AN019-Discrete-Cosine-Transform-AppNote
text-davinci-003返回半句话

text-davinci-003返回半句话
“text-davinci-003返回半句话”指的是使用OpenAI的text-davinci-003模型时,模型返回的输出结果不完整或者是不准确的情况。
text-davinci-003是OpenAI推出的一种先进的自然语言处理模型,它可以理解和生成人类语言,并能够完成各种自然语言处理任务,如文本分类、问答、摘要生成等。
然而,由于语言本身的复杂性和模型本身的局限性,text-davinci-003在处理某些复杂或特定情境的语言时可能会出现返回不完整或错误的结果。
当text-davinci-003返回半句话时,意味着模型没有完全理解或正确处理输入的文本,导致输出的结果不完整或者是不准确。
这可能是由于输入文本的复杂性、歧义性、长度等因素导致的。
为了避免这种情况,在使用text-davinci-003模型时,需要注意以下几点:1.输入文本应尽量简洁、清晰、准确,避免使用过于复杂、歧义或冗长的文
本。
2.对于重要的任务或场景,建议使用多个不同的输入和测试方法来验证模型
的输出结果。
3.对于不完整或错误的结果,可以尝试调整输入文本或使用其他模型进行验
证和比较。
总之,“text-davinci-003返回半句话”指的是使用该模型时可能出现的不完整或错误的结果,需要注意并采取相应的措施来保证结果的准确性和可靠性。
2206故障代码

1RBS 2206 故障列表版权© Ericsson 2003 年版权所有- 保留所有权利免责声明未经版权所有者书面许可,不得复制本文中的任何内容。
由于方法、设计和制造的不断变化,文中内容将做修订,恕不另行通知。
对于使用本文件发生的任何故障和损失,爱立信不承担任何责任。
注册商标列表2目录1 故障列表 (4)1.1 术语 (4)1.1.1 故障编号 (4)1.1.2 故障映射 (4)1.1.3 逻辑替换单元 (5)1.2 故障映射概况 (6)1.2.1 故障映射注意事项 (6)1.3 SO CF 故障映射 (8)1.3.1 SO CF ,外部条件映射级别1 (8)1.3.2 SO CF ,外部条件映射级别2 (8)1.3.3 SO CF ,内部错误映射级别1A (10)1.3.4 SO CF ,内部错误映射级别2A (15)1.3.5 SO CF ,替换单元映射 (31)1.4 SO TRXC 故障映射............................................................................................................411.4.1 SO TRXC ,外部条件映射级别1 (41)1.4.2 SO TRXC ,内部故障映射级别1A (42)1.4.3 SO TRXC ,内部故障映射级别1B (50)1.4.4 SO TRXC ,内部故障映射级别2A (52)1.4.5 SO TRXC ,替换单元映射 (63)1.5 AO 故障映射.......................................................................................................................651.5.1 AO CON ,外部条件映射级别1 (66)1.5.2 AO CON ,外部条件映射级别2 (66)1.5.3 AO DP (66)1.5.4 AO RX ,内部故障映射级别1B (67)1.5.5 AO RX ,内部故障映射级别2A (71)1.5.6 AO TF ,外部条件映射级别1 (73)1.5.7 AO TF ,外部条件映射级别2 (75)1.5.8 AO TF ,内部故障映射级别2A (76)31.5.9 AO TS ,外部条件映射级别1 (76)1.5.10 AO TX ,内部故障映射级别1A (77)1.5.11 AO TX ,内部故障映射级别1B (77)1.5.12 AO TX ,内部故障映射级别2A (86)41 故障列表本章介绍了报告到BSC 的各种故障,以及怀疑可能导致故障的硬件装置。
Autodesk Nastran 2022 用户手册说明书

MPA, MPI (design/logo), MPX (design/logo), MPX, Mudbox, Navisworks, ObjectARX, ObjectDBX, Opticore, Pixlr, Pixlr-o-matic, Productstream,
Publisher 360, RasterDWG, RealDWG, ReCap, ReCap 360, Remote, Revit LT, Revit, RiverCAD, Robot, Scaleform, Showcase, Showcase 360,
TrueConvert, DWG TrueView, DWGX, DXF, Ecotect, Ember, ESTmep, Evolver, FABmep, Face Robot, FBX, Fempro, Fire, Flame, Flare, Flint,
ForceEffect, FormIt, Freewheel, Fusion 360, Glue, Green Building Studio, Heidi, Homestyler, HumanIK, i-drop, ImageModeler, Incinerator, Inferno,
Autodesk Nastran 2022
Reference Manual
Nastran Solver Reference Manual
Konica AF 35mm 自动对焦相机说明书

• Red indicator light glows in viewfinder to tell user when to use the built-in flash.
Flash . ................ Built-in , pop-up electronic flash . Guide No . 45 (feet) 14 (m.etric) at ASA 100 . Recycle time 5 - 7 seconds. Approximately
132 0 action, with double exposure prevention device. Rewind . . .. . ........ ... . . .. Rapid rewind crank handle. Frame Counter . .. ... Counts number of exposures taken .
Viewfinder Window
Back Cover Release
r-------------'"-----::;nutter Release Button r-----...,--------- Twin Autofocus Sensors r - - - - - Built-in " Pop-Up" Electronic Flash
Cat. No. '106-117'
@Copyrloht 1980 Berkey Marftetlng Companies
KonicaAF
35mmcamera
MicroDIMM设计规范

4.20.12 - 214-Pin DDR2 SDRAM Unbuffered MicroDIMM DesignSpecificationPC2-4200/PC2-3200 DDR2 Unbuffered MicroDIMM Reference Design SpecificationRevision 0.526,April, 2004Contents1. Product Description (3)Product Family Attributes (3)Raw Card Summary (3)2. Environmental Requirements (4)Absolute Maximum Ratings (4)3. Architecture (4)Pin Description (4)Input/Output Functional Description (5)DDR2 SDRAM MicroDIMM Pinout (6)Block Diagram x16 2Ranks Raw Card A (7)Block Diagram x16 1Rank Raw Card B (8)4. Component Details (9)x16 Ballout for 256Mb, 512Mb, 1Gb, 2Gb and 4Gb DDR2 SDRAMs (Top View) (9)DDR2 SDRAM FBGA Component Specifications (9)Reference SPD Component Specifications (9)SPD Component DC Electrical Characteristics (9)5. Unbuffered MicroDIMM Details (10)DDR2 SDRAM Module Configurations (Reference Designs) (10)Input Loading Matrix (10)DDR2 MicroDIMM Gerber File Releases (11)Example Raw Card Component Placement (12)6. MicroDIMM Wiring Details (13)Signal Groups (13)General Net Structure Routing Guidelines (13)Explanation of Net Structure Diagrams (13)Differential Clock Net Structures (14)Data Net Structures (16)Control Net Structures S[1:0], CKE[1:0], ODT[1:0] (18)Address/Control Net Structures Ax, BAx, RAS, CAS, WE (19)Cross Section Recommendations (21)Test Points (22)7. Serial Presence Detect Definition (23)Serial Presence Detect Data Example (23)8. Product Label (26)9. MicroDIMM Mechanical Specifications (27)1. Product DescriptionThis reference specification defines the electrical and mechanical requirements for the PC2-4200 memory module, a 214-pin, 267 MHz clock (533 MT/s data rate), 64-bit wide, Unbuffered Synchronous Double Data Rate 2(DDR2) DRAM Micro Dual In-Line Memory Module (DDR2 SDRAM MicroDIMMs). It also defines a slower version, the PC2-3200, using 200MHz clock (400 MT/s data rate) DDR2 SDRAMs. These DDR2 SDRAM MicroDIMMs are intended for use as main memory when installed in systems such as mobile per-sonal computers.Reference design examples are included which provide an initial basis for Unbuffered MicroDIMM designs. Any modifications to these reference designs must meet all system timing, signal integrity and thermal requirements for 267 MHz clock rate support. Other designs are acceptable, and all Unbuffered DDR2MicroDIMM implementations must use simulations and lab verification to ensure proper timing requirements and signal integrity in the design.Raw Card SummaryProduct Family AttributesAttribute:Values:Notes:MicroDIMM Organizationx 64MicroDIMM Dimensions (nominal)30 mm high, 54.0mm wide MicroDIMM Types Supported Unbuffered Pin Count214SDRAMs Supported 256 Mb, 512 Mb, 1 Gb, 2 Gb, 4 GbCapacity128 MB, 256 MB, 512 MB, 1 GB, 2GB, 4 GB Serial Presence DetectConsistent with JEDEC Rev. 1.0Voltage Options, Nominal1.8 V V DD 1.8 V V DD Q1.8 V to 3.3 V V DD SPD 1InterfaceSSTL_18Note 1: V DD SPD is not tied to V DD or V DD Q on the DDR2 MicroDIMM.Raw CardNumber of DDR2 SDRAMsSDRAM OrganizationNumber of RanksA 8x162B4x1612. Environmental RequirementsPC2-4200 DDR2 SDRAM Unbuffered MicroDIMMs are intended for use in mobile computing environments that have limited capacity for heat dissipation.3. ArchitectureAbsolute Maximum RatingsSymbol ParameterRating Units Notes T OPR Operating Temperature (ambient) 0 to +65°C 1H OPR Operating Humidity (relative) 10 to 90%1T STG Storage Temperature-50 to +100°C 1H STGStorage Humidity (without condensation) 5 to 95%1Barometric Pressure (operating & storage)105 to 69kPa1, 21.Stresses greater than those listed may cause permanent damage to the device. This is a stress rating only, and device functional operation at or above the conditions indicated is not implied. Exposure to absolute maximum rating conditions for extended periods may affect reliability.2.Up to 9850 ft.Pin DescriptionCK[1:0] Clock Inputs, positive line 2 DQ[63:0] Data Input/Output 64CK[1:0]Clock inputs, negative line 2DM[7:0] Data Masks 8CKE[1:0]Clock Enables 2DQS[7:0]Data strobes8RAS Row Address Strobe 1DQS[7:0]Data strobes complement8CAS Column Address Strobe 1WE Write Enable 1NC,TESTLogic Analyzer specific test pin (No connecton MicroDIMM1S[1:0]Chip Selects2A[9:0],A[15:11]Address Inputs15V DD Core and I/O Power 15A10/AP Address Input/Autoprecharge 1V SS Ground56BA[2:0] SDRAM Bank Address 3V REF Input/Output Reference 1ODT[1:0]On-die termination control2V DD SPD SPD Power1SCL Serial Presence Detect (SPD)Clock Input1RFU Reserved for future use 12 SDA SPD Data Input/Output 1 NCNo connect4SA[1:0]SPD address2Total:214Input/Output Functional DescriptionSymbol Type Polarity FunctionCK0/CK0, CK1/CK1InputCrosspointThe system clock inputs. All address and command lines are sampled on the cross point of therising edge of CK and falling edge of CK. A Delay Locked Loop (DLL) circuit is driven from theclock inputs and output timing for read operations is synchronized to the input clock.RFU pins for 2 CK pairs reserved.CKE[1:0]Input Active High Activates the DDR2 SDRAM CK signal when high and deactivates the CK signal when low. By deactivating the clocks, CKE low initiates the Power Down mode or the Self Refresh mode. RFU pins for 2 CKEs reserved.S[1:0]Input Active Low Enables the associated DDR2 SDRAM command decoder when low and disables the com-mand decoder when high. When the command decoder is disabled, new commands are ignored but previous operations continue. Rank 0 is selected by S0; Rank 1 is selected by S1. Ranks are also called "Physical banks". RFU pins for 2 Ss reserved.RAS, CAS,WE Input Active Low When sampled at the cross point of the rising edge of CK and falling edge of CK CAS, RAS, and WE define the operation to be executed by the SDRAM.BA[2:0]Input—Selects which DDR2 SDRAM internal bank of four or eight is activated.ODT[1:0]Input Active High Asserts on-die termination for DQ, DM, DQS, and DQS signals if enabled via the DDR2SDRAM mode register. RFU pins for 2 ODTs reserved.A[9:0],A10/AP, A[15:11]Input—During a Bank Activate command cycle, defines the row address when sampled at the crosspoint of the rising edge of CK and falling edge of CK. During a Read or Write command cycle,defines the column address when sampled at the cross point of the rising edge of CK and fall-ing edge of CK. In addition to the column address, AP is used to invoke autoprecharge opera-tion at the end of the burst read or write cycle. If AP is high, autoprecharge is selected andBA0-BAn defines the bank to be precharged. If AP is low, autoprecharge is disabled. During aPrecharge command cycle, AP is used in conjunction with BA0-BAn to control which bank(s) toprecharge. If AP is high, all banks will be precharged regardless of the state of BA0-BAninputs. If AP is low, then BA0-BAn are used to define which bank to precharge.DQ[63:0]In/Out—Data Input/Output pins.DM[7:0]Input Active High The data write masks, associated with one data byte. In Write mode, DM operates as a byte mask by allowing input data to be written if it is low but blocks the write operation if it is high. In Read mode, DM lines have no effect.DQS[7:0], DQS[7:0]In/Out CrosspointThe data strobes, associated with one data byte, sourced with data transfers. In Write mode,the data strobe is sourced by the controller and is centered in the data window. In Read mode,the data strobe is sourced by the DDR2 SDRAMs and is sent at the leading edge of the datawindow. DQS signals are complements, and timing is relative to the crosspoint of respectiveDQS and DQS. If the module is to be operated in single ended strobe mode, all DQS signalsmust be tied on the system board to VSS and DDR2 SDRAM mode registers programmedappropriately.V DD, V DD SPD,V SSSupply—Power supplies for core, I/O, Serial Presence Detect, and ground for the module.SDA In/Out—This is a bidirectional pin used to transfer data into or out of the SPD EEPROM. A resistor must be connected to V DD to act as a pull up.SCL Input—This signal is used to clock data into and out of the SPD EEPROM. A resistor may be con-nected from SCL to V DD to act as a pull up.SA[1:0]Input—Address pins used to select the Serial Presence Detect base address. RFU pins for 2nd SPD reserved.NC,TEST In/Out—The TEST pin is reserved for bus analysis tools and is not connected on normal memory mod-ules (MicroDIMMs)..DDR2 SDRAM MicroDIMM PinoutPin #LowerSidePin#UpperSidePin#LowerSidePin#UpperSidePin#LowerSidePin#UpperSidePin#LowerSidePin#UpperSide1V REF108V SS28DQS2135Vss55BA0162BA182DQ43189DQ47 2V SS109DQ429Vss136DQ2856WE163RAS83V SS190V SS 3DQ0110DQ530DQ18137DQ2957V DD164V DD84DQ48191DQ52 4DQ1111V SS31DQ19138Vss58RFU(S2)165S085DQ49192DQ535V SS112DM032Vss139DQS359RFU(ODT2)166ODT086V SS193V SS6DQS0113V SS33DQ24140DQS360CAS167A1387RFU(CK3)194CK17DQS0114DQ634DQ25141Vss61V DD168V DD88RFU(CK3)195CK18V SS115DQ735Vss142DQ3062S1169RFU(S3)89V SS196V SS9DQ2116V SS36DM3143DQ3163ODT1170RFU(ODT3)90DM6197DQS610DQ3117DQ1237Vss144Vss64V DD171V DD91V SS198DQS6 11V SS118DQ1338DQ26145NC,TEST65NC172NC92DQ50199V SS 12DQ8119V SS39DQ27146V DD66V SS173V SS93DQ51200DQ54 13DQ9120DM140Vss147CKE167DQ32174DQ3694V SS201DQ5514V SS121V SS41NC148RFU(CKE3)68DQ33175DQ3795DQ56202V SS15RFU(CK2)122CK042V DD149V DD69V SS176V SS96DQ57203DQ6016RFU(CK2)123CK043CKE0150A1570DQS4177DM497V SS204DQ6117V SS124V SS44RFU(CKE2)151A1471DQS4178V SS98DQS7205V SS18DQS1125DQ1445V DD152V DD72V SS179DQ3899DQS7206DM7 19DQS1126DQ1546BA2153A1273DQ34180DQ39100V SS207V SS 20V SS127V SS47A11154A974DQ35181V SS101DQ58208DQ62 21DQ10128DQ2048A7155A875V SS182DQ44102DQ59209DQ63 22DQ11129DQ2149V DD156V DD76DQ40183DQ45103V SS210V SS 23Vss130Vss50A5157A677DQ41184V SS104SDA211SA0 24DQ16131DM251A4158A378V SS185DQS5105SCL212RFU(*1) 25DQ17132Vss52A2159A179DM5186DQS5106NC213SA1 26Vss133DQ2253V DD160V DD80V SS187V SS107V DD SPD214RFU(*2) 27DQS2134DQ2354A10/AP161A081DQ42188DQ46Note: NC = No Connect; NC,TEST(pin 145) is for bus analysis tool and is not connected on normal memory modules. (*1) = SA0 for 2nd SPD, (*2) = SA1 for 2nd SPD.Block Diagram: Raw Card Version A (Populated as 2 ranks of x16 SDRAMs)Block Diagram: Raw Card Version B (Populated as 1 rank of x16 SDRAMs)#Unless otherwise noted, resistorand V DD Q values are 22 Ω ± 5%DQ wiring may differ from that described in this drawing;however, DQ/DM/DQS/DQS relationships are maintained as shown8pFLoad CapacitorsA0-AN RAS CAS WEmatching on ± 0.5pFBA0-BA23.0Ω±5%4. Component Detailsx16 Ballout for 256Mb, 512Mb, 1Gb, 2Gb and 4Gb DDR2 SDRAMs (Top View) 123789NC NC A NC NCBCVDD NC VSS D VSSQ UDQS VDDQ UDQ6VSSQ UDM E UDQS VSSQ UDQ7 VDDQ UDQ1VDDQ F VDDQ UDQ0VDDQ UDQ4VSSQ UDQ3G UDQ2VSSQ UDQ5VDD NC VSS H VSSQ LDQS VDDQ LDQ6VSSQ LDM J LDQS VSSQ LDQ7 VDDQ LDQ1VDDQ K VDDQ LDQ0VDDQ LDQ4VSSQ LDQ3L LDQ2VSSQ LDQ5 VDDL VREF VSS M VSSDL CK VDD CKE WE N RAS CK ODT BA2BA0BA1P CAS CSA10A1R A2A0VDD VSS A3A5T A6A4A7A9U A11A8VSS VDD A12A14V A15A13WYNC NC AA NC NCDDR2 SDRAM FBGA Component SpecificationsThe DDR2 SDRAM components used with this DIMM design specification are intended to be consistent with JEDEC MO-207 DK-Z and DL-Z.Reference SPD Component SpecificationsThe Serial Presence Detect EEPROMs have their own power pin, V DD SPD, so that they can be programmed or read without powering up the rest of the module. The wide voltage range permits use with 1.8V, 2.5V or 3.3V serial buses.SPD Component DC Electrical CharacteristicsSymbol Parameter Min Max UnitsV DD SPD Core Supply Voltage 1.7 3.6V5. Unbuffered MicroDIMM DetailsDDR2 SDRAM Module Configurations (Reference Designs)Raw Card MicroDIMMCapacityMicroDIMMOrganizationSDRAMDensitySDRAMOrganization# ofSDRAMs# ofRanksSDRAMPackage Type# of banks inSDRAM# Address bitsrow/colA256 MB32 M x 64256 Mbit16 M x 1682FBGA413/9 A512 MB64 M x 64512 Mbit32 M x 1682FBGA413/10 A 1 GB128 M x 64 1 Gbit64 M x 1682FBGA813/10 A 2 GB256 M x 64 2 Gbit128 M x 1682FBGA814/10 A 4 GB512 M x 64 4 Gbit256 M x 1682FBGA8TBDRaw Card MicroDIMMCapacityMicroDIMMOrganizationSDRAMDensitySDRAMOrganization# ofSDRAMs# ofRanksSDRAMPackage Type# of banks inSDRAM# Address bitsrow/colB128 MB16 M x 64256 Mbit16 M x 1641FBGA413/9 B256 MB32 M x 64512 Mbit32 M x 1641FBGA413/10 B512 MB64 M x 64 1 Gbit64 M x 1641FBGA813/10B 1 GB128 M x 64 2 Gbit128 M x 1641FBGA814/10B 2 GB256 M x 64 4 Gbit256 M x 1641FBGA8TBD Input Loading MatrixSignal NamesInputDeviceR/C A R/C BClock (CKn, CKn )SDRAM42 CKEn/Sn/ODTn SDRAM44 Addr/RAS/CAS/BA/WE SDRAM84 DQn/DQSn/DQSn/DMn SDRAM21 SCL/SDA/SAn EEPROM11DDR2 MicroDIMM Gerber File ReleasesReference design file updates will be released as needed. This specification will reflect the most recent design files, but may be updated to reflect clarifications to the specification only; in these cases, the design files will not be updated. The following table outlines the most recent design file releasesNote: Future design file releases will include both a date and a revision label. All changes to the design file are also documented within the ‘read-me’ file.Raw Card SpecificationRevisionApplicable Design File NotesA0.5A0 B0.5B0Example Raw Card Component PlacementThe component layout for Raw Cards A, and B are similar. In the case of Raw Card B, DDR2 SDRAMs will be included on the front side of the card; however, passive components are on both sides of the board. This example is for reference only; refer to JEDEC standard MO-TBD for details.6. MicroDIMM Wiring DetailsSignal GroupsThis specification categorizes SDRAM timing-critical signals into four groups whose members have identical loadings and routings. The following table summarizes the signals contained in each group..Signal Group Signals In Group PageClocks for Unbuffered MicroDIMM CK [1:0], CK [1:0]14, 15Data, Data Mask, Data Strobe DQ [63:0], DM[7:0], DQS[7:0], DQS[7:0]16, 17Select, Clock Enable, ODT S [1:0], CKE [1:0], ODT[1:0]18Address/Control Ax, BAx, RAS, CAS, WE19, 20General Net Structure Routing GuidelinesNet structures and lengths must satisfy signal quality and setup/hold time requirements for the memory inter-face. Net structure diagrams for each signal group are shown in the following sections. Each diagram is accompanied by a trace length table that lists the minimum and maximum allowable lengths for each trace segment and/or net.The general routing recommendations are as follows. Other stackups and layouts are possible that meet the electrical characteristics.•Route all signal traces using appropriate trace width(e.g: 0.075mm) and enough spacing(e.g: 0.15mm) between adjacent traces considering cross talk effect.•Route clocks as much as possible using the inner layers.•Test points are required.Explanation of Net Structure DiagramsThe net structure routing diagrams provide a reference design example for each raw card version. These designs provide an initial basis for unbuffered MicroDIMM designs. The diagrams should be used to deter-mine individual signal wiring on a MicroDIMM for any supported configuration. Only transmission lines (repre-sented as cylinders and labeled with trace length designators “TL”) represent physical trace segments. All other lines are zero in length. To verify MicroDIMM functionality, a full simulation of all signal integrity and tim-ing is required. The given net structures and trace lengths are not inclusive for all solutions.Once the net structure has been determined, the permitted trace lengths for the net structure can be read from the table below each net structure routing diagram. Some configurations require the use of multiple net structure routing diagrams to account for varying load quantities on the same signal. All diagrams define one load as one DDR2 SDRAM input unless mentioned. It is highly recommended that the net structure routing data in this document be simulated by the user.Differential Clock Net Structures CK[1:0], CK[1:0]DDR2 SDRAM clock signals must be carefully routed to meet the following requirements:•Signal quality •Rise/Fall time•Cross point of the differential pair in the SDRAM •JEDEC-compatible reference delays•Minimal segment length differences (less than 2.54mm total) between clocks of the same functionClock Net Wiring (Raw card A)Clock Routing Trace Lengths (Raw card A)Raw card TL0 Outer TL1 Inner TL2 Inner TL3 Outer TL4 Inner TL5 Outer Notes Min Max Min Max Min Max Min Max Min Max Min Max A2.02.36.26.77.78.13.84.36.37.90.70.911.All distances are given in millimeters and must be kept within a tolerance of ± 0.8 millimeter.TL0MicroDIMM ConnectorTL1TL2TL3TL3CK CKSDRAM SDRAMTL5TL2TL3TL3SDRAMSDRAMTL5R = 200 Ω± 5%R = 200 Ω± 5%TL4TL4Clock Net Wiring (Raw card B)Clock Routing Trace Lengths (Raw card B)Raw card TL0 Outer TL1 Inner TL2 Inner TL3 Outer TL4 Outer Notes Min Max Min Max Min Max Min Max Min Max B2.02.318.218.47.78.13.84.31.52.011.All distances are given in millimeters and must be kept within a tolerance of ± 0.8 millimeter.TL0MicroDIMM ConnectorTL1TL2TL3CK CKSDRAMTL2TL3SDRAMR = 200 Ω± 5%R = 200 Ω± 5%TL4TL4Data Net StructuresDQ[63:0], DM[7:0], DQS[7:0], DQS[7:0]Special attention has been paid to balancing the data nets within a DDR2 SDRAM, within a particularMicroDIMM, and across the MicroDIMM family. Data nets have been placed in order to bound the data strobe nets. Because data travels with the data strobe, the placement of the strobe in the middle of the narrow win-dow aids in data timing. Although it is not necessary to ensure consistent delays between SDRAMs and/or card types, doing so facilitates system design, system simulation, and DIMM specifications. It is recommend to maintain consistent delays for all nets as described in the following tables.Net Structure Routing for DQ[63:0], DM[7:0], DQS[7:0], DQS[7:0] (Raw card A)Trace Lengths for DQ[63:0], DM[7:0], DQS[7:0], DQS[7:0] (Raw card A)Raw card TL0 Outer TL1 Outer TL2 Outer TotalR1Ohms Notes Min Max Min Max Min Max Min Max A1.04.618.720.92.93.125.325.5221,2,3,41.All distances are given in millimeters and must be kept within a tolerance of ± 0.8 millimeter.2.Total Min and Total Max refer to the min and max respectively of TL0 + TL1 + TL2.3.TL0 and TL1 of Raw Card A is adjusted to compensate for the delay caused by vias on DQ nets. Traces with one via are assumed to have 1.6mm additional length. Traces with two vias are assumed to have 3.2mm additional length.4.These signals must be referenced to ground.TL0MicroDIMM Connector22 Ω ± 5%TL2SDRAM PinTL2SDRAM PinTL1Net Structures Routing for DQ[63:0], DM[7:0], DQS[7:0], DQS[7:0] (Raw card B )Trace Lengths for DQ[63:0], DM[7:0], DQS[7:0], DQS[7:0] (Raw card B )Raw cardTL0 Outer TL1 OuterTotalR1Ohms Notes Min Max Min Max Min Max B1.04.621.723.925.325.5221,2,3,41.All distances are given in millimeters and must be kept within a tolerance of ± 0.8 millimeter.2.Total Min and Total Max refer to the min and max respectively of TL0 + TL1.3.TL0 and TL1 of Raw Card B is adjusted to compensate for the delay caused by via on DQ nets.Traces with one via are assumed to have 1.6mm additional length. Traces with two vias are assumed to have 3.2mm additional length.4.These signals must be referenced to ground.TL0MicroDIMM Connector22 Ω ± 5%SDRAM PinTL1Control Net Structures S [1:0], CKE[1:0], ODT[1:0] (Raw cards A, B)Net Structure Routing for Control Net Structures S [1:0], CKE[1:0], ODT[1:0] (Raw cards A, B)Trace Lengths for Control Net Structures S [1:0], CKE[1:0], ODT[1:0] (Raw cards A, B)TL0 OuterTL1 Outer/Inner TL2 Inner TL3 Inner TL4 Outer Notes Raw CardMin Max Min Max Min Max Min Max Min Max A 1.0 4.622.029.116.017.5 6.57.1 2.7 4.21,2,3B1.04.622.029.116.017.56.57.12.74.21,2,31. All distances are given in mm and should be kept within a tolerance of ± 0.8 mm2. TL0 and TL1 are adjusted to compensate for the delay caused by via. Traces with one via are assumed to have 1.6mm additional length. Traces with two vias are assumed to have3.2mm additional length.3. These signals must be referenced to VDD.TL0MicroDIMM ConnectorTL2TL23.0 Ω ± 5%TL1TL3TL3TL4SDRAM PinTL4SDRAM PinTL4SDRAM PinTL3TL3TL4SDRAM PinAddress/Control Net Structures Ax, BAx, RAS, CAS, WE (Raw card A ).Net Structure Routing for Address/Control Net Structures Ax, BAx, RAS, CAS, WE (Raw card A )Trace Lengths for Address/Control Net Structures Ax, BAx, RAS, CAS, WE (Raw card A )TL0 OuterTL1 Outer/Inner TL2 Inner TL3 inner TL4 Outer Notes Raw CardMin Max Min Max Min Max Min Max Min Max A1.04.622.029.116.017.56.57.11.08.31,2,31. All distances are given in mm and should be kept within a tolerance of ± 0.8 mm2. TL0 and TL1 are adjusted to compensate for the delay caused by via. Traces with one via are assumed to have 1.6mm additional length. Traces with two vias are assumed to have3.2mm additional length. 3. These signals must be referenced to VDD.TL0MicroDIMM ConnectorTL4SDRAM PinTL2TL23.0 Ω ± 5%TL1TL3TL3TL4SDRAM PinTL4SDRAM PinTL4SDRAM PinTL4SDRAM PinTL3TL3TL4SDRAM Pin TL4SDRAM PinTL4SDRAM PinAddress/Control Net Structures Ax, BAx, RAS, CAS, WE (Raw card B).Net Structure Routing for Address/Control Net Structures Ax, BAx, RAS, CAS, WE (Raw card B)Trace Lengths for Address/Control Net Structures Ax, BAx, RAS, CAS, WE (Raw card B)TL0 OuterTL1 Outer/Inner TL2 Inner TL3 inner TL4 Outer TL5 Outer Notes Raw CardMin Max Min Max Min Max Min Max Min Max Min Max B1.04.622.029.116.017.56.57.11.08.33.04.01,2,31. All distances are given in mm and should be kept within a tolerance of ± 0.8 mm2. TL0 and TL1 are adjusted to compensate for the delay caused by via. Traces with one via are assumed to have 1.6mm additional length. Traces with two vias are assumed to have3.2mm additional length.3. These signals must be referenced to VDD.TL0MicroDIMM ConnectorTL2TL23.0 Ω ± 5% TL1TL3TL3TL4SDRAM PinTL4SDRAM PinTL4SDRAM PinTL3TL3TL4SDRAM PinTL58pF ± 0.5pFCross Section RecommendationsAn example of the DDR2 MicroDIMM printed circuit board design uses six-layers of glass epoxy material. PCBs should contain full plane layers for reference plane. The reference planes can be divided so adjacent signal layers maintain a constant Vss or Vdd reference. All data group signals are referenced to Vss and all address/command are referenced to Vdd. The required board impedance is 60 Ω± 10%.PCB Electrical SpecificationsParameter Min Max UnitsTrace velocity: S0 (outer layers) 5.5 6.7ps/mmTrace velocity: S0 (inner layers) 6.57.6ps/mmTrace impedance: Z0 (all layers)5466OhmsExample Layer Stackup for 0.075mm width traceTest PointsAll DDR2 components are in BGA packages which makes the package pads inaccessible for probing during-system development. The DDR2 MicroDIMMs have test points identified to make initial evaluation easier. In some cases test pads have been added and in other cases existing vias are used as test points. An effort has been made to provide testability on some signals in all signal groups but 100% coverage is not possible.Raw Card A Test Points Example(Front View)DQ22CK0-CK1-DQS at resistor pack.CK0CK1DQ7DQ44DQ52DQ28Raw Card B Test Points Example(Front View)BA2DQ22CK0-CK1-A7A3A12A10A9A14S0-A11A6BA0A2BA1CKE0A15A5A1CAS-ODT0RAS-WE-DQS at resistor pack.CK0CK1DQ7DQ44DQ52A13A0A4A8DQ28DQ367. Serial Presence Detect DefinitionThe Serial Presence Detect (SPD) function MUST be implemented on the PC2-4200 DDR2 SDRAM Unbuf-fered MicroDIMM. The component used and the data contents must adhere to the most recent version of the JEDEC DDR2 SDRAM SPD Specifications. Please refer to this document for all technical specifications and requirements of the serial presence detect devices.The following table is intended to be an example of a typical PC2-4200 MicroDIMM. SPD values indicating different MicroDIMM performance characteristics will be utilized based on specific characteristics of the SDRAMs or MicroDIMMs. This example assumes:•Module Organization: 512MB•Device Composition: 32Mx16•Device Package: FBGA•Module Physical Ranks: 2•CAS latency: 4(DDR2-533), 3(DDR2-400)Serial Presence Detect Data Example (Part 1 of 3)Byte # (dec)Byte #(hex)DescriptionSPD Entry ValueSerial PDData Entry(Hexadecimal)NotesDDR2-533DDR2-400DDR2-533DDR2-400000Number of Serial PD Bytes written during production128801 101Total Number of Bytes in Serial PD device256082202Fundamental Memory Type (FPM, EDO, SDRAM,DDR, DDR2, ...)DDR2 SDRAM08303Number of Row Addresses on Assembly130D 404Number of Column Addresses on Assembly100A505Number of DIMM RanksModule height:30mm, Planar,card on card: no,2Ranks61606Data Width of this Assembly x6440 707Reserved Undefined00 808Voltage Interface Level of this assembly SSTL 1.8V05909SDRAM Cycle Time at maximum supported CASlatency (CL), CL = X3.75ns 5.00ns3D503100A SDRAM Access from Clock+/-0.50ns+/-0.50ns5050110B DIMM configuration type (Non-parity, or ECC)Non-Parity00120C Refresh Rate/Type7.8us/SR823,4 130D Primary SDRAM Width x1610140E Error Checking SDRAM Width NA00150F Reserved Undefined001.This will typically be programmed as 128 bytes.2.This will typically be programmed as 256 bytes.3.From Data sheet.4.High order bit is self refresh "flag". If set to "1", the assembly supports self refresh.5.These are optional, in accordance with JEDEC specification.1610SDRAM device attributes: Burst lengths supported4,80C1711SDRAM device attributes: Number of Banks onSDRAM device40431812SDRAM device attributes: CAS Latency4310083 1913Reserved Undefined000 2014DIMM type information MicroDIMM082115SDRAM Module Attributes Normal DIMM002216SDRAM device attributes: General no optional aspect002317Minimum Clock Cycle at CLX -1Undefined FF32418Maximum Data Access Time (t AC) from Clock at CLX -1Undefined FF32519Minimum Clock Cycle Time at CLX-2Undefined FF3261A Maximum Data Access Time (t AC) from Clockat CLX-2Undefined FF3271B Minimum Row Precharge Time (t RP)15.0ns15.0ns3C3C3 281C Minimum Row Active to Row Active delay (t RRD)7.5ns7.5ns1E1E3 291D Minimum RAS to CAS delay (t RCD)15.0ns15.0ns3C3C3 301E Minimum Active to Precharge Time (t RAS)45.0ns45.0ns2D2D3 311F Module Rank Density256MB403220Address and Command input Setup Time BeforeClock (t IS)0.60ns0.60ns606033321Address and Command input Hold Time After Clock(t IH)0.60ns0.60ns606033422Data Input Setup Time Before Clock (t DS)0.35ns0.35ns35353 3523Data Input Hold Time After Clock (t DH)0.35ns0.35ns35353 3624Write recovery time (t WR)15.0ns15.0ns3C3C3 3725Internal write to read command delay (t WTR)7.5ns10ns1E283 3826Internal read to precharge command delay (t RTP)7.5ns7.5ns1E1E3 3927Memory analysis probe characteristics Undefined004028Reserved Undefined004129SDRAM device minimum active to active/auto refreshtime (t RC)60.0ns60.0ns3C3C3422A SDRAM device minimum auto-refresh to active/autorefresh command period (t RFC)105.0ns105.0ns69693Serial Presence Detect Data Example (Part 2 of 3)Byte # (dec)Byte #(hex)DescriptionSPD Entry ValueSerial PDData Entry(Hexadecimal)NotesDDR2-533DDR2-400DDR2-533DDR2-4001.This will typically be programmed as 128 bytes.2.This will typically be programmed as 256 bytes.3.From Data sheet.4.High order bit is self refresh "flag". If set to "1", the assembly supports self refresh.5.These are optional, in accordance with JEDEC specification.。
Atomic Decomposition by Basis pursuit

SIAM R EVIEWc2001Society for Industrial and Applied Mathematics Vol.43,No.1,pp.129–159Atomic Decomposition by BasisPursuit ∗Scott Shaobing Chen †David L.Donoho ‡Michael A.Saunders §Abstract.The time-frequency and time-scale communities have recently developed a large number ofovercomplete waveform dictionaries—stationary wavelets,wavelet packets,cosine packets,chirplets,and warplets,to name a few.Decomposition into overcomplete systems is not unique,and several methods for decomposition have been proposed,including the method of frames (MOF),matching pursuit (MP),and,for special dictionaries,the best orthogonal basis (BOB).Basis pursuit (BP)is a principle for decomposing a signal into an “optimal”superpo-sition of dictionary elements,where optimal means having the smallest l 1norm of coef-ficients among all such decompositions.We give examples exhibiting several advantages over MOF,MP,and BOB,including better sparsity and superresolution.BP has interest-ing relations to ideas in areas as diverse as ill-posed problems,abstract harmonic analysis,total variation denoising,and multiscale edge denoising.BP in highly overcomplete dictionaries leads to large-scale optimization problems.With signals of length 8192and a wavelet packet dictionary,one gets an equivalent linear program of size 8192by 212,992.Such problems can be attacked successfully only because of recent advances in linear and quadratic programming by interior-point methods.We obtain reasonable success with a primal-dual logarithmic barrier method and conjugate-gradient solver.Key words.overcomplete signal representation,denoising,time-frequency analysis,time-scale anal-ysis, 1norm optimization,matching pursuit,wavelets,wavelet packets,cosine pack-ets,interior-point methods for linear programming,total variation denoising,multiscale edges,MATLAB code AMS subject classifications.94A12,65K05,65D15,41A45PII.S003614450037906X1.Introduction.Over the last several years,there has been an explosion of in-terest in alternatives to traditional signal representations.Instead of just represent-ing signals as superpositions of sinusoids (the traditional Fourier representation)we now have available alternate dictionaries—collections of parameterized waveforms—of which the wavelets dictionary is only the best known.Wavelets,steerable wavelets,segmented wavelets,Gabor dictionaries,multiscale Gabor dictionaries,wavelet pack-∗Publishedelectronically February 2,2001.This paper originally appeared in SIAM Journal onScientific Computing ,Volume 20,Number 1,1998,pages 33–61.This research was partially sup-ported by NSF grants DMS-92-09130,DMI-92-04208,and ECS-9707111,by the NASA Astrophysical Data Program,by ONR grant N00014-90-J1242,and by other sponsors./journals/sirev/43-1/37906.html†Renaissance Technologies,600Route 25A,East Setauket,NY 11733(schen@).‡Department of Statistics,Stanford University,Stanford,CA 94305(donoho@).§Department of Management Science and Engineering,Stanford University,Stanford,CA 94305(saunders@).129D o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h p130S.S.CHEN,D.L.DONOHO,AND M.A.SAUNDERSets,cosine packets,chirplets,warplets,and a wide range of other dictionaries are now available.Each such dictionary D is a collection of waveforms (φγ)γ∈Γ,with γa parameter,and we envision a decomposition of a signal s ass =γ∈Γαγφγ,(1.1)or an approximate decomposition s =m i =1αγi φγi +R (m ),(1.2)where R (m )is a residual.Depending on the dictionary,such a representation de-composes the signal into pure tones (Fourier dictionary),bumps (wavelet dictionary),chirps (chirplet dictionary),etc.Most of the new dictionaries are overcomplete ,either because they start out that way or because we merge complete dictionaries,obtaining a new megadictionary con-sisting of several types of waveforms (e.g.,Fourier and wavelets dictionaries).The decomposition (1.1)is then nonunique,because some elements in the dictionary have representations in terms of other elements.1.1.Goals of Adaptive Representation.Nonuniqueness gives us the possibility of adaptation,i.e.,of choosing from among many representations one that is most suited to our purposes.We are motivated by the aim of achieving simultaneously the following goals .•Sparsity.We should obtain the sparsest possible representation of the object—the one with the fewest significant coefficients.•Superresolution.We should obtain a resolution of sparse objects that is much higher resolution than that possible with traditional nonadaptive approaches.An important constraint ,which is perhaps in conflict with both the goals,follows.•Speed.It should be possible to obtain a representation in order O (n )or O (n log(n ))time.1.2.Finding a Representation.Several methods have been proposed for obtain-ing signal representations in overcomplete dictionaries.These range from general approaches,like the method of frames (MOF)[9]and the method of matching pursuit (MP)[29],to clever schemes derived for specialized dictionaries,like the method of best orthogonal basis (BOB)[7].These methods are described briefly in section 2.3.In our view,these methods have both advantages and shortcomings.The principal emphasis of the proposers of these methods is on achieving sufficient computational speed.While the resulting methods are practical to apply to real data,we show below by computational examples that the methods,either quite generally or in important special cases,lack qualities of sparsity preservation and of stable superresolution.1.3.Basis Pursuit.Basis pursuit (BP)finds signal representations in overcom-plete dictionaries by convex optimization:it obtains the decomposition that minimizes the 1normof the coefficients occurring in the representation.Because of the nondif-ferentiability of the 1norm,this optimization principle leads to decompositions that can have very different properties fromthe MOF—in particular,they can be m uch sparser.Because it is based on global optimization,it can stably superresolve in ways that MP cannot.D o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h pATOMIC DECOMPOSITION BY BASIS PURSUIT131BP can be used with noisy data by solving an optimization problem trading offa quadratic misfit measure with an 1normof coefficients.Examples show that it can stably suppress noise while preserving structure that is well expressed in the dictionary under consideration.BP is closely connected with linear programming.Recent advances in large-scale linear programming—associated with interior-point methods—can be applied to BP and can make it possible,with certain dictionaries,to nearly solve the BP optimization problem in nearly linear time.We have implemented primal-dual log barrier interior-point methods as part of a MATLAB [31]computing environment called Atomizer,which accepts a wide range of dictionaries.Instructions for Internet access to Atomizer are given in section 7.3.Experiments with standard time-frequency dictionaries indicate some of the potential benefits of BP.Experiments with some nonstandard dictionaries,like the stationary wavelet dictionary and the heaviside dictionary,indicate important connections between BP and methods like Mallat and Zhong’s [29]multiscale edge representation and Rudin,Osher,and Fatemi’s [35]total variation-based denoising methods.1.4.Contents.In section 2we establish vocabulary and notation for the rest of the article,describing a number of dictionaries and existing methods for overcomplete representation.In section 3we discuss the principle of BP and its relations to existing methods and to ideas in other fields.In section 4we discuss methodological issues associated with BP,in particular some of the interesting nonstandard ways it can be deployed.In section 5we describe BP denoising,a method for dealing with problem (1.2).In section 6we discuss recent advances in large-scale linear programming (LP)and resulting algorithms for BP.For reasons of space we refer the reader to [4]for a discussion of related work in statistics and analysis.2.Overcomplete Representations.Let s =(s t :0≤t <n )be a discrete-time signal of length n ;this may also be viewed as a vector in R n .We are interested in the reconstruction of this signal using superpositions of elementary waveforms.Traditional methods of analysis and reconstruction involve the use of orthogonal bases,such as the Fourier basis,various discrete cosine transformbases,and orthogonal wavelet bases.Such situations can be viewed as follows:given a list of n waveforms,one wishes to represent s as a linear combination of these waveforms.The waveforms in the list,viewed as vectors in R n ,are linearly independent,and so the representation is unique.2.1.Dictionaries and Atoms.A considerable focus of activity in the recent sig-nal processing literature has been the development of signal representations outside the basis setting.We use terminology introduced by Mallat and Zhang [29].A dic-tionary is a collection of parameterized waveforms D =(φγ:γ∈Γ).The waveforms φγare discrete-time signals of length n called atoms .Depending on the dictionary,the parameter γcan have the interpretation of indexing frequency,in which case the dictionary is a frequency or Fourier dictionary,of indexing time-scale jointly,in which case the dictionary is a time-scale dictionary,or of indexing time-frequency jointly,in which case the dictionary is a time-frequency ually dictionaries are complete or overcomplete,in which case they contain exactly n atoms or more than n atoms,but one could also have continuum dictionaries containing an infinity of atoms and undercomplete dictionaries for special purposes,containing fewer than n atoms.Dozens of interesting dictionaries have been proposed over the last few years;we focusD o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h p132S.S.CHEN,D.L.DONOHO,AND M.A.SAUNDERSin this paper on a half dozen or so;much of what we do applies in other cases as well.2.1.1.T rivial Dictionaries.We begin with some overly simple examples.The Dirac dictionary is simply the collection of waveforms that are zero except in one point:γ∈{0,1,...,n −1}and φγ(t )=1{t =γ}.This is of course also an orthogonal basis of R n —the standard basis.The heaviside dictionary is the collection of waveforms that jump at one particular point:γ∈{0,1,...,n −1};φγ(t )=1{t ≥γ}.Atoms in this dictionary are not orthogonal,but every signal has a representation s =s 0φ0+n −1 γ=1(s γ−s γ−1)φγ.(2.1)2.1.2.Frequency Dictionaries.A Fourier dictionary is a collection of sinusoidalwaveforms φγindexed by γ=(ω,ν),where ω∈[0,2π)is an angular frequency variable and ν∈{0,1}indicates phase type:sine or cosine.In detail,φ(ω,0)=cos(ωt ),φ(ω,1)=sin(ωt ).For the standard Fourier dictionary,we let γrun through the set of all cosines with Fourier frequencies ωk =2πk/n ,k =0,...,n/2,and all sines with Fourier frequencies ωk ,k =1,...,n/2−1.This dictionary consists of n waveforms;it is in fact a basis,and a very simple one:the atoms are all mutually orthogonal.An overcomplete Fourier dictionary is obtained by sampling the frequencies more finely.Let be a whole number >1and let Γ be the collection of all cosines with ωk =2πk/( n ),k =0,..., n/2,and all sines with frequencies ωk ,k =1,..., n/2−1.This is an -fold overcomplete system.We also use complete and overcomplete dictionaries based on discrete cosine transforms and sine transforms.2.1.3.Time-Scale Dictionaries.There are several types of wavelet dictionaries;to fix ideas,we consider the Haar dictionary with “father wavelet”ϕ=1[0,1]and “mother wavelet”ψ=1(1/2,1]−1[0,1/2].The dictionary is a collection of transla-tions and dilations of the basic mother wavelet,together with translations of a father wavelet.It is indexed by γ=(a,b,ν),where a ∈(0,∞)is a scale variable,b ∈[0,n ]indicates location,and ν∈{0,1}indicates gender.In detail,φ(a,b,1)=ψ(a (t −b ))·√a,φ(a,b,0)=ϕ(a (t −b ))·√a.For the standard Haar dictionary,we let γrun through the discrete collection ofmother wavelets with dyadic scales a j =2j /n ,j =j 0,...,log 2(n )−1,and locations that are integer multiples of the scale b j,k =k ·a j ,k =0,...,2j −1,and the collection of father wavelets at the coarse scale j 0.This dictionary consists of n waveforms;it is an orthonormal basis.An overcomplete wavelet dictionary is obtained by sampling the locations more finely:one location per sample point.This gives the so-called sta-tionary Haar dictionary,consisting of O (n log 2(n ))waveforms.It is called stationary since the whole dictionary is invariant under circulant shift.A variety of other wavelet bases are possible.The most important variations are smooth wavelet bases,using splines or using wavelets defined recursively fromtwo-scale filtering relations [10].Although the rules of construction are more complicated (boundary conditions [33],orthogonality versus biorthogonality [10],etc.),these have the same indexing structure as the standard Haar dictionary.In this paper,we use symmlet -8smooth wavelets,i.e.,Daubechies nearly symmetric wavelets with eight vanishing moments;see [10]for examples.D o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h pATOMIC DECOMPOSITION BY BASIS PURSUIT133Time 00.5100.20.40.60.81(c) Time DomainFig.2.1Time-frequency phase plot of a wavelet packet atom.2.1.4.Time-Frequency Dictionaries.Much recent activity in the wavelet com-munities has focused on the study of time-frequency phenomena.The standard ex-ample,the Gabor dictionary,is due to Gabor [19];in our notation,we take γ=(ω,τ,θ,δt ),where ω∈[0,π)is a frequency,τis a location,θis a phase,and δt is the duration,and we consider atoms φγ(t )=exp {−(t −τ)2/(δt )2}·cos(ω(t −τ)+θ).Such atoms indeed consist of frequencies near ωand essentially vanish far away from τ.For fixed δt ,discrete dictionaries can be built fromtim e-frequency lattices,ωk =k ∆ωand τ = ∆τ,and θ∈{0,π/2};with ∆τand ∆ωchosen sufficiently fine these are complete.For further discussions see,e.g.,[9].Recently,Coifman and Meyer [6]developed the wavelet packet and cosine packet dictionaries especially to meet the computational demands of discrete-time signal pro-cessing.For one-dimensional discrete-time signals of length n ,these dictionaries each contain about n log 2(n )waveforms.A wavelet packet dictionary includes,as special cases,a standard orthogonal wavelets dictionary,the Dirac dictionary,and a collec-tion of oscillating waveforms spanning a range of frequencies and durations.A cosine packet dictionary contains,as special cases,the standard orthogonal Fourier dictio-nary and a variety of Gabor-like elements:sinusoids of various frequencies weighted by windows of various widths and locations.In this paper,we often use wavelet packet and cosine packet dictionaries as exam-ples of overcomplete systems,and we give a number of examples decomposing signals into these time-frequency dictionaries.A simple block diagram helps us visualize the atoms appearing in the decomposition.This diagram,adapted from Coifman and Wickerhauser [7],associates with each cosine packet or wavelet packet a rectangle in the time-frequency phase plane.The association is illustrated in Figure 2.1for a cer-tain wavelet packet.When a signal is a superposition of several such waveforms,we indicate which waveforms appear in the superposition by shading the corresponding rectangles in the time-frequency plane.D o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h p134S.S.CHEN,D.L.DONOHO,AND M.A.SAUNDERS2.1.5.Further Dictionaries.We can always merge dictionaries to create mega-dictionaries;examples used below include mergers of wavelets with heavisides.2.2.Linear Algebra.Suppose we have a discrete dictionary of p waveforms and we collect all these waveforms as columns of an n -by-p matrix Φ,say.The decompo-sition problem(1.1)can be written Φα=s ,(2.2)where α=(αγ)is the vector of coefficients in (1.1).When the dictionary furnishes a basis,then Φis an n -by-n nonsingular matrix and we have the unique representation α=Φ−1s .When the atoms are,in addition,mutually orthonormal,then Φ−1=ΦT and the decomposition formula is very simple.2.2.1.Analysis versus Synthesis.Given a dictionary of waveforms,one can dis-tinguish analysis from synthesis .Synthesis is the operation of building up a signal by superposing atoms;it involves a matrix that is n -by-p :s =Φα.Analysis involves the operation of associating with each signal a vector of coefficients attached to atoms;it involves a matrix that is p -by-n :˜α=ΦT s .Synthesis and analysis are very differ-ent linear operations,and we must take care to distinguish them.One should avoid assuming that the analysis operator ˜α=ΦT s gives us coefficients that can be used as is to synthesize s .In the overcomplete case we are interested in,p n and Φis not invertible.There are then many solutions to (2.2),and a given approach selects a particular solution.One does not uniquely and automatically solve the synthesis problemby applying a sim ple,linear analysis operator.We now illustrate the difference between synthesis (s =Φα)and analysis (˜α=ΦTs ).Figure 2.2a shows the signal Carbon .Figure 2.2b shows the time-frequency structure of a sparse synthesis of Carbon ,a vector αyielding s =Φα,using a wavelet packet dictionary.To visualize the decomposition,we present a phase-plane display with shaded rectangles,as described above.Figure 2.2c gives an analysis of Carbon ,with the coefficients ˜α=ΦT s ,again displayed in a phase plane.Once again,between analysis and synthesis there is a large difference in sparsity.In Figure 2.2d we compare the sorted coefficients of the overcomplete representation (synthesis)with the analysis coefficients.putational Complexity of Φand ΦT .Different dictionaries can im-pose drastically different computational burdens.In this paper we report compu-tational experiments on a variety of signals and dictionaries.We study primarily one-dimensional signals of length n ,where n is several thousand.Signals of this length occur naturally in the study of short segments of speech (a quarter-second to a half-second)and in the output of various scientific instruments (e.g.,FT-NMR spec-trometers).In our experiments,we study dictionaries overcomplete by substantial factors,say,10.Hence the typical matrix Φwe are interested in is of size “thousands”by “tens-of-thousands.”The nominal cost of storing and applying an arbitrary n -by-p matrix to a p -vector is a constant times np .Hence with an arbitrary dictionary of the sizes we are interested in,simply to verify whether (1.1)holds for given vectors αand s would require tens of millions of multiplications and tens of millions of words of memory.In contrast,most signal processing algorithms for signals of length 1000require only thousands of memory words and a few thousand multiplications.Fortunately,certain dictionaries have fast implicit algorithms .By this we mean that Φαand ΦT s can be computed,for arbitrary vectors αand s ,(a)without everD o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h pATOMIC DECOMPOSITION BY BASIS PURSUIT135Time0.5100.20.40.60.81Time0.5100.20.40.60.81(d) Sorted CoefficientsSynthesis: SolidAnalysis: Dashed Fig.2.2Analysis versus synthesis of the signal Carbon .storing the matrices Φand ΦT ,and (b)using special properties of the matrices to accelerate computations.The most well-known example is the standard Fourier dictionary for which we have the fast Fourier transform algorithm.A typical implementation requires 2·n storage locations and 4·n ·J multiplications if n is dyadic:n =2J .Hence for very long signals we can apply Φand ΦT with much less storage and time than the matrices would nominally require.Simple adaptation of this idea leads to an algorithm for overcomplete Fourier dictionaries.Wavelets give a more recent example of a dictionary with a fast implicit algorithm;if the Haar or S8-symmlet is used,both Φand ΦT may be applied in O (n )time.For the stationary wavelet dictionary,O (n log(n ))time is required.Cosine packets and wavelet packets also have fast implicit algorithms.Here both Φand ΦT can be applied in order O (n log(n ))time and order O (n log(n ))space—much better than the nominal np =n 2log 2(n )one would expect fromnaive use of the m atrix definition.For the viewpoint of this paper,it only makes sense to consider dictionaries with fast implicit algorithms.Among dictionaries we have not discussed,such algorithms may or may not exist.2.3.Existing Decomposition Methods.There are several currently popular ap-proaches to obtaining solutions to (2.2).2.3.1.Frames.The MOF [9]picks out,among all solutions of (2.2),one whose coefficients have minimum l 2norm:min α 2subject toΦα=s .(2.3)The solution of this problemis unique;label it α†.Geometrically,the collection of all solutions to (2.2)is an affine subspace in R p ;MOF selects the element of this subspace closest to the origin.It is sometimes called a minimum-length solution.There is aD o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h p136S.S.CHEN,D.L.DONOHO,AND M.A.SAUNDERSTime0.5100.20.40.60.81Time0.5100.20.40.60.81Fig.2.3MOF representation is not sparse.matrix Φ†,the generalized inverse of Φ,that calculates the minimum-length solution to a systemof linear equations:α†=Φ†s =ΦT (ΦΦT )−1s .(2.4)For so-called tight frame dictionaries MOF is available in closed form.A nice example is the standard wavelet packet dictionary.One can compute that for all vectors v ,ΦT v 2=L n · v 2,L n =log 2(n ).In short Φ†=L −1n ΦT .Notice that ΦTis simply the analysis operator.There are two key problems with the MOF.First,MOF is not sparsity preserving .If the underlying object has a very sparse representation in terms of the dictionary,then the coefficients found by MOF are likely to be very much less sparse.Each atom in the dictionary that has nonzero inner product with the signal is,at least potentially and also usually,a member of the solution.Figure 2.3a shows the signal Hydrogen made of a single atom in a wavelet packet dictionary.The result of a frame decomposition in that dictionary is depicted in a phase-plane portrait;see Figure 2.3c.While the underlying signal can be synthesized from a single atom,the frame decomposition involves many atoms,and the phase-plane portrait exaggerates greatly the intrinsic complexity of the object.Second,MOF is intrinsically resolution limited .No object can be reconstructed with features sharper than those allowed by the underlying operator Φ†Φ.Suppose the underlying object is sharply localized:α=1{γ=γ0}.The reconstruction will not be α,but instead Φ†Φα,which,in the overcomplete case,will be spatially spread out.Figure 2.4presents a signal TwinSine consisting of the superposition of two sinusoids that are separated by less than the so-called Rayleigh distance 2π/n .We analyze these in a fourfold overcomplete discrete cosine dictionary.In this case,reconstruction by MOF (Figure 2.4b)is simply convolution with the Dirichlet kernel.The result is the synthesis fromcoefficients with a broad oscillatory appearance,consisting not of twoD o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h pATOMIC DECOMPOSITION BY BASIS PURSUIT137Fig.2.4Analyzing TwinSine with a fourfold overcomplete discrete cosine dictionary.but of many frequencies and giving no visual clue that the object may be synthesized fromtwo frequencies alone.2.3.2.Matching Pursuit.Mallat and Zhang [29]discussed a general method for approximate decomposition (1.2)that addresses the sparsity issue directly.Starting froman initial approxim ation s (0)=0and residual R (0)=s ,it builds up a sequence of sparse approximations stepwise.At stage k ,it identifies the dictionary atomthat best correlates with the residual and then adds to the current approximation a scalar multiple of that atom,so that s (k )=s (k −1)+αk φγk ,where αk = R (k −1),φγk and R (k )=s −s (k ).After m steps,one has a representation of the form(1.2),with residual R =R (m ).Similar algorithms were proposed by Qian and Chen [39]for Gabor dictionaries and by Villemoes [48]for Walsh dictionaries.A similar algorithm was proposed for Gabor dictionaries by Qian and Chen [39].For an earlier instance of a related algorithm,see [5].An intrinsic feature of the algorithmis that when stopped after a few steps,it yields an approximation using only a few atoms.When the dictionary is orthogonal,the method works perfectly.If the object is made up of only m n atoms and the algorithmis run for m steps,it recovers the underlying sparse structure exactly.When the dictionary is not orthogonal,the situation is less clear.Because the algorithmis m yopic,one expects that,in certain cases,it m ight choose wrongly in the first few iterations and end up spending most of its time correcting for any mistakes made in the first few terms.In fact this does seem to happen.To see this,we consider an attempt at superresolution.Figure 2.4a portrays again the signal TwinSine consisting of sinusoids at two closely spaced frequencies.When MP is applied in this case (Figure 2.4c),using the fourfold overcomplete discrete cosine dictionary,the initial frequency selected is in between the two frequencies making up the signal.Because of this mistake,MP is forced to make a series of alternating corrections that suggest a highly complex and organized structure.MPD o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h p138S.S.CHEN,D.L.DONOHO,AND M.A.SAUNDERSFig.2.5Counterexamples for MP.misses entirely the doublet structure.One can certainly say in this case that MP has failed to superresolve.Second,one can give examples of dictionaries and signals where MP is arbitrarily suboptimal in terms of sparsity.While these are somewhat artificial,they have a character not so different fromthe superresolution exam ple.DeVore and Temlyakov’s Example.Vladimir Temlyakov,in a talk at the IEEE Confer-ence on Information Theory and Statistics in October 1994,described an example in which the straightforward greedy algorithmis not sparsity preserving.In our adapta-tion of this example,based on Temlyakov’s joint work with DeVore [12],one constructs a dictionary having n +1atoms.The first n are the Dirac basis;the final atomin-volves a linear combination of the first n with decaying weights.The signal s has an exact decomposition in terms of A atoms,but the greedy algorithm goes on forever,with an error of size O (1/√m )after m steps.We illustrate this decay in Figure 2.5a.For this example we set A =10and choose the signal s t =10−1/2·1{1≤t ≤10}.The dictionary consists of Dirac elements φγ=δγfor 1≤γ≤n andφn +1(t )=c,1≤t ≤10,c/(t −10),10<t ≤n,with c chosen to normalize φn +1to unit norm.Shaobing Chen’s Example.The DeVore–Temlyakov example applies to the original MP algorithmas announced by Mallat and Zhang in 1992.A later refinem ent of the algorithm(see Pati,Rezaiifar,and Krishnaprasad [38]and Davis,Mallat,and Zhang [11])involves an extra step of orthogonalization.One takes all m terms that have entered at stage m and solves the least-squares problemmin (αi )s −m i =1αi φγi2D o w n l o a d e d 08/09/14 t o 58.19.126.38. R e d i s t r i b u t i o n s u b j e c t t o S I A M l i c e n s e o r c o p y r i g h t ; s e e h t t p ://w w w .s i a m .o r g /j o u r n a l s /o j s a .p h p。
Indradrive 系列 故障代码

Error MessagesF9001 Error internal function call.F9002 Error internal RTOS function callF9003 WatchdogF9004 Hardware trapF8000 Fatal hardware errorF8010 Autom. commutation: Max. motion range when moving back F8011 Commutation offset could not be determinedF8012 Autom. commutation: Max. motion rangeF8013 Automatic commutation: Current too lowF8014 Automatic commutation: OvercurrentF8015 Automatic commutation: TimeoutF8016 Automatic commutation: Iteration without resultF8017 Automatic commutation: Incorrect commutation adjustment F8018 Device overtemperature shutdownF8022 Enc. 1: Enc. signals incorr. (can be cleared in ph. 2) F8023 Error mechanical link of encoder or motor connectionF8025 Overvoltage in power sectionF8027 Safe torque off while drive enabledF8028 Overcurrent in power sectionF8030 Safe stop 1 while drive enabledF8042 Encoder 2 error: Signal amplitude incorrectF8057 Device overload shutdownF8060 Overcurrent in power sectionF8064 Interruption of motor phaseF8067 Synchronization PWM-Timer wrongF8069 +/-15Volt DC errorF8070 +24Volt DC errorF8076 Error in error angle loopF8078 Speed loop error.F8079 Velocity limit value exceededF8091 Power section defectiveF8100 Error when initializing the parameter handlingF8102 Error when initializing power sectionF8118 Invalid power section/firmware combinationF8120 Invalid control section/firmware combinationF8122 Control section defectiveF8129 Incorrect optional module firmwareF8130 Firmware of option 2 of safety technology defectiveF8133 Error when checking interrupting circuitsF8134 SBS: Fatal errorF8135 SMD: Velocity exceededF8140 Fatal CCD error.F8201 Safety command for basic initialization incorrectF8203 Safety technology configuration parameter invalidF8813 Connection error mains chokeF8830 Power section errorF8838 Overcurrent external braking resistorF7010 Safely-limited increment exceededF7011 Safely-monitored position, exceeded in pos. DirectionF7012 Safely-monitored position, exceeded in neg. DirectionF7013 Safely-limited speed exceededF7020 Safe maximum speed exceededF7021 Safely-limited position exceededF7030 Position window Safe stop 2 exceededF7031 Incorrect direction of motionF7040 Validation error parameterized - effective thresholdF7041 Actual position value validation errorF7042 Validation error of safe operation modeF7043 Error of output stage interlockF7050 Time for stopping process exceeded8.3.15 F7051 Safely-monitored deceleration exceeded (159)8.4 Travel Range Errors (F6xxx) (161)8.4.1 Behavior in the Case of Travel Range Errors (161)8.4.2 F6010 PLC Runtime Error (162)8.4.3 F6024 Maximum braking time exceeded (163)8.4.4 F6028 Position limit value exceeded (overflow) (164)8.4.5 F6029 Positive position limit exceeded (164)8.4.6 F6030 Negative position limit exceeded (165)8.4.7 F6034 Emergency-Stop (166)8.4.8 F6042 Both travel range limit switches activated (167)8.4.9 F6043 Positive travel range limit switch activated (167)8.4.10 F6044 Negative travel range limit switch activated (168)8.4.11 F6140 CCD slave error (emergency halt) (169)8.5 Interface Errors (F4xxx) (169)8.5.1 Behavior in the Case of Interface Errors (169)8.5.2 F4001 Sync telegram failure (170)8.5.3 F4002 RTD telegram failure (171)8.5.4 F4003 Invalid communication phase shutdown (172)8.5.5 F4004 Error during phase progression (172)8.5.6 F4005 Error during phase regression (173)8.5.7 F4006 Phase switching without ready signal (173)8.5.8 F4009 Bus failure (173)8.5.9 F4012 Incorrect I/O length (175)8.5.10 F4016 PLC double real-time channel failure (176)8.5.11 F4017 S-III: Incorrect sequence during phase switch (176)8.5.12 F4034 Emergency-Stop (177)8.5.13 F4140 CCD communication error (178)8.6 Non-Fatal Safety Technology Errors (F3xxx) (178)8.6.1 Behavior in the Case of Non-Fatal Safety Technology Errors (178)8.6.2 F3111 Refer. missing when selecting safety related end pos (179)8.6.3 F3112 Safe reference missing (179)8.6.4 F3115 Brake check time interval exceeded (181)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand ControlsI Bosch Rexroth AG VII/XXIITable of ContentsPage8.6.5 F3116 Nominal load torque of holding system exceeded (182)8.6.6 F3117 Actual position values validation error (182)8.6.7 F3122 SBS: System error (183)8.6.8 F3123 SBS: Brake check missing (184)8.6.9 F3130 Error when checking input signals (185)8.6.10 F3131 Error when checking acknowledgment signal (185)8.6.11 F3132 Error when checking diagnostic output signal (186)8.6.12 F3133 Error when checking interrupting circuits (187)8.6.13 F3134 Dynamization time interval incorrect (188)8.6.14 F3135 Dynamization pulse width incorrect (189)8.6.15 F3140 Safety parameters validation error (192)8.6.16 F3141 Selection validation error (192)8.6.17 F3142 Activation time of enabling control exceeded (193)8.6.18 F3143 Safety command for clearing errors incorrect (194)8.6.19 F3144 Incorrect safety configuration (195)8.6.20 F3145 Error when unlocking the safety door (196)8.6.21 F3146 System error channel 2 (197)8.6.22 F3147 System error channel 1 (198)8.6.23 F3150 Safety command for system start incorrect (199)8.6.24 F3151 Safety command for system halt incorrect (200)8.6.25 F3152 Incorrect backup of safety technology data (201)8.6.26 F3160 Communication error of safe communication (202)8.7 Non-Fatal Errors (F2xxx) (202)8.7.1 Behavior in the Case of Non-Fatal Errors (202)8.7.2 F2002 Encoder assignment not allowed for synchronization (203)8.7.3 F2003 Motion step skipped (203)8.7.4 F2004 Error in MotionProfile (204)8.7.5 F2005 Cam table invalid (205)8.7.6 F2006 MMC was removed (206)8.7.7 F2007 Switching to non-initialized operation mode (206)8.7.8 F2008 RL The motor type has changed (207)8.7.9 F2009 PL Load parameter default values (208)8.7.10 F2010 Error when initializing digital I/O (-> S-0-0423) (209)8.7.11 F2011 PLC - Error no. 1 (210)8.7.12 F2012 PLC - Error no. 2 (210)8.7.13 F2013 PLC - Error no. 3 (211)8.7.14 F2014 PLC - Error no. 4 (211)8.7.15 F2018 Device overtemperature shutdown (211)8.7.16 F2019 Motor overtemperature shutdown (212)8.7.17 F2021 Motor temperature monitor defective (213)8.7.18 F2022 Device temperature monitor defective (214)8.7.19 F2025 Drive not ready for control (214)8.7.20 F2026 Undervoltage in power section (215)8.7.21 F2027 Excessive oscillation in DC bus (216)8.7.22 F2028 Excessive deviation (216)8.7.23 F2031 Encoder 1 error: Signal amplitude incorrect (217)VIII/XXII Bosch Rexroth AG | Electric Drivesand ControlsRexroth IndraDrive | Troubleshooting GuideTable of ContentsPage8.7.24 F2032 Validation error during commutation fine adjustment (217)8.7.25 F2033 External power supply X10 error (218)8.7.26 F2036 Excessive position feedback difference (219)8.7.27 F2037 Excessive position command difference (220)8.7.28 F2039 Maximum acceleration exceeded (220)8.7.29 F2040 Device overtemperature 2 shutdown (221)8.7.30 F2042 Encoder 2: Encoder signals incorrect (222)8.7.31 F2043 Measuring encoder: Encoder signals incorrect (222)8.7.32 F2044 External power supply X15 error (223)8.7.33 F2048 Low battery voltage (224)8.7.34 F2050 Overflow of target position preset memory (225)8.7.35 F2051 No sequential block in target position preset memory (225)8.7.36 F2053 Incr. encoder emulator: Pulse frequency too high (226)8.7.37 F2054 Incr. encoder emulator: Hardware error (226)8.7.38 F2055 External power supply dig. I/O error (227)8.7.39 F2057 Target position out of travel range (227)8.7.40 F2058 Internal overflow by positioning input (228)8.7.41 F2059 Incorrect command value direction when positioning (229)8.7.42 F2063 Internal overflow master axis generator (230)8.7.43 F2064 Incorrect cmd value direction master axis generator (230)8.7.44 F2067 Synchronization to master communication incorrect (231)8.7.45 F2068 Brake error (231)8.7.46 F2069 Error when releasing the motor holding brake (232)8.7.47 F2074 Actual pos. value 1 outside absolute encoder window (232)8.7.48 F2075 Actual pos. value 2 outside absolute encoder window (233)8.7.49 F2076 Actual pos. value 3 outside absolute encoder window (234)8.7.50 F2077 Current measurement trim wrong (235)8.7.51 F2086 Error supply module (236)8.7.52 F2087 Module group communication error (236)8.7.53 F2100 Incorrect access to command value memory (237)8.7.54 F2101 It was impossible to address MMC (237)8.7.55 F2102 It was impossible to address I2C memory (238)8.7.56 F2103 It was impossible to address EnDat memory (238)8.7.57 F2104 Commutation offset invalid (239)8.7.58 F2105 It was impossible to address Hiperface memory (239)8.7.59 F2110 Error in non-cyclical data communic. of power section (240)8.7.60 F2120 MMC: Defective or missing, replace (240)8.7.61 F2121 MMC: Incorrect data or file, create correctly (241)8.7.62 F2122 MMC: Incorrect IBF file, correct it (241)8.7.63 F2123 Retain data backup impossible (242)8.7.64 F2124 MMC: Saving too slowly, replace (243)8.7.65 F2130 Error comfort control panel (243)8.7.66 F2140 CCD slave error (243)8.7.67 F2150 MLD motion function block error (244)8.7.68 F2174 Loss of motor encoder reference (244)8.7.69 F2175 Loss of optional encoder reference (245)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand Controls| Bosch Rexroth AG IX/XXIITable of ContentsPage8.7.70 F2176 Loss of measuring encoder reference (246)8.7.71 F2177 Modulo limitation error of motor encoder (246)8.7.72 F2178 Modulo limitation error of optional encoder (247)8.7.73 F2179 Modulo limitation error of measuring encoder (247)8.7.74 F2190 Incorrect Ethernet configuration (248)8.7.75 F2260 Command current limit shutoff (249)8.7.76 F2270 Analog input 1 or 2, wire break (249)8.7.77 F2802 PLL is not synchronized (250)8.7.78 F2814 Undervoltage in mains (250)8.7.79 F2815 Overvoltage in mains (251)8.7.80 F2816 Softstart fault power supply unit (251)8.7.81 F2817 Overvoltage in power section (251)8.7.82 F2818 Phase failure (252)8.7.83 F2819 Mains failure (253)8.7.84 F2820 Braking resistor overload (253)8.7.85 F2821 Error in control of braking resistor (254)8.7.86 F2825 Switch-on threshold braking resistor too low (255)8.7.87 F2833 Ground fault in motor line (255)8.7.88 F2834 Contactor control error (256)8.7.89 F2835 Mains contactor wiring error (256)8.7.90 F2836 DC bus balancing monitor error (257)8.7.91 F2837 Contactor monitoring error (257)8.7.92 F2840 Error supply shutdown (257)8.7.93 F2860 Overcurrent in mains-side power section (258)8.7.94 F2890 Invalid device code (259)8.7.95 F2891 Incorrect interrupt timing (259)8.7.96 F2892 Hardware variant not supported (259)8.8 SERCOS Error Codes / Error Messages of Serial Communication (259)9 Warnings (Exxxx) (263)9.1 Fatal Warnings (E8xxx) (263)9.1.1 Behavior in the Case of Fatal Warnings (263)9.1.2 E8025 Overvoltage in power section (263)9.1.3 E8026 Undervoltage in power section (264)9.1.4 E8027 Safe torque off while drive enabled (265)9.1.5 E8028 Overcurrent in power section (265)9.1.6 E8029 Positive position limit exceeded (266)9.1.7 E8030 Negative position limit exceeded (267)9.1.8 E8034 Emergency-Stop (268)9.1.9 E8040 Torque/force actual value limit active (268)9.1.10 E8041 Current limit active (269)9.1.11 E8042 Both travel range limit switches activated (269)9.1.12 E8043 Positive travel range limit switch activated (270)9.1.13 E8044 Negative travel range limit switch activated (271)9.1.14 E8055 Motor overload, current limit active (271)9.1.15 E8057 Device overload, current limit active (272)X/XXII Bosch Rexroth AG | Electric Drivesand ControlsRexroth IndraDrive | Troubleshooting GuideTable of ContentsPage9.1.16 E8058 Drive system not ready for operation (273)9.1.17 E8260 Torque/force command value limit active (273)9.1.18 E8802 PLL is not synchronized (274)9.1.19 E8814 Undervoltage in mains (275)9.1.20 E8815 Overvoltage in mains (275)9.1.21 E8818 Phase failure (276)9.1.22 E8819 Mains failure (276)9.2 Warnings of Category E4xxx (277)9.2.1 E4001 Double MST failure shutdown (277)9.2.2 E4002 Double MDT failure shutdown (278)9.2.3 E4005 No command value input via master communication (279)9.2.4 E4007 SERCOS III: Consumer connection failed (280)9.2.5 E4008 Invalid addressing command value data container A (280)9.2.6 E4009 Invalid addressing actual value data container A (281)9.2.7 E4010 Slave not scanned or address 0 (281)9.2.8 E4012 Maximum number of CCD slaves exceeded (282)9.2.9 E4013 Incorrect CCD addressing (282)9.2.10 E4014 Incorrect phase switch of CCD slaves (283)9.3 Possible Warnings When Operating Safety Technology (E3xxx) (283)9.3.1 Behavior in Case a Safety Technology Warning Occurs (283)9.3.2 E3100 Error when checking input signals (284)9.3.3 E3101 Error when checking acknowledgment signal (284)9.3.4 E3102 Actual position values validation error (285)9.3.5 E3103 Dynamization failed (285)9.3.6 E3104 Safety parameters validation error (286)9.3.7 E3105 Validation error of safe operation mode (286)9.3.8 E3106 System error safety technology (287)9.3.9 E3107 Safe reference missing (287)9.3.10 E3108 Safely-monitored deceleration exceeded (288)9.3.11 E3110 Time interval of forced dynamization exceeded (289)9.3.12 E3115 Prewarning, end of brake check time interval (289)9.3.13 E3116 Nominal load torque of holding system reached (290)9.4 Non-Fatal Warnings (E2xxx) (290)9.4.1 Behavior in Case a Non-Fatal Warning Occurs (290)9.4.2 E2010 Position control with encoder 2 not possible (291)9.4.3 E2011 PLC - Warning no. 1 (291)9.4.4 E2012 PLC - Warning no. 2 (291)9.4.5 E2013 PLC - Warning no. 3 (292)9.4.6 E2014 PLC - Warning no. 4 (292)9.4.7 E2021 Motor temperature outside of measuring range (292)9.4.8 E2026 Undervoltage in power section (293)9.4.9 E2040 Device overtemperature 2 prewarning (294)9.4.10 E2047 Interpolation velocity = 0 (294)9.4.11 E2048 Interpolation acceleration = 0 (295)9.4.12 E2049 Positioning velocity >= limit value (296)9.4.13 E2050 Device overtemp. Prewarning (297)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand Controls| Bosch Rexroth AG XI/XXIITable of ContentsPage9.4.14 E2051 Motor overtemp. prewarning (298)9.4.15 E2053 Target position out of travel range (298)9.4.16 E2054 Not homed (300)9.4.17 E2055 Feedrate override S-0-0108 = 0 (300)9.4.18 E2056 Torque limit = 0 (301)9.4.19 E2058 Selected positioning block has not been programmed (302)9.4.20 E2059 Velocity command value limit active (302)9.4.21 E2061 Device overload prewarning (303)9.4.22 E2063 Velocity command value > limit value (304)9.4.23 E2064 Target position out of num. range (304)9.4.24 E2069 Holding brake torque too low (305)9.4.25 E2070 Acceleration limit active (306)9.4.26 E2074 Encoder 1: Encoder signals disturbed (306)9.4.27 E2075 Encoder 2: Encoder signals disturbed (307)9.4.28 E2076 Measuring encoder: Encoder signals disturbed (308)9.4.29 E2077 Absolute encoder monitoring, motor encoder (encoder alarm) (308)9.4.30 E2078 Absolute encoder monitoring, opt. encoder (encoder alarm) (309)9.4.31 E2079 Absolute enc. monitoring, measuring encoder (encoder alarm) (309)9.4.32 E2086 Prewarning supply module overload (310)9.4.33 E2092 Internal synchronization defective (310)9.4.34 E2100 Positioning velocity of master axis generator too high (311)9.4.35 E2101 Acceleration of master axis generator is zero (312)9.4.36 E2140 CCD error at node (312)9.4.37 E2270 Analog input 1 or 2, wire break (312)9.4.38 E2802 HW control of braking resistor (313)9.4.39 E2810 Drive system not ready for operation (314)9.4.40 E2814 Undervoltage in mains (314)9.4.41 E2816 Undervoltage in power section (314)9.4.42 E2818 Phase failure (315)9.4.43 E2819 Mains failure (315)9.4.44 E2820 Braking resistor overload prewarning (316)9.4.45 E2829 Not ready for power on (316)。
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
诺西

没有功能解析:传真 T61或者T62数据通信:BS21-BS26< ZMIO:IMSI=460023028050026;LOADING PROGRAM VERSION 9.24-1HLRi CDHR16 2008-07-31 14:37:19SUBSCRIBER INFORMATION:INTERNATIONAL MOBILE SUBSCRIBER IDENTITY (460023028050026)MOBILE STATION ISDN NUMBER (8615002801040)ATTACHED IMSI ..............................MOBILE STATION CATEGORY .................... OR //pr vip优先接入ROUTING CATEGORY ........................... NADDITIONAL ROUTING CATEGORY ................ NSERVICE AREA OF MSISDN ..................... NAT //国内漫游 *ALL 国际漫游 ACTIVATION STATUS .......................... DVLR-ADDRESS ................................ 交换机地址SIGNALLING POINT CODE (00000000)MSC-ADDRESS ................................ 交换机地址交换机地址PRIMARY BASIC SERVICE CODE ................. T11语音业务PRIMARY BASIC SERVICE CODE INDEX ........... 000 ---国际漫游不可少ROAMING PROFILE INDEX ...................... N N(National)表示国内漫游 21 ORIGINATING CCBS ........................... NTERMINATING CCBS ........................... NFRAUD PROFILE .............................. N 诺西HLR :CALLING LINE IDENTIFICATION ENHANCEMENT .... NCOMMON MSISDN NUMBER ....................... N MSO : IMSI=X OVERRIDE COMMON CLI PARAMETERS ............. NCMSISDN IS HUNTING GROUP NUMBER ............ N CLIP= Y DENY DIRECT CALLS .......................... N CLIP=NDENY USSD WITH MEMBER NUMBER ............... N CLIR=PERM 已 DENY DIRECT SMS ............................ N CLIR=PCBNCLIR=N ZONE CODES: CW=Y,HOLD=MPTY=N 三MSC AREA RESTRICTED ........................ NHLRU IDENTITY (3)EMLPP MAXIMUM ENTITLED PRIORITY ............ NEMLPP DEFAULT PRIORITY ..................... NHOME COUNTRY CODE .......................... NNETWORK DESTINATION CODE ................... NROAMING TO UTRAN RESTRICTED ................ N 接入方式ROAMING TO GERAN RESTRICTED ................ NCOMMAND EXECUTED~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~HOME SUBSCRIBER IDENTIFICATION HANDLING COMMAND <MI_>< ZMBO:IMSI=460023028050026;LOADING PROGRAM VERSION 7.1-0HLRi CDHR16 2008-07-31 14:37:19BASIC SERVICE DATA:INTERNATIONAL MOBILE SUBSCRIBER IDENTITY (460023028050026)MOBILE STATION ISDN NUMBER (8615002801040)BASIC SERVICE .............................. T11,000 语音通话服务。
ST原厂内部指令资料

DIAGNOSTIC COMMANDS Compatible with Drives with >64k CylindersJanuary 13, 2003SERIAL PORT INPUT PARAMETER REPRESENTATIONCommand parameters in this document are represented with single letters, separated by commas.e.g. Sx,y,z - This signifies a serial port command, “S”, that takes in three parameters. Exception: When one parameter is used to input two different values to the command, field width of each parameter will be shown.e.g. Dxxyy – This signifies a serial port command, “D”, that takes in one parameter. Thehigh byte of this parameter (xx) is used to pass one value to the command and the lowbyte (yy) is used to pass a second value to the command.The serial port will accept a max of up to one word (ffffh) for each parameter. For drives with greater than 64k cylinders, the serial port will accept up to a double word (ffff ffffh) for each parameter. S ee the appropriate command description to determine the valid size of a particular parameter.Unless otherwise noted, leading zeros are NOT required.SERIAL PORT OUTPUT DISPLAY REPRESENTATIONOutput display values in this document are represented with either letters or numbers and will show exact field width to aid in the creation and maintenance of serial port parsing software.e.g.When the log is displayed the output to the screen is formatted as shown below.(Log Type 2) (Log Type 4)___x_______Head___x_______Headvv wwww.xxx yyy zz vv wwww.xxx yyy zzwhere wwww is physical cylinder where wwww is physical cylinderLog format for drives with >64k cylinders:(Log Type 2) (Log Type 4)___Head___x_________x_________Headvv wwwww.xxx yyy zz vv wwwww.xxx yyy zzwhere wwwww is physical cylinder where wwwww is physical cylinderor output formatted as follows:Zone0:0006-0B4F800389.020Output format for drives with >64k cylinders:Zone00:0CC84-0DE36884414.1017TABLE OF CONTENTSON-LINE COMMANDS (10)I NTERFACE-S PECIFIC C OMMANDS (10)^E Interface State: Error codes, Max C.H.S, Current transfer mode settings (10)^F Read Segment Record(s) (10)^G Write Queue (10)^I Controller Register Dump (10)^K Niwot RdWr State (10)^Q Resume after ^S (age 50 only) (10)^S Pause intf task and swap to diag monitor (10)^U Currently unused (10)^V Interface Command Echo and Activity Trace Toggle (10)^X Interface and Niwot Command History (10)^Y Display Raw SMART DST Values (for Serial Port running of DST) (10)‘~’Interface Command State (10)G ENERAL C OMMANDS (10)^A Send Certification Code Rev (10)^B(Reserved for Servo Use) (10)^C Firmware Reset (10)^D, ^N Retry Activity Display Toggle. (See Appendix B. for Retry Display Characters.) (10)^L Display Sign-on Message, including firmware version. ** (10)^O, ^]Advance Servo Tracing (10)^P Power Chop enable/disable toggle (11)^Q Cert Display Debug enable/disable toggle ( not age 50 ) (11)^R Restart the Diagnostic Monitor, load overlay from disc (11)^T Restart testing at the current age (11)^W Read/Write statistics gathering enable/disable toggle (11)^Z Restart the Diagnostic Monitor, do not load overlay from disc (11)!Display Current R/W Channel Settings (11)%Show Mux Status. ** (See Appendix B for Description) (11)‘Display Transfer Status (See Appendix B Description) (11).Display Active Status. ** (See Appendix B for Description) (11);Display Machine Status. ** (See Appendix B for Description) (11)<Decrement read/write scope synchronization pulse position (11)>Increment read/write scope synchronization pulse position (11)?Show Buffer Allocation. ** (See Appendix B for Description) (11)^Show Elapsed Time since start of cert test or last ^Z (11)`Show Read/Write Statistics. (See Appendix B for Description) (11){(Reserved for Servo Diagnostic Use) (11)}(Reserved for Servo Diagnostic Use) (11)ESC Interrupt Loop, Batch file or SeaDex script execution (11)COMMON COMMANDS: (AVAILABLE FROM ALL LEVELS EXCEPT LEVEL 8).12 /x Change Level to Diagnostic Monitor Level x (12)CR Loop Break (12)*Special Function for batch file: (12)@x Batch File Label (12)|Batch file terminator (12)+x,y Peek Byte. Display the byte data content of the specified memory address: (12)=x,y,z Poke Byte. Replace the contents of the specified address with the specified data (12)-x,y Peek Word. Display the word contents of the specified address (12)A x,y,z Set Test Space (13)L x,y Loop. Causes the next command to repeat execution, subject to controls specified by x: (13)LEVEL T COMMANDS: CERT PROCESS / TEST (14)A Enable/Disable throttling of drive messaging (14)B x,y Set Baud Rate (14)*** C,,z Reset Certification Test. (available only when overlay is valid) (14)*** D x,y,z Display Cert Logs sequentially from Log x. (available only when overlay is valid) (14)E x,y,z Display/Edit Cert Log(s) (14)F Set Stuff 14*** H x,y,z Display/Reset Health Status Bits. (available only when overlay is valid) (15)*** I,y,z Initialize System Region. (available only when overlay and cert table are valid) (15)J x,y Set Scope Sync from Cert Log entries: (15)K Download Congen file (15)N x,y,z Set Drive Age to x (15)R Read System Sector into System RAM (15)S Check User Slip List for empty or unordered slip list (15)T x Run Factory Test x (15)*** V x,y Display Defect List(s) to screen and add to active log (15)W x,y,z Save System RAM into System Sector (15)Y x,y Set Drive Type (16)a Drive messaging pause toggle switch (16)b,,z Initialize the overlay area of the disc (16)c Write overlays to the disc (16)d x,y,z Download Cert Code (for automated use only) (16)e x,y Download overlay (for automated use only) (16)f Burn new serial flash code that is already downloaded to the buffer and transition to it (16)g x,y,z Call overlay function (16)h Download cert table (for automated use only) (17)*** i x,y,z Initialize/Reset Defect List(s) (available only when overlay is valid) (17)*** j Download SeaDex script (for automated use only) (available only when overlay is valid) (17)k x,y,z Initialize what head to depop (17)*** l x Initialize and write zone buffers in the overlay to RAM (17)*** m,,z Defect Map System Area (available only when overlay is valid) (17)r Reload Cert from Disc and report version number (17)*** s x,y,z Save Defect List(s) (available only when overlay is valid) (17)w x,y Write (Save) Overlay code to Disc (for automated use only) (18)*** x ll,ss,nn Page Log To Host (available only when overlay is valid) (18)#,,z Enter HDA Serial Number (18)$Enter PCBA Serial Number (18)[x,y ASCII Log Control: (18)LEVEL ONE COMMANDS: MEMORY MANIPULATION COMMANDS (19)B x,y Buffer Display (19)D x,y,z Display Memory (19)F Enable Forced Write Bit (19)M Show Flash ROM Information (19)N x,y,z SMART Serial Port Control (19)P Display PCBA Information (19)S x,y,z Edit Memory Byte (20)U x,y,z Edit Buffer Byte (20)*** Y x Converts desired cylinder number to gray code and display the result (20)*** c x,y,z Compare Buffers (available only when overlay is valid) (20)d x Clear overlay code from disc (for automated use only) (20)m x,y,z Edit memory word. Operates same as level 1 ‘S’ command, except operates on words (20)r Read cert code from disc (20)s Send Drive Information (20)t Read cert table from disc (20)u Read SeaDex script from disc (20)*** y x Converts desired gray code to a cylinder number and displays the result (20)LEVEL TWO COMMANDS: NIWOT READ/WRITE COMMANDS (21)B x,y Display Buffer (21)C x,y,z Copy Buffers (21)E x,y,z Display/Edit Cert Log(s) (21)F x,y,z,a Modify Track Defect List (21)G x,y,z,a,b,c MRT Test (available only when overlay is valid) (22)H x Select Head (23)I x,y,z Display/Modify Adaptive Settings (23)J x,y Scope Sync from Log (23)K x,y Set Tracking Offset (23)M x,y,z,w Quick Margin Test (23)N x Adaptive Test for all Heads in Specified Zone (23)O x,y,z Seek-Seek on current head: (23)P x,y,zzww Set Buffer Pattern: (23)Q x,y,,a Write/Read/Read Data (23)R x,y,z,a Read Data (24)S x,y,z Seek Cyl/Head (24)*** T x,y,z Measure Throughput. (available only when overlay is valid) (24)U x,y Spin-Up (25)*** V x,y,z Read/Compare against corresponding write buffer (25)W x,y,z,a Write Data (25)*** X x,y,z Display Data IDs on current track. (available only when overlay is valid) (25)Y x,y,zzaa,b Show/Set Retry Controls (26)Z Spin-Down (26)*** c x,y,z Compare Buffers (available only when overlay is valid) (26)*** d x,y,z,a R e-assign Errors from Log. (available only when overlay is valid) (26)*** e x,y Save Log to Cert Log y. (available only when overlay is valid) (26)*** f x,y,z Wedge Defect Map Current Track(available only when overlay is valid) (26)*** g x,y Slip Servo Wedge (available only when overlay is valid) (27)*** h x Translate Physical sector to Logical sector (27)*** i x,y Show Track Defect List in Active Log (27)*** j,y Read Wedge (27)*** l x Translate Logical sector to Physical sector (27)p x Full Pack Read Or Write (available only when overlay is valid) (28)r x,y,z,a Read Long from current track (28)s x,y,z Seek to Physical Cyl/Head (29)*** t c,hhss,o Translate Physical Cylinder, Servo Sector, Byte offset to LPL (29)u x,y,z Enable display of channel and preamp registers during retry (29)w x Write Long to current track (29)x Show Zone Boundaries and system cylinders as well as the last LBA of the drive (31)y x,z Set Direct Write Mode (31)*** z,y Write Wedge (31)LEVEL THREE COMMANDS: SERVO SEEKING COMMANDS (33)C x,y Acceleration Constant Measurement Test (33)D x,y,z,a,b,c Seek Access Times (33)E x,y,z Display/Edit Certification Test Log(s) (33)*** G x Translate Hex Cylinder to Gray Code (available only when overlay is valid) (33)H x Head Select (33)*** J x Head Switch Offsets (available only when overlay is valid) (33)*** M x,y Actuator Open-loop Move (available only when overlay is valid) (33)O x,y,z Seek-Seek on current head: (33)P x,y,z Position Error Display (33)Q xx,yy Certification Write/Read (34)*** R x,y,z Read Grey Code (available only when overlay is valid) (34)S x,y,z Seek Cyl/Head (34)T Servo Transducer Calibrations (34)U x Spin-Up 34V x,y,z Read GC123 registers (available only when overlay is valid) (34)*** W Read physical Grey Code (available only when overlay is valid) (34)*** Y Hysteresis (available only when overlay is valid) (34)Z Spin-Down (34)*** c Test Air Latch Closed (available only when overlay is valid) (34)*** g x Translate Gray to Hex (available only when overlay is valid) (34)j x,y,z Ramp Test. (Ramp Load drives only – currently Saturn) (35)k Measure Head Position (35)*** m Servo Actuator Geometry Test for MDW (available only when overlay is valid) (35)*** o Test Air Latch Open (available only when overlay is valid) (35)*** p x,y Translate Physical sector to Logical sector. (available only when overlay is valid) (35)*** q x,y Translate Logical sector to Physical sector. (available only when overlay is valid) (35)s x,y,z Seek to Physical Cyl/Head (35)LEVEL FOUR COMMANDS: SERVO TRACKING COMMANDS (36)C xxyy,z,a,b Tracking Test. (available only when overlay is valid) (36)D x,y,z,a,b,c Seek Access Times (36)E x,y,z Display Active Log (36)*** G x Set Tracking/Seek Gain (available only when overlay is valid) (36)H x Select Head x (36)*** I x,y,z Head Stability Test for Heads (default is All Heads) (available only when overlay is valid) (36)K x Servo Offset (37)*** M x,y Actuator Open-loop Move (available only when overlay is valid) (37)N x Napa Servo Adaptive Test for all Heads in Specified Zone (37)O Show MR Head Offset (for current head) (37)P x,y,z Position Error Display for current track (37)S x,y,z Seek Cyl/Head (37)T x,y,z Napa Servo Adaptive Test at the Specified Track (37)*** W Read physical Grey Code (available only when overlay is valid) (37)X x Display 1 rev of servo burst information for current track (37)*** Z x Zap Servo Burst x of the current track. (available only when overlay is valid) (37)*** a Slip error code 90's from the log (available only when overlay is valid) (37)*** c x Track 0 Cal for MDW (available only when overlay is valid) (38)d x Disable/Enable servo from using the ZAP coefficients in the ZAP table (38)*** f Fill Skipped Cylinders (NOT IMPLEMENTED) (available only when overlay is valid) (38)i x Enable/disable ZAP reads (available only when overlay is valid) (38)j,x Adaptive Coherent Feedforward Compensator (ACFC) calibration (MDW only) (38)k Skip MDW serial number cylinders (available only when overlay is valid) (MDW only) (38)l xx Will scan the current position for servo defects and zap the track (38)*** m RRO ZAP System cylinders (available only when overlay is valid) (38)n y,,x Calculate the zap coefficients at the current position (38)p x,y,z Display Spin Error (39)*** q x Change Spin Speed (available only when overlay is valid) (39)r x Reads and displays the specific Track ID contents (39)***s x,y,z Show error count for given log (available only when overlay is valid) (39)t x,y Modifies and views the ZAP RAM table (39)v x,y,z,a ButterFlySeekTest (39)w x Writes the ZAP values in the ZAP RAM table to the Track Ids of the current track (39)x c,,z Skip Cylinder (40)y Show Skipped Cylinders (40)z c,,z Unskip Skipped Cylinder(s) (40)LEVEL SIX COMMANDS: BATCH FILE COMMANDS (41)B x Run Batch File (41)D x List Batch File (41)E x Enter Batch File (41)*Special Function for batch file: (41)@x Batch File Label (41)|Batch file terminator (41)LEVEL SEVEN COMMANDS: READ CHANNEL ADAPTIVE COMMANDS (42)B x,y Display Buffer (42)C x,y,z Copy Buffers (42)D x Display Temperature Diode Values (42)E x,y Display Log(s) (42)F x,y Format Sector/Track (42)G x,y,z Toggle ECC Seed Finder tool (42)H x Select Head x (42)I x,y,z,a Display/Modify Adaptive Settings for the Current Head (42)M x,y,z Napa Single Adaptive Parameter Test (42)N x Napa Data Adaptive Test for all Heads in Specified Zone (43)O h,z, s Read/Write Coarse Offset Calibration (43)P x,y,zzww Set Buffer Pattern: (44)Q x,y Write/Read/Read Data (44)R x,y Read Data (44)S x,y,z Seek Cyl/Head (44)T x,y,z Napa Data Adaptive Test at the Specified Track (44)U x,y Spin-Up (44)V f Set MR Head Read Bias Current for all Heads (44)W x,y Write Data (44)Y x,y,zzaa,b Show/Set Retry Controls (44)Z Spin Down Command (45)a x,y,z MR Bias Backoff (45)b x,y PE and OTC measurements (45)c x,y,z Generate OTC bath tubs by sector (47)d x,y,f Reset Adaptives to the Default Settings (47)e Show diagnostic error counter in the Valiant (DIAGERRCNT) (47)f f Shows the number of TAs/ data retries done (47)g xxxx,yyyy,zz Does Error Rate by sector command (47)i x Issue read / write command (use after p) (47)j Ramp unload without spin-down (Ramp drives only – currently Saturn) (47)n Run the read channel noise calibration at the current track (47)o x,y,z OTC command (48)p Set parameters for Read / Write operation (precedes i command) (48)r Read Adaptives from the System Sectors (48)s xy,z,a Send Byte to Read Channel or Preamp (48)t x,z Get Data from Read Channel or Preamp (48)u Write Unsafe Enable Toggle (48)v,f VCO calibration / display (48)w x,y,z Save System RAM into System Sector (48)x Show Zone Boundaries (49)y x,z Set Direct Write Mode (49)z Toggle Data Randomizer (49)7x,y,z Generate 747 curve (49)9x,y,z Adapt Write Delay (50)LEVEL EIGHT COMMANDS: SERVO TRACK WRITER COMMANDS (53)A Abort any pending servo diagnostic command (53)B Set the read head bias to the serial preamp (53)C x,y,z Execute the servo diagnostic sub commands (53)D Dump Drive Configuration (55)E Lock Spindle Motor (56)F Write Pack-writer Auto Stamp (56)G x Set Spin Gain (56)H x Select head directly (57)I x Push-Inward Actuator (57)J x Spin Speed Adjust (57)K x Added track offset in track follow state (57)Lx Load Head Mask (57)M Increment Head (current head + 1) (57)N Report Logical Spin State (57)O x Message Display (57)P x Push-Out Actuator (57)Q x Read channel (57)R x Read Gray Code (57)S x,y,z Seek Cyl/Head (58)U x Spin-Up Motor (58)Vx Spin-Up 58W x Set Write Current (58)Z Spin-Down (58)c Crash test the Actuator/Crashstops/HDA (58)fx,y Set bank write mode (58)g IMRON signal polarity (58)LEVEL A COMMANDS: NIWOT READ/WRITE LBA COMMANDS(FULLSLIP) (59)C x,y Convert LBA to LPL and display to screen (59)D x,y Convert LBA to PCHS and display to screen (59)E x,y Display Log(s) (59)M x,y Set GrandB Test ports (59)Q,x Write/Read/Read LBA (59)R,x Read LBA Command (59)S x,y,z Seek LBA Command (59)W,x Write LBA Command (59)Y x,y,za Show/Set Retry Controls (59)c x,y,z Convert LPL to LBA and display to screen (59)d x,y,z Convert PCHS to LBA and display to screen (59)l x,y,z Display # of unslipped sectors for LPL to screen (60)LEVEL C COMMANDS: CERT DIAGNOSTIC CTS COMMANDS (61)D Display the Cert Test sequence (61)F vvww,x,yyzz Run Cert CTS Test F with input parameters (61)***P Load Buffers 10-1A with NAPA specific 127 bit pattern, load buffers 1B-1F with 0’s (available only when overlay is valid) (61)***l xxxxx,yPerform Lazy Write / On-Track-Erasure Screen. (available only when overlay is valid) (61)*** p xx,yy Parse Cert Log for Errors by Head (available only when overlay is valid) (62)*** s x,y,z,a CTSSpinUpandDn (available only when overlay is valid) (63)LEVEL D COMMANDS: SEADEX COMMANDS (64)E x,y,z Display SeaDex Log, level-T E-command style (64)I x SeaDex Information tables (64)S x Single Step SeaDex script (64)T x,y,...SeaDex Test Step. (64)b x,y,z Script assembly Breakpoint (65)c x SeaDex Checkpoint (65)l x,y Display SeaDex Log (65)p x Display SeaDex Tune Parameter (65)s x,y Set or Display SeaDex System Variable (65)t x SeaDex Trace Levels (66)v Verify SeaDex Script (66)w x,y,z,a Set or Display SeaDex Word (67)LEVEL E COMMANDS:DRIVE ZONE AND FORMAT COMMANDS (68)a x,y Displays / modifies drive zone parameters. (available only when overlay is valid) (68)b x,y,z Displays / modifies frame format information. (available only when overlay is valid) (69)BOOT CODE DIAGNOSTIC COMMANDS (70)ONLINE COMMANDS, BOOT CODE (70)^D, ^N Retry Activity Display Toggle. ** (See Appendix B. for Retry Display Characters.) (70)^L Display Sign-on Message, including firmware version (70)^O, ^]Advance Servo Tracing (70)^Z Restart the Diagnostic Monitor, do not load overlay from disk (70)!Display Current R/W Channel Settings (70)%Show Mux Status. ** (See Appendix B for Description) (70)‘Display Transfer Status (See Appendix B Description) (70).Display Active Status. ** (See Appendix B for Description) (70);Display Machine Status. ** (See Appendix B for Description) (70)<Decrement read/write scope synchronization pulse position (70)>Increment read/write scope synchronization pulse position (70)LEVEL F COMMANDS:LIMITED BOOT CODE DEBUG SUPPORT (71)+x,y Peek Byte. Display the byte data content of the specified memory address: (71)=x,y,z,w Poke memory. Replace the contents of the specified address with the specified data (71)-x,y Peek Word. Display the word contents of the specified address (71)B x,y Display Buffer (71)C x,y,z Copy Buffers (71)D x,y,z Display Memory (71)P x,y,zzww Set Buffer Pattern: (71)R x Read system sectors information (72)U x Spin-Up 72Z Spin-Down (72)b x,y Set Baud Rate (72)d x,y Download code, used in conjunction with SDLD (72)e x,y,z,w Serial flash access routines (73)r,y,z Reserve tracks read (73)s x Seek to Physical Cyl (FULLSLIP) (73)t x,y,z Write to serial device (73)APPENDIX A: ERROR CODES (74)APPENDIX B: SPECIAL AND RETRY DISPLAY CHARACTERS (75)APPENDIX C: ONLINE COMMAND DISPLAY DESCRIPTIONS (76)S TATISTICS D ISPLAY D ESCRIPTION(`) (76)M UX S TATUS D ISPLAY D ESCRIPTION(%) (78)T RANSFER S TATUS D ISPLAY D ESCRIPTION(‘) (79)A CTIVE S TATUS D ISPLAY D ESCRIPTION(.) (81)M ACHINE S TATUS D ISPLAY D ESCRIPTION(;) (82)B UFFER A LLOCATION D ISPLAY D ESCRIPTION(?) (83)H EALTH B ITS D EFINITIONS: (84)E RROR L OG D ISPLAY (85)Header Format: (85)Defect List Format: (85)ON-LINE COMMANDSThe On-Line commands may be initiated at any time. For the Interface-specific commands, the Interface code must be present in the current memory map for successful execution; the General commands are always avail-able.Interface-Specific CommandsCommand Description(AT)^E Interface State: Error codes, Max C.H.S, Current transfer mode settings^F Read Segment Record(s)Queue^G Write^I Controller Register Dump^K Niwot RdWr State^Q Resume after ^S (age 50 only)^S Pause intf task and swap to diag monitorunused^U Currently^V Interface Command Echo and Activity Trace Toggle^X Interface and Niwot Command History^Y Display Raw SMART DST Values (for Serial Port running of DST)‘~’ Interface Command StateGeneral CommandsCommand Description^A Send Certification Code Rev^B(Reserved for Servo Use)Reset^C Firmware^D, ^N Retry Activity Display Toggle. (See Appendix B. for Retry Display Characters.)^L Display Sign-on Message, including firmware version. **^O, ^] Advance Servo TracingOnline General Commands (Continued)Command Description^P Power Chop enable/disable toggle.^Q Cert Display Debug enable/disable toggle ( not age 50 )^R Restart the Diagnostic Monitor, load overlay from disc.^T Restart testing at the current age.^W Read/Write statistics gathering enable/disable toggle.^Z Restart the Diagnostic Monitor, do not load overlay from disc!Display Current R/W Channel Settings% Show Mux Status. ** (See Appendix B for Description)‘ Display Transfer Status (See Appendix B Description). Display Active Status. ** (See Appendix B for Description); Display Machine Status. ** (See Appendix B for Description)< Decrement read/write scope synchronization pulse position.>Increment read/write scope synchronization pulse position.? Show Buffer Allocation. ** (See Appendix B for Description)^Show Elapsed Time since start of cert test or last ^Z.`Show Read/Write Statistics. (See Appendix B for Description){ (Reserved for Servo Diagnostic Use)} (Reserved for Servo Diagnostic Use)ESC Interrupt Loop, Batch file or SeaDex script execution.** - Standardized and documented in Test Engineering’s Internal Reference Manual, “Microcode Command Set”.COMMON COMMANDS: (Available from All Levels except Level 8) The Common Commands may be executed whenever the diagnostic monitor prompt is present and the monitor is waiting for a command request, except at level 8. The level 8 commands take precedence over the com-mon commands.Command Description/x Change Level to Diagnostic Monitor Level x.Break.CR Loop* Special Function for batch file:*1 Pause batch file execution until input*2,x Delay x milliseconds*3,x Branch to Label x*4,x Increment head and branch to Label x*5 Clear monitor screen*6 Stop on error*7,x Load batch loop counter with x.*8,x Decrement batch loop counter, Branch to Label x if 0.@x Batch File Label.During batch file entry, define this location as Label x.x - Single digit numeric label specification.|Batch file terminatorTerminates the entry of batch files.+x,y Peek Byte. Display the byte data content of the specified memory address:x - upper bits of a greater-than-16 bit addressy - lower 16 bits of a greater-than-16 bit address or the 16 bit address=x,y,z Poke Byte. Replace the contents of the specified address with the specified data.x - upper bits of a greater-than-16 bit addressy - lower 16 bits of a greater-than-16 bit address or the 16 bit addressz - byte data content to be written at the specified address.-x,y Peek Word. Display the word contents of the specified address.x - upper bits of >16 bit addressy - lower 16 bits of >16 bit address or the 16 bit addressCommon Commands (Continued)Command DescriptionA x,y,z Set Test Space x Bit Meanings:Bit # If x = 1 If x = 07 Random Data Existing Buffer Data6 Sequential Out Sequential In5 Odd Cylinders All Cylinders4 Even Cylinders All Cylinders3 (unspecified) (unspecified)2 Random Cylinder/Head Sequential Cylinder/Head1 All Cylinders Current Cylinder0 All Heads Current HeadSpecial ValuesA8,y Set Minimum Cylinder to y >64k cyl compatible* A9,y Set Maximum Cylinder to y >64k cyl compatible* AA,y Set Maximum Head to yAD Set Mins/Maxs to DefaultsA87 Sets random data, random cylinder, random head, all cyls & hds AC7 Randomly select 80% Sequential In, 20% Random addresses IF (Random_Start = TRUEA,,z Select Random start and lengthBit0 set = random start sectorBit1 set = random lengthBit0 set = Display aboveL x,y Loop. Causes the next command to repeat execution, subject to controls specified by x: x Bit Meanings:Bit # If = 1 If = 07 Looping active (internal use) Looping not active (internal use)6 Looping primed (internal use) Looping not primed (internal use)5 Stop on Error Code = y Do Loop Count (y<>0)4 Inhibit Error Message on error Display Error Message on error3 (unspecified) (unspecified)2 Spin Down on Error Remain spinning on error1 Stop on No Error0 Continue on error Stop on errory: Error Code to stop on (if Stop on Error Code is enabled.)Loop Count (default is forever.)* Will accept up to 8 digits for drives with >64k cylindersLEVEL T COMMANDS: Cert Process / TestCommand DescriptionA Enable/Disable throttling of drive messaging.Toggles the state of the drive messaging toggling. Power-up state is throttled - oncebuffer is full, drive messaging system will wait for characters to be transmittedbefore processing further output informationB x,y Set Baud Ratex = 0 Set baud rate to POR default, typically 9600x = 1 Display supported baud rates in the format: =xxxxx > 1 Set supported baud rateTypical baud rates (xxxx leading zeros may be omitted)ratex baud1228 1,228,000921,000921625 625,000460,000460230 230,000115,00011557,60057619,20019296 9,60048 4,80024 2,400y - if entered y contains the delay time in milliseconds. Default isdo not wait for host to return CR, just set new baud rate. If y is enteredthe code will check every millisecond up to y milliseconds for a carriagereturn to be sent back from the host at the new baud rate. If no CR is seen thedrive will default back to 9600 baud.*** C,,z Reset Certification Test. (available only when overlay is valid)Resets health bits and sets age to 1. Clears Scratch Fill Done flag.z - if z = 22h then reset certification test.- if z <> 22 then ignore this command.*** D x,y,z Display Cert Logs sequentially from Log x. (available only when overlay is valid)x - Log to start sequential display; if blank, display only logs of failed tests.y - Displays only log entries with this error codez - Special function:= 40 - Enable fast dump capability for data cataloger capture. Inhibits time delaybetween log dumps and enables fast, unformatted log dump.E x,y,z Display/Edit Cert Log(s)See /2 E for further detail.StuffF SetThe Set Stuff data may be up to 512 characters long. The Set Stuff data format is de-fined by the Seagate-Longmont ATA Vendor Specific Stuff document.。
python 稀疏矩阵 余弦相似度计算

标题:Python在稀疏矩阵中计算余弦相似度的方法在日常的数据分析和机器学习任务中,我们经常需要计算向量之间的相似度。
而在稀疏矩阵中,由于其大部分元素都是零,传统的向量相似度计算方法并不适用。
在这种情况下,我们可以利用余弦相似度来衡量向量之间的相似程度。
本文将介绍如何使用Python在稀疏矩阵中计算余弦相似度的方法。
1. 何为稀疏矩阵?稀疏矩阵是指大部分元素为零的矩阵。
在实际的数据中,很多情况下我们会遇到这种稀疏性很高的矩阵。
在自然语言处理中的文本数据、推荐系统中的用户-物品评分矩阵等都可以看作是稀疏矩阵。
由于其大部分元素为零,因此传统的计算方法在稀疏矩阵上表现并不理想。
2. 余弦相似度计算余弦相似度是一种衡量两个向量方向相似程度的指标,其计算方法如下:\[ \cos(\theta) = \frac{\textbf{A} \cdot\textbf{B}}{\|\textbf{A}\|\|\textbf{B}\|} \]其中,A、B为两个向量,\(\cdot\)代表向量的点积,\(\|\cdot\|\)表示向量的模长。
余弦相似度的取值范围在[-1, 1]之间,值越接近1表示两个向量越相似,值越接近-1表示两个向量方向越相反,值为0表示两个向量方向正交。
3. 使用Python计算稀疏矩阵的余弦相似度在Python中,我们可以使用scipy库来处理稀疏矩阵,并且计算余弦相似度。
我们需要导入相应的库:```pythonimport scipyimport numpy as npfrom scipy.sparse import csr_matrix```我们可以利用csr_matrix函数将普通的稀疏矩阵表示转换为压缩稀疏行矩阵(Compressed Sparse Row matrix,CSR)的表示形式:```pythonA = csr_matrix(A)B = csr_matrix(B)```接下来,我们可以使用scipy库中的cosine_similarity函数来计算稀疏矩阵的余弦相似度:```pythonfrom sklearn.metrics.pairwise import cosine_similarity similarity_matrix = cosine_similarity(A, B)```这样,我们就可以得到稀疏矩阵A和B之间的余弦相似度矩阵了。
IBM Cognos 软件开发工具包版本 11.0.0 混搭服务开发人员指南说明书

Java samples..............................................................................................................................................11 Java sample file locations.................................................................................................................... 11 Running the Java samples................................................................................................................... 12
Chapter 2. Overview of the Mashup Service............................................................ 7
Programming interfaces...............................................................................................................................7 Identifying reports....................................................................................................................................... 8 Output formats.............................................................................................................................................9 Sample programs.......................................................................................................................................10
PCV-2V压力释放阀,直接操作手动可调说明书

w e e n g i n e e r y o u r p r o g r e s sTable of Contents1 Product Details .....................................................................................................................................................................................2 1.1 Application ............................................................................................................................................................................................. 2 1.2 Recommended Installation .................................................................................................................................................................... 2 2 Function ................................................................................................................................................................................................ 2 2.1 Features ................................................................................................................................................................................................. 23 Technical Data ...................................................................................................................................................................................... 34 Ordering Information ........................................................................................................................................................................... 3 4.1 Type Code ............................................................................................................................................................................................. 3 4.2Versions currently available (3)5 Description of Characterisics in Accordance with Type Code ........................................................................................................ 4 5.1 Characteristic 1: Variant DSU ................................................................................................................................................................ 4 5.2 Characteristic 2: Port / Case: Variant CA - Cartridge ............................................................................................................................. 4 5.3 Characteristic 3: input flow rate .............................................................................................................................................................. 4 5.4 Characteristic 4: Max.permissible pressure ........................................................................................................................................... 4 5.5 Characteristic 5: Activation / Setting ...................................................................................................................................................... 4 5.6 Characteristic 6: Stepped cavity 8.00239 (corresponds to Bucher UVP- 4) ......................................................................................... 4 Das vorgesteuerte Druckbegrenzungsventil ist ein Cartridgebauteil und wird in eine Stufenbohrung entsprechend nebenstehender Zeichnung eingeschraubt. ..................................................................................................................................................................................................... 4 5.7 Characteristic 7: Seal ............................................................................................................................................................................. 4 6 Installation ............................................................................................................................................................................................ 5 6.1 General information ............................................................................................................................................................................... 5 6.2 Connection Recommendations .............................................................................................................................................................. 5 6.3 Installation - installation space ............................................................................................................................................................... 5 7 Notes, Standards and Safety Instructions ......................................................................................................................................... 5 7.1 General Instructions ............................................................................................................................................................................... 5 7.2 Standards ............................................................................................................................................................................................... 58 Zubehör .................................................................................................................................................................................................5w e e n g i n e e r y o u r p r o g r e s s1The pressure valve is designed as cartridge valve. It is a direct operated valve for flow rates up to 10 l / min, which can be adjusted manually. The adjustment can be protected by a cap. The components are designed robust. The valve can be charged up to 500 bar and is delivered at a certain pressure.1.1 ApplicationThe pressure valve is used to protect high volume lift cylinders in truck cranes. It should avoid excessive pressure increase in unmoving cylin-ders due to warming (“sushine valve”).1.2 Recommended Installation2 FunctionThe pressure valve operates as a direct acting seat valve. The pressure can be set using an adjusting screw. The screw is locked after adjustment with a backup sealing nut and can be protected by a cap.2.1 Features▪ Cartridge type▪ Small installation space ▪ Robust construction▪Stepped cavity (corresponds to Bucher UVP-4) ▪Seat valve, leakage freeP – protected port T - tankw e e n g i n e e r y o u r p r o g r e s s3 Technical Data4 4.1 Type CodeXXX – fest vorgegebene Merkmale XXX – vom Kunden wählbare Merkmale4.2 Versions currently availableThe versions listed below are available as standard. Further versions as part of the options given on the type code can be configured upon request.designationtype codepart nr.PRV –DSU –CA -10LPM -500BAR –MAN230BAR –239 -NBR PRV –DSU –CA -10 -500 –MAN230 –239 -N 412.072.451.9 PRV –DSU –CA -10LPM -500BAR –MAN235BAR –239 -NBR PRV –DSU –CA -10 -500 –MAN235 –239 -N 412.072.430.9 PRV –DSU –CA -10LPM -500BAR –MAN290BAR –239 -NBR PRV –DSU –CA -10 -500 –MAN290 –239 -N 412.072.433.9 PRV –DSU –CA -10LPM -500BAR –MAN340BAR –239 -NBR PRV –DSU –CA -10 -500 –MAN340 –239 -N 412.072.431.9 PRV –DSU –CA -10LPM -500BAR –MAN420BAR –239 -NBR PRV –DSU –CA -10 -500 –MAN420 –239 -N 412.072.432.9CriteriaUnit Value Installation position any Weightkg 0,1Surface protectiveZinc coated Maximum input pressure (P) bar 550Adjustable pressurebar 100 - 500 Maximum Tankpressure (T) bar 8 Maximum input flow rate (P) l/min 10Hydraulic fluidMineral oil (HL, HLP) conforming with DIN 51524, other fluids upon re-Hydraulic fluid pressure range °C -25 bis +80 Ambient temperature °C < +50 Viscosity rangemm2/s 2,8 - 500Contamination gradeFiltering conforming with NAS 1638, class 9, with minimum retentionPRVDSUCA10500239N000102030405060700 Product group Pressure relief valves PRV 01 Variant manual adjustable DSU 02 Port / Case Cartridgeventil CA 03 Input flow rate Qmax.10 l/min 1004 Max.permissible pressure Pmax.. 500bar50005 Activation Man ually adjustable 100-500barMAN100 06 Stepped cavity WESSEL-Patrone 8.00239 (stepped cavity) 239 07 Seal NBR, temperatur range -25°C bis +80°CNw e e n g i n e e r y o u r p r o g r e s s5 5.1 Characteristic 1: Variant DSUAdjustable pressure relief valve5.2 Characteristic 2: Port / Case: Variant CA - CartridgeAs variant CA, the valve is delivered as a cartridge valve. The Cavity has to be designed according to characteristic 6 (stepped cavity)5.3 Characteristic 3: input flow rateRecommended maximum flow rate of 10 l/min.5.4 Characteristic 4: Max.permissible pressureMaximum permissible pressure is 500bar (adjustable range100 - 500bar)5.5 Characteristic 5: Activation / SettingThe valve can be adjusted with a set screw. For this purpose, the protective cap must be removed and the counter nut undone.5.6 Characteristic 6: Stepped cavity 8.00239 (corresponds to Bucher UVP- 4)Das vorgesteuerte Druckbegrenzungsventil ist ein Cartridgebauteilund wird in eine Stufenbohrung entsprechend nebenstehender Zeichnung eingeschraubt.5.7 Characteristic 7: SealNBR, temperature range -25°C bis +80°Cw e e n g i n e e r y o u r p r o g r e s s6 Installation6.1 General information▪ Observe all installation and safety information of the construction machine / attachment tools manufacturer. ▪ Only technically permitted changes are to be made on the construction machine. ▪ The user has to ensure that the device is suitable for the respective application. ▪ Application exclusively for the range of application specified by the manufacturer. ▪ Before installation or de-installation, the hydraulic system is to be depressurized. ▪ Settings are to be made by qualified personnel only.▪ Opening is only to be performed with the approval of the manufacturer, otherwise the warranty is invalidated.6.2 Connection RecommendationsNOTE : Enclosed proposed resolution is not always guaranteed. The functionality and the technical details of the construction ma-chine must be checked.5.3 Montage – BauraumObserve connection names.Do not damage seals and flange surface. Its hydraulic system must be ventedEnsure sufficient free space for setting and installation work6.3 Installation - installation space▪ Observe connection names.▪ Do not damage seals and flange surface. ▪ Its hydraulic system must be vented▪ Ensure sufficient free space for setting and installation workCAUTION: Hydraulic hoses must not touch the pressure relief valve, otherwise they are subject to thermal damaging. Tightening torques must be observed. Torque wrench needed.77.1 General Instructions▪The views in drawings are shown in accordance with the European normal projection variant▪ A comma ( , ) is used as a decimal point in drawings ▪All dimensions are given in mm7.2 StandardsThe following standards must be observed when installing and operating the valve:▪ DIN EN ISO 13732-1:2008-12, Temperatures on accessible surfaces8 ZubehörSafety cap: 275.066.000.6。
Discrete cosine transform

Discrete cosine transformA discrete cosine transform (DCT ) expresses a finite sequence of data points in terms of a sum of cosine functions oscillating at different frequencies. DCTs are important to numerous applications in science and engineering, from lossy compression of audio (e.g. MP3) and images (e.g. JPEG) (where small high-frequency components can be discarded), to spectral methods for the numerical solution of partial differential equations. The use of cosine rather than sine functions is critical in these applications: for compression, it turns out that cosine functions are much more efficient (as described below, fewer functions are needed to approximate a typical signal), whereas for differential equations the cosines express a particular choice of boundary conditions.In particular, a DCT is a Fourier-related transform similar to the discrete Fourier transform (DFT), but using only real numbers. DCTs are equivalent to DFTs of roughly twice the length, operating on real data with even symmetry (since the Fourier transform of a real and even function is real and even), where in some variants the input and/or output data are shifted by half a sample. There are eight standard DCT variants, of which four are common.The most common variant of discrete cosine transform is the type-II DCT, which is often called simply "the DCT",(N. Ahmed, T. Natarajan and K.R.Rao, 1974; K.R.Rao and P.Yip, 1990); its inverse, the type-III DCT, is correspondingly often called simply "the inverse DCT" or "the IDCT". Two related transforms are the discrete sine transform (DST), which is equivalent to a DFT of real and odd functions, and the modified discrete cosine transform (MDCT), which is based on a DCT of overlapping data.ApplicationsThe DCT, and in particular the DCT-II, is often used in signal and image processing, especially for lossy data compression, because it has a strong "energy compaction" property (Ahmed, Natarajan and Rao, 1974; Rao and Yip,1990): most of the signal information tends to be concentrated in a few low-frequency components of the DCT,approaching the Karhunen-Loève transform (which is optimal in the decorrelation sense) for signals based on certain limits of Markov processes. As explained below, this stems from the boundary conditions implicit in the cosine functions.DCT-II (bottom) compared to the DFT (middle) of an input signal (top).A related transform, the modifieddiscrete cosine transform, or MDCT(based on the DCT-IV), is used inAAC, Vorbis, WMA, and MP3 audiocompression.DCTs are also widely employed insolving partial differential equations byspectral methods, where the differentvariants of the DCT correspond toslightly different even/odd boundaryconditions at the two ends of the array.DCTs are also closely related toChebyshev polynomials, and fast DCTalgorithms (below) are used inChebyshev approximation of arbitraryfunctions by series of Chebyshevpolynomials, for example inClenshaw –Curtis quadrature.JPEGThe DCT is used in JPEG image compression, MJPEG, MPEG, DV, and Theora video compression. There, the two-dimensional DCT-II of blocks are computed and the results are quantized and entropy coded. In this case, is typically 8 and the DCT-II formula is applied to each row and column of the block. The result is an 8 × 8transform coefficient array in which theelement (top-left) is the DC (zero-frequency) component and entries with increasing vertical and horizontal index values represent higher vertical and horizontal spatial rmal overviewLike any Fourier-related transform, discrete cosine transforms (DCTs) express a function or a signal in terms of a sum of sinusoids with different frequencies and amplitudes. Like the discrete Fourier transform (DFT), a DCT operates on a function at a finite number of discrete data points. The obvious distinction between a DCT and a DFT is that the former uses only cosine functions, while the latter uses both cosines and sines (in the form of complex exponentials). However, this visible difference is merely a consequence of a deeper distinction: a DCT implies different boundary conditions than the DFT or other related transforms.The Fourier-related transforms that operate on a function over a finite domain, such as the DFT or DCT or a Fourier series, can be thought of as implicitly defining an extension of that function outside the domain. That is, once you write a function as a sum of sinusoids, you can evaluate that sum at any , even for where the originalwas not specified. The DFT, like the Fourier series, implies a periodic extension of the original function. A DCT, like a cosine transform, implies an even extension of the original function.Illustration of the implicit even/odd extensions of DCT input data, for N =11 data points(red dots), for the four most common types of DCT (types I-IV).However, because DCTs operate onfinite , discrete sequences, two issuesarise that do not apply for thecontinuous cosine transform. First, onehas to specify whether the function iseven or odd at both the left and rightboundaries of the domain (i.e. themin-n and max-n boundaries in thedefinitions below, respectively).Second, one has to specify aroundwhat point the function is even or odd.In particular, consider a sequence abcdof four equally spaced data points, andsay that we specify an even leftboundary. There are two sensiblepossibilities: either the data are evenabout the sample a , in which case theeven extension is dcbabcd , or the dataare even about the point halfwaybetween a and the previous point, inwhich case the even extension isdcbaabcd (a is repeated).These choices lead to all the standardvariations of DCTs and also discretesine transforms (DSTs). Each boundary can be either even or odd (2 choices per boundary) and can be symmetric about a data point or the point halfway between two data points (2 choices per boundary), for a total of 2 × 2 × 2 × 2= 16 possibilities. Half of these possibilities, those where the left boundary is even, correspond to the 8 types of DCT; the other half are the 8 types of DST.These different boundary conditions strongly affect the applications of the transform and lead to uniquely useful properties for the various DCT types. Most directly, when using Fourier-related transforms to solve partial differential equations by spectral methods, the boundary conditions are directly specified as a part of the problem being solved. Or, for the MDCT (based on the type-IV DCT), the boundary conditions are intimately involved in the MDCT's critical property of time-domain aliasing cancellation. In a more subtle fashion, the boundary conditions are responsible for the "energy compactification" properties that make DCTs useful for image and audio compression,because the boundaries affect the rate of convergence of any Fourier-like series.In particular, it is well known that any discontinuities in a function reduce the rate of convergence of the Fourier series, so that more sinusoids are needed to represent the function with a given accuracy. The same principle governs the usefulness of the DFT and other transforms for signal compression: the smoother a function is, the fewer terms in its DFT or DCT are required to represent it accurately, and the more it can be compressed. (Here, we think of the DFT or DCT as approximations for the Fourier series or cosine series of a function, respectively, in order to talk about its "smoothness".) However, the implicit periodicity of the DFT means that discontinuities usually occur at the boundaries: any random segment of a signal is unlikely to have the same value at both the left and right boundaries.(A similar problem arises for the DST, in which the odd left boundary condition implies a discontinuity for any function that does not happen to be zero at that boundary.) In contrast, a DCT where both boundaries are even always yields a continuous extension at the boundaries (although the slope is generally discontinuous). This is why DCTs, and in particular DCTs of types I, II, V, and VI (the types that have two even boundaries) generally perform better for signal compression than DFTs and DSTs. In practice, a type-II DCT is usually preferred for such applications, in part for reasons of computational convenience.Formal definitionFormally, the discrete cosine transform is a linear, invertible function (where denotes the set of real numbers), or equivalently an invertible N × N square matrix. There are several variants of the DCT with slightly modified definitions. The N real numbers x 0, ..., x N -1 are transformed into the N real numbers X 0, ..., X N -1 according to one of the formulas:DCT-ISome authors further multiply the x 0 and x N -1 terms by √2, and correspondingly multiply the X 0 and X N -1 terms by 1/√2. This makes the DCT-I matrix orthogonal, if one further multiplies by an overall scale factor of , but breaks the direct correspondence with a real-even DFT.The DCT-I is exactly equivalent (up to an overall scale factor of 2), to a DFT of real numbers with even symmetry. For example, a DCT-I of N =5 real numbers abcde is exactly equivalent to a DFT of eight real numbers abcdedcb (even symmetry), divided by two. (In contrast, DCT types II-IV involve a half-sample shift in the equivalent DFT.)Note, however, that the DCT-I is not defined for N less than 2. (All other DCT types are defined for any positive N .)Thus, the DCT-I corresponds to the boundary conditions: x n is even around n =0 and even around n =N -1; similarly for X k .DCT-IIThe DCT-II is probably the most commonly used form, and is often simply referred to as "the DCT" (Ahmed,Natarajan, Rao 1974); (Rao & Yip, 1990).This transform is exactly equivalent (up to an overall scale factor of 2) to a DFT ofreal inputs of even symmetry where the even-indexed elements are zero. That is, it is half of the DFT of theinputs , where, for , , and for .Some authors further multiply the X 0 term by 1/√2 and multiply the resulting matrix by an overall scale factor of(see below for the corresponding change in DCT-III). This makes the DCT-II matrix orthogonal, but breaks the direct correspondence with a real-even DFT of half-shifted input.The DCT-II implies the boundary conditions: x n is even around n =-1/2 and even around n =N -1/2; X k is even around k =0 and odd around k =N .DCT-IIIBecause it is the inverse of DCT-II (up to a scale factor, see below), this form is sometimes simply referred to as "the inverse DCT" ("IDCT"), (Rao & Yip, 1990).Some authors further multiply the x 0 term by √2 and multiply the resulting matrix by an overall scale factor of(see above for the corresponding change in DCT-II), so that the DCT-II and DCT-III are transposes of one another. This makes the DCT-III matrix orthogonal, but breaks the direct correspondence with a real-even DFT of half-shifted output.The DCT-III implies the boundary conditions: x n is even around n =0 and odd around n =N ; X k is even around k =-1/2and even around k =N -1/2.DCT-IVThe DCT-IV matrix becomes orthogonal (and thus, being clearly symmetric, its own inverse) if one further multiplies by an overall scale factor of .A variant of the DCT-IV, where data from different transforms are overlapped , is called the modified discrete cosine transform (MDCT) (Malvar, 1992).The DCT-IV implies the boundary conditions: x n is even around n =-1/2 and odd around n =N -1/2; similarly for X k .DCT V-VIIIDCT types I-IV are equivalent to real-even DFTs of even order (regardless of whether N is even or odd), since the corresponding DFT is of length 2(N−1) (for DCT-I) or 4N (for DCT-II/III) or 8N (for DCT-VIII). In principle, there are actually four additional types of discrete cosine transform (Martucci, 1994), corresponding essentially to real-even DFTs of logically odd order, which have factors of N±½ in the denominators of the cosine arguments. Equivalently, DCTs of types I-IV imply boundaries that are even/odd around either a data point for both boundaries or halfway between two data points for both boundaries. DCTs of types V-VIII imply boundaries that even/odd around a data point for one boundary and halfway between two data points for the other boundary.However, these variants seem to be rarely used in practice. One reason, perhaps, is that FFT algorithms for odd-length DFTs are generally more complicated than FFT algorithms for even-length DFTs (e.g. the simplest radix-2 algorithms are only for even lengths), and this increased intricacy carries over to the DCTs as described below.(The trivial real-even array, a length-one DFT (odd length) of a single number a, corresponds to a DCT-V of length N=1.)Inverse transformsUsing the normalization conventions above, the inverse of DCT-I is DCT-I multiplied by 2/(N-1). The inverse of DCT-IV is DCT-IV multiplied by 2/N. The inverse of DCT-II is DCT-III multiplied by 2/N and vice versa. (See e.g. Rao & Yip, 1990.)Like for the DFT, the normalization factor in front of these transform definitions is merely a convention and differsbetween treatments. For example, some authors multiply the transforms by so that the inverse does notrequire any additional multiplicative factor. Combined with appropriate factors of √2 (see above), this can be used to make the transform matrix orthogonal.Multidimensional DCTsMultidimensional variants of the various DCT types follow straightforwardly from the one-dimensional definitions: they are simply a separable product (equivalently, a composition) of DCTs along each dimension.For example, a two-dimensional DCT-II of an image or a matrix is simply the one-dimensional DCT-II, from above, performed along the rows and then along the columns (or vice versa). That is, the 2d DCT-II is given by the formula (omitting normalization and other scale factors, as above):Two-dimensional DCT frequencies from the JPEG DCT Technically, computing a two- (or multi-) dimensionalDCT by sequences of one-dimensional DCTs alongeach dimension is known as a row-column algorithm(after the two-dimensional case). As withmultidimensional FFT algorithms, however, there existother methods to compute the same thing whileperforming the computations in a different order (i.e.interleaving/combining the algorithms for the differentdimensions).The inverse of a multi-dimensional DCT is just aseparable product of the inverse(s) of the correspondingone-dimensional DCT(s) (see above), e.g. theone-dimensional inverses applied along one dimensionat a time in a row-column algorithm.The image to the right shows combination of horizontaland vertical frequencies for an 8 x 8 ( ) two-dimensional DCT. Each step from left to rightand top to bottom is an increase in frequency by 1/2 cycle. For example, moving right one from the top-left square yields a half-cycle increase in the horizontal frequency. Another move to the right yields two half-cycles. A move down yields two half-cycles horizontally and a half-cycle vertically. The source data (8x8) is transformed to a linear combination of these 64 frequency squares.ComputationAlthough the direct application of these formulas would require O(N 2) operations, it is possible to compute the same thing with only O(N log N ) complexity by factorizing the computation similarly to the fast Fourier transform (FFT).One can also compute DCTs via FFTs combined with O(N ) pre- and post-processing steps. In general, O(N log N )methods to compute DCTs are known as fast cosine transform (FCT) algorithms.The most efficient algorithms, in principle, are usually those that are specialized directly for the DCT, as opposed to using an ordinary FFT plus O(N ) extra operations (see below for an exception). However, even "specialized" DCT algorithms (including all of those that achieve the lowest known arithmetic counts, at least for power-of-two sizes)are typically closely related to FFT algorithms —since DCTs are essentially DFTs of real-even data, one can design a fast DCT algorithm by taking an FFT and eliminating the redundant operations due to this symmetry. This can even be done automatically (Frigo & Johnson, 2005). Algorithms based on the Cooley –Tukey FFT algorithm are most common, but any other FFT algorithm is also applicable. For example, the Winograd FFT algorithm leads to minimal-multiplication algorithms for the DFT, albeit generally at the cost of more additions, and a similar algorithm was proposed by Feig & Winograd (1992) for the DCT. Because the algorithms for DFTs, DCTs, and similar transforms are all so closely related, any improvement in algorithms for one transform will theoretically lead to immediate gains for the other transforms as well (Duhamel & Vetterli, 1990).While DCT algorithms that employ an unmodified FFT often have some theoretical overhead compared to the best specialized DCT algorithms, the former also have a distinct advantage: highly optimized FFT programs are widely available. Thus, in practice, it is often easier to obtain high performance for general lengths N with FFT-based algorithms. (Performance on modern hardware is typically not dominated simply by arithmetic counts, and optimization requires substantial engineering effort.) Specialized DCT algorithms, on the other hand, see widespread use for transforms of small, fixed sizes such as the DCT-II used in JPEG compression, or the small DCTs (or MDCTs) typically used in audio compression. (Reduced code size may also be a reason to use a specialized DCT forembedded-device applications.)In fact, even the DCT algorithms using an ordinary FFT are sometimes equivalent to pruning the redundant operations from a larger FFT of real-symmetric data, and they can even be optimal from the perspective of arithmetic counts. For example, a type-II DCT is equivalent to a DFT of size with real-even symmetry whose even-indexed elements are zero. One of the most common methods for computing this via an FFT (e.g. the method used in FFTPACK and FFTW) was described by Narasimha & Peterson (1978) and Makhoul (1980), and this method in hindsight can be seen as one step of a radix-4 decimation-in-time Cooley–Tukey algorithm applied to the "logical" real-even DFT corresponding to the DCT II. (The radix-4 step reduces the size DFT to four size-DFTs of real data, two of which are zero and two of which are equal to one another by the even symmetry, hence giving a single size- FFT of real data plus butterflies.) Because the even-indexed elements are zero, thisradix-4 step is exactly the same as a split-radix step; if the subsequent size- real-data FFT is also performed by a real-data split-radix algorithm (as in Sorensen et al., 1987), then the resulting algorithm actually matches what waslong the lowest published arithmetic count for the power-of-two DCT-II ( real-arithmetic operations[1]). So, there is nothing intrinsically bad about computing the DCT via an FFT from an arithmetic perspective—it is sometimes merely a question of whether the corresponding FFT algorithm is optimal. (As a practical matter, the function-call overhead in invoking a separate FFT routine might be significant for small , but this is an implementation rather than an algorithmic question since it can be solved by unrolling/inlining.)Example of IDCTConsider this 8x8 grayscale image of capital letter A.Original size, scaled 10x (nearest neighbor),scaled 10x (bilinear).DCT of the image.Basis functions of the discrete cosinetransformation with corresponding coefficients(specific for our image).Each basis function is multiplied by its coefficient and then this product is added to the final image.On the left is final image. In the middle isweighted function (multiplied by coefficient)which is added to the final image. On the right isthe current function and correspondingcoefficient. Images are scaled (using bilinearinterpolation) by factor 10x.Notes[1]The precise count of real arithmetic operations, and in particular the count of real multiplications, depends somewhat on the scaling of thetransform definition. The count is for the DCT-II definition shown here; two multiplications can be saved if the transform is scaled by an overall factor. Additional multiplications can be saved if one permits the outputs of the transform to be rescaled individually, as was shown by Arai et al. (1988) for the size-8 case used in JPEG.References•Wen-Hsiung Chen; Smith, C.; Fralick, S. (September 1977). "A Fast Computational Algorithm for the Discrete Cosine Transform". IEEE Transactions on Communications25 (9): 1004–1009.doi:10.1109/TCOM.1977.1093941.•Narasimha, M.; Peterson, A. (June 1978). "On the Computation of the Discrete Cosine Transform". IEEE Transactions on Communications26 (6): 934–936. doi:10.1109/TCOM.1978.1094144.•Makhoul, J. (February 1980). "A fast cosine transform in one and two dimensions". IEEE Transactions on Acoustics, Speech, and Signal Processing28 (1): 27–34. doi:10.1109/TASSP.1980.1163351.•Sorensen, H.; Jones, D.; Heideman, M.; Burrus, C. (June 1987). "Real-valued fast Fourier transform algorithms".IEEE Transactions on Acoustics, Speech, and Signal Processing35 (6): 849–863.doi:10.1109/TASSP.1987.1165220.•Arai, Y.; Agui, T.; Nakajima, M. (November 1988). "A fast DCT-SQ scheme for images" (http://search.ieice.org/bin/summary.php?id=e71-e_11_1095). IEICE Transactions71 (11): 1095–1097.•Duhamel, P.; Vetterli, M. (April 1990). "Fast fourier transforms: A tutorial review and a state of the art". Signal Processing19 (4): 259–299. doi:10.1016/0165-1684(90)90158-U.•Rao, K; Yip, P (1990), Discrete Cosine Transform: Algorithms, Advantages, Applications, Boston: Academic Press, ISBN 0-12-580203-X•Ahmed, N. (January 1991). "How I came up with the discrete cosine transform" (/doc/ 52879771/DCT-History-How-I-Came-Up-with-the-Discrete-Cosine-Transform). Digital Signal Processing1 (1): 4–9. doi:10.1016/1051-2004(91)90086-Z.•Feig, E.; Winograd, S. (September 1992). "Fast algorithms for the discrete cosine transform". IEEE Transactions on Signal Processing40 (9): 2174–2193. doi:10.1109/78.157218.•Malvar, Henrique (1992), Signal Processing with Lapped Transforms, Boston: Artech House, ISBN 0-89006-467-9•Martucci, S. A. (May 1994). "Symmetric convolution and the discrete sine and cosine transforms". IEEE Transactions on Signal Processing42 (5): 1038–1051. doi:10.1109/78.295213.•Oppenheim, Alan; Schafer, Ronald; Buck, John (1999), Discrete-Time Signal Processing (2nd ed.), Upper Saddle River, N.J: Prentice Hall, ISBN 0-13-754920-2•Frigo, M.; Johnson, S. G. (February 2005). "The Design and Implementation of FFTW3" (/ fftw-paper-ieee.pdf). Proceedings of the IEEE93 (2): 216–231. doi:10.1109/JPROC.2004.840301.•Press, WH; Teukolsky, SA; Vetterling, WT; Flannery, BP (2007), "Section 12.4.2. Cosine Transform" (http:// /empanel/index.html#pg=624), Numerical Recipes: The Art of Scientific Computing (3rd ed.), New York: Cambridge University Press, ISBN 978-0-521-88068-8External links•"Tutorial: Discrete Cosine Transform" (/Discrete-Cosine-Transform-Tutorial.htm).Hakan Haberdar, University of Houston. Retrieved March 2012.•discrete cosine transform (/?op=getobj&from=objects&id=1469), .•The Discrete Cosine Transform (DCT): Theory and Application (.pk/ publications/tech_reports/DCT_TR802.pdf)•Implementation of MPEG integer approximation of 8x8 IDCT (ISO/IEC 23002-2) (/ software.html#IDCT)•Matteo Frigo and Steven G. Johnson: FFTW, /.A free (GPL) C library that can compute fast DCTs (types I-IV) in one or more dimensions, of arbitrary size.•Tim Kientzle: Fast algorithms for computing the 8-point DCT and IDCT, /parallel/ 184410889.Article Sources and Contributors10Article Sources and ContributorsDiscrete cosine transform Source: /w/index.php?oldid=539464406 Contributors: Adcasaa, Agamemnon2, Ahoerstemeier, Alejo2083, Alomov, Amusingmuses, Arkadi kagan, Armistej, Arnacer, Berland, Buscha, Can't sleep, clown will eat me, Cburnett, Cdecoro, Cferrero, Crazy runner, CryptoDerk, CyberSkull, Daniel.Cardenas, Darkwind, Davehein,Davidmeo, Dcoetzee, Deepakr, DmitriyV, DopefishJustin, Electron9, EvilStorm, Foolip, Gaius Cornelius, Giftlite, Glanthor Reviol, Gurijala, Guyburns, Hanakus, Hankwang, Harumphy, Helwr, Henning Makholm, Imjustmatthew, Isnow, Jjdawson7, Jogfalls1947, John Quincy Adding Machine, JordoCo, KHamsun, Lorem Ip, Lourakis, LutzL, Mallapurbharat, Mangledorf, Matusz,Mellery, Metacomet, Michael Hardy, Misternuvistor, Mixer, Momet, Mordecai lee, Mstuomel, Mulligatawny, Nfvr, Nikai, Nixdorf, Novacatz, Obradovic Goran, Ods15, Oli Filth, OverlordQ,PanagosTheOther, Photonique, PierreAbbat, Poneng, Qutezuce, Rafostry, Raj75081, Rik Bos, Rs 71 77 ta 92 93 9, Rs 71 77 ta 92 93 95, Rychomaciol, Salgueiro, Samuell, Sardar.ali, Saucepan, SciCompTeacher, Shanes, Shawn K. Quinn, Sobreira, Stassats, Stevenj, Tbackstr, That Guy, From That Show!, The Anome, Tolstoy143, Tpa87, Vrable, Widr, Wiki13, X-Fi6, Yuchen, Yunshui, 213 anonymous editsImage Sources, Licenses and ContributorsImage:Example dft dct.svg Source: /w/index.php?title=File:Example_dft_dct.svg License: Creative Commons Attribution-ShareAlike 3.0 Unported Contributors:Alessio DamatoImage:DCT-symmetries.svg Source: /w/index.php?title=File:DCT-symmetries.svg License: GNU Free Documentation License Contributors: en:StevenjImage:Dctjpeg.png Source: /w/index.php?title=File:Dctjpeg.png License: Public Domain Contributors: AnonMoos, Devcore, FelixH, Foroa, Stephantom,WikipediaMaster, 1 anonymous editsFile:letter-a-8x8.png Source: /w/index.php?title=File:Letter-a-8x8.png License: Public Domain Contributors: HanakusFile:dct-table.png Source: /w/index.php?title=File:Dct-table.png License: Public Domain Contributors: HanakusFile:idct-animation.gif Source: /w/index.php?title=File:Idct-animation.gif License: Creative Commons Attribution-Sharealike 3.0 Contributors: HanakusLicenseCreative Commons Attribution-Share Alike 3.0 Unported///licenses/by-sa/3.0/。
cosineembeddingloss损失函数使用

cosineembeddingloss损失函数使用摘要:1.cosineembeddingloss 损失函数的定义2.cosineembeddingloss 损失函数的应用场景3.cosineembeddingloss 损失函数的优点与不足4.cosineembeddingloss 损失函数的实例正文:cosineembeddingloss 损失函数是一种用于度量两个向量之间余弦相似度的损失函数,主要应用于高维向量的嵌入(embedding) 任务中。
它的目标是学习一组向量表示,使得相似的样本在嵌入空间中的距离较小,而不相似的样本在嵌入空间中的距离较大。
在深度学习中,特别是自然语言处理和计算机视觉领域,我们常常需要将高维的输入数据(如文本、图像等) 映射到低维的嵌入空间中,以便进行后续的计算和分析。
而cosineembeddingloss 损失函数就是在这种背景下应运而生的。
cosineembeddingloss 损失函数的计算公式为:$L = frac{1}{2}(CE_loss + alpha(1-CE_loss))$其中,$CE_loss$是余弦相似度损失,$alpha$是平衡系数,用于在相似度和对立性之间进行平衡。
在实际应用中,cosineembeddingloss 损失函数常常用于文本分类、图像分类、机器翻译等任务中。
以文本分类为例,假设我们有一个训练集,其中每个样本都由一个词向量和一个标签组成,我们可以使用cosineembeddingloss 损失函数来学习一个词向量表示,使得相似的词在嵌入空间中的距离较小,而不相似的词在嵌入空间中的距离较大。
cosineembeddingloss 损失函数的优点在于,它能够很好地度量向量之间的相似度,并且在学习过程中能够自适应地调整向量的表示,使得相似的样本在嵌入空间中的距离较小,而不相似的样本在嵌入空间中的距离较大。
但是,cosineembeddingloss 损失函数也有其不足之处,它可能会过度优化相似度,导致模型在嵌入空间中学习到错误的结构。
NEMA 4X (IP65) 工业气体流量控制器和计量仪说明书
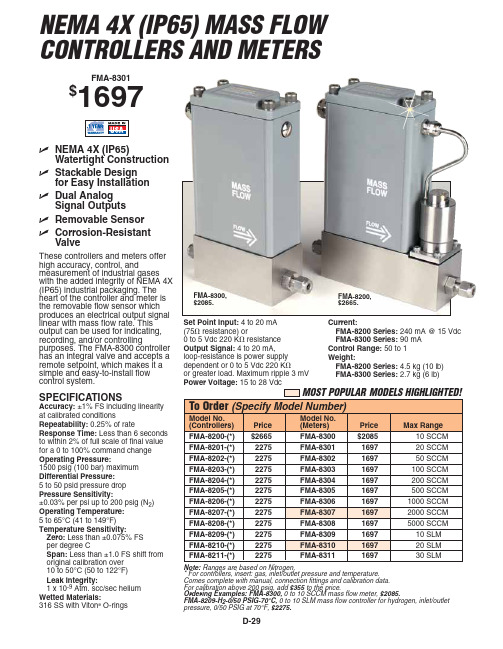
NEMA 4X (IP65) MASS FLOW CONTROLLERS AND METERSFMA-8301$1697ߜNEMA 4X (IP65)Watertight ConstructionߜStackable Designfor Easy InstallationߜDual AnalogSignal OutputsߜRemovable SensorߜCorrosion-ResistantValveThese controllers and meters offerhigh accuracy, control, andmeasurement of industrial gaseswith the added integrity of NEMA 4X(IP65) industrial packaging. Theheart of the controller and meter isthe removable flow sensor whichproduces an electrical output signal linear with mass flow rate. This output can be used for indicating, recording, and/or controlling purposes. The FMA-8300 controller has an integral valve and accepts a remote setpoint, which makes it a simple and easy-to-install flow control system. SPECIFICATIONSAccuracy:±1% FS including linearity at calibrated conditions Repeatability:0.25% of rate Response Time:Less than 6 seconds to within 2% of full scale of final value for a 0 to 100% command change Operating Pressure:1500 psig (100 bar) maximum Differential Pressure:5 to 50 psid pressure dropPressure Sensitivity:±0.03% per psi up to 200 psig (N2) Operating Temperature:5 to 65°C (41 to 149°F)Temperature Sensitivity:Zero:Less than ±0.075% FSper degree CSpan:Less than ±1.0 FS shift from original calibration over10 to 50°C (50 to 122°F)Leak Integrity:1 x 10-9Atm. scc/sec heliumWetted Materials:316 SS with Viton®O-rings Set Point Input:4 to 20 mA(75⍀ resistance) or0 to 5 Vdc 220 K⍀ resistanceOutput Signal:4 to 20 mA,loop-resistance is power supply dependent or 0 to 5 Vdc 220 K⍀or greater load. Maximum ripple 3 mV Power Voltage:Current:FMA-8200 Series:240 mA @15 VdcFMA-8300 Series:90 mAControl Range:50 to 1Weight:FMA-8200 Series:4.5 kg (10 lb)FMA-8300 Series:2.7 kg (6 lb)Note:Ranges are based on Nitrogen.* For controllers, insert: gas, inlet/outlet pressure and temperature.Comes complete with manual, connection fittings and calibration data.For calibration above 200 psig, add $355to the price.Ordering Examples: FMA-8300,0 to 10 SCCM mass flow meter,$2085.FMA-8209-H2-0/50 PSIG-70°C, 0 to 10 SLM mass flow controller for hydrogen, inlet/outlet pressure, 0/50 PSIG at 70°F,$2275.FMA-8300,$2085.FMA-8200,$2665.D-29CANADA www.omega.ca Laval(Quebec) 1-800-TC-OMEGA UNITED KINGDOM www. Manchester, England0800-488-488GERMANY www.omega.deDeckenpfronn, Germany************FRANCE www.omega.frGuyancourt, France088-466-342BENELUX www.omega.nl Amstelveen, NL 0800-099-33-44UNITED STATES 1-800-TC-OMEGA Stamford, CT.CZECH REPUBLIC www.omegaeng.cz Karviná, Czech Republic596-311-899TemperatureCalibrators, Connectors, General Test and MeasurementInstruments, Glass Bulb Thermometers, Handheld Instruments for Temperature Measurement, Ice Point References,Indicating Labels, Crayons, Cements and Lacquers, Infrared Temperature Measurement Instruments, Recorders Relative Humidity Measurement Instruments, RTD Probes, Elements and Assemblies, Temperature & Process Meters, Timers and Counters, Temperature and Process Controllers and Power Switching Devices, Thermistor Elements, Probes andAssemblies,Thermocouples Thermowells and Head and Well Assemblies, Transmitters, WirePressure, Strain and ForceDisplacement Transducers, Dynamic Measurement Force Sensors, Instrumentation for Pressure and Strain Measurements, Load Cells, Pressure Gauges, PressureReference Section, Pressure Switches, Pressure Transducers, Proximity Transducers, Regulators,Strain Gages, Torque Transducers, ValvespH and ConductivityConductivity Instrumentation, Dissolved OxygenInstrumentation, Environmental Instrumentation, pH Electrodes and Instruments, Water and Soil Analysis InstrumentationHeatersBand Heaters, Cartridge Heaters, Circulation Heaters, Comfort Heaters, Controllers, Meters and SwitchingDevices, Flexible Heaters, General Test and Measurement Instruments, Heater Hook-up Wire, Heating Cable Systems, Immersion Heaters, Process Air and Duct, Heaters, Radiant Heaters, Strip Heaters, Tubular HeatersFlow and LevelAir Velocity Indicators, Doppler Flowmeters, LevelMeasurement, Magnetic Flowmeters, Mass Flowmeters,Pitot Tubes, Pumps, Rotameters, Turbine and Paddle Wheel Flowmeters, Ultrasonic Flowmeters, Valves, Variable Area Flowmeters, Vortex Shedding FlowmetersData AcquisitionAuto-Dialers and Alarm Monitoring Systems, Communication Products and Converters, Data Acquisition and Analysis Software, Data LoggersPlug-in Cards, Signal Conditioners, USB, RS232, RS485 and Parallel Port Data Acquisition Systems, Wireless Transmitters and Receivers。
离散余弦变换的缩写

离散余弦变换的缩写
离散余弦变换(Discrete Cosine Transform,简称DCT)是一种将时间域信号转换为频域信号的变换技术,被广泛应用于信号处理、图
像处理、音频处理等领域。
DCT的缩写形式包括:
- CT:离散余弦变换
- DCT:离散余弦-正弦变换
- CTF:离散余弦傅里叶变换
- DTFT:离散时间傅里叶变换
-DCT:离散余弦变换
DCT的基本思想是将输入信号(可以是时间域或频域信号)通过一组系数进行变换,使得频域信号与时域信号相互转换,同时保留信号
的基本结构信息。
DCT的数学模型包括一个离散的余弦矩阵和正弦矩阵,它们的对
角线上的元素表示频域信号的系数,对角线下的元素表示时域信号的
系数。
通过组合这些系数,可以得到频域和时域信号之间的对应关系。
在实际应用中,DCT常常与其他信号处理技术结合使用,例如滤波、去噪、压缩等。
DCT的应用领域非常广泛,包括音频处理、图像处理、信号识别、模式识别、通信系统等。
拓展:
除了CT、DCT、CTF、DTFT等常见的缩写形式外,DCT还有很多变体形式,例如FFT(快速傅里叶变换)、IDCT(内部逆变换)等。
这些变
体形式都有不同的特点和适用范围,具体使用哪种形式取决于具体的应用场景和需求。
DCT是一种非常重要的信号处理技术,可以帮助我们更好地理解和分析信号。
了解DCT的缩写形式和相关应用,有助于我们更好地掌握这门技术,并在实际应用中发挥出它的最大价值。
cosineembeddingloss损失函数使用

cosineembeddingloss损失函数使用【原创实用版】目录1.cosineembeddingloss 损失函数的概述2.cosineembeddingloss 损失函数的计算方法3.cosineembeddingloss 损失函数的应用场景4.cosineembeddingloss 损失函数的优点与局限性正文cosineembeddingloss 损失函数是一种用于度量两个向量之间余弦相似度的损失函数,常用于度量嵌入(Metric Learning)任务中。
在深度学习模型训练过程中,该损失函数可以有效地引导模型学习到更加相似的嵌入向量,从而提高模型的性能。
计算 cosineembeddingloss 损失函数的方法相对简单。
首先,需要计算两个向量的点积,然后除以两个向量的模的乘积,最后取负数。
公式表示如下:cosineembeddingloss(x, y) = - (x·y) / (||x|| * ||y||)其中,x 和 y 分别表示两个向量,||x||和||y||分别表示它们的模。
cosineembeddingloss 损失函数的应用场景主要包括:1.在度量嵌入任务中,用于度量两个不同词汇表示的向量之间的相似度;2.在图像分类任务中,用于度量同一类别的不同样本表示的向量之间的相似度;3.在推荐系统中,用于度量用户和物品向量之间的相似度,从而为用户提供个性化推荐。
cosineembeddingloss 损失函数具有以下优点:1.可以有效地引导模型学习到更加相似的嵌入向量,提高模型的性能;2.计算简便,易于实现和优化;3.对不同尺度的向量具有鲁棒性,适用于不同长度的输入序列。
然而,cosineembeddingloss 损失函数也存在一定的局限性:1.对于某些任务,余弦相似度可能不是最合适的度量标准,需要根据具体任务选择合适的损失函数;2.当样本数量较少时,该损失函数可能会出现过拟合现象,需要结合其他正则化方法使用。
ReactNative打包异常:Androidresourcelinkingfailed(原创)

ReactNative打包异常:Androidresourcelinkingfailed(原创)异常原⽂:FAILURE: Build failed with an exception.* What went wrong:Execution failed for task ':react-native-orientation:verifyReleaseResources'.> A failure occurred while executing com.android.build.gradle.internal.tasks.Workers$ActionFacade> Android resource linking failed/root/.gradle/caches/transforms-2/files-2.1/1ebe56e8a2698b86e38474ff767fc615/appcompat-1.0.2/res/values-v26/values-v26.xml:5:5-8:13: AAPT: error: resource android:attr/colorError not found./root/.gradle/caches/transforms-2/files-2.1/1ebe56e8a2698b86e38474ff767fc615/appcompat-1.0.2/res/values-v26/values-v26.xml:9:5-12:13: AAPT: error: resource android:attr/colorError not found./root/.gradle/caches/transforms-2/files-2.1/1ebe56e8a2698b86e38474ff767fc615/appcompat-1.0.2/res/values-v26/values-v26.xml:13:5-16:13: AAPT: error: style attribute 'android:attr/keyboardNavigationCluster' not found. /root/.gradle/caches/transforms-2/files-2.1/1ebe56e8a2698b86e38474ff767fc615/appcompat-1.0.2/res/values-v28/values-v28.xml:5:5-8:13: AAPT: error: resource android:attr/dialogCornerRadius not found./root/.gradle/caches/transforms-2/files-2.1/1ebe56e8a2698b86e38474ff767fc615/appcompat-1.0.2/res/values-v28/values-v28.xml:9:5-12:13: AAPT: error: resource android:attr/dialogCornerRadius not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:57:5-88:25: AAPT: error: resource android:attr/fontStyle not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:57:5-88:25: AAPT: error: resource android:attr/font not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:57:5-88:25: AAPT: error: resource android:attr/fontWeight not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:57:5-88:25: AAPT: error: resource android:attr/fontVariationSettings not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:57:5-88:25: AAPT: error: resource android:attr/ttcIndex not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:89:5-125:25: AAPT: error: resource android:attr/startX not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:89:5-125:25: AAPT: error: resource android:attr/startY not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:89:5-125:25: AAPT: error: resource android:attr/endX not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:89:5-125:25: AAPT: error: resource android:attr/endY not found./root/.gradle/caches/transforms-2/files-2.1/b633e8a572c08ec36267fa720bdc9a9b/core-1.0.1/res/values/values.xml:126:5-132:25: AAPT: error: resource android:attr/offset not found.* Try:Run with --stacktrace option to get the stack trace. Run with --info or --debug option to get more log output. Run with --scan to get full insights.* Get more help at https://Deprecated Gradle features were used in this build, making it incompatible with Gradle 7.0.Use '--warning-mode all' to show the individual deprecation warnings.See https:///6.5/userguide/command_line_interface.html#sec:command_line_warningsBUILD FAILED in 1m 11s814 actionable tasks: 235 executed, 498 from cache, 81 up-to-date解决⽅案:在node_modules⽂件夹下找到插件位置, android/build.gradle可以看到:修改红⾊字体属性(compileSdkVersion、buildToolsVersion、minSdkVersion、targetSdkVersion)的值为绿⾊的值android {compileSdkVersion pileSdkVersionbuildToolsVersion rootProject.ext.buildToolsVersiondefaultConfig {minSdkVersion rootProject.ext.minSdkVersiontargetSdkVersion rootProject.ext.targetSdkVersionversionCode 1versionName "1.0"ndk {abiFilters "armeabi-v7a", "x86"}}gradle clean后重新打包。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
A PPLICATION N OTE: 8X8 D ISCRETE C OSINET RANSFORMR EL. 1.0D OC. N O. AN019M ARCH 2011T ILERA C ORPORATIONCopyright © 2006-2011 Tilera® Corporation. All rights reserved. Printed in the United States of America.No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, except as may be expressly permitted by the applicable copyright statutes or in writing by the Publisher.The following are registered trademarks of Tilera Corporation: Tilera and the Tilera logo.The following are trademarks of Tilera Corporation: Embedding Multicore, The Multicore Company, Tile Processor, TILE Architecture, TILE64, TILE Pro, TILE Pro36, TILE Pro64, TILExpress, TILExpress-64, TILExpress-20G, TILExpress Pro-22G, iMesh, TileDirect, TILEmpower, TILEncore, TILE-Gx, TILE-Gx16, TILE-Gx36, TILE-Gx64, TILE-Gx100, DDC, Multicore Development Environment, Gentle Slope Programming, iLib, TMC (Tilera Multicore Components), hardwall, Zero Overhead Linux (ZOL), MiCA (Multistream iMesh Crypto Accelerator), and mPIPE (multicore Programmable Intelligent Packet Engine). All other trademarks and/or registered trademarks are the property of their respective owners.Third-party software: The Tilera IDE makes use of the BeanShell scripting library. Source code for the BeanShell library can be found at the BeanShell website (/developer.html).This document contains advance information on Tilera products that are in development, sampling or initial production phases. This information and specifications contained herein are subject to change without notice at the discretion of Tilera Corporation.No license, express or implied by estoppels or otherwise, to any intellectual property is granted by this document. Tilera disclaims any express or implied warranty relating to the sale and/or use of Tilera products, including liability or warranties relating to fitness for a particular purpose, merchantability or infringement of any patent, copyright or other intellectual property right.Products described in this document are NOT intended for use in medical, life support, or other hazardous uses where malfunction could result in death or bodily injury.THE INFORMATION CONTAINED IN THIS DOCUMENT IS PROVIDED ON AN “AS IS” BASIS. Tilera assumes no liability for damages arising directly or indirectly from any use of the information contained in this document.Publishing Information:Contact Information:Document Number AN019 Release 1.0Date3/29/11Tilera CorporationInformation info@Web Site 8X8 DISCRETE COSINE TRANSFORM1OverviewThis Application Note describes Tilera’s implementation of the 8x8 Discrete Cosine Transform(DCT) routine on the TILE64™ processor. This routine processes incoming data, specifically pix-els, in 12Q0 format with output in 16Q0 format.The DCT routine performs a series of 2D discrete cosine transforms on a list of 8x8 blocks of pix-els. The routine implements the Chen FDCT1 and rounds output values operating in place. This algorithm is a key part of MPEG-2, JPEG compression, and is a common video benchmark.2UsageThe signature of the 8x8 Discrete Cosine Transform routine is as follows:void tilera_dct_multi(int16_t* dct_data, int num_fdcts);3InputsThe inputs to the tilera_dct_multi() routine are as follows:• A pointer to the input data (an array of 8x8 blocks of 16-bit values)•An integer representing the number of 8x8 blocks to transform4OutputThe tilera_dct_multi() routine operates in place, as it overwrites the input data with thetransformed result.1.“A Fast computational Algorithm for the Discrete Cosine Transform,” W. A. Chen, C.Harrison, and S.C. Fralick. IEEE Transac-tions on Communications. Vol. COM-25, No. 9, Sept. 1977, pp. 1004–1011.Application Note:8x8 Discrete Cosine Transform 1Tilera Confidential — Subject to Change Without NoticeApplication Note:28x8 Discrete Cosine TransformTilera Confidential — Subject to Change Without Notice 5About the tilera_dct_multi() RoutineThis routine relies on three helper functions:static inline vec_half2 macrndh(uint32_t c0, vec_half2 x0, uint32_t c1, vec_half2 x1);This function takes two scalar coefficients, c0 and c1, and two vectors of halfwords, x0 and x1. The function returns a vector of halfwords where result[i] = (c0 * x0[i] + c2 * x1[i] + 0x8000) >> 16. (i is the index into the vector).static inline vec_half2 msurndh(uint32_t c0, vec_half2 x0, uint32_t c1, vec_half2 x1);This function takes two scalar coefficients, c0 and c1, and two vectors of halfwords, x0 and x1. The function returns a vector of halfwords, where result[i] = (c0 * x0[i] - c2 * x1[i] + 0x8000) >> 16. (i is the index into the vector).static inline vec_half2 sclrndh(uint32_t c0, vec_half2 x0)This function takes a scalar coefficient, c0, and a vector of halfwords, x0, and returns a vector of halfwords where result[i] = (c0*x0[i]+0x8000) >> 16.Listing 1-1. tilera_dct_multi() Routine#include <vec_ops.h>#include <stdint.h>static inline vec_half2 macrndh(uint32_t c0, vec_half2 x0, uint32_t c1, vec_half2 x1){vec_half2 rh=0x8000;vec_half2 rl=0x8000;rh=__insn_mulhla_su(rh, x0,c0);rh=__insn_mulhla_su(rh, x1,c1);rl=__insn_mullla_su(rl, x0,c0);rl=__insn_mullla_su(rl, x1,c1);return(vec_inthh(rh,rl));}static inline vec_half2 sclrndh(uint32_t c0, vec_half2 x0){vec_half2 rh=0x8000;vec_half2 rl=0x8000;rh=__insn_mulhla_su(rh, x0,c0);rl=__insn_mullla_su(rl, x0,c0);return(vec_inthh(rh,rl));}static inline vec_half2 msurndh(uint32_t c0, vec_half2 x0, uint32_t c1, vec_half2 x1){int rh=0x8000;int rl=0x8000;rh=__insn_mulhla_su(rh,x0,c0);rl=__insn_mullla_su(rl,x0,c0);rh-=__insn_mulhl_su(x1,c1);rl-=__insn_mulll_su(x1,c1);return(vec_inthh(rh,rl));}void tilera_dct_multi(int16_t *dct_data, int num_fdcts) {const uint32_t c1 = 0x1f62, c3 = 0x1A9B;const uint32_t c5 = 0x11C7, c7 = 0x063E;const uint32_t c2 = 0x29CF, c6 = 0x1151;const uint32_t C1 = 0xFB15, C3 = 0xD4DB;const uint32_t C5 = 0x8E3A, C7 = 0x31f1;const uint32_t C2 = 0xA73D, C6 = 0x4546;const uint32_t C4 = 0xB505;int32_t count;int32_t iters=num_fdcts<<3;vec_half2 *data = (vec_half2*) dct_data;// Apply column DCTs to each column in// all blocksfor (count = 0; count < iters; count+=2){int32_t j=(count&7)>>1;int32_t i=(count)>>4;// We use SIMD ops to compute two// column DCTs simultaneouslyvec_half2 tmp0 = data[i*32+0*4+j];vec_half2 tmp1 = data[i*32+1*4+j];vec_half2 tmp2 = data[i*32+2*4+j];vec_half2 tmp3 = data[i*32+3*4+j];vec_half2 tmp4 = data[i*32+4*4+j];vec_half2 tmp5 = data[i*32+5*4+j];vec_half2 tmp6 = data[i*32+6*4+j];vec_half2 tmp7 = data[i*32+7*4+j];vec_half2 g0 = vec_addh(tmp0, tmp7);vec_half2 g1 = vec_addh(tmp1, tmp6);vec_half2 h1 = vec_addh(tmp2, tmp5);vec_half2 h0 = vec_addh(tmp3, tmp4);vec_half2 g3 = vec_subh(tmp2, tmp5);vec_half2 g2 = vec_subh(tmp3, tmp4);vec_half2 h2 = vec_subh(tmp0, tmp7);vec_half2 h3 = vec_subh(tmp1, tmp6);Application Note:8x8 Discrete Cosine Transform 3Tilera Confidential — Subject to Change Without Noticevec_half2 p0 = vec_addh(g0 , h0);vec_half2 r0 = vec_subh(g0 , h0);vec_half2 p1 = vec_addh(g1 , h1);vec_half2 r1 = vec_subh(g1 , h1);vec_half2 q1a = vec_addh(g2 , g2);vec_half2 s1a = vec_addh(h2 , h2);vec_half2 s0 = vec_addh(h3 , g3);vec_half2 q0 = vec_subh(h3 , g3);vec_half2 P0 = vec_addh(p0 , p1);vec_half2 P1 = vec_subh(p0 , p1);vec_half2 r0_ = vec_addh(r0 , r0);vec_half2 r1_ = vec_addh(r1 , r1);vec_half2 q1 = sclrndh(C4, q1a);vec_half2 s1 = sclrndh(C4, s1a);vec_half2 R1 = macrndh(C6,r1_, C2, r0_);vec_half2 R0 = msurndh(C6,r0_, C2, r1_);vec_half2 Q1 = vec_addh(q1 , q0);vec_half2 Q0 = vec_subh(q1 , q0);vec_half2 S1 = vec_addh(s1 , s0);vec_half2 S0 = vec_subh(s1 , s0);data[i*32+0*4+j] = P0;data[i*32+1*4+j] = macrndh(C7,Q1, C1,S1);data[i*32+2*4+j] = R1;data[i*32+3*4+j] = msurndh(C3,S0, C5,Q0);data[i*32+4*4+j] = P1;data[i*32+5*4+j] = macrndh(C3,Q0, C5,S0);data[i*32+6*4+j] = R0;data[i*32+7*4+j] = msurndh(C7,S1, C1,Q1);}// Apply row DCTs to each row in all blocksfor (count = 0; count < iters; count+=2){// We use SIMD ops to compute two row DCTs// simultaneouslyvec_half2 t0=data[count*4+0];vec_half2 t1=data[count*4+1];vec_half2 t2=data[count*4+2];vec_half2 t3=data[count*4+3];vec_half2 t4=data[count*4+4];vec_half2 t5=data[count*4+5];vec_half2 t6=data[count*4+6];vec_half2 t7=data[count*4+7];// Since the row data is not naturally// compact we need to interleave it herevec_half2 tmp0 = vec_intlh(t4,t0);vec_half2 tmp1 = vec_inthh(t4,t0);vec_half2 tmp2 = vec_intlh(t5,t1);vec_half2 tmp3 = vec_inthh(t5,t1);vec_half2 tmp4 = vec_intlh(t6,t2);vec_half2 tmp5 = vec_inthh(t6,t2);vec_half2 tmp6 = vec_intlh(t7,t3);vec_half2 tmp7 = vec_inthh(t7,t3);Application Note: 48x8 Discrete Cosine TransformTilera Confidential — Subject to Change Without Noticevec_half2 g0 = vec_addh(tmp0, tmp7);vec_half2 g1 = vec_addh(tmp1 , tmp6);vec_half2 h1 = vec_addh(tmp2 , tmp5);vec_half2 h0 = vec_addh(tmp3 , tmp4);vec_half2 h2 = vec_subh(tmp0, tmp7);vec_half2 h3 = vec_subh(tmp1 , tmp6);vec_half2 g3 = vec_subh(tmp2 , tmp5);vec_half2 g2 = vec_subh(tmp3 , tmp4);vec_half2 p0 = vec_addh(vec_addh(g0 , h0), 0x00040004);vec_half2 p1 = vec_addh(g1 , h1);vec_half2 r0 = vec_subh(g0 , h0);vec_half2 r1 = vec_subh(g1 , h1);vec_half2 q1a = sclrndh(C4, g2);vec_half2 s1a = sclrndh(C4, h2);vec_half2 q1 = vec_addh(q1a , q1a);vec_half2 s1 = vec_addh(s1a , s1a);vec_half2 s0 = vec_addh(h3 , g3);vec_half2 q0 = vec_subh(h3 , g3);vec_half2 P0 = vec_sraih(vec_addh(p0,p1),3);vec_half2 P1 = vec_sraih(vec_subh(p0,p1),3);vec_half2 Q1 = vec_addh(q1 , q0);vec_half2 Q0 = vec_subh(q1 , q0);vec_half2 S1 = vec_addh(s1 , s0);vec_half2 S0 = vec_subh(s1 , s0);vec_half2 R1 = macrndh(c6,r1,c2,r0);vec_half2 R0 = msurndh(c6,r0,c2,r1);vec_half2 out1 = macrndh(c7,Q1,c1,S1);vec_half2 out7 = msurndh(c7,S1,c1,Q1);vec_half2 out5 = macrndh(c3,Q0,c5,S0);vec_half2 out3 = msurndh(c3,S0,c5,Q0);t0=vec_intlh(out1,P0);t4=vec_inthh(out1,P0);t1=vec_intlh(out3,R1);t5=vec_inthh(out3,R1);t2=vec_intlh(out5,P1);t6=vec_inthh(out5,P1);t3=vec_intlh(out7,R0);t7=vec_inthh(out7,R0);//store the outputdata[count*4+ 0] = t0;data[count*4+ 1] = t1;data[count*4+ 2] = t2;data[count*4+ 3] = t3;data[count*4+ 4] = t4;data[count*4+ 5] = t5;data[count*4+ 6] = t6;data[count*4+ 7] = t7;}}Application Note:8x8 Discrete Cosine Transform 5Tilera Confidential — Subject to Change Without Notice6TILE64 PerformanceTILE64 single core performance:• 1 DCT / 514 cycles• 1.36 million DCTs / second (at 700 MHz)TILE64 multicore performance:•64 DCTs / 514 cycles•87.16 million DCTs / second (@700MHz)7SummaryTILE64 combines its per-core SIMD instruction set extensions and wide multicore architecture to deliver outstanding performance on the 8x8 DCT kernel.Application Note: 68x8 Discrete Cosine TransformTilera Confidential — Subject to Change Without Notice。
