1思科虚拟无线控制器安装解析文档
思科无线: 2500 系列无线控制器部署指南新

思科 ISE 网络部署说明书

思科ISE中的网络部署此产品的文档集力求使用无偏见语言。
在本文档集中,无偏见定义为不暗示基于年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。
由于产品软件的用户界面中使用的硬编码语言,基于RFP文档使用的语言或引用的第三方产品使用的语言,文档中可能存在例外情况。
注释•Cisco ISE网络架构,第1页•Cisco ISE部署术语,第2页•分布式部署中的节点类型和角色,第2页•独立和分布式ISE部署,第3页•分布式部署方案,第4页•小型网络部署,第4页•中型网络部署,第6页•大型网络部署,第7页•每个部署模式的最大支持会话数,第9页•SNS3500/3600系列设备的部署规模和扩展建议,第11页•支持Cisco ISE功能所需的交换机和无线局域网控制器配置,第11页Cisco ISE网络架构Cisco ISE架构包括以下组件:•节点和角色类型•Cisco ISE节点-Cisco ISE节点可以承担以下任意或所有角色:管理、策略服务、监控或pxGrid•网络资源•终端策略信息点表示外部信息传达给策略服务角色所在的点。
例如,外部信息可以是轻量级目录访问协议(LDAP)属性。
Cisco ISE 部署术语本指南在讨论Cisco ISE 部署方案时使用以下术语:定义术语角色提供的特定功能,例如网络访问、分析、状态、安全组访问、监控和故障排除。
服务单个物理或虚拟思科ISE 设备。
节点思科ISE 节点可以承担下列任何角色:管理、策略服务、监控节点类型确定节点提供的服务。
思科ISE 节点可以承担以下任一或全部角色:。
通过管理用户界面可使用的菜单选项取决于节点承担的角色和人员。
角色确定节点是独立节点、主要节点还是辅助节点,并且仅适用于管理和监控节点。
角色分布式部署中的节点类型和角色Cisco ISE 节点可以根据它承担的角色提供各种服务。
部署中的每个节点均可承担管理、策略服务、pxGrid 和监控角色。
思科C9800-CL无线控制器 虚拟部署指南
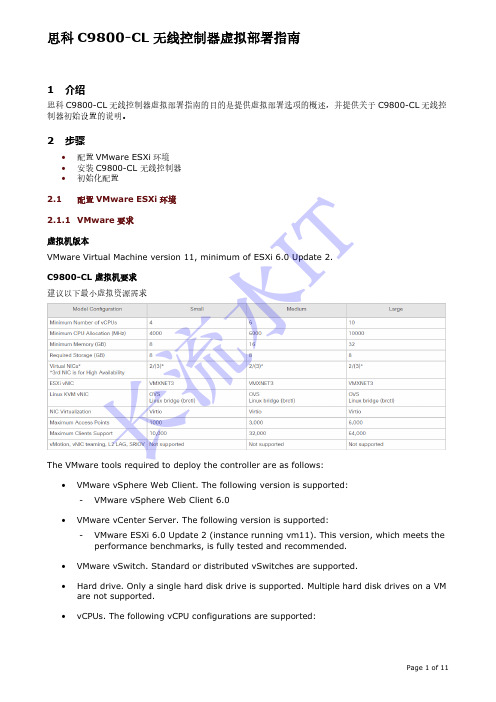
1 介绍思科C9800-CL 无线控制器虚拟部署指南的目的是提供虚拟部署选项的概述,并提供关于C9800-CL 无线控制器初始设置的说明。
2 步骤• 配置VMware ESXi 环境 • 安装C9800-CL 无线控制器 • 初始化配置2.1配置VMware ESXi 环境2.1.1 VMware 要求 虚拟机版本VMware Virtual Machine version 11, minimum of ESXi 6.0 Update 2. C9800-CL 虚拟机要求 建议以下最小虚拟资源需求The VMware tools required to deploy the controller are as follows:• VMware vSphere Web Client. The following version is supported:-VMware vSphere Web Client 6.0•VMware vCenter Server. The following version is supported: -VMware ESXi 6.0 Update 2 (instance running vm11). This version, which meets the performance benchmarks, is fully tested and recommended.• VMware vSwitch. Standard or distributed vSwitches are supported.•Hard drive. Only a single hard disk drive is supported. Multiple hard disk drives on a VM are not supported.•vCPUs. The following vCPU configurations are supported:长流水I T- Small Template —4 vCPUs (requires minimum 4-GB RAM allocation) - Medium Template —6 vCPUs (requires minimum 16-GB RAM allocation) - Large Template —10 vCPUs (requires minimum 32-GB RAM allocation)• Virtual CPU core• Virtual hard disk space —Minimum 8 GB is required.•Virtual Network Interface Cards (vNICs).2.1.2 Creating a Network Interface on a VMIn ESXi, configure the appropriate networking needed to support C9800-CL WLC. Therecommendation is to use a trunk port for wireless management interface, use an optional access port for the Device Management interface, and use an optional access port for high-availability interface. Such as the example below:Perform the following steps in the VMware vSphere Client to create a network interface.Step 1 Log in to the VMware vSphere Client.Step 2 In the vSphere GUI, select the VM host that will deploy C9800-CL WLC. Click theConfiguration tab.Step 3 In the Networking area, click Add Networking…Step 4 Under Connection Type , retain the default settings, and click Next .Step 5 Under Network Access , select the trunk VM NIC, and Click Next.The VM NIC uplink switch port must be a “trunk ” mode port.长流水I TStep 6 Under Connection Settings , enter a name in the Network Label field. From the VLANID (Optional) drop-down list, choose ‘All (4095)’. And then click Next.Step 7 Under Summary , confirm the updates and click Finish.The newly added network interface is now available in the Networking area.vSwitch Promiscuous ModeBy default, a hypervisor vSwitch is configured to “Reject ” promiscuous mode. If C9800 is using tagged traffic (e.g. management VLAN, AP VLAN, etc.) via management port, promiscuous mode allows the vSwitch to carry tagged tr affic. Therefore configure to “Accept ” promiscuous mode for the vSwitch.长流水I TStep 1 Under hypervisor > Configuration > Networking > Networking select vSwitch# beingmapped to the C9800 management interface.Step 2 Properties> Ports > vSwitch and click Edit.长流水I TStep 3 In Security Tab > Policy Exceptions > set Promiscuous mode = Accept.2.2Installing C9800-CL in a VMware ESXi EnvironmentStep 1 Log in to the VMware vSphere Client.Step 2 From the vSphere Client menu, choose File > Deploy OVF Template.长流水I TStep 3 In the OVA wizard, select the source of the controller OVA that is to be deployed. Click Next.Step 4 In the OVA Template details field, click Next.Step 5 In the Name and Location field, specify the name for the VM and click Next.Step 6 Under Deployment Configuration , select the required profile from the drop-down list and click Next.长流水I TStep 7 Under Disk Format , select ‘Thin Provision ’ and click Next.Step 8 From the Network Mapping drop-down list, allocate one or more virtual Network Interface Cards (vNICs) to the destination network. Connect each network to a unique interface. The following mapping is recommended:• GigabitEthernet 1 to device management interface and map it to the out-of-bandmanagement network.• GigabitEthernet 2 to wireless management interface and map it to the network to reach APs and services. Usually this interface is a trunk to carry multiple VLANs. •GigabitEthernet 3 to high-availability interface and map it to a separate network for peer-to-peer communication for SSO.Note Do not connect 2 interfaces to a single subnet as that causes network loop.Click Next . And then click Next to skip the management configuration.长流水I TStep 9 Under Ready to Complete , verify all the deployment settings.长流水I TStep 10 Click Finish to deploy the OVA.The controller VM will appear on the left panel when the deployment is completed.长流水I T2.3Configuring C9800-CL initial setup from consoleStep 1 Click Power On to power on the C9800-CL WLC.Step 2 Open the C9800-CL WLC Console, it is important to click into the console window and press ANY key to access the terminal when it show "Press any key to continue."Step 3 Select “vWLC – packages.conf ”Step 4 Terminate the configuration wizard.Would you like to enter the initial configuration dialog? [yes/no]: no Would you like to terminate autoinstall? [yes]:yes长流水I T思科C9800-CL 无线控制器虚拟部署指南Page 11 of 11Step 5 Set the hostname WLC#enableWLC#configure terminalWLC(config)#hostname C9800Step 6 Add login credentials using the following command: C9800(config)#username cisco privilege 15 password Cisco123 C9800(config)#enable secret Cisco123 C9800(config)#service password-encryptionStep 7 Add an IP address on the device Management interface. C9800(config)#interface gi1 C9800(config-if)#no switchport C9800(config-if)#ip address 192.168.1.2 255.255.255.0 //Change the IP accordingly C9800(config-if)#no shut C9800(config-if)#exit Step 8 Add the route to the remote network where you want to manage the C9800-CL from. C9800(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.1 //Change the gateway IP accordinglyStep 9 Configure VTYC9800(config)#line vty 0 4C9800(config-line)#login local C9800(config-line)#transport input allC9800(config-line)#exitStep 10 Login C9800-CL WLCNow you can login the C9800-CL WLC from CLI by SSH the management IP(192.168.1.2) or WEB GUI https://192.168.1.2 长流水I T。
思科路由模拟软件Packet Tracer安装及汉化教程
茂名门户: 茂名Seo:思科路由模拟软件Packet Tracer安装及汉化教程Packet Tracer 是由Cisco公司发布的一个辅助学习工具,为学习思科网络课程的初学者去设计、配置、排除网络故障提供了网络模拟环境。
用户可以在软件的图形用户界面上直接使用拖曳方法建立网络拓扑图,并可提供数据包在网络中行进的详细处理过程,观察网络实时运行情况。
可以学习IOS的配置、锻炼故障排查能力。
是要学习路由配置必不可少的模拟软件哦,今天茂名Seo就先给大家分享一下Packet Tracer的安装及汉化!工具/原料破电脑一台Packet Tracer模拟软件安装包一个Packet Tracer汉化补丁一、安装步骤:1、解压安装包,双击PacketTracer53_setup_no_tutorials.exe运行安装程序!2、安装提示,直接Next3、安装协议,选择I accept the agreement(我接受协议),继续单击Next!茂名门户: 茂名Seo:4、选择安装路径(喜欢安装在哪里就选择哪里吧)Next!5、问你这软件安装好了以后,在开始菜单里面的名称叫什么,可以自己随便填写,自己能记得就好!Next!茂名门户: 茂名Seo:6、有两个框,上面那个Create a desktop icon意思是问你是否要创建一个桌面图标(默认是选上的)另一个Create a Quick Launch icon意思是问你是否要创建一个快速启动图标!自己考虑,Next!7、检查确认你的安装信息!没问题就Install(安装)吧!茂名门户: 茂名Seo:8、安装完毕,问你是否需要马上启动Packet Tracer(勾上那个框就马上启动),然后单击Finish 完成安装大家现在可以看到,Packet Tracer的界面了,但现在界面还是英文的,怎么办呢?这时候就需要用到汉化补丁了!汉化步骤如下茂名门户: 茂名Seo:二、汉化1、解压汉化补丁所在的压缩包,把语言包“chinese.ptl”复制到文件安装目录下的“languages”目录下!2、启动Packet Tracer,在菜单栏选择“Options>>preferences”或按快捷键Ctrl+R弹出首选项!3、在弹出界面的下面“Select Language”范围中选择“chinese.ptl”补丁,点击“Change Language(更改语言)”。
思科UCSM VM-FEX安装配置手册

思科UCSM VM-FEX安装配置手册Cisco UCS针对虚拟化环境的网络管理提供了两种解决方案:一种是纯软件的Cisco Nexus 1000V;一种是基于Cisco UCS VIC (Virtual Interface Card)网卡的硬件解决方案。
Cisco Nexus 1000V是唯一的第三方分布式虚拟交换机,同样实现了交换机的数据功能和控制功能的分离。
基于硬件的解决方案服务器需要配置Cisco UCS VIC卡。
这块卡的虚拟化功能非常强大。
本文简要介绍一下Cisco UCS基于硬件的虚拟化网络管理解决方案的配置过程。
配置动态UCS vNIC登录到UCS Manager,进入服务器配置管理选项卡,选择某个Service Profile的vNIC配置,如图1所示,在Actions中选择“Change Dynamic vNIC Connection Policy”。
图1. 在UCSM中更改动态vNIC连接策略如图2所示,在弹出的“Change Dynamic vNIC Connection Policy”对话框中设置Dynamic vNIC的数量为53并选择适配器策略为VMwarePassThru。
图2. 设置动态vNIC数量以及适配器策略需要说明的是,每片UCS 刀片服务器的Cisco UCS VIC网卡能够虚拟的网卡和HBA卡数量总和为:vHBAs+vNICs+Dynamic vNICs=(15*n)-2 ,其中n为上联链路数量。
在我们的实验环境中,有4条上联链路,虚拟的vHBA卡为2块,vNIC为3块,所以能够虚拟的Dynamic vNIC数量为15*4-2-2-3=53。
利用Cisco UCS VIC网卡创建的vHBA、vNIC如图3所示。
图3. 在UCSM中创建的vHBA、动态vNIC、静态vNIC信息下表说明了在使用VMware平台时,不同连接情况下Cisco UCS VIC 可以支持的vHBA、动态vNIC、静态vNIC数量。
cisco思科怎么配置无线AP.doc

cisco思科怎么配置无线AP有许多人在使用了思科路由器后,不知道如何配置无线AP,不用急,在这里给大家详细介绍sisco思科如何配置无线AP。
cisco思科配置无线AP的方法无线接入点(AP)在无线网络中充当用户的中心通信点,可以连接有线和无线网络。
使用Web浏览器和命令行接口(CLI)都可以完成配置。
一般来说,AP可以配置两个接口以太网接口和无线端口。
a:配置方式1:控制台端口(需要翻转线)2:Telnet(远程登录)3:Web浏览器(这是最简单的配置方法,只需要在图形界面(GUI)上就可以操作)b:配置过程1:图形界面(GUI)根据IOS的不同,一般有两种基本的GUI 界面。
GUI配置简单这里就不说明了。
2:通过Telnet在MS-Dos中输入Telnet ip-address3:使用CLI(命令行)配置是本文的重点。
下面我将详细给大家说明。
首先连接物理线缆,打开超级终端(在系统开始菜单中的通讯中)。
超级终端的配置参数如下:* 每秒比特数:9600;*数据位:8;*奇偶效验:无;*停止位:1;*流控:Xon/Xoff或者无;进入命令行的界面如下:User Access VerificationUsername: CiscoPassword:Ap show version //可以查看当前版本信息一:设置系统名Ap enableAp#config tAp(config)#hostname myap //设置系统名,默认是ap二:为BVI分配IP地址当AP连接到有线网络的时候,会自动创建一个BVI(网桥虚拟接口)连接到网络,允许所有端口都聚合在一个IP地址下。
[说明一下我们只能在BVI接口上配置AP的IP地址,不能在其他接口]Ap#config tAp(config)#interface bvi1 //进入BVI接口配置模式Ap(config-if)#ip address address mask //第二个address为你分配的ip地址mask为掩码三:察看网络映射Ap(config)#dot11 network-map 30 //要建立无线网络映射Ap#show dot11 network-map //显示无线网络映射Ap#show dot11 adjacent-ap //显示一个与某个AP邻连的AP 列表下面给大家一个示范:Ap(config-if)#ip address 10.0.0.1 255.255.255.0Ap(config-if)#ip address dhcp ?Client-id Specify client-id to useHostname Specify value for hostname optionAp(config-if)#ip address dhcp关于启用和禁用接口的命令:shutdown 禁用no shutdown 启用四:配置SSIDSSID(服务集标示符)一个唯一的标识符,允许客户端识别出一个接入点(AP)Ap(config)#int dot11radio 0Ap(config-if)#ssid myAPAp(config-if-ssid)#authentication open //设置认证类型五:监控AP状态Ap#show interface dot11radio 加上相应接口号六:配置一些相应的服务1:Telnet/SSHAp(config)#line vty 0 4Ap(config-line)#login localAp(config-line)#endAp#show run!line con 0line vty 0 4login localline vty 5 15login!end2:热备份备用设备位于它监控的AP附近,并且它的配置与被监控的设备相同。
思科无线局域网控制器(WLC)错误和系统消息常见问题说明书

查看无线局域网控制器(WLC)错误和系统消息常见问题目录简介规则错误消息常见问题解答相关信息简介本文档介绍有关思科无线局域网(WLAN)控制器(WLC)的错误消息和系统消息的常见问题(FAQ)。
规则有关文档规则的详细信息,请参阅 Cisco 技术提示规则。
错误消息常见问题解答问:开始使用Cisco 4404 WLC将200多个接入点(AP)从Cisco IOS®软件转换为轻量AP协议(LWAPP)。
48个AP的转换已完成,WLC上收到的消息显示: [] spam_lrad.c 42121APAP。
为什么会出现此错误?A.您必须创建其他AP管理器接口才能支持超过48个AP。
否则,您将收到如下错误消息:Wed Sep 28 12:26:41 2005 [ERROR] spam_lrad.c 4212: AP cannot join becausethe maximum number of APs on interface 1 is reached.配置多个 AP 管理器接口,并配置其他 AP 管理器接口未使用的主/备份端口。
您必须创建另一个AP管理器接口以启动其他AP。
但是,请确保每个管理器的主端口和备份端口配置不会重叠。
换句话说,如果 AP 管理器 1 使用端口 1 作为主端口,端口 2 作为备份端口,则 AP 管理器 2 必须使用端口 3 作为主端口,端口 4 作为备份端口。
问:我有一台无线局域网控制器(WLC)4402,我使用1240个轻量接入点(LAP)。
我在WLC上启用了128位加密。
当我在WLC上选择128位WEP加密时,我收到一个错误消息,指出1240s不支持128位:[ERROR] spam_lrad.c 12839WEP128CISCO AP xx:xx:xx:xx:xx:xx:xx:xx:xx:xxSSID型。
为什么我会收到此错误消息?A.WLC上显示的密钥长度实际上是共享密钥中的位数,不包括初始化向量(IV)的24位。
思科 RV160W 路由器快速入门指南-1690805760.1775157说明书

快速入门指南思科 RV160W 路由器装箱清单•思科 RV160W 路由器•电源适配器•本快速入门指南•RoHS 合规信息卡•技术支持联系信息卡•以太网电缆•欧盟指令 2014/53/EU 合规信息(仅适用于欧盟 SKU)欢迎感谢您选择思科 RV160W 路由器。
RV160W 路由器不仅提供可靠的互联网访问连接,而且具备以下功能:•通过多种设置向导简化 UI 使用。
• 4 端口无线 AC VPN 路由器。
•支持 IPv6 防火墙。
•双频 WLAN(2.4GHz 和 5GHz)•企业级一体化小型企业网络。
本指南介绍思科 RV160W 的安装方法以及基于 Web 的设备管理器启动方法。
安装思科 RV160W1为防止设备过热或受损,请注意以下要求:•环境温度 - 请勿在环境温度超过 40°C (104°F) 的区域中使用本设备。
•通风 - 请确保设备周围通风良好。
若以壁挂方式安装设备,请确保散热孔朝向侧面。
•电路过载 - 接通设备电源不得造成电路过载。
•机械负载 - 请确保设备保持水平、平稳,以免出现任何危险情况;同时还应确保设备牢固固定,以防止其滑动或移位。
请勿在设备顶部放置任何物品,因为重量过高会损坏设备。
桌面安装若要将设备放置在桌面上,请将设备放置在平坦的表面上,以便设备依靠其四个橡胶支脚来支撑。
壁挂式安装路由器的底部面板上有两个壁挂槽。
要将路由器安装到墙壁上,需要使用壁挂式安装套件螺钉(随路由器提供)。
路由器壁挂式安装指南当选择路由器在墙壁上的安装位置时,需要考虑电缆限制和墙壁结构。
•安装路由器时,使前面板朝上。
确保将路由器安装在能够看到 LED 的高度。
2思科 RV160W 路由器快速入门指南•确保将电源放置在地板或桌面等水平表面上。
如果电源未得到适度支撑,电源适配器电缆过度拉紧可能会使其从路由器脱落。
•请勿将路由器或其电源安装在靠近任何类型热源(包括暖风出口)的位置。
您可以将路由器安装在空心墙或墙体立柱上。
Cisco2500系列无线控制器部署指南

Cisco2500系列⽆线控制器部署指南简介本⽂档是思科 2500 系列⽆线控制器的部署指南。
Cisco 2500系列⽆线控制器是零售、企业分⽀和中⼩型企业的⼀个有效系统⽆线解决⽅案。
当⽹络增长,控制器在⽹络能扩展。
Cisco 2500系列⽆线控制器混和到Cisco Unified⽆线⽹络(CUWN)并且与Cisco轻量级接⼊点(AP)⼀起使⽤和思科⽆线控制系统(WCS)或Cisco⽹络控制系统(NCS)或头等基础设施(PI)为了提供全系统的⽆线局域⽹功能。
⽆线AP之间的Cisco 2500系列⽆线控制器提供实时通信和其它设备为了提供集中化安全策略、访客访问、⽆线⼊侵防御系统(wIPS),上下⽂意识(位置),⽆线电频率(RF)管理和服务质量(QoS)移动服务的例如语⾳和视频和OfficeExtend接⼊点(OEAP)⽀持远程⼯作者解决⽅案的。
Cisco 2500系列⽆线控制器⽀持最多50轻量AP增量与⾄少的5个AP许可证5 AP许可证,做它零售和中⼩型企业的⼀个有成本效益的解决⽅案。
Cisco 2500系列⽆线控制器提供与802.11 a/b/g 的稳健覆盖或提供与使⽤的史⽆前例的可靠性802.11n、802.11ac和Cisco NEXT-GENERATION⽆线解决⽅案和Cisco企业⽹状⽹。
贡献⽤尼古拉斯Darchis, Cisco TAC⼯程师。
先决条件要求本⽂档没有任何特定的要求。
使⽤的组件本⽂档中的信息是基于思科 2500 系列⽆线控制器的。
硬件规格数据端⼝- 4 x 1千兆以太⽹端⼝控制台端⼝- 1个x RJ45外部 48V 电源本⽂档中的信息都是基于特定实验室环境中的设备编写的。
本⽂档中使⽤的所有设备最初均采⽤原始(默认)配置。
如果您使⽤的是真实⽹络,请确保您已经了解所有命令的潜在影响。
附加功能⽆线接⼊点(CAPWAP)协议控制和供应的⽀持。
在CAPWAP数据的加密建⽴隧道((可选)的DTL)。
CISCOWRVS4400N安装及配置

CISCO WRVS4400N的安装
使用WEB管理WRVS4400N
WRVS4400N的web界面默认只能通过有 线登陆,而不支持无线管理。所以要使用 一根网线连接到WRVS4400N的任意LAN 接口,并连接到计算机,将计算机的本地 连接设置为自动获取IP地址。
查看无线网络连接状态,自动获取到 了IP地址
支持4个服务集识别符(SSID) 3个全向 2-dBi增益外置天线 802.11Wi-Fi受保护访问(WPA)和高级加密标准(AES)(WPA2)
产品规格
路由(静态、RIPv1、v2、vlan间路由) 支持4个活动vlan 态主机配置协议(DHCP)服务器,DHCP客户端,DHCP中继代理 访问控制 5个远程访问的VPN隧道 5个用于分支机构间互联的网关到网关的IPSec隧道 服务质量QoS DES、3DES和高级加密AES加密算法的全面 IPsec VPN 功能 支持 MD5 和 SHA 身份验证算法 千兆以太网(10/100/1000) WAN 端口 4端口全双工10/100/1000 以太网交换机 NAT吞吐量:在禁用IPS时为800 Mbps
思科 ISE 安装 1说明书

安装思科ISE•使用CIMC安装思科ISE,第1页•思科ISE的运行设置程序,第3页•验证思科ISE安装过程,第6页使用CIMC安装思科ISE本部分列出简要安装步骤帮助您快速安装思科ISE:开始之前•确保您已满足本指南中指定的系统要求。
•(可选;仅在虚拟机上安装思科ISE时需要满足此要求)确保您已正确创建虚拟机。
有关详细信息,请参阅以下主题:•#unique_42•#unique_43•在Hyper-V上创建思科ISE虚拟机•(可选;仅在SNS硬件设备上安装思科ISE时需要满足此要求)确保要设置思科集成管理接口(CIMC)配置实用工具以管理设备并配置BIOS。
有关详细信息,请参阅以下文档:•有关SNS3500系列设备,请参阅Cisco SNS-3500系列设备硬件安装指南。
•有关SNS-3600系列设备,请参阅思科SNS-3600系列设备硬件安装指南。
步骤1如果要在以下设备上安装思科ISE:•思科SNS设备-安装硬件设备。
连接到CIMC进行服务器管理。
•虚拟机-确保VM已正确配置。
1步骤2下载思科ISE ISO 映像。
a)转至/go/ise 。
您必须已经具有有效的 登录凭证才能访问此链接。
b)单击为此产品下载软件(Download Software for this Product)。
思科ISE 映像上已经安装90天的评估许可证,因此在完成安装和初始配置后,可以对所有思科ISE 服务进行测试。
步骤3启动设备或虚拟机。
•思科SNS 设备:1.连接到CIMC 并使用CIMC 凭证登录。
2.启动KVM 控制台。
3.选择“虚拟媒体”(Virtual Media)>“激活虚拟设备”(Activate Virtual Devices)。
4.选择“虚拟媒体”(Virtual Media)>“映射CD/DVD ”(Map CD/DVD),并选择ISE ISO 映像,然后单击“映射设备”(Map Device)。
CiscoWLAN控制器的配置详解

关于Cisco控制器的操作系统为IOS系统,初始配置如同Cisco交换机和路由器一样,我们可以使用Console线缆接到WLC(WLAN Ctroller)Console端口对其进行初始化配置,然后再使用GUI的方式进行深入功能的配置。
1、基本配置(1)、配置控制器管理接口配置步骤:∙show interface detailed management*/显示管理接口的设置信息config wlan disable wlan-number*/关闭设备上所有WLAN∙config interface address management ip-addr ip-netmask gateway */配置管理接口的地址、掩码、网关config interface vlan management {vlan-id | 0}*/配置管理接口VLAN,0代表untagged VLAN,非0值代表tagged VLAN,而思科控制器只识别tagged VLAN。
config interface port management physical-ds-port-number*/配置管理接口的物理目的端口config interface dhcpmanagement ip-address-of-primary-dhcp [ip-address-of-secondary-dhcp-serve r]*/配置管理接口的主DHCP服务器和次DHCP服务器。
config interface acl management access-control-list-name*/配置管理接口的ACL(控制列表)∙∙∙∙∙∙∙∙∙save config*/保存配置∙show interface detailed management*/显示管理接口的设置信息(2)、配置AP管理接口配置步骤:∙show interface summary*/显示接口汇总信息∙show interface detailed ap-manager*/显示AP管理接口设置信息config wlan disable wlan-number*/关闭该接wlan通讯config interface address ap-manager ip-addr ip-netmask gateway */配置AP管理接口的IP地址、掩码、网关config interface vlan ap-manager {vlan-id | 0}*/配置AP管理接口的VLAN,0代表untagged VLAN,非0值代表tagged VLAN,而思科控制器只识别tagged VLAN。
思科无线: 2500 系列无线控制器部署指南新

思科无线控制器配置基础

44xx WLAN Controller
§ 型号 4402
支持 12, 25, 和50 AP
§ 型号 4404
支持100 APs
Presentation_ID
© 2019 Cisco Systems, Inc. All rights reserved.
无线控制器配置基础
Presentation_ID
© 2019 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
1
PDF 文件使用 "pdfFactory Pro" 试用版本创建 fineprint
基本配置任务及过程
§ 准备工作
1. 控制器启动配置和升级控制器软件版本 2. 熟悉控制器配置界面 3. 连接AP到控制器上
配置3层交换机
§ p dhcp excluded-address 192.168.10.1
§ ip dhcp excluded-address 192.168.10.254
§ ip dhcp excluded-address 192.168.10.2
§! § ip dhcp pool AP
§ network 192.168.10.0 255.255.255.0
PDF 文件使用 "pdfFactory Pro" 试用版本创建 fineprint
$18,890 $10,070
$4,875
5
4400系列无线控制器
§ 1 RU 高度
2口 或者 4口千兆上联
§ 支持 12, 25, 50 or 100 AP § 支持 5000 MAC地址转发表 § 10/100Base-TX 以太网 Service Port § 9 pin 串口Console口 § 2 扩展槽和1个utility port目前未使用 § 2 热插拔电源模块插槽
思科 Catalyst 9800 无线控制器 N+1 高可用性白皮书说明书
High Availability White PaperTable of ContentsIntroduction (3)N+1 High Availability Overview (3)Components Used (4)Difference Between SSO (Stateful Switchover) and N+1 High availability (4)Moving APs between controllers and preserving tags (5)N+1 High Availability Configuration using WebUI (5)Configuration on AP Join Profile (6)CAPWAP Timers (6)Configuration on Access Points (7)N+1 High availability workflow using Cisco DNA Center (8)Image Upgrade with N+1 deployment (8)Licensing (8)IntroductionThis guide provides information on the theory of operation and configuration for the Cisco Catalyst 9800 Wireless Controller as it pertains to N+1 mode of High Availability allowing a single WLC to be used as a backup controller for ‘N’ primary controllers. This solution allows for High availability to be configured for controllers that are geographically on separate L3 network or across the WAN link.N+1 High Availability Overview•The N+1 High Availability architecture provides redundancy for controllers across geographically apart data centers with low cost of deployment.• A single backup controller can be used in order to provide backup for multiple primary WLCs, considering appropriate compatibility in terms of AP mode.•These WLCs are independent of each other and do not share configuration or IP addresses on any of their interfaces. Each of the WLCs needs to be managedseparately and can run a different hardware and a different software version. Notethat if the software version is different between the Primary and secondarycontrollers, the AP will download the software upon joining the secondary controller and result in higher failover time will.•These WLCs can be deployed in different datacenters across the WAN link.•N+1 HA is not stateful, meaning that no state information about APs and clients is shared between controllers and thus the AP’s CAPWAP state machine will berestarted when the primary controller fails.•When a primary WLC resumes operation, the APs fall back from the backup WLC to the primary WLC automatically if the AP fallback option is enabled.•APs with high priority on the Primary always connect first to the Backup controller even if they have to push out low priority APs.•The N+1 HA can be configured in combination with AP SSO where the Primary and/or secondary controllers are their own SSO pair.•It is recommended to have the same configuration in terms of WLANs, profiles, mobility group, policy, RF and site tags as well as AP-to-tag mappings on theprimary, secondary and tertiary controllers to avoid AP flaps and service disruptions when failing over.Components UsedThe information in this document is based on these software and hardware versions: •Catalyst Wireless Controllers 9800-L, 9800-40, 9800-80, 9800-CL, Embedded wireless controller on switch and Embedded Wireless Controller(EWC) on AP9100s. •802.11ax, Wave 2 and Wave 1 802.11ac Access points.•IOS XE Release 16.10 and higher.Difference Between SSO (Stateful Switchover) and N+1 HighavailabilityMoving APs between controllers and preserving tagsThe following should be considered when moving APs between two C9800 wireless controllers for N+1 HA (C9800-1 and C9800-2):●If the AP on C9800-1 doesn’t hold any tag information (the command ap name <AP name>write tag-config was not used)and there is no mapping configured for that AP on C9800-2, the AP will be assigned default tags when moved to C9800-2.●The AP will retain the tag information when moving between the controllers, if both have thesame mapping of AP to tags. This can be done via static configuration, by assigning the AP toa location, or via filters.●The AP will also retain its tag when moved between the two controllers if the tags are savedto the AP (with the write tag-config command) and the tags are defined on both controllers.●If the AP has a saved tag assigned via the write tag-config command and joins a controllerwhere those tags are not present, it will be assigned to the default tags (assuming no other mapping is configured on the controller that the AP is joining).●In all cases, if the AP retains its tag name assignment but the settings within the tag aredifferent on the two controllers, the AP will be configured based on the settings present on the currently joined controller.When moving an AP from an AireOS controller to a C9800 controller, since the AP doesn’t carry any tag information from AireOS, it will be mapped to the default tags; this is true unless a static or dynamic tag pre-assignment has been done on the C9800 controller, as explained above.When configuring N+1 HA,•make sure that the controller has the tags and AP-to-tag mapping defined using static mapping or regular expression mapping based on AP name/location.OR•Use the write tag-config command to save the tags on the AP and define the tags on the secondary controller.N+1 High Availability Configuration using WebUIThere are two ways to configure N+1 High Availability on the Catalyst 9800: Using the AP join Profiles or High Availability configuration individually on the Access point.Configuration on AP Join ProfileUnder Configuration > Tags & Profiles > AP Join, configure the Primary Controller Name and IP and Secondary Controller Name and IP. The Enable Fallback option determines if the APs fall back from the backup WLC to the primary WLC automatically if the Primary becomes available. This is enabled by default. CAPWAP Timers and Retransmit timers are used to customize heartbeat and discovery timeouts as well as the retransmit count and interval to track the AP’s connection to the controller.CAPWAP Timers•In the Heartbeat Timeout field, enter the time (in seconds) to configure the heartbeat timer for all access points. Specifying a small heartbeat interval reduces the amount of time it takes to detect device failure.•In the Discovery Timeout field, enter a value between 1 and 10 seconds (inclusive) to configure the AP discovery request timer.•In the Primary Discovery Timeout field, enter a value between 30 and 3000 seconds (inclusive) to configure the access point primary discovery requesttimer.•In the Primed Join Timeout field, enter a value between 120 and 43200 seconds (inclusive) to configure the access point primed join timeout.•In the Retransmit Timers Count field, enter the number of times that you want the AP to retransmit the request to the device and vice-versa. Validrange is between 3 and 8.•In the Retransmit Timers Interval field, enter the time duration between retransmission of requests. Valid range is between 2 and 5.CLI Commands:WLC(config-ap-profile)#capwap backup ?primary Configures primary Controllersecondary Configures secondary ControllerWLC(config-ap-profile)#capwap fallbackCLIs for CAPWAP Timers:WLC(config-ap-profile)#capwap retransmit ?count Configures AP CAPWAP control packet retransmit countinterval Configures AP CAPWAP control packet retransmit interval WLC(config-ap-profile)#capwap timerWLC(config-ap-profile)#capwap timers ?discovery-timeout Configures AP Discovery Timeoutfast-heartbeat-timeout Configures fast heartbeat timeoutheartbeat-timeout Configures heartbeat timeoutprimary-discovery-timeout Configures primary discovery timeoutprimed-join-timeout Configures primed join timeout Configuration on Access PointsUnder Configuration > Wireless > Access Points, click on the AP. Under the High Availability tab configure Primary, Secondary, Tertiary Controller. AP failover priority determines priority on the access points that connecting to the Primary controller.CLI Commands:WLC#ap name 00f2.8b26.8a30 controller ?primary Configure primary controllersecondary Configure secondary controllertertiary Configure tertiary controllerWLC#ap name 00f2.8b26.8a30 priority ?<1-4> Enter priority numberImage Upgrade with N+1 deploymentZero downtime network upgrade is a challenge for Wireless Networks. The reason is that these networks are made up of a set of interlocked devices, WLCs and a set of APs, which all need to be up to keep the network operational.The advent of Rolling AP Upgrade opens up new possibilities for upgrading the controller code in a network without bringing the network down using an N+1 controller. This can effectively achieve a Zero Downtime network upgrade in a N+1 deployment.The idea here is to upgrade access points in a wireless network in a staggered manner, using the same Rolling AP update infrastructure as described earlier in this document, such that an appropriate number of APs are always up and running in the network and providing RF coverage to clients. For N+1 Rolling AP Upgrade to work seamlessly it is essential that the WLCs be part of the same mobility group and have the same WLAN configuration.This is explained in detail in the Patching guide here:https:///c/dam/en/us/td/docs/wireless/controller/9800/17-1/deployment-guide/c9800-ha-rau-apsp-apdp-issu-rel-17-1.pdfCisco DNA Center Configuration for N+1 High AvailabilityCisco DNA Center supports Primary and Secondary configurations for N+1 HA. The below sequence outlines the workflow to configure N+1 High Availability using Cisco DNA CenterStep 1: Discover both the primary and secondary WLC devices.Check for network connectivity between these devicesStep 2: Create buildings where the access points will be connecting to the primary and secondary controllers. In the example below the two buildings, building-sj and building-cali are created where building-sj will be a Primary managed location for WLC-1 and same will be a Secondary managed location for WLC-2.Building-cali is configured as only a primary managed location for WLC-2.managed by WLC-1Step 4: Provision the Secondary device WLC-2. In this example, WLC-2 is the primary device for building-cali and secondary device for building-sj. So, building-sj APs have Primary as WLC-1 and secondary N+1 as WLC-2Select the building-sj primary managed locationPrimary device has 1 managed primary location.Configure interface and VLANSecondary device has 1 managed primary location as building-caliAnd one secondary managed location as building-sjStep 5: Verify AP Provisioning SummarySecondary device has 1managed primary locationand 1 secondary ManagedlocationConfigure interface andVLANManaged locations ofsecondary device Selecting the floor from primary managed location of building-sjLicensing•With Catalyst 9800 since Smart Licensing is mandatory, only as many licenses as the total number of APs in the network are required.•When APs failover from primary to secondary and tertiary controllers, the smart licensing infrastructure seamless handles the failover since the AP MAC is sent in the entitlement request to the CSSM portal.•N+1 HA is part of DNA Essentials Licensing Tier.•There is no HA-SKU on the Catalyst 9800 wireless controllers.For a more detailed overview on Cisco Licensing, go to /go/licensingguide. Legal InformationTHE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEENADVISED OF THE POSSIBILITY OF SUCH DAMAGES.Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.All printed copies and duplicate soft copies are considered un-Controlled copies and the original on-line version should be referred to for latest version.Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at /go/offices.Cisco TrademarkCisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: /go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)Cisco Copyright© 2021 Cisco Systems, Inc. All rights reserved.。
思科虚拟无线局域网控制器 8.2 配置向导和最佳实践说明书
思科虚拟无线局域网控制器 8.2 配置向导和最佳实践 v1最后更新日期:2015 年 11 月 23 日关于本解决方案虚拟无线控制器 (vWLC) 能够以具成本效益的方式管理、保护和优化本地和分支机构无线网络的性能。
虚拟无线控制器有助于服务器整合,并通过减少中断提高业务连续性,是中小型企业的理想之选。
作为思科统一无线网络的组件之一,虚拟无线控制器能够实现 Cisco Aironet 接入点、Cisco Prime 基础设施和思科移动业务引擎之间的实时集中通信。
这款虚拟无线控制器专为具有虚拟化意向的组织而设计,而且能够为中小型企业部署提供以下优势:•为最多 200 个分支机构提供集中式无线网络可视性和可控性功能•IT 管理人员能够通过 FlexConnect 对最多 200 个接入点和 3000 个客户端进行配置、管理和故障排除•实现安全访客接入、符合支付卡行业 (PCI) 法规的非法检测,以及本地交换 Wi-Fi 音频和视频•与分支机构网络的 Cisco FlexConnect 解决方案实现可靠连接•防止连接至远程控制器的接入点因分支机构 WAN 故障而受到影响更多 vWLC 资源信息位于/c/en/us/products/wireless/virtual-wireless-controller/index.html关于本演示本演示展示如何使用运行 8.2.1.97 软件的 vWLC 所提供的基于 HTTP 的配置向导。
通过配置向导可配置控制器上的基本设置。
从工厂收到控制器后或已将控制器重置到出厂默认设置后,可运行该向导。
注意:本演示中使用的当前代码为 Beta 版,而且不支持某些 AP 型号。
在本演示中,不建议用户将 AP 连接到控制器上。
本预配置演示包括以下内容:•场景 1:vWLC 配置向导•场景 2:最佳实践要求下表概括该预配置演示要求。
表 1.演示要求监控工作站•笔记本电脑终端套件首选终端路由器•已为 dCloud 注册并配置的 819W 路由器受支持终端路由器/AP•已为 dCloud 注册并配置的路由器•Cisco Aironet 系列接入点(3000、2000、1000 系列)用户设备•平板电脑/智能手机/笔记本电脑拓扑此内容包含预配置的用户和组件,旨在说明解决方案脚本场景和功能。
cisco无线控制配置说明

cisco⽆线控制配置说明ContentsIntroductionPrerequisitesRequirementsComponents UsedConventionsBackground InformationConfigureNetwork DiagramConfigure the WLC for Basic OperationConfigure the Switch for the WLCConfigure the Switch for the APsVerifyTroubleshootCommandsController Does Not Defend AP-Manager IP AddressTroubleshoot a Lightweight Access Point Not Joininga Wireless LAN ControllerCisco Support Community - Featured ConversationsRelated InformationIntroductionThis document provides a basic configuration example of a lightweight access point (AP) that is connected to a Cisco Wireless LAN (WLAN) Controller (WLC) through a Cisco Catalyst Switch.PrerequisitesRequirementsEnsure that you meet these requirements before you attempt this configuration:Basic knowledge of the configuration of lightweight APs and Cisco WLCsBasic knowledge of Lightweight AP Protocol (LWAPP)Knowledge of the configuration of an external DHCP server and/or domain name server (DNS)Basic configuration knowledge of Cisco switchesComponents UsedThe information in this document is based on these software and hardware versions:Cisco Aironet 1232AG Series Lightweight APCisco 4402 Series WLC that runs firmware 5.2.178.0Microsoft Windows Server 2003 Enterprise DHCP serverThis configuration works with any other Cisco WLC and any lightweight AP.The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.ConventionsRefer to the Cisco Technical Tips Conventions for more information on document conventions.Background InformationIn order for the WLC to be able to manage the LAP, the LAP should discover the controller and register with the WLC. There are different methods that an LAP uses in order to discover the WLC. For detailed information on the different methods the LAPs use to register to the WLCs, refer to Lightweight AP (LAP) Registration to a Wireless LAN Controller (WLC)This document describes the configuration steps needed to register the LAP to the WLC and for basic operation of the LWAPP wireless network.ConfigureIn order to register the LAP to the WLC and for basic operation of the LWAPP wireless network, complete these steps:1.Have a DHCP server present so that the APs can acquire a networkaddress.Note: Option 43 is used if the APs reside in a different subnet.2.Configure the WLC for basic operation.3.Configure the switch for the WLC.4.Configure the switch for the APs.5.Register the lightweight APs to the WLCs.Note: Use the Command Lookup Tool (registered customers only) in order to obtain more information on the commands used in this section.Network DiagramThis document uses this network setup:Configure the WLC for Basic OperationWhen the controller boots at factory defaults, the bootup script runs the configuration wizard, which prompts the installer for initial configuration settings. This procedure describes how to use the configuration wizard on the command-line interface (CLI) in order to enter initial configuration settings.Note: Be sure that you understand how to configure an external DHCP server and/or DNS.Complete these steps in order to configure the WLC for basicoperation:1.Connect your computer to the WLC with a DB-9 null modem serial cable.2.Open a terminal emulator session with these settings:o9600 baudo8 data bitso 1 stop bito No parityo No hardware flow control3.At the prompt, log in to the CLI.The default username is admin, and the default password is admin.4.If necessary, enter reset system in order to reboot the unit andstart the wizard.5.At the first wizard prompt, enter a system name. The system namecan include up to 32 printable ASCII characters.6.Enter an administrator user name and password. The user name andpassword can include up to 24 printable ASCII characters.7.Enter the service-port interface IP configuration protocol, eithernone or DHCP.Enter none if you do not want to use the service port or if you want to assign a static IP address to the service port. 8.If you entered none in step 7 and need to enter a static IP addressfor the service port, enter the service-port interface IP address and netmask for the next two prompts.If you do not want to use the service port, enter 0.0.0.0 for the IP address and netmask.9.Enter values for these options:o Management interface IP addresso Netmasko Default router IP addresso Optional VLAN identifierYou can use a valid VLAN identifier or 0 for untagged.10.Note: When the management interface on the controller isconfigured as part of the 'native vlan' on the switchport to which it connects, the controller should NOT tag the frames. Therefore, you must set the VLAN to be zero (on the controller).11.Enter the Network Interface (Distribution System) Physical Portnumber.For the WLC, the possible ports are 1 through 4 for a front-panel gigabit Ethernet port.12.Enter the IP address of the default DHCP server that supplies IPaddresses to clients, the management interface, and theservice-port interface, if you use one.13.Enter the LWAPP Transport Mode, either LAYER2 or LAYER3.Note: If you configure the WLC 4402 via Wizard and select AP transport Mode LAYER2, the Wizard does not ask the details of AP Manager.14.Enter the Virtual Gateway IP Address.This address can be any fictitious, unassigned IP address, such as1.1.1.1, for the Layer 3 Security and Mobility managers to use.Note: Usually the Virtual Gateway IP Address that is used is a private address.15.Enter the Cisco WLAN Solution Mobility Group/RF Group name.16.Enter the WLAN 1 service set identifier (SSID) or network name.This identifier is the default SSID that lightweight APs use in order to associate to a WLC.17.Allow or disallow Static IP Addresses for clients.Enter yes in order to allow clients to supply their own IP addresses.Enter no in order to require clients to request an IP address froma DHCP server.18.If you need to configure a RADIUS server on the WLC, enter yes andenter this information:o RADIUS server IP addresso The communication porto The shared secretIf you do not need to configure a RADIUS server or you want to configure the server later, enter no.19.Enter a country code for the unit.Enter help in order to see a list of the supported countries.20.Enable and disable support for IEEE 802.11b, IEEE 802.11a, and IEEE802.11g.21.Enable or disable radio resource management (RRM) (auto RF).WLC 4402—Configuration WizardWelcome to the Cisco Wizard Configuration ToolUse the '-' character to backupSystem Name [Cisco_43:eb:22]: c4402Enter Administrative User Name (24 characters max): adminEnter Administrative Password (24 characters max): *****Service Interface IP Address Configuration [none][DHCP]: noneEnable Link Aggregation (LAG) [yes][NO]: No Management Interface IP Address:192.168.60.2Management Interface Netmask:255.255.255.0Management Interface Default Router: 192.168.60.1Management Interface VLAN Identifier (0 = untagged): 60Management Interface Port Num [1 to 2]: 1 Management Interface DHCP Server IP Address: 192.168.60.25AP Transport Mode [layer2][LAYER3]: LAYER3 AP Manager Interface IP Address:192.168.60.3AP-Manager is on Management subnet, using same valuesAP Manager Interface DHCP Server(192.168.50.3): 192.168.60.25Virtual Gateway IP Address: 1.1.1.1 Mobility/RF Group Name: RFgroupname Network Name (SSID): SSIDAllow Static IP Addresses [YES][no]: yes Configure a RADIUS Server now? [YES][no]: no Enter Country Code (enter 'help' for a list of countries) [US]: USEnable 802.11b Network [YES][no]: yes Enable 802.11a Network [YES][no]: yes Enable 802.11g Network [YES][no]: yes Enable Auto-RF [YES][no]: yesNote: The management interface on the WLC is the only consistently pingable interface from outside of the WLC. So it is an expected behavior if you are not able to ping the AP manager interface from outside of the WLC.Note: You must configure the AP manager interface in order for the APs to associate with the WLC.Configure the Switch for the WLCThis example uses a Catalyst 3750 switch that uses only one port. The example tags the AP-manager and management interfaces and places these interfaces on VLAN 60. The switch port is configured as an IEEE 802.1Q trunk and only the appropriate VLANs, which are VLANs 2 through 4 and 60 in this case, are allowed on the trunk. The management and AP-manager VLAN (VLAN 60) is tagged and is not configured as the native VLAN of the trunk. So when the example configures those interfaces on the WLC, the interfaces are assigned a VLAN identifier.This is an example 802.1Q switch port configuration:interface GigabitEthernet1/0/1description Trunk Port to Cisco WLCswitchport trunk encapsulation dot1qswitchport trunk allowed vlan 2-4,60switchport mode trunkno shutdownNote: When you connect the WLC gigabit port, make sure it is connected to the switch gigabit port only. If you connect the WLC gigabit Ethernet to the Switch FastEthernet port then it will not work.Notice that this configuration example configures the neighbor switch port in a way that only allows relevant VLANs on the 802.1Q trunk. All other VLANs are pruned. This type of configuration is not necessary, but it is a deployment best practice. When you prune irrelevant VLANs, the WLC only processes relevant frames, which optimizes performance.Configure the Switch for the APsThis is an example VLAN interface configuration from the Catalyst 3750: interface VLAN5description AP VLANip address 10.5.5.1 255.255.255.0While the Cisco WLCs always connect to 802.1Q trunks, Cisco lightweight APs do not understand VLAN tagging and should only be connected to the access ports of the neighbor switch.This is an example switch port configuration from the Catalyst 3750:interface GigabitEthernet1/0/22description Access Port Connection to Cisco Lightweight APswitchport access vlan 5switchport mode accessno shutdownThe infrastructure is now ready for connection to the APs. The LAPs use the different WLC discovery methods and select a WLC to join. The LAP then registers with the controller.Here is a link to a video on the Cisco Support Community that explainsthe initial configuration of Wireless LAN Controller using the CLI and GUI: Initial configuration of Wireless LAN Controller using the CLI andGUIVerifyUse this section in order to confirm that your configuration works properly.After the LAPs register with the controller, you can view them under Wireless at the top of the user interface of the controller:On the CLI, you can use the show ap summary command in order to verify that the LAPs registered with the WLC: (Cisco Controller) >show ap summaryNumber of APs (1)Global AP User Name.............................. Not Configured Global AP Dot1x User Name........................ Not ConfiguredAP Name Slots AP Model Ethernet MAC Location Port Country Priority------------------ ----- ------------------- --------------------------------- ---- ------- ------AP001b.d4e3.a81b 2 AIR-LAP1232AG-A-K9 00:1b:d4:e3:a8:1b default location 2 IN 1On the WLC CLI, you can also use the show client summary command in order to see the clients that are registered with the WLC:(Cisco Controller) >show client summaryNumber of Clients (1)MAC Address AP Name Status WLAN Auth Protocol Port----------------- ------------- ------------- ---- ---- -------- ----00:40:96:a1:45:42 ap:64:a3:a0 Associated 4 Yes 802.11a 1(Cisco Controller) >Here is a video demonstration that explains how to perform the initial configuration of a Wireless LAN Controller using the GUI and CLI: InitialConfiguration of Wireless Lan Controller using CLI and GUITroubleshootUse this section in order to troubleshoot your configuration. CommandsUse these commands in order to troubleshoot your configuration.Note: Refer to Important Information on Debug Commands before you use debug commands.This debug lwapp events enable WLC command output shows that the lightweight AP gets registered to the WLC: (Cisco Controller) >debug lwapp events enableTue Apr 11 13:38:47 2006: Received LWAPP DISCOVERY REQUEST from AP00:0b:85:64:a3:a0 to ff:ff:ff:ff:ff:ff on port '1'Tue Apr 11 13:38:47 2006: Successful transmission of LWAPPDiscovery-Responseto AP 00:0b:85:64:a3:a0 on Port 1Tue Apr 11 13:38:58 2006: Received LWAPP JOIN REQUEST from AP00:0b:85:64:a3:a0 to 00:0b:85:33:a8:a0 on port '1'Tue Apr 11 13:38:58 2006: LWAPP Join-Request MTU path from AP00:0b:85:64:a3:a0is 1500, remote debug mode is 0Tue Apr 11 13:38:58 2006: Successfully added NPU Entry for AP00:0b:85:64:a3:a0 (index 48) Switch IP: 192.168.60.2, Switch Port: 12223,intIfNum 1, vlanId 60 AP IP: 10.5.5.10, AP Port: 19002, next hop MAC: 00:0b:85:64:a3:a0Tue Apr 11 13:38:58 2006: Successfully transmission of LWAPP Join-Reply to AP00:0b:85:64:a3:a0Tue Apr 11 13:38:58 2006: Register LWAPP event for AP00:0b:85:64:a3:a0 slot 0Tue Apr 11 13:38:58 2006: Register LWAPP event for AP 00:0b:85:64:a3:a0 slot 1Tue Apr 11 13:39:00 2006: Received LWAPP CONFIGURE REQUEST from AP00:0b:85:64:a3:a0 to 00:0b:85:33:a8:a0Tue Apr 11 13:39:00 2006: Updating IP info for AP 00:0b:85:64:a3:a0 -- static 0, 10.5.5.10/255.255.255.0, gtw 192.168.60.1 Tue Apr 11 13:39:00 2006: Updating IP 10.5.5.10 ===> 10.5.5.10 for AP 00:0b:85:64:a3:a0Tue Apr 11 13:39:00 2006: spamVerifyRegDomain RegDomain set for slot 0 code 0regstring -A regDfromCb -ATue Apr 11 13:39:00 2006: spamVerifyRegDomain RegDomain set for slot 1 code 0regstring -A regDfromCb -ATue Apr 11 13:39:00 2006: spamEncodeDomainSecretPayload:Send domain secretMobilityGroup<6f,39,74,cd,7e,a4,81,86,ca,32,8c,06,d3,ff,ec,6d,95,10,99,dd>to AP 00:0b:85:64:a3:a0Tue Apr 11 13:39:00 2006: Successfully transmission of LWAPPConfig-Message to AP 00:0b:85:64:a3:a0Tue Apr 11 13:39:00 2006: Running spamEncodeCreateVapPayload for SSID 'SSID'Tue Apr 11 13:39:00 2006: AP 00:0b:85:64:a3:a0 associated. Last AP failure wasdue to Configuration changes, reason: operator changed 11g mode Tue Apr 11 13:39:00 2006: Received LWAPP CHANGE_STATE_EVENT from AP 00:0b:85:64:a3:a0Tue Apr 11 13:39:00 2006: Successfully transmission of LWAPPChange-State-EventResponse to AP 00:0b:85:64:a3:a0Tue Apr 11 13:39:00 2006: Received LWAPP Up event for AP 00:0b:85:64:a3:a0 slot 0!Tue Apr 11 13:39:00 2006: Received LWAPP CONFIGURE COMMAND RES from AP 00:0b:85:64:a3:a0Tue Apr 11 13:39:00 2006: Received LWAPP CHANGE_STATE_EVENT from AP 00:0b:85:64:a3:a0Tue Apr 11 13:39:00 2006: Successfully transmission of LWAPPChange-State-EventResponse to AP 00:0b:85:64:a3:a0Tue Apr 11 13:39:00 2006: Received LWAPP Up event for AP00:0b:85:64:a3:a0 slot 1!This output shows these useful WLC debug commands:debug pem state enable—Configures the access policy manager debug optionsdebug pem events enabledebug dhcp message enable—Shows the debug of DHCP messages that are exchanged to and from the DHCP server debug dhcp packet enable—Shows the debug of DHCP packet details that are sent to and from the DHCP serverTue Apr 11 14:30:49 2006: Applied policy for mobile 00:40:96:a1:45:42 Tue Apr 11 14:30:49 2006: STA [00:40:96:a1:45:42,192.168.1.41] Replacing FastPath rule type = Airespace AP Client on AP 00:0B:85:64:A3:A0, slot 0InHandle = 0x00000000, OutHandle = 0x00000000 ACL Id = 255, Jumbo Frames= NO, interface = 1 802.1P = 0, DSCP = 0, TTue Apr 11 14:30:49 2006: Successfully plumbed mobile rule for mobile 00:40:96:a1:45:42 (ACL ID 255)Tue Apr 11 14:30:49 2006: Plumbed mobile LWAPP rule on AP00:0b:85:64:a3:a0for mobile 00:40:96:a1:45:42Tue Apr 11 14:30:53 2006: DHCP proxy received packet, src: 0.0.0.0, len = 320Tue Apr 11 14:30:53 2006: dhcpProxy: Received packet: Client00:40:96:a1:45:42DHCP Op: BOOTREQUEST(1), IP len: 320, switchport: 1, encap: 0xec03 Tue Apr 11 14:30:53 2006: dhcpProxy(): dhcp request, client:00:40:96:a1:45:42: dhcp op: 1, port: 1, encap 0xec03, old mscbport number: 1Tue Apr 11 14:30:53 2006: dhcp option len, including the magic cookie = 84Tue Apr 11 14:30:53 2006: dhcp option: received DHCP REQUEST msgTue Apr 11 14:30:53 2006: dhcp option: skipping option 61, len 7Tue Apr 11 14:30:53 2006: dhcp option: requested ip = 192.168.1.41 Tue Apr 11 14:30:53 2006: dhcp option: skipping option 12, len 15Tue Apr 11 14:30:53 2006: dhcp option: skipping option 81, len 19Tue Apr 11 14:30:53 2006: dhcp option: vendor class id = MSFT 5.0 (len 8)Tue Apr 11 14:30:53 2006: dhcp option: skipping option 55, len 11Tue Apr 11 14:30:53 2006: dhcpParseOptions: options end, len 84, actual 84Tue Apr 11 14:30:53 2006: mscb->dhcpServer: 192.168.60.2,mscb->dhcpNetmask:255.255.255.0,mscb->dhcpGateway: 192.168.60.1, mscb->dhcpRelay:192.168.60.2 VLAN: 60Tue Apr 11 14:30:53 2006: Local Address: 192.168.60.2, DHCP Server: 192.168.60.2, Gateway Addr: 192.168.60.2, VLAN: 60, port: 1Tue Apr 11 14:30:53 2006: DHCP Message Type received: DHCP REQUEST msg Tue Apr 11 14:30:53 2006: op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 1Tue Apr 11 14:30:53 2006: xid: 3371152053, secs: 0, flags: 0Tue Apr 11 14:30:53 2006: chaddr: 00:40:96:a1:45:42Tue Apr 11 14:30:53 2006: ciaddr: 0.0.0.0, yiaddr: 0.0.0.0Tue Apr 11 14:30:53 2006: siaddr: 0.0.0.0, giaddr: 192.168.60.2Tue Apr 11 14:30:53 2006: Forwarding DHCP packet locally (348 octets) from 192.168.60.2 to 192.168.60.2Tue Apr 11 14:30:53 2006: Received 348 byte dhcp packet from 0x0201a8c0 192.168.60.2:68Tue Apr 11 14:30:53 2006: DHCP packet: 192.168.60.2 -> 192.168.60.2 using scope "InternalScope"Tue Apr 11 14:30:53 2006: received REQUESTTue Apr 11 14:30:53 2006: Checking node 192.168.1.41 Allocated 1144765719,Expires 1144852119 (now: 1144765853)Tue Apr 11 14:30:53 2006: adding option 0x35Tue Apr 11 14:30:53 2006: adding option 0x36Tue Apr 11 14:30:53 2006: adding option 0x33Tue Apr 11 14:30:53 2006: adding option 0x03Tue Apr 11 14:30:53 2006: adding option 0x01Tue Apr 11 14:30:53 2006: dhcpd: Sending DHCP packet(giaddr:192.168.60.2)to192.168.60.2:67 from 192.168.60.2:1067Tue Apr 11 14:30:53 2006: sendto (548 bytes) returned 548Tue Apr 11 14:30:53 2006: DHCP proxy received packet, src: 192.168.60.2, len = 548Tue Apr 11 14:30:53 2006: dhcpProxy: Received packet: Client00:40:96:a1:45:42DHCP Op: BOOTREPLY(2), IP len: 548, switchport: 0, encap: 0x0Tue Apr 11 14:30:53 2006: dhcp option len, including the magic cookie = 312Tue Apr 11 14:30:53 2006: dhcp option: received DHCP ACK msgTue Apr 11 14:30:53 2006: dhcp option: server id = 192.168.60.2Tue Apr 11 14:30:53 2006: dhcp option: lease time (seconds) = 86400 Tue Apr 11 14:30:53 2006: dhcp option: gateway = 192.168.60.1Tue Apr 11 14:30:53 2006: dhcp option: netmask = 255.255.255.0Tue Apr 11 14:30:53 2006: dhcpParseOptions: options end, len 312, actual 64Tue Apr 11 14:30:53 2006: DHCP Reply to AP client: 00:40:96:a1:45:42, frame len 412, switchport 1Tue Apr 11 14:30:53 2006: DHCP Message Type received: DHCP ACK msgTue Apr 11 14:30:53 2006: op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0Tue Apr 11 14:30:53 2006: xid: 3371152053, secs: 0, flags: 0Tue Apr 11 14:30:53 2006: chaddr: 00:40:96:a1:45:42Tue Apr 11 14:30:53 2006: ciaddr: 0.0.0.0, yiaddr: 192.168.1.41Tue Apr 11 14:30:53 2006: siaddr: 0.0.0.0, giaddr: 0.0.0.0Tue Apr 11 14:30:53 2006: server id: 1.1.1.1 rcvd server id:192.168.60.2You can use these additional debug commands in order to troubleshoot your configuration:debug lwapp errors enable—Shows output of the debug of LWAPP errors debug pm pki enable—Shows the debug ofcertificate messages that are passed between the AP and the WLCController Does Not Defend AP-Manager IP AddressThis issues is a result of bug CSCsg75863. If the user accidently injects a device on the subnet that uses the AP-manager IP address of the controller, the Address Resolution Protocol (ARP) cache on the default gateway router is refreshed with the wrong MAC address. When this occurs, the APs can no longer reach the controller and drop into their discovery phase to look for a controller. The APs send discovery requests, and the controller responds with discovery replies, but the JOIN requests never reach the AP-manager interface of the controller because of the bad ARP entry on the gateway router. After the default 4 hour ARP refresh interval, the APs join the controller if the device is removed.A workaround for this issue is to configure the static ARP entries on the gateway router of the controller for these IP addresses:Management IP address—Customers gain access to the graphical user interface (GUI) from another subnet, and the controller receives the AP discovery requests.AP-Manager IP address—APs join the controller from another subnet.Every Dynamic interface IP address—Packets from other subnets reach the dynamic interface of the controller.DHCP packets transmit from the interface of the wireless client. Telnet or SSH to the gateway address of the controller, and use the arp command in order to add the ARP entries. Use the ping command on the default router of the controller to the different addresses in order to refresh the ARP cache on the router. In order to discover the MAC addresses, use this command: show arp | include .Troubleshoot a Lightweight Access Point Not Joining a Wireless LAN ControllerRefre to Troubleshoot a Lightweight Access Point Not Joining a Wireless LAN Controller for information on some of the issues why a Lightweight Access Point (LAP) fails to join a WLC and how to troubleshoot the issues.Cisco Support Community - Featured ConversationsCisco Support Community is a forum for you to ask and answer questions, share suggestions, and collaborate with your peers. Below are just some of the most recent and relevant conversations happening right now.。
思科无线控制系统(WCS)

产品手册思科无线控制系统 (WCS)图 1. 思科无线控制系统 (WCS)产品概述Cisco®无线控制系统 (WCS) 是业内最全面的管理平台,用于对802.11n和 802.11a/b/g 企业级无线网络的生命周期进行管理。
这一强大的管理平台可提供经济高效的管理解决方案,使IT 管理员可以成功规划、部署、监控室内和室外无线网络的情况,并进行排除故障和报告(图 1)。
作为思科统一无线网络的管理平台,Cisco WCS 是支持高性能的应用程序和关键任务的解决方案,简化业务运营并提高生产效率。
该系统还支持Cisco CleanAir 技术,这项技术是思科统一无线网络的系统级功能,它使用硅片级智能创建自行恢复和自行优化的无线网络。
Cisco CleanAir 技术在为802.11n 网络提供性能保护的同时,通过自动减缓射频(RF) 干扰的影响,提高无线网络的可靠性,来支持关键任务应用程序。
Cisco WCS 是一个全面的平台,伸缩自如,可满足跨本地、远程、国内和国际位置的大中小型无线局域网的各种需求。
此项获奖的解决方案可使IT 经理在需要时立即使用所需的工具,只要从一个集中位置便可实施和维护安全的无线局域网,不仅效率更高,而且最大程度地减少了 IT 人员配备。
Cisco WCS 直观的用户界面和使用简易的内置工具,可提高 IT 效率、降低 IT 培训成本并最大程度地降低对 IT 人员配备需求,从而显著降低运营成本,即使网络不断扩展也是如此。
与重叠管理工具不同的是,Cisco WCS 通过将全方位管理需求(包括射频、控制器和服务)结合到单个统一平台来降低运营成本。
灵活易用的平台Cisco WCS 是新老IT 管理员理想的管理平台。
对需要自动化管理体验的用户来说,Cisco WCS 简单直观的用户界面可降低复杂性,而全面的生命周期管理功能可满足最高级 IT 管理员的需求。
Cisco WCS 内在的灵活性使每位用户都能够定制管理界面,仅显示达成运营目标和业务目标所需的最相关信息。
思科 ONE软件产品手册说明书

产品手册面向无线接入的思科 ONE思科 ONE™软件帮助客户购买合适的软件功能以满足他们的业务需求。
这一软件套装形式可以帮助降低复杂度、简化购买流程,并让客户安心地知晓今天在软件方面的投资在未来仍可继续发挥作用。
这些产品以优惠套装的价格为客户提供更多的功能,从而带来更大的价值。
思科 ONE 软件具备四大主要优势:•通过思科®软件支持服务 (SWSS) 获得思科持续的创新技术和新技术•可通过软件服务进行软件许可证移植,从而实现对软件购买投资的保护•价格经济的软件套装能满足常见的用户使用需求•灵活的许可模式可让客户分期投入软件支出,避免开支剧增的情况表 1 列出常见的 IT 挑战以及思科 ONE 软件如何帮助客户应对这些挑战。
表 1.IT 管理挑战和思科 ONE 软件的优势IT 管理挑战思科 ONE 软件的优点IT 预算削减IT 需求在持续加速增长,而预算却在不断缩减。
随着 IT 的成本和停机时间的剧增,企业需要通过易于部署的网络来提高运营效率并平衡不断削减的预算。
让投资产生更大价值思科 ONE 软件针对普通客户使用场景设计,并以价格经济的套装形式提供,从而使完整解决方案的部署变得简单并且费用更低。
强化投资保护具备由软件服务支持的许可证迁移功能,可确保软件许可证能够不受硬件升级和更换影响,始终保持最新状态,而且无需支付额外费用。
无法适应变化的基础设施缺乏一套自动化方案的 IT 组织很难满足不断变化的业务要求和对更多资源的需求。
采购和配置新的网络服务往往需要数周的时间才能完成。
提高业务灵活性思科 ONE 软件能够提供关键业务解决方案,并提供相应工具以部署、维护和管理您的软件。
缺乏购买选择企业需要更多方式以购买软件,来提升灵活性、降低风险和缩减成本。
灵活的软件许可模式采用订阅型和其他灵活的购买模式来分期投入软件开销。
实施障碍部署软件和实施新的用例,常常会对现有业务运行造成严重中断。
减小风险,缩短停机时间思科的技术和专业服务可提供减少风险和缩短停机时间所需的专业知识、智能工具和久经考验的流程。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Cisco虚拟无线控制器导入到虚拟机
打开虚拟机按任意键
配置密码qaz@123
配置管理ip,无线名称
配置时间
配置完成后重启,ping网关测试
在进行web访问,进行登录
MONITOR
Provides a view of this controller, its APs and wireless clients
监视器提供这个控制器、它的AP和无线客户机的视图。
WLANs
Provides WLAN configurations such as SSIDs and security policies for all user group
无线局域网WLAN的配置等提供的所有用户组的SSID和安全政策
CONTROLLER
Provides controller wide configurations such as Layer 2/3 mode, Multicast and mobility settings 控制器提供控制器范围配置,如第2层/3层模式、组播和移动性设置
WIRELESS
Provides AP configurations, clients management and various RF settings 提供无线AP的配置,客户管理和各种射频设置
SECURITY
Provides integration into security structure such RADIUS connectivity
安全性提供了与安全结构的集成,例如RADIUS连接。
MANAGEMENT
Provides integration into the network such as IP addressing and SNMP 管理提供与网络的集成,如ip寻址和snmp。
COMMANDS
Provides administrative options such as upgrades and backups
命令提供了诸如升级和备份等管理选项
Refresh
Switch web interface will refresh every five minutes but when looking at statistics, it is recommended to observe the latest information which can be provided by clicking Refresh
交换机Web界面将每隔五分钟刷新一次,但在查看统计信息时,建议通过单击“刷新”来观察可以提供的最新信息
Cisco Airespace Controller can be managed via WLAN clients but this capability is disabled by default
思科airespace控制器可以通过WLAN客户端,但这个功能默认是禁用的
Local Management Users accounts are used by both CLI and switch web interface
CLI和交换机Web界面都使用本地管理用户帐户
After Switch Web configuration wizard saves the configuration and reboots the controller, HTTPS access will be enabled and it uses PKI to secure the transaction while HTTP access will be disabled by default
交换机Web配置向导保存配置并重新启动控制器后,将启用HTTPS访问,并且它使用PKI 来安全事务,而HTTP访问将由D禁用default未履行任务或责任
Cisco Airespace Controller supports both Telnet & SSH but SSH is enabled by default to secure the transactions
CiscoAISREACACE控制器支持Telnet和SSH,但默认情况下启用SSH来保护事务
Serial port timeout and data rate can be managed from switch web interface
可以从交换机Web界面管理串行端口超时和数据速率
Cisco Airespace Controller can also be managed via CLI and monitored from switch web interface 思科airespace控制器也可以通过CLI和Web界面监控开关
User Idle Timeout controls the amount of idle time an administrator has prior to being logged off by the controller from the CLI
用户空闲超时控制管理员在控制器从CLI注销之前的空闲时间量。
