期末考试复习计算机网络英文版
计算机网络英文复习题

、英译汉(10分)1.TCP(Transmission Control Protocol) 传输控制协议2.IP(Internet Protocol) 互联网协议3.RFC(Requests for comments) 请求评议4.SMTP(Simple Mail Transfer Protocol) 简单邮件传输协议5.Congestion-control 拥塞控制6.Flow control 流控制7.UDP (User Datagram Protocol) 用户数据报协议8.FTP(File Transfer Protocol) 文件传输协议9.HTTP( Hyper-Text Transfer Protocol ) 超文本传输协议10.TDM 时分复用11.FDM 频分复用12.ISP(Internet Service Provider) 互联网服务提供商13.DSL(Digital Subscriber Line) 数字用户线路14.DNS(Domain Name System) 域名系统15.ARQ(Automatic Repeat Request) 自动重发请求16.ICMP(Internet Control Message Protocol) 网间控制报文协议17.AS(Autonomous Systems) 自制系统18.RIP(Routing Information Protocol)\ 路由信息协议19.OSPF(Open Shortest Path First) 开放最短路径优先20.BGP (Border Gateway Protocol) 边界网关协议21.HFC 光纤同轴电缆混合网22.CRC(Cyclic Redundancy Check) 循环冗余检验23.CSMA/CD 带冲突检测的载波侦听多路存取24.ARP 地址解析协议25.RARP 反向地址解析协议26.DHCP 动态主机配置协议27.RTT 循环时间28.IETF(P5) 互联网工程任务组29.URL(P88) 统一资源定位30.API 应用程序编程接口31.MIME 多用途互联网邮件扩展32.MTU(P328) 最大传输单元二、单项选择题(每小题l分,共30分)1. DSL divides the communication link between the home and the ISP into three nonoverlapping frequency bands, a upstream channel is in _A_________.A)50 kHz to 1MHz band B) 1MHz to 2MHz bandC)4 kHz to 50kHz band D) 0 to 4kHz band2. As a data packet moves from the upper to the lower layers, headers are A .A) Added; B) subtracted; C) rearranged; D) modified3. What is the main function of the network layer? DA) node-to-node delivery; B) process-to-process message deliveryC) synchronization; D) updating and maintenance of routing tables4. Which of the following is the default mask for the address 168.0.46.201? BA) 255.0.0.0; B) 255.255.0.0; C) 255.255.255.0; D) 255.255.255.2555. A router reads the address on a packet to determine the next hop. AA) IP ; B) MAC; C) source; D)ARP6 . Which device can’t isolates the departmental collis ion domains. AA) Hub; B) switch; C) router; D) A and B7. Input port of a router don’t perform ____D____ functions.A) the physical layer functions B) the data link layer functionsC) lookup and forwarding function D) network management8. HTTP has a mechanism that allows a cache to verify that its objects are up to date. The mechanism is DA) persistent connections B) cookies C) Web Caching D) conditional GET9. A protocol layer can be implemented in ___D_____.A) software B) hardware C) a combination of the software and hardware D) All of the above10. A protocol has three important factors, they are_A______.A)syntax, semantics, order B) syntax, semantics, layerC)syntax, semantics, packet D) syntax , layer, packet11. There are two broad classes of packet-switched networks: datagram networks and virtual-circuit networks. The virtual-circuit networks forward packets in their switches use ___D___.A) MAC addresses B) IP addressesC) e-mail addresses D) virtual-circuit numbers12. TCP service model doesn’t provide ___D_______service.A) reliable transport service B) flow control serviceC) congestion-control service D) guarantee a minimum transmission rate service.13. Usually elastic applications don’t include____B______.A) Electronic mail B) Internet telephonyC) file transfer D) Web transfer14. A user who uses a user agent on his local PC receives his mail sited in a mail server by using _B___ protocol.A)SMTP B) POP3C)SNMP D) FTP15. Considering sliding-window protocol, if the size of the transmitted window is N and the size of the receiving window is 1,the protocol is BA) stop-and-wait protocol B) Go-Back-N protocolC) selective Repeat protocol D) alternating-bit protocol16. which IP address is effective___B______.A) 202,131,45,61 B) 126.0.0.1C) 192.268.0.2 D) 290.25.135.1217. if IP address is 202.130.191.33, subnet mask is 255.255.255.0,then subnet prefix is__D_____A) 202.130.0.0 B) 202.0.0.0C) 202.130.191.33 D)202.130.191.018.The command Ping s implemented with __B______messagesA) DNS B) ICMPC) IGMP D) RIP19. Which layer-function is mostly implemented in an adapter? __A________A) physical layer and link layer B) network layer and transport layerC)physical layer and network layer D) transport layer and application layer20. If a user brings his computer from Chengdu to Peking, and accesses Internet again. Now, __B_____ of his computer needs to be changed.A) MAC address B) IP addressC) e-mail address D) user address1. .traceroute is implemented with __B____messages.A) DNS B) ICMPC) ARP D) RIP2. A router reads the A address on a packet to determine the next hop.A. IP ;B. MAC;C. source;D.ARP3. There are two broad classes of packet-switched networks: datagram networks and virtual-circuitnetworks. The virtual-circuit networks forward packets in their switches use ___D___.A) MAC addresses B) IP addressesC) e-mail addresses D) virtual-circuit numbers4. About subnet, which underlying description isn’t right______A) device interfaces with same subnet part of IP addressB) can’t physically reach each other without intervening a router.C) all of the devices on a given subnet having the same subnet address.D) A portion of an interface’s IP address must be d etermined by the subnet to which it is connected.5. if IP address is 102.100.100.32, subnet mask is 255.255.240.0,then subnet prefix is___A___A) 102.100.96.0 B) 102.100.0.0C) 102.100.48.0 D) 102.100.112.06 If a user brings his computer from chengdu to beijing, and accesses Internet again. Now, ___B__ ofhis computer needs to be changed.A) MAC address B) IP addressC) e-mail address D) user address7.In put port of a router don’t perform ____D___ functions.A) the physical layer functions B) the data link layer functionsC) lookup and forwarding function D) network management8.switching fabric is at the heart of a router, switching can be accomplished in a number of ways,donit include_ D _A)Switching via memory B)Switching via crossbarC)Switching via a bus D) Switching via buffer9.if a host wants to emit a datagram to all hosts on th e same subnet, then the datagram’s destination IPaddress is ___B__A)255.255.255.0 B) 255.255.255.255C)255.255.255.254 D) 127.0.0.110.The advantage of Circuit switching does not include________.A) small transmission delay B)small Processing costC) high link utilization D)no limited to format of message1.an ARP query sent to __A__A) local network B) all over the Internet.2. .packet-switching technologies that use virtual circuits include__B___:A) X.25, ATM, IP B) X.25, A TM, frame relay.C) IPX, IP, ATM D) IPX, IP, TCP3. In Internet, _ D_ protocol is used to report error and provide the information forun-normal cases.A) IP B) TCP C)UDP D) ICMP1.A is a Circuit-switched network.A. TDMB. Datagram networkC. InternetD. virtual circuit network2.The store-and-forward delay is DA. processing delayB. queuing delayC. propagation delayD. transmission delay3.Which is not the function of connection-oriented service? DA. flow controlB. congestion controlC. error correctionD. reliable datatransfer4.The IP protocol lies in CA. application layerB. transport layerC. network layerD. link layer5.Which of the following is the PDU for application layer __B___A.datagram;B. message;C. frame;D. segment6.bandwidth is described in _B__A) Bytes per second B) Bits per secondC) megabits per millisecond D) centimeters7.A user who uses a user agent on his local PC receives his mail sited in a mail server by using __A__ protocol.A)SMTP B) POP3C)SNMP D) FTP8.As a data packet moves from the lower to the upper layers, headers are B .A)Added; B. subtracted; C. rearranged; D. modified三、填空题(每空1分,共22分 (注意:所有填空题不能写中文,否则中文答案对的情况下扣0.5分)1. link-layer address is variously called a LAN address, a MAC address, or a physical address.2 In the layered architecture of computer networking, n layer is the user of n-1 layer and the service provider of n+1 layer.A) n B) n+3 C) n+1 D) n-1四、判断题(每小题1分,共10分)1. √The services of TCP’s reliable data transfer founded on the services of the unreliable datatransfer.2. √Any protocol that performs handshaking between the communication entities beforetransferring data is a connection-oriented service.3. × HOL blocking occur in output ports of router.4. √Socket is globally unique.5. √SMTP require multimedia data to be ASCII encoded before transfer.6. ×The transmission delay is a function of the distance between the two routers.7. ×IP address is associated with the host or router. SO one device only have one IP address.8. √ In packet-switched networks, a session’s messages use the resources on demand,and Internet makes its best effort to deliver packets in a timely manner.9. × UDP is a kind of unreliable transmission layer protocol, so there is not any checksum field in UDP datagram header.10. √ Forwarding table is configured by both Intra and Inter-AS routing algorithmIP is a kind of reliable transmission protocol . F8.Forwarding table is configured by both Intra and Inter-AS routing algorithm. T 9.Distance vector routing protocol use lsa to advertise the network which router knows. F 10.RIP and OSPF are Intra-AS routing protocols T 11. Packet switching is suitable for real-time services, and offers better sharing of bandwidththan circuit switching F五、计算题 (28 points)1.Consider the follow ing network. With the indicated link costs, use Dijkstra’s shortest -path algorithm to compute the shortest path from X to all network nodes.2 Given: an organization has been assigned the network number 198.1.1.0/24 and it needs to define six subnets. The largest subnet is required to support 25 hosts. Please:● Defining the subnet mask; (2分) 27bits or 255.255.255.224● Defining each of the subnet numbers; which are starting from 0# (4分)198.1.1.0/27 198.1.1.32/27 198.1.1.64/27 198.1.1.96/27 198.1.1.128/27198.1.1.160/27 198.1.1.192/27 198.1.1.224/27● Defining the subnet 2#’s broadcast address.(2分) 198.1.1.95/27● Defining host addresses scope for subnet 2#. (2分) 198.1.1.65/27--198.1.1.94/273. Consider sending a 3,000-byte datagram into a link that has an MTU of 1500bytes.Suppose the original datagram is stamped with the identification number 422 .Assuming a 20-byte IP header,How many fragments are generated? What are their characteristics?(10分)3 w。
计算机英语期末考试试题及答案

计算机英语期末考试试题及答案一、选择题1. 在计算机网络中,IP地址用于标识网络上的的哪个设备?A. 路由器B. 交换机C. 服务器D. 主机答案:D2. 在计算机安全中,以下哪项属于恶意软件?A. 防火墙B. 杀毒软件C. 木马病毒D. 数据备份答案:C3. 在计算机术语中,RAM代表什么?A. 随机读取存储器B. 只读存储器C. 可擦除可编程读取存储器D. 磁盘存储器答案:A4. 在计算机网络中,HTTP协议是用于实现什么功能的?A. 网络连接B. 文件传输C. 数据加密D. 网络浏览答案:D5. 下列哪个不属于常见的文件压缩格式?A. .zipB. .rarC. .isoD. .txt答案:D二、填空题1. 在计算机程序中,循环结构可以用来多次执行特定的代码段,常见的循环结构包括_______和_______。
答案:for、while2. 在计算机图像处理中,________是指将一幅图像分割成若干个连续的小区域,并对每个小区域进行处理。
答案:图像分割三、判断题1. 计算机网络是指将多台计算机通过通信设备连接起来,实现信息共享和资源共享。
答案:正确2. 在计算机程序中,注释是用来向其他程序员解释代码功能的。
答案:正确四、简答题请简述计算机网络的优点和缺点。
优点:1. 资源共享:计算机网络可以实现多台计算机之间的文件共享、打印共享等,提高资源利用率;2. 信息交流:计算机网络可以快速传输信息,实现实时通信,方便人们之间的交流;3. 远程访问:计算机网络可以远程访问其他计算机,方便远程办公和学习。
缺点:1. 安全性问题:计算机网络容易受到黑客攻击和恶意软件感染,存在一定的安全隐患;2. 依赖性:对于依赖网络的应用和服务而言,一旦网络故障,将会导致服务中断,影响工作和生活;3. 隐私问题:在计算机网络中,个人信息和隐私面临泄露的风险,需要加强数据保护和隐私保护措施。
答案仅供参考,具体答案可能根据题目要求有所变化。
计算机专业英语期末考复习资料

英语翻译成汉语:1、In order to solve a computational problem, its solution must be specified in terms of a sequence of computational steps, each of which may be performed by a human or a digital computer.If you want to solve the computational problem with a computer, you should learn how to program.The task of developing programs for the soultion of computational problems is referred to as programming.Computer programming is the process of planning and creating a sequence of steps for a computer to follow.In general,this process will help us resolve a problem,which is either too tedious (冗长的) or difficult to work out otherwise.So programming is breaking a task down into small steps.译:为解决计算问题,其解决方案必须被指定在一个计算步骤的序列,每一个可能由一个人或一个数字计算机。
如果你想解决计算问题的计算机,你应该学会如何计划。
制定发展任务的计划称为编程。
计算机编程的过程中规划和创建一个序列的计算机执行步骤。
一般来说,这个过程将帮助我们解决一个问题,是太冗长的或难以解决的方式。
计算机网络英文版——提供给学生部分习题答案

计算机⽹络英⽂版——提供给学⽣部分习题答案Solution of Selected Exercises from the End of Chapter ExercisesChapter 1 - Introduction And Overview1.4 To what aspects of networking does data communications refer?Answer:Data communications refers to the study of low-level mechanisms and technologies used to send information acrossa physical communication medium, such as a wire, radio wave, or light beam.1.5 What is packet-switching, and why is packet switching relevant to the Internet?Answer: Packet switching divides data into small blocks, called packets, and includes an identification of the intended recipient in each packet. Packet switching changed networking in a fundamental way, and provided the basis for the modern Internet. Packet switching allows multiple senders to transmit data over a shared network.1.8 What is a communication protocol? Conceptually, what two aspects of communication does a protocol specify? Answer: A communication protocol refer to a specification for network communication.Major aspects of a protocol are syntax (format) and semantics (meaning) of the protocol.1.9 What is a protocol suite, and what is the advantage of a suite?Answer:protocols are designed in complete, cooperative sets called suites or families, instead of creating each protocol in isolation. Each protocol in a suite handles one aspect of communication; together, the protocols in a suite cover all aspects of communication. The entire suite is designed to allow the protocols to work together efficiently. 1.11 List the layers in the TCP/IP model, and give a brief explanation of each.(See Textbook)1.14 Give a brief explain of the layers in the ISO Open System Interconnection model.(See Textbook)Chapter 3 - Internet Applications And Network Programming3.1 What are the two basic communication paradigms used in the Internet?Answer: There are various approaches, but according to textbook, we can specify them as Stream Paradigm and Message Paradigm.3.2 Give six characteristics of Internet stream communication.(See Textbook)3.3 Give six characteristics of Internet message communication.(See Textbook)3.4 If a sender uses the stream paradigm and always sends 1024 bytes at a time, what size blocks can the Internet deliverto a receiver?Answer: stream paradigm does not provide any guarantees for block sizes, so all depends on individual transfer.3.6 What are the three surprising aspects of the Internet’s message delivery semantics?Answer:The Internet’s message delivery has the followi ng undesirable characteristics:* Messages can be lost* Messages can be duplicated* Messages can be delivered out-of-order3.8 When two applications communicate over the Internet, which one is the server?Answer: T he application that waits for some other applications to contact is called server, and the application that contact other one is called client.3.14 What two identifiers are used to specify a particular server?Answer: A particular server is identified by the following identifiers:* An identifier for the computer on which a server runs (IP Address)* An identifier for a particular service on the computer (Port Number)Chapter 4 - Traditional Internet Applications4.1 What details does an application protocol specify?(See Textbook)4.3 What are the two key aspects of application protocols, and what does each include?(See Textbook)4.6 What are the four parts of a URL, and what punctuation is used to separate the parts?Answer: The URL into four components: a protocol, a computer name, a document name, and parameters. The computer name and protocol port are used to form a connection to the server on which the page resides. And the document name and parameters are used to request a specific page.4.7 What are the four HTTP request types, and when is each used?(See Textbook)4.12 When a user requests an FTP directory listing, how many TCP connections are formed? Explain.Answer: FTP uses two types of connections to perform its functionality, namely* A control connection is reserved for commands. Each time the server needs to download or upload a file, the server opens a new connection.* A data connection is used to transfer files.4.16 List the three types of protocols used with email, and describe each.(See Textbook)4.17 What are the characteristics of SMTP?(See Textbook)4.20 What are the two main email access protocols?Answer: Two major email access protocols are:* Post Office Protocol (POP)* Internet Mail Access Protocol (IMAP)Chapter 6- Information Sources and Signals6.4 State and describe the four fundamental characteristics of a sine wave.(See Textbook)6.9 What is the analog bandwidth of a signal?Answer: Analog bandwidth of signal can be defined as to be the difference between the highest and lowest frequencies of the constituent parts (i.e., the highest and lowest frequencies obtained by Fourier analysis)6.11 Suppose an engineer increases the number of possible signal levels from two to four. How many more bits can be sent in the same amount of time? Explain.Answer: The number of levels that can be represented by n bits is given by 2n . So if number of levels changes from 2→4, it means number of bits goes from 1→2612. What is the definition of baud?Answer: Baud is defined as the number of times that a signal can change per second.6.14 What is the bandwidth of a digital signal? Explain.Answer: According to the definition of analog bandwidth, a digital signal has infinite bandwidth because Fourier analysis of a digital signal produces an infinite set of sine waves with frequencies that grow to infinity.6.18 What is the chief advantage of a Differential Manchester Encoding?Answer: The most important property of differential encoding is that the encoding works correctly even if the two wires carrying the signal are accidentally reversed.6.20 If the maximum frequency audible to a human ear is 20,000 Hz, at what rate must the analog signal from a microphone be sampled when converting it to digital?Answer: The sampling rate = 2 × f max, so the signal should be sampled at 2x20,000 = 40,000 HzChapter 7 - Transmission Media7.2 What are the three energy types used when classifying physical media according to energy used?Answer: Three types of energy used when classifying physical media are electrical, electromechanical (radio), and light7.4 What three types of wiring are used to reduce interference form noise?(See Textbook)7.10 List the three forms of optical fiber, and give the general properties of each.(See Textbook)7.21 What is the relationship between bandwidth, signal levels, and data rate?Answer: If a transmission system uses K possible signal levels and has an anal og bandwidth B, Nyquist’s Theorem states that the maximum data rate in bits per second, D, is: D = 2 B log2K7.22 If two signal levels are used, what is the data rate that can be sent over a coaxial cable that has an analog bandwidthof 6.2 MHz?Answer: Using the D= 2 B log2 K relationship, D = 2*6.2*log22 = 2*6.2*1 = 12.4 Mbps7.24 If a system has an input power level of 9000, and an output power level of 3000, what is the difference when expressed in dB?Answer: Decibel is expressed as 10log10(P out/P in) → 10log10(3,000/9,000) = to be determined by reader7.23 If a system has an average power level of 100, an average noise level of 33.33, and a bandwidth of 100 MHz, whatis the effective limit on channel capacity?Answer: Shannon theorem specify the maximum data rate that could be achieved over a transmission system that experiences noise: C = Blog2 (1 + S/N) = 100,000,000 * log2 (1 + 100/33.33) = 100,000,000 * log24 = 200,000,000 = 200 Mbps7.25 If a telephone system can be created with a signal-to-noise ratio of 40 dB and an analog bandwidth of 3000 Hz, how many bits per second could be transmitted?Answer: First we should convert 40 dB to a real number, namely if 40 = 10 log10S/N→S/N = 10,000 , Using the Shannon’s capacity expression C = B log2(1 + S/N) → C = 3,000 log2 (1+ 10,000) = to be determined by readerCh 8 - Reliability And Channel Coding8.1 List and explain the three main sources of transmission errors.(See Textbook)8.3 In a burst error, how is burst length measured?Answer: For a burst error, the burst size, or length, is defined as the number of bits from the start of the corruption to the end of the corruption.8.4 What is a codeword?Answer: We can define the set of all possible messages to be a set of datawords, and define the set of all possible encoded versions to be a set of codewords. So each possible code sequence is considered to be a codeword.8.8 Compute the Hamming distance for the following pairs: (0000, 0001), (0101, 0001), (1111, 1001), and ( 0001, 1110). (See Textbook)8.11 Generate a RAC parity matrix for a (20, 12) coding of the dataword 100011011111.(See Textbook)8.15 Express the two values in the previous exercise as polynomials.Answer:X10+ X7 + X5 + X3 + XX4+ X2+ 1Ch 9 - Transmission Modes9.1 Describe the difference between serial and parallel transmission.Answer: Transmission modes can be divided into two fundamental categories:* Serial: one bit is sent at a time* Parallel: multiple bits are sent at the same time9.2 What are the advantages of parallel transmission? What is the chief disadvantage?Answer: A parallel mode of transmission has two chief advantages:* High speed: Because it can send N bits at the same time, a parallel interface can operate N times faster than an equivalent serial interface.* Match to underlying hardware: Internally, computer and communication hardware uses parallel circuitry.Thus, a parallel interface matches the internal hardware well.The main disadvantage of parallel transmission is number of cables required, for long distance communication, this is an important consideration.9.4 What is the chief characteristic of asynchronous transmission?Answer:Asynchronous transmission can occur at any time, with an arbitrary delay between the transmission of two data items, it allows the physical medium to be idle for an arbitrary time between two transmissions.Chapter 11 - Multiplexing And Demultiplexing11.2 What are the four basic types of multiplexing?(See Textbook)11.4 What is a guard band?Answer: For proper communication without interference, we should choose a set of carrier frequencies with a gap between them known as a guard band. The guard band reduces or eliminates the possible interference between neighboring carrier signals.11.8 Explain how a range of frequencies can be used to increase data rate.Answer:To increase the overall data rate, a sender divides the frequency range of the channel into K carriers, and sends 1 /K of the data over each carrier.11.12 Suppose N users compete using a statistical TDM system, and suppose the underlying physical transport can sendK bits per second. What is the minimum and maximum data rate that an individual user can experience?Answer: If we neglect the overhead generated by statistical TDM, a system will have two possibilities: * Minimum: If all channels have equal data then the rate will be K/N bps* Maximum: If only one channel active and the others are passive, then rate will be K bpsChapter 13 - Local Area Networks: Packets, Frames, And Topologies13.1 What is circuit switching, and what are its chief characteristics?Answer: The term circuit switching refers to a communication mechanism that establishes a path between a sender and receiver with guaranteed isolation from paths used by other pairs of senders and receivers. The circuit switching has the following main characteristics:* Point-to-point communication* Separate steps for circuit creation, use, and termination* Performance equivalent to an isolated physical path13.3 In a packet switching system, how does a sender transfer a large file?Answer: The packet switching system requires a sender to divide each message into blocks of data that are known as packets . The size of a packet varies; each packet switching technology defines a maximum packet size. So, a large file will be divided into smaller pieces and sent.13.5 What are the characteristics of LANs, MANs, and W ANs?Answer: There are lots of details that can be said and discussed for categorization of network types based on geography, few points are highlighted below:* Local Area Network (LAN): Least expensive; spans a single room or a single building* Metropolitan Area Network (MAN) Medium expense; spans a major city or a metroplex* Wide Area Network (WAN) Most expensive; spans sites in multiple cities13.6 Name the two sublayers of Layer 2 protocols defined by IEEE, and give the purpose of each.Answer: The Layer 2 protocols defined by IEEE defines two sub-layers as mentioned below:* Logical Link Control (LLC) Addressing and demultiplexing* Media Access Control (MAC) Access to shared media13.8 What are the four basic LAN topologies?Answer: The four basic LAN topologies are star, ring, mesh and bus.13.10 In a mesh network, how many connections are required among 20 computers?Answer: The expression to calculate number of connections in a mesh network is given by n (n-1)/2. So for 20 computers then number of connections required will be = 20 (20 – 1)/2 =19013.15 Give a definition of the term frame .Answer: In a packet-switched network, each frame corresponds to a packet processed at data link layer.Chapter 14 - The IEEE MAC Sub-Layer14.1 Explain the three basic approaches used to arbitrate access to a shared medium.(See Textbook)14.3 List the three main types of channelization and the characteristics of each.(See Textbook)14.6 What is a token, and how are tokens used to control network access?Answer: A special control message is called a token. In a token passing system, when no station has any packets to send, the token circulates among all stations continuously. When a station captures the token, it sends its data, and when transmission completed, it releases the token.14.8 Expand the acronym CSMA/CD, and explain each part.Answer: The acronym CSMA/CD stands for Carrier Sense Multi-Access with Collision Detection, which means the following: * Carrier Sense: Instead of allowing a station to transmit whenever a packet becomes ready, Ethernet requires each station to monitor the cable to detect whether another transmission is already in progress.* Multiple Access: The system allows multiple users/hosts to make use of a common/shared media* Collision Detection. A collision can occur if two stations wait for a transmission to stop, find the cable idle, and both start transmitting.14.10 Why does CSMA/CD use a random delay? (Hint: think of many identical computers on a network.)Answer: Randomization is used to avoid having multiple stations transmit simultaneously as soon as the cable is idle.That is, the standard specifies a maximum delay, d, and requires each station to choose a random delay less than d after a collision occurs. In most cases, when two stations each choose a random value, the station that chooses the smallest delay willChapter 15 - Wired LAN Technology (Ethernet And 802.3)15.1 How large is the maximum Ethernet frame, including the CRC?Answer: According to Fig. 15.1 a conventional Ethernet frame has the following fields:* Header: 14 bytes (fixed)* Payload: 46-1500 bytes (there is a minimum frame size because of collision detection)* CRC: 4 bytes (fixed)Accordingly an Ethernet frame will be maximum 1518 bytes and minimum 64 bytes15.3 In an 802.3 Ethernet frame, what is the maximum payload size?Answer: The 802.3 Ethernet makes use of 8-bytes of the original/conventional Ethernet for Logical Link Control / Sub-Network Attachment Point (LLC / SNAP) header instead of extending/increasing the header. This is for sake of backward compatibility. So the maximum pay load is reduced from 1500 bytes to 1492 bytes.15.6 How did a computer attach to a Thicknet Ethernet?Answer: Hardware used with Thicknet was divided into two major parts:* Transceiver: A network interface card (NIC) handled the digital aspects of communication, and a separate electronic device called a transceiver connected to the Ethernet cable and handled carrier detection, conversion of bits into appropriate voltages for transmission, and conversion of incoming signals to bits.* AUI: A physical cable known as an Attachment Unit Interface (AUI) connected a transceiver to a NIC in a computer. A transceiver was usually remote from a computer.15.7 How were computers attached to a Thinnet Ethernet?Answer: Thinnet Ethernet (formally named 10Base2) uses a thinner coaxial cable that was more flexible than Thicknet. The wiring scheme differed dramatically from Thicknet. Instead of using AUI connections between a computer and a transceiver, Thinnet integrates a transceiver directly on the NIC, and runs a coaxial cable from one computer to another.15.8 What is an Ethernet hub, and what wiring is used with a hub?Answer: An electronic device that serves as the central interconnection is known as a hub. Hubs were available in a variety of sizes, with the cost proportional to size. The hubs are becoming old-fashioned, and being replaced with switches.15.3 What category of twisted pair wiring is needed for a 10 Mbps network? 100 Mbps? 1000 Mbps?Answer: The three major categories of Ethernet and their wiring is listed below:* 10 Mbps: 10BaseT (Ethernet) Category 5* 100 Mbps: 100BaseT (Ethernet Fast) Category 5E* 1 Gbps: 1000BaseT (Gigabit Ethernet) Category 6Chapter 20 - Internetworking: Concepts, Architecture, and Protocols20.2 Will the Internet be replaced by a single networking technology? Why or why not?Answer: Incompatibilities make it impossible to form a large network merely by interconnecting the wires among networks. The beauty of the Internet is interconnection of wide range of technologies from various manufacturers.Diversity of the products and solutions is a richness instead of limitation as long as they all adopt the same set of protocols.20.3 What are the two reasons an organization does not use a single router to connect all its networks?Answer:An organization seldom uses a single router to connect all of its networks. There are two major reasons: * Because the router must forward each packet, the processor in a given router is insufficient to handle the traffic passing among an arbitrary number of networks.* Redundancy improves internet reliability. To avoid a single point of failure, protocol software continuously monitors internet connections and instructs routers to send traffic along alternative paths when a network or router fails.20.6 In the 5-layer reference model used with the TCP/IP Internet protocols, what is the purpose of each of the five layers?(See 1.11)Chapter 21- IP: Internet Addressing21.3 In the original classful address scheme, was it possible to determine the class of an address from the address itself? Explain.Answer:Yes, since in the classful addressing scheme initial bit(s) gives indication about the class being used.21.7 If an ISP assigned you a /28 address block, how many computers could you assign an address?Answer: When an organization is assigned /28 CIDR address, it means 28 bits out of 32 bits are fixed, so 32-28 = 4 bits available for user space. So number of users 24-2 = 4, since the all 0s and all 1s address are having special use and can’t be assigned to a user.21.8 If an ISP offers a / 17 address block for N dollars per month and a / 16 address block for 1.5 N dollars per month,which has the cheapest cost per computer?Answer: Number of addresses in /17 block 232-17 = 215Price per address: N /215 = N / 215Number of addresses in /16 block 232-16 = 216Price per address: 1.5N /216 = 0.75N/215 So /16 address block will be cheaper in comparison with the price given for /17 block.21.10 Suppose you are an ISP with a / 24 address block. Explain whether you accommodate a request from a customer who needs addresses for 255 computers. (Hint: consider the special addresses.)Answer: For a/24 address block, number of available addresses will be 232-24 = 28 = 256. However, a suffix with all 0s address is reserved for network ID and a suffix with all 1s address is reserved for broadcast address, so number of addresses that can be assigned to computers/hosts will be 256 -2 = 254.21.11 Suppose you are an ISP that owns a / 22 address block. Show the CIDR allocation you would use to allocateaddress blocks to four customers who need addresses for 60 computers each.Answer: The /22 address block can be assigned as follows:ddd.ddd.ddd.00/26ddd.ddd.ddd.01/26ddd.ddd.ddd.10/26ddd.ddd.ddd.11/26Chapter 22- Datagram Forwarding22.1 What are the two basic communication paradigms that designers consider when designing an internet?Answer:* Connection-oriented service * Connectionless service22.2 How does the Internet design accommodate heterogeneous networks that each have their own packet format?Answer: To overcome heterogeneity, the Internet Protocol defines a packet format that is independent of the underlying hardware. The result is a universal, virtual packet that can be transferred across the underlying hardware intact. The Internet packet format is not tied directly to any hardware. The underlying hardware does not understand or recognize an Internet packet.22.5 What is the maximum length of an IP datagram?In the current version of the Internet Protocol (IP version 4), a datagram can contain at most 64 K (65535) octets, including the header.22.7 If a datagram contains one 8-bit data value and no header options, what values will be found in header fields H.LEN and TOTAL LENGTH?Answer: H. LEN indicated header in 32-quantities, since no options, then this value will be 5. The TOTAL LENGTH indicated the number of bytes in a datagram including the header. This means 5x4 bytes + 1 (8-bits) = 21 bytesChapter 23 - Support Protocols And Technologies23.1 When a router uses a forwarding table to look up a next-hop address, the result is an IP address. What must happenbefore the datagram can be sent?Answer: Each router along the path uses the destination IP address in the datagram to select a next-hop address, encapsulates the datagram in a hardware frame, and transmits the frame across one network. A crucial step of the forwarding process requires a translation: forwarding uses IP addresses, and a frame transmitted across a physical network must contain the MAC address of the next hop.23.2 What term is used to describe the mapping between a protocol address and a hardware address?Answer: Translation from a computer’s IP address to an equivalent hardware address is known as address resolution, and an IP address is said to be resolved to the correct MAC address. The TCP/IP protocol being used for this is called Address Resolution Protocol (ARP). Address resolution is local to a network.23.5 How many octets does an ARP message occupy when used with IP and Ethernet addresses?Answer: According to Fig 23.3 an ARP message has 7-lines of each being 32-bit (4 bytes or octets), therefore,number of octets in an ARP can be determined as 7x4 = 28 octets23.10 What types of addresses are used in layers below ARP?Answer:ARP forms a conceptual boundary in the protocol stack; layers above ARP use IP addresses, and layers below ARP use MAC addresses.23.17 What is the chief difference between BOOTP and DHCP?Answer:The main difference is that the BOOTP protocol required manual administration. So before a computer could use BOOTP to obtain an address, a network administrator had to configure a BOOTP server to know the computer’s I P address. Chapter 24 - The Future IP (IPv6)24.3 List the major features of IPv6, and give a short description of each.(See Textbook)24.4 How large is the smallest IPv6 datagram header?Answer: IPv6 datagram header consists of a base header + zero or more extension header. Since, smallest header is being asked, we assume zero extension header and consider IPv6 will have only base header. If we look at IPv6 header format in Fig. 24.3, it shows that 10x4 bytes = 40 bytes.Chapter 26 - TCP: Reliable Transport Service26.2 List the features of TCP.(See Textbook)26.6 When using a sliding window of size N, how many packets can be sent without requiring a single ACK to be received?Answer: If the size of the window is N, then it means a sender can transmit up to N packets without waiting for an ACK, as long as other controls are in place.26.9 What is the chief cause of packet delay and loss in the Internet?Answer: The main cause of packet delay and loss in the Internet is congestion.Chapter 28 - Network Performance (QoS and DiffServ)28.1 List and describe the three primary measures of network performance.(See Textbook)28.2 Give five types of delay along with an explanation of each.(See Textbook)Chapter 30 - Network Security30.1 List the major security problems on the Internet, and give a short description of each.(See Textbook)30.2 Name the technique used in security attacks.(See Textbook)30.8 List and describe the eight basic security techniques.(See Textbook)。
计算机网络试卷及答案-英文版
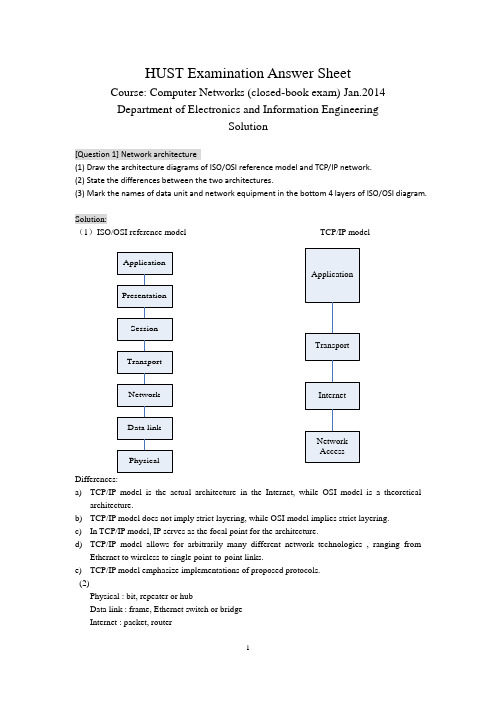
HUST Examination Answer SheetCourse: Computer Networks (closed-book exam) Jan.2014 Department of Electronics and Information EngineeringSolution[Question 1] Network architecture(1) Draw the architecture diagrams of ISO/OSI reference model and TCP/IP network. (2) State the differences between the two architectures.(3) Mark the names of data unit and network equipment in the bottom 4 layers of ISO/OSI diagram.Solution:(1)ISO/OSI reference model TCP/IP modelDifferences:a) TCP/IP model is the actual architecture in the Internet, while OSI model is a theoreticalarchitecture.b) TCP/IP model does not imply strict layering, while OSI model implies strict layering. c) In TCP/IP model, IP serves as the focal point for the architecture.d) TCP/IP model allows for arbitrarily many different network technologies , ranging fromEthernet to wireless to single point-to-point links.e) TCP/IP model emphasize implementations of proposed protocols. (2)Physical : bit, repeater or hubData link : frame, Ethernet switch or bridge Internet : packet, routerTransport : message, gateway[Question 2] Principles of network designSelect ONE of the following principles, tell its main ideas and provide an example. (1) Keep it simple and stupid(2) Complex edge and simple core (3) Smart sender and dumb receiverSolution:(1) KISS: Keep It Simple and StupidIt means that you should make things simple in the designing. One example following it : Ethernet(2) Complex edge and simple coreIt means that the hosts are very complex and have many functions while the nodes are very simple and have few functions.One example following it : The design of router, or the functions of TCP and IP(3) Smart sender and dumb receiverIt means that the function of sender is more complex than that of the receiver, which is help to improve the robustness and performance of communication protocol. One example following it: The flow control of TCP protocol[Question 3] Error detection(1) Tell the main idea of error detection and error correction in communication.(2) Given the CRC polynomial x 4 + x 3 + 1, if the original message is 10110011010, what is the CRC message to send?(3) Suppose the first bit of the message in (2) is inverted due to the noise in transmission. How can the receiver detect it via CRC verification?Solution:(1)1087431()M x x x x x x x =+++++, 43()1C x x x =++. So k=4.a) Multiply M(x) by 2kto get 141211875()T x x x x x x x =+++++,b) Then divide T(x) by C(x) to get the remainder 0000.c) The message that should be transmitted is 101100110100000.(2)The message received is 001100110100000.Divide it by C(x), then the remainder is 1100.So it is not divisible by C(x).So the receiver knows that an error has occurred.(1) What are the essential components to realize reliable transmission?(2) Suppose two computers are communicated via Stop-and-wait protocol. The link bandwidth is 5kbps, and the one-way propagation delay is 20ms. To reach 80% or higher link utilization, what is the minimal frame size for this communication?(3) If it is upgraded to Sliding-Window protocol. To reach the same goal with (2), what is the minimal window size, how many bits are required to describe the frame sequence in window? (Suppose the frame size is 1 or 100Byte)Solution:(1)ACK, and timerActual_throughput = Data / Total_DelayTotal_Delay = RTT + Data / BWLink_Utilization = 100 * Actual_throughput / BWSo: Data/throughput = RTT + Data/BW(BW/throughput - 1) Data = BW*RTTData = BW*RTT/(1/Utilization -1)For the stop-and-wait protocol, for each RTT only one frame is sent,Thus Frame_size = Data = BW*RTT/(1/Utilization - 1) = 5kbps * 40ms / (1/0.8 - 1)= 200 bit / 0.25 = 800 bit = 100 ByteIf the students ignore the data transmission delay, their answer isframe_size = BW*RTT*Utilization = 5000 bit/sec * 40 / 1000 sec * 0.8 = 160 bit = 20 ByteIn this case, at least -2 score.(3)For the sliding-window protocol, in each RTT the data window can be transmitted at most.Thus Window_size = Data = BW*RTT/(1/Utilization - 1) = 5kbps * 40ms / (1/0.8 - 1)= 200 bit / 0.25 = 800 bit = 100 ByteIf the frame size is 100Byte, 1 frames are allowed.To indicate the frames in both sides of sender and receiver, the sequence number should describe 2 frames, thus the [log2(2) ]=1 bitIf the students ignore the data transmission delay, their answer iswindow_size = BW*RTT*Utilization = 5000 bit/sec * 40 / 1000 sec * 0.8 = 160 bit = 20 ByteIf the frame size is 100Byte, 1 frames are allowed.To indicate the frames in both sides of sender and receiver, the sequence number should describe 2 frames, thus the [log2(2) ]=1 bitIn this case, at least -2 score.(1) What is the main idea of CSMA/CD (Carrier Sense Multiple Access/Collision Detection) in traditional Ethernet? Can it be deployed for wireless local network, why?(2) Suppose one traditional Ethernet has 1km cable, the signal propagation speed is 2*105km/s, and the transmission rate is designed to be 100Mbps. What is the minimal frame size to support carrier sensing?Solution:(1) the main idea of CSMA/CD include two parts. One is carrier sensing, which means the node should detect the channel before sending any data. If the node finds the channel is idle, it begins to transmit. Otherwise, the node stop for next round. The second issues is collision detection, which means the node should detect the channel in the duration of its data transmission. If the node finds the channel become busy, or in other word, there is a collision, it should stop transmitting immediately.CSMA/CD cannot be deployed in wireless LAN, because the wireless radio transmitter and receiver can not work in dual mode. The wireless node cannot detect collision when it is transmitting data.(2)the minimal frame should be transmitted throughout the whole traditional Ethernet.Thus t = frame_size / transmit_rate = 2 * cable_length / prop_speed.Frame_size = 100 * 106 bits/sec * 2 * 103 m / (2 * 108)m/sec = 1000 bits = 125 Byte[Question 6] Switched network(1) What are the differences between circuit switching and packet switching?(2) For the following linear topology network, each link has 2ms propagation delay and 4 Mbps bandwidth.A B C DIf we use circuit switching, circuit setup requires a 1KB message to make one round-trip on the path, which incurs a 1ms delay at each switch after the message has been completely received. Then we can send the file as one contiguous bit stream. What is the delay for circuit switching to transmit n-byte from A to D?(3) If we use packet switching in the network of (2), we can break the file into 1KB packets, which has 24byte header and 1000byte payload. The switch takes 1ms process delay after receiving the packet, and then sent it continuously. What is the condition for packet switching to have less delay performance than circuit switching?Solution:(1)(2)T pkt = Packet_Size / Bandwidth = 1 KB / 4Mbps = 1024 *8 / (4 * 106) = 2.048 ms T p = 2 ms, T s = 1 ms,T t = n B / 4MbpsIn circuit switching, Total time duration:D = Singling_Delay + Transmission_Delay = 2 * Packet_Duration + Transmission_Delay = 2 * (T pkt * 2 + T p * 3 + T s * 2 + T pkt ) + (T p * 3 + T t ) = T pkt * 6 + T p * 9 + T s * 4 + T tThus, D = 2.048 * 6 + 2 * 9 + 1 * 4 + n * 8 bits / 4Mbps = 34.288 (ms) + 2n (us)(3)Main ideaThe reliability provided by endhost The reliability provided by thenetwork Information in packet Every packet has its dest-addrin header Every packet has its temp VCIlocally Forwarding action inswitch Every packet was treatedindependentlyThe packets are processed inthe manner of VCPackets received indestinationNot in sequenceIn sequenceT pkt = Packet_Size / Bandwidth = 1 KB / 4Mbps = 1024 *8 / (4 * 106) = 2.048 msT p = 2 ms,T s = 1 ms,T t = 1.024 * n B / 4MbpsIn packet switching, Total time duration:D = Delay_at_Switch * Switch_Num + Delay_at_last_hop= (T p + T pkt +T s)*2 + (T p + T t )= T pkt * 2 + T p * 3 + T s * 2 + T tThus, D = 2.048 * 2 + 2 * 3 + 1 * 2 + 1.024 * n B / 4Mbps= 12.096 (ms) + 2.048 n (us)In order to make34.288 (ms) + 2n (us) > 12.096 (ms) + 2.048 n (us)Thus 22.192(ms) > 0.048 n(us)n < 22.192 * 1000 / 0.048 = 462333 Byte = 451.5 KB[Question 7] Ethernet Switch(1) What are the differences between hub and switch in Ethernet?(2) Suppose one server and nine clients are connected via hub in 10Mbps Ethernet, what is the maximal bandwidth for the client-server connection?(3) If the hub is upgraded to switch, can the client-server connection obtain more bandwidth? if can, how much is it?Solution:(1)hub works in Layer2, it works as the shared media and relays the frames to all the nodes connecting to hub. Switch works in Layer2, it forwards the frames to the specific node according to the destination address embedded in the frame header.(2)the max bandwidth in client-server connection is 10Mbps/(1+9)= 1Mbps(3)the max bandwidth in client-server connection is 10Mbps/9 = 1.1111MbpsAdditional 0.1111 Mbps is obtained for each connection.[Question 8] Router(1) Somebody says that, ``the only difference between switch and router is that they do switch function based on the address in different layers.’’ Is it correct? Why?(2) If we obtain the following information from one router. What kind of routing protocol does itSolution:(1)it is not fully correct. The part talking about the forwarding function is correct, while it is not the only difference. Another but not the last difference is that, router has more functions on control plane, which do routing and find the paths for packets.(2)The routing protocol is RIP.The routing table is:Destination Next hop Interface192.168.1.0/24 * Fa 0/4192.168.2.0/24 * Fa 0/6192.168.10.0/24 192.168.1.1 Fa 0/4192.168.30.0/24 192.168.2.2 Fa 0/6[Question 9] Routing algorithm(1) State the main differences between distance vector routing and link state routing.(2) For the network given in the following figure, provide the steps of forward search in Dijkstra algorithm for node A finding the shortest path to node ESolution:(1) The idea of distance vector routing is to tell the neighbors about the learned topology to all the nodes in the network. The idea of link state routing is to tell all the nodes in network about the neighborhood topology.Step 1 2 3 4 5 6 7 8 9Confirmed (A,0,-) (A,0,-) (A,0,-)(D,2,D)(A,0,-)(D,2,D)(A,0,-)(D,2,D)(B,4,D)(A,0,-)(D,2,D)(B,4,D)(A,0,-)(D,2,D)(B,4,D)(E,6,D)(A,0,-)(D,2,D)(B,4,D)(E,6,D)(A,0,-)(D,2,D)(B,4,D)(E,6,D)(C,7,D)Tentative (B,5,B)(D,2,D)(B,5,B) (B,4,D)(E,7,D)(E,7,D)(E,6,D)(C,8,D)(C,8,D) (C,7,D)A→E A→D→EA→D→B→EA→D→B→E[Question 10] IP address allocationA company has one C class IP address of 200.1.1.*. It has four departments.(1) If each department has less than 25 computers. Provide a kind of IP address allocation. Give the network address, subnet mask, and the available IP address range for each department. (2) If the four departments have 72, 35, 34, 20 computers respectively. Provide the IP address allocation scheme again.Solution:(1)Since each department has less than 25 computers, even considering the additional two more IP address for gateway and broadcast, the 64-computer subnet is enough for them.One IP address allocation scheme is to even divide the 256 IP addresses into 4 subnets, each subnet allows 64 hosts.Another IP address allocation scheme is to even divide the 256 IP addresses into 4 subnets, each subnet allows 32 hosts.(2) Since one of the department has more requirements than 64, then the even distribution scheme[Question 11] TCP protocol(1) Somebody says that, ``because of the reliable transmission service in layer 2, there is no need to provide such service again within TCP protocol in layer 4’’. Is it correct? Why?(2) State the main rules of TCP connection setup according to the following figure. Explain every word and number in the figure.Solution:(1) It is wrong. TCP is based on the un-reliable IP layer, which only provides best effort service. If TCP wants to provide reliable transmission service, it has to realize this by itself.(2)TCP use three hand-shakes to setup the connection.According to the figure, there are two nodes. The sender is with IP address of 192.168.1.163 and the receiver 192.168.1.165 respectively.●At first, the sender send a request ``SYN’’to the receiver to setup the connection. Thismessage is with the sequence number of 424CF1DC;●Secondly, the receiver reply an acknowledgment message ``SYN/ACK’’ to the sender. Thismessage has two sequence numbers. The seq in the ACK is 424CF1DD, which is to confirm the last ``SYN’’ from sender. The seq in the SYN is 30318555, which is a new message from the receiver.●Thirdly, the sender reply an acknowledgment message ``ACK’’ to the receiver. The seq in theACK is 30318556, which is to confirm the last ``SYN’’ from receiver.In the end, both the sender and receiver knows that the other side is ready for this TCP connection.[Question 12] TCP congestion control(1) Both flow control and congestion control in TCP are realized by window based packet control. How can TCP get the window sizes in these two mechanisms?(2) Assume that TCP implements an extension that allows window sizes much larger than 64 KB. Suppose that you are using this extended TCP over a 1Gbps link with a latency of 150ms. TCP packet size is 1KB, and the max receive window is 1 MB. Suppose there is no real congestion and packet loss in transmission. How many RTTs does it take until slow start opens the send window to 1 MB? How long does it take to send the complete file? ( Suppose file size is 10MB )Solution:(1) In flow control, TCP sender knows the window size by the field of advertise-window replied from the receiver. In congestion control, TCP sender learns the window size adaptively by AIMD( Additive Increase and Multiplicative Decrease) mechanism responding to the packet lossevent.(2)When TCP realizes congestion control mechanism, its effective send window size will be min (CongestionWindow, AdvertizedWindow). In original design of TCP header, the field of AdvertizedWindow is 16 bit, which is 216=26*210=64 KB. So the maximum effective window of original TCP sender is 64KB. The assumption of the first sentence in this question relaxes such constraint for TCP.In slow start, the send window starts from w0=1 packet, which is 1 KB. For each RTT after a successful transmission, the window size will be doubled. After i RTT, it will be 2i * w0. Let 2i * 1KB = 1MB, soi = log2(1MB/1KB) = log2(210) = 10.It will take 10 RTTs to reach 1MB send window.Case 1: if the receiver window remains as 1MBIn the first 10 RTTs, total (1 + 2 + 4 + … + 210) * 1KB has been transmitted.Which is (211 - 1) * 1KB = 2 MB - 1 KB, the rest file is 10MB - (2MB - 1KB) = 8MB + 1KBIn the reset transmission, each RTT can only support 1MB transmission.Thus, additional 9 RTTs are required. Total 19 RTT = 19 * 150ms = 2.85 sCase 2: if the receiver window can be changed.Since there is no congestion and loss, the maximum send window will be the bandwidth * delay for this TCP connection.w max= 1G bps * 150ms = 109 * 150 * 10-3= 150 *106 bit = 18.75 * 106 byte = 17.88 MB.So, this 10 MB file can be transferred before reaching w max. In another word, it can be sent in its slow start phase. Assume x RTT is required to send this file, then:(1 + 2 + 4 + … + 2x) * 1KB ≥ 10 MB2 * 2x–1 ≥ 10 * 1024x ≥ log2(10241) – 1 = 12.3Thus x = 13, it will take 13 RTTs to transfer this file. 13RTT = = sTotal delay = 13RTT + Filesize/BW = 13 * 150ms+ 10MB / 1Gbps =1.95 + 0.08 * 1.024^2=2.03 s11。
计算机网络英文题库(附答案)chapter1(推荐文档)

Chapter 1 Computer Networks and the Internet1.The ( ) is a worldwide computer network, that is, a network that interconnects millions of computing devices throughout the world.ppt3A public InternetB IntranetC switch netD television net2.Which kind of media is not a guided media? ( )A twisted-pair copper wireB a coaxial cableC fiber opticsD digital satellite channel3.Which kind of media is a guided media? ( )A geostationary satelliteB low-altitude satelliteC fiber opticsD wireless LAN4.The units of data exchanged by a link-layer protocol are called ( ).A FramesB SegmentsC DatagramsD bit streams5.Which of the following option belongs to the circuit-switched networks? ( )A FDMB TDMC VC networksD both A and B6.( )makes sure that neither side of a connection overwhelms the other side by sending too many packets too fast.A Reliable data transferB Flow controlC Congestion controlD Handshaking procedure7.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Store-and-forward transmissionB FDMC End-to-end connectionD TDM8.Datagram networks and virtual-circuit networks differ in that ( ).A datagram networks are circuit-switched networks, andvirtual-circuit networks are packet-switched networks.B datagram networks are packet-switched networks, andvirtual-circuit networks are circuit-switched networks.C datagram networks use destination addresses and virtual-circuitnetworks use VC. numbers to forward packets toward theirdestination.D datagram networks use VC. numbers and virtual-circuit networksuse destination addresses to forward packets toward their destination. 9.In the following options, which one is not a guided media? ( )A twisted-pair wireB fiber opticsC coaxial cableD satellite10.Processing delay does not include the time to ( ).A examine the packet’s headerB wait to transmit the packet onto the linkC determine where to direct the packetD check bit-error in the packet11.In the following four descriptions, which one is correct? ( )A The traffic intensity must be greater than 1.B The fraction of lost packets increases as the traffic intensitydecreases.C If the traffic intensity is close to zero, the average queuing delaywill be close to zero.D If the traffic intensity is close to one, the average queuing delaywill be close to one.12.The Internet’s network layer is responsible for moving network-layer packets known as ( ) from one host to another.A frameB datagramC segmentD message13.The protocols of various layers are called ( ).A the protocol stackB TCP/IPC ISPD network protocol14.There are two classes of packet-switched networks: ( ) networks and virtual-circuit networks.A datagramB circuit-switchedC televisionD telephone15.Access networks can be loosely classified into three categories: residential access, company access and ( ) access.A cabledB wirelessC campusD city areaQuestion 16~17Suppose, a is the average rate at which packets arrive at the queue, R is the transmission rate, and all packets consist of L bits, then the traffic intensity is ( 16 ), and it should no greater than ( 17 ).16. A LR/aB La/RC Ra/LD LR/a17.A 2B 1C 0D -118.In the Internet, the equivalent concept to end systems is ( ).A hostsB serversC clientsD routers19.In the Internet, end systems are connected together by ( ).A copper wireB coaxial cableC communication linksD fiber optics20.End systems access to the Internet through its ( ).A modemsB protocolsC ISPD sockets21.End systems, packet switches, and other pieces of the Internet, run ( ) that control the sending and receiving of information within theInternet.A programsB processesC applicationsD protocols22.There are many private networks, such as many corporate and government networks, whose hosts cannot exchange messages withhosts outside of the private network. These private networks are often referred to as ( ).A internetsB LANC intranetsD WAN23.The internet allows ( ) running on its end systems to exchange data with each other.A clients applicationsB server applicationsC P2P applicationsD distributed applications24.The Internet provides two services to its distributed applications: a connectionless unreliable service and () service.A flow controlB connection-oriented reliableC congestion controlD TCP25.It defines the format and the order of messages exchanged between two or more communicating entities, as well as the actions taken on thetransmission and/or receipt of a message or other event. The sentence describes ( ).A InternetB protocolC intranetD network26.In the following options, which does not define in protocol? ( )A the format of messages exchanged between two or morecommunicating entitiesB the order of messages exchanged between two or morecommunicating entitiesC the actions taken on the transmission of a message or other eventD the transmission signals are digital signals or analog signals 27.In the following options, which is defined in protocol? ( )A the actions taken on the transmission and/or receipt of a message orother eventB the objects exchanged between communicating entitiesC the content in the exchanged messagesD the location of the hosts28.In the following options, which does not belong to the network edge? ( )A end systemsB routersC clientsD servers29.In the following options, which belongs to the network core? ( )A end systemsB routersC clientsD servers30.In the following options, which is not the bundled with the Internet’s connection-oriented service? ( )A reliable data transferB guarantee of the transmission timeC flow controlD congestion-control31.An application can rely on the connection to deliver all of its data without error and in the proper order. The sentence describes ( ).A flow controlB congestion-controlC reliable data transferD connection-oriented service32.It makes sure that neither side of a connection overwhelms the other side by sending too many packets too fast. The sentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer33.It helps prevent the Internet from entering a state of gridlock. When a packet switch becomes congested, its buffers can overflow and packet loss can occur. The sentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer34.The Internet’s connection-oriented service has a name, it is ( ).A TCPB UDPC TCP/IPD IP35.In the following options, which service does not be provided to an application by TCP?( )A reliable transportB flow controlC video conferencingD congestion control36.The Internet’s connectionless service is called ( ).A TCPB UDPC TCP/IPD IP37.In the following options, which does not use TCP?( )A SMTPB internet telephoneC FTPD HTTP38.In the following options, which does not use UDP?( )A Internet phoneB video conferencingC streaming multimediaD telnet39.There are two fundamental approaches to building a network core, ( ) and packet switching.A electrical current switchingB circuit switchingC data switchingD message switching 40.In ( ) networks, the resources needed along a path to provide for communication between the end system are reserved for the duration of the communication session.A packet-switchedB data-switchedC circuit-switchedD message-switched41.In ( ) networks, the resources are not reserved; a session’s messages use the resources on demand, and as a consequence, may have to wait for access to communication link.A packet-switchedB data-switchedC circuit-switchedD message-switched42.In a circuit-switched network, if each link has n circuits, for each link used by the end-to-end connection, the connection gets ( ) of thelink’s bandwidth for the duration of the connection.A a fraction 1/nB allC 1/2D n times43.For ( ), the transmission rate of a circuit is equal to the frame rate multiplied by the number of bits in a slot.A CDMAB packet-switched networkC TDMD FDM44.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Queuing delayB Store-and-forward transmissionC Packet lossD Propagation45.The network that forwards packets according to host destination addresses is called ( ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram46.The network that forwards packets according to virtual-circuit numbers is called ( ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram47.In the following entries, which is not a kind of access network?( )A residential accessB company accessC wireless accessD local access48.Suppose there is exactly one packet switch between a sending host and a receiving host. The transmission rates between the sending host and the switch and between the switch and the receiving host are R1 and R2,respectively. Assuming that the switch uses store-and-forward packetswitching, what is the total end-to-end delay to send a packet of length L? (Ignore queuing delay, propagation delay, and processing delay.)( )A L/R1+L/R2B L/R1C L/R2D none of the above49.The time required to examine the packet’s header and determine where to direct the packet is part of the ( ).A queuing delayB processing delayC propagation delayD transmission delay50.The time required to propagate from the beginning of the link to the next router is ( ).A queuing delayB processing delayC propagation delayD transmission delay51.Consider sending a packet of 3000bits over a path of 5 links. Each link transmits at 1000bps. Queuing delays, propagation delay and processing delay are negligible. (6 points)(1).Suppose the network is a packet-switched virtual circuit network. VC setup time is 0.1 seconds. Suppose the sending layers add a total of 500 bits of header to each packet. How long does it take to send the file from source to destination?(2).Suppose the network is a packet-switched datagram network and a connectionless service is used. Now suppose each packet has 200 bits of header. How long does it take to send the file?(3).Suppose that the network is a circuit-switched network. Further suppose that the transmission rate of the circuit between source and destination is 200bps. Assuming 0.02s setup time and 200 bits of header appended to the packet, how long does it take to send the packet?Solution: (1). t=5*(3000+500)/1 000+0.1=17.6s(2). t=5*(3000+200)/1 000=16s(3). t=(3000+200)/20 0+0.02=16.02s。
计算机网络英语期末复习试题及答案

《计算机网络英语》期末复习试题及答案一选择题1.A ( ) protocol is used to move a datagram over an individual link.A application-layerB transport-layerC network-layerD link-layer2.The units of data exchanged by a link-layer protocol are called ( ).A datagramsB framesC segmentsD messages3.Which of the following protocols is not a link-layer protocol? ( )A EthernetB PPPC HDLCD IP4.In the following four descriptions, which one is not correct? ( )A link-layer protocol has the node-to-node job of moving network-layer datagrams over a single link in the path.B The services provided by the link-layer protocols may be different.C A datagram must be handled by the same link-layer protocols on the different links in the path.D The actions taken by a link-layer protocol when sending and receiving frames include error detection, flow control and random access.5.Which of the following services can not offered by a link-layer protocol? ( )A congestion controlB Link AccessC Error controlD Framing6.( ) protocol serves to coordinate the frame transmissions of the many nodes when multiple nodes share a single broadcast link.A ARPB MACC ICMPD DNS7.In the following four descriptions about the adapter, which one is not correct? ( )A The adapter is also called as NIC.B The adapter is a semi-autonomous unit.C The main components of an adapter are bus interface and the link interface.D The adapter can provide all the link-layer services.8.Consider CRC error checking approach, the four bit generator G is 1011, and suppose that the data D is 10101010, then the value of R is( ).A 010B 100C 011D 1109.In the following four descriptions about random access protocol, which one is not correct? ( )A In slotted ALOHA, nodes can transmit at random time.B In pure ALOHA, if a frame experiences a collision, the node will immediately retransmit it with probability p.C The maximum efficiency of a slotted ALOHA is higher than a pure ALOHA.D In CSMA/CD, one node listens to the channel before transmitting.10.In the following descriptions about MAC address, which one is not correct? ( )A The MAC address is the address of one node’s adapter.B No two adapters have the same MAC address.C The MAC address doesn’t change no matter where the adapter goes.D MAC address has a hierarchical structure.11.The ARP protocol can translate ( ) into ( ). ( )A host name, IP addressB host name, MAC addressC IP address, MAC addressD broadcast address, IP address12.The value of Preamble field in Ethernet frame structure is ( )A 10101010 10101010……10101010 11111111B 10101011 10101011……10101011 10101011C 10101010 10101010……10101010 10101011D 10101010 10101010……10101010 1010101013.There are four steps in DHCP, the DHCP server can complete ( ).A DHCP server discoveryB DHCP server offersC DHCP requestD DHCP response14.In CSMA/CD, the adapter waits some time and then returns to sensing the channel. In the following four times, which one is impossible? ( )A 0 bit timesB 512 bit timesC 1024 bit timesD 1028 bit times15.The most common Ethernet technologies are 10BaseT and 100BaseT. “10” and “100”indicate( ).A the maximum length between two adaptersB the minimum length between two adaptersC the transmission rate of the channelD the transmission rate of the node16.The principal components of PPP include but not( ).A framingB physical-control protocolC link-layer protocolD network-layer protocol17.In the following four options, which service can not be provided by switch? ( )A filteringB self-learningC forwardingD optimal routing18.In the following four services, which one was be required in PPP? ( )A packet framingB error detectionC error correctionD multiple types of link19.The ability to determine the interfaces to which a frame should be directed, and then directing the frame to those interfaces is( ).A filteringB forwardingC self-learningD optimal routing20.In ( ) transmission(s), the nodes at both ends of a link may transmit packets at the same time.A full-duplexB half-duplexC single-duplexD both full-duplex and half-duplex21.Consider the data D is 01110010001, if use even parity checking approach, the parity bit is( ①), if use odd parity checking approach, the parity bit is( ②). ( )A ①0 ②1B ①0 ②0C ①1 ②1D ①1 ②022.In the following four descriptions about parity checks, which one is correct? ( )A Single-bit parity can detect all errors.B Single-bit parity can correct one errors.C Two-dimensional parity not only can detect a single bit error, but also can correct that error.D Two-dimensional parity not only can detect any combination of two errors, but also can correct them.23.MAC address is ( ) bits long.A 32B 48C 128D 6424.Wireless LAN using protocol ( ).A IEEE 802.3B IEEE 802.4C IEEE 802.5D IEEE 802.1125.The following protocols are belonging to multiple access protocols except for ( ).A channel partitioning protocolsB routing protocolsC random access protocolsD taking-turns protocols26.Which of the following is not belonging to channel partitioning protocols? ( )A CSMAB FDMC CDMAD TDM27.In the following four descriptions about CSMA/CD, which one is not correct? ( )A A node listens to the channel before transmitting.B If someone else begins talking at the same time, stop talking.C A transmitting node listens to the channel while it is transmitting.D With CSMA/CD, the collisions can be avoided completely.28.( ) provides a mechanism for nodes to translate IP addresses to link-layer address.A IPB ARPC RARPD DNS29.A MAC address is a ( )address.A physical-layerB application-layerC link-layerD network-layer30.Which of the following is correct? ( )A No two adapters have the same MAC address.B MAC broadcast address is FF-FF-FF-FF-FF-FF.C A portable computer with an Ethernet card always has the same MAC address, no matter where the computer goes.D All of the above31.In the following four descriptions, which one is not correct? ( )A ARP resolves an IP address to a MAC address.B DNS resolves hostnames to IP addresses.C DNS resolves hostnames for hosts anywhere in the Internet.D ARP resolves IP addresses for nodes anywhere in the Internet.32.In the LAN, ( )protocol dynamically assign IP addresses to hosts.A DNSB ARPC DHCPD IP33.DHCP protocol is a four-step process: ①DHCP request. ②DHCP ACK. ③DHCP server discovery. ④DHCP server offer(s). The correct sequence is ( )A ①②③④B ③②①④C ③④①②D ①④③②34.In the Ethernet frame structure, the CRC field is ( )bytes.A 2B 4C 8D 3235.In the Ethernet frame structure, the Data field carries the ( ).A IP datagramB segmentC frameD message36.In the following four descriptions, which one is not correct? ( )A Ethernet uses baseband transmission.B All of the Ethernet technologies provide connection-oriented reliable service to the network layer.C The Ethernet 10Base2 technology uses a thin coaxial cable for the bus.D The Ethernet 10BaseT technology uses a star topology.37.Ethernet’s multiple access protocol is ( ).A CDMAB CSMA/CDC slotted ALOHAD token-passing protocol38.In the following four descriptions about CSMA/CD, which one is not correct? ( )A An adapter may begin to transmit at any time.B An adapter never transmits a frame when it senses that some other adapter is transmitting.C A transmitting adapter aborts its transmission as soon as it detects that another adapter is also transmitting.D An adapter retransmits when it detects a collision.39.Which of the following descriptions about CSMA/CD is correct? ( )A No slots are used.B It uses carrier sensing.C It uses collision detection.D All of the above.40.The Ethernet 10BaseT technology uses( )as its physical media.A fiber opticsB twisted-pair copper wireC coaxial cableD satellite radio channel41.For 10BaseT, the maximum length of the connection between an adapter and the hub is ( )meters.A 100B 200C 500D 1042.A ( )is a physical-layer device that acts on individual bits rather than on frames.A switchB hubC routerD gateway43.A hub is a ( )device that acts on individual bits rather than on frames.A physical-layerB link-layerC network-layerD ransport-layer44.A switch is a( )device that acts on frame.A physical-layerB link-layerC network-layerD transport-layer45.In the following four descriptions, which one is not correct? ( )A Switches can interconnect different LAN technologies.B Hubs can interconnect different LAN technologies.C There is no limit to how large a LAN can be when switches are used to interconnect LAN segments.D There is restriction on the maximum allowable number of nodes in a collision domain when hubs are used to interconnect LAN segments.46.The ability to determine whether a frame should be forwarded to some interface or should just be dropped is ( ).A filteringB forwardingC self-learningD optimal routing47.Which of the following devices is not a plug and play device? ( )A hubB routerC switchD repeater48.Which of the following devices is not cut-through device? ( )A hubB routerC switchD repeater49.In the following four descriptions, which one is not correct? ( )A Switches do not offer any protection against broadcast storms.B Routers provide firewall protection against layer-2 broadcast storms.C Both switches and routers are plug and play devices.D A router is a layer-3 packet switch, a switch is a layer-2 packet switch.50.Which device has the same collision domain? ( )A HubB SwitchC RouterD Bridge51.IEEE802.2 protocol belong to ( )layerA networkB MACC LLCD physical52.IEEE802.11 protocol defines ( )rules.A Ethernet BusB wireless WANC wireless LAND Token Bus53.In data link-layer, which protocol is used to share bandwidth? ( )A SMTPB ICMPC ARPD CSMA/CD54.When two or more nodes on the LAN segments transmit at the same time, there will be a collision and all of the transmitting nodes well enter exponential back-off, that is all of the LAN segments belong to the same( ).A collision domainB switchC bridgeD hub55.( )allows different nodes to transmit simultaneously and yet have their respective receivers correctly receive a sender’s encoded data bits.A CDMAB CSMAC CSMA/CDD CSMA/CA56.Because there are both network-layer addresses (for example, Internet IP addresses) and link-layer addresses (that is, LAN addresses), there is a need to translate between them. Forthe Internet, this is the job of ( ).A RIPB OSPFC ARPD IP57.PPP defines a special control escape byte, ( ). If the flag sequence, 01111110 appears anywhere in the frame, except in the flag field, PPP precedes that instance of the flag pattern with the control escape byte.A 01111110B 01111101C 10011001D 1011111058.The device ( ) can isolate collision domains for each of the LAN segment.A modemB switchC hubD NIC59.In the following four descriptions about PPP, which one is not correct? ( )A PPP is required to detect and correct errors.B PPP is not required to deliver frames to the link receiver in the same order in which they were sent by the link sender.C PPP need only operate over links that have a single sender and a single receiver.D PPP is not required to provide flow control.60.In the PPP data frame, the( ) field tells the PPP receivers the upper-layer protocol to which the received encapsulated data belongs.A flagB controlC protocolD checksum61.PPP’s link-control protocols (LCP) accomplish ( ).A initializing the PPP linkB maintaining the PPP linkC taking down the PPP linkD all of the above62.The PPP link always begins in the ( ) state and ends in the ( ) state. ( )A open, terminatingB open, deadC dead, deadD dead, terminating63.For( ) links that have a single sender at one end of the link and a single receiver at the other end of the link.A point-to-pointB broadcastC multicastD all of the above64.With ( )transmission, the nodes at both ends of a link may transmit packets at the same time.A half-duplexB full-duplexC simplex(单工)D synchronous65.With ( ) transmission, a node can not both transmit and receive at the same time.A half-duplexB full-duplexC simplex(单工)D synchronous66.Which of the following functions can’t be implemented in the NIC? ( )A encapsulation and decapsulationB error detectionC multiple access protocolD routing67.Which of the following four descriptions is wrong? ( )A The bus interface of an adapter is responsible for communication with the adapter’s parent node.B The link interface of an adapter is responsible for implementing the link-layer protocol.C The bus interface may provide error detection, random access functions.D The main components of an adapter are the bus interface and the link interface. 68.For odd parity schemes, which of the following is correct? ( )A 011010001B 111000110C 110101110D 00011011069.( )divides time into time frames and further divides each time frame into N time slots.A FDMB TMDC CDMAD CSMA70.With CDMA, each node is assigned a different ( )A codeB time slotC frequencyD link71.Which of the following four descriptions about random access protocol is not correct? ( )A A transmission node transmits at the full rate of the channelB When a collision happens, each node involved in the collision retransmits at once.C Both slotted ALOHA and CSMA/CD are random access protocols.D With random access protocol, there may be empty slots.72.PPP defines a special control escape byte 01111101. If the data is b1b201111110b3b4b5, the value is( )after byte stuffing.A b1b20111110101111110b3b4b5B b1b20111111001111101b3b4b5C b5b4b30111111001111101b2b1D b5b4b30111110101111110b2b173.MAC address is in ( ) of the computer.A RAMB NICC hard diskD cache74.Which of the following is wrong? ( )A ARP table is configured by a system administratorB ARP table is built automaticallyC ARP table is dynamicD ARP table maps IP addresses to MAC addresses75.NIC works in ( )layer.A physicalB linkC networkD transport76.In LAN, if UTP is used, the common connector is( ).A AUIB BNCC RJ-45D NNI77.The modem’s function(s) is(are) ( ).A translates digital signal into analog signalB translates analog signal into digital signalC both translates analog signal into digital signal and translates digital signal into analog signalD translates one kind of digital signal into another digital signal78.( )defines Token-Ring protocol.A IEEE 802.3B IEEE 802.4C IEEE 802.5D IEEE 802.279.( )defines Token-Bus protocol.A IEEE 802.3B IEEE 802.4C IEEE 802.5D IEEE 802.280.( ) defines CSMA/CD protocol.A IEEE 802.3B IEEE 802.4C IEEE 802.5D IEEE 802.281.The computer network that concentrated in a geographical area, such as in a building or on a university campus, is ( )A a LANB a MANC a WAND the Internet82.The MAC address is ( ) bits long.A 32B 48C 128D 25683.Which of the following four descriptions about MAC addresses is wrong? ( )A a MAC address is burned into the adapter’s ROMB No two adapters have the same addressC An adapter’s MAC address is dynamicD A MAC address is a link-layer address84.Which of the following four descriptions about DHCP is correct? ( )A DHCP is C/S architectureB DHCP uses TCP as its underlying transport protocolC The IP address offered by a DHCP server is valid foreverD The DHCP server will offer the same IP address to a host when the host requests an IP address85.The ( )field permits Ethernet to multiplex network-layer protocols.A preambleB typeC CRCD destination MAC address86.For 10BaseT, the maximum length of the connection between an adapter and the hub is ( ) meters.A 50B 100C 200D 50087.An entry in the switch table contains the following information excepts for ( )A the MAC address of a nodeB the switch interface that leads towards the nodeC the time at which the entry for the node was placed in the tableD the IP address of a node二、阅读理解The central processing unit (CPU) is the heart of the computer systems. Among other things, its configuration determines whether a computer is fast or slow in relation to other computers. The CPU is the most complex computer system component, responsible for directing most of the computer system activities based on the instructions provided. As one computer generation has evolved to the next, the physical size of the CPU has often become smaller and smaller, while its speed and capacity have increased tremendously. Indeed, these changes have resulted in microcomputers that are small enough to fit on your desk or your lap.The CPU comprises the control unit and the arithmetic / logic unit (ALU).The control unit is responsible for directing and coordinating most of the computer systems activities. It determines the movement of electronic signals between main memory and the arithmetic/logic unit, as well as the control signals between the CPU and input/output devices. The ALU performs all the arithmetic and logical (comparison) functions — that is, it adds, subtracts, multiplies, divides, and does comparisons. These comparisons, which are basically “less than”, “greater than”, and “equal to”, can be combined into several common expressions, such as “greater than or equal to”. The objective of most instructions that use comparisons is to determine which instruction should be executed next.Tell whether the following statements are true(T) or false(F) according to the passage A.(根据上文的内容判断下列句子的正误)1. With the development of computer, the physical size of the CPU has often become bigger and bigger. ( )2. The movement of electronic signals between main memory and the ALU as well as the control signal between the CPU and input /output devices are controlled by the control unit of the CPU. ( )3. The CPU comprises the control unit and memory. ( )4. The control unit performs all the arithmetic and logical (comparison) functions5. The central processing unit (CPU) is the heart of the computer systems. ( )三、翻译下面的文章。
计算机网络英文题库附答案chapter定稿版

计算机网络英文题库附答案c h a p t e r精编W O R D版IBM system office room 【A0816H-A0912AAAHH-GX8Q8-GNTHHJ8】Chapter 1 Computer Networks and the Internet 1.The ( ) is a worldwide computer network, that is, a network that interconnects millions of computing devices throughout the world.ppt3A public InternetB IntranetC switch netD television net2.Which kind of media is not a guided media ( )A twisted-pair copper wireB a coaxial cableC fiber opticsD digital satellite channel3.Which kind of media is a guided media ( )A geostationary satelliteB low-altitude satelliteC fiber opticsD wireless LAN4.The units of data exchanged by a link-layer protocol are called ( ).A FramesB SegmentsC DatagramsD bit streams5.Which of the following option belongs to the circuit-switched networks ( )A FDMB TDMC VC networksD both A and B6.( )makes sure that neither side of aconnection overwhelms the other side bysending too many packets too fast.A Reliable data transferB Flow controlC Congestion controlD Handshaking procedure7.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Store-and-forward transmissionB FDMC End-to-end connectionD TDM8.Datagram networks and virtual-circuit networks differ in that ( ).A datagram networks are circuit-switchednetworks, and virtual-circuit networks arepacket-switched networks.B datagram networks are packet-switchednetworks, and virtual-circuit networks arecircuit-switched networks.C datagram networks use destinationaddresses and virtual-circuit networks useVC. numbers to forward packets towardtheir destination.D datagram networks use VC. numbersand virtual-circuit networks use destinationaddresses to forward packets toward theirdestination.9.In the following options, which one is not a guided media ( )A twisted-pair wireB fiber opticsC coaxial cableD satellite10.Processing delay does not include the time to ( ).A examine the packet’s headerB wait to transmit the packet onto the linkC determine where to direct the packetD check bit-error in the packet11.In the following four descriptions, which one is correct ( )A The traffic intensity must be greaterthan 1.B The fraction of lost packets increases asthe traffic intensity decreases.C If the traffic intensity is close to zero,the average queuing delay will be close tozero.D If the traffic intensity is close to one, theaverage queuing delay will be close to one.12.The Internet’s network layer isresponsible for moving network-layerpackets known as ( ) from one host toanother.A frameB datagramC segmentD message13.The protocols of various layers are called ( ).A the protocol stackB TCP/IPC ISPD network protocol14.There are two classes of packet-switched networks: ( ) networks and virtual-circuitnetworks.A datagramB circuit-switchedC televisionD telephone15.Access networks can be loosely classified into three categories: residential access,company access and ( ) access.A cabledB wirelessC campusD city areaQuestion 16~17Suppose, a is the average rate at which packets arrive at the queue, R is the transmission rate, and all packets consist of L bits, then the traffic intensity is ( 16 ), and it should no greater than ( 17 ).16.A LR/aB La/RC Ra/LD LR/a 17.A 2B 1C 0D -118.In the Internet, the equivalent concept to end systems is ( ).A hostsB serversC clientsD routers19.In the Internet, end systems are connected together by ( ).A copper wireB coaxial cableC communication linksD fiber optics20.End systems access to the Internet through its ( ).A modemsB protocolsC ISPD sockets21.End systems, packet switches, and other pieces of the Internet, run ( ) that controlthe sending and receiving of informationwithin the Internet.A programsB processesC applicationsD protocols22.There are many private networks, such as many corporate and government networks,whose hosts cannot exchange messageswith hosts outside of the private network.These private networks are often referredto as ( ).A internetsB LANC intranetsD WAN23.The internet allows ( ) running on its end systems to exchange data with each other.A clients applicationsB server applicationsC P2P applicationsD distributed applications24.The Internet provides two services to its distributed applications: a connectionlessunreliable service and () service.A flow controlB connection-oriented reliableC congestion controlD TCP25.It defines the format and the order of messages exchanged between two or morecommunicating entities, as well as theactions taken on the transmission and/orreceipt of a message or other event. Thesentence describes ( ).A InternetB protocolC intranetD network26.In the following options, which does not define in protocol ( )A the format of messages exchangedbetween two or more communicatingentitiesB the order of messages exchangedbetween two or more communicatingentitiesC the actions taken on the transmission ofa message or other eventD the transmission signals are digitalsignals or analog signals27.In the following options, which is defined in protocol ( )A the actions taken on the transmissionand/or receipt of a message or othereventB the objects exchanged between communicating entitiesC the content in the exchanged messagesD the location of the hosts28.In the following options, which does not belong to the network edge ( )A end systemsB routersC clientsD servers29.In the following options, which belongs to the network core ( )A end systemsB routersC clientsD servers30.In the following options, which is not the bundled with the Internet’s connection-oriented service( )A reliable data transferB guarantee of the transmission timeC flow controlD congestion-control31.An application can rely on the connection to deliver all of its data without error andin the proper order. The sentencedescribes ( ).A flow controlB congestion-controlC reliable data transferD connection-oriented service32.It makes sure that neither side of aconnection overwhelms the other side bysending too many packets too fast. Thesentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer33.It helps prevent the Internet from enteringa state of gridlock. When a packet switchbecomes congested, its buffers canoverflow and packet loss can occur. Thesentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer34.The Internet’s connection-oriented service has a name, it is ( ).A TCPB UDPC TCP/IPD IP 35.In the following options, which service does not be provided to an application by TCP( )A reliable transportB flow controlC video conferencingD congestion control36.The Internet’s connectionless service is called ( ).A TCPB UDPC TCP/IPD IP37.In the following options, which does not use TCP()A SMTPB internet telephoneC FTPD HTTP38.In the following options, which does not use UDP( )A Internet phoneB video conferencingC streaming multimediaD telnet39.There are two fundamental approaches to building a network core, ( ) and packetswitching.A electrical current switchingB circuit switchingC data switchingD message switching40.In ( ) networks, the resources needed along a path to provide forcommunication between the end systemare reserved for the duration of thecommunication session.A packet-switchedB data-switchedC circuit-switchedD message-switched41.In ( ) networks, the resources are not reserved; a session’s messages use theresources on demand, and as aconsequence, may have to wait for accessto communication link.A packet-switchedB data-switchedC circuit-switchedD message-switched42.In a circuit-switched network, if each link has n circuits, for each link used by theend-to-end connection, the connectiongets ( ) of the link’s bandwidth for theduration of the connection.A a fraction 1/nB allC 1/2D n times43.For ( ), the transmission rate of a circuit is equal to the frame rate multiplied by thenumber of bits in a slot.A CDMAB packet-switched networkC TDMD FDM 44.( ) means that the switch must receive the entire packet before it can begin totransmit the first bit of the packet onto theoutbound link.A Queuing delayB Store-and-forward transmissionC Packet lossD Propagation45.The network that forwards packetsaccording to host destination addresses iscalled ( ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram46.The network that forwards packetsaccording to virtual-circuit numbers iscalled ( ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram47.In the following entries, which is not a kind of access network()A residential accessB company accessC wireless accessD local access48.Suppose there is exactly one packet switch between a sending host and a receivinghost. The transmission rates between thesending host and the switch and betweenthe switch and the receiving host are R1and R2, respectively. Assuming that theswitch uses store-and-forward packetswitching, what is the total end-to-enddelay to send a packet of length L (Ignorequeuing delay, propagation delay, andprocessing delay.) ( )A L/R1+L/R2B L/R1C L/R2D none of the above49.The time required to examine thepacket’s header and determine where todirect the packet is part of the ( ).A queuing delayB processing delayC propagation delayD transmission delay50.The time required to propagate from the beginning of the link to the next router is( ).A queuing delayB processing delayC propagation delayD transmission delay51.Consider sending a packet of 3000bits over a path of 5 links. Each link transmits at 1000bps. Queuing delays, propagation delay and processing delay are negligible. (6 points) (1).Suppose the network is a packet-switched virtual circuit network. VC setup time is 0.1 seconds. Suppose the sending layers add a total of 500 bits of header to each packet. How long does it take to send the file from source to destination?(2).Suppose the network is a packet-switched datagram network and a connectionless serviceis used. Now suppose each packet has 200 bitsof header. How long does it take to send the file?(3).Suppose that the network is a circuit-switched network. Further suppose that the transmission rate of the circuit between sourceand destination is 200bps. Assuming 0.02s setuptime and 200 bits of header appended to the packet, how long does it take to send the packet?So lution:(1).t=5*(3000+500)/1000+0.1=17.6s( 2).t=5*(3000+200)/1000=16s( 3).t=(3000+200)/200+0.02=16.02s。
计算机网络(全英文版)期末复习

计算机网络是非题1.In computer networking jargon, the computers connected to the Internet are referred to as end systems, including servers , routers, mobile computers.2.One of the attractive features of DSL and HFC is that the services are always on。
3.HTTP/1.1 uses inpersistent HTTP with pipelining.4.UDP socket is identified by two-tuple: dest IP address, dest port number.5.The IPv6 addresses space is 264.6.ARP translates computer name to network-layer address.7.HTTP uses reliably transfer email message from client to server, port number is 52.8.Link Layer Services include Error Detection, full-duplex etc.9.Star topology popular through mid 90s, Now bus topology prevails.10.FTP,SMTP,POP3 and IMAP run on top of TCP rather than UDP.11.With the SR protocol ,it is possible for the sender to receive an ACK for a packet that falls outside of its current window.12.With GBN, it is possible for the sender to receive an ACK for a packet that falls outside of its current window.13.Ethernet frames can carry more than 1500 bytes of data ,whereas frames for some wide-area links can carry no mare than 576 bytes.14.Ipv6 allows for fragmentation at routers and IP header to be extended,but Ipv4 not.15.For TDM, the time domain is segmented into four circuits; each circuit is assigned the same dedicated slot in the revolving TDM frames. The transmission rate of the frame is equal to the frame rate multiplied by the number of bits in a slot.16.Most packet switches use store and forward transmission at the inputs to the links. Store-and-forward transmission means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.17.If a network employs virtual circuits, then the network's switches must maintain the ongoing connections. Specifically, each time a new connection is established connection entry must be added to the switch's VC number translation table; and each time a connection is released, an entry must be removed from the table.名词解释:写英文全称和汉语全称DNS Domain Name System 域名系统FDM Frequency Division Multiplexing 频分多路复用SMTP Simple Mail Transfer Protocol 简单邮件传输协议TCP Transport Control Protocol 传输控制协议RIP Routing Information Protocol 路由信息协议ARP Address Resolution Protocol 地址解析协议CSMA/CD Carrier Sense multiple Access/ Collision Detection 带有碰撞检测的载波侦听多点访问MIME Multipurpose Internet Mail Extensions 多用途英特网邮件扩充协议填空题1.DNScvoked by an application to obtain the canonical hostname for a supplied alias hostname as well as the(IP address)of the host。
计算机网络(全英文版)期末复习

计算机网络(全英文版)期末复习As an AI language model, I can help you with the content of your article on "Computer Networks - Final Exam Review". However, please note that I am unable to format the document according to specific requirements, such as adding a word count or creating sections with headings. I will provide you with a comprehensive overview of computer networks in English, covering the essential concepts and topics that are typically covered in a final exam review. Here is the article:Computer Networks - Final Exam ReviewIntroduction:Computer networks are an integral part of modern society, facilitating communication and enabling the exchange of information between devices and users. Understanding the fundamentals of computer networks is crucial for professionals in the field of IT and related disciplines. This article aimsto provide a comprehensive review of key concepts and topics in computer networks to help you prepare for your final exam.Network Topologies:A network topology refers to the physical or logical layout of devices in a network. Several common network topologies include bus, star, ring, mesh, and hybrid topologies. Each topology has advantages and disadvantages, and understanding these can help network administrators design and maintain efficient networks.Network Protocols:Network protocols provide a set of rules and guidelines for devices to communicate with each other in a network. The TCP/IP protocol suite is the foundation of modern network communication, consisting of protocols such as IP (Internet Protocol), TCP (Transmission Control Protocol), and UDP (User Datagram Protocol). These protocols ensure reliable and efficient data transfer over networks.OSI Model:The Open Systems Interconnection (OSI) model is a conceptual framework that standardizes the functions of a network into several layers. These layers - physical, data link, network, transport, session, presentation, and application - define how data is transmitted, processed, and presented across a network. Understanding the OSI model aids in troubleshooting network issues and implementing effective network solutions.Network Addressing:In computer networks, devices are identified and addressed using unique addresses. IP addressing, specifically IPv4 and IPv6, allow devices to establish connections and route data packets across networks. IP addressing includes both network and host addresses, enabling efficient communication within and between networks.Routing and Switching:Routing involves determining the optimal path for data packets to travel from source to destination across interconnected networks. Routers, using routing tables and protocols such as OSPF (Open Shortest Path First) and BGP (Border Gateway Protocol), facilitate this process. Switching, on theother hand, involves the efficient forwarding of data packets within a local area network (LAN) using MAC addresses.Network Security:As networks become increasingly complex and interconnected, ensuring network security is paramount. Network security measures include firewalls, intrusion detection systems, encryption, and authentication protocols. Protecting networks from unauthorized access, data breaches, and other threats is essential to maintain data integrity and user privacy.Wireless Networks:Wireless networks have revolutionized connectivity, allowing devices to communicate without physical cables. Wi-Fi, Bluetooth, and cellular networks are examples of wireless technologies widely used today. Understanding wireless networking protocols, security considerations, and challenges is important in a world where wireless connectivity is pervasive.Network Troubleshooting:Network administrators often encounter issues that require troubleshooting skills. Effective troubleshooting involves using diagnostic tools, analyzing network logs, and understanding common network issues such as connectivity problems, latency, and bandwidth constraints. By following logical steps and employing best practices, network administrators can identify and resolve network problems efficiently.Conclusion:Computer networks are the backbone of modern communication and information exchange. This article has provided an overview of key concepts and topics in computer networks, including network topologies, protocols, the OSI model, addressing, routing and switching, network security, wireless networks, and network troubleshooting. Remember to review these concepts thoroughly to prepare for your final exam.。
计算机网络英文复习题

计算机网络英文复习题1、请简述英文“network”是什么含义?并举出一个具体的网络应用实例。
“Network”的英文意思是网络。
网络是由多个节点(nodes)通过各种协议(protocols)进行连接,以实现信息的交换和共享的一种系统。
网络应用实例包括:电子邮件(Email)、万维网(World Wide Web)、文件传输(FTP)、远程登录(Telnet)等。
2、什么是局域网(Local Area Network,LAN)?请举例说明。
局域网(LAN)是一种在有限区域内(如一座大楼、一个校园或一个工厂等)连接计算机和其他设备的高速网络。
例如,家庭网络、办公室网络和校园网络等都是局域网的例子。
3、什么是广域网(Wide Area Network,WAN)?请举例说明。
广域网(WAN)是一种跨越较大地理范围的网络,通常由多个局域网组成,并通过各种传输媒介(如光纤、卫星等)连接在一起。
例如,因特网(Internet)就是一种广域网的例子。
4、请简述TCP/IP协议是什么?并列举其中两个主要的协议。
TCP/IP协议是一种在网络通信中广泛使用的协议套件,它包含了传输控制协议(TCP)和互联网协议(IP)。
这两个协议是TCP/IP协议的重要组成部分。
此外,TCP/IP协议还包括其他一些协议,如HTTP、FTP等。
5、什么是IP?请简述其结构。
IP是互联网协议(IP)中用来唯一标识网络主机或设备的。
它通常由四个数字组成,每个数字在0-255之间。
这些数字由点号分隔,形如 x.x.x.x。
例如,192.168.1.1就是一个IP的例子。
6、什么是DNS?请简述其作用。
DNS(Domain Name System)是域名系统,它可以将网站的域名解析为对应的IP,从而让用户可以通过域名访问网站。
DNS的作用是在用户访问网站时进行解析,将域名转化为对应的IP,这样用户就可以通过浏览器访问网站了。
计算机网络复习题一、选择题1、OSI模型将计算机网络分为几个层次?A. 4个B. 6个C. 7个D. 8个2、TCP/IP协议包含哪两个主要的协议?A. TCP和HTTPB. TCP和UDPC. HTTP和FTPD. FTP和SMTP3、以下哪个协议用于传输电子邮件?A. SMTPB. IMAPC. POP3D. FTP4、以下哪个网络设备用于将网络分成若干个子网?A.路由器B.交换机C.网关D.集线器5、以太网使用什么类型的传输方式?A.异步传输B.同步传输C.基带传输D.宽带传输二、填空题1、OSI模型的第一层是_________层,负责在计算机之间建立连接。
计算机网络英文题库

计算机网络英文题库(附答案)c h a p t e r2(总17页) -本页仅作为预览文档封面,使用时请删除本页-Chapter 2 Application Layer1. In the following four descriptions, which one is correctA In C/S architecture, clients communicate with each other directly.B In C/S architecture, client has a fixed well-known address.C In P2P architecture, peers communicate with each other directly.D In P2P architecture, peer has a fixed well-known address.2. In the context of a communication session between a pair of process, the process that initiates the communication is labeled as the , the process that waits to be contacted to begin the session is labeled as the .A client process, server processB sending process, receiving processC input process, output processD communicating process, connecting process3. A socket is the interface between within a host.A the network layer and the link layerB the link layer and the physical layerC the application layer and the transport layerD the transport layer and the network layer4. In the following applications, which one is a loss-tolerant applicationA E-mailB file transferC instant messagingD real-time audio5. In the following applications, which one is a bandwidth-sensitive applicationA E-mailB web applicationC real-time audioD file transfer6. The service of TCP can’t guarantee .A delivery of all data without errorB delivery of all data in the proper orderC the rate of deliveryD congestion control7. In the following applications, which one uses UDPA E-mailB web applicationC file transferD DNS8. In the following descriptions about HTTP, which one is not correctA HTTP uses non-persistent connections in its default mode.B HTTP uses TCP as its underlying transport protocol.C HTTP is a stateless protocol.D HTTP is client-server architecture.9. Suppose a web page consists of a base HTML file, 5 JEPG images and a java applet, and also suppose HTTP uses persistent connection without pipelining, the total response timeis .A 2RTTB 8RTTC 12 RTTD 14RTT10. In HTTP response message, if the requested HTTP protocol version is not supported, the status code is .A 200B 301C 400D 5051~5 CACDC 6~10 CDABD11. The port number of web application is .A 25B 20C 80D 5312. A network entity that satisfies HTTP requests on the behalf of an origin web server is .A server farmB server stackC proxy serverD edge server13. In the following descriptions about persistent connection, which one is not correctA The server leaves the TCP connection open after sending a response.B Each TCP connection is closed after the server sending one object.C There are two versions of persistent connection: without pipelining and with pipelining.D The default mode of HTTP uses persistent connection with pipelining.14. FTP uses two parallel TCP connections to transfer a file, there are .A control connection and data connectionB receiving connection and sending connectionC client connection and sever connectionD program connection and process connection15. In the following descriptions about FTP, which one is correctA FTP is p2p architecture.B FTP sends its control information out-of-band.C FTP uses persistent connection.D FTP is a stateless protocol.16. In the commands of FTP, which one does not have parameterA USERB PASSC LISTD STOR17. The Internet mail system has three components which they are .A user agent, SMTP, POP3B SMTP, POP3, IMAPC user agent, SMTP, IMAPD user agent, SMTP, mail server18. If the status code in HTTP response message is 404, it means .A Request succeeded.B The requested document doesn’t exit on this server.C This is a generic error code indicating that the request could not be understood by the server.D Requested object has been permanently mover.19. Comparison HTTP with SMTP, the correct is .A HTTP is a push protocol, and SMTP is a pull protocol.B In the default mode, both of them use persistent connection.C HTTP place s all of the message’s objects into one message, and SMTP sends every object one by one.D HTTP requires each message to be in 7-bit ASCII format, and SMTP doesn’t impose this restriction.20. The headers in the MIME message must include except .A FromB Content-typeC Content-transfer-encodingD MIME version11~15CCBAB 16~20 DDBBD21. In the following protocol, which one is statelessA POP3B SMTPC FTPD IMAP22. DNS means .A Data Name SystemB Data National SystemC Domain Name SystemD Domain National System23. There are three classes of DNS server except .A Root DNS serverB Local DNS serverC TLD server D Authoritative DNS server24. DNS provides some services except .A Host aliasingB Mail server aliasingC Load distributionD A single point of failure25. There are three architectures for locating content in P2P file sharing, KaZaA uses .A Centralized Directory (Napster)B Query Flooding(Gnutella)C Exploiting Heterogeneity (p141)D Incentive Priorities26. There are three architectures for locating content in P2P file sharing, Napster uses .A Centralized Directory (p137)B Query FloodingC Exploiting HeterogeneityD Incentive Priorities27. The following architectures in P2P file sharing, which is an overlay networkA Centralized DirectoryB Query Flooding(p139)C Exploiting HeterogeneityD Incentive Priorities28. The time it takes for a small packet to travel from client to server and then back to the client is .A round-travel timeB next-hop timeC round-trip timeD prefix-matching time29. Suppose A ( with a Web-based e-mail account ) sends a message to B ( who accesses his mail server using POP3), which application-layer protocol is not usedA HTTPB SMTPC POP3D IMAP30. In the four following options, which protocol is included in Mail Access ProtocolA SMTPB DHCPC IMAPD FTP31. In FTP commands, is used to send user password to the server.A UserB PassC RetrD Stor32. The function of the additional header field in MIME Content-Type is .A to convert the message body to its origin non-ASCII formB to determine what actions it should take on message bodyC to send an E-mail to the receiving user agentD to indicate what type the message is33. In the four following options, which application is organized as hybrid of C/S and P2P architectureA E-mailB OICQC File transferD Web application34. In the four following options, which is not a centralized DNS design’s problemA a single point of failureB traffic volumeC distant centralized databaseD slow (maintenance)35.In the following options, from the application developer’s perspective, which is not correctA the network architecture is fixedB the network architecture provides a specific set of services to applicationsC the application architecture is designed by the physical devicesD the application architecture dictates how the application is organized over the various end systems36. There are three predominant architectures used in modern network applications, which one is not includedA the client-server architectureB the P2P architectureC a hybrid of the client-server and P2P architectureD a hybrid of the client-server and browser-server architecture37. In the following options about C/S architecture, which is not correctA In C/S architecture, there is an always-on host, called the server.B In C/S architecture, there is an always-on host, called the client.C The server has a fixed, well-known address, called IP address.D Clients do not directly communicate with each other.38. are often used to create a powerful virtual server in C/S architecture.A PeersB Server farmC server stackD local server39. A process sends messages into, and receives messages from, the network through its .A socketB programC clientD peer40. Which one is not defined by an application-layer protocolA the types of messages exchangedB the syntax of various message typesC the semantics of the fieldsD rules for determining when and how to translate the socket41. HTTP can use two types of connections, which are .A persistent and non-persistent connectionB connection with pipelining and without pipeliningC TCP and UDPD parallel and serial connection42. takes for a small packet to travel from client to server and then back to the client.A RDTB thresholdC RTTD overhead43. The default mode of HTTP uses .A non-persistent connection with pipeliningB non-persistent connection without pipeliningC persistent connection with pipeliningD persistent connection without pipelining44. In HTTP request messages, the request line has three fields, there are .A the method field, the URL field and the HTTP version fieldB the method, the connection and URL fieldC the user-agent, the method and HTTP version fieldD the user-agent, the URL and the HTTP version field45. In the header lines of HTTP request message, if the field of Connection is close, it specifies .A the host on which object residesB what type of the user agentC that the browser wants the server to close the connection after sending the requested objectD which language can the browser receive46. In HTTP response message, if the status code is 404, it means .A request succeeded and the information is returned in the responseB requested object has been permanently movedC the requested HTTP protocol version is not supported by the serverD the requested document does not exist on this server47. is a network entity that satisfies HTTP requests on the behalf of an origin Web server.A proxy serverB local serverC DNS serverD Web server48. In the following four options about web cache, which one is not correctA A web cache is both a server and a client at the same time.B A web cache is purchased and installed by an ISP.C A web cache can raise the response time for a client request.D A web cache can reduce traffic on an institution’s access link to the Internet.49. The request message in the conditional GET must include the header line.A Last-ModifiedB Last-ReferencedC If-Modified-SinceD If –Referenced-Since50. FTP uses two parallel connections to transfer a file, they are .A TCP and UDP connectionB connection with pipelining and without pipeliningC control an data connectionD client-server and browser-server connection51. In FTP commands, which one is used to ask the server to send back a list of all files in the current remote directoryA USERB PASSC LISTD RETR52. In the Internet mail system, allow users to read, reply to, forward, save and compose message.A User agentsB mail serversC SMTPD TCP53. The two key MIME headers for supporting multimedia are .A Content-Type and MIME-VersionB Content-Type and Content-Transfer-EncodingC Content-Transfer-Encoding and MIME-VersionD MIME-Version and MIME-Type54. For Internet mail, the mail access protocol is used to .A transfer mail from the recipient’s mail server to the recipient’s user agentB transfer mail from the sender’s mail server to the recipient’s mail serverC translate the mail fr om the sender’s mail serverD translate the mail into the recipient’s mail server55. POP3 progresses through three phases, which they are .A authorization, translation and transactionB authorization, translation and updateC authorization, transaction and updateD translation, transaction and update56. In the following four services, which one can not provide by DNSA Host aliasingB Mail server aliasingC translate hostname to IP addressesD translate MAC addresses to IP addresses57. There are three classes of DNS servers, there are .A root DNS server, top-level domain DNS server and local DNS serverB root DNS server, top-level domain DNS server and authoritative DNS serverC root DNS server, local DNS server and authoritative DNS serverD root DNS server, local DNS server and top-level domain DNS server58. In the following four options about POP3, which one is not correctA The user agent employed only three commands: List, Retr and QuitB The server does not carry state information across POP3 sessionsC The port number is 110D The POP3 protocol does not provide any means for a user to create remote folders and assign messages to folders.59. A resource record in DNS distributed database is a four-tuple, which field can be ignored(p132) A Name B Value C Type D TTL 60. In the following four options about DNSresource record, which one is correctA The meaning of Name and Value depend on Type.B The meaning of Value and Type depend on Name.C If Type=A, then Name is a domain and Value is the IP address for the hostname.D If Type=MX, then Name is domain and Value is the IP address for the hostname.61. In the following four options about DNS messages, which one is not correctA There are only two kinds of DNS message.(p133)B Both query and reply message have the same format.C The header section in DNS message has 12 bytes.D The authority section contains the resource records for the same that was originally queri ed.62. In DNS message, contains information about the query that is being made.(p133)A authority sectionB question sectionC answer sectionD additional section63. There are three techniques are employed in most any P2P file-sharing systems, which one is not include (p144)A Request queuingB incentive prioritiesC parallel downloadingD Response queuing64. In the following four options about P2P file-sharing, which one is not correctA P2P file-sharing is highly scalable.B P2P file-sharing relies on P2P architecture.C The means for locating content in different P2P file-sharing are different.D P2P file-sharing systems not only share MP3s,but also videos, software, documents and images.65. In MIME header lines, specifies the name of the SMTP server that sent the message (f rom),the name of the SMTP server that received the message (by), and the time an which the rec eiving server received the message.A ReceivedB FromC ToD MIME-Version66. If the header line Connection is close, it means that the client wants .A persistent connection with pipeliningB persistent connection without pipeliningC nonpersistent connectionD not connection67. In HTTP request message, the entity body is empty with the method, but is used with the method.A GET, POSTB POST,GETC GET, HEAD D POST, HEAD68. In HTTP response message, if the Date: header ;one indicates the time Fri. 08 Aug. 2008 12:00:00 GMT, the Last-Modified: header line can not be .A Fri. 08 Aug. 2008 11:00:00 GMTB Fri. 08 Aug. 2008 11:30:00 GMTC Fri. 08 Aug. 2008 12:00:00 GMTD Fri. 08 Aug. 2008 12:30:00 GMT69. In the following four options, which one is not the part of cookie technologyA Cookie header lines in the HTTP response message and request message.B One cookie header file kept on the user’s end system and managed by the user’s browser.C A network entity that satisfies HTTP requests on the behalf of an origin Web server.D A back-end database at the Web site70. On-top of stateless HTTP, can be used to create a user session layer.A proxy serverB Web cacheC cookieD socket71. Processes communicate with each other by reading from and writing to .A programsB threadsC socketsD channels72. In the following four options about network architecture, which one is not correctA The network architecture is fixed.B The network architecture provides a specific set of services to application.C The network architecture is designed by application developer.D The network architecture dictates how the application is organized over special server.73. In Client-Server architecture, the clients visit the server’s through .A client’s socketB client’s IP addressC server’s socketD server’s IP address74. can be thought of as a program that is running within end system.A processB threadC socketD context75. API means .A Application Program InterfaceB Application Process InterfaceC Appellation Program InterfaceD Appellation Process Interface76. One host can be running many network applications, so the system assigns them differentto distinguish each other.A IP addressB port numberC hostnameD section77. In the following four applications, which one is both bandwith-sensitive and require tight timing constraintsA real-time audioB file transferC E-mailD Web documents78. The port number of the Web server is .A 25B 20C 80D 808079. The port number of the mail server is .A 25B 20C 80D 808080. Look the URL the object’s path name is .A B /rjxy/ D81. Each URL has components, they are .A transport protocol and object’s path nameB host name and object’s path nameC transport protocol and host nameD client name and server name1. Consider an HTTP client will request a WEB page from a WEB server. Suppose the URL of the page is /somedir/. The client does not want to use persistent connections and want to receive French version of the object. The user agent is Windows NT . Give the request message according to the given format.Request line:Header lines:2. Telnet into a Web server and send a multiline request message. Include in the request message the If-modified-since: header line to force a response message with the 304 Not Modified status code.Solution:Request line:Header lines:3. Suppose within you Web browser you click on a link to obtain a Web page. The IP address for the associated URL is not cached in your local host, so a DNS look-up is necessary to obtain the IP address. Suppose that n DNS servers are visited before your host receives the IP address from DNS; the successive visits incur an RTT of RTT1,…,RTT n. Further suppose that the Web page associated with the link contains exactly one object, consisting of a small HTML text. Let RTT0 denote the RTT between the local host and the server containing the object. Assuming zero transmission time of the object, how much time elapses from when the client clicks on the link until the client receives the object5. Suppose that you send an e-mail message whose only data is a microsoft excell attachment. What might the header lines (including MIME lines) look like。
计算机网络英文题库(附答案)chapter1

Chapter 1 Computer Networks and the Internet 1.The The ( ( ) ) is is is a a a worldwide worldwide worldwide computer computer computer network, network, network, that that that is, is, is, a a a network network network that that interconnects millions of computing devices throughout the world. ppt3 A public Internet B Intranet C switch net D television net 2.Which kind of media is not a guided media? ( ) A twisted-pair copper wire B a coaxial cable C fiber optics D digital satellite channel 3.Which kind of media is a guided media? ( ) A geostationary satellite B low-altitude satellite C fiber optics D wireless LAN 4.The units of data exchanged by a link-layer protocol are called ( ). A Frames B Segments C Datagrams D bit streams 5.Which of the following option belongs to the circuit-switched networks? ( ) A FDM B TDM C VC networks D both A and B 6.( )makes sure that that neither neither neither side side side of of of a a a connection overwhelms connection overwhelms the the other other side by sending too many packets too fast. A Reliable data transfer B Flow control C Congestion control D Handshaking procedure 7.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link. A Store-and-forward transmission B FDM C End-to-end connection D TDM 8.Datagram networks and virtual-circuit networks differ in that ( ). A datagram networks are circuit-switched networks, and virtual-circuit networks are packet-switched networks. B datagram networks are packet-switched networks, and virtual-circuit networks are circuit-switched networks. C datagram networks use destination addresses and virtual-circuit networks use VC. numbers to forward packets toward their destination. D datagram networks use VC. numbers and virtual-circuit networks use destination addresses to forward packets toward their destination. 9.In the following options, which one is not a guided media? ( ) A twisted-pair wire B fiber optics C coaxial cable D satellite 10.Processing delay does not include the time to ( ). A examine the packet ’s header B wait to transmit the packet onto the link C determine where to direct the packet D check bit-error in the packet 11.In the following four descriptions, which one is correct? ( ) A The traffic intensity must be greater than 1. B The fraction of lost packets increases as the traffic intensity decreases. C If the traffic intensity is close to zero, the average queuing delaywill be close to zero. D If the traffic intensity is close to one, the average queuing delay will be close to one. 12.The The Internet Internet Internet’’s s network network network layer layer layer is is is responsible responsible responsible for for for moving moving moving network-layer network-layer packets known as ( ) from one host to another. A frame B datagram C segment D message 13.The protocols of various layers are called ( ). A the protocol stack B TCP/IP C ISP D network protocol 14.There are two classes of packet-switched networks: ( ) networks and virtual-circuit networks. A datagram B circuit-switched C television D telephone 15.Access networks can be loosely classified into three categories: residential access, company access and ( ) access. A cabled B wireless C campus D city area Question 16~17 Suppose, a is the average rate at which packets arrive at the queue, R is the the transmission transmission transmission rate, rate, rate, and and and all all all packets packets packets consist consist consist of of L bits, bits, then then then the the the traffic traffic intensity is ( 16 ), and it should no greater than ( 17 ). 16. A LR /aB La /RC Ra /L D LR /a 17.A 2 B 1 C 0 D -1 18.In the Internet, the equivalent concept to end systems is ( ). A hosts B servers C clients D routers 19.In the Internet, end systems are connected together by ( ). A copper wire B coaxial cable C communication links D fiber optics 20.End systems access to the Internet through its ( ). A modems B protocols C ISP D sockets 21.End systems, packet switches, and other pieces of the Internet, run ( ) that control the sending and receiving of information within the Internet. A programs B processes C applications D protocols 22.There are many private networks, such as many corporate and government networks, whose hosts cannot exchange messages with hosts outside of the private network. These private networks are often referred to as ( ). A internets B LANC intranets D W AN 23.The internet allows ( ) running on its end systems to exchange data with each other. A clients applications B server applications C P2P applications D distributed applications 24.The Internet provides two services to its distributed applications: a connectionless unreliable service and () service. A flow control B connection-oriented reliable C congestion control D TCP 25.It defines the format and the order of messages exchanged between twoor more communicating entities, as well as the actions taken on the transmission and/or receipt of a message or other event. The sentence describes ( ). A Internet B protocol C intranet D network 26.In the following options, which does not define in protocol? ( ) A the format of messages exchanged between two or more communicating entities B the order of messages exchanged between two or more communicating entities C the actions taken on the transmission of a message or other evenD the transmission signals are digital signals or analog signals 27.In the following options, which is defined in protocol? ( ) A the actions taken on the transmission and/or receipt of a message oother event B the objects exchanged between communicating entities C the content in the exchanged messages D the location of the hosts 28.In the following options, which does not belong to the network edge( ) A end systems B routers C clients D servers 29.In the following options, which belongs to the network core? ( ) A end systems B routers C clients D servers 30.In the following options, which is not the bundled with the Internet ’s connection-oriented service? ( ) A reliable data transfer B guarantee of the transmission time C flow control D congestion-control 31.An application can rely on the connection to deliver all of its data without error and in the proper order. The sentence describes ( ). A flow control B congestion-control C reliable data transfer D connection-oriented service 32.It makes sure that neither side of a connection overwhelms the other side by sending too many packets too fast. The sentence describes ( ). A flow control B congestion-control C connection-oriented service D reliable data transfer 33.It helps prevent the Internet from entering a state of gridlock. When a packet switch becomes congested, its buffers can overflow and packet loss can occur. The sentence describes ( ). A flow control B congestion-control C connection-oriented service D reliable data transfer 34.The Internet ’s connection-oriented service has a name, it is ( ). A TCP B UDP C TCP/IP D IP 35.In In the the the following following following options, options, options, which which which service service service does does does not not not be be be provided provided provided to to to an an application by TCP?( ) A reliable transport B flow control C video conferencing D congestion control 36.The Internet ’s connectionless service is called ( ). A TCP B UDP C TCP/IP D IP 37.In the following options, which does not use TCP?( ) A SMTP B internet telephone C FTP D HTTP 38.In the following options, which does not use UDP?( ) A Internet phone B video conferencing C streaming multimedia D telnet 39.There are two fundamental approaches to building a network core, ( ) and packet switching. A electrical current switching B circuit switching C data switching D message switching 40.In ( ) networks, the resources needed along a path to provide for communication between the end system are reserved for the duration ofthe communication session. A packet-switched B data-switched C circuit-switched D message-switched 41.In ( ) networks, the resources are not reserved; a session’s messages use the resources on demand, and as a consequence, may have to wait for access to communication link. A packet-switched B data-switched C circuit-switched D message-switched 42.In a circuit-switched network, if each link has n circuits, for each link used by the end-to-end connection, the connection gets ( ) of the link link’’s bandwidth for the duration of the connection. A a fraction 1/n B all C 1/2 D n times 43.For ( ), the transmission rate of a circuit is equal to the frame rate multiplied by the number of bits in a slot. A CDMA B packet-switched network C TDM D FDM 44.( ) means that the switch must receive the entire packet before it canbegin to transmit the first bit of the packet onto the outbound link. A Queuing delay B Store-and-forward transmission C Packet loss D Propagation 45.The network that forwards packets according to host destination addresses is called ( ) network. A circuit-switched B packet-switched C virtual-circuit D datagram 46.The network that forwards packets according to virtual-circuit numbers is called ( ) network. A circuit-switched B packet-switched C virtual-circuit D datagram 47.In the following entries, which is not a kind of access network?( ) A residential access B company access C wireless access D local access 48.Suppose there is exactly one packet switch between a sending host and a receiving host. The transmission rates between the sending host and the switch and between the switch and the receiving host are R 1 and R 2, respectively. Assuming that the switch uses store-and-forward packet switching, what is the total end-to-end delay to send a packet of length L ? (Ignore queuing delay, propagation delay, and processing delay.) ( )A L /R 1+L /R 2 B L /R 1C L /R 2D none of the above 49.The time required to examine the packet ’s header and determine where to direct the packet is part of the ( ). A queuing delay B processing delay C propagation delay D transmission delay 50.The time required to propagate from the beginning of the link to the next router is ( ). A queuing delay B processing delay C propagation delay D transmission delay 51.Consider sending a packet of 3000bits over a path of 5 links. Each link transmits transmits at at at 1000bps. 1000bps. 1000bps. Queuing Queuing Queuing delays, delays, delays, propagation propagation propagation delay delay delay and and and processing processing delay are negligible. (6 points) (1).Suppose (1).Suppose the the the network network network is is is a a a packet-switched packet-switched packet-switched virtual virtual virtual circuit circuit circuit network. network. network. VC VC setup time is 0.1 seconds. Suppose the sending layers add a total of 500 bits of header to each packet. How long does it take to send the file from source to destination? (2).Suppose the the network network network is is is a a a packet-switched packet-switched datagram datagram network network network and and and a a connectionless connectionless service service service is is is used. used. used. Now Now Now suppose suppose suppose each each each packet packet packet has has has 200 200 200 bits bits bits of of header. How long does it take to send the file? (3).Suppose that the network is a circuit-switched network. Further suppose that that the the the transmission transmission transmission rate rate rate of of of the the the circuit circuit circuit between between between source source source and and and destination destination destination is is 200bps. Assuming 0.02s setup time and 200 bits of header appended to the packet, how long does it take to send the packet? Solution: (1). t=5*(3000+500)/1000+0.1=17.6s(2). t=5*(3000+200)/1000=16s(3). t=(3000+200)/200+0.02=16.02s。
期末考试复习计算机网络英文版

期末考试复习计算机网络英文版第一章计算机网络概述? Identify the five components of a data communications system. (数据通信系统5个组成部分:报文发送方接受方传输介质协议)message,sender,receiver,transmission medium and protocol. ? What are thethree criteria necessary for an effective and efficient network? performance, reliability,and security. ? What is an internet(互联网)?What is the Internet(因特网)? ★ An internet is an interconnection of networks which is a collection of networks connected by internetworking devices such as routers. ★ The Internet is the name of a specific worldwide network that uses the TCP/IP protocol suite and is the largest internet in the world. 第二章数据和信号? Which practical methods are used for analysis of a signal? And whichis suitable for network techniques? 研究电磁信号的方法是哪两种?适用于网络技术的?①Time domain and frequency domain ②frequencydomain ? Why can't any digital signal be transferred with no distortionin communication transmission?(数字信号为什么不能无失真传输?)1.Because to receive an exact replica of the digital signal, all of the frequency components must be faithfully through the transmission medium,if certain harmonic cannot transfer successful, the signal we receive willbe distorted. However, any medium transfers signals only within certain frequency ranges, that is, has a limited bandwidth. 2.Transmission impairments of signals (attenuation, distortion and noise) always exist,so signal errors unavoidable. ? What's the bandwidth(带宽)? Explainbriefly what correlation do bandwidth, data rate and cost have in communication process?带宽、数据率、成本之间的关系? The range of frequencies contained in a composite signal is its bandwidth. In networking, we use the term bandwidth in two contexts with two differentmeasuring values: Bandwidth in Hertz is the range of frequencies in a composite signal or the range of frequencies that a channel can pass, usually used to present the performance of analog channels and transmission media. (Another is) Bandwidth in bits per second is the speedof bit transmission in a channel,a link,or even a network, usually usedto present the performance of links and communication devices of a network.(课本P84) The greater the transmission bandwidth,the greater the data rate, and the higher the cost. ? Q3-3: How can a composite signalbe decomposed into its individual frequencies? 复位信号如何分解成单独的频率成分? If the composite signal is periodic, we can ues Fourier Series decompose it into a series of signals with discrete frequencies;if the composite signal is nonperiodic, we can ues Fourier Transform decompose it into a combination of sine waves with continuous frequencies. ? Q3-4: Name three types of transmission impairment. 三种传输减损? Attenuation, distortion,and noise. 衰减、失真和噪声 ?Q3-7: What does the Nyquist theorem have to do with communications? 奈奎斯特公式在通信中的作用? Estimate the channel capacity ofnoise-free digital channels, , when the channel is greater than the data rate transmitted on channel capacity, it will be failure due to severe distortion. ☆ The Nyquist theorem defines the theoretical maximum bit rate of a noiseless channel. ? Q3-8: What does the Shannon capacityhaveto do with communications? 香农容量原理在通信中的作用? Estimate the thermal noise interference channel capacity (theoretical upper limit), the data rate is higher, damage caused by noise will be more serious. ☆The Shannon capacity defines the theoretical highest data rate for noisy channel. 第三章传输介质? Briefly describe the main applications of three types of guided transmission media. 三种重要的有向传输介质的应用总的说:Twisted-pair cable is used for voice and data communications. Coaxialcable is used in cable TV networks and traditional Ethernet LANs. Fiber-optic cable is used in backbone networks, cable TV networks, and Fast Ethernet networks. 分别说: twisted-pair cable: 双绞线(广泛用于楼内布线) ed as telephone lines to provide voice and data channels – connecting subscribers to the central telephone office. ed as DSL (digital subscriber line) loop to provide high-data-rate Internet connection – the so called Family Broad Band. ed in LANs to provide high-data-rate baseband transmission (10 and 100 Mbps). coaxial cable: 同轴电缆(不用了,目前主要用于有线电视) 1.Was widely used in analog telephone networks (10000 voice signals) and in digital telephone networks (data rate up to 600 Mbps). However, it has largely been replaced with fiber-optic cable.2.Was widely used in cable TV networks However, cable TV providers replaced most of coax with fiber-optic cable.3.Was widely used in early traditional Ethernet LANs. However, it has been replaced with UTP which has data rate up to 100 Mbps. ☆ Now, mainly used for CATV fiber-optic cable: 光纤(广泛用于楼间布线和长途传输)widely used for wirings between buildings or long-distance transmission.such as: 1.High-speed backbone networks because its wide bandwidth is cost-effective. 2.Cable TV networks use usually a combination of optical fiber and coaxial cable. 3.Backbone channels in LANs, CANs and WANs4.Lightning-proof networks5.Secrecy networks against wiretapping ? What types of optical fiber transmission modes are there? Which of them is suitable for long distance transmission? Types:sigal mode and multimode, and the multimode include two types:Step-index and Graded-index. The sigal mode is suitable for long distance transmission. 第四章? What is Encoding? Why must encoding be used for data transmission?(1)【什么是编码?】Convert internal data of a sender into line signals suitable for transmission is called encoding.(2)【数据发送时为什么要编码?】1) Electromagnetic signals in information process devices are not allowed transmitting directly over communication lines.2) The signal type of a device differs from the signal type of a communication line. 3) The parameter requirements of device signals differs from the one of line signals. 4) Specific requirements in synchronization, efficiency , error control, etc..★ Because electromagnetic signals in information process devices are not allowed transmitting directly over communication lines, so encoding must be used for data transmission to converts internal data of a sender into line signals suitable for transmission.2.3.4.机内信号与线路类型不一样;机内信号参数与线路传输的要求不一样;同步、效率、纠错等方面的特殊要求? Which two techniques are used when analog data transmitted by digital signals?Which of them is the most important? Why?用数字信号传输模拟数据常用技术有哪两种?最常用的是?为什么?(1) Pulse Code Modulation(PCM) and Delta Modulation(DM). (2) Pulse Code Modulation(PCM) is the most important.(3) The principal advantage of DM over PCM is the simplicity of its implementation. In general, PCM exhibits better SNR characteristics at the same data rate.? What processes will be involved when analog data are digitized by PCM technique? 用PCM技术将模拟数据数字化时,要经过哪些处理步骤?Sampling (PAM)---->quantization---->binary encoding---->digital to digital coding ? Q4-1 List three techniques of digital-to-digital conversion. They are line coding,block coding and scrambling coding. ? Q4-4 Define baseline wandering and its effect on digital transmission.(1)In decoding a digital signal, the receiver calculates a running average of the received signal power. This average is called the baseline.(2)The incoming signal power is evaluated against this baseline to determine the value of the data element.(3)A long string of 0s or 1s can cause a drift in the baseline (baseline wandering) and make it difficult for the receiver to decode correctly. ? Q4-5 Define a DC component and its effect on digital transmission. (Define) When the voltage level in a digital signal is constant for a while, the specturm creates very low frequencies(results of Fourier analysis). These frequences around zero,called DC(derect-current) components, that present problems for a system that can not pass low frequencies or a system that uses electrical coupling.(Effect) DC component means 0/1 parity that can cause base-line wondering. 直流分量的影响不仅仅是基线偏移,还有更重要的原因。
《计算机网络》期末复习资料

家庭的外貌英语作文My Family's Appearance。
My family is a typical Chinese family with five members. My parents are both in their 50s, and they have three children. I am the youngest one, and my two elder sisters are both married and have their own families.My father is a tall and strong man with a round faceand a pair of big eyes. He has a full head of black hair, which is a little bit curly. He always wears a pair of glasses, which makes him look more intellectual. He likesto wear casual clothes, such as T-shirts and jeans, which are comfortable and easy to move in.My mother is a kind and gentle lady with a slim figure and a beautiful face. She has long black hair, which she always wears in a bun. She has a pair of big eyes, whichare always full of love and warmth. She likes to wear dresses and skirts, which make her look elegant andfeminine.My eldest sister is a tall and slim woman with a cheerful personality. She has a long face and a pair of bright eyes. She has short hair, which she likes to stylein different ways. She likes to wear fashionable clothes, such as high heels and tight dresses, which make her look sexy and confident.My second sister is a short and plump woman with a sweet smile. She has a round face and a pair of cute dimples. She has long hair, which she always wears in a ponytail. She likes to wear casual clothes, such as T-shirts and shorts, which are comfortable and easy to wear.As for me, I am a medium-sized girl with a lively personality. I have a round face and a pair of big eyes. I have long hair, which I like to wear in different styles. I like to wear comfortable clothes, such as T-shirts and jeans, which are easy to move in.In conclusion, my family members have differentappearances, but we all love each other and get along well. We are a happy and harmonious family.。
计算机网络英文题库(附答案)chapte4

计算机网络英文题库(附答案) chapter 41. What is the purpose of the Network Layer in the OSI Model?The Network Layer, also known as the fourth layer in the OSI Model, is responsible for the logical addressing and routing of data packets between different networks. Its purpose is to enable the transfer of data between devices that may be located on different networks.2. What are the main functions of the Network Layer?The Network Layer performs the following main functions:•Logical Addressing: The Network Layer assigns logical addresses to devices, allowing them to be uniquelyidentified on a network. This is done using protocols suchas IP (Internet Protocol).•Routing: The Network Layer determines the optimal path for data packets to be transmitted from thesource to the destination. It uses routing algorithms andprotocols to make routing decisions and manage networktraffic.•Packet Switching: The Network Layer breaks data into smaller packets and adds control information to eachpacket. These packets are then transmitted independently over the network and reassembled at the destination.•Congestion Control: The Network Layer is responsible for managing network congestion andpreventing network resources from becomingoverwhelmed. It uses techniques such as traffic shapingand packet prioritization to ensure efficient and reliabledata transmission.•Network Interoperability: The Network Layer enables different types of networks to interconnect andcommunicate with each other. It provides mechanisms to facilitate the exchange of data between networks withdifferent protocols and technologies.3. What is IP addressing?IP addressing refers to the assignment and use of unique logical addresses, called IP addresses, to devices connected to an IP network. IP addresses are used by the Network Layer to identify and locate devices on a network.An IP address is a 32-bit binary number, typically represented in a dotted decimal notation (e.g., 192.168.0.1). It consists of two parts: the network part and the host part. The network part identifies the specific network to which the device is connected, while the host part identifies the individual device on that network.There are two types of IP addresses: IPv4 (32-bit) and IPv6 (128-bit). IPv4 is the most widely used addressing scheme and provides approximately 4.3 billion unique addresses. IPv6 is the next generation IP addressing scheme, designed to address the limitations of IPv4 and provide a significantly larger address space.4. What is routing? How does it work?Routing is the process of determining the optimal path for data packets to be transmitted from the source to the destination across a network. It is a key function of the Network Layer.When a device wants to send data to a destination device, it determines the destina tion’s IP address. It then consults its routing table, which contains information about the network topology and available paths. The routing table helps the device identify the next hop, which is the next device that will receive the data packet and forward it towards the destination.The routing table is populated through various methods, such as static routing (manually configured routes) and dynamic routing (automatically updated routes based on routing protocols). Routing protocols, such as RIP (Routing Information Protocol) and OSPF (Open Shortest Path First), are used to exchange information between routers and ensure accurate routing decisions.Routers use routing algorithms and metrics to calculate the best path for data packets. These algorithms consider factors such as the number of hops, link speeds, and network congestion to determine the most efficient route. Once the next hop is determined, the data packet is forwarded to that device, and the process is repeated until the packet reaches its destination.5. What is packet switching? How does it differ from circuit switching?Packet switching is a method of data transmission in which data is divided into smaller packets and transmitted independently over a network. It is the primary mode of transmission used in modern computer networks, including the Internet.In packet switching, data is broken into packets, each containing a portion of the original data and control information. Each packet is then labeled with the source and destination IP addresses. These packets are transmitted individually over the network and can take different paths to reach the destination. At the destination, the packets are reassembled to reconstruct the original data.Packet switching differs from circuit switching, which was commonly used in traditional telephone networks. In circuit switching, a dedicated communication path, known as a circuit, is established between the source and destination for the duration of the communication session. The entire message is transmitted along this dedicated circuit, without being divided into smaller units. This approach requires the reservation of network resources for the entire duration of the communication, even if no data is being transmitted.Packet switching offers several advantages over circuit switching, including better resource utilization, improved network efficiency, and the ability to handle variable network conditions. It allows multiple devices to share the same network resources and adapt to changing traffic patterns. Additionally, packet switching enables the transmission ofdiverse data types, such as voice, video, and text, over the same network.ConclusionThe Network Layer plays a crucial role in computer networks by facilitating the logical addressing, routing, and interconnectivity of devices across networks. It provides essential functions such as IP addressing, routing, packet switching, congestion control, and network interoperability. Understanding the concepts and principles of the Network Layer is vital for effective network design, management, and troubleshooting.This chapter has covered the purpose of the Network Layer, its main functions, IP addressing, routing, and packet switching. By grasping these concepts, you are now well-equipped to navigate the complexities of computer networks and ensure efficient data transmission.Keep learning and exploring the fascinating world of computer networking!。
宁波大学计算机网络期末试卷(英文)

I.Choose the single correct answer from following choose. (1.5*20=30)[Correct checked:1.5; Other wise:0]1.Which physical media has high-speed operation and low error rate:A[] A.Fiber optic cable[] B.Coaxial cable[] C.Twisted pair[] D.Radio2.If no free buffers in router, the arriving packets will be: B[] A.dropped[] B.queued[] C.returned[] D.marked3.Which can provides delay measurement from source to router along end-end Internet path towards destination: A[] A.Ping[] B.Traceroute[] C.Ipconfig[] D.Nslookup4.In TCP/IP, which layer can make routing of datagrams from source to destination: C[] A.Applicaion[] B.Transport[] work[] D.Data Link5.Web page consists of ( ) which includes several referenced objects:A[] A.referenced HTML-file[] B.host HTML-file[] C.path HTML-file[] D.base HTML-file6.What is the default persistent model in HTTP/1.1:C[] A.Nonpersistent HTTP[] B.Persistent without pipelining[] C.Persistent with pipelining[] D.Nonpersistent with pipelining7.Web server maintains no information about past client requests, so HTTP is:B[] A.stateful[] B.stateless[] C.satisfied[] D.unsatisfied8.FTP client browses remote directory by sending commands over: D[] A.connection-less[] B.free connection[] C.data connection[] D.control connection9.Which can satisfy client request without involving origin server A[] A.Web caches[] B.Write caches[] C.TCP buffer[] D.Router buffer10.UDP socket identified by:B[] A.two-tuple (source IP address, source port number)[] B.two-tuple (dest IP address, dest port number)[] C.two-tuple (source IP address, dest port number)[] D.two-tuple (dest IP address, source port number)11.In GBN,when receiver receive a out-of-order packet,then discard and re-ACK the packet with:[] A. highest in-order sequence # A[] B. lowest in-order sequence #[] C. highest in-order port #[] D. lowest in-order port #12.In RDT Approachs, which is designed for performance: B[] A. checksum[] B. pipeline[] C. sequence #[] D. ACK or NAK13.Queued datagram at front of router’s queue prevents others in queue from moving forward is:A[] A.Head-of-the-Line (HOL) blocking[] B.Hops-of-the-Line (HOL) blocking[] C.Head-of-the-List (HOL) blocking[] D.Hops-of-the-List (HOL) blocking14.Wha t’s a network ? From IP address perspective they can physically reach each other without intervening router and the device interfaces with: C[] A. same IP address[] B. same TCP port #[] C. same network part of IP address[] D. same host part of IP address15. Large IP datagram divided (“fragmented”) within network,it will be reassembled:B[] A. only at last router[] B. only at final destination[] C. only at next router[] D. maybe at next router16.Which is not a common Intra-AS routing protocols:D[] A.RIP: Routing Information Protocol[] B.OSPF: Open Shortest Path First[] C.IGRP: Interior Gateway Routing Protocol[] D.ICMP: Interior Control Message Protocol17.Which is not a MAC Random Access protocol in Ethernet: D[] A.SCMA[] B.SCMA/CA[] C.SCMA/CD[] D.Slotted SCMA18.In DHCP client-server scenario, which message has DHCP-options field:D[] A. host broadcasts “DHCP discover”[] B. DHCP server responds with “DHCP offer”[] C. host requests IP address: “DHCP request”[] D. DHCP server sends a ddress: “DHCP ack”19.How to determine MAC address of host B, If knowing host B’s IP address?A[] A.ARP[] B.RARP[] C.RAP[] D.RIP20. Which device can break subnet into LAN segments: C[] A.IP mask[] B.NAT[] C.Router[] D.SwitchII.Choose the multiple correct answer from following choose. (2*10=20)[All correct checked:2; Part correct checked:1; No checked:0; Full checked:0]1.Which is the part of network structure: ABD[] work edge[] work core[] work user[] D.access networks2.How to connect end systems to edge router? BCD[] A.Microsoft access networks[] B.Residential access networks[] C.Institutional access networks[] D.Mobile access networks3.What kind of transport service does an application need? ABC[] A.Data loss[] B.Timing[] C.Bandwidth[] D.Security4.Electronic Mail three phases of transfer is: ABD[] A.handshaking (greeting)[] B.transfer of messages[] C.opens the 2nd TCP connection[] D.close5.In TCP Connection Management, initialize TCP variables include:AB[] A.sequence #[] B.buffers[] C.Sender MTU[] D.RcvWindow6.How does sender perceive congestion? AB[] A.timeout[] B.3 duplicate ACKs[] C.3 duplicate data[] D.slow start7.TCP Congestion Control use three mechanisms: ABC[] A.additive increase and multiplicative decrease[] B.slow start[] C.Conservative after timeout events[] D.additive decrease and multiplicative increase8.What are the Key Network-Layer Functions: ABC[] A.forwarding[] B.routing[] C.connection setup[] D.flow control9.Link Layer Services include: ABD[] A.Reliable delivery between adjacent nodes[] B.Flow Control between adjacent nodes[] C.Connection Manage[] D.Error Detection and Correction10.MAC Protocol’s taxonomy, three broad classes is: ABC[] A.Channel Partitioning[] B.Random Access[] C.Taking turns[] D.Peer-to-peerIII.Fill the blank from options. (1.5*16=24)1).The network protocols define format , order of message sent andreceived among network entities, and action taken on message transmission, receipt.(options: delay / format / policy / order / request / replay / actions taken / price / interface )2).InTCP Congestion Control, after 3 duplicate ACKs CongWin is cut in half and window then grows____linearly___. But after timeout event, CongWin instead set to 1 MSS , window then grows___exponentially____, when it up to a __threshold____ again, then grows linearly.(options: half / double / 1 MSS / 0 MSS / linearly / exponentially / threshold / top / bottom )3).Please fill the general format of Http request message:HTTP request message general format9.[Method] sp 10.[URL] sp 11.[version]12.[CR LP ]……13.[header field name ] : 14.[field value] 15. [Cr Lf ]16. [ Cr Lf ]Entity Body(options: header field name / URL / field value / version / method / Cr Lf/ 200 OK )IV.Question (26)1.As follow, LAN1 connect to LAN2 via a router:In session 1, Host A send a HTTP connection to WEB server D,if Host A initial TCP port 1025,Host D use TCP port 80;In session 2, Host A send a HTTP connection to WEB server B,if Host A initial TCP port 1026,Host B use TCP port 80;Session Step SourceMACDestinationMACSourceIPDestinationIPSourcePort#DestinationPort#Host A :1025 –> Host D:80 Host A –> ROUTER ROUTER–> Host DHost A :1026 –> Host B:80 Host A –> Host B2.Read and answer:(17)Two of the most important fields in the TCP segment header are the sequence number field and the acknowledgment number field. These fields are a critical part of TCP's reliable data transfer service. But before discussing how these fields are used to provide reliable data transfer, let us first explain what exactly TCP puts in these fields.TCP views data as an unstructured, but ordered, stream of bytes. TCP's use of sequence numbers reflects this view in that sequence numbers are over the stream of transmitted bytes and not over the series of transmitted segments. The sequencenumber for a segment is the byte-stream number of the first byte in the segment. Let's look at an example. Suppose that a process in host A wants to send a stream of data to a process in host B over a TCP connection. The TCP in host A will implicitly number each byte in the data stream. Suppose that the data stream consists of a file consisting of 500,000 bytes, that the MSS is 1,000 bytes, and that the first byte of the data stream is numbered zero. As shown in Figure 3.5-3, TCP constructs 500 segments out of the data stream. The first segment gets assigned sequence number 0, the second segment gets assigned sequence number 1000, the third segment gets assigned sequence number 2000, and so on.. Each sequence number is inserted in the sequence number field in the header of the appropriate TCP segment.Figure 3.5-3: Dividing file data into TCP segments.Now let us consider acknowledgment numbers. These are a little trickier than sequence numbers. Recall that TCP is full duplex, so that host A may be receiving data from host B while it sends data to host B (as part of the same TCP connection). Each of the segments that arrive from host B have a sequence number for the data flowing from B to A. The acknowledgment number that host A puts in its segment is sequence number of the next byte host A is expecting from host B. It is good to look at a few examples to understand what is going on here. Suppose that host A has received all bytes numbered 0 through 535 from B and suppose that it is about to send a segment to host B. In other words, host A is waiting for byte 536 and all the subsequent bytes in host B's data stream. So host A puts 536 in the acknowledgment number field of the segment it sends to B.As another example, suppose that host A has received one segment from host B containing bytes 0 through 535 and another segment containing bytes 900 through1,000. For some reason host A has not yet received bytes 536 through 899. In this example, host A is still waiting for byte 536 (and beyond) in order to recreate B's data stream. Thus, A's next segment to B will contain 536 in the acknowledgment number field. Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide cumulative acknowledgements.This last example also brings up an important but subtle issue. Host A received the third segment (bytes 900 through 1,000) before receiving the second segment (bytes 536 through 899). Thus, the third segment arrived out of order. The subtle issue is: What does a host do when it receives out of order segments in a TCP connection? Interestingly, the TCP RFCs do not impose any rules here, and leave the decision up to the people programming a TCP implementation. There are basically two choices: either (i) the receiver immediately discards out-of-order bytes; or (ii) the receiver keeps the out-of-order bytes and waits for the missing bytes to fill in the gaps. Clearly, the latter choice is more efficient in terms of network bandwidth, whereas the former choice significantly simplifies the TCP code. Throughout the remainder of this introductory discussion of TCP, we focus on the former implementation, that is, we assume that the TCP receiver discards out-of-order segments.In Figure 3.5.3 we assumed that the initial sequence number was zero. In truth, both sides of a TCP connection randomly choose an initial sequence number. This is done to minimize the possibility a segment that is still present in the network from an earlier, already-terminated connection between two hosts is mistaken for a valid segment in a later connection between these same two hosts (who also happen to be using the same port numbers as the old connection) .Question 1: Does TCP's use of sequence numbers over the series of transmitted segments? (3) Question 2: What does the sequence number for a segment means? For example. (4)Question 3: What does the acknowledgment number means, that host A puts in its segment to host B?(3)Question 4: How does TCPs to choose an initial sequence number? (3)Question 5: What does a host do when it receives out of order segments in a TCP connection? (4) (所有答案请填在答题卡上,答在试卷上的答案一律无效)。
计算机网络英文版复习

Transport Layer
❖Solution 2 -- P34
g)The threshold is set to half the value of the congestion window when packet loss is detected. When loss is detected during transmission round 22, the congestion windows size is 26. Hence the threshold is 13 during the 24th transmission round. i)The congestion window and threshold will be set to half the current value of the congestion window (8) when the loss occurred. Thus the new values of the threshold and window will be 4.
Transport Layer
❖Solution 2 -- P34
d)After the 22nd transmission round, segment loss is detected due to timeout, and hence the congestion window size is set to 1. e)The threshold is initially 32, since it is at this window size that slowtart stops and congestion avoidance begins. f)The threshold is set to half the value of the congestion window when packet loss is detected. When loss is detected during transmission round 16, the congestion windows size is 42. Hence the threshold is 21 during the 18th transmission round.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
. .word 资料. ..第一章 计算机网络概述第二章 数据和信号第三章传输介质第四章. .word资料. ....word 资料. ..● What is Encoding? Why must encoding be used for data transmission?(1)【什么是编码?】Convert internal data of a sender into line signals suitable for transmission is called encoding .(2)【数据发送时为什么要编码?】1) Electromagnetic signals in information process devices are not allowed transmitting directly over communication lines.2) The signal type of a device differs from the signal type of a communication line.3) The parameter requirements of device signals differs from the one of line signals.4) Specific requirements in synchronization, efficiency , error control, etc.. ★ Because electromagnetic signals in information process devices are not allowed transmitting directly over communication lines, so encoding must be used for data transmission to converts internal data of a sender into line signals suitable for transmission.2.3.4.机信号与线路类型不一样;机信号参数与线路传输的要求不一样;同步、效率、纠错等方面的特殊要求● Which two techniques are used when analog data transmitted by digital signals?Which of them is the most important? Why? 用数字信号传输模拟数据常用技术有哪两种?最常用的是?为什么?(1) Pulse Code Modulation(PCM) and Delta Modulation(DM). (2) Pulse Code Modulation(PCM) is the most important.(3) The principal advantage of DM over PCM is the simplicity of its implementation. In general, PCM exhibits better SNR characteristics at the same data rate.● What processes will be involved when analog data are digitized by PCMtechnique? 用PCM 技术将模拟数据数字化时,要经过哪些处理步骤?Sampling (PAM)---->quantization---->binary encoding ---->digital to digital coding ● Q4-1 List three techniques of digital-to-digital conversion. ● Q4-4 Define baseline wandering and its effect on digital transmission.(1)In decoding a digital signal, the receiver calculates a running average of the received signal power. This average is called the baseline.(2)The incoming signal power is evaluated against this baseline to determine the value of the data element. (3)A long string of 0s or 1s can cause a drift in the baseline (baseline wandering) and make it difficult for the receiver to decode correctly.● Q4-5 Define a DC component and its effect on digital transmission.(Define) When the voltage level in a digital signal is constant for a while, the specturm creates very low frequencies(results of Fourier analysis). These frequences around zero,called DC(derect-current) components , that present problems for a system that can not pass low frequencies or a system that uses electrical coupling. (Effect) DC component means 0/1 parity that can cause base-line wondering. 直流分量的影响不仅仅是基线偏移,还有更重要的原因。
看看教材和课件,或看看原书作业答案。
● Q4-9 Define scrambling and give its purpose.(Define) Scrambling is a way to avoid a long sequence of 0s in the original stream,Scrambling is a technique that does not increase the number of bits and does. .word 资料...第五章● Which modulation techniques are used in analog transmission? Which of themis the most susceptible to noise? Which of them is the mechanism commonly used in all modern modems. 1.Amplitude shift keying ( ASK) Frequency shift keying ( FSK ) Phase shift keying ( PSK)Quadrature Amplitude Modulation(QAM)2.The most susceptible to noise of the four digital-to-analog conversion techniques is ASK.3.The mechanism commonly used in all modern modems of them is QAM.● Q5-2 Define carrier signal and explain its role in analog transmission.(Define) A sender produces an analog signal as fundamental wave to carry digital signals. The fundamental wave is called carrier signal.(explain) Digital data are converted into modulated signals through changing one or more of three characteristics of a carrier signal: amplitude, frequency and phase.Most familiar application is for transmitting digital data through the public telephone network via a modem.(A carrier is a single-frequency signal that has one if its characteristic (amplitude, frequency, or phase) changed to represent the baseband signal.【In analog transmission, the sending device produces a high frequency analog signal that acts as a base for the information signals (data). The base signal is called the carrier signal. It is to represent the baseband signal.】) ● Q5-3 Definne digital-to-analog conversion.Digital-to-analog conversion is the process of changing one of the characteristics of an analog signal based on the information in digital data. It is also called modulation of a digital signal. The baseband digital signal representing the digital data modulations the carrier to create a broadband analog signal.● Q5-4 Which of characteristics of an analog signal are changed to represent thedigital signal in each of the following digital-analog conversions? a.ASK changes the amplitude of the carrier.b.FSK changes the frequency of the carrier.c.PSK changes the phase of the carrier.d.QAM changes both the amplitude and phase of the carrier.QAM is the most efficient of these options and is the mechanism commonly used in all modern modems.●Q5-5 Which of the four digital-to-analog conversion techniques(ASK,FSK,PSKor QAM) is the most susceptible to noise?Defend your answer.(Answer) The most susceptible to noise of the four digital-to-analog conversion techniques is ASK.(Define) Noise usually affects the amplitude; therefore, ASK is the modulation technique most affected by noise than phase or frequency.第六章●Which of the four multiplexing techniques is (are) suitable for analog channels?Which of them is (are) suitable for digital channels? (See P181 Questions Q6-3) Frequency-division and wavelength-division multiplexing are suitable foranalog channelsSynchronous time-division multiplexing and asynchronous time-divisionmultiplexing are suitable for digital channels.●Which of the four multiplexing techniques is (are) suitable for electricallinks? Which of them is (are) suitable for optical links?Frequency-division , Synchronous time-division and asynchronous time-division multiplexingare suitable forelectrical links .Wavelength-division multiplexing is suitable for optical links.光传输信道都属于模拟信道,而时分复用只适用于数字信道。
