Checkpoint SIC
中国移动Checkpoint防火墙安全配置手册V0.1.doc

密级:文档编号:项目代号:中国移动Checkpoint防火墙安全配置手册Version *.*中国移动通信有限公司二零零四年十一月拟制: 审核: 批准: 会签: 标准化:Firewall 版本控制分发控制目录1 综述 (5)2 Checkpoint的几种典型配置 (6)2.1 checkpoint 初始化配置过程: (6)2.2 Checkpoint Firewall-1 GUI安装 (13)2.3 Checkpoint NG的对象定义和策略配置 (18)3 Checkpoint防火墙自身加固 (34)1综述本配置手册介绍了Checkpoint防火墙的几种典型的配置场景,以加强防火墙对网络的安全防护作用。
同时也提供了Checkpoint防火墙自身的安全加固建议,防止针对防火墙的直接攻击。
通用和共性的有关防火墙管理、技术、配置方面的内容,请参照《中国移动防火墙安全规范》。
2Checkpoint的几种典型配置2.1 checkpoint 初始化配置过程:在安装完Checkpoint软件之后,需要在命令行使用cpconfig命令来完成Checkpoint的配置。
如下图所示,SSH连接到防火墙,在命令行中输入以下命令:IP350[admin]# cpconfigWelcome to Check Point Configuration Program=================================================Please read the following license agreement.Hit 'ENTER' to continue...(显示Checkpoint License版权信息,敲回车继续,敲q可直接跳过该License提示信息)Do you accept all the terms of this license agreement (y/n) ?y(输入y同意该版权声明)Which Module would you like to install ?-------------------------------------------(1) VPN-1 & FireWall-1 Enterprise Primary Management and Enforcement Module(2) VPN-1 & FireWall-1 Enforcement Module(3) VPN-1 & FireWall-1 Enterprise Primary ManagementCheckpoint Firewall-1/VPN-1支持多种安装模式,Firewall-1/VPN-1主要包括三个模块:GUI:用户看到的图形化界面,用于配置安全策略,上面并不存储任何防火墙安全策略和对象,安装于一台PC机上;Management:存储为防火墙定义的各种安全策略和对象;Enforcement Module:起过滤数据包作用的过滤模块,它只与Managerment通信,其上的安全策略由管理模块下载;以上三个选项中如果Management与Enforcement Module安装于同一台设备上,则选择(1),如果Management与Enforcement Module分别安装于不同的设备上,则选择(2)或(3)。
Check Point教程

Check point防火墙基本操作手册CheckPoint(中国)TEL:(86)10 8419 3348 FAX:(86)10 8419 3399©2010 Check Point Software Technologies Ltd. All rights reserved.Classification:目录目录 (2)防火墙架构 (3)防火墙的Web管理 (3)配置IP: (4)配置DNS和Host: (5)配置路由: (5)通过防火墙的管理客户端管理 (5)添加防火墙 (7)添加策略步骤 (10)IP节点添加 (10)添加网段 (11)IPS的配置 (13)更新IPS库 (14)新建IPS动作库 (14)应用控制 (16)更新数据库 (16)添加应用控制策略 (17)App Wike (18)自定义添加应用 (18)QOS配置 (20)Qos策略的添加 (20)日志工具的使用 (20)筛选日志 (21)临时拦截可以连接 (22)©2010 Check Point Software Technologies Ltd. All rights reserved.Classification:©2010 Check Point Software Technologies Ltd. All rights reserved.Classification:防火墙架构Check point 防火墙的管理是通过一个三层架构来实现的。
首先我们可以在任意的机器上安装防火墙客户端控制台,然后利用控制台的图形化界面登录check point 的管理服务器,定义出各个网络对象,定义企业各条策略,最后下发到防火墙执行模块。
具体实现过程见图示:防火墙的Web 管理首先打开Web 管理界面,出现登录界面:登陆后的界面设备的Web界面只能配置设备的IP地址,网关,DNS和路由。
还可以针对设备的事件,SNMP监控,代理等信息。
Checkpoint-管理服务器的HA

管理服务器(SmartCenter)的HA一.概述环境:一台设备是管理服务器+gateway(已经安装好),另一台设备只安装secondary 管理服务器(下面会显示安装和配置)。
这里只演示安装secondary管理服务器以及HA的配置。
Checkpoint的这个功能,不会自动切换的,需要手动进行切换。
二.安装Secondary Management光盘安装过程一样,仅仅在网页进行初始化的时候选择有不同。
在初始化只选择Security Management和选择secondary。
输入连接密码vpn123然后退出没配置HA的话是不能登录到Secondary的服务器上的。
三.配置Management HA登录到主Management的smartdashboard,右键新建一个Checkpoint的HOST类型的对象然后编辑这个对象,填上IP信息和management的相关属性打勾输入密码vpn123然后建立SIC建立成功然后在Topology里新建一个接口点击OK关闭编辑这个对象!这个时候这个对象就新建好了。
确认一下是否已经选择了自动同步(默认)然后在菜单栏选择Launch menu----policy----Install the Datebase将策略都下发到两个管理服务器上在菜单栏选择Launch menu----policy----Management High Availability查看同步状态:这里显示是Never Synchronization!等待变成Synchronization。
注意:记得添加防火墙规则,让GW和新的管理服务器能够互相通信四.如何切换如果要切换,直接点击“Change to Standby”(注意只开启dashboard,关闭其他smarconsole应用程序),让主服务器变成Standby状态。
点击YES,将会失去和主管理服务器的连接然后输入副服务器的IP连接到新的管理服务器上。
Check Point Smartcenter安装步骤(WIN2K3)

防火墙管理服务器(SmartCenter)安装步骤(win2003)CheckPoint(中国)TEL:(86)10 8419 3348FAX:(86)10 8419 3399文档修订记录标题 smartCenter安装步骤(win2003)管理文档 □ 设计方案 □ 实施文档 X 类别配置文档 □ 测试文档 □ 其他 □ 当前版本 1.00创建日期 2010-05-01文档作者文件名称 smartCenter安装步骤(win2003)版本号 日期 修改人 审阅人 摘要1.00 2010-05-01 初稿文档说明此文档是由以色列捷邦安全软件科技公司于2010年05月制定的内部文档。
本文档仅就CheckPoint内部与相关合作伙伴和CheckPoint最终用户使用。
版权说明本文档中出现的任何文字叙述、文档格式、插图、照片、方法、代码等内容,除由特别注明,版权均属于以色列捷邦安全软件科技公司所有,受到有关产权及版权法保护。
任何个人、机构未经以色列捷邦安全软件科技公司的书面授权许可,不得以任何方式复制或引用本文档的任何片断。
1.安装smartcenter for win2003sp2第一步,准备好Windows 2003操作系统,安装最新的安全补丁,杀毒软件并且更新到最新版本,同时对smartCenter管理服务器进行必要加固,如选择复杂的管理员密码,关闭文件共享服务和其他不必要的服务。
将安装介质插入光驱,选择所使用的 smartcenter NGX R65 for windows 版本第二步,开始安装,根据购买的版本选择,在此选择 checkpoint power‐‐Æforward第三步,选择new installation 全新安装。
第四步,选择所要安装的组件,第一项Gateway是火墙,第二项Management是管理组件,比如报表模块,IPS‐1管理模块,以及火墙管理Console,在此只安装smartcenter/smartconsole,第五步,不需选择install plugin 插件,因为该模块为Connectra(SSL VPN网关)管理服务器,如果有connectra(SSL VPN网关)需要被集中管理,则请选用该组件,也可以以后再安装。
CheckPoint防火墙安装手册

防火墙安装操作手册By Shixiong Chen一、准备安装介质和服务器安装CheckPoint防火墙基于开放的服务器平台需要准备两点:如果选用的是Checkpoint的硬件,UTM-1则不需要考虑这些问题。
第一,准备好服务器,服务器最好选择IBM\HP\或者其他大品牌厂商的硬件平台,并且事先确认该品牌和型号的服务器与CheckPoint软件兼容性,将网卡扩展至与真实火墙一致,服务器需要自带光驱。
第二,准备好CheckPoint防火墙安装介质,注意软件的版本号与真实环境火墙一致,同时准备好最新的防火墙补丁。
二、SecurePlatform系统安装过程硬件服务器初始状态是裸机,将服务器加电后,设置BIOS从光盘启动,将CheckPoint软件介质放入光驱,然后出现如下界面:敲回车键盘开始安装。
出现如下界面,选择OK,跳过硬件检测。
选择安装的操作系统类型,根据自己防火墙操作系统的版本选择。
SecurePlatform Pro是带有高级路由和支持Radius的系统版本。
选择键盘支持的语言,默认选择US,按TAB键,继续安装。
配置网络接口,初始我们配置外网接口即可,选择eth0配置IP, 输入IP地址、子网掩码、以及默认网关,然后选择OK,继续。
选择OK.开始格式化磁盘。
格式化完成后开始拷贝文件,最后提示安装完成,按照提示点击OK.系统会自动重新启动。
然后出现登陆界面,如下所示。
第一次登陆系统,默认账号和密码都是admin,登陆后需要出入新的密码和管理员账号。
三、CheckPoint防火墙软件安装过程运行sysconfig 命令,启动安装防火墙包。
选择n,继续安装。
打开网络配置页面,选择1,配置主机名,选择3配置DNS服务器,选择4配置网络,选择5配置路由,注意要与生产线设备的配置保持一致,特别是路由要填写完整,主机名、接口IP和子网掩码要填写正确。
配置完成后,选择n,下一步继续配置,如下图所示,选择1配置时区(选择5,9,1),选择2配置日期,选择3配置本地系统时间,选择4查看配置情况。
Checkpoint防火墙命令行维护说明材料

Checkpoint防火墙命令行维护手册制订模版:NGX-R65版本号:V1.0目录一、基本配置命令 (1)1.1SYSCONFIG (1)1.2CPCONFIG (2)1.3CPSTOP (3)1.4CPSTART (3)1.5EXPERT (4)1.6IDLE (4)1.7WEBUI (4)1.8脚本添加路由 (4)二、查看系统状态 (1)2.1TOP (1)2.2DF –H (3)2.3FREE (3)三、HA相关命令 (1)3.1CPHAPROB STAT (1)3.2CPHAPROB –A IF (1)3.3CPHACONF SET_CCP BROADCAST (1)3.4CPHAPROB LIST (2)3.5CPHASTART/CPHASTOP (3)四、常用维护命令 (1)4.1VER (1)4.2FW VER (1)4.3查看防火墙UTM/POWER版本 (1)4.4查看防火墙硬件型号 (1)4.5LICENSE查看和添加 (1)4.6IFCONFIG/IFCONFIG –A (1)4.7MII-TOOL (1)4.8ETHTOOL (1)4.9CPSTAT FW (2)4.10会话数查看 (1)五、日志查看命令 (1)5.1FW LOG (1)5.2FW LSLOGS (1)5.3FW LSLOGS –E (1)5.4FW LOGSWITCH (2)5.5导出日志文件 (2)六、防火墙的备份和恢复 (1)6.1备份防火墙 (1)6.2在IE中备份 (1)6.4恢复防火墙 (2)一、基本配置命令1.1sysconfig可以对系统进行配置和修改,比如主机名修改,DNS配置修改,以及路由的配置等,另外还可以配置DHCP功能,以及产品的安装等等如上图所示,在命令提示符输入:sysconfig,将会出现下图所列一些选项,在Your choice后面输入你想配置的选项前的数字,然后按回车可以看到,依次的选项为主机名,域名,域名服务,时间和日期,网络连接,路由,DHCP服务配置,DHCP中继配置,产品安装,产品配置等例如我们选择5,为防火墙新增一个接口IP地址然后选择2,进行连接配置,也就是配置IP地址选择1进行IP地址配置更改如上图所示按照提示配置IP地址和子网掩码进行其他配置也如同上述操作,选择对应的编号然后按照提示进行配置1.2cpconfig可以对checkpoint防火墙进行相关的配置,如下图所示,也是按照列表的形式列出,分别是license,snmp,PKCS#11令牌,随机池,SIC,禁用cluster,禁用安全加速,产品自动启动常用的选项一般为SIC的配置,cluster功能模块的启用等;选择7是开启cluster功能模块;选择5是设置SIC。
checkpoint培训手册[1]
![checkpoint培训手册[1]](https://img.taocdn.com/s3/m/2cade610a76e58fafab00366.png)
完成Hide NAT的配置后我们需要验证NAT是否配置成功
对服务器作静态NAT
首先把服务器对象定义出来,在Nodes上点击右键,然后选择Host,然后 配置服务器的属性,再选择左边窗口中的NAT属性。
点击NAT,编辑NAT属性,选择Add Automatic Address Translation rules,然后在 Translation method 中选择选择Static,然后在下面的小框中输入自己分配给服 务器的公网地址。最后在install on上选择当前防火墙然后点击确定。静态 NAT就配置完成。
• 出现防火墙接口信息,如果我们系统的接 口和路由配置好后,我们单击Get,然后选择 Interface或是interface with topology 就可以 得到接口配置信息。这里我们需要在网ቤተ መጻሕፍቲ ባይዱ 接口上配置Anti Spoofing ,所以首先双击其 中任一接口开始配置。首先双击外网接口, 在下面弹出的对话框中选择Topology,
在防火墙上重置SIC
• • • • • • • • • • • • • • • • • • • • • • 在防火墙上重置SIC [admin@C25-HJZX-IDC-1 admin]$ su Password: [root@C25-HJZX-IDC-1 admin]# cpconfig This program will let you re-configure your Check Point products configuration. Configuration Options: ---------------------(1) Licenses (2) SNMP Extension (3) Group Permissions (4) PKCS#11 Token (5) Random Pool (6) Secure Internal Communication (7) VPNx (8) Disable cluster membership for this gateway (9) Disable Check Point SecureXL (10) Automatic start of Check Point Products (11) Exit Enter your choice (1-11) :6 Configuring Secure Internal Communication... ============================================ The Secure Internal Communication is used for authentication between Check Point components Trust State: Trust established Would you like re-initialize communication? (y/n) [n] ? y Note: The Secure Internal Communication will be reset now, and all Check Point Services will be stopped (cpstop). No communication will be possible until you reset and re-initialize the communication properly! Are you sure? (y/n) [n] ? y Enter Activation Key: xxxxxx Retype Activation Key: xxxxxx initial_module: Compiled OK.
APA格式中文写作指南

APA格式中文写作指南APA格式中文写作指南雷雳(首都师范大学教育科学学院自然科学心理学系,北京2001年8月)摘要第二页应包含论文摘要。
摘要是简洁而全面地对您的论文的总结。
摘要应该是准确的、具体的、简练且明确的、非评价性的、连贯的、易读的。
它初衷仍须反映您论文的目的和内容。
英译摘要长度不超过960个字符和空格(大约120字),外语摘要长度不超过480字(包括标点)。
综述性或理论性的论文摘要,英文应限制在75—100字左右,中文为300-400字左右。
美国心理协会提出不该这类论文应该包含以下信息:用一个句子写成的考题;论文的目的、主题,或论文的组织整体和论文涉猎的范围(先期的或有选择的);材料来源(亲自的观察、已发表的文献);还有结论。
摘要以“块”的形式呈现,不分段,首行缩进4个空格(两个汉字的空间)。
APA格式中文写作指南APA写作格式是美国心理基金会出版手册(第4版,1994)上面制定的撰写格式。
本指南是撰写论文的一个简捷的参考,并不能完全替换手册本身。
记住:若你正在为一门课撰写一篇论文,那么导师的具体要求比手册的要求则更重要。
每个检验点(checkpoint)结尾处给出的页码告诉我们到何处去寻找出版手册中关于主题的具体信息。
一、基本格式1. 从页顶、底、边算起,页边空白为2.54cm(除稿件页眉外)。
2. 所有地方均使用1.5倍行距。
3. 英文字体使用Courier 或Times Ne., i.e.。
(四)数字用阿拉伯数字表示10以上的数(12、50,等),除非要和10如下的数进行对比。
比如,4年级与11年级进行对比检验。
但在摘要中所有数字都应用阿拉伯数字表示。
在使用英文时,句首和小于10的数字应完整详尽复制出英文单词,此时中文则使用汉字,英文数字复数只需在数字后面加上s,而无需加“’”号(the 1990s)。
数字单词和数字的联合应紧接着被修饰对象(six 2-point scales)。
checkpoint简单安装
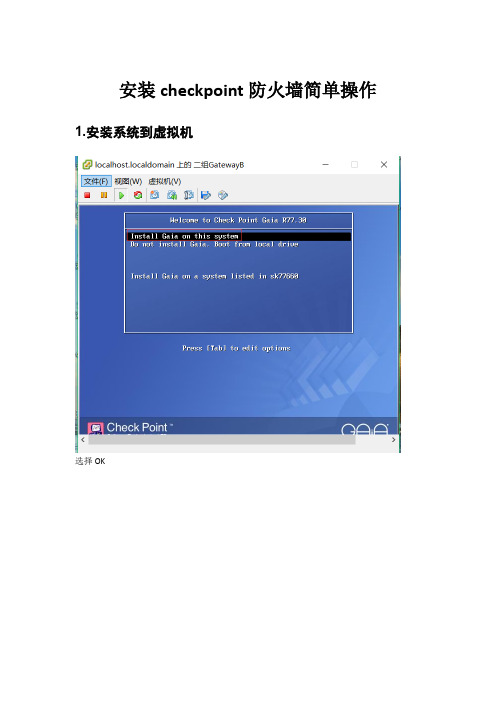
安装checkpoint防火墙简单操作1.安装系统到虚拟机
选择OK
选择OK
自己合理分配每个目录下的空间大小;之后选择OK
设置登录密码,默认账号是admin(此账号用于登陆命令行和web管理界面的);
设置登录的管理地址ip地址和默认网关。
完成之后reboot设备就可以。
2.Checkpoint防火墙初始化
打开web页面输入刚刚设置的管理地址,输入登录账号密码。
一直点击next
这是设置修改管理地址的;
设置设备主机名的
设置设备的时间
2.1选择management,这是把该设备设置成一台单独的smart center管理中心
设置登录smartdashboard的账号密码
设置允许登录center的设备,我们测试选择any
2.2选择security gateway,表示这是台单独的FW
设置SIC,用于center管理FW的key
3.center关联FW
右击checkpoint。
选择如下图所示:
输入FW的name和ip,点击conmmunication,输入之前设置的key,点击initialize
关联正常,之后就是添加策略和对象进行测试。
Checkpoint防火墙基本操作和应急操作

网路安全的基本概念
• 通过采用各种技术和管理措施 • 使网络系统正常运行,从而确保网络数
据的可用性、完整性和保密性 • 建立网络安全保护措施的目的: • 是确保经过网络传输和交换的数据不会
发生增加、修改、丢失和泄露等
2020/3/2
Checkpoint防火墙的基本操作
• Checkpoint防火墙结构 • Checkpoint防火墙部署方式 • IPSO的基础配置 • Checkpoint的安装和初始化 • 防火墙策略配置及下发 • SmartCenter备份与恢复 • 防火墙日志管理 • 系统性能指标巡检
2020/3/2
防火墙日志管理
• 通过SmartView Tracter查看日志
2020/3/2
Checkpoint防火墙的基本操作
• Checkpoint防火墙结构 • Checkpoint防火墙部署方式 • IPSO的基础配置 • Checkpoint的安装和初始化 • 防火墙策略配置及下发 • SmartCenter备份与恢复 • 防火墙日志管理 • 系统性能指标巡检
Checkpoint防火墙结构
• Checkpoint防火墙为软件防火墙, 可以在不同的操作系统上安装
– Windows操作系统 – Solaris操作体统 – Linux操作系统 – Nokia的专有操作系统IPSO
2020/3/2
Checkpoint防火墙结构
• Checkpoint防火墙层次结构
2020/3/2
防火墙策略配置及下发
2020/3/2
Checkpoint防火墙的基本操作
• Checkpoint防火墙结构 • Checkpoint防火墙部署方式 • IPSO的基础配置 • Checkpoint的安装和初始化 • 防火墙策略配置及下发 • SmartCenter备份与恢复 • 防火墙日志管理 • 系统性能指标巡检
CHECKPOINT安_配置中文手

安装配置CHECKPOINT防火墙大纲一、首先明确两个概念二、V PN/FW Moudule 或者Managerment Server 在WINDOWS上安装的最小需求三、G UI Client在WINDOWS上安装的最小需求四、安装之前的准备工作五、安装软件总过程六、配置防火墙总过程七、具体安装过程八、安装Licenses九、启动GUI ,定义网络对象十、定义安全策略(Rule Base)十一、定义NAT十二、创建一个管理员帐号Administrator十三、创建一个GUI Cilent十四、Key Hit Session十五、Certificate Authority十六、Fingerprint(指纹)十七、高可用性HA(High Availability)一、首先明确两个概念:1、VPN/FW Moudule;部署在网关上,其安全策略在Managerment Server 上创建并编译后下载到Moudule上执行。
它可以安装在多种硬件平台上。
它包括两部分:一、检测模块:根据安全策略对所有通过它的通讯进行检测。
二、安全服务器:提供认证和应用层的内容安全。
2、Managerment Server:在Policy Editor GUI上定义的安全策略,最后保存在Managerment Server上。
它的主要工作是维护CHECK POINT 数据库,包括:定义的网络对象,定义的用户,LOG文件等。
二、VPN/FW Moudule 或者Managerment Server 在WINDOWS上安装的最小需求:1、操作系统:NT 、WIN20002、CPU:PII300以上3、硬盘剩余空间:40M4、内存:128M三、GUI Client在WINDOWS上安装的最小需求:1、操作系统:WIN9X、WIN ME、WIN NT4+SP6、WIN2000professional2、硬盘剩余空间:40M3、内存:128M四、安装之前的准备工作1、在安装VPN-1/FW-1的计算机去掉不需要的服务,例如:NETBEUI、FTP、HTTP server2、保证内网、外网、DMZ区都能互通(ping)3、关闭WINDOWS上的IP Forwding,该功能由VPN-1/FW-1来控制。
05什么是Checkpoint文件

Control Builder中几个常用的命令
Rev.01
Project:组态窗口
Library:库窗口
Monitoring:监视窗口
服务器RTDB 实时数据库
Project 组态窗口
Monitor 监视窗口
Checkpoint 文件 Load:组态内容下装 Upload:控制器里的信息上装
C300 控制器内存
选择要保存的控制器 点击此处
Checkpoint文件名: C300_1:控制器名称 Jul312009_10_44_44:时间
保存成功
C:\Documents and Settings\All Users\Application Data\Honeywell\Experion PKS
定义自动保存
– C300控制器的组态 – I/O卡和通道的组态 – CM(控制模块)的组态 – SCM(顺序控制模块)的组态
checkpoint防火墙培训

12
可视化策略编辑器
checkpoint防火墙培训
13
第一部分:
• 复习 • 问题解答
checkpoint防火墙培训
14
第一部分:
• 问题 #1:
• 安装过程中,哪些参数需要设置或可以修改?
Licenses, administrators (name and password), GUI clients (client/server model), remote modules (client/server model), groups, default filter
checkpoint防火墙培训
34
Implicit 和 Explicit 规则
Implicit 规则 Implicit Drop 规则
checkpoint防火墙培训
35
全局策略菜单
checkpoint防火墙培训
36
全局策略- VPN-1/FireWall-1 NG Implied 规则
checkpoint防火墙培训
checkpoint防火墙培训
54
第二部分:
• 问题 #2:
• implicit 和 explicit 规则有什么不同?
Implicit (or pseudo) rules are created by VPN-1/FireWall-1 NG, and are derived from the security properties.
checkpoint防火墙培训
51
– SecureUpdate 界面
checkpoint防火墙培训
52
第二部分:
• 复习 • 问题解答
checkpoint防火墙培训
双CheckPoint防火墙实施方案

双CheckPoint防火墙实施方案目录第一章客户环境概述 (4)1.1概述 (4)1.2网络拓扑与地址分配表 (4)1.3安装前准备事宜 (6)第二章Nokia IP380安装与配置 (7)2.1概述 (7)2.2初始化nokia380 (7)2.3设置nokia基本信息 (8)2.3.1 Nokia 端口IP地址设定 (8)2.3.2设置网关路由 (8)2.3.3设置Nokia平台时间 (9)2.3.4设定Nokia高可用VRRP参数 (9)2.4初始化checkpoint (14)2.4.1在nokia平台上checkpoint的安装与卸载 (14)2.4.2初始化checkpoint (16)第三章管理服务器的安装与配置 (17)3.1checkpoint smartcenter的安装 (18)3.1.1安装前的准备 (18)3.1.2安装步骤 (18)3.2配置checkpoint对象和参数 (20)3.2.1 建立sic (20)3.2.2 定义防火墙对象拓扑结构 (21)3.2.3使用同样的步骤按照表1的参数建立IP380B checkpoint gateway对象。
(21)3.3基于nokia vrrp或者cluster的设置 (22)3.3.1基于Nokia VRRP的设置 (22)3.3.2为nokia vrrp定义策略 (22)3.3.3高可用性的检查 (23)3.4nokia cluster 的设置 (23)3.5暂时没有 (23)第四章策略设定 (24)4.1概述 (24)4.2 netscreen的策略 (24)4.3经过整理后转换成checkpoint的策略 (24)4.4 设定策略 (24)4.4.1 定义主机对象 (24)4.4.2 定义网络对象 (25)4.4.3定义组 (26)4.4.4 定义服务 (26)4.4.5 添加标准策略 (27)4.4.6 添加NAT策略 (27)第五章切换与测试 (29)5.1切换 (29)5.2测试 (29)5.3回退 (30)第六章日常维护 (31)6.1防火墙的备份与恢复 (31)6.1.1 nokia 防火墙的备份与恢复方法 (31)6.1.2 checkpoint management 上的备份与恢复 (33)第一章客户环境概述1.1概述XXXXXX公司因应企业内部的网络需求,对总部网络进行扩容改动,中心防火墙从原来的netscreen换成两台Nokia IP380,两台nokia互为热备。
Checkpoint防火墙实施维护手册
Checkpoint防火墙实施维护手册一、前言经过一段时间的学习和实际的工作,下面把学习和工作中的一些资料加以整理,方便以后更好地工作。
由于学习不系统和工作经验不足,有什么错漏的地方希望大家不吝指教。
二、防火墙的创建1、创建Gateway防火墙◆创建Gateway对象◆选择创建防火墙的模式◆配置防火墙的基本属性◆编辑防火墙的拓扑◆编辑防地址欺骗首先双击外网接口,在下面弹出的对话框中选择Topology。
选择如图所示外网口Anti-Spoofing功能启用了。
首先双击内网接口,在下面弹出的对话框中选择Topology。
选择如图所示内网口Anti-Spoofing功能启用了。
2、创建Cluster防火墙◆创建Cluster对象◆选择创建防火墙的模式◆配置防火墙的基本属性◆添加并配置Cluster成员注:IP为的管理地址(192.168.0.246)◆输入SIC码添加Cluster2同理◆编辑Topology点击Edit Topology进入编辑窗口,在编辑窗口点击Get all members’topology按钮,topology内容自动获取:如要修改,双击要修改的内容,在弹出的窗口中修改:编辑完成后,在Topology属性中能看到完整的Topology结构:3、创建VXS防火墙◆创建vsx对象◆配置vsx基本属性 ip address为管理地址◆添加物理接口◆编辑vsx拓扑◆添加接口◆添加路由◆添加vr◆配置vr属性◆配置vr拓扑◆创建vs◆配置vs基本属性◆配置vs拓扑◆创建vsw◆配置vsw基本属性◆配置vsw拓扑三、Nodes和Networks的创建1、添加Nodes对象2、添加Networks对象四、策略的创建1、策略和对象的管理◆策略包管理 (Policy package management)(仅包含规则集)◆给策略包命名并选择策略类型:◆数据库版本控制 (Database Revision Control) (包括对象和规则集)2、编辑策略◆添加新策略,选择Rules->Add Rule->Below或者点击红圈中的添加按钮:配置策略内容(在需要添加的地方点击右键添加,已经有定义好的对象拖拽也可):NO:规则序号NAME:规则名称SOURCE:源地址DESTINATION:目的地址SERVICE:选择允许或禁止的服务ACTION:此策略要做的动作(Accept,Drop,Reject)TRACK:是否要记录日志(Log,Alert,Account)INSTALL ON:选择安装在那个防火墙上TIME:可以编辑策略生效的时间段◆Server的添加假如列表中没有server,可以自己新建3、下发策略◆选择Policy->Install或者点击红圈下发按钮◆在弹出的对话框中选择策略安装的防火墙,点击OK下发五、NAT配置1、静态地址映射◆将Nodes做静态地址映射◆将Networks做静态地址映射2、动态地址映射◆将Nodes做动态地址映射◆将Networks做动态地址映射动态映射的地址可以是Gateway也可以映射到指定的IP Address3、手工添加NAT4、针对不同的防火墙映射成不同的地址六、添加License◆确认服务器与防火墙是否相通◆假如原来有License,把原来的License Detach◆在防火墙上重置SIC,然后在服务器上重建SIC连接◆把Licenses添加到管理服务器上◆在服务器上Attach/Get Licenses◆在防火墙上Attach/Get Licenses◆最后检查Licenses是否生效七、查看防火墙状态◆SmartView Monitor中可查看防火墙运行状态◆查看防火墙状态、CPU利用率、内存利用率、硬盘剩余百分比八、查看日志◆在SmartView Tracker中可查看日志◆双击日志可以查看日志的详细信息◆使用日志过滤方便查看关心的日志九、备份和恢复1、管理服务器的定期备份Unix、Linux和Solaris系统下,$FWDIR/conf 和 $FWDIR/lib 目录需要定期备份。
checkpoint扫盲

checkpoint扫盲什么是checkpoint在数据库系统中,写日志和写数据文件是数据库中IO消耗最大的两种操作,在这两种操作中写数据文件属于分散写,写日志文件是顺序写,因此为了保证数据库的性能,通常数据库都是保证在提交(commit)完成之前要先保证日志都被写入到日志文件中,而脏数据块着保存在数据缓存(buffer cache)中再不定期的分批写入到数据文件中。
也就是说日志写入和提交操作是同步的,而数据写入和提交操作是不同步的。
这样就存在一个问题,当一个数据库崩溃的时候并不能保证缓存里面的脏数据全部写入到数据文件中,这样在实例启动的时候就要使用日志文件进行恢复操作,将数据库恢复到崩溃之前的状态,保证数据的一致性。
检查点是这个过程中的重要机制,通过它来确定,恢复时哪些重做日志应该被扫描并应用于恢复。
一般所说的checkpoint是一个数据库事件(event),checkpoint事件由checkpoint 进程(LGWR/CKPT进程)发出,当checkpoint事件发生时DBWn会将脏块写入到磁盘中,同时数据文件和控制文件的文件头也会被更新以记录checkpoint信息。
checkpoint的作用checkpoint主要2个作用:1.保证数据库的一致性,这是指将脏数据写入到硬盘,保证内存和硬盘上的数据是一样的;2.缩短实例恢复的时间,实例恢复要把实例异常关闭前没有写出到硬盘的脏数据通过日志进行恢复。
如果脏块过多,实例恢复的时间也会很长,检查点的发生可以减少脏块的数量,从而提高实例恢复的时间。
通俗的说checkpoint就像word的自动保存一样。
检查点分类∙完全检查点(Normal checkpoint)∙增量检查点(Incremental checkpoint)checkpoint相关概念术语在说明checkpoint工作原理之前我们先了解一些相关的术语。
RBA(Redo Byte Address), Low RBA(LRBA), High RBA(HRBA)RBA就是重做日志块(redo log block)的地址,相当与数据文件中的ROWID,通过这个地址来定位重做日志块。
Check Point 安全管理 R80 管理员手册说明书

C l a s s i f i c a t i o n : [P r o t e c t e d ]© 2017 Check Point Software Technologies Ltd.保留所有权利。
本产品及相关文档受版权保护,并且凭限制其使用、复制、分发及反编译的许可进行分销。
未经Check Point 的事先书面授权,不得对本产品或相关文档的任何部分,以任何形式或任何方式进行复制。
在本手册编制过程中以已非常谨慎,但Check Point 不对任何错误或疏漏承担责任。
本出版物及其中所述功能如有更改,恕不另行通知。
限制权利图注:政府的使用、复制或纰漏须符合DFARS 252.227-7013 和FAR 52.227-19 的“技术数据和计算机软件权利”一条中第(c)(1)(ii) 款规定的限制。
商标:参考版权页/copyright.html以获取我们的商标清单。
参考第三方版权声明/3rd_party_copyright.html以获取相关版权和第三方许可的清单。
重要信息Latest Software我们建议您安装最新版软件,以获得最新的完善功能、更好的稳定性、更高的安全级别,并防止发展中的新攻击入侵。
Check Point R80如需更多有关此版本的信息,请参见R80主页/solutions?id=sk108623。
Latest Version of this Document下载此文档的最新版本/documentation_download?ID=46534。
如需了解更多内容,请访问Check Point 支持中心 。
FeedbackCheck Point 一直在致力于完善其文档。
请发送您的意见给我们,以帮助我们不断改进mailto:**********************************?subject=FeedbackonCheckPointSecurity Management R80 Administration Guide 。
Checkpoint防火墙命令行维护手册

Checkpoint防火墙命令行维护手册制订模版:NGX-R65版本号:V1.0目录一、基本配置命令 (1)1.1SYSCONFIG (1)1.2CPCONFIG (2)1.3CPSTOP (3)1.4CPSTART (3)1.5EXPERT (3)1.6IDLE (4)1.7WEBUI (4)1.8脚本添加路由 (4)二、查看系统状态 (1)2.1TOP (1)2.2DF –H (1)2.3FREE (1)三、HA相关命令 (1)3.1CPHAPROB STAT (1)3.2CPHAPROB –A IF (1)3.3CPHACONF SET_CCP BROADCAST (1)3.4CPHAPROB LIST (1)3.5CPHASTART/CPHASTOP (2)3.6FW CTL PSTAT (2)四、常用维护命令 (1)4.1VER (1)4.2FW VER (1)4.3查看防火墙UTM/POWER版本 (1)4.4查看防火墙硬件型号 (1)4.5LICENSE查看和添加 (1)4.6IFCONFIG/IFCONFIG –A (1)4.7MII-TOOL (1)4.8ETHTOOL (1)4.9CPSTAT FW (2)4.10会话数查看 (1)五、日志查看命令 (1)5.1FW LOG (1)5.2FW LSLOGS (1)5.3FW LSLOGS –E (1)5.4FW LOGSWITCH (1)5.5导出日志文件 (1)六、防火墙的备份和恢复 (1)6.1备份防火墙 (1)6.2在IE中备份 (1)6.3在防火墙上备份 (2)6.4恢复防火墙 (2)一、基本配置命令1.1sysconfig可以对系统进行配置和修改,比如主机名修改,DNS配置修改,以及路由的配置等,另外还可以配置DHCP功能,以及产品的安装等等如上图所示,在命令提示符输入:sysconfig,将会出现下图所列一些选项,在Your choice 后面输入你想配置的选项前的数字,然后按回车可以看到,依次的选项为主机名,域名,域名服务,时间和日期,网络连接,路由,DHCP 服务配置,DHCP中继配置,产品安装,产品配置等例如我们选择5,为防火墙新增一个接口IP地址然后选择2,进行连接配置,也就是配置IP地址选择1进行IP地址配置更改如上图所示按照提示配置IP地址和子网掩码进行其他配置也如同上述操作,选择对应的编号然后按照提示进行配置1.2cpconfig可以对checkpoint防火墙进行相关的配置,如下图所示,也是按照列表的形式列出,分别是license,snmp,PKCS#11令牌,随机池,SIC,禁用cluster,禁用安全加速,产品自动启动常用的选项一般为SIC的配置,cluster功能模块的启用等;选择7是开启cluster功能模块;选择5是设置SIC。
Checkpoint防火墙命令行维护手册

Checkpoint防火墙命令行维护手册制订模版:NGX-R65版本号:V1.0目录一、基本配置命令 (1)1.1 SYSCONFIG (1)1.2 CPCONFIG (2)1.3 CPSTOP (3)1.4 CPSTART (3)1.5 EXPERT (3)1.6 IDLE (4)1.7 WEBUI (4)1.8 脚本添加路由 (4)二、查看系统状态 (1)2.1 TOP (1)2.2 DF –H (2)2.3 FREE (2)三、HA相关命令 (1)3.1 CPHAPROB STAT (1)3.2 CPHAPROB –A IF (1)3.3 CPHACONF SET_CCP BROADCAST (1)3.4 CPHAPROB LIST (2)3.5 CPHASTART/CPHASTOP (3)3.6 FW CTL PSTAT (3)四、常用维护命令 (1)4.1 VER (1)4.2 FW VER (1)4.3 查看防火墙UTM/POWER版本 (1)4.4 查看防火墙硬件型号 (1)4.5 LICENSE查看和添加 (1)4.6 IFCONFIG/IFCONFIG –A (1)4.7 MII-TOOL (1)4.8 ETHTOOL (1)4.9 CPSTAT FW (2)4.10 会话数查看 (1)五、日志查看命令 (1)5.1 FW LOG (1)5.2 FW LSLOGS (1)5.3 FW LSLOGS –E (1)5.4 FW LOGSWITCH (1)5.5 导出日志文件 (2)六、防火墙的备份和恢复 (1)6.1 备份防火墙 (1)6.2 在IE中备份 (1)6.3 在防火墙上备份 (2)6.4 恢复防火墙 (2)一、基本配置命令1.1sysconfig可以对系统进行配置和修改,比如主机名修改,DNS配置修改,以及路由的配置等,另外还可以配置DHCP功能,以及产品的安装等等如上图所示,在命令提示符输入:sysconfig,将会出现下图所列一些选项,在Your choice后面输入你想配置的选项前的数字,然后按回车可以看到,依次的选项为主机名,域名,域名服务,时间和日期,网络连接,路由,DHCP 服务配置,DHCP中继配置,产品安装,产品配置等例如我们选择5,为防火墙新增一个接口IP地址然后选择2,进行连接配置,也就是配置IP地址选择1进行IP地址配置更改如上图所示按照提示配置IP地址和子网掩码进行其他配置也如同上述操作,选择对应的编号然后按照提示进行配置1.2cpconfig可以对checkpoint防火墙进行相关的配置,如下图所示,也是按照列表的形式列出,分别是license,snmp,PKCS#11令牌,随机池,SIC,禁用cluster,禁用安全加速,产品自动启动常用的选项一般为SIC的配置,cluster功能模块的启用等;选择7是开启cluster功能模块;选择5是设置SIC。
Check Point安全解决方案-example

XXXXXX有限公司防火墙安全管理方案目录1防火墙设计方案 (3)1.1概述 (3)1.2防火墙设计目标 (3)1.3新数据中心防火墙的部署 (4)1.4产品选型分析 (4)2 防火墙安全管理设计方案 (5)2.1当前防火墙管理模式 (5)2.2存在的问题 (6)2.3建议方案 (6)2.3.1方案(一):Smart Center集中管理 (6)2.3.2方案(二):Provider-1分权管理 (7)2.3.3 Provider-1版本的选择 (8)2.3.4 Provider-1扩展性分析 (8)2.4 部署方案 (8)3 产品配置清单 (10)3.1方案(一)Smart Center集中管理配置清单 (10)3.2 方案(二)Provider-1分权管理配置清单 (11)1防火墙设计方案1.1概述此次防火墙项目涉及到新数据中心边界安全的建设,同时担当着安全域划分的角色,即根据功能、安全等级、策略定义等因素进行安全隔离与管控,把复杂的安全问题缩小到局部范围内。
因此,防火墙产品必须满足高安全性、高稳定性、可扩展性、可管理性等四个要求。
根据XXXXX目前网络安全的部署情况来看,Check Point防火墙已经帮助XXXXX实现了XXXX及分公司的网络边界的高安全性,作为网络安全的基石,保护企业内部网络来自Internet的各种攻击与威胁。
因此,为了实现边界安全建设的四个要求,在新数据中心的建设中我们依旧选择Check Point防火墙产品。
1.2防火墙设计目标(1)保护脆弱的服务通过过滤不安全的服务,防火墙可以极大地提高网络安全和减少子网中主机的风险。
例如,防火墙可以过滤保护NIS、NFS、SSH、SQL、CIFS等高风险级别的服务,同时可以拒绝SYN Flood、UDP Flood、源路由和ICMP重定向封包等攻击。
(2)控制对系统的访问防火墙可以提供对系统的访问控制。
如允许从外部访问某些主机的特定端口,同时禁止访问其他服务或其他主机。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Secure Internal Communications (SIC) 26-Jun-2001NG-FCS VersionAbstractCheck Point Software has enhanced the Internal Communications method for the components within a Next Generation (NG) Check Point System. This method is based on Digital Certificates, and will be further described below. This is a new and improved method for all of the internal communications, so if you are familiar with "fw putkeys", you will not have to go back there…Document Title: Secure Internal CommunicationsCreation Date: 08-Feb-2001Modified Date: 26-Jun-2001Document Revision: 2 (meaning this is the 3rd revision)Product Class: FireWall-1 / VPN-1Product and Version: NGAuthor: Joe DiPietroDISCLAIMERThe Origin of this information may be internal or external to Check Point Software Technologies. Check Point Software Technologies makes all reasonable efforts to verify this information. However, the information provided in this document is for your information only. Check Point Software Technologies makes no explicit or implied claims to the validity of this information.Any trademarks referenced in this document are the property of their respective owners. Consult your product manuals for complete trademark information.Given the Diagram below, we will establish a Trust Relationship with the Management Station and the FireWall-1 Module. The Management Server is located at 10.1.2.3, and the FireWall-1 Module will be defined as 10.1.2.1.Table of ContentsDescription Page SIC Overview (3)FireWall-1 Object Definition on Management Station (4)Initialize Trust Relationship (5)Interface Definition (6)Policy Install (8)Troubleshooting (9)Netstat (9)cpstop/cpstart (10)cpd –d (10)Secure Internal Communications (SIC) is the new method for how Check Point components will communicate with each other in Check Point Next Generation (NG). It is based on SSL with Digital Certificates. When you install the management station, you will create a Certificate Authority (CA). This Certificate Authority will issue certificates for all components that need to communicate to each other. For example, a distributed FireWall-1 Module will need a certificate from the management station prior to downloading a policy to this module (or even licensing this module remotely via the new license method). Here is a quick snapshot of a Primary Management Station installation, where the CA will be created.Once the Primary Management Station is up and active, then it can initialize the remote FireWall-1 Module if it has the same One Time Password (OTP). The following screen shows a snapshot of the FireWall-1 Module installation, where youmust enter a One Time Password(OTP) for the InitializationProcess with the ManagementStation. You can also run"cpconfig" after the installationand initialize the OTP at thatpoint.FireWall-1 Module InstallationDefining the Network Object on the Management StationWhen defining the Network Object for SIC communications on the Management Station, the password entered must match the OTP defined on the module, in order for the Certificate to be distributed to the FireWall-1 Module and communications to be established. The screen below shows the object definition for a FireWall-1 Module. This has changed significantly from prior versions.In this example, the Module is a "Gateway " with Check Point version "NG " Installed.Also, note that you must now select what components are installed on this machine. In our case, we have VPN-1 & FireWall-1 installed .Please notice that until the DN: portion is filled in, we are not communicating with thismodule. We must now select Communication in order to initialize the SIC process.Remember, the Management Station must be able tocommunicate to the Remote Module before you can "remotely" apply the Check Point license from the Management Station.By selecting "communication " above, thescreen on the left appears. This is where we need to enter the OTP that was defined on the FireWall-1 Module during installation as shown below.Next select, InitializeNotice that we now have a "Trust" relationshipestablished between the Management Station and the FireWall-1 Module. SIC is now up and running.Unlike putkeys, it is possible to check that SIC is Working. Using the Test SIC status you will see that GW1 is communicating.NB: Name resolution must be functioning correctly.The Management Station is nowcommunicating with the FireWall-1 Module, and the Certificate has been issued and received. Notice the DN: field at the bottom of this object. It is now filled in with the appropriate information.Next, continue defining the other components of the Gateway Object so that the Management Station will be able to push a policy to the FireWall-1 Module.You must define the FireWall-1 “interfaces ” at a minimum. Select the “Topology ” tab, and then Select “Get Interfaces ”.The screen to the left will show up with filled in Interface Information.Next, Edit the interface information.Next Select the “Topology” tab of the Interface Properties. This is where we will define what connects to this particular Interface. In our example, this interface will connect to the Internet. Also note, that Anti-Spoofing information can be based off of the Topology Information defined here.Define the Internal Interface information as shown.Now the final interface definition is shown on the RightThis is where we can also define the VPN Domain information. So far, we have the following Network Diagram as created by the Visual Policy Editor.The Management Station (mgmt-p- 10.1.2.3), the FireWall-1 Gateway (GW1- 10.1.2.1), and the three networks defined by the topology information(10.1.2.1/255.255.255.0), (192.168.10.0/255.255.255.0), and (199.203.71.0/255.255.255.0) which connects to the Internet Cloud.If we select “Show” under the “VPN Domain” in the screen above, this will show us what the“Encryption” domain will be calculated to be. It is shown in the screen below with the highlighted objects in Red.For our Purposes, we will make it just the 192.168.10.0 network. So the final VPN Topology information will be as follows:Please note that we have made this topology “exportable” for SecuRemote. This will allow us to download this topology information to the SecuRemote machine.Now we can push the policy:Select “OK ” from the scre en on the right, and the screen below will appear:Notice that the Policy was successfully installed.TroubleshootingIf you get the following error message, a number of things could be wrong:1. Connectivity issues from the ManagementStation to the FireWall-1 Module2. CPshared is not installed on the FireWall-1Module3. The FireWall-1 Module is not listening on theproper ports for the SIC communicationsThis is the next screen that appears on the Management Station. This means the digitalcertificate has been initialized on the CA, but has not been delivered to the FireWall-1 Module.Let's troubleshoot at the FireWall-1 ModuleFirst check the Network Port that SIC is trying to listen on with the"netstat" command. It should be listening on port 18211 as shown to the right.If you see the screen above, reset your OTP by using the CPCONFIG utility as shown to the right by selecting:Start → Programs → Check Point Management Clients → Check Point Configuration NG on the FireWall-1 ModuleRemember to use the same password on theManagement Station, as you define within this screen.After you initialize the OTP again, then try and Initialize the object at the management station.If you don't see the host listening on this port, then perform the following steps as shown belowThere is a common infrastructure component called "CPShared" with Check Point NG. This component is located under C:\Program Files\CheckPoint\CPShared\5.0. There is a subdirectory call "bin", which has all of the commands for this shared component. To stop and start the shared component infrastructure, use the commands "CPSTOP " and "CPSTART " respectively. An excellent troubleshooting program for this communications is the "CPD " application. To troubleshooting the SIC communications between the Management Station and the FireWall-1 Module, perform the following steps on the FireWall-1 Module. First stop all of the FireWall-1 Processes on the module with the "cpstop" command.Now, put the Module into Debug Mode by running the CPD application with the "-d" flag.Now try and "initialize" the FireWall-1 object on the Management Station by selecting the "Initialize" button as shown to the right.If the OTP's are in sync, then you should see the "Trust Established" on the management station, as shown to the right.On the FireWall-1 Module, you will see the following:If the FireWall-1 Module already has a certificate, as shown below:Re-initialize the OTP, so that the Management Station can issue the correct certificate to this FireWall-1 Module.In this particular case, SIC has already been initialized on this module, but unable to communicate with the Management Station. You have to reset the OTP in order to get another certificate from the Management Station as shown below.Select "Reset " as shown on the rightThe following screen will appear to remind you that the OTP's must be the same on the Management Station object, and the FireWall-1 Module.Select "Yes", and then enter the OTP on the FireWall-1 Module.Next restart the "CPShare" processes by issuing "cpstop " and then "cpstart " commands.Next, try to "initialize" the Object at the Management Station, and you should see the following screen to the right.。
