思科ASA5505防火墙配置成功实例
思科5505防火墙配置

asa 5505 常用配置2009-06-01 16:13asa 55051.配置防火墙名ciscoasa> enableciscoasa# configure terminalciscoasa(config)# hostname asa55052.配置telnetasa5505(config)#telnet 192.168.1.0 255.255.255.0 inside//允许内部接口192.168.1.0网段telnet防火墙3.配置密码asa5505(config)# password cisco//远程密码asa5505(config)# enable password cisco//特权模式密码4.配置IPasa5505(config)# interface vlan 2//进入vlan2asa5505(config-if)# ip address 218.xxx.37.222 255.255.255.192 //vlan2配置IPasa5505(config)#show ip address vlan2//验证配置5.端口加入vlanasa5505(config)# interface e0/3//进入接口e0/3asa5505(config-if)# switchport access vlan 3//接口e0/3加入vlan3asa5505(config)# interface vlan 3//进入vlan3asa5505(config-if)# ip address 10.10.10.36 255.255.255.224//vlan3配置IPasa5505(config-if)# nameif dmz//vlan3名asa5505(config-if)# no shutdown//开启asa5505(config-if)# show switch vlan//验证配置6.最大传输单元MTUasa5505(config)#mtu inside 1500//inside最大传输单元1500字节asa5505(config)#mtu outside 1500//outside最大传输单元1500字节asa5505(config)#mtu dmz 1500//dmz最大传输单元1500字节7.配置arp表的超时时间asa5505(config)#arp timeout 14400//arp表的超时时间14400秒8.FTP模式asa5505(config)#ftp mode passive//FTP被动模式9.配置域名asa5505(config)#domain-name 10.启动日志asa5505(config)#logging enable//启动日志asa5505(config)#logging asdm informational//启动asdm报告日志asa5505(config)#Show logging//验证配置11.启用http服务asa5505(config)#http serverenable//启动HTTP server,便于ASDM连接。
CiscoASA5505ipsecl2l配置

CiscoASA5505ipsecl2l配置CiscoASA5505 ipsec l2l配置Cisco ASA5505配置ASA(config)# crypto isakmp policy 10 #建立IKE策略,优先级为10ASA(config-isakmp-policy)# encryption 3des #使用3des加密ASA(config-isakmp-policy)# authentication pre-share #使用预共享的密码进行身份认证ASA(config-isakmp-policy)# hash md5 #指定hash算法为md5(其他sha、rsa)ASA(config-isakmp-policy)# lifetime 28800 #指定SA有效期时间。
默认86400秒,两端要一致ASA(config-isakmp-policy)# group 1 #指定密钥位数,1表示768位,2表示1024为,2更安全,更耗cpu资源ASA(config-isakmp-policy)# exitASA(config)# crypto isakmp key bj2legend add 210.82.111.121 #预共享密码,远程网关ipASA(config)# crypto ipsec transform-set bjicpark esp-3des esp-md5-hmac#定义一个IPSEC交换集,两端要一样ASA(config)# access-list bjparkvpn permit ip 172.18.5.0 255.255.255.128192.168.3.0 255.255.255.0 #定义加密通道ASA(config)# access-list bjparkvpn permit ip 172.18.5.0 255.255.255.128192.168.2.0 255.255.255.0ASA(config)# crypto map bjparkmap 20 match addressbjparkvpn #创建加密图ASA(config)# crypto map bjparkmap 20 set peer 210.82.111.121 #目标地址ASA(config)# crypto map bjparkmap 20 set transform-set bjpark #指定加密图使用的IPSEC交换集ASA(config)# crypto map bjparkmap interface outside #应用加密图到接口ASA(config)# crypto isakmp identity address #网关ID,默认IP地址,两端要一致ASA(config)# crypto isakmp enable outside #接口上开启ike ASA(config)# crypto isakmp nat-traversal 20 #支持nat穿越方正方御FG3000E防火墙配置:IKE协商模式:主动模式IKE算法:自动协商认证方式:预共享本地网关ID:无远程网关ID:无IPSec算法:自动协商高级选项:生存周期:ISAKMP SA:8小时0分0秒IPSec SA:24小时0分0秒支持DPD(Dead Peer Detection):选择打勾DPD探测频率:30秒DPD探测超时:10秒DPD超时操作:重新启动连接支持IP载荷压缩:不选择支持完美向前加密(PFS):不选择支持密钥重建(Rekeying):选择打勾重试次数:0相关知识点:对称加密或私有密钥加密:加密解密使用相同的私钥DES--数据加密标准 data encryption standard3DES--3倍数据加密标准 triple data encryption standardAES--高级加密标准 advanced encryption standard一些技术提供验证:MAC梷消息验证码 message authentication codeHMAC梷散列消息验证码 hash-based message authentication codeMD5和SHA是提供验证的散列函数对称加密被用于大容量数据,因为非对称加密站用大量cpu资源非对称或公共密钥加密:RSA rivest-shamir-adelman用公钥加密,私钥解密。
Cisco ASA5505防火墙详细配置教程及实际配置案例

Cisco ASA5505防火墙详细配置教程及实际配置案例interface Vlan2nameif outside ----------------------------------------对端口命名外端口security-level 0 ----------------------------------------设置端口等级ip address X.X.X.X 255.255.255.224 --------------------调试外网地址!interface Vlan3nameif inside ----------------------------------------对端口命名内端口security-level 100 ----------------------------------------调试外网地址ip address 192.168.1.1 255.255.255.0 --------------------设置端口等级!interface Ethernet0/0switchport access vlan 2 ----------------------------------------设置端口VLAN与VLAN2绑定!interface Ethernet0/1switchport access vlan 3 ----------------------------------------设置端口VLAN与VLAN3绑定!interface Ethernet0/2shutdown!interface Ethernet0/3shutdown!interface Ethernet0/4shutdown!interface Ethernet0/5shutdown!interface Ethernet0/6shutdown!interface Ethernet0/7shutdown!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passivedns domain-lookup insidedns server-group DefaultDNSname-server 211.99.129.210name-server 202.106.196.115access-list 102 extended permit icmp any any ------------------设置ACL列表(允许ICMP全部通过)access-list 102 extended permit ip anyany ------------------设置ACL列表(允许所有IP全部通过)pager lines 24mtu outside 1500mtu inside 1500icmp unreachable rate-limit 1 burst-size 1no asdm history enablearp timeout 14400global (outside) 1 interface ----------------------------------------设置NAT地址映射到外网口nat (inside) 1 0.0.0.0 0.0.0.0 0---------------------------------NAT地址池(所有地址)0无最大会话数限制access-group 102 in interface outside ------------------―――设置ACL列表绑定到外端口route outside 0.0.0.0 0.0.0.0 x.x.x.x 1 ------------------设置到外网的默认路由timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout uauth 0:05:00 absoluteno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstart telnet 0.0.0.0 0.0.0.0 inside ----------------------------------------设置TELNET所有地址进入telnet timeout 5ssh 0.0.0.0 0.0.0.0 outside ----------------------------------------设置SSH所有地址进入ssh timeout 30ssh version 2console timeout 0!dhcpd address 192.168.1.100-192.168.1.199inside ------------------设置DHCP服务器地址池dhcpd dns 211.99.129.210 202.106.196.115 interfaceinside ------------------设置DNS服务器到内网端口dhcpd enableinside --------------------------------------------------------------设置DHCP应用到内网端口!前几天去客户那调试CISCO-ASA-5505设备,第一次摸,跟PIX一样,呵呵.没有技术含量,都是最基本的.其他业务配置暂时没配,会及时更新的.Cisco ASA5505配置cisco, config, telnet, 防火墙, Cisco1.配置防火墙名ciscoasa> enableciscoasa# configure terminalciscoasa(config)# hostname asa55052.配置telnetasa5505(config)#telnet 192.168.1.0 255.255.255.0 inside ↑//允许内部接口192.168.1.0网段telnet防火墙3.配置密码asa5505(config)# password cisco ------------------远程密码asa5505(config)# enable password cisco ------------------特权模式密码4.配置IPasa5505(config)# interface vlan 2 ------------------进入vlan2asa5505(config-if)# ip address 218.16.37.222 255.255.255.192 ------------------vlan2配置IPasa5505(config)#show ip address vlan2 ------------------验证配置5.端口加入vlanasa5505(config)# interface e0/3 ------------------进入接口e0/3asa5505(config-if)# switchport access vlan 3 ------------------接口e0/3加入vlan3asa5505(config)# interface vlan 3 ------------------进入vlan3asa5505(config-if)# ip address 10.10.10.36 255.255.255.224 ------------------vlan3配置IPasa5505(config-if)# nameif dmz ------------------vlan3名asa5505(config-if)# no shutdown ------------------开启asa5505(config-if)# show switch vlan ------------------验证配置6.最大传输单元MTUasa5505(config)#mtu inside 1500 ------------------inside最大传输单元1500字节asa5505(config)#mtu outside 1500 ------------------outside最大传输单元1500字节asa5505(config)#mtu dmz 1500 ------------------dmz最大传输单元1500字节7.配置arp表的超时时间asa5505(config)#arp timeout 14400 ------------------arp表的超时时间14400秒8.FTP模式asa5505(config)#ftp mode passive ------------------FTP被动模式9.配置域名asa5505(config)#domain-name 10.启动日志asa5505(config)#logging enable ------------------启动日志asa5505(config)#logging asdm informational ------------------启动asdm报告日志asa5505(config)#Show logging ------------------验证配置11.启用http服务asa5505(config)#http server enable ------------------启动HTTP server,便于ASDM连接。
Cisco_ASA5500_firewall_配置技巧及实例

一、思科ASA防火墙精华配置总结思科防火墙PIX ASA 配置总结一(基础):下面是我工作以来的配置总结,有些东西是6.3版本的,但不影响在7.*版本的配置。
一:6个基本命令:nameif、interface、ip address 、nat、global、route。
二:基本配置步骤:step1: 命名接口名字nameif ethernet0 outside security0nameif ethernet1 inside security100nameif ethernet2 dmz security50**7版本的配置是先进入接口再命名。
step2:配置接口速率interface ethernet0 10full autointerface ethernet1 10full autointerface ethernet2 10fullstep3:配置接口地址ip address outside 218.106.185.82ip address inside 192.168.100.1 255.255.255.0ip address dmz 192.168.200.1 255.255.255.0step4:地址转换(必须)* 安全高的区域访问安全低的区域(即内部到外部)需NAT和global;nat(inside) 1 192.168.1.1 255.255.255.0global(outside) 1 222.240.254.193 255.255.255.248***nat (inside) 0 192.168.1.1 255.255.255.255 表示192.168.1.1这个地址不需要转换。
直接转发出去。
* 如果内部有服务器需要映像到公网地址(外网访问内网)则需要static和conduit或者acl.static (inside, outside) 222.240.254.194 192.168.1.240static (inside, outside) 222.240.254.194 192.168.1.240 10000 10后面的10000为限制连接数,10为限制的半开连接数。
思科ASA5505防火墙配置成功实例

配置要求:1、分别划分inside(内网)、outside(外网)、dmz(安全区)三个区域。
2、内网可访问外网及dmz内服务器(web),外网可访问dmz内服务器(web)。
3、Dmz服务器分别开放80、21、3389端口。
说明:由于防火墙许可限制“no forward interface Vlan1”dmz内服务器无法访问外网。
具体配置如下:希望对需要的朋友有所帮助ASA Version 7.2(4)!hostname asa5505enable password tDElRpQcbH/qLvnn encryptedpasswd 2KFQnbNIdI.2KYOU encryptednames!interface Vlan1nameif outsidesecurity-level 0ip address 外网IP 外网掩码!interface Vlan2nameif insidesecurity-level 100ip address 192.168.1.1 255.255.255.0!interface Vlan3no forward interface Vlan1nameif dmzsecurity-level 50ip address 172.16.1.1 255.255.255.0!interface Ethernet0/0description outside!interface Ethernet0/1description insideswitchport access vlan 2!interface Ethernet0/2description dmzswitchport access vlan 3!interface Ethernet0/3description insideswitchport access vlan 2!interface Ethernet0/4shutdown!interface Ethernet0/5shutdown!interface Ethernet0/6shutdown!interface Ethernet0/7shutdown!ftp mode passiveobject-group service outside-to-dmz tcpport-object eq wwwport-object eq ftpport-object eq 3389access-list aaa extended permit tcp any host 外网IP object-group outsid e-to-dmzaccess-list bbb extended permit tcp host 172.16.1.2 192.168.1.0 255.255. 255.0 object-group outside-to-dmzpager lines 24mtu outside 1500mtu inside 1500mtu dmz 1500icmp unreachable rate-limit 1 burst-size 1asdm image disk0:/asdm-524.binno asdm history enablearp timeout 14400global (outside) 1 interfaceglobal (dmz) 1 172.16.1.10-172.16.1.254 netmask 255.255.255.0nat (inside) 1 192.168.1.0 255.255.255.0nat (dmz) 1 172.16.1.0 255.255.255.0alias (inside) 221.203.36.86 172.16.1.2 255.255.255.255static (dmz,outside) tcp interface www 172.16.1.2 www netmask 255.255.2 55.255 dnsstatic (dmz,outside) tcp interface ftp 172.16.1.2 ftp netmask 255.255.2 55.255 dnsstatic (dmz,outside) tcp interface 3389 172.16.1.2 3389 netmask 255.255. 255.255dnsstatic (inside,dmz) 172.16.1.2 192.168.1.0 netmask 255.255.255.255 dns access-group aaa in interface outsideaccess-group bbb in interface dmzroute outside 0.0.0.0 0.0.0.0 外网网关 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00timeout sip-provisional-media 0:02:00 uauth 0:05:00 absoluteno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstart telnet timeout 5ssh timeout 5console timeout 0!class-map inspection_defaultmatch default-inspection-traffic!!policy-map type inspect dns preset_dns_mapparametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns preset_dns_mapinspect ftpinspect h323 h225inspect h323 rasinspect netbiosinspect rshinspect rtspinspect skinnyinspect esmtpinspect sqlnetinspect sunrpcinspect tftpinspect sipinspect xdmcpinspect http!service-policy global_policy globalprompt hostname contextCryptochecksum:9d2a6010d4fc078cf026f98dcec96007 : endasa5505(config)#。
CiscoASA防火墙详细图文配置实例解析
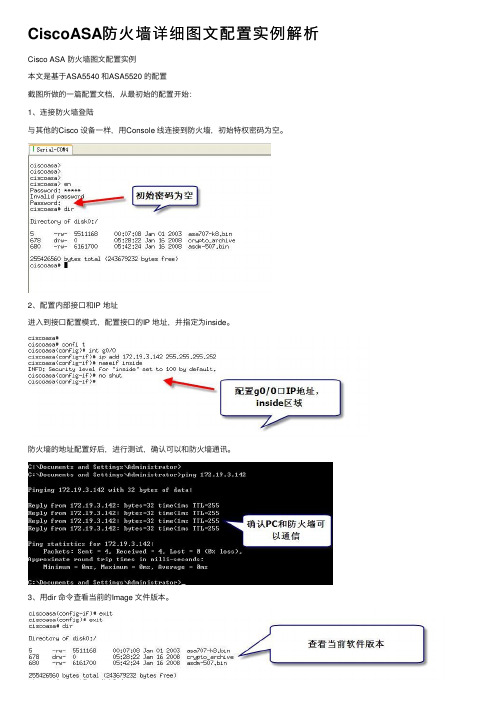
CiscoASA防⽕墙详细图⽂配置实例解析Cisco ASA 防⽕墙图⽂配置实例本⽂是基于ASA5540 和ASA5520 的配置截图所做的⼀篇配置⽂档,从最初始的配置开始:1、连接防⽕墙登陆与其他的Cisco 设备⼀样,⽤Console 线连接到防⽕墙,初始特权密码为空。
2、配置内部接⼝和IP 地址进⼊到接⼝配置模式,配置接⼝的IP 地址,并指定为inside。
防⽕墙的地址配置好后,进⾏测试,确认可以和防⽕墙通讯。
3、⽤dir 命令查看当前的Image ⽂件版本。
4、更新Image ⽂件。
准备好TFTP 服务器和新的Image ⽂件,开始更新。
5、更新ASDM。
6、更新完成后,再⽤dir 命令查看7、修改启动⽂件。
以便于ASA 防⽕墙能够从新的Image 启动8、存盘,重启9、⽤sh version 命令验证启动⽂件,可以发现当前的Image ⽂件就是更新后的10、设置允许⽤图形界⾯来管理ASA 防⽕墙表⽰内部接⼝的任意地址都可以通过http 的⽅式来管理防⽕墙。
11、打开浏览器,在地址栏输⼊防⽕墙内部接⼝的IP 地址选择“是”按钮。
12、出现安装ASDM 的画⾯选择“Install ASDM Launcher and Run ASDM”按钮,开始安装过程。
13、安装完成后会在程序菜单中添加⼀个程序组14、运⾏ASDM Launcher,出现登陆画⾯15、验证证书单击“是”按钮后,开始登陆过程16、登陆进去后,出现防⽕墙的配置画⾯,就可以在图形界⾯下完成ASA 防⽕墙的配置17、选择⼯具栏的“Configuration”按钮18、选择“Interface”,对防⽕墙的接⼝进⾏配置,这⾥配置g0/3接⼝选择g0/3 接⼝,并单击右边的“Edit”按钮19、配置接⼝的 IP 地址,并将该接⼝指定为 outside单击OK 后,弹出“Security Level Change”对话框,单击OK20、编辑g0/1 接⼝,并定义为DMZ 区域21、接⼝配置完成后,要单击apply 按钮,以应⽤刚才的改变,这⼀步⼀定不能忘22、设置静态路由单击Routing->Static Route->Add23、设置enable 密码24、允许ssh ⽅式登录防⽕墙25、增加⽤户定义ssh ⽤本地数据库验证26、⽤ssh 登录测试登录成功27、建⽴动态NAT 转换选择Add Dynamic NAT RuleInterface 选择inside,Source 处输⼊any单击Manage 按钮单击add,增加⼀个地址池Interface 选择Outside,选择PAT,单击Add 按钮。
配置asa 5505防火墙
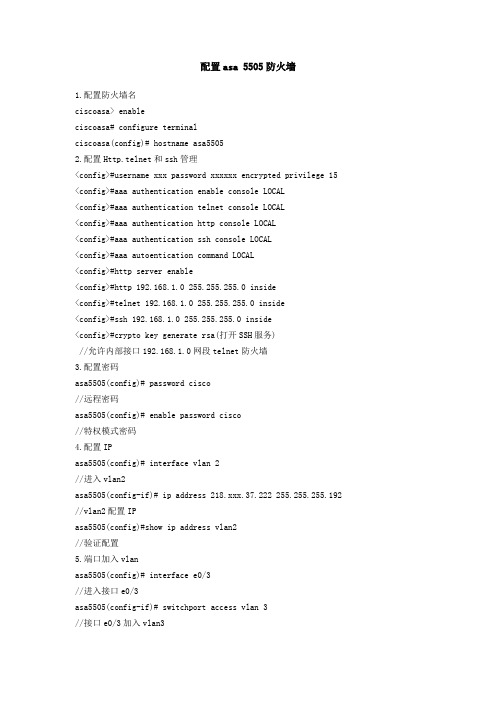
配置asa 5505防火墙1.配置防火墙名ciscoasa> enableciscoasa# configure terminalciscoasa(config)# hostname asa55052.配置Http.telnet和ssh管理<config>#username xxx password xxxxxx encrypted privilege 15 <config>#aaa authentication enable console LOCAL<config>#aaa authentication telnet console LOCAL<config>#aaa authentication http console LOCAL<config>#aaa authentication ssh console LOCAL<config>#aaa autoentication command LOCAL<config>#http server enable<config>#http 192.168.1.0 255.255.255.0 inside<config>#telnet 192.168.1.0 255.255.255.0 inside<config>#ssh 192.168.1.0 255.255.255.0 inside<config>#crypto key generate rsa(打开SSH服务)//允许内部接口192.168.1.0网段telnet防火墙3.配置密码asa5505(config)# password cisco//远程密码asa5505(config)# enable password cisco//特权模式密码4.配置IPasa5505(config)# interface vlan 2//进入vlan2asa5505(config-if)# ip address 218.xxx.37.222 255.255.255.192 //vlan2配置IPasa5505(config)#show ip address vlan2//验证配置5.端口加入vlanasa5505(config)# interface e0/3//进入接口e0/3asa5505(config-if)# switchport access vlan 3//接口e0/3加入vlan3asa5505(config)# interface vlan 3//进入vlan3asa5505(config-if)# ip address 10.10.10.36 255.255.255.224//vlan3配置IPasa5505(config-if)# nameif dmz//vlan3名asa5505(config-if)# no shutdown//开启asa5505(config-if)# show switch vlan//验证配置6.最大传输单元MTUasa5505(config)#mtu inside 1500//inside最大传输单元1500字节asa5505(config)#mtu outside 1500//outside最大传输单元1500字节asa5505(config)#mtu dmz 1500//dmz最大传输单元1500字节7.配置arp表的超时时间asa5505(config)#arp timeout 14400//arp表的超时时间14400秒8.FTP模式asa5505(config)#ftp mode passive//FTP被动模式9.配置域名asa5505(config)#domain-name 10.启动日志asa5505(config)#logging enable//启动日志asa5505(config)#logging asdm informational//启动asdm报告日志asa5505(config)#Show logging//验证配置11.启用http服务asa5505(config)#http server enable ///启动HTTP server,便于ASDM连接。
ASA5500-X身份防火墙与CDA配置指南

ASA5500-X身份防火墙与CDA配置指南一、目的 (1)二、网络拓扑 (1)三、CDA的安装与配置 (2)四、ASA5515-X安装CX模块 (4)五、Windows 2008 R2的配置 (8)六、ASA-CX的策略配置 (17)七、ASA-CX功能验证 (26)一、目的本文介绍了在ASA5515-X防火墙上,通过与思科Context Directory Agent(简称CDA)软件协同工作,实现基于身份的访问策略与控制。
主要内容包括以下几个部分::ASA5515-X上CX模块的安装与配置步骤。
CDA的安装与配置步骤。
Windows 2008 R2服务器与CDA配合时,需要的修改哪些内容。
二、网络拓扑以下是本次配置实例的网络拓扑图:三、CDA的安装与配置思科Context Directory Agent(简称CDA)是一套软件,ASA5515-X的CX模块通过CDA能够获取IP地址与用户身份的映射关系,从而可以在ASA-CX上实现基于用户身份的安全访问策略。
通过思科CCO可以下载获取CDA的ISO格式的软件。
CDA软件本身包含了操作系统,它可以安装在一台专用的x86服务器上,或者VMware的ESX或ESXi虚拟机上。
在VMWare 虚拟机上安装时,注意Guest OS类型要选择:Linux CentOS 4/5 32bit。
以下是将CDA安装在ESXi5.0服务器上的安装和配置步骤:步骤1:在CCO下载CDA软件:/download/type.html?mdfid=284143128&flowid=31442步骤2:在VMware ESXi5.0上安装CDA。
步骤3:完成安装后,在login提示符下输入setup,进行基本配置。
以下为配置举例:localhost.localdomain login: setupPress ‘Ctrl-C’ to abort setupEnter Hostname[]: cda-serverEnter IP address []: 10.10.10.83Enter IP netmask []: 255.255.255.0Enter IP default gateway []: 10.10.10.3Enter default DNS domain []: Enter primary nameserver []: 10.10.10.80Enter secondary nameserver? Y/N: nEnter primary NTP server []: 10.10.10.80Enter secondary NTP server? Y/N: nEnter system timezone [UTC]: Asia/ShanghaiEnter username [admin]: adminEnter password:Enter password again:Bringing up the network interface...Pinging the gateway...Pinging the primary nameserver...Do not use ‘Ctrl-C’ from this point on...Installing applications...Installing cda...Pre installPost InstallApplication bundle (cda) installed successfully=== Initial setup for application: cda ===Generating configuration...Rebooting...步骤4:打开浏览器,输入https://10.10.10.83,输入已经创建好的用户名和密码,登陆CDA的GUI页面。
实验四 cisco思科asa 5505 从内网访问DMZ服务器(真实防火墙)

实验四 ASA 5505 从内网访问DMZ区服务器(真实防火墙)一、实验目标在这个实验中朋友你将要完成下列任务:1.创建vlan2.给vlan命名3.给vlan分配IP4.把接口加入到相应的VLAN,并配置接口的速率、双工(半工)5.配置内部转化地址池(nat)外部转换地址globla6.配置WWW和FTP服务器二、实验拓扑------------------------------------------------------------------------------------------------------------------------三、实验过程1. ASA 5505基本配置:ciscoasa>ciscoasa> enablePassword:ciscoasa#ciscoasa# configure terminalciscoasa(config)# interface vlan44 *建立ID为44的虚拟局域网(vlan)ciscoasa(config-if)# nameif dmz *把vlan44的接口名称配置为dmzciscoasa(config-if)# security-level 50 *配置dmz 安全级别为50ciscoasa(config-if)# ip address 11.0.0.1 255.0.0.0 *给vlan44配置IP地址ciscoasa(config-if)# interface vlan33 *建立ID为33的虚拟局域网(vlan)ciscoasa(config-if)# nameif inside *把vla33的接口名称配置为inside,并指定安全级别,安全级别取值范围为1~100,数字越大安全级别越高。
在默认情况下,inside安全级别为100。
INFO: Security level for "inside" set to 100 by default.ciscoasa(config-if)# ip address 192.168.0.211 255.255.255.0 *给vlan33配置IP地址ciscoasa(config-if)# exitciscoasa(config)# interface ethernet0/2 *进入e0/2接口的配置模式ciscoasa(config-if)# switchport access vlan 44 *把e0/2接口划分到vlan22中ciscoasa(config-if)# speed auto *设置e0/2接口的速率为自动协商ciscoasa(config-if)# duplex auto *设置e0/2接口的工作模式为自动协商ciscoasa(config-if)# no shutdown *打开e0/2接口ciscoasa(config-if)# interface e0/0 *进入e0/1接口的配置模式ciscoasa(config-if)# switchport access vlan 33 *把e0/0接口划分到vlan33中ciscoasa(config-if)# speed auto *设置e0/0接口的速率为自动协商ciscoasa(config-if)# duplex auto *设置e0/0接口的工作模式为自动协商ciscoasa(config-if)# no shutdown *打开e0/0接口ciscoasa(config-if)# exitciscoasa(config)#2. ASA 5505本身接口的连通性测试①测试防火墙本身vlan44接口连通性ciscoasa# ping 11.0.0.1Sending 5, 100-byte ICMP Echos to 11.0.0.1, timeout is 2 seconds:Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms②测试防火墙本身vlan33接口连通性ciscoasa# ping 192.168.0.211Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.0.211, timeout is 2 seconds:3. 配置PC:具体网络参数如拓扑图所示。
asa 5505 常用配置

access-list acl_out extended permit tcp any host 218.xxx.37.224 eq 3389
//允许tcp协议3389端口到218.xxx.37.224主机
access-list acl_out extended permit tcp any host 218.xxx.37.225 eq 1433
asa5505(config)#mtu inside 1500
//inside最大传输单元1500字节
asa5505(config)#mtu outside 1500
//outside最大传输单元1500字节
asa5505(config)#mtu dmz 1500
//dmz最大传输单元1500字节
//允许内部接口192.168.1.0网段telnet防火墙
3.配置密码
asa5505(config)# password cisco
//远程密码
asa5505(config)# enable password cisco
//特权模式密码
4.配置IP
asa5505(config)# interface vlan 2
//故障倒换接口名standby
asa5505(config)#failover interface ip standby 172.168.32.1 255.255.255.252 standby 172.168.32.2
//配置主防火墙IP:172.168.32.1,备用防火墙IP:172.168.32.2
asa5505# show failover
思科5505火墙配置

asa 5505 常用配置2009-06-01 16:13asa 55051.配置防火墙名ciscoasa> enableciscoasa# configure terminalciscoasa(config)# hostname asa55052.配置telnetasa5505(config)#telnet inside//允许内部接口3.配置密码asa5505(config)# password cisco//远程密码asa5505(config)# enable password cisco //特权模式密码4.配置IPasa5505(config)# interface vlan 2//进入vlan2asa5505(config-if)# ip address//vlan2配置IPasa5505(config)#show ip address vlan2 //验证配置5.端口加入vlan//进入接口e0/3asa5505(config-if)# switchport access vlan 3 //接口e0/3加入vlan3asa5505(config)# interface vlan 3//进入vlan3asa5505(config-if)# ip address//vlan3配置IPasa5505(config-if)# nameif dmz//vlan3名asa5505(config-if)# no shutdown//开启asa5505(config-if)# show switch vlan//验证配置6.最大传输单元MTUasa5505(config)#mtu inside 1500//inside最大传输单元1500字节asa5505(config)#mtu outside 1500//outside最大传输单元1500字节asa5505(config)#mtu dmz 1500//dmz最大传输单元1500字节7.配置arp表的超时时间//arp表的超时时间14400秒8.FTP模式asa5505(config)#ftp mode passive//FTP被动模式9.配置域名asa5505(config)#domain-name 10.启动日志asa5505(config)#logging enable//启动日志asa5505(config)#logging asdm informational //启动asdm报告日志asa5505(config)#Show logging//验证配置11.启用http服务asa5505(config)#http serverenable//启动HTTP server,便于ASDM连接。
思科5505配置详解
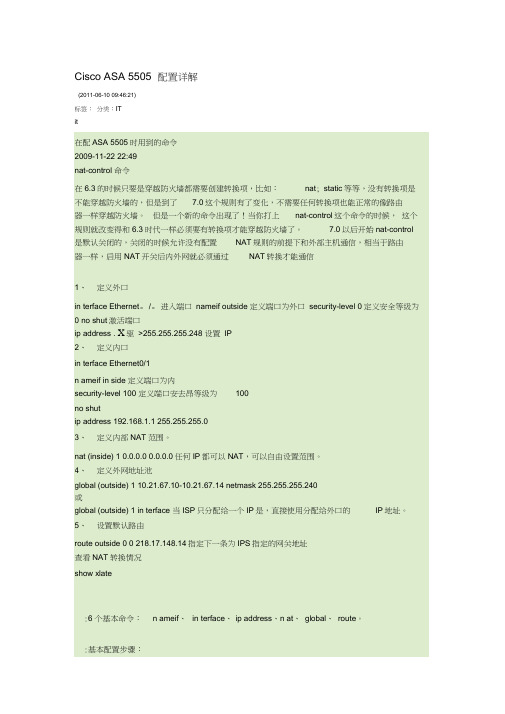
*如果内部有服务器需要映射到公网地址(外网访问内网)则需要static和conduit或者acl.
static (in side, outside) 222.240.254.194 192.168.1.240
nat命令配置语法:n at (if_ name) n at_id local_ip [n etmark]
必要的漏洞)
ACL实现的功能和conduit一样都可实现策略访问,只是ACL稍微麻烦点。conduit现在在
7版本已经不能用了。
Access-list101permit tcp any host 222.240.254.194 eq 101 in in terface outside (绑定到接口)
1、定义外口
in terface Ethernet。/。进入端口nameif outside定义端口为外口security-level0定义安全等级为0no shut激活端口
ip address .X驱>255.255.255.248设置IP
2、定义内口
in terface Ethernet0/1
n ameif in side定义端口为内
或
global (outside) 1 in terface当ISP只分配给一个IP是,直接使用分配给外口的IP地址。
5、设置默认路由
route outside0 0218.17.148.14指定下一条为IPS指定的网关地址
查看NAT转换情况
show xlate
:6个基本命令:n ameif、in terface、ip address、n at、global、route。
cisco-asa-5505基本配置

cisco-asa-5505基本配置interface Vlan2nameif outside ----------------------------------------对端口命名外端口security-level 0 ----------------------------------------设置端口等级ip address X.X.X.X 255.255.255.224 --------------------调试外网地址!interface Vlan3nameif inside ----------------------------------------对端口命名内端口security-level 100 ----------------------------------------调试外网地址ip address 192.168.1.1 255.255.255.0 --------------------设置端口等级!interface Ethernet0/0switchport access vlan 2 ----------------------------------------设置端口VLAN与VLAN2绑定!interface Ethernet0/1switchport access vlan 3 ----------------------------------------设置端口VLAN与VLAN3绑定!interface Ethernet0/2shutdown!interface Ethernet0/3shutdown!interface Ethernet0/4shutdown!interface Ethernet0/5shutdown!interface Ethernet0/6shutdown!interface Ethernet0/7shutdown!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passivedns domain-lookup insidedns server-group DefaultDNSname-server 211.99.129.210name-server 202.106.196.115access-list 102 extended permit icmp any any ------------------设置ACL列表(允许ICMP全部通过)access-list 102 extended permit ip any any ------------------设置ACL列表(允许所有IP全部通过)pager lines 24mtu outside 1500mtu inside 1500icmp unreachable rate-limit 1 burst-size 1no asdm history enablearp timeout 14400global (outside) 1 interface ----------------------------------------设置NAT地址映射到外网口nat (inside) 1 0.0.0.0 0.0.0.0 0---------------------------------NAT地址池(所有地址)0无最大会话数限制access-group 102 in interface outside ------------------―――设置ACL列表绑定到外端口route outside 0.0.0.0 0.0.0.0 x.x.x.x 1 ------------------设置到外网的默认路由timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout uauth 0:05:00 absoluteno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstarttelnet 0.0.0.0 0.0.0.0 inside ----------------------------------------设置TELNET所有地址进入telnet timeout 5ssh 0.0.0.0 0.0.0.0 outside ----------------------------------------设置SSH所有地址进入ssh timeout 30ssh version 2console timeout 0!dhcpd address 192.168.1.100-192.168.1.199 inside ------------------设置DHCP 服务器地址池dhcpd dns 211.99.129.210 202.106.196.115 interface inside ------------------设置DNS服务器到内网端口dhcpd enable inside --------------------------------------------------------------设置DHCP应用到内网端口!前几天去客户那调试CISCO-ASA-5505设备,第一次摸,跟PIX一样,呵呵.没有技术含量,都是最基本的.其他业务配置暂时没配,会及时更新的.Cisco ASA5505配置cisco, config, telnet, 防火墙, Cisco1.配置防火墙名ciscoasa> enableciscoasa# configure terminalciscoasa(config)# hostname asa55052.配置telnetasa5505(config)#telnet 192.168.1.0 255.255.255.0 inside ↑//允许内部接口192.168.1.0网段telnet防火墙3.配置密码asa5505(config)# password cisco ------------------远程密码asa5505(config)# enable password cisco ------------------特权模式密码4.配置IPasa5505(config)# interface vlan 2 ------------------进入vlan2asa5505(config-if)# ip address 218.16.37.222 255.255.255.192 ------------------vlan2配置IPasa5505(config)#show ip address vlan2 ------------------验证配置5.端口加入vlanasa5505(config)# interface e0/3 ------------------进入接口e0/3asa5505(config-if)# switchport access vlan 3 ------------------接口e0/3加入vlan3asa5505(config)# interface vlan 3 ------------------进入vlan3asa5505(config-if)# ip address 10.10.10.36 255.255.255.224 ------------------vlan3配置IPasa5505(config-if)# nameif dmz ------------------vlan3名asa5505(config-if)# no shutdown ------------------开启asa5505(config-if)# show switch vlan ------------------验证配置6.最大传输单元MTUasa5505(config)#mtu inside 1500 ------------------inside最大传输单元1500字节asa5505(config)#mtu outside 1500 ------------------outside最大传输单元1500字节asa5505(config)#mtu dmz 1500 ------------------dmz最大传输单元1500字节7.配置arp表的超时时间asa5505(config)#arp timeout 14400 ------------------arp表的超时时间14400秒8.FTP模式asa5505(config)#ftp mode passive ------------------FTP被动模式9.配置域名asa5505(config)#domain-name 10.启动日志asa5505(config)#logging enable ------------------启动日志asa5505(config)#logging asdm informational ------------------启动asdm报告日志asa5505(config)#Show logging ------------------验证配置11.启用http服务asa5505(config)#http server enable ------------------启动HTTP server,便于ASDM连接。
实验2ASA防火墙配置.

国家高等职业教育网络技术专业教学资源库PIX防火墙PIX防火墙安全典型案例实验二ASA防火墙配置实验二ASA防火墙配置一、实验目的通过该实验了解ASA防火墙的软硬件组成结构,掌握ASA防火墙的工作模式,熟悉ASA 防火墙的基本指令,掌握ASA防火墙的动态、静态地址映射技术,掌握ASA防火墙的访问控制列表配置,熟悉ASA防火墙在小型局域网中的应用。
二、实验任务●观察ASA防火墙的硬件结构,掌握硬件连线方法●查看ASA防火墙的软件信息,掌握软件的配置模式●了解ASA防火墙的基本指令,实现内网主机访问外网主机,外网访问DMZ区三、实验设备ASA5505防火墙一台,CISCO 2950交换机两台,控制线一根,网络连接线若干,PC机若干四、实验拓扑图及内容详细配置:内网R6:R1>enR1#R1#conf tEnter configuration commands, one per line. End with CNTL/Z.R1(config)#int f0/0R1(config-if)#ip add 10.1.1.2 255.255.255.0R1(config-if)#no shutR1(config-if)#*Mar 1 00:01:32.115: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up *Mar 1 00:01:33.115: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to upR1(config-if)#exitR1(config)#ip route 0.0.0.0 0.0.0.0 10.1.1.3R1(config)#exitR1#DMZ区R3:R2>enR2#conf tEnter configuration commands, one per line. End with CNTL/Z.R2(config)#int f0/0R2(config-if)#ip add 20.1.1.2 255.255.255.0R2(config-if)#no shutR2(config-if)#*Mar 1 00:01:28.895: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up *Mar 1 00:01:29.895: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to upR2(config-if)#exitR2(config)#ip route 0.0.0.0 0.0.0.0 20.1.1.3R2(config)#exitR2#*Mar 1 00:03:11.227: %SYS-5-CONFIG_I: Configured from console by consoleR2#外网R4:R4#conf tEnter configuration commands, one per line. End with CNTL/Z.R4(config)#int f0/0R4(config-if)#ip add 192.168.1.2 255.255.255.0R4(config-if)#no shutR4(config-if)#*Mar 1 00:00:45.559: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up *Mar 1 00:00:46.559: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to upR4(config-if)#exitR4(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.3R4(config)#exitR4#PIX防火墙上的配置:pixfirewall# conf tpixfirewall(config)# hostname pixpix(config)# int e0pix(config-if)# ip add 10.1.1.3 255.255.255.0pix(config-if)# nameif insideINFO: Security level for "inside" set to 100 by default.pix(config-if)# no shutpix(config-if)# int e1pix(config-if)# nameif outsideINFO: Security level for "outside" set to 0 by default.pix(config-if)# ip add 192.168.1.3 255.255.255.0pix(config-if)# no shutpix(config-if)# int e2pix(config-if)# nameif dmzINFO: Security level for "dmz" set to 0 by default.pix(config-if)# secpix(config-if)# security-level 50pix(config-if)# ip add 20.1.1.3 255.255.255.0pix(config-if)# no shutpix(config-if)# nat (inside) 11 10.1.1.0 255.255.255.0pix(config)# nat (inside) 11 10.1.1.0 255.255.255.0Duplicate NAT entrypix(config)# global (outside) 11 20.1.1.74 netmask 255.255.255.255INFO: Global 20.1.1.74 will be Port Address Translatedpix(config)# access-list 100 permit icmp any anypix(config)# access-grpix(config)# access-group 100 in interface outsidepix(config)# static (dmz,outside) 192.168.1.5 20.1.1.5 netmask 255.255.255.255 pix(config)# access-group 100 in interface dmzpix(config)#五、实验结果内网PING外网:外网PING DMZ:外网PING内网:总结:比起上次试验,这次是多添加了一个DMZ区,在DMZ和outside之间配置static命令。
思科ASA5505防火墙配置成功实例
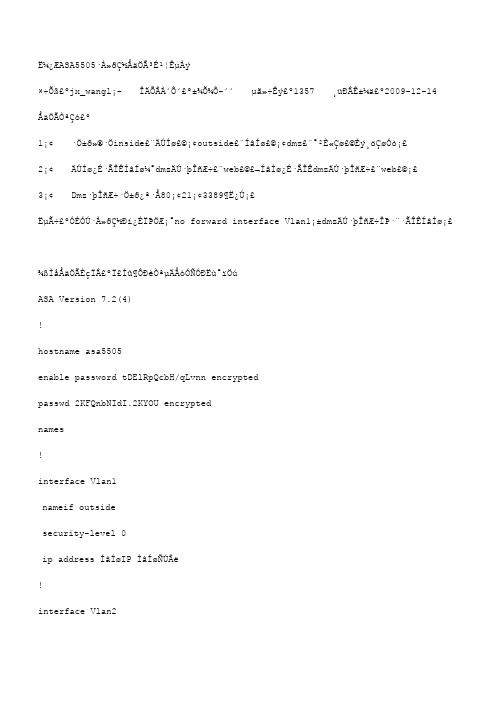
˼¿ÆASA5505·À»ðǽÅäÖóɹ¦ÊµÀý×÷Õߣºjx_wangl¡- ÎÄÕÂÀ´Ô´£º±¾Õ¾Ô-´´ µã»÷Êý£º1357 ¸üÐÂʱ¼ä£º2009-12-14 ÅäÖÃÒªÇó£º1¡¢ ·Ö±ð»®·Öinside£¨ÄÚÍø£©¡¢outside£¨ÍâÍø£©¡¢dmz£¨°²È«Çø£©Èý¸öÇøÓò¡£2¡¢ ÄÚÍø¿É·ÃÎÊÍâÍø¼°dmzÄÚ·þÎñÆ÷£¨web£©£¬ÍâÍø¿É·ÃÎÊdmzÄÚ·þÎñÆ÷£¨web£©¡£3¡¢ Dmz·þÎñÆ÷·Ö±ð¿ª·Å80¡¢21¡¢3389¶Ë¿Ú¡£ËµÃ÷£ºÓÉÓÚ·À»ðǽÐí¿ÉÏÞÖÆ¡°no forward interface Vlan1¡±dmzÄÚ·þÎñÆ÷ÎÞ·¨·ÃÎÊÍâÍø¡£¾ßÌåÅäÖÃÈçÏ£ºÏ£Íû¶ÔÐèÒªµÄÅóÓÑÓÐËù°ïÖúASA Version 7.2(4)!hostname asa5505enable password tDElRpQcbH/qLvnn encryptedpasswd 2KFQnbNIdI.2KYOU encryptednames!interface Vlan1nameif outsidesecurity-level 0ip address ÍâÍøIP ÍâÍøÑÚÂë!interface Vlan2nameif insidesecurity-level 100ip address 192.168.1.1 255.255.255.0 !interface Vlan3no forward interface Vlan1nameif dmzsecurity-level 50ip address 172.16.1.1 255.255.255.0 !interface Ethernet0/0description outside!interface Ethernet0/1description insideswitchport access vlan 2!interface Ethernet0/2description dmzswitchport access vlan 3!interface Ethernet0/3description insideswitchport access vlan 2!interface Ethernet0/4shutdown!interface Ethernet0/5shutdown!interface Ethernet0/6shutdown!interface Ethernet0/7shutdown!ftp mode passiveobject-group service outside-to-dmz tcpport-object eq wwwport-object eq ftpport-object eq 3389access-list aaa extended permit tcp any host ÍâÍøIP object-group outside- to-dmzaccess-list bbb extended permit tcp host 172.16.1.2 192.168.1.0 255.255.255.0 ob ject-group outside-to-dmzpager lines 24mtu outside 1500mtu inside 1500mtu dmz 1500icmp unreachable rate-limit 1 burst-size 1asdm image disk0:/asdm-524.binno asdm history enablearp timeout 14400global (outside) 1 interfaceglobal (dmz) 1 172.16.1.10-172.16.1.254 netmask 255.255.255.0nat (inside) 1 192.168.1.0 255.255.255.0nat (dmz) 1 172.16.1.0 255.255.255.0alias (inside) 221.203.36.86 172.16.1.2 255.255.255.255static (dmz,outside) tcp interface www 172.16.1.2 www netmask 255.255.255.255 d nsstatic (dmz,outside) tcp interface ftp 172.16.1.2 ftp netmask 255.255.255.255 d nsstatic (dmz,outside) tcp interface 3389 172.16.1.2 3389 netmask 255.255.255.255 dnsstatic (inside,dmz) 172.16.1.2 192.168.1.0 netmask 255.255.255.255 dnsaccess-group aaa in interface outsideaccess-group bbb in interface dmzroute outside 0.0.0.0 0.0.0.0 ÍâÍøÍø¹Ø 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absoluteno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstarttelnet timeout 5ssh timeout 5console timeout 0!class-map inspection_defaultmatch default-inspection-traffic!!policy-map type inspect dns preset_dns_mapparametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns preset_dns_mapinspect ftpinspect h323 h225inspect h323 rasinspect netbiosinspect rshinspect rtspinspect skinnyinspect esmtpinspect sqlnetinspect sunrpcinspect tftpinspect sipinspect xdmcpinspect http!service-policy global_policy globalprompt hostname contextCryptochecksum:9d2a6010d4fc078cf026f98dcec96007: endasa5505(config)#。
CiscoASA5505防火墙详细配置教程及实际配置案例

CiscoASA5505防火墙详细配置教程及实际配置案例interfaceVlan2nameifoutside对端口命名外端口security-level0设置端口等级ipaddressX.X.X.X255.255.255.224调试外网地址!interfaceVlan3nameifinside对端口命名内端口security-level100调试外网地址ipaddress192.168.1.1255.255.255.0设置端口等级!interfaceEthernet0/0switchportaccessvlan2设置端口VLAN与VLAN绯定!interfaceEthernet0/1switchportaccessvlan3设置端口VLAN与VLAN3W定!interfaceEthernet0/2shutdown!interfaceEthernet0/3shutdown!interfaceEthernet0/4shutdowninterfaceEthernet0/5shutdown!interfaceEthernet0/6shutdown!interfaceEthernet0/7shutdown!passwd2KFQnbNIdI.2KYOUencryptedftpmodepassivednsdomain-lookupinsidednsserver-groupDefaultDNSname-server211.99.129.210name-server202.106.196.115access-list102extendedpermiticmpanyany设置ACL歹U表(允许ICMP全部通过)access-list102extendedpermitipanyany设置ACL列表(允许所有IP全部通过)pagerlines24mtuoutside1500mtuinside1500icmpunreachablerate-limit1burst-size1noasdmhistoryenablearptimeout14400global(outside)1interface设置NAT地址映射到外网口nat(inside)10.0.0.00.0.0.00NAT地址池(所有地址)0无最大会话数限制access-group102ininterfaceoutside设置ACL列表绑定到外端口routeoutside0.0.0.00.0.0.0x.x.x.x1设置到外网的默认路由timeoutxlate3:00:00timeoutconn1:00:00half-closed0:10:00udp0:02:00icmp0:00:02timeoutsunrpc0:10:00h3230:05:00h2251:00:00mgcp0:05:00mgcp-pat0:05:00timeoutsip0:30:00sip_media0:02:00sip-invite0:03:00sip-disconnect0:02:00timeoutuauth0:05:00absolutenosnmp-serverlocationnosnmp-servercontactsnmp-serverenabletrapssnmpauthenticationlinkuplinkdowncoldstarttelnet0.0.0.00.0.0.0inside设置TELNETS有地址进入telnettimeout5ssh0.0.0.00.0.0.0outside设置SSH所有地址进入sshtimeout30sshversion2consoletimeout0dhcpdaddress192.168.1.100-192.168.1.199inside设置DHCP!艮务器地址池dhcpddns211.99.129.210202.106.196.115interfaceinside设置DNS服务器到内网端口dhcpdenableinside设置DHCPZ用到内网端口前几天去客户那调试CISCO-ASA-5505设备,第一次摸,跟PIX一样,呵呵.没有技术含量,都是最基本的.其他业务配置暂时没配,会及时更新的.CiscoASA5505配置cisco,config,telnet,防火墙,Cisco1.配置防火墙名ciscoasa>enableciscoasa#configureterminalciscoasa(config)#hostnameasa55052.配置telnetasa5505(config)#telnet192.168.1.0255.255.255.0insideT〃允许内部接口192.168.1.0网段telnet防火墙3.配置密码asa5505(config)#passwordcisco远程密码asa5505(config)#enablepasswordcisco特权模式密码4.配置IPasa5505(config)#interfacevlan2进入vlan2asa5505(config-if)#ipaddress218.16.37.222255.255.255.192vlan2配置IPasa5505(config)#showipaddressvlan2验证配置5.端口力口入vlanasa5505(config)#interfacee0/3进入接口e0/3asa5505(config-if)#switchportaccessvlan3接口e0/3力口入vlan3asa5505(config)#interfacevlan3进入vlan3asa5505(config-if)#ipaddress10.10.10.36255.255.255.224vlan3配置IPasa5505(config-if)#nameifdmzvlan3名asa5505(config-if)#noshutdown开启asa5505(config-if)#showswitchvlan验证配置6.最大传输单元MTUasa5505(config)#mtuinside1500inside最大传车^单元1500字节asa5505(config)#mtuoutside1500outside最大传输单元1500字节asa5505(config)#mtudmz1500dmz最大传输单元1500字节7.配置arp表的超时时间asa5505(config)#arptimeout14400arp表的超日^时间14400秒8.FTP模式asa5505(config)#ftpmodepassiveFTP被动模式9.配置域名asa5505(config)#10.启动日志asa5505(config)#loggingenable启动日志asa5505(config)#loggingasdminformational启动asdm报告日志asa5505(config)#Showlogging验证配置11.启用http服务asa5505(config)#httpserverenable启动HTTPserver便于ASDM连接。
cisco asa 5505防火墙VPN L2L配置(Center)

pre-shared-key cisco123 ! ! prompt hostname context Cryptochecksum:faa5d81684f6b30919ba7d659fe80a0e : end
authentication pre-share encryption des hash sha group 2 lifetime 86400 crypto isakmp policy 65535
authentication pre-share encryption 3des hash sha group 2 lifetime 86400 telnet timeout 5 ssh timeout 5 console timeout 0 vpdn username 280020952180 password 11441480 store-local dhcpd dns 202.96.128.86 8.8.8.8 ! dhcpd address 10.31.1.2-10.31.1.129 inside dhcpd enable inside !
shutdown ! interface Ethernet0/7
switchport access vlan 10 ! ftp mode passive access-list ipsec-data extended permit ip 10.31.1.0 255.255.255.0 10.30.1.0 255.255.255.0 access-list nonat extended permit ip 10.31.1.0 255.255.255.0 10.30.1.0 255.255.255.0 pager lines 24 mtu outside 1500 mtu inside 1500 icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 global (outside) 1 interface nat (inside) 0 access-list nonat nat (inside) 1 0.0.0.0 0.0.0.0 route outside 0.0.0.0 0.0.0.0 192.168.15.254 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute dynamic-access-policy-record DfltAccessPolicy no snmp-server location no snmp-server contact snmp-server enable traps snmp authentication linkup linkdown coldstart crypto ipsec transform-set mytrans esp-des esp-sha-hmac crypto ipsec security-association lifetime seconds 28800 crypto ipsec security-association lifetime kilobytes 4608000 crypto map mymap 10 match address ipsec-data crypto map mymap 10 set peer 192.168.15.100 crypto map mymap 10 set transform-set mytrans crypto map mymap 10 set security-association lifetime seconds 28800 crypto map mymap 10 set security-association lifetime kilobytes 4608000 crypto map mymap interface outside crypto isakmp enable outside crypto isakmp policy 10
ASA5505透明模式下完全配置

ASA5505透明模式下完全配置2008-08-01 13:04ciscoasa# show run: Saved:ASA Version 7.2(3)!firewall transparenthostname ciscoasadomain-name default.domain.invalidenable password 8Ry2YjIyt7RRXU24 encryptednames!interface Vlan1nameif insidesecurity-level 100!interface Vlan2nameif outsidesecurity-level 0!interface Ethernet0/0!interface Ethernet0/1!interface Ethernet0/2!interface Ethernet0/3!interface Ethernet0/4switchport access vlan 2!interface Ethernet0/5switchport access vlan 2!interface Ethernet0/6!interface Ethernet0/7!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passivedns server-group DefaultDNSdomain-name default.domain.invalidaccess-list 111 extended permit tcp any any eq ftp-dataaccess-list 111 extended permit tcp any any eq sshaccess-list 111 extended permit tcp any any eq wwwaccess-list 111 extended permit tcp any any eq 8080access-list 111 extended permit tcp any any eq 6600access-list 111 extended permit tcp any any eq 7877access-list 111 extended permit tcp any any range 2020 2121access-list 111 extended permit tcp any any range 6800 6900access-list 111 extended permit tcp any any range 5200 5400access-list 111 extended permit icmp any anypager lines 24mtu inside 1500mtu outside 1500ip address 192.168.100.100 255.255.255.0icmp unreachable rate-limit 1 burst-size 1asdm image disk0:/asdm-523.binno asdm history enablearp timeout 14400access-group 111 in interface outsidetimeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00timeout uauth 0:05:00 absolutehttp server enablehttp 0.0.0.0 0.0.0.0 insideno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstart telnet 0.0.0.0 0.0.0.0 insidetelnet timeout 5ssh timeout 5console timeout 0!class-map inspection_defaultmatch default-inspection-traffic!!policy-map type inspect dns preset_dns_mapparametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns preset_dns_mapinspect ftpinspect h323 h225inspect h323 rasinspect rshinspect rtspinspect esmtpinspect sqlnetinspect skinnyinspect sunrpcinspect xdmcpinspect sipinspect netbiosinspect tftp!service-policy global_policy globalprompt hostname contextCryptochecksum:871ee08b54631ff021ad0c4a1a3db59d: endciscoasa#ciscoasa#ciscoasa#ciscoasa#ciscoasa# show verciscoasa# show versionCisco Adaptive Security Appliance Software Version 7.2(3) Device Manager Version 5.2(3)Compiled on Wed 15-Aug-07 16:08 by buildersSystem image file is "disk0:/asa723-k8.bin"Config file at boot was "startup-config"ciscoasa up 5 mins 34 secsHardware: ASA5505, 256 MB RAM, CPU Geode 500 MHzInternal ATA Compact Flash, 128MBBIOS Flash M50FW080 @ 0xffe00000, 1024KBEncryption hardware device : Cisco ASA-5505 on-board accelerator (revision 0x0)Boot microcode : CNlite-MC-Boot-Cisco-1.2SSL/IKE microcode: CNlite-MC-IPSEC-Admin-3.03IPSec microcode : CNlite-MC-IPSECm-MAIN-2.040: Int: Internal-Data0/0 : address is 001e.4a39.b59d, irq 111: Ext: Ethernet0/0 : address is 001e.4a39.b595, irq 2552: Ext: Ethernet0/1 : address is 001e.4a39.b596, irq 2553: Ext: Ethernet0/2 : address is 001e.4a39.b597, irq 2554: Ext: Ethernet0/3 : address is 001e.4a39.b598, irq 2555: Ext: Ethernet0/4 : address is 001e.4a39.b599, irq 2556: Ext: Ethernet0/5 : address is 001e.4a39.b59a, irq 2557: Ext: Ethernet0/6 : address is 001e.4a39.b59b, irq 2558: Ext: Ethernet0/7 : address is 001e.4a39.b59c, irq 2559: Int: Internal-Data0/1 : address is 0000.0003.0002, irq 25510: Int: Not used : irq 25511: Int: Not used : irq 255Licensed features for this platform:Maximum Physical Interfaces : 8VLANs : 3, DMZ RestrictedInside Hosts : 10Failover : DisabledVPN-DES : EnabledVPN-3DES-AES : EnabledVPN Peers : 10WebVPN Peers : 2Dual ISPs : DisabledVLAN Trunk Ports : 0This platform has a Base license.Serial Number: JMX1145Z03DRunning Activation Key: 0x33184371 0x3cfb93d2 0xbc80d584 0x8efca824 0xcb0aadacConfiguration register is 0x1Configuration has not been modified since last system restart. ciscoasa#ciscoasa#ciscoasa#ciscoasa# show inciscoasa# show interfaceInterface Vlan1 "inside", is up, line protocol is upHardware is EtherSVIMAC address 001e.4a39.b59d, MTU 1500IP address 1.1.1.1, subnet mask 255.255.255.255Traffic Statistics for "inside":48 packets input, 3275 bytes68 packets output, 3206 bytes3 packets dropped1 minute input rate 0 pkts/sec, 5 bytes/sec1 minute output rate 0 pkts/sec, 15 bytes/sec1 minute drop rate, 0 pkts/sec5 minute input rate 0 pkts/sec, 10 bytes/sec5 minute output rate 0 pkts/sec, 9 bytes/sec5 minute drop rate, 0 pkts/secInterface Vlan2 "outside", is up, line protocol is up Hardware is EtherSVIMAC address 001e.4a39.b59e, MTU 1500IP address 1.1.1.1, subnet mask 255.255.255.255Traffic Statistics for "outside":113 packets input, 6686 bytes13 packets output, 855 bytes60 packets dropped1 minute input rate 0 pkts/sec, 26 bytes/sec1 minute output rate 0 pkts/sec, 5 bytes/sec1 minute drop rate, 0 pkts/sec5 minute input rate 0 pkts/sec, 18 bytes/sec5 minute output rate 0 pkts/sec, 2 bytes/sec5 minute drop rate, 0 pkts/secInterface Ethernet0/0 "", is up, line protocol is up Hardware is 88E6095, BW 100 MbpsAuto-Duplex(Full-duplex), Auto-Speed(100 Mbps)Available but not configured via nameifMAC address 001e.4a39.b595, MTU not setIP address unassigned25 packets input, 2547 bytes, 0 no bufferReceived 4 broadcasts, 0 runts, 0 giants0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort 0 L2 decode drops0 switch ingress policy drops112 packets output, 7756 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 babbles, 0 late collisions, 0 deferred0 lost carrier, 0 no carrier0 rate limit drops0 switch egress policy dropsInterface Ethernet0/1 "", is down, line protocol is down Hardware is 88E6095, BW 100 MbpsAuto-Duplex, Auto-SpeedAvailable but not configured via nameifMAC address 001e.4a39.b596, MTU not setIP address unassigned0 packets input, 0 bytes, 0 no bufferReceived 0 broadcasts, 0 runts, 0 giants0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort 0 L2 decode drops0 switch ingress policy drops0 packets output, 0 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 babbles, 0 late collisions, 0 deferred0 lost carrier, 0 no carrier0 rate limit drops0 switch egress policy dropsInterface Ethernet0/2 "", is down, line protocol is down Hardware is 88E6095, BW 100 MbpsAuto-Duplex, Auto-SpeedAvailable but not configured via nameifMAC address 001e.4a39.b597, MTU not setIP address unassigned0 packets input, 0 bytes, 0 no bufferReceived 0 broadcasts, 0 runts, 0 giants0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort 0 L2 decode drops0 switch ingress policy drops0 packets output, 0 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 babbles, 0 late collisions, 0 deferred0 lost carrier, 0 no carrier0 rate limit drops0 switch egress policy dropsInterface Ethernet0/3 "", is down, line protocol is down Hardware is 88E6095, BW 100 MbpsAuto-Duplex, Auto-SpeedAvailable but not configured via nameifMAC address 001e.4a39.b598, MTU not setIP address unassigned0 packets input, 0 bytes, 0 no bufferReceived 0 broadcasts, 0 runts, 0 giants0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort 0 L2 decode drops0 switch ingress policy drops0 packets output, 0 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 babbles, 0 late collisions, 0 deferred0 lost carrier, 0 no carrier0 rate limit drops0 switch egress policy dropsInterface Ethernet0/4 "", is down, line protocol is down Hardware is 88E6095, BW 100 MbpsAuto-Duplex, Auto-SpeedAvailable but not configured via nameifMAC address 001e.4a39.b599, MTU not setIP address unassigned0 packets input, 0 bytes, 0 no bufferReceived 0 broadcasts, 0 runts, 0 giants0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort 0 L2 decode drops0 switch ingress policy drops0 packets output, 0 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 babbles, 0 late collisions, 0 deferred0 lost carrier, 0 no carrier0 rate limit drops0 switch egress policy dropsInterface Ethernet0/5 "", is up, line protocol is up Hardware is 88E6095, BW 100 MbpsAuto-Duplex(Full-duplex), Auto-Speed(100 Mbps)Available but not configured via nameifMAC address 001e.4a39.b59a, MTU not setIP address unassigned113 packets input, 8726 bytes, 0 no bufferReceived 97 broadcasts, 0 runts, 0 giants0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort 0 L2 decode drops0 switch ingress policy drops13 packets output, 1089 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 babbles, 0 late collisions, 0 deferred0 lost carrier, 0 no carrier0 rate limit drops0 switch egress policy dropsInterface Ethernet0/6 "", is down, line protocol is down Hardware is 88E6095, BW 100 MbpsAuto-Duplex, Auto-SpeedAvailable but not configured via nameifMAC address 001e.4a39.b59b, MTU not setIP address unassigned0 packets input, 0 bytes, 0 no bufferReceived 0 broadcasts, 0 runts, 0 giants0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort0 L2 decode drops0 switch ingress policy drops0 packets output, 0 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 babbles, 0 late collisions, 0 deferred0 lost carrier, 0 no carrier0 rate limit drops0 switch egress policy dropsInterface Ethernet0/7 "", is down, line protocol is down Hardware is 88E6095, BW 100 MbpsAuto-Duplex, Auto-SpeedAvailable but not configured via nameifMAC address 001e.4a39.b59c, MTU not setIP address unassigned47 packets input, 3554 bytes, 0 no bufferReceived 30 broadcasts, 0 runts, 0 giants1 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort0 L2 decode drops0 switch ingress policy drops12 packets output, 1458 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 babbles, 0 late collisions, 0 deferred0 lost carrier, 0 no carrier0 rate limit drops0 switch egress policy dropsciscoasa#ciscoasa#ciscoasa#开启web管理asdm image disk0:/asdm-523.binhttp server enablehttp 192.168.100.0 255.255.255.0 insideusername cisco password 3USUcOPFUiMCO4Jk encrypted privilege 15 配置透明模式的时候,一定要配置管理地址,不然是不会通的!清空配置wr erase。
思科5505火墙配置

asa 5505 常用配置2009-06-01 16:13asa 55051.配置防火墙名ciscoasa> enableciscoasa# configure terminalciscoasa(config)# hostname asa55052.配置telnetasa5505(config)#telnet 192.168.1.0 255.255.255.0 inside //允许内部接口192.168.1.0网段telnet防火墙3.配置密码asa5505(config)# password cisco//远程密码asa5505(config)# enable password cisco//特权模式密码4.配置IPasa5505(config)# interface vlan 2asa5505(config-if)# ip address 218.xxx.37.222 255.255.255.192 //vlan2配置IPasa5505(config)#show ip address vlan2//验证配置5.端口加入vlanasa5505(config)# interface e0/3//进入接口e0/3asa5505(config-if)# switchport access vlan 3//接口e0/3加入vlan3asa5505(config)# interface vlan 3//进入vlan3asa5505(config-if)# ip address 10.10.10.36 255.255.255.224//vlan3配置IPasa5505(config-if)# nameif dmzasa5505(config-if)# no shutdown//开启asa5505(config-if)# show switch vlan //验证配置6.最大传输单元MTUasa5505(config)#mtu inside 1500//inside最大传输单元1500字节asa5505(config)#mtu outside 1500//outside最大传输单元1500字节asa5505(config)#mtu dmz 1500//dmz最大传输单元1500字节7.配置arp表的超时时间asa5505(config)#arp timeout 14400//arp表的超时时间14400秒8.FTP模式asa5505(config)#ftp mode passive//FTP被动模式9.配置域名asa5505(config)#domain-name 10.启动日志asa5505(config)#logging enable//启动日志asa5505(config)#logging asdm informational //启动asdm报告日志asa5505(config)#Show logging//验证配置11.启用http服务asa5505(config)#http serverenable//启动HTTP server,便于ASDM连接。
将CiscoASA5500作为一种卓越的防火墙解决方案.doc

1.1 XX将Cisco ASA 5500作为一种卓越的防火墙解决方案CiscoASA5500 系列自适应安全设备提供领先的防火墙功能,并能够通过扩展支持其它安全服务。
在所有机构的网络安全基础设施中,防火墙都提供第一道防线。
它采用的具体作法是,将XX制定的用户网络访问权限策略与每次访问操作的连接信息进行比较.如果用户策略与连接信息不匹配,防火墙就不允许建立连接。
如果相互匹配,则防火墙允许流量流经网络。
通过这种方式,防火墙XX了XX机构网络安全基础设施的基本模块。
由于防火墙能够提供卓越的性能,延长关键业务运作的网络正常运行时间,因而物超所值。
但是,随着XX网络上XX、XX和协作流量的快速增长,企业不但要求防火墙引擎以超高速度运行,还要求它支持应用级检查.标准的L2和L3防火墙能够防止对内部和外部网络的非法接入,如果增加了应用级检测,防火墙将能够在L7检测、识别和验证应用类型,有效阻止不需要或误操作的应用流量。
利用这些功能,防火墙不但能执行端点用户XX和认证,还能有效控制多XX应用的使用。
1.1.1 对速度的要求在网络能够不断增强业务生产率、协作和通信的同时,防火墙也得到了同步的.例如,Cisco® ASA 5500 系列自适应安全设备就是专门为数百种应用协议的标准策略实施和应用级防火墙检测而开发的。
XX的第三方测试表明,这种防火墙的性能远远超过了同类产品.另外,在全球市场调查XXGartner于2021年6月进行的防火墙“魔方”调查中,Cisco ASA5500系列自适应安全设备在概念和技术上都名列榜首。
利用Cisco ASA5500系列的高性能应用检测功能,网络对待流量的详细策略依据不但能基于端口、状态和地址信息,还能基于深埋在数据帧头与负载中的应用信息。
通过对这种深度数据包检测信息与XX策略的比较,防火墙能够允许或阻止某些流量通过。
例如,如果XX策略禁止企图通过XX端口进入网络的应用流量通过网络,那么,即使这种流量在用户和连接水平上看似合法流量,也会被自动丢弃。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
配置要求:
1、分别划分inside(内网)、outside(外网)、dmz(安全区)三个区域。
2、内网可访问外网及dmz内服务器(web),外网可访问dmz内服务器(web)。
3、Dmz服务器分别开放80、21、3389端口。
说明:由于防火墙许可限制“no forward interface Vlan1”dmz内服务器无法访问外网。
具体配置如下:希望对需要的朋友有所帮助
ASA Version 7.2(4)
!
hostname asa5505
enable password tDElRpQcbH/qLvnn encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan1
nameif outside
security-level 0
ip address 外网IP 外网掩码
!
interface Vlan2
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan3
no forward interface Vlan1
nameif dmz
security-level 50
ip address 172.16.1.1 255.255.255.0
!
interface Ethernet0/0
description outside
!
interface Ethernet0/1
description inside
switchport access vlan 2
!
interface Ethernet0/2
description dmz
switchport access vlan 3
!
interface Ethernet0/3
description inside
switchport access vlan 2
!
interface Ethernet0/4
shutdown
!
interface Ethernet0/5
shutdown
!
interface Ethernet0/6
shutdown
!
interface Ethernet0/7
shutdown
!
ftp mode passive
object-group service outside-to-dmz tcp
port-object eq www
port-object eq ftp
port-object eq 3389
access-list aaa extended permit tcp any host 外网IP object-group outsid e-
to-dmz
access-list bbb extended permit tcp host 172.16.1.2 192.168.1.0 255.255. 255.0 ob
ject-group outside-to-dmz
pager lines 24
mtu outside 1500
mtu inside 1500
mtu dmz 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-524.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
global (dmz) 1 172.16.1.10-172.16.1.254 netmask 255.255.255.0
nat (inside) 1 192.168.1.0 255.255.255.0
nat (dmz) 1 172.16.1.0 255.255.255.0
alias (inside) 221.203.36.86 172.16.1.2 255.255.255.255
static (dmz,outside) tcp interface www 172.16.1.2 www netmask 255.255.2 55.255 d
ns
static (dmz,outside) tcp interface ftp 172.16.1.2 ftp netmask 255.255.2 55.255 d
ns
static (dmz,outside) tcp interface 3389 172.16.1.2 3389 netmask 255.255. 255.255
dns
static (inside,dmz) 172.16.1.2 192.168.1.0 netmask 255.255.255.255 dns access-group aaa in interface outside
access-group bbb in interface dmz
route outside 0.0.0.0 0.0.0.0 外网网关 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart telnet timeout 5
ssh timeout 5
console timeout 0
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect http
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:9d2a6010d4fc078cf026f98dcec96007 : end
asa5505(config)#。
