CCNA第一学期Finalexam考试英文版答案
思科CCNA1第八章试题及答案英文版

1. 1. QuestionWhat is a result of connecting two or more switches together?o The number of broadcast domains is increased.o The size of the broadcast domain is increased.o The number of collision domains is reduced.o The size of the collision domain is increased.2. 2. QuestionRefer to the exhibit. How many broadcast domains are there?CCNA1 v6.0 Chapter 8 Exam 005o 1o 2o 3o43. 3. QuestionWhat are two reasons a network administrator might want to create subnets?(Choose two.)o simplifies network designo improves network performanceo easier to implement security policieso reduction in number of routers neededo reduction in number of switches needed4. 4. QuestionRefer to the exhibit. A company uses the address block of 128.107.0.0/16 for its network. What subnet mask would provide the maximum number of equal size subnets while providing enough host addresses for each subnet in the exhibit?CCNA1 v6.0 Chapter 8 Exam 007o 255.255.255.0o 255.255.255.128o 255.255.255.192o 255.255.255.224o 255.255.255.2405. 5. QuestionRefer to the exhibit. The network administrator has assigned the LAN of LBMISS an address range of 192.168.10.0. This address range has beensubnetted using a /29 prefix. In order to accommodate a new building, the technician has decided to use the fifth subnet for configuring the newnetwork (subnet zero is the first subnet). By company policies, the router interface is always assigned the first usable host address and the workgroup server is given the last usable host address. Which configuration should be entered into the properties of the workgroup server to allow connectivity to the Internet?CCNA1 v6.0 Chapter 8 Exam 004o IP address: 192.168.10.65 subnet mask: 255.255.255.240, default gateway: 192.168.10.76o IP address: 192.168.10.38 subnet mask: 255.255.255.240, default gateway: 192.168.10.33o IP address: 192.168.10.38 subnet mask: 255.255.255.248, default gateway: 192.168.10.33o IP address: 192.168.10.41 subnet mask: 255.255.255.248, default gateway: 192.168.10.46o IP address: 192.168.10.254 subnet mask: 255.255.255.0, defaultgateway: 192.168.10.16. 6. QuestionIf a network device has a mask of /28, how many IP addresses are available for hosts on this network?o 256o 254o 62o 32o 16o 147. 7. QuestionWhich subnet mask would be used if 5 host bits are available?o 255.255.255.0o 255.255.255.128o 255.255.255.224o 255.255.255.2408. 8. QuestionHow many host addresses are available on the network 172.16.128.0 with a subnet mask of 255.255.252.0?o 510o 512o1022o 1024o 2046o 20489. 9. QuestionHow many bits must be borrowed from the host portion of an address to accommodate a router with five connected networks?o twoo threeo fouro five10. 10. QuestionA network administrator wants to have the same network mask for allnetworks at a particular small site. The site has the following networks and number of devices:IP phones – 22 addressesPCs – 20 addresses neededPrinters – 2 addresses neededScanners – 2 addresses neededThe network administrator has deemed that 192.168.10.0/24 is to be the network used at this site. Which single subnet mask would make the most efficient use of the available addresses to use for the four subnetworks?o 255.255.255.0o 255.255.255.192o 255.255.255.224o 255.255.255.240o 255.255.255.248o 255.255.255.25211. 11. QuestionA company has a network address of 192.168.1.64 with a subnet mask of255.255.255.192. The company wants to create two subnetworks that would contain 10 hosts and 18 hosts respectively. Which two networks wouldachieve that? (Choose two.)o 192.168.1.16/28o 192.168.1.64/27o 192.168.1.128/27o 192.168.1.96/28o 192.168.1.192/2812. 12. QuestionA network administrator is variably subnetting a network. The smallestsubnet has a mask of 255.255.255.248. How many usable host addresses will this subnet provide?o 4o 6o 8o 10o 1213. 13. QuestionRefer to the exhibit. Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224 for all subnets, how many total host addresses are unused in the assigned subnets?CCNA1 v6.0 Chapter 8 Exam 001o 56o 60o 64o 68o7214. 14. QuestionRefer to the exhibit. Considering the addresses already used and having to remain within the 10.16.10.0/24 network range, which subnet address could be assigned to the network containing 25 hosts?CCNA1 v6.0 Chapter 8 Exam 002o 10.16.10.160/26o 10.16.10.128/28o 10.16.10.64/27o 10.16.10.224/26o 10.16.10.240/27o 10.16.10.240/2815. 15. QuestionA network administrator needs to monitor network traffic to and fromservers in a data center. Which features of an IP addressing scheme should be applied to these devices?o random static addresses to improve securityo addresses from different subnets for redundancyo predictable static IP addresses for easier identificationo dynamic addresses to reduce the probability of duplicate addresses 16. 16. QuestionWhich two reasons generally make DHCP the preferred method of assigning IP addresses to hosts on large networks? (Choose two.)o It eliminates most address configuration errors.o It ensures that addresses are only applied to devices that require apermanent address.o It guarantees that every device that needs an address will get one.o It provides an address only to devices that are authorized to be connected to the network.o It reduces the burden on network support staff.17. 17. QuestionA DHCP server is used to assign IP addresses dynamically to the hosts on anetwork. The address pool is configured with 192.168.10.0/24. There are 3 printers on this network that need to use reserved static IP addresses from the pool. How many IP addresses in the pool are left to be assigned to other hosts?o 254o251o 252o 25318. 18. QuestionRefer to the exhibit. A company is deploying an IPv6 addressing scheme for its network. The company design document indicates that the subnet portion of the IPv6 addresses is used for the new hierarchical network design, with the s ite subsection to represent multiple geographical sites of the company, the s ub-site section to represent multiple campuses at each site, and thes ubnet section to indicate each network segment separated by routers. With such a scheme, what is the maximum number of subnets achievedper sub-site?CCNA1 v6.0 Chapter 8 Exam 003o 0o 4o16o 25619. 19. QuestionWhat is the prefix for the host address 2001:DB8:BC15:A:12AB::1/64?o 2001:DB8:BC15o 2001:DB8:BC15:Ao 2001:DB8:BC15:A:1o 2001:DB8:BC15:A:1220. 20. QuestionConsider the following range of addresses:2001:0DB8:BC15:00A0:0000::2001:0DB8:BC15:00A1:0000::2001:0DB8:BC15:00A2:0000::…2001:0DB8:BC15:00AF:0000::The prefix-length for the range of addresses is /6021. 21. QuestionMatch the subnetwork to a host address that would be included within the subnetwork. (Not all options are used.)CCNA1 v6.0 Chapter 8 Exam 0122. 22. QuestionRefer to the exhibit. Match the network with the correct IP address and prefix that will satisfy the usable host addressing requirements for each network. (Not all options are used.)CCNA1 v6.0 Chapter 8 Exam 006。
CCNA2-FINAL-(A+B+C套)英文版

CCNA第二学期《Final Examinnation》英文A卷1 What are two functions of a router? (Choose two.)It forwards data packets toward their destination.It forwards the packet to the destination if the TTL value is 0.It changes the destination IP address of data packets before forwarding them to an exit interface.It determines the best path based on the destination MAC address.It acts as an intersection between multiple IP networks.2 Which router component contains a scaled-down version of the IOS that can be used to reload a complete version of the IOS in the event that the IOS becomes damaged or corrupted?ROMFlashSDRAMNVRAM3 Using default settings, what is the next step in the router boot sequence after the IOS loads from flash? Perform the POST routine.Search for a backup IOS in ROM.Load the bootstrap program from ROM.Load the running-config file from RAM.Locate and load the startup-config file from NVRAM.4Refer to the exhibit. How many routes are ultimate routes?34575ADCABCIt will load balance the traffic between ADC and ABCIt will send the traffic via ABC, and will use ADC as a backup path only when ABC fails.6Refer to the exhibit. Routers R1 and R3 use different routing protocols with default administrative distance values. All devices are properly configured and the destination network is advertised by both protocols.Which path will be used to transmit the data packets from PC1 to PC2?The packets will travel via R2-R1.The packets will travel via R2-R3.The traffic will be load-balanced between two paths — via R2-R1 and via R2-R3.The packets will travel via R2-R3, and the other path via R2-R1 will be retained as the backup path.Refer to the exhibit. The network is configured for OSPF routing with default settings. The bandwidths have been configured correctly for each link. If the T1 link between router A and router E fails, what path will a packet from router A take to reach the LAN attached to router F when the network has converged?A, B, C, FA, B, C, E, FA, D, G, E, FA, D, G, H, F8 In a lab test environment, a router has learned about network 172.16.1.0 through four different dynamic routing processes. Which route will be used to reach this network?D 172.16.1.0/24 [90/2195456] via 192.168.200.1, 00:00:09, Serial0/0/0O 172.16.1.0/24 [110/1012] via 192.168.200.1, 00:00:22, Serial0/0/0R 172.16.1.0/24 [120/1] via 192.168.200.1, 00:00:17, Serial0/0/0I 172.16.1.0/24 [100/1192] via 192.168.200.1, 00:00:09, Serial0/0/09 Which two statements are true for link-state routing protocols? (Choose two.)Routers that run a link-state protocol can establish a complete topology of the network.Routers in a multipoint network that run a link-state protocol can exchange routing tables.Routers use only hop count for routing decisions.The shortest path first algorithm is used.Split horizon is used to avoid routing loops.10with static routeswith a routed protocolwith a routing protocolwith directly connected routes11Refer to the exhibit. What is the meaning of the highlighted value 120?It is the metric that is calculated by the routing protocol.It is the value that is used by the DUAL algorithm to determine the bandwidth for the link.It is the administrative distance of the routing protocol.It is the hold-down time, measured in seconds, before the next update.12 Which statement is true about the metrics used by routing protocols?A metric is a value used by a particular routing protocol to compare paths to remote networks.A common metric is used by all routing protocols.The metric with the highest value is installed in the routing table.The router may use only one parameter at a time to calculate the metric.13 Which routing protocol by default uses bandwidth and delay to calculate the metric of a route? RIPv1RIPv2OSPFEIGRP14 Which three routing metrics are correctly defined? (Choose three.)delay - the link speedreliability - the error rate on a linkload - the amount of traffic on a linkcost - the value to indicate preference for a routehop count - the path selected with the highest bandwidthbandwidth - the amount of time it takes a packet to travel a link15 Which two statements about routing protocols are accurate? (Choose two.)OSPF supports VLSM.RIPv1 supports VLSM.RIPv2 does not have a hop count limit.EIGRP supports discontiguous network designs.16Refer to the exhibit. A device is required to complete the connection between router R1 and the WAN. Which two devices can be used for this? (Choose two.)a CSU/DSU devicea modeman Ethernet switcha huba bridge17 When connecting two devices, which situation would normally require the use of a crossover cable? connecting a host to a switchconnecting a switch to a routerconnecting a switch to a switchconnecting a host to a router console port18Refer to the exhibit. A network administrator has run the show interface command. The output of this command is displayed. What is the first step that is required to make this interface operational?Switch the cable with a known working cable.Issue the no shutdown command on the interface.Configure the interface as a loopback interface.Set the encapsulation for the interface.19 Which port should a terminal emulator be connected to in order to access a router without network connectivity?T1serialconsoleFastEthernet20 Which router mode is accessed by entering the enable command?user EXECprivileged EXECglobal configurationinterface configuration21Refer to the exhibit. When a static IP address is being configured on the host, what address should be used for the default gateway?10.1.1.110.1.1.2172.16.1.122Refer to the exhibit. The show cdp neighbors command was run on one of the devices as shown. Based on this information, which two facts can be determined? (Choose two.)The command was run on the router.ABCD is a non- CISCO device.Layer 3 connectivity between two devices exists.ABCD supports routing capability.ABCD is connected to the Fa0/0 interface of the neighboring device.23Refer to the exhibit. Which statement is true about the Ethernet interfaces shown in the network?A frame leaves interface Fa0/0 of R1 with the source MAC address as 000C.3010.9260.A packet will not be forwarded between R1 and R2 until the no shutdown command is issued on the Fa0/0 interface of R1.24Refer to the exhibit. Which solution provides the most efficient use of router resources for forwarding traffic between BR and HQ?RIPRIPv2EIGRPstatic routes25Refer to the exhibit. Pings are failing between HostA and HostB. The network administrator discovers that Router1 does not have a route to the 172.16.0.0 network. Assuming Router2 is configured correctly, which two static routes could be configured on Router1 to enable Host A to reach network 172.16.0.0? (Choose two.)ip route 172.16.0.0 255.255.0.0 S0/0ip route 172.16.0.0 255.255.0.0 S0/1ip route 172.16.0.0 255.255.0.0 192.168.0.1ip route 192.168.0.1 172.16.0.0 255.255.0.0 S0/0ip route 192.168.0.1 172.16.0.0 255.255.0.0 S0/126Refer to the exhibit. How was the OSPF default gateway entry for R2 determined?Default routes are automatically injected by OSPF into all advertisements.A static default gateway route is defined in the configuration of R2.The default-information originate command is applied on R1.The ISP defines the gateway of last resort and automatically passes it to R1 and R2.The ip default-gateway command is applied on R2.27Refer to the exhibit. On the basis of the show running-config output, which option correctly reflects the routes that will be listed in the R2 routing table?答案:D28192.168.2.1192.135.250.129 Because of a topology change, the next hop IP address in the current static route must be reconfigured. How can a static route entry be altered to accommodate a topology change?Keep the existing static route and configure a new static route with the correct next hop IP address.Negate the existing static route and configure a new static route with the correct next hop IP address.Do nothing. The existing static route will automatically update the next hop entry with the new IP address. Keep the existing static route, reload the router, and configure a new static route with the correct next hop IP address.30Refer to the exhibit. The entire 192.168.1.0 network has been allocated to address hosts in the diagram. Utilizing VLSM with contiguous address blocks, which set of addresses and prefixes could be used to create an addressing solution with a minimum waste of IP addresses?答案:D31Refer to the exhibit. Which host has a combination of IP address and subnet mask on the same network as Fa0/0 of Router1?host Ahost Bhost Chost D32Refer to the exhibit. If the EIGRP routing protocol is used throughout the network, which IP address and mask prefix should be sent by router R1 to the Edge router as a result of manual summarization of LANs A, B, C, and D?33Refer to the exhibit. Routers RTRA and RTRB are running OSPF. What entry does RTRA add in the routing table when Serial 0/0/0 receives an update about the network that is attached to RTRB?O 172.16.7.0/30 [110/51] via 10.10.10.2, 00:00:25, Serial0/0/0O 172.16.7.16/28 [110/51] via 10.10.10.2, 00:00:25, Serial0/0/0O 172.16.7.0/24 [110/51] via 10.10.10.2, 00:00:25, Serial0/0/0O 172.16.0.0/16 [110/51] via 10.10.10.2, 00:00:25, Serial0/0/034Refer to the exhibit. If RIPv1 is used as the routing protocol throughout the network, what RIPv1 route will router R1 advertise to router R3?10.1.0.010.1.1.010.1.2.035 Which statement correctly describes a feature of RIP?RIP is a link-state routing protocol.RIP uses only one metric—hop count— for path selection.Advertised routes with hop counts greater than 10 are unreachable.Messages are broadcast every 10 seconds.36Refer to the exhibit. The network is using the RIPv2 routing protocol. If network 10.0.0.0 goes down, what mechanism will prevent Router1 from advertising false routing information back to Router2?triggered updatespoison reverseholddown timerssplit horizonroute poisoningsplit horizonhold-down timertriggered updates38Refer to the exhibit. When troubleshooting a network, it is important to interpret the output of various router commands. On the basis of the exhibit, which three statements are true? (Choose three.)The missing information for Blank 1 is the command show ip route.The missing information for Blank 1 is the command debug ip route.The missing information for Blank 2 is the number 100.The missing information for Blank 2 is the number 120.The missing information for Blank 3 is the letter R.The missing information for Blank 3 is the letter C.39Refer to the exhibit. R1 and R2 are adjacent routers both running RIP. All interfaces on both routers are correctly configured and operational. Both routers are configured to include all connected interfaces in routing updates. R2 is not showing any routes from R1 in the routing table. What is the likely cause?The adjacent interfaces are passive.The distance of 120 exceeds 15 hops.R2 will not accept version 1 updates from R1.Routes are being summarized by R1 but not by R2.40Refer to the exhibit. All routers are configured to use the EIGRP routing protocol with defaultIt will travel via A, B, and C.It will travel via A, F, E, D, and C.It will travel via A, G, H, and C.41 Which multicast address does EIGRP use to send hello and updates packets?224.0.0.5224.0.0.6224.0.0.942 A router has EIGRP configured as the only routing protocol. In what way might EIGRP respond if there is no feasible successor route to a destination network and the successor route fails?It broadcasts hello packets to all routers in the network to re-establish neighbor adjacencies.It sends queries to adjacent neighbors until a new successor route is found.It immediately sends its entire routing table to its neighbors.It will set the metric for the failed route to infinity.43Refer to the exhibit. EIGRP 1 has been configured on R1. What is the effect of configuring the ip bandwidth-percent eigrp command?The EIGRP bandwidth routing metric will be reduced by 30%.EIGRP 1 protocol traffic will be restricted to 30% of the link bandwidth.Packets that are routed based on EIGRP routing table entries will be limited to 30% of the link bandwidth. EIGRP traffic will be permitted to burst for short periods to 30% above the configured link bandwidth.44Refer to the exhibit. Which two statements are true based on the exhibited output? (Choose two.)All routes are stable.Each route has one feasible successor.The administrative distance of EIGRP has been set to 50.The show ip eigrp topology command has been run on R1.45Refer to the exhibit. A network designer is testing a prototype of WAN connections. All of the routers in the exhibit are configured for OSPF routing. The design requires that the path between routers A and D through ISP-A is the primary and the path through ISP-B servers as a backup. The designer notices that router A has two equal-cost paths to the LAN on router D. How can the designer correct this problem?Issue a clock rate 2000000 interface command on S0/0/1 of router ISP-B.Change the default OSPF reference bandwidth on router A.Configure two static routes with administrative distances of 10.Use the bandwidth command to change the default bandwidth on the link to router B.46Refer to the exhibit. R1 and R2 are unable to establish an adjacency. What two configuration changes will correct the problem? (Choose two.)Set a lower priority on R2.Configure the routers in the same area.Set a lower cost on R2 compared to R1.Add a backup designated router to the network.Match the hello and dead timers on both routers.47Refer to the exhibit. If the router loopback interfaces, FastEthernet interfaces, and OSPF priorities are configured as shown, which router would win an OSPF DR election?ABCD48 Two routers need to be configured within a single OSPF area. Which two components need to be configured on both routers to achieve this? (Choose two.)the same process IDthe same area IDnetwork addresses and wildcard masksthe same router IDthe same loop back address49Refer to the exhibit. What OSPF network statements are required for the router B to advertise the three networks that are attached?router ospf 1network 10.0.0.0 0.0.0.255 area 0router ospf 1network 10.1.1.0 0.3.255.255 area 0network 10.10.1.0 0.255.255.255 area 0network 10.20.1.0 0.255.255.255 area 0router ospf 1network 10.1.1.0 0.0.0.3 area 0network 10.10.1.0 0.0.255.255 area 0network 10.20.1.0 0.0.255.255 area 0router ospf 1network 10.1.1.0 0.0.0.3 area 0network 10.10.1.0 0.0.0.255 area 0network 10.20.1.0 0.0.0.255 area 050Refer to the exhibit. A network administrator is trying to determine why router JAX has no OSPF routes in its routing table. All routers are configured for OSPF area 0. From the JAX router, the administrator is able to ping its connected interfaces and the Fa0/1 interface of the ORL router but no other router interfaces. What is a logical step that the network administrator should take to troubleshoot the problem?Reboot the routers.Change the OSPF process ID on all of the routers to 0.Check to see if the cable is loose between ORL and JAX.Check to see if CDP packets are passing between the routers.Use show and debug commands to determine if hellos are propagating.CCNA第二学期《Final Examinnation》英文B卷1 A network administrator is in charge of two separate networks that share a single building. What device will be required to connect the two networks and add a common connection to the Internet that can be shared?hubrouteraccess pointEthernet switch2 Which two router component and operation pair are correctly described? (Choose two.)DRAM - loads the bootstrapRAM - stores the operating systemFlash - executes diagnostics at bootupNVRAM - stores the configuration fileROM - stores the backup configuration filePOST - runs diagnostics on hardware modules3 A router boots and enters setup mode. What is the reason for this?The IOS image is corrupt.Cisco IOS is missing from flash memory.The configuration file is missing from NVRAM.The POST process has detected hardware failure.4Refer to the exhibit. Packets destined to which two networks will require the router to perform a recursive lookup? (Choose two.)5 Which candidate route has the longest match for a packet with a destination address of 10.30.16.48?6Refer to the exhibit. Routers R1 and R3 use different routing protocols with default administrative distance values. All devices are properly configured and the destination network is advertised by both protocols.Which path will be used to transmit the data packets from PC1 to PC2?The packets will travel via R2-R1.The packets will travel via R2-R3.The traffic will be load-balanced between two paths — via R2-R1 and via R2-R3.The packets will travel via R2-R3, and the other path via R2-R1 will be retained as the backup path.R 192.168.1.0/24 [120/3] via 192.168.110.1, 00:00:17, Serial0/1/0R 192.168.1.0/24 [120/2] via 192.168.200.1, 00:00:17, Serial0/0/0R 192.168.1.0/24 [120/1] via 192.168.100.1, 00:00:17, Serial0/0/1R 192.168.1.0/24 [120/4] via 192.168.101.1, 00:00:17, Serial0/1/18Refer to the exhibit. The router receives a packet that is destined for 192.168.5.79. How will the router handle this packet?It will forward the packet via the FastEthernet0/0 interface.It will forward the packet via the Serial0/0/0 interface.It will forward the packet via the Serial0/0/1 interface.It will drop the packet.9 A network administrator uses the RIP routing protocol to implement routing within an autonomous system. What are two characteristics of this protocol? (Choose two.)It uses the Bellman-Ford algorithm to determine the best path.It displays an actual map of the network topology.It offers rapid convergence in large networks.It periodically sends complete routing tables to all connected devices.It is beneficial in complex and hierarchically designed networks.10 Which two statements are true for link-state routing protocols? (Choose two.)Routers that run a link-state protocol can establish a complete topology of the network.Routers in a multipoint network that run a link-state protocol can exchange routing tables.Routers use only hop count for routing decisions.The shortest path first algorithm is used.Split horizon is used to avoid routing loops.11 Which two statements are true about classless routing protocols? (Choose two.)They can be used for discontiguous subnets.They can forward supernet routes in routing updates.They cannot implement classful routes in routing tables.They use only a hop count metric.They do not include the subnet mask in routing updates.12 Which statement is true regarding routing metrics?All routing protocols use the same metrics.EIGRP uses bandwidth as its only metric.Routers compare metrics to determine the best route.The larger metric generally represents the better path.13 Which routing protocol by default uses bandwidth and delay to calculate the metric of a route?RIPv2OSPFEIGRP14 You have been asked to explain converged networks to a trainee. How would you accurately describe a converged network?A network is converged when all routers have formed an adjacency.A network is converged immediately after a topology change has occurred.A network is converged when all routers flush the unreachable networks from their routing tables.A network is converged after all routers share the same information, calculate best paths, and update their routing tables.15Refer to the exhibit. All the routers are properly configured to use the RIP routing protocol with default settings, and the network is fully converged. Router A is forwarding data to router E. Which statement is true about the routing path?Router A will send the data via the A-D-E path that is listed in the routing table.Router A will load-balance the traffic between A-B-E and A-C-E.Router A will determine that all paths have equal metric cost.Router A will send the data through A-D-E and keep A-B-E and A-C-E as the backup paths.16Refer to the exhibit. A device is required to complete the connection between router R1 and the WAN. Which two devices can be used for this? (Choose two.)a CSU/DSU devicean Ethernet switcha huba bridge17 Which component is typically used to connect the WIC interface of a router to a CSU/DSU?V.35 cableRJ-45 adaptercrossover cablestraight-through cable18 Which router mode is accessed by entering the enable command?user EXECprivileged EXECglobal configurationinterface configuration19Refer to the exhibit. What are the effects of the exhibited commands on the router?All passwords are encrypted.Only Telnet sessions are encrypted.Only the enable password is encrypted.Only the enable password and Telnet session are encrypted.Enable and console passwords are encrypted.20Refer to the exhibit. A technician has configured the interfaces on the Router, but upon inspection discovers that interface FastEthernet0/1 is not functioning. Which action will most likely correct the problem with FastEthernet0/1?A clock rate should be added to the interface configuration.The subnet mask should be added to the interface configuration.An interface description needs to be added to the interface configuration.The no shutdown command needs to be added to the interface configuration.21Refer to the exhibit. Which two facts can be derived from this output? (Choose two.)Three network devices are directly connected to Router2.The serial interface between Router2 and Router3 is up.Router1 and Router3 are directly connected.Six devices are up and running on the network.Layer 3 functionality between routers is configured properly.22Refer to the exhibit. Which route in the routing table of R1 will be discarded by its neighboring router? 192.168.2.0192.168.3.0192.168.9.0192.168.10.0192.168.11.023Refer to the exhibit. All interfaces are addressed and functioning correctly. The network administrator runs the tracert command on host A. Which two facts could be responsible for the output of this command? (Choose two.)The gateway for Host A is missing or improperly configured.The gateway for Host B is missing or improperly configured.24 In which situation would a default static route be recommended?when connecting an edge router to the Internetwhen variable length subnet masking is in effectwhen there is more than one valid route for a destination networkwhen a destination network has a larger mask than any routes in the routing table25 What is the advantage of configuring a static route with an exit interface instead of a next-hop address?The router will perform a recursive lookup.This route will automatically be used as the gateway of last resort.The exit interface configuration consumes less router processing time.The exit interface configuration has an administrative distance value of 1.26Refer to the exhibit. On the basis of the show running-config output, which option correctly reflects the routes that will be listed in the R2 routing table?答案:D27 A static route has been configured on a router. However, the destination network no longer exists. What should an administrator do to remove the static route from the routing table?Change the routing metric for that route.Nothing. The static route will go away on its own.Change the administrative distance for that route.Remove the route using the no ip route command.28Refer to the exhibit. Hosts on the 192.168.1.0 network cannot communicate with hosts on the 172.16.1.1 network. The network administrator has run the show ip route command on R1.What could be the cause of this problem?The FastEthernet interface on R1 is disabled.Autosummarization is enabled on R1.The serial interface S0/0/0 of R1 is administratively down.No static route or routing protocol is configured.29A new static route must be configured on R1 with the R3 serial interface as the next hop.A new default route must be configured on R1 with the R3 serial interface as the next hop.The default route on R2 should be configured with the R3 serial interface as the next hop.The default route on R2 must be replaced with a new static route and the next hop should be the R1 FastEthernet interface.31Refer to the exhibit. Which summarization should R1 use to advertise its networks to R2?32Refer to the exhibit. Host A is unable to access the Internet. What is the reason for this?The IP address of host A is incorrect.The default gateway of host A is incorrect.The Fa0/1 interfaces of the two routers are configured for different subnets.The subnet mask for the Fa0/0 interface of R1 is incorrect.33Automatic summarization is enabled on R1.The routing table of R2 contains only classful networks.R2 will reject this update.The routing protocol that is configured on both routers is RIPv1.34 Which additional piece of information is included in the updates of classless routing protocols to support the use of VLSM and discontiguous networks?metricnetwork maskneighbor router IDadministrative distance35Refer to the exhibit. The network is running the RIP routing protocol. Network 10.0.0.0 goes down. Which statement is true regarding how the routers in this topology will respond to this event?Router4 will learn about the failed route 30 seconds later in the next periodic update.Split horizon will prevent Router4 from fowarding packets to the 10.0.0.0 network until the holddown timer expires.Router5 immediately flushes the unreachable route from its routing table.Router5 will send Router4 a triggered update with a metric of 16 for network 10.0.0.0.clears an unreachable route from the routing table after the invalid timer expiresprevents regular update messages from inappropriately reinstating a route that may have gone badremoves an unreachable route from the routing table after the flush timer expireslimits the period of time or number of hops a packet can traverse through the network before it should be discardedused to mark the route as unreachable in a routing update that is sent to other routers37 Which two technologies can be used in distance vector routing protocols to prevent routing loops? (Choose two.)authenticationlink-state advertisementshold-down timersSpanning Tree Protocolsplit horizon38Refer to the exhibit. PC1 is unable to access the Internet. What is the cause of the problem?An incorrect IP address is configured between the two routers.No static route is configured on Router2.A routing loop has occurred.No routing protocol is configured on either of the two routers.39。
思科CCNA5.0Final答案汇总

1PDU 封装的正确顺序是什么?答案说明最高分值correctness of response 2 points for Option 10 points for any other option22管理员在发出 ping 命令之后在交换机上使用 Ctrl-Shift-6 键组合。
使用这些按键有什么用途?重新启动ping 进程中断 ping 进程退出到不同的配置模式允许用户完成命令要中断一个 IOS 进程(例如 ping 或 traceroute ),用户可以输入 Ctrl-Shift-6 键组合。
Tab 用于完成命令参数或变量的其余部分。
要退出配置模式并进入特权模式,可以使用 Ctrl-Z 按键。
CTRL-R 将会重新显示当前键入的行,这样便于用户按 Enter 并重新发出 ping 命令。
答案说明最高分值correctness of response 2 points for Option 2 0 points for any other option23 建立融合网络有何用途?为所有终端设备提供高速连接确保平等对待所有类型的数据包实现数据网络基础架构设备的容错能力和高可用性降低部署和维护通信基础设施的成本随着技术的发展,各个公司现在可以将不同的网络整合到一个平台之上,称为融合网络。
在融合网络中,语音、视频和数据通过同一网络传输,从而使人们不必再创建和维护各个单独的网络。
这也降低了提供和维护通信网络基础设施相关的成本。
答案说明最高分值correctness of response 2 points for Option 40 points for any other option24请参见图示。
哪个区域最有可能是图中所示的公司网络的外联网?区域A区域B区域C区域D外联网是外部实体访问其他公司的数据的平台。
其形式可能是产品供应商所使用的库存服务器,也可能是外部实体用来访问当天客户数量的当前信息的Web 服务器。
CCNA英文试题_(含答案)

1. Refer to the exhibit. What could bepossible causes for the "Serial0/0 is down"interfacestatus? (Choosetwo.)A. A Layer 1 problem exists.B. The bandwidth is set too low.C. A protocol mismatch exists.D. An incorrect cable is being used.E. There is an incorrect IP address on the Serial 0/0 interface.Answer: AD2. Before installing a new, upgraded version of the IOS, what should be checked on the router, andwhichcommand should be used to gather this information? (Choose two.)A. the amount of available ROMB. the amount of available flash and RAM memoryC. the version of the bootstrap software present on the routerD. show versionE. show processesF. show running-configAnswer: BD3. Refer to the exhibit. Which two statements are true about interVLAN routing in the topologythat is shownin the exhibit? (Choose two.)中国思科华为3COM 网络技术发布A. Host E and host F use the same IP gateway address.B. Router1 and Switch2 should be connected via a crossover cable.C. Router1 will not play a role in communications between host A and hostD.D. The FastEthernet 0/0 interface on Router1 must be configured with subinterfaces.E. Router1 needs more LAN interfaces to accommodate the VLANs that are shown in the exhibit.F. The FastEthernet 0/0 interface on Router1 and Switch2 trunk ports must be configured using thesameencapsulation type.Answer: DF4. Refer to the exhibit. Which two statements are true about the loopback address that isconfigured onRouterB? (Choose two.)A. It ensures that data will be forwarded by RouterB.B. It provides stability for the OSPF process on RouterB.中国思科华为3COM 网络技术发布C. It specifies that the router ID for RouterB should be 10.0.0.1.D. It decreases the metric for routes that are advertised from RouterB.E. It indicates that RouterB should be elected the DR for the LAN.Answer: BC5. A network administrator is explaining VTP configuration to a new technician. What should thenetworkadministrator tell the new technician about VTP configuration? (Choose three.)A. A switch in the VTP client mode cannot update its local VLAN database.B. A trunk link must be configured between the switches to forward VTP updates.C. A switch in the VTP server mode can update a switch in the VTP transparent mode.D. A switch in the VTP transparent mode will forward updates that it receives to other switches.E. A switch in the VTP server mode only updates switches in the VTP client mode that have a higherVTPrevision number.F. A switch in the VTP server mode will update switches in the VTP client mode regardless of the configured VTP domain membership.Answer: ABD6. Which two locations can be configured as a source for the IOS image in the boot system command?(Choose two.)A. RAMB. NVRAMC. flash memoryD. HTTP serverE. TFTP serverF. TelnetserverAnswer: CE7. What are two reasons a network administrator would use CDP? (Choose two.)A. to verify the type of cable interconnecting two devicesB. to determine the status of network services on a remote deviceC. to obtain VLAN information from directly connected switchesD. to verify Layer 2 connectivity between two devices when Layer 3 failsE. to obtain the IP address of a connected device in order to telnet to the deviceF. to determine the status of the routing protocols between directly connected routersAnswer: DE中国思科华为3COM 网络技术发布8. Refer to the exhibit. Both switches are using a default configuration. Which two destinationaddresses willhost 4 use to send data to host 1? (Choose two.)A. the IP address of host 1B. the IP address of host 4C. the MAC address of host 1D. the MAC address of host 4E. the MAC address of the Fa0/0 interface of the R1 routerF. the MAC address of the Fa0/1 interface of the R1 routerAnswer: AF9. Refer to the exhibit. The router has been configured with these commands:hostname Gatewayinterface FastEthernet 0/0ip address 198.133.219.14 255.255.255.248no shutdowninterface FastEthernet 0/1ip address 192.168.10.254 255.255.255.0no shutdowninterface Serial 0/0ip address 64.100.0.2 255.255.255.252no shutdownip route 0.0.0.0 0.0.0.0 64.100.0.1What are the two results of this configuration? (Choose two.)中国思科华为3COM 网络技术发布A. The default route should have a next hop address of 64.100.0.3.B. Hosts on the LAN that is connected to FastEthernet 0/1 are using public IP addressing.C. The address of the subnet segment with the WWW server will support seven more servers.D. The addressing scheme allows users on the Internet to access the WWW server.E. Hosts on the LAN that is connected to FastEthernet 0/1 will not be able to access the Internetwithoutaddress translation.Answer: DE10. A company is installing IP phones. The phones and office computers connect to the same device.Toensure maximum throughput for the phone data, the company needs to make sure that the phonetraffic ison a different network from that of the office computer data traffic. What is the best networkdevice to whichto directly connect the phones and computers, and what technology should be implemented on thisdevice?(Choose two.)A. hubB. routerC. switchD. STPE. subinterfacesF. VLANAnswer: CF11. What are two benefits of using VTP in a switching environment? (Choose two.)中国思科华为3COM 网络技术发布A. It allows switches to read frame tags.B. It allows ports to be assigned to VLANs automatically.C. It maintains VLAN consistency across a switched network.D. It allows frames from multiple VLANs to use a single interface.E. It allows VLAN information to be automatically propagated throughout the switching environment.Answer: CE12. Which two statements are true about the command ip route172.16.3.0 255.255.255.0 192.168.2.4?(Choose two.)A. It establishes a static route to the 172.16.3.0 network.B. It establishes a static route to the 192.168.2.0 network.C. It configures the router to send any traffic for an unknown destination to the 172.16.3.0network.D. It configures the router to send any traffic for an unknown destination out the interface withthe address192.168.2.4.E. It uses the default administrative distance.F. It is a route that would be used last if other routes to the same destination exist.Answer: AE13. What are two advantages of Layer 2 Ethernet switches over hubs? (Choose two.)A. decreasing the number of collision domainsB. filtering frames based on MAC addressesC. allowing simultaneous frame transmissionsD. increasing the size of broadcast domainsE. increasing the maximum length of UTP cabling between devicesAnswer: BC14. Refer to the exhibit. A network associate needs to configure the switches and router in thegraphic sothat the hosts in VLAN3 and VLAN4 can communicate with the enterprise server in VLAN2. Which twoEthernet segments would need to be configured as trunk links? (Choose two.)中国思科华为3COM 网络技术发布A. AB. BC. CD. DE. EF. FAnswer: CF15. Which two values are used by Spanning Tree Protocol to elect a root bridge? (Choose two.)A. amount of RAMB. bridge priorityC. IOS versionD. IP addressE. MAC addressF. speed of the linksAnswer: BE16. Refer to the exhibit. Assume that the routing protocol referenced in each choice below isconfigured withits default settings and the given routing protocol is running onall the routers. Which twoconditionalstatements accurately state the path that will be chosen between networks 10.1.0.0 and 10.3.2.0for therouting protocol mentioned? (Choose two.)中国思科华为3COM 网络技术发布A. If OSPF is the routing protocol, the path will be from R1 to R3to R4 to R5.B. If OSPF is the routing protocol, the path will be from R1 to R2to R5.C. If OSPF is the routing protocol, the path will be from R1 to R5.D. If RIPv2 is the routing protocol, the path will be from R1 to R3to R4 to R5.E. If RIPv2 is the routing protocol, the path will be from R1 to R5.Answer: AE17. Refer to the exhibit. A network administrator is adding two new hosts to SwitchA. Which threevaluescould be used for the configuration of these hosts? (Choose three.)A. host A IP address: 192.168.1.79。
思科第一学期期末试题目及答案

1请参见图示。
主机 A 用户向主机 B 用户发送了一封电子邮件。
主机 A 发送了哪种类型的信息?广播组播同播单播2为了将PC 加入到网络环境中,应通过软件配置哪两个组件?(选择两项。
)MAC 地址IP 地址内核外壳(shell)子网掩码3哪两项是MAC 地址的特征?(选择两项。
)指示网络中主机的物理位置。
由DHCP 服务器动态分配。
以十六进制格式显示。
是物理地址。
是一种基于电缆的地址。
4哪种连接需要使用直通电缆?PC 端口至PC 端口PC 端口至路由器接口交换机端口至路由器端口交换机端口至交换机端口5路由器在收到包含广播MAC 地址的帧时会执行什么操作?它不会将该帧转发给另一个网络。
它会以其IP 地址作为回复将该帧转发回发送主机。
它会将帧从除该帧所在接口的其它所有接口转发出去。
它会将该帧转发回接收接口,以确保局域网中的所有主机都能收到。
6DNS 服务器的功能是什么?将IP 地址映射为MAC 地址。
将计算机或域名转换为相应的IP 地址。
管理客户端所在的域。
接收从客户端发来的HTTP 请求。
7哪两种网络故障与物理层相关?(选择两项。
)电缆和接头损坏编址不正确子网掩码不正确组件过热默认网关不正确8哪一层是主机进入网络的第一个进入点?核心层接入层网络层分布层9下列哪些是私有IP 地址的地址范围?(选择三项。
)10.0.0.0 到10.255.255.255200.100.50.0 到200.100.25.255150.150.0.0 到150.150.255.255172.16.0.0 到172.31.255.255192.168.0.0 到192.168.255.255127.16.0.0 到127.31.255.25510请参见图示。
一家组织的安全策略允许员工在家里连接办公室内部网。
这是一种什么安全策略?合理使用事件处理网络维护远程访问11请参见图示。
将Linksys 集成路由器上的安全模式设置为WEP 有什么作用?WEP 安全模式能够使接入点向客户端告知它的存在。
CCNA Exploration 1 Final Exam Answers

CCNA Exploration 1 Final Exam Answers1.Refer to the exhibit. What three statements are true about the IP configuration that is shown? (Choose three.)The address that is assigned to the computer represents private addressing.The computer is unable to communicate outside of the local network.The network of this computer can have 126 hosts.The prefix of the computer address is /27.The IP address that is assigned to the computer is routable on the Internet.The IP address that is assigned to the computer is a broadcast address.2. As network administrator, what is the subnet mask that allows 510 hosts given the IP address 172.30.0.0?255.255.0.0255.255.248.0255.255.252.0255.255.254.0255.255.255.0255.255.255.1283. Which OSI layers offers reliable, connection-oriented data communication services? applicationpresentationsessiontransportnetwork4. Which type of media is immune to EMI and RFI? (Choose two.)10 Base-T10 Base-210 Base-5100 Base-FX100 Base TX1000 Base LX5. When connectionless protocols are implemented at the lower layers of the OSI model, what is usually used to acknowledge that the data was received and to request the retransmission of missing data?IPUDPEtherneta connectionless acknowledgementan upper-layer, connection-oriented protocol or service6. Which combination of network id and subnet mask correctly identifies all IP addresses from 172.16.128.0 through 172.16.159.255?172.16.128.0 255.255.255.224172.16.128.0 255.255.0.0172.16.128.0 255.255.192.0172.16.128.0 255.255.224.0172.16.128.0 255.255.255.1927. During the encapsulation process, which identifiers are added at the transport layer?two networks routing the packetstwo applications communicating the datatwo hosts at either end of the communicationtwo nodes on the local network exchanging the frame8. What are three characteristics of CSMA/CD? (Choose three)Devices can be configured with a higher transmission priority.A jam signal indicates that the collision has cleared and the media is not busy.A device listens and waits until the media is not busy before transmitting.The device with the electronic token is the only one that can transmit after a collision.All of the devices on a segment see data that passes on the network medium.After detecting a collision, hosts can attempt to resume transmission after a random time delay has expired.9.Refer to the exhibit. Each media link is labeled. What type of cable should be used to connect the different devices?Connection 1 – rollover cableConnection 2 – straight-through cableConnection 3 – crossover cableConnection 1 – crossover cableConnection 2 – rollover cableConnection 3 – crossover cableConnection 1 – straight-through cableConnection 2 – crossover cableConnection 3 – crossover cableConnection 1 – straight-through cableConnection 2 – crossover cableConnection 3 – straight-through cableConnection 1 – crossover cableConnection 2 – straight-through cableConnection 3 – crossover cable10.Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host A. What is a valid configuration for Host A?IP address: 192.168.100.19; Subnet Mask: 255.255.255.248; Default Gateway: 192.16.1.2IP address: 192.168.100.20; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.17 IP address: 192.168.100.21; Subnet Mask: 255.255.255.248; Default Gateway: 192.168.100.18 IP address: 192.168.100.22; Subnet Mask: 255.255.255.240; Default Gateway: 10.1.1.5IP address: 192.168.100.30; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.1.1IP address: 192.168.100.31; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.18Refer to the exhibit. Host A is transmitting data to host B. What addresses will host A use to for the destination IP and MAC addresses in this communication?Destination MAC: BBBB:BBBB:BBBB Destination IP: 172.22.0.62Destination MAC: DDDD:DDDD:DDDD Destination IP: 172.22.0.75Destination MAC: EEEE:EEEE:EEEE Destination IP: 172.22.0.62Destination MAC: BBBB:BBBB:BBBB Destination IP: 172.22.0.75Destination MAC: EEEE:EEEE:EEEE Destination IP: 172.22.0.75Destination MAC: DDDD:DDDD:DDDD Destination IP: 172.22.0.9412.Refer to the exhibit. Assume all devices are using default configurations. How many subnets are required to address the topology that is shown?145713.Refer to the exhibit. Which two statements describe the information that is represented in the header? (Choose two)This is a server response.The UDP protocol is being used.The destination port indicates a Telnet session.The return segment will contain a source port of 23.The next session originated from the client of this session will use the source port number 13358.14.Refer to the exhibit. The command that is shown was issued on a PC. What does the IP address 192.168.33.2 represent?IP address of the hostdefault gateway of the hostIP address of the homepage for the hostprimary domain name server for the hostIP address of the website resolver1.mooki.local15.Refer to the exhibit. A router, whose table is shown, receives a packet that is destined for 192.168.1.4. How will router treat the packet?The packet will be dropped.The packet will be forwarded via FastEthernet 0/0.The packet will be forwarded to the destination host.The packet will be forwarded to the 192.168.1.3 next-hop address.16.Refer to the exhibit. A network administrator remotely accesses the CLI of RouterB from PC1 using Telnet. Which statement is true about this connection?The data is automatically encrypted.A Telnet server process is running on PC1.The connection is made through a VTY session on the router.A GET request was sent to RouterB to retrieve data during this session.17. Which three IPv4 addresses represent a broadcast for a subnet? (Choose three.)172.16.4.63 /26172.16.4.129 /26172.16.4.191 /26172.16.4.51 /27172.16.4.95 /27172.16.4.221 /2718.Refer to the exhibit. What is required on host A for a network technician to create the initial configuration on Router1?an FTP clienta Telnet clienta terminal emulation programa web browser19. Which three statements characterize the transport layer protocols? (Choose three.) TCP and UDP port numbers are used by application layer protocols.TCP uses port numbers to provide reliable transportation of IP packets.UDP uses windowing and acknowledgments for reliable transfer of data.TCP uses windowing and sequencing to provide reliable transfer of data.TCP is a connection-oriented protocol. UDP is a connectionless protocol.20. The Layer 4 header contains which type of information to aid in the delivery of data? service port numberhost logical addressdevice physical addressvirtual connection identifier21.Refer to the exhibit. The tracert command is initiated from PC1 to PC4. Which device will send a response to the initial tracert packet from PC1?AthensAnkaraLondonParisPC422.Refer to the exhibit. Host A attempts to establish a TCP/IP session with host C. During this attempt, a frame was captured with the source MAC address 0050.7320.D632 and the destination MAC address 0030.8517.44C4. The packet inside the captured frame has an IP source address 192.168.7.5, and the destination IP address is 192.168.219.24. At which point in the network was this packet captured?leaving host Aleaving ATLleaving Dallasleaving NYC23Refer to the exhibit. Which set of devices contains only intermediary devices?A, B, D, GA, B, E, FC, D, G, IG, H, I, J24Refer to the exhibit. What two facts can be determined from the information that is given? (Choose two.)This exchange is part of the three-way handshake.The source port indicates that a Telnet session has been initiated.The data is flowing from server to client.The destination port indicates that an HTTP session has been initiated.The data listed is associated with the transport layer.The source port does not support communication with the destination port that is listed.25. Due to a security violation, the router passwords must be changed. What information can be learned from the following configuration entries? (Choose two)Router(config)# line vty 0 3Router(config-line)# password c13c0Router(config-line)# loginThe entries specify three Telnet lines for remote access.The entries specify four Telnet lines for remote access.The entries set t he console and Telnet password to “c13c0″.Telnet access will be denied because the Telnet configuration is incomplete.Access will be permitted for Telnet using “c13c0″ as the password.26.Refer to the exhibit. Cable 1 and cable 2 have the ends wired for specific physical layer requirements. The table lists each segment by number and the cable which has been installed by the network technician between the network components on that segment. From the data given, which segments have the correct cable installed? (Choose three.)segment1segment2segment3segment4segment527. Which password is automatically encrypted when it is created?vtyauxconsoleenable secretenable password28.Refer to the exhibit. Which logical topology best describes the exhibited network?starringpoint-to-pointmultiaccessmesh29.Refer to the exhibit. The network containing router B is experiencing problems. A network associate has isolated the issue in this network to router B. What action can be preformed to correct the network issue?issue the clock rate command on interface Serial 0/0/0issue the description command on interface Serial 0/0/1issue the ip address command on interface FastEthernet 0/0issue the no shutdown command on interface FastEthernet 0/130. What are two characteristics of the data link layer? (Choose two.)It segments and reorders the data.It exchanges the frames between nodes.It defines the method by which network devices place data onto the media.It manages the transfer of data between the processes that run on each host.It retrieves signals from the media and restores them to their bit representations.31. Which of the following are the address ranges of the private IP addresses? (Choose three.) 10.0.0.0 to 10.255.255.255200.100.50.0 to 200.100.25.255150.150.0.0 to 150.150.255.255172.16.0.0 to 172.31.255.255192.168.0.0 to 192.168.255.255127.16.0.0 to 127.31.255.25532.Refer to the exhibit. The diagram represents the process of sending email between clients. Select the list below that correctly identifies the component or protocol used at each numbered stage of the diagram.1.MUA2.MDA3.MTA4.SMTP5.MTA6.POP7.MDA8.MUA1.MUA2.POP3.MDA4.SMTP5.MTA6.MDA7.SMTP8.MUA1.MUA2.POP3.SMTP4.MDA5.MTA6.SMTP7.POP8.MUA1.MDA2.SMTP3.MTA4.SMTP5.MTA6.MUA7.POP8.MDA1.MUA2.SMTP3.MTA4.SMTP5.MTA6.MDA7.POP8.MUA33.Refer to the exhibit. On the basis of the IP configuration that is shown, what is the reason that Host A and Host B are unable to communicate outside the local network?Host A was assigned a network address.Host B was assigned a multicast address.Host A and Host B belong to different networks.The gateway address was assigned a broadcast address.34.Refer to the exhibit. What is the correct destination socket number for a web page request from Host A to the web server?00-08-a3-b6-ce-46198.133.219.25:80C 198.133.219.0/24 is directly connected, FastEthernet0/035. A routing issue has occurred in you internetwork. Which of the following type of devices should be examined to isolate this error?access pointhosthubrouterswitch36. Which OSI layer does IP rely on to determine whether packets have been lost and to request retransmission?applicationpresentationsessiontransport37. Which range of port numbers are reserved for services that are commonly used by applications that run on servers?0 to 2550 to 10231024 to 4915149152 to 6553538.Examine the graphic with current configurations. Host A in the Clerical offices failed and was replaced. Although a ping to 127.0.0.1 was successful, the replacement computer can not access the company network. What is the likely cause of the problem?IP address incorrectly enterednetwork cables unpluggedsubnet mask incorrectly enterednetwork card failure39.Refer to the exhibit. When computer A sends a frame to computer D, what computers receive the frame?only computer Donly computer A and computer Donly computer B, computer C, and computer Dall computers40. In a Cisco IOS device, where is the startup-configuration file stored?FlashNVRAMRAMROM41.Refer to the exhibit. With the router running NAT, what IP addresses can be applied to the computer to allow access to the Internet? (Choose three)192.168.18.38192.168.18.48192.168.18.49192.168.18.52192.168.18.59192.168.18.6342. A technician is asked to secure the privileged EXEC mode of a switch by requiring a password. Which type of password would require this login and be considered the most secure?consoleenableenable secretVTY43. Which prompt represents the appropriate mode used for the copy running-configstartup-config command ?Switch-6J>Switch-6J#Switch-6J(config)#Switch-6J(config-if)#Switch-6J(config-line)#44.Refer to the exhibit. A technician is working on a network problem that requires verification of the router LAN interface. What address should be pinged from this host to confirm that the router interface is operational?127.0.0.1192.168.64.196192.168.254.1192.168.254.9192.168.254.25445. What is true regarding network layer addressing? (Choose three)uses a flat structureprevent broadcastsheirarchicaluniquely identifies each host48 bits in lengthcontains a network portion46.Refer to the exhibit. What function does router RT_A need to provide to allow Internet access for hosts in this network?address translationDHCP servicesftpdweb server47. A PC can not connect to any remote websites, ping its default gateway, or ping a printer that is functioning properly on the local network segment. Which action will verify that the TCP/IP stack is functioning correctly on this PC?Use the ipconfig /all co mmand at the host’s command prompt.Use the ping 127.0.0.1 command at the command prompt.Use the traceroute command at the command prompt to identify any failures on the path to the gateway.Use FTP to check for connectivity to remote sites.Download a troubleshooting tool from the PC manufacturer’s website.48.Refer to the exhibit. What two facts can be determined about the exhibited topology? (Choose two)A single broadcast domain is presentTwo logical address ranges are required.Three broadcast domains are shown.Four networks are needed.Five collision domains exist.49. Which two functions of the OSI model occur at layer two? (Choose two.)physical addressingencodingroutingcablingmedia access control50. When must a router serial interface be configured with the clock rate command?when the interface is functioning as a DTE devicewhen the interface timers have been clearedwhen the connected DTE device is shut downwhen the interface is functioning as a DCE device。
(完整版)ccna1章节与期末答案

第一章:正确答案:2.4.5•解析:由于不需要使用网络设备和专用服务器,对等网络易于创建,复杂性更低,且成本更少。
而且对等网络也没有集中管理。
这种网络安全性更低,不可扩展,而且那些同时充当客户端和服务器的设备可能性能更差正确答案:1解析:正确答案: 3.5解析:选择网络介质的条件包括:所选介质可以成功传送信号的距离、要安装所选介质的环境、必须传输的数据量和速度以及介质和安装的成本。
正确答案:3和4解析:终端设备上的应用程序可以生成数据,更改数据内容并且负责启动封装过程。
正确答案:1和4解析:终端设备会发出通过网络传输的数据。
中间设备会在链路发生故障时通过备用路径传输数据,并且会过滤数据传输以增强安全性。
网络介质提供网络消息的传输通道。
正确答案:4解析:外联网是公司外部的人或企业合作伙伴访问数据的网络区域。
内部网只描述通常仅供内部人员访问的网络区域。
当设备连接到有线网络时,有线LAN 会受BYOD(自带设备)影响。
使用大学无线LAN 的设备多为平板电脑和智能手机。
大学生主要使用无线WAN 来访问他们的手机运营商网络。
.正确答案:2解析:由于通过Internet 可以联系在线供应商,所以家庭用户通过Internet 进行网上购物。
内联网基本上是仅供内部使用的局域网。
外联网是外部合作伙伴访问组织内部特定资源的网络。
家庭用户并不一定使用LAN 来访问Internet。
例如,PC 可以通过调制解调器直接连接到ISP。
正确答案:1解析:内部网这个术语用于表示一个组织的私有局域网和广域网连接。
内部网的设计旨在仅允许该组织的成员、员工或其他获得授权的人员进行访问。
正确答案:2和4解析:电缆和DSL 均能实现高带宽、始终联网,并提供到主机计算机或LAN 的以太网连接。
10正确答案:2和3解析:移动电话连接需要使用移动电话网络。
卫星连接通常用于家庭或企业外部不便使用物理布线的位置。
11正确答案:2解析:当对网络资源的请求超出了可用容量时,网络就会变得拥堵。
CCNA第一学期Finalexam考试英文版答案

CCNA第一学期Finalexam考试英文版答案(R&S.)C 1A medium-sized business is researching available options for connecting to the Internet.Thecompany is looking for a high speed option with dedicated, symmetric access.Whichconnection type should the company choose?DSLdialupsatelliteleased linecable modem2What is the purpose of having a converged network?to provide high speed connectivity to all end devicesto make sure that all types of data packets will be treated equallyto achieve fault tolerance and high availability of data network infrastructure devicesto reduce the cost of deploying and maintaining thecommunication infrastructure3What characteristic of a network enables it to quickly grow to support new users andapplications without impacting the performance of the service being delivered to existing users?reliabilityscalabilityquality of serviceaccessibility4Which connection provides a secure CLI session with encryption to a Cisco switch?a console connectionan AUX connectiona Telnet connectionan SSH connection5A network technician is attempting to configure an interface by entering the followingcommand:SanJose(config)#ip address192.168.2.1255.255.255.0.The command isrejected by the device.What is the reason for this? The command is being entered from the wrong mode of operation.The command syntax is wrong.The subnet mask information is incorrect.The interface is shutdown and must be enabled before the switch will accept the IP address.6After several configuration changes are made to a router, the copy running-configurationstartup-configuration command is issued.Where will the changes be stored?flashROMNVRAMRAMthe configuration registera TFTP server7Refer to the exhibit.From global configuration mode,an administrator is attempting to create a message-of-the-day banner by using thecommand banner motd V Authorized access only!Violators will be prosecuted!V When users log in using Telnet,the banner does not appear correctly.What is the problem? The banner message is too long.The delimiting character appears in the banner message.The symbol“!”signals the end of a banner message.Message-of-the-day banners will only appear when a user logs in through the console port.8What are three characteristics of an SVI?(Choose three.) It is designed as a security protocol to protect switch ports.It is not associated with any physical interface on a switch.It is a special interface that allows connectivity by different types of media.It is required to allow connectivity by any device at any location.It provides a means to remotely manage a switch.It is associated with VLAN1by default.9A technician configures a switch with these commands: SwitchA(config)#interface vlan1SwitchA(config-if)#ip address192.168.1.1255.255.255.0 SwitchA(config-if)#no shutdownWhat is the technician configuring?Telnet accessSVIpassword encryptionphysical switchport access10In computer communication,what is the purpose of message encoding?to convert information to the appropriate form for transmissionto interpret informationto break large messages into smaller framesto negotiate correct timing for successful communication11What protocol is responsible for controlling the size of segments and the rate at whichsegments are exchanged between a web client and a web server?TCPIPHTTPEthernet12What are two benefits of using a layered network model? (Choose two.)It assists in protocol design.It speeds up packet delivery.It prevents designers from creating their own model.It prevents technology in one layer from affecting other layers.It ensures a device at one layer can function at the next higher layer.13What is the process of dividing a data stream into smaller pieces before transmission?segmentationencapsulationencodingflow control14When IPv4addressing is manually configured on a web server,which property of the IPv4configuration identifies the network and host portion for an IPv4address?DNS server addresssubnet maskdefault gatewayDHCP server address15A network administrator is troubleshootingconnectivity issues on a ing a tester,the administrator notices that the signals generated by the server NIC are distorted and not usable.In which layer of the OSI model is the error categorized?presentation layernetwork layerphysical layerdata link layer16A network engineer is measuring the transfer of bits across the company backbone for amission critical database application.The engineer notices that the network throughputappears lower than the bandwidth expected.Which three factors could influence thedifferences in throughput?(Choose three.)the amount of traffic that is currently crossing the networkthe sophistication of the encapsulation method applied to the datathe type of traffic that is crossing the networkthe latency that is created by the number of network devices that the data is crossingthe bandwidth of the WAN connection to the Internetthe reliability of the gigabit Ethernet infrastructure of the backbone17Which type of UTP cable is used to connect a PC to a switch port?consolerollovercrossoverstraight-through18What is a characteristic of the LLC sublayer?It provides the logical addressing required that identifies the device.It provides delimitation of data according to the physical signaling requirements of the medium.It places information in the frame allowing multiple Layer 3protocols to use the same network interface and media.It defines software processes that provide services to the physical layer.19What are the three primary functions provided by Layer 2data encapsulation?(Choosethree.)error correction through a collision detection methodsession control using port numbersdata link layer addressingplacement and removal of frames from the mediadetection of errors through CRC calculationsdelimiting groups of bits into framesconversion of bits into data signals20What will a host on an Ethernet network do if it receives a frame with a destination MACaddress that does not match its own MAC address?It will discard the frame.It will forward the frame to the next host.It will remove the frame from the media.It will strip off the data-link frame to check the destination IP address.21What are two actions performed by a Cisco switch? (Choose two.)building a routing table that is based on the first IP address in the frame headerusing the source MAC addresses of frames to build and maintain a MAC address tableforwarding frames with unknown destination IP addresses to the default gatewayutilizing the MAC address table to forward frames via the destination MAC addressexamining the destination MAC address to add new entries to the MAC address table22What are two examples of the cut-through switching method?(Choose two.)store-and-forward switchingfast-forward switchingCRC switchingfragment-free switchingQOS switching23Refer to the exhibit.If host A sends an IP packet to host B,what will the destination address be in the frame when it leaves host A?DD:DD:DD:DD:DD:DD172.168.10.99CC:CC:CC:CC:CC:CC172.168.10.65BB:BB:BB:BB:BB:BBAA:AA:AA:AA:AA:AA24What are two services provided by the OSI network layer?(Choose two.)performing error detectionrouting packets toward the destinationencapsulating PDUs from the transport layerplacement of frames on the mediacollision detection25What information is added during encapsulation at OSI Layer3?source and destination MACsource and destination application protocolsource and destination port numbersource and destination IP address26What are two functions of NVRAM?(Choose two.)to store the routing tableto retain contents when power is removedto store the startup configuration fileto contain the running configuration fileto store the ARP table27Refer to the exhibit.The network administrator for a small advertising company has chosen to use the192.168.5.96/27 network for internal LAN addressing.As shown in the exhibit,a static IP address is assigned to the company web server.However,the web server cannot access the Internet.The administrator verifies that local workstations with IP addresses that are assigned by a DHCP server can access the Internet,and the web server is able to ping local workstations.Which component is incorrectly configured?subnet maskDNS addresshost IP addressdefault gateway address28Why does a Layer3device perform the ANDing process on a destination IP address andsubnet mask?to identify the broadcast address of the destination networkto identify the host address of the destination hostto identify faulty framesto identify the network address of the destination network29What are the three ranges of IP addresses that are reserved for internal private use?(Choosethree.)10.0.0.0/864.100.0.0/14127.16.0.0/12172.16.0.0/12192.31.7.0/24192.168.0.0/1630Which three addresses are valid public addresses? (Choose three.)198.133.219.17192.168.1.24510.15.250.5128.107.12.117192.15.301.24064.104.78.22731What type of IPv6address is FE80::1?loopbacklink-localmulticastglobal unicast32Refer to the exhibit.On the basis of the output,which two statements about network connectivity are correct? (Choose two.)There is connectivity between this device and the device at192.168.100.1.The connectivity between these two hosts allows for videoconferencing calls.There are4hops between this device and the device at 192.168.100.1.The average transmission time between the two hosts is2 milliseconds.This host does not have a default gateway configured.33Which subnet would include the address192.168.1.96as a usable host address?192.168.1.64/26192.168.1.32/27192.168.1.32/28192.168.1.64/2934How many hosts are addressable on a network that has a mask of255.255.255.248?268141625435Which statement is true about variable-length subnet masking?Each subnet is the same size.The size of each subnet may be different,depending on requirements.Subnets may only be subnetted one additional time.Bits are returned,rather than borrowed,to create additional subnets.36Refer to the exhibit.Consider the IP address of 192.168.10.0/24that has been assigned to a high school building.The largest network in this building has100 devices.If192.168.10.0is the network number for the largest network,what would be the network number for thenext largest network,which has40devices?192.168.10.0192.168.10.128192.168.10.192192.168.10.224192.168.10.24037In what two situations would UDP be the preferred transport protocol over TCP?(Choosetwo.)when applications need to guarantee that a packet arrives intact,in sequence,and unduplicatedwhen a faster delivery mechanism is neededwhen delivery overhead is not an issuewhen applications do not need to guarantee delivery of the datawhen destination port numbers are dynamic38What important information is added to the TCP/IPtransport layer header to ensurecommunication and connectivity with a remote network device?timing and synchronizationdestination and source port numbersdestination and source physical addressesdestination and source logical network addresses39What is the TCP mechanism used in congestion avoidance? three-way handshakesocket pairtwo-way handshakesliding window40Which three statements characterize UDP?(Choose three.)UDP provides basic connectionless transport layer functions.UDP provides connection-oriented,fast transport of data at Layer 3.UDP relies on application layer protocols for error detection.UDP is a low overhead protocol that does not provide sequencing or flow control mechanisms.UDP relies on IP for error detection and recovery.UDP provides sophisticated flow control mechanisms.41Which two tasks are functions of the presentation layer? (Choose two.)compressionaddressingencryptionsession controlauthentication42Which two protocols operate at the highest layer of the TCP/IP protocol stack?(Choose two.)DNSEthernetIPPOPTCPUDP43Which two roles can a computer assume in a peer-to-peer network where a file is beingshared between two computers?(Choose two.)clientmasterserverslavetransient44What is the function of the HTTP GET message?to request an HTML page from a web serverto send error information from a web server to a web clientto upload content to a web server from a web clientto retrieve client email from an email server using TCP port11045A wireless host needs to request an IP address.What protocol would be used to process therequest?FTPHTTPDHCPICMPSNMP46When planning for network growth,where in the network should packet captures take place toassess network traffic?on as many different network segments as possibleonly at the edge of the networkbetween hosts and the default gatewayonly on the busiest network segment47When applied to a router,which command would help mitigate brute-force password attacksagainst the router?exec-timeout30service password-encryptionbanner motd$Max failed logins=5$login block-for60attempts5within6048Refer to the exhibit.An administrator is testing connectivity to a remote device with the IP address10.1.1.1.What does the output of this command indicate?Connectivity to the remote device was successful.A router along the path did not have a route to the destination.A ping packet is being blocked by a security device along the path.The connection timed out while waiting for a reply fromthe remote device.。
Final Exam (part I) (英语试卷的参考答案)
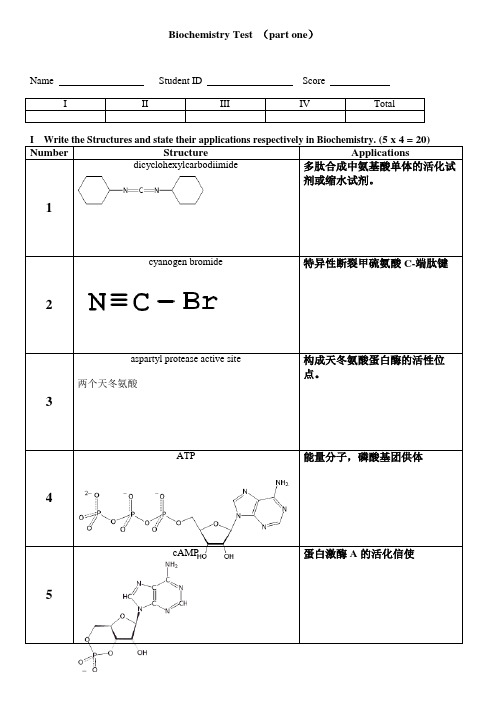
Biochemistry Test (part one)Name Student ID ScoreI I Matching Questions (30 x 1 = 30)1.Some inverted repeat sequences or palindromic sequences can be specifically cleaved by ____11A_________.2.The process by which very different evolutionary pathways lead to a protein with similar function is referred to as__2B___ evolution.3.Under normal conditions, the iron of heme in myoglobin and hemoglobin is in the ___16D____ oxidation state.4.Carbon dioxide reacts with the amino terminal groups of hemoglobin to form carbamate groups, which carry a___10D___ charge.5.In normal adult hemoglobin, HbA, the β6 position is a glutamate residue, whereas in sickle-cell hemoglobin, HbS, itis a __7E___ residue.6.The T-state of hemoglobin is stabilized by a salt bridge between β1 Asp 94 and the C-terminal ____7B____ of the β1chain.7.In trypsin, the specificity pocket contains a/an ____7D____ residue that binds to amino acid residue carryingpositive charge of the substrate.8.In proteases such as papain, a _____7A___ residue is activated by hydrogen-bonding to a histidine residue.9.Multiple forms of homologous enzymes within the same organism that catalyze the same reaction but with differentkinetic properties are ____14A____.10.The effects of substrates on allosteric enzymes are referred to as _____9D_____ effects.11.___9A___ is the most common donor molecule in phosphorylation reactions catalyzed by protein kinases.12.α helices, β sheets, and turns are referred as__10B___ structure of proteins.13.The purification based on the attraction of the protein for a particular chemical group is ___3C__ chromatography.14.The information-carrying intermediates for translation are _17C_.15.The person who noted the A:T and G:C ratios in DNA are approximately 1:1 is _13C_.16.Codons that specify the same amino acids are termed __4A__.17. A pattern of DNA fragments by restriction digestions can serve as a _12E of a particular DNA molecule.18.Glutamine substitution with __6E__ is an example of a conservative amino acid change.19.The decreased production of one of the subunits of hemoglobin can cause _2D__.20.Two α chains and two γ chains are used to constitute ___11E___ hemoglobin.21.The k cat is often referred to as the _6A__.22.Enzymes that do not obey Michaelis-Menten kinetics are _14C__.23.The activity of carbonic anhydrase requires metal ion __15D__.24.We can use __18A___ to determine structure/function relationships in enzymes.25.We usually refer the inhibition of the first step by the final product of the pathway as__5D__inhibition.26.Activation of prothrombin requires modified amino acid __8A__ in gla domain.27.The enzyme used to create DNA from RNA is 16A .28.Removal of phosphates from proteins is catalyzed by protein __1E__.29.Ω, β turns and loops are often found on 4E of proteins.30.Blood clotting cascades are controlled by __1A_.III Fill in the Blanks (2 x 10 = 20)1. The aromatic amino acids in proteins are Phe, Tyr, and Trp .2. During protein purification, both 测定比活性和回收率 are necessary each step.3. Monoclonal antibodies are made by 生产抗体的B 细胞与小鼠骨髓瘤细胞融合 .4. Semi-conservative replication of DNA was confirmed by M. Meselson and F. W. Stahlexperiment(s). 5.Distal histidine in hemoglobin donates hydrogen bond to oxyhemoglobin complex, which inhibits the oxidation of the iron to the ferric state. 6.α-hemoglobin is stabilized by AHSP . 7.The meaning of Vmax catalyzed by an enzyme is 所有活性位点都与底物结合时的反应初速度 . 8.An affinity label of an enzyme is 有反应活性基团的底物类似物 . 9.The central amino acid residue of the catalytic triad in chymotrypsin is His . 10. For medical diagnosis, LDH 同工酶 can be used as heart attack indicators.IV Short-Answer Questions (5 x 6 = 30)1. Oxygen-binding curves by hemoglobin are shown in Fig 1, which indicates that O 2 affinity of the protein isregulated by O 2, pH, CO 2, and 2,3-bisphosphate glycerol. Propose the molecular mechanisms to interpret theoxygen-binding curves with the knowledge you have learnt in class.2. Briefly describe immunoassay in Biochemistry.3. A 10 kb DNA fragment digested with different restriction endonuclease(s) shown in Fig 2. Please draw a possiblerestriction map for the original fragment.4. Describe structural alternation when the peptide bond between amino acid residues 15 and 16 is cleaved.5. How to create high density arrays of oligonucleotides in Affymatrix Co? What can be done if we use such arrays?Fig 1. Oxygen-binding curves of hemoglobin.Fig 2. Analysis of a DNA fragment by restriction enzymes.III Fill in the Blanks1.2.3.4.5.6.7.8.9.10.IV Short-answer questions1 氧气与血红蛋白结合是正协同,呈S型曲线;CO2是血红蛋白的负调节剂,有助于血红蛋白T态结构;使S型曲线右移;2,3-BPG能够与T态血红蛋白结合,稳定T-态结构;CO2和2,3-BPG 同时存在,负别构调节作用更强,S曲线进一步右移。
思科CCNA50Final答案

思科CCNA50Final答案1PDU 封装的正确顺序是什么?答案说明最高分值correctness ofresponse2 points for Option 1 0 points for any other option22管理员在发出 ping 命令之后在交换机上使用 Ctrl-Sh 组合。
使用这些按键有什么用途?重新启动ping 进程 中断 ping 进程退出到不同的配置模式允许用户完成命令要中断一个 IOS 进程(例如 ping 或 traceroute ),用户可以输入 Ctrl-Shift-6 键组合。
Tab 用于完成命令参数或变量的其余部分。
要退出配置模式并进入特权模式,可以使用 Ctrl-Z 按键。
CTRL-R 将会重新显示当前键入的行,这样便于用户按 Enter 并重新发出 ping 命令。
答案说明最高分值correctness ofresponse2 points for Option 20 points for any other option23建立融合网络有何用途?为所有终端设备提供高速连接确保平等对待所有类型的数据包实现数据网络基础架构设备的容错能力和高可用性降低部署和维护通信基础设施的成本随着技术的发展,各个公司现在可以将不同的网络整合到一个平台之上,称为融合网络。
在融合网络中,语音、视频和数据通过同一网络传输,从而使人们不必再创建和维护各个单独的网络。
这也降低了提供和维护通信网络基础设施相关的成本。
答案说明最高分值correctness ofresponse2 points for Option 4 0 points for any other option24请参见图示。
哪个区域最有可能是图中所示的公司网络网?区域 A区域 B区域 C区域 D外联网是外部实体访问其他公司的数据的平台。
其形式可能是产品供应商所使用的库存服务器,也可能是外部实体用来访问当天客户数量的当前信息的 Web 服务器。
思科CCNA1第七章试题及答案英文版

25. QuestionWhat is the binary equivalent of the decimal number 232?o 11101000o 11000110o 10011000o 1111001026. QuestionWhat is the decimal equivalent of the binary number 10010101?o149o 157o 168o 1921. QuestionHow many bits are in an IPv4 address?o32o 64o 128o 2562. QuestionWhich two parts are components of an IPv4 address? (Choose two.)o subnet portiono network portiono logical portiono host portiono physical portiono broadcast portion3. QuestionWhat does the IP address 172.17.4.250/24 represent?o network addresso multicast addresso host addresso broadcast address4. QuestionWhat is the purpose of the subnet mask in conjunction with an IP address?o to uniquely identify a host on a networko to identify whether the address is public or privateo to determine the subnet to which the host belongso to mask the IP address to outsiders5. QuestionWhat subnet mask is represented by the slash notation /20?o 255.255.255.248o 255.255.224.0o 255.255.240.0o 255.255.255.0o 255.255.255.1926. QuestionA message is sent to all hosts on a remote network. Which type of message isit?o limited broadcasto multicasto directed broadcasto unicast7. QuestionWhat are three characteristics of multicast transmission? (Choose three.)o The source address of a multicast transmission is in the range of 224.0.0.0 to 224.0.0.255.o A single packet can be sent to a group of hosts.o Multicast transmission can be used by routers to exchange routing information.o The range of 224.0.0.0 to 224.0.0.255 is reserved to reach multicast groups on a local network.o Computers use multicast transmission to request IPv4 addresses.o Multicast messages map lower layer addresses to upper layer addresses.8. QuestionWhich three IP addresses are private ? (Choose three.)o 10.1.1.1o 172.32.5.2o 192.167.10.10o 172.16.4.4o 192.168.5.5o 224.6.6.69. QuestionWhich two IPv4 to IPv6 transition techniques manage the interconnection of IPv6 domains? (Choose two.)o trunkingo dual stacko encapsulationo tunnelingo multiplexing10. QuestionWhich of these addresses is the shortest abbreviation for the IP address:3FFE:1044:0000:0000:00AB:0000:0000:0057?o 3FFE:1044::AB::57o 3FFE:1044::00AB::0057o 3FFE:1044:0:0:AB::57o 3FFE:1044:0:0:00AB::0057o 3FFE:1044:0000:0000:00AB::57o 3FFE:1044:0000:0000:00AB::005711. QuestionWhat type of address is automatically assigned to an interface when IPv6 is enabled on that interface?o global unicasto link-localo loopbacko unique local12. QuestionWhat are two types of IPv6 unicast addresses? (Choose two.)o multicasto loopbacko link-localo anycasto broadcast13. QuestionWhat are three parts of an IPv6 global unicast address? (Choose three.)o an interface ID that is used to identify the local network for a particular hosto a global routing prefix that is used to identify the network portion of the address that has been provided by an ISPo a subnet ID that is used to identify networks inside of the local enterprise siteo a global routing prefix that is used to identify the portion of the network address provided by a local administratoro an interface ID that is used to identify the local host on the network14. QuestionAn administrator wants to configure hosts to automatically assign IPv6 addresses to themselves by the use of Router Advertisement messages, but also to obtain the DNS server address from a DHCPv6 server. Which address assignment method should be configured?o SLAACo stateless DHCPv6o stateful DHCPv6o RA and EUI-6415. QuestionWhich protocol supports Stateless Address Autoconfiguration (SLAAC) for dynamic assignment of IPv6 addresses to a host?o ARPv6o DHCPv6o ICMPv6o UDP16. QuestionWhich two things can be determined by using the ping command? (Choose two.)o the number of routers between the source and destination deviceo the IP address of the router nearest the destination deviceo the average time it takes a packet to reach the destination and for theresponse to return to the sourceo the destination device is reachable through the networko the average time it takes each router in the path between source and destination to respond17. QuestionWhat is the purpose of ICMP messages?o to inform routers about network topology changeso to ensure the delivery of an IP packeto to provide feedback of IP packet transmissionso to monitor the process of a domain name to IP address resolution 18. QuestionWhat is indicated by a successful ping to the ::1 IPv6 address?o The host is cabled properly.o The default gateway address is correctly configured.o All hosts on the local link are available.o The link-local address is correctly configured.o IP is properly installed on the host.19. QuestionA user is executing a tracert to a remote device. At what point would a router,which is in the path to the destination device, stop forwarding the packet?o when the router receives an ICMP Time Exceeded messageo when the RTT value reaches zeroo when the host responds with an ICMP Echo Reply messageo when the value in the TTL field reaches zeroo when the values of both the Echo Request and Echo Reply messages reach zero20. QuestionWhat field content is used by ICMPv6 to determine that a packet has expired?o TTL fieldo CRC fieldo Hop Limit fieldo Time Exceeded field21. QuestionFill in the blank.The decimal equivalent of the binary number 10010101is 149 .22. QuestionFill in the blank.The binary equivalent of the decimal number 232 is 1110100023. QuestionFill in the blank.What is the decimal equivalent of the hex number 0x3F? 63。
CCNA考试题库中英文翻译版及标准答案

CCNA考试题库中英文翻译版及答案————————————————————————————————作者:————————————————————————————————日期:CCNA考试题库中英文翻译版及答案1[1]1. What are two reasons that a network administrator would use access lists? (Choose two.)1.出于哪两种理由,网络管理员会使用访问列表?A. to control vty access into a routerA.控制通过VTY访问路由器B. to control broadcast traffic through a routerB.控制广播流量穿越路由器2.一个默认的帧中继WAN被分类为哪种物理网络类型?A. point-to-pointA.点到点B. broadcast multi-accessB.广播多路访问C. nonbroadcast multi-accessC.非广播多路访问D. nonbroadcast multipointD.非广播多点E. broadcast point-to-multipointE.广播点到多点Answer: C3. A single 802.11g access point has been configured and installed in the center of a squarA few wireless users are experiencing slow performance and drops while most users are oat peak efficiency. What are three likely causes of this problem? (Choose three.)3.一个802.11接入点被部署在一个方形办公室的中央,当大多数用户在大流量传输数一些无线用户发现无线网络变得缓慢和出现丢包A. mismatched TKIP encryptionB. null SSIDC. cordless phonesD. mismatched SSIDE. metal file cabinetsF. antenna type or directionAnswer: CEF4. Refer to the exhibit. How many broadcast domains exist in the exhibited topology?根据下图,图中的拓扑中存在多少个广播域?A. one A.1B. two B.2C. three C.3D. four D.4E. five E.5F. six F.6Answer: C5. Refer to the exhibit. What two facts can be determined from the WLAN diagram? (Choose two.)5.根据下图,WLAN diagram决定了哪两个事实A. The area of overlap of the two cells represents a basic service set (BSS).A. 两个 cells的overlap的区域描述了一个basic service setB. The network diagram represents an extended service set (ESS).B. 网络描述了一个extended service setC. Access points in each cell must be configured to use channel 1.C. 再每个CELL中的AP必须被配置成使用channel 1D. The area of overlap must be less than 10% of the area to ensure connectivity.D. 为了确保连通性,重叠区域必须小于10%E. The two APs should be configured to operate on different channels.E. 两个访问点应该被配置成工作在不同的频道Answer: BE6. The command frame-relay map ip 10.121.16.8 102 broadcast was entered on the router.Which of the following statements is true concerning this command?6.路由器上输入命令frame-relay map ip 10.121.16.8 102 broadcast,以下选项正确的是?A. This command should be executed from the global configuration mode.A.该命令应该在全局配置模式下被执行B. The IP address 10.121.16.8 is the local router port used to forward data.B.IP地址10.121.16.8是本地路由器用来转发数据的接口C. 102 is the remote DLCI that will receive the information.C.102是远端的DLCI它将接受信息。
CCNA 1 Final Exam Answer v5

It aborts the current command and returns to configuration mode. It exits configuration mode and returns to user EXEC mode. It moves the cursor to the beginning of the next line. It completes the remainder of a partially typed word in a command.
2. A host is accessing a Web server on a remote network. Which three functions are performed by intermediary network devices during this conversation? (Choose three.)
CCNA 1 Final Exam Answer 003 (v5.02, 2015)
My Switch(config)#? Switch(config)#? MySwitch(config)#? My(config)#? Switch#
11. Refer to the exhibit. A network administrator is configuring access control to switch SW1. If the administrator uses Telnet to connect to the switch, which password is needed to access user EXEC mode?
CCNA_3_Final_Exam_V4.0_Answers
CCNA3 Answers – CCNA Exam – CCNA Exams1. Which security protocol or measure would provide the greatest protection for a wireless LAN?WPA2cloaking SSIDsshared WEP keyMAC address filtering2.Refer to the exhibit. All trunk links are operational and all VLANs are allowed on all trunk links. An ARP request is sent by computer 5. Which device or devices will receive this message?only computer 4computer 3 and RTR-Acomputer 4 and RTR-Acomputer 1, computer 2, computer 4, and RTR-Acomputer 1, computer 2, computer 3, computer 4, and RTR-Aall of the computers and the router3.Refer to the exhibit. Hosts A and B, connected to hub HB1, attempt to transmit a frame at the same time but a collision occurs. Which hosts will receive the collision jamming signal?only hosts A and Bonly hosts A, B, and Conly hosts A, B, C, and Donly hosts A, B, C, and E4.Refer to the exhibit. Router RA receives a packet with a source address of 192.168.1.65 and a destination address of 192.168.1.161. What will the router do with this packet?The router will drop the packet.The router will forward the packet out interface FastEthernet 0/1.1.The router will forward the packet out interface FastEthernet 0/1.2.The router will forward the packet out interface FastEthernet 0/1.3.The router will forward the packet out interface FastEthernet 0/1.2 and interface FastEthernet 0/1.3.5.Refer to the exhibit. Which two settings show the default value of VTP configuration on a Cisco 2960 switch? (Choose two.)revision numberexisting VLANsoperating modedomain namepruning mode6. Which value determines if a switch becomes the central point of reference in the spanning tree topology?lowest bridge IDhighest revision numberlowest numeric IP addresshighest numeric MAC address7. What is the purpose of the Spanning Tree algorithm?It propagates VLAN configurations to other switches.It restricts broadcast packets to a single VLAN.It segments a network into multiple broadcast domains.It prevents loops in a switched network with redundant paths.8. What are two benefits of the IEEE 802.11n standard over the IEEE 802.11G? (Choose two.)requires less equipmentprovides improved rangepermits increased data rateshas a single-input and a single-outputneeds no hardware upgrade for compatibility9.Which configuration changes will increment the configuration revision number on the VTP server?configuring trunk links on the VTP serverconfiguring or changing the VTP passwordconfiguring or changing the VTP domain nameconfiguring or changing the VTP version numberconfiguring or deleting a VLAN or creating a VLAN name10.Refer to the exhibit. A company has acquired a new office in a campus environment. Switches in the existing office and the new office are directly connected by a trunk link. The VLANs and IP addressing are setup as shown in the exhibit. The computers in each office are not able to ping each other. What will fix the problem?Use an access link between S2 and S3.Connect S2 and S3 to a common router.Set the subnet mask in the new office to /24.Configure the new office default gateway to 172.17.10.1Change the port assignments in the new office to a different VLAN.11. What is a possible impact of setting too short an aging time in the MAC address table of a switch?overly large address tableunnecessary flooding of packetsexcessive timeouts of static addressesimpaired ability to dynamically learn new addresses12.Refer to the exhibit. The network administrator has just added VLAN 50 to Switch1 and Switch2. Hosts A, B, C, and D are correctly configured with IP addresses in the subnet range for VLAN 50. Host A can communicate with host B, but cannot communicate with host C or host D. What is the cause of this problem?There is a native VLAN mismatch.The Fa0/11 interface of Switch1 is not configured as a trunk.The link between Switch1 and Switch2 is up but not trunked.VLAN 50 is not allowed on the trunk link between Switch1 and Switch2.Refer to the exhibit. Users complain that they do not have connectivity to the web server that is connected to SW1. What should be done to remedy the problem?Allow all VLANs on the trunk link.Configure VLAN 100 as the native VLAN for SW1.Configure the trunk port in trunk mode on SW1.Attach the web server to a router and configure inter-VLAN routing.14. What VLANs are allowed across a trunk when the range of allowed VLANs is set to the default value?only the management VLANall VLANs except the extended range VLANsall VLANs except 1 and 1002-1005all VLANs15.Refer to the exhibit. A new host needs to be connected to VLAN 1. Which IP address should be assigned to this new host?192.168.1.11 /28192.168.1.22 /28192.168.1.33 /28192.168.1.44 /28192.168.1.55 /2816. Using the command copy tftp:backup.cfg startup-config, an administrator downloaded a saved configuration from a TFTP server to a switch. Why does the administrator not detect any changes in the switch configuration after the download completes?The command should have been copy startup-config tftp:backup.cfg.A backup configuration from a TFTP server cannot be copied directly into the startup-config.The command copy running-config startup-config should be used to save the changes on the switch.Downloading to the startup-config requires the switch to be reloaded in order for the configuration to take effect.17. What two methods can be used to remove MAC address table entries froma switch? (Choose two.)Power cycle the switch to clear all dynamically learned addresses.The clear switching-tables command will remove statically configured entries.The clear mac-address-table command will remove statically and dynamically configured table entries.The erase flash command will clear all statically configured table entries.Statically configured MAC addresses will automatically be removed from the address table 300 minutes after the last activity on a switch port.18. Which type of traffic can still be received on a switch interface that is in STP blocking mode?BPDU framesmulticast framesbroadcast framesLayer 3 packets19. Which method establishes an administrative connection for configuring the Linksys WRT300N wireless access point?Associate with the access point and then open a HyperTerminal session with the access point.Physically connect to the access point and then reboot the computer to launch the configuration software.From a computer in the same IP subnet as the access point, enter the default IP address of the access point in a web browser.Modify the TCP/IP properties of the computer connected to the access point so that it exists on the same network, and then reboot your computer to establish a connection.20.Refer to the exhibit. All edge ports are configured with the spanning-tree portfast command. Host1 is recently connected to port Fa0/1 on switch SW1 . Which statement is true about the status of port Fa0/1?The port will transition into blocking state.The port will transition immediately into forwarding state.The port will transition into blocking state and then immediately into forwarding state.The port will transition into blocking state and immediately transition through the listening and learning states.21.Refer to the exhibit. What is true of the configuration of switch S1?A Cisco proprietary protocol is in use for ports Fa0/1 and Fa0/3.Switch ports Fa0/1 and Fa0/3 have been configured with the switchport mode access command.Untagged frames received on ports Fa0/1 and Fa0/3 will be placed on VLAN 1.Switch ports Fa0/1 and Fa0/3 are configured to carry data from multiple VLANs.22.Refer to the exhibit. The configuration steps that are listed in the exhibit have been entered in switch S1 via the console. Subsequent attempts to telnet to the switch are not successful. What is causing the problem?The switch must be configured with SSH version 1.The transport input command must specify Telnet access.The RSA keys must be returned to zero before SSH will permit Telnet access.The ip domain-name command must also be entered in line configuration mode for the vty lines.23.Refer to the exhibit. Which switch will be elected as the root bridge of the spanning tree topology?Cat-ACat-BCat-CCat-D24.Refer to the exhibit. VTP has been configured with VTP pruning enabled on all switches. If HostA sends a broadcast frame to SW1, which devices will receive the frame?SW1, SW3, HostFSW1, HostB, HostCSW1, SW2, SW3, SW4, HostFSW1, SW2, SW3, SW4, all hosts25.Refer to the exhibit. Which two statements are true about the operation of the interfaces? (Choose two.)Incoming traffic with VLAN ID 0 is processed by interface fa0/0.Incoming traffic that has a VLAN ID of 2 is processed by subinterface fa0/0.2.Both subinterfaces remain up with line protocol up, even if fa0/0 line protocol is down.Subinterfaces use unique MAC addresses by adding the 802.1Q VLAN ID to the hardware address.Traffic inbound on this router is processed by different subinterfaces, depending on the VLAN from which the traffic originated.26. The network administrator wants to configure a switch to pass VLAN update information to other switches in the domain but not update its own local VLAN database. Which two steps should the administrator perform to achieve this? (Choose two.)Reset the VTP counters.Configure VTP version 1 on the switch.Configure the VTP mode of the switch to transparent.Verify that the switch has a higher configuration revision number.Configure the switch with the same VTP domain name as other switches in the network.27.Refer to the exhibit. The devices in the network are operational and configured as indicated in the exhibit. However, hosts B and D cannot ping each other. What is the most likely cause of this problem?The link between the switches is up but not trunked.The Fa0/11 interface of Switch1 is not configured as a trunk.Hosts B and D are configured with IP addresses from different subnets. VLAN 20 and VLAN 30 are not allowed on the trunk between the switches.28.Refer to the exhibit. Users A and B are reporting intermittent connectivity problems. Pre-installation surveys showed strong signal strength from the AP locations to the client locations. Outside electrical interference has been eliminated. What will fix the problem?Relocate the APs closer to each other.Increase the distance between the clients.Change the channel on AP-B to 6 or 11.Place AP-A and AP-B on the same wireless channel.29. Why is it advisable that a network administrator use SSH instead of Telnet when managing switches?SSH uses TCP whereas Telnet does not.SSH encrypts only the username and password when logging in.SSH encrypts all remote management communications whereas Telnet does not.SSH sends a clear text message steam which reduces the bandwidth use for management.30.Refer to the exhibit. The teacher host is connected to port Fa0/7 on switch STW. A student has decided to share access to the Internet by attaching a hub and laptop to STW as shown. What will be the result of the student making this connection?The Fa0/7 port of STW will be shutdown.The student will gain full access to the Internet.Both the teacher and student will be able to receive data but only the teacher will be able to send.The frames from the laptop will be dropped, but the teacher host will maintain connectivity with the network.31. A network administrator configures a switch port with the command switchport mode dynamic auto. What is the resulting behavior of the switch port?The switch port is able to trunk if the remote switch port is set to auto.The switch port is able to trunk if the remote switch port is set to desirable.The switch port will be disabled if it is unable to successfully negotiate trunking.A successful trunk will be established if the remote switch is non-Cisco but the port is configured for trunking.32. Which STP port type can only appear once on a segment, and must be present in order for traffic to flow on that segment?non-root portdisabled portdesignated portnon-designated port33.Refer to the exhibit. What would happen if the network administrator moved the network cable of Host A from interface Fa0/1 to Fa0/3 on switch SW1?Host A remains a member of VLAN 10, because the router is routing traffic between VLANs.Host A is no longer a member of VLAN 10, because port Fa0/3 has been manually assigned to VLAN 30.Host A remains a member of VLAN 10, because the switch provides dynamic VLAN assignment for the port.Host A maintains connectivity to all members of VLAN 10, because it is connected to the same physical network.Host A is no longer a member of VLAN 10, but because port Fa0/3 was unused, it is now a member of VLAN 1.34.Refer to the exhibit. VLAN 10 has been configured on the VTP server. Users who are assigned to VLAN 10 are connected as shown in the exhibit. On the basis of the outputs that are provided, which group of users will be able to communicate with the users on VLAN 10 on SW1?all the users who are connected only to SW2users on VLAN 10 who are connected only to SW3users on VLAN 10 who are connected only to SW4users on VLAN 10 who are connected to both SW3 and SW435.Refer to the exhibit. Which three options correctly identify information that could be associated with this output?(Choose three.)Interface FastEthernet3/0/0 is subinterfaced.A non-proprietary trunking protocol is in use.The configuration is appropriate for a router-on-a-stick network design.A shutdown command has been applied to interface FastEthernet3/0/0.Interface FastEthernet3/0/0.3 is mapped to the default management VLAN.An IP address should be applied to FastEthernet3/0/0 for correct data routing.36.Refer to the exhibit. The Layer 2 switching design that is shown has been implemented in a campus environment that is using Spanning Tree Protocol. All inter-switch links that are shown are trunks. Whenever an inter-switch link fails, the network takes nearly a minute to completely converge. How can the convergence time be reduced?Increase the capacity of the distribution and core trunk links to 10 Gb/s.Add a trunk link that directly connects D1 and D2.Use Layer 3 switching on the core switch.Implement Rapid Spanning Tree Protocol.37.Refer to the exhibit. Each switch is configured to participate in STP for VLANs 1, 10, 20, and 30. Which switch will become the root for VLAN 20?ABCD38.Refer to the exhibit. Switches S2 and S3 are properly connected using an ethernet cable. A network administrator has configured both switches with VTP, but S3 is unable to propagate VLANs to S2. What could be the reason for this?The VTP configuration revision is different on both switches.The VTP domains are different on both switches.VTP pruning is disabled.VTP v2 is disabled.39. In a three-layer hierarchical network design, which distribution layer function delineates broadcast domains?routing between VLANsaggregating traffic flowsproviding redundant linksreducing the network diameter40. Which parameter is used to uniquely identify one wireless network from another?SSIDOFDMWEPDSSS41. What is one disadvantage that 802.11a wireless has compared to 802.11g?Use of the 5GHz band requires much larger antennas.The OFDM modulation technique results in a slower data rate.There are fewer non-overlapping channels available to help reduce RF interference.The use of higher frequencies means that signals are more likely to be obstructed.42. Which three statements are correct concerning the default configuration of a new switch? (Choose three.)It is configured in VTP server mode.STP is automatically enabled.The first VTY line is automatically configured to allow remote connections.VLAN1 is configured with a management IP address.All switch ports are assigned to VLAN1.The enable password is configured as cisco.43.Refer to the exhibit. How is port Gi1/1 on SWT-A functioning in the spanning-tree topology?It is sending and receiving data frames.It is receiving BPDUs, but not sending data frames.It is participating in the election process by forwarding the BPDUs it receives.It is receiving BPDUs and populating the MAC address table, but not sending data.44. While configuring a new switch, a network administrator configures the switch as an HTTP server. What benefits does this configuration provide?This allows the switch to host web pages for the network.This allows remote VPN connections to the switch over the Internet.This is required if a web server or web farm is attached to the switch. This allows web-based configuration tools to be used with the switch.45. Which statement describes the use of voice VLANs in Cisco IP telephony? The voice VLAN carries both tagged and untagged traffic.The voice VLAN carries untagged traffic having special QoS markings.The voice VLAN must be configured on the switch port to which the IP phone attaches.Data and voice frames are tagged with same VLAN ID between the IP phone and the switch when a voice VLAN is configured.46.Refer to the exhibit. If switch SW1 is configured with the four VLANs as shown in the exhibit, how many physical interfaces are needed on router R1 to configure inter-VLAN routing using subinterfaces?zeroonetwofour47.Refer to the exhibit. What does the term DYNAMIC indicate in the output that is shown?This entry can only be removed from the MAC address table by a network administrator.When forwarding a frame to the device with address 0060.5c5b.cd23, the switch does not have to perform a lookup to determine the final destination port.Only the device with MAC address 0060.5c5b.cd23 will be allowed to connect to port Fa0/18.The switch learned this MAC address from the source address in a frame received on Fa0/18.48.Refer to the exhibit. The VTP domain has been configured as shown in the exhibit. The network technician accidentally configured the VTP server as a VTP client. After the technician reloaded the switches, all usersin the VTP domain started to complain that they lost connectivity to the users on the same VLANs that are connected to other switches. What should be done in the future to prevent losing all VLAN configurations in a VTP domain?Configure all switches in VTP transparent mode and copy the VLAN configuration into flash.Configure all switches in the network as VTP clients and copy the VLAN configuration into NVRAM.Create a new domain and configure a second switch as a VTP server to take over in case of a primary VTP server failure.In the same domain, configure a second switch as a VTP server to take over in case of a primary VTP server failure.49.Refer to the exhibit. How does SW1 manage traffic coming from Host A?SW1 drops the traffic because it is untagged.SW1 leaves the traffic untagged and forwards it over the trunk.SW1 tags the traffic with the lowest VLAN ID value and forwards it over the trunk link.SW1 encapsulates the traffic with 802.1Q encapsulation and forwards it over the trunk link.50. An administrator is troubleshooting a PC on the network which is suffering from slow and intermittent connectivity. The PC has a ping success rate to the default gateway of less than half the ping attempts. Other PCs on the switch can consistently ping the default gateway. The switch port is configured for auto duplex and the PC is configured for full duplex. What will commonly cause this problem?The PC is set to full duplex. The switch port fails to autonegotiate the duplex setting and defaults to half duplex, which causes a duplex mismatch.The switch traffic is exceeding available frame buffers. The result is that frames are being dropped.The PC and the default gateway have different bandwidth Ethernet ports.The default gateway is not on the same switch that the PC is.51.Refer to the exhibit. A network administrator has segmented the network into two VLANs and configured Router1 for inter-VLAN routing. A test of the network, however, shows that hosts on each VLAN can only access local resources and not resources on the other VLAN. What is the most likely cause of this problem?Switch port Fa0/1 is not trunking.Router interface Fa0/0 is possibly down.No routing protocol is configured on Router1.One of the router subinterfaces is possibly down.52.What impact does the use of the mdix auto configuration command have on an Ethernet interface on a switch?automatically detects duplex settingsautomatically detects interface speedautomatically detects copper cable typeautomatically assigns the first detected MAC address to an interface。
思科CCNA第一学期期末考试答案Final

1下列哪个端口号范围为服务器上运行的应用程序常用的服务而保留?0 到2550 到10231024 到4915149152 到655352以下哪组网络ID 和子网掩码正确标识了从172.16.128.0 到172.16.159.255 的所有IP 地址?172.16.128.0 255.255.255.224172.16.128.0 255.255.0.0172.16.128.0 255.255.192.0172.16.128.0 255.255.224.0172.16.128.0 255.255.255.1923以下哪个OSI 协议层提供面向连接的可靠数据通信服务?应用层演示文稿会话传输层network4何时必须使用clock rate命令配置路由器串行接口?当该接口充当DTE 设备时当该接口计时器已经清除时当连接的DTE 设备关闭时当该接口充当DCE 设备时5下列哪些是私有IP 地址的地址范围?(选择三项。
)10.0.0.0 到10.255.255.255200.100.50.0 到200.100.25.255150.150.0.0 到150.150.255.255172.16.0.0 到172.31.255.255192.168.0.0 到192.168.255.255127.16.0.0 到127.31.255.2556请参见图示。
每条介质链路都已标记。
应该使用哪种类型的电缆连接不同设备?连接 1 - 全反电缆连接 3 - 交叉电缆连接 1 - 交叉电缆连接 3 - 交叉电缆连接 1 - 直通电缆连接 3 - 交叉电缆连接 1 - 直通电缆连接 3 - 直通电缆连接 1 - 交叉电缆连接 3 - 交叉电缆7请参见图示。
IP 地址192.168.33.2 代表什么?主机的默认网关。
主机的IP 地址。
主机的首选域名服务器。
网站resolver1.mooki.local 的IP 地址。
主机的主页IP 地址。
CCNA考试题库中英文翻译版及答案

CCNA考试题库中英文翻译版及答案1[1]1. What are two reasons that a network administrator would use access lists? (Choose two.)1.出于哪两种理由,会使用访问列表?A. to control vty access into a routerA.控制通过VTY访问器B. to control broadcast traffic through a routerB.控制广播流量穿越路由器2.一个默认的帧中继WAN被分类为哪种物理网络类型?A. point-to-pointA.点到点B. broadcast multi-accessB.广播多路访问C. nonbroadcast multi-accessC.非广播多路访问D. nonbroadcast multipointD.非广播多点E. broadcast point-to-multipointE.广播点到多点Answer: C3. A single 802.11g access point has been configured and installed in the center of a squarA few wireless users are experiencing slow performance and drops while most users are oat peak efficiency. What are three likely causes of this problem? (Choose three.)3.一个802.11接入点被部署在一个方形办公室的中央,当大多数用户在大流量传输数一些用户发现无线网络变得缓慢和出现丢包A. mismatched TKIP encryptionB. null SSIDC. cordless phonesD. mismatched SSIDE. metal file cabinetsF. antenna type or directionAnswer: CEF4. Refer to the exhibit. How many broadcast domains exist in the exhibited topology?根据下图,图中的拓扑中存在多少个广播域?A. one A.1B. two B.2C. three C.3D. four D.4E. five E.5F. six F.6Answer: C5. Refer to the exhibit. What two facts can be determined from the WLAN diagram? (Choose two.)5.根据下图,WLAN diagram决定了哪两个事实A. The area of overlap of the two cells represents a basic service set (BSS).A. 两个 cells的overlap的区域描述了一个basic service setB. The network diagram represents an extended service set (ESS).B. 网络描述了一个extended service setC. Access points in each cell must be configured to use channel 1.C. 再每个CELL中的AP必须被配置成使用channel 1D. The area of overlap must be less than 10% of the area to ensure connectivity.D. 为了确保连通性,重叠区域必须小于10%E. The two APs should be configured to operate on different channels.E. 两个访问点应该被配置成工作在不同的频道Answer: BE6. The command frame-relay map ip 10.121.16.8 102 broadcast was entered on the router.Which of the following statements is true concerning this command?6.器上输入命令frame-relay map ip 10.121.16.8 102 broadcast,以下选项正确的是?A. This command should be executed from the global configuration mode.A.该命令应该在全局配置模式下被执行B. The IP address 10.121.16.8 is the local router port used to forward data.B.IP地址10.121.16.8是本地路由器用来转发数据的接口C. 102 is the remote DLCI that will receive the information.C.102是远端的DLCI它将接受信息。
CCNA 4 - Final Exam (C)

CCNA 4 - Final Exam (C)Posted by beotron at 9:23 PM1. Which of the following describes the roles of devices in a WAN? (Choose three.)• A CSU/DSU terminates a digital local loop.• A modem terminates a digital local loop.• A CSU/DSU terminates an analog local loop.• A modem terminates an analog local loop.• A router is commonly considered a DTE device.• A router is commonly considered a DCE device.2. What value in the address field of a Frame Relay header identifies the destination of the frame? • CIR• DE• DLCI• ISDN• FRAD• PVC3. The serial PPP link between the Left and Right routers is configured as shown in the diagram. Which configuration issue explains why the link is unable to establish a PPP session?• The IP addresses must be on different subnets.• The usernames are misconfigured.• The passwords must be different for the CHAP authentication.• The clock rate must be 56000.• The clock rate is configured on the wrong end of the link.• Interface serial 0/0 on Left must connect to interface serial 0/1 on Right.4. The output of the show interfaces serial 0/0 command for a frame-relay connection indicates that the serial line is up but the line protocol is down. What are possible causes for this? (Choose two.)• There is an LMI-type mismatch between the Frame Relay switch and the router.• There is no clock present on the serial interface.• The interface is shut down.• RARP is not functioning on the router.• The cable is disconnected.5. Which statements are correct about the point in the network where the responsibility of the service provider ends? (Choose three.)• The International point is on the customer side of the network terminating unit(NTU).• The United States point is at the interface of the customer-provided equipment and the local loop.• The responsibility for this point is controlled by IANA.• The point is called the demarcation point.• The point is typically located at the service provider’s central office.• The point is located between the customer’s local area networks.6. While prototyping an internetwork in the corporate lab, a network administrator is testing a serial link between serial 0/0 interfaces on two routers. The labels on the serial cable ends have been damaged and are unreadable. What command can be issued to determine which router is connected to the DCE cable end?• show interfaces serial 0/0• show version• show controllers serial 0/0• show protocols serial 0/0• show status serial 0/07. A network technician determines DHCP clients are not working properly. The clients are receiving IP configuration information from a DHCP server configured on the router but cannot access the Internet. From the output in the graphic, what is the most likely problem?• The DHCP server service is not enabled.• The inside interface for DCHP is not defined.• The DHCP pool is not bound to the interface.• The pool does not have a default router defined for the clients.• All the host addresses have been excluded from the DHCP pool.8. A technician enters the interface serial 0/0.1 multipoint command when configuring a router. What effect will the multipoint keyword have in this configuration? (Choose two.)• Split-horizon issues will need to be resolved for this network if RIP is the routing protocol.• A subinterface will be defined for each PVC.• All the participating interfaces of remote routers will be configured in the same subnet.• A single DLCI will be used to define all the PVCs to the remote routers.• An IP address will need to be configured on the main interface.9. When configuring a Frame Relay connection, when should a static Frame Relay map be used? (Choose two.)• when the remote router is a non-Cisco router• whe n the remote router does not support Inverse ARP• when the local router is using IOS Release 11.1 or earlier• when broadcast traffic and multicast traffic over the PVC must be controlled• when globally significant rather than locally significant DLCIs a re being used10. Which router command would be used to associate a Layer 2 address with the corresponding Layer 3 address in the internetwork in the diagram?• RouterA(config-if)#frame-relay pvc 100 192.168.15.2• RouterA(config-if)#dialer-map ip 192.168.15.1 100 broadcast• RouterA(config-if)#frame-relay map ip 192.168.15.2 100 broadcast• RouterA (config-if)#dialer-map 192.168.15.1 101 serial 0 broadcast• RouterA (config-if)#frame-relay dlci 101 192.168.15.1 broadcast• RouterA (config-if)#dialer-map 192.168.15.1 inverse-arp broadcast11. Which of the following ISDN protocols is responsible for call setup and call teardown?• ITU-T Q.921• ITU-T Q.931• ITU-T I.430• ITU-T I.43112. What are two ways to resolve split-horizon issues in a Frame Relay network? (Choose two.)• create a full-mesh topology• disable Inverse ARP• use point-to-point subinterfaces• use multipoint subinterfaces• remove the broadcast keyword from the frame-relay map command13. What is the purpose of the command marked with an arrow shown in the partial configuration output of a Cisco 806 broadband router?• defines which addresses are allowed out of the router• defines which addresses are allowed into the router• defines which addresses can be translated• defines which address es are assigned to a NAT pool14. A system administrator is unable to ping the Serial0/0 interface of RouterB from RouterA. During the troubleshooting process, the following facts are established:- IP addressing and subnet masks are correct.- RouterA is a Cisco router and RouterB is a router from another vendor.- RouterA is configured with the default encapsulation.- The serial interfaces on both routers are up.- The protocol is down on the serial interfaces of both routers.What should the administrator do to solve the problem?• Add a clock rate on RouterA.• Enable the serial interface on RouterB.• Change the encapsulation on both routers to PPP.• Connect the serial cable to the correct interface on RouterB.• Use the correct serial cable to attach the CSU/DSU to RouterB.15. An ISDN circuit from a branch office is remaining connected to the regional office. A network administrator determines a user has initiated a continuous ping from a desktop computer to the regional office. Which configuration change would allow the ISDN circuit to disconnect during any attempts to ping, while otherwise functioning properly?• change DDR from legacy to dialer profiles• remove the dialer list statement from the configuration• change the dialer list to exclude IC MP as interesting• disable inverse ARP16. Below is a list of DDR steps. Which of the following identifies the proper order of DDR?1 - dial number is looked up2 - interesting traffic triggers DDR3 - route to destination is determined4 - call is made• 1,2,3,4• 1,3,2,4• 2,3,1,4• 2,1,3,4• 3,2,1,4• 3,1,2,417. Which protocol should be chosen to support WAN connectivity in a multi-vendor system and provide strong security through authentication?• NAT with DHCP• Frame Relay• HDLC with encryption• H DLC with CHAP• PPP with PAP• PPP with CHAP18. Which of the following are valid steps for a basic ISDN BRI configuration? (Choose two.)• create subinterfaces• define the LMI type• set the SPIDs if required by the ISDN switch• set the interface DLCI• set the switch type• specify the encapsulation as either Cisco or IETF19. A branch office reports excessive connect time charges for an ISDN circuit used to connect to the regional office. Upon investigation of this issue, it is discovered that when an ISDN connection is initiated to the regional office it remains connected for an excessive amount of time. Which of the following configuration changes could be made to DDR on the router to reduce these connect time charges?• use PPP multilink• lower idle timer setting• use CHAP authentication• change DDR from legacy to dialer profiles20. A network administrator is having difficulty in establishing a serial link between a Cisco router and a router from another vendor. Both routers are configured for HDLC encapsulation. Which statements are true regarding this configuration? (Choose two.)• The Cisco HDLC frame uses a proprietary “Type” field that may not be compatible with equipment of other vendors.• HDLC requires a clock rate to be configured on the r outers at both ends of the serial link.• PPP encapsulation is recommended for serial links between equipment from multiple vendors.• Usernames must be configured at both ends of the HDLC serial link.• The HDLC vendor type must be enabled on the Cisco ro uter.• There is a mismatch in the HDLC authentication password configurations.21. Given the partial router configuration in the graphic, why does the workstation with the IP address 192.168.1.153/28 fail to access the Internet? (Choose two.)• The NAT in side interfaces are not configured properly.• The NAT outside interface is not configured properly.• The router is not properly configured to use the access control list for NAT.• The NAT pool is not properly configured to use routable outside addresses.• The access control list does not include the IP address 192.168.1.153/28 to access the Internet.22. The serial PPP link between the Left and Right routers is configured as shown in the diagram. Which configuration issue will prevent IP traffic from crossing this link?• The passwords must be different for the CHAP authentication.• The usernames are misconfigured.• The clock rate must be 56000.• The clock rate is configured on the wrong end of the link.• The IP addresses must be on the same subnet.• Interface serial 0/0 on Left must connect to interface serial 0/1 on Right.23. What causes a DDR call to be placed?• dial string• DLCI• idle time out• interesting traffic• PVC24. Which two layers of the OSI model are described by WAN standards?• Application Layer, Physical Layer• Data Link Layer, Physical Layer• Data Link Layer, Transport Layer• Physical Layer, Network Layer25. A technician is testing RouterA in the graphic. What is the condition of the circuit?• The routers are configured fo r different encapsulations.• The clock rate is not properly configured on the routers.• The circuit from WAN provider has failed.• Authentication is not properly configured on the routers.• The circuit is functioning properly.26. A network administrator must provide WAN connectivity between a central office and three remote sites: Orlando, Atlanta, and Phoenix. The Orlando and Atlanta remote offices receive sales orders and transmit shipping confirmations to the Central office consistently throughout the day. The Phoenix remote office consists of one salesperson traveling through the southwest territory. The salesperson occasionally needs to connect to the Central office for e-mail access. How should the networkadministrator connect the remote sites to the Central office? (Choose two.)• Connect to the Atlanta and Orlando remote offices with Frame Relay connections.• Connect to the Atlanta and Orlando remote offices with ISDN connections.• Connect to the Atlanta and Orlando re mote offices with POTS dial-up connections.• Connect to the Phoenix remote office with a Frame Relay connection.• Connect to the Phoenix remote office with a POTS dial-up connection.27. When a Frame Relay switch detects an excessive buildup of frames in its queue, which of the following may occur? (Choose two.)• Frames with the DE bit set are dropped from the switch queue.• Frames with the FECN and BECN bits set are dropped from the switch queue.• Frames in excess of the CIR are not accepted by the sw itch.• The switch sets the FECN bit on all frames it places on the congested link and sets the BECN bit on all frames it receives on the congested link.• The switch sets the FECN bit on all frames it receives on the congested link and sets the BECN bit o n all frames it places on the congested link.28. A system administrator is troubleshooting a connectivity issue between two routers in a new installation. The administrator enters the debug ppp authentication command on the WHSE router. The graphic shows a part of the output received. From this output, what is the most likely cause of this connectivity issue?• There is not a route to the remote router.• The ISDN circuit on the remote router has failed.• The username/password was not properly configured on the WHSE router.• The remote router has a different authentication protocol configured.29. What does the output of the show frame-relay map command shown below represent? (Choose two.) • Serial 0 (up): ip 172.30.151.4 dlci 122, dynamic, broadcast, sta tus defined, active• 172.30.151.4 represents the IP address of the remote router.• 172.30.151.4 represents the IP address of the local serial interface.• DLCI 122 represents the interface of the remote router.• broadcast indicates that a dynamic routin g protocol such as RIP v1 can send packets across this PVC. • dynamic indicates that a dynamic routing protocol is enabled for this connection.• active indicates that the ARP process is working.30. What does the status inactive indicate in the output of the show frame-relay pvc command?• The DLCI is programmed in the switch but is not usable.• The DLCI was formerly programmed in the switch but is no longer there.• The DLCI is usable but has little activity.• The DLCI has been renamed for that PVC.31. Which of the following IP addresses are defined by RFC 1918 as private addresses? (Choose three.) • 192.168.146.0/22• 172.10.25.0/16• 172.31.0.0/16• 20.0.0.0/8• 10.172.92.8/2932. After configuring a dialup ISDN circuit, a network associate begins testing the dialup connection. When attempting to ping a host on the remote network, the local router does not attempt to dial the remote access server. Which of the following are possible errors in this configuration? (Choose three.) • PPP authentication is not properly configured.• No dialer map is configured.• The ISDN circuit connected to the remote access server is busy.• No interesting traffic is defined.• No route is determined to the remote network.• A wrong number is configured in the dial string.33. Two routers are connected through a Frame Relay, point-to-point PVC. The remote router is from a vendor other than Cisco. Which interface command is required to configure the link between the Cisco router and the other router?• frame-relay pvc multipoint• frame-relay pvc point-to-point• encapsulation frame-relay cisco• encapsulation frame-relay ietf• frame-relay lmi-type ansi34. Which circuit-switched WAN technology is often used to provide a backup for a leased line and additional capacity during peak usage times?• X.25• DSL• ISDN• cable modem35. After the ISDN BRI interface is configured, which command can be used to verify that the router is communicating correctly with the ISDN switch?• show dialer• show isdn status• show interfaces b ri0/0:1• show interfaces serial0/0.136. A system administrator needs to configure the regional office with ISDN for DDR connections to three remote sites. Each remote site requires different IP subnets, different encapsulations, and different authentication methods. The sites will not be connected at the same time. The company would like to accomplish this in the most cost effective manner. What method can the system administrator use to accomplish this task using the fewest B channels?• Install and conf igure a PRI.• Install and configure a BRI interface with separate SPIDs for each remote site.• Install and configure a BRI with multiple switch types in global configuration.• Install and configure a BRI using dialer profiles.• Install and configure a separate BRI for each remote site.37. A system administrator must provide Internet connectivity for ten hosts in a small remote office. The ISP has assigned two public IP addresses to this remote office. How can the system administrator configure the router to provide Internet access to all ten users at the same time?• Configure static NAT for all ten users.• Configure dynamic NAT for ten users.• Configure dynamic NAT with PAT.• Configure DHCP and static NAT.• What the administrator wants to do cannot be done.38. Which of the following are characteristics of Frame Relay? (Choose two.)• circuit-switched• connection oriented• OSI Layer 3• packet-switched• reliable39. Which of the following is the order for the three phases of establishing a PPP serial link with authentication?• authentication, link-establishment, network layer protocols• authentication, network layer protocols, link-establishment• network layer protocols, link-establishment, authentication• network layer protocols, authenticati on, link-establishment• link-establishment, authentication, network layer protocols• link-establishment, network layer protocols, authentication。
CCNAS SECURITY FINAL 100% 思科安全课程final答案

Take Assessment - CCNAS Final Exam - CCNA Security: Implementing Network Security (Version 1.0)Time Remaining:02:38:471Which statement describes the operation of the IKE protocol?It uses IPsec to establish the key exchange process.It uses sophisticated hashing algorithms to transmit keys directly across a network.It calculates shared keys based on the exchange of a series of data packets.It uses TCP port 50 to exchange IKE information between the security gateways.2Which statement describes a factor to be considered when configuring a zone-based policy firewall?An interface can belong to multiple zones.The router always filters the traffic between interfaces in the same zone.The CBAC ip inspect command can coexist with ZPF as long as it is used on interfaces that are in the same security zones.A zone must be configured with the zone security global command before it can be used in the zone-member security command.3What are two disadvantages of using network IPS? (Choose two.)Network IPS has a difficult time reconstructing fragmented traffic to determine if an attack was successful.Network IPS is incapable of examining encrypted traffic.Network IPS is operating system-dependent and must be customized for each platform.Network IPS is unable to provide a clear indication of the extent to which the network is being attacked.Network IPS sensors are difficult to deploy when new networks are added.4Which three security services are provided by digital signatures? (Choose three.)authenticates the sourceauthenticates the destinationguarantees data has not changed in transitprovides nonrepudiation of transactionsprovides nonrepudiation using HMAC functionsprovides confidentiality of digitally signed data5Which three statements describe zone-based policy firewall rules that govern interface behavior and the traffic moving between zone mem (Choose three.)An interface can be assigned to multiple security zones.Interfaces can be assigned to a zone before the zone is created.Pass, inspect, and drop options can only be applied between two zones.If traffic is to flow between all interfaces in a router, each interface must be a member of a zone.Traffic is implicitly prevented from flowing by default among interfaces that are members of the same zone.To permit traffic to and from a zone member interface, a policy allowing or inspecting traffic must be configured between that zone a zone.6Which type of SDM rule is created to govern the traffic that can enter and leave the network based on protocol and port number?NAC ruleNAT ruleIPsec ruleaccess rule7Which three types of views are available when configuring the Role-Based CLI Access feature? (Choose three.)superuser viewroot viewsuperviewCLI viewadmin viewconfig view8Which two statements match a type of attack with an appropriate example? (Choose two.)To conduct an access attack, an attacker uses L0phtCrack to obtain a Windows server password.To conduct an access attack, an attacker uses Wireshark to capture interesting network traffic.To conduct a reconnaissance attack, an attacker initiates a ping of death attack to a targeted server.To conduct a DoS attack, an attacker uses handler systems and zombies to obtain a Windows server password.To conduct a DoS attack, an attacker initiates a smurf attack by sending a large number of ICMP requests to directed broadcast addTo conduct a reconnaissance attack, an attacker creates a TCP SYN flood causing the server to spawn many half-open connections unresponsive.9Which statement describes configuring ACLs to control Telnet traffic destined to the router itself?The ACL must be applied to each vty line individually.The ACL is applied to the Telnet port with the ip access-group command.Apply the ACL to the vty lines without the in or out option required when applying ACLs to interfaces.The ACL should be applied to all vty lines in the in direction to prevent an unwanted user from connecting to an unsecured port.10Refer to the exhibit. When configuring SSH on a router using SDM from the Configure menu, which two steps are required? (Choose twoChoose Additional Tasks > Router Access > SSH to generate the RSA keys.Choose Additional Tasks > Router Access > VTY to specify SSH as the input and output protocol.Choose Additional Tasks > Router Properties > Netflow to generate the RSA keys.Choose Additional Tasks > Router Properties > Logging to specify SSH as the input and output protocol.Choose Additional Tasks > Router Access > AAA to generate the RSA keys.Choose Additional Tasks > Router Access > Management Access to specify SSH as the input and output protocol.11Refer to the exhibit. Based on the output from the show secure bootset command on router R1, which three conclusions can be drawn IOS Resilience? (Choose three.)A copy of the Cisco IOS image file has been made.A copy of the router configuration file has been made.The Cisco IOS image file is hidden and cannot be copied, modified, or deleted.The Cisco IOS image filename will be listed when the show flash command is issued on R1.The copy tftp flash command was issued on R1.The secure boot-config command was issued on R1.12Which three OSI layers can be filtered by a stateful firewall? (Choose three.)Layer 2Layer 3Layer 4Layer 5Layer 6Layer 713What is an important difference between network-based and host-based intrusion prevention?Host-based IPS is more scalable than network-based IPS.Host-based IPS can work in promiscuous mode or inline mode.Network-based IPS is better suited for inspection of SSL and TLS encrypted data flows.Network-based IPS provides better protection against OS kernel-level attacks on hosts and servers.Network-based IPS can provide protection to hosts without the need of installing specialized software on each one.14What will be disabled as a result of the no service password-recovery command?aaa new-model global configuration commandchanges to the configuration registerpassword encryption serviceability to access ROMmon15Which function does an IPS perform?It passively monitors the traffic on a network.It works in inline mode for processing all ingress and egress traffic.It compares the captured traffic stream with known malicious signatures in an offline manner.It can only send an alarm to the management console when malicious traffic is detected.16Refer to the exhibit. An administrator has entered the commands that are shown on router R1. At what trap level is the logging function s235617What are access attacks?attacks that prevent users from accessing network servicesattacks that modify or corrupt traffic as that traffic travels across the networkattacks that exploit vulnerabilities to gain access to sensitive informationattacks that involve the unauthorized discovery and mapping of systems, services, and vulnerabilities18Which mitigation technique can help prevent MAC table overflow attacks?root guardBPDU guardstorm controlswitchport security19Which three major subpolicies should comprise a comprehensive security policy that meets the security needs of a typical enterprise? (Cend-user policiesdepartmental policiesgoverning policieshuman resource policiesorganizational policiestechnical policies20Which three statements describe SSL-based VPNs? (Choose three.)Asymmetric algorithms are used for authentication and key exchange.It is impossible to configure SSL and IPsec VPNs concurrently on the same router.Special-purpose client software is required on the client machine.Symmetric algorithms are used for bulk encryption.The authentication process uses hashing technologies.The application programming interface is used to extensively modify the SSL client software.The primary restriction of SSL VPNs is that they are currently supported only in hardware.21Refer to the exhibit. Which Cisco IOS security feature is implemented on router R2?CBAC firewallreflexive ACL firewallzone-based policy firewallAAA access control firewall22When port security is enabled on a Cisco Catalyst switch, what is the default action when the maximum number of allowed MAC addresseThe violation mode for the port is set to restrict.The MAC address table is cleared, and the new MAC address is entered into the table.The port remains enabled, but the bandwidth is throttled until the old MAC addresses are aged out.The port is shut down.23Which two protocols allow SDM to gather IPS alerts from a Cisco ISR router? (Choose two.)FTPHTTPSSDEESSHSyslogTFTP24Which three statements describe limitations in using privilege levels for assigning command authorization? (Choose three.)There is no access control to specific interfaces on a router.The root user must be assigned to each privilege level defined.Commands set on a higher privilege level are not available for lower privileged users.Views are required to define the CLI commands that each user can access.Creating a user account that needs access to most but not all commands can be a tedious process.It is required that all 16 privilege levels be defined, whether they are used or not.25Which device supports the use of SPAN to enable monitoring of malicious activity?Cisco NACCisco IronPortCisco Security AgentCisco Catalyst switch26Which two statements describe appropriate general guidelines for configuring and applying ACLs? (Choose two.)Multiple ACLs per protocol and per direction can be applied to an interface.If an ACL contains no permit statements, all traffic is denied by default.The most specific ACL statements should be entered first because of the top-down sequential nature of ACLs.Standard ACLs are placed closest to the source, whereas Extended ACLs are placed closest to the destination.If a single ACL is to be applied to multiple interfaces, it must be configured with a unique number for each interface.27Refer to the exhibit. Which AAA command logs the activity of a PPP session?aaa accounting connection start-stop group radiusaaa accounting connection start-stop group tacacs+aaa accounting exec start-stop group radiusaaa accounting exec start-stop group tacacs+aaa accounting network start-stop group radiusaaa accounting network start-stop group tacacs+28What login enhancement configuration command helps prevent successive login DoS attacks?exec-timeoutlogin block-forprivilege exec levelservice password-encryption29Which access list statement permits HTTP traffic that is sourced from host 10.1.129.100 port 4300 and destined to host 192.168.30.10?access-list 101 permit tcp any eq 4300access-list 101 permit tcp 192.168.30.10 0.0.0.0 eq 80 10.1.0.0 0.0.255.255access-list 101 permit tcp 10.1.129.0 0.0.0.255 eq www 192.168.30.10 0.0.0.0 eq wwwaccess-list 101 permit tcp 10.1.128.0 0.0.1.255 eq 4300 192.168.30.0 0.0.0.15 eq wwwaccess-list 101 permit tcp host 192.168.30.10 eq 80 10.1.0.0 0.0.255.255 eq 430030Refer to the exhibit. A network technician has entered the commands that are shown on router R1. However, the authentication with the N What is a possible cause?The NTP key value does not meet the MD5 requirements.Authentication has not been enabled on R1.The NTP key numbers have to match on R1.The NTP server has to be specified on R1.31Refer to the exhibit. Which type of VPN is implemented?remote-access GRE VPNremote-access IPsec VPNremote-access SSL VPNsite-to-site GRE VPNsite-to-site IPsec VPNsite-to-site SSL VPN32Refer to the exhibit. Which three things occur if a user attempts to log in four times within 10 seconds using an incorrect password? (ChoSubsequent virtual login attempts from the user are blocked for 60 seconds.During the quiet mode, an administrator can virtually log in from any host on network 172.16.1.0/24.Subsequent console login attempts are blocked for 60 seconds.A message is generated indicating the username and source IP address of the user.During the quiet mode, an administrator can log in from host 172.16.1.2.No user can log in virtually from any host for 60 seconds.33 A network technician is configuring SNMPv3 and has set a security level of auth. What is the effect of this setting?authenticates a packet using the SHA algorithm onlyauthenticates a packet by a string match of the username or community stringauthenticates a packet by using either the HMAC with MD5 method or the SHA methodauthenticates a packet by using either the HMAC MD5 or HMAC SHA algorithms and encrypts the packet using either the DES, 3D algorithms34What is a result of securing the Cisco IOS image using the Cisco IOS Resilient Configuration feature?The Cisco IOS image file is not visible in the output of the show flash command.The Cisco IOS image is encrypted and then automatically backed up to a TFTP server.The Cisco IOS image is encrypted and then automatically backed up to the NVRAM.When the router boots up, the Cisco IOS image is loaded from a secured FTP location.35Refer to the exhibit. What information can be obtained from the AAA configuration statements?The authentication method list used for Telnet is named ACCESS.The authentication method list used by the console port is named ACCESS.The local database is checked first when authenticating console and Telnet access to the router.If the TACACS+ AAA server is not available, no users can establish a Telnet session with the router.If the TACACS+ AAA server is not available, console access to the router can be authenticated using the local database.36Which three additional precautions should be taken when remote access is required in addition to local access of networking devices? (CA legal notice should not be displayed when access is obtained.All activity to the specified ports that are required for access should be unrestricted.All configuration activities should require the use of SSH or HTTPS.All administrative traffic should be dedicated to the management network.The number of failed login attempts should not be limited, but the time between attempts should.Packet filtering should be required so that only identified administration hosts and protocols can gain access.37What occurs after RSA keys are generated on a Cisco router to prepare for secure device management?All vty ports are automatically configured for SSH to provide secure management.The general-purpose key size must be specified for authentication with the crypto key generate rsa general-keys modulus commThe keys must be zeroized to reset secure shell before configuring other parameters.The generated keys can be used by SSH.38The use of which two options are required for IPsec operation? (Choose two.)AH protocols for encryption and authenticationDiffie-Hellman to establish a shared-secret keyIKE to negotiate the SAPKI for pre-shared-key authenticationSHA for encryption39Which two guidelines relate to in-band network management? (Choose two.)Apply in-band management only to devices that must be managed on the production network.Implement separate network segments for the production network and the management network.Attach all network devices to the same management network.Use IPSec, SSH, or SSL.Deploy a terminal server with console connections to each network device.40Which two statements are characteristics of the IPsec protocol? (Choose two)IPsec is a framework of open standards.IPsec is implemented at Layer 4 of the OSI model.IPsec ensures data integrity by using a hash algorithm.IPsec uses digital certificates to guarantee confidentiality.IPsec is bound to specific encryption algorithms, such as 3DES and AES.41Which element of the Cisco Threat Control and Containment solution defends against attempts to attack servers by exploiting application system vulnerabilities?threat control for emailthreat control for endpointsthreat control for infrastructurethreat control for systems42Refer to the exhibit. Based on the IPS configuration that is provided, which statement is true?The signatures in all categories will be retired and not be used by the IPS.The signatures in all categories will be compiled into memory and used by the IPS.Only the signatures in the ios_ips basic category will be compiled into memory and used by the IPS.The signatures in the ios_ips basic category will be retired and the remaining signatures will be compiled into memory and used by43Which two Cisco IPS management and monitoring tools are examples of GUI-based, centrally managed IPS solutions? (Choose two.)Cisco Adaptive Security Device ManagerCisco IPS Device ManagerCisco Router and Security Device ManagerCisco Security ManagerCisco Security Monitoring, Analysis, and Response System44What are three common examples of AAA implementation on Cisco routers? (Choose three.)authenticating administrator access to the router console port, auxiliary port, and vty portsauthenticating remote users who are accessing the corporate LAN through IPsec VPN connectionsimplementing public key infrastructure to authenticate and authorize IPsec VPN peers using digital certificatesimplementing command authorization with TACACS+securing the router by locking down all unused servicestracking Cisco Netflow accounting statistics45Which action best describes a MAC address spoofing attack?altering the MAC address of an attacking host to match that of a legitimate hostbombarding a switch with fake source MAC addressesforcing the election of a rogue root bridgeflooding the LAN with excessive traffic46Refer to the exhibit. An administrator is configuring ZPF using the SDM Basic Firewall Configuration wizard. Which command is generate administrator selects the Finish button?zone security Out-zone on interface Fa0/0zone security Out-zone on interface S0/0/0zone-member security Out-zone on interface Fa0/0zone-member security Out-zone on interface S0/0/047An organization requires that individual users be authorized to issue specific Cisco IOS commands. Which AAA protocol supports this reTACACS+ because it separates authentication and authorization, allowing for more customization.RADIUS because it supports multiple protocols, including ARA and NetBEUI.TACACS+ because it supports extensive accounting on a per-user or per-group basis.RADIUS because it implements authentication and authorization as one process.48Which three principles are enabled by a Cisco Self-Defending Network? (Choose three.)adaptabilitycollaborationinsulationintegrationmitigationscalability49Refer to the exhibit. Which interface configuration completes the CBAC configuration on router R1?R1(config)# interface fa0/0R1(config-if)# ip inspect INSIDE inR1(config-if)# ip access-group OUTBOUND inR1(config)# interface fa0/1R1(config-if)# ip inspect INSIDE inR1(config-if)# ip access-group OUTBOUND inR1(config)# interface fa0/1R1(config-if)# ip inspect OUTBOUND inR1(config-if)# ip access-group INSIDE outR1(config)# interface fa0/0R1(config-if)# ip inspect OUTBOUND inR1(config-if)# ip access-group INSIDE inR1(config)# interface fa0/1R1(config-if)# ip inspect OUTBOUND inR1(config-if)# ip access-group INSIDE in50Which three statements should be considered when applying ACLs to a Cisco router? (Choose three.)Place generic ACL entries at the top of the ACL.Place more specific ACL entries at the top of the ACL.Router-generated packets pass through ACLs on the router without filtering.ACLs always search for the most specific entry before taking any filtering action.A maximum of three IP access lists can be assigned to an interface per direction (in or out).An access list applied to any interface without a configured ACL allows all traffic to pass.51What precaution should be considered when the no service password-recovery command has been issued on an IOS device?The passwords in the configuration files are in clear text.IOS recovery requires a new system flash with the IOS image.When the password is lost, access to the device will be terminated.The device must use simple password authentication and cannot have user authentication.52Which three statements describe the IPsec protocol framework? (Choose three.)AH uses IP protocol 51.AH provides encryption and integrity.AH provides integrity and authentication.ESP uses UDP protocol 50.ESP requires both authentication and encryption.ESP provides encryption, authentication, and integrity.53Refer to the exhibit. An administrator has configured router R1 as indicated. However, SDEE messages fail to log. Which solution correctIssue the logging on command in global configuration.Issue the ip ips notify sdee command in global configuration.Issue the ip audit notify log command in global configuration.Issue the clear ip ips sdee events command to clear the SDEE buffer.54Which command would an administrator use to clear generated crypto keys?Router(config)# crypto key decryptRouter(config-line)# transport input ssh clearRouter(config)# crypto key rsaRouter(config)# crypto key zeroize rsa55Refer to the exhibit. Which two statements are correct regarding the configuration on switch S1? (Choose two.)Port Fa0/5 storm control for broadcasts will be activated if traffic exceeds 80.1 percent of the total bandwidth.Port Fa0/6 storm control for multicasts and broadcasts will be activated if traffic exceeds 2,000,000 packets per second.Port Fa0/6 storm control for multicasts will be activated if traffic exceeds 2,000,000 packets per second.Port Fa0/5 storm control for multicasts will be activated if traffic exceeds 80.1 percent of the total bandwidth.Port Fa0/5 storm control for broadcasts and multicasts will be activated if traffic exceeds 80.1 percent of 2,000,000 packets per sec56What functionality is provided by Cisco SPAN in a switched network?It mitigates MAC address overflow attacks.It prevents traffic on a LAN from being disrupted by a broadcast storm.It mirrors traffic that passes through a switch port or VLAN to another port for traffic analysis.It protects the switched network from receiving BPDUs on ports that should not be receiving them.It inspects voice protocols to ensure that SIP, SCCP, H.323, and MGCP requests conform to voice standards.It copies traffic that passes through a switch interface and sends the data directly to a syslog or SNMP server for analysis.57Which three commands are required to configure SSH on a Cisco router? (Choose three.)ip domain-name name in global configuration modetransport input ssh on a vty lineno ip domain-lookup in global configuration modepassword password on a vty lineservice password-encryption in global configuration modecrypto key generate rsa in global configuration mode58Refer to the exhibit. Based on the SDM screen shown, which two conclusions can be drawn about the IKE policy being configured? (ChoIt will use digital certificates for authentication.It will use a predefined key for authentication.It will use a very strong encryption algorithm.It will be the default policy with the highest priority.It is being created using the SDM VPN Quick Setup Wizard.59Which statement describes the SDM Security Audit wizard?After the wizard identifies the vulnerabilities, the SDM One-Step Lockdown feature must be used to make all security-related configuAfter the wizard identifies the vulnerabilities, it automatically makes all security-related configuration changes.The wizard autosenses the inside trusted and outside untrusted interfaces to determine possible security problems that might exist.The wizard is based on the Cisco IOS AutoSecure feature.The wizard is enabled using the Intrusion Prevention task.60What is a feature of the TACACS+ protocol?It combines authentication and authorization as one process.It encrypts the entire body of the packet for more secure communications.It utilizes UDP to provide more efficient packet transfer.It hides passwords during transmission using PAP and sends the rest of the packet in plaintext.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CCNA第一学期Finalexam考试英文版答案(R&S.)C1 A medium-sized business is researching available options for connecting to the Internet. Thecompany is looking for a high speed option with dedicated, symmetric access. Whichconnection type should the company choose?DSLdialupsatelliteleased linecable modem2 What is the purpose of having a converged network? to provide high speed connectivity to all end devicesto make sure that all types of data packets will be treated equallyto achieve fault tolerance and high availability of data network infrastructure devicesto reduce the cost of deploying and maintaining the communication infrastructure3 What characteristic of a network enables it to quickly grow to support new users andapplications without impacting the performance of the service being delivered to existing users?reliabilityscalabilityquality of serviceaccessibility4 Which connection provides a secure CLI session with encryption to a Cisco switch?a console connectionan AUX connectiona Telnet connectionan SSH connection5 A network technician is attempting to configure aninterface by entering the followingcommand: SanJose(config)# ip address 192.168.2.1 255.255.255.0. The command isrejected by the device. What is the reason for this? The command is being entered from the wrong mode of operation.The command syntax is wrong.The subnet mask information is incorrect.The interface is shutdown and must be enabled before the switch will accept the IP address.6 After several configuration changes are made to a router, the copy running-configurationstartup-configuration command is issued. Where will the changes be stored?flashROMNVRAMRAMthe configuration registera TFTP server7Refer to the exhibit. From global configuration mode, an administrator is attempting to create a message-of-the-day banner by using thecommand banner motd V Authorized access only! Violators will be prosecuted! V When users log in using Telnet, the banner does not appear correctly. What is the problem?The banner message is too long.The delimiting character appears in the banner message.The symbol “!”signals the end of a banner message.Message-of-the-day banners will only appear when a user logs in through the console port.8 What are three characteristics of an SVI? (Choose three.)It is designed as a security protocol to protect switchports.It is not associated with any physical interface on a switch.It is a special interface that allows connectivity by different types of media.It is required to allow connectivity by any device at any location.It provides a means to remotely manage a switch.It is associated with VLAN1 by default.9 A technician configures a switch with these commands:SwitchA(config)# interface vlan 1SwitchA(config-if)# ip address 192.168.1.1 255.255.255.0SwitchA(config-if)# no shutdownWhat is the technician configuring?Telnet accessSVIpassword encryptionphysical switchport access10 In computer communication, what is the purpose of message encoding?to convert information to the appropriate form for transmissionto interpret informationto break large messages into smaller framesto negotiate correct timing for successful communication11 What protocol is responsible for controlling the size of segments and the rate at whichsegments are exchanged between a web client and a web server?TCPIPHTTPEthernet12 What are two benefits of using a layered network model? (Choose two.)It assists in protocol design.It speeds up packet delivery.It prevents designers from creating their own model.It prevents technology in one layer from affecting other layers.It ensures a device at one layer can function at the next higher layer.13 What is the process of dividing a data stream into smaller pieces before transmission?segmentationencapsulationencodingflow control14 When IPv4 addressing is manually configured on aweb server, which property of the IPv4 configuration identifies the network and host portion for an IPv4 address?DNS server addresssubnet maskdefault gatewayDHCP server address15 A network administrator is troubleshooting connectivity issues on a server. Using a tester, the administrator notices that the signals generated by the server NIC are distorted and not usable. In which layer of the OSI model is the error categorized? presentation layernetwork layerphysical layerdata link layer16 A network engineer is measuring the transfer of bits across the company backbone for amission critical database application. The engineer notices that the network throughputappears lower than the bandwidth expected. Which three factors could influence thedifferences in throughput? (Choose three.)the amount of traffic that is currently crossing the networkthe sophistication of the encapsulation method applied to the datathe type of traffic that is crossing the networkthe latency that is created by the number of network devices that the data is crossingthe bandwidth of the WAN connection to the Internetthe reliability of the gigabit Ethernet infrastructure of the backbone17 Which type of UTP cable is used to connect a PC to a switch port?consolerollovercrossoverstraight-through18 What is a characteristic of the LLC sublayer?It provides the logical addressing required that identifies the device.It provides delimitation of data according to the physical signaling requirements of the medium.It places information in the frame allowing multiple Layer 3 protocols to use the same network interface and media.It defines software processes that provide services to the physical layer.19 What are the three primary functions provided by Layer 2 data encapsulation? (Choosethree.)error correction through a collision detection methodsession control using port numbersdata link layer addressingplacement and removal of frames from the mediadetection of errors through CRC calculationsdelimiting groups of bits into framesconversion of bits into data signals20 What will a host on an Ethernet network do if it receives a frame with a destination MACaddress that does not match its own MAC address?It will discard the frame.It will forward the frame to the next host.It will remove the frame from the media.It will strip off the data-link frame to check the destination IP address.21 What are two actions performed by a Cisco switch? (Choose two.)building a routing table that is based on the first IP address in the frame headerusing the source MAC addresses of frames to build and maintain a MAC address tableforwarding frames with unknown destination IP addresses to the default gatewayutilizing the MAC address table to forward frames via the destination MAC addressexamining the destination MAC address to add new entries to the MAC address table22 What are two examples of the cut-through switching method? (Choose two.)store-and-forward switchingfast-forward switchingCRC switchingfragment-free switchingQOS switching23Refer to the exhibit.If host A sends an IP packet to host B, what will the destination address be in the frame when it leaves host A?DD:DD:DD:DD:DD:DD172.168.10.99CC:CC:CC:CC:CC:CC172.168.10.65BB:BB:BB:BB:BB:BBAA:AA:AA:AA:AA:AA24 What are two services provided by the OSI network layer? (Choose two.)performing error detectionrouting packets toward the destinationencapsulating PDUs from the transport layerplacement of frames on the mediacollision detection25 What information is added during encapsulation at OSI Layer 3?source and destination MACsource and destination application protocolsource and destination port numbersource and destination IP address26 What are two functions of NVRAM? (Choose two.) to store the routing tableto retain contents when power is removedto store the startup configuration fileto contain the running configuration fileto store the ARP table27Refer to the exhibit. The network administrator for a small advertising company has chosen to use the 192.168.5.96/27 network for internal LAN addressing. As shown in the exhibit, a static IP address is assignedto the company web server. However, the web server cannot access the Internet. The administrator verifies that local workstations with IP addresses that are assigned by a DHCP server can access the Internet, and the web server is able to ping local workstations. Which component is incorrectly configured?subnet maskDNS addresshost IP addressdefault gateway address28 Why does a Layer 3 device perform the ANDing process on a destination IP address andsubnet mask?to identify the broadcast address of the destination networkto identify the host address of the destination hostto identify faulty framesto identify the network address of the destinationnetwork29 What are the three ranges of IP addresses that are reserved for internal private use? (Choosethree.)10.0.0.0/864.100.0.0/14127.16.0.0/12172.16.0.0/12192.31.7.0/24192.168.0.0/1630 Which three addresses are valid public addresses? (Choose three.)198.133.219.17192.168.1.24510.15.250.5128.107.12.117192.15.301.24064.104.78.22731 What type of IPv6 address is FE80::1?loopbacklink-localmulticastglobal unicast32Refer to the exhibit. On the basis of the output, which two statements about network connectivity are correct? (Choose two.)There is connectivity between this device and the device at 192.168.100.1.The connectivity between these two hosts allows for videoconferencing calls.There are 4 hops between this device and the device at 192.168.100.1.The average transmission time between the two hosts is 2 milliseconds.This host does not have a default gateway configured.33 Which subnet would include the address 192.168.1.96 as a usable host address?192.168.1.64/26192.168.1.32/27192.168.1.32/28192.168.1.64/2934 How many hosts are addressable on a network that has a mask of 255.255.255.248?268141625435 Which statement is true about variable-length subnet masking?Each subnet is the same size.The size of each subnet may be different, depending on requirements.Subnets may only be subnetted one additional time.Bits are returned, rather than borrowed, to create additional subnets.36Refer to the exhibit. Consider the IP address of 192.168.10.0/24 that has been assigned to a high school building. The largest network in this building has 100 devices. If 192.168.10.0 is the network number for the largest network, what would be the network number for the next largest network, which has 40 devices?192.168.10.0192.168.10.128192.168.10.192192.168.10.224192.168.10.24037 In what two situations would UDP be the preferred transport protocol over TCP? (Choosetwo.)when applications need to guarantee that a packet arrives intact, in sequence, and unduplicatedwhen a faster delivery mechanism is neededwhen delivery overhead is not an issuewhen applications do not need to guarantee delivery of the datawhen destination port numbers are dynamic38 What important information is added to the TCP/IP transport layer header to ensurecommunication and connectivity with a remote network device?timing and synchronizationdestination and source port numbersdestination and source physical addressesdestination and source logical network addresses39 What is the TCP mechanism used in congestion avoidance?three-way handshakesocket pairtwo-way handshakesliding window40 Which three statements characterize UDP? (Choose three.)UDP provides basic connectionless transport layer functions.UDP provides connection-oriented, fast transport of data at Layer 3.UDP relies on application layer protocols for errordetection.UDP is a low overhead protocol that does not provide sequencing or flow control mechanisms.UDP relies on IP for error detection and recovery.UDP provides sophisticated flow control mechanisms.41 Which two tasks are functions of the presentation layer? (Choose two.)compressionaddressingencryptionsession controlauthentication42 Which two protocols operate at the highest layer of the TCP/IP protocol stack? (Choose two.)DNSEthernetIPPOPTCPUDP43 Which two roles can a computer assume in a peer-to-peer network where a file is beingshared between two computers? (Choose two.)clientmasterserverslavetransient44 What is the function of the HTTP GET message?to request an HTML page from a web serverto send error information from a web server to a web clientto upload content to a web server from a web clientto retrieve client email from an email server using TCP port 11045 A wireless host needs to request an IP address. What protocol would be used to process therequest?FTPHTTPDHCPICMPSNMP46 When planning for network growth, where in the network should packet captures take place toassess network traffic?on as many different network segments as possibleonly at the edge of the networkbetween hosts and the default gatewayonly on the busiest network segment47 When applied to a router, which command would help mitigate brute-force password attacksagainst the router?exec-timeout 30service password-encryptionbanner motd $Max failed logins = 5$login block-for 60 attempts 5 within 6048Refer to the exhibit.An administrator is testing connectivity to a remote device with the IP address 10.1.1.1. What does the output of this command indicate?Connectivity to the remote device was successful.A router along the path did not have a route to the destination.A ping packet is being blocked by a security device along the path.The connection timed out while waiting for a reply from the remote device.。
