15213RecitationSectionC
linux c entercriticalsection -回复

linux c entercriticalsection -回复如何在Linux中实现进入临界区。
在多线程编程中,如果多个线程同时访问共享数据,可能会发生竞态条件(Race Condition)问题,导致程序出错或产生不正确的结果。
为了避免这种情况的发生,我们需要引入临界区(Critical Section)的概念。
临界区是指一段代码,当某个线程进入临界区时,其他线程需要等待,直到当前线程离开临界区为止。
在Linux中,我们可以使用互斥锁来实现进入临界区的操作。
下面是一步一步的解释:1. 引入头文件首先,我们需要引入pthread.h头文件,该头文件包含了我们需要用到的线程相关的函数和数据类型的声明。
我们需要在代码的开头添加以下一行代码:#include <pthread.h>2. 创建互斥锁接下来,我们需要创建一个互斥锁,用来控制临界区的访问。
可以通过声明一个pthread_mutex_t类型的变量来创建互斥锁。
在主函数中添加以下代码:pthread_mutex_t mutex;3. 初始化互斥锁创建完互斥锁后,我们需要对其进行初始化。
可以使用pthread_mutex_init函数来完成初始化操作。
在主函数中添加以下代码:pthread_mutex_init(&mutex, NULL);4. 进入临界区当需要进入临界区时,我们可以使用pthread_mutex_lock函数来获取对互斥锁的锁定。
这会阻塞其他线程对互斥锁的访问,直到当前线程释放锁。
在需要进入临界区的代码之前添加以下代码:pthread_mutex_lock(&mutex);5. 临界区代码在获取了互斥锁之后,我们可以放心地执行临界区代码,因为此时其他线程无法进入该区域。
在这段代码中,我们可以安全地操作共享数据,而不用担心竞态条件的问题。
6. 离开临界区当当前线程完成对临界区的操作后,我们需要释放互斥锁,以允许其他线程再次进入临界区。
linux c entercriticalsection -回复

linux c entercriticalsection -回复在Linux C中,如何进入临界区(Enter Critical Section)临界区是指在多线程程序中只能被一个线程访问的代码片段。
在临界区中,访问共享资源的操作是互斥的,这样可以避免并发访问导致的数据竞争和不确定的结果。
在Linux C中,我们可以使用多种方法来实现临界区的进入。
下面将一步一步回答以下问题,详细介绍这些方法。
问题1:什么是临界区?在多线程程序中,临界区是指一段代码片段,在同一时间内只能由一个线程访问。
在临界区中,对共享资源的访问需要进行互斥操作,以保证数据的一致性和正确性。
问题2:为什么需要临界区?在多线程程序中,多个线程可能同时访问共享资源,如果不对访问进行控制,可能会导致数据竞争和不确定的结果。
通过使用临界区,可以确保多个线程按照规定的顺序访问共享资源,避免并发访问导致的问题。
问题3:如何进入临界区?在Linux C中,有多种方法可以实现临界区的进入。
下面将介绍三种常用的方法:互斥锁、条件变量和原子操作。
方法1:互斥锁互斥锁是一种最常用的同步机制,可以用于实现临界区的进入。
在Linux C 中,可以使用pthread_mutex_t结构体来表示一个互斥锁,相关的函数包括pthread_mutex_init、pthread_mutex_lock和pthread_mutex_unlock。
首先,需要创建一个互斥锁,并进行初始化,可以使用pthread_mutex_init 函数来完成。
然后,在需要进入临界区的地方调用pthread_mutex_lock 函数,该函数将尝试获取互斥锁。
如果获取成功,表示进入临界区,否则会一直等待直到获取到锁。
在临界区的代码执行完毕后,需要调用pthread_mutex_unlock函数释放互斥锁,以便其他线程可以获取锁并进入临界区。
方法2:条件变量条件变量是一种用于线程间通信的同步机制,也可以用于实现临界区的进入。
iar section用法

iar section用法"IAR section"通常指的是在IAR Embedded Workbench中用于定义内存区段(Memory Sections)的一种方式。
通过使用section,你可以将特定类型的数据或代码放置在特定的内存区域中,以满足嵌入式系统对内存布局的要求。
以下是一些关于IAR section用法的基本信息:1. 声明Section使用`#pragma`指令声明一个section。
例如:```c#pragma location=".my_section"const char myData[] = "Hello, World!";```这将把`myData`数组放置在名为`.my_section`的内存区域中。
2. 指定Section属性你还可以指定section的属性,如`ro`(read-only)或`zi`(zero-initialized)。
例如:```c#pragma location=".my_section"#pragma data_alignment=4const char myData[] = "Hello, World!";```这将`myData`数组放置在`.my_section`中,并确保数据按照4字节对齐。
3. 使用IAR IDE设置Section属性在IAR Embedded Workbench的IDE中,你也可以通过图形界面设置section属性。
在项目文件的Options中,选择Linker选项卡,然后在Memory Regions部分添加或编辑sections。
4. Linker Configuration文件你还可以通过IAR的Linker Configuration文件(通常是`.icf`文件)来配置section。
在该文件中,你可以更详细地定义内存区域的起始地址、大小等。
PILZ编程手册翻译

2.3.3 Program blocks (PB) 过程块.........................................................................................2-15 2.3.4 Function blocks (FB) 函数块 .........................................................................................2-15
2.3.5 Standard function blocks (SB) 标准函数块 ..................................................................2-21
2.3.5.1 Parameters 参数 ................................................................................................................ 2-22 2.3.5.2 Programming and calling SBs 编写和调用SB块 ................................................................2-22 2.3.5.3 Standard function blocks from Pilz PILZ提供的SB ..............................................................2-22
windows initializecriticalsection

windows initializecriticalsection Windows InitializeCriticalSectionWindows InitializeCriticalSection是一种同步对象,用于保护多个线程同时访问共享资源时的互斥。
InitializeCriticalSection函数用于初始化一个临界区对象,以便可以使用EnterCriticalSection和LeaveCriticalSection函数来管理它。
本文将详细介绍Windows InitializeCriticalSection的相关知识。
一、InitializeCriticalSection函数概述1.1 函数定义BOOL WINAPI InitializeCriticalSection(_Out_ LPCRITICAL_SECTION lpCriticalSection);1.2 函数参数lpCriticalSection:指向CRITICAL_SECTION结构体的指针,该结构体用于表示要初始化的临界区对象。
1.3 函数返回值如果函数成功,则返回TRUE;如果失败,则返回FALSE。
二、CRITICAL_SECTION结构体概述2.1 结构体定义typedef struct _CRITICAL_SECTION {PVOID DebugInfo;LONG LockCount;LONG RecursionCount;HANDLE OwningThread;HANDLE LockSemaphore;ULONG_PTR SpinCount;} CRITICAL_SECTION, *PCRITICAL_SECTION, LPCRITICAL_SECTION;2.2 结构体成员变量说明DebugInfo:指向调试信息的指针。
LockCount:表示当前持有临界区对象的线程数。
RecursionCount:表示当前线程已经进入临界区对象的次数。
C语言常见错误代码释义之欧阳引擎创编

C语言常见错误代码释义欧阳引擎(2021.01.01)错误代码及错误信息错误释义error 1: Out of memory内存溢出error 2: Identifier expected 缺标识符error 3: Unknown identifier 未定义的标识符error 4: Duplicate identifier重复定义的标识符error 5: Syntax error 语法错误error 6: Error in real constant 实型常量错误error 7: Eiror in integer constant 整型常量错误enor 8: String constant exceeds line 字符串常量超过一行error 10: Unexpected end of file 文件非正常结束error 11: Line too long 行太长enor 12: Type identifier expected 未定义的类型标识符error 13: Too many open files打开文件太多enor 14: Invalid file name无效的文件名error 15: File not found 文件未找到error 16: Disk full 磁盘满error 17: Invalid compiler directive 无效的编译命令error 18: Too many files 文件太多error 19: Undefined type in pointer def 指针定义中未定义类型eiror 20: Variable identifier expected 缺变量标识符error 21: Error in type 类型错误error 22: Structure too large 结构类型太长error 23: Set base type out of range 集合基类型越界error 24: File components may not be files or objectsfile 分量不能是文彳牛或对象error 25: Invalid string length 无效的字符串长度error 26: Type mismatch 类型不匹配error 27: error 27: Invalid subrange base type 无效的子界基类型eiTor 28 : Lower bound greater than upper bound 下界超过上界error 29: Ordinal type expected 缺有序类型error 30: Integer constant expected 缺整型常量enor 31 : Constant expected 缺常量error 32 : Integer or real constant expected 缺整型或实型常量error 33 : Pointer Type identifier expected 缺指针类型标识符error 34: Invalid function result type 无效的函数结果类型error 35 : Label identifier expected缺标号标识符error 36 : BEGIN expected 缺BEGINerror 37 : END expected 缺ENDerror 38 : Integer expression expected 缺整型表达式eiTor 39: Ordinal expression expected 缺有序类型表达式error 40 : Boolean expression expected 缺布尔表达式enor 41 : Operand types do not match 操作数类型不匹配error 42: Error in expression 表达式错误error 43 : Illegal assignment 非法赋值error 44: Field identifier expected 缺域标识符eixor 45 : Object file too large目标文件太大error 46: Undefined external未定义的外部过程与函数error 47: Invalid object file record 无效的OBJ 文件格式error 48: Code segment too large 代码段太长eixor 49: Data segment too large 数据段太长error 50: DO expected 缺DOerror 51: Invalid PUBLIC definition 无效的PUBLIC 定义error 52: Invalid EXTRN definition 无效的EXTRN 定义error 53: Too many EXTRN definitions 太多的EXTRN 定义error 54: OF expected 缺OFerror 55 : INTERFACE expected 缺INTERFACEerror 56 : Invalid relocatable reference 无效的可重定位引用error 57 : THEN expected 缺THENerror 58 : TO or DOWNTO expected 缺TO 或DOWNTOerror 59: Undefined forward 提前引用未经定义的说明error 61 : Invalid typecast 无效的类型转换error 62 :Division by zero 被零除eiror 63 : Invalid file type 无效的文件类型eiror 64: Cannot read or write variables of this type 不能读写此类型变量error 65 : Pointer variable expected缺指针类型变量error 66: String variable expected 缺字符串变量error 67: String expression expected 缺字符串表达式enor 68 : Circular unit reference 单元UNIT 部件循环引用error 69: Unit name mismatch 单元名不匹配error 70: Unit version mismatch单元版本不匹配error 71 : Internal stack overflow 内部堆栈溢出error 72: Unit file format eiror 单元文件格式错误error 73 : IMPLEMENTATION expected 缺IMPLEMENTATIONerror 74 : Constant and case types do not match 常量和CASE 类型不匹配error 75 : Record or object variable expected 缺记录或对象变量error 76: Constant out of range 常量越界error 77 : File variable expected 缺文件变量error 78 : Pointer expression expected 缺指针表达式error 79 : Integer or real expression expected 缺整型或实型表达式error 80: Label not within current block 标号不在当前块内error 81: Label already defined 标号已定义error 82: Undefined label in preceding statement part 在前面未定义标号error 83 : Invalid @ argument 无效的 @参数error 84 : UNIT expected 缺UNITenor 85:expected 缺";5"error 86 : M:n expected 缺":P ITOT 87 : expected 缺",''error 88 : ”(”expected 缺“ ("error 89 :")" expected 缺“)"eiior 90 : "=" expected 缺“=''erroT 91 : n:=" expected 缺“:=''eiTor 92: or ”Expected 缺或“(."enoT 93:T or expected 缺“]”或“.)"error 94: ”・” expected 缺“."error 95: expected 缺".."erroT 96 : Too many variables 变量太多error 97: Invalid FOR control variable 无效的FOR 循环控制变量error 98: Integer variable expected 缺整型变量error 99: Files and procedure types are not allowed here该处不允许文件和过程类型error 100:String length mismatch 字符串长度不匹配error 101 : Invalid ordering of fields 无效域顺序error 102: String constant expected 缺字符串常量error 103 : Integer or real variable expected 缺整型或实型变量eiTor 104: Ordinal variable expected缺有序类型变量error 105 : INLINE eixor INLINE 错误enor 106 : Character expression expected 缺字符表达式error 107 : Too many relocation items 重定位项太多error 108 : Overflow in arithmetic operation 算术运算溢出error 112 : CASE constant out of range CASE 常量越界error 113 : Error in statement 表达式错误error 114: Cannot call an interrupt procedure 不能调用中断过程error 116: Must be in 8087 mode to compile this 必须在8087 模式编译error 117: Target address not found 找不到目标地址error 118 : Include files are not allowed here 该处不允许INCLUDE 文件error 119: No inherited methods are accessible here 该处继承方法不可访问error 121 : Invalid qualifier 无效的限定符error 122: Invalid variable reference 无效的变量引用error 123: Too many symbols 符号太多error 124 : Statement part too large 语句体太长error126: Files must be var parameters 文件必须是变量形参error127: Too many conditional symbols 条件符号太多error 128 : Misplaced conditional directive 条件指令错位error 129 : ENDIF directive missing 缺ENDIF 指令eixor 130 : Eixor in initial conditional defines 初始条件定义错误error 131: Header does not match previous definition和前面定义的过程或函数不匹配error133: Cannot evaluate this expression 不能计算该表达式error134: Expression incorrectly terminated 表达式错误结束error 135: Invalid format specifier 无效格式说明符error 136:Invalid indirect reference 无效的间接引用error 137 : Structured variables are not allowed here 该处不允许结构变量error 138 : Cannot evaluate without System unit 没有System 单元不能计算error 139: Cannot access this symbol 不能存取符号error 140: Invalid floating point operation 无效的符号运算error 141 : Cannot compile overlays to memory不能编译覆盖模块至内存error 142: Pointer or procedural variable expected 缺指针或过程变量error 143 : Invalid procedure or function reference 无效的过程或函数调用error 144 : Cannot overlay this unit 不肯总覆盖该单元error 146: File access denied 不允许文件访问error 147 : Object type expected 缺对象类型error 148 : Local object types are not allowed 不允许局部对象类型error 149 : VIRTUAL expected缺VIRTUALeiTor 150: Method identifier expected 缺方法标识符error 151: Virtual constructors are not allowed 不允许虚构造函数error 152:Constructor identifier expected 缺构造函数标识符error 153: Destructor identifier expected 缺析构函数标识符eiTor 154: Fail only allowed within constructors 只能在构造函数内使用Fail 标准过程error 155 : Invalid combination of opcode and operands 操作数与操作符无效组合error 156: Memory reference expected 缺内存引用指针error 157 : Cannot add or subtract relocatable symbols 不能加减可重定位符号error 158 : Invalid register combination 无效寄存器组合eixor 159: 286/287 instructions are not enabled 未激活286/287 指令error 160 : Invalid symbol reference 无效符号指针enor 161: Code generation error 代码生成错误error 162: ASM expected 缺ASMerror 166: Procedure or function identifier expected 缺过程或函数标识符eixor 167 : Cannot export this symbol 不能输出该符号error 168 : Duplicate export name 外部文件名重复error 169: Executable file header to error 170: Too many segments 段太多。
C语言CRITICAL_SECTION用法案例详解

C语⾔CRITICAL_SECTION⽤法案例详解很多⼈对CRITICAL_SECTION的理解是错误的,认为CRITICAL_SECTION是锁定了资源,其实,CRITICAL_SECTION是不能够“锁定”资源的,它能够完成的功能,是同步不同线程的代码段。
简单说,当⼀个线程执⾏了EnterCritialSection之后,cs⾥⾯的信息便被修改,以指明哪⼀个线程占⽤了它。
⽽此时,并没有任何资源被“锁定”。
不管什么资源,其它线程都还是可以访问的(当然,执⾏的结果可能是错误的)。
只不过,在这个线程尚未执⾏LeaveCriticalSection之前,其它线程碰到EnterCritialSection语句的话,就会处于等待状态,相当于线程被挂起了。
这种情况下,就起到了保护共享资源的作⽤。
也正由于CRITICAL_SECTION是这样发挥作⽤的,所以,必须把每⼀个线程中访问共享资源的语句都放在EnterCritialSection和LeaveCriticalSection之间。
这是初学者很容易忽略的地⽅。
当然,上⾯说的都是对于同⼀个CRITICAL_SECTION⽽⾔的。
如果⽤到两个CRITICAL_SECTION,⽐如说:第⼀个线程已经执⾏了EnterCriticalSection(&cs)并且还没有执⾏LeaveCriticalSection(&cs),这时另⼀个线程想要执⾏EnterCriticalSection(&cs2),这种情况是可以的(除⾮cs2已经被第三个线程抢先占⽤了)。
这也就是多个CRITICAL_SECTION实现同步的思想。
⽐如说我们定义了⼀个共享资源dwTime[100],两个线程ThreadFuncA和ThreadFuncB都对它进⾏读写操作。
当我们想要保证 dwTime[100]的操作完整性,即不希望写到⼀半的数据被另⼀个线程读取,那么⽤CRITICAL_SECTION来进⾏线程同步如下:第⼀个线程函数:DWORD WINAPI ThreadFuncA(LPVOID lp){EnterCriticalSection(&cs);...// 操作dwTime...LeaveCriticalSection(&cs);return 0;}写出这个函数之后,很多初学者都会错误地以为,此时cs对dwTime进⾏了锁定操作,dwTime处于cs的保护之中。
操作系统实验三、线程的互斥

操作系统实验三、线程的互斥实验三线程的互斥1.实验⽬的(1) 熟练掌握Windows系统环境下线程的创建与撤销。
(2)熟悉Windows系统提供的线程互斥API。
(3)使⽤WIndows系统提供的线程互斥API解决实际问题。
2.实验准备知识:相关API函数介绍临界区对象临界区对象(CriticalSection)包括初始化临界区(InitializeCriticalSection())、进⼊临界区(EnterCriticalSection())、退出临界区(LeaveCriticalSection())及删除临界区(DeleteCriticalSection())等API函数。
(1)初始化临界区IntializeCriticalSection() ⽤于初始化临界区对象。
原型:IntializeCriticalSection(LPCRITICAL_SECTION IpCriticalSection);参数说明:IpCriticalSection:指出临界区对象的地址。
**返回值:**⽆。
⽤法举例:LPCRITICAL_SECTION hCriticalSection;CRITICAL_SECTION Critical;hCriticalSection=&Critical;InitializeCriticalSection(hCriticalSection);(2)进⼊临界区EnterCriticalSection()等待进⼊临界区的权限,当获得该权限后进⼊临界区。
原型:VOID EnterCriticalSection(LPCRITICAL_SECTION IpCriticalSection);参数说明:IpCriticalSection:指出临界区对象的地址。
**返回值:**⽆。
LPCRITICAL_SECTION hCriticalSection;CRITICAL_SECTION Critical;hCriticalSection=&Critical;EnterCriticalSection(hCriticalSection);(3)退出临界区LeaveCriticalSection()释放临界区的使⽤权限。
深入理解CRITICAL_SECTION

深入理解CRITICAL_SECTION摘要临界区是一种防止多个线程同时执行一个特定代码节的机制,这一主题并没有引起太多关注,因而人们未能对其深刻理解。
在需要跟踪代码中的多线程处理的性能时,对 Windows 中临界区的深刻理解非常有用。
本文深入研究临界区的原理,以揭示在查找死锁和确认性能问题过程中的有用信息。
它还包含一个便利的实用工具程序,可以显示所有临界区及其当前状态。
在我们许多年的编程实践中,对于 Win32 临界区没有受到非常多的“under the hood”关注而感到非常奇怪。
当然,您可能了解有关临界区初始化与使用的基础知识,但您是否曾经花费时间来深入研究 WINNT.H 中所定义的 CRITICAL_SECTION 结构呢?在这一结构中有一些非常有意义的好东西被长期忽略。
我们将对此进行补充,并向您介绍一些很有意义的技巧,这些技巧对于跟踪那些难以察觉的多线程处理错误非常有用。
更重要的是,使用我们的 MyCriticalSections 实用工具,可以明白如何对 CRITICAL_SECTION 进行微小地扩展,以提供非常有用的特性,这些特性可用于调试和性能调整(要下载完整代码,参见本文顶部的链接)。
老实说,作者们经常忽略 CRITICAL_SECTION 结构的部分原因在于它在以下两个主要Win32 代码库中的实现有很大不同:Microsoft Windows 95 和 Windows NTH嗣侵勒饬街执肟舛家丫⒄钩龃罅亢笮姹荆ㄆ渥钚掳姹痉直鹞 Windows Me 和 Windows XP),但没有必要在此处将其一一列出。
关键在于 Windows XP 现在已经发展得非常完善,开发商可能很快就会停止对 Windows 95 系列操作系统的支持。
我们在本文中就是这么做的。
诚然,当今最受关注的是 Microsoft .NET Framework,但是良好的旧式 Win32 编程不会很快消失。
北约克综合医院政策手册说明书

North York General Hospital Policy ManualRecord Retention and Destruction Policy NUMBER:V-50CROSS REFERENCE: Privacy & Data Protection Policy V-25Legal Health Record Policy, V-80ORIGINATOR: Chief Privacy & Freedom of Information OfficerAPPROVED BY: Medical Advisory CommitteeOperations CommitteeORIGINAL DATE APPROVED June 1995LAST DATE REVIEWED/REVISED: October 2019DATE OF IMPLEMENTATION : November 2019Page 1 of 7 POLICY:All records in the custody or under the control of North York General (NYGH) will be managed, retained and securely disposed of in accordance with applicable federal and provincial statutes and NYGH policies.This policy contains the following sections:1. Definitions2. Record Retention3. Destruction4. Log, Request to Destroy, Certificate of Destruction –Personal Health Information5. Approval to Destroy and Certificate of Destruction – Corporate/General Records6. Record Retention Schedule1. Definitions:The term “record” under the Freedom of Information & Protection of Privacy Act and in this policy means any record of information however recorded, whether in printed form, on film, by electronic means or otherwise and includes,(a) correspondence, a memorandum, a book, a plan, a map, a drawing, a diagram, apictorial or graphic work, a photograph, a film, a microfilm, a sound recording, avideotape, a machine readable record, any other documentary material, regardless ofphysical form or characteristics, and any copy thereof, and(b) subject to the regulations, any record that is capable of being produced from a machinereadable record under the control of an institution by means of computer hardware and software or any other information storage equipment and technical expertise normallyused by the institution.The term ”personal health information” in the Personal Health Information Protection Act and in this policy means identifying information about an individual in oral or recorded form, if the information,a) relates to the physical or mental health of the individual, including the health history ofthe individual’s family;b) relates to the provision of health care to the individual including the identification of aperson as a health care provider to the individual;c) is a plan of service for the individual within the meaning of the Home Care andCommunity Services Act,d) relates to payments or eligibility for health care, or eligibility for health care coverage, inrespect of the individual,e) relates to the donation by of the individual of body parts or substances or is derived fromthe testing or examination of the part or substancef) the individual’s health numberg) Identifies the individual’s substitute-decision maker.The term “personal information” in the Freedom of Information & Protection of Privacy Act” and in this policy means recorded information about an identifiable individual, including:a) information relating to the race, national or ethnic origin, colour, religion age, sex, sexualorientation or marital or family status of the individual,b) information relating to the education or medical, psychiatric, psychological, criminal oremployment history of the individual or information relating to financial transactions inwhich the individual has been involved,c) any identifying number, symbol or other particular assigned to the individual,d) the address, telephone number, fingerprints or blood type of the individual,e) the personal opinions or views of the individual except where they relate to anotherindividual,f) correspondence sent to an institution by the individual that is implicitly or explicitly of aprivate or confidential nature, and replies to that correspondence that would reveal thecontents of the original correspondence,g) the views or opinions of another individual about the individual, andh) the individual’s name where it appears with other information relating to the individual orwhere the disclosure of the name would reveal other personal information about theindividual;The term “Official Custodian” means the Director of the department and/or designated individual who holds official responsibility for preservation, retention and secure disposal of records. The Official Custodian for each record series is identified in the Record Retention Schedule.2. Record Retention:All records including personal health information in the custody or under the control of NYGH will be retained according to the retention period set out in the Record Retention Schedule or longer if necessary to meeting NYGH’s legal, financial or administrative obligations.The retention periods apply to original records. The retention period for all records except financial records is calculated from the end of the calendar year in which the records were created. The retention period for financial records is calculated from the end of the fiscal year in which they were created.The department or individual designated as the Official Custodian in the Records Retention Schedule is responsible for retaining and disposing of original records in consultation with the Chief Privacy & Freedom of Information Officer or designate. Duplicate copies of the record should be disposed of when no longer needed providing they do not contain comments or quotes that may alter the purpose or direction of the record. Records containing these types ofcomments or quotes should be provided to the Official Custodian of the original records for retention. .Legal or Other Proceeding:If NYGH receives notice of a court action, or of an investigation, assessment, inspection, inquest or other inquiry (a Proceeding) before the retention period has expired from any of the following bodies:a) a professional Collegeb) the Medical Advisory Committeec) the Coronerd) a tribunale) a financial or other regulatory bodyNYGH will retain the applicable records until the Proceeding is complete. Extension of the retention period must be noted by the area/department receiving notice of the Proceeding and the necessary steps must be taken to preserve the records until the Proceeding is complete.A Proceeding is not complete until all appeals have been exhausted.Storage:Paper/Microfilm/Microfiche/film/tape: All records must be stored in a secure location and protected from theft, loss, unauthorized access, use, disclosure, modification, disposal or de-composition. The information custodian shall ensure that stored records are properly labeled as to their contents, custodianship and the retention expiry date.Electronic records must be securely stored on the NYGH network and not on personal network drives or local computer discs to ensure they are accessible and retrievable. When new software or hardware is being introduced for use or systems changed, provision must be made for conversion of existing records to the new system or, in the alternative, for accessible storage until the retention period has expired. Accessible storage means that the records are retrievable in a timely fashion without the need of external resources.Email retention periods are determined by the content of the record i.e. by the applicable record series as described in the attached Retention Schedule. As a general rule, emails and their attachments that relate to operational, financial or accountability matters or to legal or other proceedings must be downloaded, saved offline and stored together with the subject matter files to which they relate in a timely manner. Contact the Information Services Help Desk if guidance in saving offline is needed. The copies of saved emails remaining in the email system are considered duplicates and should be regularly deleted. A Certificate of Destruction is not required when deleting duplicate emails.Email accounts of individuals no longer associated with the hospital are disabled and any copies of remaining records are destroyed after 30 days. In cases where some of these records may be relevant to a legal or other proceeding as described above,the relevant Manager/Director/Vice-President/President must notify InformationServices on or before the last employment day so that the records may be accessed and retained until the conclusion of the matter.3. Destruction:Once the retention period has been reached and there is no outstanding Proceeding, the Official Custodian will securely dispose of records in accordance with applicable laws and NYGH policies. A log of all original records destroyed must be maintained together with a Certificate of Destruction regardless of the medium or format of the record. Certificates of Destruction must be maintained by the Official Custodian identified in the Record Retention Schedule. Please note that duplicate copies may be destroyed when they are no longer needed for reference purposes and a Certificate of Destruction is not required.Destruction of hard copy records or microfilm/microfiche/film/tape that contain personal or personal health information or that have been identified as confidential will be finelyshredded/cross cut or incinerated by an NYGH approved record destruction company. Destruction of electronic records (and other media), will be subject to current, Information Technology (IT) approved processes which must ensure that reconstruction of the information is not reasonably foreseeable in the circumstances.Hardcopy Records, Microfilm/ Microfiche/Film/TapeHardcopy records, microfilm/microfiche/tape/film that have passed the NYGH Retention time period and where there is no additional reason to maintain the record for a longer period of time will be destroyed.The Official Custodian must provide prior approval of destruction. The destruction of records will be completed in consultation with the Chief Privacy & Freedom of Information Officer or designate.The log and Request to Destroy Personal Health Information and Validation of Destruction will be signed and dated by the Official Custodian and by the Chief Privacy & Freedom of Information Officer, or designate.The Master Patient Record (Index) which is retained permanently will serve as a log of patient records that have been destroyed.Hardcopy records will be finely shredded/cross cut or incinerated by an NYGH approved record destruction company.Hardcopy Health Records where an electronic copy is availableHardcopy records of Personal Health Information which have been microfilmed, scanned or printed from an electronic system will be destroyed by fine shredding/cross cut or by incineration immediately following fulfillment of the purposes for which it was printed and/or produced. Hardcopy records containing comments or quotes added after printing should be retained if the comments/quotes alter the purpose or direction of the record. These copies may only be destroyed after they are linked to or scanned into the legal health record. Patient level detail logs are not required as the electronic record replaces the hardcopy.Electronic Health RecordsElectronic records (e.g., Cerner, PACS) that have passed the NYGH Retention period will not be destroyed in order to provide a comprehensive longitudinal view of the patient’s history in accordance with the current Healthcare system view of maintaining a lifelong health record. Transitory RecordsTransitory records may be destroyed when the task or event to which they relate concludes. The types of records that are considered transitory are limited to those that have no ongoing operational, evidential or historical value regardless of format. Records intended for short-term use may include notes, working papers and drafts, convenience or duplicate copies of material in paper or electronic format including email. Drafts should not be destroyed until the final is agreed upon. A Certificate of Destruction is not required when destroying transitory records.4. Log and Request to Destroy Personal Health Information &Certificate of DestructionDate: _______________________________________________ Service Provider: _______________________________________________1. Log of Records for Destruction must include the names of patients/individuals towhom the records relate and the date and manner of destruction. The log may beelectronic or hard copy. Do not destroy any records related to an ongoing oranticipated investigation, legal action, Freedom of Information request, audit orreview even if the record has already met its retention period.Dates of Records for Destruction: ______________________________________________ Exclusions of Records for Destruction: __________________________________________ ____________________________________________________________________________ Approval - Official Custodian (Program Director)_________________________________________________ ________________________ProgramApproval - Chief Privacy & Freedom of Information Officer:_________________________________________________Dear Service Provider:To ensure the privacy of records containing any personal health information, please complete the required information below to validate the destruction of the records identified above.____________________________________validates that the above named records have been company namereceived from _________________________________________, North York General andprogramhave been destroyed by ____________________________________________________.preferred method of destruction: finely shredded/cross cut or incineration Signed by _________________________, ____________________________ at _______this signature please print name time_______ day of ____________________ 20______.date month yearPlease retain a copy for your files and return the signed original to:_______________________, North York General Hospital, 4001 Leslie S. Toronto, ON M2K 1E1ProgramNorth York General Hospital Policy Manual:Record Retention and Destruction Policy NUMBER:V-50PAGE 7 OF 7 5. Certificate of Destructionfor Corporate/General Records Department: Contact Name: Telephone:Record Type Brief DescriptionDate RangeDestruction Method From: To:Approved by Official Custodian: Department:Signature: Date:Approved by: Chief Privacy & Freedom of Information Officer:Signature: Date:2. Use this form for the destruction of official corporate records (not personal health information).3. Only dispose of records that have met or exceeded their retention period. See NYGH RecordsRetention Schedule.4. List the records to be destroyed, a description of the record, the date range of the records and themethod of destruction. Do not include any personal information i.e. any information that identifies an individual or would lead to their identification. .5. Do not destroy any records related to an ongoing or anticipated investigation, legal action,Freedom of Information request, audit or review even if the record has already met its retentionperiod.Note: this form is not required for the destruction of transitory records.Print and retain a copy of the completed form. It may have to be produced as evidence that the records were appropriately destroyed and in accordance with the Record Retention Schedule.。
UCODE EPC G2 SL3 DS

109930
© NXP B.V. 2010. All rights reserved.
Product data sheet
Rev. 3.0 — 7 September 2006
2 of 33
NXP Semiconductors
SL3 ICS 10
UCODE EPC G2
PUBLIC
2.4 Memory Features
2.3 RF Interface Features
Contact-less transmission of data and supply energy (no battery needed) Long-range operating distance Operating frequency within the released operating bands from 860 MHz to 960 MHz High data integrity: 16 bit CRC, framing High anti-collision and inventory speed Data rates: R -> T: 40 – 160 kbps, T -> R: 40 – 465 kbps (Divide ratio DR = 8) or 95 – 640 kbps (DR = 64/3) Uses a slotted random anti-collision algorithm where the UCODE EPC G2 IC loads a random (or pseudo-random) number into a slot counter, decrement this slot counter based on interrogator commands, and reply to the interrogator when their slot counter reaches zero. Supports the full mandatory command set as well as optional and Customer commands according to the standard
critical_section

critical_sectionCritical SectionIntroductionIn computer science, a critical section refers to a part of a computer program that accesses shared resources, such as variables or data structures, that may be modified by multiple concurrent threads or processes. The critical section is crucial because if multiple threads attempt to access the shared resource simultaneously, it can result in undefined behavior or data corruption. To ensure the correct execution of the program, synchronization mechanisms must be implemented to allow only one thread to enter the critical section at a time.Problem of Concurrent AccessConcurrent access to shared resources can lead to race conditions, deadlocks, and other synchronization problems. Let's consider a simple example to illustrate the problem. Suppose we have two threads, Thread A and Thread B, that both need to access and update a shared variable, X. Without proper synchronization, the following scenario can occur:1. Thread A reads the value of X into a register.2. Thread B reads the value of X into a different register.3. Thread A updates the value of X based on its register's value.4. Thread B updates the value of X based on its register's value.5. Both threads write the updated value of X back to memory.In this scenario, if Thread A and Thread B read the value of X simultaneously and update it independently, the final value of X in memory will be incorrect. This is because the updates made by one thread will overwrite the changes made by the other, resulting in unexpected behavior.Critical Section SolutionTo prevent concurrent access to shared resources, synchronization mechanisms are used, with the most common one being locks or mutexes. A lock is used to guard the critical section by allowing only one thread to enter it at a time. Here's how it works:1. Before entering the critical section, a thread must acquire the lock.2. If the lock is not already acquired by another thread, the current thread proceeds to the critical section.3. If the lock is already acquired by another thread, the current thread is blocked or put to sleep until the lock becomes available.4. Once a thread is done with the critical section, it releases the lock, allowing another waiting thread to acquire it and enter the critical section.The synchronization mechanism ensures that only one thread can be in the critical section at any given time, eliminating the possibility of data corruption or concurrent modifications.Deadlocks and StarvationWhile using locks to protect the critical section solves the problem of concurrent access, it introduces new challenges, such as deadlocks and starvation. Deadlock occurs when two or more threads are waiting indefinitely for each other to release resources, resulting in a system freeze. Starvation, on the other hand, happens when a thread is unfairly denied access to the critical section for a prolonged period.To prevent deadlocks, various techniques can be employed, such as using timeouts, resource ordering, or deadlock detection algorithms. Timeouts ensure that a thread doesn't wait indefinitely for a lock, while resource ordering establishes a systematic order in which threads can request and acquire locks to avoid cyclic dependencies. Deadlock detection algorithms periodically check the system for deadlock conditions and take appropriate actions to resolve them.To minimize or eliminate starvation, fairness policies can be implemented, ensuring that threads waiting for the critical section are granted access in a fair manner. For example, a common technique is to use a queue to track the order of thread requests and grant access based on a first-come-first-served basis.ConclusionIn concurrent programming, the critical section is a fundamental concept for ensuring data integrity and synchronization. By using locks or mutexes to guard shared resources, a program can prevent race conditions and ensure that only one thread accesses the critical section at any giventime. However, care must be taken to prevent deadlocks and starvation, which can arise from improper synchronization. Proper design and implementation of synchronization mechanisms are crucial for creating efficient and reliable concurrent programs.。
linux c entercriticalsection -回复

linux c entercriticalsection -回复关于在Linux环境下进入和操作临界区(Critical Section)的相关讨论临界区是指在多线程编程中一段对共享资源进行访问和操作的代码区域。
由于同时访问共享资源可能导致数据不一致或其他问题,因此需要保证在任意时刻只有一个线程可以进入临界区。
在Linux环境下,我们可以使用各种方法和技术来实现对临界区的进入和保护。
在Linux环境中,最常用的方法之一是使用互斥锁(Mutex)。
互斥锁是一种同步原语,用于保护共享资源的访问。
它允许线程进入临界区,并阻塞其他线程直到该线程释放锁。
互斥锁可以通过pthread库实现。
在进入临界区之前,线程必须先获取互斥锁,在退出临界区之前,必须释放互斥锁。
以下是一个简单的示例代码:c#include <stdio.h>#include <pthread.h>pthread_mutex_t mutex;void* thread_func(void* arg) {线程尝试获取互斥锁pthread_mutex_lock(&mutex);临界区代码printf("线程进入临界区\n");访问共享资源释放互斥锁pthread_mutex_unlock(&mutex);return NULL;}int main() {pthread_t thread_id;pthread_mutex_init(&mutex, NULL);创建多个线程来访问临界区for (int i = 0; i < 5; i++) {pthread_create(&thread_id, NULL, thread_func, NULL);}pthread_mutex_destroy(&mutex);pthread_exit(NULL);return 0;}在上面的代码中,我们首先定义了一个全局的互斥锁`mutex`。
关于#pragma DATA_SECTION的解释

关于#pragma DATA_SECTION的解释> 自定义段(C语言)#pragma DATA_SECTION(函数名或全局变量名,"用户自定义在数据空间的段名"); #pragma CODE_SECTION(函数名或全局变量名,"用户自定义在程序空间的段名"); 不能在函数体内声明。
必须在定义和使用前声明#pragma可以阻止对未调用的函数的优化3. 连接命令文件(CMD)1> MEMORY指定存储空间MEMORY9}8eIg5y*k OGuest{oo)w?(lm9NRGuestPAGE 0:$HH7Tu2A+eH%K3xr}Guest name 0 [attr] : origin = constant, length = constantPAGE n: EETOP专业博客---电子工程师自己的家园2o:b1G5?c$Zz5WOname n [attr] : origin = constant, length = constant}PAGE n:标示存储空间,n<255;PAGE 0为程序存储空间;PAGE 1为data存储空间name:存储空间名称attr:存储空间属性:只读R,只写W,可包含可执行代码X,可以被初始化I。
orgin:用来定义存储空间的起始地址Lenth:用来定义存储空间的长度2> SECTIONS分配段SECTIONS{name : [property,property,……]}name:输出段的名称property:输出段的属性:load=allocation(强制地址或存储空间名称)同>allocation:定义输出段将会被装载到哪里。
run= allocation(强制地址或存储空间名称)同>allocation:定义输出段将会在哪里运行。
注:CMD文件中只出现一个关键字load或run时,表示两者的地址时表示两者的地址时重合的。
解释一个ldscript资料

解释一个ld.script资料GNU ld (GNU Binutils for Ubuntu)2.20.1-system.20100303Supported emulations:elf_i386i386linuxelf_x86_64elf_l1omusing internal linker script:============================================== ====/* Script for -z combreloc: combine and sort reloc sections */ OUTPUT_FORMAT("elf32-i386", "elf32-i386","elf32-i386")OUTPUT_ARCH(i386)ENTRY(_start)SEARCH_DIR("/usr/i486-linux-gnu/lib32");SEARCH_DIR("/usr/local/lib32");SEARCH_DIR("/lib32"); SEARCH_DIR("/usr/lib32"); SEARCH_DIR("/usr/i486-linux-gnu/lib");SEARCH_DIR("/usr/local/lib"); SEARCH_DIR("/lib");SEARCH_DIR("/usr/lib");SECTIONS{/* Read-only sections, merged into text segment: */ PROVIDE (__executable_start =SEGMENT_START("text-segment", 0x08048000));. = SEGMENT_START("text-segment", 0x08048000) + SIZEOF_HEADERS;.interp : { *(.interp) }.note.gnu.build-id : { *(.note.gnu.build-id) }.hash : { *(.hash) }.gnu.hash : { *(.gnu.hash) }.dynsym : { *(.dynsym) }.dynstr : { *(.dynstr) }.gnu.version : { *(.gnu.version) }.gnu.version_d : { *(.gnu.version_d) }.gnu.version_r : { *(.gnu.version_r) }.rel.dyn :{*(.rel.init)*(.rel.text .rel.text.* .rel.gnu.linkonce.t.*)*(.rel.fini)*(.rel.rodata .rel.rodata.* .rel.gnu.linkonce.r.*) *(.rel.data.rel.ro* .rel.gnu.linkonce.d.rel.ro.*)*(.rel.data .rel.data.* .rel.gnu.linkonce.d.*)*(.rel.tdata .rel.tdata.* .rel.gnu.linkonce.td.*)*(.rel.tbss .rel.tbss.* .rel.gnu.linkonce.tb.*)*(.rel.ctors)*(.rel.dtors)*(.rel.got)*(.rel.bss .rel.bss.* .rel.gnu.linkonce.b.*)*(.rel.ifunc)}.rel.plt :{*(.rel.plt)PROVIDE_HIDDEN (__rel_iplt_start = .);*(.rel.iplt)PROVIDE_HIDDEN (__rel_iplt_end = .);}.init :{KEEP (*(.init))} =0x90909090.plt : { *(.plt) *(.iplt) }.text :{*(.text.unlikely .text.*_unlikely)*(.text .stub .text.* .gnu.linkonce.t.*)/* .gnu.warning sections are handled specially by elf32.em. */*(.gnu.warning)} =0x90909090.fini :{KEEP (*(.fini))} =0x90909090PROVIDE (__etext = .);PROVIDE (_etext = .);PROVIDE (etext = .);.rodata : { *(.rodata .rodata.* .gnu.linkonce.r.*) } .rodata1 : { *(.rodata1) }.eh_frame_hdr : { *(.eh_frame_hdr) }.eh_frame : ONLY_IF_RO { KEEP (*(.eh_frame)) } .gcc_except_table : ONLY_IF_RO{ *(.gcc_except_table .gcc_except_table.*) }/* Adjust the address for the data segment. We want to adjust up tothe same address within the page on the next page up. */ . = ALIGN (CONSTANT (MAXPAGESIZE)) - ((CONSTANT (MAXPAGESIZE) - .) & (CONSTANT (MAXPAGESIZE) - 1)); . = DATA_SEGMENT_ALIGN (CONSTANT (MAXPAGESIZE), CONSTANT (COMMONPAGESIZE));/* Exception handling */.eh_frame : ONLY_IF_RW { KEEP (*(.eh_frame)) } .gcc_except_table : ONLY_IF_RW{ *(.gcc_except_table .gcc_except_table.*) }/* Thread Local Storage sections */.tdata : { *(.tdata .tdata.* .gnu.linkonce.td.*) }.tbss : { *(.tbss .tbss.* .gnu.linkonce.tb.*)*(.tcommon) }.preinit_array :{PROVIDE_HIDDEN (__preinit_array_start = .);KEEP (*(.preinit_array))PROVIDE_HIDDEN (__preinit_array_end = .);}.init_array :{PROVIDE_HIDDEN (__init_array_start = .);KEEP (*(SORT(.init_array.*)))KEEP (*(.init_array))PROVIDE_HIDDEN (__init_array_end = .); }.fini_array :{PROVIDE_HIDDEN (__fini_array_start = .); KEEP (*(.fini_array))KEEP (*(SORT(.fini_array.*)))PROVIDE_HIDDEN (__fini_array_end = .); }.ctors :{/* gcc uses crtbegin.o to find the start ofthe constructors, so we make sure it isfirst. Because this is a wildcard, itdoesn't matter if the user does notactually link against crtbegin.o; thelinker won't look for a match awildcard. The wildcard also means that itdoesn't matter which directory crtbegin.ois in. */KEEP (*crtbegin.o(.ctors))KEEP (*crtbegin?.o(.ctors))/* We don't want to include the .ctor section fromthe crtend.o after the sorted ctors.The .ctor section from the crtend theend of ctors marker and it must be last */KEEP (*(EXCLUDE_FILE (*crtend.o *crtend?.o ) .ctors)) KEEP (*(SORT(.ctors.*)))KEEP (*(.ctors))}.dtors :{KEEP (*crtbegin.o(.dtors))KEEP (*crtbegin?.o(.dtors))KEEP (*(EXCLUDE_FILE (*crtend.o *crtend?.o ) .dtors)) KEEP (*(SORT(.dtors.*)))KEEP (*(.dtors))}.jcr : { KEEP (*(.jcr)) }.data.rel.ro :{ *(.data.rel.ro.local* .gnu.linkonce.d.rel.ro.local.*)*(.data.rel.ro* .gnu.linkonce.d.rel.ro.*) }.dynamic : { *(.dynamic) }.got : { *(.got) *(.igot) }. = DATA_SEGMENT_RELRO_END (12, .);.got.plt : { *(.got.plt) *(.igot.plt) }.data :{*(.data .data.* .gnu.linkonce.d.*)SORT(CONSTRUCTORS)}.data1 : { *(.data1) }_edata = .; PROVIDE (edata = .);__bss_start = .;.bss :{*(.dynbss)*(.bss .bss.* .gnu.linkonce.b.*)*(COMMON)/* Align here to ensure that the .bss section occupies space up to_end. Align after .bss to ensure correct alignment even if the.bss section disappears because there are no input sections.FIXME: Why do we need it? When there is no .bss section, we don'tpad the .data section. */. = ALIGN(. != 0 ? 32 / 8 : 1);}. = ALIGN(32 / 8);. = ALIGN(32 / 8);_end = .; PROVIDE (end = .);. = DATA_SEGMENT_END (.);/* Stabs debugging sections. */.stab 0 : { *(.stab) }.stabstr 0 : { *(.stabstr) }.stab.excl 0 : { *(.stab.excl) }.stab.exclstr 0 : { *(.stab.exclstr) }.stab.index 0 : { *(.stab.index) }.stab.indexstr 0 : { *(.stab.indexstr) }.comment 0 : { *(.comment) }/* DWARF debug sections.Symbols in the DWARF debugging sections are relative to the beginningof the section so we begin them at 0. *//* DWARF 1 */.debug 0 : { *(.debug) }.line 0 : { *(.line) }/* GNU DWARF 1 extensions */.debug_srcinfo 0 : { *(.debug_srcinfo) }.debug_sfnames 0 : { *(.debug_sfnames) }/* DWARF 1.1 and DWARF 2 */.debug_aranges 0 : { *(.debug_aranges) }.debug_pubnames 0 : { *(.debug_pubnames) }/* DWARF 2 */.debug_info 0 : { *(.debug_info .gnu.linkonce.wi.*) }.debug_abbrev 0 : { *(.debug_abbrev) }.debug_line 0 : { *(.debug_line) }.debug_frame 0 : { *(.debug_frame) }.debug_str 0 : { *(.debug_str) }.debug_loc 0 : { *(.debug_loc) }.debug_macinfo 0 : { *(.debug_macinfo) }/* SGI/MIPS DWARF 2 extensions */.debug_weaknames 0 : { *(.debug_weaknames) }.debug_funcnames 0 : { *(.debug_funcnames) }.debug_typenames 0 : { *(.debug_typenames) }.debug_varnames 0 : { *(.debug_varnames) }/* DWARF 3 */.debug_pubtypes 0 : { *(.debug_pubtypes) }.debug_ranges 0 : { *(.debug_ranges) }.gnu.attributes 0 : { KEEP (*(.gnu.attributes)) }/DISCARD/ : { *(.note.GNU-stack) *(.gnu_debuglink)*(.gnu.lto_*) }}============================================== ====下面逐句解释。
LTE in Bullets - RRC Establishment
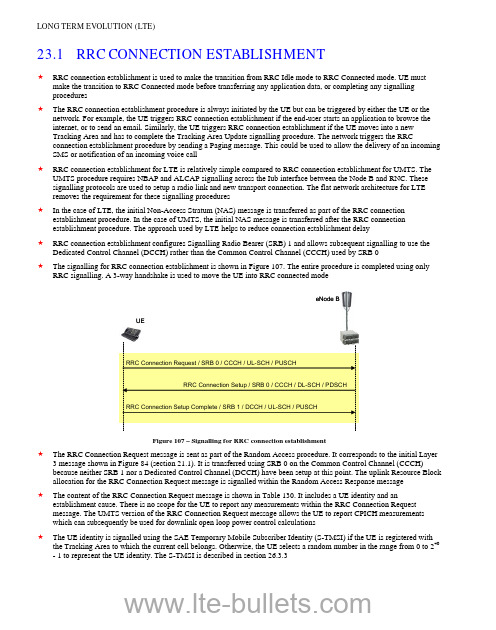
eNode B
UEຫໍສະໝຸດ RRC Connection Request / SRB 0 / CCCH / UL-SCH / PUSCH
RRC Connection Setup / SRB 0 / CCCH / DL-SCH / PDSCH
RRC Connection Setup Complete / SRB 1 / DCCH / UL-SCH / PUSCH
批注本地保存成功开通会员云端永久保存去开通
LONG TERM EVOLUTION (LTE)
23.1 RRC CONNECTION ESTABLISHMENT
RRC connection establishment is used to make the transition from RRC Idle mode to RRC Connected mode. UE must make the transition to RRC Connected mode before transferring any application data, or completing any signalling procedures The RRC connection establishment procedure is always initiated by the UE but can be triggered by either the UE or the network. For example, the UE triggers RRC connection establishment if the end-user starts an application to browse the internet, or to send an email. Similarly, the UE triggers RRC connection establishment if the UE moves into a new Tracking Area and has to complete the Tracking Area Update signalling procedure. The network triggers the RRC connection establishment procedure by sending a Paging message. This could be used to allow the delivery of an incoming SMS or notification of an incoming voice call RRC connection establishment for LTE is relatively simple compared to RRC connection establishment for UMTS. The UMTS procedure requires NBAP and ALCAP signalling across the Iub interface between the Node B and RNC. These signalling protocols are used to setup a radio link and new transport connection. The flat network architecture for LTE removes the requirement for these signalling procedures In the case of LTE, the initial Non-Access Stratum (NAS) message is transferred as part of the RRC connection establishment procedure. In the case of UMTS, the initial NAS message is transferred after the RRC connection establishment procedure. The approach used by LTE helps to reduce connection establishment delay RRC connection establishment configures Signalling Radio Bearer (SRB) 1 and allows subsequent signalling to use the Dedicated Control Channel (DCCH) rather than the Common Control Channel (CCCH) used by SRB 0 The signalling for RRC connection establishment is shown in Figure 107. The entire procedure is completed using only RRC signalling. A 3-way handshake is used to move the UE into RRC connected mode
initializecriticalsectionandspincount

initializecriticalsectionandspincountInitializecriticalsectionandspincount是一种特殊的技术,它能够有效地保护系统资源,防止其他程序对它们的违规操作。
Initializecriticalsectionandspincount是由Microsoft Windows组件开发商提供的一种安全机制。
它的功能是创建一个临界区,通过设定一个旋转的计数器来保护系统共享资源。
在多任务环境中,当一个任务执行对某个资源的访问时,系统会检查这个资源的临界区,如果发现有另一个任务正在访问它,则会等待直到那个任务完成,然后才允许请求的任务访问它。
Initializecriticalsectionandspincount能够被用于任何需要同步访问的任务,其中包括网络服务器上的程序,数据库中的存储过程,文件系统中的文件操作,以及多线程应用程序中的代码段。
此外,还可以使用此技术来实现锁定,确保多个任务在同一时间只能有一个任务访问某个资源,而其他任务都必须等待该资源释放。
Initializecriticalsectionandspincount技术可以有效地提高内存使用效率,降低系统占用的CPU资源,并保护系统共享资源。
它有助于减少并发问题,保护系统资源免受不恰当的使用,从而确保系统的稳定性和安全性。
此外,Initializecriticalsectionandspincount还可以有效地帮助提高服务器的性能,减少内存的使用率和提高系统的可靠性。
使用它的方式也相当简单,只需要在C/C++程序中添加相应的函数调用即可,因此使用这种技术的开发人员可以轻松的利用它的功能,有效地提高服务稳定性和可靠性。
总之,Initializecriticalsectionandspincount是一种非常有用的技术,它有助于保护系统资源,同时也可以提高系统性能和可靠性。
如果您正在开发服务器程序,那么您一定应该考虑使用这种技术,以此来提升系统的性能和稳定性。
ImportREC修复IAT数据工具教程

ImportREC修复IAT数据工具教程Import REConstructor 可以从杂乱的IAT中重建一个新的Import 表(如:加壳软件),它可以重建Import表的描述符、IAT和所有的ASCII函数名。
配合手动脱壳,可以脱UPX、CDilla1、PECompact、PKLite32、Shrinker、ASPack, ASProtect 等壳。
该工具位于:光盘\tools\PE tools\Rebuilders\Import REConstructor。
运行条件:1)目标文件己完全被Dump(转储)到另一文件2)目标文件必须正在运行中3)事先要找到真正的OEP(入口点)4)最好加载IceDump,这样建立的输入表较少出现跨平台问题使用步骤:(1)找被脱壳的OEP(入口点)(2)完全Dump(转储)目标文件(3)运行 Import REConstructor 和需要脱壳的应用程序(4)在Import REConstructor下拉列表框中选择应用程序进程(5)在左下角填上应用程序的真正入口点偏移OEP(入口点)(6)按IAT AutoSearch按钮,让其自动检测IAT位置,出现Found address which may be in the Original IAT.Try 'Get Import'对话框,表示输入的OEP(入口点)发挥作用了。
(7)按Get Import按钮,让其分析IAT 结构得到基本信息(8)如发现某个DLL显示valid :NO,按"Show Invalids"按钮将分析所有的无效信息,在Imported Function Found栏中点击鼠标右键,选择 "Trace Level1 (Disasm)",再按"Show Invalids"按钮。
如果成功,可以看到所有的DLL都为valid:YES 字样(9)再次刷新"Show Invalids"按钮查看结果,如仍有无效的地址,继续手动用右键的Level 2或3修复(10)如还是出错,可以利用"Invalidate function(s)"、"Delete thunk(s)"、编辑Import 表(双击函数)等功能手动修复。
C语言读取INI配置文件
C语言读取INI配置文件Ini.h#pragma once#include"afxTempl.h"class DLLPORT CIni{private:CString m_strFileName;public:CIni(CString strFileName) :m_strFileName(strFileName){}public://一般性操作:BOOL SetFileName(LPCTSTR lpFileName); //设置文件名CString GetFileName(void); //获得文件名BOOL SetValue(LPCTSTR lpSection, LPCTSTR lpKey, LPCTSTR lpValue, bool bCreate = true); //设置键值,bCreate是指段名及键名未存在时,是否创建。
CString GetValue(LPCTSTR lpSection, LPCTSTR lpKey); //得到键值.BOOL DelSection(LPCTSTR strSection); //删除段名BOOL DelKey(LPCTSTR lpSection, LPCTSTR lpKey); //删除键名public://高级操作:int GetSections(CStringArray& arrSection); //枚举出全部的段名int GetKeyValues(CStringArray& arrKey, CStringArray& arrValue, LPCTSTR lpSection); //枚举出一段内的全部键名及值BOOL DelAllSections();};/*使用方法:CIni ini("c:\\a.ini");int n;/*获得值TRACE("%s",ini.GetValue("段1","键1"));*//*添加值ini.SetValue("自定义段","键1","值");ini.SetValue("自定义段2","键1","值",false);*//*枚举全部段名CStringArray arrSection;n=ini.GetSections(arrSection);for(int i=0;i<n;i++)TRACE("%s\n",arrSection[i]);*//*枚举全部键名及值CStringArray arrKey,arrValue;n=ini.GetKeyValues(arrKey,arrValue,"段1");for(int i=0;i<n;i++)TRACE("键:%s\n值:%s\n",arrKey[i],arrValue[i]); *//*删除键值ini.DelKey("段1","键1");*//*删除段ini.DelSection("段1");*//*删除全部ini.DelAllSections();*/Ini.cpp#include"StdAfx.h"#include"Ini.h"#define MAX_ALLSECTIONS 2048 //全部的段名#define MAX_SECTION 260 //一个段名长度#define MAX_ALLKEYS 6000 //全部的键名#define MAX_KEY 260 //一个键名长度BOOL CIni::SetFileName(LPCTSTR lpFileName){CFile file;CFileStatus status;if (!file.GetStatus(lpFileName, status))return TRUE;m_strFileName = lpFileName;return FALSE;}CString CIni::GetFileName(void){return m_strFileName;}BOOL CIni::SetValue(LPCTSTR lpSection, LPCTSTR lpKey, LPCTSTR lpValue, bool bCreate) {TCHAR lpTemp[MAX_PATH] = { 0 };//以下if语句表示如果设置bCreate为false时,当没有这个键名时则返回TRUE(表示出错)//!*&*none-value*&!* 这是个垃圾字符没有特别意义,这样乱写是防止凑巧相同。
