.This model relieves the object-oriented paradigm from theidea of transparent blocking,and naturally enforces reactiv-ity and state consistency.We illustrate our point by a pro-gram example that offers substantial improvements in sizeand simplicity over a corresponding Java-based solution.1BackgroundIn the traditional view of programming,the program isassumed to be the master of its environment,and interactionwith the environment is accordingly expressed in terms ofthe subroutine abstraction.This programming model datesback to the early age of batch-oriented computing,whenprogrammers saw a need to abstract away from low-leveldetails of peripheral devices—such as card-readers and line-printers—that were used at the time.The key idea here is thatblocking of execution is made transparent;that is,the pro-grammer is supposed not to be interested in knowing whethera subroutine obtains its result by some internal computation,or by means of synchronization with an external device.Despite many advances in language design,this sim-ple,traditional view of I/O still prevails in contemporaryobject-oriented languages.But modern software executes inmuch more complex environments,with interactive point-and-click graphics,ubiquitous networks,multiple threads ofensuring liveness and avoiding deadlocks.Notice,though,that in the AWT-plus-sockets scenario sketched above there is nothing that actually suggests con-current execution;what the extra threads achieve is really the ability to perform concurrent blocking.While concur-rency is an important tool in real-time programming,being forced to use it just to circumvent an inappropriate I/O model is not satisfactory.Also note that an abstract object model of the example would probably consist of just one simple ob-ject,equipped with methods corresponding to the events it is required to handle:mouse clicks,key presses,and packet arrivals.A central argument of this paper is that the heavy encodings needed to turn even simple event-driven models into working code is most unfortunate,and is an important factor behind the perceived complexity of concurrent object-oriented programming.The current practice of using threads to circumvent the traditional I/O model is extremely fragile,in the sense that an accidental call to a blocking operation in the middle of an event-handler will immediately destroy the responsive-ness of that thread.That is,transparent blocking makes re-sponsiveness a delicate property that can only be upheld by careful programming,requiring knowledge not only of the complex APIs that encode events and threads,but also of all operations which potentially might block,and which thus must be avoided.As an illustration,consider the following quote from the documentation for Java’s New I/O library[9]: That a selection key indicates that its channel isready for some operation is a hint,but not a guar-antee,that such an operation can be performed bya thread without causing the thread to block.Itis imperative that code that performs multiplexedI/O be written so as to ignore these hints when theyprove to be incorrect.Clearly some special skill or rigorous discipline is required to navigate safely through such dangerous waters.It is es-pecially noteworthy that this comment concerns a new li-brary with pretensions to make event-driven Java program-ming significantly easier than before.The idea of transparent blocking takes its most so-phisticated form in the remote-procedure-call paradigm,or remote-method-invocation(RMI)as it is called using Java terminology.Again,hiding the intricacies of synchroniza-tion with a remote machine under a familiar subroutine-like interface seems attractive atfirst,because it makes the code of distributed programs look quite similar to code written for use in a strictly local context.However,the similarity is deceptive.A defining aspect of a distributed system is usually that it is subject to partial failure;that is,programs are expected to continue running even if a remote server is down,broken,or otherwise unac-cessible.Contrast this to failures directly affecting the local node:here the failure of one component is equivalent to the whole node going down.So in order to hide distribution,the RMI paradigm must also hide the possibility of partial fail-ures.What this means is that failure of any remote machine in an RMI setup is equivalent to a total system failure.In practice,RMI-based programs can only regain some form of robustness by protecting the remote invocations by timeouts and exception handlers.However,this of course also makes the RMI paradigm considerably less convenient(and distri-bution less transparent)[8].2Reactive objectsThe conclusion we have drawn from the problems asso-ciated with transparent blocking and batch-oriented I/O is that significantly more robust event-based software can be obtained by abandoning indefinite blocking altogether,and letting an event-driven design permeate the whole program-ming model.Thread packages,design patterns,and various middleware layers can only do so much to alleviate the pro-grammer from a fundamentally computer-centric view,and they cannot help at all with enforcing responsiveness as long as every method call has a potential of blocking.Our alternative programming model takes as its start-ing point the intuition behind the classical object-oriented paradigm:objects are autonomous,objects maintain a state, objects have methods,methods execute in response to mes-sages.The main step towards a reactive variant of this model is to relieve the classical model from any ties to the tra-ditional way of viewing I/O.In its place,a more orthodox object-oriented scheme of interaction can be devised:•input—the environment calls a method of a program object•output—the program calls a method of an environment objectMethod calls in these categories do not just carry data,they can also be seen as representing the actual input and output events themselves.Notice in particular the asymmetry be-tween input and output that results from this scheme:output is a concrete act of the program,while input is modelled as a passive capability to react.In other words,objects have full control over the output events,but leave the input events to be scheduled by the environment.The autonomy and integrity of objects is essential to this view,though.Just as it is usually beneficial to view real-world objects as having a certain level of atomicity of op-eration,so is it essential to keep software objects from be-coming invaded by multiple method invocations at the same time.On the other hand,the concurrent operation of distinct objects is a natural aspect of the real world,and we wish ourreactive objects to support the same intuition.We therefore take it as a semantic foundation of our model thatevery object is an autonomous unit of executionthat is either executing the sequential code of ex-actly one method,or passively maintaining itsstate.The combination of inter-object concurrency with internal sequential execution effectively makes a reactive object a union of the well-known concepts of an encapsulated state and a critical region.Because objects are autonomous execution units,it makes sense to distinguish between asynchronous and synchronous method invocations.In the former case,the sender of a mes-sage continues execution in parallel with the receiving ob-ject,whereas in the latter case,the sender and receiver per-form a rendezvous.Of course,only synchronous methods provide an opportunity to directly return a result from the receiver to the sender of a message.At afirst glance,synchronous methods seem to provide a way of reintroducing traditional input methods like getc in the model.We do however make an important restriction that will prohibit such use:no methods—in environments or in programs—must block execution indefinitely.This restriction rules out language constructs like selective methodfiltering,as well as environments that provide naive interfaces to blocking system calls.All that a synchronous method call can do is to compute a reply based on the current state of the receiver,possibly after performing some side-effects.The serialization of all method executions of the re-ceiving object does not change the fact that a synchronous method is essentially an ordinary subroutine,since,by an argument of transitivity,if the receiver is not ready to imme-diately execute a synchronous call,it must be busy servicing one of the non-blocking calls that stand in the way.Reactive objects thus alternate between phases of passive inactivity and temporary outbursts of method execution.In contrast to so called active objects,a reactive object does not have a continuous thread of execution;all executable code of an object is defined in terms of its methods.A method of a reactive object is furthermore guaranteed to ter-minate,provided that it does not deadlock or enter an infinite loop.However,due to the absence of blocking constructs in this model,the only source of deadlock is the synchronous method call,and a cyclic chain of such calls is easily de-tectable at run-time.The reactive object model has been realized in the lan-guage Timber that we will survey in the next section.The model is general enough,though,that we would like to sum-marize a few informal claims about its properties before we go into language details.•Reactive objects is a simple and natural model of event-driven systems on various level of detail,from hardware devices to full distributed applications.•It is a straightforward integration of concurrency and object-oriented programming,with the added bonus of automatic protection of state consistency.•A single reactive object can easily handle input from multiple asynchronous sources.•Under assumptions of freedom from non-termination and a very simple form of detectable deadlock,a re-active object is also guaranteed to be responsive in all states.3Reactive objects in TimberWe will now give the model of reactive objects a more concrete form,by showing how it is realized in the pro-gramming language Timber[4].Timber is a strongly typed, object-oriented language with constructs specifically aimed at real-time programming;however,its foundation in the re-active object model makes it suitable as a general purpose language as well.We will introduce Timber by a small pro-gramming example,after pointing out some distinguishing details.•In the syntax of Timber,=denotes a definition,let intro-duces local definitions,f x y is a function f applied to two arguments,and:=is assignment to a state vari-able.•Methods havefirst-class status:they can be passed as parameters and stored in data structures.•Commands and declarations are grouped using layout.Our example is a variant of the program Ping.java from the New I/O API in Java1.4.This program demonstrates how to concurrently measure the time it takes to connect to a particular TCP port on a number of remote hosts.The Tim-ber source is shown in Figure1,and the output of a typical run looks as follows:dogbert:20.018msratbert:41.432msratburg:NetError"lookup failure"theboss:no responsePing is implemented as an object template(i.e.,a class). It is parameterized over a list of hosts and a port number, and a record env that contains methods for interacting with the environment.Templates define a number of state vari-ables as well as an interface,which is typically a record of methods that the environment can invoke.All methods inping hosts port env=templateoutstanding:=hostsin letclient host start peer=recordconnect=actionenv.putStrLn(host++":"++show(baseline-start))outstanding:=remove host outstandingpeer.closeneterror err=actionenv.putStrLn(host++":"++show err)outstanding:=remove host outstandingdeliver pkt=action doneclose=action donecleanup=actionforall h<-outstanding doenv.putStrLn(h++":no response")env.quitin recordmain=actionforall h<-hosts doenv.inet.tcp.open h port(client h baseline) after(2*seconds)cleanupFigure1.Ping in Timberthis example are asynchronous(as determined by the action keyword).The Ping program is started by creating an instance of the template,and then invoking its main method.Internally, Ping objects maintain the state variable outstanding,a list of hosts from which a response has not been seen.The main method calls inet.tcp.open of the environment in order to initiate a TCP connection to the designated port on every given host(forall expresses a loop construct,with h as a loop variable).These calls do not wait for the connection to complete,though;instead,the local method connect is set up to be invoked when the connection has been established. The record client used for this purpose is parameterized over the host we are trying to connect to,the start time of the program,and an environment-provided record contain-ing methods for communicating with the peer host.For tim-ing purposes,actions can refer to the pre-defined variable baseline,which is set to the arrival time of the event that triggered the action.After all connections have been initiated,the asyn-chronous method cleanup is scheduled to be called two seconds after the baseline of main.Note that nowhere does the execution of main block,it just sets up other actions to react to future events.All methods of an object can safely manipulate its state variables in a single-threaded fashion. E.g.,it is irrele-vant here that some methods are defined within the record client,and others elsewhere.Thisflexibility allows us to express a straightforward solution using only one object, with a single state variable.In contrast,the Java program is 287lines of code,has ten class variables,and needs three threads:one for the demultiplexing of connection events, one for single-threaded printing,and one for timeout.4Related workThe reactive object model described in this paper was first developed for the programming language O’Haskell[7]. The current work is,however,ourfirst attempt to distill the programming model as a contribution in its own right. Our language Timber inherits much of its basic design from O’Haskell,but adds several important features,of which the notion of a time-constrained reaction is the most relevant to this paper.Current work on reactive languages is mostly concerned with the synchronous approach to reactivity[3,5].The main hypotheses made in this model are that computations take zero time and event delivery is instantaneous.From these as-sumptions it follows that events received or generated some-where between two clock ticks are actually occurring simul-taneously,and hence,for example,multiple invocations of a particular method during an instant must be indistinguish-able from just a single invocation.The unification of the object and process concepts is an idea that stems from the Actor model[1,2].However,the state of an actor is identified with its current mapping from names to method bodies,and messages to undefined meth-ods are simply queued.Hence actors do not possess the re-sponsiveness property we are emphasizing with our model. Moreover,the Actor model lacks anything similar to our syn-chronous methods,and asynchronous message delivery is not order-preserving.References[1]G.Agha.Actors:A Model of Concurrent Computation in Dis-tributed Systems.MIT Press,1986.[2]G.Agha,I.A.Mason,S.F.Smith,and C.L.Talcott.A foun-dation for actor computation.Journal of Functional Program-ming,7:1–72,1997.[3] A.Benveniste and G.Berry.The Synchronous Approachto Reactive and Real-time Systems.Technical Report1445, INRIA-Rennes,1991.[4] A.P.Black,M.Carlsson,M.P.Jones,R.Kieburtz,and J.Nord-lander.Timber:A programming language for real-time em-bedded systems.Technical Report,/ PacSoft/projects/Timber/,April2002.[5] F.Boussinot,G.Doumenc,and J.Stefani.Reactive Objects.Annals of Telecommunications,51(9-10):459–473,1996. [6]P.Chan and R.Lee.The Java Class Libraries,Second Edition,Volume2.Addison-Wesley,1997.[7]J.Nordlander.Reactive Objects and Functional Programming.PhD thesis,Department of Computer Science,Chalmers Uni-versity of Technology,G¨o teborg,Sweden,May1999.[8]J.Waldo,G.Wyant,A.Wollrath,and S.Kendall.A Noteon Distributed Computing.Technical Report SMLI TR-94-29, Sun Microsystems Laboratories,Inc.,Nov.1994.[9]J.Zukowski.New I/O Functionality for Java2Stan-dard Edition 1.4./developer/ technicalArticles/releases/nio/,October2001.。
数据挖掘算法原理与实现第2版第三章课后答案

数据挖掘算法原理与实现第2版第三章课后答案
1.密度聚类分析:
原理:密度聚类分析是指通过测量数据对象之间的密度(density)
来将其聚成几个聚类的一种聚类分析方法。
它把距离邻近的数据归入同一
类簇,并把不相连的数据分成不同的类簇。
实现:通过划分空间中每一点的邻域来衡量数据点之间的聚类密度。
它将每个数据点周围与它最近的K个数据点用一个空间圆包围起来,以定
义该数据点处的聚类密度。
然后,可以使用距离函数将所有点分配到最邻
近的类中。
2.引擎树:
原理:引擎树(Search Engine Tree,SET)是一种非常有效的数据
挖掘方法,它能够快速挖掘关系数据库中指定的有价值的知识。
实现:SET是一种基于决策树的技术,通过从关系数据库的历史数据
中提取出有价值的信息,来建立一种易于理解的引擎树,以及一些有益的
信息发现知识,以便用户快速找到想要的信息。
SET对原始数据进行一系
列数据挖掘处理后,能够提取出其中模式分析的信息,从而实现快速、高
效的引擎。
3.最大期望聚类:
原理:最大期望聚类(Maximization Expectation Clustering,MEC)是一种有效的数据挖掘算法,它可以自动识别出潜在的类簇结构,提取出
类簇内部的模式,帮助用户快速完成类簇分析任务。
纹理物体缺陷的视觉检测算法研究--优秀毕业论文

摘 要
在竞争激烈的工业自动化生产过程中,机器视觉对产品质量的把关起着举足 轻重的作用,机器视觉在缺陷检测技术方面的应用也逐渐普遍起来。与常规的检 测技术相比,自动化的视觉检测系统更加经济、快捷、高效与 安全。纹理物体在 工业生产中广泛存在,像用于半导体装配和封装底板和发光二极管,现代 化电子 系统中的印制电路板,以及纺织行业中的布匹和织物等都可认为是含有纹理特征 的物体。本论文主要致力于纹理物体的缺陷检测技术研究,为纹理物体的自动化 检测提供高效而可靠的检测算法。 纹理是描述图像内容的重要特征,纹理分析也已经被成功的应用与纹理分割 和纹理分类当中。本研究提出了一种基于纹理分析技术和参考比较方式的缺陷检 测算法。这种算法能容忍物体变形引起的图像配准误差,对纹理的影响也具有鲁 棒性。本算法旨在为检测出的缺陷区域提供丰富而重要的物理意义,如缺陷区域 的大小、形状、亮度对比度及空间分布等。同时,在参考图像可行的情况下,本 算法可用于同质纹理物体和非同质纹理物体的检测,对非纹理物体 的检测也可取 得不错的效果。 在整个检测过程中,我们采用了可调控金字塔的纹理分析和重构技术。与传 统的小波纹理分析技术不同,我们在小波域中加入处理物体变形和纹理影响的容 忍度控制算法,来实现容忍物体变形和对纹理影响鲁棒的目的。最后可调控金字 塔的重构保证了缺陷区域物理意义恢复的准确性。实验阶段,我们检测了一系列 具有实际应用价值的图像。实验结果表明 本文提出的纹理物体缺陷检测算法具有 高效性和易于实现性。 关键字: 缺陷检测;纹理;物体变形;可调控金字塔;重构
Keywords: defect detection, texture, object distortion, steerable pyramid, reconstruction
II
CA Application Delivery Analysis Multi-Port Monito

第 2 章: 已知问题
39
权限设置限制 ............................................................................................................................................................ 39 在打开了另一个浏览器窗口或选项卡的情况下,导出到 PDF 失败。 ................................................................39
第 1 章: 欢迎使用版本 10.1 5
此版本中的新增功能
此版本中的新增功能
Multi-Port Monitor 版本 10.1 提供以下功能和增强功能:
全新 CA6300 硬件设备 ■ 全新 CA6300 设备现提供 MTP 版本 10.1。通过支持更大数量的 SPAN
数据、更快的处理器速度、更大的系统阵列和数据阵列磁盘空间以及 实现 RAID 6 从而提升数据阵列可靠性并为智能平台管理接口 (IPMI) 提供内置支持,CA6300 可提供更为优异的性能。有关 CA6300 设备的 规格,请参见《安装指南》。 ■ 通过使用适用于 CA6300 设备的 IPMI 功能,不但能远程控制和重新启 动设备,还可为发送环境警报提供支持;其中,此类警报涉及影响 CA6300 运行状况的电源、温度、风扇及其他项目。
监视端到端的性能,以度量应用程序响应时间。 ■ 来自完全 HTTP 数据包的数据可以帮助 CA APM 映射环境中的事务,
以便监视最终用户体验并度量服务水平协议。 Multi-Port Monitor 通过被动监视多个端口的大量通信量,帮助您维持稳 定的端到端系统性能记录。 这些《版本说明》提供了有关版本 10.1 中增强功能和已知问题的信息。 这些信息是对产品文档中所列信息的补充,甚至可以取代后者。
详解面向对象编程的基本概念和原则

详解面向对象编程的基本概念和原则面向对象编程(Object-Oriented Programming,简称OOP)是一种常用的编程范式,它的基本概念和原则对于程序员来说非常重要。
本文将详细解释面向对象编程的基本概念和原则,帮助读者更好地理解和应用这一编程方法。
一、封装性(Encapsulation)封装性是面向对象编程的基本特征之一。
它指的是将数据和操作数据的方法封装在一个类中,通过访问控制来保护数据的安全性。
封装性的优势在于隐藏了类的内部实现细节,使得类的使用者只需要关注类的接口,而不需要关心具体的实现细节。
这样可以提高代码的可维护性和可复用性。
二、继承性(Inheritance)继承性是面向对象编程的另一个重要特征。
它指的是一个类可以派生出子类,子类可以继承父类的属性和方法。
通过继承,子类可以拥有父类的所有成员,并且可以在此基础上进行扩展和修改。
继承性的优势在于可以减少代码的重复性,提高代码的可维护性和可扩展性。
三、多态性(Polymorphism)多态性是面向对象编程的核心概念之一。
它指的是同一方法在不同的对象上可以有不同的实现。
多态性的优势在于可以通过统一的接口来处理不同类型的对象,提高代码的灵活性和可扩展性。
在面向对象编程中,多态性通常通过接口和抽象类来实现。
四、抽象性(Abstraction)抽象性是面向对象编程的另一个重要特征。
它指的是将对象的共同特征提取出来,形成抽象类或接口。
抽象类定义了一组共同的属性和方法,而接口定义了一组共同的方法。
通过抽象性,可以将对象的共同特征进行统一管理,提高代码的可维护性和可扩展性。
面向对象编程的基本原则:1. 单一职责原则(Single Responsibility Principle,SRP):一个类应该只有一个引起它变化的原因。
这意味着一个类应该只负责一项职责,避免一个类承担过多的责任。
2. 开放封闭原则(Open-Closed Principle,OCP):一个类应该对扩展开放,对修改封闭。
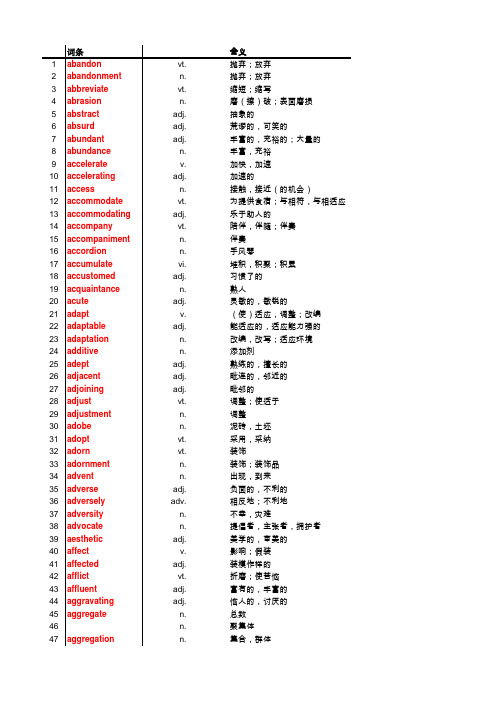
老俞词汇
49alchemy n.炼金术50alder n.赤杨树51algae n.海藻52alien adj.相异的;陌生的53all but词组+ adj. 几乎…54all inclusive词组无所不包的55allocate vt.分配56alloy n.合金57alternative adj.另一可选的,另外的58altitude n.高度59ambience n.周围环境,气氛60amenable adj.顺从的;应服从的61amplify vt.放大;扩大;增强62ancestor n.祖先,祖宗63annihilate vt.消灭;消减64annual adj.每年的65annually adv.一年一次,每年66anomaly n.异常,不规则;异常的人或物67anonymous adj.匿名的68antibiotic adj.抗菌的,抗生的69antiquate vt.使古旧,废弃70antiquated adj.陈旧的,过时的71antiquity n.古迹;古物72apart from词组除…之外73appeal n.吸引力74apprentice n.学徒75approach n.方法76aptly adv.适当地,得体地77arc n.弧形,拱形78archaeology n.考古学79archaeological adj.考古学的80archipelago n.群岛81architect n.建筑师82arduous adj.费力的,艰难的83arena n.竞技场,舞台84arid adj.干旱的;贫瘠的85armor n.装甲;装甲车86aromatic adj.芬芳的87array n.展示,陈列;一系列88arthritis n.关节炎89artificial adj.人造的,人工的90artisan n.手工业工人,手艺人91as far as词组就...来说;远及92as such词组就象这样做,就本身而论93as a rule词组通常,总的来说94as a rule of thumb词组大概来说95ascend vt.(渐渐)上升,升高;攀登96ascent n.攀登,上升97aspiring adj.有抱负的,有理想的,积极向上的98assemble vt.集合,装配99assert vt.声称,坚持100associate v.关联,联合101assorted adj.各式各样的,多样混合的102assortment n.各类物品的聚集,混合物103assume vt.假定,设想104assumption n.假设;就职105assure vt.确保;向…保证,使确信106astonishing adj.惊人的,奇迹的107astounding adj.令人吃惊的108astute adj.机敏的,精明的109at intervals词组不时;相隔一段距离110at one session词组一下子,一次性111at the cuttingedge of词组在…的关键时刻/状态/位置112atomization n.原子化;雾化113attachment n.依恋,喜欢114attach vt.系,缚115attached adj.附加的,附属的116attain vt.达到,获得117attainment n.成就118attire n.穿着,服饰(正规服装的总称)119auditorium n.大礼堂120auger n.螺丝钻,钻孔机121aurora n.极光=auroral light122automated adj.自动的123available adj.自由的,有空的124aviation n.航空;航空学125avocational adj.副业的,嗜好的126awareness n.意识127awkwardly adv.(见到生人)局促不安地,笨拙地128backdrop n.舞台背景;背景129ballet n.芭蕾舞130balmy adj.芳香的;(空气)温和的131barb n.(鱼钩等的)倒钩;倒刺132barbed wire词组带倒钩的铁丝(铁丝网)133barge n.驳船134bark n.树皮135barn n.谷仓;畜棚136barren adj.贫瘠的;荒凉的137barrier n.屏障,障碍;栅栏138barter n./v.物品交换,易货贸易139basement n.地下室140basin n.盆;盆地141be taken by词组被迷住,被吓住142be up to词组由…做;胜任,从事于143beam n.大梁144bequest n.遗产;遗赠145besiege vt.围攻;困扰146bestow vt.给与,赐赠147bias n.偏见,偏好148bitterness n.苦味;辛酸,苦难149bizarre adj.奇异的,古怪的150blanket n.毯子;厚的遮盖物151blast vi.爆破152blazing adj.炽烧的;闪耀的153bleak adj.荒凉的;凄凉的154blend vt.混合,掺混155blessing n.祝福,恩赐156block n.一块(木头或石头等)157blossom n./vi.花/开花158blues n.抑郁,沮丧;布鲁斯音乐159bluff n.悬崖,绝壁;v.诈骗,吓唬160blunt adj.直言不讳的161bolster n.垫子,枕垫162boom n.繁荣163boon n.恩惠,恩赐164boost vt.增加,提高,促进165boring adj.令人厌烦的166boundary n.分界线,边界167bow n.弓;弓形168breach vt.打破,突破169break all ties with词组与…断绝一切关系170breeze n.微风171brittle adj.易碎的172bronze n.青铜;铜像173bubble n.气泡,水泡174buckle n.皮带扣环175buggy n.小马车,童车176building block词组积木177bulk n.大批;大部分178bundle n.捆,束,包179burdensome adj.繁重的,劳累的180burgeon vi.迅速成长,发展181burrow n.洞穴182bust n.半身像,半身雕像183bustle n.喧闹,匆匆忙忙184by a factor of词组翻…倍185by far词组迄今为止186cab n.出租马车、汽车187the Cabinet n.内阁 cabinet n. 橱柜188cacti n.(pl)仙人掌-单数cactus189calibration n.校准;标度,刻度190campaign n.(政治或商业性)活动,竞选活动191cannibalism n.同类相食192canopy n.天篷,遮篷193canyon n.峡谷194capability n.能力195capacity n.容量;能力196carbohydrate n.碳水化合物197cardiac adj.心脏的198cargo n.货物199carnival n.狂欢节200carnivorous adj.食肉的201carving n.雕刻品,雕花202cast vt.浇铸203casting n.铸件,铸造204cast off词组丢弃,摆脱205category n.种类,类目;范畴206cater vi.满足需要,迎合207cathedral n.总教堂,大教堂208cavern n.大山洞,大洞穴209cavity n.洞;腔210cease v.停止,终止211celestial adj.天体的;天上的212cell n.细胞,单人牢房,电池213cellist n.大提琴家214census n.人口调查,人口普查215ceremonial n.仪式216ceremony n.典礼,仪式;礼节217chafe vt.(将皮肤等)擦热,擦破218chamber n.室;房间219chaos n.混乱220be characterized by词组以…为特征,典型代表221charcoal n.炭;木炭222charter v.包租;特许223chateau n.城堡,高级旅馆224check vt.检查,核对;阻止,控制225chill vt.使冷,变冷;冷却226chilly adj.寒冷的227chimpanzee n.黑猩猩228chisel n.凿子229chivalry n.骑士气概,侠义;(男人)对女人彬彬有礼,献殷勤230chop vt.砍231choppy adj.波浪起伏的,(风)不断改变方向的232chord n.琴弦,心弦233chunk n.大块;矮胖的人或物234circulate v.(使)循环;(使)传播235circulation n.循环;流通236circumscribe vt.划界限;限制237cite vt.引用,举例238civility n.彬彬有礼,斯文239civilian adj.平民的;民用的240claim n.要求,要求权241clam n.蛤,蛤肉242clamor n.叫嚣,喧哗243clan n.家族,宗族244classify vt.把…分类,分等级245classification n.分类,分级246clay n.粘土;泥土247cliff n.悬崖峭壁248clockwise adj./adv.顺时针方向的(地)249clumsy adj.笨拙的;愚笨的250cluster n.簇,串,群251code of laws词组法典252coexist vi.同时存在,共存253cohesion n.附着(力),凝聚力254cohesive adj.粘着的255coil n.(一)卷;线圈256coincide vi.同时发生;相符合,相巧合257coincident adj.一致的,巧合的258collaboration n.合作259collective adj.集体的,共同的260collide vi.碰撞;冲突261colossal adj.巨大的262combustible adj.易燃的263combustion n.燃烧264comet n.彗星265commission vt.委任,任命;委托,委托制作266committed adj.效忠的;忠于…的267commodity n.商品,日用品268commonsense adj.具有常识的269communal adj.公共的;公社的270community n.社区;社会271commuter n.经常往返者272compact adj.紧凑的,紧密的;简洁的273companion n.同伴,同事274comparable adj.可比的,比得上的;类似的275compatible adj.可以并存的,相容的,协调的276compel vt.强迫,使不得不277compensation n.补偿,赔偿278competitiveness n.竞争能力279competing adj.有竞争性的,不相上下的280compile vt.汇集,编辑281complacence n.自满,自以为是282complement vt.补充,使完善283complementary adj.补充的,补足的284complex adj.复杂的,费解的;结构复杂的285complicated adj.费解的,棘手的;结构复杂的286comply with词组遵从,符合287component n.成分,组成部分288be composed of词组由…组成289composition n.构成,组成290compound n.化合物291compress vt.压缩,浓缩292comprise vt.包含;由…组成293conceal vt.隐藏,隐瞒294concede v.承认295conceive vt.构思;设想296conception n.观念,认识297concerted adj.商议好的,协定的298concise adj.简洁的,简明的299concrete n.水泥300condensation n.压缩,浓缩301condor n.秃鹰302conductivity n.导电率;传导率303confederacy n.联盟304configuration n.轮廓,构型305confinement n.限制,禁闭306confirm vt.证实,使…更坚定307conflict n.争论,冲突,斗争308conflicting adj.相冲突的,相矛盾的309confront vt.面对,正视310congenial adj.合得来的;适意的311congestion n.拥挤,拥塞312congregate v.聚集313consecutive adj.连续的314consequence n.结果,后果315conservative adj.保守的,谨慎的;守旧的316conserve vt.保存,保藏 n.可长期保存的食物317conservation n.保存,保持318conspiracy n.阴谋,共谋319constant adj.不变的,持续的;一再重复的320constantly adv.不断地321constellation n.星座322constituent n.成分,要素323constitution n.组织;宪法324constitute vt.建立(政府),组成,构成325constitutional adj.宪法的;章程的326constrain vt.限制,约束327constraint n.限制,约束328constrict vt.约束;收缩329constricted adj.抑制的,约束的330construction n.建筑,建造331consumption n.消耗,消费332contact vt.使接触,与…联系333container n.容器;集装箱334contemporary adj.当代的,现代的335context n.上下文,语境336contour n.contours 轮廓337contraction n.缩短,收缩338contractor n.定约人,承包人339contribute to词组有助于,对…起作用340convention n.会议;传统341conventional adj.传统的,习俗的342conventionally adv.按照惯例地,照常套地343converge vi.聚合,集中于一点,会聚344convert vt.转换;转变信仰345converter n.炼钢转炉346convict vt.证明…有罪,宣告…有罪347convincing adj.令人信服的348convinced adj.确信的,深信的349convivial adj.欢乐的,快乐的350coral reef词组珊瑚礁=corals351core n.中心,核心;地核352correlate vt.使相互关联;使相互影响353correlated adj.有相互关系的354corrosion n.腐蚀,侵蚀355corruption n.腐败,贪污,堕落356cosmic adj.宇宙的357costume n.服装358counteract vt.消除,抵消359counterbalance v.使平衡360counterclockwise adj./adv.逆时针的(地)361counterpart n.相似的人或物,配对物362cowhand n.牛仔,牧牛工363crab n.蟹364crack n.裂缝,裂纹;缺点365craft n.手艺;容器366craftspeople n.手工艺人367crater n.火山口;弹坑368crawl vi.爬,爬行369crayon n.彩色蜡笔、粉笔或其绘画370credence n.信任,相信371creditor n.债权人372crevice n.缺口,裂缝373cripple vt.削弱;使残废374crippling adj.令人震惊的375crisscross vi.交叉往来376crossbones n.十字骨头377crossbreeding n.(生物)杂种378crow n.乌鸦379crude adj.粗糙的,粗鲁的;原始的380crumple vt.把…弄皱;起皱381crust n.硬外皮;地壳382crustacean n.甲壳动物383crystalline adj.水晶的,透明的384crystallize v.明确;使结晶化385crystallized adj.变成晶体的386cubism n.立体主义387cue n.提示,暗示388culminate v.达到高潮/顶点389cumbersome adj.笨重的,难处理的390curator n.(博物馆等)馆长391curriculum n.学校的全部课程392custodian n.看守人,管理人393cuticle n.表皮394cylinder n.圆筒,圆柱体395dash off词组水猛冲;感情爆发396daunting adj.使人畏缩的397dawn n.黎明;开端,开始398dazzling adj.眼花缭乱的;耀眼的399debate n.争论,辩论400debris n.废墟,残骸;碎片401declaration n.宣布,宣言402decline vi./n.衰退;下降,减退403decorate vt.装饰,装潢,修饰404decoration n.装饰,装饰品405decorative adj.装饰的,可作装饰的406defecate vi.排粪;通大便407deferential adj.恭敬的, 恭顺的408deference n.尊重,顺从;敬意409deficiency n.缺乏;不足410deform vt.使变形411deformation n.损坏,变形412deft adj.灵巧的,熟练的413degrade v.使降级,贬低414degradation n.退化;降级,降格415dehydrate vt.使脱水416dehydrated adj.干燥的,脱水的417deliberate adj.故意的,早有准备的418delicate adj.脆的,易损的;娇弱的419delta n.三角洲420demobilize vt.遣散,使复员421demolish vt.破坏,摧毁422dense adj.密集的,浓厚的423density n.密度424depict vt.描绘;描写,描述425deplete vt.耗尽,使衰竭426deposit vt.堆积,沉淀427depredation n.劫掠,蹂躏428depression n.不景气,萧条期429deprive vt.剥夺,使失去430derive vt.得到,获取;源于431desalination n.脱盐,去盐作用432descend v.传下,遗传433descendant n.子孙,后裔434descent n.血统,世袭435designate vt.指定,任命436desirable adj.令人向往的;令人满意的437desperate adj.绝望的,不顾一切的,拼死的438despoiler n.掠夺者439destruction n.破坏;毁灭440detect vt.察觉,发觉;探测,侦查441detectable adj.可发觉的;可查明的442deter vt.阻碍,制止,使踌躇443deterrent n.制止物,威慑力量444deteriorate v.使恶化;质量下降445determinant n.决定因素446devastate vt.毁坏447devastation n.毁坏448devour vt.贪婪地吃,吞食449diagonal n./adj.对角线(的)450diagonally adv.成对角线地,斜对地451diameter n.直径452dictate vt.规定;决定,确定453diction n.措辞,用语454differentiate v.区分,区别455diffuse v.扩散;散播456digest vt.消化457digression n.离题,扯到枝节上458diminish v.(使)减少,(使)变小459discard vt.丢弃460discern vt.看出;察觉到461discernible adj.可识别的=discernable462discharge vt.释放;排出463n.流出464n.放电465discipline n.纪律,训练466discouraging adj.令人气馁的467discourse n.讲道,演讲468discrete adj.独立的;不连续的,离散的469disintegrate v.(使)瓦解,(使)碎裂470dispense vt.分配,分发471disperse vt.分散,散开472disposal n.垃圾倾倒;处置473dispute n.争论,纠纷474disrepute n.坏名声,不光彩475disseminate vt.传播,宣传476dissipate vi.消失;消散477dissipated adj.沉迷于酒色的, 浪荡的478dissolve vt.使溶解479distend vt./vi.(使)扩大,(使)扩张480distent adj.膨胀的,扩张的481distinction n.差别,特性482distinct adj.明确的,确实的;不同的483distinctly adv.清楚地,显然484distinctive adj.有特色的,出众的485distinctively adv.特殊地,区别地486distort vt.弄歪(形状等);歪曲487distract vt.使…分心,分散注意力488distribute vt.分配;分发,散布489distribution n.分发,分配490diver n.潜水者,跳水运动员491divergence n.分歧,岔开492diverse adj.不同的;变化多的493diversity n.差异,多样494diversified adj.多样化的495diversification n.多样化496diversion n.消遣,娱乐497documentation n.文件498dogma n.教条,教义499dolphin n.海豚500domain n.领域,范围501domestic adj.家里的;家养的502dominant adj.支配的,占优势的503dominate vt.统治,支配,控制504dormant adj.静止的,休眠的505dorsal adj.背部的,背脊的506draft animal词组役用动物507drain v.(使)流走,(使)排光508dramatically adv.戏剧性地;引人注目地509drawback n.弊端,缺点510drill vt.钻孔,打眼511drought n.干旱512ductile adj.易延展的;柔软的513dump vt.倾泻,倾倒514durable adj.持久的;耐用的515dwarf n.侏儒516eccentricity n.反常,怪癖517eclipse n.日蚀,月蚀518ecological adj.生态的;生态学的519economize vi.节约,节省520ecosystem n.生态系统521edentate n.贫齿类动物522edible adj.可食用的523edifice n.宏伟的建筑物524educable adj.可教育的,可培养的525eject vt.喷出,喷射526elaborate adj.精细的,精心的;详尽的527elaborately adv.精细地,详尽地528elegance n.高雅, 典雅, 优雅, 雅致529elevation n.高度,海拔530elicit vt.得出;引出531eligible adj.合格的,有资格的532eliminate vt.排除,剔除533elixir n.长生不老药,万能药534elliptical adj.椭圆的535elusive adj.难懂的,难捉摸的536embed vt.插入;镶嵌537embellish vt.装饰,修饰538emboss v.加浮雕花纹于,使凸出539embryological adj.胚胎学的540emerge vi.出现,浮现541emerging adj.正在不断出现的542emergence n.出现,形成543emigrant n.移民(出国)544emission n.散发;发射545emit vt.发出,放射546employ vt.用,使用547enactment n.设定,制定548encounter vt.遭遇,遇到549engraving n.雕刻术, 雕版, 雕版图550enormous adj.极大的,庞大的551enterprise n.事业,企业552enterprising adj.有进取心的,有事业心的,有魄力的553entrepreneur n.企业家,创业人554enzyme n.酶555epidermis n.表皮556epoch n.新纪元,时代557equilibrium n.平衡,均衡558equivalent n.等同品559erect vt.使树立;建立,创立560erode v.腐蚀,侵蚀561erosion n.腐蚀,侵蚀562eruption n.爆发,喷发563eternal adj.永恒的;永远的564ethically adv.在伦理上,道德上565ethnic adj.种族的566evaporate v.(使)蒸发;消失567eventful adj.多事的,充满大事的;意义重大的568evergreen adj.常绿的569evident adj.明显的570eviscerate vt.取出内脏;除去主要部分571evoke vt.引起,激起,唤起572exalted adj.崇高的,高贵的573excavation n.挖掘574exceed vt.超越,胜过575excel vi.胜过,杰出576exceptional adj.异常的,杰出的577exceptionally adv.特殊地;异常地578excess adj.过度的,额外的579excessive adj.过度的,过分的,过多的580exclusion n.排除,逐出581exclusive adj.单独的,唯一的;排外的582execution n.实施,执行;完成583exempt vt.使免除,豁免584exert vt.运用,行使,施加585exhale vt.呼出,呼气586exhibition n.展览会;展览品587exorbitant adj.(价格、索价)过高的,过分的588expansion n.扩张,发展589expenditure n.支出, 花费590expertise n.专门技术,技能591explicit adj.明确的,清楚的592exploit vt.开拓;开采,开发593exponential adj.指数的,幂数的594express business词组特快专递业务595express train词组特快列车596expressive adj.有表现力的,富有表情的,生动的597extend v.延长;扩大598extended adj.延长的,扩大的599extensive adj.广的;多方面的,广泛的600external adj.外部的;表面的601extinct adj.灭绝的;不再活跃的,熄灭的602extinction n.消失,灭绝603extract vt.拔出;榨取604fabric n.织物,布605facilitate vt.使容易;有助于,促进606facilitation n.促进,帮助607facility n.设施,设备608faction n.派别,宗派,小集团609factor n.因素;变量610faculty n.教职工的总称611fade vi.逐渐消失612famine n.饥荒,饥饿613fanatical adj.狂热的;入迷的614fascination n.入迷,迷恋;魅力615fashionable adj.流行的,时髦的,上流社会的616fatal adj.致命的617fatigue n.疲乏,劳累618faucet n.水龙头619fauna n.动物群,动物区系620flora n.植物群621feasible adj.切实可行的622feat n.功绩,壮举623feed on词组吃,以…为食624fencing n.围墙,栅栏;击剑,剑术625fend for oneself词组自己谋生626fertile adj.肥沃的,富饶的;能繁殖的627fertilize vt.施肥,使丰饶;使受精628fertilized egg词组受精卵629festival n.节日630feverish adj.发烧的631fiber n.纤维,光纤632fiction n.小说,(虚构)故事633fidelity n.忠实,忠诚634field research词组野外实地考察635figurehead n.装饰船头的雕像, 破浪神, 有名无实的领袖636file n.档案637fir n.杉木638flair n.才能,本领639flake v.使成薄片;雪片般落下640flea n.跳蚤641fleeting adj.短暂的,飞逝的642flexible adj.易弯曲的,柔软的;变通的643flexibility n.灵活性644float v.漂浮,使漂浮645flock n.(畜、禽)群,大量646flock to词组成群结队地去647fluctuation n.波动,起伏648flux n.变迁;涨潮649folklore n.民间传说650follow suit词组跟着做651folly n.愚笨,愚蠢,荒唐事652forage v.搜寻(食物)653forbidding adj.可怕的,令人难以亲近的,令人生畏的654foremost adj.最重要的;最先的655foresee vt.预见,预知656foreshadow vt.成为先兆,预示657formalized adj.形式化的,使程序化的658format n.模式,格式659formation n.形成,构成660formidable adj.令人敬畏的,可怕的661formulate vt.系统地阐述(或提出)662fort n.要塞,堡垒663fortify vt.加强,巩固664fortuitous adj.偶然的,意外的665fortuitously adv.偶然地,意外地666fossilize vt.使成化石667fossilized adj.变成化石的668foster vt.鼓励,促进669fracture n.骨折;破裂670fragile adj.易碎的,脆的;脆弱的671fragility n.脆弱672fragment n.碎片,破片673fray vi.磨损,磨破674freight n.货物,货运675frenetic adj.狂乱的,发狂的676frenzy n.狂暴;狂怒677frigid adj.寒冷的678fringe n.边缘;边界679from a far词组从遥远的地方680frustrate v.挫败,破坏681frustration n.挫败,挫折682frustrating adj.令人沮丧胆683fumigate vt.烟熏;用香薰684functioning n.运转,操作685fungi n.(fungus的复数)真菌686furnish vt.装备;提供687fusion n.核聚变688galaxy n.星系;银河689gallery n.画廊,美术馆690galvanize vt.通电流于;刺激,激起691gap n.裂口;缺口692gaseous adj.气体的,气态的693generate vt.造成,产生694generous adj.慷慨的695genetic adj.遗传的,起源的696genetically adv.遗传上697genial adj.和蔼可亲的698genre n.文学上的流派和体裁699genuine adj.真正的,真实的;真诚的700get in the way of词组阻挡701giant n.巨人,巨大的怪物702girder n.钢结构大梁703give way to词组让步,让路704glacial adj.冰的,冰河的;冰冷的705glacier n.冰川706glamorous adj.迷人的,富有魅力的707gland n.腺体708glandular adj.腺体的709glassware n.玻璃制品710glimpse n.一瞥,一看711global adj.全球性的712go broke词组破产713gorgeous adj.华丽的;灿烂的714gourmet n.美食家715graphic adj.绘画似的;图解的,生动的716grasshopper n.蚱蜢,蚂蚱717gravitational adj.地心引力的,重力的718gravity n.地心引力719graze vi.(牲畜)吃草;放牧720grazing land词组牧场,草场721grumble n./v.抱怨722gulf n.海湾723gush vi.喷涌,涌流724gymnastic adj.体操的,体育的725habitat n.产地,栖息地726hail n.冰雹727hallmark n.标志,特征728halt n./vt.(使)停止729hamper vt.妨碍,使困难730handicraft n.手工艺品731hands-on亲手抓的732harden v.使变硬733hardware n.五金制品734harness vt.利用(河流、瀑布等)产生动力735haste n.匆忙,急忙;草率736hatch vt.孵化737haunt vt.(思想、回忆等)萦绕心头738haunted adj.闹鬼的,鬼魂出没的,受到折磨的739haven n.避难所,安全地740hazard n.危险;危害物741heed n./v.注意,留意742heel n.脚后跟743helium n.氦744hem n.(衣服或裙子)褶边,边缘745hemisphere n.半球;半脑746herald vt.宣布…的消息;预示…的来临747herculean adj.力大无比的, 巨大的748herd n.兽群;人群749heritage n.遗产,继承物;传统750heterogeneous adj.异类的,不同的751hibernation n.冬眠752hierarchy n.阶层,等级制度753highlight vt.使显著,突出754hinge n.(门等)铰链,枢纽755hinterland n.穷乡僻壤;腹地756hold a large stake词组拥有巨额股份,带有极大冒险性757hollow adj.空心的,凹陷的758homogeneous adj.同类的;均匀的,同质的759horizon n.地平线;眼界,视野760horizontal adj.水平的761hostile adj.敌对的,不友好的762huddle vi.缩成一团;挤成一团763hummingbird n.蜂鸟764hurl vt.用力投掷765hydrogen n.氢766hypersensitive adj.高灵敏度的;感觉过敏的767hypothesis n.假设,假说768iceberg n.冰山769ice sheet词组冰层770icicle n.冰柱,冰垂771icon n.圣像,偶像772identical adj.同一的;完全相同的773identify vt.识别,认出;鉴定774identifiable adj.可辨认的775identity n.身份776ideology n.意识形态777idiom n.方言,土语;习惯用语778igneous adj.(地理)火的,火成的779illuminate v.照明,照亮780illumination n.照明;启发781illusion n.幻觉;错觉782illustrate vt.(用图或例子)说明,阐明783imaginative adj.富于想象力的784imaginary adj.想象中的,虚构的785imbibe v.吸;吸收786imitation n.模仿;仿制品787immense adj.巨大的;无边的788immobilize vt.使不动,使固定789immune adj.(对…)免疫的,不受影响的790immunity n.免疫,免疫性791impact n.影响792impair vt.损害,使弱793impart vt.传授;传递,传达794impediment n.妨碍,阻碍(物)795imperative adj.必要的;强制的796impermeable adj.不可渗透的;不透水的797impersonal adj.不受个人感情支配的,客观的,无私的798impersonate vt.模仿,扮演799impersonation n.模仿,扮演800impetus n.推动力;激励物801implement n.工具,器具802implication n.暗示,意义803implicit adj.不明确的,含蓄的804impose vt.把…强加于;施加影响805imposing adj.使人难忘的, 壮丽的806impressive adj.给人深刻印象的;威严的807imprint n.印痕,痕迹;深刻的印象808imprisonment n.监禁809improvise vt.即席创作,即兴表演810improvision n.即席创作811in accord with词组与…一致812in common词组共有,有共同之处813in scale词组相称,成比例814in terms of词组根据;就…而论815inaccessible adj.难达到的,不可及的;不能得到的816inactivate vt.使…不活跃817inadequate adj.不充分的,不适当的818inappropriate adj.不适当的,不相称的819incapacitate vt.使失去能力;使不胜任820incessant adj.不停的,连续的821incident n.事件822inclination n.嗜好,倾向823incongruity n.不一致,不和谐824incongruous adj.不协调的,不一致的825incorpoarate vt.合并,并入;包含826incredible adj.难以置信的,惊人的827indent vt.切割成锯齿状828indicate vt.指示,指出;象征,表明829indispensable adj.不可缺少的,必需的830individualism n.个人主义831inducible adj.可诱导的832industrialization n.工业化833industrialized vt.工业化的834inevitably adv.不可避免地,必然地835inextricably adv.无法摆脱地836infection n.传染(病)837inferiority n.自卑感838infest vt.骚扰,大批滋生839inflation n.通货膨胀840inflict vt.造成;(使)遭受(痛苦、损伤等) 841influx n.流入,汇集842ingenious adj.机灵的,有独创性的843ingeniously adv.天才地,独创地844ingredient n.配料,成份845inhabit vt.居住于,栖息于846inhabitant n.居民,住户847inherit vt.继承848inhibit vt.抑制;阻止849innumerable adj.无数的,数不清的850insanity n.精神错乱,疯狂851insight n.洞察力,见识852insistence n.坚持853inspection n.检查,细看854inspire vt.鼓舞;给…以灵感855inspiration n.灵感856instantaneous adj.瞬间的,即刻的857instinctive adj.天生的,本能的858instinctively adv.本能地;凭直觉地859institution n.机构;惯例860institutionalize v.使制度化861instructive adj.有益的;教育性的862instrumentalist n.器乐家,器乐演奏者863insulation n.绝缘;隔离;孤立864insulting adj.侮辱性的,欺负人的865insurmountable adj.不能克服的,不能超越的866intact adj.尚未被人碰到的,完整的867integral adj.整体的;构成整体所需的868integrate vt.使成为整体,使一体化869integrated adj.整合的,一体化的870intelligible adj.明了的,可理解的871intense adj.强烈的,剧烈的872intensive adj.加强的;集中的,密集的873interaction n.相互作用874interact vi.互相作用,互相影响875interconnected adj.相互连接的876interconnecting adj.相互连接的877interdependence n.互相依赖878interdependent adj.相互依赖的,互助的879interference n.冲突;干涉880interior n./adj.内部(的)881interlocking adj.连锁的,关联的882interpersonal adj.人与人之间的;关于人与人之间关系的883interpretation n.解释884interrupt vt.打断,使中断885interstellar adj.星际的886interval n.间隔时间887intervention n.干涉,介入888intimacy n.亲密,熟悉889intoxication n.陶醉,醉酒890intricate adj.复杂的,错综的891intricately adv.杂乱地892intriguing adj.吸引人的,引起兴趣(或好奇心)的893intrinsic adj.固有的,内在的894intrusion n.侵扰,干扰895intruder n.入侵者,闯入者896intruding adj.入侵性的897invade vt.侵略,侵犯898inventory n.存货清单;库存品899invertebrate n./adj.无脊椎动物(的)900ion n.离子901irresistible adj.无法抗拒的,无法抵抗的;诱人的902irreverent adj.不敬的903irreverence n.不敬;不敬的行为904irreversible adj.不可改变的;不可撤销的905irrevocable adj.不能取消的906irrigate vt.灌溉907irrigation n.灌溉908isolated adj.与世隔绝的,偏僻的;孤独的909isolation n.隔离;孤立910jealousy n.妒忌,羡慕911jellyfish n.水母912jibe with词组与…一致913jolting adj.令人震惊的914journalism n.新闻业, 报章杂志915junction n.连接;汇合处916jury n.陪审团917juxtaposition n.毗邻,并置,并列918keen adj.(感觉、观察、理解等)敏锐的,敏捷的919kennel n.狗舍,狗窝920kernel n.仁,核心;(去壳的)麦粒,谷粒921kerosene n.煤油922kinetic adj.运动的;动力学的923laborious adj.费力的,艰难的924labyrinth n.迷宫;错综复杂的事件925lament vt.为…悲痛,痛惜926landmass n.大片陆地927landscape n.风景,山水;风景画928landslide n.山崩929laser n.激光930latitude n.纬度,范围931lava n.熔岩,岩浆932lave vt.为沐浴, 洗933layer n.层,层次;阶层934layman n.俗人,犯人;外行935lease n.租约936ledge n.壁架, 架状突出物, 暗礁, 矿层937legacy n.遗产,遗物938legume n.豆类,豆荚939lengthen vt.延长,使变长940lettuce n.莴苣,生菜941light bulb词组灯泡942limestone n.石灰石943linger vi.逗留;徘徊944livelihood n.生计,谋生945living quarters词组住房,住处946locomote v.移动,行动947locomotion n.运动,移动948locomotive n.火车头949log n.圆木;航海日志;vt. 记录950long-range词组远程的951loom n.织布机952lore n.口头传说;学问,知识953lumber n.木材,木料954luminosity n.亮度,发光度955luminous adj.发光的;明亮的956lure vt.引诱,诱惑957lyric n.抒情诗;歌词958magnify vt.放大,扩大959magnitude n.大小,光度,重要960maize n.玉米961majestic adj.壮观的,庄严的962majority n.多数963makeup n.组成,结构964mallet n.槌棒965malleable adj.可锻的,可塑的,可延展的966malleability n.可锻性,可塑性,延展性967mammal n.哺乳动物968mammoth n.猛犸象969maneuver vt.(敏捷地)操纵;(用策略)调动970mania n.狂热971manifestation n.表现,显示972manipulate vt.操作;操纵,利用973mansion n.大厦;公寓974mantle n.地幔;覆盖物975margin n.边缘;余地976marine adj.海的,航海的,海产的977maritime adj.海上的,海事的978markedly adv.显著地,明显地979marrow cavity n.骨髓腔980mask n.面具981masonry n.石工术;石匠职业982massive adj.大而重的,庞大的;可观的983masterpiece n.杰作,名著984mate v.结伴,成配偶985meager adj.缺乏的,不足的986measures n.措施,方法987mechanical adj.机械的;机械性的,呆板的988mechanism n.机械;机理,运作机制989media n.媒体990medium n.媒体,媒介;方法991memorial n.纪念物992mercantile adj.商业的,贸易的993merchandise n.商品994metabolic adj.新陈代谢的995meteorite n.陨星,陨石996meteorologist n.气象学者997meticulous adj.一丝不苟的,过细的998metropolitan adj.主要都市的,大城市的999microorganism n.微生物1000microscope n.显微镜1001microscopic adj.用显微镜可见的;极小的1002microwave n.微波(炉)1003migrate vi.移动,迁徙1004migration n.定期迁移;迁居1005milestone n.里程碑;划时代的事件1006millennia n.一千年,千禧年1007mimetic adj.模仿的,(生物)拟态的1008mingle v.(使)混合1009mingling adj.混合的1010miniature adj.微型的,缩小的1011minimize v.最小化,减到最小1012minuscule adj.极小的1013minute adj.微小的1014miraculous adj.奇迹的,不可思议的1015mobility n.流动性;灵活性1016mock v.(模仿性的)嘲笑1017modify vt.修改,变更1018moisture n.潮湿,湿气;湿度1019molecule n.分子1020molecular adj.分子的1021molten adj.熔融的,熔化的1022monochromatic adj.单色的,一色的1023monopolize vt.独占,垄断1024monument n.纪念碑;纪念物1025morale n.士气1026morphololgy n.形态学,形态论1027motif n.(作品)主题,主旨1028motivation n.动机,刺激1029mud mortar词组灰泥浆1030multi-faceted adj.多方面的;多才多艺的1031multiple adj.多样的,多重的1032multiply v.繁殖,增加1033multistory n.多层建筑1034multitude n.大量,多数1035mundane adj.世俗的,平凡的1036municipal adj.市的,市政的1037muscular adj.强壮的,肌肉发达的1038myriad n.许多,无数1039mysterious adj.神秘的1040myth n.神话,神话故事1041mythology n.(总称)神话1042narcotic adj.麻醉的,催眠的;n. 麻醉剂1043narrator n.讲述者1044native to词组土生土长的1045neat adj.整洁的;整齐的1046needy adj.贫穷的,生活艰辛的1047neoclassical adj.新古典主义的1048neon n.[化]氖;霓虹灯1049nerve cord词组脊髓1050spinal cord词组脊髓1051neuron n.神经元,神经细胞1052neutron n.中子1053niche n.壁龛1054nickel n.镍;镍币1055nonconformist adj./n.不遵照传统生活的(人)1056nontraditional adj不遵照传统生活的1057nostalgia n.思家病,怀旧1058not…so much as…词组与其…还不如…1059not as yet词组迄今为止,还没有1060notch n.刻痕1061note n.音符1062notorious adj.臭名昭著的,声名狼藉的1063notoriously adv.声名狼藉地1064noxious adj.有害的,有毒的1065nuclei n.核子;核心1066nucleus n.合子,核心1067object to词组反对1068obscure vt.隐藏,使…模糊1069obsessed adj.心神不宁的,鬼迷心窍的,沉迷的1070obstacle n.障碍1071occurrence n.事件;发生1072of scale词组大规模的1073offshore adj.离岸的, 海面上的1074offspring n.子孙,后代1075olfactory adj.嗅觉的1076onset n.开始1077onslaught n.冲击;猛攻1078opaque adj.不透明的;晦涩难懂的1079optical adj.视觉的;光学的1080optimal adj.最佳的,最理想的1081optimum adj.最适宜的1082orchid n.兰花1083ore n.矿石1084organically adv.器官上地, 有机地,有组织地1085organism n.生物,有机物1086orientation n.定向;介绍性指导1087originality n.创意,新奇1088originate vt.发生;发起,创办1089ornament n.装饰;装饰物1090ornamentation n.装饰;装饰品1091ornamental adj.装饰的1092ounce n.盎司1093outbreak n.发作;爆发1094outlet n.(河流、烟等)出口1095output n.输出,产品;生产量1096oval adj.卵形的,椭圆的1097overlap vt.部分重叠,与…交搭,迭盖1098overlapping adj./n.交迭(的)1099overload vt.使超载,使超过负荷1100oversee vt.监督,管理1101overtax vt.课税过重1102overwhelm vt.战胜;压倒1103overwhelmingly adv.压倒性地;不可抵抗地1104pack vt.装;将…挤入,塞满1105packed adj.压紧的,压实的1106painstaking adj.辛苦的,辛勤的1107pane n.窗格玻璃1108panel n.镶板1109panic n.恐慌1110pants n.裤子;短裤1111paralysis n.瘫痪,中风1112paramount adj.最重要的;最高权力的1113paraphrase vt.将…释义,改写1114parasite n.寄生虫,食客1115particle n.颗粒,微粒1116pasture n.牧场,草地1117patent n.专利1118pathogen n.病菌,病原体1119patrol v.巡逻,巡视1120patron n.赞助人,资助人1121patronage n.赞助;惠顾1122pebble n.小鹅卵石1123peculiarity n.特性,怪癖1124pendant n.垂饰;下垂物1125penetrate vt.穿透;渗透1126penetrating adj.(声音)响亮的,尖锐的1127peninsula n.半岛1128perceive vt.感知;察觉,发觉1129perception n.理解;感知,感觉1130percussion n.打击乐器;震荡,影响1131peripheral adj.周边的,外围的1132perishable adj.(尤指食物)易腐的,易坏的1133permeate vt.弥漫;渗透,透过1134perpetuate vt.使…延续,使永存1135perplexing adj.使人困惑的;令人费解的1136persist vi.坚持;持续1137perspective n.(判断事物的)角度,方法,观点1138pertinent adj.相关的,切题的;中肯的1139pest n.害虫;令人讨厌的人或物1140petal n.花瓣1141pigment n.色素,颜料1142pillow n.枕头1143pine n.松树1144pit n.坑,地坑;煤矿1145pivotal adj.枢轴的,关键的1146a pivotal figure词组关键人物1147plank n.厚木板1148plaster n.灰泥,石膏1149plate n.盘子;版图;大片平面1150platitude n.陈词滥调1151pliable adj.易弯的,柔软的1152plight n.(恶劣的)情势,困境1153plumbing n.(供水)管道系统1154polarize vt.使极化,使两极分化1155pollination n.授粉1156pollen n.花粉1157pollinator n.传粉媒介,传粉昆虫1158pollutant n.污染物质1159popular tune词组流行歌曲1160portable adj.编携的,手提的;轻便的1161portend vt.预兆,预示1162portion n.一部分;部分1163positive adj.(电)阳极的1164possess vt.拥有,占有1165possession n.拥有,占有;财产1166postal service词组邮政服务1167postdate vt.填迟…的日期1168antedate vt.填早...的日期。
CCF推荐国际学术期刊

CCF 推荐国际学术期刊中国计算机学会推荐国际学术期刊 (计算机系统与⾼性能计算)⼀、A类⼆、B类三、C类中国计算机学会推荐国际学术刊物(计算机⽹络)⼀、A类序号刊物简称刊物全称出版社⽹址1TOCS ACM Transactions on Computer Systems ACM 2TOC IEEE Transactions on ComputersIEEE 3TPDSIEEE Transactions on Parallel and Distributed SystemsIEEE序号刊物简称刊物全称出版社⽹址1TACO ACM Transactions on Architecture and Code OptimizationACM 2TAAS ACM Transactions on Autonomous and Adaptive SystemsACM 3TODAES ACM Transactions on Design Automation of Electronic SystemsACM 4TECS ACM Transactions on Embedded Computing Systemsn ACM 5TRETS ACM Transactions on Reconfigurable Technology and SystemsACM 6TOS ACM Transactions on StorageACM 7TCAD IEEE Transactions on COMPUTER-AIDED DESIGN of Integrated Circuits and Systems IEEE 8TVLSI IEEE Transactions on VLSI SystemsIEEE 9JPDC Journal of Parallel and Distributed Computing Elsevier 10 PARCOParallel ComputingElsevier 11Performance Evaluation: An International JournalElsevier序号刊物简称刊物全称出版社⽹址1 Concurrency and Computation: Practice and Experience Wiley 2DC Distributed ComputingSpringer 3FGCS Future Generation Computer Systems Elsevier 4Integration Integration, the VLSI JournalElsevier 5 JSA The Journal of Systems Architecture: Embedded Software DesignElsevier 6 Microprocessors and Microsystems: Embedded Hardware DesignElsevier 7JGC The Journal of Grid computing Springer 8TJSC The Journal of SupercomputingSpringer 9JETC The ACM Journal on Emerging Technologies in Computing SystemsACM 10JETJournal of Electronic Testing-Theory and ApplicationsSpringer序号刊物简称刊物全称出版社⽹址⼆、B类三、C类中国计算机学会推荐国际学术刊物 (⽹络与信息安全)⼀、A类⼆、B类1TON IEEE/ACM Transactions on NetworkingIEEE, ACM 2JSAC IEEE Journal of Selected Areas in Communications IEEE 3TMCIEEE Transactions on Mobile ComputingIEEE序号刊物简称刊物全称出版社⽹址1TOIT ACM Transactions on Internet Technology ACM 2TOMCCAP ACM Transactions on Multimedia Computing, Communications and Applications ACM 3TOSN ACM Transactions on Sensor Networks ACM 4CN Computer NetworksElsevier 5TOC IEEE Transactions on CommunicationsIEEE 6TWCIEEE Transactions on Wireless CommunicationsIEEE序号刊物简称刊物全称出版社⽹址1 Ad hoc NetworksElsevier 2CC Computer CommunicationsElsevier 3TNSM IEEE Transactions on Network and Service Management IEEE 4 IET CommunicationsIET 5JNCA Journal of Network and Computer Applications Elsevier 6MONETMobile Networks & Applications Springer 7 NetworksWiley 8PPNA Peer-to-Peer Networking and Applications Springer 9WCMC Wireless Communications & Mobile Computing Wiley.10Wireless NetworksSpringer序号刊物简称刊物全称出版社⽹址1TDSC IEEE Transactions on Dependable and Secure Computing IEEE 2TIFS IEEE Transactions on Information Forensics and Security IEEE 3Journal of CryptologySpringer序号刊物简称刊物全称出版社⽹址1TISSEC ACM Transactions on Information and System SecurityACM 2 Computers & SecurityElsevier 3 Designs, Codes and Cryptography Springer 4JCSJournal of Computer SecurityIOS Press三、C类中国计算机学会推荐国际学术刊物 (软件⼯程、系统软件与程序设计语⾔)⼀、A类⼆、B类三、C类序号刊物简称刊物全称出版社⽹址1CLSR Computer Law and Security Reports Elsevier 2 EURASIP Journal on Information Security Springer 3 IET Information SecurityIET 4IMCS Information Management & Computer Security Emerald 5ISTR Information Security Technical Report Elsevier 6IJISP International Journal of Information Security and PrivacyIdea GroupInc 7IJICS International Journal of Information and Computer SecurityInderscience8SCNSecurity and Communication NetworksWiley序号刊物简称刊物全称出版社⽹址1TOPLAS ACM Transactions on Programming Languages &SystemsACM 2TOSEM ACM Transactions on Software Engineering MethodologyACM 3TSEIEEE Transactions on Software EngineeringIEEE序号刊物简称刊物全称出版社⽹址1ASE Automated Software Engineering Springer 2 Empirical Software EngineeringSpringer 3 TSC IEEE Transactions on Service Computing IEEE 4 IETS IET SoftwareIET 5 IST Information and Software Technology Elsevier 6JFP Journal of Functional Programming Cambridge University Press7 Journal of Software: Evolution and Process Wiley 8JSS Journal of Systems and Software Elsevier 9RE Requirements Engineering Springer 10SCP Science of Computer Programming Elsevier 11SoSyM Software and System Modeling Springer 12SPE Software: Practice and ExperienceWiley 13STVRSoftware Testing, Verification and ReliabilityWiley序号刊物简称刊物全称出版社⽹址1 Computer Languages, Systems and Structures Elsevier 2IJSEKEInternational Journal on Software Engineering and Knowledge EngineeringWorld Scientific中国计算机学会推荐国际学术刊物 (数据库、数据挖掘与内容检索)⼀、A类⼆、B类三、C类3STTT International Journal on Software Tools for Technology TransferSpringer 4 Journal of Logic and Algebraic Programming Elsevier 5JWE Journal of Web EngineeringRinton Press 6 Service Oriented Computing and Applications Springer 7 SQJ Software Quality JournalSpringer 8TPLPTheory and Practice of Logic ProgrammingCambridge University Press序号刊物简称刊物全称出版社⽹址1TODS ACM Transactions on Database Systems ACM 2TOIS ACM Transactions on Information and SystemsACM 3TKDE IEEE Transactions on Knowledge and Data Engineering IEEE Computer Society 4VLDBJVLDB JournalSpringer-Verlag序号刊物简称刊物全称出版社⽹址1TKDD ACM Transactions on Knowledge Discovery from DataACM 2AEI Advanced Engineering Informatics Elsevier 3DKE Data and Knowledge Engineering Elsevier 4DMKD Data Mining and Knowledge Discovery Springer 5EJIS European Journal of Information Systems The OR Society6 GeoInformaticaSpringer 7IPM Information Processing and Management Elsevier 8 Information Sciences Elsevier 9ISInformation SystemsElsevier 10JASISTJournal of the American Society for Information Science and TechnologyAmerican Society for Information Science and Technology 11JWS Journal of Web SemanticsElsevier 12KIS Knowledge and Information Systems Springer 13TWEBACM Transactions on the WebACM序号刊物简称刊物全称出版社⽹址1DPD Distributed and Parallel Databases Springer 2I&M Information and Management Elsevier 3IPL Information Processing Letters Elsevier 4Information RetrievalSpringer中国计算机学会推荐国际学术刊物 (计算机科学理论)⼀、A类⼆、B类三、C类5IJCIS International Journal of Cooperative Information SystemsWorld Scientific 6IJGIS International Journal of Geographical Information ScienceTaylor &Francis 7IJIS International Journal of Intelligent Systems Wiley 8IJKM International Journal of Knowledge ManagementIGI 9IJSWIS International Journal on Semantic Web and Information SystemsIGI 10JCIS Journal of Computer Information Systems IACIS 11JDM Journal of Database Management IGI-Global 12JGITM Journal of Global Information Technology ManagementIvy League Publishing 13JIIS Journal of Intelligent Information Systems Springer 14JSISJournal of Strategic Information SystemsElsevier序号刊物简称刊物全称出版社⽹址1IANDC Information and Computation Elsevier 2SICOMPSIAM Journal on ComputingSIAM序号刊物简称刊物全称出版社⽹址1TALG ACM Transactions on Algorithms ACM 2TOCL ACM Transactions on Computational LogicACM 3TOMS ACM Transactions on Mathematical Software ACM 4 AlgorithmicaSpringer 5 Computational complexity Springer 6FAC Formal Aspects of Computing Springer 7 Formal Methods in System Design Springer 8 INFORMS Journal on ComputingINFORMS 9JCSS Journal of Computer and System Sciences Elsevier 10JGO Journal of Global Optimization Springer 11 Journal of Symbolic ComputationElsevier 12MSCS Mathematical Structures in Computer Science Cambridge University Press 13TCSTheoretical Computer ScienceElsevier序号刊物简称刊物全称出版社⽹址1 Annals of Pure and Applied Logic Elsevier2 Acta InformaticaSpringer 3Discrete Applied MathematicsElsevier中国计算机学会推荐国际学术期刊 (计算机图形学与多媒体)⼀、A类⼆、B类三、C类4 Fundamenta Informaticae IOS Press5 Higher-Order and Symbolic ComputationSpringer 6Information Processing Letters Elsevier 7JCOMPLEXITY Journal of ComplexityElsevier 8LOGCOMJournal of Logic and Computation Oxford University Press 9 Journal of Symbolic LogicAssociation for Symbolic Logic10LMCS Logical Methods in Computer Science LMCS 11SIDMA SIAM Journal on Discrete Mathematics SIAM 12Theory of Computing SystemsSpringer序号刊物简称刊物全称出版社⽹址1TOG ACM Transactions on GraphicsACM 2TIP IEEE Transactions on Image ProcessingIEEE 3TVCGIEEE Transactions on Visualization and Computer GraphicsIEEE序号刊物简称刊物全称出版社⽹址1TOMCCAP ACM Transactions on Multimedia Computing,Communications and Application ACM 2CAD Computer-Aided DesignElsevier 3CAGD Computer Aided Geometric Design Elsevier 4CGF Computer Graphics Forum Wiley 5GM Graphical ModelsElsevier 6 TCSVT IEEE Transactions on Circuits and Systems for Video TechnologyIEEE 7TMM IEEE Transactions on Multimedia IEEE 8JASA Journal of The Acoustical Society of AmericaAIP 9SIIMS SIAM Journal on Imaging Sciences SIAM 10Speech ComSpeech CommunicationElsevier序号刊物简称刊物全称出版社⽹址1CAVW Computer Animation and Virtual Worlds Wiley 2C&G Computers & Graphics-UKElsevier 3CGTA Computational Geometry: Theory and ApplicationsElsevier 4DCG Discrete & Computational Geometry Springer 5 IET Image Processing IET 6IEEE Signal Processing LetterIEEE中国计算机学会推荐国际学术刊物 (⼈⼯智能与模式识别)⼀、A类⼆、B类7JVCIR Journal of Visual Communication and Image Representation Elsevier 8MS Multimedia SystemsSpringer 9MTA Multimedia Tools and Applications Springer 10 Signal ProcessingElsevier 11 Signal procesing:image communication Elsevier 12TVCThe Visual ComputerSpringer序号刊物简称刊物全称出版社⽹址1AI Artificial IntelligenceElsevier 2TPAMI IEEE Trans on Pattern Analysis and Machine IntelligenceIEEE 3IJCV International Journal of Computer Vision Springer 4JMLRJournal of Machine Learning ResearchMIT Press序号刊物简称刊物全称出版社⽹址1TAP ACM Transactions on Applied Perception ACM 2TSLP ACM Transactions on Speech and Language Processing ACM 3 Computational LinguisticsMIT Press 4CVIU Computer Vision and Image Understanding Elsevier 5DKE Data and Knowledge Engineering Elsevier 6 Evolutionary ComputationMIT Press 7TAC IEEE Transactions on Affective Computing IEEE 8TASLP IEEE Transactions on Audio, Speech, and Language ProcessingIEEE 9 IEEE Transactions on CyberneticsIEEE 10TEC IEEE Transactions on Evolutionary Computation IEEE 11TFS IEEE Transactions on Fuzzy Systems IEEE 12TNNLS IEEE Transactions on Neural Networks and learning systemsIEEE 13IJAR International Journal of Approximate Reasoning Elsevier 14JAIR Journal of AI ResearchAAAI 15Journal of Automated ReasoningSpringer 16JSLHRJournal of Speech, Language, and Hearing ResearchAmerican Speech-Language Hearing Association 17 Machine Learning Springer 18 Neural Computation MIT Press 19Neural NetworksElsevier三、C类20Pattern Recognition Elsevier序号刊物简称刊物全称出版社⽹址1TALIP ACM Transactions on Asian LanguageInformation ProcessingACM3Applied Intelligence Springer 4AIM Artificial Intelligence in Medicine Elsevier 5Artificial Life MIT Press6AAMAS Autonomous Agents and Multi-AgentSystemsSpringer7Computational Intelligence Wiley 8Computer Speech and Language Elsevier9Connection Science Taylor & Francis10DSS Decision Support Systems Elsevier 11EAAI Engineering Applications of Artificial Intelligence Elsevier 12Expert Systems Blackwell/Wiley 13ESWA Expert Systems with Applications Elsevier 14Fuzzy Sets and Systems Elsevier15T-CIAIGIEEE Transactions on Computational Intelligence andAI in GamesIEEE16IET Computer Vision IET 17IET Signal Processing IET 18IVC Image and Vision Computing Elsevier 19IDA Intelligent Data Analysis Elsevier20IJCIA International Journal of ComputationalIntelligence and ApplicationsWorldScientific21IJDAR International Journal on Document Analysisand RecognitionSpringer22IJIS International Journal of Intelligent Systems Wiley23IJNS International Journal of Neural SystemsWorld Scientific24IJPRAI International Journal of Pattern Recognitionand Artificial IntelligenceWorldScientific25International Journal of Uncertainty,Fuzziness and KBSWorldScientific26JETAI Journal of Experimental and TheoreticalArtificial IntelligenceTaylor &Francis27KBS Knowledge-Based Systems Elsevier 28Machine Translation Springer 29Machine Vision and Applications Springer 30Natural Computing Springer31NLE Natural Language Engineering Cambridge University32NCA Neural Computing & Applications Springer 33NPL Neural Processing Letters Springer中国计算机学会推荐国际学术期刊 (⼈机交互与普适计算)⼀、A类⼆、B类三、C类中国计算机学会推荐国际学术期刊 (前沿、交叉与综合)⼀、A类⼆、B类34 NeurocomputingElsevier 35PAA Pattern Analysis and Applications Springer 36PRL Pattern Recognition Letters Elsevier 37 Soft ComputingSpringer 38WIASWeb Intelligence and Agent SystemsIOS Press序号刊物简称刊物全称出版社⽹址1TOCHI ACM Transactions on Computer-Human Interaction ACM 2IJHCSInternational Journal of Human Computer StudiesElsevier序号刊物简称刊物全称出版社⽹址1CSCW Computer Supported Cooperative Work Springer 2HCI Human Computer Interaction Taylor & Francis 3IWC Interacting with ComputersOxford University Press4UMUAIUser Modeling and User-Adapted InteractionSpringer序号刊物简称刊物全称出版社⽹址1BIT Behaviour & Information TechnologyTaylor & Francis 2IJHCI International Journal of Human-Computer Interaction Taylor & Francis3PMC Pervasive and Mobile Computing Elsevier 4PUCPersonal and Ubiquitous ComputingSpringer序号刊物简称刊物全称出版社⽹址1Proc. IEEE Proceedings of the IEEE IEEE 2JACMJournal of the ACMACM序号刊物简称刊物全称出版社⽹址1 BioinformaticsOxford UniversityPress 2 Briefings in BioinformaticsOxford UniversityPress3CognitionCognition :International Journal of Cognitive ScienceElsevier 4 PLOS Computational BiologyPublic Library of Science5TMI IEEE Transactions on Medical Imaging IEEE 6TGARSIEEE Transactions on Geoscience and Remote SensingIEEEIEEE Transactions on Intelligent三、C类7TITS Transportation Systems IEEE 8TR IEEE Transactions on Robotics IEEE 9TASAE IEEE Transactions on Automation Science and Engineering IEEE 10JCST Journal of Computer Science and TechnologySCIENCE PRESS/Springer 11JAMIA Journal of the American Medical Informatics AssociationBMJ Journals 12 Science China Information Sciences Science in China Press/Springer 13The Computer JournalOxford UniversityPress序号刊物简称刊物全称出版社⽹址1 BMC BioinformaticsBioMed Central 2 Cybernetics and SystemsTaylor &Francis 3 IEEE Geoscience and Remote Sensing Letters IEEE 4TITB IEEE Transactions on Information Technology in BiomedicineIEEE 5TCBB IEEE-ACM Transactions on Computational Biology and BioinformaticsIEEE/ACM6 IET Intelligent Transport Systems IET7 Medical Image Analysis Elsevier 8FCSFrontiers of Computer ScienceHigher Education Press。
SPEARS 中国版《塑料管手册》说明书

Table of Contents
General Information .........................................................................................................1 Purpose of this Manual..................................................................................................1 Spears® PVC & CPVC Materials ..................................................................................1
Physical Properties of PVC & CPVC Pipe......................................................................2 Dimensions & Pressure Ratings.....................................................................................3
SPEARS® PLASTIC PIPE HANDBOOK
Plastic Pipe
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
The requirements that we formulated for concurrent object-oriented languages provide some guidelines for the design of languages and their mechanisms. However, a framework pro-viding a more rigorous formulation of the requirements and the evaluation of mechanisms would be extremely helpful for the development of better language designs. Our current research [11] is directed towards the development of such a framework as well as an improved version of Hy-brid.References[1]P. America, ‘‘POOL-T: A Parallel Object-Oriented Language,” in Object-Oriented Concurrent Program-ming, ed. A. Yonezawa, M. Tokoro, pp. 199-220, The MIT Press, Cambridge, Massachusetts, 1987.[2]G.R. Andrews and F.B. Schneider, ‘‘Concepts and Notations for Concurrent Programming,’’ ACM Comput-ing Surveys, vol. 15, no. 1, pp. 3-43, March 1983.[3]G.R. Andrews, R.A. Olsson and M. Coffin, ‘‘An Overview of the SR Language and Implementation,’’ ACMTOPLAS, vol. 10, no. 1, pp. 51-86, January 1988.[4] A. Bjornerstedt and S. Britts, ‘‘AVANCE: An Object Management System,’’ SIGPLAN Notices, vol. 23, no.11, pp. 206-221, ACM, san diego, November 1988.[5] A. Black, N. Hutchinson, E. Jul and H. Levy, ‘‘Object Structure in the Emerald System,’’ ACM SIGPLANNotices, Proceedings OOPSLA ’86, vol. 21, no. 11, pp. 78-86, Nov 1986.[6] C.A.R. Hoare, ‘‘Monitors : An Operating System Structuring Concept,’’ CACM, vol. 17, no. 10, pp. 549-557,ACM, October 1974.[7] D.G. Kafura and K.H. Lee,”Inheritance in Actor Based Concurrent Object-Oriented Languages,” in Proceed-ings of the Thrird European Conference on Object-Oriented Programming, Cambridge University Press, 1989.[8] D. Konstantas, O.M. Nierstrasz and M. Papathomas, ‘‘An Implementation of Hybrid,’’ in Active Object En-vironments Technical Report, Centre Universitaire d’Informatique, University of Geneva, ed. D. Tsichritzis, pp. 61-105, 1988.[9] B. Liskov, M. Herlihy and L. Gilbert, ‘‘Limitations of Synchronous Communication with Static ProcessStructure in Languages for Distributed Computing,’’ in Proceedings of the 13th ACM symposium on Princi-ples of Programming Languages, St. Petersburg, Florida, 1986.[10]J.E.B. Moss and W.H. Kohler, ‘‘Concurrency Features for the Trellis/Owl Language,’’ BIGRE, no. 54, pp.223-232, June 1987.[11]O. Nierstrasz, ‘‘Active Objects in Hybrid,’’ Object-Oriented Programming Systems Languages and Applica-tions (OOPSLA), Special Issue of SIGPLAN Notices, vol. 22, no. 12, pp. 243-253, Dec. 1987.[12]O. Nierstrasz and M. Papathomas,‘‘Viewing Objects as Patterns of Communicating Agents,’’ Object-Orient-ed Programming Systems Languages and Applications (OOPSLA), Oct. 1990. To appear. (also in this vol-ume)[13] M. Papathomas, ‘‘Concurrency Issues in Object-Oriented Languages,’’ in Object Oriented DevelopmentTechnical Report, Centre Universitaire d’Informatique, University of Geneva, ed. D. Tsichritzis, pp. 207-245, 1989.[14]P. Wegner, ‘‘Dimensions of Object-Based Language Design,’’ in Proceedings OOPSLA ’87, SIGPLAN No-tices, vol. 22, pp. 168-182, ACM, Orlando, Florida, December 1987.[15]Y. Yokote and M. Tokoro, ‘‘Concurrent Programming in ConcurrentSmalltalk,’’ in Object-Oriented Corcur-rent Programming, ed. M. Tokoro, pp. 129-158, The MIT press, Cambridge, Massachusetts, 1987.[16] A. Yonezawa, E. Shibayama, T. Takada and Y. Honda, ‘‘Modelling and Programming in an Object-OrientedConcurrent Language ABCL/1,’’ in Object-Oriented Corcurrent Programming, ed. M. Tokoro, pp. 55-89, The MIT Press, Cambridge, Massachusetts, 1987.are not interchangeable (unless the object and its clients are in different doamins) because of the use of delegated calls. It would not be possible to upgrade a sequential implementation of an ob-ject to a parallel one without affecting the clients of the object (unless it can be determined that the object to be upgrated is never in the same domain as its callers).7.3Scheduling RequestsThere are several cases where objects need to service requests in an order that is different from the order in which they arrive. The resource allocator, in section 5., showed that one reason for doing this is that it may not be possible to service a request at a certain point in time. For in-stance, when not enough resources are available, allocation requests may only be processed after deallocation requests despite their order of arrival. Another reason is that it may be more effi-cient to serve requests in a certain order. A disk head scheduler is a typical example. The possi-bility to service requests in an order that minimizes the disk head’s movements has substantial efficiency gains.The general solution for scheduling requests in Hybrid, presented in section 5.3, uses a combination of delay queues and delegated calls. Because of this, scheduling of requests is an implementation decision that may not, in general (only if the object is not in the same domain as its clients), be made transparently to an object’s clients.8.ConclusionHybrid served as a concrete example showing how some aspects in the design of a concurrent object-oriented language satisfy or fail to satisfy the requirements stated in section 3. The exam-ination of Hybrid’s features allows us to draw general conclusions about the design of concur-rent object-oriented languages and the integration of concurrency and object-oriented program-ming.The comparison of Hybrid’s active view of objects to other approaches showed that this ap-proach is the most suitable for object-oriented programming. It is the most appropriate for sup-porting encapsulation and data abstraction. Moreover, considering all objects as active server-like entities presents higher re-use potential than distinguishing among data and active objects and may be implemented at least as efficiently.The concurrency mechanisms of Hybrid are well suited for concurrent programming and more particularly for the client-server structure of object-oriented programs. However, in sec-tion 7, we presented examples that revealed some limitations in their support for data abstrac-tion. In particular, in order to correctly reuse objects it has to be known whether delegated calls are used in their implementation. Moreover, objects that are implemented by using delegated calls are not, in general, substitutable with those that do not, despite the fact that they may present the same interface and provide the same services to their clients.An important observation is that the limitations of Hybrid’s concurrency mechanisms for supporting data abstraction was demonstrated by bringing up the appropriate examples. Obtain-ing such examples for evaluating the design of a language is not always easy and sometimes only possible after the language has been implemented and used.exact way in which it is implemented. Furthermore, conforming to abstract typing, it should be possible to interchange objects with compatible interfaces and implementations.The delegated call mechanism of Hybrid fails to meet this requirement. It is not possible to substitute an object with one that uses delegated calls in its implementation, despite the fact that it has the same interface and provides the same services. Below, we first explain what in the se-mantics of the delegated call mechanism causes this problem. Then, we discuss two practical cases where, because of delegated calls, it is not possible to hide certain implementation choices from objects’ clients. These are the use of delegated calls for executing requests in parallel and for scheduling requests.7.1The Delegated Call ProblemWhen an object issues a delegated call its domain becomes idle a thread may then be triggered for processing a request addressed to any object in the domain. This has the effect that the exe-cution of a delegated call in an object may trigger the execution of a thread in another object in the domain.Consider an object A which calls a method of another object B which is in the same domain. If B issues a delegated call, it may trigger the execution of a method of another object in its do-main. In particular, the delegated call may trigger the execution of another method of A. This causes an interleaved execution of A’s methods since the method that invoked B in the first place is not yet completed. This interleaved execution of A’s methods, which occurs in points that are not controlled by A but by objects that are called by it, may cause the execution of A’s method to fail. There is no guarantee that a class invariant, which is a necessary precondition for the cor-rect execution of A’s methods, holds when A calls B or any other object in the same domain that performs a delegated call.This problem may be circumvented by an appropriate implementation of A that takes into account the fact that delegated calls are used in B. It is possible to implement A in such a way that the class invariant is satisfied before calling B’s methods or to prevent the activation of other A’s methods by using delay queues or by having A and B be in separate domains.These solutions may be inconvenient and rely on the fact that it is known that B’s implementation uses delegated calls. This is contrary to data abstraction, since it is necessary to know how an object is imple-mented in order to construct correct programs. Furthermore, it is not possible to safely replace the implementation of an object that didn’t use delegated calls by one that does without re-ex-amining all the programs that were based on the old implementation.7.2Parallel Execution of RequestsAs only one thread at a time may be active in a Hybrid domain, the only way to implement ob-jects that process requests in parallel is by using several objects, each in a separate domain, that cooperate in order to realize the required functionality.In Hybrid, the administrator example, discussed in section 5.2, is a typical way of imple-menting an object that executes requests in parallel. However, such an implementation makes use of delegated calls. This means that two implementations of an object, the one sequential and the other parallel, with the object implemented as an administrator managing a set of workers,ing Domains and Activities For Coordinating ObjectsComputations often involve collections of cooperating objects. The correctness of the computa-tion is based on assertions that are made by an object about the state of another object.The con-current execution of objects may cause state changes that invalidate such assertions.Consider the following example. A resource allocator object manages a number of reusable resources. It has the methods: request, release and atHand which are used for requesting, releas-ing a number of resources and inquiring about the number of resources that are available. Re-quests made by objects for more than the currently available resources are delayed until enough resources are released. Assume that for the needs of some application, an object should not get suspended if its request may not be handled immediately. A way to handle this without modify-ing the allocator would be for the object to first find out whether enough resources are available by invoking the atHand method, and then invoke the request method. However, requests issued by concurrently executing objects may get processed in between. So because of concurrent ex-ecution the assertion made by the client that enough resources are available may be invalid by the time that request is executed by the allocator.The domain and activity concepts provide the possibility to coordinate the execution of ob-jects so that no interference may occur by their concurrent execution. Moreover, it is not re-quired for the objects to be coded in a special way or to modify them for achieving the desired synchronization. In the above example, it is enough for the allocator object and the client that shouldn’t wait to be in the same domain. In this case, the allocator may not accept requests from other activities while an activity is active within the domain. Thus, no other calls to request may be accepted by the allocator between the calls to atHand and request made by the client.The concepts of domain and activity are very useful when it is needed to coordinate the ex-ecution of a collection of objects. However, domains and activities present some limitations. The domains of objects are specified at the time they are created and cannot be changed during their lifetimes. In the allocator example presented above, once the allocator and the client are created in the same domain they will never be able to execute concurrently. This is overconstraining since there are cases where they could perfectly do so.We are investigating extensions of the domain and activity concepts that, while retaining their advantages, they would be more flexible and permit more parallelism. For instance, a use-ful extension would be to allow objects to join and leave domains dynamically. In the allocator example, the client would request the allocator to join its domain just for the execution of the method that calls atHand and request. After that, the allocator and client would be able to execute concurrently.7.Support For Data AbstractionIn our requirements for the concurrency constructs of object-oriented languages presented in section 3. we stated that the concurrency constructs should be compatible with and provide sup-port for data abstraction. In particular, it should be possible for clients of an object to ignore theThe main disadvantages of this approach are that the code of the administrator becomes rather complex and that the objects acting as workers have to be designed especially so that they may cooperate with the administrator. Concerning the latter, the replies to requests have to be returned by asynchronous messages that should contain some information allowing the admin-istrator to associate a reply to a request. This may be avoided by mechanisms such as Concur-rentSmalltalk’s CBoxes[15] or ABCL/1’s future type message passing[16]. With these mecha-nisms the objects that may be used as workers by the administrator do not have to be designed in any special way.Early reply is a technique that is used for simulating asynchronous message passing when it is not supported by the language. The main idea is that the administrator returns immediately to the client the identifier of another object which it should call for getting the result. This allows the administrator to accept requests from other clients before it has processed the first client’s request. The same technique can be used for the interaction of the administrator and workers so that the administrator is not blocked during the time that a worker processes a request.The main problem with this technique is that it requires a specific interaction protocol to be observed between objects. A client object must be prepared to cope with early reply by first ob-taining the identity of the object to call for getting the result of its request and then calling this object to effectively get hold of the result. Concerning clients, an object implemented following the administrator paradigm presents a different more complex interface than objects with a se-quential implementation. This is contrary to data abstraction and has the disadvantage that ob-jects implemented following the administrator paradigm cannot be used in the place of other ob-jects.Multi-Thread ObjectsThe dynamic creation of threads within objects for the execution of requests eliminates the prob-lems of explicitly multiplexing the single object thread among several requests. However, the concurrent execution of threads within the object presents synchronization problems due to their access to shared instance variables. If these threads are created dynamically whenever a method is invoked, it will be necessary to explicitly synchronize the execution of methods. Such an ap-proach is similar to the orthogonal approach, discussed in section 4., and provides limited sup-port for encapsulation, data abstraction and object reuse.The delegated call mechanism presented in section 5.2 provides a satisfactory compromise between the above alternatives. It avoids the problems due to the explicit multiplexing of the sin-gle object thread by using a separate thread for each request. Moreover, by providing more con-trol on the creation and concurrent execution of threads within objects it avoids the problems of the orthogonal view of objects. However, by requiring that only one thread be active within an object, this approach unnecessarily restricts concurrency in some cases. For instance, multiple requests that only read an object’s state cannot be processed in parallel.there is a delayed call. If not, the delay queue would remain open and the next call to suspend would not be delayed.5.4Comparison to Other Approaches5.4.1Local DelaysDelay queues combined with delegated calls, in the way presented in section 5.3, can handle any local delay. However, it would be more convenient if we were able to do it in a more compact and elegant way. Moreover, as we will show in section 7, this way of handling local delays does not combine well with data abstraction.Other alternatives for local delays are condition variables and selective acceptance of re-quests with guards, that may depend on method arguments, as in the programming language SR[3]. Condition variables are used in monitors[6]to suspend the execution of a monitor proce-dure. This may take place after testing a condition that may depend on both the object’s state and method arguments. Guards are boolean expressions that are associated with a method. Requests for invoking a method are accepted only when the associated guard is true.Delay queues resemble a restricted form of guard that tests whether the associated delay queue is open. The combination of delay queues and delegated calls used in section 5.3 resem-bles the use of condition variables in monitors.The easiest way in which delay queues can be extended in the current design and imple-mentation of Hybrid is by adding an operation “wait” to the delay queue type. This operation would suspend the invoking thread if a condition necessary for its execution is not satisfied. This is similar to the use of condition variables in monitors.5.4.2Remote DelaysThe issues concerning remote delays differ depending on whether or not the language supports single threaded objects. In the case where objects are single threaded or there is a fixed number of threads per object, the main issue is how to multiplex an object’s thread among several re-quests. In the case where a thread may be created for each request the problem is the synchroni-zation of threads within the object. We further discuss these issues below based on the adminis-trator example from section 5.2.Single Thread ObjectsWith single thread objects remote delays may be handled by using asynchronous message pass-ing or, in the case where asynchronous message passing is not supported, by a technique called early reply[9].With asynchronous message passing the administrator object issues requests to workers by asynchronous messages. This allows it to accept and process more client requests. The replies to the requests made to the workers are returned to the administrator by another asynchronous message. These messages identify the requests so that the administrator may associate the replies with the corresponding requests. The administrator should be programmed in such a way that it is able to accept new client requests as well as replies returned by workers.pass on the requested work by issuing a delegated callresult <- delegate(@workers[workerIndex].doIt(work));gather some statistics about workers based on resultreturn the result to the caller.return(result);}}The delegate(...) expression causes the executing thread to be suspended and the call mes-sage to be passed on to the selected worker. While the worker handles the call, another call may be accepted by the administrator. This call is handled by the implicit creation of a new thread. However, there may not be more than one active thread at a time within an object. Suspended threads are resumed after the delegated call has returned and there are no other active threads within the object.5.3Using Delegated Calls and Delay Queues for Local DelaysIn section 5.1 we mentioned that some local delays that cannot be handled by delay queues can be handled by combining delay queues and delegated calls.In order to suspend the execution of one of its methods, an object may issue a delegated call to another object. The delegated call causes the invoking thread to be suspended and the object is free to accept further requests. If the method invoked by the delegated call is associated with a closed delay queue, the suspended thread in the calling object is delayed until the execution of another method opens the delay queue. This causes the call to be accepted so that the delegated call may return.A typical object, used for suspending the execution of another object’s methods, would pro-vide two methods: suspend and resume implemented as follows:private{var suspendDelay: Delay; # This delay is initially closed so that callers are delayedsuspend():->; uses suspendDelay;{# Close the delay so that the next caller will be suspendedsuspendDelay.close();}resume(): ->;{suspendDelay.open();}}The delay queue suspendDelay is initially closed. An object willing to suspend the execu-tion of one of its methods issues a delegated call of the form: delegate(@secondObject.suspend()). This suspends the calling activity until a call to resume opens the delay queue. As suspend is called by a delegated call the calling object is free to accept further calls before the call to sus-pend returns. A call to resume opens the delay queue and so that the call to suspend may be pro-cessed and the invoking thread resumed. The resumed thread closes the delay queue so that the next call to suspend will also be delayed. This example assumes that resume is called only when...insert an itemif the buffer is now fullputDelay.close();getDelay.open();}}The delay queues getDelay and putDelay are used for avoiding the acceptance of get and put requests when the buffer is empty and full respectively. Initially the delay queue getDelay is closed so that no get requests are accepted and the delay putDelay is open so that put requests are accepted and items may be inserted in the buffer. When the method put is executed it opens the delay queue getDelay so that get requests may be accepted. The method g et determines whether the buffer is empty and then closes the getDelay delay queue. The method put closes the putDelay delay queue when the buffer is full.In the above example, whether a request will lead to a local delay is determined by the re-quested method and the local state of the object. However, there are cases where this information is not sufficient and it is also necessary to know the values of the method’s arguments. Such cas-es are dealt with in Hybrid by combining delay queues with the delegated call mechanism. In section 5.3, after we have introduced the delegated call mechanism, we will show how to handle more complex cases by a combination of delay queues and delegated calls.5.2Remote Delays With Delegated CallsThe delegated call mechanism is well suited for remote delays. When an object issues a delegat-ed call the executing thread is suspended. Another request may then be processed by another thread. A thread that was suspended because of a delegated call is resumed after the delegated call returns and there are no other active threads within the object.As an example illustrating the use of the delegated call mechanism, consider an object that operates as an administrator for a collection of worker objects. This object is acquainted with a collection of worker objects that it uses for servicing the requests made by clients. Remote de-lays occur when the administrator invokes a particular worker for doing the job. It would not make sense for the administrator to wait until the worker finishes the requested work. Instead, it should accept other requests and pass them on to other workers that would process them in par-allel. The use of the delegated call mechanism allows the administrator to switch its attention to another request while a call is passed on to a worker. The outline of the administrator is given below.type administrator: abstract {doWork(work: WorkType)-> resultType;} ;private{var workers: array[1..MAX] of oid of workerType;doWork(work: WorkType) -> resultType{var workerIndex: integer;var result : resultType;select the worker appropriate for this work,assign its index to workerIndex.structured as a collection of active modules acting as servers and clients. As this structure closely matches object-oriented programs we use these requirements for evaluating Hybrid’s concurren-cy features.The main requirement formulated in [9] is that when an activity becomes blocked within a module (object in the case of Hybrid) other activities should be able to proceed. They identify two common situations where an activity may get blocked: local delay and remote delay.Local delay is the situation where an object has to put aside a request because of the tem-porary unavailability of a resource. In such a case, the object should be able to set aside this re-quest and turn its attention to others. It would be wasteful for the object to be blocked on a re-quest while there are other requests that could be processed. Not being able to set aside a request that cannot be processed immediately may also cause unnecessary deadlocks. For instance, while being blocked because of the unavailability of a local resource, the object would be unable to accept requests that would made the resource available.Remote delay is the situation in which an activity is delayed within an object because of a call to another “lower level” server. The delay may be due to the communication delay, the time needed by the lower level server for handling the request or a local delay in the lower level serv-er. During this time further requests could be accepted and processed by the object.5.1Local Delays With Delay QueuesIn Hybrid, simple forms of local delay are handled easily with delay queues. The use of delay queues allows objects to avoid accepting a request that would lead to a local delay. An illustra-tion of the use of delay queues for simple cases of local delays is given below by the code outline of a bounded buffer.type boundedBuffer : abstract {init : ->;put : string ->; uses delay;get : -> string; uses delay;};private {var putDelay, getDelay: delay;var buffer: strarray;...init: ->;{...putDelay.open();getDelay.close();}get: -> string; uses getDelay;{...get an item.if the buffer is now emptygetDelay.close();putDelay.open();...}put: string ->; uses putDelay;{object determines whether its methods need to be synchronized. Based on this information, the compiler generates synchronization code only in methods of “concurrent” objects. Thus, no syn-chronization overhead takes place for executing the methods of “data” objects. In an homoge-neous approach all objects are of the same kind, so it may seem that synchronization code has to be generated in the methods of all objects.In Hybrid the synchronization takes place when objects are invoked, rather than by code generated within methods. The use of different kinds of references for objects makes it possible to synchronize only the invocations of objects whose methods may be invoked concurrently.The predefined object type, oid, is used for specifying a reference to an object. Oids may be passed around to other objects so that the methods of an object having an oid may be invoked concurrently. On the other hand, objects that are addressed by instance variable names are local to the enclosing object and are not known to other objects so their methods may not be invoked concurrently. As objects that are addressed by instance variable names may not be addressed by oids and inversely, only invocations through oids need to be synchronized.The use of the type oid is illustrated below in the definition of a type A with a method an-AMethod. Instances of this type have two instance variables, local and shared, for referencing two objects of a type B. The object stored in local may only be addressed through this name and thus it may not be known outside the scope of the containing object of type A. Variable shared stores an oid that is used to refer to another object of type B. The oid may be known to other objects, consequently invocations of objects addressed by oids, as @shared.aBMethod, are synchronized. No synchronization occurs when invoking methods of objects that are addressed by local names, as in local.aBMethod().type A: abstract {anAMethod: ->;} ;private{var local: B;var shared: oid of B;anAMethod: -> ;{...local.aBMethod(); @shared.aBMethod(); ..}}The approach taken in Hybrid for supporting a homogeneous view of objects is at least as efficient as an heterogeneous approach. The run-time overhead caused by synchronization just takes place for objects that may be shared by concurrent threads. Moreover, it may show some performance gains over the heterogeneous approach. This is because the performance of the het-erogeneous approach depends on the appropriate choice of object types that is made explicitly by programmers. An inappropriate choice of object types would cause unneeded run-time over-head.5.Threads, Communication and Synchronization PrimitivesLiskov et al. [9] have formulated concurrency requirements for evaluating the suitability of a combination of concurrency features for developing distributed programs. These programs are。
