东南大学数字通信试卷(附答案)
东南大学数字通信期末试卷04-05(附答案)

diversity,
diversity,
diversity.
5. 5. Three major sources of degradation in wireless communications
are
院 ,
, and
; the latter
学 心 two are byproducts of multipath.
2. 2. For a period of the maximal-length sequence, the autocorrelation function is similar to that of a random binary wave.
3. 3. For slow-frequency hopping,symbol rate Rs of MFSK signal is an integer multiple of the hop rate Rh. That is, the carrier frequency will change or hop several times during the transmission of one symbol.
4. 4. Frequency diversity can be done by choosing a frequency spacing
学院 心 equal to or less than the coherence bandwidth of the channel. 息 导中 5. 5. The mutual information of a channel therefore depends not only on
信 辅 the channel but also on the way in which the channel used. 学习 6. 6. Shannon’s second theorem specifies the channel capacity C as a
数字通信原理复习题及参考答案

《数字通信原理》课程复习资料一、填空题:1.已知二进制数字信号每个码元占有的时间为1ms ,0、1码等概率出现,则码元速率为__________,信息速率为__________;2.从信息传输角度来看,数字通信系统的主要质量指标是__________和__________。
3.高斯白噪声是指噪声的概率密度服从__________分布,功率谱密度服从__________分布。
4.通常,在纠、检错编码中引入的监督码元越多,信道的____ _ _____下降也越多。
5.若要检出3个错码,则分组码的最小码距dmin 应__ __ ____。
6.码重是码组中__ __的个数。
7.对线性分组码,如果找到了码的__ _ ___,那么编码方法就完全确定了。
8.常用的简单差错控制码有奇偶监督码、水平奇偶监督码、水平垂直奇偶监督码、群计数码和_____码。
9.已知(5,1)重复码,它的两个码组分别为00000和11111,则(5,1)重复码的最小码距为________,只用于检错,能检出________位错码。
10.四进制数字信号的信息传输速率为800b/s ,其码元速率为____________,若传送1小时后,接收到40个错误码元,其误码率为____________。
11.数字信号有时也称离散信号,这个离散是指信号的___________是离散变化的,而不一定指___________离散12.如果在已知发送独立的符号中,符号“E”出现的概率为0.125,则符号“E”所包含的信息量为 。
13.在2PSK 输出信号中存在倒相现象,其解决方法是采用___________。
14.假设分组码的最小码距为8,则它能检测误码的位数至多为 15.假设线性分组码信息码元长为5,若希望所编数字调制能够纠正1位错,码字最小码长为 。
16.通信系统的性能指标主要有 和 ,在模拟通信系统中前者用有效传输带宽衡量,后者用接收端输出的 衡量。
通信考试题及答案

通信考试题及答案一、单项选择题(每题2分,共20分)1. 以下哪个选项不是数字通信系统的基本组成部分?A. 信源编码器B. 信道编码器C. 调制器D. 信道答案:D2. 在数字通信中,以下哪个选项不是误码率的单位?A. 比特误码率(BER)B. 块误码率(BLER)C. 符号误码率(SER)D. 帧误码率(FER)答案:D3. 以下哪个选项不是多址接入技术?A. FDMAB. TDMAC. SDMAD. CDMA答案:C4. 在无线通信中,以下哪个选项不是信号衰落的原因?A. 多径传播B. 阴影效应C. 多普勒效应D. 信号放大答案:D5. 以下哪个选项不是调制技术?A. ASKB. FSKC. PSKD. PCM答案:D6. 在数字通信中,以下哪个选项不是信道编码的目的?A. 检测错误B. 纠正错误C. 提高数据传输速率D. 改善信号的传输质量答案:C7. 以下哪个选项不是无线通信中的天线类型?A. 偶极子天线B. 抛物面天线C. 螺旋天线D. 微带天线答案:C8. 在光纤通信中,以下哪个选项不是光纤的类型?A. 单模光纤B. 多模光纤C. 塑料光纤D. 同轴电缆答案:D9. 以下哪个选项不是卫星通信的特点?A. 覆盖范围广B. 通信距离远C. 传输速度快D. 受天气影响小答案:C10. 在移动通信中,以下哪个选项不是蜂窝网络的优点?A. 频率复用B. 容量大C. 信号覆盖范围广D. 移动性差答案:D二、多项选择题(每题3分,共15分)11. 以下哪些因素会影响无线信号的传播?A. 建筑物B. 地形C. 植被D. 温度答案:ABCD12. 在数字通信中,以下哪些技术可以提高信号的传输质量?A. 信道编码B. 调制技术C. 信号放大D. 多址接入技术答案:ABC13. 以下哪些是光纤通信的优点?A. 高带宽B. 抗干扰能力强C. 信号衰减小D. 成本高答案:ABC14. 在移动通信中,以下哪些因素会影响蜂窝网络的性能?A. 基站的布局B. 频率复用C. 用户的移动性D. 天气条件答案:ABCD15. 以下哪些是卫星通信的应用领域?A. 电视广播B. 军事通信C. 移动通信D. 互联网接入答案:ABCD三、填空题(每题2分,共20分)16. 数字通信系统的基本组成部分包括信源编码器、________、调制器和________。
大学《数字通信原理》试卷及答案(二)

大学《数字通信原理》试卷及答案一、填空题(每题2分)1、模拟信号转变为数字信号需要经过以下三个过程:_________ 、__________和__________ 。
2、将数字基带信号直接送到信道传输的方式称为_基带传输___________ 。
3、相对于模拟信号来说,数字信号的特点是在____幅度_______上是离散的。
6、人们把低于64kbit/s数码率的话音编码方法称为__________ 。
8、码组(0011010)的码重为_______ ,与码组(0100100)之间的码距为________ 。
9、要求码组能检测5个错码同时纠正3个错码,则其最小码距是______。
二、单项选择题(每题2分)1、CCITT规定,数字通信中语音信号的抽样频率是:(a) 8kHz (b) 16kHz (c) 4kHz (d) 12kHz2、根据抽样定理,如果要对频带限制在f m以下的连续信号进行抽样,则抽样频率fs必须满足:(a) fs≥2f m(b) fs≥3f m(c) fs≤2f m(d) fs≤3f m3、数字通信中,在对语音信号进行量化时通常采用:(a) 均匀量化(b)非均匀量化(c)两者均可(d)两者均不可4、A律13折线通常采用量化级数为:(a) 256 (b)128 (c)64 (d)5125、根据奈奎斯特第一准则,传输速率为8.448 Mbit/s 的数字信号,在理想情况下要求最小传输信道的带宽为:(a)8.448 MHz (b) 4.224MHz (c)2.816 MHz (d) 16.896MHz6、在实际传输系统中,如果采用的是滚降系数α=100%的滚降特性,则系统的传输效率是:(a) 2 bit / (s·Hz) (b) 1.5 bit / (s·Hz)(c) 1 bit / (s·Hz) (d) 3 bit / (s·Hz)7、实验中,我们可以通过眼图观察:(a) 量化信噪比的大小(b) 码间干扰的情况(c) 时钟同步情况(d) 以上三者皆可8、设在125毫秒内传输了1024个二进制码元,若在5秒内有3个码元发生了误码,则误码率为:(a) 0.29% (b) 60 % (c) 0.0073% (d)0.037%9、由4级移位寄存器产生的m 序列,其周期为:(a) 13 (b) 14 (c) 15 (d)1610、以下差错控制方式中,哪一种不属于检错重发:(a) 停发等候重发 (b) 返回重发 (c) 选择重发 (d)前向纠错三、PCM 基带传输通信系统框图如下,试填写空缺部分(10分)四、已知二进制信息码为 1000100001100000100001试写出其AMI 码、 HDB 3码和CMI 码。
数字通信题库答案及答案

一、单项选择题1.传送话音信号的基带传输系统模型中无信道编码、无调制2.某数字通信系统传输l0000000个码元,其中误1个码元,误码率为10-73.抽样后的PAM信号的特点是幅度离散、时间连续4.解决均匀量化小信号的量化信噪比低的最好方法是采用非均匀量化5.样值的绝对值相同其幅度码也相同的码型为折叠二进制码6.A律13折线编码器输出的码型是NRZ码7.PCM30/32系统第18路信令码的传输位置(即在帧结构中的位置)为F3帧TS16的后4位码第1-15路是TS16前4位码,是第几路就是F几帧第16-30路是TS16后4位码是第几路就是第几路-15帧的得数8.PCM30/32系统复帧同步码的码型为00009.DPCM是属于波形编码10.按SDH标准速率STM-4的速率是622.080Mb/s11.PCM四次群的接口码型为CMI码12.SDH中继网适合采用的拓扑结构为环形和线形13.可用于数字信号基带传输的信道为电缆信道(光缆信道、卫星信道、微波信道为频带传输的)14.再生中继系统中的升余弦波的特点是无码间干扰、均放特性容易实现15.属于频带传输系统的有数字微波传输系统和数字卫星传输系统16.人讲话的语声信号为模拟信号17.脉冲编码调制信号为数字信号18.均匀量化的特点是量化间隔不随信号幅度大小而改变19.A律13折线压缩特性中的第7段线的斜率是0.51段:16,2段16,3段8,4段4,5段2,6段1,7段0.5,8段0.2520.PCM30/32系统中对每路信号的抽样帧频率是8kHz21.STM—1的一帧的字节数为9×270×1STM-1一帧的比特数为9×270×822.PCM30/32系统复帧的周期是2ms23.异步复接在复接过程中需要进行码速调整【同步复接---码速变换;异步复接—码速调整】24.PCM30/32系统发送帧同步码的周期是25025.以下4种传输码型中含有直流分量的传输码型是单极性归零码【CMI码也含有直流分量】26.PCM30/32系统发送复帧同步码的周期是2ms27.对SDH网络同步而言,在SDH网络范围内正常的工作方式是同步方式28.样值为513,它属于A律13折线的(l=8) 第7量化段P38表格29.PCM一次群的接口码型为HDB3码30.A律13折线编码器量化级数N越大,则小信号时量化信噪比越小31.一个二进制数字信号码元时间长度为0.1μs,在传输过程中平均2.5秒产生一个错码,则其平均误码率近似为4×10-8(0.1μs/2.5s)μs=10^(-6)32.已知一个8进制信号的符号速率为4800波特,则其对应的信息速率是14400bit/s8进制就是用3个比特代表一个符号,每3比特变成一个符号。
东南大学数字通信期终试卷1998-2002

一、简要回答下列问题1.说明三种数字模型的信道对数字信号传输产生的主要影响。
2.给出下图(1)中信号的平均功率,假定任两点信号间的距离为d 。
3.对图(2)中的可能接收信号,分别画出相关解调器和匹配滤波解调的输出信号波形。
4.比较线性均衡器使用峰值失真准则和均方误差准则的性能。
5.比较LMS 自适应均衡算法和RLS 自适应均衡算法的优缺点。
6.说明多径衰落信道相干频率和相干时间的物理意义。
二、信息序列{a n }是iid 随机变量序列,每个符号等概取+1和-1,此信息序列以下列信号波形传输()()n n s t a g t nT ∞=−∞=−∑,其中,2sin ()()0 ()tA t T g t Totherwise π⎧≤≤⎪=⎨⎪⎩ 1.计算信号()s t 的功率谱密度函数。
2.信息进行预编码1n n n b a a −=+,然后利用同样的()g t 进行传输,求出此时的信号功率谱函数。
三、分析使用单纯信号集的三进制数字信号传输系统的性能。
四、某限带系统产生的ISI 可表示为: (0)()()/2 (1)0 ()b b E k s t s t kT dt E k otherwise ∞−∞=⎧⎪−==±⎨⎪⎩∫,信息序列是二进制不相关序列,加性噪声是方差为N 0的白噪声序列。
1.分别求出三抽头线性均衡器、两抽头前向和单抽头反馈均衡器DFE 的抽头系数。
2.分别求出两种均衡器的最小均方误差和输出信噪比。
3.比较当N 0=0.001时两种均衡器的性能。
五、二进制等效基带信号为s l (t)通过二径慢衰落信道传输,接收信号为,()() (0,1,2)l k k l k r a s t z t t T k =±+≤≤=二径中的噪声分量为零均值的高斯噪声,具有噪声功率谱密度N 0,衰落因子a 1,a 2相互独立,在区间[0,1]均匀分布。
1.以方块图的形式给出最佳接收机的结构框图。
有关通信专业试题及答案

有关通信专业试题及答案一、选择题(每题2分,共20分)1. 以下哪个是数字信号的特点?A. 连续性B. 离散性C. 模拟性D. 非线性答案:B2. 在移动通信中,用于区分不同用户的是:A. 基站B. 信道C. 频率D. 地址答案:D3. 光纤通信中,光信号的传输介质是:A. 空气B. 真空C. 光纤D. 水答案:C4. 下列哪个协议是用于电子邮件的?A. HTTPB. FTPC. SMTPD. TCP答案:C5. 以下哪个是无线通信中常用的调制方式?A. AMB. FMC. PMD. QAM答案:D6. 在数字通信中,误码率(BER)是指:A. 传输数据的比特率B. 传输数据的字节率C. 传输数据中错误比特的比例D. 传输数据中正确比特的比例答案:C7. 下列哪个是第三代移动通信技术?A. 2GB. 3GC. 4GD. 5G答案:B8. 在通信系统中,信噪比(SNR)的单位是:A. dBB. HzC. mWD. km答案:A9. 通信网络中,交换机的主要功能是:A. 数据存储B. 数据传输C. 数据路由D. 数据交换答案:D10. 以下哪个是通信网络中的安全协议?A. SSLB. SMTPC. HTTPD. FTP答案:A二、填空题(每空2分,共20分)1. 光纤通信中,光的传播方式是________。
答案:全反射2. 通信系统中,信号的调制过程是指将________信号转换为适合传输的________信号。
答案:基带;带通3. 在数字通信中,带宽是指信号的________频率范围。
答案:最高与最低频率之间的4. 移动通信中,多址接入技术主要有FDMA、TDMA、CDMA和________。
答案:OFDMA5. 通信网络中,TCP/IP协议栈的第四层是________。
答案:传输层三、简答题(每题10分,共30分)1. 简述数字通信与模拟通信的区别。
答案:数字通信是指传输数字信号的通信方式,具有抗干扰能力强、易于加密、便于实现数字化处理等特点。
数字信号处理-东南大学试卷

数字信号处理一、选择题1.下列可能是因果序列的z变换的是_______(A)(B)(C)(D)[n]的z变换的收敛域为_______2.x[n]=sin(0.5πn)R5(A)|z|≥0(B)|z| 〉 0(C)|z|≥1(D) |z| 〉 13.已知一个序列x[n]的z变换的数学表达式X(z),则关于它的极点和收敛域正确的是_______(A)收敛域内不能有极点处于收敛域以外,如果将之代入X(z)的数学表达式,则一(B)设z)=∞定得到X(z(C)如果x[n]是非因果序列,则X(z)的数学表达式在一定有极点(D)如果X(z)的数学表达式在z=∞没有极点,则x[n]一定是因果序列4.系统是因果系统的条件是_______(A) h[n]是因果序列(B)零输入的响应是零输出(C) 当前输出与以后的输入无关(D)如果n〈n0时输入为零,则n<n0时的输出也为零5.求周期序列的傅立叶变换表示的方法是_______(A) z变换(B)拉氏变换(C)傅立叶变换(D) DFS二、填空题1. 已知连续时间周期信号的采样为周期序列(A )写出x [n ]的周期N=_______;(B )写出x [n ]的DFS X[K]在区间0≤K≤N—1的值_______。
2. 考虑如下序列其傅利叶变换W(e jω)=_______。
3. 已知因果稳定的LTI 系统的系统函数,令H ap (z)= H i (z )H (z), H ap (z)是只有一个零点和极点的全通系统,则H i (z )=_______。
4. 某序列x[n ]的z 变换为,收敛域包括单位圆.则其x[0]的值为_______5. 的极点是_______, 零点是_______。
如果是右边序列,则ROC 是_______, x [n]= _______; 如果是左边序列,则ROC 是_______,x[n ]=_______; 如果是双边序列,则ROC 是_______, x[n]=_______。
数字通信考试试题
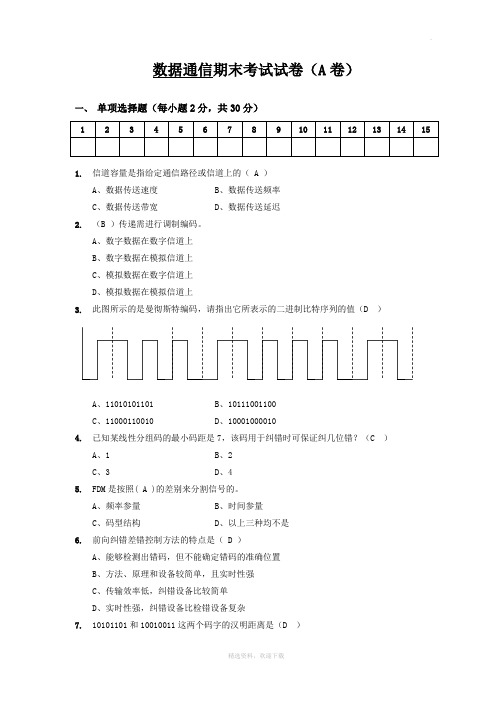
数据通信期末考试试卷(A卷)一、单项选择题(每小题2分,共30分)1.信道容量是指给定通信路径或信道上的( A )A、数据传送速度B、数据传送频率C、数据传送带宽D、数据传送延迟2.(B )传递需进行调制编码。
A、数字数据在数字信道上B、数字数据在模拟信道上C、模拟数据在数字信道上D、模拟数据在模拟信道上3.此图所示的是曼彻斯特编码,请指出它所表示的二进制比特序列的值(D )A、11010101101B、10111001100C、11000110010D、100010000104.已知某线性分组码的最小码距是7,该码用于纠错时可保证纠几位错?(C )A、1B、2C、3D、45.FDM是按照( A )的差别来分割信号的。
A、频率参量B、时间参量C、码型结构D、以上三种均不是6.前向纠错差错控制方法的特点是( D )A、能够检测出错码,但不能确定错码的准确位置B、方法、原理和设备较简单,且实时性强C、传输效率低,纠错设备比较简单D、实时性强,纠错设备比检错设备复杂7.10101101和10010011这两个码字的汉明距离是(D )A、2B、3C、4D、58.异步传输模式传送的数据每次为( A )A、一个字符B、一个字节C、一个比特D、一个帧9.在1200bit/s的电话线路上,经过测试在1小时内共有108bit误码信息,则该系统的误码率为(B )A、0.025%B、0.0025%C、0.09%D、0.9%10.某一数字脉冲编码调制复用系统包含32路话音,采用8000次/秒采样,每次采样值量化为128个离散电平,则该系统得总传输率为( B )A、1.024Mb/sB、1.792Mb/sC、2.048Mb/sD、2.568Mb/s11.在同一信道上的同一时刻,能够进行双向数据传送的通信方式为(C )A、单工B、半双工C、全双工D、以上三种均不是12.无电压用“0”来表示,恒定电压用“1”来表示的编码方式是(A )A、不归零码B、归零码C、曼彻斯特码D、差分曼彻斯特码13.一个连续变化的模拟信号,假设有最高频率或带宽F max ,若对它周期采样,采样后的离散序列就能无失真的恢复出原始连续模拟信号的条件是( A)A、采样频率F>2 F maxB、采样频率F>3 F maxC、采样频率F<2 F maxD、采样频率F<3 F max14.下列哪一项不是数字数据的调制编码的形式?( C )A、振幅键控B、频移键控C、频率键控D、相移键控15.下列关于数据传输速率和带宽的关系的叙述中不正确的是(C )A、数据信号传输速率越高,其有效的带宽越宽B、传输系统的带宽越宽,该系统能传送的数据传输速率越高C、中心频率越高,则数据传输速率越低D、中心频率越高,则潜在带宽就越宽二、填空题(每空1分,共15分)16.在数据通信中,为了保证数据被正确接收,必须采用一些同一编码解码频率的措施,这就是所谓的位同步的同步技术。
数字通信原理(附答案)[1]综述
![数字通信原理(附答案)[1]综述](https://img.taocdn.com/s3/m/dd497d18cfc789eb172dc879.png)
1、已知一个4进制信号的码元速率为4800波特,则其对应的信息速率是( C )A.4800bit/sB.2400bit/sC.9600bit/sD.14400bit/s2、产生已抽样信号频谱混叠的原因是( C )A.f s≥f mB.f s=2f mC.f s<2f mD.f s≥2f m3、样值为301△,它属于A律13折线的( B )A.第5量化段B.第6量化段C.第7量化段D.第8量化段4、在同一条链路上可传输多路信号,利用的是各路信号之间的( B )A. 相似性B.正交性C. 一致性D. 重叠5、在光纤中采用的多路复用技术是( C )A.时分复用B. 频分复用C.波分复用D. 码分复用R=( ), 信1、在4进制系统中,每秒钟传递1000个4进制符号,此系统的码元速率B R( ).( A )息速率bA.1000Bd,2000b/sB.2000Bd,2000b/sC. 2000Bd,1000b/sD. 1000Bd,1000b/s2、满足抽样定理时低通型信号的抽样频率应选为( D )A.f s≥f mB.f s=2f mC.f s<2f mD.f s≥2f m3、设模拟信号s(t)的幅度在[-2,2]v内均匀分布,对它进行奈奎斯特速率抽样,并均匀量化后,编为2进制码。
量化间隔为1/64v,需要多少量化电平数?( D )A.64B.128C.192D.2564、消息码为:1010001110001,对应的AMI码为:( A )A. +10-1000+1-1+1000-1B. +10-00000-1+1000-1C. -10+1000+1-1+1000-1D. +10+1000-1-1+1000+15、PCM30/32的二次群速率为( B )A.64 kb/sB.8.448Mb/sC.384kb/sD.2.048Mb/s2、产生已抽样信号频谱混叠的原因是( C )A.f s≥f mB.f s=2f mC.f s<2f mD.f s≥2f m3、均匀量化的PCM系统中,编码位数每增加1位,量化信噪比可增加( C )dB.A.2B. 4C. 6D. 84、绝对码为:10010110,对应的相对码为:( B )A. 10100101B.11100100C. 11100110D. 110001105、SDH采用的数字复接方法一般为( B )A.异步复接B.同步复接C.异步复接或同步复接D.以上都不是1、出现概率越__小__ 的消息,其所包含信息量越大;2、模拟信号的数字化过程主要包括抽样、_量化 _和编码;3、数字复接的方式主要有按位复接、按字复接和按帧复接;4、为了减小相干载波的稳态相位误差,应减小带通滤波器带宽和增大锁相环的增益;5、分组码(n,k)的编码效率为_ k/n ;1、衡量数字通信系统可靠性的主要指标是___差错率;2、模拟信号的数字化过程主要包括抽样、量化和编码;3、数字复接的方式主要有按位复接、按字复接和按帧复接;4、匹配滤波器就是指在某一特定时刻,使滤波器的瞬时输出信噪比最大的线性滤波器;5、码组0011011与码组0011011之间的码距是_ 0 _;1、已知8进制数字信号的传输速率为1600波特,若信息速率保持不变,变换成2进制数字信号的传输速率为 4800 波特。
电子通信专业考试题及答案

电子通信专业考试题及答案一、选择题(每题2分,共20分)1. 以下哪个不是数字通信系统的特点?A. 传输速度快B. 抗干扰能力强C. 传输距离远D. 传输带宽窄答案:D2. 在模拟通信中,信号的传输方式是:A. 数字化B. 模拟化C. 编码D. 解码答案:B3. 以下哪个是数字信号的优点?A. 易于产生B. 抗干扰能力弱C. 易于传输D. 易于失真答案:C4. 信号的频带宽度与信号的什么有关?A. 频率B. 振幅C. 相位D. 功率答案:A5. 以下哪个是调制的类型?A. 线性调制B. 非线性调制C. 频率调制D. 所有选项都是答案:D6. 以下哪个不是数字信号的特点?A. 易于存储B. 易于处理C. 易于传输D. 抗干扰能力弱答案:D7. 以下哪个是数字通信系统的优点?A. 传输距离短B. 传输速率低C. 传输质量高D. 传输带宽宽答案:C8. 以下哪个是数字信号的缺点?A. 易于产生B. 易于传输C. 抗干扰能力强D. 需要较高的传输速率答案:D9. 在数字通信中,以下哪个不是数字信号的编码方式?A. PCM编码B. PSK编码C. QAM编码D. FM编码答案:D10. 以下哪个是数字信号调制的特点?A. 调制简单B. 调制复杂C. 抗干扰能力强D. 传输带宽窄答案:B二、简答题(每题5分,共30分)1. 简述数字通信与模拟通信的区别。
答案:数字通信与模拟通信的主要区别在于信号的类型和处理方式。
数字通信使用数字信号,即信号以离散的数值形式表示,而模拟通信使用模拟信号,即信号以连续变化的形式表示。
数字通信具有更高的抗干扰能力,易于加密,易于实现信号的存储和处理,但需要更高的传输速率。
2. 解释什么是调制,以及调制的目的是什么。
答案:调制是将低频信号(如语音或数据)转换为适合在通信信道上传输的高频信号的过程。
调制的目的是使信号能够在信道上有效传输,同时减少信号的失真和干扰,提高信号的传输效率。
东南大学通信初试真题大合集(信号系统 逻辑)

四、(10 分)试叙述并证明傅里叶变换的卷积性质。
共5页 第 2 页
试题编号: 420
试题名称: 专业基础综合
第二部分 “数字电路” 50分 一、(15 分)在输入信号 A、B、C、D 的作用下,产生输出信号 F,波形如(图 1)所
图 2-1 二、(15 分)分析如图 2-2 所示的电路,写出电路的状态转移方程,做出状
态转移表,和在 CP 作用下 Q3、Q2、Q1 的输出波形(设初始状态均为 0)
图 2-2
共5页 第4页
试题编号: 420
试题名称: 专业基础综合
三、(10 分)图 2-3 为 PAL16L8 的一部分电路,试分析该电路,写出电路在 X
控制下的函数 F 对应于输入 A、B、C 的逻辑表达式。
图 2-3
四、(15 分)试用下降沿 D 触发器和适当的门电路设计一 1101 序列检测器, 该检测器有一个输入端,一个输出端。当输入的序列为 1101 时,输出为 1; 在其他输入时,输出为 0。
附:7485 功能表
A3 B3 A2 B2 A1 B1 A0 B0 A>B A<B A=B
+ e(t )
-
U +
c
(t
) -
1F +
1Ω
y(t ) -
(a)
e(t ) 1
e −( t−1)
1
t
(b)
图 1-1
Байду номын сангаас
四 (12 分)已知某线性系统框图如图 1-2 所示。其中系统 H(f)的频域传输函数 为
H( f ) = [ε ( f −15) −ε ( f ] +15) e− j2 f (f 为自然频率, f = ω )
数字通信习题解答

第l章1.模拟信号与数字信号各自的主要特点是什么?模拟信号:模拟信号的特点是信号强度(如电压或电流)的取值随时间连续变化。
由于模拟信号的强度是随时间连续变化的,所以模拟信号也称为连续信号。
数字信号:与模拟信号相反,数字信号强度参量的取值是离散变化的。
数字信号又叫离散信号,离散的含义是其强度的取值是有限个数值。
2.画出时分多路复用的示意图并说明其工作原理。
时分复用的电路结构示意图如图所示。
图中SA1和SA2为电子转换开关,它们在同步系统的控制下以同起点、同速度顺序同步旋转,以保证收、发两端同步工作。
在发端,开关的旋转接点接于某路信源时,就相当于取出某路信源信号的离散时间的幅度数值。
旋转接点按顺序旋转,就相当于按顺序取出各路信源信号在离散时间的幅度数值并合成,然后经模/数变换电路变为数字信号,再与同步信号合成即可送给信道传输。
在接收端,首先分出同步信号,再进行数/模变换后即可由旋转开关分别送给相应的信息接收者。
3.试述数字通信的主要特点。
(1)抗干扰能力强,无噪声积累(2)便于加密处理(3)利于采用时分复用实现多路通信(4) 设备便于集成化、小型化(5) 占用频带宽4.简单说明数字通信系统有效性指标,可靠性指标各是什么?并说明其概念。
有效性指标(1)信息传输速率: 信道的传输速率是以每秒钟所传输的信息量来衡量的。
信息传输速率的单位是比特/秒,或写成bit/s ,即是每秒传输二进制码元的个数。
(2)符号传输速率 :符号传输速率也叫码元速率。
它是指单位时间内所传输码元的数目,其单位为“波特”(bd )。
(3)频带利用率 :频带利用率是指单位频带内的传输速率。
可靠性指标(1)误码率 :在传输过程中发生误码的码元个数与传输的总码元数之比。
(2)信号抖动 :在数字通信系统中,信号抖动是指数字信号码元相对于标准位置的随机偏移。
第2章1、假设某模拟信号的频谱如图1所示,试画出M s f f 2=时抽样信号的频谱。
通信测试题及答案

通信测试题及答案一、选择题(每题2分,共20分)1. 通信系统中最基本的功能是:A. 信号调制B. 信号解调C. 信号编码D. 信号传输2. 下列哪项不是数字通信的优点?A. 抗干扰能力强B. 传输质量高C. 易于实现多路复用D. 传输速率慢3. 在移动通信中,以下哪个频段被广泛用于蜂窝网络?A. VHFB. UHFC. SHFD. EHF4. 以下哪个是调制的基本原理?A. 改变信号的频率以适应传输媒介B. 改变信号的振幅以适应传输媒介C. 改变信号的相位以适应传输媒介D. 所有以上选项5. 以下哪种编码方式不属于数字信号编码?A. PCMB. FSKC. PSKD. QAM二、填空题(每空1分,共10分)6. 通信的三个基本要素包括信源、__________和信宿。
7. 信号的带宽是指信号所包含的频率范围,通常用__________来表示。
8. 在数字通信中,__________是指在单位时间内传输的比特数。
9. 移动通信系统中,__________技术可以有效地减少多径效应的影响。
10. 光纤通信利用的是光的__________原理。
三、简答题(每题5分,共20分)11. 简述模拟信号与数字信号的区别。
12. 描述调制在通信系统中的作用。
13. 解释什么是信道容量,并给出其计算公式。
14. 阐述移动通信中的多径传播现象及其影响。
四、计算题(每题10分,共20分)15. 假设有一个通信系统,其信道带宽为3000Hz,信噪比为30dB,求该系统的信道容量。
16. 给定一个数字信号的比特率是256kbps,如果使用8-PSK调制方式,求该信号的传输速率。
五、论述题(每题15分,共30分)17. 论述现代通信系统中多路复用技术的应用及其重要性。
18. 讨论移动通信中的干扰类型及其对通信质量的影响。
参考答案:一、选择题1. D2. D3. B4. D5. B二、填空题6. 信道7. Hz(赫兹)8. 比特率9. RAKE接收机10. 反射三、简答题11. 模拟信号是连续变化的信号,可以是时间的任何值;数字信号是离散的,只有有限的状态。
数字通信考试试题

数字通信考试试题一、选择题(每题 3 分,共 30 分)1、在数字通信系统中,以下哪个不是数字信号的优点?()A 抗干扰能力强B 便于加密C 传输效率高D 易于存储2、数字通信系统中,抽样定理要求抽样频率至少是信号最高频率的()A 1 倍B 2 倍C 3 倍D 4 倍3、在 PCM 编码中,采用非均匀量化的目的是()A 提高小信号的量化信噪比B 降低编码的复杂度C 减少量化误差D 提高编码效率4、以下哪种数字调制方式带宽利用率最高?()A ASKB FSKC PSKD QAM5、在同步数字系列(SDH)中,STM-1 的速率是()A 155520 Mbit/sB 622080 Mbit/sC 2048 Mbit/sD 1544 Mbit/s6、差错控制编码中,能检测出多位错误并能纠正一位错误的编码是()A 奇偶校验码B 循环冗余校验码C 海明码D 卷积码7、以下哪个不是数字通信中的同步技术?()A 位同步B 帧同步C 网同步D 频率同步8、在数字通信系统中,信源编码的主要目的是()A 提高传输效率B 增强抗干扰能力C 保证通信的保密性D 实现同步9、以下哪种复用技术可以在同一时间传输多个信号?()A 频分复用B 时分复用C 码分复用D 以上都是10、数字通信系统中,衡量通信系统有效性的指标是()A 误码率B 信噪比C 传输速率D 带宽二、填空题(每题 3 分,共 30 分)1、数字通信系统的主要性能指标包括有效性和()。
2、数字基带信号的功率谱包含连续谱和()。
3、在数字调制中,ASK 是指()。
4、常见的差错控制方式有前向纠错、检错重发和()。
5、数字通信中的同步包括()、位同步、帧同步和网同步。
6、信源编码可分为()和熵编码两类。
7、均匀量化的量化间隔是()。
8、数字复接的方法主要有同步复接和()复接。
9、数字通信系统中,加性噪声通常可以分为()噪声和脉冲噪声。
10、在 QPSK 调制中,每个码元携带()比特的信息。
东南大学通信原理试卷及参考答案

东南大学考试卷( A 卷)课程名称通信原理考试学期04-05-3 得分适用专业考试形式闭卷考试时间长度150分钟Section A(30%): True or False (Give your reason if False,2% for each question)1. A typical mobile radio channel is a free propagation, linear, and time invariant channel.( )2.The power spectral density of a stationary process is always nonnegative. ( )3.In a communication system, noise is unwanted and over which we have incompletecontrol. ( ) 4.If a random process is stationary, it is ergodic; if a Gaussian random process is stationary,then it is also strictly stationary. ( ) 5.Double Sideband-Suppressed Carrier (DSB-SC), Single Sideband (SSB), and FrequencyModulation (FM) are all linear modulation schemes. ( ) 6.Figure of merit (defined as (SNR)O/(SNR)C) of AM of DSB-SC is 1/3, and figure of meritof Amplitude Modulation (AM) is less than or equal to 1/3. ( )7. -law is a nonlinear compression law and A-law is a linear compression law. ( )8.The matched filter at the receiver maximizes the peak pulse signal-to-noise ratio, thus isoptimal in a baseband data transmission system with Inter-Symbol Interference (ISI).( ) 9.Correlative-level coding (also known as partial-response signaling) schemes are used toavoid ISI. ( ) 10.Time-Division Multiplexing (TDM) is used in Asymmetric Digital Subscriber Lines(ADSL) to separate voice signals and data transmission. ( ) 11.If coefficients of an equalizer is adjusted using the Least-Mean-Square (LMS) algorithmadaptively, then the matched filter in front of the equalizer is not necessary. ( ) 12.In an M-ary Phase-Shift Keying (M-PSK) system, if the average probability of symbolerror is P e, then the average Bit Error Rate (BER) of the system is P e/log2M. ( ) 13.With the same Signal-to-Noise Ratio (SNR), 16-ary Quadrature Amplitude Modulation(16-QAM) has better performance than 16-ary Phase-Shift Keying (16-PSK). The reason is that 16-QAM has constant envelop. ( ) 14.With the same SNR, Minimum Shift Keying (MSK) has better performance than Sunde’sFrequency-Shift Keying (FSK). They are both Continuous-Phase Frequency-Shift Keying (CPFSK). ( ) 15.If the largest frequency component of an band-limited signal X(t) is at 100 Hz, then thecorresponding Nyquist rate is 200 Hz. ( )共10 页第1 页Section B(30%): Fill in the Blanks (3% for each question)1.The power spectral density of a stationary process X(t) is S X(f), then the autocorrelationfunction of X(t) is R X(t) = .2. A random process Y(t) is defined as Y(t) = X(t) cos(2πf c t + Θ), where X(t) is a stationaryprocess, f c is a constant frequency, and the phase Θis randomly distributed over the interval [0, 2π]. Suppose the power spectral density of X(t) is S X(f), the power spectral density of Y(t) is S Y(f) = .3.In a Frequency Modulation (FM) system, the modulating signal is m(t) = 2 cos (6πt) V, thefrequency sensitivity is k f = 0.3 Hz/V. Using Carson’s rule, bandwidth of the FM signal is approximately Hz.4.An analog signal is first encoded into a binary Pulse-Code Modulation (PCM) wave.Sampling rate of the PCM system is 8 kHz, number of representation levels is 64. The binary PCM wave is transmitted over a baseband channel using a 4-ary Pulse-Amplitude Modulation (PAM) (that is, a PAM with 4 amplitude levels). The minimum bandwidth requirement for transmitting the PAM wave is kHz.5.Basic operations performed in the transmitter of a PCM systeminclude , , and .6.Bandwidth efficiency of 4-ary Quadrature Amplitude Modulation (QAM) is ;bandwidth efficiency of 8-ary Phase-Shift Keying (8PSK) is .7.In a Delta Modulation (DM) system, sampling rate is f s = 8 kHz and step size is ∆ = 0.1 V.If the input to the DM system is a 1 kHz sinusoidal signal, then to avoid slope overload, the maximum amplitude of this input signal is V.8.12 different message signals, each with a bandwidth of 20 kHz, are to be multiplexed andtransmitted. If the multiplexing and modulation methods are Frequency-Division Multiplexing (FDM) and Single-Sideband Modulation (SSB), respectively, then the minimum bandwidth required is kHz; if the multiplexing and modulation methods are Time-Division Multiplexing (TDM) and PAM, then the minimum bandwidth required is kHz;9.The binary data sequence {b k} = 1010110 is applied to a duobinary (class I partialresponse) system with precoding, as shown in Fig. P1-9 (see next page), where d k = b k⊕d k-1, ⊕denotes modulo-two addition, and a k= 2×d k–1. The initial value of d k is 1.The output of the duobinary encoder is {c k} = . If at the receiving end, the first received digit is 1.25 due to noise, then the receiver output is ˆ{}k b = .共10 页第2 页共 10 页 第 3 页Fig. P1-910. A communication system has the signal-space diagram shown in Fig. P1-10, wheremessage points have equal probability of transmitting. Assume communication channel in this system is Additive White Gaussian Noise (AWGN) channel, and E/N 0 is 12, where N 0 is single-sideband power spectral density of the AWGN. Using union band, theaverage probability of symbol error is overbounded as P e ≤ . (Express using complementary error function erfc(⋅).)1()t φ2()t φ120°120°Message point 1Message point 2Message point 3EFig. P1-10共 10 页 第 4 页Section C(40%): Calculations (8% for each question)1. In a coherent Binary Phase-Shift Keying (BPSK) system, symbols 1 and 0 are representedby signals s 1(t) and s 2(t), respectively.The signals are defined by12())0())c b c s t f t t T s t f t πππ⎧=⎪⎪≤≤⎨⎪=+⎪⎩where E b is the transmitted signal energy per bit, and T b is one bit duration.a) Determine the basis function(s) of coherent BPSK signal constellation; b) Plot the signal-space diagram of coherent BPSK system; c) Determine the error probability of BPSK;d) If there is a phase error ϕ between the phase references of the transmitter andreceiver, determine the error probability of BPSK in this condition again.2. Spectrum of a message signal m(t) is shown in Fig. P3-2. This message signal is DoubleSideband-Suppressed Carrier (DSB-SC) modulated with a carrier wave A c cos(2πf c t). a) If f c = 2 kHz, plot the spectrum of the modulated signal s(t); b) What is the baseband bandwidth W of the message signal m(t)?c) What is the transmission bandwidth B T of the DSB-SC modulated signal?d) What is the lowest value of f c that keeps the DSB-SC modulation from sidebandoverlap?f1 kHz -1 kHzFig. P3-2共 10 页 第 5 页3. Consider a Quadriphase-Shift Keying (QPSK) system. The transmitted signal set isdefined as:cos[2(21)/4],0()0, otherwise c i f t i t Ts t ππ+-≤≤⎧=⎨⎩where i = 1, 2, 3, 4. Every two input bits select one of the signals in transmitted signalset to transmit. The rule of mapping is 10 → s 1(t), 00 → s 2(t), 01 → s 3(t), 11 → s 4(t). a) Determine the basis function(s) of QPSK signal constellation; b) Express s i (t) using the basis function(s);c) If the input binary sequence is 01101000, and suppose fc = 2/T, plot the QPSKwaveform;d) Is the QPSK waveform continuous phase?4. Consider the signal s(t) shown in Fig. P3-4,a) Assuming h(t) is the matched filter of s (t), plot the impulse response of h (t); b) When s (t) is applied to h (t), plot the matched filter output in the time domain.tT0A-A2T/3T/3s(t)Fig. P3-45. Suppose X(t) = Acos(2πft – Θ), where A is a constant, and f and Θ are independent. Θ isuniformly distributed over the interval [0, 2π]. Determine the power spectrum density of X(t) in terms of the probability density function of the frequency f.共 10 页 第 6 页通信原理期终考试参考答案和评分标准考试学期:04-05-3Section A: (30分)1. ⨯ The mobile radio channel is typically time variant.2. √3. √4. ⨯ Stationary is not necessary ergodic.5. ⨯ FM is not a linear modulation scheme6. ⨯ Figure of merit of DSB-SC is 1, not 1/3.7. ⨯ A-law is also a nonlinear compression law.8. ⨯ The matched filter is optimal with AWGN channel.9. ⨯ Correlative-level coding is to use ISI to achieve 2W signaling rate in abandwidth of W Hz. 10. ⨯ FDM is used in ADSL. 11. √12. ⨯ The BER is usually not P e /log 2M. 13. ⨯ 16-QAM is not constant envelop. 14. √ 15. √Section B: (30分) 1.()exp(2)X S f j f df πτ∞-∞⎰共 10 页 第 7 页2.1[()()]4X c X c S f f S f f -++ 3. 7.2 4. 125. Sampling, Quantizing, and Encoding6. 1, 1.57. 1.278. 240, 2409. 0 -2 0 2 0 0 2, 0010110 10. erfc(3)Section C:(40分)1.(a) The basis function is:1()),0c b t f t t T φπ=≤≤. (2分) (b) The signal-space diagram is: (2分)φ1(t)(c) The error probability is 1erfc 2e P =. (2分) (d) With phase error ϕ, the error probability becomes 1erfc 2e P ϕ⎫=⎪⎪⎭. (2分)2. (a) The spectrum is: (2分)共 10 页 第 8 页2 kHz -2 kHz0S(f)f(b) W = 1 kHz; (2分) (c) B T = 2 kHz; (2分)(d) To avoid sideband overlap, the lowest frequency is 1 kHz. (2分)3. (a) The basis functions are: (2分)122()cos(2),02()sin(2),0c c t f t t T Tt f t t T T φπφπ⎧=≤≤⎪⎪⎨⎪=≤≤⎪⎩(b)12()cos (21)()sin (21)(),1,2,3,42424i T T s t i t i t i ππφφ⎡⎤⎡⎤=---=⎢⎥⎢⎥⎣⎦⎣⎦ (2分)(c) The QPSK waveform is: (2分)(d) The QPSK waveform is not continuous phase. (2分)4. (a) h(t) is shown below, where k is a positive constant. (4分)共 10 页 第 9 页tT0kA-kAT/32T/3h(t)(b) The filter output is shown below. (4分)tT 0-kA 2T/3T/32T/3Response of h(t) to s(t)-kA 2T4T/35T/32T5. The autocorrelation function of X(t) is: (2分)22()[()()][cos(22)cos(2)][cos(42)cos(2)]2X R E X t X t A E Ft F Ft A E Ft F F ττππτπππτπτ=+=+-Θ-Θ=+-Θ+ Since Θ is uniformly distributed over the interval [0, 2π], we get: (2分)共 10 页 第 10 页22()[cos(2)]2()cos(2)2X F A R E F A f f f df τπτπτ∞-∞==⎰ Since X(t) is a real-valued random process, S X (f) is an even function of frequency, we also have: (2分)()()exp(2)()cos(2)X X X R S f j f dfS f j f dfτπτπτ∞-∞∞-∞==⎰⎰where S x (f) is the power spectrum density of X(t). Therefore, we get: (2分)2()()2X F A S f f f =。
东南大学数字通信试卷(附答案)

东南大学考试卷(A卷)课程名称 数 字 通 信 考试学期 04-05-2得分适用专业无线电工程系 考试形式闭 卷 考试时间长度120分钟共 页Section A:True or False (15%)1. 1.When the period is exactly 2m, the PN sequence is called amaximal-length-sequence or simply m-sequence.2. 2.For a period of the maximal-length sequence, the autocorrelationfunction is similar to that of a random binary wave.3. 3.For slow-frequency hopping,symbol rate R s of MFSK signal is aninteger multiple of the hop rate R h. That is, the carrier frequency will change or hop several times during the transmission of one symbol. 4. 4.Frequency diversity can be done by choosing a frequency spacingequal to or less than the coherence bandwidth of the channel.5. 5.The mutual information of a channel therefore depends not only onthe channel but also on the way in which the channel used.6. 6.Shannon’s second theorem specifies the channel capacity C as afundamental limit on the rate at which the transmission of reliable error-free messages can take place over a discrete memoryless channel and how to construct a good code.7.7.The syndrome depends not only on the error pattern, but also onthe transmitted code word.8.8.Any pair of primitive polynomials of degree m whose correspondingshift registers generate m-sequences of period 2m-1 can be used to generate a Gold sequence.9.9.Any source code satisfies the Kraft-McMillan inequality can be aprefix code.10.10.Let a discrete memoryless source with an alphabet ϕ have entropyHϕ and produce symbols once every s T seconds. Let a discrete ()memoryless channel have capacity and be used once everyC c Tseconds. Then , if()ϕ≥s cH CT T , there exists a coding scheme for whichthe source output can be transmitted over the channel and be reconstructed with an arbitrarily small probability of error. Section B:Fill in the blanks (35%)1. 1.The two commonly used types of spread-spectrum modulation:and .2. 2. A pseudo-noise (PN) sequence is a periodic binary sequence with awaveform that is usually generated by means of a.3. 3.Due to , wireless communication is no longeridealized AWGN channel model.4. 4.There are the following diversity techniques in our discussion ,diversity, diversity, diversity.5. 5.Three major sources of degradation in wireless communicationsare, , and ; the latter two are byproducts of multipath.6. 6.The information capacity of a continuous channel of bandwidth Bhertz, perturbed by additive white Gaussian noise of power spectral density N0/2 and limited in bandwidth to B, is given by.7.7.The or syndrome) is definedas: .8.8.For Linear Block Codes ,Correct all error patterns of Hammingweight w(e)≤t2 ,if and only if .9.9.TCM Combine and as a single entity toattain a more effective utilization of the availableand .10.10.In a DS/BPSK system, the feedback shift register used togenerate the PN sequence has length m=19, than the processing gain is .11.11.Let X represent the outcome of a single roll of a fair die(骰子).The entropy of X is .12.12. A voice-grade channel of the telephone network has a bandwidthof 3.4kHz,the information capacity of the telephone channel for a signal-to-noise ratio of 30dB is , the minimum signal-to-noise ratio required to support informationtransmission through the telephone channel at the rate of 9,600b/s is .13. 13. For a m-sequence generated by a linear feedback shift register oflength 5, the total number of runs is , number of length-two runs is , the autocorrelation R(j)= (j ≠0).14. 14. If the coherent bandwidth of the channel is small compared to themessage bandwidth, the fading is said to be . If the coherence time of the channel is large compared to the duration of the signal duration, the fading is said to be .15. 15. A source emits one of five symbols with probabilities 1/2, 1/4, 1/8, 1/16, 1/16, respectively. The successive symbols emitted by the source are statistically independent. The entropy of the source is 01234,,s and s s s s . The average code-word length for any distortionless source encoding scheme for this source is bounded as .16. 16. For a finite variance σ2, the random variable has the largest differential entropy attainable by any random variable, and the entropy is uniquely determined by the .17. 17. Set partitioning design partitions the M-ary constellation ofinterest successively and has progressively larger increasingbetween their respective signal points. 18. 18. code and code have an errorperformance within a hair’s breadth of Shannon’s theoretical limit on channel capacity in a physically realizable fashion.19. 19. When an infinite number of decoding errors are caused by a finitenumber of transmission errors, the convolutional code is called a .Section C :Problems (50%)1.A radio link uses a pair of 2m dish antennas with an efficiency of 70 percent each, as transmitting and receiving antennas. Other specifications of the link are:Transmitted power = 2 dBW (not include the power gain of antenna ) Carrier frequency = 12 GHzDistance of the receiver form the transmitter = 200 m Calculate (a) the free-space loss,(b) the power gain of each antenna,(c)the received power in dBW.2. A computer executes four instructions that are designated by the code words (00,01,10,11). Assuming that the instructions are used independently with probabilities(1/2,1/8,1/8,1/4).(a) (a) Construct a Huffman code for the instructions.(b) (b) Calculate the percentage by which the number of bits used for the instructions may be reduced by the use of a Huffman code.3. Consider the (15,8) cyclic code defined by the generator polynomial37()1g X X X X =+++(a) (a) Develop the encoder for this code.(b) (b) Get the generator matrix and the parity-check matrix.(c) (c) Construct a systematic code word for the message sequence 10110011.(d) (d) The received word is 110001000000001, determine the syndrome polynomial s(X) for this received word.4. Consider the rate r = 1/3, constraint length K = 3 convolutional encoder. The generator sequences the encoder are as follows:(1)(1,0,0)g = ,, (2)(1,0,1)g =(3)(1,1,1)g =(a) (a) Draw the block diagram of the encoder. (b) (b) Construct the code tree(c) (c) Construct the signal-flow graph and obtain the input-output state equations.(d) (d) Determine the encoder output produced by the message sequence 10111….(e) (e) The received sequence is 110,001,101,110,000,011. Use the Viterbialgorithm to compute the decoded sequence. 答案Section A :True or False (每题1.5分,共15分)11. 1. When the period is exactly 2m, the PN sequence is called amaximal-length-sequence or simply m-sequence. (F )12. 2. For a period of the maximal-length sequence, the autocorrelationfunction is similar to that of a random binary wave. (T )13. 3. For slow-frequency hopping ,symbol rate R s of MFSK signal is aninteger multiple of the hop rate R h . That is, the carrier frequency will change or hop several times during the transmission of one symbol . (F ) 14. 4. Frequency diversity can be done by choosing a frequency spacingequal to or less than the coherence bandwidth of the channel. (F ) 15. 5. The mutual information of a channel therefore depends not only onthe channel but also on the way in which the channel used. (T ) 16. 6. Shannon’s second theorem specifies the channel capacity C as afundamental limit on the rate at which the transmission of reliable error-free messages can take place over a discrete memoryless channel and how to construct a good code. (F )17. 7. The syndrome depends not only on the error pattern, but also onthe transmitted code word. (F )18. 8. Any pair of primitive polynomials of degree m whose correspondingshift registers generate m-sequences of period 2m -1 can be used to generate a Gold sequence. (F )19. 9. Any source code satisfies the Kraft-McMillan inequality can be aprefix code. (F )20. 10. Let a discrete memoryless source with an alphabet ϕ haveentropy ()H ϕ and produce symbols once every s T seconds. Let a discrete memoryless channel have capacity and be used once every seconds. Then , ifC c T ()s cH T T Cϕ≥ , there exists a coding scheme for which the source output can be transmitted over the channel and be reconstructed with an arbitrarily small probability of error. (F )Section B :Fill in the blanks (每空1分,共35分)20. 1. The two commonly used types of spread-spectrum modulation:direct sequence and frequency hopping.21. 2. A pseudo-noise (PN) sequence is a periodic binary sequence with anoiselike waveform that is usually generated by means of a feedback shift register .22. 3. Due to multipath , wireless communication is no longer idealizedAWGN channel model.23. 4. There are the following diversity techniques in our discussion ,Frequency diversity ,Time diversity ,Space diversity.24. 5. Three major sources of degradation in wireless communicationsare co-channel interference , fading , and delay spread ; the latter two are byproducts of multipath .25. 6. The information capacity of a continuous channel of bandwidth Bhertz, perturbed by additive white Gaussian noise of power spectral density N 0/2 and limited in bandwidth to B, is given by20log (1) bits per second =+PC B N B .26. 7. The error-syndrome vector (or syndrome) is defined as: s = rH T27. 8. For Linear Block Codes ,Correct all error patterns of Hammingweight w (e )≤t 2 ,if and only if d min ≥ 2 t 2 + 1.28. 9. TCM Combine coding and modulation as a single entity to attain amore effective utilization of the available bandwidth and power .29. 10. In a DS/BPSK system, the feedback shift register used togenerate the PN sequence has length m=19, than the processing gain is 57dB .30. 11. Let X represent the outcome of a single roll of a fair die(骰子).The entropy of X is log 2(6) = 2.586 bits/symbol.31. 12. A voice-grade channel of the telephone network has a bandwidthof 3.4kHz,the information capacity of the telephone channel for a signal-to-noise ratio of 30dB is 33.9 kbits/second ,the minimum signal-to-noise ratio required to support information transmission through the telephone channel at the rate of 9,600b/s is 7.8dB . 32. 13. For a m-sequence generated by a linear feedback shift register oflength 5, the total number of runs is 16 , number of length-two runs is 4 , the autocorrelation R(j)= -1/31 (j ≠0).33. 14. If the coherent bandwidth of the channel is small compared to themessage bandwidth, the fading is said to be frequency selective . If the coherence time of the channel is large compared to the duration of the signal duration, the fading is said to be time nonselective or time flat. 34. 15. A source emits one of five symbols with probabilities 1/2, 1/4, 1/8, 1/16, 1/16, respectively. The successivesymbols emitted by the source are statistically independent. The entropy of the source is 15/8=1.875bits/symbol 01234,, s ands s s s . The average code-word length for any distortionless source encoding scheme for this source is bounded as ϕ≥()L H .35. 16. For a finite variance σ2, the Guassian random variable has thelargest differential entropy attainable by any random variable, and the entropy is uniquely determined by the variance of X .36. 17. Set partitioning design partitions the M-ary constellation ofinterest successively and has progressively larger increasing minimum Euclidean distance between their respective signal points.37. 18. Turbo codes and Low-density parity-check codes have an errorperformance within a hair’s breadth of Shannon’s theoretical limit on channel capacity in a physically realizable fashion.38. 19. When an infinite number of decoding errors are caused by a finitenumber of transmission errors, the convolutional code is called a catastrophic code.Section C :Problems1.A radio link uses a pair of 2m dish antennas with an efficiency of 70 percent each, as transmitting and receiving antennas. Other specifications of the link are:Transmitted power = 2 dBW (not include the power gain of antenna ) Carrier frequency = 12 GHzDistance of the receiver form the transmitter = 200 m Calculate (a)the free-space loss,(b) the power gain of each antenna,(c)the received power in dBW. (本题10分)Solution:(a) Free-space loss 21010log 4λπ⎛⎞=⎜⎟⎝⎠freespace L d8910310/12/1020log 1004200π⎛⎞×==⎜⎟××⎝⎠dB −(b) The power gain of each antenna is 1010102410log 10log 10log πλ××⎛⎞==⎜⎟⎝⎠t r A G G ()1028940.710log 310/12/1046.46ππ⎛⎞×××⎜⎟=⎜⎟×⎝⎠=dB(c) The received power = transmitted power + G t +G r + free-space loss = 2 + 46.46 + 46.46 + (-100) = -5.08dBW2. A computer executes four instructions that are designated by the codewords (00,01,10,11). Assuming that the instructions are used independently with probabilities(1/2,1/8,1/8,1/4).(c)(a)Construct a Huffman code for the instructions.(d)(b)Calculate the percentage by which the number of bits used for theinstructions may be reduced by the use of a Huffman code.(本题10分)Solution:(a) As low as possibleAs high as possibleComputer code Probability Huffman Code00 1/2 111 1/4 0100001 1/810 1/8 001(e)(c)The number of bits used for the constructions based on thecomputer code, in a probabilistic sense, is equal to3. Consider the (15,8) cyclic code defined by the generator polynomial37()1g X X X X =+++842()1h X X X X X (++++)=(e) (a) Develop the encoder for this code.(f) (b) Get the generator matrix and the parity-check matrix.(g) (c) Construct a systematic code word for the message sequence 10110011.(h) (d) The received word is 110001000000001, determine the syndrome polynomial s(X) for this received word. (本题15分) Solution: (a)(b) generator matrix3724822353346445755686679177810()1()()()()()()()=+++=+++=+++=+++=+++=+++=+++=+++g X X X X Xg X X X X X 9101112314X g X X X X X X g X X X X X X g X X X X XX g X X X X X X g X X X X X X g X X X X X110100010000000011010001000000001101000100000000110100010000000011010001000000001101000100000000110100010000000011010001⎡⎤⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥′=⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎣⎦G 11010001000000001101000100000000110100010000000011010001000011011100000100001101110000010011100110000001010100010001⎡⎤⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥=⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎣⎦G Parity-check matrix8146789157891012689101113791011()1()()()X h X X X X X X h X X X X X X X h X X X X X XX h X X X X X X −−−−=++++=++++=++++=++++121481011121315911121141610121314()()()3X h X X X X X X X h X X X X X X X h X X X X X X −−−=++++=++++=++++100010111000000010001011100000001000101110000'000100010111000000010001011100000001000101110000000100010111⎡⎤⎢⎥⎢⎥⎢⎥⎢⎥=⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎣⎦H 100000010001011010000011001110001000001100111000100010111000000010001011100000001000101110000000100010111⎡⎤⎢⎥⎢⎥⎢⎥⎢⎥=⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎣⎦H (c) For the message sequence 10110011, the corresponding message polynomial is236()1=++++m X X X X X 7 Firstly, 79101314()−=++++n k X m X X X X X X Secondly, divide ()−n k X m X by ,()g X 7910131423467637371111++++++++=++++++++++X X X X X X X X X X X X X X X X X XThe remainder is 234()1=++++b X X X X X 64 Hence, the desired code polynomial is234679101314()()()1−=+=+++++++++n k c X b X X m X X X X X X X X X X The systematic code word is 1011101,10110011(d) The code polynomial corresponding to the received word 110001000000001 is51()1+=++r X X X X divide by , we get()r X ()g X 5142567337371+111+++++=++++++++++X X X X X X X X X X X X X X X XHence, the syndrome polynomial s(X) for this received word is (0110011) 25()=+++s X X X X X 64. Consider the rate r = 1/3, constraint length K = 3 convolutional encoder. The generator sequences the encoder are as follows:(1)(1,0,0)g = , , (2)(1,0,1)g =(3)(1,1,1)g =(f) (a) Draw the block diagram of the encoder. (g) (b) Construct the code tree(h) (c) Construct the signal-flow graph and obtain the input-output state equations.(i) (d) Determine the encoder output produced by the message sequence 10111….(j) (e) The received sequence is 110,001,101,110,000,011. Use the Viterbialgorithm to compute the decoded sequence. (本题15分) Solution:(a) Encoder diagram (b) Code treea b c d a b c d(f) (d) Encoder output produced by the message sequence 10111 is 111, 001, 100, 110, 101, 010, 011, 000, …(g) (e) The received sequence is 110,001,101,110,000,011. The correct sequence is 111, 001, 100, 110, 010, 011. The decoded sequence is 101100.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
东南大学考试卷(A卷)课程名称 数 字 通 信 考试学期 04-05-2得分适用专业无线电工程系 考试形式闭 卷 考试时间长度120分钟共 页Section A:True or False (15%)1. 1.When the period is exactly 2m, the PN sequence is called amaximal-length-sequence or simply m-sequence.2. 2.For a period of the maximal-length sequence, the autocorrelationfunction is similar to that of a random binary wave.3. 3.For slow-frequency hopping,symbol rate R s of MFSK signal is aninteger multiple of the hop rate R h. That is, the carrier frequency will change or hop several times during the transmission of one symbol. 4. 4.Frequency diversity can be done by choosing a frequency spacingequal to or less than the coherence bandwidth of the channel.5. 5.The mutual information of a channel therefore depends not only onthe channel but also on the way in which the channel used.6. 6.Shannon’s second theorem specifies the channel capacity C as afundamental limit on the rate at which the transmission of reliable error-free messages can take place over a discrete memoryless channel and how to construct a good code.7.7.The syndrome depends not only on the error pattern, but also onthe transmitted code word.8.8.Any pair of primitive polynomials of degree m whose correspondingshift registers generate m-sequences of period 2m-1 can be used to generate a Gold sequence.9.9.Any source code satisfies the Kraft-McMillan inequality can be aprefix code.10.10.Let a discrete memoryless source with an alphabet ϕ have entropyHϕ and produce symbols once every s T seconds. Let a discrete ()memoryless channel have capacity and be used once everyC c Tseconds. Then , if()ϕ≥s cH CT T , there exists a coding scheme for whichthe source output can be transmitted over the channel and be reconstructed with an arbitrarily small probability of error. Section B:Fill in the blanks (35%)1. 1.The two commonly used types of spread-spectrum modulation:and .2. 2. A pseudo-noise (PN) sequence is a periodic binary sequence with awaveform that is usually generated by means of a.3. 3.Due to , wireless communication is no longeridealized AWGN channel model.4. 4.There are the following diversity techniques in our discussion ,diversity, diversity, diversity.5. 5.Three major sources of degradation in wireless communicationsare, , and ; the latter two are byproducts of multipath.6. 6.The information capacity of a continuous channel of bandwidth Bhertz, perturbed by additive white Gaussian noise of power spectral density N0/2 and limited in bandwidth to B, is given by.7.7.The or syndrome) is definedas: .8.8.For Linear Block Codes ,Correct all error patterns of Hammingweight w(e)≤t2 ,if and only if .9.9.TCM Combine and as a single entity toattain a more effective utilization of the availableand .10.10.In a DS/BPSK system, the feedback shift register used togenerate the PN sequence has length m=19, than the processing gain is .11.11.Let X represent the outcome of a single roll of a fair die(骰子).The entropy of X is .12.12. A voice-grade channel of the telephone network has a bandwidthof 3.4kHz,the information capacity of the telephone channel for a signal-to-noise ratio of 30dB is , the minimum signal-to-noise ratio required to support informationtransmission through the telephone channel at the rate of 9,600b/s is .13. 13. For a m-sequence generated by a linear feedback shift register oflength 5, the total number of runs is , number of length-two runs is , the autocorrelation R(j)= (j ≠0).14. 14. If the coherent bandwidth of the channel is small compared to themessage bandwidth, the fading is said to be . If the coherence time of the channel is large compared to the duration of the signal duration, the fading is said to be .15. 15. A source emits one of five symbols with probabilities 1/2, 1/4, 1/8, 1/16, 1/16, respectively. The successive symbols emitted by the source are statistically independent. The entropy of the source is 01234,,s and s s s s . The average code-word length for any distortionless source encoding scheme for this source is bounded as .16. 16. For a finite variance σ2, the random variable has the largest differential entropy attainable by any random variable, and the entropy is uniquely determined by the .17. 17. Set partitioning design partitions the M-ary constellation ofinterest successively and has progressively larger increasingbetween their respective signal points. 18. 18. code and code have an errorperformance within a hair’s breadth of Shannon’s theoretical limit on channel capacity in a physically realizable fashion.19. 19. When an infinite number of decoding errors are caused by a finitenumber of transmission errors, the convolutional code is called a .Section C :Problems (50%)1.A radio link uses a pair of 2m dish antennas with an efficiency of 70 percent each, as transmitting and receiving antennas. Other specifications of the link are:Transmitted power = 2 dBW (not include the power gain of antenna ) Carrier frequency = 12 GHzDistance of the receiver form the transmitter = 200 m Calculate (a) the free-space loss,(b) the power gain of each antenna,(c)the received power in dBW.2. A computer executes four instructions that are designated by the code words (00,01,10,11). Assuming that the instructions are used independently with probabilities(1/2,1/8,1/8,1/4).(a) (a) Construct a Huffman code for the instructions.(b) (b) Calculate the percentage by which the number of bits used for the instructions may be reduced by the use of a Huffman code.3. Consider the (15,8) cyclic code defined by the generator polynomial37()1g X X X X =+++(a) (a) Develop the encoder for this code.(b) (b) Get the generator matrix and the parity-check matrix.(c) (c) Construct a systematic code word for the message sequence 10110011.(d) (d) The received word is 110001000000001, determine the syndrome polynomial s(X) for this received word.4. Consider the rate r = 1/3, constraint length K = 3 convolutional encoder. The generator sequences the encoder are as follows:(1)(1,0,0)g = ,, (2)(1,0,1)g =(3)(1,1,1)g =(a) (a) Draw the block diagram of the encoder. (b) (b) Construct the code tree(c) (c) Construct the signal-flow graph and obtain the input-output state equations.(d) (d) Determine the encoder output produced by the message sequence 10111….(e) (e) The received sequence is 110,001,101,110,000,011. Use the Viterbialgorithm to compute the decoded sequence. 答案Section A :True or False (每题1.5分,共15分)11. 1. When the period is exactly 2m, the PN sequence is called amaximal-length-sequence or simply m-sequence. (F )12. 2. For a period of the maximal-length sequence, the autocorrelationfunction is similar to that of a random binary wave. (T )13. 3. For slow-frequency hopping ,symbol rate R s of MFSK signal is aninteger multiple of the hop rate R h . That is, the carrier frequency will change or hop several times during the transmission of one symbol . (F ) 14. 4. Frequency diversity can be done by choosing a frequency spacingequal to or less than the coherence bandwidth of the channel. (F ) 15. 5. The mutual information of a channel therefore depends not only onthe channel but also on the way in which the channel used. (T ) 16. 6. Shannon’s second theorem specifies the channel capacity C as afundamental limit on the rate at which the transmission of reliable error-free messages can take place over a discrete memoryless channel and how to construct a good code. (F )17. 7. The syndrome depends not only on the error pattern, but also onthe transmitted code word. (F )18. 8. Any pair of primitive polynomials of degree m whose correspondingshift registers generate m-sequences of period 2m -1 can be used to generate a Gold sequence. (F )19. 9. Any source code satisfies the Kraft-McMillan inequality can be aprefix code. (F )20. 10. Let a discrete memoryless source with an alphabet ϕ haveentropy ()H ϕ and produce symbols once every s T seconds. Let a discrete memoryless channel have capacity and be used once every seconds. Then , ifC c T ()s cH T T Cϕ≥ , there exists a coding scheme for which the source output can be transmitted over the channel and be reconstructed with an arbitrarily small probability of error. (F )Section B :Fill in the blanks (每空1分,共35分)20. 1. The two commonly used types of spread-spectrum modulation:direct sequence and frequency hopping.21. 2. A pseudo-noise (PN) sequence is a periodic binary sequence with anoiselike waveform that is usually generated by means of a feedback shift register .22. 3. Due to multipath , wireless communication is no longer idealizedAWGN channel model.23. 4. There are the following diversity techniques in our discussion ,Frequency diversity ,Time diversity ,Space diversity.24. 5. Three major sources of degradation in wireless communicationsare co-channel interference , fading , and delay spread ; the latter two are byproducts of multipath .25. 6. The information capacity of a continuous channel of bandwidth Bhertz, perturbed by additive white Gaussian noise of power spectral density N 0/2 and limited in bandwidth to B, is given by20log (1) bits per second =+PC B N B .26. 7. The error-syndrome vector (or syndrome) is defined as: s = rH T27. 8. For Linear Block Codes ,Correct all error patterns of Hammingweight w (e )≤t 2 ,if and only if d min ≥ 2 t 2 + 1.28. 9. TCM Combine coding and modulation as a single entity to attain amore effective utilization of the available bandwidth and power .29. 10. In a DS/BPSK system, the feedback shift register used togenerate the PN sequence has length m=19, than the processing gain is 57dB .30. 11. Let X represent the outcome of a single roll of a fair die(骰子).The entropy of X is log 2(6) = 2.586 bits/symbol.31. 12. A voice-grade channel of the telephone network has a bandwidthof 3.4kHz,the information capacity of the telephone channel for a signal-to-noise ratio of 30dB is 33.9 kbits/second ,the minimum signal-to-noise ratio required to support information transmission through the telephone channel at the rate of 9,600b/s is 7.8dB . 32. 13. For a m-sequence generated by a linear feedback shift register oflength 5, the total number of runs is 16 , number of length-two runs is 4 , the autocorrelation R(j)= -1/31 (j ≠0).33. 14. If the coherent bandwidth of the channel is small compared to themessage bandwidth, the fading is said to be frequency selective . If the coherence time of the channel is large compared to the duration of the signal duration, the fading is said to be time nonselective or time flat. 34. 15. A source emits one of five symbols with probabilities 1/2, 1/4, 1/8, 1/16, 1/16, respectively. The successivesymbols emitted by the source are statistically independent. The entropy of the source is 15/8=1.875bits/symbol 01234,, s ands s s s . The average code-word length for any distortionless source encoding scheme for this source is bounded as ϕ≥()L H .35. 16. For a finite variance σ2, the Guassian random variable has thelargest differential entropy attainable by any random variable, and the entropy is uniquely determined by the variance of X .36. 17. Set partitioning design partitions the M-ary constellation ofinterest successively and has progressively larger increasing minimum Euclidean distance between their respective signal points.37. 18. Turbo codes and Low-density parity-check codes have an errorperformance within a hair’s breadth of Shannon’s theoretical limit on channel capacity in a physically realizable fashion.38. 19. When an infinite number of decoding errors are caused by a finitenumber of transmission errors, the convolutional code is called a catastrophic code.Section C :Problems1.A radio link uses a pair of 2m dish antennas with an efficiency of 70 percent each, as transmitting and receiving antennas. Other specifications of the link are:Transmitted power = 2 dBW (not include the power gain of antenna ) Carrier frequency = 12 GHzDistance of the receiver form the transmitter = 200 m Calculate (a)the free-space loss,(b) the power gain of each antenna,(c)the received power in dBW. (本题10分)Solution:(a) Free-space loss 21010log 4λπ⎛⎞=⎜⎟⎝⎠freespace L d8910310/12/1020log 1004200π⎛⎞×==⎜⎟××⎝⎠dB −(b) The power gain of each antenna is 1010102410log 10log 10log πλ××⎛⎞==⎜⎟⎝⎠t r A G G ()1028940.710log 310/12/1046.46ππ⎛⎞×××⎜⎟=⎜⎟×⎝⎠=dB(c) The received power = transmitted power + G t +G r + free-space loss = 2 + 46.46 + 46.46 + (-100) = -5.08dBW2. A computer executes four instructions that are designated by the codewords (00,01,10,11). Assuming that the instructions are used independently with probabilities(1/2,1/8,1/8,1/4).(c)(a)Construct a Huffman code for the instructions.(d)(b)Calculate the percentage by which the number of bits used for theinstructions may be reduced by the use of a Huffman code.(本题10分)Solution:(a) As low as possibleAs high as possibleComputer code Probability Huffman Code00 1/2 111 1/4 0100001 1/810 1/8 001(e)(c)The number of bits used for the constructions based on thecomputer code, in a probabilistic sense, is equal to3. Consider the (15,8) cyclic code defined by the generator polynomial37()1g X X X X =+++842()1h X X X X X (++++)=(e) (a) Develop the encoder for this code.(f) (b) Get the generator matrix and the parity-check matrix.(g) (c) Construct a systematic code word for the message sequence 10110011.(h) (d) The received word is 110001000000001, determine the syndrome polynomial s(X) for this received word. (本题15分) Solution: (a)(b) generator matrix3724822353346445755686679177810()1()()()()()()()=+++=+++=+++=+++=+++=+++=+++=+++g X X X X Xg X X X X X 9101112314X g X X X X X X g X X X X X X g X X X X XX g X X X X X X g X X X X X X g X X X X X110100010000000011010001000000001101000100000000110100010000000011010001000000001101000100000000110100010000000011010001⎡⎤⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥′=⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎣⎦G 11010001000000001101000100000000110100010000000011010001000011011100000100001101110000010011100110000001010100010001⎡⎤⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥=⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎣⎦G Parity-check matrix8146789157891012689101113791011()1()()()X h X X X X X X h X X X X X X X h X X X X X XX h X X X X X X −−−−=++++=++++=++++=++++121481011121315911121141610121314()()()3X h X X X X X X X h X X X X X X X h X X X X X X −−−=++++=++++=++++100010111000000010001011100000001000101110000'000100010111000000010001011100000001000101110000000100010111⎡⎤⎢⎥⎢⎥⎢⎥⎢⎥=⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎣⎦H 100000010001011010000011001110001000001100111000100010111000000010001011100000001000101110000000100010111⎡⎤⎢⎥⎢⎥⎢⎥⎢⎥=⎢⎥⎢⎥⎢⎥⎢⎥⎢⎥⎣⎦H (c) For the message sequence 10110011, the corresponding message polynomial is236()1=++++m X X X X X 7 Firstly, 79101314()−=++++n k X m X X X X X X Secondly, divide ()−n k X m X by ,()g X 7910131423467637371111++++++++=++++++++++X X X X X X X X X X X X X X X X X XThe remainder is 234()1=++++b X X X X X 64 Hence, the desired code polynomial is234679101314()()()1−=+=+++++++++n k c X b X X m X X X X X X X X X X The systematic code word is 1011101,10110011(d) The code polynomial corresponding to the received word 110001000000001 is51()1+=++r X X X X divide by , we get()r X ()g X 5142567337371+111+++++=++++++++++X X X X X X X X X X X X X X X XHence, the syndrome polynomial s(X) for this received word is (0110011) 25()=+++s X X X X X 64. Consider the rate r = 1/3, constraint length K = 3 convolutional encoder. The generator sequences the encoder are as follows:(1)(1,0,0)g = , , (2)(1,0,1)g =(3)(1,1,1)g =(f) (a) Draw the block diagram of the encoder. (g) (b) Construct the code tree(h) (c) Construct the signal-flow graph and obtain the input-output state equations.(i) (d) Determine the encoder output produced by the message sequence 10111….(j) (e) The received sequence is 110,001,101,110,000,011. Use the Viterbialgorithm to compute the decoded sequence. (本题15分) Solution:(a) Encoder diagram (b) Code treea b c d a b c d(f) (d) Encoder output produced by the message sequence 10111 is 111, 001, 100, 110, 101, 010, 011, 000, …(g) (e) The received sequence is 110,001,101,110,000,011. The correct sequence is 111, 001, 100, 110, 010, 011. The decoded sequence is 101100.。
