Sophos 全线产品介绍
Sophos UTM 功能特性介绍

Sophos UTM 功能特性介绍Written By Suntengfei2013年11月目录1功能特性........................................................................................................................................... - 3 -1.1基础防火墙功能 ....................................................................................................................... - 3 -1.2网络安全 ................................................................................................................................... - 4 -1.3网页安全 ................................................................................................................................... - 8 -1.4反垃圾邮件功能 ..................................................................................................................... - 10 -1.5终端防病毒功能 ..................................................................................................................... - 12 -1.6无线保护 ................................................................................................................................. - 13 -1.7网页应用服务器防护 ............................................................................................................. - 16 -1功能特性1.1基础防火墙功能1.2网络安全1.2.1.1入侵防御系统●支持对全球IP地址按国家、地区分类,并可进行实时通讯拦截●支持TCP/SYN/UDP/ICMP Flood攻击防御●支持端口扫描攻击防御●支持在线式的IPS系统,支持万余条攻击特征代码●支持攻击特征代码库通过Internet在线实时更新●支持可用手工方式启用或停用某条特征代码●支持异常协议检测●支持针对Windows、Unix、Linux、ios、安卓、windows Mobile、Symbian等操作系统的弱点进行防御支持邮件告警通告入侵事件入侵防护部署示意图终端补丁库1.2.1.2VPN功能●支持最新终端使用包括Mac、Lunix、Windows等最新操作系统通过设备登录●支持多种远程访问方式,如PPTP、L2TP over IPSec协议,兼容iphone、iPad、Android系统的智能移动平台●与第三方标准IPSec设备兼容●支持VPN加速技术,使用VPN压缩等技术实现提高访问速度和减少数据流量的效果●支持DES、3DES、AES 128、AES 192、AES 256、Blowfish、Twofish、Serpent加密算法●支持UMTS/3G USB卡连接InternetVPN 部署示意图RED VPN部署示意图SSL VPN配置文件下载1.2.1.3QOS功能针对不同的应用,提供灵活的方式,在不同时刻对不同网络、主机或用户组应用不同的策略。
Sophos全线产品介绍

欧洲排名第一的防杀病毒软件-Sophos随着计算机网络的迅速普及,搭乘了网络信息高速列车的计算机病毒,传播速度倍增。
国际间的新病毒只需在几小时之内便会出现在我国用户面前,使他们的计算机体系时刻处于新病毒的威胁之中。
因此,反病毒产品技术的优劣,对用户的计算机安全起着至关重要的作用。
如果用户能够真正判别反病毒产品的优劣,那么,计算机安全其实近在咫尺。
对于用户来说,防病毒产品的质量直接关系到计算机体系的防护。
但是,选择质量优秀的反病毒产品,对用户既是重要的却又是困难的。
重要性体现在防病毒产品是否能够有效查杀病毒,查杀时是否具备安全性,它与软、硬平台是否存在兼容性、可靠性的问题,以及运行效率如何… 这些都直接关系到用户的切身利益。
而困难性则体现在当前我国反病毒产品市场, 受广告宣传主导因素的影响非常大。
用户在没有专业测试手段的情况下,对反病毒产品的优劣难以判断。
其实,国际权威机构的测试及其认证是解决用户上述问题的最好方式,因为被测试产品只有完全通过严格的专业测试-,才能获得认证标志。
作为欧洲最大防病毒提供商,Sophos的反病毒产品提供了全方位的的防毒和杀毒的功能。
其频获大奖的技术、完备的产品系列, 以及杰出的工程设计水准能为企业用户提供全方位的病毒防护。
SOPHOS产品系列由Sophos Anti-virus、MailMonitor、SAV Interface、SOPHOS SBE中小企业版四部分组成:其中Sophos Anti-virus用于文件服务器、桌面工作站以及移动设备的病毒防护;MailMonitor用于邮件系统(SMTP server和Email Server)的病毒防护;SAV interface则是提供给第三方的二次开发接口,允许用户把Sophos病毒引擎整合到他们的产品中。
SBE中小企业版可以支持WINDOWS和苹果MAC操作系统,分为Sophos Small Business Suite、Sophos Anti-Virus Small Business Edition、PureMessage Small Business Edition三个产品,支持5用户、10用户、25用户、50用户和100用户五个用户数量等级。
sophos安全产品介绍及成功案例

Sophos 安全产品介绍及成功案例销售工程师 Nick Niu 牛玉孝 Nick.niu@Sophos 公司介绍Sophos,守护使,意思是智慧, 20年前创立于牛津 年前创立于牛津, Sophos,守护使,意思是智慧, 20年前创立于牛津,创始人来自于牛津大学 中文网站: 中文网站: 为商业、教育、政府机构提供完整的终端安全解决方案 为商业、教育、政府机构提供完整的终端安全解决方案 机构提供 提供反病毒 间谍/广告软件、垃圾邮件、个人防火墙;应用程序控制、 提供反病毒、间谍/广告软件、垃圾邮件、个人防火墙;应用程序控制、设备 软件 控制、行为分析、NAC、 控制、行为分析、NAC、数据安全功能 年销售额4亿美元, 年销售额4亿美元,列全球安全行业第三 全球1500多名员工 全球1500多名员工 1500 2007年 获得国内“最佳企业终端安全奖” 2007年,获得国内“最佳企业终端安全奖”2业界领先的端点保护和数据保护行业领先端点保护Gartner领导象限 Gartner领导象限 Gartner领导象限 领导象限行业领先数据保护Gartner领导象限 领导象限赛门铁克SafeGuard DLP/CMF SafeGuard 设备加密 SafeGuard 数据交换 SafeGuard 管理中心 SafeGuard 文件和文件夹 加密 SafeGuard 端口和配置 保护 SafeGuard 合作伙伴: 合作伙伴: 微软、英特尔、 微软、英特尔、 希捷Check Point 软件技术Utimaco安全软件 安全软件 GuardianEdge技术集中式管理Panda统一代理5业界领先的安全供应商 业界领先的安全供应商顶尖的端点保护产品 数据保护产品 端点保护产品和数据保护产品 端点保护产品 高可用性产品带来的高效益 配套的解决方案咨询和客户服务32007年端点安全市场份额 年端点安全市场份额Worldwide Corporate Endpoint Security Software Revenue by Vendor, 2007Source: IDC, 2008Total = $2,647.8M4SOPHOS安全产品列表 安全产品列表产品端点安全产品型号Endpoint security and control Sophos Antivirus功能管理中心、反病毒、个人防火墙、恶意软件、 管理中心、反病毒、个人防火墙、恶意软件、 间谍软件、应用程序控制, 间谍软件、应用程序控制,NAC 管理中心、 管理中心、反病毒 管理中心、反病毒、 管理中心、反病毒、个人防火墙 管理中心、反病毒、防火墙、 管理中心、反病毒、防火墙、垃圾邮件 控制未授权、客人、 控制未授权、客人、不合法主机接入网络 反垃圾邮件、病毒、间谍软件、 反垃圾邮件、病毒、间谍软件、邮件内容过滤说明>100用户 用户中小企业安全包Sophos 计算机安全 Sophos 安全包< 100用户 用户 支持Mac、 、 支持 Windows网络访问控制NAC Advanced ES1000 ES50005万邮件 小时 万邮件/小时 万邮件 38万邮件 小时 万邮件/小时 万邮件 55万邮件 小时 万邮件/小时 万邮件反垃圾邮件网关ES8000 邮件安全软件 for Unix/Exchange/Notes反垃圾邮件、病毒、间谍邮件、 反垃圾邮件、病毒、间谍邮件、邮件内容过滤网页安全网关 数据保护产品WS500 WS1000 WS1100 SafeGuard Enterprise网页过滤、病毒、间谍软件、网站访问控制、 网页过滤、病毒、间谍软件、网站访问控制、 广告及应用控制 硬盘加密,文件加密,邮件加密, 盘加密和 硬盘加密,文件加密,邮件加密,U盘加密和 控制1U机箱 机箱5Sophos端点安全产品 端点安全产品Endpoint Security and Control6安全风险日渐升高变化迅速的安全环境 从前 恶作剧 现在 有金钱目的 网络边界正在瓦解简单有智慧散播缓慢散播快速无特定对象有明确目标终端计算机是安全防护最脆弱的一环7Sophos端点安全与控制 端点安全与控制防病毒 主动防御 (HIPS) 反间谍软件 流氓程序 网络访问控制 (NAC)Web Security and Control一个产品完成端点评估、 一个产品完成端点评估、控制和防护Email Security and ControlEndpoint Security and Control管理、控制应用程序 P2P, 盘等) 管理、控制应用程序 (VoIP, IM, P2P,U盘等) 个人防火墙 个人防火墙悉尼 牛津 波士顿 波士顿 温哥华 病毒 分析 间谍软件 间谍软件 分析 行为 分析 弱点 分析Sophos NAC Advanced垃圾邮 垃圾邮件 分析应用程序 分析网页 分析 8端点安全产品特性 Sophos 端点安全产品特性一个License支持所有功能 一个License支持所有功能 License 支持全球最广泛的操作系统, 2003,2008, 支持全球最广泛的操作系统,如:Windows Vista, XP, 2003,2008,NT, 95/98/Me, MAC, 十种操作系统,无须额外付费。
迈欧资迅Sophos端点安全介绍

迈欧资讯 公司组织架构
迈欧资讯 公司战略伙伴
二、SOPHOS公司背景 SOPHOS公司背景
Sophos 公司介绍
Sophos,守护使,意思是智慧; Sophos,守护使,意思是智慧; 公司成立于1985年前创立于牛津,创始人来自于牛津大学; 公司成立于1985年前创立于牛津,创始人来自于牛津大学; 1985年前创立于牛津 为商业、教育、政府机构提供完整的终端安全解决方案; 为商业、教育、政府机构提供完整的终端安全解决方案; 机构提供完整的终端安全解决方案 提供反病毒 间谍/广告软件、垃圾邮件、个人防火墙;应用程序控制、 提供反病毒、间谍/广告软件、垃圾邮件、个人防火墙;应用程序控制、设备 软件 控制、行为分析、NAC、数据安全功能; 控制、行为分析、NAC、数据安全功能; 有1亿用户,年销售额,列全球安全行业第三; 亿用户,年销售额,列全球安全行业第三; 全球1500多名员工; 全球1500多名员工; 1500多名员工 2007年,获得“最佳企业终端安全奖” 2007年 获得“最佳企业终端安全奖” 中文网站: 中文网站:
端点防护
应用程序和设备控制 控制未授权使用的应用程序,比如即时通信(QQ, MSN…),P2P下载(电驴,迅雷…),游戏等。 允许、限制或阻止使用未授权的移动设备,如U盘 ,以及无线网络。 反病毒、 反病毒、 HIPS 和个人防火墙 以我们快速,低资源消耗的代理一次扫描完成所有安 全检查。 通过基于行为的基因族技术(Behavioral Genotype Protection),不用更新病毒库,即可查杀最新和变种 病毒。 通过脚本检查,阻止基于网页的病毒入侵。 网络准入控制 评估端点是否安全 告警提示系统漏洞,比如防火墙未启用或病毒软件未 更新。 自动隔离不安全的计算机,禁止访问网络。 数据泄露保护(DLP) 数据泄露保护 通过数据监控和过滤,避免核心数据泄露。 避免无意的或有针对性的数据窃取攻击
Sophos Mobile 管理员帮助(产品版本号:9)说明书

内容关于本帮助 (1)关于 Sophos Mobile (2)关于 Sophos Mobile Admin (3)仪表板 (3)表格视图 (4)前提条件 (4)用户角色 (4)更改您的密码 (5)密码恢复 (5)使用 Sophos Mobile 管理设备的主要步骤 (7)报告 (8)任务 (9)监视任务 (9)警报 (12)安装 (13)配置个人设置 (13)配置密码策略 (13)配置 SMC 应用设置 (14)配置电子邮件 (14)配置 IT 部门联系人 (15)配置隐私设置 (15)配置 iOS 设置 (16)Apple 推送通知服务证书 (16)配置 iOS AirPlay 目标 (19)Android 设置 (19)设置 Android 管理模式 (20)在您的 Web 服务器上托管 Sophos 应用 (20)配置 Sophos Mobile Control 应用的同步间隔 (21)启用百度云推送服务 (21)注册 Samsung Knox 许可证 (21)配置 Windows 设备的轮询间隔 (22)检查您的许可证 (22)简单证书注册协议 (SCEP) (22)创建客户属性 (23)配置 SSL/TLS 证书 (24)配置 EAS 代理 (24)配置网络访问控制 (24)配置电子邮件服务器连接 (24)配置代理服务器连接 (24)配置门户访问权限 (24)配置文件上传限制 (25)开启审核日志 (25)创建系统消息 (25)配置自助服务门户 (26)配置自助服务门户设置 (26)创建注册文本 (27)可用的自助服务门户操作 (28)合规性策略 (31)创建合规性策略 (31)可用的合规性规则 (32)将合规策略分配到设备组 (37)检查设备合规性 (37)设备 (38)添加设备 (38)注册设备 (39)取消设备注册 (46)管理设备 (47)自定义设备属性 (58)Zero-touch 注册 (59)Knox Mobile Enrollment (62)Apple DEP (64)Duo Security 集成 (74)TeamViewer 远程控制 (75)设备组 (77)创建设备组 (77)删除设备组 (77)用户 (78)配置自助服务门户用户管理 (79)配置外部目录连接 (80)联合身份验证 (81)配置 LDAP 连接 (83)创建用户 (83)导入用户 (84)创建用户组 (84)配置文件和策略 (86)开始使用设备策略 (87)创建配置文件或策略 (87)导入用 Apple Configurator 创建的 iOS 设备配置文件 (88)导入 iOS 应用的设置配置文件 (89)关于 macOS 策略 (89)Windows 密码复杂性规则 (90)Samsung Knox 支持 (90)配置文件和策略中的占位符 (91)在设备上安装配置文件 (91)向设备分配策略 (92)卸载配置文件 (92)下载配置文件和策略 (93)Android 设备配置文件的配置 (93)Android 企业工作配置文件策略的配置 (109)Android 企业设备策略的配置 (120)Android 的 Sophos 容器策略的配置 (132)Android 的 Mobile Security 策略的配置 (141)Knox 容器配置文件的配置 (144)Android Things 策略的配置 (148)iOS 设备配置文件的配置 (148)iOS 的 Sophos 容器策略的配置 (175)iOS 的 Mobile Security 策略的配置 (183)macOS 设备策略的配置 (185)macOS 用户策略的配置 (199)Windows Mobile 策略的配置 (215)Windows 策略的配置 (224)Windows IoT 策略的配置 (234)任务捆绑包 (237)创建任务捆绑包 (237)可用的 Android 任务类型 (238)可用的 iOS 任务类型 (241)可用的 macOS 任务类型 (243)可用的 Windows 任务类型 (244)复制任务捆绑包 (246)将任务捆绑包传输至个人设备或设备组 (246)应用程序 (247)添加应用 (247)安装应用 (248)卸载应用 (249)应用设置 (Android) (250)应用设置 (iOS) (252)应用设置 (macOS) (254)应用设置 (Windows Mobile) (255)应用设置 (Windows) (256)确定 Windows MSI 链接的设置 (257)iOS 的托管应用 (258)管理 Apple VPP 应用 (258)将 VPN 连接分配给 iOS 应用 (263)将托管应用配置添加到 iOS 应用 (263)应用组 (265)创建应用组 (265)导入应用组 (266)企业文档 (268)添加公司文档 (268)Android 企业 (270)设置 Android 企业 - 概述 (270)设置 Android 企业(托管 Google Play 帐户方案) (271)设置 Android 企业(托管 Google 域方案) (272)配置 Android 企业设备注册 (275)管理 Android 企业用户(托管 Google 网域方案) (276)创建工作配置文件 (277)锁定工作配置文件 (277)从设备删除工作配置文件 (278)用户启动的工作配置文件删除 (278)Android 恢复出厂设置保护 (278)托管的 Google Play 应用 (280)Intune 应用保护 (286)设置 Microsoft Intune 集成 (286)创建 Intune 应用保护策略 (287)将应用分配给 Intune 应用保护策略 (287)将用户分配给 Intune 应用保护策略 (287)Intune 应用保护策略设置 (Android) (288)Intune 应用保护策略设置 (iOS) (292)管理 Sophos Mobile Security (296)Sophos Mobile Security 合规性规则 (296)配置第三方 EMM 集成 (298)创建管理员 (300)向设备发送消息 (301)Sophos 容器 (302)配置 Sophos 容器注册 (302)Mobile Advanced 许可证 (302)管理 Sophos 容器应用 (303)重置 Sophos 容器密码 (304)锁定和解锁 Sophos 容器 (304)企业 Keyring 同步 (305)将内容传递到 Sophos Central (306)导出内容 (306)导入内容 (306)用语表 (308)技术支持 (309)法律声明 (310)Sophos Mobile1 关于本帮助本帮助提供了有关Sophos Mobile Admin管理控制台的信息,并对操作程序进行了详细解释。
Sophos系列产品介绍

Sophos系列产品介绍

○ 适用于远程接入
‒ IPSec ‒ SSL
○ 适用于 WAF ○ 适用于用户门户 ○ 适用于无线热点 ○ 适用于 UTM 管理界面
28
偏远地区和分支机构VPN解决方案
• 远程办公室的工作人员往往技术能力较弱 • 远程办公室往往没有专职的IT安全人员 • 因此远端往往是网络安全的弱点 • 中央IT人员不能总是及时的解决远端的问题 • 建立远端安全相对麻烦
War driving Ransomware ASCII bombs Bluesnarfing Worms Decrypting Reverse engineering
Phreaking Port Scanning
20
Sophos UTM —— All in One
Network Firewall Network Protection
Command & Control Server
3
谨慎地自动回联
受感染的系统连接到命令与控 制(C&C)服务器执行进一步 指令或开始传递敏感数据
4
暗地扩散
恶意软件会不留痕迹的、缓 慢的,利用未打补丁的漏洞 或盗用凭证等方式,将自身 扩散到其他系统。
25
SophosLabs
24/7 Advanced Threat Protection Monitoring and Analytics
26
高级威胁防御(ATP)
6
精确的沙箱技术
对潜在的未知威胁可疑样本被 送到SopohsLabs云进行分析。 新的威胁情报送往UTM。
X
1
多层次防御
Sophos Web,邮件与端点保护 作为第一道防线,防止传染进 入网络
sophso企业版特点功能介绍

降低性能影响 – 一次快速的扫描即可以发现病毒,恶意程序,可疑文件和未授权软件
在员工计算机或客人计算机接入网络前,检查其安全状态。
综合的数据保护
以业界领先的Sophos SafeGuard 加密技术轻松的保护你硬盘和移动设备上的数据
提供用户上网浏览似的安全保护,针对http, https数据流进行病毒防护,及根据网站分类和内容控制用户访问权限。 产品型号: WS1000
4. 网络准入控制: Sophos NAC Advanced
以纯软件的方案实现网络准入控制,检查员工(已知计算机)或客人(未知计算机)是否符合安全要求,若不符合要求,自动提示用户修正漏洞或者隔离用户,限定其可以访 问的网络资源。
9. 新病毒爆发平约在2小时到4小时间解决。
10. 全球7*24小时365天不间断病毒、木马、恶意软件垃圾信侦测。
主要特性
Sophos Endpoint Security and Data Protection
以反病毒,防火墙 NAC 和数据加密保护你的计算机和机密数据
在客户端部署过程中自动卸载旧有的杀毒软件
产品介绍
端点安全产品:Sophos Endpoint Security and Data Protection 业界支持平台最为广泛的终端安全软件之一“Sophos端点安全”由于支持平台多,占用空间资源小,服务响应快,运行稳定,价格低廉,拥有强大的:集中管理,全硬盘加密和设备控制,应用程序和网络访问控制等功能,使你能轻松地保护你的公司业务不受病毒木马的侵害
主要产品
1. 端点安全产品: Sophos Endpoint Security and Control
Sophos UTM 产品说明说明书

Sophos UTM Feature ListGeneral ManagementÌCustomizable dashboardÌRole-based administration: Auditor, read-only and manager for all functionsÌNo-charge, centralized management of multipleUTMs via Sophos UTM Manager (SUM)ÌConfigurable update serviceÌReusable system object definitions for networks, services, hosts, time periods, users and groups, clients and servers ÌPoint & Click IPS rule managementÌSelf-service user portal for one-click VPN setupÌConfiguration change trackingÌManual or fully automated backup and restore optionsÌEmail or SNMP trap notification optionsÌSNMP supportÌOne-time password (OTP) / Two-factor authentication(2FA) supports OATH protocol for WebAdmin, User Portal, SSL VPN, IPSec VPN, HTML5 Portal and SSH Login*ÌOne-click secure access for Sophos customer support** Network Routing and ServicesÌRouting: static, multicast (PIM-SM)and dynamic (BGP, OSPF)ÌNAT static, masquerade (dynamic)ÌP rotocol independent multicast routing with IGMP snooping ÌBridging with STP support and ARP broadcast forwarding ÌW AN link balancing: 32 Internet connections, auto-link health check, automatic failover, automatic andweighted balancing and granular multipath rulesÌZ ero-config active/passive high- availabilityÌA ctive/active clustering for up to 10 appliancesÌ802.3ad interface link aggregationÌQoS with full control over bandwidth pools anddownload throttling using Stochastic Fairness Queuingand Random Early Detection on inbound trafficÌF ull configuration of DNS, DHCP and NTPÌS erver load balancingÌI Pv6 supportÌR ED supportÌVLAN DHCP support and tagging**ÌMultiple bridge support**Network ProtectionÌStateful deep packet inspection firewallÌIntrusion protection: Deep packet inspectionengine, 18,000+ patternsÌSelective IPS patterns for maximumperformance and protectionÌIPS pattern aging algorithm for optimal performance*ÌFlood protection: DoS, DDoS and portscan blockingÌCountry blocking by region or individual country(over 360 countries) with separate inbound/outbound settings and exceptionsÌSite-to-site VPN: SSL, IPSec, 256- bit AES/3DES,PFS, RSA, X.509 certificates, pre-shared keyÌRemote access: SSL, IPsec, iPhone/iPad/Cisco VPN client supportÌVoIP handling for SIP and H.323 connectionsÌConnection tracking helpers: FTP, IRC, PPTP, TFTPÌIdentity-based rules and configuration withAuthentication Agent for usersAdvanced Threat Protection*ÌDetect and block network traffic attempting tocontact command and control servers usingDNS, AFC, HTTP Proxy and firewallÌIdentify infected hosts on the network Sandstorm Protection***ÌCloud-based sandbox to detect, block and gain visibility into evasive zero-day targeted attacks in active content such as executables, PDFs, Office Documents, and more ÌPreviously unseen suspicious files aredetonated in the cloud-sandbox and monitoredbefore being released to the end-userÌComplete reporting on all suspicious file activityincluding detailed sandbox analysis results AuthenticationÌTransparent, proxy authentication (NTLM/Kerberos) or client authenticationÌAuthentication via: Active Directory, eDirectory,RADIUS, LDAP and TACACS+ÌSingle sign-on: Active directory, eDirectoryÌSophos Transparent Authentication Suite (STAS)provides AD agent for transparent reliable SSOauthentication with Microsoft Active Directory***ÌSSL supportÌTools: server settings check, username/passwordtesting and authentication cache flushÌGraphical browser for users and groupsÌAutomatic user creationÌScheduled backend synchronization prefetchÌComplex password enforcementWeb ProtectionÌURL Filter database with 35 million+ sitesin 96 categories and 65+ languagesÌApplication Control: Accurate signatures andLayer 7 patterns for thousands of applicationsÌDynamic application control based onproductivity or risk thresholdÌView traffic in real-time, choose to block or shapeÌMalware scanning: HTTP/S, FTP and web-based email via dual independent antivirus engines (Sophos & Avira) block all forms of viruses, web malware, trojans and spywareÌFully transparent HTTPS filtering of URLs*ÌOption for selective HTTPS Scanning of untrusted sites**ÌAdvanced web malware protectionwith JavaScript emulation*ÌLive Protection real-time in-the-cloud lookupsfor the latest threat intelligenceÌPotentially unwanted application (PUA) download blocking*ÌMalicious URL reputation filtering backed by SophosLabs ÌReputation threshold: set the reputation threshold awebsite requires to be accessible from internal networkÌActive content filter: File extension, MIME type,JavaScript, ActiveX, Java and FlashÌTrue-File-Type detection/scan within archive files**ÌYouTube for Schools enforcementÌSafeSearch enforcementÌGoogle Apps enforcement*Web PolicyÌAuthentication: Active Directory, eDirectory,LDAP, RADIUS, TACACS+ and local databaseÌSingle sign-on: Active Directory,eDirectory, Apple Open DirectoryÌProxy Modes: Standard, (Fully) Transparent, Authenticated, Single sign-on and Transparent with AD SSO*ÌTransparent captive portal with authenticationÌSupport for separate filtering proxies in different modesÌTime, user and group-based access policiesÌBrowsing quota time policies and quota reset option**ÌAllow temporary URL filter overrides with authentication ÌClient Authentication Agent for dedicated per-user tracking ÌCloning of security profilesÌCustomizable user-messages for events in local languages ÌCustom HTTPS verification CA supportÌSetup wizard and context sensitive online helpÌCustomizable block pagesÌCustom categorization to override categoriesor create custom categories*ÌSite tagging for creating custom site categories**ÌAuthentication and filtering options by device typefor iOS, Android, Mac, Windows and others*ÌPolicy testing tool for URLs, times,users and other parameters*Email ProtectionÌReputation service with spam outbreak monitoring based on patented Recurrent-Pattern-Detection technologyÌAdvanced spam detection techniques: RBL, heuristics,SPF checking, BATV, URL scanning, grey listing, RDNS/HELO checks, expression filter and recipient verification ÌBlock spam and malware during the SMTP transaction ÌDetects phishing URLs within e-mailsÌGlobal & per-user domain and address black/white lists ÌRecipient Verification against Active Directory accountÌE-mail scanning with SMTP and POP3 supportÌDual antivirus engines (Sophos & Avira)ÌTrue-File-Type detection/scan within archive files**ÌScan embedded mail formats: Block maliciousand unwanted files with MIME type checkingÌQuarantine unscannable or over-sized messagesÌFilter mail for unlimited domains and mailboxesÌAutomatic signature and pattern updatesÌSophos Live Anti-Virus real-time cloud lookups** Email Encryption and DLPÌPatent-pending SPX encryption for one-way message encryption*ÌRecipient self-registration SPX password management**ÌAdd attachments to SPX secure replies**ÌTransparent en-/decryption and digitalsigning for SMTP e-mailsÌCompletely transparent, no additionalsoftware or client requiredÌSupports S/MIME, OpenPGP, and TLS standardsÌPGP key server supportÌAllows content/virus scanning even for encrypted e-mails ÌCentral management of all keys and certificates- no key or certificate distribution requiredÌDLP engine with automatic scanning of emailsand attachments for sensitive data*ÌPre-packaged sensitive data type contentcontrol lists (CCLs) for PII, PCI, HIPAA, andmore, maintained by SophosLabs*Email ManagementÌUser-quarantine reports mailed outdaily at customizable timesÌLog Management service supportÌCustomizable User Portal for end-usermail management, in 15 languagesÌAnonymization of reporting data to enforce privacy policy ÌOver 50 Integrated reportsÌPDF and CSV exporting of reportsÌCustomizable email footers and disclaimersÌSetup wizard and context sensitive online helpÌEmail header manipulation support**End-User PortalÌSMTP quarantine: view and releasemessages held in quarantineÌSender blacklist/whitelistÌHotspot access informationÌDownload the Sophos Authentication Agent (SAA)ÌDownload remote access clientsoftware and configuration filesÌHTML5 VPN portal for opening clientless VPN connections to predefined hosts using predefined servicesÌDownload HTTPS Proxy CA certificatesVPNÌPPTP, L2TP, SSL, IPsec, HTML5-based and Ciscoclient-based remote user VPNs, as well as IPsec, SSL,Amazon VPC-based site-to-site tunnels and SophosRemote Ethernet Device (RED) plug-and-play VPNÌIPv6 SSL VPN support***VPN IPsec ClientÌAuthentication: Pre-Shared Key (PSK), PKI(X.509), Smartcards, Token and XAUTHÌEncryption: AES (128/192/256), DES, 3DES(112/168), Blowfish, RSA (up to 2048 Bit), DHgroups 1/2/5/14, MD5 and SHA-256/384/512ÌIntelligent split-tunneling for optimum traffic routingÌNAT-traversal supportÌClient-monitor for graphical overview of connection status ÌMultilingual: German, English and FrenchÌIPsec Tunnel BindingVPN SSL ClientÌProven SSL-(TLS)-based securityÌMinimal system requirementsÌProfile support for varying levels of accessÌSupports MD5, SHA, DES, 3DES and AESÌWorks through all firewalls, regardless of proxies and NAT ÌSupport for iOS and AndroidClientless VPNÌTrue clientless HTML5 VPN portal for accessingapplications securely from a browser on any device VPN One-ClickÌEasy setup and installations of every client within minutes ÌDownload of client-software, individual configurationfiles, keys and certificates one click away fromthe Security Gateway end-user portalÌAutomatic installation and configuration of the clientÌNo configuration required by end userVPN REDÌCentral Management of all REDappliances from Sophos UTMÌNo configuration: Automatically connectsthrough a cloud-based provisioning serviceÌSecure encrypted tunnel using digital X.509certificates and AES256- encryptionÌRED sites are fully protected by the Network, Weband Mail security subscriptions of the Central UTM.ÌVirtual Ethernet for reliable transfer ofall traffic between locationsÌIP address management with centrally definedDHCP and DNS Server configurationÌRemotely de-authorize RED devicesafter a select period of inactivityÌCompression of tunnel traffic* (RED50, RED 10 revision 2, 3)ÌVLAN port configuration options* (RED 50)ÌSupport for RED 15w with integrated 802.11n WiFi AP*** Secure Wi-FiÌSimple plug-and-play deployment,automatically appearing in the UTMÌCentral monitor and manage all access points (APs) and wireless clients through the built-in wireless controller ÌIntegrated security: All Wi-Fi traffic isautomatically routed through the UTMÌWireless 802.11 b/g/n at 2.4 GHz and 5GHz (AP 50)ÌPower-over-Ethernet 802.3af (AP 30/50)ÌMultiple SSID support: Up to 8ÌStrong encryption supports state-of-the-artwireless authentication including WPA2-Enterpriseand IEEE 802.1X (RADIUS authentication)ÌWireless guest Internet access with customizablesplash pages on your captive portalÌVoucher-based guest access for daily or weekly access ÌTime-based wireless network accessÌWireless repeating and bridging meshednetwork mode with AP 50ÌHotspot backend authentication support*(RADIUS, TACACS, LDAP, AD)ÌAutomatic channel selection background optimization**ÌMulti-tenant hotspot administration**ÌSupport for HTTPS login support**Web Application Firewall ProtectionÌReverse proxyÌURL hardening engineÌForm hardening engineÌDeep-linking controlÌDirectory traversal preventionÌSQL injection protectionÌCross-site scripting protectionÌDual-antivirus engines (Sophos & Avira)ÌHTTPS (SSL) encryption offloadingÌCookie signing with digital signaturesÌPath-based routingÌOutlook anywhere protocol supportÌReverse authentication (offloading) for form-basedand basic authentication for server access*ÌPersistent session cookie support***Web Application Firewall ManagementÌAuto server discovery scans attachednetworks and identifies web serversÌIntegrated load balancer spreadsvisitors across multiple serversÌPredefined firewall profiles for MicrosoftOutlook Web Access (OWA)ÌQuick server switch allows easy maintenanceÌSkip individual checks in a granular fashion as required ÌMatch requests from source networksor specified target URLsÌSupport for logical and/or operatorsÌAssists compatibility with various configurationsand non-standard deploymentsÌOptions to change WAF performance parameters**ÌUpload custom WAF rules**ÌScan size limit option**ÌAllow/Block IP ranges**ÌWildcard support for server paths**ÌAutomatically append a prefix/suffix for authentication** UTM Endpoint ProtectionÌWindows endpoint protection with SophosAntivirus and device controlÌOn-access, on-demand or scheduled scanningfor malware, viruses, spyware and TrojansÌPUA scanningÌLive Protection Antivirus provides real-time, in-the-cloud lookups for the latest threat intelligenceÌHIPS with suspicious behavior detectionÌWeb protection with malicious site protectionÌDownload scanningÌDevice control including removable storage, optical media, modems, Bluetooth, wireless, infrared and more * New in UTM Accelerated (9.2)** New in UTM Advantage (9.3)*** New in UTM Elevated (9.4)ÌWeb in Endpoint enforcement of web policy and webmalware scanning on the endpoint with full policyand reporting synchronization with the UTMUTM Endpoint ManagementÌFully managed within the UTMÌEasy deployment from the UTM using using our installer ÌMonitor connected endpoints, threat statusand device utilization with full log accessÌAlerts for infected endpoints*SEC Endpoint Integration*ÌI ntegration with Sophos Enterprise ConsoleEndpoint Management provides UTM webpolicy and reporting for Web in EndpointLogging and ReportingÌLogging: Remote syslog, nightly rotation, email/ftp/SMB/SSH archiving and log management serviceÌOn-box reporting: Packet filter, intrusion protection,bandwidth and day/week/month/year scalesÌIdentity-based reportingÌPDF or CSV report exportingÌE xecutive report scheduling and archivingÌR eactive reporting engine crafts reports as you click on data ÌS ave, instantly email or subscribe recipients to any reports ÌP DF and CSV exporting of reportsÌN ightly compression and rotation of logsÌL og file archiving: On-box, FTP, SMB, SSH, Email and Syslog ÌH undreds of on-box reportsÌD aily activity reportingÌU RL filter override reportÌP er-user tracking and auditingÌA nonymization of reporting data to enforce privacy policy ÌF ull transaction log of all activity in human-readable formatUnited Kingdom and Worldwide Sales Tel: +44 (0)8447 671131Email:****************North American SalesToll Free: 1-866-866-2802Email:******************Australia and New Zealand SalesTel: +61 2 9409 9100Email:****************.auAsia SalesTel: +65 62244168Email:********************Oxford, UK | Boston, USA© Copyright 2016. Sophos Ltd. All rights reserved.Registered in England and Wales No. 2096520, The Pentagon, Abingdon Science Park, Abingdon, OX14 3YP, UK Sophos is the registered trademark of Sophos Ltd. All other product and company names mentioned are trademarks or registered trademarks of their respective owners.1129-02.13DD.dsna.simple。
ORTHOPHOS XG 5 DS CEPH-CH
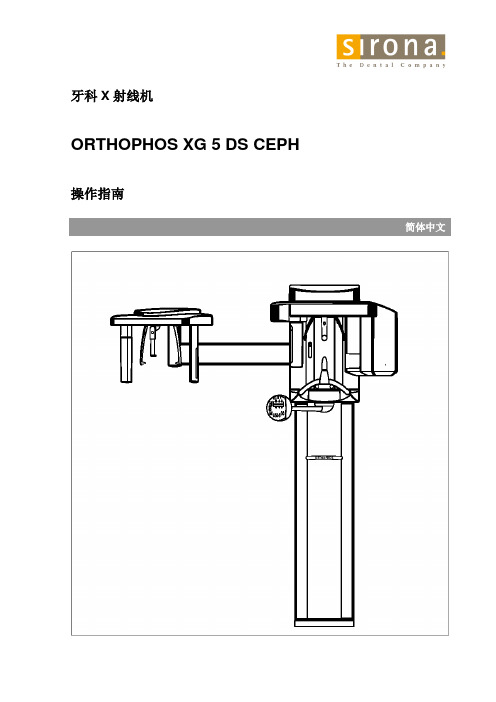
牙科X射线机ORTHOPHOS XG 5 DS CEPH操作指南简体中文德国西诺德牙科设备有限公司ORTHOPHOS XG 5 DS / Ceph 操作指南60 04 746 D3352 D3352.201.03.09.022概要亲爱的客户:维修保养: 欣悉阁下购置新型牙科X 射线机ORTHOPHOS XG 。
采用数码成像技术拍摄标准视图(颌部),鼻窦视图(上颌窦区)以及颞下颌关节视图已成为可能。
如果该系统配备侧位单元延长臂,您还可以利用数码成像技术获得头部测量图像。
兹特奉上本机技术资料一套,以便随时、迅速查阅之需。
为维护阁下的保修权,请在设备安装之后与技术服务工程是一同填写随机附带的“安装协议/保修卡”进行登记。
请在对患者进行X 光拍摄前详细阅读本操作指南以熟悉本机。
遵守辐射防护守则以及安全须知。
本操作指南与SIDEXIS 软件非常类似。
根据德意志联邦共和国X 光相关法令规定,X 光系统用户必须对设备定期执行稳定性测试,以确保患者和操作人员的安全。
ORTHOPHOS XG 5机组为确保患者、操作者以及第三方的安全和健康,必须定期进行设备检测及预防性维修,以确保设备操作安全及功能可靠(执行IEC 601-1 / DIN EN 60601-1等标准)。
操作者有责任确认检测维修工作的执行。
一旦操作者忘记履行执行检测维修的义务,或者忽略了错误信息,由此造成的设备损坏,德国西诺德牙科设备有限公司及其授权经销商不承担责任。
注册证号:国食药监械(进)字2008第2303722号 标准编号:YZB/GEM 4911-2008售后服务:西诺德牙科设备商贸(上海)有限公司德国西诺德牙科设备有限公司ORTHOPHOS XG 5 DS / Ceph操作指南60 04 746 D3352D3352.201.03.01.023 目录1警示标志和安全信息 (5)1.1安全信息概述 (5)1.2ESD保护措施 (8)1.3关于静电放电的物理性质 (9)2技术说明 (10)3控制器和功能组件 (14)3.1控制器和显示屏 (14)4全景单元附件 (17)4.1支座和支架 (17)4.2插入颞下颌关节支架的要点 (18)4.3全景单元防护罩 (19)4.4侧位单元防护罩 (20)5全景单元程序组 (21)5.1P1标准全景视图 (21)5.2P1L标准全景视图—左半侧 (22)5.3P1R标准全景视图—右半侧 (23)5.4P1A标准全景视图—伪影消减 (24)5.5P1C1.25倍固定放大倍率标准全景视图 (25)5.6P10大幅降低辐射剂量专用于儿童的标准视图 (26)5.7P12断层厚度——前牙区 (27)5.8TM1.1/TM1.2闭口位与张口位在同一图像中显示的颞下颌关节侧视图 (28)5.9S1副鼻窦 (29)5.10TS1轴向加厚断层(后牙区) (30)6操作 (31)6.1照射准备 (31)6.2患者定位 (33)6.3准备完毕(全景视图) (41)6.4设置照射参数 (42)6.5重新编程设置K V/M A匹配值 (42)6.6触发照射 (43)6.7遥控器 (45)7侧位照射(侧位) (46)7.1侧位照射准备(侧位程序) (46)7.2侧位单元准备 (48)7.3对侧位患者进行定位 (49)7.4触发侧位照射 (54)8信息与技术支持菜单 (56)8.1信息菜单 (56)8.2技术支持菜单 (56)9程序值 (57)德国西诺德牙科设备有限公司ORTHOPHOS XG 5 DS / Ceph 操作指南60 04 746 D3352D3352.201.03.09.0249.1 全景视图——列表2A 程序值 ················································································· 57 9.2 全景视图——列表4A 程序值 ················································································· 58 9.3 侧位图像程序值 ·································································································· 59 9.4 头部测量图像程序值 ···························································································· 60 10信息列表 (61)10.1 帮助信息列表 (61)10.2 错误信息格式 ..................................................................................................... 62 10.2.1 错误信息代码具有下列格式 ......................................................................................................... 62 10.2.2 Ex ..................................................................................................................................................... 62 10.2.3 yy ...................................................................................................................................................... 63 10.2.4 zz ...................................................................................................................................................... 63 11 外表面处理 ........................................................................................................ 64 12 检测及维修 ........................................................................................................ 65 12.1 由操作人员或其他经过授权的人员执行年度检查 ........................................................ 65 12.2 由技术服务工程师进行维修保养 ............................................................................. 65 12.3 检查图像质量 .. (65)德国西诺德牙科设备有限公司ORTHOPHOS XG 5 DS / Ceph操作指南60 04 746 D3352D3352.201.03.01.02 51警示标志和安全信息1.1 安全信息概述识别警示标志和安全信息符号使用预期使用保养与维修系统改造与其他设备相组合通风孔对患者进行X光照射为防止人员伤害及设备损坏,您必须阅读本操作指南中的安全须知。
Sophos 杀毒软件竞争对比分析报告 杀毒软件竞争对比分析报告
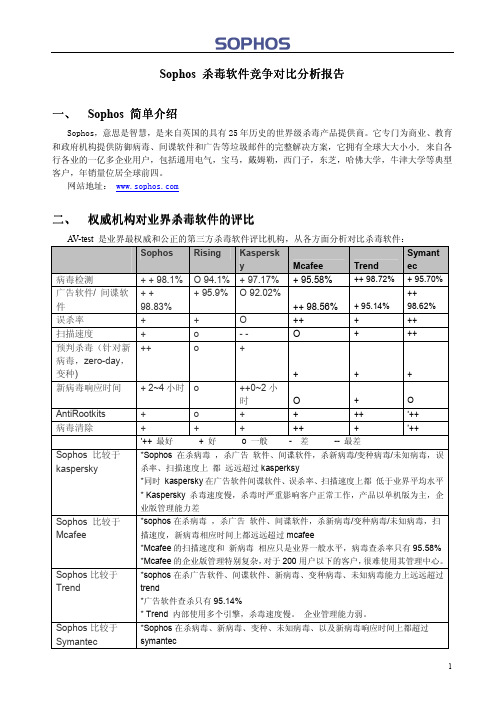
Symantect Endpoint Protection 11.0
可用性及管理
可视性
有效性(基本)
有效性(zero-day)
性能
总体
快速总结
McAfee Total
Sophos Endpoint
Protection for
Security and Control
Enterprise在Active 是一款设计很好的产
关键字: 差, 清楚
一般
好
优秀
四、 为什么选择 Sophos
20 多年病毒防御经验 全球 1 亿多客户的选择
公 司 实 力 全球销量前三的安全软件公司
2
强大
杀毒能力 强劲 安全防护 功能完整 集成的网 络准入控 制(NAC)
强大的集 中控管
简单,易 用
全线安全 产品
专注于企业、教育、政府客户,不向个人用户零售 单引擎提供防御病毒、广告软件、间谍软件、未知病毒、HIPS、应用程序控制 2008 年最新 AV-test 测试中,唯一一家在病毒、广告软件、间谍软件、未知病毒、变种 病毒、新病毒各方面都获得”++”顶级鉴定的安全软件 扫描速度快 全盘扫描时,不影响用户正常工作 专利缓存决策技术:用户重复扫描硬盘时,只扫描必要文件,速度非常快 完美防御最新的 U 盘病毒等恶性病毒 应用程序控制:监控或阻止客户端使用 QQ、Skype、eDonkey、游戏等数百种应用 设备控制:监控或阻止客户段使用软盘、U 盘、光驱、蓝牙、wifi 等移动设备,避免机 密数据流失 HIPS 运行时行为分析:实时检测可疑行为及缓冲区溢出,阻断可以进程或仅报告给管 理员。 监测并评估客户端安全水平(windows 补丁,杀毒软件状态,个人防火墙状态),不符 合要求者,隔离处理。 支持应用代理和 Web 代理,支持 DHCP 隔离 纯软件产品,安装简单,不需要改动任何已有网络硬件。 提供整个网络安全漏洞报告 一个管理窗口下,同时管理监控多达数十万客户端 支持 Windows、MAC、Linux 的同时监控 支持总部—分公司---客户端级联环境,内外网隔离环境 管理面板实时显示各客户端的状态:是否染毒,病毒名称,病毒样本更新情况,防火墙 状态,是否在使用受控应用程序和受控设备,策略是否一致,其他错误和提示信息 管理中心可以远程控制客户端:下发最新策略,更新样本库,全盘扫描,清除已发现病 毒等 支持客户端分组,可以以组的方式,控制组内所有客户端 提供灵活的报告,分析某时间段、某些客户端的染毒情况,支持导出为 pdf,html,xls 等 格式 支持 Active directory 自动部署 ,客户端不用做任何事 管理中心生成企业定制的安装包,客户端只需获得安全包,点击“下一步”或“确定”, 无需其它任何配置,即可部署完以上所有功能。
罗森商空产品介绍

罗森商空产品介绍卤钨灯系列卤钨灯俗称“石英灯”,是在白炽灯内填充卤化物,壳使用石英玻璃的光源。
其寿命比普通白炽灯长,光效和色温比普通白炽灯高。
卤钨灯的基本性能1.光效:20~30lm/W2.色温:2900~3200K,暖色调3.显色性:1004.最大功率:10000W5.平均寿命:2000~5000小时6.亮度:整个寿命期光通输出稳定,寿终时光通量仍可达到初始值的95%,可调节7.低压:配变压器一起使用卤钨灯用途1.双端灯:泛光,广告和区域等室外照明2.单端灯:室内照明应用领域,象商场,酒店,旅馆,家居等的重点和装饰照明,办公室,阅览室的局部照明,这些地方主要考虑较高显色性,暖色调和调光的要求照明用卤钨灯和反射定向照明卤钨灯广泛用于家庭照明、商业照明、艺术照明中,能在较小的立体角范围内获得较高的光强,它的主要照射角度可分为10°、25°、38°、60°四种,也就是窄光、中光、宽光、超宽光四种配光。
在玻壳内涂有二氧化硅—二氧化钛等硬膜,耐温好,使用寿命长。
石英玻璃一个显著优点是有高的透明度和好的抗热冲击性能,工作温度高(达到900摄氏度),光学透过特性好,照明用卤钨灯根据灯丝的绕制方式分为横丝和直丝两种,我司主要采用直丝灯珠。
其插脚的材料根据不同的用途也有钼脚和镍脚两种。
需焊接加工的,必须采用镍脚。
我司有JL-XXXX、NL-XXXX、ML-XXXX系列产品。
反射定向照明卤钨灯根据外型尺寸分为MR11(D=35)和MR16(D=50)两种类型,其中MR11有20W、35W两个规格,MR16有20W、35W、50W三种规格。
并有加玻璃盖和不加玻璃盖之分,玻璃盖又有平盖、凸盖之分,我司的灯杯产品所加玻璃盖均为平面钢化玻璃盖,采用德国进口灯丝,特加厚镀膜技术,防紫外线功能,高显色性,使用寿命达3000小时以上射灯,优点为灯珠的玻璃外壳为石英所制,故耐高温,热稳定性好,灯杯使用了反光镜聚焦原理,因此光集中,还原性好。
Sophos SG系列产品列表v1.0

无线标准 (只有W模式支持) 802.11b/g/n 2.4GHz
SG105/105W
4*1Gbe电口
SG115/115W
4*1Gbe电口
802.11b/g/n 2.4GHz
SG125
8*1Gbe电口
SG135
1Gbe电口
SG210
防火墙吞吐量11Gbps 6*1Gbe电口;一个模块(可插8*1 VPN吞吐量1Gbps Gbe电口或8*1Gbe IPS吞吐量2Gbps SFP口,或2*10Gbe SFP+) 防病毒吞吐量500Mbps 防火墙吞吐量13Gbps 6*1Gbe电口;一个模块(可插8*1 VPN吞吐量2Gbps Gbe电口或8*1Gbe IPS吞吐量3Gbps SFP口,或2*10Gbe SFP+) 防病毒吞吐量800Mbps 8*1Gbe电口,2*1Gbe 防火墙吞吐量17Gbps SFP口;一个模块(可插8*1Gbe电 VPN吞吐量3Gbps 口或8*1Gbe SFP口,或2*10Gbe IPS吞吐量5Gbps SFP+) 防病毒吞吐量1.2Gbps 8*1Gbe电口,2*1Gbe 防火墙吞吐量20Gbps SFP口;一个模块(可插8*1Gbe电 VPN吞吐量4Gbps 口或8*1Gbe SFP口,或2*10Gbe IPS吞吐量6Gbps SFP+) 防病毒吞吐量1.5Gbps 防火墙吞吐量25Gbps 8*1Gbe电口;两个模块(可插8*1 VPN吞吐量4Gbps Gbe电口或8*1Gbe IPS吞吐量7Gbps SFP口,或2*10Gbe SFP+) 防病毒吞吐量2Gbps 防火墙吞吐量27Gbps 8*1Gbe电口;两个模块(可插8*1 VPN吞吐量5Gbps Gbe电口或8*1Gbe IPS吞吐量8Gbps SFP口,或2*10Gbe SFP+) 防病毒吞吐量2.5Gbps 防火墙吞吐量40Gbps 8*1Gbe电口;两个模块(可插8*1 VPN吞吐量8Gbps Gbe电口或8*1Gbe IPS吞吐量12Gbps SFP口,或2*10Gbe SFP+) 防病毒吞吐量3.5Gbps
Sophos XG Firewal - 设备注册与MySophos

40
点击查看网络防护
• 网络防护中的主要内容是:
○ ○ ○ ○
查看设备 注册设备 固件更新 下载安装包
SOPHOS TRAINING
41
网络防护中查看设备
• 查看设备:
SOPHOS TRAINING
42
网络防护中注册设备
• 注册设备:
SOPHOS TRAINING
43
© Sophos Ltd. All rights reserved.
SOPHOS TRAINING
25
Network Configuration Wizard
• Configure settings for email notifications
SOPHOS TRAINING
26
Network Configuration Wizard
• Set date, time and NP configuration
• 网络配置向导 • 部署模式一:网关模式; • 部署模式二:桥模式
SOPHOS TRAINING
11
初始化XG Firewall向导-网络
○ ○ ○
配置接口Lan 配置接口Wan 配置DNS
SOPHOS TRAINING
12
注册
• 从设备注册
○ ○
建立您自已的SophosID
‒ https:///mysophos/注册
• Built-in wizard for ease of deployment
SOPHOS TRAINING
21
Network Configuration Wizard
• Select deployment mode
SOPHOS TRAINING
Sophos XG系列硬件设备操作说明书

Operating InstructionsXG 105(w)/115(w)/125(w)/135(w) Rev. 3/XG 106(w) Rev.1ForewordWe are pleased to welcome you as a new customer of our Sophos XG appliances.To install and configure the hardware appliance you can use the following documents:ÌHardware Quick Start Guide: Connection to thesystem peripherals in a few stepsÌOperating Instructions: Notes on the security andcommissioning of the hardware applianceÌAdministration Guide: Installing and configuring the software applianceThe Hardware Quick Start Guide and the Safety Instructions are also deliveredin printed form together with the hardware appliance. The instructions must be read carefully prior to using the hardware and should be kept in a safe place.You may download all user manuals and additional documentation from the support webpage at: /supportSecurity SymbolsThe following symbol and its meaning appears in the Hardware Quick Start Guide, Safety Instructions and in these Operating Instructions.Caution and Important Note. If these notes are not correctly observed:ÌThis is dangerous to life and the environmentÌThe appliance may be damagedÌThe functions of the appliance will be no longer guaranteedÌSophos shall not be liable for damages arising from afailure to comply with the Safety InstructionsDesigned UseThe hardware appliances are developed for use in networks.The XG 105(w)/106(w)/115(w)/125(w)/135(w) models may be operated asa standalone appliance. The hardware appliance can be used in commercial, industrial and residential environments.The XG 105(w)/106(w)/115(w)/125(w)/135(w) models belong to the appliance group B.The hardware appliance must be installed pursuant to the current installation notes. Otherwise failure-free and safe operation cannot be guaranteed. The EU declaration of conformity is available at the following address:Sophos Technology GmbHAmalienbadstr. 41/Bau 5276227 KarlsruheGermanyCE Labeling, FCC and ApprovalsThe XG 105(w)/106(w)/115(w)/125(w)/135(w) appliances comply with CB, CE, FCC Class B, ISED, VCCI, RCM, UL, CCC, and BIS.Important Note: For computer systems to remain CE and FCC compliant, only CE and FCC compliant parts may be used. Maintaining CE and FCC compliance also requires proper cable and cabling techniques.Operating Elements and ConnectionsXG 105(w)/115(w)*(Rev. 3)/XG 106(w) Rev.1Status LEDs (w-model has additional Wi-Fi LED)1 x COM (RJ45)2 x USB 2.0 1 x Micro USB4 x GbE copper port1 x GbE SFP (shared)1 x HDMI Power Supply Connector for optional 2nd redundant power supply2 x external antenna(XG 125w and XG 135w only)XG 125(w)/135(w)*(Rev. 3)Status LEDs (w-model has additional Wi-Fi LED)1 x COM(RJ45)3 x external antenna(XG 125w andXG 135w only)2 x USB 2.08 x GbE copper port Power Supply Optional 2nd redundant power supply1 x MicroUSB1 x HDMI Expansion bay (shown with optionalmodule incl. 2 antennas)1 x GbE SFP * The displayed front images are of the XG 115 and 135 device. The displayed back images are of the XG 115w device and the XG 135w. Devices may vary slightly.LED StatusSpeed (Right LED)Amber On The Ethernet port is operating at 1,000 Mbps. Green On The Ethernet port is operating at 100 Mbps.Off The Ethernet port is operating at 10 Mbps.Speed(Right LED)Amber On The Ethernet port is operating at 1,000 MbpsPutting into OperationCaution: Risk of explosion if battery is replaced by an incorrect type. Dispose of used batteries according to the instructions.Scope of SupplyThe supplied parts are indicated in the Hardware Quick Start Guide. Mounting InstructionsThe XG 105(w)/106(w)/115(w)/125(w)/135(w) appliances can be placed on a stable horizontal surface or can be mounted to a rack or you can hang it on the wall by using the optionally available rackmount kit.Warnings and PrecautionsThe appliance can be operated safely if you observe the following notes and the notes on the appliance itself.Rack PrecautionsÌEnsure that the leveling jacks on the bottom of the rack are fullyextended to the floor with the full weight of the rack resting on them.ÌIn single rack installation, stabilizers should be attached to the rack.ÌIn multiple rack installations, the racks should be coupled together.ÌAlways make sure the rack is stable beforeextending a component from the rack.ÌYou should extend only one component at a time—extending two ormore simultaneously may cause the rack to become unstable.General Server PrecautionsÌReview the electrical and general safety precautions that camewith the components you are adding to your appliance.ÌDetermine the placement of each component inthe rack before you install the rails.ÌInstall the heaviest server components on thebottom of the rack first, and then work up.ÌAllow the hot plug hard drives and power supplymodules to cool before touching them.ÌAlways keep the rack‘s front door, all panels and server componentsclosed when not servicing to maintain proper cooling.Rack Mounting ConsiderationsÌAmbient operating temperature: If installed in a closed or multi-unit rack assembly, the ambient operating temperature of the rack environmentmay be greater than the ambient temperature of the room. Therefore,you should install the equipment in an environment compatiblewith the manufacturer’s maximum rated ambient temperature.ÌReduced airflow: Equipment should be mounted intoa rack with sufficient airflow to allow cooling.ÌMechanical loading: Equipment should be mounted into a rack so that a hazardous condition does not arise due to uneven mechanical loading.ÌCircuit overloading: Consideration should be given to the connectionof the equipment to the power supply circuitry and the effect that anypossible overloading of circuits might have on overcurrent protectionand power supply wiring. Appropriate consideration of equipmentnameplate ratings should be used when addressing this concern.ÌReliable ground: Reliable grounding must be maintained at all times.To ensure this, the rack itself should be grounded. Particular attentionshould be given to power supply connections other than the directconnections to the branch circuit (i.e., the use of power strips, etc.).Connection and ConfigurationHow to connect the appliance is described in the Hardware Quick Start Guide. For configuration you can follow the initial setup wizard described in the WebAdmin Quick Start Guide or cancel it and perform a manual setup (see the Sophos XG Firewall Administrator Guide).SFP PortThe XG1xx rev.3 and XG 106(w) rev.1 models provide a SFP port allowing you to either insert a SFP Mini-GBIC (transceiver) to connect to a 1 GbE fiber or copper cable or to insert a VDSL2 SFP modem to directly connect to a VDSL line (via a RJ11 cable).These modules are not delivered with the appliance but available through your Sophos partner.Please note that there are different Mini-GBIC module types. The required type is determined by the existing network. The following SFP GBIC module types may be used:SFP:1000 Base-TIEEE 802.3 - 1 Gbit/s via Ethernet cable. An Ethernet cable category 5 covers a maximum distance about 100 meters.1000 Base-SXIEEE 802.3 - 1 Gbit/s via fiberglass. Multi-mode fiberglass cables (MMF) cover a distance of 200 m to 550 m.1000 Base-LXIEEE 802.3 - 1 Gbit/s via fiberglass. Here, exclusively singlemode-fiber glass is used. This transmission option covers approximately 10 km.Expansion ModulesThe XG 125(w)/135(w) support an additional expansion module allowing you to insert an optional 3G/4G or Wireless module (on XG 135w only). These modules are not delivered with the appliance but available through your Sophos partner. Please note that there are different 3G/4G modules available depending on the region you want to operate it in Americas/EMEA and APAC.Please see table below for further details.For installing the module please read the mounting instructions which are shipped with each module.Serial ConsoleYou can connect a serial console to either of the COM ports of the Sophos XG hardware appliances. You can use, for instance, the Hyperterminal terminal program which is included with most versions of Microsoft Windows to log on to the appliance console. Use an RJ45 to DB9 adapter cable or the provided USB cable to connect the console to your hardware appliance.The required connection settings are:ÌBits per second: 38,400ÌData bits: 8ÌParity: N (none)ÌStop bits: 1Access via the serial console is activated by default on ttyS1. The connections of the appliances and the respective functionality are listed in chapter “Operating Elements and Connections.”United Kingdom and Worldwide Sales Tel: +44 (0)8447 671131Email:****************North American SalesToll Free: 1-866-866-2802Email:******************Australia and New Zealand SalesTel: +61 2 9409 9100Email:****************.auAsia SalesTel: +65 62244168Email:********************© Copyright 2018. Sophos Ltd. All rights reserved.Registered in England and Wales No. 2096520, The Pentagon, Abingdon Science Park, Abingdon, OX14 3YP, UK Sophos is the registered trademark of Sophos Ltd. All other product and company names mentioned are trademarks or registered trademarks of their respective owners.。
sophos防火墙操作手册

Sophos防火墙操作手册一、简介Sophos防火墙是网络安全领域的一款强大产品,能够为企业和个人用户提供全面的网络防护。
本操作手册旨在为用户提供Sophos防火墙的基本操作和使用指南。
二、安装与配置1、硬件和软件要求:确保您的系统满足Sophos防火墙的最低硬件和软件要求。
下载并安装Sophos防火墙软件。
2、配置网络接口:根据您的网络环境,正确配置网络接口。
3、设置管理账户:创建一个具有适当权限的管理账户以便进行后续操作。
三、基本操作1、登录Sophos防火墙管理界面:使用管理账户登录防火墙管理界面。
2、查看防火墙状态:查看防火墙的运行状态、网络流量等信息。
3、配置网络规则:根据需要设置入站和出站网络的规则,包括允许或拒绝特定IP、端口等。
4、配置安全策略:创建安全策略以定义在不同情境下如何处理网络流量。
5、更新与升级:定期检查并安装防火墙的更新和升级,以确保安全性。
四、高级操作1、配置VPN:设置虚拟私人网络(VPN),以便远程用户安全地访问公司网络。
2、配置入侵检测与防御:启用并配置入侵检测与防御功能,提高网络安全防护能力。
3、配置应用控制:控制网络流量,以阻止不必要的应用程序访问网络。
4、自定义日志:根据需求,自定义日志记录,以便于问题排查和审计。
5、多防火墙管理:使用中央管理控制台管理多个Sophos防火墙,实现统一配置和管理。
五、故障排除与支持1、查看日志文件:查看防火墙的日志文件,以便发现和解决潜在问题。
2、使用支持服务:如有需要,可联系Sophos技术支持以获得帮助。
3、软件故障排除:尝试重新启动防火墙或重新安装软件以解决常见故障。
4、网络问题排查:检查网络连接、接口配置等,以确保网络正常运行。
六、注意事项1、安全更新:始终保持防火墙软件为最新版本,以获取最新的安全更新和补丁。
2、定期审查:定期审查防火墙规则和安全策略,以确保其仍然符合组织的安全需求。
3、文档记录:记录所有防火墙配置和更改,以便于后续审计和故障排查。
HUDSON全线产品概述

小容量喷雾器
用于药液的雾化吸入,适用于医院和家庭中治疗气道 阻塞症状.
28
深呼吸训练器
用于激发、促进病人深呼吸及咳嗽,预防、 治疗肺不张(用于心胸外科手术前或后)
8884719025
29
8884717301
呼吸回路及附件
用于在呼吸治疗时机械通气的管道
30
麻醉面罩
用于气体麻醉时佩戴于病人口鼻处,输送麻醉气体到 呼吸道.
带有注药接口,可局部滴注麻醉剂。 医用等级/热敏性PVC材料 高容量/低压气囊 经口/经鼻 15mm标准连接接口 圆滑无损伤尖端 贯穿导管全长的不透X线标记 深度指示标记 不含乳胶成份 无菌包装
(5-205xx)
15
双腔支气管插管
(5-161xx/5-160xx)
产品培训
1
SHERDIDAN 气管插管
2
产品特点
包装可见尺寸标记 清晰可见的深度标记 不透X线标记线贯穿导管全长 热敏性、医用等级PVC材料制成 无菌:5年有效期 高容量/低压力 气囊壁薄/顺应性好
带有Murphy孔 指示球有自封阀,指示球对气囊的变化敏感。
3
8
为满足特殊外科手术需求而设计 医用等级/热敏性PVC材料 高容量/低压气囊 经口/经鼻 带有Murphy孔 15mm标准连接接口 圆滑无损伤尖端 贯穿导管全长的不透X线标记 深度指示标记 不含乳胶成份 无菌包装
加强型气管插管
医用等级/热敏性PVC材料 加强的管腔 高容量/低压气囊 经口/经鼻 带有Murphy孔 15mm标准连接接口 圆滑无损伤尖端 不透X线标记 深度指示标记 不含乳胶成份 无菌包装
SOPHOS 加密产品介绍

DL 和
PC端口控制
SafeGuard Enterprise 模块
SafeGuard 管理中心 (Management Center)
贯彻和执行普遍的、全机构的安 全策略结构,在各种IT环境中提 供一个管理控制的中心点
SafeGuard 设备加密 (Device Encryption)
对笔记本电脑、台式电脑及外部 媒体上的数据进行透明加密,保 护用户数据免遭未授权的访问、 丢失或窃取
堪称移动数据保护领域魔术象限(Magic Quadrant) 的领袖 “愿景完整性(Completeness of Vision)” 得分最高
一般标准 EAL 3+
FIPS 140-2 认证的加密技术
2008/09 至 2009/10 年度获得五星 级评分(满分) “一个非常棒的企业产品,拥有大量 的实用功能” “安装…简单” “性能良好”
*未来发布。现在这个功能由 SafeGuard LAN Crypt 提供。
美国,波士顿 | 英国,牛津 2010版权所有。Sophos Plc. 保留所有权利。所有商标均为各自所有者拥有。
ds/100305
您数据加密和保护的中央密钥
SafeGቤተ መጻሕፍቲ ባይዱard Enterprise 提供多层级的终端数据保护,这种保护结合了加密和 数据泄漏防护 (DLP) 。中央管理解决方案保护台式电脑、笔记本电脑、PDA、智能 手机及可移动媒体上的数据安全。其透明数据加密提高了用户的工作效率,同时还 可防止恶意用户读取丢失的或失窃的媒体。 SafeGuard Enterprise 通过控制访问 物理及无线接口(例如USB、FireWire、Wi-Fi)和存储设备(例如MP3播放器、可 移动媒体)防止终端数据泄漏。
Sonos 产品说明书

Important Product InformationTHIS DOCUMENT CONT AINS INFORMATION THAT IS SUBJECT TO CHANGE WITHOUT NOTICE.No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including but not limited to photocopying, recording, information retrieval systems, or computer network without the written permission of Sonos, Inc.SONOS and all other Sonos product names and slogans are trademarks or registered trademarks of Sonos, Inc. SONOS Reg. U.S. Pat. & Tm. Off.Sonos products may be protected by one or more patents. Our patent-to-product information can be found here: /legal/patents.Apple, AirPlay®, Apple Music™, iPad®, iPhone®, iPod®, iT unes®, and OS X® are trademarks of Apple Inc., registered in the U.S. and other countries. Use of the Works with Apple badge means that an accessory has been designed to work specifically with the technology identified in the badge and has been certified by the developer to meet Apple performance standards.Windows® is a registered trademark of Microsoft Corporation in the United States and other countries.Android® is a trademark of Google Inc.Manufactured under license from Dolby Laboratories. Dolby, Dolby Audio, Pro Logic, and the double-D symbol are trademarks of Dolby Laboratories.Amazon, Kindle, Kindle Fire, Echo, Alexa, and all related logos are trademarks of , Inc. or its affiliates. Bluetooth® is a registered trademark of Bluetooth SIG, Inc.The terms HDMI and HDMI High-Definition Multimedia Interface, and the HDMI logos are trademarks or registered trademarks of HDMI Licensing LLC in the United States and other countries.Sonos uses MSNTP software, which was developed by N.M. Maclaren at the University of Cambridge.© Copyright, N.M. Maclaren, 1996, 1997, 2000; © Copyright, University of Cambridge, 1996, 1997, 2000.All other products and services mentioned may be trademarks or service marks of their respective owners.© 2004-2019 by Sonos, Inc. All rights reserved.T echnical Support•Web site•Visit our Web site at /support. There you can visit our Forums, browse our Frequently Asked Questions (FAQ) pages, or request assistance.•Email•*****************Sonos1 License Agreement and Limited Warranty(U.S. and rest of world, excluding Europe)Sonos, Inc.READ THE TERMS OF THIS LICENSE AGREEMENT AND LIMITED WARRANTY ("AGREEMENT") GOVERNING THE USE OF THE SOFTWARE AND RELATED FIRMWARE AND DOCUMENTATION (COLLECTIVEL Y, THE "SOFTWARE") PROVIDED TO YOU BY SONOS ("SONOS") CAREFULL Y BEFORE USING THE APPLICABLE SONOS PRODUCT (SUCH HARDWARE, TOGETHER WITH THE SOFTWARE, REFERRED TO AS THE "PRODUCT").BY OPENING THIS PACKAGE, INSTALLING AND USING THE PRODUCT, YOU ARE (1) REPRESENTING THAT YOU ARE OVER THE AGE OF 18, (2) REPRESENTING THAT YOU HAVE THE RIGHT AND AUTHORITY TO LEGALL Y BIND YOURSELF OR YOUR COMPANY, AS APPLICABLE, AND (3) CONSENTING TO BE LEGALL Y BOUND BY ALL OF THE TERMS OF THIS AGREEMENT. IF YOU DO NOT AGREE TO ALL THESE TERMS OR CANNOT MAKE SUCH REPRESENTATIONS, DO NOT USE THE PRODUCT. IF YOU ELECT NOT TO ACCEPT THE TERMS OF THIS AGREEMENT, YOU MAY RETURN THE NEW, UNUSED PRODUCT WITHIN THIRTY (30) DAYS OF PURCHASE TO THE RETAIL LOCATION WHERE YOU PURCHASED IT, WITH ALL ORIGINAL PACKAGING FOR A FULL REFUND.1.GRANT OF LICENSE(a) Subject to the terms and conditions of this Agreement, Sonos grants to Y ou a worldwide, non-exclusive, non-transferable, personal license (without the right to sub-license) to (i) use the Software as embedded in the Product for the purpose of operating the Product, and (ii) use the desktop application portion(s) of the Software on any personal computer owned or controlled by Y ou during the T erm. Except as provided above, Y ou may not transfer the Software to any other computing device or otherwise remove the Software from the Product. Notwithstanding any license granted herein by Sonos, Y ou acknowledge and agree that it is Y our sole responsibility to comply with U.S. and international copyright laws with respect to Y our use of the Software.(b) Y ou agree not to copy, modify, reverse engineer, decompile or disassemble the Product to the extent that such restriction is not prohibited by law. Except for the limited license granted herein, Sonos and its suppliers hereby retain all right, title and interest in and to all worldwide intellectual property rights embodied in the Software. All other rights are reserved by Sonos. Y ou acknowledge and agree that the technology embedded in and used to create the Product constitute the valuable trade secrets and know-how of Sonos, and to the extent you discover any such trade secrets, Y ou will not disclose them to any third party.(c) Sonos shall have no obligation to provide any updates or upgrades to the Product, but in the event that it does, such updates, upgrades and any documentation shall be deemed the "Product", and shall be subject to the terms and conditions of this Agreement.2.TERM OF AGREEMENT(a) Y ou may terminate this Agreement at any time by notifying Sonos, discontinuing use of the Product and purging the Software from Y our computing device.(b) This Agreement will automatically terminate if Y ou violate any of its terms.(c) Sections 1(b), 3, 4, 6(c), 7 and 9 shall survive termination or expiration for any reason.PLIANCE WITH COPYRIGHT LAWSSonos complies with U.S. and international copyright laws and in consideration of the licenses granted herein, Y ou agree to do the same. Y ou acknowledge that unauthorized copying or distribution of music or other content accessed using the Product ("Content") is prohibited by such copyright laws, and Y ou agree that Y ou2Important Product Information will not, directly or indirectly, copy or distribute any Content without the express written authorization of the copyright holder. Y ou agree to indemnify and hold harmless Sonos and its licensors from and against any and all claims, suits, losses, damages, liabilities, costs and expenses incurred by Sonos or its licensors arising out of or related to Y our failure to comply with the terms of this Section 3.4.SONOS PRIVACY POLICYUse of Sonos Products is subject to the Sonos Privacy Policy, which can be found at/legal/privacy_policy.htm and by reference is made a part of this Agreement. The Sonos Privacy Policy outlines the type of information that may be collected from you by Sonos and how such information may be used by Sonos. It is important that you read and understand the terms of the Privacy Policy.5.THIRD PARTY CONTENT AND TECHNOLOGIES SUPPORTFrom time to time, Sonos may provide access to third party content providers via the Product. In addition, Sonos may support certain third party technologies, such as specific file formats or codecs. Sonos reserves the right to discontinue access to and/or support for such third party content or technologies at any time, and for any reason. Sonos makes no representations or warranties whatsoever regarding the selection of, or continuing support for, any such third party content or technologies.6.WARRANTY AND DISCLAIMER(a) Limited Warranty. Sonos warrants to Y ou that for a period of one (1) year after the date of original purchase of the Product, the Product will be free from defects in materials and workmanship. SONOS DOES NOT WARRANT THAT THE PRODUCT WILL OPERATE WITHOUT INTERRUPTION OR WILL BE ERROR-FREE, OR THAT ALL ERRORS MAY BE CORRECTED. EXCEPT AS SET FORTH IN SECTION 6(C), SONOS' SOLE LIABILITY, AND YOUR SOLE REMEDY, FOR BREACH OF THE FOREGOING WARRANTY WILL BE, AT SONOS' SOLE DISCRETION, REPAIR OR REPLACEMENT OF THE PRODUCT, OR, IF NEITHER OF THE FOREGOING ARE REASONABL Y AVAILABLE, A REFUND OF THE AMOUNT YOU PAID, LESS AMOUNTS ATTRIBUTABLE TO YOUR PRIOR USE.(b) Limitations. The foregoing warranty does not extend to problems in the Product that result from: (i) Y our failure to implement all bug fixes or error corrections to the Product which are made available by Sonos; (ii) any use of the Product in a manner for which it was not designed or as not authorized under this Agreement; or (iii) any use of the Product with other products, hardware or products not supplied by, and/or inconsistent with the documentation provided by, Sonos.(c) Disclaimer. EXCEPT AS EXPRESSL Y SET FORTH ABOVE, SONOS MAKES NO WARRANTIES, WHETHER EXPRESS, IMPLIED, STATUTORY OR OTHERWISE, WITH RESPECT TO THE PRODUCT. SONOS AND ITS SUPPLIERS HEREBY SPECIFICALL Y DISCLAIM ALL OTHER EXPRESS, STATUTORY AND IMPLIED WARRANTIES AND CONDITIONS, INCLUDING THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NON-INFRINGEMENT AND THE IMPLIED CONDITION OF SATISFACTORY QUALITY. EXCEPT AS EXPRESSL Y STATED IN SECTION 6(A), THE PRODUCT IS SUPPLIED ON AN "AS IS" BASIS WITHOUT WARRANTY. YOU ASSUME ALL RESPONSIBILITIES FOR SELECTION OF THE PRODUCT TO ACHIEVE YOUR INTENDED RESULTS, AND FOR THE INSTALLATION AND USE OF THE PRODUCT. Some jurisdictions do not allow a limitation on implied warranties, and so the foregoing disclaimer may not apply to Y ou. In any event, any implied warranties that may exist under the laws of Y our jurisdiction are limited to the one (1) year period set forth in the limited warranty given under subsection (a) above.7.LIMITATION OF LIABILITY(a) TO THE MAXIMUM EXTENT ALLOWED UNDER LAW, IN NO EVENT WILL SONOS OR ITS SUPPLIERS BE LIABLE FOR ANY DAMAGES, INCLUDING BUT NOT LIMITED TO, INCIDENTAL, SPECIAL,Sonos3 CONSEQUENTIAL, EXEMPLARY, OR INDIRECT DAMAGES, AND INCLUDING BUT NOT LIMITED TO, COST OF COVER, LOSS OF DATA, LOSS OF PROFITS, BUSINESS INTERRUPTION, LOSS OF BUSINESS INFORMATION, OR OTHER PECUNIARY LOSS ARISING FROM THE USE OF (OR INABILITY TO USE) THE PRODUCT, NO MATTER HOW CAUSED AND ON ANY THEORY OF LIABILITY. BECAUSE SOME STATES/ JURISDICTIONS DO NOT ALLOW THE EXCLUSION OR LIMITATION OF LIABILITY FOR CONSEQUENTIAL OR INCIDENTAL DAMAGES, SOME OF THE ABOVE LIMITATIONS MAY NOT APPL Y TO YOU, BUT THEY SHALL APPL Y TO THE MAXIMUM EXTENT PERMITTED BY LAW.(b) IN NO EVENT SHALL SONOS' TOTAL LIABILITY TO YOU FOR ALL DAMAGES IN ANY ONE OR MORE CAUSES OF ACTION EXCEED THE AMOUNT PAID BY YOU FOR THE PRODUCT.(c) The limitations in Section 7 will apply even if Sonos, its suppliers or dealers have been advised of the possibility of such damage or of any type of use intended by Y ou. These limitations shall apply notwithstanding the failure of essential purpose of any limited remedy. Y ou acknowledge that these limitations reflect a reasonable allocation of risk.8.INFRINGEMENT INDEMNITY(a) Indemnity. Sonos shall defend or settle any claim, demand, suit, proceeding or action ("Claim") against Y ou to the extent that such Claim is based on an allegation that any portion of the Product, as furnished to Y ou under this Agreement and used as authorized in this Agreement, infringes any third party's U.S. copyright or misappropriates such third party's trade secrets, provided that Y ou: (i) give prompt written notice of the Claim to Sonos; (ii) give Sonos the exclusive authority to control and direct the defense or settlement of such Claim; and (iii) give Sonos, at Sonos' expense (except for the value of Y our time), all necessary information and assistance with respect to the Claim. Sonos shall pay all settlement amounts, damages and costs finally awarded to the extent attributable to such Claim. Y ou may participate in the defense of Claim at Y our expense. Sonos will not be liable for any costs or expenses incurred without its prior written authorization. (b) Limit on Indemnity. The foregoing notwithstanding, Sonos shall have no liability for a Claim to the extent based on: (i) the use by Y ou of any Product more than thirty (30) days after Sonos notifies Y ou in writing that continued use of the Product may give rise to such Action; (ii) the combination of the Product, or any part thereof, with other hardware or products not provided by Sonos, which Claim would have been avoided if the Products had not been so combined; or (iii) use of the Products other than as authorized under this Agreement.(c) Entire Liability. THE FOREGOING PROVISIONS OF THIS SECTION 8 STATE THE ENTIRE LIABILITY AND OBLIGATIONS OF SONOS, AND YOUR EXCLUSIVE REMEDY, WITH RESPECT TO ANY ACTUAL OR ALLEGED INFRINGEMENT OF OR MISAPPROPRIATION OF ANY INTELLECTUAL PROPERTY RIGHT BY THE PRODUCT.9.MISCELLANEOUSY ou acknowledge that the Product is subject to the export control law and regulations of the United States, and any amendments thereto. Y ou warrant that Y ou will comply in all respects with United States exports laws and regulations. This Agreement shall be governed by the laws of the State of California, without reference to its conflict of law principles. Y ou consent to the jurisdiction of the federal and state courts sitting in the State of California. This Agreement constitutes the entire agreement between Y ou and Sonos with respect to the subject matter hereof, and supersedes all prior oral or written understandings, communications or agreements not specifically incorporated herein. If any provision of this Agreement is found to be invalid or unenforceable pursuant to judicial decree or decision, the remainder of this Agreement shall remain valid and enforceable according to its terms. Y ou may not assign this Agreement, or any of its rights or obligations hereunder, whether by operation of law or otherwise, without the prior written consent of Sonos. Any attempted assignment by Y ou without prior written consent shall be void.4Important Product Information ForinquiriesorquestionsregardingthisAgreement,******************************************* (800) 680-2345.License Agreement and Limited Warranty (Europe)Sonos Europe B.V.Schuttersweg 101217 PZ HilversumThe NetherlandsREAD THE TERMS OF THIS LICENSE AGREEMENT AND LIMITED WARRANTY ("AGREEMENT") GOVERNING THE USE OF THE SOFTWARE AND RELATED FIRMWARE AND DOCUMENTATION (COLLECTIVEL Y, THE “SOFTWARE”) PROVIDED TO YOU BY SONOS EUROPE B.V. (“SONOS”) CAREFULL Y BEFORE BUYING THE APPLICABLE SONOS PRODUCT (SUCH HARDWARE, TOGETHER WITH THE SOFTWARE, REFERRED TO AS THE “PRODUCT”).BY PURCHASING THE PRODUCT, YOU ARE (1) REPRESENTING THAT YOU ARE OVER THE AGE OF 18, (2) REPRESENTING THAT YOU HAVE THE RIGHT AND AUTHORITY TO LEGALL Y BIND YOURSELF OR YOUR COMPANY, AS APPLICABLE, AND (3) CONSENTING TO BE LEGALL Y BOUND BY ALL OF THE TERMS OF THIS AGREEMENT. IF YOU DO NOT AGREE TO ALL THESE TERMS OR CANNOT MAKE SUCH REPRESENTATIONS, DO NOT PURCHASE THE PRODUCT.1.GRANT OF LICENSE(a) Subject to the terms and conditions of this Agreement, Sonos grants to Y ou a worldwide, non-exclusive, non-transferable, personal license (without the right to sub-license) to (i) use the Software as embedded in the Product for the purpose of operating the Product, and (ii) use the desktop application portion(s) of the Software on any personal computer owned or controlled by Y ou during the T erm. Y ou may not transfer the Software to any other computing device or otherwise remove the Software from the Product. Notwithstanding any license granted herein by Sonos, Y ou acknowledge and agree that it is Y our sole responsibility to comply with U.S. and international copyright laws with respect to Y our use of the Software.(b) Y ou agree not to copy, modify, reverse engineer, decompile or disassemble the Product to the extent that such restriction is not prohibited by applicable mandatory law. Except for the limited license granted herein, Sonos and its suppliers hereby retain all right, title and interest in and to all worldwide intellectual property rights embodied in the Software. All other rights are reserved by Sonos. Y ou acknowledge and agree that the technology embedded in and used to create the Product constitute the valuable trade secrets and know-how of Sonos, and to the extent Y ou discover any such trade secrets, Y ou will not disclose them to any third party.(c) Sonos shall have no obligation to provide any updates or upgrades to the Product, but in the event that it does, such updates, upgrades and any documentation shall be deemed the “Product”, and shall be subject to the terms and conditions of this Agreement.2.TERM OF AGREEMENT(a) Y ou may terminate this Agreement at any time by notifying Sonos, discontinuing use of the Product and purging the Software from Y our computing device.(b) This Agreement will automatically terminate if Y ou violate Section 1 and/or 3 of this Agreement.(c) Sections 1(b), 2(c), 3, 6(c), 7 and 9 shall survive termination or expiration for any reason.Sonos5PLIANCE WITH COPYRIGHT LAWSSonos complies with U.S. and international copyright laws and in consideration of the licenses granted herein, Y ou agree to do the same. Y ou acknowledge that unauthorized copying or distribution of music or other content accessed using the Product (“Content”) is prohibited by such copyright laws, and Y ou agree that Y ou will not, directly or indirectly, copy or distribute any Content without the express written authorization of the copyright holder. Further, Y ou agree to compensate Sonos and its licensors for all losses, damages, liabilities, costs and expenses incurred by Sonos or its licensors as a result of claims or actions brought against Sonos or its licensors arising out of or related to Y our failure to comply with the terms of this Section 3.4.SONOS PRIVACY POLICYUse of Sonos Products is subject to the Sonos Privacy Policy, which can be found at / legal/privacy_policy.htm and by reference is made a part of this Agreement. The Sonos Privacy Policy outlines the type of information that may be collected from you by Sonos and how such information may be used by Sonos. It is important that you read and understand the terms of the Privacy Policy.5.THIRD PARTY CONTENT AND TECHNOLOGIES SUPPORTFrom time to time, Sonos may provide access to third party content providers via the Product. In addition, Sonos may support certain third party technologies, such as specific file formats or codecs. Sonos reserves the right to discontinue access to and/or support for such third party content or technologies at any time, and for any reason. Sonos makes no representations or warranties whatsoever regarding the selection of, or continuing support for, any such third party content or technologies.6.WARRANTY AND DISCLAIMER(a) Limited Warranty. Sonos warrants to Y ou that, for a period of two (2) years after the date of original purchase of the Product, the Product will be free from defects in materials and workmanship. SONOS DOES NOT WARRANT THAT THE PRODUCT WILL OPERATE WITHOUT INTERRUPTION OR WILL BE ERROR-FREE, OR THAT ALL ERRORS MAY BE CORRECTED. IF YOU ARE A CONSUMER, THIS WARRANTY IS IN ADDITION TO AND DOES NOT AFFECT YOUR STATUTORY RIGHTS. EXCEPT AS SET FORTH IN SECTION 4(C) AND SUBJECT TO ANY MANDATORY CONSUMER PROTECTION LAWS TO THE CONTRARY, SONOS SOLE LIABILITY, AND YOUR SOLE REMEDY, FOR BREACH OF THE FOREGOING WARRANTY WILL BE REPAIR OR REPLACEMENT OF THE PRODUCT, OR, IF NEITHER OF THE FOREGOING ARE REASONABL Y AVAILABLE, A REFUND OF THE AMOUNT YOU PAID, LESS AMOUNTS ATTRIBUTABLE TO YOUR PRIOR USE.(b) Limitations. The foregoing warranty does not extend to problems in the Product to the extent that such results from: (i) Y our failure to implement all bug fixes or error corrections to the Product which are made available by Sonos; (ii) any use of the Product in a manner for which it was not designed or as not authorized under this Agreement; or (iii) any use of the Product with other products, hardware or products not supplied by, and/or inconsistent with the documentation provided by, Sonos.(c) Disclaimer. EXCEPT AS EXPRESSL Y SET FORTH ABOVE, SONOS MAKES NO WARRANTIES, WHETHER EXPRESS, IMPLIED, STATUTORY OR OTHERWISE, WITH RESPECT TO THE PRODUCT. SONOS AND ITS SUPPLIERS HEREBY SPECIFICALL Y DISCLAIM ALL OTHER EXPRESS, STATUTORY AND IMPLIED WARRANTIES AND CONDITIONS, INCLUDING THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NON-INFRINGEMENT AND THE IMPLIED CONDITION OF SATISFACTORY QUALITY. EXCEPT AS EXPRESSL Y STATED IN SECTION 6(A), THE PRODUCT IS SUPPLIED ON AN “AS IS” BASIS WITHOUT WARRANTY. YOU ASSUME ALL RESPONSIBILITIES FOR SELECTION OF THE PRODUCT TO ACHIEVE YOUR INTENDED RESULTS, AND FOR THE INSTALLATION AND USE OF THE PRODUCT. SOME JURISDICTIONS DO NOT ALLOW A LIMITATION ON IMPLIED WARRANTIES, AND SO, PARTICULARL Y IF YOU ARE A CONSUMER, THE6Important Product Information FOREGOING DISCLAIMER MAY NOT APPL Y TO YOU. In any event, to the extent permitted under the laws of Y our jurisdiction, any implied warranties that may exist under the laws of Y our jurisdiction are limited to the two (2) year period set forth in the limited warranty given under subsection (a) above.7.LIMITATION OF LIABILITY(a) TO THE MAXIMUM EXTENT ALLOWED UNDER LAW, IN NO EVENT WILL SONOS OR ITS SUPPLIERS BE LIABLE FOR ANY INCIDENTAL, SPECIAL, CONSEQUENTIAL, EXEMPLARY, OR INDIRECT DAMAGES, AND INCLUDING BUT NOT LIMITED TO, COST OF COVER, LOSS OF DATA, LOSS OF PROFITS, BUSINESS INTERRUPTION, LOSS OF BUSINESS INFORMATION, OR OTHER PECUNIARY LOSS ARISING FROM THE USE OF (OR INABILITY TO USE) THE PRODUCT, NO MATTER HOW CAUSED AND ON ANY THEORY OF LIABILITY.(b) IN NO EVENT SHALL SONOS’ TOTAL LIABILITY TO YOU FOR ALL DAMAGES IN ANY ONE OR MORE CAUSES OF ACTION EXCEED THE AMOUNT PAID BY YOU FOR THE PRODUCT UNLESS OTHERWISE REQUIRED BY LAW.(c) The limitations in Section 7 will apply even if Sonos, its suppliers or dealers have been advised of the possibility of such damage or of any type of use intended by Y ou. These limitations shall apply notwithstanding the failure of essential purpose of any limited remedy. Y ou acknowledge that these limitations reflect a reasonable allocation of risk.(d) The limitations in this section 7 shall not apply to damage resulting from willful misconduct or gross negligence on the part of Sonos. The limitations of section 7 shall further not apply to damage resulting from loss of life or personal injury caused by willful misconduct or negligence or breach of contract by Sonos or its directors or any third party Sonos has used to fulfill its contractual obligations towards Y ou. With regard to product liability, the limitations in this section 7 shall only apply to the extent permitted by mandatory rules regarding product liability.(e) The limitations in this section 7 shall not affect your statutory rights as a consumer.8.INFRINGEMENT INDEMNITY(a) Indemnity. Sonos shall defend or settle any claim, demand, suit, proceeding or action (“Claim”) againstY ou to the extent that such Claim is based on an allegation that any portion of the Product, as furnished toY ou under this Agreement and used as authorized in this Agreement, infringes any third party's copyright or misappropriates such third party’s trade secrets, provided that Y ou: (i) give prompt written notice of the Claim to Sonos; (ii) give Sonos the exclusive authority to control and direct the defense or settlement of such Claim; and (iii) give Sonos, at Sonos’ expense (except for the value of Y our time), all necessary information and assistance with respect to the Claim. Sonos shall pay all settlement amounts, damages and costs finally awarded to the extent attributable to such Claim. Y ou may participate in the defense of Claim at Y our expense. Sonos will not be liable for any costs or expenses incurred without its prior written authorization. (b) Limit on Indemnity. The foregoing notwithstanding, Sonos shall have no liability for a Claim to the extent based on: (i) the use by Y ou of any Product more than thirty (30) days after Sonos notifies Y ou in writing that continued use of the Product may give rise to such Action and offers, in return for Y ou ceasing all further use of the Product, to refund the price paid by Y ou for the Product less amounts attributable to Y our prior use; (ii) the combination of the Product, or any part thereof, with other hardware or products not provided by Sonos, which Claim would have been avoided if the Products had not been so combined; or (iii) use of the Products other than as authorized under this Agreement.(c) Entire Liability. THE FOREGOING PROVISIONS OF THIS SECTION 8 STATE THE ENTIRE LIABILITY AND OBLIGATIONS OF SONOS, AND YOUR EXCLUSIVE REMEDY, WITH RESPECT TO ANY ACTUAL ORSonos7 ALLEGED INFRINGEMENT OF OR MISAPPROPRIATION OF ANY INTELLECTUAL PROPERTY RIGHT BY THE PRODUCT.9.MISCELLANEOUSY ou acknowledge that the Product may be subject to the export control law and regulations of the jurisdiction in which Y ou purchased the Product and you warrant that Y ou will comply in all respects with such laws and regulations. This Agreement shall be governed by the laws of the Netherlands, without reference to its conflict of law principles, The United Nations Convention on contracts for the International sale of goods is not applicable to this Agreement. This Agreement constitutes the entire agreement between Y ou and Sonos with respect to the subject matter hereof, and supersedes all prior oral or written understandings, communications or agreements not specifically incorporated herein. If any provision of this Agreement is found to be invalid or unenforceable pursuant to judicial decree or decision, the remainder of this Agreement shall remain valid and enforceable according to its terms. Y ou may not assign this Agreement, or any of its rights or obligations hereunder, whether by operation of law or otherwise, without the prior written consent of Sonos, which consent shall not, if Y ou are a consumer, be unreasonably refused. Any attempted assignment by Y ou without prior written consent shall be void.ForinquiriesorquestionsregardingthisAgreement,*************************************. Contrat de licence et garantie limitée.(Aux États-Unis et dans le reste du monde, à l'exception de l'Europe)Sonos, Inc.LISEZ ATTENTIVEMENT LES TERMES DE CE CONTRAT DE LICENCE ET DE CETTE GARANTIE LIMITÉE (« CONTRAT ») RÉGISSANT L’UTILISATION DU LOGICIEL AINSI QUE DU PROGICIEL ET DE LA DOCUMENTATION ASSOCIÉS (COLLECTIVEMENT, LE « LOGICIEL »), QUI VOUS SONT FOURNIS PAR SONOS (« SONOS ») AVANT D’UTILISER LE PRODUIT SONOS APPLICABLE (MATÉRIEL QUI, AVEC LE LOGICIEL, EST CONSIDÉRÉ COMME LE « PRODUIT »).EN OUVRANT CET EMBALLAGE, EN INSTALLANT ET EN UTILISANT LE PRODUIT, VOUS (1) DÉCLAREZ QUE VOUS AVEZ PLUS DE 18 ANS, VOUS (2) DÉCLAREZ QUE VOUS AVEZ LE DROIT DE VOUS ENGAGER OU D’ENGAGER VOTRE SOCIÉTÉ LÉGALEMENT LE CAS ÉCHÉANT ET VOUS (3) CONSENTEZ À ÊTRELÉGALEMENT ENGAGÉ PAR TOUS LES TERMES DE CE CONTRAT. SI VOUS N’ACCEPTEZ PAS TOUS CES TERMES OU SI VOUS NE REMPLISSEZ PAS CES CRITÈRES, N’UTILISEZ PAS LE PRODUIT. SI VOUS CHOISISSEZ DE NE PAS ACCEPTER LES TERMES DE CE CONTRAT, VOUS POUVEZ RETOURNER LE PRODUIT NEUF ET INUTILISÉ AU MAGASIN OÙ VOUS L’AVEZ ACHETÉ DANS UN DÉLAI DE TRENTE (30) JOURS APRÈS L’ACHAT, AVEC SON EMBALLAGE D’ORIGINE POUR UN REMBOURSEMENT INTÉGRAL.1. ATTRIBUTION DE LICENCE(a) Selon les termes et conditions de ce contrat, Sonos vous accorde une licence personnelle non-transférable, non-exclusive et mondiale (sans droit de sous-licence) pour (i) utiliser le logiciel lorsqu’il estintégré au produit afin de faire fonctionner ce dernier et pour (ii) utiliser la ou les parties d'application de bureau du logiciel sur un ordinateur personnel dont vous êtes propriétaire ou que vous contrôlez durant la période. Sauf disposition contraire ci-dessus, vous ne pouvez pas transférer le logiciel vers un autre périphérique informatique, ni le supprimer du produit. En dépit de toute licence accordée ici par Sonos, vous assumez et acceptez qu’il est de votre seule responsabilité de satisfaire aux lois de copyright internationales et des États-Unis d’après votre utilisation du logiciel.(b) Vous acceptez de ne pas copier, modifier, faire de l’ingénierie inverse, décompiler ou désassembler le produit dans la mesure où une telle restriction n’est pas prohibée par la loi. Sauf pour la licence limitée accordée ici, Sonos et ses fournisseurs conservent par le présent document tous les droits, habilitations et。
Sophos RED 15和RED 50应用程序操作说明说明书

Operating Instructions Sophos RED 15 and RED 50 AppliancesIntroductionThese operating instructions will help you install and configure the Sophos RED appliances and provide technical specifications of all RED devices. In addition,please also see the following documents that contain useful information on safety regulations, regulatory compliance, and configuration options: ÌSophos RED Appliances Safety Instructions & Regulatory Information (part of the scope of supply) ÌSophos RED 15/50 Quick Start Guide (part of the scope of supply depending on RED model) ÌSophos UTM Administration GuideThe instructions must be read carefully prior to using the device and should be kept in a safe place. You may download all user manuals and additional documentation from the Sophos Knowledgebase at /en-us/support/knowledgebase.aspx .RED 15Scope of supplyPreliminary stepsMake sure that the RED appliance has been shipped to the branch office. Ask the person who is going to put the RED appliance into operation at the branch office to provide the unique RED-ID, which is printed at the bottom of the device. Note that the RED appliance requires a working Internet connection at your branch office.Configuring the RED applianceConfigure the RED appliance in the central UTM appliance as described in the Sophos UTM Administration Guide.RED ID#Manufactured: December 2012RJ45 Ethernet cableQuick Start Guide and Sophos RED 15 Appliance Power supplyConnecting branch office PCs to the RED applianceAt the branch office, use standard Ethernet cables to connect the PCs to the LAN ports (LAN1-LAN4) of the RED appliance, either directly or via a network switch. Use the orange Ethernet cable (from the scope of supply) to connect the WAN port of the RED appliance to the interface of your router or cable modem that connects to the Internet.Connecting the RED appliance to the power supplyConnect the RED appliance to the power supply from the scope of supply. Plug the power supply into the electrical outlet. The Power LED will light.After the system has booted, it will connect to the Internet. The status LEDs System, Router, and Internet will light:System bootedRouter reachableInternet connectivity upIf all four status LEDs are flashing (from left to right and vice versa), the device is installing a new firmware version.Important note: Do not unplug the power while the firmware is updating. Otherwise the RED appliance will be rendered inoperable and must be returned to the reseller. Establishing a tunnel between the branch office and the central UTM Gateway The RED appliance will now automatically retrieve its configuration file from the Internet and establish an encrypted tunnel to the central office. The Tunnel LED will now light:Tunnel upIf any of the four status LEDs is not lit or if the System LED is red and blinking, please refer to “Controls and LED codes” section below to identify the error.Controls and LED CodesControlsLED codesStatus signal10/100/1000 Base-TX portsPower1 x 10/100/1000 Base-TX ports4 x 10/100/1000 Base-TX portsPower1 x USB portConsoleTechnical specificationsRED 50Scope of supplyPreliminary stepsMake sure that the RED appliance has been shipped to the branch office. Ask the person who is going to put the RED appliance into operation at the branch office to provide the unique RED-ID, which is printed at the bottom of the device. Note that the RED appliance requires a working Internet connection at your branch office.RJ45 Ethernet cableQuick Start Guide and Sophos RED 50 Appliance Power supplyStarting RED> A0000014EE22E39 Tunnel is up (wan1) > UTM 10.8.16.32Configuring the RED applianceConfigure the RED appliance in the central UTM appliance as described in the Sophos UTM Administration Guide.Connecting branch office PCs to the RED applianceAt the branch office, use standard Ethernet cables to connect the PCs to the LAN ports (LAN1-LAN4) of the RED appliance, either directly or via a network switch.Use the orange shielded Ethernet cable of the scope of supply to connect the WAN1 interface of the RED 50 appliance to the interface of your router or cable modem that connects to the Internet.(Optional) If your office is equipped with a standby Internet connection, also connect the WAN2 interface of the RED 50 appliance to the interface of your router or cable modem that connects to the second Internet line.Connecting the RED appliance to the power supplyConnect the RED appliance to the power supply from the scope of supply. Plug the power supply into the electrical outlet. The Power LED will light and the system will boot. The LCD will show the message “Starting RED” and the RED-ID. Establishing a tunnel between the branch office and the central UTM Gateway The RED 50 will now automatically retrieve its configuration from the Internet and establish a tunnel to your central office. After successfully establishing the tunnel, the LCD will show the message “Tunnel is up (wan1)” and either the IP address or the hostname of the UTM appliance to which the RED 50 is connected.Wall mounting instructionsThe Sophos RED 50 can be mounted on the wall. Screws are not included in the scope of supply. Only use screws whose dimensions correspond with the mounting holes on the back.Secure the screws to the wall, and mount by inserting the screws into the mounting holes on the back. Do not connect the power cable until mounting to the wall is complete.RED 50 Mounting templateDo not shrink to fit when printing8mmControls, LED Codes and LCD messagesControlsThe following menu entries are avaiablePower/ErrorLEDs10/100/1000Base-TX ports LEDsNavigation keys10/100/1000Base-TX portsPowerConsole2 x USB2.0 portsLCDLCD messagesBooting up The RED device is bootingShutting down The RED device is shutting downStarting RED ID $RED_ID The RED device is starting (the displays showsthe RED ID as printed on the product label) Starting RED Network Setup The RED device is configuring DHCP or a static setupStarting RED Try $uplink The RED device is connecting to thedisplayed uplink (wan1, wan2, or umts)Starting RED UTM $hostname The RED device is connecting to the UTM appliance Got new config The RED device has received a new configurationTunnel is up ($uplink) UTM $hostname The RED tunnel has been established; $uplink can be wan1, wan2, or umts; $hostname can be hostname or IP address of UTM applianceERROR Invalid device ID The RED device has not been provisioned correctly Technical specificationsRack-Mount instructionsTo mount the appliance to a rack (1U), you need the special RED 50 rack-mount ears, which is a separate item to be ordered. Make sure you only use the screws supplied with the rack-mount ears. Using the wrong screws could damage the hardware appliance and would invalidate your warranty.1. Attach the rack-mount ears to the appliancePlace the appliance on a hard, flat surface with the front panel facing you.Attach the rack–mount ears to the left and right side of the appliance with the supplied screws. Make sure the ears are properly attached to the appliance. 2. Choose the rack locationFor general warnings on rack-mount installations, see below.3. Attach the brackets to the rack with appropriate screws (not included). General Warnings for Rack-Mount Installations1. E levated Operating Ambient – If installed in a closed or multi-unit rackassembly, the operating ambient temperature of the rack environmentmay be greater than room ambient. Therefore, consideration should begiven to installing the equipment in an environment compatible with themaximum ambient temperature (Tma) specified by the manufacturer.2. Reduced Air Flow – Installation of the equipment in a rackshould be such that the amount of air flow required for safeoperation of the equipment is not compromised.3. M echanical Loading – Mounting of the equipment in the rack should be suchthat a hazardous condition is not achieved due to uneven mechanical loading.4. Circuit Overloading – Consideration should be given to theconnection of the equipment to the supply circuit and the effect thatoverloading of the circuits might have on overcurrent protection andsupply wiring. Appropriate consideration of equipment nameplateratings should be used when addressing this concern.5. R eliable Earthing – Reliable earthing of rack-mounted equipment should bemaintained. Particular attention should be given to supply connections otherthan direct connections to the branch circuit, (e.g. use of power strips).Operating InstructionsUnited Kingdom and Worldwide Sales Tel: +44 (0)8447 671131Email:****************North American SalesToll Free: 1-866-866-2802Email:******************Australia and New Zealand SalesTel: +61 2 9409 9100Email:****************.auAsia SalesTel: +65 62244168Email:********************Oxford, UK | Boston, USA© Copyright 2015. Sophos Ltd. All rights reserved.Registered in England and Wales No. 2096520, The Pentagon, Abingdon Science Park, Abingdon, OX14 3YP, UK Sophos is the registered trademark of Sophos Ltd. All other product and company names mentioned are trademarks or registered trademarks of their respective owners.2015-07-23 OI-NA (DD-2173)。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
欧洲排名第一的防杀病毒软件-Sophos
随着计算机网络的迅速普及,搭乘了网络信息高速列车的计算机病毒,传播速度倍增。
国际间的新病毒只需在几小时之内便会出现在我国用户面前,使他们的计算机体系时刻处于新病毒的威胁之中。
因此,反病毒产品技术的优劣,对用户的计算机安全起着至关重要的作用。
如果用户能够真正判别反病毒产品的优劣,那么,计算机安全其实近在咫尺。
对于用户来说,防病毒产品的质量直接关系到计算机体系的防护。
但是,选择质量优秀的反病毒产品,对用户既是重要的却又是困难的。
重要性体现在防病毒产品是否能够有效查杀病毒,查杀时是否具备安全性,它与软、硬平台是否存在兼容性、可靠性的问题,以及运行效率如何… 这些都直接关系到用户的切身利益。
而困难性则体现在当前我国反病毒产品市场, 受广告宣传主导因素的影响非常大。
用户在没有专业测试手段的情况下,对反病毒产品的优劣难以判断。
其实,国际权威机构的测试及其认证是解决用户上述问题的最好方式,因为被测试产品只有完全通过严格的专业测试-,才能获得认证标志。
作为欧洲最大防病毒提供商,Sophos的反病毒产品提供了全方位的的防毒和杀毒的功能。
其频获大奖的技术、完备的产品系列, 以及杰出的工程设计水准能为企业用户提供全方位的病毒防护。
SOPHOS产品系列由Sophos Anti-virus、MailMonitor、SAV Interface、SOPHOS SBE中小企业版四部分组成:其中
Sophos Anti-virus用于文件服务器、桌面工作站以及移动设备的病毒防护;
MailMonitor用于邮件系统(SMTP server和Email Server)的病毒防护;
SAV interface则是提供给第三方的二次开发接口,允许用户把Sophos病毒引擎整合到他们的产品中。
SBE中小企业版可以支持WINDOWS和苹果MAC操作系统,分为Sophos Small Business Suite、Sophos Anti-Virus Small Business Edition、PureMessage Small Business Edition三个产品,支持5用户、10用户、25用户、50用户和100用户五个用户数量等级。
Small Business Suite包括了Anti-Virus Small Business Edition和PureMessage Small Business Edition两个产品的功能,能提供网络、服务器、桌面、邮件服务器防病毒和垃圾邮件过滤等全面保护。
PureMessage Small Business Edition提供邮件服务器防病毒和垃圾邮件过滤,Small Business Suite提供网络服务器和桌面电脑的防病毒。
1.Sophos Anti-virus
它提供查毒和杀毒功能,能对 台式机、网络操作系统、笔记本电脑、工作站和服务器进行保护。
它能提供实时和定时二种病毒扫描方式。
其中实时扫描,能通过Intercheck技术对需要进行访问的每个文件进行扫描,只有没有感染病毒它才允许用户访问有使用该文件。
在工作站和终端用户无需进行操作的情况下,Sophos的安装、配置、以及升级,都可由系统管理员通过SAVadmin的中央安装目录(CID)来处理,因此使用很方便。
通过Enterprise Manager 还可以实现从Sophos 网站到服务器、工作站及终端用户的自动升级。
Sophos Anti-virus能够监控所以入口点,包括磁盘、程序、文档、网络驱动器、光盘以及电子邮件和从因特网下载到台式机上的各种东西;它能检测和清除各种宏病毒,引导区病毒和PE 可执行文件病毒;支持对压缩文件的查杀。
Sophos Anti-virus还支持多操作系统和多文件系统(file systems)。
能及时完整地提供病毒告警消息:desktop alerts,network message,intercheck server event,SMTPemail,SNMP trap和log files。
2.MailMonitor
由于目前绝大多数的病毒都是通过电子邮件来传播的,因而Sophos推出了MailMonitor网关级系列的产品。
它通过与SMTP 服务器、Exchange2000 服务器、Notes/Domino 服务器协同工作来保护邮件在传输过程中避免病毒感染,同时也对附件(包括压缩文件)进行保护。
在产品安装使用过程中,MailMonitor 与Sophos anti-virus同时使用,协同工作。
其特点为:提供全面的邮件服务器保护,对从WAN和LAN口出入的病毒都可以进行实时的扫描;支持多种压缩方式的文件;能提供多种schedule 来配置自动扫描database;持续升级能力和用户透明化等特性。
3.Enterprise Manager
是SOPHOS产品中的集中管理功能,提供对sophos产品系列的统一安装,配置,升级及监控的一个平台。
通过它能与sophos databank website连接取得一些升级数据,同时又能监控到内部网上所有PC机。
其特点:能够按预订的时间自动与sophos站点连接并下载数据包;能自动下载和分发病毒库;提供自动和手动分发sophos 安装包;能通过savadmin对网络的服务器和工作站进行配置;通过中央控制台对网部网上所有pc进行强制安装,设定卸载权限,防止员工进行恶意病毒传播;充许管理员制定何时下载数据包;自动检查和替换已破坏的下载数据包;能做到传输过程中只传输必要的文件以节省带宽等功能
4.SAV Interface
SAVI是专门充许第三方的把sophos 反病毒产品集成到自主产品的一个接口。
SAVI作为sophos anti-virus的一部分,利用sophos提供的二次开发接口,用户能把反病毒产品集成到自己的防火墙,网关以及其它应用软件中。
Sophos反病毒系列产品使用是该公司自主开发的病毒引擎,是欧洲最大的反病毒安全提供商。
其产品通过了ISCA认证。
Sophos它能为用户提供全方位的病毒安全防护,其产品除了强大的查毒,杀毒功能外,友好的管理界面和中央管理器使得用户很方便地实现对整个网络的病毒进行管理,维护,配置,监控和升级。
方案介绍:
如图为企业的一个典型的防病毒方案,在企业内部网络的文件服务器(File server)装有Sophos Anti-vrius和Enterprise manager,通过File server可与sophos网站进行实时的版本升级和病毒一致性文件的下载,同时可以用Enterprise manager实现整个网络的病毒的安装、升级、监控等管理工作。
在所有桌面工作站(Desktop)或移动设备都装上sophos的Anti-vrius,以提供按实时、按计划、按需的病毒侦测和清除工作。
在邮件服务器中可以通过Mailmonitor来监控,侦测和清除进出的邮件是否感染病毒,Mailmonitor提供对多种压缩附件的支持。
通过上图可以看出,通过安装sophos防毒系列产品为企业提供了全方位的病毒保护工作。
方案优势
• SOPHOS作为欧洲最大的反病毒提供商,其产品对付病毒能力超群;其丰富的工程设计经验,7×24的技术支持以及快速的反应能力使用户及时迅速的完成数据的保护。
• SOPHOS独特的杀毒技术频获大奖,具有强大的研发力量,程序内核安全可靠 。
• 升级方便快捷,sophos通过Internet网、磁盘拷贝、媒体光盘提供多种自动或手动升级方式。
• SOPHOS防病为企业提供全方位的保护,系统易于扩充,其提供的SAV interface 接口能为用户提供更方便病毒防护。
适用对象
----所有使用计算机及网络的用户。
