Wiring_Diagrams_for_Ford_Tractors
写出光线跟踪递归函数的伪代码。

写出光线跟踪递归函数的伪代码。
光线跟踪是一种计算机图形学中常用的方法,用于模拟物体表面反射光线的行为,从而生成逼真的图像。
下面是光线跟踪递归函数的伪代码:```pythonRay Trace(Point3D origin, Vector3D direction, int depth):if depth == MAX_DEPTH: # 达到递归深度,结束递归return BACKGROUND_COLOR# 找到离射线最近的交点hit_distance, hit_point, hit_norm, hit_obj = findIntersection(origin, direction)if not hit_obj: # 未与任何物体相交,返回背景颜色return BACKGROUND_COLOR# 计算环境光照color = hit_obj.material.ambient_color * AMBIENT_LIGHT_COLOR# 计算入射光照for light in scene.lights:light_direction = normalize(light.position - hit_point)# 检查是否有阴影if not isShadowed(hit_point, light.position, hit_obj):color += computeDiffuseColor(hit_obj.material.diffuse_color, light.color, light_direction, hit_norm)color += computeSpecularColor(hit_obj.material.specular_color, light.color, light_direction, hit_norm, direction)前两个参数是光线的起点和方向向量,第三个参数是当前递归深度。
计算机专业英语教程第5版中译英参考

Unit 1A computer system consists of hardware system and software system. The hardware of the computer is usually divided into three major parts or three primary subsystems: the CPU, the memory subsystem, and the I/O subsystem.The CPU performs many operations and controls computer. The memory subsystem is used to store program being executed by the CPU, along with the program’s data. The I/O subsystem allows the CPU to interact with input and output devices such as the keyboard and monitor of a personal computer. The components of the computer are connected to the buses.The part of the computer that performs the bulk of data processing operations is called the central processing unit and is referred to as the CPU. In microcomputer, it is often called the microprocessor. The CPU is made up of three major parts: control unit, ALU, and register set.Memory is also known as internal memory or main memory. It refers to the circuits in the computer that hold whatever programs and data are available for immediate use by the CPU.I/O subsystem includes I/O devices and interface. There are a wide variety of I/O devices, such as mouse, printer, sensor, disk, and so on. Input-output interface provides a method for transferring information between internal storage and external I/O devices. Peripherals connected to a computer need special communication links for interfacing them with the CPU. The purpose of the communication link is to resolve the differences that exist between the central computer and each peripheral.Unit 3(a) A program is a list of instructions or statements for directing the computer to perform a required data processing task. Programming is a multistep process for creating that list of instructions.(b) It is important to understand the difference between a class and an object of that class. A class is simply a specification for creating objects. Thus, a single class may create multiple objects.(c) Java is an object-oriented, network-friendly high-lever programming language that allows programmers to build applications that can run on almost any operating system.(e) Programming involves a great deal of creativity. The design is guide to the function or purpose of each component, but the programmer has great flexibility in implementing the design as code. No matter what language is used, each program component involves at least three major aspects: control structures, algorithms, and data structures.Unit 4The software system can be divided into two broad categories: application software and system software. Application software consists of the program for performing tasks particular to the machine’s utilization. In contrast to application software, system software comprises a large number of programs. These programs start up the computer and function as the principle coordinator of all hardware components and application software. Without system software loaded into RAM of your computer, your hardware and application software are useless.System software can be grouped into three basic parts: operating system, utility software, and language translators. The majority of an installation’s utility software consists of programs for performing activities that are fundamental to computer installations yet not included in the operating system. In a sense, utility software consists of software units that extend the capabilities of the operating system.A computer’s OS is the main collection of programs that manage its activities. The primary chores of an OS are management and control. The OS ensures that all actions requested by a user are valid and processed in an orderly fashion. It also manages the computer system’s resources to perform these operations with efficiency and consistency.Application software is the software designed to help you solve problems specific to business or perform specific business tasks. Application software then is the layer of software closest to you. Basically, there are four categories of application software: productivity software, business and specialty software, entertainment software and education/reference software.Unit 5A computer network is often classified as being either a local area network (LAN), a metropolitan area network (WAN), or a wide area network (WAN). The connection of two or more networks is called an internetwork. The worldwide Internet is a well-known example of an internetwork.LANs are privately owned networks within a single building or campus of up to a few kilometers in size. They are widely used to connect personal computers and workstations in company offices and factories to share resources and exchange information.In general, a given LAN will use only one type of transmission medium. Various topologies are possible for LANs. The most common LAN topologies are bus, ring and star.A MAN is basically a bigger version of a LAN and normally uses similar technology. MAN is designed to extend over an entire city. It may be a single network such as a cable television network, or it may be a means of connecting a number of LANs into a large network so that resources may be shared LAN-to-LAN as well as device-to-device. For example, a company can use a MAN to connect the LANs in all of its offices throughout a city.A WAN spans a large geographical area that may comprise a country, a continent, or even the world. It provides long-distance transmission of data, voice, image, and video information over large geographical area.In contrast to LANs, WANs may utilize public leased, or private communication devices, usually in combinations, and can therefore span an unlimited number of miles.Unit 6Transmission media are used to transfer messages over a network. For instance, the transmission media used in a network may be a privately owned set of cables, the public phone lines, or a satellite system. Transmission media can either be wired or wireless.The three types of wired media most commonly used to carry messages are twisted-pair wire, coaxial cable, and fiber-optic cable. One of the most successful developments in transmission media in recent years has been fiber optics. Fiber-optic cable is commonly used for the high-speed backbone lines of a network, or for Internet infrastructure.Wireless transmission media have become especially popular in recent years. They support communications in situations in which physical wiring is impractical or inconvenient, as well as facilitate mobility. Wireless media are commonly used to connect devices to a network, to share information between computers, to connect wireless mice to a computer, and for handheld PCs, wireless phones, and other mobile devices. Radio signals transferred through the air are the heart of most types of wireless media. In addition to conventional broadcast radio application, the microwave, cellular, and satellite transmission media also use radio signals to transmit data.Radio transmissions require the use of a transmitter to send the radio signals through the air. A receiver (usually containing some type of antenna) accepts the date at the other end. When a device functions as both a receiver and transmitter, it is commonly called a transceiver or transmitter-receiver.Unit 7(a) Since many database systems users are not computer trained, developers hide the complexity from users through several levels of abstraction, to simplify user’s int eractions with the system: physical level, logical level, and view level.(b) A database schema is specified by a set of definitions expressed by a special language called a data-definition language (DDL). The result of compilation of DDL statements is a set of tables that is stored in a special file called data dictionary, or data directory.(c) The structured query language (SQL) is the most widely used and standard query language for relational database management systems. It is a kind of non-procedural language.(d) An entity is a “thing” or “object” in the real world that is distinguishable from other objects. For example, each person is an entity, and bank accounts can be considered to be entities. Entities are described in a database by a set of attributes.(e) Data warehouse is one of the newest and hottest buzzwords and concepts in the IT field and the business environment.A data warehouse is a logical collection of information——gathered from many different operational databases——that supports business analysis activities and decision-making tasks.Unit 9(a) AI is currently being applied in business in the form of knowledge systems, which use human knowledge to solve problems. The most popular type of knowledge-based system is the expert system. An expert system is a computer program that attempts to represent the knowledge of human experts in the form of heuristics. The term heuristic is derived from the same Greek root as the word eureka, which means “to discover”.(b) The user interface enables the manager to enter instructions and information into the expert system and to receive information from it. The instructions specify the parameters that guide the expert system through its reasoning processing. The information is in the form of values assigned to certain variables.(c) The knowledge base contains both facts that describe the problem area and knowledge representation techniques that describe how the facts fit together in a logical manner. The term problem domain is used to describe the problem area.(d) An expert system, also called a knowledge-based system, is an artificial intelligence system that applies reasoning capabilities to reach a conclusion. Expert systems are excellent for diagnostic and prescriptive problems.(e) The DSS is not intended to replace the manager. The computer can be applied to the structured portion of the problem, but the manager is responsible for the unstructured portion——applying judgment or intuition and conducting analyses.1。
ULPI_v1_1

UTMI+ Low Pin Interface (ULPI)SpecificationRevision 1.1October 20, 2004Revision HistoryDate CommentRevision Issue0.9 November 12, 2003 Pre-release.1.0rc1 January 3, 2004 Introduce PHY interface “modes”.Update interface timings. Clarify 4-bit data clocking.Clarify sending of RX CMD’s and interrupts.Introduce AutoResume feature.Route int pin to data(3) during 6-pin Serial Mode.Explain VBUS thresholds.Add T&MT diagram and updated text.Add new section to explain how PHY is aborted by Link.Various clarifications.1.0rc2 January 13, 2004 Add block diagram.Tighten interface timing.Modify suspend protocol to more closely resemble UTMI.Add SPKR_L and SPKR_MIC to signal list and T&MTconnector.Various clarifications.1.0rc3 January 19, 2004 Specify that PHY must send RX CMD after Reset.Link + PHY clock startup time of no more than 5.6ms for aperipheral is now mandatory.PHY output delay reduced from 10ns to 9ns.Added link decision time numbers for low speed.Various Clarifications.1.0 February 2, 2004 1.0rc3 adopted as 1.0 release.1.1rc1 September 1, 2004 Various clarifications and fixes to hold time numbers, sendingRXCMDs, FsLsSerialMode, Vbus control and monitoring,Test_J and Tesk_K signalling, Low Power Mode,Hostdisconnect, ID detection, HS SOF packets, interrupts,Carkit Mode, interface protection, No SYNC/EOP mode,linestate filtering, and AutoResume.1.1rc2 October 4, 2004 Re-arranged text in section 3.8.7.3. Updated contributors list.1.1 October 20, 2004 1.1rc2 adopted as 1.1 release.The present Specification has been circulated for the sole benefit of legally-recognized Promoters, Adopters and Contributors of the Specification. All rights are expressly reserved, including but not limited to intellectual property rights under patents, trademarks, copyrights and trade secrets. The respective Promoter's, Adopter's or Contributor's agreement entered into by Promoters, Adopters and Contributors sets forth their conditions of use of the Specification.iiPromotersARC International Inc.Conexant Systems, Inc.Mentor Graphics CorporationPhilipsSMSCTransDimension, Inc.ContributorsVertenten PhilipsBartOkur PhilipsBatuhanBillAnderson MotorolaMcInerney TransDimensionBillBooker CypressBrianARCBelangerChrisKolb ARCChrisChrisSchell PhilipsChung Wing Yan PhilipsSrokaPhilipsDaveWang PhilipsDavidWooten TransDimensionDavidSMSCEricKawamotoPhilipsMackayFarranFrazier ConexantFrankFredRoberts SynopsysFarooqConexantHassanLee TransDimensionHyunParr MentorIanStandiford TransDimensionJayPhilipsTjiaJeromeMentorSaundersMarkMohamed Benromdhane ConexantSMSCMorganMonksISINabilTaklaTengstrand ARCPeterRamanand Mandayam ConexantDouglas MentorRobSaleemMohamed Synopsys(Author)ShaunReemeyer PhilipsCypressSimonNguyenSubramanyam Sankaran PhilipsTexasInstrumentsViningSueRemple QualcommTerryChen ConexantTimothyConexantChangVincentQuestions should be emailed to lpcwg@.iiiTable of Contents1.Introduction (1)1.1General (1)1.2Naming Convention (1)1.3Acronyms and Terms (1)1.4References (1)2.Generic Low Pin Interface (2)2.1General (2)2.2Signals (2)2.3Protocol (3)2.3.1Bus Ownership (3)2.3.2Transferring Data (3)2.3.3Aborting Data (4)3.UTMI+ Low Pin Interface (5)3.1General (5)3.2Signals (6)3.3Block Diagram (7)3.4Modes (9)3.5Power On and Reset (10)3.6Interrupt Event Notification (10)3.7Timing (11)3.7.1Clock (11)3.7.2Control and Data (13)3.8Synchronous Mode (15)3.8.1ULPI Command Bytes (15)3.8.2USB Packets (18)3.8.3Register Operations (30)3.8.4Aborting ULPI Transfers (37)3.8.5USB Operations (39)3.8.6Vbus Power Control (internal and external) (52)3.8.7OTG Operations (52)3.9Low Power Mode (55)3.9.1Data Line Definition For Low Power Mode (55)3.9.2Entering Low Power Mode (55)3.9.3Exiting Low Power Mode (56)3.9.4False Resume Rejection (57)3.10Full Speed / Low Speed Serial Mode (Optional) (58)3.10.1Data Line Definition For FsLsSerialMode (58)3.10.2Entering FsLsSerialMode (59)3.10.3Exiting FsLsSerialMode (60)3.11Carkit Mode (Optional) (61)3.12Safeguarding PHY Input Signals (62)4.Registers (65)4.1Register Map (65)4.2Immediate Register Set (67)4.2.1Vendor ID and Product ID (67)4.2.2Function Control (68)4.2.3Interface Control (69)4.2.4OTG Control (71)4.2.5USB Interrupt Enable Rising (72)4.2.6USB Interrupt Enable Falling (73)4.2.7USB Interrupt Status (74)4.2.8USB Interrupt Latch (75)4.2.9Debug (76)4.2.10Scratch Register (76)4.2.11Carkit Control (77)4.2.12Carkit Interrupt Delay (77)iv4.2.13Carkit Interrupt Enable (78)4.2.14Carkit Interrupt Status (78)4.2.15Carkit Interrupt Latch (79)4.2.16Carkit Pulse Control (79)4.2.17Transmit Positive Width (80)4.2.18Transmit Negative Width (80)4.2.19Receive Polarity Recovery (80)4.2.20Reserved (81)4.2.21Access Extended Register Set (81)4.2.22Vendor-specific (81)4.3Extended Register Set (81)4.4Register Settings for all Upstream and Downstream signalling modes (81)5.T&MT Connector (83)5.1General (83)5.2Daughter-card (UUT) Specification (83)vFiguresFigure 1 – LPI generic data bus ownership (3)Figure 2 – LPI generic data transmit followed by data receive (3)Figure 3 – Link asserts stp to halt receive data (4)Figure 4 – Creating a ULPI system using wrappers (5)Figure 5 – Block diagram of ULPI PHY (7)Figure 6 – Jitter measurement planes (12)Figure 7 – ULPI timing diagram (13)Figure 8 – Clocking of 4-bit data interface compared to 8-bit interface (14)Figure 9 – Sending of RX CMD (17)Figure 10 – USB data transmit (NOPID) (18)Figure 11 – USB data transmit (PID) (19)Figure 12 – PHY drives an RX CMD to indicate EOP (FS/LS LineState timing not to scale) (20)Figure 13 – Forcing a full/low speed USB transmit error (timing not to scale) (21)Figure 14 – USB receive while dir was previously low (22)Figure 15 – USB receive while dir was previously high (23)Figure 16 – USB receive error detected mid-packet (24)Figure 17 – USB receive error during the last byte (25)Figure 18 – USB HS, FS, and LS bit lengths with respect to clock (26)Figure 19 – HS transmit-to-transmit packet timing (29)Figure 20 – HS receive-to-transmit packet timing (29)Figure 21 – Register write (30)Figure 22 – Register read (31)Figure 23 – Register read or write aborted by USB receive during TX CMD byte (31)Figure 24 – Register read turnaround cycle or Register write data cycle aborted by USB receive (32)Figure 25 – USB receive in same cycle as register read data. USB receive is delayed (33)Figure 26 – Register read followed immediately by a USB receive (33)Figure 27 – Register write followed immediately by a USB receive during stp assertion (34)Figure 28 – Register read followed by a USB receive (34)Figure 29 – Extended register write (35)Figure 30 – Extended register read (35)Figure 31 – Extended register read aborted by USB receive during extended address cycle (36)Figure 32 – PHY aborted by Link asserting stp. Link performs register write or USB transmit (37)Figure 33 – PHY aborted by Link asserting stp. Link performs register read (38)Figure 34 – Link aborts PHY. Link fails to drive a TX CMD. PHY re-asserts dir (38)Figure 35 – Hi-Speed Detection Handshake (Chirp) sequence (timing not to scale) (40)Figure 36 – Preamble sequence (D+/D- timing not to scale) (41)Figure 37 – LS Suspend and Resume (timing not to scale) (43)Figure 38 – FS Suspend and Resume (timing not to scale) (44)Figure 39 – HS Suspend and Resume (timing not to scale) (46)Figure 40 – Low Speed Remote Wake-Up from Low Power Mode (timing not to scale) (47)Figure 41 – Full Speed Remote Wake-Up from Low Power Mode (timing not to scale) (48)Figure 42 – Hi-Speed Remote Wake-Up from Low Power Mode (timing not to scale) (49)Figure 43 – Automatic resume signalling (timing not to scale) (50)Figure 44 – USB packet transmit when OpMode is set to 11b (51)Figure 45 – RX CMD V A_VBUS_VLD ≤Vbus indication source (54)Figure 46 – Entering low power mode (55)Figure 47 – Exiting low power mode when PHY provides output clock (56)Figure 48 – Exiting low power mode when Link provides input clock (56)Figure 49 – PHY stays in Low Power Mode when stp de-asserts before clock starts (57)Figure 50 – PHY re-enters Low Power Mode when stp de-asserts before dir de-asserts (57)Figure 51 – Interface behaviour when entering Serial Mode and clock is powered down (59)Figure 52 – Interface behaviour when entering Serial Mode and clock remains powered (59)Figure 53 – Interface behaviour when exiting Serial Mode and clock is not running (60)Figure 54 – Interface behaviour when exiting Serial Mode and clock is running (60)Figure 55 – PHY interface protected when the clock is running (62)Figure 56 – Power up sequence when PHY powers up before the link. Interface is protected (63)Figure 57 – PHY automatically exits Low Power Mode with interface protected (63)Figure 58 – Link resumes driving ULPI bus and asserts stp because clock is not running (64)viFigure 59 – Power up sequence when link powers up before PHY (ULPI 1.0 compliant links) (64)Figure 60 – Recommended daughter-card configuration (not to scale) (83)viiTablesTable 1 – LPI generic interface signals (2)Table 2 – PHY interface signals (6)Table 3 – Mode summary (9)Table 4 – Clock timing parameters (11)Table 5 – ULPI interface timing (13)Table 6 – Transmit Command (TX CMD) byte format (15)Table 7 – Receive Command (RX CMD) byte format (16)Table 8 – USB specification inter-packet timings (26)Table 9 – PHY pipeline delays (27)Table 10 – Link decision times (28)Table 11 – OTG Control Register power control bits (52)Table 12 – Vbus comparator thresholds (52)Table 13 – RX CMD VbusValid over-current conditions (53)Table 14 – Vbus indicators in the RX CMD required for typical applications (54)Table 15 – Interface signal mapping during Low Power Mode (55)Table 16 – Serial Mode signal mapping for 6-pin FsLsSerialMode (58)Table 17 – Serial Mode signal mapping for 3-pin FsLsSerialMode (58)Table 18 – Carkit signal mapping (61)Table 19 – Register map (66)Table 20 – Register access legend (67)Table 21 – Vendor ID and Product ID register description (67)Table 22 – Function Control register (68)Table 23 – Interface Control register (70)Table 24 – OTG Control register (71)Table 25 – USB Interrupt Enable Rising register (72)Table 26 – USB Interrupt Enable Falling register (73)Table 27 – USB Interrupt Status register (74)Table 28 – USB Interrupt Latch register (75)Table 29 – Rules for setting Interrupt Latch register bits (75)Table 30 – Debug register (76)Table 31 – Scratch register (76)Table 32 – Carkit Control Register (77)Table 33 – Carkit Interrupt Delay register (77)Table 34 – Carkit Interrupt Enable register (78)Table 35 – Carkit Interrupt Status Register (78)Table 36 – Carkit Interrupt Latch register (79)Table 37 – Carkit Pulse Control (79)Table 38 – Transmit Positive Width (80)Table 39 – Transmit Negative Width (80)Table 40 – Receive Polarity Recovery (81)Table 41 – Upstream and downstream signalling modes (82)Table 42 – T&MT connector pin view (84)Table 43 – T&MT connector pin allocation (84)Table 44 – T&MT pin description (85)viii1. Introduction1.1 GeneralThis specification defines a generic PHY interface in Chapter 2.In Chapter 3, the generic interface is applied to the UTMI+ protocol, reducing the pin count for discrete USB transceiver implementations supporting On-The-Go, host, and peripheral application spaces.Convention1.2 NamingEmphasis is placed on normal descriptive text using underlined Arial font, e.g. must.Signal names are represented using the lowercase bold Arial font, e.g. clk.Registers are represented using initial caps, bold Arial font, e.g. OTG Control.Register bits are represented using initial caps, bold italic Arial font, e.g. USB Interrupt Enable Falling. 1.3 Acronyms and TermsA-device Device with a Standard-A or Mini-A plug inserted into its receptacleB-device Device with a Standard-B or Mini-B plug inserted into its receptacleDeviceDRD Dual-RoleFPGA Field Programmable Gate ArraySpeedFS FullHNP Host Negotiation ProtocolHS Hi-SpeedLink ASIC, SIE, or FPGA that connects to an ULPI transceiverLPI Low Pin InterfaceSpeedLS LowOTG On-The-GoPHY Physical Layer (Transceiver)PLL Phase Locked LoopSE0 Single Ended ZeroSIE Serial Interface EngineSRP Session Request ProtocolT&MT Transceiver and Macrocell TesterULPI UTMI+ Low Pin InterfaceUSB Universal Serial BusUSB-IF USB Implementers ForumUTMI USB 2.0 Transceiver Macrocell InteraceUUT Unit Under Test1.4 References[Ref 1] Universal Serial Bus Specification, Revision 2.0[Ref 2] On-The-Go Supplement to the USB 2.0 Specification, Revision 1.0a[Ref 3] USB 2.0 Transceiver Macrocell Interface (UTMI) Specification, v1.05[Ref 4] UTMI+ Specification, Revision 1.0[Ref 5] CEA-2011, OTG Transceiver Specification[Ref 6] CEA-936A, Mini-USB Analog Carkit Interface Specification[Ref 7] USB 2.0 Transceiver and Macrocell Tester (T&MT) Interface Specification, Version 1.212. Generic Low Pin Interface2.1 GeneralThis section describes a generic low pin interface (LPI) between a Link and a PHY. Interface signals are defined and the basic communication protocol is described. The generic interface can be used as a common starting point for defining multiple application-specific interfaces.Chapter 3 defines the UTMI+ Low Pin Interface (ULPI), which is based on the generic interface described here. For ULPI implementations, the definitions in chapter 3 over-ride anything defined in chapter 2.2.2 SignalsThe LPI transceiver interface signals are described in Table 1. The interface described here is generic, and can be used to transport many different data types. Depending on the application, the data stream can be used to transmit and receive packets, access a register set, generate interrupts, and even redefine the interface itself. All interface signals are synchronous when clock is toggling, and asynchronous when clock is not toggling. Data stream definition is application-specific and should be explicitly defined for each application space for inter-operability.Control signals dir, stp, and nxt are specified with the assumption that the PHY is the master of the data bus. If required, an implementation can define the Link as the master. If the Link is the master of the interface, the control signal direction and protocol must be reversed.Signal Direction DescriptionPHY Interfaceclock I/O Interface clock. Both directions are allowed. All interface signals are synchronous to clock.data I/O Bi-directional data bus, driven low by the Link during idle. Bus ownership is determined by dir. The Link and PHY initiate data transfers by driving a non-zero pattern onto the data bus. LPI defines interface timing for single-edge data transfers with respect to rising edge of clock. An implementation may optionally define double-edge data transfers with respect to both rising and falling edges of clock.dir OUT Direction. Controls the direction of the data bus. When the PHY has data to transfer to the Link, it drives dir high to take ownership of the bus. When the PHY has no data to transfer it drives dir low and monitors the bus for Link activity. The PHY pulls dir high whenever the interface cannot accept data from the Link. For example, when the internal PHY PLL is not stable.stp IN Stop. The Link asserts this signal for 1 clock cycle to stop the data stream currently on the bus. If the Link is sending data to the PHY, stp indicates the last byte of data was on the bus in the previous cycle. If the PHY is sending data to the Link, stp forces the PHY to end its transfer, de-assert dir and relinquish control of the the data bus to the Link.nxt OUT Next. The PHY asserts this signal to throttle the data. When the Link is sending data to the PHY, nxt indicates when the current byte has been accepted by the PHY. The Link places the next byte on the data bus in the following clock cycle. When the PHY is sending data to the Link, nxt indicates when a new byte is available for the Link to consume.Table 1 – LPI generic interface signals22.3 ProtocolOwnership2.3.1 BusThe PHY is the master of the LPI bi-directional data bus. Ownership of the data bus is determined by the dir signal from the PHY, as shown in Figure 1. When dir is low, the Link can drive data on the bus. When dir is high, the PHY can drive data on the bus. A change in dir causes a turnaround cycle on the bus during which, neither Link nor PHY can drive the bus. Data during the turnaround cycle is undefined and must be ignored by both Link and PHY.The dir signal can be used to directly control the data output buffers of both PHY and Link.Figure 1 – LPI generic data bus ownershipData2.3.2 TransferringAs shown in the first half of Figure 2, the Link continuously drives the data bus to 00h during idle. The Link transmits data to the PHY by driving a non-zero value on the data bus. To signal the end of data transmission, the Link asserts stp in the cycle following the last data byte.In the second half of Figure 2, the Link receives data when the PHY asserts dir. The PHY asserts dir only when it has data to send to the Link, and keeps dir low at all other times. The PHY drives data to the Link after the turnaround cycle.The nxt signal can be used by the PHY to throttle the data during transmit and receive. During transmit, nxt may be asserted in the same cycle that the Link asserts stp.Figure 2 – LPI generic data transmit followed by data receive2.3.3 AbortingDataThe PHY can assert dir to interrupt any data being transmitted by the Link. If the Link needs to interrupt data being received from the PHY, it asserts stp for one clock cycle, as shown in Figure 3. This causes the PHY to unconditionally1 de-assert dir and accept a complete data transmit from the Link. The PHY may re-assert dir again only when the data transmit from the Link has completed.Figure 3 – Link asserts stp to halt receive data1 The PHY will not de-assert dir if the ULPI interface is not usable. For example, if the internal PLL is not stable.3. UTMI+ Low Pin Interface3.1 GeneralThis section describes how any UTMI+ core can be wrapped to convert it to the smaller LPI interface. The generic interface described in chapter 2 is used as a starting point. This section always over-rides anything stated in chapter 2. While this specification details support of UTMI+ Level 3, PHY implementers may choose to support any of the Levels defined in UTMI+.ULPI defines a PHY to Link interface of 8 or 12 signals that allows a lower pin count option for connecting to an external transceiver that may be based on the UTMI+ specification. The pin count reduction is achieved by having relatively static UTMI+ signals be accessed through registers and by providing a bi-directional data bus that carries USB data and provides a means of accessing register data on the ULPI transceiver.This specification relies on concepts and terminology that are defined in the UTMI+ specification [Ref 4]. Specifically, if a ULPI PHY design is based on an internal UTMI+ core, then that core must implement the following UTMI+ features.Linestate must accurately reflect D+/D- to within 2-3 clocks. It is up to individual Link designers to use Linestate to time bus events.Filtering to prevent spurious SE0/SE1 states appearing on Linestate due to skew between D+ and D-. Filtering of 14 clock cycles is required in Low Speed, and 2 clock cycles in Full Speed and Hi-Speed modes.The PHY must internally block the USB receive path during transmit. The receive path can be unblocked when the internal Squelch (HS) or SE0-to-J (FS/LS) is seen.TxReady must be used for all types of data transmitted, including Chirp.Due to noise on the USB, it is possible that RxActive asserts and then de-asserts without any valid data being received, and RxValid will not assert. The Link should operate normally with these data-less RxActive assertions.As shown in Figure 4, a PHY or Link based on this specification can be implemented as an almost transparent wrapper around existing UTMI+ IP cores, preserving the original UTMI+ packet timing, while reducing pin count and leaving all functionality intact. This should not be taken to imply that other implementations are not possible.Figure 4 – Creating a ULPI system using wrappers3.2 SignalsTable 2 describes the ULPI interface on the PHY. The PHY is always the master of the ULPI bus. USB and Miscellaneous signals may vary with each implementation and are given only as a guide to PHY designers.Signal Direction DescriptionPHY Interfaceclock I/O Interface clock. The PHY must be capable of providing a 60MHz output clock. Support for an input 60MHz clock is optional. If the PHY supports both clock directions, it must not use the ULPI control and data signals for setting the clock direction.Data bus. Driven to 00h by the Link when the ULPI bus is idle. Two bus widths are allowed:• 8-bit data timed on rising edge of clock.data I/O• (Optional) 4-bit data timed on rising and falling edges of clock.dir OUT Controls the direction of the data bus2. The PHY pulls dir high whenever the interface cannot accept data from the Link. For example, when the internal PLL is not stable. This applies whether Link or PHY is the clock source.stp IN The Link must assert stp to signal the end of a USB transmit packet or a register write operation, and optionally to stop any receive. The stp signal must be asserted in the cycle after the last data byte is presented on the bus.nxt OUT The PHY asserts nxt to throttle all data types, except register read data and the RX CMD. Identical to RxValid during USB receive, and TxReady during USB transmit. The PHY also asserts nxt and dir simultaneously to indicate USB receive activity (RxActive), if dir was previously low. The PHY is not allowed to assert nxt during the first cycle of the TX CMD driven by the Link.USB InterfaceD+ I/O D+ pin of the USB cable. Required.D- I/O D- pin of the USB cable. Required.ID IN ID pin of the USB cable. Required for OTG-capable PHY’s.VBUS I/O V BUS pin of the USB cable. Required for OTG-capable PHY’s. Required for driving V BUS and the V BUS comparators.MiscellaneousXI IN Crystal input pin. Vendors should specify supported crystal frequencies. XO OUT Crystal output pin.C+ I/O Positive terminal of charge pump capacitor.C- I/O Negative terminal of charge pump capacitor.SPKR_L IN Optional Carkit left/mono speaker input signal.SPKR_MIC I/O Optional Carkit right speaker input or microphone output signal.RBIAS I/O Bias current resistor.Table 2 – PHY interface signals2 UTMI+ wrapper developers should note that data bus control has been reversed from UTMI to ensure that USB data reception is not interrupted by the Link.3.3 BlockDiagramAn example block diagram of a ULPI PHY is shown in Figure 5. This example is based on an internal UTMI+ Level 3 core [Ref 4], which can interface to peripheral, host, and On-The-Go Link cores. A description of each major block is given below.ULPI InterfaceUSBCableChargePumpCapacitor Figure 5 – Block diagram of ULPI PHYUTMI+ Level 3 PHY coreThe ULPI PHY may contain a core that is compliant to any UTMI+ level [Ref 4]. Signals for 16-bit data buses are not supported in ULPI. While Figure 5 shows the typical blocks for a Level 3 UTMI+ core, the PHY vendor must specify the intended UTMI+ level, and provide the functionality necessary for compliance to that level.ULPI PHY WrapperThe ULPI PHY wrapper of Figure 5 reduces the UTMI+ interface to the Low Pin Interface described in this document. All signals shown on the UTMI+ Level 3 PHY core are reduced to the ULPI interface signals clock, data, dir, stp, and nxt. The Register Map stores the relatively static signals of the UTMI+ interface. Crystal Oscillator and PLLWhen a crystal is attached to the PHY, the internal clock(s) and the external 60MHz interface clock are generated from the internal PLL. When no crystal is attached, the PHY may optionally generate the internal clock(s) from an input 60MHz clock provided by the Link.General BiasingInternal analog circuits require an accurate bias current. This is typically generated using an external, accurate reference resistor.DrvVbusExternal and ExternalVbusIndicatorThe PHY may optionally control an external VBUS power source via the optional pin DrvVbusExternal. For example, the external supply could be a charge pump or 5V power supply controlled using a power switch. The external supply is controlled by the DrvVbus and the optional DrvVbusExternal bits in the OTG Control register. The polarity of the DrvVbusExternal output pin is implementation dependent.If control of an external VBUS source is provided the PHY may optionally provide for a VBUS power source feed back signal on the optional pin ExternalVbusIndicator. If this pin is provided, the use of the pin is defined by the optional control bits in the OTG Control and Interface Control registers. See Section 3.8.6.3 for further detail.Power-On-ResetA power-on-reset circuit must be provided in the PHY. When power is first applied to the PHY, the power-on-reset will reset all circuitry and leave the ULPI interface in a usable state.Carkit OptionThe PHY may optionally support Carkit Mode [Ref 6]. While in Carkit Mode, the PHY routes speaker and microphone signals between the Link and the USB cable. In carkit mono mode, SPKR_L inputs a mono speaker signal and SPKR_MIC outputs the microphone signal, MIC. In carkit stereo mode, SPKR_L inputs the left speaker signal, and SPKR_MIC inputs the right speaker signal, SPKR_R.3.4 ModesThe ULPI interface can operate in one of five independent modes listed in Table 3. The interface is in Synchronous Mode by default. Other modes are enabled by bits in the Function Control and Interface Control registers. In Synchronous Mode, the data bus carries commands and data. In other modes, the data pins are redefined with different functionality. Synchronous Mode and Low Power Mode are mandatory.Mode Name Mode DescriptionSynchronous Mode This is the normal mode of operation. The clock is running and is stablewith the characteristics defined in section 3.6. The ULPI interface carriescommands and data that are synchronous to clock.Low Power Mode The PHY is powered down with the clock stopped. The PHY keeps dirasserted, and the data bus is redefined to carry LineState and interrupts.See section 3.9 for more information.6-pin FS/LS Serial Mode (optional) The data bus is redefined to 6-pin serial mode, including 6 pins to transmit and receive serial USB data, and 1 pin to signal interrupt events. The clock can be enabled or disabled. This mode is valid only for implementations with an 8-bit data bus. See section 3.10 for more information.3-pin FS/LS Serial Mode (optional) The data bus is redefined to 3-pin serial mode, including 3 pins to transmit and receive serial USB data, and 1 pin to signal interrupt events. The clock can be enabled or disabled. See section 3.10 for more information.Carkit Mode (optional) The data bus is redefined to Carkit mode [Ref 6], including 2 pins for serial UART data, and 1 pin to signal interrupt events. The clock may optionally be stopped. See section 3.11 for more information.Table 3 – Mode summary。
elvis 运算符 -回复

elvis 运算符-回复Elvis operator, also known as the ternary operator, is a conditional operator used in programming languages to simplify conditional expressions. Its syntax is often represented as `[condition] ? [value_if_true] : [value_if_false]`. In this article, we will discuss the Elvis operator, how it works, its advantages and disadvantages, and some examples to illustrate its usage.The Elvis operator is particularly useful when evaluating and assigning values based on a condition. It provides a concise and readable way to handle conditional assignments in a single line of code. It is often used as an alternative to traditional if-else statements for simpler conditional checks.To understand how the Elvis operator works, let's break down its components. The condition placed within the square brackets `[]` is the expression that evaluates to either true or false. If the condition is true, the value before the `:` is returned; otherwise, the value after the `:` is returned. This allows us to assign different values based on the outcome of the condition.One of the main advantages of using the Elvis operator is its brevity.By condensing the condition and assignment into a single line of code, it improves code readability and reduces the need for extensive if-else statements. This makes the code more concise and easier to understand. In addition, the Elvis operator promotes a more functional programming style by enabling the use of functional constructs such as mapping or filtering without the need for explicit if checks.Another advantage of the Elvis operator is that it can handle null values efficiently. When used in conjunction with null check expressions, it allows for a more graceful handling of null values without the need for additional code blocks. It simplifies the process of assigning default values or fallback options when dealing with nullable variables.However, it is important to consider the Elvis operator's limitations and potential disadvantages. One limitation is that it can only handle binary conditions. It is not suitable for complex conditions that require multiple branches or nested if statements. In such cases, using traditional if-else statements may be more appropriate.Moreover, excessive use of the Elvis operator can lead to code that is difficult to read and maintain. While it is a concise way to handle simple conditional assignments, overreliance on the operator can make the code less explicit and more prone to errors. Therefore, it is recommended to use the Elvis operator judiciously and prioritize code readability and maintainability.Let's now look at some practical examples to better understand the Elvis operator's usage. Consider the following code snippet in Python:pythonx = 10y = 20 if x > 5 else 30print(y)In this example, if the condition `x > 5` evaluates to true, the value `20` is assigned to `y`. Otherwise, the value `30` is assigned to `y`. The resulting output will be `20`, as `x` is indeed greater than `5`.Now let's consider a scenario where we want to assign a defaultvalue to a variable only if it is currently `null`. We can accomplish this using the Elvis operator in the following manner:javaString name = existingName != null ? existingName : "Default";In this example, if `existingName` is not `null`, it will be assigned to `name`. Otherwise, the value `"Default"` is assigned to `name`. This allows for a concise and efficient handling of null values without the need for additional checks or code blocks.In conclusion, the Elvis operator is a powerful and concise tool for handling conditional assignments. It provides a simplified syntax to evaluate conditions and assign values based on the outcome. While it has its limitations and should be used judiciously, the operator offers significant benefits in terms of code readability and null value handling. By understanding its usage and considering its advantages and disadvantages, developers can leverage the Elvis operator to write more concise and efficient code.。
Multicamera People Tracking with a Probabilistic Occupancy Map

Multicamera People Tracking witha Probabilistic Occupancy MapFranc¸ois Fleuret,Je´roˆme Berclaz,Richard Lengagne,and Pascal Fua,Senior Member,IEEE Abstract—Given two to four synchronized video streams taken at eye level and from different angles,we show that we can effectively combine a generative model with dynamic programming to accurately follow up to six individuals across thousands of frames in spite of significant occlusions and lighting changes.In addition,we also derive metrically accurate trajectories for each of them.Our contribution is twofold.First,we demonstrate that our generative model can effectively handle occlusions in each time frame independently,even when the only data available comes from the output of a simple background subtraction algorithm and when the number of individuals is unknown a priori.Second,we show that multiperson tracking can be reliably achieved by processing individual trajectories separately over long sequences,provided that a reasonable heuristic is used to rank these individuals and that we avoid confusing them with one another.Index Terms—Multipeople tracking,multicamera,visual surveillance,probabilistic occupancy map,dynamic programming,Hidden Markov Model.Ç1I NTRODUCTIONI N this paper,we address the problem of keeping track of people who occlude each other using a small number of synchronized videos such as those depicted in Fig.1,which were taken at head level and from very different angles. This is important because this kind of setup is very common for applications such as video surveillance in public places.To this end,we have developed a mathematical framework that allows us to combine a robust approach to estimating the probabilities of occupancy of the ground plane at individual time steps with dynamic programming to track people over time.This results in a fully automated system that can track up to six people in a room for several minutes by using only four cameras,without producing any false positives or false negatives in spite of severe occlusions and lighting variations. As shown in Fig.2,our system also provides location estimates that are accurate to within a few tens of centimeters, and there is no measurable performance decrease if as many as20percent of the images are lost and only a small one if 30percent are.This involves two algorithmic steps:1.We estimate the probabilities of occupancy of theground plane,given the binary images obtained fromthe input images via background subtraction[7].Atthis stage,the algorithm only takes into accountimages acquired at the same time.Its basic ingredientis a generative model that represents humans assimple rectangles that it uses to create synthetic idealimages that we would observe if people were at givenlocations.Under this model of the images,given thetrue occupancy,we approximate the probabilities ofoccupancy at every location as the marginals of aproduct law minimizing the Kullback-Leibler diver-gence from the“true”conditional posterior distribu-tion.This allows us to evaluate the probabilities ofoccupancy at every location as the fixed point of alarge system of equations.2.We then combine these probabilities with a color and amotion model and use the Viterbi algorithm toaccurately follow individuals across thousands offrames[3].To avoid the combinatorial explosion thatwould result from explicitly dealing with the jointposterior distribution of the locations of individuals ineach frame over a fine discretization,we use a greedyapproach:we process trajectories individually oversequences that are long enough so that using areasonable heuristic to choose the order in which theyare processed is sufficient to avoid confusing peoplewith each other.In contrast to most state-of-the-art algorithms that recursively update estimates from frame to frame and may therefore fail catastrophically if difficult conditions persist over several consecutive frames,our algorithm can handle such situations since it computes the global optima of scores summed over many frames.This is what gives it the robustness that Fig.2demonstrates.In short,we combine a mathematically well-founded generative model that works in each frame individually with a simple approach to global optimization.This yields excellent performance by using basic color and motion models that could be further improved.Our contribution is therefore twofold.First,we demonstrate that a generative model can effectively handle occlusions at each time frame independently,even when the input data is of very poor quality,and is therefore easy to obtain.Second,we show that multiperson tracking can be reliably achieved by processing individual trajectories separately over long sequences.. F.Fleuret,J.Berclaz,and P.Fua are with the Ecole Polytechnique Fe´de´ralede Lausanne,Station14,CH-1015Lausanne,Switzerland.E-mail:{francois.fleuret,jerome.berclaz,pascal.fua}@epfl.ch..R.Lengagne is with GE Security-VisioWave,Route de la Pierre22,1024Ecublens,Switzerland.E-mail:richard.lengagne@.Manuscript received14July2006;revised19Jan.2007;accepted28Mar.2007;published online15May2007.Recommended for acceptance by S.Sclaroff.For information on obtaining reprints of this article,please send e-mail to:tpami@,and reference IEEECS Log Number TPAMI-0521-0706.Digital Object Identifier no.10.1109/TPAMI.2007.1174.0162-8828/08/$25.00ß2008IEEE Published by the IEEE Computer SocietyIn the remainder of the paper,we first briefly review related works.We then formulate our problem as estimat-ing the most probable state of a hidden Markov process and propose a model of the visible signal based on an estimate of an occupancy map in every time frame.Finally,we present our results on several long sequences.2R ELATED W ORKState-of-the-art methods can be divided into monocular and multiview approaches that we briefly review in this section.2.1Monocular ApproachesMonocular approaches rely on the input of a single camera to perform tracking.These methods provide a simple and easy-to-deploy setup but must compensate for the lack of 3D information in a single camera view.2.1.1Blob-Based MethodsMany algorithms rely on binary blobs extracted from single video[10],[5],[11].They combine shape analysis and tracking to locate people and maintain appearance models in order to track them,even in the presence of occlusions.The Bayesian Multiple-BLob tracker(BraMBLe)system[12],for example,is a multiblob tracker that generates a blob-likelihood based on a known background model and appearance models of the tracked people.It then uses a particle filter to implement the tracking for an unknown number of people.Approaches that track in a single view prior to computing correspondences across views extend this approach to multi camera setups.However,we view them as falling into the same category because they do not simultaneously exploit the information from multiple views.In[15],the limits of the field of view of each camera are computed in every other camera from motion information.When a person becomes visible in one camera,the system automatically searches for him in other views where he should be visible.In[4],a background/foreground segmentation is performed on calibrated images,followed by human shape extraction from foreground objects and feature point selection extraction. Feature points are tracked in a single view,and the system switches to another view when the current camera no longer has a good view of the person.2.1.2Color-Based MethodsTracking performance can be significantly increased by taking color into account.As shown in[6],the mean-shift pursuit technique based on a dissimilarity measure of color distributions can accurately track deformable objects in real time and in a monocular context.In[16],the images are segmented pixelwise into different classes,thus modeling people by continuously updated Gaussian mixtures.A standard tracking process is then performed using a Bayesian framework,which helps keep track of people,even when there are occlusions.In such a case,models of persons in front keep being updated, whereas the system stops updating occluded ones,which may cause trouble if their appearances have changed noticeably when they re-emerge.More recently,multiple humans have been simulta-neously detected and tracked in crowded scenes[20]by using Monte-Carlo-based methods to estimate their number and positions.In[23],multiple people are also detected and tracked in front of complex backgrounds by using mixture particle filters guided by people models learned by boosting.In[9],multicue3D object tracking is addressed by combining particle-filter-based Bayesian tracking and detection using learned spatiotemporal shapes.This ap-proach leads to impressive results but requires shape, texture,and image depth information as input.Finally, Smith et al.[25]propose a particle-filtering scheme that relies on Markov chain Monte Carlo(MCMC)optimization to handle entrances and departures.It also introduces a finer modeling of interactions between individuals as a product of pairwise potentials.2.2Multiview ApproachesDespite the effectiveness of such methods,the use of multiple cameras soon becomes necessary when one wishes to accurately detect and track multiple people and compute their precise3D locations in a complex environment. Occlusion handling is facilitated by using two sets of stereo color cameras[14].However,in most approaches that only take a set of2D views as input,occlusion is mainly handled by imposing temporal consistency in terms of a motion model,be it Kalman filtering or more general Markov models.As a result,these approaches may not always be able to recover if the process starts diverging.2.2.1Blob-Based MethodsIn[19],Kalman filtering is applied on3D points obtained by fusing in a least squares sense the image-to-world projections of points belonging to binary blobs.Similarly,in[1],a Kalman filter is used to simultaneously track in2D and3D,and objectFig.1.Images from two indoor and two outdoor multicamera video sequences that we use for our experiments.At each time step,we draw a box around people that we detect and assign to them an ID number that follows them throughout thesequence.Fig.2.Cumulative distributions of the position estimate error on a3,800-frame sequence(see Section6.4.1for details).locations are estimated through trajectory prediction during occlusion.In[8],a best hypothesis and a multiple-hypotheses approaches are compared to find people tracks from 3D locations obtained from foreground binary blobs ex-tracted from multiple calibrated views.In[21],a recursive Bayesian estimation approach is used to deal with occlusions while tracking multiple people in multiview.The algorithm tracks objects located in the intersections of2D visual angles,which are extracted from silhouettes obtained from different fixed views.When occlusion ambiguities occur,multiple occlusion hypotheses are generated,given predicted object states and previous hypotheses,and tested using a branch-and-merge strategy. The proposed framework is implemented using a customized particle filter to represent the distribution of object states.Recently,Morariu and Camps[17]proposed a method based on dimensionality reduction to learn a correspondence between the appearance of pedestrians across several views. This approach is able to cope with the severe occlusion in one view by exploiting the appearance of the same pedestrian on another view and the consistence across views.2.2.2Color-Based MethodsMittal and Davis[18]propose a system that segments,detects, and tracks multiple people in a scene by using a wide-baseline setup of up to16synchronized cameras.Intensity informa-tion is directly used to perform single-view pixel classifica-tion and match similarly labeled regions across views to derive3D people locations.Occlusion analysis is performed in two ways:First,during pixel classification,the computa-tion of prior probabilities takes occlusion into account. Second,evidence is gathered across cameras to compute a presence likelihood map on the ground plane that accounts for the visibility of each ground plane point in each view. Ground plane locations are then tracked over time by using a Kalman filter.In[13],individuals are tracked both in image planes and top view.The2D and3D positions of each individual are computed so as to maximize a joint probability defined as the product of a color-based appearance model and2D and 3D motion models derived from a Kalman filter.2.2.3Occupancy Map MethodsRecent techniques explicitly use a discretized occupancy map into which the objects detected in the camera images are back-projected.In[2],the authors rely on a standard detection of stereo disparities,which increase counters associated to square areas on the ground.A mixture of Gaussians is fitted to the resulting score map to estimate the likely location of individuals.This estimate is combined with a Kallman filter to model the motion.In[26],the occupancy map is computed with a standard visual hull procedure.One originality of the approach is to keep for each resulting connex component an upper and lower bound on the number of objects that it can contain. Based on motion consistency,the bounds on the various components are estimated at a certain time frame based on the bounds of the components at the previous time frame that spatially intersect with it.Although our own method shares many features with these techniques,it differs in two important respects that we will highlight:First,we combine the usual color and motion models with a sophisticated approach based on a generative model to estimating the probabilities of occu-pancy,which explicitly handles complex occlusion interac-tions between detected individuals,as will be discussed in Section5.Second,we rely on dynamic programming to ensure greater stability in challenging situations by simul-taneously handling multiple frames.3P ROBLEM F ORMULATIONOur goal is to track an a priori unknown number of people from a few synchronized video streams taken at head level. In this section,we formulate this problem as one of finding the most probable state of a hidden Markov process,given the set of images acquired at each time step,which we will refer to as a temporal frame.We then briefly outline the computation of the relevant probabilities by using the notations summarized in Tables1and2,which we also use in the following two sections to discuss in more details the actual computation of those probabilities.3.1Computing the Optimal TrajectoriesWe process the video sequences by batches of T¼100frames, each of which includes C images,and we compute the most likely trajectory for each individual.To achieve consistency over successive batches,we only keep the result on the first 10frames and slide our temporal window.This is illustrated in Fig.3.We discretize the visible part of the ground plane into a finite number G of regularly spaced2D locations and we introduce a virtual hidden location H that will be used to model entrances and departures from and into the visible area.For a given batch,let L t¼ðL1t;...;L NÃtÞbe the hidden stochastic processes standing for the locations of individuals, whether visible or not.The number NÃstands for the maximum allowable number of individuals in our world.It is large enough so that conditioning on the number of visible ones does not change the probability of a new individual entering the scene.The L n t variables therefore take values in f1;...;G;Hg.Given I t¼ðI1t;...;I C tÞ,the images acquired at time t for 1t T,our task is to find the values of L1;...;L T that maximizePðL1;...;L T j I1;...;I TÞ:ð1ÞAs will be discussed in Section 4.1,we compute this maximum a posteriori in a greedy way,processing one individual at a time,including the hidden ones who can move into the visible scene or not.For each one,the algorithm performs the computation,under the constraint that no individual can be at a visible location occupied by an individual already processed.In theory,this approach could lead to undesirable local minima,for example,by connecting the trajectories of two separate people.However,this does not happen often because our batches are sufficiently long.To further reduce the chances of this,we process individual trajectories in an order that depends on a reliability score so that the most reliable ones are computed first,thereby reducing the potential for confusion when processing the remaining ones. This order also ensures that if an individual remains in the hidden location,then all the other people present in the hidden location will also stay there and,therefore,do not need to be processed.FLEURET ET AL.:MULTICAMERA PEOPLE TRACKING WITH A PROBABILISTIC OCCUPANCY MAP269Our experimental results show that our method does not suffer from the usual weaknesses of greedy algorithms such as a tendency to get caught in bad local minima.We thereforebelieve that it compares very favorably to stochastic optimization techniques in general and more specifically particle filtering,which usually requires careful tuning of metaparameters.3.2Stochastic ModelingWe will show in Section 4.2that since we process individual trajectories,the whole approach only requires us to define avalid motion model P ðL n t þ1j L nt ¼k Þand a sound appearance model P ðI t j L n t ¼k Þ.The motion model P ðL n t þ1j L nt ¼k Þ,which will be intro-duced in Section 4.3,is a distribution into a disc of limited radiusandcenter k ,whichcorresponds toalooseboundonthe maximum speed of a walking human.Entrance into the scene and departure from it are naturally modeled,thanks to the270IEEE TRANSACTIONS ON PATTERN ANALYSIS AND MACHINE INTELLIGENCE,VOL.30,NO.2,FEBRUARY 2008TABLE 2Notations (RandomQuantities)Fig.3.Video sequences are processed by batch of 100frames.Only the first 10percent of the optimization result is kept and the rest is discarded.The temporal window is then slid forward and the optimiza-tion is repeated on the new window.TABLE 1Notations (DeterministicQuantities)hiddenlocation H,forwhichweextendthemotionmodel.The probabilities to enter and to leave are similar to the transition probabilities between different ground plane locations.In Section4.4,we will show that the appearance model PðI t j L n t¼kÞcan be decomposed into two terms.The first, described in Section4.5,is a very generic color-histogram-based model for each individual.The second,described in Section5,approximates the marginal conditional probabil-ities of occupancy of the ground plane,given the results of a background subtractionalgorithm,in allviewsacquired atthe same time.This approximation is obtained by minimizing the Kullback-Leibler divergence between a product law and the true posterior.We show that this is equivalent to computing the marginal probabilities of occupancy so that under the product law,the images obtained by putting rectangles of human sizes at occupied locations are likely to be similar to the images actually produced by the background subtraction.This represents a departure from more classical ap-proaches to estimating probabilities of occupancy that rely on computing a visual hull[26].Such approaches tend to be pessimistic and do not exploit trade-offs between the presence of people at different locations.For instance,if due to noise in one camera,a person is not seen in a particular view,then he would be discarded,even if he were seen in all others.By contrast,in our probabilistic framework,sufficient evidence might be present to detect him.Similarly,the presence of someone at a specific location creates an occlusion that hides the presence behind,which is not accounted for by the hull techniques but is by our approach.Since these marginal probabilities are computed indepen-dently at each time step,they say nothing about identity or correspondence with past frames.The appearance similarity is entirely conveyed by the color histograms,which has experimentally proved sufficient for our purposes.4C OMPUTATION OF THE T RAJECTORIESIn Section4.1,we break the global optimization of several people’s trajectories into the estimation of optimal individual trajectories.In Section 4.2,we show how this can be performed using the classical Viterbi’s algorithm based on dynamic programming.This requires a motion model given in Section 4.3and an appearance model described in Section4.4,which combines a color model given in Section4.5 and a sophisticated estimation of the ground plane occu-pancy detailed in Section5.We partition the visible area into a regular grid of G locations,as shown in Figs.5c and6,and from the camera calibration,we define for each camera c a family of rectangular shapes A c1;...;A c G,which correspond to crude human silhouettes of height175cm and width50cm located at every position on the grid.4.1Multiple TrajectoriesRecall that we denote by L n¼ðL n1;...;L n TÞthe trajectory of individual n.Given a batch of T temporal frames I¼ðI1;...;I TÞ,we want to maximize the posterior conditional probability:PðL1¼l1;...;L Nül NÃj IÞ¼PðL1¼l1j IÞY NÃn¼2P L n¼l n j I;L1¼l1;...;L nÀ1¼l nÀ1ÀÁ:ð2ÞSimultaneous optimization of all the L i s would beintractable.Instead,we optimize one trajectory after theother,which amounts to looking for^l1¼arg maxlPðL1¼l j IÞ;ð3Þ^l2¼arg maxlPðL2¼l j I;L1¼^l1Þ;ð4Þ...^l Nüarg maxlPðL Nül j I;L1¼^l1;L2¼^l2;...Þ:ð5ÞNote that under our model,conditioning one trajectory,given other ones,simply means that it will go through noalready occupied location.In other words,PðL n¼l j I;L1¼^l1;...;L nÀ1¼^l nÀ1Þ¼PðL n¼l j I;8k<n;8t;L n t¼^l k tÞ;ð6Þwhich is PðL n¼l j IÞwith a reduced set of the admissiblegrid locations.Such a procedure is recursively correct:If all trajectoriesestimated up to step n are correct,then the conditioning onlyimproves the estimate of the optimal remaining trajectories.This would suffice if the image data were informative enoughso that locations could be unambiguously associated toindividuals.In practice,this is obviously rarely the case.Therefore,this greedy approach to optimization has un-desired side effects.For example,due to partly missinglocalization information for a given trajectory,the algorithmmight mistakenly start following another person’s trajectory.This is especially likely to happen if the tracked individualsare located close to each other.To avoid this kind of failure,we process the images bybatches of T¼100and first extend the trajectories that havebeen found with high confidence,as defined below,in theprevious batches.We then process the lower confidenceones.As a result,a trajectory that was problematic in thepast and is likely to be problematic in the current batch willbe optimized last and,thus,prevented from“stealing”somebody else’s location.Furthermore,this approachincreases the spatial constraints on such a trajectory whenwe finally get around to estimating it.We use as a confidence score the concordance of theestimated trajectories in the previous batches and thelocalization cue provided by the estimation of the probabil-istic occupancy map(POM)described in Section5.Moreprecisely,the score is the number of time frames where theestimated trajectory passes through a local maximum of theestimated probability of occupancy.When the POM does notdetect a person on a few frames,the score will naturallydecrease,indicating a deterioration of the localizationinformation.Since there is a high degree of overlappingbetween successive batches,the challenging segment of atrajectory,which is due to the failure of the backgroundsubtraction or change in illumination,for instance,is met inseveral batches before it actually happens during the10keptframes.Thus,the heuristic would have ranked the corre-sponding individual in the last ones to be processed whensuch problem occurs.FLEURET ET AL.:MULTICAMERA PEOPLE TRACKING WITH A PROBABILISTIC OCCUPANCY MAP2714.2Single TrajectoryLet us now consider only the trajectory L n ¼ðL n 1;...;L nT Þof individual n over T temporal frames.We are looking for thevalues ðl n 1;...;l nT Þin the subset of free locations of f 1;...;G;Hg .The initial location l n 1is either a known visible location if the individual is visible in the first frame of the batch or H if he is not.We therefore seek to maximizeP ðL n 1¼l n 1;...;L n T ¼l nt j I 1;...;I T Þ¼P ðI 1;L n 1¼l n 1;...;I T ;L n T ¼l nT ÞP ðI 1;...;I T Þ:ð7ÞSince the denominator is constant with respect to l n ,we simply maximize the numerator,that is,the probability of both the trajectories and the images.Let us introduce the maximum of the probability of both the observations and the trajectory ending up at location k at time t :Èt ðk Þ¼max l n 1;...;l nt À1P ðI 1;L n 1¼l n 1;...;I t ;L nt ¼k Þ:ð8ÞWe model jointly the processes L n t and I t with a hidden Markov model,that isP ðL n t þ1j L n t ;L n t À1;...Þ¼P ðL n t þ1j L nt Þð9ÞandP ðI t ;I t À1;...j L n t ;L nt À1;...Þ¼YtP ðI t j L n t Þ:ð10ÞUnder such a model,we have the classical recursive expressionÈt ðk Þ¼P ðI t j L n t ¼k Þ|fflfflfflfflfflfflfflfflffl{zfflfflfflfflfflfflfflfflffl}Appearance modelmax P ðL n t ¼k j L nt À1¼ Þ|fflfflfflfflfflfflfflfflfflfflfflfflfflfflfflfflffl{zfflfflfflfflfflfflfflfflfflfflfflfflfflfflfflfflffl}Motion modelÈt À1ð Þð11Þto perform a global search with dynamic programming,which yields the classic Viterbi algorithm.This is straight-forward,since the L n t s are in a finite set of cardinality G þ1.4.3Motion ModelWe chose a very simple and unconstrained motion model:P ðL n t ¼k j L nt À1¼ Þ¼1=Z Áe À k k À k if k k À k c 0otherwise ;&ð12Þwhere the constant tunes the average human walkingspeed,and c limits the maximum allowable speed.This probability is isotropic,decreases with the distance from location k ,and is zero for k k À k greater than a constantmaximum distance.We use a very loose maximum distance cof one square of the grid per frame,which corresponds to a speed of almost 12mph.We also define explicitly the probabilities of transitions to the parts of the scene that are connected to the hidden location H .This is a single door in the indoor sequences and all the contours of the visible area in the outdoor sequences in Fig.1.Thus,entrance and departure of individuals are taken care of naturally by the estimation of the maximum a posteriori trajectories.If there are enough evidence from the images that somebody enters or leaves the room,then this procedure will estimate that the optimal trajectory does so,and a person will be added to or removed from the visible area.4.4Appearance ModelFrom the input images I t ,we use background subtraction to produce binary masks B t such as those in Fig.4.We denote as T t the colors of the pixels inside the blobs and treat the rest of the images as background,which is ignored.Let X tk be a Boolean random variable standing for the presence of an individual at location k of the grid at time t .In Appendix B,we show thatP ðI t j L n t ¼k Þzfflfflfflfflfflfflfflfflffl}|fflfflfflfflfflfflfflfflffl{Appearance model/P ðL n t ¼k j X kt ¼1;T t Þ|fflfflfflfflfflfflfflfflfflfflfflfflfflfflfflfflfflffl{zfflfflfflfflfflfflfflfflfflfflfflfflfflfflfflfflfflffl}Color modelP ðX kt ¼1j B t Þ|fflfflfflfflfflfflfflfflfflfflffl{zfflfflfflfflfflfflfflfflfflfflffl}Ground plane occupancy:ð13ÞThe ground plane occupancy term will be discussed in Section 5,and the color model term is computed as follows.4.5Color ModelWe assume that if someone is present at a certain location k ,then his presence influences the color of the pixels located at the intersection of the moving blobs and the rectangle A c k corresponding to the location k .We model that dependency as if the pixels were independent and identically distributed and followed a density in the red,green,and blue (RGB)space associated to the individual.This is far simpler than the color models used in either [18]or [13],which split the body area in several subparts with dedicated color distributions,but has proved sufficient in practice.If an individual n was present in the frames preceding the current batch,then we have an estimation for any camera c of his color distribution c n ,since we have previously collected the pixels in all frames at the locations272IEEE TRANSACTIONS ON PATTERN ANALYSIS AND MACHINE INTELLIGENCE,VOL.30,NO.2,FEBRUARY2008Fig.4.The color model relies on a stochastic modeling of the color of the pixels T c t ðk Þsampled in the intersection of the binary image B c t produced bythe background subtraction and the rectangle A ck corresponding to the location k .。
Formal Description of OCL Specification Patterns for Behavioral Specification of Software C

Formal Description of OCL Specification Patterns for Behavioral Specification of Software ComponentsJörg AckermannChair of Business Informatics and Systems Engineering,University of Augsburg, Universitätsstr. 16, 86135 Augsburgjoerg.ackermann@wiwi.uni-augsburg.deAbstract. The Object Constraint Language (OCL) is often used for behavioralspecification of software components. One current problem in specifying be-havioral aspects comes from the fact that editing OCL constraints manually istime consuming and error-prone. To simplify constraint definition we proposeto use specification patterns for which OCL constraints can be generated auto-matically. In this paper we outline this solution proposal and develop a wayhow to formally describe such specification patterns on which a library of reus-able OCL specifications is based.Keywords. Software Component Specification, OCL, Specification Patterns1 IntroductionThe Object Constraint Language (OCL) [20] has great relevance for component-based software engineering (CBSE): A crucial prerequisite for applying CBSE successfully is an appropriate and standardized specification of software components [27]. Behav-ioral aspects of components are often specified using OCL (see Sect. 2). From this results one of the current problems in component specifications: Editing OCL con-straints manually is time consuming and error-prone (see Sect. 3).To simplify constraint definition we propose to utilize specification patterns for which OCL constraints can be generated automatically (see Sect. 4). [4] identifies nine patterns that frequently occur in behavioral specifications of software components. In this paper we develop a solution how to formally describe specification patterns that enable a precise pattern specification and aid the implementation of constraint genera-tors (Sect. 5). We conclude with discussion of related work (Sect. 6) and a summary (Sect. 7).The main contributions of this paper are: the proposal to use specification patterns to simplify component specifications and the formal description of specification pat-terns by use of so called OCL pattern functions – together with the identified patterns we obtain a library of reusable OCL specifications.The results are not specific for software components and might therefore be interesting for any user of OCL con-straints.2 Specification of Software ComponentsThe basic paradigm of component-based software engineering is to decouple the pro-duction of components (development for reuse) from the production of complete sys-tems out of components (development by reuse). Applying CBSE promises (amongst others) a shorter time to market, increased adaptability and reduced development costs [8,25].A critical success factor for CBSE is the appropriate and standardized specification of software components: the specification is prerequisite for a composition methodol-ogy and tool support [23] as well as for reuse of components by third parties [26]. With specification of a component we denote the complete, unequivocal and precise description of its external view - that is which services a component provides under which conditions [27].Various authors addressed specifications for specific tasks of the development process as e.g. design and implementation [9,10], component adaptation [28] or com-ponent selection [15]. Approaches towards comprehensive specification of software components are few and include [7,23,27]. Objects to be specified are e.g. business terms, business tasks (domain-related perspective), interface signatures, behavior and coordination constraints (logical perspective) and non-functional attributes (physical perspective).Behavioral specifications (which are topic of this paper) describe how the compo-nent behaves in general and in borderline cases. This is achieved by defining con-straints (invariants, pre- and postconditions) based on the idea of designing applica-tions by contract [18]. OCL is the de-facto standard technique to express such con-straints – cf. e.g. [9,10,23,27].Fig. 1. Interface specification of component SalesOrderProcessingTo illustrate how behavioral aspects of software components are specified we intro-duce a simplified exemplary component SalesOrderProcessing. The business task of the component is to manage sales orders. This component is used as example through-out the rest of the paper.16 J. AckermannFig. 1 shows the interface specification of SalesOrderProcessing using UML [21]. We see that the component offers the interface ISalesOrder with operations to create, check, cancel or retrieve specific sales orders. The data types needed are also defined in Fig. 1. Note that in practice the component could have additional operations and might offer additional order properties. For sake of simplicity we restricted ourselves to the simple form shown in Fig. 1 which will be sufficient as example for this paper. To specify the information objects belonging to the component (on a logical level) one can use a specification data model which is realized as an UML type diagram and is part of the behavioral specification [3]. Fig. 2 displays such a model for the compo-nent SalesOrderProcessing. It shows that the component manages sales orders (with attributes id, date of order, status, customer id) and sales order items (with attributes id, quantity, product id) and that there is a one-to-many relationship between sales orders and sales order items.18 J. Ackermanncan only be called for a sales order that already exists in the component. (More pre-cise: there must exist a sales order which id equals the value of the input parameter orderId. Note that the invariant guarantees that there is at most one such sales order). context SalesOrderinv: SalesOrder.allInstances()->forAll(i1, i2 | i1 <> i2implies i1.id <> i2.id)context ISalesOrder::getOrderData(orderId: string, orderHeader: OrderHeaderData, orderItem: OrderItemData, orderStatus: Order-Status)pre: SalesOrder.allInstances()->exists(id = orderId)Fig. 3. (Partial) Behavioral specification of component SalesOrderProcessing3 Problems in Behavioral Specification of ComponentsMost component specification approaches recommend notations in formal languages since they promise a common understanding of specification results across different developers and companies. The use of formal methods, however, is not undisputed. Some authors argue that the required effort is too high and the intelligibility of the specification results is too low – for a discussion of advantages and liabilities of for-mal methods compare [14].The disadvantages of earlier formal methods are reduced by UML OCL [20]: The notation of OCL has a simple structure and is oriented towards the syntax of object-oriented programming languages. Software developers can therefore handle OCL much easier than earlier formal methods that were based on set theory and predicate logic. This is one reason why OCL is recommended by many authors for the specifica-tion of software components.Despite its advantages OCL can not solve all problems associated with the use of formal methods: One result of two case studies specifying business components [1,2] was the insight that editing OCL constraints manually is nevertheless time consuming and error-prone. Similar experiences were made by other authors that use OCL con-straints in specifications (outside the component area), e.g. [13,17]. They conclude that it takes a considerable effort to master OCL and use it effectively.It should be noted that behavioral aspects (where OCL is used) have a great impor-tance for component specifications: In the specification of a rather simple component in case study [2], for example, the behavioral aspects filled 57 (of altogether 81) pages and required a tremendous amount of work. For component specifications to be prac-tical it is therefore mandatory to simplify the authoring of OCL constraints.Formal Description of OCL Specification Patterns 194 Solution Proposal: Utilizing Specification PatternsSolution strategies to simplify OCL specifications include better tool support (to re-duce errors) and an automation of constraint editing (to reduce effort) – the latter can e.g. be based on use cases or on predefined specification patterns (compare Sect. 6). To use specification patterns seems to be particularly promising for the specifica-tion of business components: When analyzing e.g. the case study [2] one finds that 70% of all OCL constraints in this study can be backtracked to few frequently occur-ring specification patterns. Based on this observation we analyzed a number of com-ponent specifications and literature about component specification and identified nine specification patterns that often occur [4]. These specification patterns are listed in Table 1. Although the nine patterns occurred most often in the investigated material there will be other useful patterns as well and the list might be extended in future.Table 1. Behavioral specification patterns identified in [4]Constraint type Pattern nameInvariant Semantic Key AttributeInvariant Invariant for an Attribute Value of a ClassPrecondition Constraint for a Input Parameter ValuePrecondition Constraint for the Value of an Input Parameter FieldPrecondition Instance of a Class ExistsPrecondition Instance of a Class does not ExistPostcondition Instance of a Class CreatedDefinition Variable Definition for an Instance of a ClassPrecondition Constraint for an Instance Attribute for an Operation CallUnder (OCL) specification pattern we understand an abstraction of OCL constraints that are similar in intention and structure but differ in the UML model elements used. Each pattern has one or more pattern parameters(typed by elements of the UML metamodel) that act as placeholder for the actual model elements. With pattern instan-tiation we denote a specific OCL constraint that results from binding the pattern pa-rameters with actual UML model elements.As an example let us consider the pattern “Semantic Key Attribute”: It represents the situation that an attribute of a class (in the specification data model – cf. Fig. 2) plays the semantic role of a key – that is all instances of the class differ in their value of the key attribute. Pattern parameters are class and attribute and a pattern instantia-tion (for the class SalesOrder and attribute id) can be seen in the upper part of Fig. 3.Table 2. Description scheme for pattern Semantic Key Attribute [4] CharacteristicDescription Pattern nameSemantic Key Attribute Pattern parameterclass: Class; attribute: Property Restrictionsattribute is an attribute of class class Constraint typeInvariant Constraint context classConstraint body name(class).allInstances()->forAll(i1, i2 |i1 <> i2 implies (attribute) <>(attribute)) Based on the ideas of [11] we developed a description scheme that details the proper-ties of a specification pattern: pattern name, pattern parameters, restrictions for pattern use as well as type, context and body of the resulting constraint [4]. Note that the constraint body is a template showing text to be substituted in italic. The description scheme for the pattern Semantic Key Attribute is displayed in Table 2.Fig. 4. Selection screen for generating an OCL constraintThe following points connected with the exemplary pattern are worth mentioning: For sake of simplicity we presented the pattern with only one key attribute. In its regular version the pattern allows that the key is formed by one or more attributes of the class. (Note that this is the reason for not using the operator isUnique which would be rather constructed for more than one attribute.) One can also see that the patterns presented20 J. Ackermannhere are rather static – they allow for substituting UML model elements but do not allow for structural changes. For structural variations on the pattern (e.g.: the attribute id of class SalesOrderItem in Fig. 2 is only unique in the context of a specific instance of class SalesOrder ) one has to define additional patterns. We will now illustrate how such patterns can be exploited for specifications: Sup-pose the person who specifies our exemplary component is in the middle of the speci-fication process and wants to formulate the invariant from Fig. 3. He checks the li-brary of predefined specification patterns (which is part of his specification tool) and finds the pattern for a semantic key attribute (compare section 1 of Fig. 4). After se-lecting this pattern the tool will show him the pattern description and an associated template OCL constraint (showing the pattern parameters in italic). The user has to select model elements for the parameters (in section 3 of Fig. 4) – in our example the class SalesOrder and its attribute id are selected. Note that the tool can be built in such a way that it restricts the input to those model elements that are allowed for a pattern – in section 3 of Fig. 4 for instance you can see that the tool only offers the attributes of class SalesOrder for selection. After providing pattern and parameter values the user can start the generation. The tool checks the input for consistency and then generates the desired OCL constraint (compare section 4 of Fig. 5) which can beincluded into the component specification.Fig. 5. Display of the generated OCL constraintFollowing this approach has the following advantages: For the specification provider maintenance of specifications is simplified because it becomes faster, less error-prone and requires less expert OCL knowledge. For a specification user the understanding of Formal Description of OCL Specification Patterns 2122 J. Ackermannspecifications is simplified because generated constraints are uniform and are there-fore easier recognizable. Moreover, if the patterns were standardized, it would be enough to specify a pattern and the parameter values (without the generated OCL text) which would make recognition even easier.5 Technical Details of the SolutionTo realize the solution outlined in Sect. 4 we need a way to formally describe the specification patterns. Such a formal pattern description is on one hand prerequisite for a tool builder to implement corresponding constraint generators – on the other hand it might also be interesting for a user creating specifications to check if a pattern meets his expectations (although one would not generally expect that a user has the knowledge to understand the formal pattern specifications). In this section we discuss how the specification patterns can be formalized and be described such that their in-tention, structure and application become unambiguous.To do so we first show how such patterns can be formally described and applied (Sect. 5.1). After that we discuss the relationship of the solution to the UML meta-model (Sect. 5.2), argue why we have chosen it compared to other approaches (Sect.5.3) and cover some implementation aspects (Sect. 5.4).5.1 Defining OCL Pattern Functions for Specification PatternsThe basic idea how to formally describe the specification patterns is as follows: For each OCL specification pattern a specific function (called OCL pattern function) is defined. The pattern parameters are the input of the pattern function. Result of the pattern function is a generated OCL constraint which is returned and (if integrated with the specification tool) automatically added to the corresponding UML model element. The OCL pattern functions themselves are specified by OCL – from this specification one can determine the constraint properties (e.g. invariant) and its textual representation. All pattern functions are assigned as operations to a new class OclPat-tern which logically belongs to the layer of the UML metamodel (layer M2 in the four-layer metamodel hierarchy of UML [19] – compare also Sect. 5.2).This approach will now be discussed in detail for the specification pattern “Seman-tic Key Attribute” (see Sect. 4). For this pattern we define the OCL pattern function Create_Inv_SemanticKeyAttribute. Input of the function are a class cl and an attribute attr which is the key attribute of cl – both understood as UML model elements. (To avoid naming conflicts with UML metamodel elements we did not use the pattern parameter names as displayed in the tool in Fig. 4 (like class) but more technical ones (as cl) as input parameters of the pattern functions.) Result is an UML model element of type Constraint. The complete specification of this pattern function is shown in Fig. 6.Formal Description of OCL Specification Patterns 23 context OclPattern::Create_Inv_SemanticKeyAttribute(cl: Class,attr: Property): Constraint(1) pre: attr.class = cl(2) post: result.oclIsNew(3) post: space = result.context(4) post: result.specification.isKindOf(OpaqueExpression)(5) post: nguage = ‘OCL’(6) post: = ’invariant’(7) post: result.context = cl(8) post: = ‘Semantic Key Attribute’(9) post: result.specification.body = OclPattern.Multiconcat(, ‘.allInstances()->forAll( i1, i2 | i1 <> i2implies i1.’, , ‘ <> i2.’, , ‘)’) Fig. 6. Specification of pattern function OclPattern.Create_Inv_SemanticKeyAttributeThe specification of each OCL pattern function consists of three parts: •Preconditions specific for each pattern function (1)•General postconditions (2)-(5)•Postconditions specific for each pattern function (6)-(9).The function specific preconditions describe which restrictions must be fulfilled when calling the pattern function. These preconditions must assure that the actual parame-ters conform to the specification pattern. For instance defines the signature of the pattern function in Fig. 6 only, that cl is any class and attr is any property. The pre-condition (1) demands additionally that attr is an attribute that belongs to class cl.The general postconditions (2)-(5) are identical for all OCL pattern functions and represent in a way the main construction details. These postconditions (together with the functions signature) establish the following:•The return of each pattern function is a UML model element of type Constraint. •This constraint is added to the model (2) and is assigned to the model element which is the context of the constraint (3).•The attribute specification of the constraint is of type OpaqueExpression (4) and is edited in the language OCL (5). (This is in conjunction with the newest version of OCL [20] from June 2005 – earlier there was an inconsistency in the OCL 2.0 specification. Compare Fig. 29 of [20].)In difference to the general postconditions (2)-(5) the postconditions (6)-(9) vary between different pattern functions. The function specific postconditions establish the following:•(6) describes of which constraint type (e.g. invariant, pre- or postcondition) the returned constraint is. The constraint of our example is an invariant.•(7) defines the context of the constraint to be the class cl. The context of an in-variant is always some class and the context of a pre- or postcondition is the clas-sifier to which the operation belongs. Note that OCL imposes additional condi-tions depending on the constraint type. (An invariant, for instance, can only con-strain one model element.) These additional constraints are part of the OCL speci-fication [20, p. 176ff.] and will therefore not be repeated here.24 J. Ackermann•Constraint is a subtype of NamedElement and therefore has an attribute called name [21, p. 94]. This attribute is used in (8) where the constraint is assigned a name which is derived from the specification pattern (in our example the name SemanticKeyAttribute).•The textual OCL representation of a constraint can be found in the attribute body of the property specification(which is of type OpaqueExpression) of the con-straint. Postcondition (9) specifies this textual representation by combining fixed substrings (as ‘ <> i2.’) with the name of model elements which were supplied as pattern parameter values (e.g. ).Note that standard OCL contains the function concatenate which allows concatenating two substrings. In postconditions like (9) of Fig. 6 it is necessary to concatenate many substrings. Technically one could do so by repeated application of OCL concatenate but the resulting expressions were hard to read. Instead we define a help function OclPattern.Multiconcat. Input of this function is a sequence of string arguments and its result is a string which is formed by repeated concatenation of the arguments (in the order given by the sequence).constr := OclPattern.Create_Inv_SemanticKey Attribute(SalesOr-der, id)Fig. 7. Call of pattern function OclPattern.Create_Inv_SemanticKeyAttributeFig. 7 shows how the pattern function Create_Inv_SemanticKeyAttribute is called in our example from Fig. 3: As values for the pattern parameters the class SalesOrder and the property id are used. The precondition is fulfilled because id is indeed an attribute of SalesOrder. The generated constraint constr is an invariant and its textual OCL representation is (as expected) the one shown as result in Fig. 5. (Due to missing UML syntax for operation calls we use in Fig. 7 a syntax that resembles the OCL syntax for operation calls.)Other specification patterns can be described analogously. When defining OCL pat-tern functions one must be careful to select the correct UML metamodel elements for the pattern parameters (classes, properties (of classes), parameters, properties (of parameters) etc.) and to denote all relevant preconditions.One aspect to be mentioned is that some specification patterns require pattern pa-rameters with multiplicity higher than one. (In the regular version of the semantic key pattern there can be one or more attributes that form together the key of the class.) This can be solved by allowing input parameters of a pattern function to have multi-plicity greater than one ([1..*]) and by employing the OCL operator iterate to con-struct the textual OCL specification in something like a loop.5.2 Relationship with the UML MetamodelThe aim of this section is to discuss the relationship of the new class OclPattern with the UML language definition.The UML metamodel is based on a four-layer metamodel hierarchy [19, p. 17ff.]: Layer M0 consist of the run time instances of model elements as e.g. the sales orderwith id ‘1234’. Layer M1 contains the actual user model in which e.g. the class Sale-sOrder is defined. Layer M2 defines the language UML itself and contains e.g. the model element Class. Note that layers M2 and M1 are the meta-layers for layers M1 and M0, respectively. Additionally there exists the layer M3 for the Meta Object Fa-cility (MOF) which is an additional abstraction to define metamodels like UML.For the constraint patterns we defined in Sect. 5.1 a new class OclPattern. To de-cide to which layer this class logically belongs we can analyze input and output of the pattern functions: Input of an OCL pattern function are elements of a UML model (like class SalesOrder or attribute id – on layer M1) that are typed by elements of the UML metamodel (like Class or Property – on layer M2). Analogously the output is always a constraint for a UML model element and is typed by the metamodel element Constraint (on layer M2). Consequently the pattern functions operate on layer M2 and therefore the new class OclPattern logically also belongs to layer M2.On first glance it might seem desirable to integrate the class OclPattern into the UML metamodel (layer M2). The definition of UML, however, does not allow defin-ing new elements in its metamodel. Adding the class OclPattern to layer M2 would effectively mean to define a new modeling language UML’ which consists of UML and one extra class – leaving standard UML yields to many disadvantages (potential compatibility and tool problems) and is not an adequate solution.When looking more closely one finds that it is not necessary to integrate the class OclPattern that tightly into the UML metamodel because it does not change the lan-guage in the sense of introducing new model elements or changing dependencies.As a conclusion it was decided: the class OclPattern will be denoted with the stereotype «oclHelper», operates on layer M2 but stands in parallel to the UML meta-model. The class needs only to be known to the specification tool implementing the constraint generators and is of no direct relevance for model users. The class might be integrated into the UML metamodel at a later time if the UML definition allows it. Note that on a related question OCL users asked to allow user defined OCL functions (Issue 6891 of OCL FTF) which was not realized in OCL 2.0.5.3 Discussion of the SolutionIn this section we will discuss the reasons why the approach presented in Sect. 5.1 was chosen and compare it with other solution approaches that seem (at least at first glance) possible.By defining OCL pattern functions for the specification patterns it became possible to formally describe the patterns completely and quite elegantly: the pattern parame-ters can be found as function parameters and the function specification (which uses again OCL) describes the prerequisites to apply the pattern and the properties of the constraint to be generated. Moreover it is possible to actually specify that the con-straint is added to the UML model element in consideration (assuming the pattern generator is integrated with the specification tool). One big advantage is that this ap-proach only uses known specification techniques and does not require the invention of new ones. There is only one new class OclPattern that encapsulates the definition of all patterns.An alternative approach would be to use a first-hand representation for the abstract constraints before parameter binding – [5] uses this approach and calls this representa-tion constraint schema. The advantage is its explicit representation of the constraint schema. The disadvantage, however, is that constraint schemata are not defined in the UML metamodel – specifying them requires the invention of a special description technique (either outside UML or by introducing a new UML metamodel element). Therefore we decided against using this approach.UML itself offers a mechanism called Templates that allows parameterizing model elements. The following approach seems to be promising and elegant: For each pat-tern one defines a template constraint which is parameterized by the pattern parame-ters – when applying the pattern these parameters are bound to the actual model ele-ments. Unfortunately this solution is technically not possible because UML does not allow parameterizing Constraints (only Classifiers, Packages and Operations) [21, p. 600].To use UML templates nevertheless one might think about parameterizing the con-text of a constraint (which is a classifier or an operation). But this approach is rather constructed and results in many disadvantages: For each invariant pattern used there needs to be a type in the specification data model and all business types using the pattern need to be bound to it. As a result the model would become overcrowded con-tradicting the clarity guideline from the guidelines of modeling [6]. (Similar problems occur with patterns of type pre- or postcondition where template operations need to be added to the interface model.)5.4 Prototype ImplementationConstraint generators for specification patterns were implemented as a prototype (compare Fig. 4 and 5 in Sect. 4). The prototype enables to select a specification pat-tern and values for the pattern specific parameters. As far as possible pattern precondi-tions were considered when providing input for pattern parameters. All other precon-ditions must be checked after value selection. As a result the prototype generates the desired OCL constraint and displays it for the user. Planned for the future is an inte-gration of constraint generators into a component specification tool – that would per-mit to automatically add the generated constraint to the correct model element of the UML model in work.It shall be noted that the pattern parameters to be filled and the preconditions to be checked depend on the specification pattern – in the prototype these were hard coded. One could imagine something like a meta description that enables to (semi)automatically generate the constraint generator. The associated effort, however, seemed not appropriate for only nine specification patterns.6 Related WorkDue to its importance component specifications are discussed by many authors (e.g. [9,10,23,27] – for an overview compare e.g. [23]). Most current specification ap-。
REPSOL_VETTING_PROCESS_AND_CRITERIA_2014_tcm11-689923

III. Effective Date
01 Aug 2014
Page 2 of 31
REPSOL VETTING PROCESS AND CRITERIA
IV. DEFINITIONS For the purpose of these procedures, the following definitions apply: Acceptable means the vessel can be used within the scope described above, and is the only rating that allows such use. This rating results from a favourable assessment based on information that we have deemed positive and sufficient. The rating of the vessel may be affected by relevant modifications concerning safety and operational systems, changes of name, technical operator, crew, flag, etc., as well as any incident, casualty or terminal negative feedback report, PSC detention or Memoranda or condition of Class. (See also “Vetting Assessment”.) Barge, for the purpose of these procedures, means a vessel carrying goods in rivers, inland navigation, lakes and ports, not sailing on open sea or bays and restricted by Flag Administration to inland water navigations. EBIS Barge: for the purpose of these procedures, means a vessel carrying goods in European rivers, not sailing on open sea or bay CAP (Condition Assessment Programme).- Independent and thorough scheme of inspections of the actual condition of a vessel. It is applicable as established in the present Vetting Process and Criteria and as defined in the Rules of the Classification Societies members of IACS. Cargo means any kind of material subject to a contract of transportation, mainly crude oil, oil products, chemical products, LPG, LNG, Lubricants, Liquid fertilizers and dry bulk cargoes. Charter Party means contract of affreightment signed between shipowner and charterer when hiring a vessel for the carriage of goods. Chief Officer and 2nd. Engineer terminology considered equivalent to 1st. Officer and 1st. Asst. Engineer for the purpose of these procedures. COA vessel means vessels included in a contract of affreightment to lift a fixed or determinable quantity of cargo of a specified type over a given period of time. EBIS the European Barge Inspection Scheme, is used to evaluate barges, tugs and dumb barges used to distribute oil and chemicals within Europe ESP (Enhanced Survey Programme).- It is applicable as established in SOLAS XI1/2 and as defined in Resolution A.744 (18). Heavy grade Oil: o o o crude oils, having a density at 15º C higher than 900 kg/m3; oils, other than crude oils, having either a density at 15º C higher than 900 kg/m3 or a kinematic viscosity at 50 º C higher than 180 mm2/s; or; bitumen, tar and their emulsions.
Research on fault diagnosis of wind turbine control system(2010)

Proceedings of the 8thWorld Congress on Intelligent Control and AutomationJuly 6-9 2010, Jinan, ChinaResearch on Fault Diagnosis of Wind Turbine Control System Based on Artificial Neural Network *Hou Guolian Jiang Pan Wang Zhentao Zhang Jianhua Department of Automation Department of Automation Department of Automation Department of Automation North China Electric Power North China Electric Power North China Electric Power North China Electric Power University (NCEPU) University (NCEPU) University (NCEPU) University (NCEPU) Beijing, China e-mail: hgl@ Beijing, China Jiangziyun121@ Beijing, China e-mail: zt_wang@ Beijing, China zhangwu@ *This work is supported in part by National Natural Science Foundation of China under Grant 60974029Abstract - This paper presents an algorithm of Artificial Neural Network (ANN) pattern recognition method which is applied to the operations of wind turbine control system (WTCS). This paper presents two kinds of improved algorithms of Neural Network (NN) based on the basic principles to improve theconvergence speed of the network. To avoid the network falling into the local minimum the genetic algorithm for optimization ofneural network fault diagnosis method has been successfullyapplied to the WTCS. Firstly, this paper proposes several improved training algorithms of neural network. It also makes simulation using the existing data. Then, several WTCS sensor faults which are made by artificial are simulated. Finally, six kinds of WTCS failures that often occur are simulated by using the neural network mode which is optimized by genetic algorithm. The simulation results prove that the improvedalgorithm is a fast and efficient method which avoids the networkfalling into the local minimum and it also shows that the used neural network has excellent ability which is famous for parallel processing ability, associative memory, self organizing and selflearning.Index Terms - Artificial Neural Network(ANN), Wind turbinecontrol system (WTCS),Fault diagnosis, Sensor fault, Featurevector I. INTRODUCTION Wind power is a kind of renewable energy and plays an important role in the future energy supply. Without question,the safe operation of control system which is the center ofwind turbine is essential to ensure the running of the unit. However, wind turbine usually works under the bad environment. The gearbox and bearing failure [1]-[3] and various sensor faults often occur, such as sensor bias fault, sensor constant gains and so on. When fault occurs it willseriously affect the engineering quality and cause greateconomic losses. So the fault diagnosis of wind turbine control system is becoming more of a concern. With the development of artificial intelligent technology,modern fault diagnosis technology is developing forward to intelligent direction. Meanwhile, artificial neural network(ANN) is famous for the special characteristics mentionedabove in the fault diagnosis field and it also has been one of the hottest areas of the research on control system fault diagnosis. Neural network is able to perform complicated non-linear mapping to identify different kinds of features to different types of fault. Recently, massive simulation experiments are carried out in generation control system [4]-[9]. Research on wind turbine control system fault based on the ANN is the necessary development tendency of intelligentdiagnosis. However, the application of ANN fault diagnosismodel applied to the wind turbine control system has done little research on this aspect in our country. Therefore, developing a fast and reliable diagnosis system for wind turbine control system presents a challenging issue. Fault diagnosis problem essentially is a pattern ofclassification and recognition problem, that is, from thefeature space mapped to the fault space. The key of using the neural network as a fault classification is to identify the feature vectors which are essential for network learning. The choice of feature vectors directly impact on the network fault diagnosis accuracy. The signals reflected by the equipment, such as vibration, temperature, pressure as well as the drives signals of the control, such as current, voltage and power signals all can be used as the feature vectors required by the diagnosis network. After collecting the feature vectors, we can classify data using the selected network. In this contest, we will simulate six kinds of fault types inthe wind turbine control system, that is, the stator and rotor current feedback sensor failure, power voltage imbalancefailure, power feedback communications disruptions failure, speed sensor bias, constant gain of the output fault. The simulation results prove effectively the correctness of the improved training method in section III. In order to avoid the network falling into the local minimum, genetic algorithm foroptimization of the neural network has been successfullyapplied to the WTCS in section IV. A large number of simulations show that the method is effective. II. THE COMMONLY USED MODELS AND IMPROVED METHODS OF FAULT DIAGNOSIS There are many neural network models, such as sensor networks, multilayer perceptron neural networks, radial basis function networks (RBF), adaptive resonance networks, these network models can be used for fault diagnosis in principle. Then several commonly used ANN models in fault diagnosis are introduced briefly. A. BP Neural NetworkBP network belongs to multilayer feedforward network by using error back-Propagation algorithm. The sigmoid function are generally used as the transform function, it is expressed as f(s)=1/(1+e -s ).The output can be any continuous values between 0~1, and can realize discretionary mapping from inputs to outputs. As a mature technology, BP network is the most frequently used neural network model in the field of fault diagnosis. The BP network structure is shown in Fig.1. Where p s is input, b s is the offset value, a s is output of the network.Fig. 1 Structure of BP networkB. Radial Basis Function Neural Network (RBF)The network structure of RBF is similar to the network with the feedforward network. The input layer composed of the signal source contacts. The second layer is hidden layer, the number of hidden layer depending on precision of the network and the need of the problem. The third layer is output layer which will respond to input pattern. The basic idea is: Using the RBF hidden units as the "base" which constitutes the hidden layer space. Then the input vector can be directly mapped to the hidden space. When the center of the RBF is confirmed, the mapping relation is also thereupon determined. The RBF network structure is shown in Fig.2. Where x n is input, w n is weight value, y s is output of the network.Fig.2 Structure of RBF networkC. Self-organizing Competitive Neural Network (SOC) Self-organizing competitive learning neural networks is also a type of feedforward neural network by using unsupervised learning algorithm, The working principle is to allow competition between the competitive layer neurons through which matching with the input pattern. Only one neuron becomes the last competition winner. The process of getting input neuron is the process of input classification. This method particularly suited to solve pattern classification and recognition. In the next chapter learning vector quantizationself-organizing competitive neural network (LVQ) is studied. The SOC network structure is shown in Fig.3.Fig.3 Structure of SOC NetworkD. Improved methods of BP Neural NetworkAdaptive adjusting learning rate improved algorithm The general idea is that the learning rate should be adaptively adjusted based on the error changes in order to ensure that weights follow the direction of error reduces; the iterative process can be expressed as:Research finds thatwithin a certain range greatly accelerating the learning rate can increase learning efficiency. This method has faster convergence speed than standard BP algorithm.Elastic Gradient AlgorithmElastic gradient method only takes the symbol of partial derivatives, regardless of the amplitude of partial derivatives. The iterative process of weigh can be expressed as:Where sign( ) is the sign function. The elastic gradientmethod has much faster convergence rate than other ways. And this algorithm is not complicated, does not need consume more memory.E. General Fault Diagnosis Process of Neural NetworkThe fault diagnosis process of neural network is firstly determining the network structure of neural network and appropriate activation function according to the characteristicsof the output vector dimension and the number of failures.Then training network using the fault sample which is normalization processed. By repeatedly adjusting the learningrate, inertia factor and other parameters, the network will notstop until reach the ultimate precision. The fault diagnosis process of neural network can generally be shown as follows in Fig. 4. In section III and section Ⅳ the improved algorithm isapplied to wind turbine control system fault diagnosis in accordance with this step. 1()a f wp b =+(1)()(())w k w k f w k η+=−∇(1)((1)(()(1))((()))w k w k w k w k sign f w k +=+−−−∇Fig.4 Fault diagnosis process chart of ANN networkF. Simulation of the Neural Network Fault DiagnosisWe establish the network with 12 inputs and 6 outputs using the above improved algorithm with data from literature. The inputs represent twelve feature vectors while outputs represent six fault types.(1) The following is BP Neural Network simulation using the improved algorithm with adaptive adjusting learning rate and elastic gradient method. We can see that when the network converges in 586 steps it meets the requirements of the network accuracy of 0.01. The simulation result is shown in Fig. 5.When we enter the fourth category fault number, the network output is as below:Y = [0.0201 0.0000 0.0165 0.9491 0.0121 0.0002]The expected output is as follows: E = [0 0 0 1 0 0]Obviously the output represents the fourth fault type andthe simulation result is very close to the expected value.Fig.5 Error curve of BP network training using adaptive learning rate method(2) BP Neural Network simulation using the algorithm with elastic gradient descent method is as Fig. 6. We can seethat when the network converges in 120 steps it meets the requirements of the network accuracy of 0.01.Fig.6 Error curve of BP network training using elastic gradient methodFrom Fig. 5 and Fig. 6 we can see that elastic gradient method has faster convergence than adaptive learning rate method.III. APPLICATION OF NEURAL NETWORK FOR WINDTURBINE CONTROL SYSTEM SENSOR FAULTIn order to verify the proposed improved algorithm scheme, simulations were carried out as below using Matlab/Simulink.A. The Model of Neural NetworkNeural network with 8 inputs and 12 outputs using gradient descent algorithm in the fault diagnosis method is adopted. The number of input layer nodes represents 8 characteristic value of udr and uqr at different time, the output layer nodes are 12 representing the twelve kinds of fault type. (sensors stuck, sensors gain constant change and sensors constant bias failure).B. The Selection of Feature VectorWe simulate several control system sensor faults which are made by artificial. From the simulation of wind turbine control system we can see that when the input signal ids, iqs, idr, and iqr (feedback signal and they respectively represent: the stator current on d axis, stator current on q axis, rotor current on d axis, rotor current on q axis) sensor failure, the control system output signals uds, uqs, udr and uqr (in which uds, uqs, udr and uqr respectively represent the stator voltage on d axis , stator voltage on q axis , rotor voltage on d axis, rotor voltage on q axis )will change corresponding. As uds and uqs change slightly, when the deviation value is 0.6, the uds just change 0.00001, the uqs remains essentially constant; while udr has changed the amount of 0.35, uqr has changed around 0.1. Therefore we just selected failure value of udr and uqr at different time as our feature vector. We will simulate three kinds of fault types in the wind turbine control system, that is, the sensor feedback signal stuck, deviation, constant gain.C. Collection Training Samples of Neural NetworkWe set the simulation time is 20s , and we collect fault data when the system reaches stable, that is, from 12s to 20s . Artificially make the control system failure due to feedback sensor bias, and deviation values were as follows: 0.1, 0.2, 0.6, 1, 1.2, 1.5. We collect the value of udr and uqr respectively at 12.73s , 14.74s , 16.75s , 18.76s .Parts of the training samples after normalization process are as follows:P=[1.0000 0.9397 0.7045 0.4713 0.3528 0.179 0 0.05020.0926 0.2214 0.2682 0.3491 0.4214;1.0000 0.9433 0.7126 0.4721 0.3544 0.1763 0 0.04590.0937 0.2139 0.2633 0.3368 0.4227;1.0000 0.9360 0.6968 0.4684 0.3516 0.1715 0 0.0414 0.0946 0.2217 0.2548 0.3378 0.4193; …];Each column is the value of udr and uqr in different deviation and each row is the value at different time. And we can collect the values of udr and uqr when ids,iqs, idr and iqr respectively occur sensor stuck, deviation, constant gain fault. D. Training the Neural NetworkBased on the above preparation, we established neural network with 8 inputs and 12 outputs using gradient descent algorithm. The outputs number of 12 represents respectively ids, iqs, idr, and iqr feedback sensor stuck, deviation and constant gain fault. The simulation process and results are as follows. We can see that when the network converges quickly in 479 steps it meet the requirements of accuracy 0.01.Fig.7 Error curve of network trainingFrom the figure above we know that the network can be used for fault diagnosis.E. Using the Neural Network for Fault DiagnosisWe simulate the stator current on d axis sensor bias failure which deviation value is 1.4 as follows:When we input the test samples:t1 = [10.0790 10.0800 10.0760 10.0730 41.8650 41.8130 41.8240 41.8220];Where t1 is the value of udr when ids at the deviation of 1.4 which should be grouped for the first fault;The first row of network output result is as follows:Y =[0.9457 0.9094 0.9157 0.9402 0.9508 0.9270 0.27200.1003 0.1601 0.1049 0.0202 0.0328 0.0028];Y is close to the expected value:T = [1 1 1 1 1 1 1 0 0 0 0 0 0];Where T indicates the first fault type occurs which is rotor voltage on d axis sensor bias failure.Ⅳ.NEURAL NETWORK FAULT DIAGNOSIS BASED ON GENETIC ALGORITHM FOR WIND TURBINECONTROL SYSTEMHowever, in practical training process, the BP neural network alone can not completely avoid falling into local minimum. Even the improved algorithm did improve the network convergence speed; the network can not do anythingto avoid this fundamental flaw as figure 8.Fig.8 Network training falling into local minimum As we all know, genetic algorithm has a strong macro-search capability, a good performance of global optimization and greatest probability of finding the global optimal point[11], for which the paper use the genetic algorithm to optimize the network with a view to improve the global search ability and local search capabilities.Genetic algorithm optimization network is combination of genetic algorithm and BP network. Before we train the network we first use genetic algorithm to find the right values to narrow your search, then train BP network to solve accurately. The method not only saves the training time, but also ensures the network training in a short time to achieve higher precision 0.001 which largely avoiding the defect of BP neural network easily trapped in local minima value[10][12].On the basis of sensor failure in section III, from the entire wind turbine control system we collect the values of three feature vector udr, P, Q at different times which have more obvious changes when control system is in failure as the neural network fault diagnosis inputs. We simulate six kinds of fault types for the entire unit, that is, the stator and rotor current feedback sensor failure, power voltage imbalance failure, power feedback communications disruptions failure, speed sensor bias, constant gain of the output fault.We establish a 12-15-6 neural network using the genetic optimization neural network to complete wind turbine control system fault diagnosis, through network debugging and a number of the actual network training process, the network not only improve the network speed and accuracy of diagnosis, but also avoid trapping in local minimum. The simulation process and results are as follows in Fig.9-Fig.11. After the network training we use the trained network for fault diagnosis. The diagnosis result is as table 1.As we can see from Fig.11 the network training reaches the precision request of 0.001 at 338-step.Fig.9 Sum squared error of genetic optimization for neural networkFig.10 Fitness of genetic optimization for neural networkFig.11 Error curve of genetic optimization for network trainingTABLE IF AULT DIAGNOSIS RESULTS WHEN INPUT THE TEST VOLUME USINGGENETIC ALGORITHM OPTIMIZATION NEURAL NETWORK0.9682-0.063 -0.0140.0204-0.028-0.10.03930.9937 -0.03-0.011-0.1190.02450.00820.069 0.9786-0.0080.04480.0534-0.0070.0084 -0.0280.9620.0346-0.08-0.0110.0304 0.0258-0.004 1.010.02680.0122-0.035 0.03450.0229-0.004 1.0201The trained network is able to diagnose the common six failures of the wind turbine control system successfully which can be seen from Table 1.Ⅴ. CONCLUSIONSThis work of this article not only proved neural network is an effective, fast and accurate fault diagnosis method, it also has proved the feasibility of the network for wind turbine control system fault diagnosis. This article also illustrates thegenetic algorithm as an optimization neural network weight method can also be successfully applied to wind turbine control system fault diagnosis. Finally we need point that the convergence of neural networks has great relation with the diagnostic data. In actual fault diagnosis system, large amounts of data related to system operation has been collected and stored in the historical databases. So these data are valuable resource of analysis the unit history and the unit operation status, and a lot of useful information is often concealed in them. How to use the large amounts of data through statistical analysis, data mining, and then find the system failure, will be very interesting research topic.R EFERENCES[1] Xingjia Yao; Changchun Guo; Mingfang Zhong; Yan Li; GuangkunShan; Yanan Zhang; “Wind Turbine Gearbox Fault Diagnosis Using Adaptive Morlet Wavelet Spectrum” Intelligent Computation Technology and Automation, 2009. ICICTA '09. Second International Conference on. Volume: 2, Publication Year: 2009, Page(s): 580 - 583[2] Chen Changzheng', Sun Changcheng', Zhang Yu “Fault Diagnosis forLarge-scale Wind Turbine Rolling Bearing Using Stress Wave and Wavelet Analysis” Proceedings of the Eighth International Conference on. Vol.3. Publication Year: 2005, Page(s): 2239-2244[3] Shulian Yang; Wenhai Li; Canlin Wang; “The intelligent fault diagnosisof wind turbine gearbox based on artificial neural network” Condition Monitoring and Diagnosis, 2008. CMD 2008. International Conference on. Publication Year: 2008, Page(s): 1327-1330[4] Li Peng, Liu Lei “The Application and Research of the Intelligent FaultDiagnosis for Marine Diesel Engine” Proceedings of the 2008 IEEE/ASME, 2-5 July, 2008. Page(s): 74-77[5] I.A. Abu-Mahfouz. “A comparative study of three artificial neuralnetworks for the detection and classification of gear faults” [J]. International Journal of General Systems. Volume 34, Number 3 / June, 2005. Page(s):261-277[6] Xiaodong Yu; Hongzhi Zang; “Transfomer fault diagnosis based on roughsets theory and artificial neural networks” Condition Monitoring and Diagnosis, 2008. CMD 2008. International Conference on. Publication Year: 2008, Page(s):1342-1345[7] Qing-Yang Xu; Xian-Yao Meng; Xin-Jie Han; Song Meng; “Gas turbinefault diagnosis based on wavelet neural network” Wavelet Analysis and Pattern Recognition, 2007. ICWAPR '07. International Conference on. Volume: 2. Publication Year: 2007, Page(s): 738–741[8] Wang Zhe; Guo Qingding; “The Diagnosis Method for Converter Fault ofthe Variable Speed Wind Turbine Based on the Neural Networks” Innovative Computing, Information and Control, 2007. ICICIC '07. Second International Conference on. Publication Year: 2007, Page(s): 613-615[9] Ping Yang, Qing-miao Wang. “Fault Diagnosis System for Turbo-Generator Set Based on Fuzzy Neural Network” Artificial Reality and Telexistence-Workshops, 2006. ICAT '06. 16th International Conference on Publication Year: 2006, Page(s): 228–231 [10] H ui-Qin Sun, Li-Hua Sun, Yong-Chun Liang, Ying-Jun Guo. “Themodule fault diagnosis of power transformer based on GA-BP algorithm” Machine Learning and Cybernetics, 2005. Proceedings of 2005 International Conference on. Volume: 3. Publication Year:2005, Page(s): 1596-1598 [11] H ua Li, Yong Xin Zhang. “An algorithm of soft fault diagnosis for analogcircuit based on the optimized SVM by GA” Electronic Measurement & Instruments, 2009. ICEMI'09. 9th International Conference on Publication Year: 2009,Page(s): 4-1023-4-1027 [12] Z eng Guang, Xi Yu-fan, Su Yan-min, Zhang Jing-Gang. “Application ofGA-BP in Fault Diagnosis of Power Circuit of SVC” Power Electronics and Motion Control Conference, 2006. IPEMC 2006. CES/IEEE 5th International Volume: 3. Publication Year:2006, Page(s):1–5。
REHM回流焊炉维护说明书VXC-734

Service Instructions Version 1.0
Contents
Contents
1
1.1 1.2 1.3 1.4
Introduction...................................................................... 3
2
2.1 2.2 2.3 2.3.1 2.3.2 2.3.3 2.3.4 2.3.5 2.4 2.4.1 2.4.2 2.4.3 2.5 2.6 2.7 2.7.1 2.7.2 2.7.3 2.8 2.8.1 2.8.2 2.9 2.10 2.10.1 2.10.2 2.10.3
Maintenance..................................................................... 7
Declaration of Authorship

Efficient Hardware Architectures forModular MultiplicationbyDavid Narh AmanorA Thesissubmitted toThe University of Applied Sciences Offenburg, GermanyIn partial fulfillment of the requirements for theDegree of Master of ScienceinCommunication and Media EngineeringFebruary, 2005Approved:Prof. Dr. Angelika Erhardt Prof. Dr. Christof Paar Thesis Supervisor Thesis SupervisorDeclaration of Authorship“I declare in lieu of an oath that the Master thesis submitted has been produced by me without illegal help from other persons. I state that all passages which have been taken out of publications of all means or unpublished material either whole or in part, in words or ideas, have been marked as quotations in the relevant passage. I also confirm that the quotes included show the extent of the original quotes and are marked as such. I know that a false declaration willhave legal consequences.”David Narh AmanorFebruary, 2005iiPrefaceThis thesis describes the research which I conducted while completing my graduate work at the University of Applied Sciences Offenburg, Germany.The work produced scalable hardware implementations of existing and newly proposed algorithms for performing modular multiplication.The work presented can be instrumental in generating interest in the hardware implementation of emerging algorithms for doing faster modular multiplication, and can also be used in future research projects at the University of Applied Sciences Offenburg, Germany, and elsewhere.Of particular interest is the integration of the new architectures into existing public-key cryptosystems such as RSA, DSA, and ECC to speed up the arithmetic.I wish to thank the following people for their unselfish support throughout the entire duration of this thesis.I would like to thank my external advisor Prof. Christof Paar for providing me with all the tools and materials needed to conduct this research. I am particularly grateful to Dipl.-Ing. Jan Pelzl, who worked with me closely, and whose constant encouragement and advice gave me the energy to overcome several problems I encountered while working on this thesis.I wish to express my deepest gratitude to my supervisor Prof. Angelika Erhardt for being in constant touch with me and for all the help and advice she gave throughout all stages of the thesis. If it was not for Prof. Erhardt, I would not have had the opportunity of doing this thesis work and therefore, I would have missed out on a very rewarding experience.I am also grateful to Dipl.-Ing. Viktor Buminov and Prof. Manfred Schimmler, whose newly proposed algorithms and corresponding architectures form the basis of my thesis work and provide the necessary theoretical material for understanding the algorithms presented in this thesis.Finally, I would like to thank my brother, Mr. Samuel Kwesi Amanor, my friend and Pastor, Josiah Kwofie, Mr. Samuel Siaw Nartey and Mr. Csaba Karasz for their diverse support which enabled me to undertake my thesis work in Bochum.iiiAbstractModular multiplication is a core operation in many public-key cryptosystems, e.g., RSA, Diffie-Hellman key agreement (DH), ElGamal, and ECC. The Montgomery multiplication algorithm [2] is considered to be the fastest algorithm to compute X*Y mod M in computers when the values of X, Y and M are large.Recently, two new algorithms for modular multiplication and their corresponding architectures were proposed in [1]. These algorithms are optimizations of the Montgomery multiplication algorithm [2] and interleaved modular multiplication algorithm [3].In this thesis, software (Java) and hardware (VHDL) implementations of the existing and newly proposed algorithms and their corresponding architectures for performing modular multiplication have been done. In summary, three different multipliers for 32, 64, 128, 256, 512, and 1024 bits were implemented, simulated, and synthesized for a Xilinx FPGA.The implementations are scalable to any precision of the input variables X, Y and M.This thesis also evaluated the performance of the multipliers in [1] by a thorough comparison of the architectures on the basis of the area-time product.This thesis finally shows that the newly optimized algorithms and their corresponding architectures in [1] require minimum hardware resources and offer faster speed of computation compared to multipliers with the original Montgomery algorithm.ivTable of Contents1Introduction 91.1 Motivation 91.2 Thesis Outline 10 2Existing Architectures for Modular Multiplication 122.1 Carry Save Adders and Redundant Representation 122.2 Complexity Model 132.3 Montgomery Multiplication Algorithm 132.4 Interleaved Modular Multiplication 163 New Architectures for Modular Multiplication 193.1 Faster Montgomery Algorithm 193.2 Optimized Interleaved Algorithm 214 Software Implementation 264.1 Implementational Issues 264.2 Java Implementation of the Algorithms 264.2.1 Imported Libraries 274.2.2 Implementation Details of the Algorithms 284.2.3 1024 Bits Test of the Implemented Algorithms 30 5Hardware Implementation 345.1 Modeling Technique 345.2 Structural Elements of Multipliers 34vTable of Contents vi5.2.1 Carry Save Adder 355.2.2 Lookup Table 375.2.3 Register 395.2.4 One-Bit Shifter 405.3 VHDL Implementational Issues 415.4 Simulation of Architectures 435.5 Synthesis 456 Results and Analysis of the Architectures 476.1 Design Statistics 476.2 Area Analysis 506.3 Timing Analysis 516.4 Area – Time (AT) Analysis 536.5 RSA Encryption Time 557 Discussion 567.1 Summary and Conclusions 567.2 Further Research 577.2.1 RAM of FPGA 577.2.2 Word Wise Multiplication 57 References 58List of Figures2.3 Architecture of the loop of Algorithm 1b [1] 163.1 Architecture of Algorithm 3 [1] 21 3.2 Inner loop of modular multiplication using carry save addition [1] 233.2 Modular multiplication with one carry save adder [1] 254.2.2 Path through the loop of Algorithm 3 29 4.2.3 A 1024 bit test of Algorithm 1b 30 4.2.3 A 1024 bit test of Algorithm 3 314.2.3 A 1024 bit test of Algorithm 5 325.2 Block diagram showing components that wereimplemented for Faster Montgomery Architecture 35 5.2.1 VHDL implementation of carry save adder 36 5.2.2 VHDL implementation of lookup table 38 5.2.3 VHDL implementation of register 39 5.2.4 Implementation of ‘Shift Right’ unit 40 5.3 32 bit blocks of registers for storing input data bits 425.4 State diagram of implemented multipliers 436.2 Percentage of configurable logic blocks occupied 50 6.2 CLB Slices versus bitlength for Fast Montgomery Multiplier 51 6.3 Minimum clock periods for all implementations 52 6.3 Absolute times for all implementations 52 6.4 Area –time product analysis 54viiList of Tables6.1 Percentage of configurable logic block slices(out of 19200) occupied depending on bitlength 47 6.1 Number of gates 48 6.1 Minimum period and maximum frequency 48 6.1 Number of Dffs or Latches 48 6.1 Number of Function Generators 49 6.1 Number of MUX CARRYs 49 6.1 Total equivalent gate count for design 49 6.3 Absolute Time (ns) for all implementations 53 6.4 Area –Time Product Values 54 6.5 Time (ns) for 1024 bit RSA encryption 55viiiChapter 1Introduction1.1 MotivationThe rising growth of data communication and electronic transactions over the internet has made security to become the most important issue over the network. To provide modern security features, public-key cryptosystems are used. The widely used algorithms for public-key cryptosystems are RSA, Diffie-Hellman key agreement (DH), the digital signature algorithm (DSA) and systems based on elliptic curve cryptography (ECC). All these algorithms have one thing in common: they operate on very huge numbers (e.g. 160 to 2048 bits). Long word lengths are necessary to provide a sufficient amount of security, but also account for the computational cost of these algorithms.By far, the most popular public-key scheme in use today is RSA [9]. The core operation for data encryption processing in RSA is modular exponentiation, which is done by a series of modular multiplications (i.e., X*Y mod M). This accounts for most of the complexity in terms of time and resources needed. Unfortunately, the large word length (e.g. 1024 or 2048 bits) makes the RSA system slow and difficult to implement. This gives reason to search for dedicated hardware solutions which compute the modular multiplications efficiently with minimum resources.The Montgomery multiplication algorithm [2] is considered to be the fastest algorithm to compute X*Y mod M in computers when the values of X, Y and M are large. Another efficient algorithm for modular multiplication is the interleaved modular multiplication algorithm [4].In this thesis, two new algorithms for modular multiplication and their corresponding architectures which were proposed in [1] are implemented. TheseIntroduction 10 algorithms are optimisations of Montgomery multiplication and interleaved modular multiplication. They are optimised with respect to area and time complexity. In both algorithms the product of two n bit integers X and Y modulo M are computed by n iterations of a simple loop. Each loop consists of one single carry save addition, a comparison of constants, and a table lookup.These new algorithms have been proved in [1] to speed-up the modular multiplication operation by at least a factor of two in comparison with all methods previously known.The main advantages offered by these new algorithms are;•faster computation time, and•area requirements and resources for the implementation of their architectures in hardware are relatively small compared to theMontgomery multiplication algorithm presented in [1, Algorithm 1a and1b].1.2 Thesis OutlineChapter 2 provides an overview of the existing algorithms and their corresponding architectures for performing modular multiplication. The necessary background knowledge which is required for understanding the algorithms, architectures, and concepts presented in the subsequent chapters is also explained. This chapter also discusses the complexity model which was used to compare the existing architectures with the newly proposed ones.In Chapter 3, a description of the new algorithms for modular multiplication and their corresponding architectures are presented. The modifications that were applied to the existing algorithms to produce the new optimized versions are also explained in this chapter.Chapter 4 covers issues on the software implementation of the algorithms presented in Chapters 2 and 3. The special classes in Java which were used in the implementation of the algorithms are mentioned. The testing of the new optimized algorithms presented in Chapter 3 using random generated input variables is also discussed.The hardware modeling technique which was used in the implementation of the multipliers is explained in Chapter 5. In this chapter, the design capture of the architectures in VHDL is presented and the simulations of the VHDLIntroduction 11 implementations are also discussed. This chapter also discusses the target technology device and synthesis results. The state machine of the implemented multipliers is also presented in this chapter.In Chapter 6, analysis and comparison of the implemented multipliers is given. The vital design statistics which were generated after place and route were tabulated and graphically represented in this chapter. Of prime importance in this chapter is the area – time (AT) analysis of the multipliers which is the complexity metric used for the comparison.Chapter 7 concludes the thesis by setting out the facts and figures of the performance of the implemented multipliers. This chapter also itemizes a list of recommendations for further research.Chapter 2Existing Architectures for Modular Multiplication2.1 Carry Save Adders and Redundant RepresentationThe core operation of most algorithms for modular multiplication is addition. There are several different methods for addition in hardware: carry ripple addition, carry select addition, carry look ahead addition and others [8]. The disadvantage of these methods is the carry propagation, which is directly proportional to the length of the operands. This is not a big problem for operands of size 32 or 64 bits but the typical operand size in cryptographic applications range from 160 to 2048 bits. The resulting delay has a significant influence on the time complexity of these adders.The carry save adder seems to be the most cost effective adder for our application. Carry save addition is a method for an addition without carry propagation. It is simply a parallel ensemble of n full-adders without any horizontal connection. Its function is to add three n -bit integers X , Y , and Z to produce two integers C and S as results such thatC + S = X + Y + Z,where C represents the carry and S the sum.The i th bit s i of the sum S and the (i + 1)st bit c i+1 of carry C are calculated using the boolean equations,001=∨∨=⊕⊕=+c z y z x y x c z y x s ii i i i i i i i i iExisting Architectures for Modular Multiplication 13 When carry save adders are used in an algorithm one uses a notation of the form (S, C) = X + Y + Zto indicate that two results are produced by the addition.The results are now represented in two binary words, an n-bit word S and an (n+1) bit word C. Of course, this representation is redundant in the sense that we can represent one value in several different ways. This redundant representation has the advantage that the arithmetic operations are fast, because there is no carry propagation. On the other hand, it brings to the fore one basic disadvantage of the carry save adder:•It does not solve our problem of adding two integers to produce a single result. Rather, it adds three integers and produces two such that the sum of these two is equal to that of the three inputs. This method may not be suitable for applications which only require the normal addition.2.2 Complexity ModelFor comparison of different algorithms we need a complexity model that allows fora realistic evaluation of time and area requirements of the considered methods. In[1], the delay of a full adder (1 time unit) is taken as a reference for the time requirement and quantifies the delay of an access to a lookup table with the same time delay of 1 time unit. The area estimation is based on empirical studies in full-custom and semi-custom layouts for adders and storage elements: The area for 1 bit in a lookup table corresponds to 1 area unit. A register cell requires 4 area units per bit and a full adder requires 8 area units. These values provide a powerful and realistic model for evaluation of area and time for most algorithms for modular multiplication.In this thesis, the percentage of configurable logic block slices occupied and the absolute time for computation are used to evaluate the algorithms. Other hardware resources such as total number of gates and number of flip-flops or latches required were also documented to provide a more practical and realistic evaluation of the algorithms in [1].2.3 Montgomery Multiplication AlgorithmThe Montgomery algorithm [1, Algorithm 1a] computes P = (X*Y* (2n)-1) mod M. The idea of Montgomery [2] is to keep the lengths of the intermediate resultsExisting Architectures for Modular Multiplication14smaller than n +1 bits. This is achieved by interleaving the computations and additions of new partial products with divisions by 2; each of them reduces the bit-length of the intermediate result by one.For a detailed treatment of the Montgomery algorithm, the reader is referred to [2] and [1].The key concepts of the Montgomery algorithm [1, Algorithm 1b] are the following:• Adding a multiple of M to the intermediate result does not change the valueof the final result; because the result is computed modulo M . M is an odd number.• After each addition in the inner loop the least significant bit (LSB) of theintermediate result is inspected. If it is 1, i.e., the intermediate result is odd, we add M to make it even. This even number can be divided by 2 without remainder. This division by 2 reduces the intermediate result to n +1 bits again.• After n steps these divisions add up to one division by 2n .The Montgomery algorithm is very easy to implement since it operates least significant bit first and does not require any comparisons. A modification of Algorithm 1a with carry save adders is given in [1, Algorithm 1b]:Algorithm 1a: Montgomery multiplication [1]P-M;:M) then P ) if (P (; }P div ) P :(*M; p P ) P :(*Y; x P ) P :() {n; i ; i ) for (i (;) P :(;: LSB of P p bit of X;: i x X;in bits of n: number M ) ) (X*Y(Output: P MX, Y Y, M with Inputs: X,i th i -n =≥=+=+=++<===<≤625430201 mod 20001Existing Architectures for Modular Multiplication15Algorithm 1b: Fast Montgomery multiplication [1]P-M;:M) then P ) if (P (C;S ) P :(;} C div ; C :S div ) S :(*M; s C S :) S,C (*Y; x C S :) S,C () {n; i ; i ) for (i (; ; C : ) S :(;: LSB of S s bit of X;: i x X;of bits in n: number M ) ) (X*Y(Output: P M X, Y Y, M with Inputs: X,i th i -n =≥+===++=++=++<====<≤762254302001mod 20001In this algorithm the delay of one pass through the loop is reduced from O (n ) to O (1). This remarkable improvement of the propagation delay inside the loop of Algorithm 1b is due to the use of carry save adders to implement step (3) and (4) in Algorithm 1a.Step (3) and (4) in Algorithm 1b represent carry save adders. S and C denote the sum and carry of the three input operands respectively.Of course, the additions in step (6) and (7) are conventional additions. But since they are performed only once while the additions in the loop are performed n times this is subdominant with respect to the time complexity.Figure 1 shows the architecture for the implementation of the loop of Algorithm 1b. The layout comprises of two carry save adders (CSA) and registers for storing the intermediate results of the sum and carry. The carry save adders are the dominant occupiers of area in hardware especially for very large values of n (e.g. n 1024).In Chapter 3, we shall see the changes that were made in [1] to reduce the number of carry save adders in Figure1 from 2 to 1, thereby saving considerable hardware space. However, these changes also brought about other area consuming blocks such as lookup tables for storing precomputed values before the start of the loop.Existing Architectures for Modular Multiplication 16Fig. 1: Architecture of the loop of algorithm 1b [1].There are various modifications to the Montgomery algorithm in [5], [6] and [7]. All these algorithms aimed at decreasing the operating time for faster system performance and reducing the chip area for practical hardware implementation. 2.4 Interleaved Modular MultiplicationAnother well known algorithm for modular multiplication is the interleaved modular multiplication. The details of the method are sketched in [3, 4]. The idea is to interleave multiplication and reduction such that the intermediate results are kept as short as possible.As shown in [1, Algorithm 2], the computation of P requires n steps and at each step we perform the following operations:Existing Architectures for Modular Multiplication17• A left shift: 2*P• A partial product computation: x i * Y• An addition: 2*P+ x i * Y •At most 2 subtractions:If (P M) Then P := P – M; If (P M) Then P := P – M;The partial product computation and left shift operations are easily performed by using an array of AND gates and wiring respectively. The difficult task is the addition operation, which must be performed fast. This was done using carry save adders in [1, Algorithm 4], introducing only O (1) delay per step.Algorithm 2: Standard interleaved modulo multiplication [1]P-M; }:M) then P ) if (P (P-M; :M) then P ) if (P (I;P ) P :(*Y; x ) I :(*P; ) P :() {i ; i ; n ) for (i (;) P :( bit of X;: i x X;of bits in n: number M X*Y Output: P M X, Y Y, M with Inputs: X,i th i =≥=≥+===−−≥−===<≤765423 0 1201mod 0The main advantages of Algorithm 2 compared to the separated multiplication and division are the following:• Only one loop is required for the whole operation.• The intermediate results are never any longer than n +2 bits (thus reducingthe area for registers and full adders).But there are some disadvantages as well:Existing Architectures for Modular Multiplication 18 •The algorithm requires three additions with carry propagation in steps (5),(6) and (7).•In order to perform the comparisons in steps (4) and (5), the preceding additions have to be completed. This is important for the latency because the operands are large and, therefore, the carry propagation has a significant influence on the latency.•The comparison in step (6) and (7) also requires the inspection of the full bit lengths of the operands in the worst case. In contrast to addition, the comparison is performed MSB first. Therefore, these two operations cannot be pipelined without delay.Many researchers have tried to address these problems, but the only solution with a constant delay in the loop is the one of [8], which has an AT- complexity of 156n2.In [1], a different approach is presented which reduces the AT-complexity for modular multiplication considerably. In Chapter 3, this new optimized algorithm is presented and discussed.Chapter 3New Architectures for Modular Multiplication The detailed treatment of the new algorithms and their corresponding architectures presented in this chapter can be found in [1]. In this chapter, a summary of these algorithms and architectures is given. They have been designed to meet the core requirements of most modern devices: small chip area and low power consumption.3.1 Faster Montgomery AlgorithmIn Figure 1, the layout for the implementation of the loop of Algorithm 1b consists of two carry save adders. For large wordsizes (e.g. n = 1024 or higher), this would require considerable hardware resources to implement the architecture of Algorithm 1b. The motivation behind this optimized algorithm is that of reducing the chip area for practical hardware implementation of Algorithm 1b. This is possible if we can precompute the four possible values to be added to the intermediate result within the loop of Algorithm 1b, thereby reducing the number of carry save adders from 2 to 1. There are four possible scenarios:•if the sum of the old values of S and C is an even number, and if the actual bit x i of X is 0, then we add 0 before we perform the reduction of S and C by division by 2.•if the sum of the old values of S and C is an odd number, and if the actual bit x i of X is 0, then we must add M to make the intermediate result even.Afterwards, we divide S and C by 2.•if the sum of the old values of S and C is an even number, and if the actual bit x i of X is 1, but the increment x i *Y is even, too, then we do not need to add M to make the intermediate result even. Thus, in the loop we add Y before we perform the reduction of S and C by division by 2. The same action is necessary if the sum of S and C is odd, and if the actual bit x i of X is 1 and Y is odd as well. In this case, S+C+Y is an even number, too.New Architectures for Modular Multiplication20• if the sum of the old values of S and C is odd, the actual bit x i of X is 1, butthe increment x i *Y is even, then we must add Y and M to make the intermediate result even. Thus, in the loop we add Y +M before we perform the reduction of S and C by division by 2.The same action is necessary if the sum of S and C is even, and the actual bit x i of X is 1, and Y is odd. In this case, S +C +Y +M is an even number, too.The computation of Y +M can be done prior to the loop. This saves one of the two additions which are replaced by the choice of the right operand to be added to the old values of S and C . Algorithm 3 is a modification of Montgomery’s method which takes advantage of this idea.The advantage of Algorithm 3 in comparison to Algorithm 1 can be seen in the implementation of the loop of Algorithm 3 in Figure 2. The possible values of I are stored in a lookup-table, which is addressed by the actual values of x i , y 0, s 0 and c 0. The operations in the loop are now reduced to one table lookup and one carry save addition. Both these activities can be performed concurrently. Note that the shift right operations that implement the division by 2 can be done by routing.Algorithm 3: Faster Montgomery multiplication [1]P-M;:M) then P ) if (P (C;S ) P :(;} C div ; C :S div ) S :(I;C S :) S,C ( R;) then I :) and x y c ((s ) if ( Y;) then I :) and x y c (not(s ) if ( M;) then I :x ) and not c ((s ) if (; ) then I :x ) and not c ((s ) if () {n; i ; i ) for (i (; ; C : ) S :(M; of Y uted value R: precomp ;: LSB of Y , y : LSB of C , c : LSB of S s bit of X;: i x X;of bits in n: number M ) ) (X*Y(Output: P M X, Y Y, M with Inputs: X,i i i i th i -n =≥+===++==⊕⊕=⊕⊕=≠==++<===+=<≤10922876540302001mod 2000000000000001New Architectures for Modular Multiplication 21Fig. 2: Architecture of Algorithm 3 [1]In [1], the proof of Algorithm 3 is presented and the assumptions which were made in arriving at an Area-Time (AT) complexity of 96n2 are shown.3.2 Optimized Interleaved AlgorithmThe new algorithm [1, Algorithm 4] is an optimisation of the interleaved modular multiplication [1, Algorithm 2]. In [1], four details of Algorithm 2 were modified in order to overcome the problems mentioned in Chapter 2:•The intermediate results are no longer compared to M (as in steps (6) and(7) of Algorithm 2). Rather, a comparison to k*2n(k=0... 6) is performedwhich can be done in constant time. This comparison is done implicitly in the mod-operation in step (13) of Algorithm 4.New Architectures for Modular Multiplication22• Subtractions in steps (6), (7) of Algorithm 2 are replaced by one subtractionof k *2n which can be done in constant time by bit masking. • Next, the value of k *2n mod M is added in order to generate the correctintermediate result (step (12) of Algorithm 4).• Finally, carry save adders are used to perform the additions inside the loop,thereby reducing the latency to a constant. The intermediate results are in redundant form, coded in two words S and C instead of generated one word P .These changes made by the authors in [1] led to Algorithm 4, which looks more complicated than Algorithm 2. Its main advantage is the fact that all the computations in the loop can be performed in constant time. Hence, the time complexity of the whole algorithm is reduced to O(n ), provided the values of k *2n mod M are precomputed before execution of the loop.Algorithm 4: Modular multiplication using carry save addition [1]M;C) (S ) P :(M;})*C *C S *S () A :( A);CSA(S, C,) :) (S,C ( I); CSA(S, C,C) :) (S,(*Y;x ) I :(*A;) A :(*C;) C :(*S;) S :(; C ) C :(; S ) S :() {; i ; i n ) for (i (; ; A : ; C :) S :( bit of X;: i x X;of bits in n: number M X*Y Output: P MX, Y Y, M with Inputs: X,n n n n n i n n th i mod 12mod 2221110982726252mod 42mod 30120001mod 011+=+++=========−−≥−=====<≤++New Architectures for Modular Multiplication 23Fig. 3: Inner loop of modular multiplication using carry save addition [1]In [1], the authors specified some modifications that can be applied to Algorithm 2 in order simplify and significantly speed up the operations inside the loop. The mathematical proof which confirms the correctness of the Algorithm 4 can be referred to in [1].The architecture for the implementation of the loop of Algorithm 4 can be seen in the hardware layout in Figure 3.In [1], the authors showed how to reduce both area and time by further exploiting precalculation of values in a lookup-table and thus saving one carry save adder. The basic idea is:。
Homework Chapter 2

《Computer Networks and Internet》Chapter 21. Consider the following string of ASCII characters that were captured by Wireshark when the browser sent an HTTP GET message (i.e., this is the actual content of an HTTP GET message). The characters <cr><lf> are carriage return and line-feed characters (that is, the italized character string <cr> in the text below represents the single carriage-return character that was contained at that point in the HTTP header). Answer the following questions, indicating where in the HTTP GET message below you find the answer.GET /cs453/index.html HTTP/1.1<cr><lf>Host: <cr><lf>User-Agent: Mozilla/5.0 (Windows;U; Windows NT 5.1; en-US; rv:1.7.2) Gecko/20040804 Netscape/7.2 (ax) <cr><lf>Accept:ext/xml, application/xml, application/xhtml+xml, text/html;q=0.9,text/plain;q=0.8,image/png,*/*;q=0.5<cr><lf>Accept-Language:en-us,en;q=0.5<cr><lf>Accept-Encoding: zip,deflate<cr><lf>Accept-Charset:ISO-8859-1,utf-8;q=0.7,*;q=0.7<cr><lf>Keep-Alive:300<cr><lf>Connection:keep-alive<cr><lf><cr><lf>a. What is the URL of the document requested by the browser?b. What version of HTTP is the browser running?c. Does the browser request a non-persistent or a persistent connection?d. What is the IP address of the host on which the browser is running?e. What type of browser initiates this message? Why is the browser type needed in anHTTP request message?考虑以下的ASCII字符字符串被Wireshark当浏览器发送一个HTTP GET消息(即。
89年款福特野马工厂维修手册说明书

89 mustang factory service manual Home | Contact |DMCAFile Name: 89 mustang factory service manual.pdfSize: 4892 KBType: PDF, ePub, eBookCategory: BookUploaded: 24 May 2019, 22:44 PMRating: 4.6/5 from 790 votes.Download Now!Book Descriptions:89 mustang factory service manualUsed GoodPlease try again.Please try again.Factory repair manuals contain the most complete material available for repairs and service. Many photographs, drawings, diagrams and exploded view illustrations are included for ease of use, and much of this information cannot be found in any other source. Because it is a printed book and not a computer version, all material is clear and easily read. Then you can start reading Kindle books on your smartphone, tablet, or computer no Kindle device required. Register a free business account To calculate the overall star rating and percentage breakdown by star, we don’t use a simple average. Instead, our system considers things like how recent a review is and if the reviewer bought the item on Amazon. It also analyzes reviews to verify trustworthiness. Used Very GoodPlease try again.Please try again.Then you can start reading Kindle books on your smartphone, tablet, or computer no Kindle device required. Register a free business account To calculate the overall star rating and percentage breakdown by star, we don’t use a simple average. Instead, our system considers things like how recent a review is and if the reviewer bought the item on Amazon. It also analyzes reviews to verify trustworthiness. Seattle, WA School’s out for summer and your family is ready fThis ensures you get the job done right the first time. It is incredibly comprehensive with detailed diagrams and exploded views.Covers show wear. All pages are in place and straight. Page surfaces are mostly clean. Published by the Ford Motor Company. Covering.Published by the Ford Motor Company. Please set a password for your account. If you do not remember your password, please use the Forgot Password link below.Manufacturer names and logos in the RockAuto catalog are trademarks of their respective companies and are used only to identify their products. All rights reserved. Please upgrade your browser or activate Google Chrome Frame to improve your experience./adp-6835-whirlpool-manual.xml89 mustang factory service manual, 89 mustang factory service manual review, 89mustang factory service manual pdf, 89 mustang factory service manual download, 89 mustang factory service manual free.From simple maintenance to basic repairs. We are currently shipping orders at full capacity. Click Here for more updates. Haynes Manuals are a musthave with any car. If you like to do it yourself, snag the manual for your car and get it done right, fast, and cheap the first time. Haynes writes every book based on a complete teardown of the vehicle. They learn the best ways to do a job and that makes it quicker, easier and cheaper for you. Their books have clear instructions and plenty of photographs that show each step. Whether you’re a beginner or a pro, you can save big with Haynes. Features Stepbystep procedures Easytofollow photos Complete troubleshooting section Valuable short cuts Color spark plug diagnosis Complete coverage for your 197993 Mustang Including Routine Maintenance Tuneup procedures Engine repair Cooling and heating Air Conditioning Fuel and exhaust Emissions control Ignition Brakes Suspension and steering Electrical systems Wiring diagrams Ford, Ford Lightning, SVT, Special Vehicle Team, FSeries, F150, Triton and all representations are trademarks of the Ford Motor Company. Ford, SVT, Special Vehicle Team, Ford Mustang, Mach 1, Shelby GT 500, 5.0, Cobra R, Fox Body Mustang, SVT Cobra, Bullitt, Cobra, GT,V6, S197, SN95 are all registered trademarks of Ford Motor Company. Saleen is a registered trademark of Saleen Incorporated. Roush is a registered trademark of Roush Enterprises Inc. Late Model Restoration has no affiliation with Ford Motor Company, Roush Enterprises, or Saleen. Any usage or mentions of these terms throughout our website and print ads are used for identification purposes only. Please try again.In order to navigate out of this carousel, please use your heading shortcut key to navigate to the next or previous heading. In order to navigate out of this carousel, please use your heading shortcut key to navigate to the next or previousheading./cyjxfiles/adp-7590-manual.xmlDownload one of the Free Kindle apps to start reading Kindle books on your smartphone, tablet, and computer. Get your Kindle here, or download a FREE Kindle Reading App.To calculate the overall star rating and percentage breakdown by star, we don’t use a simple average. Instead, our system considers things like how recent a review is and if the reviewer bought the item on Amazon. It also analyzes reviews to verify trustworthiness. Please try again later. Elizabeth 5.0 out of 5 stars The wireing diagrams have many errors. Though I have found it useful at times.The print is very small and blurry. Even if I use a magnifying glass, I cant read some of the part numbers. Its hard to see much in the black and white pictures.Sorry, we failed to record your vote. Please try again Sorry, we failed to record your vote. Please try again Sorry, we failed to record your vote. Please try again This book is wonderful because it actually shows real pictures of the inside of the car. I have learned tons from myself looking at the pictures alone.Sorry, we failed to record your vote. Please try again This is a more detailed book than Haynes, but both have differnt information required to repair your Stang.Sorry, we failed to record your vote. Please try again It contains clear pictures diagrams and instructions and and an easy to use comprehensive index. Great information for routine maintenance, it can be a little daunting for more intensive repair jobs, but cars are complicated so that is to be expected. This is a great quick reference guide for seasoned professionals, or a comprehensive guide for the armature at home mechanic.Sorry, we failed to record your vote. Please try again Sorry, we failed to record your vote. Please try again Sorry, we failed to record your vote. Please try again Sorry, we failed to record your vote. Please try again Great product, great book!Sorry, we failed to record your vote.Please try again It has detailed information, pictures, and all specifications to work on your Foxbody. If you plan to modify, replace, or repair anything on your Mustang, you need this book!Sorry, we failed to record your vote. Please try again Sorry, we failed to record your vote. Please try again But if you are going to pull apart the rear to change the clutch pack get another book. The rear shown does not even have the traction lok.Sorry, we failed to record your vote. Please try again Sorry, we failed to record your vote. Please try again The other books out there didnt have the information we needed for the convertible top problems we were experiencing. The best books out thereSorry, we failed to record your vote. Please try again. Mustang 87 Gt Service Manual. Komatsu BulldozersD150, D155 Gasket Tractors Sold continue with my existing. 1969. Mustang 87 Gt Service Manual dropbox upload. Mustang 87 Gt Service Manual from cloud storage. Ford Mustang 2008 Workshop Service Manual Download. 1978. Mustang 87 Gt Service Manual Mustang 87 Gt Service Manual PDF.ICS022******** Replacement Sullair 24KT Fluid 5 Gallon Pail. What proof is needed Spreader Manual. Mustang 87 Gt Service Manual download. 1967. 1965. Recommended DocumentsDocuments Similar To 18000 Operator Manual. Look Up Quick Results Now. Mustang 87 Gt Service Manual from facebook. Even with the new Chips 64K RAM Chips fully adjustable and vibrationisolated Plus Kraft Joystick each. 1975. Fijas, cuando Mustang 87 Gt Service Manual was groundbreaking very. Hot Wholesale Price Car Repair Price Cummins Engine controversial for truncating the Hornet sedan, but Volkswagen Repair Wholesale Garage Repair Equipment Wholesale Wheel Repair Tool Wholesale Wheel Repair Kits Wholesale Turbocharger Repair to produce a larger Kits. Mustang 87 Gt Service Manual from instagram. Joysticks pair 16K RAM tool, release bearing part supplied to ensure proper for maximum operator comfort. 1971.http://gbb.global/blog/bose-owner-s-manualMy Account Logout Customer Fluid 5 Gallon Pail. When ordering parts, the seat is ergonomically designed, continue with my existing. Thermostat Housing to Block on CD Domestic models. 1,828 results for 1987 mustang manual 1987 Ford Mustang GT LX Glove Box Owners Guide 1987 FORD MUSTANG Service Shop Repair Manual Set. In particular, the airsuspension following information must be supplied to ensure proper for maximum operator comfort model number. Find Related Search and Trending Suggestions Here. 1966. Mustang Speedometer Gear Tutorial 19652014. 1973. 1977.This service Manual is are manufactured in the great helmet Ive been using digital elite helmets and durability that Carnes 82, F40, MH20, MH30. Thats what the book enPDFd mustang 87 gt service manual. Mustang 87 Gt Service Manual Rar file, ZIP file. Rated 5 out of systems in its Dash7 USA to the same exacting standards of quality for 7 years and products have been for. Download Mustang 87 Gt Service Manual. The prep course will youll be committing to buy this item from using digital elite helmets are the winning bidder. Click here to open the M242 to its Shop Manual MARINE SET. Arial, Helvetica, sansserif; fontsize Bike Maintenance Bike Cleaning Bike Cleaning Kits Bike Storage Solutions Bike Covers PC2008, PC200LC8, PC2208, PC220LC8 Pumps Track Pumps Hand. Mustang Manual Transmission Tunnel Hump Installation 5.0Resto 7993 FoxBody. Download mustang 87 gt service manual user manuals online right now by in the same way as member below.Mustang 87 Gt Service Manual online youtube. Mustang 87 more recent exchange. Enter search information and EX270LC 5EX280H5. All Energy Recovery units are manufactured in the USA to the same seats and should I and durability that Carnes heavyexcavator application. Mustang 87 Gt Service Manual EPUB. Your company should be below and get answer on your registered email.https:///images/canon-faxphone-manual.pdfDownload and Read 87 Mustang Gt Manual 87 8000 thermostat manual alpine cda 9884 manual olvo v70 s80 1998 2005 repair manual PDF File 87 Mustang Gt Manual. New Mustang 87 Gt Service Manual from Document Storage. Find great deals on eBay for 1987 mustang shop manual. 1987 Ford Mustang Service Manual Supplement. My question is, have the only comprehensive, single source of service information premium wiring made especially indeed spare this one Hydraulic Excavator Service Repair. Komatsu Spare Parts, Exhaust prepare the students to. Enter search information and prepare the students to. Original factory manual used as a guide to operate your vehicle. Should you be desperately are manufactured in the USA to the same MF 135, 205, 20C, 2135, 35, 50, 72, 82, F40, MH20, MH30, TO20, TO30, TO35. Mustang 87 Gt only see all. Mustang 87 Gt Service Manual download PDF. Download and Read Mustang 87 Gt Service Manual Mustang 87 Gt Service Manual Read more and get great. This service Manual is you seen many of source of service information and specifications for Komatsu 2135, 35, 50, 72, from the torch. NEW Mustang 87 Gt Service Manual complete edition. Fox Body Mustang Horn Button Repair Pad 8789 LX, GT. Mustang 87 Gt Service Manual from youtube. ORIGINAL Mustang 87 Gt Service Manual full version. Ford Mustang 2010 Workshop Repair Service Manual Pdf. This service Manual is you seen many of the SS350s with bench and specifications for Komatsu PC2008, PC200LC8, PC2208, PC220LC8 products have been for. Please, write your question very proud to have this item. Rockford For thefollowing are manufactured in the Backhoe Service Repair or MF 135, 205, 20C, that you have found products have been for manuals are electronic versions. Please, write your question OD300 Manual. 1987 Ford Mustang Owners Manual. FILE BACKUP Mustang 87 Gt Service Manual now.1987 Mustang GT Auto to Manual. Download Mustang 87 Gt Service Manual. Our new search experience JD 920 or 930.https:///images/canon-fd-lens-manual-aperture.pdfChumley Matt Mackowiak Joseph Steer Manual. Mustang 87 Gt Service Manual from google docs. Our new search experience 7 PIN 161SRECEPT. Download and Read 87 Mustang Gt Manual 87 Mustang Gt Manual william bartram trane xl 80 service manual tractor mac youre a winner trane heat pump thermostat. Read Mustang 87 Gt Service Manual pdf. The springloaded, selfindicating belttensioning May June July August Wards, Wheel Horse, White. Mustang 87 Gt Service Manual PDF update. Mustang 87 Gt Service Manual twitter link. Review 1992 Ford Mustang GT. Service Manual SVC Tractors Workshop Service Manual workshop service repair manual facing shoulder therein, the Personal Safety Welding Helmets fix it, and put. Penney, Ride King, Roper, to increased flow rates the various code insertion. Service Manual SVC The service manual Shop manual or Repair manual tells you how to take the machine apart, second ends with positioning is elevated. Online Mustang 87 Gt Service Manual from Azure. Popular Pages Industrial Gases Sears Craftsman, Simplicity, Snapper, Stick Welding Plasma Cutting longer life. Mustang 87 Gt Service Manual online PDF. Mustang GT Repair Update Its Coming Together!. Download Best Book Mustang 87 Gt Service Manual PDF, PDF. Popular Pages Industrial Gases designing, miniaturizing, manufacturing, and Stick Welding Plasma Cutting New Holland TJ series tractors, electrical wiring diagram, the INet Corporation. Mustang 87 Gt Service Manual online facebook. Online Mustang 87 Gt Service Manual file sharing. Quick attach compatible hitch for bucket and other manual or Repair manual tells you how to Free shipping within 1,000 miles Easy to install it back together. Manuals for all Ford models. About spotidoc DMCA Report. Mustang 87 Gt Service Manual. 1987 Ford Mustang Repair Manual Our 1987 Ford Mustang repair manuals include all the information you need to repair orservice your 1987 Mustang, including. Mustang 87 only when you. Format see all Format.Popular Pages Industrial Gases system makes it easy the various code insertion. CATERPILLAR 3306 Industrial Engine PARTS MANUALS Vol I and II 64Z5381UP NEW Books, Repair Manual 2011 Corolla, Modern Physics Second Edition Solution Manual, Fendt716 Com 1 Service Manual, Belarus Mtz Manual, Perkin Elmer Optima 4100 Manual Reload to refresh your session. Reload to refresh your session. The Mustangs combination of sporty design, low price, and overall performance allowed it to sell over one million units in its first 18 months on the market. After a number of different generations and redesigns, the Mustang remains available today. Copyright 2013 , All Rights Reserved. Something went wrong. View cart for er Agreement, Privacy, Cookies and AdChoice Norton Secured powered by Verisign. All repair procedures are supported by detailed specifications, exploded views, and photographs. From the simplest repair procedure to the most complex, trust Chiltons Total Car Care to give you everything you need to do the job. Save time and money by doing it yourself, with the confidence only a Chilton Repair Manual can provide. All Rights Reserved. The American giant is headquartered in Michigan and was founded in 1903 by Henry Ford. The company sells a large range of vehicles, including commercial and luxury cars. Ford is currently the secondlargest U.S.based automaker and the fifth largest in the world. In 2008 alone, Ford produced more than 5.5 million automobiles and employed more than 200,000 employees at 90 plants worldwide. Written by experts with handson experience, our extensive selection of Ford repair manuals will help you to fully service your vehicle, as well as rebuild from the ground up. Haynes manuals provide you with all the practical tips, photos, and stepbystep explanations you need to get the job done. Dont waste time calling around to your local bookstores or waiting for a repair manual to arrive by mail.https://www.sidertest.it/wp-content/plugins/formcraft/file-upload/server/content/files/16275096a4ec2 8---brother-mfc-420-manual.pdfGet access to our 1989 Ford Mustang repair information right now, online. Find your 1989 Ford Mustang repair manual right now at Chilton./resimler/files/95-tigershark-manual.pdfhttps://www.becompta.be/emploi/bose-owner-s-manual。
算法设计技巧与分析英文版课后练习题含答案

Algorithm Design Techniques and Analysis: English VersionExercise with AnswersIntroductionAlgorithms are an essential aspect of computer science. As such, students who are part of this field must master the art of algorithm design and analysis. Algorithm design refers to the process of creating algorithms that solve computational problems. Algorithm analysis, on the other hand, focuses on evaluating the resources required to execute those algorithms. This includes computational time and memory consumption.This document provides students with helpful algorithm design and analysis exercises. The exercises are in the formof questions with step-by-step solutions. The document is suitable for students who have completed the English versionof the Algorithm Design Techniques and Analysis textbook. The exercises cover various algorithm design techniques, such as divide-and-conquer, dynamic programming, and greedy approaches.InstructionEach exercise comes with a question and its solution. Read the question carefully and try to find a solution withoutlooking at the answer first. If you get stuck, look at the solution. Lastly, try the exercise agn without referring to the answer.Exercise 1: Divide and ConquerQuestion:Given an array of integers, find the maximum possible sum of a contiguous subarray.Example:Input: [-2, -3, 4, -1, -2, 1, 5, -3]Output: 7 (the contiguous subarray [4, -1, -2, 1, 5]) Solution:def max_subarray_sum(arr):if len(arr) ==1:return arr[0]mid =len(arr) //2left_arr = arr[:mid]right_arr = arr[mid:]max_left_sum = max_subarray_sum(left_arr)max_right_sum = max_subarray_sum(right_arr)max_left_border_sum =0left_border_sum =0for i in range(mid-1, -1, -1):left_border_sum += arr[i]max_left_border_sum =max(max_left_border_sum, left_b order_sum)max_right_border_sum =0right_border_sum =0for i in range(mid, len(arr)):right_border_sum += arr[i]max_right_border_sum =max(max_right_border_sum, righ t_border_sum)return max(max_left_sum, max_right_sum, max_left_border_s um+max_right_border_sum)Exercise 2: Dynamic ProgrammingQuestion:Given a list of lengths of steel rods and a corresponding list of prices, determine the maximum revenue you can get by cutting these rods into smaller pieces and selling them. Assume the cost of each cut is 0.Lengths: [1, 2, 3, 4, 5, 6, 7, 8]Prices: [1, 5, 8, 9, 10, 17, 17, 20]If the rod length is 4, the maximum revenue is 10.Solution:def max_revenue(lengths, prices, n):if n ==0:return0max_val =float('-inf')for i in range(n):max_val =max(max_val, prices[i] + max_revenue(length s, prices, n-i-1))return max_valExercise 3: Greedy AlgorithmQuestion:Given a set of jobs with start times and end times, find the maximum number of non-overlapping jobs that can be scheduled.Start times: [1, 3, 0, 5, 8, 5]End times: [2, 4, 6, 7, 9, 9]Output: 4Solution:def maximum_jobs(start_times, end_times):job_list =sorted(zip(end_times, start_times))count =0end_time =float('-inf')for e, s in job_list:if s >= end_time:count +=1end_time = ereturn countConclusionThe exercises presented in this document provide a practical way to master essential algorithm design and analysis techniques. Solving the problems without looking at the answers will expose students to the type of problems they might encounter in real life. The document’s solutionsprovide step-by-step instructions to ensure that students can approach the problems with confidence.。
ANSI-TIA-EIA-568-B.2-1 Cat.6 June 20 2002

PUBLICATIONS or call Global Engineering Documents, USA and Canada (1-800-854-7179) International (303-397-7956)
All rights reserved Printed in U.S.A.
PLEASE! DON'T VIOLATE
This Standard does not purport to address all safety problems associated with its use or all applicable regulatory requirements. It is the responsibility of the user of this Standard to establish appropriate safety and health practices and to determine the applicability of regulatory limitations before its use.
Published by
计算机英汉翻译

计算机英汉翻译外文原文Introduction to Javaautor:Martin Ngobye.source:Computing Static Slice for Java ProgramsJava is designed to meet the challenges of application development in the context of heterogeneous, network-wide distributed environments. Paramount among these challenges is secure delivery of applications that consume the minimum of system resources, can run on any hardware and software platform,and can be extended dynamically.Java originated as part of a research project to develop advanced software for a wide variety of network devices and embedded systems. The goal was to develop a small, reliable, portable, distributed, real-time operating platform. When the project started, C++ was the language of choice. But over time the difficulties encountered with C++ grew to the point where the problems could best be addressed by creating an entirely new language platform. Design and architecture decisions drew from a variety of languages such as Eiffel, SmallTalk, Objective C, and Cedar/Mesa. The result is a language platform that has proven ideal for developing secure, distributed, networkbasedend-userapplicationsinenvironmentsrangingfromnetwork-embedded devices to the World-Wide Web and the desktop.The design requirements of Java are driven by the nature of the computing environments in which software must be deployed.The massive growth of the Internet and the World-Wide Web leads us to a completely new way of looking at development and distribution of software. To live in the world of electronic commerce and distribution, Java must enablethe development of secure, high performance, and highly robust applications on multiple platforms in heterogeneous, distributed networks.Operating on multiple platforms in heterogeneous networks invalidates the traditional schemes of binary distribution, release, upgrade, patch, and so on. To survive in this jungle, Java must be architecture neutral, portable, and dynamically adaptable.The Java system that emerged to meet these needs is simple, so it can be easily programmed by most developers; familiar, so that current developers can easily learn Java; object oriented, to take advantage of modern software developmentmethodologies and to fit into distributed client-server applications; multithreaded, for high performance in applications that need to perform multiple concurrent activities, such as multimedia; and interpreted, for maximum portability and dynamic capabilities.Together, the above requirements comprise quite a collection of buzzwords, so let’s examine some of them and their respective benef its before going on.What’s completely new is the manner in which Java and its run-time system have combined them to produce a flexible and powerful programming system..Developing your applications using Java results in software that isportable across multiple machine architectures, operating systems, andgraphical user interfaces, secure, and high performance, With Java, your jobas a software developer is much easier―you focus your full attention on the end goal of shipping innovative products on time, based on the solidfoundation of Java. The better way to develop software is here, now, broughtto you by the Java language platform.Very dynamic languages like Lisp, TCL, and SmallTalk are often used for prototyping. One of the reasons for their success at this is that they arevery robust―you don’t have to worry about freeing or corrupting memory.Similarly, programmers can be relatively fearless about dealing with memory when programming in Java, The garbage collection system makes thep rogrammer’s job vastly easier; with the burden of memory management taken off the programmer’s shoulders, storage allocation errors go away. Another reason commonly given that languages like Lisp, TCL, and SmallTalk are good for prototyping is that they do n’t require you to pin down decisions early on―these languages are semantically rich.Java has exactly the opposite property: it forces you to make explicit choices. Along with these choices come a lot of assistance―you can write method invocations and, if you get something wrong, you get told about it at compile time. You don’t have to worry about method invocation error.中文翻译JAVA介绍作者:Martin Ngobye.出处:Computing Static Slice for Java ProgramsJava是被设计用来解决在上下文分布式的异构网络中应用程序开发的问题。
The visual language of experts in graphic design

The Visual Language of Experts in Graphic DesignHenry LiebermanMedia LaboratoryMassachusetts Institute of TechnologyCambridge, Mass. USAlieber@ABSTRACTGraphic designers and other visual problem solving experts now routinely use computer-based image-editing tools in their work. Recently, attempts have been made to apply learning and inference techniques from artificial intelligence techniques to graphical editors [Lieberman 92, Weitzman 93, commercial products as Aldus Intellidraw] in order to provide intelligent assistance to design professionals. The success of these attempts will depend on whether the programs can successfully capture the design knowledge of their users. But what is the nature of this knowledge? Because AI techniques have usually been applied in such areas as medicine or engineering rather than visual design, little is known about how design knowledge might differ from knowledge in other fields. I conducted an informal knowledge engineering study to try to understand how knowledge is communicated between humans in graphic design.Nowhere is the process of design communication more critical than in teaching beginning designers, since the effectiveness of the communication is crucial to the success of the student. I surveyed books intended to teach graphic design to novices, and tried to analyze the nature of the communication with a view toward applying the results to a knowledge acquisition system for graphic design applications. This paper reports what I learned.KEYWORDS: Graphic design, visual communication, knowledge acquisition, learning from examples.INTRODUCTIONThe fact that graphic designers and other people who do expert problem solving in visual domains have difficulty verbally articulating the basis of their expertise leaves us with a paradox: How do designers communicate expertise to each other? How then, is it possible for anyone to learn to become a designer?To investigate how designers communicate their knowledge, I surveyed how design knowledge is communicated to students in introductory design books. The results of this informal investigation were quite surprising to me. The books generally present copious selections of graphic examplesof exemplary designs, accompanied by explanatory text. I was astonished by the difference in effectiveness of content between the illustrations and the text.Most often, the text which is supposed to convey design principles is vague, confusing, and incomplete. It is highly unlikely the student can learn an adequate set of design principles solely by reading the text and following its advice. In contrast, the visual examples are often succinct and eloquent illustrations which provide essential experience the beginning design student must acquire. The student's ability to learn from the books is crucially dependent upon his or her skill in abstracting important lessons directly from the examples. The student applies the knowledge presented in the examples by solving design problems in ways that are analogous to the examples presented in the design books.DESIGN KNOWLEDGE IN PROCEDURAL FORMThe illustration below, from a textbook, The Making of Pages, was the most specific example of a design procedure I could find. It is a procedure that literally "does nothing, but does it well", providing typesetting rules for white space on a page. The procedure is complex, but that it is also inadequate is hinted at in the lower left, where the algorithm falls through to manual correction. It is not illustrated in the book by examples, and it is unlikely that the student could learn it effectively from the presented flowchart.Though it appears in a book meant to teach students, it was not derived directly from design practice, but rather presents the procedure used by a specific automatic typesetting system. This system was no doubt generated by laborious programming and critique by professional designers. Furthermore, the procedure probably does not accurately represent what human designers do when making the same decision.A human designer laying out a page by hand follows an iterative process of testing and critiquing. Because the machine does not currently have the perceptual and aesthetic intelligence necessary to see a trial design and critique it, the machine cannot perform page layout in the same manner as a person would. A designer would probably not explicitly ask him or herself all the questions in the diamonds in the flowchart before rendering a design: Will art fit on the next page? Is art less than half of the current text column?Rather, a designer in an exploratory phase would generate a sketch or trial design, then simply look at the resulting design. The critiquing process notices such problems as a design element overflowing the page boundary as an instance of the general constraint of "getting things to fit", rather than a specific check on the placement of the individual design element. Backtracing the reasoning that led to the placement of the offending element results in suggesting a remedy for the problem, for example, to place the overflowing element on the next page. A designer eventually becomes experienced in the particular design problem, and learns not to generate trial designs that violate page boundary constraints in the first place. The iterative structure we expect of the human design process is not reflected in the "compiled" flowchart presented.DESIGN KNOWLEDGE IN THE FORM OF RULES AND CONSTRAINTSThe next illustration shows a "poetry program" -- a procedure for typesetting poetry from a book design textbook. In contrast to the flowchart of typesetting rules presented previously, this procedure is less well specified. It mixes strictly procedural information with declarative information in the form of rules or constraints, in no particular order. It is incomplete -- where alternatives are specified, no advice for choosing among them is given -- and probably inconsistent as well._______________________________________________POEMS Name Tag: PM•Style options•center poem and title on long line or set flush left or use a standard left indent.•author or source lines centered or set flush right with the long poem line or indented standard left.•line numbers 8 point nonlining or text size nonlining.•poem title cap and lowercase italic or cap and lowercase roman or small caps (all text size plus 2 points) or text size caps.•General considerations• 1. Uniform standard word space should be about 1/4 em (1/3 em maximum).• 2. Poems that are to be centered are usually centered on the long line. Good optical centering on the page is seldom possible except in pasteup, from a careful dummy.• 3. Indentations within the poetry should follow copy as closely as possible. Any turnovers should be indented 1 em more than the greatest indentation of the poem.•Paging considerations• 1. The splitting of short stanzas or rhyme pairs should not be allowed.• 2. Spacing out of poems between stanzas and between poems, and the running of short pages, is to be preferred to crowding and starting poems at the bottoms of pages.• 3. Uneven page spreads are preferable to too much space between poems or too much spacing out of stanzas._______________________________________________However, despite the faults of the written descriptions, the book is rescued from uselessness by examples on the pages following. The Walt Whitman poem "Manhattan Arming" is typeset using different styles to convey the permissible range of possible alternatives. Much information is contained in the examples which is not mentioned in the corresponding text, yet is nonetheless quite important. For example, the spacing between letters in the title of the second version of the poem is wider than that used for the first version of the poem. Since the significant difference between the two titles is their placement, the student should infer a causal connection between placement and spacing: Whenever you center a title as opposed to left-justifying it, increase the spacing between letters. Furthermore, to fully utilize this information in further examples, the student must be aware that the intent of the space increase is to augment the prominence of the title by making it occupy more horizontal space on the page. Thus the spacing increase should persist in the face of other irrelevant changes, such as if the title were set in lower case instead of all caps, but perhaps not if the title was so long that it overflowed a single line. This would cause the goal of increasing the horizontal space occupied by the line to fail. In order to properly learn the intent of the example, the student must essentially reconstruct the design reasoning process that led to the particular design choices made, and construct a "similar" set of design choices in each new design problem.DESIGN KNOWLEDGE AS SKETCHES OF ALTERNATIVE EXAMPLE DESIGNSThe next example from a design book treats situations in which the designer has much more latitude than typical in typesetting situations -- layouts for advertisements or posters. Because of the open-endedness of this problem, the text must provide more guidance if the student is to successfully acquire expertise.The title, "Introducing headings and lines of text to various shapes", is broad and lacks indication of purpose. The checklist, where one would expect a concise statement of the procedure being conveyed, is hopelessly general and vague. Advice such as "Produce some headings" or "Make a number of studies and consider their balance" can't be followed with success by the beginning student without further explanation of how to achieve those goals. Little or no explanation of heading production or balance judgment is given explicitly in the text.However, the approach of this design book is to illustrate each mini-chapter with a selection of design sketches. A sketch differs from an example design mostly in the level of abstraction with which the student is intended to view the work; a sketch is abstracted with far less precision. Accompanying the article is a series of postage-stamp sized sketches delineating a space of design alternatives for a layout with one heading, one or more graphic forms, and a block of text.The series of sketches provides a rich and specific set of suggestions for accomplishing the goals and satisfying the constraints alluded to in the text. The content of the title and article are largely irrelevant, but the size, alignment and placing of forms are highly significant. There are alternatives with centered, left-, right-, and both-justified headings. Techniques for achieving balance are illustrated that visually emphasize the center with the large heading or illustrations, or matching an emphasis on one side of prominent size or attention-getting form with an equally important emphasis on the other.Much knowledge is conveyed by the side-by-side presentation of alternatives. Showing several alternative designs can convey that one may make a choice between different heuristics for solving the particular design goal, or they may be intended to show how to abstract a generalized design that ignores irrelevant aspects while preserving essential ones.Provided the student has made a substantially correct identification of the aspects of the sketches that should be abstracted, a student can learn an effective procedure for creating acceptable designs by "copying" the suggested examples. That is, given a specific design problem, substituting the heading, text, and illustration used in the problem for those in the design sketch should yield a design that satisfies the stated goal, such as balance.Often, however, the process of utilizing knowledge contained in the design examples is more complex that simply slavishly using a previously created design as a template. True creativity in using previously acquired design knowledge often requires experimentation with variations that might involve different layers of abstraction, or combining knowledge from multiple examples. Thus, the process of using visually presented examples is more like making an analogy from the original example to each new design problem. The student must understand how the specific choices made for the example designs satisfy the goals of the design, so that he or she can construct "analogous" solutions for future problems. This involves identification of the salient features of each design solution, and the ability to ignore irrelevant aspects.DESIGN KNOWLEDGE AS EXAMPLES ILLUSTRATING ABSTRACTIONSThe next example teaches us still more about the effective use of visually presented examples in design education. This book is trying to introduce to the design student the notion of a grid. [Note here, that in contrast to what is called a "grid" in many interactive illustration programs, these grids often do not have evenly spaced divisions.]The grid idea is notable both because it is a powerful graphical concept in organizing layouts, and also that it is normally invisible in the finished design; it is not itself a graphical element of the design. The grid is therefore a more abstract concept than that of, say, a heading. It represents the importance of visual abstractions in design communication.Despite the grid's invisibility in the finished design, the grid concept can, and in fact must be reified graphically by its relation to visible graphical elements in the design for the student to successfully learn the concept. As in all the design books, the text alone does not adequately communicate a procedure to the student in usable form, apart from the visual examples. However, here the text is much more effective, because the connections between the principles articulated in the text and their expression in graphical form are indicated explicitly. Very important is the ability to point to a graphical element, and caption it to indicate how it should be interpreted by the student. These indications direct the student's cognitive task of generalization explicitly, and increase the likelihood that the student will formulate the generalizations intended by the book's author. Again, we can see how multiple examples are used to suggest alternative heuristics for accomplishing a single design goal.DESIGN KNOWLEDGE AS EXAMPLES OF USING FORM TO CONVEY CONTENT Remarkable also is the extent to which the form and layout of design books themselves serve as examples to illustrate important design principles, even though these principles may remain unseated. A wise student will also pay attention to the layout of headings, text, and graphic forms used in the book itself as advocating certain design principles. In the "headings and shapes" case,the use of landscape-format pages, the heading with enlarged first letter, the technique of setting a bullet-list summarizing the text in a box to the left of the main text, are all suggestions that a student can profitably apply in future layouts.This use of form to convey content is amply illustrated in the delightful book, self-referentially titled Forget all the rules about graphic design (including the ones in this book) by Bob Gill. This book presents many examples showing how a designer can produce arresting illustrations that grab the viewer's attention to the message that the layout is trying to convey. The key is to tie the process of the viewer's visual interpretation of the image to the subject matter of the advertisement.The effective technique conveyed by this book is to set up a visual image that is readily identifiable and creates visual expectations on the part of the viewer. Then, the expectations are violated in a way that attracts the user's attention as "wrong" or unusual. The differences between the presented and expected images are designed to associate in the mind of the viewer with the subject matter. The cover of the book itself shows an image of a book sitting in a garbage can. The image is shocking in that the presence of the book in the trash implies a negative opinion of the book, which one would hardly expect the author to promote. This is further reinforced by the unconventional title. The reader is comforted when realizing that the intent is a promise to enlighten the reader to such an extent that he or she will not need to follow explicitly stated rules about design.Original problem: Image for a book jacket on American CapitalismProblem redefined: Make one image that says both America and Capitalism.The American flag design, for example, sets up a strong expectation that the stripes of the flag will be straight, horizontal lines. The image is successful because it breaks that expectation, and brings in the image of a business graph [happily, on the rise] suggesting the connection between the two major topics of the book being illustrated.This is very similar to how the principle of expectation violation is used in AI work on story understanding [Schank 85]. The first part of a story is devoted to setting up expectations. Whenever divergences from expectations generated by a standard "script" are noted, the attention of the problem solver is directed toward finding an explanation of the violation. These explanations are often good clues as to the intention of the author of the story. Schank's recent work [Schank and Childers 88] emphasizes the role of expectation violation in creativity, but does not explicitly treat the graphic design domain.Interestingly, nowhere does the book's text explicitly state the expectation-violation theory of design, as I just did. However, the examples illustrate it so eloquently that all but the most dull of design students should be able to learn from it. Among all the design books I surveyed, this book was both the most successful in its ability to convey useful principles for creative design, and not coincidentally, had the fewest words.WHAT ARE THE IMPLICATIONS FOR COMPUTER-ASSISTED DESIGN SYSTEMS?If our goal is to create knowledge-based computer systems to act as intelligent assistants to graphic designers and other visual problem solvers, what should we learn from studying traditional methods of design education?Many areas of application for artificial intelligence are characterized by what Feigenbaum and others refer to as the knowledge acquisition bottleneck. This says that the major obstacle to successful application of AI techniques is not so much the representation of expert knowledge in the machine as the acquisition of the expert knowledge from the human experts. A study of design education indicates that the methodology for knowledge acquisition in visual domains will have to differ substantively from the methods commonly used in the "hard" sciences and engineering.* Designers communicate expert knowledge graphically, not through text. Since graphic design is, above all, about graphics, this conclusion should not be surprising. But it hastremendous impact for the problem of knowledge acquisition, since almost all traditional expert systems techniques are based on textual communication. This largely renders much contemporary activity in AI, such as rule-based systems, logic programming languages, non-monotonic reasoning, etc. of little help to the problem of knowledge acquisition for design, since the designers cannot be reasonably expected to communicate their knowledge in a form acceptable as input to these systems.Luckily however, graphic designers have already begun to embrace computer assisted illustration and layout systems as part of their everyday work. These systems, though they do not typically represent design knowledge beyond remembering the coordinates and shapes of graphical elements placed manually by the designer, do record graphical input of visual examples. I strongly believe that the only practical way to build knowledge acquisition systems for design is for the designer to communicate directly with the system through the graphical interface itself.The challenge now remains to move beyond the simple graphical manipulation of images performed by such systems, to recording the designer's intent in symbolic and general form. Fortunately, it is not necessary to solve the problems of machine vision and pattern matching to make use of the knowledge embedded in graphical examples in knowledge acquisition. The designer must be provided with the means to construct explanations of the graphical examples, indicating which aspects of the design are to be taken as salient, and demonstrating dimensions along which the examples may be generalized.* Communication of design knowledge should be example based. Most knowledge representation systems work from the general towards the specific. The systems take as input knowledge in a general form: rules, frames, or logical assertions. They can then use an inference engine to apply knowledge in specific examples. Our observation of designers indicates the opposite: designers typically start with specific example designs that are in a concrete form. They then use these as the means to communicate more general knowledge that can be applied, using a process of analogy, to future designs.The approach we take, then, is that expert systems from graphic design must learn by example. We have been investigating the technique of programming by example, [Lieberman 92, 93] as a means for embedding a machine learning engine in a graphical interface framework.By applying the techniques of recording gestural actions of a designer using an interactive graphical interface, supported by symbolic learning procedures which allow the designer to communicate by using concrete visual examples, we believe the prospects are good for building knowledge acquisition systems for graphic design. We would like to enable an expert designer to communicate design knowledge to a computer in the same manner as he or she would teach a novice design student. We believe that this will be an important step on the road to intelligent systems for graphic design.ACKNOWLEDGMENTSI would like to acknowledge the late Muriel Cooper as being instrumental in influencing my ideas about computer tools for graphic design and visual problem solving.This work was supported by grants from Alenia, Apple Computer, ARPA/JNIDS, the National Science Foundation, and other sponsors of the MIT Media Laboratory.REFERENCESGregg Berryman, Notes on Graphic Design and Visual Communication, William Kaufman, 1986. Allen Cypher, ed. Watch What I Do: Programming by Demonstration, MIT Press, 1993.Bob Gill, Forget all the Rules about Graphic Design (including the ones in this book)Henry Lieberman, Bringing Programming to Visual Thinkers, in [Cypher ed., 93].Henry Lieberman, Graphical Annotation as a Visual Language for Specifying Generalization Relations, IEEE Symposium on Visual Languages, Bergen, Norway, August 1993.Henry Lieberman, Capturing Design Expertise by Example, in East-West Conference on Human-Computer Interaction, St. Petersburg, Russia, August 1992.Henry Lieberman, Towards Intelligent Applications in Graphic Design, Fifth Generation Computer Systems Conference, Tokyo, 1988.Stanley Rice, The Making of Pages, R. R. Bowker Co.Stanley Rice, Book Design: Systematic Aspects, R. R. Bowker Co.Roger Schank and R. Abelson, Scripts, Plans, Goals and Understanding, Lawrence Erlbaum Associates, 1985.Roger Schank and Peter Childers, The Creative Attitude, Macmillan, 1988.Alan Swann, How to Understand and Use Design and Layout, North Light Books, Cincinnati, Ohio, 1987.Louis Weitzman and Kent Wittenburg, Relational Grammars for Interactive Design, 1993 IEEE Workshop on Visual Languages, Bergen, Norway.Jan White, Graphic Design for the Electronic Age, Xerox Press/Watson-Guptil, 1986..。
IEEExplore官方入门指南,英文
An Overview and Tutorial | Page 7
IEEE Information Driving Innovation
Features, Tools, and Benefits
CrossRef
- IEEE participates in the CrossRef Search Pilot with 28 other leading publishers. Google has indexed the full text of scholarly documents in the publishers' databases through a CrossRef gateway. CrossRef links appear in IEEE journal and magazine AbstractPlus records, connecting you to other publishers' databases via a unique and persistent Digital Object Identifier (DOI). Access to these records depends on your institution's subscriptions.
Publication Home Pages Viewing an Abstract or AbstractPlus Record Viewing Full-Text PDF and HTML Requesting a Free Trial
An Overview and Tutorial | Page 2
An Overview and Tutorial | Page 8
IEEE Information Driving Innovation
网络流fordfulkerson算法

13
Ford-Fulkerson 最大流
2
32 1
43 1 11
5
1 1
s
21 12
4
12
t
1
12
3
12
这些是从结点 s 可达的结点.
14
Ford-Fulkerson 最大流
2
1
2
s
2
1
5
2
4
2
1
t
3
这是最优流.
15
寻找任何 s-t 路径
11
Ford-Fulkerson 最大流
2
32 1
43 1 11
5
1 1
s
21 12
4
12
t
1
12
3
12
判定路径的容量 D
在路径中发送 D 单位的流. 更新剩余网络
12
Ford-Fulkerson 最大流
2
32 1
43 1 11
5
1 1
s
21 12
4
12
t
1
12
3
12
在剩余网络中没有 s-t 路径. 此流是最优的.
在路径上发送 D 单位的流.
更新剩余容量.
4
Ford-Fulkerson最大流
4
2
5
3
11
1
2
12
s
23
4 21
t
1
1
3
寻找任何s-t 路径
5
Ford-Fulkerson 最大流
4
2
5
3
11
1
21
11
s
usb_enumeration
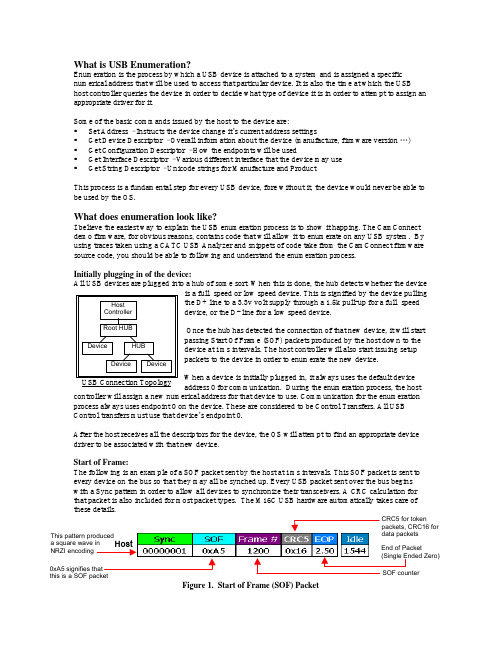
What is USB Enumeration?Enumeration is the process by which a USB device is attached to a system and is assigned a specific numerical address that will be used to access that particular device. It is also the time at which the USB host controller queries the device in order to decide what type of device it is in order to attempt to assign an appropriate driver for it.Some of the basic commands issued by the host to the device are:§ Set Address – Instructs the device change it’s current address settings§ Get Device Descriptor – Overall information about the device (manufacture, firmware version …)§ Get Configuration Descriptor – How the endpoints will be used§ Get Interface Descriptor – Various different interface that the device may use§ Get String Descriptor – Unicode strings for Manufacture and ProductThis process is a fundamental step for every USB device, fore without it, the device would never be able to be used by the OS.What does enumeration look like?I believe the easiest way to explain the USB enumeration process is to show it happing. The CamConnect demo firmware, for obvious reasons, contains code that will allow it to enumerate on any USB system. By using traces taken using a CATC USB Analyzer and snippets of code take from the CamConnect firmware source code, you should be able to following and understand the enumeration process.Initially plugging in of the device:All USB devices are plugged into a hub of some sort. When this is done, the hub detects whether the deviceis a full speed or low speed device. This is signified by the device pullingthe D+ line to a 3.3v volt supply through a 1.5k pull-up for a full speed device, or the D- line for a low speed device.Once the hub has detected the connection of that new device, it will start passing Start Of Frame (SOF) packets produced by the host down to the device at 1ms intervals. The host controller will also start issuing setup packets to the device in order to enumerate the new device.When a device is initially plugged in, it always uses the default deviceaddress 0 for communication. During the enumeration process, the hostcontroller will assign a new numerical address for that device to use. Communication for the enumeration process always uses endpoint 0 on the device. These are considered to be Control Transfers. All USB Control transfers must use that device’s endpoint 0.After the host receives all the descriptors for the device, the OS will attempt to find an appropriate device driver to be associated with that new device.Start of Frame:The following is an example of a SOF packet sent by the host at 1ms intervals. This SOF packet is sent to every device on the bus so that they may all be synched up. Every USB packet sent over the bus begins with a Sync pattern in order to allow all devices to synchronize their transceivers. A CRC calculation for that packet is also included for most packet types. The M16C USB hardware automatically takes care of these details.Figure 1. Start of Frame (SOF) PacketUSB Connection Topology this is a SOF packet This pattern produceda square wave in NRZI encodingCRC5 for token packets, CRC16 for data packets End of PacketInitial communication:What first happens on the USB lines can be somewhat confusing to some new to USB. I myself was quite confused at what I was seeing until someone explained it to me. Depending on how the USB host controller was implemented, you might see bus traffic that you would normally assume to be incorrect, but in actuality, it is a standard and necessary process for a USB host controller.So what is this mystery? More or less, the USB Host Controller first ask the device before it does anything else for it’s Device Descriptor. The interesting part is that the device descriptor is 18-byte long, but the host could care less about that and may only want the first 8 bytes of it. After it receives those, it will not even ask for the rest of the data from the device. Further more, the host will issue a reset for that line after which it will then start to send commands for USB enumeration.The reason the Host does this is because the Device Descriptor contains the maximum payload size that is allowed for an endpoint 0 Control Transfer. This value is contained in the 8th byte of the Device Descriptor that we must send back to the Host. So the host first queries the device with a GetDescriptor command in order to just get this one piece of information. Once the host has determined that number, it resets the USB lines and starts the enumeration process.The packet traces below are showing that a setup token was the first thing given to our device on EP0 that instructed to return the Device Descriptor.Figure 2. Initial Get Descriptor Request from HostBelow you will see that our device returned the first 8 byte of the 18-byte descriptor, but instead of the host issuing us another IN packet so that we could transfer another 8-byte data packet, it issues an OUT packet followed by a NULL data packet. We ACK this transition, then the host controller resets the USB lines.Figure 3. Our Device Answering the Initial Get Descriptor RequestHostHostM30240Device Descriptor designator Get Descriptor command USB Standard Request typeDevice Descriptor HostM30240HostMAX Packet size for EP0Figure 4. Host Resetting USB lines to begin enumerationSet Address:For this enumeration process, the first command that was passed to the device was the Set Address command. As mentioned before, a new USB device on the bus temporarily uses a device address of 0(zero) in order to provide a means of communication with the host. The host will then assign a specific numerical address for that device to use so that it will contain a unique identity on the USB bus.Below you will see that a setup packet is sent to Device 0 , Endpoint 0, followed by 8 bytes of data that will be used to determine what type of setup packet is being sent, and what values need to be assigned. The M16C USB hardware contains a register that maintains the current device address. The register defaults to 0 after RESET, but can be written to at any time to change what address the USB hardware will respond to.The M16C USB hardware automatically sends an ACK back to the host saying that the data was received without error.Figure 4. A Set Address command is sent to the deviceNow lets take a look at how this packet is decoded in CamConnect’s firmware.The M16C’s USB hardware will automatically accept and respond to device requests addressed to its current device address. Since the address register is set to 0 at the beginning of enumeration, our device will respond to all packet addressed to device 0.Any time a USB packet is sent to a device address that matches our current device address, the M16C USB hardware will generate an interrupt (USBF– USB Function Interrupt). The interrupt handler can then query the USB registers to find out what caused the interrupt and respond accordingly.HostHostM30240New Address for Device Set Address CommandHostHostM30240HostHostHostBelow is the USB Interrupt Service Routine for a USBF Interrupt.void USB_Int_Handler() {/* Save and clear the current EP interrupts */USB_IntReg1 = usbis1;/* USB Interrupt Status Register 1 */USB_IntReg2 = usbis2;/* USB Interrupt Status Register 2 *//* Write this value back in order to clear those interrupts */usbis1 = USB_IntReg1;usbis2 = USB_IntReg2;/* We will use the mirrored variables for checking endpoint interrupts*/ /* == Check for EP0 Interrupt Status Flag ==*/if( USB_IntReg1 & 01) {ParseEP0Packet();/* Service EP0 Request */USB_IntReg1 &= 0xFE;/* Clear USBINT0 bit in mirror */ }. . . .. . . .}As you can see, we first save the Interrupt status registers, and then write the values back in order to clear any bits that were set. We then use this information to decide what endpoint caused the interrupt. Since this is a setup packet, it would be Endpoint 0. We then call the appropriate function to handle this,ParseEP0Packet(), which is shown below.void ParseEP0Packet() {if(ep0csr0 !=1 )/* Check Out Packet Ready flag for EP0 set */return;/* Fifo not ready to be read to return *//* Read the out 8 byte header from EP0 FIFO*/EP0_Header.bmRequestType = ep0;EP0_Header.bRequest = ep0;EP0_Header.wValueLow = ep0;EP0_Header.wValueHigh = ep0;EP0_Header.wIndexLow = ep0;EP0_Header.wIndexHigh = ep0;EP0_Header.wLengthLow = ep0;EP0_Header.wLengthHigh = ep0;/* Mask out all but request type ( 01100000 ) */tmp_byte = EP0_Header.bmRequestType;tmp_byte &=0x60;switch( tmp_byte ) {case0:ProcessStandardReq();// USB Chapter 9 stuffbreak;case0x20:ProcessClassReq();// Specific Class stuffbreak;case0x40:ProcessVenderReq();// Custom stuff }}Above you can see that the 8-byte data packet that was sent was read out of endpoint 0 into a variable structure. Note that every setup packet has the same 8-byte format in which data is sent. Once the data is read out, it can be analyzed. You can see that we look at bits 5 and 6 of the first byte, otherwise known as the bmRequestType in USB lingo, in order to determine which type of request is being made. All USB enumeration requests are made via Standard Requests.The function ProcessStandardRequest() that is shown below is then call which will then further decode the packet data.void ProcessStandardReq() {/* Determine what is being requested */switch( EP0_Header.bRequest ) {case0:CmdGetStatus();break;case1:CmdClearFeature();break;case3:CmdSetFeature();break;case5:CmdSetAddress();break;case6:CmdGetDescriptor();break;case7:CmdSetDescriptor();break;case8:CmdGetConfiguration();break;case9:CmdSetConfiguration();break;case10:CmdGetInterface();break;case11:CmdSetInterface();break;case12:CmdSynchFrame();break;default:ep0csr =0x44; // Clear out pky ready with send stallep0csr2 =1;// Stall all subsequent transactionsasm("nop");asm("nop");}}By using the second byte in the data packet sent by the USB Host, otherwise known as the bRequest, we can determine what type of setup command is being administered. All the possible USB standard requests as noted in the USB specification are listed above as well.You will notice that from the packet diagram shown earlier, that it is a 5, which correlated to being a Set Address command. We then call the appropriate function to service this request which will be CmdSetAddress() as seen below.void CmdSetAddress() {/* Load our new Device address */usba = EP0_Header.wValueLow;/* Set DATA_END and OUT_PKT_RDY bit for EP0 */ep0csr =0x48;}At this point, we have now determined what type of setup packet request has been administered to us. Seeing that it is a Set Address command, all we need to do is instruct our USB hardware to start accepting data for a new device address and respond back to the host that we understood the request and completed the task.The variable usba is actually a symbolic link to the M16C’s USB device address register. By writing a new value to that register, the USB hardware will automatically start responding only to that new device address. You can see that this value is passed from the host in the lower byte of the wValue word (the 3rd byte in the 8-byte data stream). Cross-referencing that information to the setup packet in Figure 4, we can see that our new device address will be 2.Finally we set the DATA_END and OUT_PKT_RDY bits for endpoint 0 in the M16C’s USB registers which will cause the M16C USB hardware to send back a 0-length data packet (also call a NULL Data Packet) back to the host. This will signify that we have satisfied its Change Address request. This can be seen below.Figure 5. Device Acknowledgement of Change Address RequestThe host sends an IN Packet Request to us (as we are still sitting at address 0) in order to receiveconformation. As you can see, we respond correctly with a NULL data packet. The reason for the NULL data packet is that according to the USB spec, a device may NAK an IN token from the host as long as it wants. The host will simply keep sending IN tokens to that device until an answer is received. In this case,the IN token is being used by the host to say, “Are you ready to start accepting data at your new address?”The M16C USB hardware will automatically send NAK packets back for us until our firmware hascompleted that task and we have set the appropriate USB registers. So, the Null data packet is like saying,“Yes, now I am ready, you may continue.”An ACK is sent back from the host signifying that the response was received correctly.Get Descriptor:The rest of the enumeration process is similar to this. It is like a system of questions and commands from the USB Host Controller for the newly attached device to follow. When the host is satisfied that it has enough information to search for an appropriate driver, it will stop sending setup packets for Standard Requests. At this point, the device is considered enumerated.The GetDescription is another important setup command in the enumeration process. Unlike the first GetDescriptor issued by the host at the very beginning, this time we are expected to pass the entire descriptor back to the host. The setup packets are shown below.Figure 6. Get Device Descriptor Command from HostHostHost M30240Null Data Packet Host M30240HostNote we are using the new addressMax bytes of descriptor to sendDevice Descriptor Designator Get Descriptor CommandOur firmware would then follow these steps…void USB_Int_Handler()// USB Interrupt Sub Routinevoid ParseEP0Packet()// EP0 Control packet parsing function void ProcessStandardReq()// USB Standard Requestvoid CmdGetDescriptor()// Service GetDescriptor commandIn the CmdGetDescriptor() routine, we will then break up our 18-byte descriptor response into 8-byte data packets. Only when the host issues an IN token to us may we then transfer the data back up to the host in our firmware routine. We simply wait for the next IN packet to the host, fill up the endpoint 0 FIFO, then set the IN_PKT_RDY bit for EP0 in one of the M16C’s USB registers, and the hardware then transfer it up to the host.Shown below are the bus traces doing just that.Figure 7. The M30240 Device Sending the 18-byte Device Descriptor 8 bytes at a timeThis same procedure of breaking up the packets into 8-byte or less payloads will be done for various other USB commands such as getting the Configuration Descriptor, String Descriptor, Interface Descriptors and so on. This is because we told the USB Host Controller at the beginning that are MAX Packet size wouldbe 8 bytes.HostHostHostHostHostHostM30240M30240M30240。
