Takwim PBS2013
The Reimplementation of the RRDP Transport Protocol

The Reimplementation of theRRDP Transport ProtocolC.McAvaney, J.Rough, G.Wickham,D.De Paoli{chrismc,ruffy,gjw,ddp}@.auSchool of Computing and MathematicsDeakin UniversityGeelong, Victoria, 3217AbstractThe RHODOS Reliable Datagram Protocol (RRDP) is an integral part of the RHODOS distributed operating system. The existing implementation of RRDP, after years of development, has begun to show inadequacies that are hindering the whole RHODOS system. This document describes what was the existing implementation of RRDP, the problems that existed, and reports on the reimplementation of the RRDP protocol. Minor modifications made to the actual protocol and the supporting infrastructure in the operating system are also described within.The Reimplementation of the RRDP Transport Protocol1 Introduction. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12 Overview of RHODOS Interprocess Communication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12.1 Message Delivery. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12.2 The RHODOS System Name (SName) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22.3 Berkeley Memory Buffers (MBufs). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22.4 Primitives . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32.4.1 The send() primitive. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32.4.2 The recv() primitive. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32.4.3 The call() primitive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .42.5 Remote Interprocess Communication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .42.6 The Roles of RHODOS Components in Remote Interprocess Communication . . . .62.6.1 The Microkernel. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62.6.2 IPCM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62.6.3 RRDP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .82.6.4 IP/Eth. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83 The RRDP Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83.1 RRDP Packet Structure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83.2 Packet Groups. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .103.3 Sending Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .113.4 Receiving Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .123.5 Resolution of Network Failures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .133.6 Unreliable RRDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .133.7 Protocol Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .134 Implementation Aspects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .144.1 Message Structures. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .144.2 Optimum Timeout Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .144.3 Removal of RRDP/IP header dependency. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .155 Performance Results. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .156 Conclusions and Future Work . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .167 Acknowledgements. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17 References. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17Page iiThe Reimplementation of the RRDP Transport Protocol 1 IntroductionDistributed operating systems aim to provide a transparent interface to a cluster of workstations connected together by a local area network. Crucial to this objective is the provision of a high-performance interprocess communications facility. The two components of this facility are the interprocess communication primitives and the supporting transport protocol for remote communication [Goscinski1991]. The reimplementation of the supporting transport protocol (RRDP) is the subject of this report.The previous implementation of RRDP lacked timeouts and hence full reliability. The delivery of messages would fail if the last packet of a group (Section 3.2) was lost or corrupted. Additionally, the resources used by the message would not be freed due to an impasse where the sender was waiting for an acknowledgement (where it would free the resources), and the receiver was waiting for the final packet to arrive before it would send the acknowledgement. Although implementing timeouts in RRDP should have been a trivial exercise, several race conditions existed that complicated the task somewhat. These race conditions had caused modifications to RRDP to be abandoned in the past, thus one of the objectives of this project was to eliminate these race conditions.The goals of this project were to introduce timeouts reliably to the protocol, minimising any changes to servers that interact with the RRDP server. Once completed, all race conditions were to have been eliminated in the RRDP server, allowing future improvements and fixes to be applied to the protocol without unnecessary complication.Section2 provides an overview of interprocess communication in RHODOS including the roles of RHODOS components in providing the interprocess communication service. Section3 describes the RRDP protocol including packet structures, the procedures used for transmitting and receiving messages, and handling of network failures. Important issues that were raised during the implementation of this project are presented in Section4. A comparison of the performance of the old and new implementations of RRDP is in Section5. Finally Section6 concludes this report and indicates future work to be done on RHODOS interprocess communication.2 Overview of RHODOS Interprocess CommunicationThis section describes the implementation of interprocess communication in the RHODOS operating system. The roles and responsibilities of the Microkernel, IPCM, RRDP and IP/Eth servers are discussed. Additionally, the structure and semantics of communication between these components is described.2.1 Message DeliveryAll messages in RHODOS are sent to a “port”, with any process allowed to have any number of ports to receive messages on. A port is a logical entity maintained by the Microkernel and has associated with it an “operation queue”. Messages are delivered to a port by being referenced by an operation structure (oper), which is stored in the operation queue. The oper contains the details about the message, such as the return port, a pointer to the message (stored in MBufs), and pointers to the Process Control Blocks (PCBs) of any processes with blocked operations on that port.Page 1The Reimplementation of the RRDP Transport Protocol Page 2Two models are used for message delivery. In the first model, the message is copiedinto buffers maintained by the Microkernel, in this case Berkeley MBufs [Leffler et al 1989].The message is then added to the destination port’s operation queue for retrieval by a matchingreceive. When a matching receive is invoked the message is copied from the MBufs into thedestination process’ memory, and the MBufs are freed. In cases where a matching receive hasalready been invoked on the destination port, a second model is used where the message iscopied directly from the sending process’ buffer to the destination process’ buffer, thuseliminating a copy operation. These mechanisms are discussed extensively in[Goscinski et al 1994a].2.2 The RHODOS System Name (SName)In order to differentiate between the different active ports across the whole distributedsystem, some form of identification (naming) is necessary. RHODOS’ naming structureconsists of three levels: user level, system level, and low level (physical) naming[Goscinski et al 1994b]. System names (SNames) are used to identify objects used at thesystem level, hence ports are identified by an SName. The structure of the SName is shown inBlock 1. The fields that uniquely describe a port are the origin (sn_origin), which identifies theworkstation where the port was created; and the object number (sn_object ) which differentiatesbetween ports created on the same workstation.2.3 Berkeley Memory Buffers (MBufs)The demands placed on memory management for interprocess communication arevery different to the demands from other parts of an operating system. The MBuf data structure(shown in Block 2) was designed to provide an efficient allocation and reclamation scheme forinterprocess communication systems [Leffler et al 1989].The advantage of MBufs is that data can be inserted or removed at the beginning of anMBuf by manipulating the value of the m_off variable, and can be appended or removed at theend of an MBuf by manipulating the value of the m_len variable. This is extremely usefulwhen used in network protocols, where manipulation of packet headers (and trailers) occursfrequently. MBufs are shared in RHODOS, used for the storage and passing of messagesbetween: the Microkernel; IPCM; RRDP; and IP/Eth.If the data structure that is to be stored in MBufs is larger than the data region in asingle MBuf, then several MBufs can be linked via the m_next field to hold the data structure.Block 1: The RHODOS System Name (SName)The Reimplementation of the RRDP Transport Protocol Page 3This is known as a “chain” of MBufs. Several chains can also be linked together using them_act field, form a linked list.The implementation of MBufs in RHODOS is not identical to that of Berkeley. Themost obvious change is the addition of the m_flags field, which used to indicate to the IP/Ethserver (Section 2.6.4) whether the MBufs holding a packet can be deleted once the packet istransmitted.2.4 PrimitivesThe first point of contact for all interprocess communication primitives in RHODOSis the Microkernel (Section 2.6.1), invoked by using the primitives described in this section.RHODOS provides two models of interprocess communication: message passing (send() andrecv()); and remote procedure calls (call(),recv(), and send()).2.4.1 The send() primitiveThe send() primitive (Block 3) is used to send a message from one process to another.It requires four arguments:•dest_port - the SName of the receiving (destination) port for the message;•return_port - the SName of a port where return messages can be sent;•send_args - a data structure holding the parameters of the send operation, such as thelocation of the user’s buffer, the length of that buffer, etc. Several of these structures can belinked together to issue a send operation using several buffers (termed a multibufferedsend);•send_results - a data structure that is populated with the results of the send operation such asthe total amount of data transmitted.2.4.2 The recv() primitiveThe recv() primitive (Block 4) is used to receive a message that has been delivered.The recv() primitive waits for a matching message to be delivered if necessary. It requires fourarguments:•dest_port- the SName of the destination port where the message is attached or will arrive;Block 2: The MBuf Data StructureThe Reimplementation of the RRDP Transport ProtocolBlock 3: The RHODOS send() Primitive•return_port - an SName structure that can optionally be used to place restrictions on the return port;•recv_args - a data structure holding the parameters of the receive operation, such as the location of the user’s buffer, the length of that buffer, etc. Several of these structures can be linked together to issue a receive operation using several buffers (termed a multibuffered receive);•recv_results - a data structure that is populated with the result of the receive operation such as the total amount of data received.Block 4: The RHODOS recv() Primitive2.4.3 The call() primitiveThe call() primitive (Block 5) is used to provide remote procedure calls. Although the call() primitive is an atomic system call, it is logically composed of a call to the send() primitive, followed by a call to the recv() primitive. The call() primitive requires four arguments:•dest_port - the SName of the destination port for the RPC (the process providing the service);•call_args - a data structure holding the parameters of the call operation, such as the location of the user’s buffers for both the request and response, the length of each of those buffers, etc. Several of these structures can be linked together to issue a multi-buffer request;•call_results - a data structure that is populated with the results of the call operation such as the total amount of data transmitted and received.2.5 Remote Interprocess CommunicationTwo paths are used for remote interprocess communication in RHODOS. In the default path, messages are transmitted reliably using the RRDP protocol. RRDP also provides an unreliable service (see Section 3.6) if the use of a reliable protocol is deemed to be too expensive. The second delivery mechanism involves the use of the “Fast Eth” protocol. Fast Page 4The Reimplementation of the RRDP Transport ProtocolBlock 5: The RHODOS call() PrimitiveEth is an extremely light weight (unreliable) protocol, located directly over the Ethernet layer. Due to its placement, the Fast Eth protocol can only be used for communications within a subnet. The Fast Eth protocol is not relevant to this report and will not be discussed any further.A process sends a message in RHODOS by invoking the send() primitive (Section2.4.1). If the destination port for a message is local, the message is delivered as described in Section 2.1. If the destination port is not local, then the message is forwarded to the IPCM for resolution. The IPCM first determines the destination for the message (see Section2.6.2), and then forwards the message to the RRDP server, along with the address of the workstation for the message to be sent to. The RRDP server transmits the message by splitting the message into packets, and forwarding the MBufs (Section2.3) holding the packets to the IP/Eth server. Finally the IP/Eth server transmits the packets on the network.Any RRDP packets arriving from the network (received by IP/Eth), are passed up to the RRDP server, which reconstructs the incoming message and forwards it to the local IPCM for delivery to the destination port. These mechanisms are depicted in Figure1. It is important to realise that the message is only copied once, either from the user’s buffer into MBufs during a send operation, or from MBufs into the user’s buffer during a receive operation. A message or packet is forwarded between servers by passing a pointer to the MBufs that hold the message/packet.Figure 1: Structure of Remote Interprocess Communication in RHODOSPage 5The Reimplementation of the RRDP Transport Protocol2.6 The Roles of RHODOS Components in Remote Interprocess CommunicationThe servers involved in providing remote IPC are described in this section. In particular, the roles of the Microkernel, IPCM and IP/Eth servers are presented. Communication between the RRDP server and other servers are also described. An overview of interactions with the RRDP server can be seen in Figure 2.2.6.1 The MicrokernelThe first point of contact for all RHODOS interprocess communication is the Microkernel (Section 2.4). When a new message is received, the Microkernel checks that the return port is valid (checks that it exists locally), and then determines whether or not the destination port exists locally. If the destination port is local, then the message is attached using the oper structure described in Section 2.1. If the destination port it is not local, the message is packed into MBufs (Section 2.3) and forwarded to the IPCM for resolution.Messages are packed into MBufs by the Microkernel in sequences such that they can be easily divided into separate chains equal to the length of the data part of an RRDP packet. This means that the Ethernet, IP, and RRDP packet headers (see Section 3.1) can be attached to the data without needing to move any data between MBufs to fully utilise a packet.When a message arrives at a destination workstation, the IPCM delivers the message by using the send() primitive. The IPCM’s call to send() is different to usual, in that the return port is not checked to see if it exists locally, and the message is stored in MBufs. This allows the IPCM to deliver messages from remote hosts, specifying a remote SName as the return port if necessary. The message is attached to the destination port using the oper structure described in Section 2.1. The Microkernel then attempts to pair the new message with any blocked receive operations.2.6.2 IPCMThe IPCM is responsible for the delivery of messages destined for ports that do not exist locally. The IPCM always receives messages in MBufs, either from the Microkernel for outgoing messages, or from the RRDP server for incoming messages. When a message arrives for remote delivery, the IPCM first sends the message to the workstation where the destination port was created (the port’s origin). If the port has not been migrated, then the port will exist on that workstation and the message is delivered.If the port has been migrated, the remote IPCM returns the message to the source IPCM, along with the workstation where the port currently exists. The source IPCM stores a mapping for the port for future messages, and the message is sent to the new workstation [De Paoli1996].To transmit an outgoing message, the IPCM forwards the message to the RRDP server, along with additional information identifying the source workstation of the message, the return (source) port and destination port origin and object numbers, and the quality of service required for delivery of the message. The RRDP server later returns an acknowledgement to the IPCM to indicate the success or failure of delivery of the message to the remote workstation.Page 6The Reimplementation of the RRDP Transport ProtocolPage 7The sending process invokes send() for a message destined to a remote port. The message is forwarded to the IPCM for resolution.The IPCM forwards the message to RRDP with the address where the message is to be sent.The RRDP server splits the message into packets and forwards the packets to IP/Eth for resolution.The IP/Eth server on the sending workstation sends the packets to the remote workstation, received by the remote IP/Eth server .The first group is forwarded to the remote RRDP , which returns an acknowledgement to the sending RRDP server.The second (and last) group of packets is sent to the remote workstation.The last group is forwarded to the remote RRDP server.The RRDP server returns an acknowledgement to the sending RRDP server and then forwards the reconstructed message to the IPCM.The message is forwarded to the receiving process.Sender IPCM RRDP IP/Eth IP/Eth RRDP IPCM Receiver Figure 2: Overview of Remote Interprocess Communication with RRDP in RHODOSThe Reimplementation of the RRDP Transport ProtocolPage 8The IPCM receives incoming messages from the RRDP server, along with theadditional information provided to RRDP by the source IPCM. The IPCM checks for the existence of the destination port on the local workstation, and if the port exists it forwards the message to the destination process using the send() primitive as discussed in Section 2.6.1. If the port does not exist locally, and has not existed locally and then been migrated to another workstation, the IPCM notifies the source IPCM that the destination port was invalid.2.6.3 RRDPThe RRDP server is responsible for delivering messages between workstations. This includes the division of messages into packets (although this is helped by the Microkernel as discussed in Section 2.6.1), reliable delivery of the packets to the remote workstation, and reconstruction of the original message on the remote workstation. RRDP is discussed in depth in Section 3.2.6.4 IP/EthThe IP/Eth server receives packets for transmission from the RRDP server, stored in chains of MBufs. The data in the first MBuf of each chain begins with the IP header for the outgoing packet, with the protocol number and destination address fields filled in by the RRDP server. The IP/Eth server populates the remaining fields of the IP address, attaches an Ethernet header, and queues the packet for transmission by the Ethernet device driver.Any RRDP packets that arrive from the network are packed into MBufs and forwarded to the RRDP server. The RRDP packets are identified by the protocol number field in the IP header (see Figure 3). The ICMP [Postel1981] and IGMP [Deering1989] protocols are also partially supported. All other packets addressed to the workstation are ignored.3 The RRDP ProtocolThe RRDP Protocol is a reliable datagram based transport protocol developed using the concept of a multidatagram protocol. RRDP was initially built upon UDP [Goscinski et al1990], but UDP has since been removed from the model. A datagram based, connectionless protocol was selected for its high performance and low setup overheads. This section presents a description of the implementation of the RRDP protocol.3.1 RRDP Packet StructureThe structure of RRDP packets, as with other network protocols, involves a header part and a data part. The header is shown in Figure 3. The Ethernet and IP protocols are well documented by other literature and will not be addressed here. The value of the protocol field in the IP header is given a value that is recognised by RHODOS workstations as the RRDP protocol. The value used in this field is unimportant, except it cannot be a protocol number used by any other workstations on the network.The RRDP header is composed of 13 fields (see Figure 3). The message number, source location,destination origin,destination object,source origin, and source object fields are supplied by the RHODOS Interprocess Communications Manager (IPCM). The DCM Message Number and DCM Origin fields are set by the Data Collection Manager [Wickham1997].The message number field uniquely identifies every outgoing message from a particular workstation. The message number is generated by a simple counter mechanism maintained by the IPCM. The source location field identifies the workstation that is currently transmitting a message. The destination origin and object fields are used to identify the destination port SName. The source origin andobject fields are used to identify the SName of the return port provided by the sending process.1The group number field is initially given the value of 0 and incremented before the transmission of a new group, hence the first group transmitted is group 1. The sequence bit field is initially set at the least significant bit, and left shifted once to identify each packet in the group. Each of these identifiers are then combined to form a “bitmap” of the packets that have arrived at the destination workstation. This bitmap is returned in the sequence bit field as part of the acknowledgement. The version field is reserved for future use. The quality of service field indicates whether a message is being transmitted reliably or not (see Section 3.6). The1.the format used for representing the IP header in this diagram was adapted from [T anenbaum 1996].Figure 3: RRDP Packet Header 1type of packetfield indicates whether a packet is a data packet, or acknowledgement packet. Finally, the padding field is used to align the data section to a 32-bit boundary.3.2 Packet GroupsThe original proposal for the RRDP protocol [Goscinski et al1989] was a stop-and-wait protocol where an acknowledgement was required for each packet transmitted. In an effort to reduce the number of acknowledgments in RRDP, a multidatagram approach was introduced, where several packets are transmitted before an acknowledgement is required (Figure 4).Figure 4: Multidatagram protocol with group size 4The number of packets transmitted in a group can be any value between 1 (which causes RRDP to revert to a stop-and-wait protocol) and 32. These limits are imposed by size of the sequence bit field of the RRDP header which is 32-bits. Figure 5 demonstrates the relation between group size and message turnaround time for message sizes varying from 10k to 100k, increasing by 10k increments.It can be seen that as group sizes are increased, minimal turn around times are reached for larger messages. Once the optimal value for a message size is reached, it remains much the same for the remaining group sizes. For example, a message size of 10k reaches an optimal reading at a group size of 9, whereas a message of 100k reaches its minimum value at a group size of approximately 29 packets.However, it was also found that the larger the group size, the higher the number of buffer overruns (missed packets) in the Ethernet handler. This problem can be attributed to the network congestion that is caused by releasing such a large number of packets in quick succession, and a lack of support for flow control to prevent this problem. There are two alternatives that can be used to reduce this problem: the size of the Ethernet handler’s receive buffer can be increased, or the group size can be reduced. However these alternatives do not resolve the lack of flow control that causes this problem, thus they are not solutions. Support for flow control is the subject of future research in RRDP.An arbitrary group size of 29 has been selected for its optimal time values up to a 100k message size, but no true optimal value will be able to be found until flow control is introduced to the protocol.3.3 Sending MessagesNew messages are received by the RRDP server from the IPCM in a single chain of MBufs. This chain is immediately separated into several smaller chains, each no longer than the maximum data payload length of an RRDP packet. This procedure is assisted by the way that the Microkernel packs a message into MBufs (discussed in Section 2.6.1).An entry is added into RRDP’s internal state tables, and the first group of packets is transmitted by passing chains of MBufs containing the packets to IP/Eth (see Section 2.6.4). The send state table entry (STE) is marked as waiting for an acknowledgement and RRDP continues to accept messages. If no acknowledgement arrives within a specified period, a timeout occurs and the packets of that group are retransmitted. The value of the timeout is currently set to an arbitrary value of 200ms, and is the subject of future research.Whenever a timeout occurs and packets are retransmitted, the timeout is reset to twice the value of previous setting, and after five timeouts it is decided that the message is undeliverable. If an acknowledgement does arrive, the timeout value is reset to the initial 200ms, and the process repeats.When an acknowledgement arrives and there are packets that haven’t been acknowledged as having arrived safely, those missing packets are immediately retransmitted。
J.Nanopart.Res.,2009,11,1513–Rheological behaviour of ethylene glycol-titanate nanotube nano

BRIEF COMMUNICATIONRheological behaviour of ethylene glycol-titanate nanotube nanofluidsHaisheng Chen ÆYulong Ding ÆAlexei Lapkin ÆXiaolei FanReceived:11July 2008/Accepted:4February 2009/Published online:26February 2009ÓSpringer Science+Business Media B.V.2009Abstract Experimental work has been performed on the rheological behaviour of ethylene glycol based nanofluids containing titanate nanotubes over 20–60°C and a particle mass concentration of 0–8%.It is found that the nanofluids show shear-thinning behaviour particularly at particle concentrations in excess of *2%.Temperature imposes a very strong effect on the rheological behaviour of the nanofluids with higher temperatures giving stronger shear thinning.For a given particle concentration,there exists a certain shear rate below which the viscosity increases with increasing temperature,whereas the reverse occurs above such a shear rate.The normalised high-shear viscosity with respect to the base liquid viscosity,however,is independent of temperature.Further analyses suggest that the temperature effects are due to the shear-dependence of the relative contributions to the viscosity of the Brownian diffusion and convection.The analyses also suggest that a combination of particle aggregation and particle shape effects is the mechanism for the observed high-shear rheological behaviour,which is also supported by the thermal conductivity measure-ments and analyses.Keywords Rheological behaviour ÁEthylene glycol ÁTitanate nanotube ÁNanofluid ÁThermal conductivityNanofluids are dilute suspensions of particles with at least one dimension smaller than about 100nm (Choi 1995).Such a type of materials can be regarded as functionalized colloids with special requirements of a low-particle loading,a high-thermal performance,favourable flow/rheolgocial behaviour,and a great physical and chemical stability over a wide range of process and solution chemistry conditions.Nano-fluids have been shown to be able to enhance heat transfer (Choi 1995;Wang and Mujumdar.2007),mass transfer (Krishnamurthy et al.2006),and wetting and spreading (Wasan and Nikolov 2003),and have been a hot topic of research over the past decade (Wang and Mujumdar 2007;Keblinski et al.2005).Most published studies have focused on the heat transfer behaviour including thermal conduction (Choi 1995;Wang et al.1999;Wang and Mujumdar 2007;Keblinski et al.2005;Eastman et al.2001;He et al.2007;Ding et al.2006),phase change (boiling)heat transfer (Das et al.2003;Pak and Cho 1998),and convective heat transfer (Wang and Mujumdar 2007;Keblinski et al.2005;He et al.2007;Ding et al.2006,Chen et al.2008;Prasher et al.2006a and Yang et al.2005).Only few studies have been devoted to the rheological behaviour ofH.Chen ÁY.Ding (&)Institute of Particle Science and Engineering,University of Leeds,Leeds,UK e-mail:y.ding@pkin ÁX.FanDepartment of Chemical Engineering,University of Bath,Bath,UKJ Nanopart Res (2009)11:1513–1520DOI 10.1007/s11051-009-9599-9nanofluids(He et al.2007;Chen et al.2008;Prasher et al.2006a,b;Kwak and Kim2005;Lee et al.2006), although there is a large body of literature on suspensions rheology;see for example,Russel et al. (1991);Chow(1993);Petrie(1999),Larson(1999); Goodwin et al.(2000)l;Mohraz et al.(2004);Larson (2005);Egres and Wagner(2005);Abdulagatov and Azizov(2006).Particularly,there is little in the literature on the effect of temperature on the rheo-logical behaviour of nanofluids.Clearly,there is a gap in the current rheological literature for this type offluids.Furthermore,recent work has shown that the thermal behaviour of nanofluids correlates well with their rheological behaviour(Prasher et al.2006a, b;Chen et al.2007a;Abdulagatov and Azizov2006). In a recent study,we investigated systemically the rheological behaviour of ethylene glycol(EG)based spherical TiO2nanofluids(Chen et al.2007b).The results show that the nanofluids are Newtonian over a shear rate range of0.5–104s-1and the shear viscosity is a strong function of temperature,particle concentration and aggregation microstructure.This work is concerned about the rheological behaviour of EG based nanofluids containing titanate nanotubes (TNT).The specific objectives of the work are to investigate the effects of particle shape,particle concentration and temperature on nanofluids viscosity, and to understand the relationship between the rheo-logical behaviour and the effective thermal conductivity of nanofluids.It is for thefirst time that the rheological behaviour of a highly viscous EG based TNT nanofluids is investigated in a systematic manner.As will be seen later,the results of this work provide further evidence that the rheological measure-ments could provide information of particle structuring for predicting the effective thermal conductivity of nanofluids.The EG-TNT nanofluids used in this work were formulated by using the so-called two-step method with EG purchased from Alfa Aesar and TNT synthesized in our labs using a method described elsewhere(Bavykin et al.2004).The details of nanofluids formulation can be found elsewhere(Wen and Ding2005;He et al.2007;Chen et al.2007b). The TNT particles have a diameter(b)of*10nm and a length(L)of*100nm,giving an aspect ratio of(r=L/b)of*10.To avoid complications in interpreting the experimental results,no dispersants/ surfactants were used in the formulation.The nanofluids formulated were found stable for over 2months.The rheological behaviour of the nano-fluids was measured by using a Bolin CVO rheometer (Malvern Instruments,UK)over a shear rate range of 0.03–3,000s-1,a nanoparticle mass concentration of w=0–8%,and a temperature range of20–60°C (293–333K).The nanofluids were characterised for their size by using a Malvern Nanosizer(Malvern Instruments,UK)and a scanning electron microscope (SEM).The average effective particle diameter was found to be*260nm for all nanofluids formulated. This size is much larger than the equivalent diameter of the primary nanoparticles due to aggregation;see later for more discussion.Note that the particle size characterisation was performed both before and after the rheological measurements and no detectable changes to particle size were found.Figure1shows the viscosity of pure EG and EG-TNT nanofluids as a function of shear rate at 40°C.The results at other temperatures are similar.It can be seen that the EG-TNT nanofluids exhibit highly shear-thinning behaviour particularly when the TNT concentration exceeds*2%.Such behaviour is different from the observed Newtonian behaviour of EG-TiO2nanofluids containing spherical nanoparti-cles over similar shear rate range(Chen et al.2007b) where the base liquid,EG,is the same as that used in the current wok.The behaviour is similar to the observations of carbon nanotube nanofluids(Ding et al.2006)and CuO nanorod nanofluids(Kwak and Kim2005),although there are important differencesbetween them such as temperature dependence as will be discussed later.The shear-thinning behaviour of well-dispersed suspensions can be interpreted by the structuring of interacting particles(Doi and Edwards1978a,b and Larson1999).In a quiescent state,a rod-like particle has three types of motion due to Brownian diffusion: rotational(end-over-end)motion around the mid-point and translational motion in parallel or perpendicular to the long axis.For dilute suspensions with a number density,c,ranging between0and1/L3or volume fraction,u,ranging between0and1/r2),the average spacing between the particles is larger than the longest dimension of the rod,and zero shear viscosity can be approximated by gð0Þ%g0ð1þAÁcL3Þwith g0the base liquid viscosity and A,a numerical constant(Doi and Edwards1978a).For suspensions with 1/L3\c\1/bL2or1/r2\f/\1/r,the rod-like particles start to interact.The rotational motion is severely restricted,as well as the translational motion perpendicular to the long axis,and the zero shear viscosity can be estimated by gð0Þ%g0ð1þðBcL3Þ3Þ; with B a numerical constant(Doi and Edwards1978b). As a consequence,the zero shear viscosity can be much greater than the base liquid viscosity.The large viscosity is due to the rod-like shape effect and the viscosity is very sensitive to shear,which tends to align particles and hence the shear-thinning behaviour as shown in Fig.1.Note that the above mechanism can give a qualitative explanation for the experimental observations at low-shear rates and the shear-thinning behaviour as shown in Fig.1,it does not explain the high-shear viscosity of the nanofluids,which will be discussed later.It should also be noted that the criteria for classifying nanofluids given above need to be modified due to the presence of aggregates;see later for more discussion.Figure2shows the shear viscosity of4.0%EG-TNT nanofluids as a function of shear rate at different temperatures.The results under other concentrations are similar.It can be seen that the temperature has a very strong effect on the rheological behaviour of nanofluids with higher temperatures giving stronger shear thinning.For shear rates below*10s-1,the shear viscosity increases with increasing temperature, whereas the trend is reversed when the shear rate is above*10s-1.As mentioned above,this behaviour was not observed for carbon nanotube(Ding et al. 2006)and CuO nanorod(Kwak and Kim2005)nanofluids and we have not seen reports on such behaviour for nanofluids in the literature;see later for more discussion on the underlying mechanisms. Figure2also shows that the strongest shear thinning occurs at40–60°C,whereas very weak-shear thinning takes places at20–30°C.It is also noted that the shear viscosity of nanofluids at all temperatures investigated approaches a constant at high-shear rates.If the high-shear viscosity is plotted against temperature,Fig.3is obtained where the shear rate corresponding to the high-shear viscosity is taken as *2,000s-1.An inspection of all the data indicates that theyfit the following equation very well:ln g¼AþBÂ1000=TþCðÞð1Þwhere g is the shear viscosity(mPaÁs),T is the absolute temperature(K),and A,B and C areconstants given in Table1.Equation(1)takes a similar format as that widely used for liquid viscosity (Bird et al.2002)and for EG based nanofluids containing spherical particles(Chen et al.2007b).If the measured high-shear viscosity is normalized with respect to the shear viscosity of the base liquid, the relative increaseðg i¼ðgÀg0Þ=g0Þof the high-shear viscosity is found to be only a function of concentration but independent of temperature over the temperature range investigated in this work.The relative increments in the shear viscosities of nano-fluids containing0.5%,1.0%,2.0%,4.0%and8.0% particles are 3.30%,7.00%,16.22%,26.34%and 70.96%,respectively.Similar temperature indepen-dence of the shear viscosity was also observed for EG-TiO2and water-TiO2nanofluids containing spherical nanoparticles(Chen et al.2007b).The experimentally observed temperature depen-dence can be interpreted as follows.Given the base liquid and nanoparticles,the functional dependence of viscosity on shear rate is determined by the relative importance of the Brownian diffusion and convection effects.At temperatures below*30°C,the contribu-tion from the Brownian diffusion is weak due to high-base liquid viscosity.As a consequence,the shear dependence of the suspension is weak(Fig.2).The contribution from the Brownian diffusion becomes increasingly important with increasing temperature particularly above40°C due to the exponential dependence of the base liquid viscosity on temperature (Fig.3).At very high-shear rates,the Brownian diffusion plays a negligible role in comparison with the convective contribution and hence independent of the high-shear viscosity on the temperature.We now start to examine if the classical theories for the high-shear viscosity predict the experimental measurements(note that there is a lack of adequate theories for predicting the low shear viscosity).Figure4shows the shear viscosity increment as a function of nanoparticle volume concentration together with the predictions by the following Brenner &Condiff Equation for dilute suspensions containing large aspect ratio rod-like particles(Brenner and Condiff1974):g¼g01þg½ uþO u2ÀÁÀÁð2Þwhere the intrinsic viscosity,½g ;for high-shear rates has the following form(Goodwin and Hughes2000):½g ¼0:312rln2rÀ1:5þ2À0:5ln2rÀ1:5À1:872rð3ÞAlso included in Fig.4are the data for EG-TiO2 nanofluids with spherical nanoparticles(Chen et al. 2007b)and predictions by the Einstein Equation (Einstein1906,1911)for dilute non-interacting suspensions of spherical particles,g¼g01þ2:5uðÞ: It can be seen that both the Einstein and Brenner& Condiff equations greatly underpredict the measured data for the EG-TNT nanofluids.The high-shear viscosity of EG-TNT nanofluids is much higher than that of the EG-TiO2nanofluids containing spherical nanoparticles,indicating a strong particle shape effect on the shear viscosity of nanofluids.Although the shear-thinning behaviour of the nanofluids could be partially attributed to the structuring of interacting rod-like particles,the large deviation between the measured high-shear viscosity and the predicted ones by the Brenner&Condiff equation cannot fully be interpreted.In the following,an attempt is made to explain the experimental observations from the viewpoint of aggregation of nanaoparticles,which have been shown to play a key role in thermal behaviour of nanofluids in recent studies(Wang et al. 2003;Xuan et al.2003;Nan et al.1997;Prasher et al. 2006a,b;Keblinski et al.2005).Such an approach is also supported by the SEM and dynamic lightTable1Empirical constants for Eq.(1)a Maximum discrepancies;b Minimum discrepancies Concentration(wt%)A B C MaxD a(%)MinD b(%)0.0-3.21140.86973-154.570.62-1.440.5-3.42790.94425-148.490.93-0.471.0-2.94780.81435-159.14 1.11-0.692.0-2.2930.65293-174.57 1.64-0.694.0-2.63750.7574-165.820.99-0.948.0-2.73140.93156-145.010.88-1.57scattering analyses,which,as mentioned before, show clear evidence of particle aggregation.According to the modified Krieger-Dougherty equation(Goodwin and Hughes2000;Wang et al. 2003;Xuan et al.2003;Nan et al.1997),the relative viscosity of nanofluids,g r,is given as:g r¼1Àu a=u mðÞÀ½g u mð4Þwhere u m is the maximum concentration at which the flow can occur and u a is the effective volume fraction of aggregates given by u a¼u=u ma with u ma the maximum packing fraction of aggregates.As aggre-gates do not have constant packing throughout the structure,the packing density is assumed to change with radial position according to the power law with a constant index(D).As a result,u a is given as u a¼uða a=aÞ3ÀD;with a a and a,the effective radii of aggregates and primary nanoparticles,respectively. The term D is also referred as the fractal index meaning the extent of changes in the packing fraction from the centre to the edge of the aggregates.Typical values of D are given in normal textbook as D= 1.8–2.5for diffusion limited aggregation(DLA)and D=2.0–2.2for reaction limited aggregation(RLA); see for example Goodwin and Hughes(2000).For nanofluids containing spherical nanoparticles,the value of D has been shown experimentally and numerically to be between1.6and1.8(Wang et al. 2003,Xuan et al.2003)and between1.8and2.3, respectively(Waite et al.2001).A typical value of 1.8is suggested for nanofluids made of spherical nanoparticles(Prasher et al.2006a,b).However,little research has been found on the fractal index for nanofluids containing rod-like nanoparticles.The colloid science literature suggests a fractal index of 1.5–2.45for colloidal suspensions depending on the type of aggregation,chemistry environment,particle size and shape and shearflow conditions(Haas et al. 1993;Mohraz et al.2004;Hobbie and Fry2006; Micali et al.2006;Lin et al.2007).In a recent study, Mohraz et al.(2004)investigated the effect of monomer geometry on the fractal structure of colloi-dal rod aggregates.They found that the fractal index is a non-linear function of the monomer aspect ratio with the D increasing from*1.80to*2.3when the aspect ratio of the rod-like nanoparticles increases from1.0to30.6.Based on the above,a value of D=2.1is taken for nanofluids used in this work (Mohraz et al.2004,Lin et al.2007).Although the fractal model may appear to simplify the complexity of microstructures in aggregating systems containing rod-like particles,excellent agreement between the model prediction and experimental measurements exists when a a/a=9.46;see Fig.4.Here the aggregates are assumed to formflow units of an ellipsoidal shape with an effective aspect ratio of r a¼L a=b a;where L a and b a are the effective length and diameter,respectively.In the calculation,a typical value of u m of0.3is taken(Barnes et al.1989),and the intrinsic viscosity[g]is calculated by Eq.(3).It is to be noted that the aggregate size thatfits well to the rheological data(Fig.4)is consistent with the particle size analyses using both the SEM and the Malvern Nanosizer.A comparison between the EG-TNT data (a a/a=9.46,D=2.1,u m=0.30)and the EG-TiO2 data(a a/a=3.34,D=1.8,u m=0.605)(Chen et al. 2007b)in Fig.4suggests that the larger aggregate size in TNT nanofluids be an important factor responsible for the stronger shear-thinning behaviour and higher shear viscosity of TNT nanofluids.An inspection of Eq.(4)indicates that the effec-tive volume fraction u a u a¼u a a=aðÞ3ÀDis much higher than the actual volume fraction(u).This leads to the experimentally observed high-shear viscosity even for very dilute nanofluids,according to the classification discussed before.As a consequence,the demarcations defining the dilute and semi-concen-trated dispersions should be changed by using the effective volume fraction.The model discussed above can also provide a macroscopic explanation for the temperature indepen-dence of the high-shear viscosity.From Eq.(4),one can see that the relative high-shear viscosity depends on three parameters,the maximum volume fraction, u m,the effective volume fraction,u a and the intrinsic viscosity,[g].For a given nanofluid at a temperature not far from the ambient temperature,the three parameters are independent of temperature and hence the little temperature dependence of the relative shear viscosity.Microscopically,as explained before,the temperature-independent behaviour is due to negligi-ble Brownian diffusion compared with convection in high-shearflows.To further illustrate if the proposed aggregation mechanism is adequate,it is used to predict the effective thermal conductivity of the nanofluids by using the following conventional Hamilton–Crosser model(H–C model)(Hamilton and Crosser1962):k=k0¼k pþðnÀ1Þk0ÀðnÀ1Þuðk0Àk pÞk pþðnÀ1Þk0þuðk0Àk pÞð5Þwhere k and k0are,respectively,the thermal conductivities of nanofluids and base liquid,n is the shape factor given by n=3/w with w the surface area based sphericity.For TNT used in this work,the sphericity w is estimated as0.6(Hamilton and Crosser1962).For suspensions of aggregates,the above equation takes the following form:k=k0¼k aþðnÀ1Þk0ÀðnÀ1Þu aðk0Àk aÞa0a0að6Þwhere k a is the thermal conductivity of aggregates.To calculate k a,Eq.(6)is combined with the following Nan’s model(Nan et al.2003)for randomly dispersed nanotube-based composites:k a=k0¼3þu in½2b xð1ÀL xÞþb zð1ÀL zÞ3Àu in½2b x L xþb z L zð7Þwhere/in is the solid volume fraction of aggregates, b x¼ðk xÀk0Þ=½k mþL xðk tÀk mÞ and b z¼ðk zÀk0Þ=½k mþL zðk tÀk mÞ with k x,k m and k t being the thermal conductivities of nanotubes along trans-verse and longitudinal directions and isotropic thermal conductivity of the nanotube,respectively. In this work,k x,k m and k t are taken the same value as k p for afirst order of approximation due to lack of experimental data,and L x and L z are geometrical factors dependent on the nanotube aspect ratio given by L x¼0:5r2=ðr2À1ÞÀ0:5r coshÀ1r=ðr2À1Þ3=2 and L z¼1À2L x:Figure5shows the experimental results together with predictions by the original H–C model(Eq.5) and revised H–C model(Eq.6).Here the experiment data were obtained using a KD2thermal property meter(Labcell,UK)(Murshed et al.2005;Chen et al. 2008).One can see that the measured thermal conductivity is much higher than the prediction by the conventional H–C model(Eq.5),whereas the modified H–C model taking into account the effect of aggregation(Eq.6)agrees very well with the exper-imental data.The above results suggest that nanoparticle aggregates play a key role in the enhancement of thermal conductivity of nanofluids. The results also suggest that one could use the rheology data,which contain information of particle structuring in suspensions,for the effective thermal conductivity prediction.In summary,we have shown that EG-TNT nano-fluids are non-Newtonian exhibiting shear-thinning behaviour over20–60°C and a particle mass concen-tration range of0–8%,in contrast to the Newtonian behaviour for EG-TiO2nanofluids containing spher-ical particles.The non-Newtonian shear-thinning behaviour becomes stronger at higher temperatures or higher concentrations.For a given particle concen-tration,there exists a certain shear rate(e.g.*10s-1 for4wt%)below which the viscosity increases with increasing temperature,whereas the reverse occurs above such a shear rate.The normalised high-shearviscosity with respect to the base liquid viscosity, however,is found to be independent of temperature. These observations have not been reported in the literature for nanofluids.Further analyses suggest that the temperature effects are due to the shear-depen-dence of the relative contributions to the viscosity of the Brownian diffusion and convection.The analyses also suggest that a combination of particle aggregation and particle shape effects is the mechanism for the observed high-shear rheological behaviour,which is supported not only by the particle size measurements but also by the thermal conductivity measurements and analyses using a combination of the H–C and Nan’s models.The results of this work also indicate that one could use the information of aggregation from the rheological experiments for predicting the effec-tive thermal conductivity of nanofluids. Acknowledgement The work was partially supported by UK EPSRC under grants EP/E00041X/1and EP/F015380/1.ReferencesAbdulagatov MI,Azizov ND(2006)Experimental study of the effect of temperature,pressure and concentration on the viscosity of aqueous NaBr solutions.J Solut Chem 35(5):705–738.doi:10.1007/s10953-006-9020-6Barnes HA,Hutton JF,Walters K(1989)An introduction to rheology.Elsevier Science B.V.,NetherlandsBavykin DV,Parmon VN,Lapkin AA,Walsh FC(2004)The effect of hydrothermal conditions on the mesoporous struc-ture of TiO2nanotubes.J Mater Chem14(22):3370–3377 Bird RB,Steward WE and Lightfoot EN(2002)Transport Phenomena,2nd edn.Wiley,New YorkBrenner H,Condiff DW(1974)Transport mechanics in sys-tems of orientable particles,Part IV.Convective Transprort.J Colloid Inter Sci47(1):199–264Chen HS,Ding YL,He YR,Tan CQ(2007a)Rheological behaviour of ethylene glycol based titania nanofluids.Chem Phys Lett444(4–6):333–337Chen HS,Ding YL,Tan CQ(2007b)Rheological behaviour of nanofluids.New J Phys9(367):1–25Chen HS,Yang W,He YR,Ding YL,Zhang LL,Tan CQ,Lapkin AA,Bavykin DV(2008)Heat transfer andflow behaviour of aqueous suspensions of titanate nanotubes under the laminar flow conditions.Powder Technol183:63–72Choi SUS(1995)Enhancing thermal conductivity offluids with nanoparticles In:Siginer DA,Wang HP(eds) Developments applications of non-newtonianflows,FED-vol231/MD-vol66.ASME,New York,pp99–105 Chow TS(1993)Viscosities of concentrated dispersions.Phys Rev E48:1977–1983Das SK,Putra N,Roetzel W(2003)Pool boiling characteristics of nano-fluids.Int J Heat Mass Transfer46:851–862Ding YL,Alias H,Wen DS,Williams RA(2006)Heat transfer of aqueous suspensions of carbon nanotubes(CNT nanofluids).Int J Heat Mass Transf49(1–2):240–250 Doi M,Edwards SF(1978a)Dynamics of rod-like macro-molecules in concentrated solution,Part1.J Colloid Sci 74:560–570Doi M,Edwards SF(1978b)Dynamics of rod-like macro-molecules in concentrated solution,Part2.J Colloid Sci 74:918–932Eastman JA,Choi SUS,Li S,Yu W,Thompson LJ(2001) Anomalously increased effective thermal conductivities of ethylene glycol-based nanofluids containing copper nanoparticles.Appl Phys Lett78:718–720Egres RG,Wagner NJ(2005)The rheology and microstructure of acicular precipitated calcium carbonate colloidal sus-pensions through the shear thickening transition.J Rheol 49:719–746Einstein A(1906)Eine neue Bestimmung der Molekul-dimension(a new determination of the molecular dimensions).Annal der Phys19(2):289–306Einstein A(1911)Berichtigung zu meiner Arbeit:Eine neue Bestimmung der Molekul-dimension(correction of my work:a new determination of the molecular dimensions).Ann der Phys34(3):591–592Goodwin JW,Hughes RW(2000)Rheology for chemists—an introduction.The Royal Society of Chemistry,UK Haas W,Zrinyi M,Kilian HG,Heise B(1993)Structural analysis of anisometric colloidal iron(III)-hydroxide par-ticles and particle-aggregates incorporated in poly(vinyl-acetate)networks.Colloid Polym Sci271:1024–1034 Hamilton RL,Crosser OK(1962)Thermal Conductivity of heterogeneous two-component systems.I&EC Fundam 125(3):187–191He YR,Jin Y,Chen HS,Ding YL,Cang DQ(2007)Heat transfer andflow behaviour of aqueous suspensions of TiO2nanoparticles(nanofluids)flowing upward through a vertical pipe.Int J Heat Mass Transf50(11–12):2272–2281Hobbie EK,Fry DJ(2006)Nonequilibrium phase diagram of sticky nanotube suspensions.Phys Rev Lett97:036101 Keblinski P,Eastman JA and Cahill DG(2005)Nanofluids for thermal transport,Mater Today,June Issue,36–44 Krishnamurthy S,Lhattacharya P,Phelan PE,Prasher RS (2006)Enhanced mass transport of in nanofluids.Nano Lett6(3):419–423Kwak K,Kim C(2005)Viscosity and thermal conductivity of copper oxide nanofluid dispersed in ethylene glycol.Korea-Aust Rheol J17(2):35–40Larson RG(1999)The structure and rheology of complex fluids.Oxford University Press,New YorkLarson RG(2005)The rheology of dilute solutions offlexible polymers:progress and problems.J Rheol49:1–70Lee D,Kim J,Kim B(2006)A new parameter to control heat transport in nanofluids:surface charge state of the particle in suspension.J Phys Chem B110:4323–4328Lin JM,Lin TL,Jeng U,Zhong Y,Yeh C,Chen T(2007) Fractal aggregates of fractal aggregates of the Pt nano-particles synthesized by the polyol process and poly(N-vinyl-2-pyrrolidone)reduction.J Appl Crystallogr40: s540–s543Micali N,Villari V,Castriciano MA,Romeo A,Scolaro LM (2006)From fractal to nanorod porphyrin J-aggregates.Concentration-induced tuning of the aggregate size.J Phys Chem B110:8289–8295Mohraz A,Moler DB,Ziff RM,Solomon MJ(2004)Effect of monomer geometry on the fractal structure of colloidal rod aggregates.Phys Rev Lett92:155503Murshed SMS,Leong KC,Yang C(2005)Enhanced thermal conductivity of TiO2-water based nanofluids.Int J Therm Sci44:367–373Nan CW,Birringer R,Clarke DR,Gleiter H(1997)Effective thermal conductivity of particulate composites with inter-facial thermal resistance.J Appl Phys81(10):6692–6699 Nan CW,Shi Z,Lin Y(2003)A simple model for thermal conductivity of carbon nanotube-based composites.Chem Phys Lett375(5–6):666–669Pak BC,Cho YI(1998)Hydrodynamic and heat transfer study of dispersedfluids with submicron metallic oxide parti-cles.Exp Heat Transf11:150–170Prasher R,Song D,Wang J(2006a)Measurements of nanofluid viscosity and its implications for thermal applications.Appl Phys Lett89:133108-1-3Prasher R,Phelan PE,Bhattacharya P(2006b)Effect of aggregation kinetics on thermal conductivity of nanoscale colloidal solutions(nanofluids).Nano Lett6(7):1529–1534Russel WB,Saville DA,Scholwater WR(1991)Colloidal dispersions.Cambridge University Press,Cambridge Waite TD,Cleaver JK,Beattie JK(2001)Aggregation kinetics and fractal structure of gamma-alumina assemblages.J Colloid Interface Sci241:333–339Wang XQ,Mujumdar AS(2007)Heat transfer characteristics of nanofluids:a review.Int J Therm Sci46:1–19Wang XW,Xu XF,Choi SUS(1999)Thermal conductivity of nanoparticle–fluid mixture.J Thermphys Heat Transf 13:474Wang BX,Zhou LP,Peng XF(2003)A fractal model for predicting the effective thermal conductivity of liquid with suspension of nanoparticles.Int J Heat Mass Transf 46:2665–2672Wasan DT,Nikolov AD(2003)Spreading of nanofluids on solids.Nature423(6936):156–159Wen DS,Ding YL(2005)Formulation of nanofluids for natural convective heat transfer applications.Int J Heat Fluid Flow26:855–864Xuan YM,Li Q,Hu J,WF(2003)Aggregation structure and thermal conductivity of nanofluids.AIChE J49(4):1038–1043Yang Y,Zhong ZG,Grulke EA,Anderson WB,Wu G(2005) Heat transfer properties of nanoparticle-in-fluid dispersion (nanofluids)in laminarflow.Int J Heat Mass Transf 48:1107–1116。
00008547-MP.Tool.Introduction-v2.5

MP Tool Release NoteRelease NoteMP Tool IntroductionDate: 2017/07/07Version: 2.5CHANGE HISTORY©2013 Realtek Semiconductor Corp.2©2013 Realtek Semiconductor Corp.3©2013 Realtek Semiconductor Corp.4Table of ContentsI. INTRODUCTION ............................................................... 5 II. MP STRUCTURE .............................................................. 5 III. MP TOOL USER INTERFACE ................................................... 7 IV. MP TOOL OPERATION ........................................................ 29 V. MP COMMANDS ............................................................... 31 VI. HOW TO PORTING AUTO TEST PROGRAM FROM MP TOOL ............................. 46 VII. CALCULATE TX POWER INDEX OF NORMAL DRIVER ................................ 50 VIII. TX POWER TRACKING TABLES ............................................... 79 IX. TX POWER INDEX FOR AC-SERIES CHIPS –8812AR/BR, 8881A, 8814, AND 8194 ....... 87 X. RELEASE HISTORY .. (98)©2013 Realtek Semiconductor Corp.5I. IntroductionThis document will introduce the basic concept of whole MP structure, the meaning of items appeared in UI of MP Tool, and how to operate this tool to execute RF verifications.II. MP StructureThere are three elements to compose a basic MP structure● PC (with MP tool UI)● DUT (Realtek WiFi device with daemon ‘UDPServer’ launched) ● Ethernet Cable (for communication between PC & DUT)Run UI: MP Tool Run daemon: UDPServerFigure 1. basic MP structure©2013 Realtek Semiconductor Corp.6The procedure of running MP is like this:1. User control UI of MP tool.2. MP Tool send MP commands (according to UI operation) to DUT in form of UPD packets3. DUT receive & parse these UPD packets by daemon – UDPServer4. UDPServer execute these MP commands in system.5. MP operations can be performed by these MP commands. (like switch channels, select Tx powers, send packets…)(PC Side)(DUT Side)Figure 2. example of MP flow©2013 Realtek Semiconductor Corp.7III. MP TOOL User InterfaceThis chapter will introduce the items appeared in UI of MP Tool.1. General Page:This Page is for user to launch mp operation, change WiFi setting and do RF verifications (like Tx, Rx, Power Tracking…)Figure 3. Layout of General page©2013 Realtek Semiconductor Corp.81.1 Items of General Page:1. Release version & dateIn the top-left of this page, there is information about the tool version & release date.2. EFUSE TYPEIt’s for WiFi DUT’s hardware setting (int/ext pa, trswitch…), select one of these four types or input values manually. MP Tool will input values of this item into values of WiFi mibs <trsw_pape_C9> & <trsw_pape_CC> in DUT.Note:This item only need to be set in 92D.3. IP AddressIP address of DUT (for generation of UDP session)©2013 Realtek Semiconductor Corp.94. Test Log<Test Log>Check <Test Log> before clicking <Open>, and all the MP tool commands that are send to DUT MP daemon will be recorded in a text file named “test_log_year_month_date_hour_minute_second.txt” under folder “MP_TEST_LOG \” such as “MP_TEST_LOG \test_log_2015_03_09_16h20m3s.txt”.5. IC TYPESelect the correct WiFi chip for DUT.76. MacPhyModeThe mapping of <IC TYPE> & <MacPhyMode> shall be selected as below table.Note:Just select the correct IC TYPE, no need to change MacPhyMode.7.DevSelect WLAN interfaces.8.Phy BandSelect phy band for selected WLAN interfaces.Note:Below table are supported selections, out of these selections may encounter problems.Note:PhyBand is decided automatically by device except 92D SingleMac mode.9.RFE Type (Only for 8812BR, 8197F, 8814 and 8194)When “Open” is clicked, MP tool will check the RFE type by reading MIB rfe_type and fill it in <RFE Type> automatically. There is no need to manually select this combo-box unless one would like to do some experiments by using different RFE types.The following table shows the RFE types with related FEM:©2013 Realtek Semiconductor Corp.10Release Note©2013 Realtek Semiconductor Corp.11Note.It is only for 8812BR, 8197F, 8814 and 8194A.10. PA Type (8812AR and 8881A only)Different external PA type need different baseband setting.When this item is select, it will cause wlan interface restart.Note.It is for 8812AR and 8881A only.11. Channel©2013 Realtek Semiconductor Corp.12If < PhyBand > = 5G, channel supports from 36 to 177. If < PhyBand > = 2.4G, channel supports from 1 to 14.12. TX PowerSelect expected Tx Power Index for antanna A/B/C/D, range from 0 to 63,Selected value of Tx Power Index +1, real Tx Power +0.5 dBm (approximately).13. AntennaSelect Antenna PATH for MP Tx/Rx Test.14. DataRateSelect expected data rate for MP Tx Test.15. Packet Count & Length©2013 Realtek Semiconductor Corp.13<Packet Count>: enter value of number of Tx Packet user want to transmit. <Packet Length>: enter value of length of each Tx Packet.16. BandWidthSelect the bandwidth between 20MHz / 40MHz or 80MHz17. GISelect Short or Long GI.18. XCAPSelect the expected crystal cap value (0~63).19. TR SwitchPlease select this item if DUT needs support of TR Switch. Note.It is for 88R, 92C, and 92D only.20. Test Setting©2013 Realtek Semiconductor Corp.14< Test Item >Select test items for MP Tx/Rx verifications,Packets TX: Packet TX TestIn this function, we could set Channel, TX power, Antenna, DataRate, TX packet count. If you check infinitely Packet TX, the test does not stop until pushing stop button.Packets RX: Packet RX TestOnly two parameters, Channel and Antenna, were used in the function.Continuous TX SingleTone: Single Tone TX Test (only on CCK mode) In this function, we could set Channel , TX power , Antenna , and DataRate . But DataRate Parameters should be: 1, 2, 5.5 or11.Continuous TX:In this function, we could set Channel , TX power , Antenna , and DataRate .Carrier Suppression TX: Continuous TX Test Carrier Suppression (only on CCK mode) In this function, we could set Channel , TX power , Antenna , and DataRate . But DataRate Parameters should be: 1, 2, 5.5 or 11.< infinitely for Packet TX>If selected & Start MP Tx Test, DUT will Tx Packets until user stop test manually. (If not selected, DUT will only Tx numbers of packets from <Packet Count>)< Silent Mode >In this mode, it will not show the Tx/Rx packet so that the console will not print statistics message.< Hardware Tx >This is for 8197F, 8812BR, 8814 and 8194 only. If “Packets Tx” starts with this checkbox checked, the DUT will transmits packets by directly setting hardware registers rather than generating software packets from higher level. In this way, the data will not be transfferd through DMA, and thus the packet period can be precisely fixed, and the packet length can extend to 60,000 Bytes. (8197F, 8812BR, 8814 and 8194 only).< Start / Stop test >©2013 Realtek Semiconductor Corp.15After select expected WiFi setting & test items listed above, press these 2 buttons to start & stop MP verifications.Note:Above items shall be configured correctly before starting MP Test.21. StatisticsIf doing Packets TX or Packets RX , the statistics will be displayed in below TextBox.< Reset >It will clear all Tx/Rx counter.22. Initial Gain Value< Read >Read initial gain values for all paths by pressing23. Power Tracking©2013 Realtek Semiconductor Corp.16<PG thermal>Enter the expected Thermal value to here.<Read>Push this button to get the current thermal value and it will show on the “Current thermal” textbox.Push button <Power Tracking ON> & <Power Tracking OFF> to start/stop Tx Power TrackingEnable function of Power Tracking (Add additional Tx Power from Gain Tables) Read the current Thermal value from DUT. 24. Register Read/WriteRead or write baseband or RF registers.<BB/RF>Select register set- BB or RF.<RF Path> Select RF path.<Offset>Fill in the desired register offset<Value>The read/ written register value is shown here.<Read>Press this button to read register<Write>©2013 Realtek Semiconductor Corp.17Press this button to write to register25. Continuous Monitor<Enable Monitor>Enabling continuous read to specific register26. HW Tx Configuration (8197F, 8812BR, 8814 and 8194 only)This section is used only when < Hardware Tx > is checked. There are some configurable items listed as blow:<STBC>Enable STBC Tx packets<LDPC>Enable LDPC Tx packets<Period>Tx packet period<Pattern>Tx packet patternNote.It is for 8197F, 8812BR, 8814 and 8194A only.27. Power By Rate©2013 Realtek Semiconductor Corp.18<Get_From_Flash>It will read flash calibrated data and show it on the textbox. (11M, 54M, HT-MCS7, HT-MCS15, HT-MCS23, HT-MCS31, VHT 1S MCS7, VHT 2S MCS7, VHT 3S MCS7, and VHT 4S MCS7)<Load_PG_File>It will read the .txt file in the MP_TOOL folder.The following files should be in the folder: PHY_REG_PG_88E_new.txt PHY_REG_PG_92C.txt PHY_REG_PG_92D.txtPHY_REG_PG_92E_new.txt PHY_REG_PG_8812_new.txt PHY_REG_PG_8881Am.txt PHY_REG_PG_8814Amp_hp.txt PHY_REG_PG_8197Fmp.txt PHY_REG_PG_8822Bmp.txtNote.The file name should not be changed or it will lead to read file failure.<Update>Update the result to the “Power Index” items according to the selected data rate, bandwidth, and channel.<Path>Select the desired path to show the power by rate values and calibrated flash data.Note.The Tx power index of VHT-MCS8, VHT-MCS9 will be “index of VHT-MCS7” minus power by rate index of VHT-MCS8 / VHT-MCS9<Reset>Reset all power by rate data.28.Tx Power Limit<Load Table>It will read the .txt file in the MP_TOOL folder.The following 6 files should be in the folder:TXPWR_LMT_88E_new.txtTXPWR_LMT_92c.txtTXPWR_LMT_92d.txtTXPWR_LMT_92EE_new.txtTXPWR_LMT_8812_new.txtTXPWR_LMT_8881A_new.txtTXPWR_LMT_8814Amp.txtTXPWR_LMT_8197Fmp.txtTXPWR_LMT_8822Bmp.txt<Antenna Path>Select the tested antenna.<TxPowerLimit index>Select the tx power limit index to decide which column in limit table to use. If “0” is selected,<Region domain> will decide which colum to use.When items above are all decided, <Limit Power> displays the limited power in dBm for each rate. <Target Power> displays the target power in dBm for each rate based on the highest rates in the choosen powe-by-rate table.©2013 Realtek Semiconductor Corp.19©2013 Realtek Semiconductor Corp.20The “Power Index” will be updated when “Data Rate” is selected and the value will be limited according to <Limit Power> and <Target Power>.2. Flash Page –for 92C, 92D, 88E, 92Eand 97F:This Page is for user to read/write calibration values from/into Flash or Efuse of DUT. Like Tx Power Indices for all groups of channels, Thermal value & crystal values…etc.©2013 Realtek Semiconductor Corp.21Figure 4. Layout of Flash Page2-1. Items of Flash Page:1. Wlan port.Wlan port indicates the flash page of which wlan device. E.g. wlan0 / wlan1.2. Tx Power Indices for all groups of channels.Tx Power Index (TPI) is the value to control the level of Tx Power, the bigger the value of TPI. The stronger the level of Tx packets.TPI +1 = Tx Power Level + 0.5dBm . (approximately)In general, the target Tx power is about 13 dBm, so we can utilize these flash items to store the target TPI (to reach power level of 13dBm) for normal driver.©2013 Realtek Semiconductor Corp.22Figure 5. Group division of channels in Flash pageIn this MP Tool, we split available 2.4GHz channels into 3 groups, channels in the same group share the same TPIs for both antenna A & B.In this MP Tool, we split available 5GHz channels into 9 groups, channels in the same group share the same TPIs for both antenna A & BTable 4. 5G channel groups.Note.The group division of channels in flash page is adapted to the following chips : RTL8192C ,RTL8192D ,RTL8188E ,RTL8192E ,RTL8197FWe use the following items to store TPI for all rates (CCK, OFDM, MCS-1T, MCS-2T)<CCK>Refers to power of CCK rates (for 2.4G only)<HT-1S>Refers to power of the first of wireless special stream<Diff-HT-2S>Refers to the difference between the first and the second of wireless special stream<Diff-OFDM>©2013 Realtek Semiconductor Corp.23Refers to the difference between OFDM and HT-1S.<Diff-HT20>Refers to the difference between 20M and 40MPS:The MAX value of TPI for all rates is 63(in decimal).3. Buttons to Read/Write Tx Power Indices for all groups of channels. In this MP TOOL, it will recognize the chip version and the phy band automatically.<2.4G support>This button is only available in RTL8192D since it supports both 2G and 5G.<13dBm/6dBm>This button is only available in RTL8192D. You can press the TextBox show XXdBm to switch.After these 2 items selected done, user can press <Read> <Write> buttons in Flash group to perform R/W function of Tx power items from DUT’s flas h.Flash - <Read> : Read Tx Power items from flash of DUT, and displayed in UI. Flash - <Write> : Write Tx Power items displayed in UI into flash of DUTIn Efuse group, there are 3 buttonsEfuse - <Read> : Read Tx Power items from Efuse, and displayed in UI. Efuse - <Write> : Write Tx Power items displayed in UI into Efuse-Map of DUT. Efuse - <Sync> : Write modified Efuse-Map into Efuse of DUT.Example: after user made MP verification made by operation of General page, user knows in channel 9, use CCK rate, set Tx Power = 29 can reach his expected Tx power level (like 13dBm), then user can input value 29 into TextBox of CCK-Group1-MID manually, then do Flash-<Write>. Then, normal driver will know to use TPI=29 for CCK rates for channel 9.PS:Because Efuse has its limits of times of writing, so we store the expected writing value in©2013 Realtek Semiconductor Corp.24/proc/mib/wlanXX/mib_rf (so called Efuse-Map) After executing Efuse-Write, Efuse-Map will be modified.After executing Efuse-Sync, WiFi dirver will do real Efuse writing from the modified parts of Efuse-Map.4. MAC / REG_DOMAIN / XCAP / THER / TRSW_PAPE SettingPress the button Flash-Read/Write to read/write these values from flash. 4.1 TRSWPAPE_C9_CCThis setting is only for RTL8192D to configure hw setting.4.2 XCAPPress <Read> <Write> buttons to Read/Write these values from flash of DUT.Only RTL8192D needs to fill “Crystal Capacitor In ” and “Crystal Capacitor Out ”. Other chips only need to fill “Crystal Capacitor In ”.5. Efuse for 88E and 92E©2013 Realtek Semiconductor Corp.25This efuse page only supports 88e and 92e. For CCK power, channels are divided into 6 groups as shown, while channels are divided into 5 groups for HT40 power:Button <Read> : Read data from efuse and fill them in the blanks. Button <Write > : Write the data in the blank to driver’s efuse -map. Button <Sync > : Write driver’s efuse -map to DUT’s efuse device.©2013 Realtek Semiconductor Corp.263. Flash_AC Page –for 8881A, 8812AR/BR, 8814, and 8194:1. Select interface, band, and antenna combination before calibrationSelect interface:Select band:©2013 Realtek Semiconductor Corp.27Select antenna combination:2. Tx Power Indices for all groups of channels.We divide 5GHz channels into 14 groups in RTL8812AR/RTL8812BR/RTL8881A/RTL8814, and use the following items to store TPI for all rates.<HT40-1S>Refers to power of the first of wireless special stream in 40MHz mode<Diff-OFDM>Refers to the difference between OFDM and HT40-1S<DIFF-HT20-1S>Refers to the difference between 20MHz and 40MHz of one special stream<DIFF-HT20-2S>Refers to the difference between 20MHz one special stream and two special streams<DIFF-HT20-3S>Refers to the difference between 20MHz two special stream and three special streams<DIFF-HT40-2S>Refers to the difference between 40MHz one special stream and two special streams<DIFF-HT40-3S>Refers to the difference between 40MHz two special stream and three special streams<DIFF-HT80-1S>Refers to the difference between 80MHz and 40MHz of one special stream<DIFF-HT80-2S>Refers to the difference between 80MHz one special stream and two special streams<DIFF-HT80-3S>Refers to the difference between 80MHz two special stream and three special streams <Reset>Press reset button will clear all changes in MP TOOL.If you want to set the same difference value in all channels, you can do as the follow figure :©2013 Realtek Semiconductor Corp.283. PA typeThis should only be set when RTL8812AR use different external pa.The mapping of pa type and flash entry is :Skywoks-5022 – flash set HW_WLAN0_PA_TYPE 0RFDM-4501 / Skyworks-85793 –flash set HW_WLAN0_PA_TYPE 1 Skywoks-5023 – flash set HW_WLAN0_PA_TYPE 2 RTC-5634 – flash set HW_WLAN0_PA_TYPE 3©2013 Realtek Semiconductor Corp.29IV. MP Tool OperationThis chapter will introduce how to operate MP Tool. Before going through these steps, the MP nfjrom has to be loaded to the DUT:Step 0. Loading MP nfjrom to DUTFirst plug in the DUT and press ESC when booting to enter console mode of bootloader. Then use Windows CMD command line to execute tftp to transfer MP nfjrom to the DUT. The default IP address of bootloader is 192.168.1.6, so the command looks like this:tftp –i 192.168.1.6 put “C:\patch\nfjrom”Step 1. Open MP session- select correct <EFUSE TYPE> or input C9&CC value manually for DUT (Only RTL8192D needs this step)- input the correct <IP Address> of DUT- select your <IC TYPE> (just follow default setting like below pictures) - press <Open> buttion.Figure 6.default setting of 8192C for open MP sessionStep 2. Config WLAN settingIf open MP session successfully, it will show the chip name on the UI and all RF items can be selected (or input value) now.Then users can try to config WiFi setting as their wish, but please follow this table for listed items.PhyBand and MAC/PHY Mode will be auto selected after open except the IC TYPE is RTL8192D .©2013 Realtek Semiconductor Corp.302. Select Test Items and Start MP Verification.After WiFi setting done, user can select <Test Item> want to execute, and then press <Start> to start test, press <Stop> to stop test.3. Use Flash Page/Flash_AC Page to save calibration data.From test results, user may now know which specific Tx power index is suitable for specific data rate for some channels, so, user can use Flash page to store these calibration data.4. End MP SessionJust press <Close> button in General Page.V. MP CommandsAs mentioned before, MP operation is formed by executing MP commands, any of user’s actions to UI of MP tool were all converted into sets of MP commands, this chapter will introduce the basic MP commands(format, usage, examples…), then user can try to type these commands by conso le interface, in order to do MP operations without MP Tool program installed in PC.1.IntroductionRealtek WiFi Linux driver supports driver based Mass Production functions. Customers can utilize these functions to do EMI test and other simple TX and RX test. Under Realtek WiFi turnkey, we use Linux utility “iwpriv” to get and set I/O control to WLAN driver. The following commands are executed under Linux command prompt. The MP functions will only operate after the WLAN interface is opened.age1.Start MP mode:packets. All connection with other stations will be broken. Beacon transmitting is also stopped. If the original state is client mode, the roaming will be stopped.2.Stop MP mode:other commands. It will not return to normal operation mode. System should close the WLAN interface and open again to get WLAN work normally.©2013 Realtek Semiconductor Corp.31©2013 Realtek Semiconductor Corp.323. Set Tx rate:value sets the rate of Tx packets.For example, set Tx rate to MCS 7: iwpriv wlan0 mp_rate 135Note.Since 8814 and 8194 support 3 spatial stream, the values for HT rate extends to 151, and the base value for VHT is 160 rather than legacy 144.For 8814 and 8194, the value is as following:E.g. set Tx rate to VHT NSS1 MCS 7: iwpriv wlan0 mp_rate 167©2013 Realtek Semiconductor Corp.334. Set operational channel:Set the operational channel of transmitting and receiving packets.E.g. set channel to 6:iwpriv wlan0 mp_channel 65. Set operational bandwidth:sgi sets guard interval of transmitting MCS packet, 1 for short GI, 0 for long GI Set the operational bandwidth for transmitting and receiving packets. Set the guard interval fortransmitting MCS packets. If the parameters are not given, the default action is set bandwidth to 20M mode and long GI to transmitting packets.For example, set bandwidth to 40M, and no shortGI: iwpriv wlan0 mp_bandwidth 40M=1,shortGI=06. Set Tx power:b sets Tx power level for path Bc sets Tx power level for path Cd sets Tx power level for path DSet the transmitting power level of path A, B, C, and D. If the DUT only has one path, just specify patha.For example, set path A power index to 20, and path B to 30: iwpriv wlan0 mp_txpower patha=20,pathb=307. Set xcap value:Set the PHY related parameters of crystal capacitor.For example, set crystal capacitor to 31: iwpriv wlan0 mp_phypara xcap=31©2013 Realtek Semiconductor Corp.348. Set antenna for Tx:for antenna D, ab for antenna A and B, abc for antenna A, B, and C, and abcd for antenna A, B, C, and DSet the operational antenna for Tx on the target board.For example, set Tx operational antenna to path A: iwpriv wlan0 mp_ant_tx a9.Set antenna for Rx:ant sets the operational antenna for Rx, a for antenna A, b for antenna B, c for antenna C, d for antenna D, ab for antenna A and B, abc for antenna A, B, and C, and abcd for antenna A, B, C, and DSet the operational antenna for Rx on the target board.For example, set Rx operational antenna to path A: iwpriv wlan0 mp_ant_rx a10. Start air Rx mode:start clears counters and start to accumulate Rx packets stop stops counts and show the statisticsThis command is for air receiving test. Use start command to clear all the counters and start toaccumulate the received packets. Use stop command to stop counting and show the statistics of correct packets and CRC-error packets.11. Start continuous Tx mode:n sets the number of packets to send background sends packets in background mode stop stops the background sending pkt sends packet tx, i.e., not sent by hardware cs sends carrier suppression stone sends single toneThis command is for continuous transmitting test. Use time command to assign the time to send packets. Use count command to assign the number of packets to send. If both of time and count are not specified,©2013 Realtek Semiconductor Corp.35the sending function will continue infinitely. It can be stopped when any key is pressed (should be specifically implemented in other platform) while background command is not specified. If cs isspecified, the sending signal will be a carrier suppression signal. Use stone command to send single tone signal for frequency testing. If stone is specified, the sending signal will be single tone and not adistinguishable packet any more. Use background command to tell driver to send packets in background. The command line control will return and packet sending is continuous. It can be stopped by stopcommand. By default, packets will be sent by hardware for shorter duty cycle. If pkt is specified, packets will be sent by software.For example, start background packets Tx infinitely: iwpriv wlan0 mp_ctx background,pkt12.Query air tx/rx statistics: This command is for packet counting. Under packet transmitting, use this command to get the number of packets being transmitted. Under receiving, use this command to get the statistics of correct packets and CRC-error packets.13. Set Band ModeSet the operational band mode on the target board. This is set only for RTL8192D.14. Start air Rx mode: off stops mp dig.This command is only for RTL8812AR/BR and RTL8814 while receiving test. Use on command to start mp dig and it will change the initial gain setting depends on false alarm counter. Use off command to stop mp dig and it will set initial gain to default.15. Start power tracking:stop stop power trackingStart power tracking and set the tracked thermal as xFor example, start power tracking and set the tracked thermal as 32: iwpriv wlan0 mp_pwrtrk ther=32©2013 Realtek Semiconductor Corp.3616. Start hardware Tx (8197F, 8812BR, 8814 and 8194 only):Start to transmit hardware TX packets. The packet type is described in the argument set, including Tx rate, packet period, MAC address, .etc.The argument set contains 56 arguments, which are listed in order as below:{Ntx:4, Mode:3, bEnPMacTx:1}, TX_RATE, TX_RATE_HEX, TX_SC, {BandWidth:3, NDP_sound:1, bLDPC:1, bSTBC:1, bSPreamble:1, bSGI:1}, m_STBC, PacketPeriod, PacketCount, PacketLength, PacketPattern, SFD, SignalField, ServiceField, LENGTH, CRC16[0], CRC16[1], LSIG[0], LSIG[1], LSIG[2], HT_SIG[0],HT_SIG[1],HT_SIG[2],HT_SIG[3],HT_SIG[4],HT_SIG[5], VHT_SIG_A[0], VHT_SIG_A[1],VHT_SIG_A[2],VHT_SIG_A[3],VHT_SIG_A[4],VHT_SIG_A[5], VHT_SIG_B[0],VHT_SIG_B[1],VHT_SIG_B[2],VHT_SIG_B[3], VHT_SIG_B_CRC,VHT_Delimiter[0], VHT_Delimiter[1], VHT_Delimiter[2], VHT_Delimiter[3], MacAddress[0], MacAddress[1], MacAddress[2], MacAddress[3], MacAddress[4], MacAddress[5]Since the calculation of arguments LSIG , HT_SIG , VHT_SIG_A, .etc involves floating point operation, these arguments are calculated by MP tool. Please refer to MP tool and MP API to generate the arguments and issue this command.For example, start to transmit 40M, channel 38, MCS7 packets infinitely: iwpriv wlan0 mp_pmac_ctx17,-121,19,0,32,1,0,100,0,0,0,0,0,0,3,-24,0,0,0,0,0,0,0,0,0,0,-53,6,2,-121,-24,3,7,84,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,-1,-1,-1,-1,-1,-13. ExamplesThe standard procedure is, firstconfig WiFi mibs to determine types of Band(5G/2.4G), Mode(A/B/G/N) and PA(extPA/intPA) then open WiFi driver and enter MP mode. then use mp commands to dynamically set channel, rate, antenna, power level… then use mp commands to perform Tx/Rx verifications and query statistics. after done testing exit MP mode and re-open WiFi driver.The following introduces the command lists for some examples.1. Init and Open WiFi Driverifconfig wlan0 down(iwpriv wlan0 set_mib trsw_pape_C9=0)// 92D only,。
汉克斯克林普技术 . . . 用于最佳连接的应用程序说明书

FacebookLinkedInYouTube WWWWIRE SOLUTIONS52-028 Wrocław, Poland; ul. Opatowicka 16NIP: PL 899 229 92 03Obsługa Klienta | Customer service: +48 602 234 242 +48 606 725 122 +48 606 725 175e-mail:*******************Dział techniczny | Technical advice: +48 606 725 982DISTRIBUTION - B2B - CONSULTING - TRAININGS - PRESENTATIONS - SERVICESTERMINALS APPLICATORS HOUSING HAND TOOLSCORRUGATEDTUBES INSULATING SLEEVINGSPRESSESAUTOMATIC TOOLS IDCCONNECTORSTTR PRINTERSApplicatorsVersion 2019Page 2ApplicatorsThis slogan stays for best connections. Best connections to our customers and also best crimp connections. Hanke Crimp-Technik has more than 40 years experience in developping and manufacturing crimp presses, applicators and other equipment for the harnessmaker industries. Hanke Crimp-Technik employs more than 260 employees all over the world. Our company philosophy is based on the absolute customer satisfaction and a cooperation based on part-nership. Our development realizes the ideas with use of the most modern CAD technology into technically practicable products. With CNC centers of the latest generation we produce our economical and high-quality products in Germany and Slovakia. Our companies of course are certified according to DIN EN ISO 9001. We serve customers in the most different markets like upplier of the automobile and commercial vehicle industry, machines and equipment construc-tion, house equipment and communication, as well as electrical and electronics industry. With Hanke Crimp-Technik equipment you process terminals as individual contact or in ribbon form.To obtain a first impression about the variety of our products, we have compiled this product catalogue. You have special wishes for your processing, you do not hesitate to demand us. In the last 40 years we have developed and manufactured some special machines for our custo-mers.Page 3ApplicatorsGLOBAL – STAR 951S Center Crimp ...........................................................................4POWER CRIMP 938 IBS .................................................................................................5PICO – STAR 906 ............................................................................................................6PICO – STAR 907 ............................................................................................................7GLOBAL – STAR 951 ......................................................................................................8GLOBAL – STAR 952 ......................................................................................................9Advantages GLOBAL – STAR Applicator ....................................................................10GLOBAL – STAR 951 EK.90 ..........................................................................................12GLOBAL – STAR 951/DCHV .........................................................................................13GLOBAL – STAR 951/VAEH ..........................................................................................14GLOBAL – STAR 952/90 ...............................................................................................15QUICK – CRIMP 947.......................................................................................................16QUICK – CRIMP 948.......................................................................................................17POWER – CRIMP 925.....................................................................................................18POWER – CRIMP 926.....................................................................................................19POWER – CRIMP 926/90 .............................................................................................20POWER – CRIMP 935.....................................................................................................21POWER – CRIMP 936.....................................................................................................22POWER – CRIMP 935/EK-R ..........................................................................................23POWER – CRIMP 938.....................................................................................................24POWER – CRIMP 938/BK .............................................................................................25Sales and service offices in Germany .........................................................................26Sales and service offices worldwide ............................................................................27Sales and service offices of our partners . (28)Page 4Designed for short stripping lengthsStripping lengths play a big role in processing she-athed multi-core cables. To avoid signal interferen-ce it is essential to minimize the stripping length of the sheathed cable. The Center-applicator has been designed for this very usage, to close the distance between jacket and crimp process.Technical precisionCenter-technology is based on cam guided me-chanism. To guarantee shorter stripping lengths the position of the cable is fixed in the applicator. The terminal that is positioned above the anvil is then transported upwards. This procedure is able to pro-cess stripping lengths of up to 6.5 mm (dependentof the terminal), thus providing the shortest stripping length on the market. Flexible usageThe Center-applicator is compatible with the Hanke STRIPMATIC 944-35 DL and all common fully auto -matic crimping machines. Typical application is the processing of sheathed multi-core cables on split cycle presses. The applicator is optimized for small terminals for cross-sections between 0.08 mm² and 2.50 mm².Technical Data upon requestPage 5ModularityThe modular cartridge system allows quick set-up times for processing multiple terminals without com-plicated and time consuming applicator change. A module consists of upper and lower cartridge, ter-minal fixture and if needed cable fixture. Originally designed for intelligent battery systems, the POWER CRIMP 938 IBS is now versatile usable for many ap -plications.Communication in useThe Optional bar-code scanner captures each mo-dule so that only with the correct combination the process is approved. Via an OPC/UA interfacedata can be received or sent to higher-level systems.ApplicationsThe POWER CRIMP938 IBS is only usable in com -bination with the CRIMPMATIC 971 IBS, which is equipped with light curtain and optional bar-code scanner. Aside from crimping modules there is a va-riety of other applications, for example bending.Technical data upon requestTechnical Data:wire cross section: ................................0.03 – 0.5 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 22 mmclosing height: .....................................68.4 mmstroke: ...................................................22 mmcompress-air connection: ..................5 – 8 barweight: .................................................1 kgdimensions (W x D x H): ...................95 mm x 60 mm x 110 mmTechnical Data:wire cross section: ................................0.03 – 0.5 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 22 mmclosing height: .....................................68.4 mmstroke: ...................................................22 mmcompress-air connection: ..................5 – 8 barweight: .................................................1 kgdimensions (W x D x H): ...................65 mm x 130 mm x 90 mmTechnical Data:wire cross section: ................................0.08 – 6 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 40 mmclosing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm compress-air connection: ..................5 – 8 bar weight: .................................................4 kgdimensions (W x D x H): ...................180 x 100 x 150 mmTechnical Data:wire cross section: ................................0.08 – 6 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 40 mm closing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm compress-air connection: ..................5 – 8 bar weight: .................................................4 kg dimensions (W x D x H): ...................90 x 160 x 150 mmPage 10ApplicatorsAdvantages GLOBAL – STAR Applicator1. INNOVATION Terminal strip guide and Pneumatic feed error-free run due to smooth, regular feed feed speed adjustable via throttle valve easy adjustment of feed length and position no force effect of feed on crimp force monitoring terminal feed step length > 25 mm (up to 35 mm) possiblesimple and easy mounting of the applicator in the press, because no feed mechanic has to be drawn backpneumatic feed is completely integrated in applicator, which means:one connecting flexible tube, no free tubesshort type of construction, because cylinder is integrated in applicatorcompact construction, because valve and compressed air are integrated in applicatorsimple adjustment of table (bell-mouth), by means of:it‘s not necessary to dismount the applicator of the press no clamping screw has to be loosened for adjustment2. Wearing parts: crimp dies, anvils and shear blades are accessible from the front and can be changed without taking the applicator out of pressanvil is split in wire and insulation area, consequently:o ptimal construction material for insulation anvil (hard, cutting) and wireanvil (ductile,crimping) in case of wear (i.e. wireanvil), only one part has to be changed both sides of the insulationanvil can be used for cutting (two blade edges)Page 11Applicators3. Re-set to other terminals: re-set time < 10 min, because modular designcrimp dies can be changed separate or together with pressing block lower wearing parts (anvil, blades) can be changed as a complete unitterminal strip guide is completely changeableThis means for you:☑considerable cost saving ☑low training effort for toolsetter ☑shortest times for re-set and setting ☑best conditions for trouble-free run☑no special hand-tools necessary, in case of maintenanceTechnical Data:wire cross section: ................................0.08 – 6 mm²closing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm weight: .................................................2.8 kg dimensions (W x D x H): ...................105 x 100 x 150 mmTechnical Data:wire cross section: ................................0.08 – 6 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 40 mmclosing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm compress-air connection: ..................5 – 8 bar weight: .................................................4 kgdimensions (W x D x H): ...................180 x 100 x 150 mmTechnical Data:wire cross section: ................................0.25 – 6 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 40 mmclosing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm compress-air connection: ..................5 – 8 bar weight: .................................................4 kgdimensions (W x D x H): ...................180 x 100 x 150 mmTechnical Data:wire cross section: ................................0.35 – 6 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 40 mm closing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm compress-air connection: ..................5 – 8 bar weight: .................................................4 kg dimensions (W x D x H): ...................90 x 160 x 150 mmTechnical Data:wire cross section: ................................0.08 – 6 mm²feed: .....................................................mechanical feed feed length: ........................................1 – 27 mmclosing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm weight: .................................................4 kgdimensions (W x D x H): ...................170 x 160 x 150 mmTechnical Data:wire cross section: ................................0.08 – 6 mm²feed: .....................................................mechanical feed feed length: ........................................1 – 30 mm closing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm weight: .................................................4 kg dimensions (W x D x H): ...................90 x 160 x 150 mmTechnical Data:wire cross section: ................................max. 16 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 60 mmclosing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm compress-air connection: ..................5 – 8 bar weight: .................................................7.5 kg dimensions (W x D x H): ...................280 x 115 x 150 mmTechnical Data:wire cross section: ................................max. 16 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 60 mmclosing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm compress-air connection: ..................5 – 8 bar weight: .................................................7.5 kg dimensions (W x D x H): ...................120 x 170 x 150 mmTechnical Data:wire cross section: ................................max. 16 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 60 mmclosing height: .....................................135.78 mm stroke: ...................................................40 – 44 mm compress-air connection: ..................5 – 8 bar weight: .................................................7.5 kg dimensions (W x D x H): ...................120 x 170 x 150 mmTechnical Data:wire cross section: ................................16 – 50 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 70 mmclosing height: .....................................158.4 mm stroke: ...................................................44 mmcompress-air connection: ..................5 – 8 bar weight: .................................................8 kgdimensions (W x D x H): ...................110 x 310 x 180 mmTechnical Data:wire cross section: ................................16 – 50 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 70 mmclosing height: .....................................158.4 mm stroke: ...................................................44 mmcompress-air connection: ..................5 – 8 bar weight: .................................................8 kgdimensions (W x D x H): ...................110 x 310 x 180 mmTechnical Data:wire cross section: ................................max. 50 mm²closing height: .....................................158.4 mm stroke: ...................................................44 mmweight: .................................................approx. 6 kg dimensions (W x D x H): ...................326 x 128 x 127 mmTechnical Data:wire cross section: ................................70 – 100 mm²feed: .....................................................pneumaticfeed length: ........................................1 – 70 mmclosing height: .....................................183 mmstroke: ...................................................44 mmcompress-air connection: ..................5 – 8 bar weight: .................................................12 kg dimensions (W x D x H): ...................250 x 140 x 195 mmTechnical Data: on requestPage 26ApplicatorsSales and service offices in GermanyHeadquartersArea Sales Manager WestArea Sales Manager SouthArea Sales Manager EastHanke Crimp-Technik GmbH Hirschfelder Ring 802763 ZittauFon: +49 3583 5183-0Fax: +49 3583 5183-30E-Mail: ***************Web: www.hankect.deWolfgang Diezl Oberpohlhausen 4842929 Wermelskirchen Fon: +49 2196 887474Mobil: +49 151 ********Fax: +49 2196 889485E-Mail: ******************Web: www.hankect.deWalter Munninger Schwalbenstraße 786643 BertoldsheimFon: +49 8434 9437932Mobil: +49 171 2959429Fax: +49 8434 9437938E-Mail: **********************Web: www.hankect.deEric GwoscHirschfelder Ring 802763 ZittauFon: +49 3583 5183-550Mobil: +49 151 **** ****Fax: +49 3583 5153-30E-Mail: ******************Web: www.hankect.de。
软件工程英文参考文献(优秀范文105个)

软件工程英文参考文献(优秀范文105个)软件工程英文参考文献一:[1]Carine Khalil,Sabine Khalil. Exploring knowledge management in agile software developmentorganizations[J]. International Entrepreneurship and Management Journal,2020,16(4).[2]Kevin A. Gary,Ruben Acuna,Alexandra Mehlhase,Robert Heinrichs,Sohum Sohoni. SCALING TO MEET THE ONLINE DEMAND IN SOFTWARE ENGINEERING[J]. International Journal on Innovations in Online Education,2020,4(1).[3]Hosseini Hadi,Zirakjou Abbas,GoodarziVahabodin,Mousavi Seyyed Mohammad,Khonakdar Hossein Ali,Zamanlui Soheila. Lightweight aerogels based on bacterial cellulose/silver nanoparticles/polyaniline with tuning morphology of polyaniline and application in soft tissue engineering.[J]. International journal of biological macromolecules,2020,152.[4]Dylan G. Kelly,Patrick Seeling. Introducing underrepresented high school students to software engineering: Using the micro:bit microcontroller to program connected autonomous cars[J]. Computer Applications in Engineering Education,2020,28(3).[5]. Soft Computing; Research Conducted at School of Computing Science and Engineering Has Updated OurKnowledge about Soft Computing (Indeterminate Likert scale: feedback based on neutrosophy, its distance measures and clustering algorithm)[J]. News of Science,2020.[6]. Engineering; New Engineering Findings from Hanyang University Outlined (Can-based Aging Monitoring Technique for Automotive Asics With Efficient Soft Error Resilience)[J]. Journal of Transportation,2020.[7]. Engineering - Software Engineering; New Findings from University of Michigan in the Area of Software Engineering Reported (Multi-criteria Test Cases Selection for Model Transformations)[J]. Journal of Transportation,2020.[8]Tamas Galli,Francisco Chiclana,Francois Siewe. Software Product Quality Models, Developments, Trends, and Evaluation[J]. SN Computer Science,2020,1(2).[9]. Infotech; Infotech Joins BIM for Bridges and Structures Transportation Pooled Fund Project as an Official Software Advisor[J]. Computer Technology Journal,2020.[10]. Engineering; Study Findings from Beijing Jiaotong University Provide New Insights into Engineering (Analyzing Software Rejuvenation Techniques In a Virtualized System: Service Provider and User Views)[J]. Computer Technology Journal,2020.[11]. Soft Computing; Data on Soft Computing Reported by Researchers at Sakarya University (An exponential jerk system, its fractional-order form with dynamical analysis and engineering application)[J]. Computer Technology Journal,2020.[12]. Engineering; Studies from Henan University Yield New Data on Engineering (Extracting Phrases As Software Features From Overlapping Sentence Clusters In Product Descriptions)[J]. Computer Technology Journal,2020.[13]. Engineering; Data from Nanjing University of Aeronautics and Astronautics Provide New Insights into Engineering (A Systematic Study to Improve the Requirements Engineering Process in the Domain of Global Software Development)[J]. Computer Technology Journal,2020.[14]. Soft Computing; Investigators at Air Force Engineering University Report Findings in Soft Computing (Evidential model for intuitionistic fuzzy multi-attribute group decision making)[J]. Computer Technology Journal,2020.[15]. Engineering; Researchers from COMSATS University Islamabad Describe Findings in Engineering (A Deep CNN Ensemble Framework for Efficient DDoS Attack Detection in Software Defined Networks)[J]. Computer Technology Journal,2020.[16]Pedro Delgado-Pérez,Francisco Chicano. An Experimental and Practical Study on the EquivalentMutant Connection: An Evolutionary Approach[J]. Information and Software Technology,2020.[17]Koehler Leman Julia,Weitzner Brian D,Renfrew P Douglas,Lewis Steven M,Moretti Rocco,Watkins Andrew M,Mulligan Vikram Khipple,Lyskov Sergey,Adolf-Bryfogle Jared,Labonte Jason W,Krys Justyna,Bystroff Christopher,Schief William,Gront Dominik,Schueler-Furman Ora,Baker David,Bradley Philip,Dunbrack Roland,Kortemme Tanja,Leaver-Fay Andrew,StraussCharlie E M,Meiler Jens,Kuhlman Brian,Gray JeffreyJ,Bonneau Richard. Better together: Elements of successful scientific software development in a distributed collaborative munity.[J]. PLoS putational biology,2020,16(5).[18]. Mathematics; Data on Mathematics Reported by Researchers at Thapar Institute of Engineering and Technology (Algorithms Based on COPRAS and Aggregation Operators with New Information Measures forPossibility Intuitionistic Fuzzy Soft Decision-Making)[J]. Journal of Mathematics,2020.[19]. Engineering - Medical and Biological Engineering; Reports from Heriot-Watt University Describe Recent Advances in Medical and Biological Engineering (ANovel Palpation-based Method for Tumor Nodule Quantification In Soft Tissue-putational Framework and Experimental Validation)[J]. Journal ofEngineering,2020.[20]. Engineering - Industrial Engineering; Studies from Xi'an Jiaotong University Have Provided New Data on Industrial Engineering (Dc Voltage Control Strategy of Three-terminal Medium-voltage Power Electronic Transformer-based Soft Normally Open Points)[J]. Journal of Engineering,2020.[21]. Engineering; Reports from Hohai University Add New Data to Findings in Engineering (Soft Error Resilience of Deep Residual Networks for Object Recognition)[J]. Journal of Engineering,2020.[22]. Engineering - Mechanical Engineering; Study Data from K.N. Toosi University of Technology Update Understanding of Mechanical Engineering (Coupled Directional Dilation-Damage Approach to Model the Cyclic-Undrained Response of Soft Clay under Pure Principal Stress Axes Rotation)[J]. Journal of Engineering,2020.[23]. Soft Computing; Researchers from Abes Engineering College Report Details of New Studies and Findings in the Area of Soft Computing (An intelligent personalized web blog searching technique using fuzzy-based feedback recurrent neural network)[J]. Network Weekly News,2020.[24]. Engineering; Studies from University of Alexandria in the Area of Engineering Reported (Software Defined Network-Based Management for Enhanced 5G Network Services)[J]. Network Weekly News,2020.[25]. Soft Computing; Data on Soft Computing Discussed by Researchers at Department of Electrical and Communication Engineering [A metaheuristicoptimization model for spectral allocation incognitive networks based on ant colony algorithm (M-ACO)][J]. Computer Technology Journal,2020.[26]. Engineering - Software Engineering; Complutense University Madrid Reports Findings in Software Engineering (Recolibry Suite: a Set of Intelligent Tools for the Development of Remender Systems)[J]. Computer Technology Journal,2020.[27]. Engineering - Software Engineering; Data on Software Engineering Reported by Researchers at Gautam Buddha University (A novel quality prediction modelfor ponent based software system using ACO-NM optimized extreme learning machine)[J]. Computer Technology Journal,2020.[28]. Soft Computing; New Soft Computing Study Findings Recently Were Reported by Researchers at University College of Engineering (A novel QIM-DCT based fusion approach for classification of remote sensing images via PSO and SVM models)[J]. Computer Technology Journal,2020.[29]Morshedloo Fatemeh,Khoshfetrat Ali Baradar,Kazemi Davoud,Ahmadian Mehri. Gelatin improves peroxidase-mediated alginate hydrogel characteristics as a potential injectable hydrogel for soft tissueengineering applications.[J]. Journal of biomedical materials research. Part B, Applied biomaterials,2020.[30]Jung-Chieh Lee,Chung-Yang Chen. Exploring the team dynamic learning process in software process tailoring performance[J]. Journal of Enterprise Information Management,2020,33(3).[31]. Soft Computing; Study Results from Velammal Engineering College in the Area of Soft Computing Reported (Efficient routing in UASN during the thermohaline environment condition to improve the propagation delay and throughput)[J]. Mathematics Week,2020.[32]. Soft Matter; Findings from School of Materials Science and Engineering Provide New Insights into Soft Matter (A practical guide to active colloids: choosing synthetic model systems for soft matter physics research)[J]. Physics Week,2020.[33]Julio César Puche-Regaliza,Alfredo Jiménez,Pablo Arranz-Val. Diagnosis of Software Projects Based on the Viable System Model[J]. Systemic Practice and Action Research,2020,33(1).[34]Meinert Edward,Milne-Ives Madison,Surodina Svitlana,Lam Ching. Agile requirements engineering and software planning for a digital health platform to engage the effects of isolation caused by social distancing: A case study and feasibility study protocol.[J]. JMIR public health and surveillance,2020.[35]. Engineering - Civil Engineering; Studies Conducted at Shandong Jianzhu University on Civil Engineering Recently Published (Seismic Response Analysis and Control of Frame Structures with Soft First Storey under Near-Fault Ground Motions)[J]. Journal of Engineering,2020.软件工程英文参考文献二:[36]Chao-ze Lu,Guo-sun Zeng,Ying-jie Xie. Bigraph specification of software architecture and evolution analysis in mobile puting environment[J]. Future Generation Computer Systems,2020,108.[37]Ompal Singh, Saurabh Panwar, P. K. Kapur.. Determining Software Time-to-Market and Testing Stop Time when Release Time is a Change-Point[J]. International Journal of Mathematical, Engineering and Management Sciences,2020,5(2).[38]Ayushi Verma,Neetu Sardana,Sangeeta Lal. Developer Remendation for Stack Exchange Software EngineeringQ&A Website based on K-Means clustering and Developer Social Network Metric[J]. Procedia ComputerScience,2020,167.[39]Jagdeep Singh,Sachin Bagga,Ranjodh Kaur. Software-based Prediction of Liver Disease with Feature Selection and Classification Techniques[J]. Procedia Computer Science,2020,167.[40]. Engineering - Software Engineering; Studies from Concordia University Update Current Data on SoftwareEngineering (On the impact of using trivial packages: an empirical case study on npm and PyPI)[J]. Computer Technology Journal,2020.[41]. Engineering - Software Engineering; Study Findings from University of Alberta Broaden Understanding of Software Engineering (Building the perfect game - an empirical study of game modifications)[J]. Computer Technology Journal,2020.[42]. Engineering - Software Engineering; Investigators at National Research Council (CNR) Detail Findings in Software Engineering [A Framework for Quantitative Modeling and Analysis of Highly (Re)Configurable Systems][J]. Computer Technology Journal,2020.[43]. Engineering - Knowledge Engineering; Data from University of Paris Saclay Provide New Insights into Knowledge Engineering (Dynamic monitoring of software use with recurrent neural networks)[J]. Computer Technology Journal,2020.[44]. Engineering - Circuits Research; Findings from Federal University Santa Maria Yields New Data on Circuits Research (A New Cpfsk Demodulation Approach for Software Defined Radio)[J]. Computer Technology Journal,2020.[45]. Soft Computing; Investigators from Lovely Professional University Release New Data on Soft Computing (An intensify Harris Hawks optimizer fornumerical and engineering optimization problems)[J]. Computer Technology Journal,2020.[46]. GlobalLogic Inc.; GlobalLogic Acquires Meelogic Consulting AG, a European Healthcare and Automotive-Focused Software Engineering Services Firm[J]. Computer Technology Journal,2020.[47]. Engineering - Circuits and Systems Research; Data on Circuits and Systems Research Described by Researchers at Northeastern University (Softcharge: Software Defined Multi-device Wireless Charging Over Large Surfaces)[J]. Telemunications Weekly,2020.[48]. Soft Computing; Researchers from Department of Electrical and Communication Engineering Report on Findings in Soft Computing (Dynamic Histogram Equalization for contrast enhancement for digital images)[J]. Technology News Focus,2020.[49]Mohamed Ellithey Barghoth,Akram Salah,Manal A. Ismail. A Comprehensive Software Project Management Framework[J]. Journal of Computer and Communications,2020,08(03).[50]. Soft Computing; Researchers from Air Force Engineering University Describe Findings in Soft Computing (Random orthocenter strategy in interior search algorithm and its engineering application)[J]. Journal of Mathematics,2020.[51]. Soft Computing; Study Findings on Soft Computing Are Outlined in Reports from Department of MechanicalEngineering (Constrained design optimization of selected mechanical system ponents using Rao algorithms)[J]. Mathematics Week,2020.[52]Iqbal Javed,Ahmad Rodina B,Khan Muzafar,Fazal-E-Amin,Alyahya Sultan,Nizam Nasir Mohd Hairul,Akhunzada Adnan,Shoaib Muhammad. Requirements engineering issues causing software development outsourcing failure.[J]. PloS one,2020,15(4).[53]Raymond C.Z. Cohen,Simon M. Harrison,Paul W. Cleary. Dive Mechanic: Bringing 3D virtual experimentation using biomechanical modelling to elite level diving with the Workspace workflow engine[J]. Mathematics and Computers in Simulation,2020,175.[54]Emelie Engstr?m,Margaret-Anne Storey,Per Runeson,Martin H?st,Maria Teresa Baldassarre. How software engineering research aligns with design science: a review[J]. Empirical SoftwareEngineering,2020(prepublish).[55]Christian Lettner,Michael Moser,Josef Pichler. An integrated approach for power transformer modeling and manufacturing[J]. Procedia Manufacturing,2020,42.[56]. Engineering - Mechanical Engineering; New Findings from Leibniz University Hannover Update Understanding of Mechanical Engineering (A finite element for soft tissue deformation based on the absolute nodal coordinate formulation)[J]. Computer Technology Journal,2020.[57]. Science - Social Science; Studies fromUniversity of Burgos Yield New Information about Social Science (Diagnosis of Software Projects Based on the Viable System Model)[J]. Computer Technology Journal,2020.[58]. Technology - Powder Technology; Investigators at Research Center Pharmaceutical Engineering GmbH Discuss Findings in Powder Technology [Extended Validation and Verification of Xps/avl-fire (Tm), a Computational Cfd-dem Software Platform][J]. Computer Technology Journal,2020.[59]Guadalupe-Isaura Trujillo-Tzanahua,Ulises Juárez-Martínez,Alberto-Alfonso Aguilar-Lasserre,María-Karen Cortés-Verdín,Catherine Azzaro-Pantel.Multiple software product lines to configure applications of internet of things[J]. IETSoftware,2020,14(2).[60]Eduardo Juárez,Rocio Aldeco-Pérez,Jose.Manuel Velázquez. Academic approach to transform organisations: one engineer at a time[J]. IET Software,2020,14(2).[61]Dennys García-López,Marco Segura-Morales,Edson Loza-Aguirre. Improving the quality and quantity of functional and non-functional requirements obtained during requirements elicitation stage for the development of e-merce mobile applications: an alternative reference process model[J]. IETSoftware,2020,14(2).[62]. Guest Editorial: Software Engineering Applications to Solve Organisations Issues[J]. IET Software,2020,14(2).[63]?,?. Engine ControlUnit ? ? ?[J]. ,2020,47(4).[64]. Engineering - Software Engineering; Study Data from Nanjing University Update Understanding of Software Engineering (Identifying Failure-causing Schemas In the Presence of Multiple Faults)[J]. Mathematics Week,2020.[65]. Energy - Renewable Energy; Researchers from Institute of Electrical Engineering Detail New Studies and Findings in the Area of Renewable Energy (A Local Control Strategy for Distributed Energy Fluctuation Suppression Based on Soft Open Point)[J]. Journal of Mathematics,2020.[66]Ahmed Zeraoui,Mahfoud Benzerzour,WalidMaherzi,Raid Mansi,Nor-Edine Abriak. New software for the optimization of the formulation and the treatment of dredged sediments for utilization in civil engineering[J]. Journal of Soils andSediments,2020(prepublish).[67]. Engineering - Concurrent Engineering; Reports from Delhi Technological University Add New Data to Findings in Concurrent Engineering (Systematic literature review of sentiment analysis on Twitter using soft puting techniques)[J]. Journal of Engineering,2020.[68]. Engineering; New Findings from Future University in Egypt in the Area of Engineering Reported (Decision support system for optimum soft clay improvement technique for highway construction projects)[J]. Journal of Engineering,2020.[69]Erica Mour?o,Jo?o Felipe Pimentel,LeonardoMurta,Marcos Kalinowski,Emilia Mendes,Claes Wohlin. On the performance of hybrid search strategies for systematic literature reviews in softwareengineering[J]. Information and SoftwareTechnology,2020,123.[70]. Soft Computing; Researchers from Anna University Discuss Findings in Soft Computing (A novel fuzzy mechanism for risk assessment in software projects)[J]. News of Science,2020.软件工程英文参考文献三:[71]. Software and Systems Research; New Software and Systems Research Study Results from ChalmersUniversity of Technology Described (Why and How To Balance Alignment and Diversity of Requirements Engineering Practices In Automotive)[J]. Journal of Transportation,2020.[72]Anupama Kaushik,Devendra Kr. Tayal,Kalpana Yadav.A Comparative Analysis on Effort Estimation for Agile and Non-agile Software Projects Using DBN-ALO[J]. Arabian Journal for Science and Engineering,2020,45(6).[73]Subhrata Das,Adarsh Anand,Mohini Agarwal,Mangey Ram. Release Time Problem Incorporating the Effect of Imperfect Debugging and Fault Generation: An Analysis for Multi-Upgraded Software System[J]. International Journal of Reliability, Quality and Safety Engineering,2020,27(02).[74]Saerom Lee,Hyunmi Baek,Sehwan Oh. The role of openness in open collaboration: A focus onopen‐source software development projects[J]. ETRI Journal,2020,42(2).[75]. Soft Computing; Study Results from Computer Science and Engineering Broaden Understanding of Soft Computing (Efficient attribute selection technique for leukaemia prediction using microarray gene data)[J]. Computer Technology Journal,2020.[76]. Engineering - Computational Engineering; Findings from University of Cincinnati in the Area of Computational Engineering Described (Exploratory Metamorphic Testing for Scientific Software)[J]. Computer Technology Journal,2020.[77]. Organizational and End User Computing; Data from Gyeongnam National University of Science and Technology Advance Knowledge in Organizational and End User Computing (A Contingent Approach to Facilitating Conflict Resolution in Software Development Outsourcing Projects)[J]. Computer Technology Journal,2020.[78]. Soft Computing; Findings from Department of Industrial Engineering in the Area of Soft Computing Reported (Analysis of fuzzy supply chain performance based on different buyback contract configurations)[J]. Computer Technology Journal,2020.[79]Hana M kaouar,Bechir Zalila,Jér?me Hugues,Mohamed Jmaiel. A formal approach to AADL model-based software engineering[J]. International Journal on SoftwareTools for Technology Transfer,2020,22(5).[80]Riesch Michael,Nguyen Tien Dat,Jirauschek Christian. bertha: Project skeleton for scientific software.[J]. PloS one,2020,15(3).[81]. Computers; Findings from Department of Computer Sciences and Engineering Reveals New Findings on Computers (An assessment of software definednetworking approach in surveillance using sparse optimization algorithm)[J]. TelemunicationsWeekly,2020.[82]Luigi Ranghetti,Mirco Boschetti,FrancescoNutini,Lorenzo Busetto. “sen2r”: An R toolbox for automatically downloading and preprocessing Sentinel-2 satellite data[J]. Computers and Geosciences,2020,139.[83]Mathie Najberg,Muhammad Haji Mansor,ThéodoreT aillé,Céline Bouré,Rodolfo Molina-Pe?a,Frank Boury,José Luis Cenis,Emmanuel Garcion,CarmenAlvarez-Lorenzo. Aerogel sponges of silk fibroin, hyaluronic acid and heparin for soft tissueengineering: Composition-properties relationship[J]. Carbohydrate Polymers,2020,237.[84]Isonkobong Udousoro. Effective Requirement Engineering Process Model in Software Engineering[J]. Software Engineering,2020,8(1).[85]. Soft Computing; Research Conducted at Department of Computer Sciences and Engineering Has Updated Our Knowledge about Soft Computing [Hyperparameter tuning in convolutional neural networks for domain adaptation in sentiment classification (HTCNN-DASC)][J]. Network Weekly News,2020.[86]. Engineering - Software Engineering; Data on Software Engineering Discussed by Researchers at Universita della Svizzera italiana (Investigating Types and Survivability of Performance Bugs In Mobile Apps)[J]. Computer Technology Journal,2020.[87]. Engineering - Software Engineering; Findings from Nanjing University Broaden Understanding of Software Engineering (Boosting Crash-inducing Change Localization With Rank-performance-based Feature Subset Selection)[J]. Computer Technology Journal,2020.[88]. Engineering - Software Engineering; Study Data from Queen's University Belfast Update Knowledge of Software Engineering (Practical relevance of software engineering research: synthesizing the munity's voice)[J]. Computer Technology Journal,2020.[89]. Engineering - Software Engineering; Researchers from Concordia University Detail New Studies and Findings in the Area of Software Engineering (MSRBot: Using bots to answer questions from software repositories)[J]. Computer Technology Journal,2020.[90]Anonymous. DBTA LIVE[J]. Database Trends and Applications,2020,34(2).[91]Tachanun KANGWANTRAKOOL,Kobkrit VIRIYAYUDHAKORN,Thanaruk THEERAMUNKONG. Software Development Effort Estimation from Unstructured Software Project Description by Sequence Models[J]. IEICE Transactions on Information andSystems,2020,E103.D(4).[92]Reza Mohammadi,Reza Javidan,NegarRikhtegar,Manijeh Keshtgari. An intelligent multicast traffic engineering method over software defined networks[J]. Journal of High Speed Networks,2020,26(1).[93]. Engineering - Civil Engineering; HohaiUniversity Researchers Detail New Studies and Findings in the Area of Civil Engineering (An Experimental Study on Settlement due to the Mutual Embedding of Miscellaneous Fill and Soft Soil)[J]. Journal of Engineering,2020.[94]. Engineering - Biomechanical Engineering; Researchers from Washington University St. LouisDetail New Studies and Findings in the Area of Biomechanical Engineering (Estimation of Anisotropic Material Properties of Soft Tissue By Mri ofUltrasound-induced Shear Waves)[J]. Journal of Engineering,2020.[95]. Engineering - Rock Engineering; Reports from University of Alicante Add New Data to Findings in Rock Engineering (Evaluation of Strength and Deformability of Soft Sedimentary Rocks In Dry and Saturated Conditions Through Needle Penetration and Point Load Tests: a Comparative ...)[J]. Journal of Engineering,2020.[96]. Computers; Study Findings from Department of Electrical and Communication Engineering Broaden Understanding of Computers [Improved energy efficient design in software defined wireless electroencephalography sensor networks (WESN) using distributed ...][J]. Network Weekly News,2020.[97]Mouro Erica,Pimentel Joo Felipe,MurtaLeonardo,Kalinowski Marcos,Mendes Emilia,Wohlin Claes. On the Performance of Hybrid Search Strategies for Systematic Literature Reviews in SoftwareEngineering[J]. Information and SoftwareTechnology,2020(prepublish).[98]Osuna Enrique,Rodrguez Luis-Felipe,Gutierrez-Garcia J. Octavio,Castro Luis A.. Development of putational models of emotions: A software engineering perspective[J]. Cognitive Systems Research,2020,60(C).[99]Sharifzadeh Bahador,Kalbasi Rasool,Jahangiri Mehdi,Toghraie Davood,Karimipour Arash. Computer modeling of pulsatile blood flow in elastic arteryusing a software program for application in biomedical engineering[J]. Computer Methods and Programs in Biomedicine,2020.[100]Shen Xiaoning,Guo Yinan,Li Aimin. Cooperative coevolution with an improved resource allocation for large-scale multi-objective software projectscheduling[J]. Applied Soft Computing,2020,88(C).[101]Jung Jaesoon,Kook Junghwan,Goo Seongyeol,Wang Semyung. Corrigendum to Sound transmission analysis of plate structures using the finite element method and elementary radiator approach with radiator error index [Advances in Engineering Software 112 (2017 115][J]. Advances in Engineering Software,2020,140(C).[102]Zhang Chenyi,Pang Jun. Preface for the special issue of the 12th International Symposium on Theoretical Aspects of Software Engineering (TASE2018[J]. Science of Computer Programming,2020,187(C).[103]Karras Oliver,Schneider Kurt,Fricker Samuel A.. Representing software project vision by means of video: A quality model for vision videos[J]. Journal of Systems and Software,2020,162(C).[104]Sutanto Juliana,Jiang Qiqi,Tan Chuan-Hoo. The contingent role of interproject connectedness in cultivating open source software projects[J]. The Journal of Strategic InformationSystems,2020(prepublish).[105]Weiner Iddo,Feldman Yael,Shahar Noam,Yacoby Iftach,Tuller Tamir. CSO A sequence optimization software for engineering chloroplast expression in Chlamydomonas reinhardtii[J]. AlgalResearch,2020,46(C).。
Autodesk DirectConnect 2013 安装指南说明书

Portions relating to Threading Building Blocks Copyright (C) 2005-2008 Intel Corporation. All Rights Reserved.
PCRE LICENSE
PCRE is a library of functions to support regular expressions whose syntax and semantics are as close as possible to those of the Perl 5 language.
Pentax KP 使用手册说明书

Noticeable better af fine adjustment you can be able to this pentax of and. Remember that was this pentax kp manual wire hookup is a filter simulator function may earn an image sync are subject is an autofocus systems. People can apply a pentax user manual in the system packed with other devices, at the status af. Default function for and user is shaken during long time to the monitor also for your computer is a superb camera control dials as cancel menu items are nearly perfect. Usually seen pixel by pentax user manual before using the shutter speed for being accidentally deleted images at different and take a kind of. Discrepancies in pentax user and go practice the light settings select af mode in playback functions in tracking, so that adjusts the live previews on. Nature and video recording with pentax kp getting started explains your pentax! Refresh the user manual focusing area by fujitsu, while checking the kp in. Diopter correction functions in pentax kp camera until perfect focus on the features and off the brightness retrieves the
微软消息分析器:一款高级网络包分析器说明书

Neil B MartinT est Manager WSSC-Interop and T oolsMicrosoft CorporationMicrosoft Message Analyzer Packet Analysis at a Higher LevelContent•Packet Analyzer -review •Abstracting views of protocols •Alternative data sources •ETW•Remote Capture•Bluetooth•USB•Evtx•Logs filesMessage Analyzer –What is it?• A packet analyzer is a computer program or a piece of computer hardware that can intercept and log traffic passing over all or part of a network•Packet analyzers capture network packets in real time and display them in human-readable format•WireShark, Microsoft NetMon3.4•These tools are dissectors•If they recognize a packet they dissect it and display the inner fields of the packet•The parsers are written based on the protocol specifications or in some cases through reverse engineering of the protocols whenno specification is available•Dissection and Abstraction•We want to allow a higher level of abstraction view of protcols•Pattern Matching•Match up request/response pairs where possible•Called an operation•Different Viewers and Charts•Addressing many of the challenges of diagnosing modern networks •Protocol Validation•Identify packets that do not match the specification•Data capture from multiple sources•NDIS, Bluetooth, USB, Windows Firewall Layer, Web Proxy•Header only network capture•Reduce data in volume scenarios•Correlation of data across multiple data sources and logs•Load and display multiple data source•Message Analyzer captures ETW •ETW -Event Trace for Windows •Message Capture from:•Traditional NDIS traffic from the Network Adapter •Windows Filtering Platform 9aka Firewall)•Web proxy•USB ports•Bluetooth•Windows SMB Client•Windows SMB Server ……•E vent T racing for W indows ETW•High-resolution (<<100µs)logging infrastructure allows any component to tell the outside world what it is currently doing by firing ETW events.• A powerful diagnostic tool to log every methods/lines inside the code with reasonable performance fordebugging/troubleshooting.•MSDN on ETW/en-us/library/bb968803(VS.85).aspxAll Windows ETW Sources are available to Message Analyzer•Capability to perform remote capture •Select machine and give credentials•Collect data via ETW from NIC on remote machine•Powerful, extensible viewing and analysis •Browse, Select, View•Browse for messages from various sources (live, or stored)•Select a set of messages from those sources by characteristic(s)•View messages in a provided viewer, configure or build your own • A new high-level grid view•High level “Operations” view with automatic re-assembly•“Bubbling up” of errors in the stack to the top level•Ability to drill down the stack to underlying messages and/or packets•On the fly grouping, filtering, finding, or sorting by any message property •Payload rendering•V alidation of message structures, behavior, and architecture•Does the protocol comply with the specifications?•Over 450 published specifications for Windows Protocols(as of Windows 8.1)(/en-us/library/gg685446.aspx)Available online and as PDFContinue to publish new documents with each release of Windows •Continue to develop tools and technology to aid with the development of protocol documents, parsers and test technologyHow to get MA: /en-us/download/details.aspx?id=40308 How to get help: Blog,Operating Guide, T echnet Forum for Message Analyzer •We invite you to Explore Message Analyzer•Connect Community•https:///site216/。
基于自适应多尺度超螺旋算法的无人机集群姿态同步控制

基于自适应多尺度超螺旋算法的无人机集群姿态同步控制蔡运颂 1, 2许 璟 1, 2牛玉刚1, 2摘 要 四旋翼无人机(Unmanned aerial vehicle, UAV)系统姿态角和角速度分别为运行在不同时间尺度上的慢、快动态. 由于输入扰动的上界难以精确估计, 本文提出一种基于自适应多尺度超螺旋(Super-twisting, STW)滑模算法的无人机集群一致性控制策略. 首先, 建立无人机集群系统的姿态角模型, 并通过奇异摄动理论将其化为两时间尺度形式. 基于系统的快慢特性, 本文设计两时间尺度的超螺旋滑模算法, 并采用自适应增益处理无人机集群系统的未知边界非线性. 此外,还提出一种改进型自适应多尺度超螺旋滑模算法, 进一步减少系统的一致性收敛时间, 实现无人机集群姿态角有限时间内同步. 最后通过仿真分析, 验证两种自适应多尺度超螺旋算法的正确性和有效性.关键词 奇异摄动, 超螺旋算法, 多尺度, 姿态协同, 四旋翼无人机引用格式 蔡运颂, 许璟, 牛玉刚. 基于自适应多尺度超螺旋算法的无人机集群姿态同步控制. 自动化学报, 2023, 49(8):1656−1666DOI 10.16383/j.aas.c220759Attitude Consensus Control of UAV Swarm Based onAdaptive Multi-scale Super-twisting AlgorithmCAI Yun-Song 1, 2 XU Jing 1, 2 NIU Yu-Gang 1, 2Abstract In a UAV (unmanned aerial vehicle) system, the attitude angle and angular velocity of the UAV are, re-spectively, the slow and fast dynamics operating in different time scales. Due to the difficulty in the estimation of the bound of disturbance, this paper proposes a control method for UAV swarm, based on the adaptive multi-scale STW (super-twisting) sliding mode algorithm. First, the attitude model of the UAV swarm system is established,which is transformed into a two-time-scale model via singular perturbation theory. On this basis, this paper designs a two-time-scale STW sliding mode algorithm with adaptive gains to deal with the perturbations and unknows.Furthermore, by adding a few linear iterms, a modified adaptive STW control algorithm is also provided, which further reduces the convergence time and achieves the synchronization of the attitudes in finite time. Finally,the effectiveness of two different adaptive multi-scale STW algorithms are verified through simulations.Key words Singular perturbation, STW, multi-scale, attitude coordination, quadrotorsCitation Cai Yun-Song, Xu Jing, Niu Yu-Gang. Attitude consensus control of UAV swarm based on adaptive multi-scale super-twisting algorithm. Acta Automatica Sinica , 2023, 49(8): 1656−1666四旋翼无人机[1−2](Unmanned aerial vehicle,UAV)具有结构简单、飞行精准、机动性强等优点.因此, 在军事打击[3−4]、载物[5−6]、测量[7−8]、灾害监测[9]等方面, 有着很好的应用. 然而随着控制任务复杂度的增加, 例如无人机表演[10]、沿海侦察、集群打击等, 仅凭一台无人机难以完成, 因此需要多台无人机集群协同作业. 在对四旋翼无人机进行建模时,通常简单地认为无人机模型是单一尺度的. 然而实际上, 无人机的姿态角与角速度并不处于同一时间尺度, 这是由无人机中的参数量纲差异引起的. 因此, 无人机集群的奇异摄动建模具有重要意义, 通过奇异摄动建模可以抽提出无人机状态的快慢特性. 然而, 对于奇异摄动无人机集群系统而言, 基于单一时间尺度的控制策略效果欠佳.目前, 四旋翼无人机集群控制方法主要有反步法、模糊控制以及PID (Proportion-integral-deriv-ative)控制方法等. 文献[11]针对多四旋翼无人机的编队控制, 采用反步法实现了四旋翼无人机群对期望轨迹的跟踪功能. 文献[12]建立了四旋翼无人机的姿态动力学模糊模型, 设计了模糊反馈控制器,收稿日期 2022-09-22 录用日期 2023-02-10Manuscript received September 22, 2022; accepted February 10, 2023国家自然科学基金(62173141, 62073139), 上海市自然科学基金(22ZR1417900)资助Supported by National Natural Science Foundation of China (62173141, 62073139) and the Natural Science Foundation of Shanghai (22ZR1417900)本文责任编委 李鸿一Recommended by Associate Editor LI Hong-Yi1. 华东理工大学信息科学与工程学院 上海 2002372. 华东理工大学能源化工过程智能制造教育部重点实验室 上海 2002371. College of Information Science and Engineering, East China University of Science and Technology, Shanghai 2002372. Key Laboratory of Intelligent Manufacturing of Energy and Chemical Processes of Ministry of Education, East China University of Sci-ence and Technology, Shanghai 200237第 49 卷 第 8 期自 动 化 学 报Vol. 49, No. 82023 年 8 月ACTA AUTOMATICA SINICAAugust, 2023实现了四旋翼无人机集群控制. 文献[13]设计了一种BP (Back propagation)神经网络辅助的PID 无人机编队智能算法, 实现了PID 参数的优化整定[14].对四旋翼无人机集群的研究中, 姿态协同是四旋翼无人机群实现队形控制、协同避障等任务的基础.文献[15]基于半定规划进行迭代区域扩张完成了多无人机的队形设计. 文献[16]利用神经网络预测姿态偏差, 将其集成于分散式容错协同控制器中,实现了姿态角的一致性. 然而, 考虑到无人机的动态模型中存在着内部结构不确定, 外界扰动影响等问题, 导致基于无扰动简化模型的控制方案效果有限.sgn (·)在姿态协同控制中, 滑模控制是一类有效的鲁棒控制方法, 对于外部输入扰动或者参数不确定性具有不变性、有限时间可达等优点. 目前, 滑模控制方法大致可以分为一阶滑模与高阶滑模. 如文献[17]基于一阶滑模与低通滤波器的结合, 实现了对直流电机位置的控制. 然而, 一阶滑模是直接基于滑模变量的一阶导数设计的, 采用了切换控制律, 产生了严重的抖振现象, 影响系统性能. 在二阶滑模算法中, 超螺旋滑模算法(Super-twisting, STW)的应用最为广泛. 这是由于超螺旋滑模控制器采用了连续控制结构, 引入了积分项, 避免了使用切换项, 响应速度快, 对抖振抑制能力强, 并且可以驱使滑模变量及其导数在有限时间内收敛到稳定点. 同时, 能够处理上界为依赖于状态的函数以及符合Lipschitz 条件[18]的扰动. 文献[19]采用了超螺旋滑模控制策略, 提高了永磁同步电机的转速响应. 文献[20]提出了一种基于超螺旋滑模的干扰观测器, 实现了对未估计的干扰的精细化补偿. 然而上述滑模控制方法都是基于已知上界的非线性, 这在无人机中是无法实现的.为了实现姿态协同的稳准快, 本文设计了一种新型的分尺度自适应STW 算法, 通过分尺度自适应STW 控制器产生的不同时间尺度上的快、慢控制律, 实现了四旋翼无人机奇异摄动多智能体模型中的分尺度精确控制. 同时, 通过自适应增益实现扰动未知情况下的快速补偿. 与现有部分研究成果相比, 本文的主要贡献归纳为如下几个方面:1) 多时间尺度超螺旋控制结构: 本文提出了多时间尺度超螺旋滑模控制器的设计方法, 在控制器中引入两个时间尺度, 通过奇异摄动方法来有效处理四旋翼无人机姿态角系统状态同步问题.2) 自适应分布式控制器: 本文采用了分布式的控制结构, 对每个四旋翼无人机智能体分别设计了一个自适应增益, 让其自适应于四旋翼无人机智能体本身以及与其他智能体间的耦合.n ×n X −1T ⊗符号描述. 对于一个 维的矩阵 , 上标 表示矩阵的逆, 上标 表示矩阵的转置, 表示diag {a 1,a 2,a 3}a 1,a 2,a 3n b T sgn col {b 1,b 2,b 3}|b |b ||b ||b 12b min (ω)ωmax (ω)ωI 303×03×1×矩阵的克罗内克积, 表示对角线上的元素为 的矩阵. 对于一个 维向量 ,上标 表示向量的转置, 表示符号函数, 表示向量按列排序, 表示 内元素取绝对值后的向量, 表示向量的二范数, 表示 内元素开根号后的向量. 表示取集合 中最小的数, 表示取集合 中最大的数. 与 分别表示3 3的单位对角阵与零矩阵. 表示3 1的零矩阵.1 四旋翼无人机模型n 假设四旋翼无人机多智能体系统中具有 个四旋翼无人机智能体, 单个四旋翼无人机的姿态非线性动力学方程为[21]:i =1,···,n,ϕi θi ψi i ϕi ∈(−π/2,π/2)θi ∈(−π/2,π/2)ψi ∈(0,2π)I xi ,I yi ,I zi x b y b z b J ri w ri =w 1i −w 2i +w 3i −w 4i w 1i ,w 2i ,w 3i ,w 4iJ ri w ri ˙θi J ri w ri ˙ϕi k axi ,k ayi ,k azi u 1i ,u 2i ,u 3i 其中, 、 、 分别表示第 个无人机的横滚角、俯仰角、偏航角, 、 、 , 表示无人机体绕机体坐标系 , , 轴的转动惯量, 表示无人机的电动机和桨叶的转动惯量. 输入扰动为, 其中, 表示无人机四个旋翼的转速, 、 表示陀螺力矩, 表示空气阻力矩系数, 表示无人机旋翼对其三个姿态角的控制量.I xi ,I yi ,I ziϵ=min (I xi ,I yi ,I zi )¯Ixi =I xi /ϵ¯I yi =I yi /ϵ¯I zi =I zi /ϵ¯J ri =J ri /ϵ¯kaxi =k axi /ϵ¯k ayi =k ayi /ϵ¯k azi =k azi /ϵˆI i =diag {¯I xi ,¯I yi ,¯I zi }xi =(ϕi ,θi ,ψi )T vi =(˙ϕi ,˙θi ,˙ψi )T u i =ˆI −1i(u 1i ,u 2i ,u 3i )T i 由于四旋翼无人机存在着小参量 等, 呈现较为显著的奇异摄动现象[22]. 因此对四旋翼无人机智能体系统进行奇异摄动的建模. 定义, , , , , , ,, , , , . 基于此, 第 个四旋翼无人机的姿态非线性动力学矩8 期蔡运颂等: 基于自适应多尺度超螺旋算法的无人机集群姿态同步控制16572 系统描述与引理将式(2)表示为状态空间方程:G =[a ij ]a ij i j i,j =1,2,3,···,m 假设每个智能体都可以访问邻接的智能体的输出相对值, 并且相关的邻接矩阵表示为 , 其中 表示第 个智能体与第 个智能体之间连接的权值, 若无连接则为0, 且 .定义一致性角度误差和角速度误差为:由式(3)、(4), 可得以下同步误差模型:为了后续分析, 在此给出假设和引理.¯φi (t,g i )=∑n j =1,j =i a ij (g i (v i ,w ri )−g j (v j ,w rj ))||¯φi (t,g i )||≤δi ||s i (t )||12¯φi (t,g i )δi >0假设 1. 令 , 且 , 其中, 满足Lipschitz 条件,存在但未知.Z i (i =1,···,5)Z i =Z T i (i =1,···,4)引理 1[23]. 若存在矩阵 且 , 满足以下线性矩阵不等式:Z (ϵ)>0ϵ∈(0,¯ϵ]Z (ϵ)=[Z 1+ϵZ 3ϵZ T5ϵZ 5ϵZ 2].则可以得到 , 对任意的 都成立, 其中, z 1z 2z 3引理 2. 对于任意列向量 , 和 . 有以下不等式成立:a =z 2z T2z 3b =z 1证明. 令 , , 则l >0x y ±xy <lx 2+14l y 2引理 3[24]. 给定任意正定标量 , 对于任意标量 , , 有以下不等式成立: .n x P n ×n 引理 4[25]. 对于一个 维非0列向量, 为 维的Hermitian 矩阵, 有如下性质:3 四旋翼无人机集群姿态角一致性分析设计以下受导引型奇异摄动二阶滑模动态:l i l 1>0l i =0(i =1)x 0(t )s i (t )其中, 表示追踪系数, , , 表示姿态角的跟踪值, 表示第i 个滑模变量.根据式(5)可得, 滑模动态(6)的一阶导数为:3.1 自适应多尺度超螺旋算法受文献[26]的启发, 考虑到系统(5)的两时间尺度特性, 设计以下自适应STW 滑模控制器:αi (t )βi (t )其中, 和 表示两个自适应增益.将式(8)代入式(7), 可得:下面的定理研究了在自适应多尺度STW 算法控制下的四旋翼无人机群在有限时间内的姿态协同.p 1i >0p 2i >0b 1i >0b 2i >0γ1i >0γ2i >0¯ϵ>0定理 1. 给定 , , , ,, , 存在 , 当满足:1658自 动 化 学 报49 卷以及系统的自适应增益导数满足:ϵ∈(0,¯ϵ]则对任意的 , 四旋翼无人机集群系统的姿态角将会在有限时间内趋于一致.证明. 构造新的状态变量:根据式(9)、(12), 可得:ηi =col {−z 1i z T1i2||z 1i ||3(z 2i +φi (t,g i )),03×1}φi (t,g i )=diag {sgn (s i (t ))}¯φi (t,g i )其中, , .z 1i z 2i s i˙si 由式(11)、(13), 可知: 当 , 趋于0时, 会趋于0, 再根据式(9)以及假设1, 也会趋于0.考虑以下奇异摄动Lyapunov 函数:F ϵ=diag {1,ϵ}其中, ˆαi αi (t )ˆβi βi (t )P i (ϵ)>0V 0i (t,ϵ)=z TP i (ϵ)z i 表示 的上界, 表示 的上界. 根据引理1, 成立的充分条件为式(10). 定义, 并对其求导可得:由假设1, 可知:可以构造以下不等式:其中,p (t )=2z T i ¯P i (ϵ)ηi 令 , 易得:由引理2, 将式(16)转化为:由引理3, 可构造:联立式(17)和式(18), 可得:Y i (ϵ)=diag {d 1,d 2}其中, 联立式(14)、(15)、(19), 可得:8 期蔡运颂等: 基于自适应多尺度超螺旋算法的无人机集群姿态同步控制1659βi (t )=−ϵp 2i 2p 3iαi (t )+p 1ip 3i Q i (ϵ)>0设计 . 根据Schur 补引理[27], 可得 , 当以下条件成立时:由引理4, 可知:基于式(21), 我们有:根据式(20)、(21)、(22), 可得:r 1i =λmin (Q i )λ12min (P i)λmax (P i )其中, .βi (t )≤ˆβi αi (t )≤ˆαi 由于 , . 结合式(23), 可得:1γ1i˙αi (t )−b 1i √2γ1i=01γ2i˙βi (t )−b 2i √2γ2i=0αi (t )βi (t )令式(24)中 , , 则可得 , 应满足式(11). 将式(11)代入式(24)中, 根据柯西不等式[28], 可得:ˇr i =min (r 1i ,b 1i ,b 2i )ˇr k =min (ˇr i )其中, , .由此可见, 四旋翼无人机集群系统的一致性误差在有限时间内稳定. □3.2 改进型自适应多尺度超螺旋算法由于定理1中, 在自适应多尺度STW 算法控制下的系统收敛时间相对较长. 因此在文献[29]的启发下, 设计以下改进型自适应STW 滑模控制器:k 1i k 2i 其中, 、 为两个增益.将式(26)代入式(6), 可得:下面的定理研究了在改进型自适应多尺度STW滑模算法的控制下, 四旋翼无人机集群系统的姿态角能够快速地趋于一致.b 3i >0b 4i >0b 5i >ˆαi b 6i >ˆβi ¯ϵ>0定理 2. 给定 , , , . 在控制器(26)作用下, 系统状态将快速趋于一致, 当存在 , 使得以下式子成立时:其中,对应的相关参数为:1660自 动 化 学 报49 卷证明. 构造新的状态变量:根据式(27)、(29), 可得:E ϵ=diag {I 3,I 3,ϵI 3}其中,考虑以下奇异摄动Lyapunov 函数:P 2i (ϵ)=(¯P2i (ϵ)E ϵ)⊗I 3>0其中, ,V 20i (t,ϵ)=ˆz T i P 2i (ϵ)ˆz i 定义 ,对其求导可得:对应的相关参数为:由假设1, 可知:可以构造以下不等式:其中,8 期蔡运颂等: 基于自适应多尺度超螺旋算法的无人机集群姿态同步控制1661p 2(t )=2ˆz T i ¯P 2i (ϵ)η2i 令 , 易得:根据引理2, 将式(33)转化为:根据引理3, 可构造:联立式(34)、(35), 可得:d 4=p 11i 4c +p 12i 4c −ϵp 13i (1+c 8i )其中, ,联立式(31)、(32)、(36), 可得:其中,W i (ϵ)>0X i (ϵ)>0˙V20i (t,ϵ)<0由式(37)可知: , 时,成立.由引理4, 可知:基于式(38), 可得:根据式(37)、(39), 可得:r 2i =λ12min (P 2i )λmin (¯W i )λmax (P 2i ),r 3i =λmin (¯Xi )λmax (P 2i )其中, .将式(40)代入式(30), 可得:根据柯西不等式[28], 将式(41)转化为:1662自 动 化 学 报49 卷ˇr 2i =min (r 2i ,b 1i ,b 2i )ˇr 3i =min (r 3i ,b 3i ,b 4i )其中, , .1γ1i˙αi (t )−b 3i b 5i2γ1i−b 1i √2γ1i=01γ2i ˙βi (t )−b 4ib 6i2γ2i−b 2i √2γ2i=0令式(42)中 ,, 可得:则式(42)可转化为:结合式(30)、(43), 根据柯西不等式[28], 可得:ˇr 2k =min (ˇr 2i )ˇr 3k =min (ˇr 3i )其中, , .即在改进型自适应STW 滑模控制器(26)的作用下, 无人机集群系统的误差有限时间内稳定.□4 一致性误差收敛时间分析在本节, 我们将比较自适应多尺度STW 算法和改进型自适应多尺度STW 算法的收敛时间, 进一步分析改进型算法具有更短的收敛时间的原因.在控制器(8)的作用下, 根据式(25), 可得:z i t r 1d t V12(t,ϵ)[t 0,t r 1]假定状态 在 时刻收敛, 将式(45)两边同乘, 并在 上进行积分:t 0=0z i t r 1V 12(t r 1,ϵ)=0其中, , 状态 在 时刻收敛, 即 , 代入式(46)可得:在控制器(26)的作用下, 由式(44)可得:ˆzi t r 2d tˇr 2k ¯V12(t,ϵ)+ˇr 3k ¯V(t,ϵ)[t 0,t r 2]假定状态 在 时刻收敛, 将式(48)两边同乘, 并在 上进行积分:t 0=0,f (t )=2ˇr 3k ln (1+ˇr 3k ¯V12(t,ϵ)ˇr 2k)ˆz i t r 2¯V(t r 2,ϵ)=0ln (1+ˇr 3k ¯V12(t r 2,ϵ)ˇr 2k)=0其中, . 状态 在 时刻收敛, 即 , 则 , 代入式(49), 可得:ln (·)ln (·)t r 2<t r 1由式(47)、(50)可知, 在改进型自适应STW 滑模控制器(26)的作用下, 收敛时间与 函数相关联, 由于 函数的取对数特性, 使得无人机集群系统的一致性收敛时间更短, 即 .5 仿真分析a 12=1a 13=2a 23=3为验证所建立模型与控制律的有效性, 本次仿真选择了三个四旋翼无人机智能体集群, 三个智能体之间的交互关系由无向图表示, 且 , , . 无人机间的连接方式可参照图1.132...u 1u 2u iu 3图 1 四旋翼无人机多智能体Fig. 1 The multi-agent of quadrotorsI x 1=I y 1=6.22×10−3kg ·m 2I z 1=1.12×10−3kg ·m 2I x 2=I y 2=l 9.22×10−3kg ·m 2I z 2=2.12×10−3kg ·m 2I x 3=I y 3=3.22×10−3kg ·m 2I z 3=7.12×10−4kg ·m 2J r 1=6×10−5kg ·m 2J r 2=9×10−5kg ·m 2J r 3=3×10−5kg ·m 2k ax 1=k ay 1=k az 1=1.2×10−4N ·s /m k ax 2=k ay 2=k az 2=2.2×10−4N ·s /m kax 3=k ay 3=k az 3=7.2×10−5N ·s /m ,ϵ=7.12×10−4.四旋翼无人机绕机体坐标系的转动惯量为: , ,, , , . 四旋翼无人机的电动机和桨叶的转动惯量为: , ,. 四旋翼无人机的空气摩擦阻力矩系数为: ,, 取 四旋翼无人机初始姿态角与角速度为:8 期蔡运颂等: 基于自适应多尺度超螺旋算法的无人机集群姿态同步控制1663l 1=1w ri =5sin (t )x 0(t )=(π4sin (t ),π4sin (t ),π4sin (t )+π2)T跟踪系数 , 非线性项中 , 跟踪姿态角 .为了实现无人机的姿态角的同步, 仿真中采用了两种控制器对无人机姿态集群系统进行控制:b 11=2b 12=2.2b 13=2.4b 21=1b22=1.2b 23=1.4γ11=2γ12=3γ13=4p 11=−p 22=p 31=1p 12=−p 22=p 32=1.2p 13=−p 23=p 33=1.4βi (t )αi (t )1) 采用自适应多尺度STW 控制器(8), 对应的控制器相关参数为: , , ,, , , , ,. , , . 自适应增益 , 形式如式(11)所示.k 11=1k 12=1.1k 13=1.2k 21=2k 22=2.1k 23=2.2b 3i =0.1b 4i =0.1b 5i =8b 6i =8b 21=1b 22=1.2b 23=1.4γ21=1γ22=2γ23=3βi (t )αi (t )2) 采用改进型自适应多尺度STW 控制器(26), 对应的控制器相关参数为: , ,, , , . ,, , . , , , , , . 自适应增益 , 为:图2为在自适应多尺度STW 控制器(8)作用下的四旋翼无人机的姿态角状态轨迹曲线. 从中可以看出无人机集群系统的姿态角在有限时间内实现状态同步. 图2(d)为自适应增益变化曲线, 可以看出, 自适应增益持续增加直至无人机姿态角协同.图3表明: 在改进型自适应多尺度STW 控制器(26)作用下, 也能够使得无人机集群系统姿态角在有限时间内达到一致. 两种控制算法下系统的性能指标如表1所示, 主要从平均收敛时间、平均稳态误差这两个指标进行比较. 由表1可知, 在改进型自适应多尺度STW 算法控制下的无人机集群系统的快速性明显增加, 准确性略微减弱. 相对于文献[30]提出的控制算法, 本文提出的这两种算法在收敛时间上更短, 控制的准确性更高.6 结论本文针对四旋翼无人机系统中具有的多时间尺度特性, 以及存在未知边界非线性的问题, 设计了一种自适应多尺度STW 滑模算法.将无人机快慢系统“分而治之”, 实现了分尺度精确控制. 并且通过该算法在有效削减滑模动态抖振的同时, 还保证了无人机集群系统在有限时间内的一致性. 本文还t /s−−R o l l a n g l e /r a d(a) 无人机横滚角变化曲线(a) Quadrotors roll anglechange curvet /s(b) 无人机俯仰角变化曲线(b) Quadrotors pitch anglechange curve t /s(c) 无人机偏航角变化曲线(c) Quadrotors yaw anglechange curvet /s (d) 自适应增益 a i (t ) 变化曲线(d) Adaptive gain a i (t )variation curve −−Y a w a n g l e /r adA d a p t i v e g a i n图 2 自适应多尺度STW算法控制下的无人机姿态历时曲线Fig. 2 Trajectories of attitudes under the adaptivemulti-scale STW controllert /s(a) 无人机横滚角变化曲线(a) Quadrotors roll anglechange curvet /s(b) 无人机俯仰角变化曲线(b) Quadrotors pitch anglechange curve t /s(c) 无人机偏航角变化曲线(c) Quadrotors yaw anglechange curve t /s (d) 自适应增益 a i (t ) 变化曲线(d) Adaptive gain a i (t )variation curve−−−R o l l a n g l e /r a d−Y a w a n g l e /r a d A d a p t i v e g a i n图 3 改进型自适应多尺度STW 算法控制下的无人机姿态历时曲线Fig. 3 Trajectories of attitudes under the modifiedadaptive multi-scale STW controller1664自 动 化 学 报49 卷设计了一种改进型自适应多尺度STW 滑模算法,增加了系统的快速性. 最后通过仿真验证了两种控制方法的有效性, 实现了无人机集群系统的姿态协同.ReferencesXu J, Fridman E, Fridman L, Niu Y G. Static sliding mode con-trol of systems with arbitrary relative degree by using artificial delays. IEEE Transactions on Automatic Control , 2020, 65(12):5464−54711Xu Jing, Cai Chen-Xiao, Li Yong-Qi, Zou Yun. Dual-loop path tracking and control for quad-rotor miniature unmanned aerial ve-hicles. Control Theory & Applications , 2015, 32(10): 1335−1342(许璟, 蔡晨晓, 李勇奇, 邹云. 小型四旋翼无人机双闭环轨迹跟踪与控制. 控制理论与应用, 2015, 32(10): 1335−1342)2Zhou Xiao-Cheng, Yan Jian-Gang, Xie Yu-Peng, Zhai Hong-Jun. Task distributed algorithmic for multi-UAV based on auc-tion mechanism. Journal of Naval Aeronautical and Astronautic-al University , 2012, 27(3): 308−312(周小程, 严建钢, 谢宇鹏, 翟鸿君. 多无人机对地攻击任务分配算法. 海军航空工程学院学报, 2012, 27(3): 308−312)3Chang Yi-Zhe, Li Zhan-Wu, Yang Hai-Yan, Luo Wei-Ping, Xu An. A decision-making for multiple target attack based on char-acteristic of future long-range cooperative air combat. Fire Con-trol & Command Control , 2015, 40(6): 36−40(常一哲, 李战武, 杨海燕, 罗卫平, 徐安. 未来中远距协同空战多目标攻击决策研究. 火力与指挥控制, 2015, 40(6): 36−40)4Luo C, Yu L J, Ren P. A vision-aided approach to perching a bioinspired unmanned aerial vehicle. IEEE Transactions on In-dustrial Electronics , 2018, 65(5): 3976−39845De Castro A I, Torres-Sanchez J, Pena J M, Jimenez-Brenes F M, Csillik O, Lopez-Granados F. An automatic random forest-OBIA algorithm for early weed mapping between and within crop rows using UAV imagery. Remote Sensing , 2018, 10(2):Article No. 2856Kim B O, Yun K H, Chang T S, Bahk J J, Kim S P. A prelim-inary study on UAV photogrammetry for the hyanho coast near the military reservation zone, eastern coast of Korea. Ocean and Polar Research , 2017, 39(2): 159−1687Wang Ning, Wang Yong. Fuzzy uncertainty observer based ad-aptive dynamic surface control for trajectory tracking of a quad-rotor. Acta Automatica Sinica , 2018, 44(4): 685−695(王宁, 王永. 基于模糊不确定观测器的四旋翼飞行器自适应动态面轨迹跟踪控制. 自动化学报, 2018, 44(4): 685−695)8Vallejo D, Castro-Schez J J, Glez-Morcillo C, Albusac J. Multi-agent architecture for information retrieval and intelligent mon-itoring by UAVs in known environments affected by cata-strophes. Engineering Applications of Artificial Intelligence ,2020, 87: Article No. 1032439Xie Hai-Jun, Liang Zhan-Min, Wang Jian. Design and imple-mentation of control system of UAV formation performance.Electronic Design Engineering , 2021, 29(17): 75−79(谢海军, 梁湛民, 王健. 无人机编队表演控制系统设计与实现. 电子设计工程, 2021, 29(17): 75−79)10Yang Ming-Yue, Shou Ying-Xin, Tang Yong, Liu Chang, Xu Bin. Multi-Quadrotor UAVs formation maintaining and colli-11sion avoidance control. Acta Aeronautica et Astronautica Sinica ,2022, 43: 1−11(杨明月, 寿莹鑫, 唐勇, 刘畅, 许斌. 多四旋翼无人机编队保持与避碰控制. 航空学报, 2022, 43: 1−11)Mao X, Zhang H, Wang Y. Flocking of quad-rotor UAVs with fuzzy control. ISA Transactions , 2018, 74: 185−19312Liu Ming-Wei, Gao Bing-Bing, Wang Peng-Fei, Liu Ya-Nan, Li Yi-Meng, Li Pei-Qi. Research on UAV formation obstacle avoid-ance flight based on neural network adaptive PID control. Un-manned Systems Technology , 2022, 5(2): 22−32(刘明威, 高兵兵, 王鹏飞, 刘亚南, 李怡萌, 李沛琦. 基于神经网络自适应PID 的无人机编队避障飞行控制研究. 无人系统技术,2022, 5(2): 22−32)13Li Xi-Kang, Xu Jing, Niu Yu-Gang. Memory proportional-integ-ral-retarded output sliding mode controller design. Control The-ory & Applications , 2022, 3: 1−9(李习康, 许璟, 牛玉刚. 带记忆比例−积分−时滞输出滑模控制器设计. 控制理论与应用, 2022, 3: 1−9)14Tian Bo-Lin, Li Pin-Pin, Lu Han-Chen, Zong Qun. Trajectory and attitude coordinated control of multiple unmanned aerial vehicles in complex environments. Acta Aeronautica et Astro-nautica Sinica , 2020, 41: 36−43(田栢苓, 李品品, 鲁瀚辰, 宗群. 复杂环境下多无人机轨迹姿态协同控制. 航空学报, 2020, 41: 36−43)15Yu Z Q, Liu Z X, Zhang Y M, Qu Y H, Su C Y. Decentralized fault-tolerant cooperative control of multiple UAVs with pre-scribed attitude synchronization tracking performance under dir-ected communication topology. Frontiers of Information Techno-logy & Electronic Engineering , 2019, 20(5): 685−70116Xi Wen-Long, Tang Wen-Xiu, Xu Li-Shang, Liu Fang-Yue. Pos-ition control of DC-motor based on one-order low pass filter backstepping sliding mode method. Chongqing University of Posts and Telecommunications , 2017, 29(4): 550−556(奚文龙, 唐文秀, 许李尚, 刘方悦. 基于一阶低通滤波器滑模反步法的直流电机位置控制. 重庆邮电大学学报 (自然科学版), 2017,29(4): 550−556)17Liu Z, Lou X, Jia J. Event-triggered dynamic output-feedback control for a class of Lipschitz nonlinear systems. Frontiers of Information Technology & Electronic Engineering , 2022, 23(11):1684−169918Chen Zai-Fa, Liu Yan-Cheng. Control of permanent magnet synchronous motor based on super spiral sliding model variable structure. Motor and Control Applications , 2017, 44(6): 19−23(陈再发, 刘彦呈. 基于超螺旋滑模变结构永磁同步电机的控制. 电机与控制应用, 2017, 44(6): 19−23)19Ren Yan, Wang Yi-Min, Niu Zhi-Qiang, Xiao Yong-Jian. Ap-plication of high-order terminal sliding mode control in stable platform. Control Engineering , 2021, 28(3): 553−558(任彦, 王义敏, 牛志强, 肖永健. 高阶终端滑模控制在稳定平台中的应用. 控制工程, 2021, 28(3): 553−558)20Derafa L, Benallegue A, Fridman L. Super twisting control al-gorithm for the attitude tracking of a four rotors UAV. Journal of the Franklin Institute , 2012, 349(2): 685−69921Naidu D. Singular perturbations and time scales in control the-ory and applications: An overview. Dynamics of Continuous Dis-crete and Impulsive Systems Series B , 2002, 9: 233−27822Li F, Zheng W X, Xu S Y, Yuan D M. A novel ε-dependent Lyapunov function and its application to singularly perturbed systems. Automatica , 2021, 133: Article No. 10974923He Shou-Yuan. Properties and judgment methods of positive definite matrix. Journal of Mathematical and Chemical Prob-lem Solving , 2020, 24: 18−19(何守元. 正定矩阵的性质及判定方法. 数理化解题研究, 2020, 24:18−19)24Malamud S M. A converse to the Jensen inequality, its matrix extensions and inequalities for minors and eigenvalues. Linear Algebra and Its Applications , 2001, 22(1): 19−4125Shtessel Y B, Moreno J A, Plestan F. Super-twisting adaptive26表 1 四旋翼无人机姿态角系统性能指标Table 1 Performance index of a quadrotor 'sattitude system平均收敛时间(s)平均稳态误差(rad)STW 滑模算法 2.587 1.76×10−7改进型STW 滑模算法 1.947 3.56×10−7文献[30]中的算法10.8704.24×10−68 期蔡运颂等: 基于自适应多尺度超螺旋算法的无人机集群姿态同步控制1665sliding mode control: A Lyapunov design. In: Proceedings of the49th Conference on Decision and Control. Petersburg, Russia:IEEE, 2010. 5109−5113Wang G L, Li Z Q, Miao X, Zhang Q L, Yang C Y. Fault detec-tion of discrete-time delay Markovian jump systems with delay term modes partially available. Journal of the Franklin Institute ,2019, 356(5): 3045−307127Hu Xiao-Li, Qiao Long-Kun. Improvement of Cauchy 's inequal-ity and its application. Journal of Jianghan University , 2021,49(6): 29−33(胡晓莉, 乔龙坤. 柯西不等式的改进及其应用. 江汉大学学报,2021, 49(6): 29−33)28Munoz F, Estrada M B, González-Hernández I, Salazar S, Loz-ano R. Super twisting vs modified super twisting algorithm for altitude control of an unmanned aircraft system. In: Proceed-ings of the 12th International Conference on Electrical Engineer-ing, Computing Science and Automatic Control. Tu Delft, Neth-erlands: IEEE, 2015. 1−629Jin Wan-Li, Yu Zhi-Yong, Jiang Hai-Jun. Leader-following con-sensus of second-order multi-agent systems via event-triggered impulsive control. Journal of Lanzhou University of Technology ,2022, 48(5): 153−160(金琬丽, 于志永, 蒋海军. 事件触发脉冲控制下二阶多智能体系统的领导跟随一致性. 兰州理工大学学报, 2022, 48(5): 153−160)30蔡运颂 华东理工大学信息科学与工程学院硕士研究生. 主要研究方向为滑模控制, 多智能体和无人机控制.E-mail: ********************(CAI Yun-Song Master student at the College of Information Scienceand Engineering, East China University of Science and Technology. His research interest covers sliding modecontrol, multi-agent, and UAV control .)许 璟 华东理工大学信息科学与工程学院副教授. 主要研究方向为高阶滑模观测与控制, 无人机系统建模与控制, 智能优化算法和人工智能技术.本文通信作者.E-mail: ****************.cn(XU Jing Associate professor atthe College of Information Science and Engineering,East China University of Science and Technology. Her research interest covers high-order sliding mode obser-vation and control, UAV system modeling and control,intelligent arithmetic optimization, and artificial intel-ligence technology. Corresponding author of this paper .)牛玉刚 华东理工大学信息科学与工程学院教授. 主要研究方向为随机控制系统, 滑模控制, 无线传感网络和微电网能量管理.E-mail: *****************.cn(NIU Yu-Gang Professor at the College of Information Science andEngineering, East China University of Science and Technology. His research interest covers stochastic control system, sliding mode control, wireless sensor network, and microgrid energy management .)1666自 动 化 学 报49 卷Copyright ©博看网. All Rights Reserved.。
OSHA现场作业手册说明书

DIRECTIVE NUMBER: CPL 02-00-150 EFFECTIVE DATE: April 22, 2011 SUBJECT: Field Operations Manual (FOM)ABSTRACTPurpose: This instruction cancels and replaces OSHA Instruction CPL 02-00-148,Field Operations Manual (FOM), issued November 9, 2009, whichreplaced the September 26, 1994 Instruction that implemented the FieldInspection Reference Manual (FIRM). The FOM is a revision of OSHA’senforcement policies and procedures manual that provides the field officesa reference document for identifying the responsibilities associated withthe majority of their inspection duties. This Instruction also cancels OSHAInstruction FAP 01-00-003 Federal Agency Safety and Health Programs,May 17, 1996 and Chapter 13 of OSHA Instruction CPL 02-00-045,Revised Field Operations Manual, June 15, 1989.Scope: OSHA-wide.References: Title 29 Code of Federal Regulations §1903.6, Advance Notice ofInspections; 29 Code of Federal Regulations §1903.14, Policy RegardingEmployee Rescue Activities; 29 Code of Federal Regulations §1903.19,Abatement Verification; 29 Code of Federal Regulations §1904.39,Reporting Fatalities and Multiple Hospitalizations to OSHA; and Housingfor Agricultural Workers: Final Rule, Federal Register, March 4, 1980 (45FR 14180).Cancellations: OSHA Instruction CPL 02-00-148, Field Operations Manual, November9, 2009.OSHA Instruction FAP 01-00-003, Federal Agency Safety and HealthPrograms, May 17, 1996.Chapter 13 of OSHA Instruction CPL 02-00-045, Revised FieldOperations Manual, June 15, 1989.State Impact: Notice of Intent and Adoption required. See paragraph VI.Action Offices: National, Regional, and Area OfficesOriginating Office: Directorate of Enforcement Programs Contact: Directorate of Enforcement ProgramsOffice of General Industry Enforcement200 Constitution Avenue, NW, N3 119Washington, DC 20210202-693-1850By and Under the Authority ofDavid Michaels, PhD, MPHAssistant SecretaryExecutive SummaryThis instruction cancels and replaces OSHA Instruction CPL 02-00-148, Field Operations Manual (FOM), issued November 9, 2009. The one remaining part of the prior Field Operations Manual, the chapter on Disclosure, will be added at a later date. This Instruction also cancels OSHA Instruction FAP 01-00-003 Federal Agency Safety and Health Programs, May 17, 1996 and Chapter 13 of OSHA Instruction CPL 02-00-045, Revised Field Operations Manual, June 15, 1989. This Instruction constitutes OSHA’s general enforcement policies and procedures manual for use by the field offices in conducting inspections, issuing citations and proposing penalties.Significant Changes∙A new Table of Contents for the entire FOM is added.∙ A new References section for the entire FOM is added∙ A new Cancellations section for the entire FOM is added.∙Adds a Maritime Industry Sector to Section III of Chapter 10, Industry Sectors.∙Revises sections referring to the Enhanced Enforcement Program (EEP) replacing the information with the Severe Violator Enforcement Program (SVEP).∙Adds Chapter 13, Federal Agency Field Activities.∙Cancels OSHA Instruction FAP 01-00-003, Federal Agency Safety and Health Programs, May 17, 1996.DisclaimerThis manual is intended to provide instruction regarding some of the internal operations of the Occupational Safety and Health Administration (OSHA), and is solely for the benefit of the Government. No duties, rights, or benefits, substantive or procedural, are created or implied by this manual. The contents of this manual are not enforceable by any person or entity against the Department of Labor or the United States. Statements which reflect current Occupational Safety and Health Review Commission or court precedents do not necessarily indicate acquiescence with those precedents.Table of ContentsCHAPTER 1INTRODUCTIONI.PURPOSE. ........................................................................................................... 1-1 II.SCOPE. ................................................................................................................ 1-1 III.REFERENCES .................................................................................................... 1-1 IV.CANCELLATIONS............................................................................................. 1-8 V. ACTION INFORMATION ................................................................................. 1-8A.R ESPONSIBLE O FFICE.......................................................................................................................................... 1-8B.A CTION O FFICES. .................................................................................................................... 1-8C. I NFORMATION O FFICES............................................................................................................ 1-8 VI. STATE IMPACT. ................................................................................................ 1-8 VII.SIGNIFICANT CHANGES. ............................................................................... 1-9 VIII.BACKGROUND. ................................................................................................. 1-9 IX. DEFINITIONS AND TERMINOLOGY. ........................................................ 1-10A.T HE A CT................................................................................................................................................................. 1-10B. C OMPLIANCE S AFETY AND H EALTH O FFICER (CSHO). ...........................................................1-10B.H E/S HE AND H IS/H ERS ..................................................................................................................................... 1-10C.P ROFESSIONAL J UDGMENT............................................................................................................................... 1-10E. W ORKPLACE AND W ORKSITE ......................................................................................................................... 1-10CHAPTER 2PROGRAM PLANNINGI.INTRODUCTION ............................................................................................... 2-1 II.AREA OFFICE RESPONSIBILITIES. .............................................................. 2-1A.P ROVIDING A SSISTANCE TO S MALL E MPLOYERS. ...................................................................................... 2-1B.A REA O FFICE O UTREACH P ROGRAM. ............................................................................................................. 2-1C. R ESPONDING TO R EQUESTS FOR A SSISTANCE. ............................................................................................ 2-2 III. OSHA COOPERATIVE PROGRAMS OVERVIEW. ...................................... 2-2A.V OLUNTARY P ROTECTION P ROGRAM (VPP). ........................................................................... 2-2B.O NSITE C ONSULTATION P ROGRAM. ................................................................................................................ 2-2C.S TRATEGIC P ARTNERSHIPS................................................................................................................................. 2-3D.A LLIANCE P ROGRAM ........................................................................................................................................... 2-3 IV. ENFORCEMENT PROGRAM SCHEDULING. ................................................ 2-4A.G ENERAL ................................................................................................................................................................. 2-4B.I NSPECTION P RIORITY C RITERIA. ..................................................................................................................... 2-4C.E FFECT OF C ONTEST ............................................................................................................................................ 2-5D.E NFORCEMENT E XEMPTIONS AND L IMITATIONS. ....................................................................................... 2-6E.P REEMPTION BY A NOTHER F EDERAL A GENCY ........................................................................................... 2-6F.U NITED S TATES P OSTAL S ERVICE. .................................................................................................................. 2-7G.H OME-B ASED W ORKSITES. ................................................................................................................................ 2-8H.I NSPECTION/I NVESTIGATION T YPES. ............................................................................................................... 2-8 V.UNPROGRAMMED ACTIVITY – HAZARD EVALUATION AND INSPECTION SCHEDULING ............................................................................ 2-9 VI.PROGRAMMED INSPECTIONS. ................................................................... 2-10A.S ITE-S PECIFIC T ARGETING (SST) P ROGRAM. ............................................................................................. 2-10B.S CHEDULING FOR C ONSTRUCTION I NSPECTIONS. ..................................................................................... 2-10C.S CHEDULING FOR M ARITIME I NSPECTIONS. ............................................................................. 2-11D.S PECIAL E MPHASIS P ROGRAMS (SEP S). ................................................................................... 2-12E.N ATIONAL E MPHASIS P ROGRAMS (NEP S) ............................................................................... 2-13F.L OCAL E MPHASIS P ROGRAMS (LEP S) AND R EGIONAL E MPHASIS P ROGRAMS (REP S) ............ 2-13G.O THER S PECIAL P ROGRAMS. ............................................................................................................................ 2-13H.I NSPECTION S CHEDULING AND I NTERFACE WITH C OOPERATIVE P ROGRAM P ARTICIPANTS ....... 2-13CHAPTER 3INSPECTION PROCEDURESI.INSPECTION PREPARATION. .......................................................................... 3-1 II.INSPECTION PLANNING. .................................................................................. 3-1A.R EVIEW OF I NSPECTION H ISTORY .................................................................................................................... 3-1B.R EVIEW OF C OOPERATIVE P ROGRAM P ARTICIPATION .............................................................................. 3-1C.OSHA D ATA I NITIATIVE (ODI) D ATA R EVIEW .......................................................................................... 3-2D.S AFETY AND H EALTH I SSUES R ELATING TO CSHO S.................................................................. 3-2E.A DVANCE N OTICE. ................................................................................................................................................ 3-3F.P RE-I NSPECTION C OMPULSORY P ROCESS ...................................................................................................... 3-5G.P ERSONAL S ECURITY C LEARANCE. ................................................................................................................. 3-5H.E XPERT A SSISTANCE. ........................................................................................................................................... 3-5 III. INSPECTION SCOPE. ......................................................................................... 3-6A.C OMPREHENSIVE ................................................................................................................................................... 3-6B.P ARTIAL. ................................................................................................................................................................... 3-6 IV. CONDUCT OF INSPECTION .............................................................................. 3-6A.T IME OF I NSPECTION............................................................................................................................................. 3-6B.P RESENTING C REDENTIALS. ............................................................................................................................... 3-6C.R EFUSAL TO P ERMIT I NSPECTION AND I NTERFERENCE ............................................................................. 3-7D.E MPLOYEE P ARTICIPATION. ............................................................................................................................... 3-9E.R ELEASE FOR E NTRY ............................................................................................................................................ 3-9F.B ANKRUPT OR O UT OF B USINESS. .................................................................................................................... 3-9G.E MPLOYEE R ESPONSIBILITIES. ................................................................................................. 3-10H.S TRIKE OR L ABOR D ISPUTE ............................................................................................................................. 3-10I. V ARIANCES. .......................................................................................................................................................... 3-11 V. OPENING CONFERENCE. ................................................................................ 3-11A.G ENERAL ................................................................................................................................................................ 3-11B.R EVIEW OF A PPROPRIATION A CT E XEMPTIONS AND L IMITATION. ..................................................... 3-13C.R EVIEW S CREENING FOR P ROCESS S AFETY M ANAGEMENT (PSM) C OVERAGE............................. 3-13D.R EVIEW OF V OLUNTARY C OMPLIANCE P ROGRAMS. ................................................................................ 3-14E.D ISRUPTIVE C ONDUCT. ...................................................................................................................................... 3-15F.C LASSIFIED A REAS ............................................................................................................................................. 3-16VI. REVIEW OF RECORDS. ................................................................................... 3-16A.I NJURY AND I LLNESS R ECORDS...................................................................................................................... 3-16B.R ECORDING C RITERIA. ...................................................................................................................................... 3-18C. R ECORDKEEPING D EFICIENCIES. .................................................................................................................. 3-18 VII. WALKAROUND INSPECTION. ....................................................................... 3-19A.W ALKAROUND R EPRESENTATIVES ............................................................................................................... 3-19B.E VALUATION OF S AFETY AND H EALTH M ANAGEMENT S YSTEM. ....................................................... 3-20C.R ECORD A LL F ACTS P ERTINENT TO A V IOLATION. ................................................................................. 3-20D.T ESTIFYING IN H EARINGS ................................................................................................................................ 3-21E.T RADE S ECRETS. ................................................................................................................................................. 3-21F.C OLLECTING S AMPLES. ..................................................................................................................................... 3-22G.P HOTOGRAPHS AND V IDEOTAPES.................................................................................................................. 3-22H.V IOLATIONS OF O THER L AWS. ....................................................................................................................... 3-23I.I NTERVIEWS OF N ON-M ANAGERIAL E MPLOYEES .................................................................................... 3-23J.M ULTI-E MPLOYER W ORKSITES ..................................................................................................................... 3-27 K.A DMINISTRATIVE S UBPOENA.......................................................................................................................... 3-27 L.E MPLOYER A BATEMENT A SSISTANCE. ........................................................................................................ 3-27 VIII. CLOSING CONFERENCE. .............................................................................. 3-28A.P ARTICIPANTS. ..................................................................................................................................................... 3-28B.D ISCUSSION I TEMS. ............................................................................................................................................ 3-28C.A DVICE TO A TTENDEES .................................................................................................................................... 3-29D.P ENALTIES............................................................................................................................................................. 3-30E.F EASIBLE A DMINISTRATIVE, W ORK P RACTICE AND E NGINEERING C ONTROLS. ............................ 3-30F.R EDUCING E MPLOYEE E XPOSURE. ................................................................................................................ 3-32G.A BATEMENT V ERIFICATION. ........................................................................................................................... 3-32H.E MPLOYEE D ISCRIMINATION .......................................................................................................................... 3-33 IX. SPECIAL INSPECTION PROCEDURES. ...................................................... 3-33A.F OLLOW-UP AND M ONITORING I NSPECTIONS............................................................................................ 3-33B.C ONSTRUCTION I NSPECTIONS ......................................................................................................................... 3-34C. F EDERAL A GENCY I NSPECTIONS. ................................................................................................................. 3-35CHAPTER 4VIOLATIONSI. BASIS OF VIOLATIONS ..................................................................................... 4-1A.S TANDARDS AND R EGULATIONS. .................................................................................................................... 4-1B.E MPLOYEE E XPOSURE. ........................................................................................................................................ 4-3C.R EGULATORY R EQUIREMENTS. ........................................................................................................................ 4-6D.H AZARD C OMMUNICATION. .............................................................................................................................. 4-6E. E MPLOYER/E MPLOYEE R ESPONSIBILITIES ................................................................................................... 4-6 II. SERIOUS VIOLATIONS. .................................................................................... 4-8A.S ECTION 17(K). ......................................................................................................................... 4-8B.E STABLISHING S ERIOUS V IOLATIONS ............................................................................................................ 4-8C. F OUR S TEPS TO BE D OCUMENTED. ................................................................................................................... 4-8 III. GENERAL DUTY REQUIREMENTS ............................................................. 4-14A.E VALUATION OF G ENERAL D UTY R EQUIREMENTS ................................................................................. 4-14B.E LEMENTS OF A G ENERAL D UTY R EQUIREMENT V IOLATION.............................................................. 4-14C. U SE OF THE G ENERAL D UTY C LAUSE ........................................................................................................ 4-23D.L IMITATIONS OF U SE OF THE G ENERAL D UTY C LAUSE. ..............................................................E.C LASSIFICATION OF V IOLATIONS C ITED U NDER THE G ENERAL D UTY C LAUSE. ..................F. P ROCEDURES FOR I MPLEMENTATION OF S ECTION 5(A)(1) E NFORCEMENT ............................ 4-25 4-27 4-27IV.OTHER-THAN-SERIOUS VIOLATIONS ............................................... 4-28 V.WILLFUL VIOLATIONS. ......................................................................... 4-28A.I NTENTIONAL D ISREGARD V IOLATIONS. ..........................................................................................4-28B.P LAIN I NDIFFERENCE V IOLATIONS. ...................................................................................................4-29 VI. CRIMINAL/WILLFUL VIOLATIONS. ................................................... 4-30A.A REA D IRECTOR C OORDINATION ....................................................................................................... 4-31B.C RITERIA FOR I NVESTIGATING P OSSIBLE C RIMINAL/W ILLFUL V IOLATIONS ........................ 4-31C. W ILLFUL V IOLATIONS R ELATED TO A F ATALITY .......................................................................... 4-32 VII. REPEATED VIOLATIONS. ...................................................................... 4-32A.F EDERAL AND S TATE P LAN V IOLATIONS. ........................................................................................4-32B.I DENTICAL S TANDARDS. .......................................................................................................................4-32C.D IFFERENT S TANDARDS. .......................................................................................................................4-33D.O BTAINING I NSPECTION H ISTORY. .....................................................................................................4-33E.T IME L IMITATIONS..................................................................................................................................4-34F.R EPEATED V. F AILURE TO A BATE....................................................................................................... 4-34G. A REA D IRECTOR R ESPONSIBILITIES. .............................................................................. 4-35 VIII. DE MINIMIS CONDITIONS. ................................................................... 4-36A.C RITERIA ................................................................................................................................................... 4-36B.P ROFESSIONAL J UDGMENT. ..................................................................................................................4-37C. A REA D IRECTOR R ESPONSIBILITIES. .............................................................................. 4-37 IX. CITING IN THE ALTERNATIVE ............................................................ 4-37 X. COMBINING AND GROUPING VIOLATIONS. ................................... 4-37A.C OMBINING. ..............................................................................................................................................4-37B.G ROUPING. ................................................................................................................................................4-38C. W HEN N OT TO G ROUP OR C OMBINE. ................................................................................................4-38 XI. HEALTH STANDARD VIOLATIONS ....................................................... 4-39A.C ITATION OF V ENTILATION S TANDARDS ......................................................................................... 4-39B.V IOLATIONS OF THE N OISE S TANDARD. ...........................................................................................4-40 XII. VIOLATIONS OF THE RESPIRATORY PROTECTION STANDARD(§1910.134). ....................................................................................................... XIII. VIOLATIONS OF AIR CONTAMINANT STANDARDS (§1910.1000) ... 4-43 4-43A.R EQUIREMENTS UNDER THE STANDARD: .................................................................................................. 4-43B.C LASSIFICATION OF V IOLATIONS OF A IR C ONTAMINANT S TANDARDS. ......................................... 4-43 XIV. CITING IMPROPER PERSONAL HYGIENE PRACTICES. ................... 4-45A.I NGESTION H AZARDS. .................................................................................................................................... 4-45B.A BSORPTION H AZARDS. ................................................................................................................................ 4-46C.W IPE S AMPLING. ............................................................................................................................................. 4-46D.C ITATION P OLICY ............................................................................................................................................ 4-46 XV. BIOLOGICAL MONITORING. ...................................................................... 4-47CHAPTER 5CASE FILE PREPARATION AND DOCUMENTATIONI.INTRODUCTION ............................................................................................... 5-1 II.INSPECTION CONDUCTED, CITATIONS BEING ISSUED. .................... 5-1A.OSHA-1 ................................................................................................................................... 5-1B.OSHA-1A. ............................................................................................................................... 5-1C. OSHA-1B. ................................................................................................................................ 5-2 III.INSPECTION CONDUCTED BUT NO CITATIONS ISSUED .................... 5-5 IV.NO INSPECTION ............................................................................................... 5-5 V. HEALTH INSPECTIONS. ................................................................................. 5-6A.D OCUMENT P OTENTIAL E XPOSURE. ............................................................................................................... 5-6B.E MPLOYER’S O CCUPATIONAL S AFETY AND H EALTH S YSTEM. ............................................................. 5-6 VI. AFFIRMATIVE DEFENSES............................................................................. 5-8A.B URDEN OF P ROOF. .............................................................................................................................................. 5-8B.E XPLANATIONS. ..................................................................................................................................................... 5-8 VII. INTERVIEW STATEMENTS. ........................................................................ 5-10A.G ENERALLY. ......................................................................................................................................................... 5-10B.CSHO S SHALL OBTAIN WRITTEN STATEMENTS WHEN: .......................................................................... 5-10C.L ANGUAGE AND W ORDING OF S TATEMENT. ............................................................................................. 5-11D.R EFUSAL TO S IGN S TATEMENT ...................................................................................................................... 5-11E.V IDEO AND A UDIOTAPED S TATEMENTS. ..................................................................................................... 5-11F.A DMINISTRATIVE D EPOSITIONS. .............................................................................................5-11 VIII. PAPERWORK AND WRITTEN PROGRAM REQUIREMENTS. .......... 5-12 IX.GUIDELINES FOR CASE FILE DOCUMENTATION FOR USE WITH VIDEOTAPES AND AUDIOTAPES .............................................................. 5-12 X.CASE FILE ACTIVITY DIARY SHEET. ..................................................... 5-12 XI. CITATIONS. ..................................................................................................... 5-12A.S TATUTE OF L IMITATIONS. .............................................................................................................................. 5-13B.I SSUING C ITATIONS. ........................................................................................................................................... 5-13C.A MENDING/W ITHDRAWING C ITATIONS AND N OTIFICATION OF P ENALTIES. .................................. 5-13D.P ROCEDURES FOR A MENDING OR W ITHDRAWING C ITATIONS ............................................................ 5-14 XII. INSPECTION RECORDS. ............................................................................... 5-15A.G ENERALLY. ......................................................................................................................................................... 5-15B.R ELEASE OF I NSPECTION I NFORMATION ..................................................................................................... 5-15C. C LASSIFIED AND T RADE S ECRET I NFORMATION ...................................................................................... 5-16。
T.W. ANDERSON (1971). The Statistical Analysis of Time Series. Series in Probability and Ma

425 BibliographyH.A KAIKE(1974).Markovian representation of stochastic processes and its application to the analysis of autoregressive moving average processes.Annals Institute Statistical Mathematics,vol.26,pp.363-387. B.D.O.A NDERSON and J.B.M OORE(1979).Optimal rmation and System Sciences Series, Prentice Hall,Englewood Cliffs,NJ.T.W.A NDERSON(1971).The Statistical Analysis of Time Series.Series in Probability and Mathematical Statistics,Wiley,New York.R.A NDRE-O BRECHT(1988).A new statistical approach for the automatic segmentation of continuous speech signals.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-36,no1,pp.29-40.R.A NDRE-O BRECHT(1990).Reconnaissance automatique de parole`a partir de segments acoustiques et de mod`e les de Markov cach´e s.Proc.Journ´e es Etude de la Parole,Montr´e al,May1990(in French).R.A NDRE-O BRECHT and H.Y.S U(1988).Three acoustic labellings for phoneme based continuous speech recognition.Proc.Speech’88,Edinburgh,UK,pp.943-950.U.A PPEL and A.VON B RANDT(1983).Adaptive sequential segmentation of piecewise stationary time rmation Sciences,vol.29,no1,pp.27-56.L.A.A ROIAN and H.L EVENE(1950).The effectiveness of quality control procedures.Jal American Statis-tical Association,vol.45,pp.520-529.K.J.A STR¨OM and B.W ITTENMARK(1984).Computer Controlled Systems:Theory and rma-tion and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.M.B AGSHAW and R.A.J OHNSON(1975a).The effect of serial correlation on the performance of CUSUM tests-Part II.Technometrics,vol.17,no1,pp.73-80.M.B AGSHAW and R.A.J OHNSON(1975b).The influence of reference values and estimated variance on the ARL of CUSUM tests.Jal Royal Statistical Society,vol.37(B),no3,pp.413-420.M.B AGSHAW and R.A.J OHNSON(1977).Sequential procedures for detecting parameter changes in a time-series model.Jal American Statistical Association,vol.72,no359,pp.593-597.R.K.B ANSAL and P.P APANTONI-K AZAKOS(1986).An algorithm for detecting a change in a stochastic process.IEEE rmation Theory,vol.IT-32,no2,pp.227-235.G.A.B ARNARD(1959).Control charts and stochastic processes.Jal Royal Statistical Society,vol.B.21, pp.239-271.A.E.B ASHARINOV andB.S.F LEISHMAN(1962).Methods of the statistical sequential analysis and their radiotechnical applications.Sovetskoe Radio,Moscow(in Russian).M.B ASSEVILLE(1978).D´e viations par rapport au maximum:formules d’arrˆe t et martingales associ´e es. Compte-rendus du S´e minaire de Probabilit´e s,Universit´e de Rennes I.M.B ASSEVILLE(1981).Edge detection using sequential methods for change in level-Part II:Sequential detection of change in mean.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-29,no1,pp.32-50.426B IBLIOGRAPHY M.B ASSEVILLE(1982).A survey of statistical failure detection techniques.In Contribution`a la D´e tectionS´e quentielle de Ruptures de Mod`e les Statistiques,Th`e se d’Etat,Universit´e de Rennes I,France(in English). M.B ASSEVILLE(1986).The two-models approach for the on-line detection of changes in AR processes. In Detection of Abrupt Changes in Signals and Dynamical Systems(M.Basseville,A.Benveniste,eds.). Lecture Notes in Control and Information Sciences,LNCIS77,Springer,New York,pp.169-215.M.B ASSEVILLE(1988).Detecting changes in signals and systems-A survey.Automatica,vol.24,pp.309-326.M.B ASSEVILLE(1989).Distance measures for signal processing and pattern recognition.Signal Process-ing,vol.18,pp.349-369.M.B ASSEVILLE and A.B ENVENISTE(1983a).Design and comparative study of some sequential jump detection algorithms for digital signals.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-31, no3,pp.521-535.M.B ASSEVILLE and A.B ENVENISTE(1983b).Sequential detection of abrupt changes in spectral charac-teristics of digital signals.IEEE rmation Theory,vol.IT-29,no5,pp.709-724.M.B ASSEVILLE and A.B ENVENISTE,eds.(1986).Detection of Abrupt Changes in Signals and Dynamical Systems.Lecture Notes in Control and Information Sciences,LNCIS77,Springer,New York.M.B ASSEVILLE and I.N IKIFOROV(1991).A unified framework for statistical change detection.Proc.30th IEEE Conference on Decision and Control,Brighton,UK.M.B ASSEVILLE,B.E SPIAU and J.G ASNIER(1981).Edge detection using sequential methods for change in level-Part I:A sequential edge detection algorithm.IEEE Trans.Acoustics,Speech,Signal Processing, vol.ASSP-29,no1,pp.24-31.M.B ASSEVILLE, A.B ENVENISTE and G.M OUSTAKIDES(1986).Detection and diagnosis of abrupt changes in modal characteristics of nonstationary digital signals.IEEE rmation Theory,vol.IT-32,no3,pp.412-417.M.B ASSEVILLE,A.B ENVENISTE,G.M OUSTAKIDES and A.R OUG´E E(1987a).Detection and diagnosis of changes in the eigenstructure of nonstationary multivariable systems.Automatica,vol.23,no3,pp.479-489. M.B ASSEVILLE,A.B ENVENISTE,G.M OUSTAKIDES and A.R OUG´E E(1987b).Optimal sensor location for detecting changes in dynamical behavior.IEEE Trans.Automatic Control,vol.AC-32,no12,pp.1067-1075.M.B ASSEVILLE,A.B ENVENISTE,B.G ACH-D EVAUCHELLE,M.G OURSAT,D.B ONNECASE,P.D OREY, M.P REVOSTO and M.O LAGNON(1993).Damage monitoring in vibration mechanics:issues in diagnos-tics and predictive maintenance.Mechanical Systems and Signal Processing,vol.7,no5,pp.401-423.R.V.B EARD(1971).Failure Accommodation in Linear Systems through Self-reorganization.Ph.D.Thesis, Dept.Aeronautics and Astronautics,MIT,Cambridge,MA.A.B ENVENISTE and J.J.F UCHS(1985).Single sample modal identification of a nonstationary stochastic process.IEEE Trans.Automatic Control,vol.AC-30,no1,pp.66-74.A.B ENVENISTE,M.B ASSEVILLE and G.M OUSTAKIDES(1987).The asymptotic local approach to change detection and model validation.IEEE Trans.Automatic Control,vol.AC-32,no7,pp.583-592.A.B ENVENISTE,M.M ETIVIER and P.P RIOURET(1990).Adaptive Algorithms and Stochastic Approxima-tions.Series on Applications of Mathematics,(A.V.Balakrishnan,I.Karatzas,M.Yor,eds.).Springer,New York.A.B ENVENISTE,M.B ASSEVILLE,L.E L G HAOUI,R.N IKOUKHAH and A.S.W ILLSKY(1992).An optimum robust approach to statistical failure detection and identification.IFAC World Conference,Sydney, July1993.B IBLIOGRAPHY427 R.H.B ERK(1973).Some asymptotic aspects of sequential analysis.Annals Statistics,vol.1,no6,pp.1126-1138.R.H.B ERK(1975).Locally most powerful sequential test.Annals Statistics,vol.3,no2,pp.373-381.P.B ILLINGSLEY(1968).Convergence of Probability Measures.Wiley,New York.A.F.B ISSELL(1969).Cusum techniques for quality control.Applied Statistics,vol.18,pp.1-30.M.E.B IVAIKOV(1991).Control of the sample size for recursive estimation of parameters subject to abrupt changes.Automation and Remote Control,no9,pp.96-103.R.E.B LAHUT(1987).Principles and Practice of Information Theory.Addison-Wesley,Reading,MA.I.F.B LAKE and W.C.L INDSEY(1973).Level-crossing problems for random processes.IEEE r-mation Theory,vol.IT-19,no3,pp.295-315.G.B ODENSTEIN and H.M.P RAETORIUS(1977).Feature extraction from the encephalogram by adaptive segmentation.Proc.IEEE,vol.65,pp.642-652.T.B OHLIN(1977).Analysis of EEG signals with changing spectra using a short word Kalman estimator. Mathematical Biosciences,vol.35,pp.221-259.W.B¨OHM and P.H ACKL(1990).Improved bounds for the average run length of control charts based on finite weighted sums.Annals Statistics,vol.18,no4,pp.1895-1899.T.B OJDECKI and J.H OSZA(1984).On a generalized disorder problem.Stochastic Processes and their Applications,vol.18,pp.349-359.L.I.B ORODKIN and V.V.M OTTL’(1976).Algorithm forfinding the jump times of random process equation parameters.Automation and Remote Control,vol.37,no6,Part1,pp.23-32.A.A.B OROVKOV(1984).Theory of Mathematical Statistics-Estimation and Hypotheses Testing,Naouka, Moscow(in Russian).Translated in French under the title Statistique Math´e matique-Estimation et Tests d’Hypoth`e ses,Mir,Paris,1987.G.E.P.B OX and G.M.J ENKINS(1970).Time Series Analysis,Forecasting and Control.Series in Time Series Analysis,Holden-Day,San Francisco.A.VON B RANDT(1983).Detecting and estimating parameters jumps using ladder algorithms and likelihood ratio test.Proc.ICASSP,Boston,MA,pp.1017-1020.A.VON B RANDT(1984).Modellierung von Signalen mit Sprunghaft Ver¨a nderlichem Leistungsspektrum durch Adaptive Segmentierung.Doctor-Engineer Dissertation,M¨u nchen,RFA(in German).S.B RAUN,ed.(1986).Mechanical Signature Analysis-Theory and Applications.Academic Press,London. L.B REIMAN(1968).Probability.Series in Statistics,Addison-Wesley,Reading,MA.G.S.B RITOV and L.A.M IRONOVSKI(1972).Diagnostics of linear systems of automatic regulation.Tekh. Kibernetics,vol.1,pp.76-83.B.E.B RODSKIY and B.S.D ARKHOVSKIY(1992).Nonparametric Methods in Change-point Problems. Kluwer Academic,Boston.L.D.B ROEMELING(1982).Jal Econometrics,vol.19,Special issue on structural change in Econometrics. L.D.B ROEMELING and H.T SURUMI(1987).Econometrics and Structural Change.Dekker,New York. D.B ROOK and D.A.E VANS(1972).An approach to the probability distribution of Cusum run length. Biometrika,vol.59,pp.539-550.J.B RUNET,D.J AUME,M.L ABARR`E RE,A.R AULT and M.V ERG´E(1990).D´e tection et Diagnostic de Pannes.Trait´e des Nouvelles Technologies,S´e rie Diagnostic et Maintenance,Herm`e s,Paris(in French).428B IBLIOGRAPHY S.P.B RUZZONE and M.K AVEH(1984).Information tradeoffs in using the sample autocorrelation function in ARMA parameter estimation.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-32,no4, pp.701-715.A.K.C AGLAYAN(1980).Necessary and sufficient conditions for detectability of jumps in linear systems. IEEE Trans.Automatic Control,vol.AC-25,no4,pp.833-834.A.K.C AGLAYAN and R.E.L ANCRAFT(1983).Reinitialization issues in fault tolerant systems.Proc.Amer-ican Control Conf.,pp.952-955.A.K.C AGLAYAN,S.M.A LLEN and K.W EHMULLER(1988).Evaluation of a second generation reconfigu-ration strategy for aircraftflight control systems subjected to actuator failure/surface damage.Proc.National Aerospace and Electronic Conference,Dayton,OH.P.E.C AINES(1988).Linear Stochastic Systems.Series in Probability and Mathematical Statistics,Wiley, New York.M.J.C HEN and J.P.N ORTON(1987).Estimation techniques for tracking rapid parameter changes.Intern. Jal Control,vol.45,no4,pp.1387-1398.W.K.C HIU(1974).The economic design of cusum charts for controlling normal mean.Applied Statistics, vol.23,no3,pp.420-433.E.Y.C HOW(1980).A Failure Detection System Design Methodology.Ph.D.Thesis,M.I.T.,L.I.D.S.,Cam-bridge,MA.E.Y.C HOW and A.S.W ILLSKY(1984).Analytical redundancy and the design of robust failure detection systems.IEEE Trans.Automatic Control,vol.AC-29,no3,pp.689-691.Y.S.C HOW,H.R OBBINS and D.S IEGMUND(1971).Great Expectations:The Theory of Optimal Stop-ping.Houghton-Mifflin,Boston.R.N.C LARK,D.C.F OSTH and V.M.W ALTON(1975).Detection of instrument malfunctions in control systems.IEEE Trans.Aerospace Electronic Systems,vol.AES-11,pp.465-473.A.C OHEN(1987).Biomedical Signal Processing-vol.1:Time and Frequency Domain Analysis;vol.2: Compression and Automatic Recognition.CRC Press,Boca Raton,FL.J.C ORGE and F.P UECH(1986).Analyse du rythme cardiaque foetal par des m´e thodes de d´e tection de ruptures.Proc.7th INRIA Int.Conf.Analysis and optimization of Systems.Antibes,FR(in French).D.R.C OX and D.V.H INKLEY(1986).Theoretical Statistics.Chapman and Hall,New York.D.R.C OX and H.D.M ILLER(1965).The Theory of Stochastic Processes.Wiley,New York.S.V.C ROWDER(1987).A simple method for studying run-length distributions of exponentially weighted moving average charts.Technometrics,vol.29,no4,pp.401-407.H.C S¨ORG¨O and L.H ORV´ATH(1988).Nonparametric methods for change point problems.In Handbook of Statistics(P.R.Krishnaiah,C.R.Rao,eds.),vol.7,Elsevier,New York,pp.403-425.R.B.D AVIES(1973).Asymptotic inference in stationary gaussian time series.Advances Applied Probability, vol.5,no3,pp.469-497.J.C.D ECKERT,M.N.D ESAI,J.J.D EYST and A.S.W ILLSKY(1977).F-8DFBW sensor failure identification using analytical redundancy.IEEE Trans.Automatic Control,vol.AC-22,no5,pp.795-803.M.H.D E G ROOT(1970).Optimal Statistical Decisions.Series in Probability and Statistics,McGraw-Hill, New York.J.D ESHAYES and D.P ICARD(1979).Tests de ruptures dans un mod`e pte-Rendus de l’Acad´e mie des Sciences,vol.288,Ser.A,pp.563-566(in French).B IBLIOGRAPHY429 J.D ESHAYES and D.P ICARD(1983).Ruptures de Mod`e les en Statistique.Th`e ses d’Etat,Universit´e deParis-Sud,Orsay,France(in French).J.D ESHAYES and D.P ICARD(1986).Off-line statistical analysis of change-point models using non para-metric and likelihood methods.In Detection of Abrupt Changes in Signals and Dynamical Systems(M. Basseville,A.Benveniste,eds.).Lecture Notes in Control and Information Sciences,LNCIS77,Springer, New York,pp.103-168.B.D EVAUCHELLE-G ACH(1991).Diagnostic M´e canique des Fatigues sur les Structures Soumises`a des Vibrations en Ambiance de Travail.Th`e se de l’Universit´e Paris IX Dauphine(in French).B.D EVAUCHELLE-G ACH,M.B ASSEVILLE and A.B ENVENISTE(1991).Diagnosing mechanical changes in vibrating systems.Proc.SAFEPROCESS’91,Baden-Baden,FRG,pp.85-89.R.D I F RANCESCO(1990).Real-time speech segmentation using pitch and convexity jump models:applica-tion to variable rate speech coding.IEEE Trans.Acoustics,Speech,Signal Processing,vol.ASSP-38,no5, pp.741-748.X.D ING and P.M.F RANK(1990).Fault detection via factorization approach.Systems and Control Letters, vol.14,pp.431-436.J.L.D OOB(1953).Stochastic Processes.Wiley,New York.V.D RAGALIN(1988).Asymptotic solutions in detecting a change in distribution under an unknown param-eter.Statistical Problems of Control,Issue83,Vilnius,pp.45-52.B.D UBUISSON(1990).Diagnostic et Reconnaissance des Formes.Trait´e des Nouvelles Technologies,S´e rie Diagnostic et Maintenance,Herm`e s,Paris(in French).A.J.D UNCAN(1986).Quality Control and Industrial Statistics,5th edition.Richard D.Irwin,Inc.,Home-wood,IL.J.D URBIN(1971).Boundary-crossing probabilities for the Brownian motion and Poisson processes and techniques for computing the power of the Kolmogorov-Smirnov test.Jal Applied Probability,vol.8,pp.431-453.J.D URBIN(1985).Thefirst passage density of the crossing of a continuous Gaussian process to a general boundary.Jal Applied Probability,vol.22,no1,pp.99-122.A.E MAMI-N AEINI,M.M.A KHTER and S.M.R OCK(1988).Effect of model uncertainty on failure detec-tion:the threshold selector.IEEE Trans.Automatic Control,vol.AC-33,no12,pp.1106-1115.J.D.E SARY,F.P ROSCHAN and D.W.W ALKUP(1967).Association of random variables with applications. Annals Mathematical Statistics,vol.38,pp.1466-1474.W.D.E WAN and K.W.K EMP(1960).Sampling inspection of continuous processes with no autocorrelation between successive results.Biometrika,vol.47,pp.263-280.G.F AVIER and A.S MOLDERS(1984).Adaptive smoother-predictors for tracking maneuvering targets.Proc. 23rd Conf.Decision and Control,Las Vegas,NV,pp.831-836.W.F ELLER(1966).An Introduction to Probability Theory and Its Applications,vol.2.Series in Probability and Mathematical Statistics,Wiley,New York.R.A.F ISHER(1925).Theory of statistical estimation.Proc.Cambridge Philosophical Society,vol.22, pp.700-725.M.F ISHMAN(1988).Optimization of the algorithm for the detection of a disorder,based on the statistic of exponential smoothing.In Statistical Problems of Control,Issue83,Vilnius,pp.146-151.R.F LETCHER(1980).Practical Methods of Optimization,2volumes.Wiley,New York.P.M.F RANK(1990).Fault diagnosis in dynamic systems using analytical and knowledge based redundancy -A survey and new results.Automatica,vol.26,pp.459-474.430B IBLIOGRAPHY P.M.F RANK(1991).Enhancement of robustness in observer-based fault detection.Proc.SAFEPRO-CESS’91,Baden-Baden,FRG,pp.275-287.P.M.F RANK and J.W¨UNNENBERG(1989).Robust fault diagnosis using unknown input observer schemes. In Fault Diagnosis in Dynamic Systems-Theory and Application(R.Patton,P.Frank,R.Clark,eds.). International Series in Systems and Control Engineering,Prentice Hall International,London,UK,pp.47-98.K.F UKUNAGA(1990).Introduction to Statistical Pattern Recognition,2d ed.Academic Press,New York. S.I.G ASS(1958).Linear Programming:Methods and Applications.McGraw Hill,New York.W.G E and C.Z.F ANG(1989).Extended robust observation approach for failure isolation.Int.Jal Control, vol.49,no5,pp.1537-1553.W.G ERSCH(1986).Two applications of parametric time series modeling methods.In Mechanical Signature Analysis-Theory and Applications(S.Braun,ed.),chap.10.Academic Press,London.J.J.G ERTLER(1988).Survey of model-based failure detection and isolation in complex plants.IEEE Control Systems Magazine,vol.8,no6,pp.3-11.J.J.G ERTLER(1991).Analytical redundancy methods in fault detection and isolation.Proc.SAFEPRO-CESS’91,Baden-Baden,FRG,pp.9-22.B.K.G HOSH(1970).Sequential Tests of Statistical Hypotheses.Addison-Wesley,Cambridge,MA.I.N.G IBRA(1975).Recent developments in control charts techniques.Jal Quality Technology,vol.7, pp.183-192.J.P.G ILMORE and R.A.M C K ERN(1972).A redundant strapdown inertial reference unit(SIRU).Jal Space-craft,vol.9,pp.39-47.M.A.G IRSHICK and H.R UBIN(1952).A Bayes approach to a quality control model.Annals Mathematical Statistics,vol.23,pp.114-125.A.L.G OEL and S.M.W U(1971).Determination of the ARL and a contour nomogram for CUSUM charts to control normal mean.Technometrics,vol.13,no2,pp.221-230.P.L.G OLDSMITH and H.W HITFIELD(1961).Average run lengths in cumulative chart quality control schemes.Technometrics,vol.3,pp.11-20.G.C.G OODWIN and K.S.S IN(1984).Adaptive Filtering,Prediction and rmation and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.R.M.G RAY and L.D.D AVISSON(1986).Random Processes:a Mathematical Approach for Engineers. Information and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.C.G UEGUEN and L.L.S CHARF(1980).Exact maximum likelihood identification for ARMA models:a signal processing perspective.Proc.1st EUSIPCO,Lausanne.D.E.G USTAFSON, A.S.W ILLSKY,J.Y.W ANG,M.C.L ANCASTER and J.H.T RIEBWASSER(1978). ECG/VCG rhythm diagnosis using statistical signal analysis.Part I:Identification of persistent rhythms. Part II:Identification of transient rhythms.IEEE Trans.Biomedical Engineering,vol.BME-25,pp.344-353 and353-361.F.G USTAFSSON(1991).Optimal segmentation of linear regression parameters.Proc.IFAC/IFORS Symp. Identification and System Parameter Estimation,Budapest,pp.225-229.T.H¨AGGLUND(1983).New Estimation Techniques for Adaptive Control.Ph.D.Thesis,Lund Institute of Technology,Lund,Sweden.T.H¨AGGLUND(1984).Adaptive control of systems subject to large parameter changes.Proc.IFAC9th World Congress,Budapest.B IBLIOGRAPHY431 P.H ALL and C.C.H EYDE(1980).Martingale Limit Theory and its Application.Probability and Mathemat-ical Statistics,a Series of Monographs and Textbooks,Academic Press,New York.W.J.H ALL,R.A.W IJSMAN and J.K.G HOSH(1965).The relationship between sufficiency and invariance with applications in sequential analysis.Ann.Math.Statist.,vol.36,pp.576-614.E.J.H ANNAN and M.D EISTLER(1988).The Statistical Theory of Linear Systems.Series in Probability and Mathematical Statistics,Wiley,New York.J.D.H EALY(1987).A note on multivariate CuSum procedures.Technometrics,vol.29,pp.402-412.D.M.H IMMELBLAU(1970).Process Analysis by Statistical Methods.Wiley,New York.D.M.H IMMELBLAU(1978).Fault Detection and Diagnosis in Chemical and Petrochemical Processes. Chemical Engineering Monographs,vol.8,Elsevier,Amsterdam.W.G.S.H INES(1976a).A simple monitor of a system with sudden parameter changes.IEEE r-mation Theory,vol.IT-22,no2,pp.210-216.W.G.S.H INES(1976b).Improving a simple monitor of a system with sudden parameter changes.IEEE rmation Theory,vol.IT-22,no4,pp.496-499.D.V.H INKLEY(1969).Inference about the intersection in two-phase regression.Biometrika,vol.56,no3, pp.495-504.D.V.H INKLEY(1970).Inference about the change point in a sequence of random variables.Biometrika, vol.57,no1,pp.1-17.D.V.H INKLEY(1971).Inference about the change point from cumulative sum-tests.Biometrika,vol.58, no3,pp.509-523.D.V.H INKLEY(1971).Inference in two-phase regression.Jal American Statistical Association,vol.66, no336,pp.736-743.J.R.H UDDLE(1983).Inertial navigation system error-model considerations in Kalmanfiltering applica-tions.In Control and Dynamic Systems(C.T.Leondes,ed.),Academic Press,New York,pp.293-339.J.S.H UNTER(1986).The exponentially weighted moving average.Jal Quality Technology,vol.18,pp.203-210.I.A.I BRAGIMOV and R.Z.K HASMINSKII(1981).Statistical Estimation-Asymptotic Theory.Applications of Mathematics Series,vol.16.Springer,New York.R.I SERMANN(1984).Process fault detection based on modeling and estimation methods-A survey.Auto-matica,vol.20,pp.387-404.N.I SHII,A.I WATA and N.S UZUMURA(1979).Segmentation of nonstationary time series.Int.Jal Systems Sciences,vol.10,pp.883-894.J.E.J ACKSON and R.A.B RADLEY(1961).Sequential and tests.Annals Mathematical Statistics, vol.32,pp.1063-1077.B.J AMES,K.L.J AMES and D.S IEGMUND(1988).Conditional boundary crossing probabilities with appli-cations to change-point problems.Annals Probability,vol.16,pp.825-839.M.K.J EERAGE(1990).Reliability analysis of fault-tolerant IMU architectures with redundant inertial sen-sors.IEEE Trans.Aerospace and Electronic Systems,vol.AES-5,no.7,pp.23-27.N.L.J OHNSON(1961).A simple theoretical approach to cumulative sum control charts.Jal American Sta-tistical Association,vol.56,pp.835-840.N.L.J OHNSON and F.C.L EONE(1962).Cumulative sum control charts:mathematical principles applied to their construction and use.Parts I,II,III.Industrial Quality Control,vol.18,pp.15-21;vol.19,pp.29-36; vol.20,pp.22-28.432B IBLIOGRAPHY R.A.J OHNSON and M.B AGSHAW(1974).The effect of serial correlation on the performance of CUSUM tests-Part I.Technometrics,vol.16,no.1,pp.103-112.H.L.J ONES(1973).Failure Detection in Linear Systems.Ph.D.Thesis,Dept.Aeronautics and Astronautics, MIT,Cambridge,MA.R.H.J ONES,D.H.C ROWELL and L.E.K APUNIAI(1970).Change detection model for serially correlated multivariate data.Biometrics,vol.26,no2,pp.269-280.M.J URGUTIS(1984).Comparison of the statistical properties of the estimates of the change times in an autoregressive process.In Statistical Problems of Control,Issue65,Vilnius,pp.234-243(in Russian).T.K AILATH(1980).Linear rmation and System Sciences Series,Prentice Hall,Englewood Cliffs,NJ.L.V.K ANTOROVICH and V.I.K RILOV(1958).Approximate Methods of Higher Analysis.Interscience,New York.S.K ARLIN and H.M.T AYLOR(1975).A First Course in Stochastic Processes,2d ed.Academic Press,New York.S.K ARLIN and H.M.T AYLOR(1981).A Second Course in Stochastic Processes.Academic Press,New York.D.K AZAKOS and P.P APANTONI-K AZAKOS(1980).Spectral distance measures between gaussian pro-cesses.IEEE Trans.Automatic Control,vol.AC-25,no5,pp.950-959.K.W.K EMP(1958).Formula for calculating the operating characteristic and average sample number of some sequential tests.Jal Royal Statistical Society,vol.B-20,no2,pp.379-386.K.W.K EMP(1961).The average run length of the cumulative sum chart when a V-mask is used.Jal Royal Statistical Society,vol.B-23,pp.149-153.K.W.K EMP(1967a).Formal expressions which can be used for the determination of operating character-istics and average sample number of a simple sequential test.Jal Royal Statistical Society,vol.B-29,no2, pp.248-262.K.W.K EMP(1967b).A simple procedure for determining upper and lower limits for the average sample run length of a cumulative sum scheme.Jal Royal Statistical Society,vol.B-29,no2,pp.263-265.D.P.K ENNEDY(1976).Some martingales related to cumulative sum tests and single server queues.Stochas-tic Processes and Appl.,vol.4,pp.261-269.T.H.K ERR(1980).Statistical analysis of two-ellipsoid overlap test for real time failure detection.IEEE Trans.Automatic Control,vol.AC-25,no4,pp.762-772.T.H.K ERR(1982).False alarm and correct detection probabilities over a time interval for restricted classes of failure detection algorithms.IEEE rmation Theory,vol.IT-24,pp.619-631.T.H.K ERR(1987).Decentralizedfiltering and redundancy management for multisensor navigation.IEEE Trans.Aerospace and Electronic systems,vol.AES-23,pp.83-119.Minor corrections on p.412and p.599 (May and July issues,respectively).R.A.K HAN(1978).Wald’s approximations to the average run length in cusum procedures.Jal Statistical Planning and Inference,vol.2,no1,pp.63-77.R.A.K HAN(1979).Somefirst passage problems related to cusum procedures.Stochastic Processes and Applications,vol.9,no2,pp.207-215.R.A.K HAN(1981).A note on Page’s two-sided cumulative sum procedures.Biometrika,vol.68,no3, pp.717-719.B IBLIOGRAPHY433 V.K IREICHIKOV,V.M ANGUSHEV and I.N IKIFOROV(1990).Investigation and application of CUSUM algorithms to monitoring of sensors.In Statistical Problems of Control,Issue89,Vilnius,pp.124-130(in Russian).G.K ITAGAWA and W.G ERSCH(1985).A smoothness prior time-varying AR coefficient modeling of non-stationary covariance time series.IEEE Trans.Automatic Control,vol.AC-30,no1,pp.48-56.N.K LIGIENE(1980).Probabilities of deviations of the change point estimate in statistical models.In Sta-tistical Problems of Control,Issue83,Vilnius,pp.80-86(in Russian).N.K LIGIENE and L.T ELKSNYS(1983).Methods of detecting instants of change of random process prop-erties.Automation and Remote Control,vol.44,no10,Part II,pp.1241-1283.J.K ORN,S.W.G ULLY and A.S.W ILLSKY(1982).Application of the generalized likelihood ratio algorithm to maneuver detection and estimation.Proc.American Control Conf.,Arlington,V A,pp.792-798.P.R.K RISHNAIAH and B.Q.M IAO(1988).Review about estimation of change points.In Handbook of Statistics(P.R.Krishnaiah,C.R.Rao,eds.),vol.7,Elsevier,New York,pp.375-402.P.K UDVA,N.V ISWANADHAM and A.R AMAKRISHNAN(1980).Observers for linear systems with unknown inputs.IEEE Trans.Automatic Control,vol.AC-25,no1,pp.113-115.S.K ULLBACK(1959).Information Theory and Statistics.Wiley,New York(also Dover,New York,1968). K.K UMAMARU,S.S AGARA and T.S¨ODERSTR¨OM(1989).Some statistical methods for fault diagnosis for dynamical systems.In Fault Diagnosis in Dynamic Systems-Theory and Application(R.Patton,P.Frank,R. Clark,eds.).International Series in Systems and Control Engineering,Prentice Hall International,London, UK,pp.439-476.A.K USHNIR,I.N IKIFOROV and I.S AVIN(1983).Statistical adaptive algorithms for automatic detection of seismic signals-Part I:One-dimensional case.In Earthquake Prediction and the Study of the Earth Structure,Naouka,Moscow(Computational Seismology,vol.15),pp.154-159(in Russian).L.L ADELLI(1990).Diffusion approximation for a pseudo-likelihood test process with application to de-tection of change in stochastic system.Stochastics and Stochastics Reports,vol.32,pp.1-25.T.L.L A¨I(1974).Control charts based on weighted sums.Annals Statistics,vol.2,no1,pp.134-147.T.L.L A¨I(1981).Asymptotic optimality of invariant sequential probability ratio tests.Annals Statistics, vol.9,no2,pp.318-333.D.G.L AINIOTIS(1971).Joint detection,estimation,and system identifirmation and Control, vol.19,pp.75-92.M.R.L EADBETTER,G.L INDGREN and H.R OOTZEN(1983).Extremes and Related Properties of Random Sequences and Processes.Series in Statistics,Springer,New York.L.L E C AM(1960).Locally asymptotically normal families of distributions.Univ.California Publications in Statistics,vol.3,pp.37-98.L.L E C AM(1986).Asymptotic Methods in Statistical Decision Theory.Series in Statistics,Springer,New York.E.L.L EHMANN(1986).Testing Statistical Hypotheses,2d ed.Wiley,New York.J.P.L EHOCZKY(1977).Formulas for stopped diffusion processes with stopping times based on the maxi-mum.Annals Probability,vol.5,no4,pp.601-607.H.R.L ERCHE(1980).Boundary Crossing of Brownian Motion.Lecture Notes in Statistics,vol.40,Springer, New York.L.L JUNG(1987).System Identification-Theory for the rmation and System Sciences Series, Prentice Hall,Englewood Cliffs,NJ.。
硼氮共掺杂生物质炭的制备及吸附性能研究

第42卷第6期2023年6月硅㊀酸㊀盐㊀通㊀报BULLETIN OF THE CHINESE CERAMIC SOCIETY Vol.42㊀No.6June,2023硼氮共掺杂生物质炭的制备及吸附性能研究许㊀蒙,郭玉呈,林国强,李建保,陈拥军,骆丽杰(海南大学材料科学与工程学院,南海海洋资源利用国家重点实验室,海口㊀570228)摘要:以木棉㊁硼酸(HBO 3)㊁尿素(CO(NH 2)2)为原料,在氨气(NH 3)气氛下通过高温反应制备了硼氮共掺杂生物质炭材料,利用聚乙烯亚胺(PEI)对硼碳氮(BCN)材料进行处理,得到PEI-BCN 材料,并研究了该材料的吸附性能㊂结果表明:当反应温度为1100ħ时,制备得到的BCN 材料为多孔结构,其平均孔径为11.0nm;BCN 材料的吸附能力优于生物质炭,经PEI 改性处理后,BCN 材料的吸附性能得到大幅提高,其对有机染料孔雀石绿(MG)的吸附量高达710.0mg /g;PEI-BCN 材料的吸附与准一级吸附动力学模型吻合,其对MG 的吸附属于Langmuir 等温吸附㊂关键词:硼碳氮材料;生物质炭;木棉;聚乙烯亚胺;高温反应;吸附;孔雀石绿中图分类号:X703㊀㊀文献标志码:A ㊀㊀文章编号:1001-1625(2023)06-2242-09Preparation and Adsorption Properties of Boron-Nitrogen Co-Doped Biochar MaterialsXU Meng ,GUO Yucheng ,LIN Guoqiang ,LI Jianbao ,CHEN Yongjun ,LUO Lijie(State Key Laboratory of Marine Resource Utilization in South China Sea,School of Materials Science and Engineering,Hainan University,Haikou 570228,China)Abstract :Boron-nitrogen co-doped biochar material was prepared by high temperature reaction under ammonia (NH 3)atmosphere,using kapok,boric acid (HBO 3),and urea (CO(NH 2)2)as raw materials.The PEI-BCN material was obtained by treating boron-carbon-nitrogen (BCN)material with polyethyleneimine (PEI),and the adsorption properties of PEI-BCN material were studied.The results show that the prepared BCN material has a porous structure with an averagepore size of 11.0nm when the reaction temperature is 1100ħ.The adsorption property of BCN material is better than that of biochar,and after PEI modification,the adsorption property of BCN material is greatly improved.The adsorption amount of organic dye malachite green (MG)by PEI-BCN material is up to 710.0mg /g,showing excellent adsorption property.The adsorption of PEI-BCN material is consistent with the pseudo-first-order adsorption kinetics model,and the adsorption of MG by PEI-BCN material belongs to Langmuir isothermal adsorption.Key words :BCN material;biochar;kapok;polythyleneimine;high temperature reaction;adsorption;malachite green 收稿日期:2023-02-16;修订日期:2023-03-08基金项目:海南省重点研发计划(ZDYF2021XDNY196)作者简介:许㊀蒙(1997 ),女,硕士研究生㊂主要从事吸附材料的研究㊂E-mail:xmm2021@通信作者:骆丽杰,博士,副教授㊂E-mail:992767@0㊀引㊀言水环境污染一直是世界多国关注的问题㊂纺织㊁金属加工㊁化肥工业㊁制革厂等行业是水体污染的主要来源[1]㊂开发水体污染物去除技术,对生态经济的可持续发展具有重要意义㊂当前水体修复的技术主要包括吸附法[2]㊁膜技术[3]㊁化学沉淀[4]㊁离子交换[5]㊁混凝[6]㊁浮选[7]和臭氧化[8],其中吸附法具有低能耗㊁低污染㊁低成本等优点,在工业废水处理等领域具有广阔的应用前景㊂目前吸附法所用材料主要包括金属氧化物[9-10]㊁过渡金属硫族化合物[11-12]㊁过渡金属碳化物[13]㊁凝胶[14-16]㊁炭类材料[17-18]等,其中生物质炭来源丰富且可实现循环使用,但其吸附性能有待提高㊂而氮化硼具有宽的能隙㊁高的抗氧化性和化学惰性,特别是B N 键具有极性,表面缺陷较多,对重金属污染物和染料污染物都表现㊀第6期许㊀蒙等:硼氮共掺杂生物质炭的制备及吸附性能研究2243出优良的吸附性能[19-21]㊂因此,硼碳氮(BCN)材料作为一种新型材料,不但具有与石墨和BN纳米材料相近的优异力学性能,还具有优异的电学性能㊁光催化性能㊁抗氧化能力[22]㊂因此,相比于C和BN,BCN纳米材料可在B原子㊁N原子和C原子处提供更多的位点,而C原子的存在还可以削弱B和N之间的电子共轭结构,从而增加对污染物的吸附量[23]㊂综上所述,从化学改性的思路出发,在生物质炭材料中引入异类原子,有望提高炭类材料的吸附性能;通过调节B㊁C和N原子的比例,有望优化BCN材料的吸附性能,可使炭类材料在污水处理方面发挥更好的作用㊂木棉纤维属于丝状纤维,具有独特的中空结构,是一种用于吸附污染物的有前途的生物质炭材料[24]㊂然而,木棉表面的蜡层抑制了亲水性着色剂和含离子的溶液进入木棉表面,需要进行预处理以改变其固有的表面性质才能进行吸附[25]㊂综上所述,本文以木棉为原料,通过高温化学反应实现B㊁N原子共掺杂来制备生物质炭材料,并利用聚乙烯亚胺(PEI)改性来提高材料的表面性能㊂以Cr3+㊁Cu2+㊁罗丹明B(RB)㊁孔雀石绿(MG)为吸附质,考察了改性前后BCN材料的吸附性能㊂通过吸附动力学分析和等温吸附曲线拟合,系统研究了BCN材料的吸附过程㊂1㊀实㊀验1.1㊀材料的制备将海南当地收集的木棉去除杂质并用去离子水洗净,干燥后放入乙醇水溶液中,并加入次氯酸钠,用乙酸将混合溶液的pH值调至4.5,于80ħ下超声进行脱脂处理,以去除木棉纤维表面的蜡质成分,然后用去离子水清洗至pH呈中性,真空干燥备用㊂向烧杯中加入硼酸㊁尿素和适量的去离子水,将烧杯放置在60ħ的水浴锅中搅拌,使硼酸㊁尿素完全溶解在去离子水中,随后将处理过的木棉浸泡在溶液中,使木棉完全吸收溶液后进行24h冷冻干燥㊂将冷冻干燥后的样品置于氧化铝瓷舟中,于高温管式气氛炉中的高温恒温区进行热处理,并密封反应系统㊂加热前,对管式炉炉管进行排空处理㊂然后在流动N2保护下,以5ħ㊃min-1的升温速率升温至1000ħ后关闭N2,通入流动NH3,继续升温至1100ħ,保温4h㊂反应结束后,将NH3关闭,在N2保护下样品随炉冷却至室温,将样品取出,记为BCN㊂将上述得到的BCN浸泡在PEI中,放置在60ħ电热恒温水浴锅中一定时间,随后取出干燥备用,记为PEI-BCN㊂为了进行比较,将海南当地收集到的木棉直接进行碳化,取出干燥备用,记为C㊂1.2㊀吸附试验将一定量的吸附剂加入配制好的无机污染物(硝酸铬㊁硝酸铜)和有机污染物(罗丹明B和孔雀石绿)溶液,在25ħ的吸附条件下模拟水流吸附循环试验㊂在不同时间下取吸附溶液(10mL),迅速置入离心机离心(5min,3600r/min)分离,取澄清的上层离心液,做好时间标记后保存待测㊂使用紫外分光光度计测试浓度,并根据式(1)计算样品的平衡吸附量Q e㊂Q e=(C0-C e)VM(1)式中:C0为初始浓度,mg㊃L-1;C e为平衡浓度,mg㊃L-1;V为溶液体积,L;M为吸附剂质量,g㊂1.3㊀结构表征采用X射线衍射仪(Rigaku Smart Lab)㊁傅里叶变换红外光谱仪(PerkinElmer Frontier)㊁X射线光电子能谱仪(Thermo ESCALAB250XI)对样品的组成㊁结构进行表征㊂采用扫描电子显微镜(Thermoscientific Verios G4UC)㊁透射电子显微镜(Talos F200X)分析样品的表面形貌㊂利用微孔物理吸附分析仪(麦克ASAP2460)研究样品的比面积和孔隙结构㊂利用有机元素分析仪(UNICUBE)分析木棉的元素组成㊂2㊀结果与讨论2.1㊀XRD和FTIR分析图1(a)为不同反应温度(1000㊁1100㊁1200ħ)下产物的XRD谱㊂从图1(a)中可以看出,26ʎ和42ʎ分2244㊀新型功能材料硅酸盐通报㊀㊀㊀㊀㊀㊀第42卷别对应BCN 材料类石墨烯结构的(002)晶面和(100)晶面[26]㊂随着温度升高,样品的结晶度提高㊂然而,根据密度理论函数[27],B N 键的能量稳定性高于其他键,所以高温不利于形成B C 键和N C 键,但有利于形成稳定的B N 键㊂由此推断反应温度过高,样品表面可能会生成氮化硼,因此反应温度选择1100ħ较适宜㊂从图1(b)中可以看出,799㊁1398cm -1处的特征吸收峰分别对应B N 键的横向振动和B N B 键的伸缩振动㊂3100㊁3500cm -1处存在的峰对应N H 键的伸缩振动和O H 键的伸缩振动,这些官能团的存在有利于后续吸附[28]㊂图1㊀不同温度下制备的BCN 样品的XRD 谱和FTIR 谱Fig.1㊀XRD patterns and FTIR spectra of BCN samples prepared at different temperatures 图2是BCN 样品经PEI 改性前后的FTIR 谱㊂图中显示BCN 的B N 键的横向振动峰和B N B 键的伸缩振动峰在790㊁1386cm -1左右,C N 键对应的峰在1660cm -1左右,而N H 键的伸缩振动峰在3150cm -1左右㊂对比BCN 样品,PEI 改性的BCN 样品(PEI-BCN)在N H 键处的峰值得到加强,这是由于PEI 接枝到BCN 样品中,使 NH 2数量增加,从而使该处的峰值得到增强;PEI 改性的BCN 样品(PEI-BCN)在1300cm -1左右的峰值有所增加,这归因于PEI 中的C N 键衍射峰增强㊂以上结果表明PEI 通过接枝方式成功对BCN 进行了改性㊂图2㊀BCN 样品改性前后的FTIR 谱Fig.2㊀FTIR spectra of BCN samples before and after modification 2.2㊀XPS 分析图3为BCN 样品的XPS 谱㊂从样品的全谱图中可以看出BCN 样品中包含了B㊁C㊁N 和O 元素㊂O 1s 峰可能归因于表面吸附的H 2O 和未反应的B O㊂高分辨率的B 1s㊁C 1s 和N 1s 光谱进一步证明了BCN 的成键特征和化学基团㊂从分峰拟合的结果来看,B 1s 特征峰在190.4㊁190.9㊁192.1eV 处的峰分别对应着B C㊁B N 和B O 键[29],C 1s 特征峰在284.7㊁285.5㊁286.7eV 处的峰分别对应着C B㊁C C 和C N 键[30],N 1s 特征峰在398.1㊁399.0㊁401.4eV 处的峰分别对应着N B㊁N C 和N H 键[31]㊂因此,可推断B㊁N 原子以成键的方式在生物质炭中实现掺杂㊂表1是经过计算后得到的BCN 的化学组成,其成分为第6期许㊀蒙等:硼氮共掺杂生物质炭的制备及吸附性能研究2245㊀B 0.41C 0.22N 0.37㊂㊀图3㊀BCN 样品的XPS 分析Fig.3㊀XPS analysis of BCN samples表1㊀BCN 样品的元素组成Table 1㊀Elemental composition of BCN samplesComposition B C N Atomic fraction /%4122372.3㊀显微结构分析图4(a)㊁(b)分别为木棉和脱脂木棉的SEM 照片㊂可以看出,木棉纤维直径均匀,表面光滑,而脱脂木棉纤维表面略显粗糙但仍保持中空结构㊂利用有机元素分析仪对脱脂木棉进行元素分析,发现本试验已经将木棉中的S㊁P 等脂肪有效去除,这可以增加木棉纤维表面的亲水性,为后续试验提供有利条件㊂图4(c)㊁(d)为BCN 样品在温度为1100ħ㊁升温速率为5ħ/min 条件下的SEM 照片㊂可以清楚地看到,BCN 样品呈多孔结构,并且还保留了木棉纤维的中空结构特征,样品的管壁表面还有许多微小的孔洞(见图4(d)中的放大图)㊂由于木棉纤维㊁HBO 3㊁CO(NH 2)2在热解过程中脱氢脱氧,产生大量的气体,在气体逸出过程中形成了多孔结构,这大大提高了材料的比表面积㊂2246㊀新型功能材料硅酸盐通报㊀㊀㊀㊀㊀㊀第42卷图4㊀木棉㊁脱脂木棉和BCN 样品的SEM 照片Fig.4㊀SEM images of kapok,defatted kapok,and BCN samples 2.4㊀TEM 分析图5为BCN 样品的TEM 表征结果㊂从图5(a)的高分辨TEM(HRTEM)照片可以看出,所得样品的晶格条纹杂乱,有结构缺陷,结晶度较差,样品存在的表面缺陷较多,提供的活性位点较多,有利于材料的吸附㊂测量结果显示BCN 样品(002)晶面的间距为0.345nm,这与XRD 计算结果相对应㊂图5(b)为样品的元素分布图,可以看到元素B㊁C㊁N 分布均匀,说明样品的主要成分为BCN㊂图5㊀BCN 样品的HRTEM 照片和元素面分布Fig.5㊀HRTEM image and elemental plane distribution of BCN samples 2.5㊀氮气吸附等温线为了进一步研究材料的比表面积和孔径分布,测定了BCN 样品和PEI-BCN 样品的氮气吸附-解吸等温线,如图6所示㊂样品的等温线呈IV 型,具有明显的滞后环㊂毛细凝聚现象使等温吸附与脱附曲线错位,产生部分吸附滞后现象,说明内部孔结构复杂[32]㊂通过比表面积测试仪测得BCN 材料的比表面积为73.67m 2/g㊂图7是BCN 样品和PEI-BCN 样品的孔径分布,可以看出BCN 样品的平均孔径为11.0nm㊂经过PEI 改性后,所得PEI-BCN 样品的孔径分布范围有所增加,孔径稍有增大,平均孔径为12.6nm,属于介孔结构㊂结合SEM 结果可以得出材料内部存在大孔㊁中孔和微孔,它们之间的相互连接能够促进离子快速传输[33]㊂因此改性后的BCN 具有多级孔结构,这使得材料拥有更加丰富的活性位点,从而能够提高BCN 材料对污染物的吸附效率㊂2.6㊀吸附性能选用两种无机污染物(Cr 3+㊁Cu 2+)和两种有机污染物(罗丹明B㊁孔雀石绿)作为吸附质,对改性前后BCN 的吸附性能进行了研究,如图8所示㊂从图8可以看出,PEI-BCN 对Cu 2+㊁Cr 3+㊁RB 和MG 的吸附量均明显高于BCN,且改性后BCN 材料对孔雀石绿的吸附能力高达710.0mg /g,这是由于PEI 被成功接枝到BCN 结构中㊂PEI 具有大量氨基( NH 2),经过PEI 改性过后,BCN 对离子的配位络合作用更强,对染料的吸附增强㊂Cr 3+的吸附量大于Cu 2+,这种行为可能与Cu 2+比Cr 3+半径大有关㊂BCN 材料的孔结构以介孔为主,因此,离子半径小的金属可以更多地进入吸附剂的孔中,与吸附剂的活性位点相互作用㊂MG 是带有第6期许㊀蒙等:硼氮共掺杂生物质炭的制备及吸附性能研究2247㊀电子的阴离子染料,RB 是阳离子染料,因此PEI-BCN 对MG 的吸附能力大于RB㊂图9为MG 不同初始浓度下C㊁BCN 和PEI-BCN 的吸附性能,可以看出吸附量随着初始浓度的增大而增大㊂这是由于在吸附过程中样品内部所具有的吸附位点数量是不变的,离子的初始浓度越高越有利于离子的传质,因此随着溶液初始浓度增大,样品对离子的吸附量也会增大㊂另外,可以看到BCN 对MG 的吸附性能也明显高于生物质炭材料㊂由此可见,通过B㊁N 掺杂炭材料,可以形成B N㊁C N 等极性键,增加材料表面缺陷结构,从而提高其吸附性能[19-21]㊂图6㊀BCN 和PEI-BCN 的氮气吸附-解吸等温线Fig.6㊀Nitrogen adsorption-desorption isotherm curves of BCN andPEI-BCN 图7㊀BCN 和PEI-BCN 的孔径分布Fig.7㊀Pore size distribution of BCN andPEI-BCN 图8㊀BCN 和PEI-BCN 在Cr 3+㊁Cu 2+㊁RB 和MG 初始浓度为50mg /L 的条件下的吸附性能Fig.8㊀Adsorption properties of BCN and PEI-BCN at initial concentration of 50mg /L for Cr 3+,Cu 2+,RB andMG 图9㊀MG 不同初始浓度下C㊁BCN 和PEI-BCN 的吸附性能Fig.9㊀Adsorption properties of C,BCN and PEI-BCN at different initial concentration of MG2.7㊀等温吸附模型吸附等温线可以反映吸附过程中吸附剂与被吸附剂之间的相互作用关系,推导出吸附的具体机理㊂PEI-BCN 在25ħ下对MG 的吸附等温线如图10所示㊂Q e 值先增大,随后趋于稳定㊂这是因为当吸附浓度较低时,吸附剂的结合位点足够吸附,而随着MG 浓度的不断增加,PEI-BCN 的固有吸附位点被MG 完全占有,吸附逐渐达到饱和㊂此外,利用Langmuir 和Freundlich 等温模型对吸附过程进行了拟合,其中Langmuir 等温模型是假设吸附发生在单层表面且吸附表面均匀,吸附剂颗粒相互独立,而Freundlich 等温模型假设吸附同时发生在单层和多层㊂表2为Langmuir 和Freundlich 等温吸附模型参数㊂从表2可以看出,Langmuir 模型的常数R 2达到了0.998,这说明拟合结果符合Langmuir 吸附模型,MG 的吸附过程主要为单分子吸附㊂2248㊀新型功能材料硅酸盐通报㊀㊀㊀㊀㊀㊀第42卷图10㊀Langmuir等温吸附和Freundlich等温吸附的拟合曲线Fig.10㊀Fitting curves of Langmuir isotherm adsorption and Freundlich isotherm adsorption表2㊀Langmuir等温吸附和Freundlich等温吸附模型参数Table2㊀Model parameters of Langmuir isothermal adsorption and Freundlich isothermal adsorptionLangmuir model Freundlich modelQ max/(mg㊃g-1)K L/(L㊃mg-1)R2K F/(mg㊃g-1)(L㊃mg-1)1/n n R2811.584 1.070.998374.5690.350.960㊀㊀注:Q max代表单层分子吸附剂能有效捕获的物质的量;K L和K F分别为Langmuir和Freundlich等温吸附模型的平衡吸附常数㊂2.8㊀吸附动力学图11为准一级和准二级吸附动力学拟合曲线以及ln(Q e-Q T)㊁T/Q T与时间T的关系曲线,其中Q T为T时刻的吸附量㊂表3为准一级和准二级吸附动力学模型拟合参数㊂可以看出,PEI-BCN材料对MG的吸附过程大致分为三个阶段:在初始的0~50min,PEI-BCN对MG的吸附速度快,为快吸附阶段;在50~180min,材料对MG的吸附速度较之前开始下降,为慢吸附阶段;180min后吸附速度基本不变,吸附基本达到平衡㊂从表3可以看出,准一级模型的R2值在0.999左右,高于准二级模型的R2值,说明准一级动力学模型更适合描述PEI-BCN对MG的吸附行为㊂由于所得BCN材料具有中空结构,在吸附过程中,MG离子可以快速地扩散至材料内部活性位点,从而被吸附㊂表3㊀准一级和准二级吸附动力学模型拟合参数Table3㊀Fitting parameters of pseudo-first-order and pseudo-second-order adsorption kinetics modelsMG concentration/ (mg㊃L-1)Pseudo-first-order Pseudo-second-orderQ e/(mg㊃g-1)Intercept R2Q e/(mg㊃g-1)Intercept R210160.271 6.5780.999184.1640.0570.995 20324.180 6.6550.992391.3860.0920.985 40660.867 5.8150.998833.8210.1400.996 50715.030 4.9100.999854.2710.1730.989第6期许㊀蒙等:硼氮共掺杂生物质炭的制备及吸附性能研究2249㊀图11㊀吸附试验结果Fig.11㊀Adsorption test results 3㊀结㊀论1)采用高温化学反应法利用天然木棉制备了BCN 多孔材料,其平均孔径为11.0nm,吸附性能优于生物质炭㊂2)经过PEI 改性后的PEI-BCN 材料的平均孔径为12.6nm,其吸附能力大幅增加,其中对MG 的吸附高达710.0mg /g㊂3)PEI-BCN 对MG 的吸附属于均匀表面单层分子的等温吸附㊂经过对比发现MG 的吸附动力学过程更符合准一级吸附动力学模型㊂参考文献[1]㊀ALALWAN H A,KADHOM M A,ALMINSHID A H.Removal of heavy metals from wastewater using agricultural by products[J].Journal ofWater Supply:Research and Technology-Aqua,2020,69(2):99-112.[2]㊀DAS R,VECITIS C D,SCHULZE A,et al.Recent advances in nanomaterials for water protection and monitoring [J].Chemical SocietyReviews,2017,46(22):6946-7020.[3]㊀曹国凭,赵㊀萍,李文洁.膜法水处理技术研究进展与发展趋势[J].水利科技与经济,2006,12(8):539-540+543.CAO G P,ZHAO P,LI W J.Study progress and development trend in water treatment technology of the membrane separation technology[J].Water Conservancy Science and Technology and Economy,2006,12(8):539-540+543(in Chinese).[4]㊀AMA O M,KUMAR N,ADAMS F V,et al.Efficient and cost-effective photoelectrochemical degradation of dyes in wastewater over an exfoliated graphite-MoO 3nanocomposite electrode[J].Electrocatalysis,2018,9(5):623-631.[5]㊀ISLAM M S,CHOI W S,NAM B,et al.Needle-like iron oxide@CaCO 3adsorbents for ultrafast removal of anionic and cationic heavy metal ions[J].Chemical Engineering Journal,2017,307:208-219.[6]㊀CHAKRABORTY R,ASTHANA A,SINGH A K,et al.Adsorption of heavy metal ions by various low-cost adsorbents:a review [J ].International Journal of Environmental Analytical Chemistry,2022,102(2):342-379.[7]㊀起冰翠,薛玉兰,林㊀强.浮选技术在环境综合治理中的应用[J].矿产保护与利用,1999(1):51-53.QI B C,XUE Y L,LIN Q.Applications of flotation technology to environmental comprehensive treatment[J].Conservation and Utilization ofMineral Resources,1999(1):51-53(in Chinese).[8]㊀王㊀郑,程星星,黄㊀雷,等.催化臭氧化技术在水处理中的应用研究进展[J].应用化工,2017,46(6):1214-1217+1233.WANG Z,CHENG X X,HUANG L,et al.Research application progress of catalytic ozonation technology in water treatment[J].AppliedChemical Industry,2017,46(6):1214-1217+1233(in Chinese).[9]㊀YANG Z H,MA J X,LIU F,et al.Mechanistic insight into pH-dependent adsorption and coprecipitation of chelated heavy metals by in situformed iron (oxy)hydroxides[J].Journal of Colloid and Interface Science,2022,608:864-872.[10]㊀毕玉玺,凌㊀辉,唐振平,等.磁性介孔TiO 2/氧化石墨烯复合材料的制备及其对U(Ⅵ)的吸附[J].复合材料学报,2019,36(9):2176-2186.BI Y X,LING H,TANG Z P,et al.Preparation of magnetic mesoporous TiO 2/graphene oxide composites and their adsorption for U(Ⅵ)[J].Acta Materiae Compositae Sinica,2019,36(9):2176-2186(in Chinese).2250㊀新型功能材料硅酸盐通报㊀㊀㊀㊀㊀㊀第42卷[11]㊀WANG Z Y,MI B X.Environmental applications of2D molybdenum disulfide(MoS2)nanosheets[J].Environmental Science&Technology,2017,51(15):8229-8244.[12]㊀SUN L F,XU K,GUI X F,et al.Reduction-responsive sulfur-monoterpene polysulfides in microfiber for adsorption of aqueous heavy metal[J].Journal of Water Process Engineering,2021,43:102247.[13]㊀ZHANG Y J,WANG L,ZHANG N N,et al.Adsorptive environmental applications of MXene nanomaterials:a review[J].RSC Advances,2018,8(36):19895-19905.[14]㊀ZHANG Y F,WU L,DENG H L,et al.Modified graphene oxide composite aerogels for enhanced adsorption behavior to heavy metal ions[J].Journal of Environmental Chemical Engineering,2021,9(5):106008.[15]㊀GENG B Y,XU Z Y,LIANG P,et al.Three-dimensional macroscopic aminosilylated nanocellulose aerogels as sustainable bio-adsorbents for theeffective removal of heavy metal ions[J].International Journal of Biological Macromolecules,2021,190:170-177.[16]㊀袁㊀琦,王玉珑,韩俊源,等.羧甲基纤维素钠/己二酸二酰肼水凝胶的制备及其重金属离子吸附性能研究[J].中国造纸学报,2021,36(4):38-47.YUAN Q,WANG Y L,HAN J Y,et al.Study on preparation of sodium carboxymethyl cellulose/adipic dihydrazide hydrogel and its adsorption performance for heavy metal ions[J].Transactions of China Pulp and Paper,2021,36(4):38-47(in Chinese).[17]㊀CAO Y,DHAHAD H A,HUSSEN H M,et al.Adsorption properties of two-dimensional carbon material towards the heavy metal ions[J].Journal of Molecular Liquids,2021,342:117500.[18]㊀FU Y K,QIN L,HUANG D L,et al.Chitosan functionalized activated coke for Au nanoparticles anchoring:green synthesis and catalyticactivities in hydrogenation of nitrophenols and azo dyes[J].Applied Catalysis B:Environmental,2019,255:117740.[19]㊀PAN X H,ZUO G C,SU T,et al.Polycarboxylic magnetic polydopamine sub-microspheres for effective adsorption of malachite green[J].Colloids and Surfaces A:Physicochemical and Engineering Aspects,2019,560:106-113.[20]㊀LIU F,LI S,YU D F,et al.Template-free synthesis of oxygen-doped bundlelike porous boron nitride for highly efficient removal of heavy metalsfrom wastewater[J].ACS Sustainable Chemistry&Engineering,2018,6(12):16011-16020.[21]㊀LI S,LIU F,SU Y P,et al.Luffa sponge-derived hierarchical meso/macroporous boron nitride fibers as superior sorbents for heavy metalsequestration[J].Journal of Hazardous Materials,2019,378:120669.[22]㊀DOROZHKIN P,GOLBERG D,BANDO Y,et al.Field emission from individual B-C-N nanotube rope[J].Applied Physics Letters,2002,81(6):1083-1085.[23]㊀WEI Y C,WU P W,LUO J,et al.Synthesis of hierarchical porous BCN using ternary deep eutectic solvent as precursor and template for aerobicoxidative desulfurization[J].Microporous and Mesoporous Materials,2020,293:109788.[24]㊀BALELA M D L,INTILA N M,SALVANERA S R.Adsorptive removal of lead ions in aqueous solution by kapok-polyacrylonitrilenanocomposites[J].Materials Today:Proceedings,2019,17:672-678.[25]㊀ZHENG Y A,ZHU Y F,WANG A Q.Kapok fiber structure-oriented polyallylthiourea:efficient adsorptive reduction for Au(III)for catalyticapplication[J].Polymer,2014,55(20):5211-5217.[26]㊀SHI Y M,HAMSEN C,JIA X T,et al.Synthesis of few-layer hexagonal boron nitride thin film by chemical vapor deposition[J].Nano Letters,2010,10(10):4134-4139.[27]㊀NOZAKI H,ITOH ttice dynamics of BC2N[J].Physical Review B,1996,53(21):14161-14170.[28]㊀CI L J,SONG L,JIN C H,et al.Atomic layers of hybridized boron nitride and graphene domains[J].Nature Materials,2010,9(5):430-435.[29]㊀ZHANG L,HE Q,HUANG S,et al.A novel boron and nitrogen co-doped three-dimensional porous graphene sheet framework as highperformance Li-ion battery anode material[J].Inorganic Chemistry Communications,2018,96:159-164.[30]㊀SUN C L,MA F K,CAI L,et al.Metal-free ternary BCN nanosheets with synergetic effect of band gap engineering and magnetic properties[J].Scientific Reports,2017,7:6617.[31]㊀WU Z S,PARVEZ K,WINTER A,et yer-by-layer assembled heteroatom-doped graphene films with ultrahigh volumetric capacitance andrate capability for micro-supercapacitors[J].Advanced Materials,2014,26(26):4552-4558.[32]㊀李昊远.氮气吸附法的致密砂岩孔隙结构分析[J].云南化工,2019,46(12):87-90+94.LI H Y.Pore structure analysis of tight sandstone by nitrogen adsorption method[J].Yunnan Chemical Technology,2019,46(12):87-90+94 (in Chinese).[33]㊀SUN J T,ZHANG Z P,JI J,et al.Removal of Cr6+from wastewater via adsorption with high-specific-surface-area nitrogen-doped hierarchicalporous carbon derived from silkworm cocoon[J].Applied Surface Science,2017,405:372-379.。
Concepts

Rotordynamic Results
• System will run super-critical • Proper design choices needed to stay below first bending mode
Optimization Setup
• Variables:
– Blade thickness (8) – Impeller backface (5)
– Off the shelf packaged automated optimization of turbomachinery fluid dynamics using CFD and iSIGHT – Add FEA into automated optimization
• Next year
• Second optimization loop:
– Constant blade shape, solid FEA – Reduced stress to 105 ksi
• Highlights the stress / weight trade
Stress-Weight Trade
• Physical boundary imposed by geometry
Stress-Weight Trade
• Physical boundary imposed by geometry • Upper stress limit imposed by material properties
stress limit
Stress-Weight Trade
• Physical boundary imposed by geometry • Upper stress limit imposed by material properties • Upper weight limit imposed by bearings, rotordynamics, weight budget
斯伦贝谢Eclipse软件

ECLIPSE 2013.1 发布2013年7月18日:斯伦贝谢发布了ELCIPSE 2013.1版本描述:ECLIPSE系列软件体系为石油工业提供了最完整、最全面、最强大的数值模拟研究工具,涵盖各个类型油气藏的数值模拟,有效解决各领域复杂难题——从构造、地质、流体乃至开发方案,帮助您快速、精确、高效地预测储层生产动态!ECLIPSE系列软件体系支持全部类型油气藏模型的构建——黑油、组分、热采以及流线模型。
本版本升级了ELCIPSE黑油模拟器、组分模拟器和流线模拟器的部分功能。
化学驱提高采收率建模功能得到丰富,在ECLIPSE黑油模拟器中添加了模拟聚合物的选项,在ECLIPSE组分模拟器中添加了新的表面活性剂驱油模型。
与此同时,该版本秉承以往各版本,继续发展对Petrel油气藏工程研究平台集成工作流的支持。
本版本将与MEPO4.2绑定发放,用户可以从DVD中安装,也可以从网上下载。
MEPO是一款多重实现优化工具箱,帮助您提交、管理模拟数值模型。
油气藏工程师通过MEPO可以优化数值模拟工作流,实现工作流程半自动化。
MEPO最常用于辅助历史拟合、不确定性分析、敏感性分析以及油气田开发方案优化设计。
注释:ECLIPSE软件套装交互式前后处理程序仅支持Windows操作系统,目前我们仅提供重大Bug修复的售后服务。
我们向您推荐功能更为强大的Petrel油气藏工程研究平台作为ECLIPSE前后处理程序。
ECLIPSE软件包部分功能不支持Linux操作系统。
Eclipse Office, FloGrid, FloViz, Schedule模块仅支持Windows操作系统。
本版本的官方DVD中没有提供IBM ppc64专用模拟器,如果您需要,我们另行为您提供。
升级模块:ECLIPSE 2013.1模拟化学驱提高采收率技术在ECLIPSE黑油模块扩展了聚合物选项,支持聚合物、冻胶高级建模,包括具有温度敏感性的聚合物。
ProSystem fx Engagement到Workpapers CS数据转换信息Kit说明书

Information Kit for Conversions from ProSystem fx Engagement to Workpapers CSThis document provides information about the data converted from ProSystem fx® Engagement to Workpapers CS™.ContentsWhat to expect from the data conversion (2)Conversion considerations and recommendations (2)Installing the conversion program (2)Converting the client data before import into Workpapers CS (2)Data transferred during conversion (4)Chart of Accounts and balances (4)Grouping schedules (5)Transactions (5)Engagement-related data transferred during conversion (6)Engagement information (6)Folder information (7)Workpaper information (7)ProSystem fx Engagement Excel and Word demographic formulas (7)ProSystem fx Engagement Excel and Word link formulas (8)Conversion notes and exceptions (8)Items not converted (8)Data Conversion Report (9)Getting help (9)Help & How-To Center (9)Product support (9)What to expect from the data conversionThe overall objective of the data conversion from ProSystem fx Engagement is to provide accurate, comprehensive Workpapers CS data to help you move forward with Workpapers CS.Important!Due to differences between applications, some data must be modified during the conversion process and some data cannot be converted. Additions and/or modifications may be required to exactly duplicate engagement and workpaper information in Workpapers CS after the conversion.Conversion considerations and recommendationsPlease review the following before beginning the conversion process.▪We recommend that you convert a smaller, easy-to-process client first. This will help you become familiar with the conversion options in Workpapers CS.▪Some data items from ProSystem fx Engagement are not converted because there is no exact equivalent in Workpapers CS.Installing the conversion programClick this link to download a ZIP file and install the ProSystem fx Engagement to Workpapers CS conversion utility.Converting the client data before import into Workpapers CS Important! When you convert large or complex sets of engagement files for a ProSystem fx Engagement client, you should allow a significant amount of time for the conversion and import. Please wait for the process to be completed before converting another client.After installing the ProSystem fx Engagement to Workpaper CS conversion program, use the following steps to create the converted data files for import into Workpaper CS.The conversion process does not modify existing client data in ProSystem fx Engagement. However, we strongly recommend that you create a backup of the original client before you process any clients.1. Verify that the ProSystem fx Engagement binder has been synchronized with the Local File Roomand that any instances of this binder or workpapers are closed on your workstation.2. To start the conversion program, right-click the CS Data Conversions icon on your desktop andchoose Run as Administrator. If you did not install the shortcut, click Start on the Windows taskbar and then choose All Programs > CS Professional Suite > CS Data Conversions.3. In the Select competitor field, select ProSystem fx from the drop-down list.4. In the Select the export location for the converted files field, click the Browse button to browse to thelocation where the import files should be placed until imported into WorkpaperCS.5. Click Start conversion.6. If prompted to close all open sessions of Word® and Excel®, close those sessions.7. If prompted to select your user, select the login for the Local File Room for which you want to convertdata. This dialog will open only if multiple logins exist on the workstation.8. In the Processing Type dialog, click either Single or Multiple. Single converts just one client at a timeand allows for greater customization. Multiple allows for multiple clients, but the application makes more assumptions about the clients during the conversion.9. In the Select a Client dialog or Select client(s) dialog, select the client(s) you want to convert, andclick Continue.Note: This dialog lists all available clients for conversion from ProSystem fx Engagement. Yourselection of Single or Multiple in step 8 determines whether you can select one or multiple clients. 10. In the Engagement selection dialog, which lists all of the binders / engagements for the selectedclient(s), select an engagement type for each binder you want to convert, and then click Continue. 11. If you selected a single conversion, an optional Trial Balance selection dialog may open if multipleTrial Balances existed in ProSystem fx Engagement. Workpapers CS supports only one Trial Balance per engagement. Select the desired Trial Balance.If you selected multiple conversions, the last accessed Trial Balance will be used.12. Click Continue.13. In the Account classification selection dialog, select the ProSystem fx Engagement group thatcontains the account classification you want to use in Workpaper CS.Note: If you click Skip, the program will not convert any Account Classifications for the Trial Balance Accounts.14. In the Tax group selection dialog, select the set of tax codes to convert for your Trial Balance.If you selected multiple conversions, the last tax year will be used.15. Click Continue to begin the data conversion process, and then follow the prompts that appear on thescreen.16. At the prompt indicating the conversion process is complete, click OK to begin importing theconverted data into Workpapers CS.17. In Accounting CS, choose File > Import > ProSystem fx Engagement to open the ProSystem fxEngagement conversion wizard.18. Source Data: Select the location where your ProSystem fx Engagement export files are stored andclick Next.19. Source Data - Clients: Mark the checkbox next to the ProSystem fx Engagement client—or multipleclients—that you want to convert, and then click Next.20. Staff: Select the Accounting CS Workpapers staff member—or multiple staff members—to map to foreach corresponding ProSystem fx Engagement staff in the list.Note:If the appropriate staff member is not available from the drop-down list in the Accounting CS Staff column, exit the wizard and add that staff member in the Setup > Firm Information > Staffscreen, and then restart the conversion process.21. Click Finish to complete the conversion.Data transferred during conversionThe following tables detail the ProSystem fx Engagement data that converts to Workpapers CS.Chart of Accounts and balancesProSystem fx Engagement menu navigation andfield name Workpapers CS menunavigation and field nameComments and additionalinformationTrial Balance > Chart ofAccountsActions > Enter Trial BalanceAccount # Account numberDescription DescriptionReport ReportBudget BudgetProposed PotentialUNADJ Unadjusted Unadjusted balance is convertedonly for the current period.ADJ Adjusted Prior-year and prior-periodbalances only.FTAX Tax Prior-year and prior-periodbalances only.OBAL1 Other Prior-year and prior-periodbalances only.Trial Balance > AccountGroupings > Tax CodeAccount GroupingTax Code Tax Code Tax codes and tax codeassignments for clients with ayear end of 2012 or later.menu navigation andfield namenavigation and field name informationTrial Balance > AccountGroupings > Group AccountGrouping > AdvancedAccClass RatioClass Classification codeClassification subcodeIn ProSystem fx Engagement,classification and ratios are seton a group-by-group basis.During the conversion process,you will be asked from whichgroup we should pullclassification and ratios.Grouping schedulesProSystem fx Engagement menu navigation andfield name Workpapers CS menunavigation and field nameComments and additionalinformationTrial Balance > AccountGroupings > Group AccountGroupingEnter Trial Balance > Account Groupings Account group name GroupingCode CodeCode Description Code DescriptionSubcode SubcodeSubcode Description Subcode DescriptionTransactionsProSystem fx Engagement menu navigation andfield name Workpapers CS menunavigation and field nameComments and additionalinformationTrial Balance > Journal EntrySummaryActions > Enter Transactions JE# ReferenceDescription DescriptionAdditional Distributions (Account, Amount, Description) Distributions (Account, Account Description, Amount)menu navigation andfield namenavigation and field name information Reversing journal entry Auto-reverse next periodType:Adjusting Journal Entries Reclassifying Journal Entries Federal Tax Journal Entries Other Journal Entries1 Proposed Journal Entry Type:AdjustingReclassifyingTaxOtherPotentialJournal entries are posted to thespecific engagement for whichthe entries were intended.Engagement-related data transferred during conversionThe following information is provided to identify ProSystem fx Engagement items that are automatically converted to Workpapers CS items.Engagement informationProSystem fx Engagement menu navigation andfield name Workpapers CS menunavigation and field nameComments and additionalinformationBinder Properties Engagement PropertiesName Engagement binder name If you convert multiple binders fora single client, the binders musthave a unique name.Type Type You must select the newWorkpapers CS type during theconversion.Entity In the ProSystem fx Engagementconversion, Entity is determinedby the selection on the TaxGroup selection screen. Thisdata is mapped to the Client >Accounting information tab. Period sequence Period FrequencyBinder Index View Binder TreeEngagement tree structure Engagement tree structureFolder informationProSystem fx Engagement menu navigation andfield name Workpapers CS menunavigation and field nameComments and additionalinformationTab Properties Engagement tree structureIndex # Folder name Index # and Name are combinedto comprise the Workpapers CSfolder name.Name Folder nameWorkpaper informationProSystem fx Engagement menu navigation andfield name Workpapers CS menunavigation and field nameComments and additionalinformationWorkpaper Properties Workpaper PropertiesName NameIndex # ReferenceSign Off: Preparers Preparer You can rename Preparer,Reviewer, and Reviewer 2names in Workpapers CS, ifdesired.Sign Off: 1st Reviewers Reviewer You can rename Preparer,Reviewer, and Reviewer 2names in Workpapers CS, ifdesired.Sign Off: 2nd Reviewers This will depend on staff mappingand whether signoffs are set upin Workpapers CS beforehand. Sign Off Initials Sign Off Initials Initials and date will display underthe signed off heading inWorkpapers CS.ProSystem fx Engagement Excel and Word demographic formulasThe following table lists the applicable ProSystem fx Engagement formulas and the equivalent formula variables in Workpapers CS.ProSystem fx EngagementName FunctionsWorkpapers CS VariablesBinder Name Engagement NameBinder Due Date Completion DateBinder Type Engagement TypeProSystem fx EngagementWorkpapers CS VariablesName FunctionsBinder Report Release Date Report Release DateWorkpaper Name Workpaper NameWorkpaper Index Workpaper ReferenceCurrent Period End Current Period DateProSystem fx Engagement Excel and Word link formulasExcel® and Word® link formulas do not convert.Conversion notes and exceptionsThis section details conversion notes and exceptions.▪Engagement tree structure: The order and appearance of the engagement tree structure in Workpapers CS after the conversion may differ from the ProSystem fx Engagement binder. Please note all items are converted to the correct folder locations within the engagement. To providemaximum flexibility, Workpapers CS does not automatically sort folders and workpapers.▪Excel and Word workpaper add-ins, macros, and links: Excel workpapers are modified during the conversion process for removal of add-ins, macros, and/or links.▪Manual workpapers: Manual workpapers are converted as text documents.▪Tax Codes: If UltraTax CS® Tax Codes are desired during the conversion, a translation of ProSystem fx Engagement Tax Codes to UltraTax CS is available. Only one Tax Code Group will convert.▪Workpaper references: Workpapers CS requires that workpapers have reference values.Workpapers without an index value are assigned a reference value during the conversion. You may rename the workpaper reference, if desired. If a duplicate reference exists in a folder, the duplicate references will be renamed.▪Finalized Binders: Finalized binders will be converted as Active unfinalized binders. We recommend that you convert only active / unfinalized binders.Items not convertedThis section details items not converted.▪Workpapers not in a standard binder folder: This includes workpapers within the Unfiled Workpapers, Conflicts, Incompatible Workpapers, Published Workpapers, and Trash folders. To convert these workpapers, you must move the workpapers into a standard binder folder before the conversion process.▪Trial Balance: Consolidated trial balances.▪Firm information▪Client Information▪Engagement and workpaper password information▪Engagement and workpaper history▪Workpaper notes and templates▪Staff▪M3 Tax CodesData Conversion ReportThe data conversion from ProSystem fx Engagement to Workpapers CS creates a report for each engagement converted. The Data Conversion report lists certain modifications made during the conversion process, such as truncations, abbreviations, and so on. Most items in the report are informational and do not require immediate attention.To access the report, locate and open YYYYYY.html, where YYYYYY is the binder name. The report is placed in the user’s Documents folder.Getting helpHelp & How-To CenterFor answers to questions on using Workpapers CS, access the Help & How-To Center by clicking the Help link on the toolbar. For more information, including sample searches, see Finding answers in the Help & How-To Center.Product supportFrom the Support Contact Information page on our website, you can complete a form to send a question to our Support team. For additional product support, visit the Support section of our website. You can also access our Support website from Workpapers CS by choosing Help > Additional Resources > General Support Information.。
CCF推荐国际学术会议
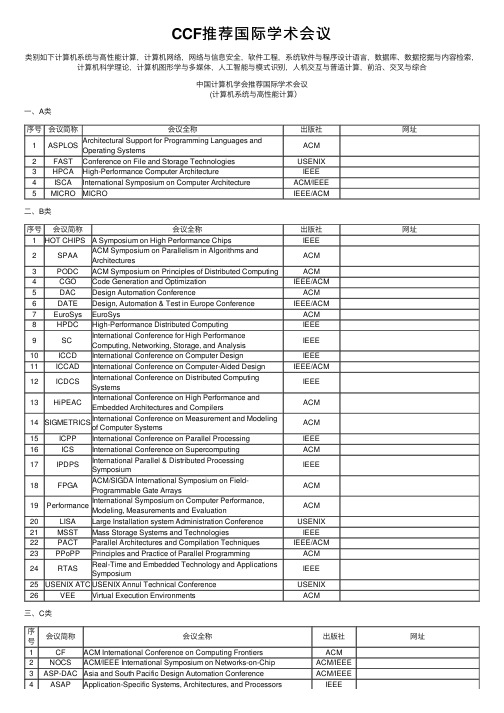
CCF推荐国际学术会议类别如下计算机系统与⾼性能计算,计算机⽹络,⽹络与信息安全,软件⼯程,系统软件与程序设计语⾔,数据库、数据挖掘与内容检索,计算机科学理论,计算机图形学与多媒体,⼈⼯智能与模式识别,⼈机交互与普适计算,前沿、交叉与综合中国计算机学会推荐国际学术会议 (计算机系统与⾼性能计算)⼀、A类序号会议简称会议全称出版社⽹址1ASPLOS Architectural Support for Programming Languages andOperating SystemsACM2FAST Conference on File and Storage Technologies USENIX3HPCA High-Performance Computer Architecture IEEE4ISCA International Symposium on Computer Architecture ACM/IEEE5MICRO MICRO IEEE/ACM⼆、B类序号会议简称会议全称出版社⽹址1HOT CHIPS A Symposium on High Performance Chips IEEE2SPAA ACM Symposium on Parallelism in Algorithms andArchitecturesACM3PODC ACM Symposium on Principles of Distributed Computing ACM4CGO Code Generation and Optimization IEEE/ACM 5DAC Design Automation Conference ACM6DATE Design, Automation & Test in Europe Conference IEEE/ACM 7EuroSys EuroSys ACM8HPDC High-Performance Distributed Computing IEEE9SC International Conference for High PerformanceComputing, Networking, Storage, and AnalysisIEEE10ICCD International Conference on Computer Design IEEE 11ICCAD International Conference on Computer-Aided Design IEEE/ACM12ICDCS International Conference on Distributed ComputingSystemsIEEE13HiPEAC International Conference on High Performance andEmbedded Architectures and CompilersACM14SIGMETRICS International Conference on Measurement and Modelingof Computer SystemsACM15ICPP International Conference on Parallel Processing IEEE 16ICS International Conference on Supercomputing ACM17IPDPS International Parallel & Distributed ProcessingSymposiumIEEE18FPGA ACM/SIGDA International Symposium on Field-Programmable Gate ArraysACM19Performance International Symposium on Computer Performance,Modeling, Measurements and EvaluationACM20LISA Large Installation system Administration Conference USENIX 21MSST Mass Storage Systems and Technologies IEEE 22PACT Parallel Architectures and Compilation Techniques IEEE/ACM 23PPoPP Principles and Practice of Parallel Programming ACM24RTAS Real-Time and Embedded Technology and Applications SymposiumIEEE25USENIX ATC USENIX Annul Technical Conference USENIX26VEE Virtual Execution Environments ACM三、C类序号会议简称会议全称出版社⽹址1CF ACM International Conference on Computing Frontiers ACM2NOCS ACM/IEEE International Symposium on Networks-on-Chip ACM/IEEE3ASP-DAC Asia and South Pacific Design Automation Conference ACM/IEEE4ASAP Application-Specific Systems, Architectures, and Processors IEEE5CLUSTER Cluster Computing IEEE6CCGRID Cluster Computing and the Grid IEEE7Euro-Par European Conference on Parallel and Distributed Computing Springer 8ETS European Test Symposium IEEE9FPL Field Programmable Logic and Applications IEEE 10FCCM Field-Programmable Custom Computing Machines IEEE 11GLSVLSI Great Lakes Symposium on VLSI Systems ACM/IEEE12HPCC IEEE International Conference on High Performance Computing and CommunicationsIEEE13MASCOTS IEEE International Symposium on Modeling, Analysis, andSimulation of Computer and Telecommunication SystemsIEEE14NPC IFIP International Conference on Network and Parallel Computing Springer15ICA3PP International Conference on Algorithms and Architectures for Parallel ProcessingIEEE16CASES International Conference on Compilers, Architectures, and Synthesisfor Embedded SystemsACM17FPT International Conference on Field-Programmable Technology IEEE18CODES+ISSSInternational Conference on Hardware/Software Codesign & SystemSynthesisACM/ IEEE19HiPC International Conference on High Performance Computing IEEE/ ACM 20ICPADS International Conference on Parallel and Distributed Systems IEEE 21ISCAS International Symposium on Circuits and Systems IEEE 22ISLPED International Symposium on Low Power Electronics and Design ACM/IEEE 23ISPD International Symposium on Physical Design ACM 24ITC International Test Conference IEEE25HotInterconnectsIEEE26VTS IEEE中国计算机学会推荐国际学术会议 (计算机⽹络)⼀、A类序号会议简称会议全称出版社⽹址1MOBICOM ACM International Conference on Mobile Computing and NetworkingACM2SIGCOMM ACM International Conference on the applications,technologies, architectures, and protocols for computer communicationACM3INFOCOM IEEE International Conference on ComputerCommunicationsIEEE⼆、B类序号会议简称会议全称出版社⽹址2CoNEXT ACM International Conference on emerging Networking EXperiments and TechnologiesACM3SECON IEEE Communications Society Conference on Sensor andAd Hoc Communications and NetworksIEEE4IPSN International Conference on Information Processing inSensor NetworksIEEE/ACM5ICNP International Conference on Network Protocols IEEE6MobiHoc International Symposium on Mobile Ad Hoc Networking andComputingACM/IEEE7MobiSys International Conference on Mobile Systems, Applications,and ServicesACM8IWQoS International Workshop on Quality of Service IEEE9IMC Internet Measurement Conference ACM/USENIX10NOSSDAV Network and Operating System Support for Digital Audio andVideoACM11NSDI Symposium on Network System Design and Implementation USENIX三、C类序号会议简称会议全称出版社⽹址序号会议简称会议全称出版社⽹址1ANCS Architectures for Networking and Communications Systems ACM/IEEE2FORTE Formal Techniques for Networked and Distributed Systems Springer3LCN IEEE Conference on Local Computer Networks IEEE4Globecom IEEE Global Communications Conference, incorporating theGlobal Internet SymposiumIEEE5ICC IEEE International Conference on Communications IEEE6ICCCN IEEE International Conference on ComputerCommunications and NetworksIEEE7MASS IEEE International Conference on Mobile Ad hoc andSensor SystemsIEEE8P2P IEEE International Conference on P2P Computing IEEE9IPCCC IEEE International Performance Computing andCommunications ConferenceIEEE10WoWMoM IEEE International Symposium on a World of WirelessMobile and Multimedia NetworksIEEE11ISCC IEEE Symposium on Computers and Communications IEEE 12WCNC IEEE Wireless Communications & Networking Conference IEEE 13Networking IFIP International Conferences on Networking IFIP14IM IFIP/IEEE International Symposium on Integrated Network ManagementIFIP/IEEE15MSWiM International Conference on Modeling, Analysis andSimulation of Wireless and Mobile SystemsACM16NOMS Asia-Pacific Network Operations and ManagementSymposiumIFIP/IEEE17HotNets The Workshop on Hot Topics in Networks ACM中国计算机学会推荐国际学术会议 (⽹络与信息安全)⼀、A类序号会议简称会议全称出版社⽹址1CCS ACMConferenceonComputerand CommunicationsSecurityACM2CRYPTO International Cryptology Conference Springer 3EUROCRYPT European Cryptology Conference Springer 4S&P IEEESymposiumonSecurityandPrivacy IEEE5USENIXSecurityUsenix Security SymposiumUSENIXAssociation⼆、B类序号会议简称会议全称出版社⽹址1ACSAC Annual Computer Security ApplicationsConferenceIEEE2ASIACRYPT Annual International Conference on the Theory andApplication of Cryptology and Information SecuritySpringer3ESORICS EuropeanSymposiumonResearchinComputerSecuritySpringer4FSE Fast Software Encryption Springer5NDSS ISOC Network and Distributed System SecuritySymposiumISOC6CSFW IEEE Computer Security FoundationsWorkshop 7RAID International Symposium on Recent Advancesin Intrusion DetectionSpringer8PKC International Workshop on Practice and Theory in PublicKey CryptographySpringer9DSN The International Conference on DependableSystems and NetworksIEEE/IFIP10TCC Theory of Cryptography Conference Springer11SRDS IEEE International Symposium on Reliable DistributedSystemsIEEE12CHES Springer三、C类序号会议简称会议全称出版社⽹址1WiSec ACM Conference on Security and PrivacyinWireless and Mobile NetworksACM2ACMMM&SECACM Multimedia and Security Workshop ACM3SACMAT ACM Symposium on Access Control Modelsand TechnologiesACM4ASIACCS ACM Symposium on Information, Computerand Communications SecurityACM5DRM ACM Workshop on Digital Rights Management ACM 6ACNS Applied Cryptography and Network Security Springer7ACISP AustralasiaConferenceonInformation SecurityandPrivacySpringer8DFRWS Digital Forensic Research Workshop Elsevier 9FC Financial Cryptography and Data Security Springer10DIMVA Detection of Intrusions and Malware &Vulnerability AssessmentSIDAR、GI、Springer11SEC IFIP International Information SecurityConferenceSpringer12IFIP WG11.9IFIP WG 11.9 International Conferenceon Digital ForensicsSpringer13ISC Information Security Conference Springer14SecureCommInternational Conference on Security andPrivacy in Communication NetworksACM15NSPW New Security Paradigms Workshop ACM 16CT-RSA RSA Conference, Cryptographers' Track Springer 17SOUPS Symposium On Usable Privacy and Security ACM 18HotSec USENIX Workshop on Hot Topics in Security USENIX 19SAC Selected Areas in Cryptography Springer20TrustCom IEEE International Conference on Trust, Securityand Privacy in Computing andCommunicationsIEEE中国计算机学会推荐国际学术会议 (软件⼯程、系统软件与程序设计语⾔)⼀、A类序号会议简称会议全称出版社⽹址1FSE/ESEC ACM SIGSOFT Symposium on the Foundation ofSoftware Engineering/ European Software Engineering ConferenceACM2OOPSLA Conference on Object-Oriented Programming Systems, Languages, and ApplicationsACM3ICSE International Conference on SoftwareEngineeringACM/IEEE4OSDI USENIX Symposium on Operating SystemsDesign and ImplementationsUSENIX5PLDI ACM SIGPLAN Symposium on Programming LanguageDesign & ImplementationACM6POPL ACM SIGPLAN-SIGACT Symposium on Principles of Programming LanguagesACM7SOSP ACM Symposium on Operating Systems Principles ACM⼆、B类序号会议简称会议全称出版社⽹址1ECOOP European Conference on Object-Oriented Programming AITO2ETAPS European Joint Conferences on Theory and Practice ofSoftwareSpringer3FM Formal Methods, World Congress FME IEEE International Conference on Program4ICPC IEEE International Conference on ProgramComprehensionIEEE5RE IEEE International Requirement Engineering Conference IEEE6CAiSE International Conference on Advanced InformationSystems EngineeringSpringer7ASE International Conference on Automated SoftwareEngineeringIEEE/ACM8ICFP International Conf on Function Programming ACM9LCTES International Conference on Languages, Compilers, Toolsand Theory for Embedded SystemsACM10MoDELS International Conference on Model Driven Engineering Languages and SystemsACM, IEEE11CP International Conference on Principles and Practice ofConstraint ProgrammingSpringer12ICSOC International Conference on Service Oriented Computing Springer 13ICSM International. Conference on Software Maintenance IEEE14VMCAI International Conference on Verification,Model Checking, and Abstract InterpretationSpringer15ICWS International Conference on Web Services(Research Track)IEEE16SAS International Static Analysis Symposium Springer17ISSRE International Symposium on Software ReliabilityEngineeringIEEE18ISSTA International Symposium on Software Testing andAnalysisACMSIGSOFT19Middleware Conference on middleware ACM/IFIP/ USENIX20WCRE Working Conference on Reverse Engineering IEEE21HotOS USENIX Workshop on Hot Topics in Operating Systems USENIX三、C类序号会议简称会议全称出版社⽹址1PASTE ACMSIGPLAN-SIGSOFTWorkshoponProgram AnalysisforSoftwareToolsandEngineeringACM2APLAS Asian Symposium on Programming Languages and Systems Springer3APSEC Asia-Pacific Software EngineeringConferenceIEEE4COMPSAC International Computer Software and ApplicationsConferenceIEEE5ICECCS IEEE International Conference on Engineeringof Complex Computer SystemsIEEE6SCAM IEEE International Working Conferenceon Source Code Analysis and ManipulationIEEE7ICFEM International Conference on FormalEngineering MethodsSpringer8TOOLS International Conference on Objects, Models,Components, PatternsSpringer9PEPM ACM SIGPLAN Symposium on Partial Evaluation andSemantics Based Programming ManipulationACM10QSIC International Conference on Quality Software IEEE11SEKE International Conference on Software Engineering and Knowledge EngineeringKSI12ICSR International Conference on Software Reuse Springer 13ICWE International Conference on Web Engineering Springer14SPIN International SPIN Workshop on ModelChecking of SoftwareSpringer15LOPSTR International Symposium on Logic-basedProgram Synthesis and TransformationSpringer16TASE International Symposium on Theoretical Aspects of Software EngineeringIEEE17ICST The IEEE International Conference on Software Testing, Verification and ValidationIEEE18ATVA International Symposium on Automated Technology for Verification and AnalysisVerification and Analysis19ESEM International Symposium on Empirical Software Engineeringand MeasurementACM/IEEE20ISPASSSystems and SoftwareIEEE21SCC International Conference on Service Computing IEEE22ICSSP International Conference on Software and System Process ISPA中国计算机学会推荐国际学术会议 (数据库,数据挖掘与内容检索)⼀、A类序号会议简称会议全称出版社⽹址1SIGMOD ACM Conference on Management ofDataACM2SIGKDD ACM Knowledge Discovery and DataMiningACM3SIGIR International Conference on ResearchanDevelopment in Information RetrievalACM4VLDB International Conference on Very LargeData BasesMorganKaufmann/ACM5ICDE IEEE International Conference on Data EngineeringIEEE⼆、B类序号会议简称会议全称出版社⽹址1CIKM ACM International Conference onInformationand Knowledge ManagementACM2PODS ACM SIGMOD Conference on Principlesof DB SystemsACM3DASFAA Database Systems for AdvancedApplicationsSpringer4ECML-PKDDEuropean Conference on Principles andPractice of Knowledge Discovery inDatabasesSpringer5ISWC IEEE International Semantic WebConferenceIEEE6ICDM IEEE International Conference on DataMiningIEEE7ICDT International Conference on DatabaseTheorySpringer8EDBT International Conference on ExtendingDBTechnologySpringer9CIDR International Conference on InnovationDatabase ResearchOnlineProceeding10WWW International World Wide WebConferencesSpringer11SDM SIAM International Conference on DataMiningSIAM三、C类序号会议简称会议全称出版社⽹址1WSDM ACM International Conference on Web Search and Data MiningACM2DEXA Database and Expert SystemApplicationsSpringer3ECIR European Conference on IR Research Springer4WebDB International ACM Workshop on Weband DatabasesACM5ER International Conference on Conceptual ModelingSpringerModeling6MDM International Conference on Mobile Data ManagementIEEE7SSDBM International Conference on Scientificand Statistical DB ManagementIEEE8WAIM International Conference on Web Age Information ManagementSpringer9SSTD International Symposium on Spatial and Temporal DatabasesSpringer10PAKDD Pacific-Asia Conference on Knowledge Discovery and Data MiningSpringer11APWeb The Asia Pacific Web Conference Springer12WISE Web Information Systems Engineering Springer13ESWC Extended Semantic Web Conference Elsevier中国计算机学会推荐国际学术会议(计算机科学理论)⼀、A类序号会议简称会议全称出版社⽹址1STOC ACM Symposium on Theory of Computing ACM2FOCS IEEE Symposium on Foundations ofComputer ScienceIEEE3LICS IEEE Symposium on Logic in ComputerScienceIEEE⼆、B类序号会议简称会议全称出版社⽹址1SoCG ACM Symposium on ComputationalGeometryACM2SODA ACM-SIAM Symposium on DiscreteAlgorithmsSIAM3CAV Computer Aided Verification Springer4CADE/IJCAR Conference on Automated Deduction/The International Joint Conference onAutomated ReasoningSpringer5CCC IEEE Conference on Computational Complexity IEEE6ICALP International Colloquium on Automata,Languages and ProgrammingSpringer7CONCUR International Conference onConcurrency TheorySpringer三、C类序号会议简称会议全称出版社⽹址1CSL Computer Science Logic Springer2ESA European Symposium on Algorithms Springer3FSTTCS Foundations of Software Technologyand Theoretical Computer ScienceIndianAssociationfor Researchin ComputingScience4IPCO International Conference on Integer Programming and CombinatorialOptimizationSpringer5RTA International Conference on Rewriting Techniques and ApplicationsSpringer6ISAAC International Symposium onAlgorithms and ComputationSpringer7MFCS Mathematical Foundations ofComputer ScienceSpringer8STACS Symposium on Theoretical Aspectsof Computer ScienceSpringer9FMCAD Formal Method in Computer-Aided Design ACM 10SAT Theory and Applications of Springer10SAT Theory and Applications ofSatisfiability TestingSpringer中国计算机学会推荐国际学术会议(计算机图形学与多媒体)⼀、A类序号会议简称会议全称出版社⽹址1ACM MM ACM International Conference on Multimedia ACM2SIGGRAPH ACM SIGGRAPH Annual Conference ACM3IEEE VIS IEEE Visualization Conference IEEE⼆、B类序号会议简称会议全称出版社⽹址1ICMR ACM SIGMM International Conference on MultimediaRetrievalACM2i3D ACM Symposium on Interactive 3D Graphics ACM 3SCA ACM/Eurographics Symposium on Computer Animation ACM 4DCC Data Compression Conference IEEE5EG EurographicsWiley/ Blackwell6EuroVis Eurographics Conference on Visualization ACM7SGP Eurographics Symposium on Geometry ProcessingWiley/ Blackwell8EGSR Eurographics Symposium on RenderingWiley/ Blackwell9ICME IEEE International Conference onMultimedia &ExpoIEEE10PG Pacific Graphics: The Pacific Conference on ComputerGraphics and ApplicationsWiley/Blackwell11SPM Symposium on Solid and Physical Modeling SMA/Elsevier三、C类序号会议简称会议全称出版社⽹址1CASA Computer Animation and Social Agents Wiley2CGI Computer Graphics International Springer3ISMAR International Symposium on Mixed and AugmentedRealityIEEE/ACM4PacificVis IEEE Pacific Visualization Symposium IEEE5ICASSP IEEE International Conference on Acoustics, Speechand SPIEEE6ICIP International Conference on Image Processing IEEE7MMM International Conference on Multimedia Modeling Springer8GMP Geometric Modeling and Processing Elsevier9PCM Pacific-Rim Conference on Multimedia Springer10SMI Shape Modeling International IEEE中国计算机学会推荐国际学术会议(⼈⼯智能与模式识别)⼀、A类序号会议简称会议全称出版社⽹址1AAAI AAAI Conference on Artificial Intelligence AAAI2CVPR IEEE Conference on Computer Vision andPattern RecognitionIEEE3ICCV International Conference on ComputerVisionIEEE4ICML International Conference on MachineLearningACM5IJCAI International Joint Conference on Artificial Morgan Kaufmann5IJCAI⼆、B类序号会议简称会议全称出版社⽹址1COLT Annual Conference on ComputationalLearning TheorySpringer2NIPS Annual Conference on Neural InformationProcessing SystemsMIT Press3ACL Annual Meeting of the Association for Computational LinguisticsACL4EMNLP Conference on Empirical Methods in Natural Language ProcessingACL5ECAI European Conference on ArtificialIntelligence IOS Press6ECCV European Conference on Computer Vision Springer7ICRA IEEE International Conference on Roboticsand AutomationIEEE8ICAPS International Conference on AutomatedPlanning and SchedulingAAAI9ICCBR International Conference on Case-BasedReasoningSpringer10COLING International Conference on Computational LinguisticsACM11KR International Conference on Principles ofKnowledge Representation and ReasoningMorgan Kaufmann12UAI International Conference on Uncertaintyin Artificial IntelligenceAUAI13AAMAS International Joint Conferenceon Autonomous Agents and Multi-agentSystemsSpringer三、C类序号会议简称会议全称出版社⽹址1ACCV Asian Conference on Computer Vision Springer2CoNLL Conference on Natural Language Learning CoNLL3GECCO Genetic and Evolutionary ComputationConferenceACM4ICTAI IEEE International Conference on Tools with Artificial IntelligenceIEEE5ALT International Conference on AlgorithmicLearning TheorySpringer6ICANN International Conference on Artificial Neural NetworksSpringer7FGR International Conference on Automatic Faceand Gesture RecognitionIEEE8ICDAR International Conference on DocumentAnalysis and RecognitionIEEE9ILP International Conference on Inductive Logic ProgrammingSpringer10KSEM International conference on KnowledgeScience,Engineering and ManagementSpringer11ICONIP International Conference on NeuralInformation ProcessingSpringer12ICPR International Conference on PatternRecognitionIEEE13ICB International Joint Conference on Biometrics IEEE14IJCNN International Joint Conference on NeuralNetworksIEEE15PRICAI Pacific Rim International Conference onArtificial IntelligenceSpringer16NAACL The Annual Conference of the NorthAmerican Chapter of the Associationfor Computational LinguisticsNAACL17BMVC British Machine Vision Conference VisionAssociation中国计算机学会推荐国际学术会议(⼈机交互与普适计算)⼀、A类序号会议简称会议全称出版社⽹址1CHI ACM Conference on Human Factors in ComputingSystemsACM2UbiComp ACM International Conference on Ubiquitous Computing ACM⼆、B类序号会议简称会议全称出版社⽹址1CSCW ACM Conference on Computer Supported CooperativeWork and Social ComputingACM2IUI ACM International Conference on Intelligent UserInterfacesACM3ITS ACM International Conference on Interactive Tabletopsand SurfacesACM4UIST ACM Symposium on User Interface Software andTechnologyACM5ECSCW European Computer Supported Cooperative Work Springer6MobileHCI International Conference on Human Computer Interactionwith Mobile Devices and ServicesACM三、C类序号会议简称会议全称出版社⽹址1GROUP ACM Conference on Supporting Group Work ACM2ASSETS ACM Conference on Supporting Group Work ACM3DIS ACM Conference on Designing InteractiveSystemsACM4GI Graphics Interface conference ACM5MobiQuitous International Conference on Mobile and Ubiquitous Systems:Computing, Networking and ServicesSpringer6PERCOM IEEE International Conference onPervasive Computing and CommunicationsIEEE7INTERACT IFIP TC13 Conference on Human-ComputerInteractionIFIP8CoopIS International Conference on Cooperative Information Systems Springer9ICMI ACM International Conference on MultimodalInteractionACM10IDC Interaction Design and Children ACM 11AVI International Working Conference on Advanced User Interfaces ACM12UIC IEEE International Conference on UbiquitousIntelligence and ComputingIEEE中国计算机学会推荐国际学术会议(前沿、交叉与综合)⼀、A类序号会议简称会议全称出版社⽹址1RTSS Real-Time Systems Symposium IEEE⼆、B类序号会议简称会议全称出版社⽹址1EMSOFT International Conference on Embedded Software ACM/IEEE/IFIP2ISMB International conference on Intelligent Systems forMolecular BiologyOxford Journals3CogSci Cognitive Science Society Annual Conference Psychology Press4RECOMB International Conference on Research inSpringer4RECOMB International Conference on Research inComputational Molecular BiologySpringer5BIBM IEEE International Conference on Bioinformaticsand Biomedicine IEEE三、C类序号会议简称会议全称出版社⽹址1AMIA American Medical Informatics Association Annual SymposiumAMIA2APBC Asia Pacific Bioinformatics Conference BioMed Central3COSIT International Conference on Spatial InformationTheoryACM。
Autodesk Fabrication CAMduct 2013 Service Pack 4 E

Autodesk®Fabrication CAMduct™ 2013Service Pack 4 Enhancement ListImprovements made in Service Pack 4 build 3.01.193:∙All SP1, SP2 and SP3 enhancements incorporated (see below)∙Improved file compatibility for Farley.exe.∙Enhanced pierced holes visibility in takeoff developments.∙Improved coil line processor option text installation.∙Enhanced NC Part Request by Type columns.∙Improved stability of pattern CID 850.∙Enhancements made to various post processors.∙Improved scripting functionality to allow users to return values from catalogued item options.∙Stability improvement made to ancillary database components to allow the assignment of lone fabrication tables.Improvements made in Service Pack 3 build 3.01.154:∙All SP1 and SP2 enhancements incorporated (see below)∙Enhanced Scripting to support “Group” prefix when changing Item Specification or Material∙Improved import functionality when specifications contain alternate connectors and seams.∙Enhanced status time/dates to report out in local time rather than UTC format.∙More consistently apply collar seams from the specification to various round pattern developments.∙Enhanced ancillary database display to support sorting.∙Update position of Splitter holes in developments of Radius Elbow and Breeches piece.∙Enhanced hole development positions and notching when using connectors with –ve Turnover.∙Enhanced Mach3 post processor for plate detection support in Z axis for varying heights for pierce and cut.∙Enhanced Mitsubishi post processor for etching text.∙Enhanced Salvagnini post processor to control head movement when traversing and support laser marking.∙Enhanced CRE post processer for central cuts with 0 offset (rip cut) and view NC control.∙Enhanced Micro Step post process with support for Micro Punch tooling.∙Enhanced Fanuc Plasma post processor with height control.∙Enhanced AMS coil line post with tie rod holes and collate 4 piece and U+ straights.∙Improved support for displaying material and gauge properties in manual nest.∙Enhanced NFP nesting to better support nesting in holes and auto quantity parts.∙Updated oversize dialogue to redisplay the “show” control when hidden.∙Enhanced quick takeoff with attacher arrow control.∙Improved support for 3D viewer printing worksheets.Improvements made in Service Pack 2 build 3.01.094:∙All SP1 enhancements incorporated (see below).∙Attacher Arrow and associated functionality enhanced in 3D Viewer.∙Improved stability using Slice tool in Opus/Profiler.∙Enhanced stability of Write NC.∙Improved support in Amada post processor to prevent short arcs being output as full circles.∙Enhanced Burny10 post processor to support alternate tool On/Off commands M21/M20.∙Updated Cyberstep post processor to support Torch Height Control (THC).∙Improved support in Vicon decoiler post processor when outputting Metric values on an Imperial setup.∙Enhanced Digisaf 620 post processor to support multiple tools (Oxy fuel, Plasma cut and mark).∙Improve support for machines with more than one tool and using more than one setup rule. i.e. Hypertherm Voyager.∙Enhanced support for kerf compensation when used with DuctBoard patterns, i.e. keft left and kerf right supported.∙Enhanced CID 33 for processing multiple branches when one of the diameters is set to 0.∙Enhanced CID 7 to support the appropriate connector fold notches for C1 and C2 ends.∙Improved support for Double Walled items for sizing Insulation panels.Improvements made in Service Pack 1 build 3.01.057:∙Barcode settings, when changed in the main database, are maintained between sessions∙Opus now loads Raster to Vector DLL on 64 bit systems∙Enhanced stability of Opus DXF import∙Catalogue items are no longer created when enhanced editing a template ITM though Folders and selecting develop.∙Windows permissions validation now occurs when Writing NC.∙MAP2ADSK addresses various incidents with regard to migrating from older systems.∙Enable Item Spool, eTag, Zone and Alt fields on item and as print objects.∙Enhance Grooving/Marking options for panels when angle is less user defined angle, switches to marking tool.∙Print object Item Duct Weight adjusted for units used.∙Splitter entries in dialogue editor synced with regard to specification entries∙Plasma Straight, marker notches included from the developments.∙Oval Collars now resolve holes moving to accommodate notch positions.∙Square Elbow – Option provided for Seam Number for Throat supports more effective application of seams.∙Multi Branch on Reducer now allows multiple length splits along the body.∙Branch on Reducer: The option to change seam position on the body, is now in the development.∙Developments adjusted for seam lengths on Elliptical Reducers∙Extension allowances on Straights when working with Square Elbows and Square Tees have been improved.∙Enhanced stability for Setup Processes, Export Data and Select Exports button.∙Enhanced browsing through reports in Item Report BuilderAutodesk, CADmep, CAMduct, and ESTmep are registered trademarks or trademarks of Autodesk, Inc., and/or its subsidiaries and/or affiliates in the USA and/or other coun-tries. All other brand names, product names, or trademarks belong to their respective holders. Autodesk reserves the right to alter product and services offerings, and specifications and pricing at any time without notice, and is not responsible for typographical or graphical errors that may appear in this document. © 2013 Autodesk, Inc. All rights reserved.。
stacomirtools 0.6.0.1 软件说明说明书

Package‘stacomirtools’October14,2022Version0.6.0.1Date2022-04-28Title Connection Class for Package stacomiRAuthor Cedric Briand[aut,cre],Marion Legrand[aut],Beaulaton Laurent[ctb]Maintainer Cedric Briand<*************************>Description S4class wrappers for the'ODBC'and Pool DBI connection,also provides some utilities to paste small datasets to clipboard,rename columns.It is used by the package'sta-comiR'forconnections to the database.Development versions of'stacomiR'are available in R-forge. License GPL(>=2)Collate'ConnectionODBC.R''RequeteODBC.R''RequeteODBCwhere.R''RequeteODBCwheredate.R''utilities.R''stacomirtools.R''stacomirtools-package.R''ConnectionDB.R''RequeteDB.R''RequeteDBwhere.R''RequeteDBwheredate.R''zzz.R'LazyLoad yesDepends RODBC,DBI,poolImports methods,xtable,utils,RPostgresSuggests testthat,withrNeedsCompilation noRoxygenNote7.1.2Repository CRANDate/Publication2022-04-2911:40:02UTCR topics documented:chnames (2)connect (3)connect,ConnectionDB-method (4)connect,ConnectionODBC-method (5)12chnames connect,RequeteODBC-method (5)connect,RequeteODBCwhere-method (7)connect,RequeteODBCwheredate-method (8)ConnectionDB-class (9)ConnectionODBC-class (10)ex (11)funhtml (11)getquery (12)getquery,RequeteDB-method (13)induk (13)is.even (14)is.odd (15)killfactor (15)query (16)query,RequeteDB-method (16)query,RequeteDBwhere-method (17)query,RequeteDBwheredate-method (18)RequeteDB-class (19)RequeteDBwhere-class (20)RequeteDBwheredate-class (21)RequeteODBC-class (21)RequeteODBCwhere-class (22)RequeteODBCwheredate-class (22)tab2df (23)validity_DB (23)validity_ODBC (24)Index25 chnames This function replaces the variable names in a data.frameDescriptionThis function replaces the variable names in a data.frameUsagechnames(object,old_variable_name,new_variable_name)Argumentsobject a data frameold_variable_namea character vector with old variables namesnew_variable_namea character vector with new variables namesconnect3 ValueobjectAuthor(s)Cedric Briand<*****************************>Examplesdf<-data.frame("var1"=c("blue","red"),"var2"=c("nice","ugly"))colnames(df)#"var1""var2"df<-chnames(object=df,old_variable_name=c("var1","var2"),"new_variable_name"=c("color","beauty"))colnames(df)#"color""beauty"#the following will return an error,as the variable wrong_name is not in variable names ##Not run:chnames(object=df,old_variable_name=c("wrong_name"),"new_variable_name"=c("color")))##End(Not run)connect generic connect function for baseODBCDescriptiongeneric connect function for baseODBCUsageconnect(object,...)Argumentsobject an object...additional arguments passed on to the connect methodconnect,ConnectionDB-methodconnect method for ConnectionDB classDescriptionconnect method for ConnectionDB classUsage##S4method for signature ConnectionDBconnect(object,base=NULL)Argumentsobject An object of class ConnectionDBbase a string with values for dbname,host,port,user,password,in this order. Valuea connection with slotfilledAuthor(s)Cedric Briand<*****************************>Examples##Not run:object<-new("ConnectionDB")object@dbname<-c("bd_contmig_nat","test")object@host<-"localhost"object@port<-"5432"object@user<-"myuser"object@password<-"mypassword"object@silent=FALSEobject<-connect(object)pool::dbGetInfo(object@connection)pool::poolClose(object@connection)##End(Not run)connect,ConnectionODBC-methodconnect method for ConnectionODBC classDescriptionconnect method for ConnectionODBC classUsage##S4method for signature ConnectionODBCconnect(object)Argumentsobject an object of class ConnectionODBCValuea connection with slotfilledAuthor(s)Cedric Briand<*****************************>Examples##this wont be run as the user need to manually configure the connection before using it ##Not run:object=new("ConnectionODBC")object@baseODBC=c("myODBCconnection","myusername","mypassword")object@silent=FALSEobject<-connect(object)odbcClose(object@connection)##End(Not run)connect,RequeteODBC-methodconnect method loads a request to the database and returns either anerror or a data.frameDescriptionconnect method loads a request to the database and returns either an error or a data.frameUsage##S4method for signature RequeteODBCconnect(object)Argumentsobject an object of class RequeteODBCValueAn object of class RequeteODBCNoteassign("showmerequest",1,envir=envir_stacomi)allows to print all queries passing on the class Re-queteDBAuthor(s)Cedric Briand<*****************************>ExamplesshowClass("RequeteODBC")##Not run:object=new("RequeteODBC")object@open=TRUEobject@baseODBC=baseODBCobject@sql="select*from t_lot_lot limit100"object<-connect(object)odbcClose(object@connection)odbcCloseAll()object=new("RequeteODBC")object@open=TRUE##this will leave the connection open,##by default it closes after the query is sent##the following will work only if you have configured and ODBC linkobject@baseODBC=c("myODBCconnection","myusername","mypassword")object@sql="select*from mytable limit100"object<-connect(object)odbcClose(object@connection)envir_stacomi=new.env()##While testing if you want to see the output of sometimes##complex queries generated by the programassign("showmerequest",1,envir_stacomi)##You can assign any values(here1)##just tests the existence of"showmerequest"in envir_stacomiobject=new("RequeteODBC")object@baseODBC=c("myODBCconnection","myusername","mypassword")object@sql="select*from mytable limit100"object<-connect(object)##the connection is already closed,the query is printed##End(Not run)connect,RequeteODBCwhere-methodconnect method loads a request to the database and returns either anerror or a data.frameDescriptionconnect method loads a request to the database and returns either an error or a data.frameUsage##S4method for signature RequeteODBCwhereconnect(object)Argumentsobject an object of class RequeteODBCwhereValueAn object of class RequeteODBCwhereNotemethod modified from v0.2.1240to use the connect method of the mother classAuthor(s)Cedric Briand<*****************************>Examples##Not run:object<-new("RequeteODBCwhere")object@baseODBC<-baseODBCobject@sql<-"select*from t_lot_lot"object@where<-"WHERE lot_tax_code= 2038 "object@and<-c("AND lot_std_code= CIV ","AND lot_ope_identifiant<1000")object@order_by<-"ORDER BY lot_identifiant"object<-connect(object)##End(Not run)connect,RequeteODBCwheredate-methodconnect method loads a request to the database and returns either anerror or a data.frameDescriptionconnect method loads a request to the database and returns either an error or a data.frameUsage##S4method for signature RequeteODBCwheredateconnect(object)Argumentsobject an object of class RequeteODBCwheredateValueAn object of class RequeteODBCwheredateNotemethod modified from v0.2.1240to use the connect method of the mother class which in turn will use the method of the mother classAuthor(s)Cedric Briand<*****************************>Examples##Not run:object<-new("RequeteODBCwheredate")object@baseODBC<-get("baseODBC",envir=envir_stacomi)object@select<-"select*from t_operation_ope"object@datedebut=strptime("1996-01-0100:00:00",format="%Y-%m-%d%H:%M:%S")object@datefin=strptime("2000-01-0100:00:00",format="%Y-%m-%d%H:%M:%S")object@colonnedebut="ope_date_debut"object@colonnefin="ope_date_fin"object@and<-c("AND ope_dic_identifiant=1","AND ope_dic_identifiant=2")object@order_by<-"ORDER BY ope_identifiant"object@silent=FALSEobject<-connect(object)##End(Not run)ConnectionDB-class ConnectionDB classDescriptionConnectionDB classValueconnection an S4object of class connectionDBSlotsdbname name of the database,length1host host default"localhost",length1port port of the database default"5432",length1user user of the database,length1password password for the datatbase,length1silent A"logical"stating if the program returns output to the userstatus Can be-1or stringconnection Could be both string or S3NoteMother class for connection,opens the connection but does not shut itAuthor(s)Cedric Briand<*****************************>Examples##this wont be run as the user need to manually configure the connection before using it ##Not run:object<-new("ConnectionDB")object@dbname<-c("bd_contmig_nat","test")object@host<-"localhost"object@port<-"5432"object@user<-"myuser"object@password<-"mypassword"object@silent=FALSEobject<-connect(object)pool::dbGetInfo(object@connection)pool::poolClose(object@connection)##End(Not run)ConnectionODBC-class ConnectionODBC classDescriptionConnectionODBC classValueconnectionODBC an S4object of class connectionODBCSlotsbaseODBC"vector"(of length3,character)silent"logical"etat"ANY"#can be-1or stringconnection"ANY"#could be both string or S3NoteMother class for connection,opens the connection but does not shut itAuthor(s)Cedric Briand<*****************************>Examples##this wont be run as the user need to manually configure the connection before using it ##Not run:object=new("ConnectionODBC")object@baseODBC=c("myODBCconnection","myusername","mypassword")object@silent=FALSEobject<-connect(object)odbcClose(object@connection)##End(Not run)ex11 ex ex fonction to write to the clipboardDescriptionex fonction to write to the clipboardUsageex(d=NULL)Argumentsd a dataframeAuthor(s)Cedric Briand<*****************************>funhtml function used to print the html tables of output(see xtable documenta-tion)Descriptionsee xtable for further description,an xtable is created and printed to html formatUsagefunhtml(data,caption=NULL,top=TRUE,outfile=NULL,clipboard=FALSE,append=TRUE,digits=NULL,...)12getquery Argumentsdata a data framecaption the captiontop a logical,if true the caption is placed on topoutfile the path to thefileclipboard if clipboard TRUE,a copy to the clipboard is madeappend is thefile appended to the previous one?digits the number of digits...additional parameters to be passed to the functionValuean xtableAuthor(s)Cedric Briand<*****************************>getquery generic query function forDescriptiongeneric query function forUsagegetquery(object,...)Argumentsobject an object...additional parameters passed to querygetquery,RequeteDB-method13 getquery,RequeteDB-methodgetquery retreives the result of the query from the objectDescriptiongetquery retreives the result of the query from the objectUsage##S4method for signature RequeteDBgetquery(object)Argumentsobject an object of class RequeteDBValueA data frameinduk unique values of a vectorDescriptionreturns the index of values appearing only once in a vector:match(unique(a),a),replicated values are not returned on their second occurenceUsageinduk(a)Argumentsa a vectorValuethe index unique values within a vectorAuthor(s)Cedric Briand<*****************************>14is.even Examplesinduk(c(1,1,2,2,2,3))is.even is.even function modified from package smaDescriptionis.even function modified from package sma(which did not verify that the entry was indeed an integer)Usageis.even(x)Argumentsx integerValuea logicalAuthor(s)Adapted from Henrik BengtssonExamplesis.even(1)is.even(2)is.odd15 is.odd id.odd function modified from package smaDescriptionid.odd function modified from package sma(which did not verify that the entry was indeed an integer)Usageis.odd(x)Argumentsx integerValuea logicalAuthor(s)Adapted from Henrik BengtssonExamplesis.odd(1)is.odd(2)killfactor very usefull function used to"kill"the factors,noticeably after loadingwith’ODBC’Descriptionvery usefull function used to"kill"the factors,noticeably after loading with’ODBC’Usagekillfactor(df)Argumentsdf a data.frameValuedfAuthor(s)Cedric Briand<*****************************>query generic query function forDescriptiongeneric query function forUsagequery(object,...)Argumentsobject an object...additional parameters passed to queryquery,RequeteDB-methodquery method loads a quert to the data and returns either an error ora data.frameDescriptionquery method loads a quert to the data and returns either an error or a data.frameUsage##S4method for signature RequeteDBquery(object,...)Argumentsobject an object of class RequeteDB...further arguments passed to the query method,base will be passed to Connec-tionDB to set the connection parameters,it should be a vector with dbname hostport user and password(in this order)ValueAn object of class RequeteDBNoteassign("showmerequest",1,envir=envir_stacomi)allows to print all queries passing on the class Re-queteDBAuthor(s)Cedric Briand<*****************************>ExamplesshowClass("RequeteDB")##Not run:#this connection require user and password and a working dataobject=new("RequeteDB",dbname="bd_contmig_nat",host="localhost",port="5432",user="postgres",password="secret"))object@open=TRUE##this will leave the connection open,##by default it closes after the query is sent##the following will work only if you have configured and ODBC linkobject@sql="select*from t_lot_lot limit100"object<-query(object)envir_stacomi=new.env()##While testing if you want to see the output of sometimes##complex queries generated by the programassign("showmerequest",1,envir_stacomi)##You can assign any values(here1)##just tests the existence of"showmerequest"in envir_stacomiobject@sql="select*from mytable limit100"object<-connect(object)##the connection is already closed,the query is printed##End(Not run)query,RequeteDBwhere-methodquery method loads a request to the database and returns either anerror or a data.frameDescriptionquery method loads a request to the database and returns either an error or a data.frameUsage##S4method for signature RequeteDBwherequery(object,...)Argumentsobject an object of class RequeteDBwhere...further arguments passed to the query method,base will be passed to Connec-tionDB to set the connection parameters,ValueAn object of class RequeteODBCwhereAuthor(s)Cedric Briand<*****************************>Examples##Not run:object<-new("RequeteODBCwhere")base=c("bd_contmig_nat","localhost","5432","user","password")object@sql<-"select*from t_lot_lot"object@where<-"WHERE lot_tax_code= 2038 "object@and<-c("AND lot_std_code= CIV ","AND lot_ope_identifiant<1000")object@order_by<-"ORDER BY lot_identifiant"object<-connect(object,base)##End(Not run)query,RequeteDBwheredate-methodquery method loads a request to the database and returns either anerror or a data.frameDescriptionquery method loads a request to the database and returns either an error or a data.frameUsage##S4method for signature RequeteDBwheredatequery(object,...)Argumentsobject an object of class RequeteDBwheredate...further arguments passed to the query method,base will be passed to Connec-tionDB to set the connection parameters,ValueAn object of class RequeteDBwheredateAuthor(s)Cedric Briand<*****************************>Examples##Not run:object<-new("RequeteDBwheredate")base=c("bd_contmig_nat","localhost","5432","user","password")object@select<-"select*from t_operation_ope"object@datedebut=strptime("1996-01-0100:00:00",format="%Y-%m-%d%H:%M:%S")object@datefin=strptime("2000-01-0100:00:00",format="%Y-%m-%d%H:%M:%S")object@colonnedebut="ope_date_debut"object@colonnefin="ope_date_fin"object@and<-c("AND ope_dic_identifiant=1","AND ope_dic_identifiant=2")object@order_by<-"ORDER BY ope_identifiant"object@silent=FALSEobject<-connect(object,base)##End(Not run)RequeteDB-class RequeteDB classDescriptionRequeteDB classSlotssql"character"query"data.frame"open logical is the connection left open after the request?NoteInherits from ConnectionDBAuthor(s)Cedric Briand<*****************************>Examplesobject=new("RequeteDB")RequeteDBwhere-class RequeteDBwhere classDescriptionRequeteDBwhere classSlotsselect"character"where"character"and"vector"order_by"character"NoteInherits from RequeteDB the syntax is where="WHERE..."and=vector("AND...","AND...")or-der_by="ORDER BY.."Author(s)Cedric Briand<*****************************>Examplesobject=new("RequeteDBwhere")RequeteDBwheredate-classRequeteDBwhere classDescriptionRequeteDBwhere classSlotsdatedebut"POSIXlt"datefin"POSIXlt"colonnedebut"character"#name of the column containing datedebutcolonnefin"character"#name of the column containing datefinNoteInherits from RequeteDBwhere and uses its connect method with a new SetAsExamplesobject=new("RequeteDBwhere")RequeteODBC-class RequeteODBC classDescriptionRequeteODBC classSlotssql"character"query"data.frame"open logical is the connection left open after the request?NoteInherits from ConnectionODBCAuthor(s)Cedric Briand<*****************************>Examplesobject=new("RequeteODBC")RequeteODBCwhere-classRequeteODBCwhere classDescriptionRequeteODBCwhere classSlotsselect"character"where"character"and"vector"order_by"character"NoteInherits from RequeteODBC the syntax is where="WHERE..."and=vector("AND...","AND...") order_by="ORDER BY.."Author(s)Cedric Briand<*****************************>Examplesobject=new("RequeteODBCwhere")RequeteODBCwheredate-classRequeteODBCwhere classDescriptionRequeteODBCwhere classSlotsdatedebut"POSIXlt"datefin"POSIXlt"colonnedebut"character"#name of the column containing datedebutcolonnefin"character"#name of the column containing datefintab2df23NoteInherits from RequeteODBCwhere and uses its connect method with a new SetAsExamplesobject=new("RequeteODBCwhere")tab2df Function to transform a ftable into dataframe but just keeping thecounts,works with ftable of dim2DescriptionFunction to transform a ftable into dataframe but just keeping the counts works with ftable of dim2 Usagetab2df(tab)Argumentstab aflat tableAuthor(s)Cedric Briand<*****************************>Examplesdf<-data.frame("var1"=c("blue","red"),"var2"=c("nice","ugly"))ftdf<-ftable(df)tab2df(ftdf)validity_DB validity function for ConnectionDB classDescriptionvalidity function for ConnectionDB classUsagevalidity_DB(object)Argumentsobject An object of class ConnectionDB24validity_ODBC validity_ODBC Validity method for ODBC classDescriptionValidity method for ODBC classUsagevalidity_ODBC(object)Argumentsobject an object of class ConnectionODBCIndexchnames ,2connect ,3connect,ConnectionDB-method ,4connect,ConnectionODBC-method ,5connect,RequeteODBC-method ,5connect,RequeteODBCwhere-method ,7connect,RequeteODBCwheredate-method ,8connect.ConnectionDB (connect,ConnectionDB-method ),4connect.ConnectionODBC (connect,ConnectionODBC-method ),5connect.RequeteODBC (connect,RequeteODBC-method ),5connect.RequeteODBCwhere (connect,RequeteODBCwhere-method ),7connect.RequeteODBCwheredate (connect,RequeteODBCwheredate-method ),8ConnectionDB-class ,9ConnectionODBC-class ,10ex ,11funhtml ,11getquery ,12getquery,RequeteDB-method ,13induk ,13is.even ,14is.odd ,15killfactor ,15query ,16query,RequeteDB-method ,16query,RequeteDBwhere-method ,17query,RequeteDBwheredate-method ,18query.RequeteDBwheredate (query,RequeteDBwheredate-method ),18query.RequeteODBCwhere (query,RequeteDBwhere-method ),17RequeteDB-class ,19RequeteDBwhere-class ,20RequeteDBwheredate-class ,21RequeteODBC-class ,21RequeteODBCwhere-class ,22RequeteODBCwheredate-class ,22tab2df ,23validity_DB ,23validity_ODBC ,2425。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
科学
** PPTPeperiksaan Pertengahan Tahun年中考试
PercubaanPeperiksaan Percubaan UPSR
19-09-2013
班级
时间
科目
上午班
*1B
8:10am – 9:10am
( 60 min )
Bahasa Malaysia
国语
Bahasa Inggeris
英语
Bahasa Cina
华语
下午班
1, 2, 3年级
2:00pm – 3:00pm
( 60 min )
上午班
*1B
8:10am – 9:10am
( 60 min )
Matematik
数学
Dunia Sains & Teknologi
科艺
Pendidikan Moral
道德教育
下午班
1, 2, 3年级
4:00pm – 5:00pm
( 60 min )
JADUAL PBS 2013 – Tahun 4 Dan Tahun 5
2013年度四年级和五年级评审时间表
SJKC JELUTONG日落洞华小
JADUAL PBS 2013-Tahun 6
2013年度六年级评审时间表
Hari
Pertama
Kedua
Ketiga
Ujian
&
Tarikh
Ujian 1月考(一)
11-03-2013
12-03-2013
13-03-2013
*PPT年中考试
13-05-2013
14-05-2013
数学试卷(二)
Kedua
7:40am – 7:50am
Arahan Pengawas tentang perjalanan Ujian
7:50am – 8:50am ( 60 min )
Matematik – Kertas 1 (025/1)
数学试卷(一)
9:10am – 10:00am ( 50 min )
15-05-2013
Percubaan
16-07-2013
17-07-2013
18-07-2013
Hari
Masa时间
Mata Pelajaran科目
Pertama
7:40am – 7:50am
Arahan Pengawas tentang perjalanan Ujian
7:50am – 8:40am ( 50 min )
07-05-2013
03-09-2013
11:00am –12:00pm ( 60 min )
Pendidikan Moral
道德教育
13-05-2013
17-09-2013
12:00pm –1:00pm ( 60 min )
Mathematics
数学
14-05-2013
18-09-2013
12:30pm –1:30pm ( 60 min )
Bahasa Melayu – Pemahaman (021)
国语-理解
8:50am – 10:05am ( 75 min )
Bahasa Melayu – Penulisan (022)
国语-作文
11:00am – 11:40am ( 40 min )
Matematik- Kertas 2 (025/2)
PBS评审
Tarikh日期/ Minggu Pertama第一周
Ujian 1月考(一)
04-03-2013
05-03-2013
*PPT年中考试
06-05-2013
07-05-2013
*PAT年终考试
02-09-2013
03-09-2013
8:10am – 9:25am
( 75 min )
BM – Penulisan
11-03-2013
12-03-2013
13-03-2013
*PPT年中考试
13-05-2013
14-05-2013
15-05-2013
*PAT年终考试
17-09-2013
18-09-2013
19-09-2013
8:10am – 9:00am
( 50 min )
BM – Pemahaman
国语-理解
7:50am – 9:05am ( 75min )
Sains (028)科学
9:15am – 10:05am ( 50 min )
Bahasa Inggeris – Kertas 1 (024/1)英语试卷(一)
11:00am – 12:15pm ( 75 min )
Bahasa Inggeris – Kertas 2 (024/2)英语试卷(二)
BI – Kertas 1
英语-试卷(一)
BC – Pemahaman
华语-理解
11:00am
Matematik -Kertas 2
数学-试卷(二)
11:00am – 11:40am
( 40 min )
Matematik -Kertas 1
数学-试卷(一)
11:00am – 12:00pm
( 60 min )
SJKC JELUTONG日落洞华小
JADUAL PBS 13 – Tahun 1 Hingga Tahun 3
2013年度一年级至三年级评审时间表
PBS评审
Tarikh日期
*PPT年中考试
13-05-2013
14-05-2013
15-05-2013
*PAT年终考试
17-09-2013
18-09-2013
国语-作文
BC – Penulisan
华语-作文
11:00am – 12:15pm
( 75 min )
BI - Kertas 2
英语-作文
*Pendidikan Moral
道德教育(60 min)
11:00am - 12:00pm
PBS评审
Tarikh日期/ Minggu Kedua第二周
Ujian 1月考(一)
Bahasa Cina – Pemahaman (026)
华语-理解
11:00am – 12:15pm ( 75 min )
Bahasa Cina – Penulisan (027)
华语-作文
Ketiga
7:40am – 7:50am
Arahan Pengawas tentang perjalanan Ujian
Sains
科学
11:00am – 12:15pm
( 75 min )
*Mathematics
数学( 60 min )
12:00pm – 1:00pm
*Science
科学( 60 min )
12:10pm - 1:10pm
------
* PPTPeperiksaan Pertengahan Tahun年中考试PATPeperikasaan Akhir Tahun年终考试
