思科网院考试题库
(完整版)思科题库2(修改)

1: PDU封装的正确顺序是什么?锁头网络报头MA网络赧头传输歿头帧头数磚tm帧头數宠赣亀帧头IM 2:建立融合网络有何用途?O为斯有终鋸设备提供高速连揺O确保平等对待所有类盘的数霸包O实规数据网络基础架撇犒的容错能力和高可用性降低部署和维护通信基珊栈施的咸本A: ISPD JP电话和PC3:请参见图示。
哪个区域最有可能是图中所示的公司网络的外联网?I」回前A1 1区域BH BSCO区域D4:主机正在访冋远程网络的FTP服务器。
中间网络设备在此对话中起到哪三个作用?(请选择三项。
)列重新生成埶据信号0充当喜户端或服务器□提供伎输消息的画适&应用安全诠置来控制数据掠a岀现错误时si知其他设冷□用作滴恳的源或目标5 一位家庭用户想要使用能够在普通电话线路上提供快速数字传输的ISP连接。
应选择哪种ISP连接类型?厨OSL0拨号U卫星口手机调制解调器0电缆调制熾调器6:在学校网络上,学生可以浏览网页、搜索图书馆数据库,还可以和日本的姊妹学校一起参加音频会议。
如果使用QoS为网络流量排列优先顺序,这些流量的优先级从高到低如何排列?働音频会仪、敎馨障、HTTPO樋库、HTTP'S®馳O音颠会械、HTTPx埶捐庫O數辖库、音频会愤、HTTP7:管理员在发出ping命令之后在交换机上使用Ctrl-Shift-6键组合。
使用这些按键有什么用途?0重新启Ejhpingjfi程•I Ping 进程O退出到不同的配置複武u咒诈用户凫成齡令& OSI模型的物理层有什么重要功能?接覺来自物理介厲的帧。
0将上层数揺封装咸帧。
匕定义硬件核口执行的介质访问方达。
•3苗砸蹣码対电子、光纤或无绕电克信总。
9:下列哪个程序用于降低铜缆中的串扰影响?1零耍正确接地连播®统合反血]电路线对O用樂馬屏護滾住錢束0设计电86基珊设庇避免串扰干扰v.懂免在安装H出珈弯曲2层交换机10:如果收到的帧的目的MAC地址不在MAC表中,第将执行什么操作?O它会友起久阿1请求。
大学计算机思科试题及答案

大学计算机思科试题及答案1. 选择题1.1) 下列哪个不是计算机网络发展的特点?A. 具有开放性和互联性B. 支持多媒体和实时通信C. 高性能和高可靠性D. 只能在局域网内部进行通信答案:D1.2) 在OSI模型中,将物理层和数据链路层合并为一个层次的模型是:A. TCP/IP模型B. 五层参考模型C. 四层参考模型D. 七层参考模型答案:B1.3) 下面哪个不是计算机网络的传输介质?A. 双绞线B. 光纤C. 无线电波D. 显示器答案:D1.4) 网络地址转换(NAT)技术在哪一层实现地址转换?A. 物理层B. 数据链路层C. 网络层D. 传输层答案:C1.5) 以下哪个协议用于到达目标主机的IP数据报的传输?A. ARPB. IPC. ICMPD. TCP答案:B2. 填空题2.1) IP地址的格式为_____位。
答案:322.2) 网络层协议IP地址由网络号和____号两部分组成。
答案:主机2.3) 在计算机网络中,____是负责监测发送的数据是否发生错误。
答案:CRC2.4) DNS的英文全称是_____。
答案:Domain Name System2.5) HTTP的英文全称是_____。
答案:Hypertext Transfer Protocol3. 简答题3.1) 请解释OSI模型的七层,以及每一层的作用。
答案:OSI模型是一种将计算机网络通信协议划分为不同层次的理论模型。
七层分别为:1) 物理层:负责传输比特流,提供物理媒介之间的直接通信。
2) 数据链路层:负责通过物理连接传递数据帧,提供错误检测和纠正功能。
3) 网络层:负责数据的分组和路由选择,实现不同网络之间的数据传输。
4) 传输层:负责端到端的可靠数据传输,提供面向连接或无连接的通信服务。
5) 会话层:负责建立、管理和终止会话连接,控制数据传输的顺序和流量。
6) 表示层:负责数据的格式化和编码,支持不同系统间的数据交换。
7) 应用层:为用户提供网络服务,包括文件传输、电子邮件、远程登录等应用。
思科网院-网络工程-CCNA1-2017计算机科学与技术-一到十一章-题库及答案

某公司正在考虑是使用客户端/服务器还是对等网络。
下列哪三项是对等网络的特征?(选择三项。
)哪种设备的功能是确定消息在网际网络中传输的路径?哪两个条件有助于您从各种网络介质当中选择一种网络介质?(请选择两项。
)下列哪两项描述了中间设备?(选择两项。
)网络上的终端设备有哪两项功能?(选择两项。
)由于许多学生带着自己的平板电脑和智能手机去学校访问学校资源,大学里的IT 人员最有可能需要重新设计的网络区域是什么?家庭用户必须要有哪种网络类型访问才能进行网上购物?一位分支机构办公室的员工正在为客户创建报价。
为此,该员工需要访问位于总部办公室的内部服务器上的机密定价信息。
该员工将要访问哪种类型的网络?下列哪两种连接选项可以为家庭办公室中的计算机提供始终在线的高带宽Internet 连接?(选择两项。
)下列哪两个Internet 连接选项不需要建筑物铺设物理电缆?(请选择两项。
)以下哪种术语描述了当对网络资源的请求超出可用容量时网络的状态?哪种类型的网络流量需要QoS?以下哪项表述准确定义了术语“带宽”?网络管理员正在实施一种要求复杂强密码的策略。
该策略支持哪种数据保护目标?下列哪种说法正确描述了云计算的特征?什么是Internet?下列哪种说法描述了电力线网络技术的用途?哪种安全侵犯会对家庭用户的生活造成最大损害?一位用户正在一个小型办公室网络上实施安全策略。
以下哪两种操作将为此网络提供求?(选择两项。
)A网络能够通过相同的通信通道传输语音、视频、文本和图形。
填空题。
缩写词是指允许员工在公司办公室中使用其个人设备访问网络和其他资源的策略。
正确答案:byod将每个描述与网络通信形式配对请将每个特征对应的internet连接类型进行匹配将每个定义与安全目标配对操作软件内核的作用是什么?网络管理员与交换机建立远程CLI 连接对其实施管理时,需要确保用户ID、密码和会话内容的保密性。
应当选择哪种访问方法?当在安全环境下执行初始配置时,下列哪个程序可用来访问Cisco 2960 交换机?哪个命令或组合键让用户返回命令层级中的上一级?某台路由器具有有效的操作系统,且NVRAM 中存储有配置文件。
思科模拟试题及答案

思科模拟试题及答案一、选择题1. 以下哪个命令用于查看路由器的接口状态?A. show interfaceB. show ip interfaceC. show running-configD. show ip route答案:A2. 在思科路由器上配置默认网关的命令是什么?A. ip default-gatewayB. default gatewayC. ip route 0.0.0.0D. route 0.0.0.0答案:C3. 以下哪个协议用于在大型网络中自动发现路由?A. RIPB. OSPFC. BGPD. EIGRP答案:B4. 以下哪个命令用于查看当前路由器的配置?A. show running-configB. show startup-configC. show interfaceD. show ip route答案:A5. 以下哪个命令用于在路由器上配置静态路由?A. ip routeB. routeC. static routeD. configure static route答案:A二、填空题6. 思科的网络操作系统称为________。
答案:IOS7. 在思科设备上,使用________命令可以进入特权模式。
答案:enable8. 配置VLAN的命令是________。
答案:VLAN configuration mode9. 动态主机配置协议的缩写是________。
答案:DHCP10. 用于测试网络连通性的命令是________。
答案:ping三、简答题11. 简述什么是子网掩码,并说明其作用。
答案:子网掩码是一种用于区分IP地址中网络部分和主机部分的位模式。
它的作用是告诉路由器或交换机,IP地址的哪部分是网络地址,哪部分是主机地址,以便正确地进行路由和数据传输。
12. 描述什么是VLAN,以及它在网络中的作用。
答案:VLAN(虚拟局域网)是一种将局域网划分为多个虚拟网络的技术。
大二思科考试题库和答案

大二思科考试题库和答案一、单项选择题(每题2分,共20分)1. 思科公司(Cisco)成立于哪一年?A. 1984年B. 1990年C. 1995年D. 2000年答案:A2. 以下哪个协议是用于在IP网络中传输数据的?A. HTTPB. FTPC. TCPD. IP答案:D3. 在OSI模型中,哪一层负责建立、维护和终止通信会话?A. 应用层B. 传输层C. 会话层D. 网络层答案:C4. 以下哪个设备不是网络交换机?A. Layer 2 SwitchB. Layer 3 SwitchC. RouterD. Hub答案:D5. 以下哪个命令用于在Cisco设备上显示当前配置?A. show running-configB. show startup-configC. show interfaceD. show ip interface brief答案:A6. 在Cisco设备上,哪个命令用于保存当前的配置到启动配置文件?A. copy running-config startup-configB. copy startup-config running-configC. save running-configD. write memory答案:A7. 以下哪个命令用于在Cisco设备上创建一个新的VLAN?A. vlan databaseB. configure terminalC. enableD. show vlan答案:A8. 以下哪个命令用于在Cisco设备上将接口配置为Trunk模式?A. switchport mode accessB. switchport mode dynamicC. switchport mode trunkD. switchport mode static答案:C9. 以下哪个协议用于在IP网络中自动分配IP地址?A. DHCPB. DNSC. FTPD. HTTP答案:A10. 在Cisco设备上,哪个命令用于查看设备的接口状态?A. show interfacesB. show ip interface briefC. show running-configD. show vlan答案:B二、多项选择题(每题3分,共15分)11. 以下哪些协议属于TCP/IP模型的应用层协议?A. HTTPB. FTPC. SNMPD. IP答案:A, B, C12. 在Cisco设备上,以下哪些命令用于配置接口?A. interfaceB. ip addressC. no shutdownD. enable答案:A, B, C13. 以下哪些设备可以作为网络的核心设备?A. SwitchB. RouterC. FirewallD. Hub答案:A, B14. 以下哪些命令用于在Cisco设备上查看网络信息?A. show ip routeB. show running-configC. show interfaceD. ping答案:A, C, D15. 以下哪些因素可以影响网络的性能?A. 带宽B. 延迟C. 丢包率D. 网络拓扑结构答案:A, B, C, D三、填空题(每题2分,共20分)16. 在Cisco设备上,使用________命令可以进入特权模式。
思科网络第一学期1-5章中文测试题及答案

ENetwork Chapter 2 - CCNA Exploration: 网络基础知识(版本4.0) 1在封装过程中,数据链路层执行什么操作?不添加地址。
添加逻辑地址。
添加物理地址。
添加进程的端口号。
2TCP/IP 网络接入层有何作用?路径确定和数据包交换数据表示、编码和控制可靠性、流量控制和错误检测详细规定构成物理链路的组件及其接入方法将数据段划分为数据包3数据链路层封装添加的报尾信息有何主要功能?支持差错校验确保数据按照顺序到达确保送达正确目的标识本地网络中的设备帮助中间设备进行处理和路径选择4请参见图示。
下列哪组设备仅包含终端设备?A、C、DB、E、G、HC、D、G、H、I、JD、E、F、H、I、JE、F、H、I、J5OSI 模型各层从最高层到最低层的正确顺序如何?物理层、网络层、应用层、数据链路层、表示层、会话层、传输层应用层、物理层、会话层、传输层、网络层、数据链路层、表示层应用层、表示层、物理层、会话层、数据链路层、传输层、网络层应用层、表示层、会话层、传输层、网络层、数据链路层、物理层表示层、数据链路层、会话层、传输层、网络层、物理层、应用层6下列哪三项陈述是对局域网(LAN) 最准确的描述?(选择三项)LAN 通常位于一个地域内。
此类网络由由一个组织管理。
LAN 中的不同网段之间一般通过租用连接的方式连接。
此类网络的安全和访问控制由服务提供商控制。
LAN 为同一个组织内的用户提供网络服务和应用程序访问。
此类网络的每个终端通常都连接到电信服务提供商(TSP)。
7第4 层端口指定的主要作用是什么?标识本地介质中的设备标识源设备和目的设备之间的跳数向中间设备标识通过该网络的最佳路径标识正在通信的源终端设备和目的终端设备标识终端设备内正在通信的进程或服务8以下哪种特征正确代表了网络中的终端设备?管理数据流发送数据流重新定时和重新传输数据信号确定数据传输路径9请参见图示。
哪个术语正确判断出了包含于绿色区域中的设备类型?源终端传输中间10OSI 模型哪两层的功能与TCP/IP 模型的网络接入层相同?(选择两项)网络层传输层物理层数据链路层会话层11请参见图示。
思科网院final考试试题
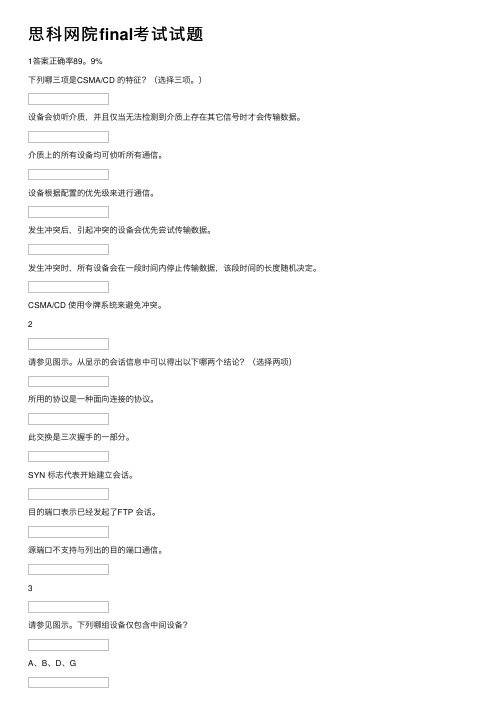
思科⽹院final考试试题1答案正确率89。
9%下列哪三项是CSMA/CD 的特征?(选择三项。
)设备会侦听介质,并且仅当⽆法检测到介质上存在其它信号时才会传输数据。
介质上的所有设备均可侦听所有通信。
设备根据配置的优先级来进⾏通信。
发⽣冲突后,引起冲突的设备会优先尝试传输数据。
发⽣冲突时,所有设备会在⼀段时间内停⽌传输数据,该段时间的长度随机决定。
CSMA/CD 使⽤令牌系统来避免冲突。
2请参见图⽰。
从显⽰的会话信息中可以得出以下哪两个结论?(选择两项)所⽤的协议是⼀种⾯向连接的协议。
此交换是三次握⼿的⼀部分。
SYN 标志代表开始建⽴会话。
⽬的端⼝表⽰已经发起了FTP 会话。
源端⼝不⽀持与列出的⽬的端⼝通信。
3请参见图⽰。
下列哪组设备仅包含中间设备?A、B、E、FC、D、G、IG、H、I、J4⽹络管理员想要限制访问路由器的特权执⾏模式。
管理员应该使⽤哪⼀种⼝令?使能aux控制台VTY5下列有关⽹络层编址的陈述中哪三项是正确的?(选择三项。
)使⽤IP 地址的最后⼀个⼆进制⼋位数来识别⽹络。
⽀持不同⽹络之间的数据通信。
由⽹络技术⼈员进⾏配置。
使⽤16 位IPv4 地址。
可阻⽌⼴播。
唯⼀标识每台主机。
6请参见图⽰。
⽤记号来表⽰每条介质链路。
⽤来连接不同设备的正确电缆类型是什么?连接 1 - 全反电缆,连接2 - 直通电缆,连接 3 - 交叉电缆连接 1 - 交叉电缆,连接2 - 全反电缆,连接 3 - 直通电缆连接 1 - 交叉电缆,连接2 - 直通电缆,连接 3 - 全反电缆连接 1 - 直通电缆,连接2 - 直通电缆,连接 3 - 直通电缆7请参见图⽰。
图中所⽰为在各层添加的头部。
哪⼀层会添加⽬的进程号和源进程号以确保将数据传递到正确的应⽤程序?物理层数据链路层⽹络层传输层8请参见图⽰。
技术⼈员正在处理⽹络问题,需要验证路由器的LAN 接⼝。
要确认路由器接⼝⼯作正常,应该从此主机ping127.0.0.1192.168.64.196192.168.254.1192.168.254.9192.168.254.2549路由器fa0/0 接⼝的IP 地址配置不正确。
思科网络 试题库

二、单选题1、 ADSL MODEM不能激活,打一个电话或振一下铃就好了,其原因可能是A、分离器损坏;B、modem工作不稳定;C、电话机有问题;D、线路接触面氧化;答案为d6、172.16.99.99/255.255.192.0 的广播地址是什么?A、172.16.99.255;B、172.16.127.255;C、172.16.255.255;D、172.16.64.127; 答案为b7、190.233.27.13./16所在网段地址A、190.233.0.0;B、190.0.0.0;C、190.233.27.0;答案为a8、224.0.0.5代表的是()地址。
A、主机地址;B、广播地址;C、网络地址;D、组播地址;答案为d10、ATM协议工作在________层。
A、物理层;B、链路层;C、网络层;D、传输层;答案为b11、ATM信元是定长的,而且信元的长度较小,只有()字节。
A、33;B、43;C、53;D、63;答案为c23、DHCP客户端申请一个新的IP地址之前,使用的初始IP地址是________。
A、0.0.0.0;B、127.0.0.1;C、255.255.255.255;D、169.254.1.1 ;答案为a24、DNS工作于()A、网络层 ;B、传输层;C、会话层;D、表示层;E、应用层;答案为e26、D类地址的缺省子网掩码有()位A、8;B、16;C、24;D、 None;答案为d28、FDDI 使用的是()局域网技术A、以太网;B、快速以太网;C、令牌环;D、令牌总线;答案为c29、IEEE 802.4是下面哪一种局域网标准?正确的选项是A、以太网;B、生成树;C、令牌环;D、令牌总线;答案为d30、IEEE于1999年颁布了用以标准化VLAN实现方案的________协议标准草案。
A、802.1B;B、802.1D;C、802.1P;D、802.1Q;答案为d32、IP报文头中固定长度部分为多少字节?A、10;B、20;C、30;D、40;答案为b33、IP报文中一部分字段专门用来描述报文的生命周期,即TTL值,它的最大值是________。
ccna考试试题库

ccna考试试题库CCNA(Cisco Certified Network Associate)考试是思科认证网络专家的初级认证,主要测试考生在网络基础、路由、交换、无线和安全等方面的知识。
以下是一些模拟CCNA考试的试题和答案:1. 什么是子网掩码,它有什么作用?答案:子网掩码是一种IP地址的附加信息,用于指定IP地址中网络部分和主机部分的界限。
它的作用是允许路由器区分IP地址中的网络地址和主机地址,从而实现不同网络之间的路由。
2. 描述静态路由和动态路由的区别。
答案:- 静态路由:由网络管理员手动配置的路由信息,不随网络结构的变化而自动调整。
- 动态路由:由路由器根据网络拓扑的变化自动生成和更新的路由信息。
3. 什么是VLAN,它有什么好处?答案: VLAN(虚拟局域网)是一种在交换机上划分不同网络的技术,即使物理上连接在同一交换机上,也可以属于不同的VLAN。
VLAN的好处包括提高安全性、减少广播域、提高网络管理的灵活性等。
4. 简述TCP和UDP的区别。
答案:- TCP(传输控制协议):提供可靠的、面向连接的传输服务,有流量控制和拥塞控制机制。
- UDP(用户数据报协议):提供不可靠的、无连接的传输服务,适用于对实时性要求高的应用。
5. 什么是DHCP,它的作用是什么?答案: DHCP(动态主机配置协议)是一种网络管理协议,用于自动分配IP地址和其他网络配置信息给网络中的设备。
它的作用是简化网络配置,避免IP地址冲突。
6. 什么是NAT,它在网络中扮演什么角色?答案: NAT(网络地址转换)是一种技术,允许多个设备共享一个公共IP地址与互联网通信。
它在网络中扮演的角色是节省IP地址资源,隐藏内部网络结构。
7. 什么是STP(生成树协议)?答案: STP(生成树协议)是一种网络协议,用于在局域网中防止网络环路的产生。
通过创建一个无环的逻辑拓扑,STP确保网络的稳定性和可靠性。
8. 描述OSPF(开放最短路径优先)协议的工作原理。
网络思科1-6章考试题整合

⽹络思科1-6章考试题整合第⼀章1.下列哪三个⽹络⼯具可以为家庭⽤户提供最低安全保护?(请选三项。
)BCFA.⼊侵防御系统B.反间谍软件C.防病毒软件D.访问控制列表E.电⼒线⽹络F.防⽕墙2.哪个表达准确定义了术语“拥塞”?DA.⽹络数据传送能⼒的⼀项衡量标准B.限制硬件或软件故障对⽹络的影响的⼀种⽅法C.管理⽹络资源使⽤率的⼀套技术D.⽹络资源需求超出可⽤容量的⼀种状态3.下列哪种说法正确描述了云计算的特征?DA.企业可以直接连接到 Internet,⽽不需要使⽤ ISPB.需要投资新的基础设施才能访问云。
C.设备能够通过现有电线连接到 Internet。
D.通过订阅可以使⽤ Internet 访问应⽤程序。
4.填空题缩写词(byod)是指最终⽤户使⽤个⼈设备访问公司⽹络和资源的趋势。
5.哪两个 Internet 解决⽅案可以为 LAN 上的计算机提供始终在线的⾼带宽连接?(请选择两项。
)BEA.卫星B.DSLC.移动电话D.电话拨号E.电缆6.要求使⽤复杂的强密码是为了实现下列哪个⽹络安全⽬标?BA.确保冗余B.确保数据保密性C.确保访问的可靠性D.维护通信完整性7.下列有关 LAN 和 WAN 两者关系的说法,哪两项是正确的?(请选择两项。
)ABA.与 LAN 连接内部终端设备相⽐,WAN 连接 LAN 的带宽速度较低。
B.WAN 通常通过多个 ISP 运营,⽽ LAN 通常由⼀个组织或个⼈运营C.WAN 必须是公共的,⽽ LAN 可以由公有或私有实体拥有。
/doc/78d8e92a1511cc7931b765ce0508763230127473.html N 和 WAN 均能连接终端设备。
E.Internet 属于 WAN。
8.选择⽹络介质时应遵循哪两个标准?(请选择两项。
)BEA.⽹络上使⽤的终端设备的成本B.介质可以成功传送信号的距离C.需要优先处理的数据类型D.安装在⽹络中的中间设备的数量E.要安装介质的环境9家庭⽤户必须要有哪种⽹络类型访问才能进⾏⽹上购物?DA.外联⽹B.内部⽹C.局域⽹D.Internet10电路交换⽹络有何特征?BA.如果电路发⽣故障,呼叫将转发到新的路径。
思科网院第一学期1-6单元部分试题及答案

第一单元1、应用程序可以分为通用软件和行业专用软件。
下列哪两项属于行业专用软件?(选择两项。
)教育工具演示文稿电子表格字处理医疗实践管理软件数据库管理2、字处理软件的哪种特征表明它是本地应用程序?该应用程序可以在不同用户之间共享。
该软件存储在本地硬盘上。
该软件可以通过网页访问。
该软件能够处理文本和图片。
3、下列哪三个术语描述了计算机的不同类型?(选择三项。
)操作系统网络笔记本电脑台式计算机Windows大型机4、将笔记本电脑连接到扩展坞有哪两项优点?(选择两项)增强了机动性。
减少了所需电力。
可以使用外部显视器。
可以使用更多无线安全选件。
可以使用备用的连接选件。
5、为何服务器通常配备重复或冗余部件?服务器需要更高功率,因此需要更多组件。
服务器要全天候可供访问。
服务器可设计为独立塔式或机架安装式。
网络标准要求服务器配备重复部件。
6、通常用什么单位来表示计算机的处理速度?位像素赫兹字节7、购买预先组装好的计算机有哪两项优点?(选择两项。
)成本通常比较低可以精确指定组件组装的等待期更长足以执行大多数一般的应用程序适合有特殊需求的客户8、某用户计划在一台计算机上同时运行多个应用程序。
哪个计算机组件是完成此任务的关键?RAMNIC显卡声卡存储设备9、哪种适配卡可让计算机系统与本地网络中的其它系统交换信息?显卡声卡调制解调器卡网络接口卡10、服务器、台式计算机、便携式计算机使用的主要存储设备是什么?磁带驱动器硬盘光盘驱动器 (DVD)软盘驱动器11、哪个组件用于消除来自电源线的高压尖峰,使其不损坏计算机系统?CPU电涌抑制器主板硬盘12、 UPS 可以提供哪两项浪涌保护器所不具备的功能?(选择两项)保护计算机不受电压浪涌的损坏。
用内部电池提供备用电源。
保护计算机不受突然电压尖峰的损坏。
让用户有时间给电力公司打电话。
在电源出现故障时,为用户提供安全关机的时间。
通过墙上插座供电的发电机提供备用电源13、哪个计算机组件是计算机系统的神经中枢,并且负责处理机器中的所有数据?RAMCPU显卡声卡操作系统14、可以通过什么来防止静电放电 (ESD)?干燥、没有湿气的环境铺有地毯的地板接地腕带整洁的工作空间15、哪两种设备可能存在危险电压电平,因此未经专门的操作培训不得打开机体?(选择两项)鼠标打印机显示器键盘硬盘电源16、在当今较新的操作系统中,安装组件后,默认将如何分配系统资源?通过操作系统手动分配由管理员手动分配由组件静态分配给预设置的资源在组件和操作系统之间动态分配17、一位用户反映说,上周为某 PC 正确安装了一台外围设备,但自从今天启动 PC 后,该设备就一直无法正常工作。
思科网络 试题库

二、单选题1、 ADSL MODEM不能激活,打一个电话或振一下铃就好了,其原因可能是A、分离器损坏;B、modem工作不稳定;C、电话机有问题;D、线路接触面氧化;答案为d6、172.16.99.99/255.255.192.0 的广播地址是什么?A、172.16.99.255;B、172.16.127.255;C、172.16.255.255;D、172.16.64.127; 答案为b7、190.233.27.13./16所在网段地址A、190.233.0.0;B、190.0.0.0;C、190.233.27.0;答案为a8、224.0.0.5代表的是()地址。
A、主机地址;B、广播地址;C、网络地址;D、组播地址;答案为d10、ATM协议工作在________层。
A、物理层;B、链路层;C、网络层;D、传输层;答案为b11、ATM信元是定长的,而且信元的长度较小,只有()字节。
A、33;B、43;C、53;D、63;答案为c23、DHCP客户端申请一个新的IP地址之前,使用的初始IP地址是________。
A、0.0.0.0;B、127.0.0.1;C、255.255.255.255;D、169.254.1.1 ;答案为a24、DNS工作于()A、网络层 ;B、传输层;C、会话层;D、表示层;E、应用层;答案为e26、D类地址的缺省子网掩码有()位A、8;B、16;C、24;D、 None;答案为d28、FDDI 使用的是()局域网技术A、以太网;B、快速以太网;C、令牌环;D、令牌总线;答案为c29、IEEE 802.4是下面哪一种局域网标准?正确的选项是A、以太网;B、生成树;C、令牌环;D、令牌总线;答案为d30、IEEE于1999年颁布了用以标准化VLAN实现方案的________协议标准草案。
A、802.1B;B、802.1D;C、802.1P;D、802.1Q;答案为d32、IP报文头中固定长度部分为多少字节?A、10;B、20;C、30;D、40;答案为b33、IP报文中一部分字段专门用来描述报文的生命周期,即TTL值,它的最大值是________。
思科(CISCO)笔试题目、解析和答案

思科(CISCO)笔试题目、解析和答案一题:解:求至少几人及格,也就是求最多多少人不及格,情况分为:做对0个,做对1个,做对2个,做对3个,做对4个,做对5个,为了使不及格人最多,不妨对做对0个的人说,为何不把你的做错的两道给做对3个或4个的人呢,这样你还是不及格并且可以多增加人不及格,这样做对0个把自己的错误2个题给别人,他错3个,同理做对1个的把自己的一个错误题给别人,这样保证了不及格人最多,经过以上分析,现在不及格人最多时,只有一下几种情况:做对2个,做对3个,做对4个,做对5个。
分别设人数为:x2,x3.x4.x5,则:当x2最大是,至少及格人数为:100-x2x2+x3+x4+x5=100 (1)总错误题数为:100*5-(80+72+84+88+56)=120则:3x2+2x3+x4=120 (2)(2)-(1)得:2x2+x3-x5=20 (3)可以看出要想使x2最大,则x3最小,x5最大,则:x3=0,x5=56,则x2=38,x4=6,即做对2个38,做对3个0,做对4个6,全对56。
也就是说至少有100-x2=100-38=62人及格,对结果进行分析:对于第五题只有56人做对,那么38+6=44,即做对4个和做对2个的都有第五题做错,那么做对2个的38人只能在前4道题中错2道:显然很好分配,分法之一:38-28=10,做错1和2的10人,做错1和3的20-10=10人,做错2和3的16-10=6人,做错2和4的12人。
二题:10人和一个司机时间最少,则车接第十人正好与前面9个人一起到达终点设第一个人坐车t1小时,步行t2小时,求t1+t2,则:100t1+5t2=1000 (1)假设在d点把第一人放下,在c点车回来接到第二人,则车从d-c时间为:t=(100t1-5t1)/105,设从车载第二人开始开始到车追上第一人时,第一个走了s公里到达e点则:车在c点时,车与第一人的距离为105t=100t1-5t1=95t1,则:(95t1+s)/100=s/5 (2)即:5t1=s第一人从d-e走了:5t+s公里同理可知第三人到第10 人与第二人一样,则车一共送10人次,回头接人(空车)9次则第一人共走了9*(5t+s)=5t2即:9*[5*(100t1-5t1)/105+s]=5t2 (3)由(1),(2)(3)可得:t1=70/13,t2=1200/13,则:t1+t2=1270/13=97.69小时。
思科认证考试题库

思科认证考试题库思科认证考试题库首发网站:1. What are two reasons that a network administrator would use access lists? (Choose two.)A. to control vty access into a routerB. to control broadcast traffic through a routerC. to filter traffic as it passes through a routerD. to filter traffic that originates from the routerE. to replace passwords as a line of defense against security incursionsAnswer: AC解释一下:在VTY线路下应用ACL,可以控制从VTY线路进来的telnet的流量。
也可以过滤穿越一台路由器的流量。
2. A default Frame Relay WAN is classified as what type of physical network?A. point-to-pointB. broadcast multi-accessC. nonbroadcast multi-accessD. nonbroadcast multipointE. broadcast point-to-multipointAnswer: C解释一下:在默认的情况下,帧中继为非广播多路访问链路。
但是也可以通过子接口来修改他的网络的类型。
3.Refer to the exhibit. How many broadcast domains exist in the exhibited topology?A. oneB. twoC. threeD. fourE. fiveF. sixAnswer: C解释一下:广播域的问题,在默认的情况下,每个交换机是不能隔离广播域的,所以在同一个区域的所有交换机都在同一个广播域中,但是为了减少广播的危害,将广播限制在一个更小的范围,有了VLAN的概念,VLAN表示的是一个虚拟的局域网,而他的作用就是隔离广播。
思科网络技术学院第三学期官方测试总复习题

第一章Question 1分数: 1在处于不同的 VLAN 中的设备间配置通信需要使用OSI 模型中的哪个层? 选择一个答案A. 第 3 层B. 第 1 层C. 第 4 层D. 第 5 层错误这次提交的分数:0/1。
Question 2 分数: 1推荐同时在核心层和分布层采用哪种分层设计特征以在发生路由故障时保护网络?选择一个答案A. 冗余B. PoEC. 访问列表D. 聚合正确这次提交的分数:1/1。
Question 3 分数: 1分层网络设计模型中的哪一层称为互连网络的高速主干层,其中高可用性和冗余性是该层的关键? 选择一个答案A. 数据链路层B. 核心层C. 接入层D. 网络层E. 物理层F. 分布层正确这次提交的分数:1/1。
Question 4 分数: 1技术人员尝试向准备安装三台可堆叠交换机的客户解释 Cisco StackWise 技术。
下列哪种解释能准确说明 StackWise 技术? 选择一个答案A. StackWise 技术可通过增加线路卡来扩展交换机功能和端口。
B. StackWise 技术最多可将八个端口绑定在一起以提高可用带宽。
C. 通过 StackWise 技术,交换机可使用现有以太网电缆为终端设备供电。
D. 通过使用完全冗余的背板,StackWise 技术最多可使九台交换机实现互连。
错误这次提交的分数:0/1。
Question 5 分数: 1企业级交换机有哪两项特点? (选择两项。
) 选择至少一个答案A. 支持链路聚合B. 端口密度低C. 延时水平高D. 端口数量预先确定E. 转发速度高正确这次提交的分数:1/1。
Question 6 分数: 1网络技术人员应要求检查现有的交换网络。
检查结束后,技术人员提议添加新的交换机并更换影响性能的现有设备。
技术人员的建议获得了批准并得到预算上的支持。
以下哪两项信息有助于确定新交换机所需的端口密度?(选择两项。
) 选择至少一个答案A. 转发速率B. 流量分析C. 未来的预计发展D. 接入层为提高性能所需的集线器数量E. 所需核心层连接的数量错误这次提交的分数:0/1。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
思科网院考试题库CCNA1 - Module 2CCNA1 - Module 21Which two layers of the OSI model have the same functions as the TCP/IP model Network Access Layer? (Choose two.)NetworkTransportPhysical**Data Link**Session2What is a primary function of the trailer information added by the data link layer encapsulation?supports error detection**ensures ordered arrival of dataprovides delivery to correct destinationidentifies the devices on the local networkassists intermediary devices with processing and path selection3During the encapsulation process, what occurs at the data link layer? No address is added.The logical address is added.The physical address is added.**The process port number is added.4What device is considered an intermediary device?file serverIP phonelaptopprinterswitch**5Which layer encapsulates the segment into packets?physicaldata link**networktransport6Which statements correctly identify the role of intermediary devices in the network? (Choose three.)determine pathways for data**initiate data communicationsretime and retransmit data signals**originate the flow of datamanage data flows**final termination point for data flow7What can be identified by examining the network layer header?the destination device on the local mediathe path to use to reach the destination host**the bits that will be transferred over the mediathe source application or process creating the data8What is the proper order of the layers of the OSI model from the highest layer to the lowest layer?physical, network, application, data link, presentation, session, transportapplication, physical, session, transport, network, data link, presentationapplication, presentation, physical, session, data link, transport, networkapplication, presentation, session, transport, network, data link, physical**presentation, data link, session, transport, network, physical, application9Refer to the exhibit. Which three labels correctly identify the network types for the network segments that are shown? (Choose three.) Network A -- WANNetwork B -- WAN**Network C -- LAN**Network B -- MANNetwork C -- WANNetwork A -- LAN**10What are the key functions of encapsulation? (Choose three.)allows modification of the original data before transmissionidentifies pieces of data as part of the same communication**enables consistent network paths for communicationensures that data pieces can be directed to the correct receiving end device**enables the reassembly of complete messages**tracks delay between end devices11Refer to the exhibit. Which networking term describes the data interleaving process represented in the graphic?pipingPDUstreamingmultiplexing**encapsulation12What is a PDU?corruption of a frame during transmissiondata reassembled at the destinationretransmitted packets due to lost communication**a layer specific encapsulation13Refer to the exhibit. "Cell A" at IP address has established an IP session with "IP Phone 1" at IP address Based upon the graphic, which device type best describes the function of wireless device "Cell A?"the destination device**an end devicean intermediate devicea media device14Refer to the exhibit. Which set of devices contains only end devices? A, C, DB, E, G, HC, D, G, H, I, JD, E, F, H, I, J**E, F, H, I, J15Refer to the exhibit. Which term correctly identifies the device type thatis included in the green area?sourceendtransfer**intermediary16Which three statements best describe a Local Area Network (LAN)? (Choose three.)**A LAN is usually in a single geographical area.**The network is administered by a single organization.The connection between segments in the LAN is usually through a leased connection.The security and access control of the network are controlled by a service provider.**A LAN provides network services and access to applications for users within a common organization.Each end of the network is generally connected to a Telecommunication Service Provider (TSP).17Refer to the exhibit. What type of network is shown?WANMAN**LANWLAN18What is the purpose of the TCP/IP Network Access layer?path determination and packet switching**data representation, encoding, and controlreliability, flow control, and error detectiondetailing the components that make up the physical link and how to access itthe division of segments into packets19Which characteristic correctly refers to end devices in a network? manage data flowsoriginate data flow**retime and retransmit data signalsdetermine pathways for data20What is the primary purpose of Layer 4 port assignment?to identify devices on the local mediato identify the hops between source and destinationto identify to the intermediary devices the best path through the network to identify the source and destination end devices that are communicating **to identify the processes or services that are communicating within the end devices21Select the statements that are correct concerning network protocols.(Choose three.)**define the structure of layer specific PDU'sdictate how to accomplish layer functions**outline the functions necessary for communications between layers limit hardware compatibility**require layer dependent encapsulationseliminate standardization among vendorsCCNA1 - Module 3CCNA1 - Module 31. What is the purpose of resource records in DNS?used by the server to resolve names2. What are two forms of application layer software?applicationssyntax3. What application layer protocol is commonly used to support for file transfers between a client and a server?FTP4. What are two characteristics of peer-to-peer networks? decentralized resourcesresource sharing without a dedicated server5. Which layer of the OSI model supplies services that allow user to interface with the network?application6. What are three properties of peer-to-peer applications?acts as both a client and server within the same communicationhybrid mode includes a centralized directory of filesdoes not require specialized software7. What is the role of the OSI application layer?provides the interface between the applications on either end of the network8. What three protocols operate at the Application layer of the OSI model? DNS, SMTP, POP9. Which email components are used to forward mail between servers? MDA, MTA10. Which two protocols are used to control the transfer of web resources from a web server to a client browser?HTTPSHTTP11. Which statements are correct concerning the role of the MTA in handling email?receives email from the client's MUApasses email to the MDA for final deliveryuses SMTP to route email between servers12. As compared to SSH, what is the primary disadvantage of telnet?does not support encryption13. Which application layer protocols correctly match a corresponding function?DNS dynamically allocates IP addresses to hostsTelnet provides a virtual connection for remote access14. What is the automated service that matches resource names with the required IP address?DNS15. Refer to the exhibit. What is the destination port for the communication that is represented on line 5?8016. What are two characteristics of clients in data networks?initiate data exchangesmay upload data to servers17. What application layer protocol describes the services that are used for file sharing in Microsoft networks?SMB18. A network administrator is designing a network for a new branch office of twenty-five users. What are the advantages of using a client-server model?centralized administrationsecurity is easier to enforce19. A small home network has been installed to interconnect three computers together for gaming and file sharing. What two properties represent this network type?User accounts are centralized.Security is difficult to enforce.20. How does the application layer on a server usually process multiple client request for services?uses support from lower layer functions to distinguish between connections to the serviceCCNA1 - Module 4CCNA1 - Module 41Refer to the exhibit. What two pieces of information can be determined from the output that is shown? (Choose two.)The local host is using well-known port numbers to identify the source ports.**A termination request has been sent toCommunication with is using HTTP Secure.**The local computer is accepting HTTP requests.is performing the three-way handshake with2After a web browser makes a request to a web server that is listening tothe standard port, what will be the source port number in the TCP header of the response from the server?1353**80102417283Which information is found in both the TCP and UDP header information? sequencingflow control**acknowledgmentssource and destination4Which is an important characteristic of UDP?acknowledgement of data delivery**minimal delays in data deliveryhigh reliability of data deliverysame order data delivery5Refer to the exhibit. Host A is using FTP to download a large file from Server 1. During the download process, Server 1 does not receive an acknowledgment from Host A for several bytes of transferred data. Whataction will Server 1 take as a result?create a Layer 1 jam signal**reach a timeout and resend the data that needs to be acknowledged send a RESET bit to the hostchange the window size in the Layer 4 header6Refer to the exhibit. In line 7 of this Wireshark capture, what TCP operation is being performed?**session establishmentsegment retransmitdata transfersession disconnect7Refer to the exhibit. The initial TCP exchange of data between two hosts is shown in the exhibit. Assuming an initial sequence number of 0, what sequence number will be included in Acknowledgment 2 if Segment 6 is lost? 236**1850343134758Why is flow control used for TCP data transfer?to synchronize equipment speed for sent datato synchronize and order sequence numbers so data is sent in complete numerical order**to prevent the receiver from being overwhelmed by incoming datato synchronize window size on the serverto simplify data transfer to multiple hosts9During a TCP communication session, if the packets arrive to the destination out of order, what will happen to the original message? The packets will not be delivered.The packets will be retransmitted from the source.**The packets will be delivered and reassembled at the destination. The packets will be delivered and not reassembled at the destination.10With TCP/IP data encapsulation, which range of port numbers identifies all well-known applications?0 to 255256 to 1022**0 to 10231024 to 204749153 to 6553511Which transport layer protocol provides low overhead and would be used for applications which do not require reliable data delivery?TCPIP**UDPHTTPDNS12What are two features of the User Datagram Protocol (UDP)? (Choose two.) **flow control**low overheadconnectionlessconnection-orientedsequence and acknowledgements13What mechanism is used by TCP to provide flow control as segments travel from source to destination?sequence numberssession establishment**window sizeacknowledgments14What is dynamically selected by the source host when forwarding data? destination logical addresssource physical addressdefault gateway address**source port15Why are port numbers included in the TCP header of a segment?to indicate the correct router interface that should be used to forward a segmentto identify which switch ports should receive or forward the segment to determine which Layer 3 protocol should be used to encapsulate the data **to enable a receiving host to forward the data to the appropriate applicationto allow the receiving host to assemble the packet in the proper order16Which two options represent Layer 4 addressing? (Choose two.) identifies the destination network**identifies source and destination hostsidentifies the communicating applications**identifies multiple conversations between the hostsidentifies the devices communicating over the local media17Which three features allow TCP to reliably and accurately track the transmission of data from source to destination?**encapsulationflow controlconnectionless services**session establishment**numbering and sequencingbest effort delivery18Which OSI model layer is responsible for regulating the flow of information from source to destination, reliably and accurately? applicationpresentationsession**transportnetwork19Based on the transport layer header shown in the diagram, which of the following statements describe the established session? (Choose two.) This is a UDP header.**This contains a Telnet request.This contains a TFTP data transfer.The return packet from this remote host will have an Acknowledgement Number of 43693.**This is a TCP header.20Which event occurs during the transport layer three-way handshake? The two applications exchange data.TCP initializes the sequence numbers for the sessions.**UDP establishes the maximum number of bytes to be sent.The server acknowledges the bytes of data received from the client. CCNA1 - Module 5CCNA1 - Module 51In an IPv4 environment, what information is used by the router to forward data packets from one interface of a router to another?**destination network addresssource network addresssource MAC addresswell known port destination address2What information is added during encapsulation at OSI Layer 3?source and destination MACsource and destination application protocolsource and destination port number**source and destination IP address3In a connectionless system, which of the following is correct?The destination is contacted before a packet is sent.**The destination is not contacted before a packet is sent.The destination sends an acknowledgement to the source that indicates the packet was received.The destination sends an acknowledgement to the source that requests the next packet to be sent.4Which IP packet field will prevent endless loops?type-of-serviceidentificationflags**time-to-liveheader checksum5Which portion of the network layer address does a router use to forward packets?host portionbroadcast address**network portiongateway address6Refer to the exhibit. Using the network in the exhibit, what would be the default gateway address for host A in the network?**7If the default gateway is configured incorrectly on the host, what is the impact on communications?The host is unable to communicate on the local network.**The host can communicate with other hosts on the local network, but is unable to communicate with hosts on remote networks.The host can communicate with other hosts on remote networks, but is unable to communicate with hosts on the local network.There is no impact on communications.8What is the purpose of a default gateway?physically connects a computer to a networkprovides a permanent address to a computeridentifies the network to which a computer is connectedidentifies the logical address of a networked computer and uniquely identifies it to the rest of the network**identifies the device that allows local network computers to communicate with devices on other networks9What type of routing uses information that is manually entered into the routing table?dynamicinterior**staticstandard10When the destination network is not listed in the routing table of a Cisco router, what are two possible actions that the router might take? (Choose two.)**The router sends an ARP request to determine the required next hop address.The router discards the packet.The router forwards the packet toward the next hop indicated in the ARP table.**The router forwards the packet to the interface indicated by the source address.The router forwards the packet out the interface indicated by the default route entry.11What are the key factors to consider when grouping hosts into a common network? (Choose three.)**gatewayspurposephysical addressingsoftware version**geographic location**ownership12What is a component of a routing table entry?the MAC address of the interface of the routerthe destination Layer 4 port numberthe destination host address**the next-hop address13Which intermediary devices could be used to implement security between networks? (Choose two.)**routerhubswitch**firewallaccess pointbridge14What are three common problems with a large network? (Choose three.) too few broadcasts**performance degradation**security issues**limited management responsibilityhost identificationprotocol compatibility15Refer to the exhibit. All devices shown in the exhibit have factory default settings. How many broadcast domains are represented in the topology that is shown?3**45781116Which three statements are true about routes and their use? (Choose three.) If no route to the destination network is found, the packet is returned to the previous router.If the destination network is directly connected, the router forwards the packet to the destination host.**If multiple network entries exist for the destination network, the most general route is used to forward the packet.**If no route exists for the destination network and a default route is present, the packet is forwarded to the next-hop router.**If the originating host has a default gateway configured, the packet for a remote network can be forwarded using that route.If a host does not have a route manually configured for the destination network, the host will drop the packet.17Refer to the exhibit. A network administrator is troubleshooting a connectivity problem and needs to determine the address that is used to forward network packets out the network. Using the netstat -r command, the administrator would identify which address as the address to whichall hosts send packets that are destined for an outside network?**18Refer to the exhibit. A network administrator notices that there are too many broadcasts on the network. What two steps can the network administrator take to resolve this problem? (Choose two.)**Replace S2 with a router.Place all servers on S1.Disable TCP/IP broadcasts.**Subnet the /24 network.Disable all unused interfaces on the switches.19Refer to the exhibit. The network in the exhibit is fully operational. What two statements correctly describe the routing for the topology that is shown? (Choose two.)** is the next-hop address that is used by R3 to route a packet from the network to the network.is the next-hop address that is used by R1 to route a packet from thenetwork to the network.** is the next-hop address that is used by R1 to route a packet from the network to the network.is the next-hop address that is used by R3 to route a packet from the to the network.is the next-hop address that is used by R2 to route a packet from the network to the network.is the next-hop address that is used by R2 to route a packet from the network to the network.20What two characteristics are commonly associated with dynamic routing protocols? (Choose two.)require no device configuration**provide routers with up-to-date routing tablesrequire less processing power than static routes requireconsume bandwidth to exchange route information**prevent manual configuration and maintenance of the routing table21What statement describes the purpose of a default route?A host uses a default route to transfer data to another host on the same network segment.A host uses a default route to forward data to the local switch as the next hop to all destinations.A host uses a default route to identify the Layer 2 address of an end device on the local network.**A host uses a default route to transfer data to a host outside the local network when no other route to the destination exists.CCNA1 - Module 6CCNA1 - Module 61How many bits make up an IPv4 address?128644832 **2Refer to the exhibit. A network administrator has to develop an IP addressing scheme that uses the /24 address space. The network that contains the serial link has already been addressed out of a separate range. Each network will be allocated the same number of host addresses. Which network mask will be appropriate to address the remaining networks?**3Refer to the exhibit. The network administrator has assigned the internetwork of LBMISS an address range of This address range has been subnetted using a /29 mask. In order to accommodate a new building, the technician has decided to use the fifth subnet for configuring the new network (subnet zero is the first subnet). By company policies, the router interface is always assigned the first usable host address and the workgroup server is given the last usable host address. Which configuration should be entered into the workgroup server's properties to allow connectivity to the network?IP address: subnet mask: default gateway:IP address: subnet mask: default gateway:IP address: subnet mask: default gateway: **IP address: subnet mask: default gateway:IP address: subnet mask: default gateway:4Refer to the exhibit. Which network prefix will work with the IP addressing scheme shown in the graphic./24/16/20/27 **/25/285Refer to the exhibit. A network administrator discovers that host A is having trouble with Internet connectivity, but the server farm has full connectivity. In addition, host A has full connectivity to the server farm. What is a possible cause of this problem?The router has an incorrect gateway.Host A has an overlapping network address.Host A has an incorrect default gateway configured.Host A has an incorrect subnet mask.NAT is required for the host A network. **6What subnet mask would a network administrator assign to a network address of if it were possible to have up to 254 hosts?**7Given the IP address and subnet mask of , which of the following would describe this address?This is a useable host address.This is a broadcast address.This is a network address. **This is not a valid address.8What three facts are true about the network portion of an IPv4 address? (Choose three.)identifies an individual deviceis identical for all hosts in a broadcast domainis altered as packet is forwarded **varies in length **is used to forward packets **uses flat addressing9What is the network address of the host /23 in binary?... **.. 00010001.01000011. 01100010.10A router interface has been assigned an IP address of with a mask of To which subnet does the IP address belong?**11Refer to the exhibit. Why would the response shown be displayed after issuing the command ping on a PC?The IP settings are not properly configured on the host. **Internet Protocol is not properly installed on the host.There is a problem at the physical or data link layer.The default gateway device is not operating.A router on the path to the destination host has gone down.12What two things will happen if a router receives an ICMP packet which hasa TTL value of 1 and the destination host is several hops away? (Choose two.)The router will discard the packet.The router will decrement the TTL value and forward the packet to the next router on the path to the destination host.The router will send a time exceeded message to the source host. **The router will increment the TTL value and forward the packet to the next router on the path to the destination host.The router will send an ICMP Redirect Message to the source host. ** 13Refer to the exhibit. An administrator is designing security rules for the /24 network. Each security rule requires an address and mask pair to represent the machines that will be affected by the rule. Which two address and mask pairs will be the most precise way to reference the servers and hosts separately. (Choose two.)****14Which of the following are features of IPv6? (Choose three.)larger address space **faster routing protocolsdata types and classes of service **authentication and encryption **improved host naming conventionssame addressing scheme as IPv415Which process do routers use to determine the subnet network address basedupon a given IP address and subnet mask?binary addinghexadecimal andingbinary divisionbinary multiplicationbinary ANDing **16What is the primary reason for development of IPv6? securityheader format simplificationexpanded addressing capabilities **addressing simplification17Which three IP addresses are private? (Choose three.)******18Which statements are true regarding IP addressing? (Choose two.)NAT translates public addresses to private addresses destined for the Internet.Only one company is allowed to use a specific private network address space.Private addresses are blocked from public Internet by router. **Network is part of the private address space.IP address can be used for a host to direct traffic to itself. **Which IPv4 subnetted addresses represent valid host addresses? (Choose three.)/26/26 **/26 **/27/27/27 **20What is a group of hosts called that have identical bit patterns in the high order bits of their addresses?an interneta network **an octeta radi **21Refer to the exhibit. Host A is connected to the LAN, but it cannot get access to any resources on the Internet. The configuration of the host is shown in the exhibit. What could be the cause of the problem?The host subnet mask is incorrect.The default gateway is a network address.The default gateway is a broadcast address.The default gateway is on a different subnet from the host. **22Which of the following network devices are recommended to be assigned static IP addresses? (Choose three.)LAN workstationsservers **network printers **routers **remote workstationslaptopsCCNA1 - Module 7CCNA1 - Module 71Which options are properties of contention-based media access for a shared media? (Choose three.)**non-deterministic**less overheadone station transmits at a time**collisions existdevices must wait their turntoken passing2What is a primary purpose of encapsulating packets into frames? provide routes across the internetworkformat the data for presentation to the user**facilitate the entry and exit of data on mediaidentify the services to which transported data is associated3。
