cisco ccnp 642-825新题汇总【2010年3月25日上传】
思科认证CCNA认证试题与答案中文版

思科认证CCNA认证试题与答案中文版思科认证CCXA认证试题与答案中文版21、一个B类网络,有5位掩码加入缺省掩码用来划分子网,每个子网最多()台主机(A)510(B)512(C)1022(D)2046答案:D22、在路由器中,能用以下命令察看路由器的路由表()(A)arp-a(B)traceroute(C)routeprint(D)displayiprouting-table答案:D23、DHCP客户端是使用地址()来中请一个新的IP地址的(A)0. 0. 0. 0(B)10. 0. 0. 1(0127. 0. 0. 1(D)255. 255. 255. 255答案:D注释:255. 255. 255. 255是全网广播,DHCP客户端发送全网广播来查找DHCP服务器.24、下而有关NAT叙述正确的是()(A)NAT是英文“地址转换”的缩写,又称地址翻译(B)XAT用来实现私有地址与公用网络地址之间的转换(C)当内部网络的主机访问外部网络的时候,一定不需要NAT(D)地址转换的提出为解决IP地址紧张的问题提供了一个有效途径答案:ABD25、以下属于正确的主机的IP地址的是()(A)224. 0. 0.5(B)127. 32. 5. 62(0202. 112.5.0(D) 162. 111. 111. Ill答案:D注释:这个题目不是太严谨,应该加上子网掩码.A:224. 0. 0. 5是多播地址B: 127. 0.0. 0保留作为测试使用C:网络地址26、设置主接口由up转down后延迟30秒切换到备份接口,主接口由down转up后60秒钟切换回主接口的配置为()(A)standbytimer3060(B)standbytimer6030(C)standbytimerenable-delay60disable-delay30(D)standbytimerenable-delay30disable-delay60答案:D27、在一个以太网中,30台pc通过QuidwayR2501路由器s0 口连接internet, QuidwayR2501路由器配置如下:[Quidway-EthernetO] ipaddressl92. 168. 1. 1255. 255. 255. 0[Quidway-EthernetO]quit[Quidway]interfacesO[Quidway-SerialOJ ipaddress211. 136. 3. 6255. 255. 255. 252[Quidway-Serial0」link-protocolppp一台PC机默认网关为192. 168. 2.1,路由器会怎样处理发自这台PC 的数据包?(A)路由器会认为发自这一台PC的数据包不在同一网段,不转发数据包(B)路由器会自动修正这一台PC机的IP地址,转发数据包(C)路由器丢弃数据包,这时候需要重启路由器,路由器自动修正误配(D)路由器丢弃数据包,不做任何处理,需要重配PC网关为192. 168. 1. 1答案:D注释:PC的'默认网关要指向路由器的以太网口的IP地址.28、ISDNB信道速率是()(A)16kbps(B)64kbps(C)144kbps(D)2048kbps答案:B参考知识点:综合数字业务网(ISDN)由数字电话和数据传输服务两部分组成,一般由电话局提供这种服务。
思科CCNA和CCNP与CCIE题库全集

Linux认证培训系列视频在线播放
/bbs/thread-13540-1-1.html
linux基础视频教材(刘晓涛主讲)
/bbs/thread-13539-1-1.html
LINUX社区强力推荐的LINUX教程集锦
/bbs/thread-13549-1-1.html
Linux安装视频教程和桌面演示
/bbs/thread-13560-1-1.html
LINUX视频教程(9集)下载 适合LINUX新手
TestInside最新题库 CCNA/CCNP/CCSP/CCIE.08年6月
本题库覆盖率98%-100%.非常精确,题量不大适合考前冲刺
/bbs/thread-12038-1-1.html
TestKing最新CCNA/CCNP/CCSP/CCIE题库.08年6月
Cisco CCNA视频教程--chinaitlab
/bbs/thread-10896-1-1.html
ChinaITLab出品Linux001-1-1.html
CISCO、RHCE等经典视频教程和题库汇总帖
/bbs/thread-13528-1-1.html
思科CCNA和CCNP、CCIE题库全集(不断更新)
/bbs/thread-8227-1-1.html
/bbs/thread-12003-1-1.html
CCNA新书(640-802)第六版学习指南大全
/bbs/thread-12505-1-1.html
新版CCNP教材下载 2008年4月更新整理
CISCO、CCNA、CCNP、CCIE、RHCE视频,IT视频教程下载专区
思科CCNA第三学期官方试题(完整版)[有答案解析]
![思科CCNA第三学期官方试题(完整版)[有答案解析]](https://img.taocdn.com/s3/m/d3a11424f18583d0496459c9.png)
参加考试 - ESwitching Final Exam - CCNA Exploration: LAN 交换和无线 (版本 4.0)剩余时间正在显示第 1 页,共 4页下一页>页跳转<上一页1 以下哪项参数用于唯一标识一个无线网络,使其与其它网络区分开来?SSID OFDMWEPDSSS2 分层网络模型具有哪三项优点?(选择三项。
)带宽争用现象减少物理布局范围减小网络的容错能力提高无需配线间无需第三层功能管理和故障排除工作简化3在将 Catalyst 交换机迁移到其它 VTP 管理域之前,应该进行哪三项任务?(选择正确的 VTP 模式和版本。
使用新管理域的名称配置交换机。
从新域中的 VTP 服务器上下载 VTP 数据库。
配置新域内的 VTP 服务器,使其识别该交换机的 BID。
重置 VTP 计数器,使交换机可与新域内的其它交换机同步。
检验交换机的配置修订版号是否比新域内的其它交换机的低。
4下列哪两种说法正确地描述了生成树协议?(选择两项。
)它只在第 2 层使用。
它在交换机上配置。
它消除了网络拓扑中的第 2 层环路。
它限制了端口上所允许的有效 MAC 地址的数量。
它使 VLAN 信息得以传播到网络中的其它交换机。
5下列哪种方法可建立用于配置 Linksys WRT300N 无线接入点的管理连接?与接入点关联,然后与接入点建立超级终端会话。
以物理方式连接到接入点,然后重新启动计算机以启动配置软件。
在接入点所在的 IP 子网内的计算机上的 web 浏览器中输入接入点的默认修改与接入点连接的计算机的 TCP/IP 属性,使其与接入点处于同一个网机以建立连接。
6请参见图示。
源地址并非 0019.d2e4.d9f7 的帧进入接口 Fa0/24 时会发生什么情况?Fa0/24 会变为 error-disabled(错误-禁用)状态。
传入帧会被丢弃。
Fa0/24 端口 LED 会关闭。
安全违规计数会增加。
CCNP最新题库 SWITCH 642-813-2
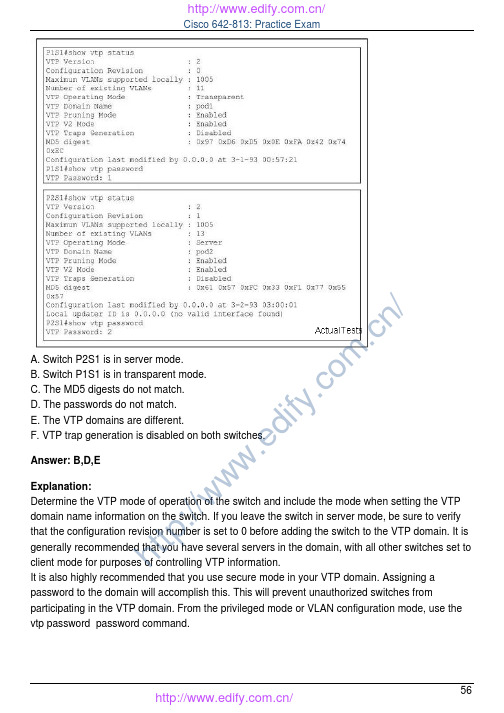
A. Switch P2S1 is in server mode.B. Switch P1S1 is in transparent mode.C. The MD5 digests do not match.D. The passwords do not match.E. The VTP domains are different.F. VTP trap generation is disabled on both switches.Answer: B,D,EExplanation:Determine the VTP mode of operation of the switch and include the mode when setting the VTP domain name information on the switch. If you leave the switch in server mode, be sure to verify that the configuration revision number is set to 0 before adding the switch to the VTP domain. It is generally recommended that you have several servers in the domain, with all other switches set to client mode for purposes of controlling VTP information.It is also highly recommended that you use secure mode in your VTP domain. Assigning a password to the domain will accomplish this. This will prevent unauthorized switches fromparticipating in the VTP domain. From the privileged mode or VLAN configuration mode, use the vtp password password command.h t t p://www.ed if y.co m .cn /QUESTION NO: 75Refer to the exhibit. Based upon the output of show vlan on switch CAT2, what can we conclude about interfaces Fa0/13 and Fa0/14?A. that interfaces Fa0/13 and Fa0/14 are in VLAN 1B. that interfaces Fa0/13 and Fa0/14 are downC. that interfaces Fa0/13 and Fa0/14 are trunk interfacesD. that interfaces Fa0/13 and Fa0/14have a domain mismatch with another switchE. that interfaces Fa0/13 and Fa0/14have a duplex mismatch with another switchAnswer: CExplanation:trunk - This setting places the port in permanent trunking mode. The corresponding switch port at the other end of the trunk should be similarly configured because negotiation is not allowed. You should also manually configure the encapsulation mode.show vlan: This commands shows the vlan, ports belonging to VLAN means that port on access mode. It doesn't shows the port on trunk mode.QUESTION NO: 76Refer to the exhibit. On the basis of the output generated by the show commands, which two statements are true? (Choose two.)h t t p://www.ed if y.co m .cn /A. Because it is configured as a trunk interface, interface gigabitethernet 0/1 does not appear in the show vlan output.B. VLAN 1 will not be encapsulated with an 802.1q header.C. There are no native VLANs configured on the trunk.D. VLAN 2 will not be encapsulated with an 802.1q header.E. All interfaces on the switch have been configured as access ports.F. Because it has not been assigned to any VLAN, interface gigabitethernet 0/1 does not appear in the show vlan output.Answer: A,BExplanation:h t t p://www.ed if y.co m .cn /The IEEE 802.1Q protocol can also carry VLAN associations over trunk links. However, this frame identification method is standardized, allowing VLAN trunks to exist and operate between equipment from multiple vendors.In particular, the IEEE 802.1Q standard defines an architecture for VLAN use, services provided with VLANs, and protocols and algorithms used to provide VLAN services.Like Cisco ISL, IEEE 802.1Q can be used for VLAN identification with Ethernet trunks. Instead of encapsulating each frame with a VLAN ID header and trailer, 802.1Q embeds its tagging information within the Layer 2 frame. This method is referred to as single-tagging or internal tagging .802.1Q also introduces the concept of a native VLAN on a trunk. Frames belonging to this VLAN are not encapsulated with any tagging information. In the event that an end station is connected to an 802.1Q trunk link, the end station can receive and understand only the native VLAN frames.This provides a simple way to offer full trunk encapsulation to the devices that can understand it,while giving normal access stations some inherent connectivity over the trunk.show vlan: This commands shows the vlan, ports belonging to VLAN means that port on access mode. It doesn't show the port on trunk mode.QUESTION NO: 77Refer to the exhibit and the show interfaces fastethernet0/1 switchport outputs. Users in VLAN 5on switch SW_A complain that they do not have connectivity to the users in VLAN 5 on switch SW_B. What should be done to fix the problem?A. Configure the same number of VLANs on both switches.h t t p://www.ed if y.co m .cn /B. Create switch virtual interfaces (SVI) on both switches to route the traffic.C. Define VLAN 5 in the allowed list for the trunk port on SW_A.D. Disable pruning for all VLANs in both switches.E. Define VLAN 5 in the allowed list for the trunk port on SW_BAnswer: CExplanation:switchport trunk allowed vlan , defines which VLANs can be trunked over thelink . By default, a switch transports all active VLANs (1 to 4094) over a trunk link. There might be times when the trunk link should not carry all VLANs. For example, broadcasts are forwarded to every switch port on a VLAN-including the trunk link because it, too, is a member of the VLAN.If the VLAN does not extend past the far end of the trunk link, propagating broadcasts across the trunk makes no sense.Section 8: Document results of VLAN implementation and verification (0 Questions)QUESTION NO: 78Refer to the exhibit. An attacker is connected to interface Fa0/11 on switch A-SW2 and attempts to establish a DHCP server for a man-in-middle attack. Which recommendation, if followed, would mitigate this type of attack?A. All switch ports in the Building Access block should be configured as DHCP untrusted ports.B. All switch ports in the Building Access block should be configured as DHCP trusted ports.h t t p://www.ed if y.co m .cn /C. All switch ports connecting to servers in the Server Farm block should be configured as DHCP untrusted ports.D. All switch ports connecting to hosts in the Building Access block should be configured as DHCP trusted ports.E. All switch ports in the Server Farm block should be configured as DHCP untrusted ports.F. All switch ports connecting to hosts in the Building Access block should be configured as DHCP untrusted ports.Answer: FExplanation:One of the ways that an attacker can gain access to network traffic is to spoof responses that would be sent by a valid DHCP server. The DHCP spoofing device replies to client DHCPrequests. The legitimate server may reply also, but if the spoofing device is on the same segment as the client, its reply to the client may arrive first.The intruder's DHCP reply offers an IP address and supporting information that designates the intruder as the default gateway or Domain Name System (DNS) server. In the case of a gateway,the clients will then forward packets to the attacking device, which will in turn send them to the desired destination. This is referred to as a "man-in-the-middle" attack, and it may go entirely undetected as the intruder intercepts the data flow through the network.Untrusted ports are those that are not explicitly configured as trusted. A DHCP binding table is built for untrusted ports. Each entry contains the client MAC address, IP address, lease time,binding type, VLAN number, and port ID recorded as clients make DHCP requests. The table is then used to filter subsequent DHCP traffic. From a DHCP snooping perspective, untrusted access ports should not send any DHCP server responses, such as DHCPOFFER, DHCPACK,DHCPNAK .QUESTION NO: 79You are responsible for increasing the security within the Company LAN. Of the following choices listed below, which is true regarding layer 2 security and mitigation techniques?A. Enable root guard to mitigate ARP address spoofing attacks.B. Configure DHCP spoofing to mitigate ARP address spoofing attacks.C. Configure PVLANs to mitigate MAC address flooding attacks.D. Enable root guard to mitigate DHCP spoofing attacks.E. Configure dynamic APR inspection (DAI) to mitigate IP address spoofing on DHCP untrusted ports.F. Configure port security to mitigate MAC address floodingG. None of the other alternatives applyAnswer: Fh t t p://www.ed if y.co m .cn /Explanation:Use the port security commands to mitigate MAC-spoofing attacks. The port security command provides the capability to specify the MAC address of the system connected to a particular port.The command also provides the ability to specify an action to take if a port-security violationoccurs. However, as with the CAM table-overflow attack mitigation, specifying a MAC address on every port is an unmanageable solution. Hold-down timers in the interface configuration menu can be used to mitigate ARP spoofing attacks by setting the length of time an entry will stay in the ARP cache.Reference: /networksecurity/NetworkSecurity.htmlSection 2: Create an implementation plan for the Security solution (3 Questions)QUESTION NO: 80You work as a network technician at . Your boss, Mrs. Tess King, is interested in switch spoofing. She asks you how an attacker would collect information with VLAN hoping through switch spoofing. You should tell her that the attacking station...A. es VTP to collect VLAN information that is sent out and then tags itself with the domain information in order to capture the data.B. ...will generate frames with two 802.1Q headers to cause the switch to forward the frames to a VLAN that would be inaccessible to the attacker through legitimate means.C. es DTP to negotiate trunking with a switch port and captures all traffic that is allowed on the trunk.D. ...tags itself with all usable VLANs to capture data that is passed through the switch, regardless of the VLAN to which the data belongs.E. None of the other alternatives applyAnswer: CExplanation:DTP should be disabled for all user ports on a switch. If the port is left with DTP auto-configured (default on many switches), an attacker can connect and arbitrarily cause the port to start trunking and therefore pass all VLAN information.Reference:/en/US/solutions/ns340/ns517/ns224/ns376/net_design_guidance0900aecd800ebd1e.pdfQUESTION NO: 81h t t p://www.ed if y.co m .cn /The Company security administrator is concerned with layer 2 network attacks. Which two statements about these attacks are true? (Select two)A. ARP spoofing attacks are attempts to redirect traffic to an attacking host by encapsulating a false 802.1Q header on a frame and causing traffic to be delivered to the wrong VLAN.B. ARP spoofing attacks are attempts to redirect traffic to an attacking host by sending an ARP message with a forged identity to a transmitting host.C. MAC address flooding is an attempt to force a switch to send all information out every port by overloading the MAC address table.D. ARP spoofing attacks are attempts to redirect traffic to an attacking host by sending an ARP packet that contains the forged address of the next hop router.E. MAC address flooding is an attempt to redirect traffic to a single port by associating that port with all MAC addresses in the VLAN.Answer: B,CExplanation:Content Addressable Memory ( CAM ) Table Overflow (MAC address Flooding)Content Addressable Memory (CAM) tables are limited in size. If enough entries are entered into the CAM table before other entries are expired, the CAM table fills up to the point that no new entries can be accepted. Typically, a network intruder floods the switch with a large number of invalid source Media Access Control (MAC) addresses until the CAM table fills up. When thatoccurs, the switch floods all ports with incoming traffic because it cannot find the port number for a particular MAC address in the CAM table. The switch, in essence, acts like a hub. If the intruder does not maintain the flood of invalid-source MAC addresses, the switch eventually times out older MAC address entries from the CAM table and begins to act like a switch again. CAM tableoverflow only floods traffic within the local VLAN so the intruder only sees traffic within the local VLAN to which he or she is connected.The CAM table overflow attack can be mitigated by configuring port security on the switch. This option provides for either the specification of the MAC addresses on a particular switch port or the specification of the number of MAC addresses that can be learned by a switch port. When an invalid MAC address is detected on the port, the switch can either block the offending MAC address or shut down the port. The specification of MAC addresses on switch ports is far too unmanageable a solution for a production environment. A limit of the number of MAC addresses on a switch port is manageable. A more administratively scalable solution is the implementation of dynamic port security at the switch. In order to implement dynamic port security, specify a maximum number of MAC addresses that will be learned.Address Resolution Protocol (ARP) SpoofingARP is used to map IP addressing to MAC addresses in a local area network segment where hosts of the same subnet reside. Normally, a host sends out a broadcast ARP request to find the MAC address of another host with a particular IP address, and an ARP response comes from the host whose address matches the request. The requesting host then caches this ARP response.Within the ARP protocol, another provision is made for hosts to perform unsolicited ARP replies.h t t p://www.ed if y.co m .cn /The unsolicited ARP replies are called Gratuitous ARP (GARP). GARP can be exploited maliciously by an attacker to spoof the identity of an IP address on a LAN segment. This istypically used to spoof the identity between two hosts or all traffic to and from a default gateway in a "man-in-the-middle" attack.When an ARP reply is crafted, a network attacker can make his or her system appear to be the destination host sought by the sender. The ARP reply causes the sender to store the MACaddress of the network attacker's system in the ARP cache. This MAC address is also stored by the switch in its CAM table. In this way, the network attacker has inserted the MAC address of his or her system into both the switch CAM table and the ARP cache of the sender. This allows the network attacker to intercept frames destined for the host that he or she is spoofing.Reference:/en/US/products/hw/switches/ps5023/products_configuration_example09186a00807c4101.shtmlQUESTION NO: 82The Company security administrator wants to prevent DHCP spoofing. Which statement is true about DHCP spoofing operation?A. DHCP spoofing and SPAN cannot be used on the same port of a switch.B. To prevent a DHCP spoofing, the DHCP server must create a static ARP entry that cannot be updated by a dynamic ARP packet.C. To prevent a DHCP spoofing, the switch must have DHCP server services disabled and a static entry pointing towards the DHCP server.D. DHCP spoofing can be prevented by placing all unused ports in an unused VLAN.E. None of the other alternatives apply.Answer: BExplanation:About DHCP Spoofing:Suppose that an attacker could bring up a rogue DHCP server on a machine in the same subnet as that same client PC. Now when the client broadcasts its DHCP request, the rogue server could send a carefully crafted DHCP reply with its own IP address substituted as the default gateway.When the client receives the reply, it begins using the spoofed gateway address. Packets destined for addresses outside the local subnet then go to the attacker's machine first. The attacker can forward the packets to the correct destination, but in the meantime, it can examine every packet that it intercepts. In effect, this becomes a type of man-in-the-middle attack; the attacker is wedged into the path and the client doesn't realize it.About ARP:h t t p://www.ed if y.co m .cn /Hosts normally use the Address Resolution Protocol (ARP) to resolve an unknown MAC address when the IP address is known. If a MAC address is needed so that a packet can be forwarded at Layer 2, a host broadcasts an ARP request that contains the IP address of the target in question.If any other host is using that IP address, it responds with an ARP reply containing its MAC address.To prevent a DHCP spoofing, the DHCP server must create a static ARP entry that cannot be updated by a dynamic ARP packetSection 3: Create a verification plan for the Security solution (4 Questions)QUESTION NO: 83Refer to the exhibit. What will happen to traffic within VLAN 14 with a source address of 172.16.10.5?A. The traffic will be forwarded to the router processor for further processing.B. The traffic will be dropped.C. The traffic will be forwarded to the TCAM for further processing.D. The traffic will be forwarded without further processing.Answer: BExplanation:VLAN maps, also known as VLAN ACLs or VACLs, can filter all traffic traversing a switch. VLAN maps can be configured on the switch to filter all packets that are routed into or out of a VLAN, or are bridged within a VLAN. VLAN maps are used strictly for security packet filtering. Unlike routerh t t p://www.ed if y.co m .cn /ACLs, VLAN maps are not defined by direction (input or output).To create a VLAN map and apply it to one or more VLANs, perform these steps: Create the standard or extended IP ACLs or named MAC extended ACLs to be applied to the VLAN. This access-list will select the traffic that will be either forwarded or dropped by the access-map. Only traffic matching the 'permit' condition in an access-list will be passed to the access-map for further processing. Enter the vlan access-map access-map-name [ sequence ] global configuration command to create a VLAN ACL map entry. Each access-map can have multiple entries. The order of these entries is determined by the sequence . If no sequence number is entered, access-map entries are added with sequence numbers in increments of 10. In access map configuration mode, optionally enter an action forward or action drop . The default is to forward traffic. Also enter the match command to specify an IP packet or a non-IP packet (with only a known MAC address),and to match the packet against one or more ACLs (standard or extended). Use the vlan filter access-map-name vlan-list vlan-list global configuration command to apply a VLAN map to one or more VLANs. A single access-map can be used on multiple VLANs.QUESTION NO: 84Company is implementing 802.1X in order to increase network security. In the use of 802.1X access control, which three protocols are allowed through the switch port before authentication takes place? (Select three)A. EAP-over-LANB. EAP MD5C. STPD. protocols not filtered by an ACLE. CDPF. TACACS+Answer: A,C,EExplanation:The IEEE 802.1x standard defines a port-based access control and authentication protocol that restricts unauthorized workstations from connecting to a LAN through publicly accessible switch ports. The authentication server authenticates each workstation that is connected to a switch port before making available any services offered by the switch or the LAN. Until the workstation is authenticated, 802.1x access control allows only Extensible Authentication Protocol over LAN (EAPOL) traffic through the port to which the workstation is connected. After authentication succeeds, normal traffic can pass through the port.The Authentication server performs the actual authentication of the client. The authentication server validates the identity of the client and notifies the switch whether or not the client is authorized to access the LAN and switch services. Because the switch acts as the proxy, theh t t p://www.ed if y.co m .cn /authentication service is transparent to the client. In this release, the Remote Authentication Dial-In User Service (RADIUS) security system with Extensible Authentication Protocol (EAP)extensions is the only supported authentication server; it is available in Cisco Secure Access Control Server version 3.0. RADIUS operates in a client/server model in which secureauthentication information is exchanged between the RADIUS server and one or more RADIUS clients.Spanning-Tree Protocol (STP) is a Layer 2 protocol that utilizes a special-purpose algorithm to discover physical loops in a network and effect a logical loop-free topology. STP creates a loop-free tree structure consisting of leaves and branches that span the entire Layer 2 network. The actual mechanics of how bridges communicate and how the STP algorithm works will be discussed at length in the following topics. Note that the terms bridge and switch are used interchangeably when discussing STP. In addition, unless otherwise indicated, connections between switches are assumed to be trunks.CDP is a Cisco proprietary protocol that operates at the Data Link layer. One unique feature about operating at Layer 2 is that CDP functions regardless of what Physical layer media you are using (UTP, fiber, and so on) and what Network layer routed protocols you are running (IP, IPX,AppleTalk, and so on). CDP is enabled on all Cisco devices by default, and is multicast every 60seconds out of all functioning interfaces, enabling neighbor Cisco devices to collect information about each other. Although this is a multicast message, Cisco switches do not flood that out to all their neighbors as they do a normal multicast or broadcast.For STP, CDP and EAP-over-LAN are allowed before Authentication.QUESTION NO: 85Refer to the exhibit. The web servers WS_1 and WS_2 need to be accessed by external and internal users. For security reasons, the servers should not communicate with each other,although they are located on the same subnet. The servers do need, however, to communicate with a database server located in the inside network. What configuration will isolate the servers from each other?h t t p://www.ed if y.co m .cn /A. The switch ports 3/1 and 3/2 will be defined as secondary VLAN community ports. The ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.B. The switch ports 3/1 and 3/2 and the ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.C. The switch ports 3/1 and 3/2 and the ports connecting to the two firewalls will be defined as primary VLAN community ports.D. The switch ports 3/1 and 3/2 will be defined as secondary VLAN isolated ports. The ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.Answer: DExplanation:Service providers often have devices from multiple clients, in addition to their own servers, on a single Demilitarized Zone (DMZ) segment or VLAN. As security issues proliferate, it becomes necessary to provide traffic isolation between devices, even though they may exist on the same Layer 3 segment and VLAN. Catalyst 6500/4500 switches implement PVLANs to keep some switch ports shared and some switch ports isolated, although all ports exist on the same VLAN.The 2950 and 3550 support "protected ports," which are functionality similar to PVLANs on a per-switch basis.A port in a PVLAN can be one of three types:Isolated: An isolated port has complete Layer 2 separation from other ports within the same PVLAN, except for the promiscuous port. PVLANs block all traffic to isolated ports, except the traffic from promiscuous ports. Traffic received from an isolated port is forwarded to only promiscuous ports.Promiscuous: A promiscuous port can communicate with all ports within the PVLAN, including the community and isolated ports. The default gateway for the segment would likely be hosted on a promiscuous port, given that all devices in the PVLAN will need to communicate with that port. Community: Community ports communicate among themselves and with their promiscuous ports.These interfaces are isolated at Layer 2 from all other interfaces in other communities, or in isolated ports within their PVLAN.QUESTION NO: 86VLAN maps have been configured on switch R1. Which of the following actions are taken in a VLAN map that does not contain a match clause?A. Implicit deny feature at end of list.B. Implicit deny feature at start of list.C. Implicit forward feature at end of listD. Implicit forward feature at start of list.Answer: Ah t t p://www.ed if y.co m .cn /Explanation:Each VLAN access map can consist of one or more map sequences, each sequence with a match clause and an action clause. The match clause specifies IP, IPX, or MAC ACLs for traffic filtering and the action clause specifies the action to be taken when a match occurs. When a flow matches a permit ACL entry the associated action is taken and the flow is not checked against theremaining sequences. When a flow matches a deny ACL entry, it will be checked against the next ACL in the same sequence or the next sequence. If a flow does not match any ACL entry and at least one ACL is configured for that packet type, the packet is denied.Reference:/en/US/products/hw/switches/ps700/products_configuration_guide_chapter09186a008007f4d4.htmlSection 4: Configure port security features (6 Questions)QUESTION NO: 87A Company switch was configured as shown below:switchport mode access switchport port-securityswitchport port-security maximum 2switchport port-security mac-address 0002.0002.0002switchport port-security violation shutdownGiven the configuration output shown above, what happens when a host with the MAC address of 0003.0003.0003 is directly connected to the switch port?A. The host will be allowed to connect.B. The port will shut down.C. The host can only connect through a hub/switch where 0002.0002.0002 is already connected.D. The host will be refused access.E. None of the other alternatives applyAnswer: AExplanation:Steps of Implementing Port Security:h t t p://www.ed if y.co m .cn /In Exhibit two MAC addresses are allowed so that host will be allowed to connect.QUESTION NO: 88Refer to the exhibit. Which interface or interfaces on switch SW_A can have the port security feature enabled?A. Ports 0/1 and 0/2B. The trunk port 0/22 and the EtherChannel portsh t t p://www.ed if y.co m .cn /C. Ports 0/1, 0/2 and 0/3D. Ports 0/1, 0/2, 0/3, the trunk port 0/22 and the EtherChannel portsE. Port 0/1F. Ports 0/1, 0/2, 0/3 and the trunk port 0/22Answer: CExplanation:Port security is a feature supported on Cisco Catalyst switches that restricts a switch port to a specific set or number of MAC addresses. Those addresses can be learned dynamically or configured statically. The port will then provide access to frames from only those addresses. If,however, the number of addresses is limited to four but no specific MAC addresses areconfigured, the port will allow any four MAC addresses to be learned dynamically, and port access will be limited to those four dynamically learned addresses. A port security feature called "sticky learning," available on some switch platforms, combines the features of dynamically learned and statically configured addresses. When this feature is configured on an interface, the interface converts dynamically learned addresses to "sticky secure" addresses. This adds them to the running configuration as if they were configured using the switchport port-security mac-address command.QUESTION NO: 89Refer to the exhibit. Based on the running configuration that is shown for interface FastEthernet0/2, what two conclusions can be deduced? (Choose two.)A. Connecting a host with MAC address 0000.0000.4147 will move interface FastEthernet0/2 into error disabled state.B. The host with address 0000.0000.4141 is removed from the secure address list after 5 seconds of inactivity.h t t p://www.ed if y.co m .cn /。
(完整版)Cisco期末考试选择题题库

第1小组成员出题集:1.一台主机已经正确布线并配置有唯一的主机名和有效的IP地址。
要使主机可以远程访问资源还应配置哪两个额外的组件?ACA.子网掩码B.MAC 地址C.默认网关D.环回IP 地址E.DHCP 服务器IP 地址2.支持可变长子网掩码的路由协议有?BCDA. RIP v1B. RIP v2C. OSPFD. IS-IS3.路由器中含有许多其他计算机中常见的硬件和软件组合,包括?CA.CPU ROM 操作系统硬盘B.主板硬盘显卡CPUC.CPU ROM 内存操作系统D.主板电源光驱CPU4.哪两项说法正确描述了路由器的组件?BCA. RAM 永久存储着在启动过程中使用的配置文件B.重新启动时闪存中的内容不会丢失C. NVRAM 存储着在启动过程中使用的IOS 的备份副本D. ROM 包含最新而且最完整的IOS 版本5.下列哪些是路由器的功能?AA. 分组交换广播域分段根据逻辑编址选择最佳路径B. 分组交换网段扩展广播域分段C. 根据物理编址选择最佳路径根据逻辑编址选择最佳路径网段扩展D. 分组交换网段扩展广播域分段6.以下哪一项正确描述了路由器启动时的顺序?AA.加载bootstrap、加载IOS、应用配置B.加载bootstrap、应用配置、加载IOSC.加载IOS、加载bootstrap、应用配置、检查硬件D.检查硬件、应用配置、加载bootstrap、加载IOS7.网络管理员需要通过路由器的FastEthernet 端口直接连接两台路由器。
应用哪种电缆?CA.直通电缆B.全反电缆C.交叉电缆D.串行电缆8.以下哪些路由表项要由网络管理员手动配置?AA.静态路由B.直接路由C.动态路由D.以上说法都不正确9.RIP协议是基于?AA.UDPB.TCPC.ICMPD.Raw IP10.以下协议属于路由协议的是 ?ABCGA.RIPB.IS-ISC.OSPFD.PPPE.IPF.IPXG.BGP11.静态路由的优点包括? CA. 管理简单B. 自动更新路由C. 提高网络安全性D. 节省带宽E. 收敛速度快12.以下哪些内容是路由信息中所不包含的?AA. 源地址B. 下一跳C. 目标网络D. 路由权值13.下列关于OSPF协议的说法正确的是?ABDA. OSPF支持基于接口的报文验证B. OSPF支持到同一目的地址的多条等值路由C. OSPF是一个基于链路状态算法的边界网关路由协议D. OSPF发现的路由可以根据不同的类型而有不同的优先级14.以下哪一项正确描述了路由器启动时的顺序?A(A)加载bootstrap、加载IOS、应用配置(B)加载bootstrap、应用配置、加载IOS(C)加载IOS、加载bootstrap、应用配置、检查硬件(D)检查硬件、应用配置、加载bootstrap、加载IOS15.输入以下命令的作用是什么?BR1(config)#line vty 0 4R1(config-line)#password check123R1(config-line)#loginA.确保在进入用户执行模式之前输入口令B.设置通过Telnet连接该路由器时使用的口令C.要求在保存配置前输入check123D.创建本地用户账户以便登陆路由器或交换机16.您需要配置图中所示的串行连接,必须在sydney路由器上发出以下哪条配置命令才能与Melboume站点建立连接?(选三项)ABDA.Sydeny(config-if)#ip address 201.100.53.2 255.255.255.0B.Sydeny(config-if)#no shutdownC.Sydeny(config-if)#ip address 201.100.53.1 255.255.255.224D.Sydeny(config-if)#clock rate 56000E.Sydeny(config-if)#ip gost Melboume 201.100.53.2答案:1-5:AC,BCD,C,B,A6-10:A,C,A,A,ABCG7-15:ACD,A,ABD,A,B16:ABD注释:第1,6,11道陈宝生出题;第2,7,12道许斌斌出题;第3,8,13道曹淑婷出题;第4,9,14道彭鹏出题;第5,10,15,16道陆志翔出题。
最新IT认证 CCNP 642-813认证考试题库

The safer , easier way to help you pass any IT exams.Exam : 642-813Title :Version : DemoImplementing Cisco IP SwitchedNetworks(SWITCH)The safer , easier way to help you pass any IT exams.pany uses layer 3 switches in the Core of their network. Which method of Layer 3 switching uses a forwarding information base (FIB)?A. Topology-based switchingB. Demand-based switchingC. Route cachingD. Flow-based switchingE. None of the other alternatives applyAnswer: A2.You need to design the VLAN scheme for the Company network. Which two statements are true about best practices in VLAN design? (Select two)A. Routing should occur at the access layer ifvoice VLANs are utilized. Otherwise, routing should occur at the distribution layer.B. Routing should always be performed at the distribution layer.C. VLANs should be localized to a switch.D. VLANs should be localized to a single switch unlessvoice VLANs are being utilized.E. Routing should not be performed between VLANs located on separate switches.Answer: B,C3.Refer to the exhibit. On the basis of the information provided in the exhibit, which two sets of procedures are best practices for Layer 2 and 3 failover alignment? (Choose two.)A. Configure the D-SW1 switch as the active HSRP router and the STP root for all VLANs.Configure the D-SW2 switch as the standby HSRP router and backup STP root for all VLANs.B. Configure the D-SW1 switch as the standby HSRP router and the STP root for VLANs 11 and 110. Configure the D-SW2 switch as the standby HSRP router and the STP root for VLANs 12 and 120.C. Configure the D-SW1 switch as the active HSRP router and the STP root for VLANs 11 and 110. Configure the D-SW2 switch as the active HSRP router and the STP root for VLANs 12 and 120.D. Configure the D-SW2 switch as the active HSRP router and the STP root for all VLANs. Configure the D-SW1 switch as the standby HSRP router and backup STP root for all VLANs.E. Configure the D-SW1 switch as the active HSRP router and the backup STP root for VLANs 11 and 110. Configure the D-SW2 switch as the active HSRP router and the backup STP root for VLANs 12 and 120.F. Configure the D-SW1 switch as the standby HSRP router and the backup STP root for VLANs 12a nd 120. Configure the D-SW2 switch as the standby HSRP router and the backup STP rootfor VLANs 11 and 110.Answer: C,F4.If you needed to transport traffic coming from multiple VLANs (connected between switches), and your CTO was insistent on using an open standard, which protocol would you use?A. 802.11BB. spanning-treeC. 802.1QD. ISLE. VTPF. Q.921Answer: C5.Under what circumstances should an administrator prefer local VLANs over end-to-end VLANs?A. Eighty percent of traffic on the network is destined for Internet sites.B. There are common sets of traffic filtering requirements for workgroups located in multiple buildings.C. Eighty percent of a workgroup's traffic is to the workgroup's own local server.D. Users are grouped into VLANs independent of physical location.E. None of the other alternatives applyAnswer: A6.What are some virtues of implementing end-to-end VLANs? (Choose two)A. End-to-end VLANs are easy to manage.B. Users are grouped into VLANs independent of a physical location.C. Each VLAN has a common set of security and resource requirements for all members.D. Resources are restricted to a single location.Answer: B,C7.Which of the following statements is true about the 80/20 rule (Select all that apply)?A. 20 percent of the traffic on a network segment should be localB. no more than 20 percent of the network traffic should be able to move across a backbone.C. no more than 80 percent of the network traffic should be able to move across a backbone.D. 80 percent of the traffic on a network segment should be localAnswer: B,D8.The Company LAN is becoming saturated with broadcasts and multicast traffic. What could you do to help a network with many multicasts and broadcasts?A. Creating smaller broadcast domains by implementing VLANs.B. Separate nodes into different hubs.C. Creating larger broadcast domains by implementing VLANs.D. Separate nodes into different switches.E. All of the above.Answer: A9.The Company LAN switches are being configured to support the use of Dynamic VLANs. Which of the following are true of dynamic VLAN membership? (Select all that apply)A. VLAN membership of a user always remains the same even when he/she is moved to another location.B. VLAN membership of a user always changes when he/she is moved to another location.C. Membership can be static or dynamic.D. Membership can be static only.E. None of the other alternatives apply.Answer: A,C10.The Company LAN switches are being configured to support the use of Dynamic VLANs. What should be considered when implementing a dynamic VLAN solution? (Select two)A. Each switch port is assigned to a specific VLAN.B. Dynamic VLANs require a VLAN Membership Policy Server.C. Devices are in the same VLAN regardless of which port they attach to.D. Dynamic VLAN assignments are made through the command line interface.Answer: B,C11.In the three-layer hierarchical network design model; what's associated with the access layer? (Select two)A. optimized transport structureB. high port densityC. boundary definitionD. data encryptionE. local VLANsF. route summariesAnswer: B,E12.You are assigning VLANs to the ports of switch R1. What VLAN number value is an assigned tothe default VLAN?A. VLAN 1003B. VLAN 1C. VLAN OND. VLAN AE. VLAN 0Answer: B13.The VLANs in switch R1 are being modified. Which of the following are updated in R1 every time a VLAN is modified? (Select all that apply)A. Configuration revision numberB. Configuration revision flag fieldC. Configuration revision reset switchD. Configuration revision databaseE. None of the other alternatives apply.Answer: A,D14.Given the above partial configuration, which two statements are true about VLAN traffic? (Choose two.)A. VLANs 1-5 will use fa0/10 as a backup only.B. VLANs 6-10 will use fa0/10 as a backup only.C. VLANs 1-5 will be blocked if fa0/10 goes down.D. VLANs 1-10 are configured to load share between fa0/10 and fa0/12.E. VLANs 6-10 have a port priority of 128 on fa0/10.Answer: B,D15.What is a characteristic of assigning a static VLAN membership?A. VMPS server lookup is requiredB. Easy to configureC. Easy of adds, moves, and changesD. Based on MAC address of the connected deviceAnswer: B16.Static VLANs are being used on the Company network. What is true about static VLANs?A. Devices use DHCP to request their VLAN.B. Attached devices are unaware of any VLANs.C. Devices are assigned to VLANs based on their MAC addresses.D. Devices are in the same VLAN regardless of which port they attach to.Answer: B17.Two Company switches are connected via a trunk using VTP. Which VTP information does a Catalyst switch advertise on its trunk ports when using VTP? (Select two)A. STP root statusB. VTP modeC. Negotiation statusD. Management domainE. Configuration revision numberAnswer: D,E18.You need to investigate a VTP problem between two Company switches. The lack of which two prevents VTP information from propagating between switches? (Select two)A. A root VTP serverB. A trunk portC. VTP priorityD. VLAN 1E. None of the other alternatives applyAnswer: B,D19.R1 and R2 are switches that communicate via VTP. What is the default VTP advertisement intervals in Catalyst switches that are in server or client mode?A. 30 secondsB. 5 minutesC. 1 minuteD. 10 secondsE. 5 secondsF. None of the other alternatives applyAnswer: B20.Refer to the exhibit. VTP has been enabled on the trunk links between all switches within theTEST domain. An administrator has recently enabled VTP pruning. Port 1 on Switch 1 and port 2 on Switch 4 are assigned to VLAN 2. A broadcast is sent from the host connected to Switch 1. Where will the broadcast propagate?A. Every switch in the network receives the broadcast and will forward it out all ports.B. Every switch in the network receives the broadcast, but only Switch 4 will forward it out port 2.C. Switches 1, 2, and 4 will receive the broadcast, but only Switch 4 will forward it out port 2.D. Only Switch 4 will receive the broadcast and will forward it out port 2.Answer: C21.You want to configure switch R1 to propagate VLAN information across the Company network using VTP. What must be configured on a Cisco switch in order to advertise VLAN information?A. VTP modeB. VTP passwordC. VTP revision numberD. VTP pruningE. VTP domain nameF. None of the other alternatives applyAnswer: E22.The Company switches have all been upgraded to use VTP version 2. What are two benefits provided in VTP Version 2 that are not available in VTP Version 1? (Select two)A. VTP version 2 supports Token Ring VLANsB. VTP version 2 allows VLAN consistency checksC. VTP version 2 allows active redundant links when used with spanning treeD. VTP version 2 reduces the amount of configuration necessaryE. VTP version 2 saves VLAN configuration memoryAnswer: A,B23.The Company network administrator needs to enable VTP pruning within the Company network. What action should a network administrator take to enable VTP pruning on an entire management domain?A. Enable VTP pruning on any switch in the management domainB. Enable VTP pruning on any client switch in the domainC. Enable VTP pruning on a VTP server in the management domainD. Enable VTP pruning on every switch in the domainE. None of the other alternatives applyAnswer: C24.VTP is configured on switch R1. Which of the following features were added in VTP version 2 that were not previously supported in VTP version 1? (Select two)A. Supports Token Ring VLANs.B. Allows VLAN consistency checks.C. Saves VLAN configuration memory.D. Reduces the amount of configuration necessary.E. Allows active redundant links when used with spanning tree.Answer: A,B25.The Company switches are configured to use VTP. What's true about the VLAN trunking protocol (VTP)? (Select two)A. VTP messages will not be forwarded over nontrunk links.B. VTP domain names need to be identical. However, case doesn't matter.C. A VTP enabled device which receives multiple advertisements will ignore advertisements with higher configuration revision numbers.D. A device in "transparent" VTP v.1 mode will not forward VTP messages.E. VTP pruning allows switches to prune VLANs that do not have any active ports associated with them.Answer: A,D26.Switch R1 and R2 both belong to the Company VTP domain. What's true about the switch operation in VTP domains? (Select all that apply)A. A switch can only reside in one management domainB. A switch is listening to VTP advertisements from their own domain onlyC. A switch is listening to VTP advertisements from multi domainsD. A switch can reside in one or more domainsE. VTP is no longer supported on Catalyst switchesAnswer: A,B27.VTP devices in a network track the VTP revision number. What is a VTP configuration revision number?A. A number for identifying changes to the network switch.B. A number for identifying changes to the network router.C. A number for identifying changes to the network topology.D. None of the other alternatives apply.Answer: C28.Switch R1 is configured to use the VLAN Trunking Protocol (VTP). What does R1 advertise in itsVTP domain?A. The VLAN ID of all known VLANs, the management domain name, and the total number oftrunk links on the switch.B. The VLAN ID of all known VLANs, a 1-bit canonical format (CF1 Indicator), and the switch configuration revision number.C. The management domain name, the switch configuration revision number, the known VLANs, and their specific parameters.D. A 2-byte TPID with a fixed value of 0x8100 for the management domain number, the switch configuration revision number, the known VLANs, and their specific parameters.E. None of the other alternatives apply.Answer: C29.VTP switches use advertisements to exchange information with each other. Which of the following advertisement types are associated with VTP? (Select all that apply)A. Domain advertisementsB. Advertisement requests from clientsC. Subset advertisementsD. Summary advertisementsAnswer: B,C,D30.Switch R1 is part of the Company VTP domain. What's true of VTP Pruning within this domain? (Select all that apply)A. It does not prune traffic from VLANs that are pruning-ineligibleB. VLAN 1 is always pruning-eligibleC. it will prune traffic from VLANs that are pruning-ineligibleD. VLAN 2 is always pruning-ineligibleE. None of the other alternatives apply.Answer: A。
CCNP642-845实验题
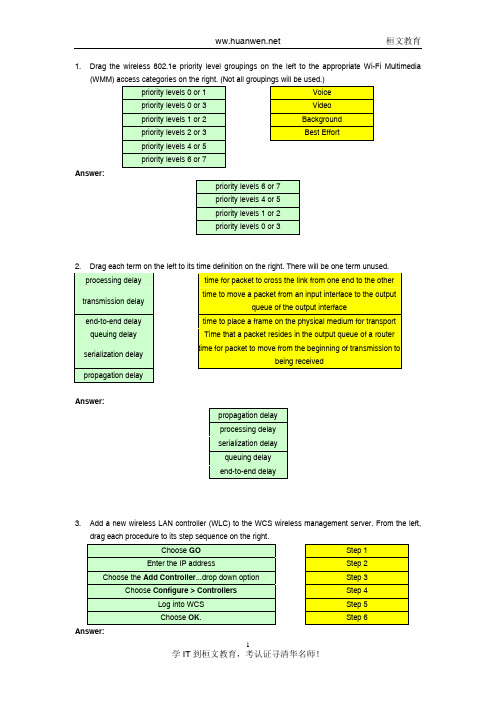
1. Drag the wireless 802.1e priority level groupings on the left to the appropriate Wi-Fi Multimedia(WMM) access categories on the right. (Not all groupings will be used.)priority levels 0 or 1 Voicepriority levels 0 or 3 Videopriority levels 1 or 2 Backgroundpriority levels 2 or 3 Best Effortpriority levels 4 or 5priority levels 6 or 7Answer:priority levels 6 or 7priority levels 4 or 5priority levels 1 or 2priority levels 0 or 32. Drag each term on the left to its time definition on the right. There will be one term unused.processing delay time for packet to cross the link from one end to the othertransmission delay time to move a packet from an input interface to the outputqueue of the output interfaceend-to-end delay time to place a frame on the physical medium for transport queuing delay Time that a packet resides in the output queue of a routerserialization delay time for packet to move from the beginning of transmission tobeing receivedpropagation delayAnswer:propagation delayprocessing delayserialization delayqueuing delayend-to-end delay3. Add a new wireless LAN controller (WLC) to the WCS wireless management server. From the left,drag each procedure to its step sequence on the right.Choose GO Step 1Enter the IP address Step 2 Choose the Add Controller...drop down option Step 3Choose Configure > Controllers Step 4Log into WCS Step 5Choose OK. Step 6Answer:Log into WCSChoose Configure > ControllersChoose the Add Controller...drop down optionChoose GOEnter the IP addressChoose OK.4. Drag each wireless EAP authentication protocol on the left to its definition on the right.LEAP client and server digital certificate required for authentication EAP-FAST server only digital certificate required for authenticationEAP-TLS user ID and password required for authenticationEAP-PEAP protected access credentials for client and serverauthenticationAnswer:EAP-TLSEAP-PEAPLEAPEAP-FAST5. Using the fewest commands possible, drag the commands on the left to the blanks on the right toconfigure and apply a QoS policy that guarantees that voice packets receive 20 percent of the bandwidth on the S0/1/0 interface.int s0/1/0policy-map voice-policymatch ip dscp efmatch ip protocol rtppriority percent 20class-map voice-packetsbandwidth percent 20service-policy output voice-policyclass voice-packetsAnswer:class-map voice-packetsmatch ip dscp efpolicy-map voice-policyclass voice-packetspriority percent 20int s0/1/0service-policy output voice-policy6. To configure Control Plan Policing (CoPP) to deny Telnet access only from 10.1.1.1, drag thecommands on the left to the boxes on the right and place the commands in the proper order.class-map telnet-classdropclass telnet-classservice-policy input control-plane-inaccess-list 140 deny tcp host 10.1.1.1any eq telnetaccess-list 140 permit tcp any any eqtelnetcontrol-planematch access-group 140policy-map control-plane-inAnswer:access-list 140 deny tcp host 10.1.1.1 any eq telnetaccess-list 140 permit tcp any any eq telnetclass-map telnet-classmatch access-group 140policy-map control-plane-inclass telnet-classdropcontrol-planeservice-policy input control-plane-in7. Drag each descriptor on the left to the QoS model on the right to which the descriptor applies. Not alldescriptors apply.limited scalability IntServ Modelhighly scalableuses DSCP to identify QoS levelno QoSuses RSVPeasy to offer many levels of QoS DiffServ Modelused to provide CACcomplex mechanisms for QoSassured QoStimely arrival of packets not importantAnswer:IntServ Modellimited scalabilityuses RSVPused to provide CACassured QoSDiffServ Modelhighly scalableuses DSCP to identify QoS leveleasy to offer many levels of QoScomplex mechanisms for QoS8. Drag each WLSE feature on the left to its benefit on the right.centralized configuration, firmware, and radiohelps in capacity planning and troubleshooting managementautoconfiguration of new APs allows the use of autoconfiguration of new APsAP utilization and client association simplifies large-scale deploymentproactively monitor AP/bridges and 802.1Ximproves WLAN uptimeEAP serverstemplates required to manage large numbers of APsAnswer:AP utilization and client associationtemplatesautoconfiguration of new APsproactively monitor AP/bridges and 802.1XEAP serverscentralized configuration, firmware, and radiomanagement9. Drag each WLSE feature above to its benefit below.tempaltes Helps in capacity planning and troubleshootingautoconfiguration of new APS Allows the use of autoconfiguration of new ApsAP utilization and client association Simplifies large-scale deploymentproactively monitor AP/bridges andImproves WLAN uptime 802.1x EAP serverscentralized configuration, firmware,Required to management large nembers of Aps and radio managementAnswer:AP utilization and client associationtempaltesautoconfiguration of new APSproactively monitor AP/bridges and 802.1x EAP servers centralized configuration, firmware, and radio management10. Drag the steps required to convert compressed digital signals to analog signals to their correct orderon the right.decompression Step 1 sampling Step 2 decodingStep 3 reconstruction encodingAnswer:decompression decoding reconstruction11. This item contains several questions that you must answer. You can view these questions byclicking on the Questions button to the left. Changing questions can be accomplished by clicking the numbers to the left each question. In order to complete the question, you will need to refer to the SDM and the topology, neither of which is currently visible.To gain access to either the topology or the SDM, click on the button to left side of the screen that corresponds to the section you wish to access. When you have finished viewing the topology or the SDM, you can return to your questions by clicking on the Questions button to the left.Your Money, Inc. is a large worldwide investment firm. Using the SDM QoS wizard, the company has recently implemented QoS policies at one of their Branch locations. As a recent addition to the network engineering team, you have been tasked with documenting the active QoS configuration at the branch router using the Cisco Router and Security Device Manager (SDM) utility. Using the SDM output from the Edit QoS Policy Tab in the Quality of Service Tasks under the Configure button, answer the following questions:Question#1Which DSCP value will the Branch router apply to voice traffic destined for the Central from the IP Phone on the local network?A. 46 (ef)B. 48 (vc6)C. 50D. 56 (cs7)E. 70Answer: AQuestion#2Which DSCP value will the Branch router apply to voice traffic destined for the IP Phone on the local network from the Central site?A. 46 (ef)B. 48 (cs6)C. 50D. 56 (cs7)E. 70Answer: BQuestion#3Which QoS model has been implemented on the Branch router by the SDM wizard for the various expected traffic types?A. Best EffortB. IntServC. DiffServD. Priority QueuingAnswer: CQuestion#4During periods of congestion which queuing method will be applied to outbound traffic on the Serial0/3/0 interface?A. Low Latency QueuingB. Class-based Weighted Fair QueuingC. Weighted Round RobinD. Round RobinE. No queuing is applied to outbound traffic on this interfaceAnswer: A12. This item contains several questions that you must answer. You can view these questions byclicking on the Questions button to the left. Changing questions can be accomplished by clicking the numbers to the left of each question. In order to complete the questions, you will need to refer to the output and the topology, neither of which is currently visible.To gain access to either the topology or the output, click on the button to left side of the screen that corresponds to the section you wish to access. When you have finished viewing the topology or the output, you can return to your questions by clicking on the Questions button to the left.Law Solutions, Inc. is a large, worldwide law firm. Using the AutoQoS feature of IOS, the company recently implemented QoS policies at one of their Branch locations. As a recent addition to the network engineering team, you have been tasked with documenting the active QoS configuration at the branch router. Additionally, the firm is experiencing poor video quality with newly installed video-conferencing equipment. The video problems at the branch location seem to occur only during peak hours when some network congestion is expected. Using the show run output of the branch router, answer the following questions:Question#1Which DSCP value will the Branch router apply to video traffic destined for the Central site from the video equipment on the local network?A. 8 (cs1)B. 10 (af11)C. 18 (af21)D. 24 (cs3)E. 46 (ef)F. No valueAnswer: EQuestion#2Which two statements most accurately identify what has caused the occasional poor video quality experienced by the Law Solutions, Inc.? (Choose two.)A. Insufficient bandwidth is creating a bottleneck transiting from the FastEthernet0/0 to the Serial0/3/0 interface.B. Auto-Discovery did not have an opportunity to detect the video traffic.C. AutoQoS was implemented on the incorrect interface.D. A policy matching DSCP value 46 (ef) was not applied on the outbound interface.Answer: BDQuestion#3Which QoS model has been implemented on the Branch router by Auto QoS for the various expected traffic types?A. Best EffortB. IntServC. DiffServD. Priority QueuingAnswer: CQuestion#4During periods of congestion, how has AutoQoS configured the router to facilitate outbound video traffic on the Serial0/3/0 interface?A. Video traffic will be associated with the priority queue by using a DSCP value of 46 (ef).B. Video traffic will be associated with the AutoQoS-Signaling-Se0/3/0 class and its related policy through use of the H.323 protocol.C. Video traffic will only be queued on the local FastEthernet0/0 interface using a DSCP value of 45 (ef).D. Video traffic will be associated with the "class-default" and use WFQ.Answer: D13. Exhibit:This item contains several questions that you must answer. You can view these questions by clicking on the corresponding button to the left. Changing questions can be accomplished by clicking the numbers to the left of each question. In order to complete the questions, you will need to refer to the topology.To gain access to the topology, click on the topology button at the bottom of the screen. When you have finished viewing the topology, you can return to your questions by clicking on the Questions button to the left.Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging it by the title bar.Ferrous Plastics, Inc. Is a medium sized company, with two locations connected through a serial WAN link. The WAN routers should be configured to only use NBAR to classify traffic through interface Fa0/1 prior to using low latency queuing on the outgoing interface s0/1/0. Recently configuration changes were made to the inter-connecting routers WAN-R1 and WAN-R2. The company is now experiencing QoS related problems which they believe are associated with these changes.You have been asked to use supported show commands to identify the correct answer to questions that the network administrator has asked.WAN-R1 Running Configuration (by typing “sh run”):WAN-R2 Running Configuration (by typing “sh run”):Question#1Router WAN-R2 is not marking traffic correctly on Fa0/1 based on NBAR classification. Which of the following is correct?A. Protocol discovery is applied to the incorrect interfaceB. CEF is not configuredC. The service-policy is applied in the wrong directionD. The service-policy configured on interface Fa0/1 should be policy1Question#2The network administrator has asked how FTP traffic is being classified on router WAN-R1. Which of the following is correct?A. FTP traffic is marked correctly, but no other active protocols are marked correctlyB. FTP traffic is marked correctly based on NBAR classificationC. FTP traffic is marked correctly, but it is not using NBAR for classificationD. FTP traffic is not marked correctly based on NBAR classification as protocol discovery is applied to the incorrect interfaceE. FTP traffic is not being marked because it is not included in a configured service-policy Answer: BQuestion#3On router WAN-R1, which protocol is being marked as af21?A. CITRIXB. ExchangeC. FTPD. HTTPF. SQLNETAnswer: AQuestion#4On router WAN-R1, which protocol is being classified as mission critical?A. CITRIXB. ExchangeC. FTPD. HTTPE. SQLNETAnswer: E14. CaseWhat will happen if the incoming mission-critical class traffic rate arriving at the fa0/0 interface is higher than the normal burst rate (CIR) but not exceeding the exceeding the excess burst rate?A. DroppedB. Marked as AF31 then transmittedC. Marked as AF32 then transmittedD. Marked as AF33 then transmittedE. Queued in the CBWFQAnswer: CQuestion#2What will happen if the incoming bulk class traffic rate arriving at the fa0/0 interface is higher than the normal burst rate (CIR)?A. DroppedB. Marked as AF11 then transmittedC. Marked as DSCP 0 then transmittedD. Queued in the excess token bucketE. Queued in the CBWFQAnswer: AQuestion#3All traffic belonging to the class-default traffic class on the s0/0 interface will be queued by a class queue that uses which type of queuing?A. FIFOB. LLQC. WFQD. Round RobinE. PQAnswer: AQuestion#4Which type of traffic receives the least amount of guaranteed bandwidth when exiting the S0/0 interface?A. ftpB. httpC. telnetD. citrixE. sqlnetAnswer: AQuestion#5Which type of software queue is used on the s0/0 interface?A. LLQB. CBWFQC. FIFOAnswer: B。
CCNP题库讲解

[题库讲解]CCNP 642-892 V3.95题库分析1 1.In the use of 802.1X access control, which three protocols are allowed through the switch port before authentication takes place? (Choose three.) A. STP B. CDP C. EAP MD5 D. TACACS+ E. EAP-over-LAN F. protocols not filtered by an ACL Answer: ABE 解释一下:IEEE 802.1X认证成功之前,客户连接的端口在LAN上只允许传递可扩展的认证协议(EAPOL),CDP,和生成树的STP。
只有认证成功后才可以传递正常的流量。
2.Which protocol specified by RFC 2281 provides network redundancy for IP networks, ensuring that user traffic immediately and transparently recovers from first-hop failures in network edge devices or access circuits? A. STP B. IRDP C. ICMP D. HSRP Answer: D 解释一下:RFC 2281中定义的是HSRP。
3.What will be the effect of applying the VLAN access map configuration on a switch? Router(config)# vlan access-map thor 10 Router(config-access-map)# match ip address net_10 Router(config-access-map)#action forward Router(config-access-map)#exit Router(config)# vlan filter thor vlan-list 12-16 A. All VLAN 12 through 16 IP traffic matching net_10 is forwarded and all other IP packets are dropped. B. IP traffic matching vlan-list 12-16 is forwarded and all other IP packets are dropped. C. IP traffic matching net_10 is dropped and all other IP packets are forwarded to VLANs 12 through 16.D. All VLAN 12 through 16 IP traffic is forwarded, other VLAN IP traffic matching net_10 is dropped. Answer: A 解释一下:这是关于VLAN access map 的使用,这是针对vlan-list中的VLAN中的流量进行的过滤,只有在vlan access-map中定义的forward的流量才可以在vlan-list中规定的VLAN中通过。
642-825题库
Exam : Cisco 642-825 Title : Update : DemoImplementing Secure Converged Wide Area Networks (ISCW)1. Refer to the exhibit, which shows a PPPoA diagram and partial SOHO77 configuration.Which command needs to be applied to the SOHO77 to complete the configuration?A. encapsulation aal5snap applied to the PVC.B. encapsulation aal5ciscoppp applied to the PVCC. encapsulation aal5ciscoppp applied to the ATM0 interfaceD. encapsulation aal5mux ppp dialer applied to the ATM0 interfaceE. encapsulation aal5mux ppp dialer applied to the PVCAnswer: E2. Which three techniques should be used to secure management protocols? (Choose three.)A. Configure SNMP with only read-only community strings.B. Encrypt TFTP and syslog traffic in an IPSec tunnel.C. Implement RFC 3704 filtering at the perimeter router when allowing syslog access from devices on the outside of a firewall.D. Synchronize the NTP master clock with an Internet atomic clock.E. Use SNMP version 2.F. Use TFTP version 3 or above because these versions support a cryptographic authentication mechanism between peers.Answer: ABC3. What are two steps that must be taken when mitigating a worm attack? (Choose two.)A. Inoculate systems by applying update patches.B. Limit traffic rate.C. Apply authentication.D. Quarantine infected machines.E. Enable anti-spoof measuresAnswer: AD4. What is a reason for implementing MPLS in a network?A. MPLS eliminates the need of an IGP in the core.B. MPLS reduces the required number of BGP-enabled devices in the core.C. Reduces routing table lookup since only the MPLS core routers perform routing table lookups.D. MPLS eliminates the need for fully meshed connections between BGP enabled devices.Answer: B5. Which three statements about IOS Firewall configurations are true? (Choose three.)A. The IP inspection rule can be applied in the inbound direction on the secured interface.B. The IP inspection rule can be applied in the outbound direction on the unsecured interface.C. The ACL applied in the outbound direction on the unsecured interface should be an extended ACL.D. The ACL applied in the inbound direction on the unsecured interface should be an extended ACL.E. For temporary openings to be created dynamically by Cisco IOS Firewall, the access-list for the returning traffic must be a standard ACL.F. For temporary openings to be created dynamically by Cisco IOS Firewall, the IP inspection rule must be applied to the secured interface.Answer: ABD6. Which three IPsec VPN statements are true? (Choose three.)A. IKE keepalives are unidirectional and sent every ten seconds.B. IKE uses the Diffie-Hellman algorithm to generate symmetrical keys to be used by IPsec peers.C. IPsec uses the Encapsulating Security Protocol (ESP) or the Authentication Header (AH) protocol for exchanging keys.D. Main mode is the method used for the IKE phase two security association negotiations.E. Quick mode is the method used for the IKE phase one security association negotiations.F. To establish IKE SA, main mode utilizes six packets while aggressive mode utilizes only three packets. Answer: ABF7. Which three MPLS statements are true? (Choose three.)A. Cisco Express Forwarding (CEF) must be enabled as a prerequisite to running MPLS on a Cisco router.B. Frame-mode MPLS inserts a 32-bit label between the Layer 3 and Layer 4 headers.C. MPLS is designed for use with frame-based Layer 2 encapsulation protocols such as Frame Relay, but is not supported by ATM because of ATM fixed-length cells.D. OSPF, EIGRP, IS-IS, RIP, and BGP can be used in the control plane.E. The control plane is responsible for forwarding packets.F. The two major components of MPLS include the control plane and the data plane.Answer: ADF8. Refer to the exhibit.What are the two options that are used to provide High Availability IPsec? (Choose two.)A. RRIB. IPsec Backup PeeringsC. Dynamic Crypto MapD. HSRPE. IPsec Stateful Switchover (SSO)F. Dual Router Mode (DRM) IPsecAnswer: AD9. Refer to the exhibit. What type of security solution will be provided for the inside network?A. The TCP connection that matches the defined ACL will be reset by the router if the connection does not complete the three-way handshake within the defined time period.B. The router will reply to the TCP connection requests. If the three-way handshake completes successfully, the router will establish a TCP connection between itself and the server.C. The TCP traffic that matches the ACL will be allowed to pass through the router and create a TCP connection with the server.D. The router will intercept the traceroute messages. It will validate the connection requests before forwarding the packets to the inside network.Answer: B10. Refer to the exhibit.Which statement about the authentication process is true?A. The LIST1 list will disable authentication on the console port.B. Because no method list is specified, the LIST1 list will not authenticate anyone on the console port.C. All login requests will be authenticated using the group tacacs+ method.D. All login requests will be authenticated using the local database method.E. The default login authentication will automatically be applied to all login connections.Answer: A11. Which three statements about the Cisco Easy VPN feature are true? (Choose three.)A. If the VPN server is configured for Xauth, the VPN client waits for a username / password challenge.B. The Cisco Easy VPN feature only supports transform sets that provide authentication and encryption.C. The VPN client initiates aggressive mode (AM) if a pre-shared key is used for authentication during the IKE phase 1 process.D. The VPN client verifies a server username/password challenge by using a AAA authentication server that supports TACACS+ or RADIUS.E. The VPN server can only be enabled on Cisco PIX Firewalls and Cisco VPN 3000 series concentrators.F. When connecting with a VPN client, the VPN server must be configured for ISAKMP group 1, 2 or 5. Answer: ABC12. What are three features of the Cisco IOS Firewall feature set? (Choose three.)A. network-based application recognition (NBAR)B. authentication proxyC. stateful packet filteringD. AAA servicesE. proxy serverF. IPSAnswer: BCF13. Refer to the exhibit.What does the "26" in the first two hop outputs indicate?A. the outer label used to determine the next hopB. the IPv4 label for the destination networkC. the IPv4 label for the forwarding routerD. the IPv4 label for the destination routerAnswer: B14. Which two statements about the Cisco AutoSecure feature are true? (Choose two.)A. All passwords entered during the AutoSecure configuration must be a minimum of 8 characters in length.B. Cisco123 would be a valid password for both the enable password and the enable secret commands.C. The auto secure command can be used to secure the router login as well as the NTP and SSH protocols.D. For an interactive full session of AutoSecure, the auto secure login command should be used.E. If the SSH server was configured, the 1024 bit RSA keys are generated after the auto secure commandis enabled.Answer: CE15. Refer to the exhibit. Which statement is true about the configuration of split tunnels using SDM?A. Any protected subnets that are entered represent subnets at the end user's site that will be accessed without going through the encrypted tunnel.B. Any protected subnets that are entered represent subnets at the end user's site that will be accessed through the encrypted tunnel.C. Any protected subnets that are entered represent subnets at the VPN server site that will be accessed without going through the encrypted tunnel.D. Any protected subnets that are entered represent subnets at the VPN server site that will be accessedthrough the encrypted tunnel.Answer: D16. Refer to the exhibit. Which statement is true about the partial MPLS configuration that is shown?A. The route-target both 100:2 command sets import and export route-targets for vrf2.B. The route-target both 100:2 command changes a VPNv4 route to a IPv4 route.C. The route-target import 100:1 command sets import route-targets routes specified by the route map.D. The route-target import 100:1 command sets import route-targets for vrf2 that override the otherroute-target configuration.Answer: A17. Which two mechanisms can be used to detect IPsec GRE tunnel failures? (Choose two).A. Dead Peer Detection (DPD)B. CDPC. isakmp keepalivesD. GRE keepalive mechanismE. The hello mechanism of the routing protocol across the IPsec tunnelAnswer: AE18. Which two statements are true about broadband cable (HFC) systems? (Choose two.)A. Cable modems only operate at Layer 1 of the OSI model.B. Cable modems operate at Layers 1 and 2 of the OSI model.C. Cable modems operate at Layers 1, 2, and 3 of the OSI model.D. A function of the cable modem termination system (CMTS) is to convert the modulated signal from thecable modem into a digital signal.E. A function of the cable modem termination system is to convert the digital data stream from the end user host into a modulated RF signal for transmission onto the cable system.Answer: BD19. What are three configurable parameters when editing signatures in Security Device Manager (SDM)? (Choose three.)A. AlarmSeverityB. AlarmKeepaliveC. AlarmTraitsD. EventMediaE. EventAlarmF. EventActionAnswer: ACF20. Which two statements about common network attacks are true? (Choose two.)A. Access attacks can consist of password attacks, trust exploitation, port redirection, andman-in-the-middle attacks.B. Access attacks can consist of password attacks, ping sweeps, port scans, and man-in-the-middle attacks.C. Access attacks can consist of packet sniffers, ping sweeps, port scans, and man-in-the-middle attacks.D. Reconnaissance attacks can consist of password attacks, trust exploitation, port redirection and Internet information queries.E. Reconnaissance attacks can consist of packet sniffers, port scans, ping sweeps, and Internet information queries.F. Reconnaissance attacks can consist of ping sweeps, port scans, man-in-middle attacks and Internet information queries.Answer: AE21. Refer to the exhibit.Which three statements describe the steps that are required to configure an IPsec site-to-site VPN using a GRE tunnel? (Choose three.)A. The command access-list 110 permit gre must be configured to specify which traffic will be encrypted.B. The command access-list 110 permit ip must be configured to specify which hosts can use the tunnel.C. The tunnel destination 172.17.63.18 command must be configured on the Tunnel0 interface.D. The tunnel mode gre command must be configured on the Tunnel0 interface.E. The tunnel source Ethernet1 command must be configured on the Tunnel0 interface.F. The tunnel source Tunnel0 command must be configured on the Tunnel0 interface.Answer: ACE22. Which form of DSL technology is typically used as a replacement for T1 lines?A. VDSLB. HDSLC. ADSLD. SDSLE. G.SHDSLF. IDSLAnswer: B23. Which three statements are true when configuring Cisco IOS Firewall features using the SDM? (Choose three.)A. A custom application security policy can be configured in the Advanced Firewall Security Configuration dialog box.B. An optional DMZ interface can be specified in the Advanced Firewall Interface Configuration dialog box.C. Custom application policies for e-mail, instant messaging, HTTP, and peer-to-peer services can be created using the Intermediate Firewall wizard.D. Only the outside (untrusted) interface is specified in the Basic Firewall Interface Configuration dialog box.E. The outside interface that SDM can be launched from is configured in the Configuring Firewall for Remote Access dialog box.F. The SDM provides a basic, intermediate, and advanced firewall wizard.Answer: ABE24. Refer to the exhibit. On the basis of the partial configuration, which two statements are true? (Choose two.)A. A CBAC inspection rule is configured on router RTA.B. A named ACL called SDM_LOW is configured on router RTA.C. A QoS policy has been applied on interfaces Serial 0/0 and FastEthernet 0/1.D. Interface Fa0/0 should be the inside interface and interface Fa0/1 should be the outside interface.E. On interface Fa0/0, the ip inspect statement should be incoming.F. The interface commands ip inspect SDM_LOW in allow CBAC to monitor multiple protocols. Answer: AF25. Which three statements about frame-mode MPLS are true? (Choose three.)A. MPLS has three distinct components consisting of the data plane, the forwarding plane, and the control plane.B. The control plane is a simple label-based forwarding engine that is independent of the type of routing protocol or label exchange protocol.C. The CEF FIB table contains information about outgoing interfaces and their corresponding Layer 2 header.D. The MPLS data plane takes care of forwarding based on either destination addresses or labels.E. To exchange labels, the control plane requires protocols such as Tag Distribution Protocol (TDP) or MPLS Label Distribution Protocol (LDP).F. Whenever a router receives a packet that should be CEF-switched, but the destination is not in the FIB, the packet is dropped.Answer: DEF26. What are the four fields in an MPLS label? (Choose four.)A. versionB. experimentalC. labelD. protocolE. TTLF. bottom-of-stack indicatorAnswer: BCEF27. Which statement is true when ICMP echo and echo-reply are disabled on edge devices?A. Pings are allowed only to specific devices.B. CDP information is not exchanged.C. Port scans can no longer be run.D. Some network diagnostic data is lost.E. Wireless devices need to be physically connected to the edge device.F. OSPF routing needs the command ip ospf network non-broadcast enabled.Answer: D28. Which statement is true about a worm attack?A. Human interaction is required to facilitate the spread.B. The worm executes arbitrary code and installs copies of itself in the memory of the infected computer.C. Extremely large volumes of requests are sent over a network or over the Internet.D. Data or commands are injected into an existing stream of data. That stream is passed between a client and server application.Answer: B29. Refer to the exhibit. Which order correctly identifies the steps to provision a cable modem to connect to a headend as defined by the DOCSIS standard?A. A, D, C, G, E, F, BB. A, D, E, G, C, F, BC. C, D, F, G, E, A, BD. C, D, F, G, A, E, BE. F, D, C, G, A, E, BF. F, D, C, G, E, A, B Answer: E30. Refer to the exhibit.On the basis of the information that is provided, which two statements are true? (Choose two.)A. An IPS policy can be edited by choosing the Edit button.B. Right-clicking on an interface will display a shortcut menu with options to edit an action or to set severity levels.C. The Edit IPS window is currently in Global Settings view.D. The Edit IPS window is currently in IPS Policies view.E. The Edit IPS window is currently in Signatures view.F. To enable an IPS policy on an interface, click on the interface and deselect Disable.Answer: AD。
思科认证考试题库

CCNA640-802 V13题库试题分析题库讲解:吴老师(艾迪飞CCIE实验室首发网站:1. What are two reasons that a network administrator would use access lists? (Choose two.)A. to control vty access into a routerB. to control broadcast traffic through a routerC. to filter traffic as it passes through a routerD. to filter traffic that originates from the routerE. to replace passwords as a line of defense against security incursionsAnswer: AC解释一下:在VTY线路下应用ACL,可以控制从VTY线路进来的telnet的流量。
也可以过滤穿越一台路由器的流量。
2. A default Frame Relay WAN is classified as what type of physical network?A. point-to-pointB. broadcast multi-accessC. nonbroadcast multi-accessD. nonbroadcast multipointE. broadcast point-to-multipointAnswer: C解释一下:在默认的情况下,帧中继为非广播多路访问链路。
但是也可以通过子接口来修改他的网络的类型。
3.Refer to the exhibit. How many broadcast domains exist in the exhibited topology?A. oneB. twoC. threeD. fourE. fiveF. sixAnswer: C解释一下:广播域的问题,在默认的情况下,每个交换机是不能隔离广播域的,所以在同一个区域的所有交换机都在同一个广播域中,但是为了减少广播的危害,将广播限制在一个更小的范围,有了VLAN的概念,VLAN表示的是一个虚拟的局域网,而他的作用就是隔离广播。
iscoccnp模拟试题与答案

C i s c o C C N P842-813e x a m Question:1uses layer 3 switches in the Core of their network. Which method of Layer 3 switching uses a forwarding information base (FIB)?A. Topology-based switchingB. Demand-based switchingC. Route cachingD. Flow-based switchingE. None of the other alternatives applyAnswer: AQuestion:2You need to design the VLAN scheme for the network. Which two statements are true about best practices in VLAN design? (Select two)A. Routing should occur at the access layer if voice VLANs are utilized. Otherwise, routingshould occur at the distribution layer.B. Routing should always be performed at the distribution layer.C. VLANs should be localized to a switch.D. VLANs should be localized to a single switch unless voice VLANs are being utilized.E. Routing should not be performed between VLANs located on separate switches. Answer: B, CQuestion:3If you needed to transport traffic coming from multiple VLANs (connected between switches),and your CTO was insistent on using an open standard, which protocol would you use?A. 802.11BB. spanning-treeC. 802.1QD. ISLE. VTPF. Q.921Answer: CQuestion:4Under what circumstances should an administrator prefer local VLANs overend-to-endVLANs?A. Eighty percent of traffic on the network is destined for Internet sites.B. There are common sets of traffic filtering requirements for workgroups located in multiplebuildings.C. Eighty percent of a workgroup’s traffic is to the workgroup’s own local server.D. Users are grouped into VLANs independent of physical location.E. None of the other alternatives applyAnswer: AQuestion:5What are some virtues of implementing end-to-end VLANs? (Choose two)A. End-to-end VLANs are easy to manage.B. Users are grouped into VLANs independent of a physical location.C. Each VLAN has a common set of security and resource requirements for all members.D. Resources are restricted to a single location.Answer: B, CQuestion:6Which of the following statements is true about the 80/20 rule (Select all that apply)?A. 20 percent of the traffic on a network segment should be localB. no more than 20 percent of the network traffic should be able to move across a backbone.C. no more than 80 percent of the network traffic should be able to move across a backbone.D. 80 percent of the traffic on a network segment should be localAnswer: B, DQuestion:7The LAN is becoming saturated with broadcasts and multicast traffic. What could you do to help a network with many multicasts and broadcasts?A. Creating smaller broadcast domains by implementing VLANs.B. Separate nodes into different hubs.C. Creating larger broadcast domains by implementing VLANs.D. Separate nodes into different switches.E. All of the above.Answer: AQuestion:8The LAN switches are being configured to support the use of Dynamic VLANs. Which of the following are true of dynamic VLAN membership? (Select all that apply)A. VLAN membership of a user always remains the same even when he/she is moved toanother location.B. VLAN membership of a user always changes when he/she is moved to another location.C. Membership can be static or dynamic.D. Membership can be static only.E. None of the other alternatives apply.Answer: A, CQuestion:9The LAN switches are being configured to support the use of Dynamic VLANs.What should be considered when implementing a dynamic VLAN solution? (Select two)A. Each switch port is assigned to a specific VLAN.B. Dynamic VLANs require a VLAN Membership Policy Server.C. Devices are in the same VLAN regardless of which port they attach to.D. Dynamic VLAN assignments are made through the command line interface. Answer: B, CQuestion:10In the three-layer hierarchical network design model; what’s associated with the access layer?(Select two)A. optimized transport structureB. high port densityC. boundary definitionD. data encryptionE. local VLANsF. route summariesAnswer: B, EQuestion:11You are assigning VLANs to the ports of switch PG1. What VLAN number value is anassigned to the default VLAN?A. VLAN 1003B. VLAN 1C. VLAN OND. VLAN AE. VLAN 0Answer: BQuestion:12The VLANs in switch PG1 are being modified. Which of the following are updated in PG1every time a VLAN is modified? (Select all that apply)A. Configuration revision numberB. Configuration revision flag fieldC. Configuration revision reset switchD. Configuration revision databaseE. None of the other alternatives apply.Answer: A, DQuestion:13What is a characteristic of assigning a static VLAN membership?A. VMPS server lookup is requiredB. Easy to configureC. Easy of adds, moves, and changesD. Based on MAC address of the connected deviceAnswer: BQuestion:14Static VLANs are being used on the network. What is true about static VLANs?A. Devices use DHCP to request their VLAN.B. Attached devices are unaware of any VLANs.C. Devices are assigned to VLANs based on their MAC addresses.D. Devices are in the same VLAN regardless of which port they attach to. Answer: BQuestion:15Two switches are connected via a trunk using VTP. Which VTP information does a Catalyst switch advertise on its trunk ports when using VTP? (Select two)A. STP root statusB. VTP modeC. Negotiation statusD. Management domainE. Configuration revision numberAnswer: D, EQuestion:16You need to investigate a VTP problem between two switches. The lack of which two prevents VTP information from propagating between switches? (Select two)A. A root VTP serverB. A trunk portC. VTP priorityD. VLAN 1E. None of the other alternatives applyAnswer: B, DQuestion:17PG1 and PG2 are switches that communicate via VTP. What is the default VTP advertisement intervals in Catalyst switches that are in server or client mode?A. 30 secondsB. 5 minutesC. 1 minuteD. 10 secondsE. 5 secondsF. None of the other alternatives applyAnswer: BQuestion:18You want to configure switch PG1 to propagate VLAN information across the network using VTP. What must be configured on a Cisco switch in order to advertise VLANinformation?A. VTP modeB. VTP passwordC. VTP revision numberD. VTP pruningE. VTP domain nameF. None of the other alternatives applyAnswer: EQuestion:19The switches have all been upgraded to use VTP version 2. What are two benefits provided in VTP Version 2 that are not available in VTP Version 1? (Select two)A. VTP version 2 supports Token Ring VLANsB. VTP version 2 allows VLAN consistency checksC. VTP version 2 allows active redundant links when used with spanning treeD. VTP version 2 reduces the amount of configuration necessaryE. VTP version 2 saves VLAN configuration memoryAnswer: A, BQuestion:20The network administrator needs to enable VTP pruning within thenetwork. What action should a network administrator take to enable VTP pruning on an entiremanagement domain?A. Enable VTP pruning on any switch in the management domainB. Enable VTP pruning on any client switch in the domainC. Enable VTP pruning on a VTP server in the management domainD. Enable VTP pruning on every switch in the domainE. None of the other alternatives applyAnswer: CQuestion:21VTP is configured on switch PG1. Which of the following features were added in VTP version2 that were not previously supported in VTP version 1? (Select two)A. Supports Token Ring VLANs.B. Allows VLAN consistency checks.C. Saves VLAN configuration memory.D. Reduces the amount of configuration necessary.E. Allows active redundant links when used with spanning tree.Answer: A, BQuestion:22The switches are configured t o use VTP. What’s true about the VLAN trunking protocol (VTP)? (Select two)A. VTP messages will not be forwarded over nontrunk links.B. VTP domain names need to be identical. However, case doesn’t matter.C. A VTP enabled device which receives multiple advertisements will ignore advertisementswith higher configuration revision numbers.D. A device in “transparent” VTP v.1 mode will not forward VTP messages.E. VTP pruning allows switches to prune VLANs that do not have any active portsassociatedwith them.Answer: A, DQuestion:23Switch PG1 and PG2 both belong to the VTP domain. What’s true about the switch operation in VTP domains? (Select all that apply)A. A switch can only reside in one management domainB. A switch is listening to VTP advertisements from their own domain onlyC. A switch is listening to VTP advertisements from multi domainsD. A switch can reside in one or more domainsE. VTP is no longer supported on Catalyst switchesAnswer: A, BQuestion:24VTP devices in a network track the VTP revision number. What is a VTP configurationrevision number?A. A number for identifying changes to the network switch.B. A number for identifying changes to the network router.C. A number for identifying changes to the network topology.D. None of the other alternatives apply.Answer: CQuestion:25Switch PG1 is configured to use the VLAN Trunking Protocol (VTP). What does PG1 advertise in its VTP domain?A. The VLAN ID of all known VLANs, the management domain name, and the total number oftrunk links on the switch.B. The VLAN ID of all known VLANs, a 1-bit canonical format (CF1 Indicator), and the switchconfiguration revision number.C. The management domain name, the switch configuration revision number, the knownVLANs, and their specific parameters.D. A 2-byte TPID with a fixed value of 0x8100 for the management domain number, theswitch configuration revision number, the known VLANs, and their specific parameters.E. None of the other alternatives apply.Answer: CQuestion:26VTP switches use advertisements to exchange information with each other. Which of thefollowing advertisement types are associated with VTP? (Select all that apply)A. Domain advertisementsB. Advertisement requests from clientsC. Subset advertisementsD. Summary advertisementsAnswer: B, C, DQuestion:27Switch PG1 is part of the VTP domain. What’s true of VTP Pruning within this domain? (Select all that apply)A. It does not prune traffic from VLANs that are pruning-ineligibleB. VLAN 1 is always pruning-eligibleC. it will prune traffic from VLANs that are pruning-ineligibleD. VLAN 2 is always pruning-ineligibleE. None of the other alternatives apply.Answer: AQuestion:28What action should you execute if you wanted to enable VTP pruning on your entire management domain?A. Enable VTP pruning on any client switch in the management domain.B. Enable VTP pruning on any switch in the management domain.C. Enable VTP pruning on every switch in the management domain.D. Enable VTP pruning on a VTP server in the management domain.E. Disable VTP pruning on a VTP server in the management domain.Answer: DQuestion:29Switch PG1 is configured with VTP. Which two VTP modes will make PG1 capable of creatingand deleting VLANs on itself? (Select two)A. ClientB. ServerC. TransparentD. Pass-throughE. No-negotiateAnswer: B, CQuestion:30When the Catalyst switch PG1 is enabled to use VTP, which information does it advertise onits trunk ports? (Select two)A. VTP modeB. STP root statusC. Negotiation statusD. Management domainE. Configuration revision numberAnswer: D, EQuestion:31Two switches are connected via a trunk link. In this network, the original frame isencapsulated and an additional header is added before the frame is carried over a trunk link.At the receiving end, the header is removed and the frame is forwarded to the assigned VLAN.This describes which technology?A. DISLB. ISLC. DTPD. IEEE 802.1QE. MPLSF. None of the other alternatives applyAnswer: BQuestion:32The core switches use 802.1Q trunks to connect to each other. How does 802.1Q trunking keep track of multiple VLANs?A. It tags the data frame with VLAN information and recalculates the CRC valueB. It encapsulates the data frame with a new header and frame check sequenceC. It modifies the port index of a data frame to indicate the VLAND. It adds a new header containing the VLAN ID to the data frameE. None of the other alternatives applyAnswer: AQuestion:33The core switches are configured to use 802.1Q trunks. Which three statements are correct with regard to the IEEE 802.1Q standard? (Select three)A. The IEEE 802.1Q frame format adds a 4 byte field to a Ethernet frameB. The packet is encapsulated with a 26 byte header and a 4 byte FCSC. The protocol uses point-to-multipoint connectivityD. The protocol uses point-to-point connectivityE. The IEEE 802.1Q frame uses multicast destination of 0x01-00-0c-00-00F. The IEEE 802.1Q frame retains the original MAC destination addressAnswer: A, D, FQuestion:34Switch PG1 has been configured with DTP using the desirable option. Which statementdescribes Dynamic Trunking Protocol (DTP) desirable mode?A. The interface actively attempts to convert the link to a trunk link.B. The interface is put into permanent trunking mode but prevented from generating DTPframes.C. The interface is put into permanent trunking mode and negotiates to convert the link into atrunk link.D. The interface is put into a passive mode, waiting to convert the link to a trunk link.E. None of the other alternatives applyAnswer: AQuestion:35You need to configure a new switch for trunking. Which switch command enables a trunking protocol that appends a four byte CRC to the packet?A. Switch(config-if)#switchport trunk encapsulation dot1qB. Switch(config-if)#switchport trunk encapsulation itefC. Switch(config-if)#switchport trunk encapsulation fddiD. Switch(config-if)#switchport trunk encapsulation islE. None of the other alternatives applyAnswer: DQuestion:36While using a packet analyzer, you notice four additional bytes being added to the packets inthe network. Which protocol inserts a four byte tag into the Ethernet frame and recalculates CRC value?A. DTPB. VTPC. 802.1QD. ISLE. None of the other alternatives applyAnswer: CQuestion:37You need to configure a new switch to support DTP. Which DTP switchport mode parameter sets the switch port to actively send and respond to DTP negotiation frames?A. AccessB. No negotiateC. TrunkD. Dynamic desirableE. Dynamic autoF. None of the other alternatives applyAnswer: DQuestion:38A new switch was just configured using the “switchport trunk native vlan 7”command. What does this interface command accomplish?A. Causes the interface to apply ISL framing for traffic on VLAN 7B. Configures the trunking interface to forward traffic from VLAN 7C. Configures the interface to be a trunking port and causes traffic on VLAN 7 to be 802.1qtaggedD. Configures the trunking interface to send traffic from VLAN 7 untaggedE. None of the other alternatives applyAnswer: DQuestion:39You need to connect two core switches via an ISL trunk. Which statement is true regarding the configuration of ISL trunks?A. A Catalyst switch cannot have ISL and IEEE 802.1q trunks enabled.B. All Catalyst switches support ISL trunking.C. A Catalyst switch will report giants if one side is configured for ISL while the other side isnot.D. ISL trunking requires that native VLANs match.E. None of the other alternatives applyAnswer: CQuestion:40Which of the following technologies would an Internet Service Provider use to supportoverlapping customer VLAN ID’s over transparent LAN services?A. 802.1q tunnelingB. ATMC. SDHD. IP Over Optical NetworkingE. ISLAnswer: AQuestion:41If you were to configure an ISL Ethernet trunk between two Cisco switches, named PG1 andPG2, what would you have to include at the end of the link for the trunk to operate correctly?(Select two)A. An identical VTP mode.B. An identical speed/duplex.C. An identical trunk negotiation parameter.D. An identical trunk encapsulation parameter.Question:42Refer to the exhibit. On the basis of the information provided in the exhibit, which two sets of procedures are best practicesfor Layer 2 and 3 failover alignment? (Choose two.)A .Configure the D-SW1 switch as the active HSRP router and the STP root for all VLANs.Configure the D-SW2 switch as the standby HSRP router and backup STP root for all VLANs.B. Configure the D-SW1 switch as the standby HSRP router and the STP root for VLANs 11 and 110.Configure the D-SW2 switch as the standby HSRP router and the STP root for VLANs 12 and 120.C. Configure the D-SW1 switch as the active HSRP router and the STP root for VLANs 11 and 110.Configure the D-SW2 switch as the active HSRP router and the STP root for VLANs 12 and 120.D. Configure the D-SW2 switch as the active HSRP router and the STP root for all VLANs.Configure the D-SW1 switch as the standby HSRP router and backup STP root for all VLANs.E. Configure the D-SW1 switch as the active HSRP router and the backup STP root for VLANs 11 and 110.Configure the D-SW2 switch as the active HSRP router and the backup STP root for VLANs 12 and 120.F. Configure the D-SW1 switch as the standby HSRP router and the backup STP root for VLANs12 a nd 120.Configure the D-SW2 switch as the standby HSRP router and the backup STP root for VLANs 11 and 110.Answer: CFExplanation:Basically, each of the routers that provides redundancy for a given gateway address is assigned to a common HSRP group. One router is elected as the primary, or active, HSRP router, another is elected as the standby HSRP router, and all the others remain in the listen HSRP state. The routers exchange HSRP hello messages at regular intervals, so they can remain aware of each。
Cisco,642-654,最新题库

Wide Area Application Services for System Engineers Number: 642-654 QUESTION 1Through which way does Cisco WAAS advanced compression DRE improve on traditional LZ compression?A. removing the transmission of previously-seen dataB. implementing a more aggressive, hardware-intensive version of the LZ compression algorithmC. pre-positioning often-used file segments on the edge WAE appliancesD. comparing hashes of each file version to avoid unnecessary file synchronization Answer: ASection: (none) Explanation/Reference:QUESTION 2Refer to the following tools, which two can be used to determine what percentage of WAN traffic will be optimized when you use a Cisco WAAS deployment? (Choose two.)A. IP SLAsB. NBARC. NetFlowD. TcpreplayAnswer: BCSection: (none) Explanation/Reference:QUESTION 3Which LAN traffic management feature is fully supported by Cisco WAAS?A. intrusion detection systemB. QoSC. NBARD. MPLSAnswer: BSection: (none) Explanation/Reference:QUESTION 4When WCCPv2 is running on a switch or router, what does it use to redirect traffic to a Cisco WAE?A. Layer 4-7 inspectionB. GRE tunnels or Layer 2 directionC. NBARD. MPLS tunnels or Layer 2 direction Answer: BSection: (none) Explanation/Reference:QUESTION 5Which method will most effectively provide management and monitoring failover for Cisco WAAS?A. Use multiple Cisco WAE devices at the data center.B. Use a primary and a secondary Central Manager.C. Use multiple Cisco WAE devices at each client location.D. Use a Cisco CDM at the data center and a Cisco CDM at the furthest client location. Answer: BSection: (none)Explanation/Reference:QUESTION 6In a Cisco WAAS environment, which TCP connection establishment messages should you examine if your customer has sent you a TCP protocol trace and asked for your help in understanding why the WAE appliances are failing to negotiate the correct, optimized policy?A. SYN and FINB. SYN and ACKC. SYN and SYN ACKD. ACK and SYN ACKAnswer: CSection: (none)Explanation/Reference:QUESTION 7Study the following exhibit carefully,your customer has installed its data center WAE as displayed Which configuration change can improve the performance of the WAE?A. change to a two-arm configurationB. use PBR redirection instead of WCCPv2C. create a PortChannel between the WAE and the routerAnswer: A Section: (none) Explanation/Reference:QUESTION 8 Your customer's service provider manages its WAN infrastructure. The customer would like to deploy Cisco WAAS to accelerate file services for a small number of branch offices, but the service provider manages the routers at each site and your customer's terms of service prohibit the customer from customizing router configurations. Which interception method will you recommend?A. PBRB. ACEC. WCCPv2D. inline card Answer: D Section: (none) Explanation/Reference:QUESTION 9 Which two options correctly identify the WAE file services integration modes available in Cisco WAAS? (Choose two.)A. transparent, in which the WAE appears as a node on the remote office LAN B. transparent, in which the WAE does not appear as a node on the remote office LANC. non-transparent, in which the WAE appears as a node on the remote office LAND. non-transparent, in which the WAE does not appear as a node on the remote office LAN Answer: BC Section: (none) Explanation/Reference:QUESTION 10 What is the function of the Catalyst 6500 ACE module in a Cisco WAAS solution?A. to perform application acceleration functions for CIFS applicationsB. to provide interception and load-balancing of WAE appliances in the data centerC. to support load balancing of large numbers of WAE appliances when deployed with WCCPv2D. to provide WAN optimization capabilities in the data center Answer: B Section: (none) Explanation/Reference:QUESTION 11 Which three are high-availability Cisco WAE solutions for a branch office? (Choose three.)A. PBRB. WCCPC. firewall load-balancing Cisco WAE devicesD. multiple Cisco WAE devices with inline cards Answer: ABD Section: (none)Explanation/Reference:QUESTION 12Your customer has purchased multiple Cisco WAE appliances, but does not want to dedicate one WAE for management purposes only. How would you advise this customer?A. There must be at least one Central Manager available for configuration and management tasks.B. The data center WAE can be used for both the Central Manager and Application Accelerator roles.C. There is no need for a dedicated Central Manager; all configuration tasks can be performed on the application accelerators using the WD. If one of the WAE appliances is configured as the Central Manager, then later, after all application accelerators are registered and on lincan be reconfigured as an application accelerator. Answer: ASection: (none) Explanation/Reference:QUESTION 13Which three characteristics are provided by Cisco WAAS to enable the consolidation of infrastructure from remote offices into the data center? (Choose three.)A. policy-based configurationB. auto-discovery of CIFS serversC. transparent integration into existing networksD. encapsulation of traffic between WAE appliances in GRE tunnels Answer: ABC Section: (none) Explanation/Reference:QUESTION 14In order to ensure the files are not stale, how often is the Cisco WAE running the edge file service able to cache previously-seen files?A. every time the file is modifiedB. every time the file is openedC. according to a user-specified scheduleD. every hour Answer: BSection: (none) Explanation/Reference:QUESTION 15When you size a Cisco WAAS solution, you should assume that how many of the total number of concurrent TCP connections per user will be optimized?A. 1-2B. 4-7C. 14-20D. 25-40Answer: BSection: (none) Explanation/Reference:QUESTION 16 The following diagram displays your customer's edge WAE configuration.Which WCCPv2 interception configuration can be applied to the Serial0 interface?A. Redirect out / service group 61B. Redirect in / service group 62C. Redirect out / service group 62D. Redirect in / service group 61 Answer: B Section: (none) Explanation/Reference:QUESTION 17 Refer to the following items, which high-availability method is used with inline interception?A. WCCPv2B. fail-to-wireC. load balancingD. load balancing with the ACE module Answer: B Section: (none)QUESTION 18 When using PBR, what do you need to configure to enable failover?A. QoSB. MPLSC. IP SLAsD. NetFlow Answer: C Section: (none) Explanation/Reference:QUESTION 19 One of your customers would like to use Active Directory to manage authentication for WAE administrative users. How to configure authentication in the Cisco WAAS Central Manager?A. Configure Active Directory as the primary login method.B. Configure TACACS+ services on the Active Directory server and set TACACS+ as the primary login method.C. Configure LDAP services on the Active Directory server and set LDAP as the primary login method.D. Configure RADIUS services on the Active Directory server and set RADIUS as the primary login method. Answer: A Section: (none) Explanation/Reference:QUESTION 20 Through which way does Cisco WAAS mark traffic so that network devices can apply QoS?A. QoS settings cannot be controlled in Cisco WAASB. the WCCP options in the Central ManagerC. the DSCP options in the traffic classifier configurationD. the DSCP options in the application definition Answer: D Section: (none) Explanation/Reference:QUESTION 21 What are three benefits of using the Cisco WAE file blocking feature? (Choose three.)A. eliminates data redundancyB. reduces the use of network resourcesC. minimizes the transfer of unsanctioned dataD. controls which file types are stored on the data center file server Answer: BCD Section: (none) Explanation/Reference:QUESTION 22A. Application OptimizerB. Central WAEC. Central ManagerD. Application AcceleratorAnswer: CDSection: (none)Explanation/Reference:QUESTION 23Can you tell me how to monitor optimization statistics for a given application across multiple CiscoWAE devices?A. Ensure that each application resides on a different subnet.B. Create a device group for all Cisco WAE devices on which the application is optimized.C. Create a separate application traffic policy for the application.D. Create a location group for all Cisco WAE devices on which the application is optimized. Answer: CSection: (none)Explanation/Reference:QUESTION 24Your customer is using firewalls. What must be permitted to pass through the firewalls in order to allow WAE auto-discovery?A. TCP optionsB. TCP port 139C. TCP port 445D. TCP SYN-ACK with dataAnswer: ASection: (none)Explanation/Reference:QUESTION 25The Cisco WAAS design of your customer calls for the Central Manager to be deployed on the Core WAE, which is a WAE-612 with 2GB of RAM. The customer initially configured the WAE as an application accelerator, and then issued the device mode central-manager command to enable Central Manager service. Now the customer complains that the WAE is no longer accelerating traffic. Why?A. The Central Manager and application accelerator cannot be deployed on the same WAE.B. Central Manager is consuming too much CPU time on the WAE. The Central Manager service should be implemented on a less-utilizedC. At least 4GB of RAM must be installed for the WAE to serve as both Central Manager and application accelerator.D. The device mode central-manager command must be issued before the device mode application-accelerator command. Answer: ASection: (none)Explanation/Reference:QUESTION 26Which function is performed by Cisco WAAS directed mode?B. to allow clients to manage the Central ManagerC. to allow clients to connect directly to the Central ManagerD. to allow third-party firewalls to support sequence number jumps with Cisco WAAS Answer: DSection: (none)Explanation/Reference:QUESTION 27Which two functions does the Central Manager provide in a Cisco WAAS environment? (Choose two.)A. application accelerationB. management of CIFS serversC. application statistics monitoringD. policy configuration and distributionAnswer: CDSection: (none)Explanation/Reference:QUESTION 28What is the advantage of generic GRE?A. Only one generic GRE tunnel can be created on the switch.B. It is faster than WCCP GRE.C. It speeds Layer 2 redirection.D. It does not spike the CPU on a Cisco Catalyst 6500 because generic GRE processes packets in hardware. Answer: DSection: (none)Explanation/Reference:QUESTION 29Which two benefits can we get by using Cisco WAAS with Cisco security devices such as Cisco Pix, Cisco ASA, and Cisco IOS firewalls? (Choose two.)A. The security devices will speed Cisco WAAS transport.B. Cisco WAAS requires Cisco security devices to be installed.C. The security devices can be configured to support Cisco WAAS automatic discovery.D. The security devices support the TCP sequence number jump that Cisco WAAS uses. Answer: CDSection: (none)Explanation/Reference:QUESTION 30How can you monitor optimization statistics for a given application across multiple Cisco WAE devices?A. Create a device group for all WAE devices on which that application is optimized.B. Create a location group for all WAE devices on which that application is optimized.C. Create a separate application traffic policy for each application.D. Ensure that each application resides on a different subnet.Answer: A本处有所有IT认证最新题库,考过付款,联系QQ:一0二0二二三一九八最新题库,保证一次性通过,60元一门。
cisco 642-631最新题库85题

A c t u al T es t s .c omWhich service component in the wireless operate phase helps isolate and resolve an incident?A. Change ManagementB. Configuration ManagementC. Incident ManagementD. Acceptance Test PlanAnswer: CQUESTION NO: 2On a Cisco Aironet 1240AG Series standalone access point, the radio LED is dark blue and blinking,but the status LED and Ethernet LED are both off. What does this indicate?A. A firmware upgrade is in progress.B. An access point buffer overflow is occurring.C. The access point is booting.D. The internal radio has failed.Answer: AQUESTION NO: 3You want to dynamically assign users to an 802.1Q VLAN as a result of their authentication. In order toaccomplish this, which two IETF RADIUS attributes should you configure on the Cisco Secure ACS?(Choose two.)A. 083 Tunnel-PreferenceB. 066 Tunnel-Client-EndpointC. 064 Tunnel-TypeD. 082 Tunnel-Assignment-IDE. 081 Tunnel-Private-Group-IDF. 067 Tunnel-Server-EndpointAnswer: C,EA ct u al T es t s .c omYou are charged with implementing a secure wireless installation which will provide Internetaccess to client devices but will not allow communications between wireless clients. In addition to implementing PSPF or peer-to-peer blocking on the wireless side, which of the following actions should you perform on the wired infrastructure?A. Implement a Cisco Secure IPS sensor.B. Implement 802.1X on the switch ports.C. Take no action, you have achieved your goal.D. Implement a protected port on the access switches.Answer: DQUESTION NO: 5A mobility group is created by a Cisco WLCM and 4402 Series Wireless LAN Controller. A client that isanchored on the Cisco WLCM roams to an access point on the 4402 controller. You then run a debugcommand on the 4402 controller.Which message would best describe the establishment of the tunnel from the foreign controller's perspective?A. Received Mobile Anchor Export messageB. Transmit Plumbing duplex mobility tunnel messageC. Received Plumbing duplex mobility tunnel messageD. Transmit Mobile Anchor Export messageAnswer: DQUESTION NO: 6In order for a controller-based access point to be allowed to participate in aggressive load balancing, itmust have heard the client within how many seconds?A. 15B. 10C. 1D. 5A ct u al T es t s .c omQUESTION NO: 7Which command will enable DHCP debugging on a WLAN controller?A. debugdhcp enableB. debugdhcp packet enableC. enabledebugdhcp packetD. debugdhcp status enableAnswer: BQUESTION NO: 8Choose the service component in the optimize phase which assesses the WLAN system and drivescontinuous improvements by recommending remediation measures including device configuration optimization, capacity planning, traffic analysis, security assessment, and quality issue resolution.A. Technology AssessmentB. Operations AssessmentC. Security AssessmentD. Security AdministrationE. Change ManagementF. Operations Readiness AssessmentAnswer: AQUESTION NO: 9In the operate phase, providing and maintaining reliable, current information about the WLAN systemhardware, software, and applications pertinent to the system's individual components and attributes is part of which service component?A. Problem ManagementB. Configuration ManagementC. Incident ManagementD. Change ManagementA ct u al T es t s .c omQUESTION NO: 10The IOS of a North American Cisco Aironet 1130AG Series standalone access point has become corrupt. You must therefore reload the TFTP firmware. Before you press and hold the MODE button, youshould verify that the file name is which of the following?A. c1130-k9w7-tar.bootB. c1130-k9w7-tar.123-7.JA1.tarC. c1130-k9w7-tar.defaultD. c1130-k9w7-tar.recoverAnswer: CQUESTION NO: 11Which of the following statements explains why it is normally best to have more than one controller-based access point participate in the containment of one rogue access point?A. Clients connected to the rogue access point must be able to connect to the containment controller-based access point.B. Multiple controller-based access points will load-balance the containment task using fewer resourcesthan a single access point.C. Clients connected to the rogue access point may be out of the range of the controller-based access pointproviding containment.D. Each controller-based access point can handle only a limited amount of clients connected to the rogueaccess points.Answer: CQUESTION NO: 12By default, on the WLAN controller for a voice application using Cisco 7921 wireless IP phones,A ct u al T es t s .c omB. 85 percentC. 56 percentD. 55 percentAnswer: AQUESTION NO: 13You are installing a Cisco 4402 Series Wireless LAN Controller. Which type of interface should you useon the controller's distribution port?A. 1000BASE-SX SFPB. 10/100/1000 Mbps RJ45C. 10/100 Mbps RJ45D. 10000BASE-SXAnswer: AQUESTION NO: 14When configuring a WLAN controller for a voice application using Cisco 7920 wireless IP phones,whichtwo general control settings should you select? (Choose two.)A. Multicast onB. Aggressive Load Balancing offC. Multicast offD. AP Fallback onE. Aggressive Load Balancing onF. AP Fallback offAnswer: B,CQUESTION NO: 15You are configuring an RF group of controllers that coordinate Radio Resource Management calculations. What is the maximum number of WLAN controllers that you can add?A ct u al T es t s .c omB. 20C. 12D. 24Answer: BQUESTION NO: 16During the installation of the Cisco WCS version 4.0, an error occurs. Where would you look for theinstallation log, in order to learn more about this error?A. at the root of the installation driveB. in the Cisco WCS installation directoryC. on the desktop of the serverD. in the Cisco WCS\Logs directoryAnswer: CQUESTION NO: 17You review the Failed Attempts logs on an AAA server and find: "unknown network access server error."Which failure could produce this error?A. AAA client and AAA server handshake failureB. supplicant authentication failureC. wrong password used by the supplicantD. failure of the wireless client and AAA server handshakeAnswer: AQUESTION NO: 18When optimizing a standalone point-to-multipoint bridge installation with eight non-root bridges,whichof the following RTS threshold and CWmin settings would be correct for the non-root bridges?A. RTS threshold = 1,CWmin = 4B. RTS threshold = 4000,CWmin = 5A ct u al T es t s .c omD. RTS threshold = 1,CWmin = 5Answer: DQUESTION NO: 19Which service component in the implement phase is typically performed prior to the handover of a wireless solution to the customer's operations organization?A. Systems IntegrationB. Skill AssessmentC. Systems Acceptance TestingD. Wireless CheckE. Project Close OutAnswer: CQUESTION NO: 20Which parameter, when enabled on a standalone access point, gives the highest priority to a voice packet even when QoS is not enabled?A. IGMP SnoopingB. WMMC. QoS Element for Wireless PhonesD. AVVID Priority MappingAnswer: CQUESTION NO: 21One of your customers has decided to deploy location-based services in addition to existing wirelessservices. The customer requires that the additional access points to be deployed in monitor-only mode. The most likely reason for this requirement is that the customer has which of these existing wireless devices?A. Data CollectionB. 802.11b/g VoIPC. 802.11b and g clientsA ct u al T es t s .c omQUESTION NO: 22When assigning a standalone access point a non-root role, which two parameters, other than Role inthe radio network settings, must be configured on the SSID Manager page? (Choose two.)A. Force Infrastructure Devices to associate only to this SSIDB. Set Infrastructure SSIDC. Multiple BSSIDD. Set Data Beacon RateE. Enable IP redirection on this SSIDAnswer: A,BQUESTION NO: 23Which definition best describes the staff training service component within the wireless implement phase?A. develops a training plan and delivers via a custom workshop or e-learningB. helps improve the performance and functionality of the infrastructure operations and network management systemC. reduces the risk of downtime caused by facilities-related problemsD. provides a step-by-step plan detailing the installation and service-commission requirement tasks to bestaged in a controlled implementation environment that emulates a customer networkAnswer: AQUESTION NO: 24Which protocol does the RADIUS server use inside the secure tunnel of EAP-FAST to authenticate theclient when one-time passwords are in use?A. GTCB. MD5C. MS-CHAP v2A ct u al T es t s .c omQUESTION NO: 25What is the recommended distance between controller-based access points for support of roaming?A. 50 feet [15 meters]B. 200 feet [60 meters]C. 150 feet [45 meters]D. 100 feet [30 meters]Answer: DQUESTION NO: 26A Cisco 4404 WLAN controller is being connected to a Cisco 6500 Catalyst Series Switch. How wouldyou interconnect and configure LAG for connectivity and ensure redundancy?A. All four ports from the Cisco WLC terminated to the same Catalyst gigabit module and channel group.B. Ports 1 and 2 from Cisco WLC to Catalyst gigabit module slot 1 channel group 10 and Cisco WLC ports3 and4 to Catalyst gigabit module slot 2 channel group 10.C. All four ports from the Cisco WLC terminated to the same Catalyst gigabit module using twochannel groups.D. Ports 1 and 2 from Cisco WLC to Catalyst gigabit module slot 1 channel group 20 and Cisco WLC ports 3 and 4 to Catalyst gigabit module slot 2 channel group 40.Answer: BQUESTION NO: 27How many WLANs can a Cisco Aironet 1242 in H-REAP mode support when actively connected to awireless controller? A. 4A ct u al T es t s.c omC. 8D. 16Answer: CQUESTION NO: 28Your customer has deployed a Cisco Wireless Location Appliance within its warehouse environment.However, employees there have been experiencing problems when tracking objects using active RFID tags.You use an access point scan to determine if the Location Appliance has been deployed correctly.Making which change to warehouse deployment location services will most likely correct the problem?A. ensure channels are deployed such that they do not overlapB. allow for the automatic containment of rogue access pointsC. ensure each area is covered by a minimum of three access pointsD. ensure a minimum RSSI value of -50Answer: CQUESTION NO: 29Cisco WCS version 4.0 is supported on which operating system?A. Windows 2000 SP4B. Windows Server 2003C. Solaris 10D. VistaE. Windows XP ProAnswer: BQUESTION NO: 30You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops.Youwant to increase the bandwidth available for the laptops by decreasing the bandwidth reserved for theA ct u al T es t s .c omWLAN controller?A. 55 percentB. 75 percentC. 40 percentD. 25 percentAnswer: CQUESTION NO: 31On a Cisco Aironet 802.11 a/b/g wireless LAN client adapter, the status LED and activity LED are alternating on and off. What does this indicate?A. The client card is not associated to the network.B. The client card has awakened from power-save mode.C. The driver has been installed incorrectly.D. The client card has failed.Answer: AQUESTION NO: 32Which Cisco Aironet Series has a built-in digital thermometer designed to protect the radio?A. CiscoAironet 1500 SeriesB. CiscoAironet 1400 SeriesC. CiscoAironet 1200 SeriesD. CiscoAironet 1300 SeriesAnswer: DQUESTION NO: 33Which of the following wireless service components occur in the implement phase?A. Project Kickoff, Staging, Systems Acceptance Testing, Ongoing Support Handoff MeetingB. WLAN Change Management, Security Administration, Technology Assessment, Operations PlanC. Security Assessment, Operations Assessment, Supplier ManagementD. Operations Readiness Assessment, Systems Requirements Validation, Planning Project Kickoff, ServiceA ct u al T es t s .c omAssuranceAnswer: AQUESTION NO: 34Which of the following best describes the purpose of using lifecycle services for deploying an advanced wireless solution?A. Create a more effective sales strategy for partners.B. Reinforce customer confidence in partners selling products.C. Provide a consistent, repeatable, and proven method to ensure the network solution that is deployeddelivers upon the customer's goals for reliability and availability.D. Maximize the number of services required to support advanced technologies.E. More clearly define the roles of account managers, systems engineers, and field engineers.Answer: CQUESTION NO: 35You are configuring a wireless LAN controller for QoS. Which 802.11e user priority tag should you applyto voice applications? A. 3B. 6C. 4D. 1Answer: BQUESTION NO: 36Clients using Cisco-LEAP and EAP-FAST authentication are having no problems logging on to the wireless network, but clients using PEAP are failing to log on. Which situation would result in this type of problem?A. Posture validation has not been enabled.B. The AAA server is set to accept both MS-CHAP v2 and GTC for PEAP authentication.A ct u al T es t s .c omC. Clients and server are not using certificates.D. Clients have been set to validate the server identity.Answer: CQUESTION NO: 37Which three of these user groups are available on Cisco WCS version 4.0? (Choose three.)A. AdminB. Users AssistantC. System MonitoringD. Power UsersE. AdministratorsF. Network OperatorAnswer: A,B,CQUESTION NO: 38On a Cisco 1000 Series controller-based access point, the alarm LED is flashing red, but the other LEDs are off. What is this access point indicating?A. Its IP address already exists.B. It is operating normally.C. It requires a code upgrade.D. It has lost contact with the controller.Answer: AQUESTION NO: 39In which service component of the wireless operate phase are incident trends analyzed to identify patterns and systemic conditions?A. System MonitoringB. Security AdministrationC. Operations SetupD. Problem ManagementAnswer: DA ct u al T es t s .c omYou are trying to change the polling parameters used by the location manager via the Cisco WCS,andyour request is being denied. What is wrong?A. Polling values can be changed only in the maintenance window.B. Polling values can be changed only on the location server.C. Your login does not have the correct permissions.D. You must wait for the location server to become available.Answer: CQUESTION NO: 41A client roams from H-REAP AP1 to H-REAP AP2. The client is unable to associate to H-REAP AP2.H-REAP AP2 has six other clients associated to it, which continue to pass traffic. What has caused this problem?A. H-REAP AP1 has reached its client limit.B. H-REAP AP2 has reached its client limit.C. H-REAP AP2 lost its connection to the controller.D. H-REAP AP1 lost its connection to the controller.Answer: CQUESTION NO: 42If it is properly deployed, a controller-based access point is capable of monitoring all VLANs on a network when you select which of the following modes from the AP Mode drop-down menu on the controller?A. MirrorB. Rogue DetectorC. SnifferD. MonitorAnswer: BA ct u al T es t s .c omThe tag timeout value for a Cisco Wireless Location Appliance should be set to which tag beacon rate?A. 4 to 6 times the tag beaconing rateB. 10 to 12 times the tab beaconing rateC. 8 to 10 times the tag beaconing rateD. 6 to 8 times the tag beaconing rateAnswer: CQUESTION NO: 44Which two service components are performed during the wireless implement phase? (Choose two.)A. Project PlanningB. Configuration ManagementC. Wireless Readiness AssessmentD. Systems Acceptance TestingE. Site Readiness SpecificationAnswer: A,DQUESTION NO: 45The WLAN controller maintains up to how many controller crash files?A. 10B. 5C. 15D. 20Answer: BQUESTION NO: 46What is the maximum number of WLAN controllers that can join a single mobility group?A ct u al T es t s .c omD. 24Answer: DQUESTION NO: 47When configuring Cisco Secure ACS to support wireless EAP authentication, which device must beconfigured as a AAA client?A. Location ApplianceB. controller-based access pointsC. wireless clientsD. Wireless Control SystemE. wireless controllersAnswer: EQUESTION NO: 48How many RADIUS servers can be added to a controller and thereafter assigned to the authentication oraccounting of individual WLAN IDs?A. 14B. 15C. 17D. 16Answer: CQUESTION NO: 49When configuring QoS on a wireless controller, the per-user, real-time bandwidth contract is enforced forwhich of the following protocols?A. IPXA ct u al T es t s .c omAnswer: CQUESTION NO: 50You are installing a Cisco Aironet 1000 Series controller-based access point. When you boot it, all theLEDs on the access point blink together. What does this indicate about the access point?A. duplicate IP addressB. code upgrade in progressC. normal operationD. searching for primary controllerAnswer: BQUESTION NO: 51Your customer has deployed a Cisco Wireless Location Appliance within its warehouse environment.However, employees there have been experiencing problems when tracking objects using active RFID tags.The RFID beacon rate is 10 seconds and you have discovered an issue with the RFID timeout value.Where and how should the RFID value be changed?A. on the Cisco WCS, to 95 secondsB. on the wireless controller, to 45 secondsC. on the wireless controller, to 95 secondsD. on the Cisco WCS, to 45 secondsAnswer: CQUESTION NO: 52EAP-FAST provides a secure tunnel during Phase One to protect the user's authentication credentials.Which of these entities initializes the secure tunnel?A ct u al T es t s .c omA. x.509 certificateB. generic token cardC. preshared keyD. Protected Access CredentialAnswer: DQUESTION NO: 53Which of the following settings will reduce packet overhead and overall latency in a standalone point-to-point bridge deployment?A. enable concatenation on the non-root bridge onlyB. enable concatenation on the root bridge onlyC. enable concatenation on both the root bridge and non-root bridgeD. enable concatenation on the root bridge and set it as desirable on the non-root bridgeE. set concatenation as desirable on the root bridge and enable it on the non-root bridgeAnswer: CQUESTION NO: 54When configuring a Cisco 3845 Integrated Services Router to support 802.11b and g clients,which of the following commands would be correct?A. router (config-if)# speed basic-1.0 2.0 5.5 6.0 9.0 11.0 12.0 18.0 24.0 36.0 48.0 54.0B. router (config-if)# speed 1.0 2.0 5.5 6.0 9.0 basic-11.0 12.0 basic-18.0 24.0 36.0 48.0 54.0C. router (config-if)# speed basic-1.0 2.0 5.5 basic-6.0 9.0 11.0 12.0 18.0 24.0 36.0 48.0 54.0D. router (config-if)# speed 1.0 2.0 5.5 basic-6.0 9.0 11.0 12.0 18.0 24.0 36.0 48.0 54.0Answer: AQUESTION NO: 55You are using standalone Cisco Aironet 1400 Series Wireless Bridges for a nine-mile point-to-pointwireless link between two buildings. Which distance setting should you use for the bridge configured as the root?A. 20 km [12.4 miles]A ct u al T es t s .c omB. 10 km [6.2 miles]C. 5 km [3.1 miles]D. 25 km [15.5 miles]E. 15 km [9.3 miles]Answer: EQUESTION NO: 56Which authentication types are allowed with the Cisco ADU when selecting WPA/WPA2/CCKM underthe security options?A. Cisco-LEAP, EAP-FAST, EAP-PEAP (GTC), EAP-TLSB. Cisco-LEAP, EAP-PSK, EAP-PEAP (MS-CHAP v2), EAP-TLSC. Cisco-LEAP, EAP-FAST, EAP-PEAP (MS-CHAP v2), EAP-TTLSD. Cisco-LEAP, EAP-MD5, EAP-PEAP (GTC), EAP-TTLSAnswer: AQUESTION NO: 57If all client exclusion policies are enabled, on which number of tries will 802.1X authentications be excluded using controller-based access points?A. fiveB. threeC. sixD. fourAnswer: DQUESTION NO: 58The Cisco Lifecycle Services approach for wireless solutions provides a framework for which of thefollowing opportunities?A. partners having a discussion with customers about the minimum service components needed to successfully deploy a wireless solutionB. customers determining a competitor's strategy for adopting advanced technologiesA ct u al T es t s.c omC. partners choosing the right products for their customersD. customers choosing the right products for their networkE. customers defining the correct strategy for advanced technology adoptionAnswer: AQUESTION NO: 59Your customer has deployed a Cisco Wireless Location Appliance within its warehouse environment.However, employees there have been experiencing problems when tracking objects using active RFID tags.The RFID tag data is not being collected.On which device would you verify that RFIDs have been enabled?A. access pointB. location managerC. wireless controllerD. Cisco WCSAnswer: CQUESTION NO: 60Which of the following commands on the wireless interface of a Cisco 3845 Integrated Services Routerallows the SSID to broadcast?A. router (config-ssid)# guest-modeB. router (config-ssid)# advertiseC. router (config-ssid)# enableD. router (config-ssid)# broadcastAnswer: AQUESTION NO: 61In a deployment using standalone access points, clients set up to authenticate with EAP-PEAP or EAP-Cisco Wireless (Cisco-LEAP) cannot authenticate. When you inspect the Failed Attempts report onthe Cisco Secure ACS, you find this error: "Unknown network access server NAS." Which problemA ct u al T es t s .c omhave caused this failure?A. misconfigured IP address of the AAA server on the access pointB. misconfigured EAP type on the access pointC. misconfigured IP address of the access point on the AAA serverD. misconfigured EAP type on the AAA serverAnswer: CQUESTION NO: 62On a Cisco Aironet 1130AG Series standalone access point, the status LED is dark blue and blinking.What does this indicate?A. The internal radio has failed.B. A firmware upgrade is in progress.C. An access point buffer overflow is occurring.D. The access point is booting.Answer: BQUESTION NO: 63Which Cisco Aironet Series devices can be powered using 802.3af inline power?A. CiscoAironet 1400 SeriesB. CiscoAironet 1300 SeriesC. CiscoAironet 1100 SeriesD. CiscoAironet 1240AG SeriesAnswer: DQUESTION NO: 64Which three wireless service components belong to the operate phase? (Choose three.)A. Operations PlanB. Operations AssessmentC. Security AdministrationA ct u al T es t s .c omE. Operations ImplementationF. Incident ManagementAnswer: C,D,FQUESTION NO: 65You are troubleshooting a one-way call problem with a Cisco 7920 wireless IP phone on a standaloneWLAN. What may have caused this problem?A. The minimum data rate is not set to 11 Mbps.B. Publicly Secure Packet forwarding is enabled.C. The access point is set to the least congested channel.D. An address resolution protocol has been disabled.Answer: DQUESTION NO: 66How does a controller-based access point configured to operate in sniffer mode behave?A. allows client traffic, captures data on all channelsB. allows client traffic, captures data on a single channelC. allows no client traffic, captures data on all channelsD. allows no client traffic, captures data on a single channelAnswer: DQUESTION NO: 67Which of these statements is true about SSIDs configured in Cisco ADU?A. SSIDs are not case-sensitive.B. SSIDs must be listed in the same order in the ADU as they are in the access point.C. A maximum of three SSIDs may be configured.D. SSIDs may have a maximum of 16 characters.Answer: CA ct u al T es t s .c omYou have just finished aligning a Cisco Aironet 1400 Series Wireless Bridge link using installation mode.When you set the link back to operational mode you loose association to the root bridge. Which action will correct the problem?A. Configure the bridge to force infrastructure devices to associate only to the SSID parameter.B. Enable passwords on both bridges.C. Configure the distance parameter value.D. Configure the proper channel.Answer: CQUESTION NO: 69On a standalone access point, client association using EAP-Cisco Wireless (Cisco-LEAP) is failing, butassociation using EAP-PEAP is functioning. What needs to be enabled on the standalone access point to correct this issue?A. network EAPB. open authentication plus MACC. open authentication plus EAPD. a shared keyAnswer: AQUESTION NO: 70Select the wireless service component in the implement phase in which operations responsibilities aredefined and transferred to the operate phase team.A. Ongoing Support Handoff MeetingB. Staff TrainingC. Detailed Design DevelopmentD. Staging and System MigrationAnswer: AA ct u al T es t s .c omWhich wireless service component is associated with maintaining historical and current informationabout the WLAN solution?A. Acceptance Test PlanB. Change ManagementC. Incident ManagementD. Configuration ManagementAnswer: DQUESTION NO: 72A Cisco Aironet 1020 controller-based access point has been connected to a Catalyst 3550-24PWRSwitch. However, when it is powered up, the access point fails. What has caused this problem?A. access point does not support 802.11hB. incorrect switch power supplyC. switch port is not enabledD. switch does not support 802.3afE. access point has not been initialized with the primary controllerAnswer: DQUESTION NO: 73You have been called upon to add location-based services into an existing controller-based wireless design which primarily encompasses handheld devices such as barcode scanners and Cisco 7920 wireless IP phones. In which mode should you deploy the additional access points to achieve the density required without excessive co-channel interference?A. tracking modeB. monitor modeC. location modeD. sniffer modeAnswer: BA ct u al T es t s .c omWhich of the following parameter sets must be configured on the Cisco Wireless Location Appliance?A. network connectionsB. location viewsC. access pointsD. object definitionsAnswer: AQUESTION NO: 75A Cisco Wireless Location Appliance has been added to track RFID tags placed on laptops being usedin a school. Classrooms at the school have concrete block walls. During testing, you discover that theaccuracy of the system needs to be improved. You decide to edit the map in the Cisco WCS to add theinterior walls.How many interior walls can you add to improve the accuracy of the location appliance?A. 50B. 150C. 100D. 200Answer: AQUESTION NO: 76You are using ADU and are authenticated and associated to an access point. However, you are unableto obtain an IP address. Which of these has caused this problem?A. invalid SSIDB. invalid WEP keyC. invalid encryption typeD. invalid 802.1X authentication type。
CCNP相关题库大集合

CCNP相关题库大集合、全搜索,绝对便于查找。
(持续更新新题库)互联神州test ccnp 825 845 892 最新题库可打印 9月29日更新/thread-26194-1-1.html最新642-901 v 3.10 (353题)/thread-40433-1-1.html642-825 全新P4S3.10 上传完成/thread-43635-1-1.html最新 2008 4月10日 pass4sure 8923.23/thread-35203-1-1.html845新版P4S 217Q /thread-31290-1-2.html892中文解释/thread-32344-1-2.html(关注)总结最近考了NP(892__845__825)的诸多网友所看题库如下/thread-31157-1-3.html642_892P4A3.23考试题库之经验总结(包括所有试验及CASE题)/thread-35484-1-3.html08年2月21日更新,最新新CCNP Pass4sure(P4S) 下载帖(642-901、812、825、845、892)/thread-10901-1-5.html642-892 pass4sure 2.93 修订版/thread-30046-1-7.html3月 testinside p4s ccna&ccnp全套题库/thread-32576-1-8.htmlTestKing(TK) 642-901 v12(2007年7月12日更新)/thread-23115-1-11.htmlCCNP642————845考试部分CASE题及选择题题解(全是考试网友的经验总结)/thread-34853-1-12.html642-845最新P4Sv3.10_312Q /thread-38915-1-21.html642——825P4S2.93考试经验之总结(包含所有CASE题)/thread-35483-1-21.htmlP4S 642-845 2.95 PDF打印版/thread-35447-1-3.html892 P4 2.93不加密版本/thread-28916-1-7.html642_892p4s3.27 /thread-40501-1-7.ht ml08.3月 testinside p4s ccna&ccnp全套题库/thread-32576-1-8.htmlPass4sure+642-812+3[1].10 /thread-40683-1-1.html642—901P4S.3.83题库/thread-42299-1-1.html 642——812pass4side3.57/thread-4 2942-1-1.html包含了8道新题和case的战报/thread-43032-1-5.html 642——845p4s-109题/thread-42314-1-4.html如何解决Pass4sure 3.10 需要订单号的问题/thread-43789-1-1.html。
ccnp测试题及答案

ccnp测试题及答案1. 在CCNP认证中,关于VLAN的以下哪个说法是正确的?A. VLAN是将交换机端口划分为多个广播域B. VLAN是将路由器端口划分为多个广播域C. VLAN是将无线接入点划分为多个广播域D. VLAN是将服务器划分为多个广播域答案:A2. 在Cisco网络设备中,哪个命令用于创建一个新的VLAN?A. `switchport mode access`B. `switchport mode trunk`C. `vlan database`D. `configure terminal`答案:C3. 以下哪个协议用于在不同VLAN之间路由?A. EIGRPB. OSPFC. RIPD. VTP答案:A4. 在Cisco设备上,如何将接口配置为Trunk模式?A. `switchport mode access`B. `switchport mode trunk`C. `interface vlan 1`D. `interface fastethernet 0/1`答案:B5. 以下哪个命令用于在Cisco设备上查看VLAN信息?A. `show vlan`B. `show interfaces`C. `show ip interface brief`D. `show running-config`答案:A6. 在CCNP考试中,关于EIGRP协议的以下哪个说法是错误的?A. EIGRP是一个距离矢量路由协议B. EIGRP使用DUAL算法计算最短路径C. EIGRP支持VLSM和CIDRD. EIGRP仅在Cisco设备上可用答案:D7. 在Cisco设备上,如何配置EIGRP的自动汇总?A. `router eigrp 100`B. `no auto-summary`C. `ip summary-address eigrp 100 0.0.0.0 0.0.0.0`D. `metric weights 0 1 1 1 0 0 0 1`答案:C8. 以下哪个命令用于在Cisco设备上查看EIGRP邻居?A. `show ip eigrp neighbors`B. `show ip ospf neighbors`C. `show ip rip neighbors`D. `show ip eigrp interface`答案:A9. 在CCNP考试中,关于OSPF协议的以下哪个说法是正确的?A. OSPF仅在Cisco设备上可用B. OSPF使用RIP算法计算最短路径C. OSPF支持VLSM和CIDRD. OSPF使用广播来发现邻居答案:C10. 在Cisco设备上,如何配置OSPF的Hello和Dead间隔?A. `ip ospf hello-interval 10`B. `ip ospf dead-interval 40`C. `timers 10 40`D. `ospf hello-interval 10 dead-interval 40`答案:C结束语:以上是CCNP测试题及答案,希望对您的学习和准备有所帮助。
ccnp642-825实验题hq

复习内容p4s ++成都战报+北京战报全部选B,碰到的题型51道HQ+1SDM+PPPOE+AAAHQ不说了,按照以下解法即可,p4s的答案是根本错误的**********************************************************HQ解法:(转自论坛某高人~)HQ的解法我是参照论坛上的,不难、背答案是绝对不行的,我做的就和P4S上的完全不一样,五种错误的顺序会变,首先5个错误你得心里有数1 ergipAS错误2 tunnel 来源3 tunnel 目的4 默认路由5 network发部不完整。
上面的5点,想过的都给我背好了!!!这道题出来后,拓扑跟题库上一样,拓扑请看题库,解题步骤请看下面(解题不要按第一题到第五题做下来,那样太难了。
其实他们是有前后关系的。
看完步骤你就明白了)左边的叫hq右边的是1-5然后5个问题一共第一步打开所有设备一共6个(包括hq)第二步全部输入show run (前面要en一下)第三步看配置从1-5里面先看(考试时候给的名字不同,但也是按1-5排列的)好像叫brance1 brance2 (5)第四步从这1-5里面找哪个没有ip route 0.0.0.0 ..(默认路由)第五步因为只有一台没有找到后比方说branc1上发现他没有就去题目里找brance1关键词,然后就在该题目里选择miss default route(没有默认路由那个选项)第六步看hq那台eigrp as号码跟1-5对比。
哪个不对,参照第5步。
把答案选好第七步到此做对2题了,然后讲tunnel来源和目的考试的时候你会发现1-5的配置里面全部是tunnel 0后面有一个tunnel来源一个tunnel目的这个结构的!!结构哦。
(来源是本地,目的是对端)第八步这个怎么看呢!!先看hq的配置它上面一共有五个tunnel配置一般是tunnel11 tunnel12 tunnel13.....5对应的连到右边拓扑连到对面的5个计算机上的1-5 的tunnel第九步hq上比方说我们看tunnel 11 对应的是右边第一个brace1 上的配置tunnel0结构里的内容(1-5上都叫tunnel0跟hq不太一样hq上倒分11-15区别开的)第十步先看brance1看到tunnel0里面写的是tunnel source s0/2 那么表示用本地接口s0/2做本地来源然后去对端hq看tunnel11里面的tunnel目的地址是不是和右边brance1本地s0/2地址匹配如果一样就对了。
ccnp模拟试题与答案

C i s c o C C N P842-813e x a m Question:1uses layer 3 switches in the Core of their network. Which method of Layer 3switching uses a forwarding information base (FIB)A. Topology-based switchingB. Demand-based switchingC. Route cachingD. Flow-based switchingE. None of the other alternatives applyAnswer: AQuestion:2You need to design the VLAN scheme for the network. Which two statements aretrue about best practices in VLAN design (Select two)A. Routing should occur at the access layer if voice VLANs are utilized. Otherwise, routing should occur at the distribution layer.B. Routing should always be performed at the distribution layer.C. VLANs should be localized to a switch.D. VLANs should be localized to a single switch unless voice VLANs are being utilized.E. Routing should not be performed between VLANs located on separate switches.Answer: B, CQuestion:3If you needed to transport traffic coming from multiple VLANs (connected between switches), and your CTO was insistent on using an open standard, which protocol would you useA.B. spanning-treeC.D. ISLE. VTPF.Answer: CQuestion:4Under what circumstances should an administrator prefer local VLANs over end-to-end VLANsA. Eighty percent of traffic on the network is destined for Internet sites.B. There are common sets of traffic filtering requirements for workgroups located in multiple buildings.C. Eighty percent of a workgroup’s traffic is to the workgroup’s own local server.D. Users are grouped into VLANs independent of physical location.E. None of the other alternatives applyAnswer: AQuestion:5What are some virtues of implementing end-to-end VLANs (Choose two)A. End-to-end VLANs are easy to manage.B. Users are grouped into VLANs independent of a physical location.C. Each VLAN has a common set of security and resource requirements for all members.D. Resources are restricted to a single location.Answer: B, CQuestion:6Which of the following statements is true about the 80/20 rule (Select all that apply)A. 20 percent of the traffic on a network segment should be localB. no more than 20 percent of the network traffic should be able to move across a backbone.C. no more than 80 percent of the network traffic should be able to move across a backbone.D. 80 percent of the traffic on a network segment should be localAnswer: B, DQuestion:7The LAN is becoming saturated with broadcasts and multicast traffic. What couldyou do to help a network with many multicasts and broadcastsA. Creating smaller broadcast domains by implementing VLANs.B. Separate nodes into different hubs.C. Creating larger broadcast domains by implementing VLANs.D. Separate nodes into different switches.E. All of the above.Answer: AQuestion:8The LAN switches are being configured to support the use of Dynamic VLANs.Which of the following are true of dynamic VLAN membership (Select all that apply)A. VLAN membership of a user always remains the same even when he/she is moved to another location.B. VLAN membership of a user always changes when he/she is moved to another location.C. Membership can be static or dynamic.D. Membership can be static only.E. None of the other alternatives apply.Answer: A, CQuestion:9The LAN switches are being configured to support the use of Dynamic VLANs.What should be considered when implementing a dynamic VLAN solution (Select two)A. Each switch port is assigned to a specific VLAN.B. Dynamic VLANs require a VLAN Membership Policy Server.C. Devices are in the same VLAN regardless of which port they attach to.D. Dynamic VLAN assignments are made through the command line interface.Answer: B, CQuestion:10In the three-layer hierarchical network design model; what’s associated with the access layer (Select two)A. optimized transport structureB. high port densityC. boundary definitionD. data encryptionE. local VLANsF. route summariesAnswer: B, EQuestion:11You are assigning VLANs to the ports of switch PG1. What VLAN number value is an assigned to the default VLANA. VLAN 1003B. VLAN 1C. VLAN OND. VLAN AE. VLAN 0Answer: BQuestion:12The VLANs in switch PG1 are being modified. Which of the following are updated in PG1 every time a VLAN is modified (Select all that apply)A. Configuration revision numberB. Configuration revision flag fieldC. Configuration revision reset switchD. Configuration revision databaseE. None of the other alternatives apply.Answer: A, DQuestion:13What is a characteristic of assigning a static VLAN membershipA. VMPS server lookup is requiredB. Easy to configureC. Easy of adds, moves, and changesD. Based on MAC address of the connected deviceAnswer: BQuestion:14Static VLANs are being used on the network. What is true about static VLANsA. Devices use DHCP to request their VLAN.B. Attached devices are unaware of any VLANs.C. Devices are assigned to VLANs based on their MAC addresses.D. Devices are in the same VLAN regardless of which port they attach to.Answer: BQuestion:15Two switches are connected via a trunk using VTP. Which VTP information doesa Catalyst switch advertise on its trunk ports when using VTP (Select two)A. STP root statusB. VTP modeC. Negotiation statusD. Management domainE. Configuration revision numberAnswer: D, EQuestion:16You need to investigate a VTP problem between two switches. The lack of whichtwo prevents VTP information from propagating between switches (Select two)A. A root VTP serverB. A trunk portC. VTP priorityD. VLAN 1E. None of the other alternatives applyAnswer: B, DQuestion:17PG1 and PG2 are switches that communicate via VTP. What is the default VTP advertisement intervals in Catalyst switches that are in server or client modeA. 30 secondsB. 5 minutesC. 1 minuteD. 10 secondsE. 5 secondsF. None of the other alternatives applyAnswer: BQuestion:18You want to configure switch PG1 to propagate VLAN information across thenetwork using VTP. What must be configured on a Cisco switch in order to advertise VLAN informationA. VTP modeB. VTP passwordC. VTP revision numberD. VTP pruningE. VTP domain nameF. None of the other alternatives applyAnswer: EQuestion:19The switches have all been upgraded to use VTP version 2. What are two benefits provided in VTP Version 2 that are not available in VTP Version 1 (Select two)A. VTP version 2 supports Token Ring VLANsB. VTP version 2 allows VLAN consistency checksC. VTP version 2 allows active redundant links when used with spanning treeD. VTP version 2 reduces the amount of configuration necessaryE. VTP version 2 saves VLAN configuration memoryAnswer: A, BQuestion:20The network administrator needs to enable VTP pruning within thenetwork. What action should a network administrator take to enable VTP pruning on an entire management domainA. Enable VTP pruning on any switch in the management domainB. Enable VTP pruning on any client switch in the domainC. Enable VTP pruning on a VTP server in the management domainD. Enable VTP pruning on every switch in the domainE. None of the other alternatives applyAnswer: CQuestion:21VTP is configured on switch PG1. Which of the following features were added in VTP version2 that were not previously supported in VTP version 1 (Select two)A. Supports Token Ring VLANs.B. Allows VLAN consistency checks.C. Saves VLAN configuration memory.D. Reduces the amount of configuration necessary.E. Allows active redundant links when used with spanning tree.Answer: A, BQuestion:22The switches are configured to use VTP. What’s true about the VLAN trunkingprotocol (VTP) (Select two)A. VTP messages will not be forwarded over nontrunk links.B. VTP domain names need to be identical. However, case doesn’t matter.C. A VTP enabled device which receives multiple advertisements will ignore advertisements with higher configuration revision numbers.D. A device in “transparent” VTP mode will not forward VTP messages.E. VTP pruning allows switches to prune VLANs that do not have any active ports associated with them.Answer: A, DQuestion:23Switch PG1 and PG2 both belong to the VTP domain. What’s true about theswitch operation in VTP domains (Select all that apply)A. A switch can only reside in one management domainB. A switch is listening to VTP advertisements from their own domain onlyC. A switch is listening to VTP advertisements from multi domainsD. A switch can reside in one or more domainsE. VTP is no longer supported on Catalyst switchesAnswer: A, BQuestion:24VTP devices in a network track the VTP revision number. What is a VTP configuration revision numberA. A number for identifying changes to the network switch.B. A number for identifying changes to the network router.C. A number for identifying changes to the network topology.D. None of the other alternatives apply.Answer: CQuestion:25Switch PG1 is configured to use the VLAN Trunking Protocol (VTP). What does PG1 advertise in its VTP domainA. The VLAN ID of all known VLANs, the management domain name, and the total number oftrunk links on the switch.B. The VLAN ID of all known VLANs, a 1-bit canonical format (CF1 Indicator), and the switchconfiguration revision number.C. The management domain name, the switch configuration revision number, the known VLANs, and their specific parameters.D. A 2-byte TPID with a fixed value of 0x8100 for the management domain number, the switch configuration revision number, the known VLANs, and their specific parameters.E. None of the other alternatives apply.Answer: CQuestion:26VTP switches use advertisements to exchange information with each other. Which of the following advertisement types are associated with VTP (Select all that apply)A. Domain advertisementsB. Advertisement requests from clientsC. Subset advertisementsD. Summary advertisementsAnswer: B, C, DQuestion:27Switch PG1 is part of the VTP dom ain. What’s true of VTP Pruning within this domain (Select all that apply)A. It does not prune traffic from VLANs that are pruning-ineligibleB. VLAN 1 is always pruning-eligibleC. it will prune traffic from VLANs that are pruning-ineligibleD. VLAN 2 is always pruning-ineligibleE. None of the other alternatives apply.Answer: AQuestion:28What action should you execute if you wanted to enable VTP pruning on your entire management domainA. Enable VTP pruning on any client switch in the management domain.B. Enable VTP pruning on any switch in the management domain.C. Enable VTP pruning on every switch in the management domain.D. Enable VTP pruning on a VTP server in the management domain.E. Disable VTP pruning on a VTP server in the management domain.Answer: DQuestion:29Switch PG1 is configured with VTP. Which two VTP modes will make PG1 capable of creatingand deleting VLANs on itself (Select two)A. ClientB. ServerC. TransparentD. Pass-throughE. No-negotiateAnswer: B, CQuestion:30When the Catalyst switch PG1 is enabled to use VTP, which information does it advertise on its trunk ports (Select two)A. VTP modeB. STP root statusC. Negotiation statusD. Management domainE. Configuration revision numberAnswer: D, EQuestion:31Two switches are connected via a trunk link. In this network, the original frame is encapsulated and an additional header is added before the frame is carried over a trunk link. At the receiving end, the header is removed and the frame is forwarded to the assigned VLAN. This describes which technologyA. DISLB. ISLC. DTPD. IEEEE. MPLSF. None of the other alternatives applyAnswer: BQuestion:32The core switches use trunks to connect to each other. How doestrunking keep track of multiple VLANsA. It tags the data frame with VLAN information and recalculates the CRC valueB. It encapsulates the data frame with a new header and frame check sequenceC. It modifies the port index of a data frame to indicate the VLAND. It adds a new header containing the VLAN ID to the data frameE. None of the other alternatives applyAnswer: AQuestion:33The core switches are configured to use trunks. Which three statementsare correct with regard to the IEEE standard (Select three)A. The IEEE frame format adds a 4 byte field to a Ethernet frameB. The packet is encapsulated with a 26 byte header and a 4 byte FCSC. The protocol uses point-to-multipoint connectivityD. The protocol uses point-to-point connectivityE. The IEEE frame uses multicast destination of 0x01-00-0c-00-00F. The IEEE frame retains the original MAC destination addressAnswer: A, D, FQuestion:34Switch PG1 has been configured with DTP using the desirable option. Which statement describes Dynamic Trunking Protocol (DTP) desirable modeA. The interface actively attempts to convert the link to a trunk link.B. The interface is put into permanent trunking mode but prevented from generating DTPframes.C. The interface is put into permanent trunking mode and negotiates to convert the link into a trunk link.D. The interface is put into a passive mode, waiting to convert the link to a trunk link.E. None of the other alternatives applyAnswer: AQuestion:35You need to configure a new switch for trunking. Which switch command enablesa trunking protocol that appends a four byte CRC to the packetA. Switch(config-if)#switchport trunk encapsulation dot1qB. Switch(config-if)#switchport trunk encapsulation itefC. Switch(config-if)#switchport trunk encapsulation fddiD. Switch(config-if)#switchport trunk encapsulation islE. None of the other alternatives applyAnswer: DQuestion:36While using a packet analyzer, you notice four additional bytes being added to the packets in the network. Which protocol inserts a four byte tag into the Ethernet frame and recalculates CRC valueA. DTPB. VTPC.D. ISLE. None of the other alternatives applyAnswer: CQuestion:37You need to configure a new switch to support DTP. Which DTP switchport mode parameter sets the switch port to actively send and respond to DTP negotiation framesA. AccessB. No negotiateC. TrunkD. Dynamic desirableE. Dynamic autoF. None of the other alternatives applyAnswer: DQuestion:38A new switch was just configured using the “switchport trunk native vlan 7”command. What does this interface command accomplishA. Causes the interface to apply ISL framing for traffic on VLAN 7B. Configures the trunking interface to forward traffic from VLAN 7C. Configures the interface to be a trunking port and causes traffic on VLAN 7 to be taggedD. Configures the trunking interface to send traffic from VLAN 7 untaggedE. None of the other alternatives applyAnswer: DQuestion:39You need to connect two core switches via an ISL trunk. Which statement is true regarding the configuration of ISL trunksA. A Catalyst switch cannot have ISL and IEEE trunks enabled.B. All Catalyst switches support ISL trunking.C. A Catalyst switch will report giants if one side is configured for ISL while the other side is not.D. ISL trunking requires that native VLANs match.E. None of the other alternatives applyAnswer: CQuestion:40Which of the following technologies would an Internet Service Provider use to support overlapping customer VLAN ID’s over transparent LAN servicesA. tunnelingB. ATMC. SDHD. IP Over Optical NetworkingE. ISLAnswer: AQuestion:41If you were to configure an ISL Ethernet trunk between two Cisco switches, named PG1 and PG2, what would you have to include at the end of the link for the trunk to operate correctly (Select two)A. An identical VTP mode.B. An identical speed/duplex.C. An identical trunk negotiation parameter.D. An identical trunk encapsulation parameter.Question:42Refer to the exhibit. On the basis of the information provided in the exhibit, which two sets of procedures are best practicesfor Layer 2 and 3 failover alignment (Choose two.)A .Configure the D-SW1 switch as the active HSRP router and the STP root for all VLANs.Configure the D-SW2 switch as the standby HSRP router and backup STP root for all VLANs.B. Configure the D-SW1 switch as the standby HSRP router and the STP root for VLANs 11 and 110.Configure the D-SW2 switch as the standby HSRP router and the STP root for VLANs12 and 120.C. Configure the D-SW1 switch as the active HSRP router and the STP root for VLANs11 and 110.Configure the D-SW2 switch as the active HSRP router and the STP root for VLANs12 and 120.D. Configure the D-SW2 switch as the active HSRP router and the STP root for all VLANs.Configure the D-SW1 switch as the standby HSRP router and backup STP root for all VLANs.E. Configure the D-SW1 switch as the active HSRP router and the backup STP root for VLANs 11 and 110.Configure the D-SW2 switch as the active HSRP router and the backup STP root for VLANs 12 and 120.F. Configure the D-SW1 switch as the standby HSRP router and the backup STP root for VLANs12 a nd 120.Configure the D-SW2 switch as the standby HSRP router and the backup STP root for VLANs 11 and 110.Answer: CFExplanation:Basically, each of the routers that provides redundancy for a given gateway address is assigned to a common HSRP group. One router is elected as the primary, or active, HSRP router, another is elected as the standby HSRP router, and all the others remain in the listen HSRP state. The routers exchange HSRP hello messages at regular intervals, so they can remain aware of each。
cisco 真题.doc

CCNA、CCNP、CCIE模拟试题CCNA1.Which of the following types of packets will be allowed entry when a serial interface's inbound acces s list has been configured to prohibit entry for TCP and UDP ports 21, 23 and 25? (Select three option s.)A. SMTPB. STPC. FTPD. TelnetE. HTTPF. POP32.One of the trainees assigned to you want to know which services use TCP. What can you tell him? (S elect three options.)A. DHCPB. SMTPC. SNMPD. FTPE. HTTPF. TFTP3.Which of the following network masks would you use to reduce any wastage of IP addresses in point-t o- point WAN links on a network that supports VLSM?A. /38B. /30C. /27D. /23E. /184.How would you configure a router to avoid situations such as split horizon issues hampering routing updates on a Frame Relay network?A. Configure a separate sub-interface for each PVC with a unique DLCI and subnet assigned to the subi nterface.B. Configure each Frame Relay circuit as a point-to-point line to support multicast and broadcast traffic.C. Configure one sub-interface to disperse into multiple PVC connections to multiple remote router interf aces.D. Configure as many as possible sub-interfaces on the same subnet.5.With regard to ISDN, which of the following are true? (Choose all that apply.)A. Legacy DDR can use port information to define interesting traffic.B. Legacy DDR can configure multiple dialer configurations on the same interface.C. Legacy DDR can use ACLs to define interesting traffic.D. HDLC or PPP can be used to encapsulate ISDN D channel information.E. The BRI interfaces on ISDN routers with dialer profiles configured cannot belong to multiple dialer p ools.F. Dialer profiles cannot use ACLs to define interesting traffic.CCNP- BSCI6.Which of the following is a characteristic of link-state protocols?A. A network topology change generates an update that is broadcast to every router onthe network.B. The periodic routing update interval is slightly different in each router on a subnet.C. Each router creates a routing table that only includes its directly connected neighbors.D. Link-state protocols send routing updates only when there is a change in the networktopology.7.What is the term associated with synchronizing the routing tables after a topology change occurs?A. floodingB. broadcastingC. convergenceD. summarization8.Which of the following must be determined first by the router in order to route the data?A. the distance metric of the dataB. the source address of the dataC. which routing protocol is used by the dataD. whether the protocol suite of the data is active9.You are a technician at ABC. ABC has the subnet/mask of 172.29.100.0/26 set aside for small remo te locations. Each location will have 5 IP devices connected to the network. Which VLSM mask will pr ovide the minimum number of hosts you require?A. /27B. /28C. /29D. /30E. /3110.You are a trainee technician at ABC. Your instructor shows you the following route summarization entry:192.168.134.0/22 Your instructor wants to know how many class C addresses are contained in this summ arization. What would your reply be?A. 1B. 2C. 4D. 8E. 16- BCMSN11.Which command enables an EtherChannel bundle on a Catalyst 2900XL switch?A. Port groupB. Set port channel onC. Port etherchannel enableD. Set etherchannel port enable12.Which two statements about dynamic VLANs are true? (Choose two)A. Each switch port is assigned to a specific VLAN.B. Dynamic VLANs require a VLAN Membership Policy Server.C. Devices are in the same VLAN regardless of which port they attach to.D. Dynamic VLAN assignment are made through the command interface.13.Which statement is correct about 802.1Q trunking? (Select all that apply)A. Both switches must be in the same VTP domain.B. The encapsulation type of both ends of the trunk does not have to match.C. The native VLAN on both ends of the trunk must be VLAN 1.D. 802.1Q trunking can only be configured on a Layer 2 port.E. In 802.1Q trunking, all VLAN packets are tagged on the trunk link, except the native VLAN.14.You need to take advantage of FastEthernet ports. Which two actions avoid configuration problems that cause the port to be automatically disabled? (Choose two)A. Allow some ports in a channel to be disabled.B. Configure the ports in a channel as dynamic VLAN ports.C. Configure all ports in a channel to operate at the same speed and duplex mode.D. Assign all ports in a channel to the same VLAN or configure them as trunk ports.15.What is the cause of jitter?A. Variable queue delaysB. Packet dropsC. Transmitting too many small packetsD. Compression- BCRAN16.Regarding DHCP, DHCP relay and DHCP server are mutually exclusive.A. None of the choices.B. TrueC. False only for certain IOS versionD. FalseE. False only for IOS version below V1017.A LAPD Address field can be 1 or 2 bytes long.A. TrueB. FalseC. True only in the USD. True only in AsiaE. True only in Europe18.Which of the following are valid functions of the lock DTE modem attribute (Choose all that appl y)?A. Disable UART.B. Enable UART.C. Locks the data speed between the computer motherboard and the RS232 port.D. Locks the data speed between the modem and the DTE device.19.Which of the following are not the valid types of ATM addresses (Choose all that apply)?A. DCCB. GCTC. BSPD. ICDE. NSAPF. AED20.Which of the following are NOT the valid types of X.25 PLP packet fields (Choose all that appl y)?A. User DataB. LCIC. GFID. PTIE. None of the choices.- CIT21.You are a technician at . Your newly appointed ABC trainee wants to know what the si milarities between Topology Diagrams and Network Configuration Tables are.What would your reply be? (Choose all that apply.)A. Both share few components.B. Both share many of the same components.C. Both define physical memory components.D. Both are used for troubleshooting.E. Both use lines and symbols to represent network components.22.You are a technician at . Your newly appointed ABC trainee wants to know what the def ault action for the output of debug and system error messages is. What would your reply be?A. Output goes to the remote console if logging is off.B. Output is sent to the console terminal.C. Error logging automatically invokes debug output to the designated TFTP server.D. Output configuration requires a TFTP server to write filesE. Output is written to a Syslog server.23.You are the network administrator at . ABC has a switched network. You want to control the designation of the spanning-tree root bridge in the ABC network. What should you do?A. By enabling uplink-fast on the ports of the desired switch.B. By lowering the bridge priority on the desired switch.C. By setting a lower MAC address on the designated switch.D. By raising the bridge ID on one switch.24.You are a technician at ABC. You receive a report from several ABC users who complain that the y get slow responses when sending and receiving email, especially when browsing the Internet. You inve stigate the complaint by checking the output of a ping command issued from her computer and find that it indicates intermitted success and failures messages, when attempting to contact the email server. A tra cert to the corporate Internet gateway router shows high latency and occasional time out messages. What would be the most effective troubleshooting approach if you are to determine the cause of the slo w response time?A. Bottom-up approachB. Random access approachC. Divide and conquer approachD. Top-down approachE. Top-down rule-out approach25.You are a technician at . Your newly appointed ABC trainee wants to know what feature s make OSPF more suitable than RP in large network installations. What would your reply be? (Choose all that apply.)A. Diffusing Update AlgorithmB. No hop count limitationC. Higher routing update overheadD. Faster convergenceE. Lower routing update overheadCCIE26.You are the network administrator at ABC. You are troubleshooting a network problem. You want to trace the route to a Unix workstation that you want to reach through the Internet. However, Tracerout e does not work.Currently, there is an inbound access-list applied to the serial interface on Router 1. An entry in the acc ess-list states "access-list 101 permit tcp any any". What access-list entry may you need to be added to t he access-list in order to get traceroute to work?A. access-list 101 permit udp any anyB. access-list 101 permit icmp any any time-exceeded access-list 101 permit icmp any any port-unreachab leC. access-list 101 permit icmp any any time-exceeded access-list 101 permit icmp any any net-unreachableD. access-list 101 permit icmp any any echo access-list 101 permit icmp any any net-unreachableE. access-list 101 permit udp any any access-list 101 permit icmp any any protocol-unreachable27.What does the BGP backdoor command do?A. It changes the distance of an iBGP route to 20.B. It changes the distance of an eBGP route to 200.C. It changes the distance of an IGP route to 20.D. It does not effect any changes in distance of the route.E. It changes the distance of an IGRP route to 200.28.Which of the following DNS resource records is not valid?A. NSB. PTRC. MXD. FQDNE. A29.Which of the following features is provided by RIP v2 that were previously not possible with RIP v1? (Choose all that apply.)A. Classless routing and split-horizon.B. Poison reverse and updating to multicast addresses.C. Poison reverse and classless routing.D. Classless routing and updating to multicast addresses.E. Route tag and classless routing.30.Which of the following statements is valid when taking Custom Queuing into account?A. Custom queuing has the ability to restrict a particular type of traffic to a given bandwidth not matter what is load is like on that link.B. Custom queuing looks at groups of packets from the similar source-destination pairs.C. Custom queuing will not proceed to a next queue unless the current queue is empty.D. Custom queuing can prevent one type of traffic from dominating a busy link.。
Cisco 路由协议试题及答案

Cisco 路由协议试题及答案2006-01-05 CBSi中国· 类型: 转载1、解决路由环问题的方法有(ABD)A. 水平分割B. 路由保持法C. 路由器重启D. 定义路由权的最大值2、下面哪一项正确描述了路由协议(C)A. 允许数据包在主机间传送的一种协议B. 定义数据包中域的格式和用法的一种方式C. 通过执行一个算法来完成路由选择的一种协议D. 指定MAC 地址和IP地址捆绑的方式和时间的一种协议3、以下哪些内容是路由信息中所不包含的(A)A. 源地址B. 下一跳C. 目标网络D. 路由权值4、以下说法那些是正确的(BD)A. 路由优先级与路由权值的计算是一致的B. 路由权的计算可能基于路径某单一特性计算,也可能基于路径多种属性C. 如果几个动态路由协议都找到了到达同一目标网络的最佳路由,这几条路由都会被加入路由表中D. 动态路由协议是按照路由的路由权值来判断路由的好坏,并且每一种路由协议的判断方法都是不一样的5、IGP的作用范围是(C)A. 区域内B. 局域网内C. 自治系统内D. 自然子网范围内6、距离矢量协议包括(AB)A. RIPB. BGPC. IS-ISD. OSPF7、关于矢量距离算法以下那些说法是错误的(A)A. 矢量距离算法不会产生路由环路问题B. 矢量距离算法是靠传递路由信息来实现的C. 路由信息的矢量表示法是(目标网络,metric)D. 使用矢量距离算法的协议只从自己的邻居获得信息8、如果一个内部网络对外的出口只有一个,那么最好配置(A)A. 缺省路由B. 主机路由C. 动态路由9、BGP是在(D)之间传播路由的协议A. 主机B. 子网C. 区域(area)D. 自治系统(AS)10、在路由器中,如果去往同一目的地有多条路由,则决定最佳路由的因素有(AC)A. 路由的优先级B. 路由的发布者C. 路由的metirc值D. 路由的生存时间11、在RIP协议中,计算metric值的参数是(D)A. MTUB. 时延C. 带宽D. 路由跳数12、路由协议存在路由自环问题(A)A. RIPB. BGPC. OSPFD. IS-IS13、下列关于链路状态算法的说法正确的是:(bc )A. 链路状态是对路由的描述B. 链路状态是对网络拓扑结构的描述C. 链路状态算法本身不会产生自环路由D. OSPF和RIP都使用链路状态算法14、在OSPF同一区域(区域A)内,下列说法正确的是(d )A. 每台路由器生成的LSA都是相同的B. 每台路由器根据该最短路径树计算出的路由都是相同的C. 每台路由器根据该LSDB计算出的最短路径树都是相同的D. 每台路由器的区域A的LSDB(链路状态数据库)都是相同的15、在一个运行OSPF的自治系统之内:(ad )A. 骨干区域自身也必须是连通的B. 非骨干区域自身也必须是连通的C. 必须存在一个骨干区域( 区域号为0 )D. 非骨干区域与骨干区域必须直接相连或逻辑上相连16、下列关于OSPF协议的说法正确的是:(abd )A. OSPF支持基于接口的报文验证B. OSPF支持到同一目的地址的多条等值路由C. OSPF是一个基于链路状态算法的边界网关路由协议D. OSPF发现的路由可以根据不同的类型而有不同的优先级17、禁止RIP 协议的路由聚合功能的命令是(c )A. undo ripB. auto-summanyC. undo auto-summanyD. undo network 10.0.0.018、下列静态路由配置正确的是()A. ip route 129.1.0.0 16 serial 0B. ip route 10.0.0.2 16 129.1.0.0C. ip route 129.1.0.0 16 10.0.0.2D. ip route 129.1.0.0 255.255.0.0 10.0.0.219、以下不属于动态路由协议的是()A. RIPB. ICMPC. IS-ISD. OSPf20、三种路由协议RIP 、OSPF 、BGP和静态路由各自得到了一条到达目标网络,在华为路由器默认情况下,最终选选定() 路由作为最优路由A. RIPB. OSPFC. BGPD. 静态路由21、IGP 包括如下哪些协议()A. RIPB. BGPC. IS-ISD. OSPF22、路由环问题会引起(abd )A. 慢收敛B. 广播风暴C. 路由器重起D. 路由不一致23、以下哪些路由表项要由网络管理员手动配置(a )A. 静态路由B. 直接路由C. 动态路由D. 以上说法都不正确24、在运行Windows98的计算机中配置网关,类似于在路由器中配置()A. 直接路由B. 默认路由C. 动态路由D. 间接路由25、关于RIP协议,下列说法正确的有:(ac )A. RIP协议是一种IGPB. RIP协议是一种EGPC. RIP协议是一种距离矢量路由协议D. RIP协议是一种链路状态路由协议26、RIP协议是基于(a )A. UDPB. TCPC. ICMPD. Raw IP27、RIP协议的路由项在多少时间内没有更新会变为不可达?(c )A. 90sB. 120sC. 180sD. 240s28、解决路由环路的方法有(abcd )A. 水平分割B. 抑制时间C. 毒性逆转D. 触发更新29、RIP协议在收到某一邻居网关发布而来的路由信息后,下述对度量值的正确处理有哪些?( )A. 对本路由表中没有的路由项,只在度量值少于不可达时增加该路由项B. 对本路由表中已有的路由项,当发送报文的网关相同时,只在度量值减少时更新该路由项的度量值C. 对本路由表中已有的路由项,当发送报文的网关不同时,只在度量值减少时更新该路由项的度量值D. 对本路由表中已有的路由项,当发送报文的网关相同时,只要度量值有改变,一定会更新该路由项的度量值30、关于RIP V1和RIP V2,下列说法哪些正确?(bc )A. RIP V1报文支持子网掩码B. RIP V2报文支持子网掩码C. RIP V2缺省使用路由聚合功能D. RIP V1只支持报文的简单口令认证,而RIP V2支持MD5认证31、在rip中metric等于(d )为不可达A. 8B. 10C. 15D. 1632、RIP协议引入路由保持机制的作用是(b )A. 节省网络带宽B. 防止网络中形成路由环路C. 将路由不可达信息在全网扩散D. 通知邻居路由器哪些路由是从其处得到33、以下配置默认路由的命令正确的是:"a"A. ip route 0.0.0.0 0.0.0.0 172.16.2.1B. ip route 0.0.0.0 255.255.255.255 172.16.2.1C. ip router 0.0.0.0 0.0.0.0 172.16.2.1D. ip router 0.0.0.0 0.0.0.0 172.16.2.134、已知某台路由器的路由表中有如下两个表项"d" Destination/Mast protocol preferen Metric Nexthop/Interface 9.0.0.0/8 OSPF 10 50 1.1.1.1/Serial0 9.1.0.0/16 RIP 100 5 2.2.2.2/Ethernet0如果该路由器要转发目的地址为9.1.4.5的报文,则下列说法中正确的是A. 选择第一项,因为OSPF协议的优先级高B. 选择第二项,因为RIP协议的花费值(Metric)小C. 选择第二项,因为出口是Ethternet0,比Serial0速度快D. 选择第二项,因为该路由项对于目的地址9.1.4.5来说,是更精确的匹配35、Quidway系列路由器上,路由表中的直接路由(Direct)可能有以下几种来源"abc"A. 本路由器自身接口的主机路由B. 本路由器自身接口所在的网段路由C. 与本路由器直连的对端路由器的接口的主机路由D. 缺省路由36、与动态路由协议相比,静态路由有哪些优点?"cd"A. 带宽占用少B. 简单C. 路由器能自动发现网络拓扑变化D. 路由器能自动计算新的路由37、在RIP路由协议中,以下有关减少路由自环的方法正确的是"abcd"A. 触发更新是从减少路由自环发生的概率方面来考虑问题的B. 水平分割的方法只对消除两台路由器之间的自环有作用C. 设置抑制时间的方法可能导致路由的慢收敛D. 为了减轻路由自环产生的后果,RIP协议规定了最大跳数38、路由协议在收到某一邻居发布而来的路由信息后,下述对度量值的正确处理有哪些?"bd"A. 对本路由表中已有的路由项,当发送该路由信息的邻居相同时,只在度量值减少时更新该路由项的度量值B. 对本路由表中已有的路由项,当发送该路由信息的邻居相同时,只要度量值有改变,一定会更新该路由项的度量值C. 对本路由表中已有的路由项,当发送该路由信息的邻居不同时,只要度量值有改变,一定会更新该路由项的度量值D. 对本路由表中没有的路由项,只在度量值少于不可达时增加该路由项39、假设有这样的组网实例: 两个Quidway(假设为RTA和RTB)通过串口相连接,其中RTA的串口IP地址是10.110.0.1/30,RTB的串口IP地址是10.110.0.2/30,RTA通过以太口连接的本地局域网的IP地址是11.110.0.0/16,RTB通过以太口连接的本地局域网IP地址是11.111.0.0/16,在上面所有的接口上都启动RIP V1(仅仅RIP V1)协议,那么,下列说法正确的是"cd"A. 在RTA的本地局域网上的计算机可以访问在RTB本地局域网上的计算机B. 在RTB的本地局域网上的计算机可以访问在RTA本地局域网上的计算机C. 在RTA的本地局域网上的计算机不能访问在RTB本地局域网上的计算机D. 在RTB的本地局域网上的计算机不能访问在RTA本地局域网上的计算机40、在Quidway路由器上,应该使用什么命令来观察网络的路由表? "b"A. Show ip pathB. dis ip routC. Show interfaceD. Show running-configE. Show ip rip41、下面哪些协议是可路由协议(routed protocol)? "ab"A. IPB. IPXC. RIPD. NETBEUI42、以下协议属于路由协议的是"abcg"A. RIPB. IS-ISC. OSPFD. PPPE. IPF. IPXG. BGP43、下列哪些技术有助于避免路由环路? "bcdef"A. 直通交换B. 采用链路状态路由协议C. 水平分割D. 路由保持(holddown)E. 定义最大跳计数F. 路由中毒(poison reverse)44、距离矢量路由协议使用水平分割(split horizon)技术的目的是什么? "ac"A. 避免在毗邻路由器之间产生路由环路B. 确保路由更新数据报文沿着接收路线方向发送C. 与保持间隔(holddown)机制协同工作,为保持间隔的计算提供更多的可靠性D. 代替路由中毒(poison reverse)算法45、静态路由的优点包括:"acd"A. 管理简单B. 自动更新路由C. 提高网络安全性D. 节省带宽E. 收敛速度快46、静态路由配置中关键字reject 和blackhole 的区别在于:"be"A. 发往reject 路由的报文被丢弃,并且不通知源主机B. 发往blackhole 路由的报文被丢弃,并且不通知源主机C. 发往reject 路由的报文被丢弃,发往blackhole 路由的报文不被丢弃D. 发往blackhole 路由的报文被丢弃,发往reject 路由的报文不被丢弃E. 发往reject 路由的报文被丢弃,并且通知源主机F. 发往blackhole 路由的报文被丢弃,并且通知源主机47、以下对于缺省路由描述正确的是:"bc"A. 缺省路由是优先被使用的路由B. 缺省路由是最后一条被使用的路由C. 缺省路由是一种特殊的静态路由D. 缺省路由是一种特殊的动态路由48、对路由器A配置RIP协议,并在接口S0(IP地址为10.0.0.1/24)所在网段使能RIP 路由协议,在全局配置模式下使用的第一条命令是:"a"A. ripB. rip 10.0.0.0C. network 10.0.0.1D. network 10.0.0.049、对于RIP协议,可以到达目标网络的跳数(所经过路由器的个数)最多为:"b"A. 12B. 15C. 16D. 没有限制50、支持可变长子网掩码的路由协议有:"bcd"A. RIP v1B. RIP v2C. OSPFD. IS-IS51、在路由器所有接口上使能RIP协议的命令是:"a"A. network allB. neighborC. enableD. rip enable52、当接口运行在RIP-2广播方式时,它可以接收的报文有:"ac"A. RIP-1广播报文B. RIP-1组播报文C. RIP-2广播报文D. RIP-2组播报文53、以下对路由优先级的说法,正确的是"bcd"A. 仅用于RIP和OSPF之间B. 用于不同路由协议之间C. 是路由选择的重要依据D. 直接路由的优先级缺省为054、您认为下列说法哪些是不正确的?"cd"A. 每条静态路由的优先级也可以不相同B. 缺省情况下路由优先级的次序是OSPF > RIPC. 路由算法产生一种权值来表示路由的好坏。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1. Which two features can be implemented using the Cisco SDM Advanced Firewall wizard? (Choose two.)A. DMZ supportB. custom rulesC. firewall signaturesD. application securityE. IP unicast reverse path forwardingAnswer: AB2. What three classifications reflect the different approaches used to identify malicious traffic? (Choose three.)A. platform basedB. signature basedC. policy basedD. regular-expression basedE. symbol basedF. anomaly basedAnswer: BCF3. Which action can be taken by Cisco IOS IPS when a packet matches a signature pattern?A. drop the packetB. reset the UDP connectionC. block all traffic from the destination address for a specified amount of timeD. perform a reverse path verification to determine if the source of the maliciouspacket was spoofedE. forward the malicious packet to a centralized NMS where further analysis can be takenAnswer: A4. A router interface is configured with an inbound access control list and an inspection rule. How will an inbound packet on this interface be processed?A. It will be processed by the inbound ACL. If the packet is dropped by the ACL, then it will be processed by the inspection rule.B. It will be processed by the inbound ACL. If the packet is not dropped by the ACL, then it will be processed by the inspection rule.C. It will be processed by the inspection rule. If the packet matches the inspection rule, the inbound ACL will be invoked.D. It will be processed by the inspection rule. If the packet does not match the inspection rule, the inbound ACL will be invoked.Answer: B5. Which statement is true about an IPsec/GRE tunnel?A. The GRE tunnel source and destination addresses are specified within the IPsec transform set.B. An IPsec/GRE tunnel must use IPsec tunnel mode.C. GRE encapsulation occurs before the IPsec encryption process.D. Crypto map ACL is not needed to match which traffic will be protected.Answer: C6.During the Easy VPN Remote connection process,which phase involves pushing the IP address,DNS,and split tunnel attributes to the client?A: mode configurationAnswer: A1. Which two statements about common network attacks are true? (Choose two.)A. Access attacks can consist of password attacks, trust exploitation, port redirection, and man-in-the-middle attacks.B. Access attacks can consist of password attacks, ping sweeps, port scans, andman-in-the-middle attacks.C. Access attacks can consist of packet sniffers, ping sweeps, port scans, and man-in-the-middle attacks.D. Reconnaissance attacks can consist of password attacks, trust exploitation, port redirection and Internet information queries.E. Reconnaissance attacks can consist of packet sniffers, port scans, ping sweeps, and Internet information queries.F. Reconnaissance attacks can consist of ping sweeps, port scans, man-in-middle attacks and Internet information queries.Answer: AE7. Which two statements about the Cisco AutoSecure feature are true? (Choose two.)A. All passwords entered during the AutoSecure configuration must be a minimum of8 characters in length.B. Cisco123 would be a valid password for both the enable password and the enable secret commands.C. The auto secure command can be used to secure the router login as well as the NTP and SSH protocols.D. For an interactive full session of AutoSecure, the auto secure login command should be used.E. If the SSH server was configured, the 1024 bit RSA keys are generated after the auto secure command is enabled.Answer: CE8. Which three statements are correct about MPLS-based VPNs? (Choose three.)A. Route Targets (RTs) are attributes attached to a VPNv4 BGP route to indicate its VPN membership.B. Scalability becomes challenging for a very large, fully meshed deployment.C. Authentication is done using a digital certificate or pre-shared key.D. A VPN client is required for client-initiated deployments.E. A VPN client is not required for users to interact with the network.F. An MPLS-based VPN is highly scalable because no site-to-site peering is required. Answer: AEF9. Which two statements are true about broadband cable (HFC) systems? (Choose two.)A. Cable modems only operate at Layer 1 of the OSI model.B. Cable modems operate at Layers 1 and 2 of the OSI model.C. Cable modems operate at Layers 1, 2, and 3 of the OSI model.D. A function of the cable modem termination system (CMTS) is to convert the modulated signal from the cable modem into a digital signal.E. A function of the cable modem termination system is to convert the digital data stream from the end user host into a modulated RF signal for transmission onto the cable system.Answer: BD10. Which form of DSL technology is typically used as a replacement for T1 lines?A. VDSLB. HDSLC. ADSLD. SDSLE. G.SHDSLF. IDSLAnswer: B11.Which three techniques should be used to secure management protocols? (Choose two.)A. Configure SNMP with only read-only community strings.B. Encrypt TFTP and syslog traffic in an IPSec tunnel.C. Implement RFC 3704 filtering at the perimeter router when allowing syslog access from devices on theoutside of a firewall.D. Synchronize the NTP master clock with an Internet atomic clock.E. Use SNMP version 2.F. Use TFTP version 3 or above because these versions support a cryptographic authentication mechanismbetween peers.Answer:AB12.Which three techniques should be used to secure management protocols? (Choose three.)A. Configure SNMP with only read-only community strings.B. Encrypt TFTP and syslog traffic in an IPSec tunnel.C. Implement RFC 2827 filtering at the perimeter router when allowing syslog access from devices on the outside of a firewall.D. Synchronize the NTP master clock with an Internet atomic clock.E. Use SNMP version 2.F. Use TFTP version 3 or above because these versions support a cryptographic authentication mechanismbetween peers.Answer:ABC13.How can application layer attacks be mitigated?A.Install the latest patches.B.Implement RFC 2827 filtering.C.Implement traffic rate limiting.D.Implement Anti-DoS features.E.Disable port redirection.Answer:A14. Which three of these are required before you can configure your routers for SSH server operations? (Choose three.)A. each of the target routers has a unique hostnameB. each of the target routers is configured to enable secret passwordsC. a user is define in either the local database or on a remote AAA serverD. each of the target routers has a password configured on the VTY interfaceE. each of the target routers is using the correct domain name of your network Answer: ACE15.Which IOS command would display IPS default values that may not be displayed using the show running-config command ?A.show ip ips configurationB.show ip ips interfaceC.show ip ips statisticsD.show ip ips sessionAnswer:A16.Refer to the exhibit.Host 1 cannot ping Server 1. In the course of troubleshooting,you have eliminated all network issues.Based upon the partial configuration shown,what is the issue?17.Refer to the exhibit.Host 1 cannot ping Server 1. In the course of troubleshooting,you have eliminated all network issues.Based upon the partial configuration shown,what is the issue?18.What is an MPLS forwarding equivalence class?A.a set of destination networks forwarded from the same ingress routerB.a set of destination networks forwarded to the same egress routerC.a set of source networks forwarded from the same ingress routerD.a set of source networks forwarded to the same egress routerAnserwer:B19.Which two statements are true about Cisco Classic (CBAC)IOS Firewall set ?(choose two)A.It can be used to block bulk encryption attacks.B.It can be used to protect against denial of service attacksC.Traffic originating from the router is considered trusted,so it is not inspected.D.Based upon the custom firewall rules, an ACL entry statically created and added to the existing ACL permanently.E.Temporary ACL entries that allow selected traffic to pass area created and persist for the duration of the communication session.Answer:BEA Certkiller router was recently upgraded to the firewall feature set. Which two statements are true about Cisco IOS Firewall? (Select two)A. It is implemented as a per-destination process.B. It enhances security for TCP and UDP applications.C. It enhances security for TCP applications only.D. It is implemented as a per-application process.E. It enhances security for UDP applications only.Answer: B, DExplanation:Firewalls enforce access control between networks, which can be of different types and levels of trust. A common name for a group of networks reachable over a single firewall network interface is a security zone. A security zone is therefore an administratively separate domain, to or from which a firewall can filter incomingor outgoing traffic. The most notable security zones are inside and outside networks that are connected to firewalls over inside or outside interfaces, respectively. Firewall operations are based on one of the three technologies:Packet filtering: Packet filtering limits information entering a network based on static packet header information. Packet filtering is usually employed by a Layer 3 device to statically define access control lists (ACLs) that determine which traffic is permitted or denied. Packet filtering can examine protocol header information up to the transport layer to permit or deny certain traffic. Packets that make it through the filters are sent to the requesting system. All other packets are discarded.ALGs work at the application layer. An ALG is a special piece of software designed to relay application-layer requests and responses between endpoints. An ALG acts as an intermediary between an application client, for which it acts as a virtual server, and a server, for which it acts as a virtual client. The client connects to the proxy server and submits an application layer request. The application layer request includes the true destination and the data request itself. The proxy server analyzes the request and may filter or change its contents, and then opens a session to the destination server. The destination server replies to the proxy server. The proxy server passes the response, which may be filtered and changed, back to the client.Stateful packet filtering: Stateful packet filtering combines the best of packet filtering and proxy server technologies. Firewalls using stateful packet filtering are also called hybrid firewalls. Stateful packet filtering is the most widely used firewall technology. Stateful packet filtering is an application-aware method of packet filtering that works on the connection, or flow, level. Stateful packet filtering maintains a state table to keep track of all active sessions crossing the firewall. A state table, which is part of the internal structure of the firewall, tracks all sessions and inspects all packets passing through the firewall. If packets have the expected properties, predicted by the state table, they are forwarded. The state table changes dynamically according to the traffic flow.You need to configure access rules on a new Certkiller router with the firewall feature set. Which three statements are true about a Cisco IOS Firewall? (Select three)A. It can be configured to block Java traffic.B. The inspection rules can be used to set timeout values for specified protocols.C. It can be configured to detect and prevent SYN-flooding denial-of-service (DoS) network attacks.D. The ip inspect cbac-name command must be configured in global configuration mode.E. It can only examine network layer and transport layer information.F. It can only examine transport layer and application layer information.Answer: A, B, CExplanation:Cisco IOS Firewall intelligently filters TCP and UDP packets based on application layer protocol session information. It inspects traffic for sessions that originate on any interface of the router and manages state information for TCP and UDP sessions. This state information is used to create temporary openings in the ACLs to allow return traffic and additional data connections for permissible sessions. Inspecting packets at the application layer and maintaining TCP and UDP session information helps prevent certain types of network attacks, such as SYN flooding. Cisco IOS Firewall inspects packet sequence numbers in TCP connections to see if they are within expected ranges, and drops any suspicious packets. Additionally, Cisco IOS Firewall can detect unusually high rates of new connections and issue alert messages. The firewall inspection can help protect against certain denial of service (DoS) attacks involving fragmented IP packets.22.In an MPLS VPN implementation, how are overlapping customer prefixes propagated?A. A separate instance of the core IGP is used for each customerB. Separate BGP sessions are established between each customer edge LSRC. Because customers have their own upique LSPs, address space is kept separateD. A route distinguisher is attached to each customer prefixE. Because customers have their own interfaces, distributed CEFs keep the forwarding tables separateAnswer:D。
