STRATIX 工业交换机介绍
精选网络设备应用9交换机性能参数

1000Base-SX和1000Base-LX既可使用单模光纤, 也可使用多模光纤;
1000Base-ZX则只能使用单模光据转发单元的联系通 道;背板交换容量的大小直接决定了交换机的最大交换容 量,这是交换机交换性能的一个重要指标。
21
3.优先级设置 一旦网络可以区分电话通话和网上浏览,优先级处理就可
以确保进行Internet上大型下载的同时不中断电话通话。 为了确保准确的优先级处理,所有业务量都必须在网络骨 干内进行识别。在工作站终端进行的数据优先级处理可能 会因人为的差错或恶意的破坏而出现问题。黑客可以有意 地将普通数据标注为高优先级,窃取重要商业应用的带宽, 导致商业应用的失效。这种情况称为拒绝服务攻击。通过 分析进入网络的所有业务量,可以检查安全攻击,并且在 它们导致任何危害之前及时阻止。
(4)物理端口号码 与源IP地址类似,物理端口号码可以指 示哪个服务器正在发送数据。这种方法取决于交换机物理 端口和应用服务器的映射关系。虽然这是最简单的分类形 式,但是它依赖于直接与该交换机连接的服务器。
20
2.标注 在识别数据包之后,要对它进行标注,这样其他网络设备
才能方便地识别这种数据。由于分类可能非常复杂,因此 最好只进行一次。识别应用之后就必须对其数据包进行标 记处理,以便确保网络上的交换机或路由器可以对该应用 进行优先级处理。通过采纳标注数据的两种行业标准,即 IEEE 802.1p或差异化服务编码点(DSCP),就可以确保多 厂商网络设备能够对该业务进行优先级处理。 在选择交换机或路由器等产品时,一定要确保它可以识别 两种标记方案。虽然DSCP可以替换在局域网环境下主导 的标注方案IEEE 802.1p,但是与IEEE 802.1p相比,实施 DSCP有一定的局限性。在一定时期内,与IEEE 802.1p 设 备的兼容性将十分重要。作为一种过渡机制,应选择可以 从一种方案向另一种方案转换的交换机。
SIMATIC NET 工业以太网交换机 SCALANCE XC-200 操作说明说明书

SIMATIC NET工业以太网交换机SCALANCE XC-200操作说明02/2023法律资讯警告提示系统为了您的人身安全以及避免财产损失,必须注意本手册中的提示。
人身安全的提示用一个警告三角表示,仅与财产损失有关的提示不带警告三角。
警告提示根据危险等级由高到低如下表示。
危险表示如果不采取相应的小心措施,将会导致死亡或者严重的人身伤害。
警告表示如果不采取相应的小心措施,可能导致死亡或者严重的人身伤害。
小心表示如果不采取相应的小心措施,可能导致轻微的人身伤害。
注意表示如果不采取相应的小心措施,可能导致财产损失。
当出现多个危险等级的情况下,每次总是使用最高等级的警告提示。
如果在某个警告提示中带有警告可能导致人身伤害的警告三角,则可能在该警告提示中另外还附带有可能导致财产损失的警告。
合格的专业人员本文件所属的产品/系统只允许由符合各项工作要求的合格人员进行操作。
其操作必须遵照各自附带的文件说明,特别是其中的安全及警告提示。
由于具备相关培训及经验,合格人员可以察觉本产品/系统的风险,并避免可能的危险。
按规定使用 Siemens 产品请注意下列说明:警告Siemens 产品只允许用于目录和相关技术文件中规定的使用情况。
如果要使用其他公司的产品和组件,必须得到 Siemens 推荐和允许。
正确的运输、储存、组装、装配、安装、调试、操作和维护是产品安全、正常运行的前提。
必须保证允许的环境条件。
必须注意相关文件中的提示。
商标所有带有标记符号 ® 的都是 Siemens AG 的注册商标。
本印刷品中的其他符号可能是一些其他商标。
若第三方出于自身目的使用这些商标,将侵害其所有者的权利。
责任免除我们已对印刷品中所述内容与硬件和软件的一致性作过检查。
然而不排除存在偏差的可能性,因此我们不保证印刷品中所述内容与硬件和软件完全一致。
印刷品中的数据都按规定经过检测,必要的修正值包含在下一版本中。
Siemens AGDigital Industries Postfach 48 4890026 NÜRNBERG C79000-G8952-C442-14Ⓟ 02/2023 本公司保留更改的权利Copyright © Siemens AG 2016 - 2023.保留所有权利目录1简介 (7)2安全须知 (15)3安全建议 (17)4设备描述 (25)4.1产品总览 (25)4.2设备视图 (31)4.2.1SCALANCE XC206-2 (ST/BFOC) (31)4.2.2SCALANCE XC206-2 (SC) (32)4.2.3SCALANCE XC206-2G PoE (33)4.2.4SCALANCE XC206-2SFP (34)4.2.5SCALANCE XC208 (35)4.2.6SCALANCE XC208G PoE (36)4.2.7SCALANCE XC216 (37)4.2.8SCALANCE XC216-3G PoE (38)4.2.9SCALANCE XC216-4C (38)4.2.10SCALANCE XC224 (40)4.2.11SCALANCE XC224-4C (41)4.3附件 (41)4.4SELECT/SET 按钮 (47)4.5LED 指示灯 (49)4.5.1总览 (49)4.5.2“RM”LED (50)4.5.3“SB”LED (50)4.5.4“F”LED (50)4.5.5LED“DM1”和“DM2” (51)4.5.6LED“L1”和“L2” (51)4.5.7端口 LED (52)4.6C-PLUG (54)4.6.1C-PLUG 的功能 (54)4.6.2更换 C-PLUG (56)4.7组合端口 (57)4.8以太网供电 (PoE) (58)4.8.1符合标准的电源和电压范围 (58)4.8.2设备的 PoE 属性 (59)4.8.3电源传输和引脚分配 (30 W) (61)SCALANCE XC-200目录4.8.4电源传输和引脚分配 (60 W) (62)4.8.5组态 (62)5组装和拆卸 (63)5.1安装的安全注意事项 (63)5.2关于 SFP 收发器的一般说明 (66)5.3安装类型 (66)5.4在 DIN 导轨上安装 (67)5.4.1基于固定板的凹顶导轨安装 (67)5.4.2无固定板时的凹顶导轨安装 (69)5.5在标准 S7-300 导轨上安装 (70)5.5.1在带有固定板的标准导轨 S7-300 上安装 (70)5.5.2在不带固定板的标准导轨 S7-300 上安装 (71)5.6在标准导轨 S7-1500 上安装 (72)5.6.1在带有固定板的标准导轨 S7-1500 上安装 (72)5.6.2在不带固定板的标准导轨 S7-1500 上安装 (74)5.7基于固定板的墙式安装 (75)5.8更改固定销的位置 (76)5.9拆卸 (77)6连接 (79)6.1不使用 PoE 的设备的安全注意事项 (79)6.2PoE 设备的安全注意事项 (80)6.3有关在危险场所使用的安全注意事项 (82)6.4附加说明 (85)6.5接线规则 (86)6.624 V DC 电源 (87)6.754 V DC 电源 (88)6.8信号触点 (90)6.9功能性接地 (91)6.10串口 (92)6.11工业以太网 (94)6.11.1电气 (94)6.11.2光纤 (95)SCALANCE XC-200目录7维护和清洁 (97)8故障排除 (99)8.1使用 TFTP 下载新固件(无需 WBM 和 CLI) (99)8.2恢复出厂设置 (100)9技术规范 (101)9.1SCALANCE XC206-2 (ST/BFOC) 的技术规范 (101)9.2SCALANCE XC206-2 (SC) 的技术规范 (104)9.3SCALANCE XC206-2G PoE 的技术规范 (107)9.4SCALANCE XC206-2G PoE (54 V) 的技术规范 (110)9.5SCALANCE XC206-2G PoE EEC (54 V) 的技术规范 (113)9.6SCALANCE XC206-2SFP 的技术规范 (116)9.7SCALANCE XC206-2SFP G 的技术规范 (119)9.8SCALANCE XC206-2SFP EEC 的技术规范 (122)9.9SCALANCE XC206-2SFP G EEC 的技术规范 (125)9.10SCALANCE XC208 的技术规范 (128)9.11SCALANCE XC208G 的技术规范 (130)9.12SCALANCE XC208G PoE 的技术规范 (132)9.13SCALANCE XC208G PoE (54 V) 的技术规范 (134)9.14SCALANCE XC208EEC 的技术规范 (136)9.15SCALANCE XC208G EEC 的技术规范 (138)9.16SCALANCE XC216 的技术规范 (140)9.17SCALANCE XC216EEC 的技术规范 (142)9.18SCALANCE XC216-3G PoE 的技术规范 (144)9.19SCALANCE XC216-3G PoE (54 V) 的技术规范 (146)9.20SCALANCE XC216-4C 的技术规范 (150)9.21SCALANCE XC216-4C G 的技术规范 (153)9.22SCALANCE XC216-4C G EEC 的技术规范 (156)9.23SCALANCE XC224 的技术规范 (159)9.24SCALANCE XC224-4C G 的技术规范 (161)9.25SCALANCE XC224-4C G EEC 的技术规范 (164)9.26机械稳定性(运行时) (167)SCALANCE XC-200目录9.27射频辐射符合 NAMUR NE21 标准 (167)9.28电缆长度 (167)9.29交换特性 (168)10尺寸图 (171)11证书和认证 (179)索引 (189)SCALANCE XC-200简介1操作说明的用途这些操作说明适用于 SCALANCE XC-200 系列产品的安装和连接。
阿尔伦-布拉德利 Stratix 5700 工业 managed Ethernet 交换机说明书

Stratix 5700Industrial Managed Ethernet SwitchThe wide deployment of EtherNet/IP™ in industrial automation means that there is a growing demand to manage the network properly.Integtrating new machine-level networks into an existing plant network requires convergence.With more devices connected on the same Ethernet network than ever before, an industrial managed switch can help you simplify your network infrastructure. Adding a managed switch to your network architecture can also help make the process of adding new machines easier. The Allen-Bradley® Stratix 5700™ is a compact, scalable Layer 2 managed switch with embedded Cisco technology for use in applications with small isolated, to complex networks. With integration into Studio 5000 Automation Engineering and Design Environment™, you canleverage FactoryTalk® View faceplates and Add-on Profiles for simplified configuration and monitoring.By choosing a switch co-developed by Rockwell Automation and Cisco, your Operations Technology (OT) and Information Technology (IT) professionals leverage tools and technology that are familiar to them. This collaboration can also help to reduce configuration time and cost.Features and Benefits:Advanced Networking Features• Integrated Device Level Ring (DLR) connectivity helps optimize the network architecture and provide consolidated network diagnostics • Integrated Network Address Translation (NAT) provides 1:1 IP address mapping helping to reduce commissioning time • Power over Ethernet (PoE) versions provide power to devices over Ethernet minimizing cabling • Security features, including access control lists, help ensure that only authorized devices, users and traffic can access the network • Secure Digital (SD) card provides simplified device replacementOptimized integration:• Studio 5000® Add-on Profiles (AOPs) enable premier integration into the Rockwell Automation Integrated Architecture® system • Predefined Logix tags for monitoring and port control • FactoryTalk® View faceplates enable status monitoring and alarming • Built-in Cisco® Internet Operating System (IOS) helps provide secure integration with enterprise networkDesigned and Developed for EtherNet/IP Automation ApplicationsNetwork Address TranslationMachine integration onto a plant network architecture can be difficult as machine builder IP-address assignments rarely match the addresses of the end-user network. Also, network IP addresses are often unknown until the machine is being installed. The Stratix 5700 with Network Address Translation (NAT) is a Layer 2 implementation that provides “wire speed” 1:1 translations ideal for automation applications where performance is critical.NAT allows for:• Simplified integration of IP-addressmapping from a set of local,machine-level IP addresses to theend user’s broader plant network• OEMs to deliver standard machinesto end users without programmingunique IP addresses• End users to more simply integratethe machines into the larger network192.168.1.4192.168.1.4MACHINE 1MACHINE 2Private Network Private NetworkSwitch Reference ChartAllen-Bradley Stratix 5700 Industrial Ethernet SwitchSwitch Selection TableFE - Fast Ethernet GE - Gigabit EthernetPublication ENET-PP005F-EN-E – April 2016Copyright ©2016 Rockwell Automation, Inc. All Rights Reserved. Printed in USA.Supersedes Publication ENET-PP005E-EN-E – March 2015EtherNet/IP is a trademark of the ODVA.Cisco is a trademark of Cisco Systems, Inc.Allen-Bradley, CompactLogix, Factory Talk, Integrated Architecture, Kinetix, LISTEN. THINK. SOLVE., Powerflex, Rockwell Automation, Rockwell Software, Stratix 5700, Studio 5000, Studio 5000 Automation Engineering and Design Environment are trademarks of Rockwell Automation, Inc.Glossary of TermsAccess Control Lists allow you to filter network traffic. This can be used to selectively block types of traffic to provide traffic flow control or provide a basic level of security for accessing your network.CIP port control and fault detection allows for port access based on Logix controller program or controller mode (idle/fault). Allows secure access to the network based on machine conditions.CIP SYNC (IEEE1588) is the ODVAimplementation of the IEEE 1588 precision time protocol. This protocol allows very high precision clock synchronization across automation devices. CIP SYNC is an enabling technology for time-critical automation tasks such as accurate alarming for post-event diagnostics, precision motion and high precision first fault detection or sequence of events.Device Level Ring (DLR) allows direct connectivity to a resilient ring network at the device level.DHCP per port allows you to assign a specific IP address to each port, confirming that the device attached to a given port will get the same IP address. This feature allows for device replacement without having to manually configure IP addresses.Encryption provides network security by encrypting administrator traffic during Telnet and SNMP sessions.EtherChannel is a port trunking technology. EtherChannel allows grouping several physical Ethernet ports to create one logical Ethernet port. Should a link fail, the EtherChannel technology will automatically redistribute traffic across the remaining links.Ethernet/IP (CIP) interface enables premier integration to the Integrated Architecture with Studio 5000 AOP , Logix tags and View Faceplates.FlexLinks provides resiliency with a quick recovery time and load balancing on a redundant star network.IGMP Snooping (Internet Group Management Protocol) constrains the flooding of multicast traffic by dynamically configuring switch ports so that multicast traffic is forwarded only to ports associated with a particular IP multicast group.* Separate SW IOS requiredKey Software FeaturesMAC ID Port Security checks the MAC ID of devices connected to the switch to determine if it is authorized. If not the device is blocked and the controller receives a warning message. This provides a method to block unauthorized access to the network.Network Address Translation (NAT) provides 1:1 translations of IP addresses from one subnet to another. Can be used to integrate machines into an existing network architecture.Port Thresholds(Storm control & Traffic Shaping)allows you to set both incoming and outgoing traffic limits. If a threshold is exceeded alarms can be set in the Logix controller to alert an operator. Power over Ethernet (PoE) provides electrical power along with data on a single Ethernet cable to end devices.QoS – Quality of Service (QoS) is the ability to provide different priority to different applications, users, or data flows, to help provide a higher level of determinism on your network.REP (Resilient Ethernet Protocol) – A ring protocol that allows switches to be connected in a ring, ring segment or nested ring segments. REP provides network resiliency across switches with a rapid recovery time ideal for industrial automation applications.Smartports provide a set of configurations to optimize port settings for common devices like automation devices, switches, routers, PCs and wireless devices. Smartports can also be customized for specific needs.SNMP Simple Network Management Protocol (SNMP) is a management protocol typically used by IT to help monitor and configure network-attached devices.Static and InterVLAN Routing bridges the gap between layer 2 and layer 3 routing providing limited static and connected routes across VLANs.STP/RSTP/MST Spanning Tree Protocol, is a feature that provides a resilient path between switches. Used for applications that requires a fault tolerant network.VLANs with Trunking is a feature that allows you to group devices with a common set of requirements into network segments. VLANs can be used to provide scalability, security and management to your network.802.1x Security is an IEEE standard for access control and authentication. It can be used to track access to network resources and helps secure the network infrastructure.。
KORENIX JETNET 工业以太网交换机 产品应用手册

Industrial PoE Switch IP67/68 Ethernet Switch Rackmount Managed SwitchGigabit Switch Redundant Switch Entry-Level Switch Networking Computer Communication Computer Ethernet I/O ServerSerial Device Server Media Converter Multiport Serial Card SFP Module Din RailPower Supply工业以太网交换机煤矿是一种有效的能源,许多电厂采用这种低成本,高效的燃料来发电。
采矿作业正在配备先进的工业控制和传感设备来保障作业安全和高效生产。
在矿业应用中,可靠的网络对于广泛分布在各处的高带宽设备通讯是非常必要的。
一个位于波兰西里西亚地区的著名的煤矿,选用芯惠通JetNet 5010G 千兆网管型交换机用于数据传输,满足该项目可靠性和有效性要求。
JetNet 5010G 支持RSR(Rapid Super Ring)冗余网管功能,以及其它许多融合了尖端技术的软硬件功能,使其更加符合煤矿应用的严格要求。
最终确定选用JetNet 5010G 有多方面的原因,其一是它的灵活性。
JetNet 5010G 配备3个RJ-45/SFP combo 可选端口,可灵活的搭配不同的网络传输距离,支持从Cat-5线缆的100米到单模光口的70KM 。
JetNet 5010G 还支持RSR(Rapid Super Ring)快速冗余环网,自愈时间小于5ms ,以及千兆网络保障网络质量。
此外,他们还选用了Korenix 的串口设备联网服务器JetPort 5604i ,用于连接矿区各类串口设备(例如,传输带)。
使用Korenix 以太网产品搭建煤矿通讯网络,保障了煤矿开采操作的安全性和高效性。
AB交换机Stratix8000使用说明

工业以太网交换机Stratix TM 8000 动手实验目录STRATIX 8000_________________________________________________________________________3关于本动手实验_______________________________________________________________________3实验内容___________________________________________________________________________3实验设备____________________________________________________________________________3硬件______________________________________________________________________________3软件______________________________________________________________________________3恢复交换机的工厂默认设置______________________________________________________________4通过EXPRESS SETUP按钮恢复工厂默认设置_______________________________________________5运行E XPRESS S ETUP____________________________________________________________________6实验二: 理解设备管理器和SMARTPORTS___________________________________________________11获得诊断信息________________________________________________________________________11端口标识___________________________________________________________________________13端口号____________________________________________________________________________13端口状态指示灯不同颜色表示的意义:___________________________________________________13趋势图_____________________________________________________________________________14 S PANNING T REE P ROTOCOL (生产树协议)___________________________________________________18更改交换机的配置____________________________________________________________________19 E XPRESS S ETUP______________________________________________________________________21配置S MARTPORTS_____________________________________________________________________22测试S MARTPORT______________________________________________________________________23 Smartport错误检测__________________________________________________________________24实验三: 使用STRATIX 8000 RSLOGIX5000 AOI指令和 FACTORYTALK VIEW FACEPLATES_________27在RSL OGIX 5000中组态S TRATIX 8000_____________________________________________________27设置S TRATIX 8000A DD-ON 指令__________________________________________________________31使用S TRATIX 8000的F ACTORY T ALK V IEW F ACEPLATES_________________________________________39实验四: 设置端口镜像,使用WIRESHARK抓取数据包__________________________________________57通过W IRESHARK抓取数据包_____________________________________________________________57设定端口镜像________________________________________________________________________63设定端口镜像后抓取数据包_____________________________________________________________64Stratix 8000关于本动手实验本实验的目的是使您熟悉Stratix 8000交换机和组网的基本知识。
罗克韦尔自动化Stratix交换机常见问题解答

交换机 罗克韦尔自动化Stratix交换机常见问题解答常见问题解答1.工业现场布置以太网时对电缆有什么要求?在工业现场布置以太网时,可以使用屏蔽双绞线(STP)、非屏蔽双绞线(UTP)和光纤。
可以使用5类、5e、6类和6e的双绞线。
电缆的等级越高,它的性能就越好,所需的EMC保护就越少。
推荐100M时使用5e以上的双绞线,1000M推荐使用6类以上的双绞线。
使用光纤具有更强的噪音抗扰性,可以传输更长的距离。
2.双绞线和光纤的传输距离在常温(20度)下,交换机与网卡间的双绞线最大传输距离为100米,当线缆的温度上升时,信号就会衰减,导致传输距离变短;当电缆周围干扰比较大时,也会传输距离变短,因此实际安装时应该小于90米。
光纤可传输更长的距离,多模光纤在100M的速度下可以传输2km,多模光纤在1000M的速度下使用直径为50um的光纤可以传输550m,多模光纤在1000M的速度下使用直径为62.5um的光纤可以传输220m。
单模光纤可以传输距离为10km。
光纤的实际传输距离与光纤模块、光纤的类型和直径以及光纤安装时的弯曲半径有关。
下表是Stratix 系列光纤模块的传输距离3.以太网双绞线安装时应注意哪些事项?按照电磁兼容性(EMC)标准,网络通讯属于EMC-2,而交流电源、大功率输入输出以及运动驱动器与电机之间的电源线等属于EMC-1。
安装以太网双绞线时应注意以下基本原则。
a. 如果必须与电源线交叉,它们之间应该互相垂直;b.至少与高压外壳、或RF/微波发射源相隔1.5米;c.如果导体安装在一个金属导线槽或导管,1)导线槽或导管的每段接头处必须焊接以保证整个线路的导电连通性,2)入口点必须与外壳焊接在一起;d.适当的屏蔽(在需要的地方)并将其安放在配线管道中,使之与EMC-1导体隔开;e. 参考用户当地、国家以及国际关于电缆分组的标准。
不要将以太网电缆与下表所示的电缆离的太近。
电缆至少要保持的距离噪声源的强度通过电缆电压8.3 cm 小于20安培的EMC-1导体24 至10015 cm 大约20安培,低于100kVA的交流电源线101至20030 cm 高于100kVA的交流电源线201 至400g. 在导管或金属导向槽中安装UTP电缆时,请咨询电缆供应商确认是否影响电气性能;4.HUB、交换机、管理型交换机、三层交换机、路由器和网关有何区别?HUB:HUB或称集线器属于物理层的设备,HUB主要功能是对信号放大,HUB只识别数据包是0还是1,不识别其它内容,所有HUB连接在一起的设备属于一个冲突域,HUB连接的网络是一个共享式网络。
SIG中常用工业以太网交换机的产品参数整理

网管型工业以太网交换机 WISE6800系列6电口/2光口网管型工业以太网交换机·冗余自愈以太网(全负荷状态下恢复时间 <300 毫秒)·支持 QoS, IGMP snooping/GMRP, VLAN, LACP, RMON,port, Trunking ,snmp广播风暴抑制功能·产品的工作温度范围可达-35°C ~75°C概述:WISE6800卡轨式交换机具有2个上联冗余的10/100Mbit/s的双绞线光口,可以组成自愈环网,提高系统可靠性。
6个普通的10/100Base-T(X)的电口,具有自动协商功能。
WISE6800产品除了具有基于WEB网络管理系统外还可具有支持SNMP统一网管系统,对整个网络的交换机显现集中监控一.特点:a.高级工业联网能力:·即插即用,快速以太网环冗余技术(FAR-Ring,恢复时间<300ms)和RSTP(IEEE802.1W)能力·IGMP Snooping和GMRP用于过滤工业以太网协议中的多播流量·支持基于端口的VLAN、IEEE802.1Q VLAN和GVRP协议,使网络规划简单易行·支持802.3ad,LACP及Port Trunking ,最大化带宽利用·支持Qos---IEEE 802.1p/1Q和TOS/DiffServ,增加决定权·Port Trunking用于优化带宽利用·RMON功能提供有效的监视和预测能力·SNMP V1/V2C/V3适用不同安全级别的网络管理·支持IEEE802.1X和SSL,增强网络的安全性·支持SNMP网管协议,通过统一网管软件对交换机进行监控和管理b.针对工业应用的设计:·带宽管理能够预防不可预计的网络意外状况·端口锁定只允许授权MAC地址访问网络·端口镜像功能可用于在线调试·通过继电器输出可实现自动报警功能·数字输入接口可将传感器和警报与IP网络结合为一体·在线连接快速恢复(专利申请中)·冗余双直流电源输入·-35至75°C操作温度范围·长距离传输40km或者80 km·IP 40防护等级,波纹式高强度铝制外壳·DIN-Rail导轨安装·可通过Web浏览器,Telnet/Serial控制口,Windows组件进行配置·发送Ping命令以判断网络的连通性二.规格a.技术:b.接口:c.光纤:d.电源:e.机械性能:f.工作环境:g.通过认证:订购信息:LEC-3200LEC3200 19’@2U嵌入式通讯管理机Inte Atom N270嵌入工业控制器,带5×LAN,18×COM,1×DVI-I特点∙板载Atom N270 1.6GHz CPU∙最大支持到2G DDR2∙DVI-I显示,通过转换接头支持VGA显示∙电磁隔离保护∙5×LAN,10/100/1000Base-T RJ-45功能∙18×RS-232/422/485∙PCI-104插槽,4×USB 2.0∙交直流电源,开关控制,电源及IDE指示灯状态显示∙支持 Windows XP Embedded及Linux解决方案∙无风扇设计LEC-3200是一款针对产业应用所开发的高性能嵌入式工控机。
交换机基础知识

交换机基础知识交换机的基本概念:交换机的英文名称为Switch,也称为交换式集线器,是一种基于MAC地址识别,能完成封装转发数据包功能的网络设备。
交换机可以学习MAC地址,并把其存放在内部地址表中,通过在数据帧的始发者与目标接受者之间建立临时的交换路径,使数据帧直接由源头到达目的地址。
交换机的工作特点:拥有一条很高带宽的背板总线和内部交换矩阵。
所有的端口都挂接在这条背板总线上。
控制电路收到数据包以后,处理端口会查找内存中的地址对照表以确定目的MAC地址的网卡(NIC)挂接在哪个端口上,通过内部交换矩阵迅速将数据包传送到目的端口。
目的MAC不存在才会广播到所有端口,接收端口回应后交换机会学习新的地址,并把它添加入内部MAC地址表中。
交换机的特性:与网桥和集线器相比,交换机从以下几个方面改进了性能1.通过支持并行通信,提高了交换机的信息吞吐量。
2.将传统的一个大局域网上的用户分成若干工作组,每个端口连接一台设备或连接一个工作组,有效的解决拥挤现象。
3.虚拟网(Virtual LAN)技术的出现,给交换机的使用和管理带来了更大的灵活性。
4.端口密度可以与集线器相媲美,一般的网络系统都是有一个或几个服务器,而绝大部门都是普通的客户机。
客户机都需要访问服务器,这样就导致服务器的通信和事务处理能力成为整个网络性能好坏的关键。
交换机的三个主要功能:1.学习以太网交换机了解每一个端口相连设备的MAC地址,并将地址同相应的端口映射起来存放在交换机缓存中的MAC地址表中。
2.转发/过滤当一个数据帧的目的地址在MAC地址表中有映射时,它被转发到连接目的节点的端口而不是所有端口(如该数据帧为广播/组播则转发至所有端口)3.消除回路当交换机包括一个冗余回路时,以太网交换机通过生成树协议避免冗余回路的产生,同时允许存在后备路径。
交换机的交换模式概念:交换机将数据从一个端口转发至另一个端口的处理方式成为交换模式类型:存储转发(Store and Forward)特点:交换机接收到数据包后,首先将数据包存储到缓冲器中,进行CRC循环冗余校验,如果这个数据包有CRC错误,则该包将被丢弃;如果数据包完整,交换机查询地址映射表将其转发至相应的端口优点:没有残缺数据包转发,可减少潜在的不必要的数据转发缺点:转发速率比直接转发方式慢。
希尔施曼 GRS1030-16T9SMMV9HHSE2S04.1 工业以太网交换机数据表说明书
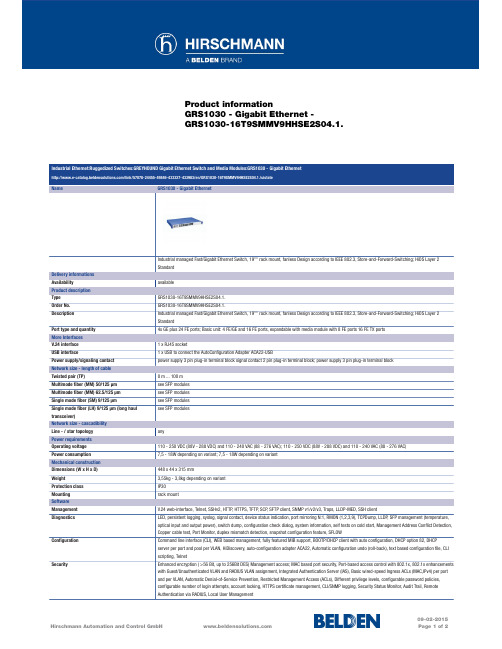
Product informationGRS1030 - Gigabit Ethernet -GRS1030-16T9SMMV9HHSE2S04.1.Industrial Ethernet:Ruggedized Switches:GREYHOUND Gigabit Ethernet Switch and Media Modules:GRS1030 - Gigabit Ethernet/link/57078-24455-49846-433327-433983/en/GRS1030-16T9SMMV9HHSE2S04.1./uistateName GRS1030 - Gigabit EthernetIndustrial managed Fast/Gigabit Ethernet Switch, 19"" rack mount, fanless Design according to IEEE 802.3, Store-and-Forward-Switching; HiOS Layer 2StandardDelivery informationsAvailability availableProduct descriptionType GRS1030-16T9SMMV9HHSE2S04.1.Order No.GRS1030-16T9SMMV9HHSE2S04.1.Description Industrial managed Fast/Gigabit Ethernet Switch, 19"" rack mount, fanless Design according to IEEE 802.3, Store-and-Forward-Switching; HiOS Layer 2StandardPort type and quantity4x GE plus 24 FE ports; Basic unit: 4 FE/GE and 16 FE ports, expandable with media module with 8 FE ports 16 FE TX portsMore InterfacesV.24 interface 1 x RJ45 socketUSB interface 1 x USB to connect the AutoConfiguration Adapter ACA22-USBPower supply/signaling contact power supply 3 pin plug-in terminal block signal contact 2 pin plug-in terminal block; power supply 3 pin plug-in terminal blockNetwork size - length of cableTwisted pair (TP)0 m ... 100 mMultimode fiber (MM) 50/125 µm see SFP modulesMultimode fiber (MM) 62.5/125 µm see SFP modulesSingle mode fiber (SM) 9/125 µm see SFP modulesSingle mode fiber (LH) 9/125 µm (long haulsee SFP modulestransceiver)Network size - cascadibilityLine - / star topology anyPower requirementsOperating voltage110 - 250 VDC (88V - 288 VDC) and 110 - 240 VAC (88 - 276 VAC); 110 - 250 VDC (88V - 288 VDC) and 110 - 240 VAC (88 - 276 VAC)Power consumption7,5 - 18W depending on variant; 7,5 - 18W depending on variantMechanical constructionDimensions (W x H x D)448 x 44 x 315 mmWeight3,55kg - 3,8kg depending on variantProtection class IP30Mounting rack mountSoftwareManagement V.24 web-interface, Telnet, SSHv2, HTTP, HTTPS, TFTP, SCP, SFTP client, SNMP v1/v2/v3, Traps, LLDP-MED, SSH clientDiagnostics LED, persistent logging, syslog, signal contact, device status indication, port mirroring N:1, RMON (1,2,3,9), TCPDump, LLDP, SFP management (temperature,optical input and output power), switch dump, configuration check dialog, system information, self tests on cold start, Management Address Conflict Detection,Copper cable test, Port Monitor, duplex mismatch detection, snapshot configuration feature, SFLOWConfiguration Command line interface (CLI), WEB based management, fully featured MIB support, BOOTP/DHCP client with auto configuration, DHCP option 82, DHCPserver per port and pool per VLAN, HiDiscovery, auto-configuration adapter ACA22, Automatic configuration undo (roll-back), text based configuration file, CLIscripting, TelnetSecurity Enhanced encryption ( >56 Bit, up to 256Bit DES) Management access; MAC based port security, Port-based access control with 802.1x, 802.1x enhancementswith Guest/Unauthenticated VLAN and RADIUS VLAN assignment, Integrated Authentication Server (IAS), Basic wired-speed Ingress ACLs (MAC,IPv4) per portand per VLAN, Automatic Denial-of-Service Prevention, Restricted Management Access (ACLs), Different privilege levels, configurable password policies,configurable number of login attempts, account locking, HTTPS certificate management, CLI/SNMP logging, Security Status Monitor, Audit Trail, RemoteAuthentication via RADIUS, Local User ManagementFor more information please contact:Hirschmann Automation and Control GmbHStuttgarter Strasse 45-5172654 NeckartenzlingenGermanyPhone: +49 7127/14-1809E-Mail:*********************The information published in the websites has been compiled as carefully as possible. It is subject to alteration without notice in technical as well as in price-related/commercial respect. The complete information and data were available on user documentation. Mandatory information can only be obtained by a concrete query.。
交换机的性能参数和使用选型概述

交换机的性能参数和使用选型概述1. 引言交换机是计算机网络中的核心设备,用于将数据包从一个网络连接传递到另一个网络连接。
它具有决定网络数据流向的作用,因此交换机的性能参数和使用选型对网络性能和可靠性起着重要的作用。
本文将介绍交换机的性能参数和使用选型概述,以便读者在购买和使用交换机时做出明智的决策。
2. 交换机的性能参数2.1 交换速率交换速率是交换机的一个重要性能参数,表示交换机在单位时间内能处理的数据量。
通常以比特每秒(bit/s)或兆比特每秒(Mbps)来度量。
交换速率越高,交换机处理数据的能力越强。
在选择交换机时,需根据网络负载和带宽需求来确定所需的交换速率。
2.2 潜时潜时是指交换机处理数据包所需的时间。
它包括输入端口潜时、交换潜时和输出端口潜时。
输入端口潜时是指数据包从输入端口到达交换机内部的时间,交换潜时是指交换机完成核心处理所需的时间,输出端口潜时是指数据包从交换机输出端口到达目标设备的时间。
较低的潜时意味着交换机能够更快地处理数据包,提高网络性能和响应速度。
2.3 缓存大小交换机通常具有缓存,用于暂存数据包。
缓存大小决定了交换机能够同时处理的数据包数量。
较大的缓存大小可以增加交换机的吞吐量,提高网络的拥塞控制能力。
在选择交换机时,需根据网络负载和数据包数量来确定所需的缓存大小。
2.4 端口数量交换机的端口数量表示交换机可以连接的设备数量。
较大的端口数量可以支持更多的设备连接,增加网络的可扩展性。
在选择交换机时,需根据网络规模和设备数量来确定所需的端口数量。
3. 交换机的使用选型概述在选择交换机时,除了考虑交换机的性能参数外,还需考虑其他因素,以满足网络需求和预算限制。
3.1 端口类型交换机通常支持不同类型的端口,如千兆以太网端口(Gigabit Ethernet)和万兆以太网端口(10 Gigabit Ethernet)。
根据设备需求和网络带宽,选择适当的端口类型。
3.2 管理型和非管理型交换机管理型交换机具有更多的功能和配置选项,可以通过网络管理软件进行配置和监控。
Stratix 系列交换机和网络设备说明书
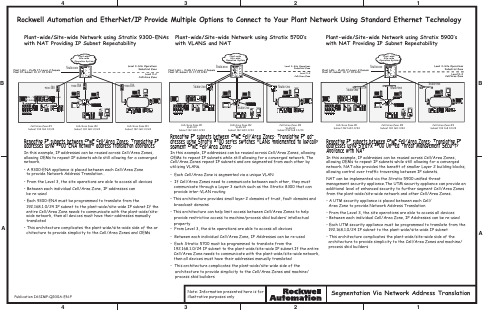
Plant LAN - VLAN 17-Layer 2 Domain Plant IP-Subnet 10.17.10.0/24Segmentation Via Network Address Translation21342134ABBACell/Area Zone #1Subnet 192 168 1.0/24Cell/Area Zone #2Subnet 192 168 1.0/24Cell/Area Zone #3Subnet 192 168 1.0/24Stratix 57009300-ENAStratix 5700Stratix 5900Stratix 5900Stratix 5900Cell/Area Zone #1Subnet 192 168 1.0/24Cell/Area Zone #2Subnet 192 168 1.024Cell/Area Zone #3Subnet 192 168 1.0/24Plant-wide/Site-wide Network using Stratix 9300-ENAs with NAT Providing IP Subnet RepeatabilityPlant-wide/Site-wide Network using Stratix 5900’s with NAT Providing IP Subnet RepeatabilityPlant-wide/Site-wide Network using Stratix 5700’swith VLANS and NAT 9300-ENA9300-ENAStratix 8300Plant-wideSite-wide Operation SystemLevel 3-Site OperationsIndustrial ZoneLevel 0-2Cell/Area ZoneLevel 3-Site OperationsIndustrial ZoneLevel 0-2Cell/Area ZoneLevel 3-Site OperationsIndustrial ZoneLevel 0-2Cell/Area ZoneStratix 8300Plant-wide Site-wide Operation SystemStratix 5700Stratix 5700Stratix 5700Stratix 8300Plant-wide Site-wide Operation SystemRockwell Automation and EtherNet/IP Provide Multiple Options to Connect to Your Plant Network Using Standard Ethernet TechnologyNote: Information presented here is for illustrative purposes onlyPlant LAN - VLAN 17-Layer 2 Domain Plant IP-Subnet 10.17.10.0/24Plant LAN - VLAN 17-Layer 2 Domain Plant IP-Subnet 10.17.10.0/24Cell/Area Zone #1VLAN 10Subnet 192 168 1.0/24Cell/Area Zone #2VLAN 20Subnet 192 168 1.0/24Cell/Area Zone #3VLAN30Subnet 192 168 1.0/24Plant LAN - VLAN 17-Layer 2 Domain Plant IP-Subnet 10.17.10.0/24Repeating IP subnets between CPwE Cell/Area Zones. Translating IP addresses using 9300-ENA network address translation appliances In this example, IP addresses can be reused across Cell/Area Zones, allowing OEMs to repeat IP subnets while still allowing for a converged network.• A 9300-ENA appliance is placed between each Cell/Area Zone to provide Network Address Translation .• From the Level 3, the site operations are able to access all devices • Between each individual Cell/Area Zone, IP addresses can be re-used• Each 9300-ENA must be programmed to translate from the192.168.1.0/24 IP subnet to the plant-wide/site-wide IP subnet.If the entire Cell/Area Zone needs to communicate with the plant-wide/site- wide network, then all devices must have their addresses manually translated• This architecture complicates the plant-wide/site-wide side of the ar chitecture to provide simplicity to the Cell/Area Zones and OEMsRepeating IP subnets between CPwE Cell/Area Zones. Translating IP addresses using Stratix 5900 Unified Threat Management Security Appliance with NATIn this example, IP addresses can be reused across Cell/Area Zones, allowing OEMs to repeat IP subnets while still allowing for a converged network. NAT also provides the benefit of smaller Layer 2 building blocks, allowing control over traffic traversing between IP subnets.NAT can be implemented via the Stratix 5900 unified threatmanagement security appliance.The UTM security appliance can provide an additional level of enhanced security to further segment Cell/Area Zones from the plant-wide/site-wide network and other Cell/Area Zones.• A UTM security appliance is placed between each Cell/ Area Zone to provide Network Address Translation• From the Level 3, the site operations are able to access all devices • Between each individual Cell/Area Zone, IP Addresses can be re-used • Each UTM security appliance must be programmed to translate from the 192.168.1.0/24 IP subnet to the plant-wide/site-wide IP subnet • This architecture complicates the plant-wide/site-wide side of the architecture to provide simplicity to the Cell/Area Zones and machine/ process skid buildersRepeating IP subnets between CPwE Cell/Area Zones. Translating IP ad-dresses using Stratix 5700 series switches VLANs implemented to logically segment CPwE Cell/Area Zones.In this example, IP addresses can be reused across Cell/Area Zones, allowing OEMs to repeat IP subnets while still allowing for a converged network. The Cell/Area Zones repeat IP subnets and are segmented from each other by utilizing VLANs.• Each Cell/Area Zone is segmented via a unique VLAN• If Cell/Area Zones need to communicate between each other, they must communicate through a Layer 3 switch such as the Stratix 8300 that can provide inter-VLAN routing• This architecture provides small layer 2 domains of trust, fault domains and broadcast domains• This architecture can help limit access between Cell/Area Zones to help provide restrictive access to machine/process skid builders’ intellectual property• From Level 3, the site operations are able to access all devices • Between each individual Cell/Area Zone, IP Addresses can be re-used • Each Stratix 5700 must be programmed to translate from the192.168.1.0/24 IP subnet to the plant-wide/site-wide IP subnet.If the entire Cell/Area Zone needs to communicate with the plant-wide/site-wide network, then all devices must have their addresses manually translated• This architecture complicates the plant-wide/site-wide side of the architecture to provide simplicity to the Cell/Area Zones and machine/ process skid buildersPublication IASIMP-QR30A-EN-PAbout the ProductsStratix 5700• Scalable Layer 2 managed industrial switch• Default configurations for industrial autom ation and EtherNet/IP devices (Global and Smartports)• Studio 5000 for configuration via Add on Profiles/Predefined Logix tags for diagnostics • FactoryTalk View Faceplates for status monitoring and alarming • Best of Cisco - Catalyst® switch architecture/ feature setStratix 8300• Full Layer 3 industrial switch that supports routing between Subnets and VLANs.• Default configurations for industrial automation and EtherNet/IP devices (Global and Smartports)• Studio 5000 for configuration via Add on Profiles/Predefined Logix tags for diagnostics • FactoryTalk View Faceplates for status monitoring and alarming • Best of Cisco - Catalyst® switch architecture/ feature setStratix 5900• Combines a number of modern security functions into a single appliance• Managed router that also provides a number of managed switching features • A single device to implement VPN, Firewall, NAT, and many other services • Best of Cisco - Fully integrated with Cisco IOS9300-ENA• NAT Appliance allowing identical machines to be placed on Ethernet networksAbout this ConfigurationThis system consists of three Cell/Area Zones, each with different hardware and potentially from three unique OEMs who would like to protect their Intellectual Property (IP). It illustrates different techniques to accomplish the following: 1. Protect intellectual property of machine/process skid builders 2. Provide small Layer 2 domains of trust and broadcast domains3. Provide logical Layer 2 building blocks to ensure a future-ready network4. Enable Network Address Translation on a plant-wide/site-wide network to provide IP subnet repeatability at the Cell/Area Zone level, providing faster commissioning time for machine/ process skid buildersSummary of Considerations for Segmentation MethodologiesAdditional ResourcesENET-PP005C-EN-E Stratix 5700 Industrial Ethernet Switch Product ProfileENET-PP002B-EN-P Stratix 8000 and 8300 Industrial Ethernet Switches Product Profile ENET-PP006A-EN-P Stratix 5900 Services Router Product ProfileENET-AT004B-EN-ESegmentation Methods within the Cell / Area ZoneIASIMP-QS038A-EN-PStratix 5700 NAT Quick StartENET-WP032A-EN-E Stratix 5700 NAT WhitepaperENET-QR001-EN-E Stratix Switch Reference Chart ENET-QR002-EN-EStratix 5700 Reference ChartGMSP-PP001-EN-E 9300-ENA Network Address Translation Device Product ProfileIASIMP-QR029A-EN-PStratix/Infrastructure Product Family Quick Reference DrawingENET-TD001-EN-PConverged Plantwide Ethernet (CPwE) Design and Implementation Guide (DIG)Reference Architecture Web Page/rockwellautomation/products-technologies/network-technology/architectures.pageBill of MaterialQty Catalog # Description System: Communication Hardware1 1783-BMS10CL Stratix 5700 Layer2 Managed Switch, 10 Ports Lite1 1783-BMS10CGN Stratix 5700 Layer2 Managed Switch, 10 Ports,Full with CIP Synch and NAT 1 1783-RMS10T Stratix 8300 Layer3 Managed Switch, 10 Ports 1 1783-MS10T Stratix 8000 Layer 2 Managed Switch, 10 Ports 1 1783-SR Stratix 5900 Security Appliance1 9300-ENA Network Address Translation ApplianceSegmentation Techniques Positive Design Considerations Negative Design ConsiderationsNo Segmentation (Not Recommended)• Initially, may appear to be simple to design anddeploy• Link Resiliency (redundant path topologies)• Same Layer 2 broadcast andfault domain, not a scalable or future ready solution.• Every node requires a unique IP address • Blurred demarcation line of network ownershipMultiple NIC Segmentation (ControlLogix Only)• Simple to design and deploy• Smaller Layer 2 domains (broadcast and fault)• Reusable IP addresses/subnets• Clear demarcation of network ownership• Not scalable or future ready, only CIP traffic can traverse a CIP bridge, limited quantity of bridge modules.• Smaller PACs do not support a dual NIC.• No Link Resiliency (redundant path topologies)NAT Appliance Segmentation 9300-ENA• Smaller Layer 2 domains (broadcast and fault)• Reusable IP addresses/subnets • Clear demarcation of network ownership• More difficult to design, deploy,and manage-manual entry and management of IP address translations• No Link resiliency (redundant path topologies)Unified Threat Management Security Appliance with NAT Stratix 5900• Smaller Layer 2 domains (broadcast and fault)• Reusable IP addresses/subnets • Clear demarcation of network ownership• Enhanced security features• More difficult to design, deploy, and manage-manual entry andmanagement of IP address translations • No Link resiliency (redundant path topologies)VLANs Only Segmentation Stratix 5700• Scalable and future ready• Smaller Layer 2 domains (broadcast and fault)• Smaller domains of trust (management of security policies)• Link Resiliency (redundant path configuration)• Layer 3 switch or router is required to forward (route) information between VLANs• Every node requires a unique IP address • Blurred demarcation line of network ownershipVLAN Segmentation with NAT Stratix 5700• Scalable and future ready• Smaller Layer 2 domains (broadcast and fault)• Smaller domains of trust (management of security policies)• Reusable IP addresses/subnets • Link Resiliency (redundant path configuration• Layer 3 switch or router is required to forward (route) information between VLANs• More difficult to design, deploy, andmanage-manual entry and management of IP address translations• Blurred demarcation line of network ownershipPlant LAN - VLAN 17-Layer 2 Domain Plant IP-Subnet 10.17.10.0/24,every device requires a unique IP addressPlant LAN - VLAN 17-Layer 2 Domain Plant IP-Subnet 10.17.10.0/24Segmentation Via VLANs21342134ABBACell/Area Zone #1VLAN 10Subnet 192 168 1.0/24Cell/Area Zone #2VLAN 20Subnet 192 168 1.0/24Cell/Area Zone #3VLAN30Subnet 192 168 1.0/24Level 3-Site OperationsIndustrial ZoneLevel 0-2Cell/Area ZoneStratix 5700Stratix 5700Stratix 5700FAULTFWD SelEsc 525FAULTFWD SelEsc 525Stratix 8300Plant-wide Site-wide Operation SystemCell/Area Zone #1VLAN 10Subnet 10.10.10.0/24Cell/Area Zone #2VLAN 20Subnet 10.10.20.0/24Cell/Area Zone #3VLAN 30Subnet 10.10.30.0/24Plant-wide/Site-wide Network using Stratix 5700’s with VLANs and Unique IP SubnetsPlant-wide/Site-wide Network using Stratix 5700’s with VLANs and NATLevel 3-Site OperationsIndustrial ZoneLevel 0-2Cell/Area ZoneStratix 5700Stratix 5700Stratix 5700FAULT FWD SelEsc 525FAULT FWD Sel Esc 525Stratix 8300Plant-wide Site-wide Operation SystemRockwell Automation and EtherNet/IP Provide Multiple Options to Connect to Your Plant Network Using Standard Ethernet TechnologyNote: Information presented here is for illustrative purposes onlyNon repeating IP subnets (with each device requiring a unique IP address) between CPwE Cell/Area Zones. Stratix 5700 series switches - VLANs implemented to logically segment CPwE Cell/Area Zones.In this example, all nodes within the Industrial Zones must have a unique IP address.IP addresses cannot be reused across machines/process skids or anywhere else within the Industrial Zone.• Each Cell/Area Zone is segmented via a unique VLAN and IP subnet• Note that CPwE VLAN best practices dictates that each Cell/Area Zone must have a unique IP subnet• If Cell/Area Zones need to communicate between each other, they must communicate through a Layer 3 switch such as the Stratix 8300 that can provide inter-VLAN routing• This architecture provides small layer 2 domains of trust, fault domains and broadcast domains• This architecture can help limit access between Cell/Area Zones to help provide restrictive access to machine/process skid builders’ intellectual property • Machine/process skid builders must adhere to addressing schema of plant-wide/ site-wide network, potentially adding complication and time to commissioningRepeating IP subnets between CPwE Cell/Area Zones. Translating IP addresses using Stratix 5700 series switches VLANs implemented to logically segment CPwE Cell/Area Zones.In this example, IP addresses can be reused across Cell/Area Zones, allowing OEMs to repeat IP subnets while still allowing for a converged network. The Cell/Area Zones repeat IP subnets and are segmented from each other by utilizing VLANs.• Each Cell/Area Zone is segmented via a unique VLAN• If Cell/Area Zones need to communicate between each other, they must communicate through a Layer 3 switch such as a Stratix 8300 that can provide inter-VLAN routing• This architecture provides small layer 2 domains of trust, fault domains and broadcast domains • This architecture can help limit access between Cell/Area Zones to help provide restrictive access to machine/process skid builders’ intellectual property• This architecture utilizes Network Address Translation provided by the Stratix 5700 switches • From Level 3, the site operations are able to access all devices • Between each individual Cell/Area Zone, IP Addresses can be re-used• Each Stratix 5700 must be programmed to translate from the 192.168.1.0/24 IP subnet to the plant-wide/site-wide IP subnet.If the entire Cell/Area Zone needs to communicate with the plant-wide/site-wide network, then all devices must have their addresses manually translated • This architecture complicates the plant-wide/site-wide side of the architecture to provide simplicity to the Cell/Area Zones and machine/process skid buildersPublication IASIMP-QR30A-EN-PAbout the ProductsStratix 5700• Scalable Layer 2 managed industrial switch• Default configurations for industrial autom ation and EtherNet/IP devices (Global and Smartports)• Studio 5000 for configuration via Add on Profiles/Predefined Logix tags for diagnostics • FactoryTalk View Faceplates for status monitoring and alarming • Best of Cisco - Catalyst® switch architecture/ feature setStratix 8300• Full Layer 3 industrial switch that supports routing between Subnets and VLANs.• Default configurations for industrial automation and EtherNet/IP devices (Global and Smartports)• Studio 5000 for configuration via Add on Profiles/Predefined Logix tags for diagnostics • FactoryTalk View Faceplates for status monitoring and alarming • Best of Cisco - Catalyst® switch architecture/ feature setStratix 5900• Combines a number of modern security functions into a single appliance• Managed router that also provides a number of managed switching features • A single device to implement VPN, Firewall, NAT, and many other services • Best of Cisco - Fully integrated with Cisco IOS9300-ENA• NAT Appliance allowing identical machines to be placed on Ethernet networksAbout this ConfigurationThis system consists of three Cell/Area Zones, each with different hardware and potentially from three unique OEMs who would like to protect their Intellectual Property (IP). It illustrates different techniques to accomplish the following: 1. Protect intellectual property of machine/process skid builders 2. Provide small Layer 2 domains of trust and broadcast domains3. Provide logical Layer 2 building blocks to ensure a future-ready network4. Enable Network Address Translation on a plant-wide/site-wide network to provide IP subnet repeatability at the Cell/Area Zone level, providing faster commissioning time for machine/ process skid buildersBill of MaterialQty Catalog # Description System: Communication Hardware1 1783-BMS10CL Stratix 5700 Layer2 Managed Switch, 10 Ports Lite1 1783-BMS10CGN Stratix 5700 Layer2 Managed Switch, 10 Ports,Full with CIP Synch and NAT 1 1783-RMS10T Stratix 8300 Layer3 Managed Switch, 10 Ports 1 1783-MS10T Stratix 8000 Layer 2 Managed Switch, 10 Ports 1 1783-SR Stratix 5900 Security Appliance1 9300-ENA Network Address Translation ApplianceSegmentation Techniques Positive Design Considerations Negative Design ConsiderationsNo Segmentation (Not Recommended)• Initially, may appear to be simple to design anddeploy• Link Resiliency (redundant path topologies)• Same Layer 2 broadcast andfault domain, not a scalable or future ready solution.• Every node requires a unique IP address • Blurred demarcation line of network ownershipMultiple NIC Segmentation (ControlLogix Only)• Simple to design and deploy• Smaller Layer 2 domains (broadcast and fault)• Reusable IP addresses/subnets• Clear demarcation of network ownership• Not scalable or future ready, only CIP traffic can traverse a CIP bridge, limited quantity of bridge modules.• Smaller PACs do not support a dual NIC.• No Link Resiliency (redundant path topologies)NAT Appliance Segmentation 9300-ENA• Smaller Layer 2 domains (broadcast and fault)• Reusable IP addresses/subnets • Clear demarcation of network ownership• More difficult to design, deploy,and manage-manual entry and management of IP address translations• No Link resiliency (redundant path topologies)Unified Threat Management Security Appliance with NAT Stratix 5900• Smaller Layer 2 domains (broadcast and fault)• Reusable IP addresses/subnets • Clear demarcation of network ownership• Enhanced security features• More difficult to design, deploy, and manage-manual entry andmanagement of IP address translations • No Link resiliency (redundant path topologies)VLANs Only Segmentation Stratix 5700• Scalable and future ready• Smaller Layer 2 domains (broadcast and fault)• Smaller domains of trust (management of security policies)• Link Resiliency (redundant path configuration)• Layer 3 switch or router is required to forward (route) information between VLANs• Every node requires a unique IP address • Blurred demarcation line of network ownershipVLAN Segmentation with NAT Stratix 5700• Scalable and future ready• Smaller Layer 2 domains (broadcast and fault)• Smaller domains of trust (management of security policies)• Reusable IP addresses/subnets • Link Resiliency (redundant path configuration• Layer 3 switch or router is required to forward (route) information between VLANs• More difficult to design, deploy, andmanage-manual entry and management of IP address translations• Blurred demarcation line of network ownershipSummary of Considerations for Segmentation MethodologiesReference Architecture Web Page/rockwellautomation/products-technologies/network-technology/architectures.pageAdditional ResourcesENET-PP005C-EN-E Stratix 5700 Industrial Ethernet Switch Product ProfileENET-PP002B-EN-P Stratix 8000 and 8300 Industrial Ethernet Switches Product Profile ENET-PP006A-EN-P Stratix 5900 Services Router Product ProfileENET-AT004B-EN-E Segmentation Methods within the Cell / Area ZoneIASIMP-QS038A-EN-PStratix 5700 NAT Quick StartENET-WP032A-EN-E Stratix 5700 NAT Whitepaper ENET-QR001-EN-E Stratix Switch Reference Chart ENET-QR002-EN-EStratix 5700 Reference ChartGMSP-PP001-EN-E 9300-ENA Network Address Translation Device Product ProfileIASIMP-QR029A-EN-PStratix/Infrastructure Product Family Quick Reference DrawingENET-TD001-EN-PConverged Plantwide Ethernet (CPwE) Design and Implementation Guide (DIG)。
SIEMENS 工业以太网交换机 说明书

SCALANCE — 性能可延展西门子全集成自动化理念已在全球各地成功演绎了无数次;通过共享工具和标准化机制,可实现集成解决方案。
最重要的基础工作之一就是致力于SIMATIC NET 工业通讯的发展。
SCALANCE 即是里程碑式成果,一种全新的有源网络部件,用于构建集成网络。
2SCALANCE XXWS安全性工业无线局域网工业以太网交换机SCALANCE S保证工业安全利用安全机制,如认证、数据加密或访问控制,SCALANCE S 可以保护网络和数据不受侵袭活动,操控和未经授权访问。
SOFTNET 安全客户机用于SCALANCE 保护下设备的安全访问。
SCALANCE W用于工业无线局域网的可靠无线电技术基于工业无线电局域网,SCALANCE W 将集成通讯拓展到一个过去很难甚至不可能进入的领域。
SCALANCE W 是通过专用的数据传输速率或监控无线连接做到这点。
SCALANCE W 采用了IEEE 802.11a / b / g / h / e / i无线局域网国际标准。
SCALANCE X从入门级到高性能网络工业以太网交换机SCALANCE X 提供一系列的不同功能的工业以太网交换机,例如:通过PROFINET 、SNMP 或是Internet诊断,以满足对网络结构、数据传输速率和端口数的不同需要。
这些有源网络部件可完美相互协同,旨在严酷的工业环境下能够集成、灵活、安全、高性能的构建网络。
工业环境下的通讯工业通讯与办公环境下的通讯有着根本上的不同。
在办公环境下,很多用户连接一台服务器;客户之间并没有交叉连接。
而这种数据传输在建立通讯连接时,多个用户同时连接服务器时会导致阻塞和延时。
这不能用于自动控制,因为循环的执行进程处理需要输入更新的数据来对组件发出适应的控制指令。
此外,应用技术,通讯关系和网络结构也必须各自能够适应严酷的工业环境。
工业网络必须能够反应灵活并在短时间内满足市场需求,重组必须快速而高效。
工业以太网交换机Carat1008TXCarat5008EFC2卓越品质

⼯业以太⽹交换机Carat1008TXCarat5008EFC2卓越品质Carat1008TX 8⼝10/100Base-TX,卡轨式⼯业以太⽹交换机,18~36VDC(可选85~265V AC/DC)Carat1008FC 7⼝10/100Base-TX, 1⼝100Base-FX(多模,2公⾥,SC),卡轨式⼯业以太⽹交换机,18~36VDC(可选85~265V AC/DC)Carat1008FC-20 7⼝10/100Base-TX, 1⼝100Base-FX(单模,20公⾥,SC),卡轨式⼯业以太⽹交换机,18~36VDC(可选85~265V AC/DC)Carat1008FC2 6⼝10/100Base-TX,2⼝100Base-FX(多模,2公⾥,SC),卡轨式⼯业以太⽹交换机,18~36VDC(可选85~265V AC/DC)Carat1008FC2-20 6⼝10/100Base-TX,2⼝100Base-FX(单模,20公⾥,SC),卡轨式⼯业以太⽹交换机,18~36VDC(可选85~265V AC/DC) 注1:85~265V AC/DC型号列表价格⽐相应的18~36VDC型号多150元。
注2:单模光⼝传输距离可选40~120KM。
Carat1006ETX 6⼝ 10/100Base-TX,卡轨式⼯业以太⽹交换机,冗余电源18~36VDC Carat1007EFC6⼝ 10/100Base-TX,1⼝100Base-FX(多模,2公⾥,SC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1007EFC-20 6⼝10/100Base-TX, 1⼝100Base-FX(单模,20公⾥,SC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1008EFC26⼝ 10/100Base-TX,2⼝100Base-FX(多模,2公⾥,SC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1008EFC2-206⼝ 10/100Base-TX,2⼝100Base-FX(单模,20公⾥,SC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010ETX10⼝ 10/100Base-TX,卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010EFC9⼝ 10/100Base-TX,1⼝100Base-FX(多模,2公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010EFC-20 9⼝10/100Base-TX, 1⼝100Base-FX(单模,20公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010EFC28⼝ 10/100Base-TX,2⼝100Base-FX(多模,2公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010EFC2-20 8⼝10/100Base-TX, 2⼝100Base-FX(单模,20公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010EGC9⼝ 10/100Base-TX,1⼝1000Base-SX(多模,2公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010EGC-20 9⼝10/100Base-TX, 1⼝1000Base-LX(单模,20公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010EGC28⼝ 10/100Base-TX,2⼝1000Base-SX(多模,2公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1010EGC2-20 8⼝10/100Base-TX, 2⼝1000Base-LX(单模,20公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1018ETX18⼝ 10/100Base-TX,卡轨式⼯业以太⽹交换机,18~36VDC,冗余电源IP40防护等级Carat1018EFC17⼝ 10/100Base-TX,1⼝100Base-FX(多模,2公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1018EFC-20 17⼝10/100Base-TX, 1⼝100Base-FX(单模,20公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1018EFC216⼝ 10/100Base-TX,2⼝100Base-FX(多模,2公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1018EFC2-20 16⼝10/100Base-TX, 2⼝100Base-FX(单模,20公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1018EGC17⼝ 10/100Base-TX,1⼝1000Base-SX(多模,0.5公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1018EGC-20 17⼝10/100Base-TX, 1⼝1000Base-LX(单模,20公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1018EGC216⼝ 10/100Base-TX,2⼝1000Base-SX(多模,0.5公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDCCarat1018EGC2-20 16⼝10/100Base-TX, 2⼝1000Base-LX(单模,20公⾥,LC),卡轨式⼯业以太⽹交换机,冗余电源18~36VDC 注1:单模光⼝传输距离可选40~120KM。
IASIMP-QS023A-ZH-P[1]
![IASIMP-QS023A-ZH-P[1]](https://img.taocdn.com/s3/m/6f8292ed81c758f5f61f675a.png)
准备计算机并加载控制器 固件
章节 2
准备事宜 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33 所需工具 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34 操作步骤 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35 安装 RSLogix 5000 软件 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
PORT MOD NET B NET A
STS
PowerFlex 70 变频器 Kinetix 350 驱动器
新用户入门 PanelView Plus 终端
开门式隔离器 急停按钮
1 (Front) 2 (Rear)
CompactLogix 5370 L3 控制系统
以太网交 换机
分布式 POINT I/O 模块
触电危险:位于设备 ( 例如,驱动器或电机 ) 表面或内部的标签,提醒相关人员可能存 在危险电压。
烧伤危险:位于设备 ( 例如,驱动器或电机 ) 表面或内部的标签,提醒相关人员表面可 能存在高温危险。
重要事项 标识对成功应用和了解本产品有重要作用的信息。
wisLink工业交换机说明书V

电源:
输入电压 连接 最大功耗
DC220V/110V(自适应) 接线端子 3W
第 1 页 共3页
wisLink W-100 工业交换机装置技术说明书(V1.0)过载电流Leabharlann 护 反向电压输入保护机械特性:
包装及防护等级 尺寸
工作环境:
工作温度 工作相对湿度
抗干扰特性:
抗干扰性能 绝缘耐压标准
支持,最大可承受 2.5 A 支持
抗干扰性能 绝缘耐压标准
10M-14880 pps、100M-148800pps、1000M-1488000pps 4.8Gbps 存储转发 全双工 IEEE802.3x,半双工背压式 8 K、自动学习 < 5ms
v100第一章wislinkw100工业交换机技术说明书第二章wislinkw1600工业交换机技术说明书第三章wislinkw1601工业交换机技术说明书第四章wislinkw1700工业交换机技术说明书第五章wislinkw802工业环网交换机技术说明书第六章wislinkw802m工业环网交换机技术说明书第七章wislinkw802g工业交换机技术说明书第八章wislinkw200光电转换器技术和使用说明书第九章wislinkw2000工业以太网交换机技术说明书第十章wislinkw2400工业交换机技术说明书wislinkw100工业交换机技术说明书版本
如需相关产品、服务和支持的更多信息,请访问金智科技网 站/。
本公司有权对本说明书的内容进行定期变更,恕不另行通知。变更内容将会补充 到新版本的说明书中。
_____________________________________________________________
wisLink W-1600 在设计中考虑工业场合的应用需求和习惯,采用交直流供电方式,直流供电 让交换机和工业设备采用相同的电压输入,增加了可靠性,减少了施工复杂性。采用网线后出线的 方式,使得网线的布置整洁、美观;同时为了方便巡视,wisLink W-1600 前面板设置了显示各个网 口工作状态的灯,使得交换机的工作状态一目了然。由于 wisLink W-1600 针对工业用户,我们在设 计上严格按照 IEC-1613、IEC61000-6-5 以及 IEC61850-3 的标准,以满足工业现场的抗电磁干扰的 需求。在交换性能上,wisLink W-1600 完全满足 RFC2899 规定的交换性能要求。
工业以太网交换机说明书

8 口 10/100M+4 路串口网管型工业以太网交换机
主要特性
◎支持 SW-Ring 环网冗余专利技术,网络故障自愈时间<20ms ◎支持 IEEE802.1Q VLAN 设置,有效控制广播域 ◎支持 Web、CLI、Telnet 管理功能 ◎支持 IEEE802.1p_QOS 功能
百兆电口:10Base-T/100Base-TX 自适应、RJ45 口 百兆光口:100Base-FX(SC 接口) 程序加载口:基于串口全局网管(RS-232),RJ45
告警端口:2 芯 7.62mm 间距接子端子
1 路继电器告警信息输出,
电流负载能力 1A@24VDC
串口 RS-232 信号:TXD,RXD,GND RS-422 信号:T+,T-,R+,R-,GND RS-485 信号:D+,D-,GND 检验位:None,Even,Odd,Space,Mark 数据位:5bit,6bit,7bit,8bit 波特率:300~115200bps 方向控制:RS-485 采用数据流向自动控制技术 负载能力:RS-485/422 端支持 32 点轮询环境(可定 制 128 点) 接口保护:RS-485/422 隔离电压 2KV,静电保护 15KV
EN61000-4-8(PFM),Level 5
冲击:IEC 60068-2-27 自由跌落:IEC60068-2-23 震动:IES 60068-2-6 质保 保修期:5年 认证 CE、FCC、RoHS、UL508(认证中) 产品最新认证动态请查询 3onedata 网站
订购信息
可选型号
标准型号
简介
IES618-4D 系列是最新一代多业务接入型网管冗余工业以太网交换机,具有集成度高,功能丰富,简 单方便等特点,代表行业内最高水平。支持丰富的工业运用所需的以太网交换机二层协议,支持自主研发 的 SWRing 冗余环网协议,自愈时间<20ms,保障了网络的实时性和稳定性。
AB交换机Stratix8000使用说明

工业以太网交换机Stratix TM 8000 动手实验目录STRATIX 8000_________________________________________________________________________3关于本动手实验_______________________________________________________________________3实验内容___________________________________________________________________________3实验设备____________________________________________________________________________3硬件______________________________________________________________________________3软件______________________________________________________________________________3恢复交换机的工厂默认设置______________________________________________________________4通过EXPRESS SETUP按钮恢复工厂默认设置_______________________________________________5运行E XPRESS S ETUP____________________________________________________________________6实验二: 理解设备管理器和SMARTPORTS___________________________________________________11获得诊断信息________________________________________________________________________11端口标识___________________________________________________________________________13端口号____________________________________________________________________________13端口状态指示灯不同颜色表示的意义:___________________________________________________13趋势图_____________________________________________________________________________14 S PANNING T REE P ROTOCOL (生产树协议)___________________________________________________18更改交换机的配置____________________________________________________________________19 E XPRESS S ETUP______________________________________________________________________21配置S MARTPORTS_____________________________________________________________________22测试S MARTPORT______________________________________________________________________23 Smartport错误检测__________________________________________________________________24实验三: 使用STRATIX 8000 RSLOGIX5000 AOI指令和 FACTORYTALK VIEW FACEPLATES_________27在RSL OGIX 5000中组态S TRATIX 8000_____________________________________________________27设置S TRATIX 8000A DD-ON 指令__________________________________________________________31使用S TRATIX 8000的F ACTORY T ALK V IEW F ACEPLATES_________________________________________39实验四: 设置端口镜像,使用WIRESHARK抓取数据包__________________________________________57通过W IRESHARK抓取数据包_____________________________________________________________57设定端口镜像________________________________________________________________________63设定端口镜像后抓取数据包_____________________________________________________________64Stratix 8000关于本动手实验本实验的目的是使您熟悉Stratix 8000交换机和组网的基本知识。
思科交换机产品介绍

思科交换机产品介绍关于思科交换机产品介绍思科公司是全球领先的网络解决方案供应商。
Cisco的名字取自San Francisco(旧金山),那里有座闻名于世界的金门大桥。
以下是店铺收集的思科交换机产品介绍,欢迎大家参考!一、Cisco Nexus 7000系列交换机Cisco Nexus 7000系列交换机是一个模块化数据中心级产品系列,适用于高度可扩展的万兆以太网网络,其交换矩阵架构的速度能扩展至15Tbps以上。
它的设计旨在满足大多数关键任务数据中心的要求,提供永续的系统运营和无所不在的虚拟化服务。
Cisco Nexus 7000系列建立在一个成熟的操作系统上,借助增强特性提供了实时系统升级,以及出色的可管理性和可维护性。
它的创新设计专门用于支持端到端数据中心连接,将IP、存储和IPC网络整合到单一以太网交换矩阵之上。
作为第一款下一代交换机平台,Cisco Nexus 7000系列10插槽机箱(图1)提供了集成永续性,以及专为数据中心可用性、可靠性、可扩展性和易管理性而优化的特性。
N7K-C7010 10 Slot Chassis, No Power Supplies, Fans IncludedN7K-SUP1 Nexus 7000 - Supervisor, Includes External 8GB Log FlashN7K-C7010-FAB-1 Nexus 7000 - 10 Slot Chassis - 46Gbps/Slot Fabric ModuleN7K-AC-6.0KW Nexus 7000 - 6.0KW AC Power Supply ModuleN7K-C7018 18 Slot Chassis, No Power Supplies, Fans IncludedN7K-C7018-FAB-1 Nexus 7000 - 18 Slot Chassis - 46Gbps/Slot Fabric ModuleN7K-AC-7.5KW-INT Nexus 7000 - 7.5KW AC Power Supply Module International (cabN7K-AC-7.5KW-US Nexus 7000 - 7.5KW AC Power Supply Module US (cable includedN7K-C7010-BUN Nexus 7010 Bundle (Chassis,SUP1,(3)FAB1,(2)AC-6KW PSU)N7K-C7010-BUN-R Nexus 7010 Bundle (Chassis,(2)SUP1,(3)FAB1,(3)AC-6KW PSU)N7K-DC-6.0KW Nexus 7000 - 6.0KW DC Power Supply Module (Cables Included)N7K-DC-PIU Nexus 7000 - DC Power Interface UnitN7K-M132XP-12 Nexus 7000 - 32 Port 10GbE, 80G Fabric (req. SFP+)N7K-M148GT-11 Nexus 7000 - 48 Port 10/100/1000, RJ-45N7K-M148GS-11 Nexus 7000 - 48 Port 1G, SFPN7K-M148GS-11L Nexus 7000 - 48 Port GE Module with XL Option (req. SFP)N7K-M108X2-12L Nexus 7000 - 8 Port 10GbE with XL option (req. X2)N7K-C7010-FD-MB Nexus 7010 Front Door KitN7K-CPF-2GB Nexus Compact Flash Memory 2GB (Expansion Flash - Slot 0)N7K-C7010-AFLT Nexus 7010 Air FilterN7K-C7018-FD-MB Nexus 7018 Front Door Kit二、Cisco Nexus 5000系列交换机Cisco Nexus 5000系列是Cisco Nexus系列数据中心级交换机的一个组成部分,它提供了一个创新架构,通过实施基于标准的高性能以太网统一阵列,简化了数据中心转型。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Stratix 8000 硬件概述
Catalog
模块类型 模块端口数 总的端口数 10/100 M电口数 100Base-FX 光口述 10/100/1000 电口数 光纤SFP插槽数 支持的SFP类型 工作温度 防护等级
1783-MS06T
6 22 4 -
1783-MS10T
10 26 8 -
1783-MX08T
无需PC,无需设置,无需组态!
IEEE 1588 v2 – 精确时间同步协议
• 精确时间同步协议(Precision Time Protocol ,PTP)
– 在分布式系统中实现实时同步
• 在高性能的工业应用中需要这种技术
– 运动控制要求亚微妙的时间精度 – 所有设备同步他们的时钟,误差可小 于1us – SOE应用 – 预定义时间点协同动作 (ex: all systems stop at time=x)
• Stratix 6000 – 固定端口管理型
– 优化工厂现场网络 – 自动化工程师所熟悉的 – RSLogix 5000 配置,Logix标签和FactoryTalk View 面板
• Stratix – 嵌入式技术
– – – – 嵌入在罗克韦尔自动化产品中的两端口交换机 能实现高速环形和线形拓扑 无需配置 最初发布的产品: • Stratix 4000 3端口分接器 • 1756-EN2TR – ControlLogix 网桥模块
Stratix 8000的DHCP可根据端口来分配IP地址 端设备更换简单易行
• 更换终端设备后, 分配之前相同的IP地址给新设备
DHCP 服务器
DHCP 服务器
172.20.3.1
172.20.3.3
172.20.3.1
172.20.3.3
172.20.3.2
出故障的设备
172.20.3.2
更换变频器
集成企业和制造业现场网络特点
3
Stratix 系列交换机定位
$
非管理型
• 端口配置:
• 4, 5, 7, & 8 端口 • 可选光纤和电口
固定端口管理型
• 端口配置:
• 4电口,8电口带一个SFP插槽
• 特点:
• RSLogix 5000 组态, 标签 和面板 • 支持VLANs, QoS, SNMP, IGMP,端口镜像 , MAC ID端口安全和根据端口来分配IP 地址的DHCP
REP 通用链路的冗余选择
A
L3 Domain
B
Etherchannel
C
D
Spanning Tree
REP Segment
E
F
G
H
REP可以实现VLAN负载平衡
REP技术
Primary Edge Port 0/1 Blocking for VLAN 1-200 And 401-4094
其它环网技术
Secondary Edge Port 0/2
ALL VLAN
Preferred Port blocking for VLAN 201-400
REP的环间耦合与其它厂商环网的环间耦合
REP环间耦合 其它厂商环网环间耦合
A D
B
i E k
H
j F
G
Etherchannel (端口聚合)
• 组合几条物理链路为一个逻 辑连接的技术,可增加交换 机间的带宽 • 可实现负载平衡和网络冗余 能力 • STP将EtherChannel看成一条 路径
Stratix 8000 模块化管理型
• 端口配置:
• 6 - 26 端口 • 基本模块6,10口两种 • 扩展模块:8电口、8光口
• 特点:
• 无需配置,没有诊断功能,无 网络安全特点
• 特点:
• Cisco 技术: IOS, CLI, DeviceManager & Automation Smartports • RSLogix 5000 组态, 标签和面板 • 支持VLANs, QoS, SNMP, 端口镜像, MAC ID 端口安全,根据端口来分配IP地址的DHCP, REP –支持环形拓扑 • CF卡存储IOS和配置数据
Stratix 工业以太网交换机
Insert Photo Here 何华
Copyright © 2009 Rockwell Automation, Inc. All rights reserved.
制造业企业的网络参考架构
• 标准的未经更改的以太网 • 网络安全 • 设计指导
– – – – – 建立在工业标准上 最佳实践 文档化的设计组态方法 经过工业应用的检验 Cisco验证的网络设计规范
工厂底层网络和企业网络集成应用的理想产品
联合品牌产品 – Stratix 8000
• 模块化管理型交换机系列产品,Stratix 8000 • 由Allen-Bradley和Cisco联合品牌和设计 • 6到26端口
Cisco最佳特性 • 和企业网的安全集成
– Cisco互联网操作系统(IOSTM) TM – Cisco Catalyst 系列交换机架构和功能集 – IT熟悉的工具:命令行界面 (CLI),CNA和设备管理 器
Enterprise Zone Levels 4 and 5
• Remote desktop connection • VPN
Windows 2003 Servers
Demilitarized Zone (DMZ)
Gbps Link for Failover Detection
Firewall (Standby) Demilitarized Zone (DMZ) Manufacturing Zone Level 3 Network Services
具有如下特点的工业以太网交换机: • 对组态、监控、安全和维护进行了优化 • 模块化和可扩展的 • 使复杂的以太网应用简单化
概述
关键好处
• IT所熟悉的解决方案 • 容易将机器系统与企业网络的集成 • 集成架构编程工具和特点 • 安全的远程访问用于提高生产力和OEE
应用
• 连接的或隔离的机器系统的应用,过程控制应用 • 车间现场与企业网络的集成 • 需要被监控和控制的分布式网络设备
+
......成功打造企业和制造集成环境
Stratix 8000 配置工具
CNA 面板
CLI
AOP 设备管理器
预先定义的Smartports设置
Smartports: •预先定义的配置可为通 用设备设置如下功能: •优化网络ቤተ መጻሕፍቲ ባይዱ量 •将响应时间减到最小
交换机端口不同的设备选择不同的Smartport参数,可优化网络
• DNS, DHCP, syslog server • Network and security management
Firewall (Active) FactoryTalk 应用服务器
• • • • View Historian AssetCentre Transaction Manager
• 面向今天,适应未来的网 络
线形或环形
• Stratix 2000 – 固定端口非管理型
– 紧凑型尺寸 – IP20和IP67版本 – 无需配置
• 物理介质 – 电缆,连接器,预制电缆
多种选择– 管理型, 非管理型和嵌入式
Copyright © 2009 Rockwell Automation, Inc. All rights reserved. 5
Master Clock
网络安全保护
• • • •
使用RSLogix5K 程序打开和关闭端 口 支持访问控制表 (ACL) 支持 802.1x 工业标准的身份验证 在RSLogix 5000中,可配置设备的 身份验证表(MAC ID端口安全)
阻止非授权的访问和保护数据
Resilient Ethernet Protocol (REP) 快速弹性以太网
– CIP Safety, CIP Sync, CIP Motion – Voice, Video
Layer 3 Router
FactoryTalk 服务平台
• Directory • Security
数据服务器
Layer 3 Switch Stack
Level 0–2
Cell/Area Zone
Layer 2 Switch Drive Controller HMI Distributed I/O Controller
分段REP用于不同的拓扑
Bridged domain
A D A E
Segment 2
B C
B
M
Segment 1 Segment 3
C F H G I H K D
E
Segment 1
J K L
I
Segment 3
L
Segment 2
J
F
G
REP Segment Alternate (Blocking) Port Edge Port
HMI HMI
Controller
Drive Cell/Area #2 (Ring Topology) Distributed I/O
Drive Cell/Area #3 (Bus/Star Topology)
Cell/Area #1 (Redundant Star Topology)
Stratix 系列产品概述
• Resilient Ethernet Protocol (REP)
– Stratix 8000及某些思科交换机支持的环 网协议 – 支持环网、环段和嵌套的环段 – 提供单点故障的网络恢复
• 光纤环网:小于70ms网络恢复,不会造成 EtherNet/IP IO连接的中断
