CCIE模拟考试题_思科认证考试.doc
CISCO 真题word精品文档14页

CCNA、CCNP、CCIE模拟试题CCNA1.Which of the following types of packets will be allowed entr y when a serial interface's inbound access list has been config ured to prohibit entry for TCP and UDP ports 21, 23 and 25? (Se lect three options.)A. SMTPB. STPC. FTPD. TelnetE. HTTPF. POP32.One of the trainees assigned to you want to know which servic es use TCP. What can you tell him? (Select three options.)A. DHCPB. SMTPC. SNMPD. FTPE. HTTPF. TFTP3.Which of the following network masks would you use to reduce any wastage of IP addresses in point-to- point WAN links on a n etwork that supports VLSM?A. /38B. /30C. /27D. /23E. /184.How would you configure a router to avoid situations s uch as split horizon issues hampering routing updates on a Fram e Relay network?A. Configure a separate sub-interface for each PVC with a uniqu e DLCI and subnet assigned to the subinterface.B. Configure each Frame Relay circuit as a point-to-point line to support multicast and broadcast traffic.C. Configure one sub-interface to disperse into multiple PVC co nnections to multiple remote router interfaces.D. Configure as many as possible sub-interfaces on the same sub net.5.With regard to ISDN, which of the following are true? (Choose all that apply.)A. Legacy DDR can use port information to define interesting tr affic.B. Legacy DDR can configure multiple dialer configurations on t he same interface.C. Legacy DDR can use ACLs to define interesting traffic.D. HDLC or PPP can be used to encapsulate ISDN D channel inform ation.E. The BRI interfaces on ISDN routers with dialer profiles conf igured cannot belong to multiple dialer pools.F. Dialer profiles cannot use ACLs to define interesting traffi c.CCNP- BSCI6.Which of the following is a characteristic of link-sta te protocols?A. A network topology change generates an update that is broadc ast to every router onthe network.B. The periodic routing update interval is slightly different i n each router on a subnet.C. Each router creates a routing table that only includes its d irectly connected neighbors.D. Link-state protocols send routing updates only when there is a change in the networktopology.7.What is the term associated with synchronizing the rou ting tables after a topology change occurs?A. floodingB. broadcastingC. convergenceD. summarization8.Which of the following must be determined first by the router in order to route the data?A. the distance metric of the dataB. the source address of the dataC. which routing protocol is used by the dataD. whether the protocol suite of the data is active9.You are a technician at ABC. ABC has the subnet/mask of 172.29.100.0/26 set aside for small remote locations. Each lo cation will have 5 IP devices connected to the network. Which V LSM mask will provide the minimum number of hosts you require?A. /27B. /28C. /29D. /30E. /3110.You are a trainee technician at ABC. Your instructor shows you the following route summarization entry:192.168.134.0/22 Your instructor wants to know how many class C addresses are contained in this summarization. What would your reply be?A. 1B. 2C. 4D. 8E. 16- BCMSN11.Which command enables an EtherChannel bundle on a Cat alyst 2900XL switch?A. Port groupB. Set port channel onC. Port etherchannel enableD. Set etherchannel port enable12.Which two statements about dynamic VLANs are true? (C hoose two)A. Each switch port is assigned to a specific VLAN.B. Dynamic VLANs require a VLAN Membership Policy Server.C. Devices are in the same VLAN regardless of which port they a ttach to.D. Dynamic VLAN assignment are made through the command interfa ce.13.Which statement is correct about 802.1Q trunking? (Se lect all that apply)A. Both switches must be in the same VTP domain.B. The encapsulation type of both ends of the trunk does not ha ve to match.C. The native VLAN on both ends of the trunk must be VLAN 1.D. 802.1Q trunking can only be configured on a Layer 2 port.E. In 802.1Q trunking, all VLAN packets are tagged on the trunk link, except the native VLAN.14.You need to take advantage of FastEthernet ports. Whi ch two actions avoid configuration problems that cause the port to be automatically disabled? (Choose two)A. Allow some ports in a channel to be disabled.B. Configure the ports in a channel as dynamic VLAN ports.C. Configure all ports in a channel to operate at the same spee d and duplex mode.D. Assign all ports in a channel to the same VLAN or configure them as trunk ports.15.What is the cause of jitter?A. Variable queue delaysB. Packet dropsC. Transmitting too many small packetsD. Compression- BCRAN16.Regarding DHCP, DHCP relay and DHCP server are mutual ly exclusive.A. None of the choices.B. TrueC. False only for certain IOS versionD. FalseE. False only for IOS version below V1017.A LAPD Address field can be 1 or 2 bytes long.A. TrueB. FalseC. True only in the USD. True only in AsiaE. True only in Europe18.Which of the following are valid functions of the loc k DTE modem attribute (Choose all that apply)?A. Disable UART.B. Enable UART.C. Locks the data speed between the computer motherboard and th e RS232 port.D. Locks the data speed between the modem and the DTE device.19.Which of the following are not the valid types of ATM addresses (Choose all that apply)?A. DCCB. GCTC. BSPD. ICDE. NSAPF. AED20.Which of the following are NOT the valid types of X.25 PLP packet fields (Choose all that apply)?A. User DataB. LCIC. GFID. PTIE. None of the choices.- CIT21.You are a technician at ABC. Your newly appointed ABC trainee wants to know what the similarities between Topology D iagrams and Network Configuration Tables are.What would your reply be? (Choose all that apply.)A. Both share few components.B. Both share many of the same components.C. Both define physical memory components.D. Both are used for troubleshooting.E. Both use lines and symbols to represent network components.22.You are a technician at ABC. Your newly appointed ABC trainee wants to know what the default action for the output o f debug and system error messages is. What would your reply be?A. Output goes to the remote console if logging is off.B. Output is sent to the console terminal.C. Error logging automatically invokes debug output to the desi gnated TFTP server.D. Output configuration requires a TFTP server to write filesE. Output is written to a Syslog server.23.You are the network administrator at ABC. ABC has a s witched network. You want to control the designation of the spa nning-tree root bridge in the ABC network. What should you do?A. By enabling uplink-fast on the ports of the desired switch.B. By lowering the bridge priority on the desired switch.C. By setting a lower MAC address on the designated switch.D. By raising the bridge ID on one switch.24.You are a technician at ABC. You receive a report from several ABC users who complain that they get slow responses whe n sending and receiving email, especially when browsing the Int ernet. You investigate the complaint by checking the output of a ping command issued from her computer and find that it indica tes intermitted success and failures messages, when attempting to contact the email server. A tracert to the corporate Interne t gateway router shows high latency and occasional time out mes sages.What would be the most effective troubleshooting approach if yo u are to determine the cause of the slow response time?A. Bottom-up approachB. Random access approachC. Divide and conquer approachD. Top-down approachE. Top-down rule-out approach25.You are a technician at ABC. Your newly appointed ABC trainee wants to know what features make OSPF more suitable than RP in large network installations. What would your reply be? (Choose all that apply.)A. Diffusing Update AlgorithmB. No hop count limitationC. Higher routing update overheadD. Faster convergenceE. Lower routing update overheadCCIE26.You are the network administrator at ABC. You are tro ubleshooting a network problem. You want to trace the route to a Unix workstation that you want to reach through the Internet. However, Traceroute does not work.Currently, there is an inbound access-list applied to the seria l interface on Router 1. An entry in the access-list states "ac cess-list 101 permit tcp any any". What access-list entry may y ou need to be added to the access-list in order to get tracerou te to work?A. access-list 101 permit udp any anyB. access-list 101 permit icmp any any time-exceeded access-lis t 101 permit icmp any any port-unreachableC. access-list 101 permit icmp any any time-exceeded access-lis t 101 permit icmp any any net-unreachableD. access-list 101 permit icmp any any echo access-list 101 per mit icmp any any net-unreachableE. access-list 101 permit udp any any access-list 101 permit ic mp any any protocol-unreachable27.What does the BGP backdoor command do?A. It changes the distance of an iBGP route to 20.B. It changes the distance of an eBGP route to 200.C. It changes the distance of an IGP route to 20.D. It does not effect any changes in distance of the route.E. It changes the distance of an IGRP route to 200.28.Which of the following DNS resource records is not va lid?A. NSB. PTRC. MXD. FQDNE. A29.Which of the following features is provided by RIP v2 that were previously not possible with RIP v1? (Choose all tha t apply.)A. Classless routing and split-horizon.B. Poison reverse and updating to multicast addresses.C. Poison reverse and classless routing.D. Classless routing and updating to multicast addresses.E. Route tag and classless routing.30.Which of the following statements is valid when taking Custom Queuing into account?A. Custom queuing has the ability to restrict a particular type of traffic to a given bandwidth not matter what is load is lik e on that link.B. Custom queuing looks at groups of packets from the similar s ource-destination pairs.C. Custom queuing will not proceed to a next queue unless the c urrent queue is empty.D. Custom queuing can prevent one type of traffic from dominati ng a busy link.希望以上资料对你有所帮助,附励志名言3条:1、宁可辛苦一阵子,不要苦一辈子。
思科认证640-802模拟试卷27(题后含答案及解析)

思科认证640-802模拟试卷27(题后含答案及解析) 题型有:1. 单选题 2. 多选题单选题1.Refer to the exhibit.The show vtp status command is executed at a switch that is generating the exhibited output.Which statement is true for this switch?A.The switch forwards its VLAN database to other switches in the ICND VTP domain.B.The configuration revision number increments each time the VLAN database is updated.C.The switch forwards VTP updates that are sent by other switches in the ICND domain.D.The VLAN database is updated when VTP information is received from other switches.正确答案:C解析:VTP是为了动态学习和同步VLAN信息的,但是他的同步和学习都是以域为单位的,只有同一个域中的VLAN信息才可以同步和学习。
而VTP的模式有三种:server , client , transparent。
其中transparent模式为通明桥的模式,在这种模式下的VLAN的信息是不能被其他设备学习到的,而切这种模式下的设备也不学习其他设备的VLAN信息,他只是转发VLAN的信息,但是不学习。
2.A Cisco router is booting and has just completed the POST process.It is now ready to find and load an IOS image.What function does the router perform next?A.It checks the configuration register.B.It attempts to boot from a TFTP server.C.It loads the first image file in flash memory.D.It inspects the configuration file in NVRAM for boot instructions.正确答案:A3.What is the function of the command switchport trunk native vlan 999 on a Cisco Catalyst switch?A.It creates a VLAN 999 interface.B.It designates VLAN 999 for untagged traffic.C.It blocks VLAN 999 traffic from passing on the trunk.D.It designates VLAN 999 as the default for all unknown tagged traffic.正确答案:B解析:native vlan是不打标签的VLAN,这指定native vlan 为999,表明VLAN 999为不用打标签的VLAN4.When a new trunk is configured on a 2950 switch, which VLANs by default are allowed over the trunk link?A.no VLANsB.all VLANsC.only VLANs 1 - 64D.only the VLANs that are specified when creating the trunk正确答案:B解析:Trunk上默认是可以转发所有VLAN的数据的。
思科认证640-802模拟试卷6(题后含答案及解析)

思科认证640-802模拟试卷6(题后含答案及解析) 题型有:1. 单选题 2. 多选题 3. 不定项选择题单选题1.The network administrator has configured port security on a Ezonexam switch. Why would a network administrator configure port security on this Ezonexam device?A.To prevent unauthorized hosts from getting access to the LANB.To limit the number of Layer 2 broadcasts on a particular switch portC.To prevent unauthorized Telnet or SSH access to a switch portD.To prevent the IP and MAC address of the switch and associated portsE.None of the above正确答案:A解析:Explanation:You can use the port security feature to restrict input to an interface by limiting and identifying MAC addresses of the stations allowed to access the port. When you assign secure MAC addresses to a secure port, the port does not forward packets with source addresses outside the group of defined addresses. If you limit the number of secure MAC addresses to one and assign a single secure MAC address, the workstation attached to that port is assured the full bandwidth of the port.If a port is configured as a secure port and the maximum number of secure MAC addresses is reached, when the MAC address of a station attempting to access the port is different from any of the identified secure MAC addresses, a security violation occurs. Also, if a station with a secure MAC address configured or learned on one secure port attempts to access another secure port, a violation is flagged.2.You are a senior network administrator at Ezonexam, and while performing the password recovery procedure on your 2500 series Cisco router, you type in the following command:o/r 0x2142What is the purpose of this command?A.It is used to restart the router.B.It is used to bypass the configuration in NVRAM.C.It is used to enter ROM Monitor mode.D.It is used to view the lost password.E.It is used to save the changes to the configuration.正确答案:B解析:Explanation:Theo/r 0x2142 command changes the value of config-register to 2142 in a Cisco 2500 series router, so that the Router ignores the NVRAM contents and reverts to the initial setup configuration mode when it boots.3.Why might the Ezonexam network administrator set the configuration register to 0x2142 on a 2600 series Cisco router?A.To boot the IOS from ROMB.To reset the console passwordC.To upload a new version of the configuration fileD.To upload a new version of the IOSE.To allow a new memory upgrade to be recognized by the router正确答案:B解析:Explanation:About 99 percent of the time someone uses a config-register, it’s more than likely because of a lost router password. The two config-registers for recovering passwords are 0x2102 and 0x2142.The first config-register, 0x2102, is the normal config-register if you boot the router from internal Flash. You can see this config-register by using the show version command.In this output, you’ll notice the last line says, “Configuration register is 0x2102.”This is normal.But let’s say you forgot the router’s password. To recover this password (as long as it’s unencrypted), boot the router and bypass the startup-config using config-register 0x2142; you should then be able to see the password in the startup-config. You can use the same method for encrypted passwords, but you’ll need to overwrite the original password with a new one. To change the configuration register, enter the following:Router(config)# config-register 0x2142This will instruct the router to bypass the configuration and boot up as if it were a brand new router using factory default settings.4.While troubleshooting an issue in the Ezonexam LAN you notice that a network interface port has collision detection and carrier sensing enabled on a shared twisted pair network. From this statement, what is known about the network interface port?A. This is an Ethernet port operating at half duplexB. This is an Ethernet port operating at full duplexC. This is a port on a network interface card in a PCD. This is 10 MB/s switch portE. This is a 100 MB/s switch portF. None of the above正确答案:A5.Why would the Ezonexam administrator change the value of the spanning-tree priority of a switch?A. in order to optimize the path that frames take from source to destinationB. to increase the priority so a designated port will become a root portC. to increase the BID, so the switch is more likely to become root bridgeD. in order to allow VLANs to be sent from one switch to another across a single linkE. to force a given switch to become an STP serverF. None of the above正确答案:A解析:Explanation:The Bridge Priority is used to measure the preference of a bridge in the spanning-tree Algorithm. The possible values range between 0 and65,535. The default setting is 32,768. By adjusting the priority, the root bridge can be manually assigned to meet the needs of the network administrator.6.After working on a router, some problems arise and you wish to view the commands that you recently entered. Which IOS command opens the history buffer and displays the most recently entered commands?A. Show historyB. Show buffersC. Show typed commandsD. Show terminal bufferE. Show commandF. None of the above正确答案:A解析:Explanation:The router will buffer previously entered commands. By default, the “show history”command will display the previous ten commands that were entered. To see the contents of the buffer you enter the show history command.Incorrect Answers:B. This command will show the memory buffer informationC, D. These are invalid commands.7.A network administrator wants to control which user hosts can access the network based on their MAC address. What will prevent workstations with unauthorized MAC addresses from connecting to the network through a switch?A. BPDUB. Port securityC. RSTPD. STPE. VTPF. Blocking mode正确答案:B解析:Explanation:Understanding How Port Security Works:You can use port security to block input to an Ethernet, Fast Ethernet, or Gigabit Ethernet port when the MAC address of the station attempting to access the port is different from any of the MAC addresses specified for that port. Alternatively, you can use port security to filter traffic destined to or received from a specific host based on the host MAC address.When a secure port receives a packet, the source MAC address of the packet is compared to the list of secure source addresses that were manually configured or autoconfigured (learned) on the port. If a MAC address of a device attached to the port differs from the list of secure addresses, the port either shuts down permanently (default mode), shuts down for the time you have specified, or drops incoming packets from the insecure host.The port’s behavior depends on how you configure it to respond to a security violation. If a security violation occurs, the Link LED for that port turns orange, and a link-down trap is sent to the Simple Network Management Protocol (SNMP) manager. An SNMP trap is not sent if you configure the port for restrictive violation mode. A trap is sent only if you configure the port to shut down during a security violation.8.Which OSI layer is associated with the following: The acknowledgement of transmissions, sequencing, and flow control across a network?A. Layer 2B. Layer 3C. Layer 4D. Layer 5E. Layer 6F. Layer 7正确答案:C解析:Explanation:The Transport layer (Layer 4) defines several functions, including the choice of protocols. The most important Layer 4 functions are error recovery and flow control. The transport layer may provide for retransmission, i.e., error recovery, and may use flow control to prevent unnecessary congestion by attempting to send data at a rate that the network can accommodate, or it might not, depending on the choice of protocols. Multiplexing of incoming data for different flows to applications on the same host is also performed. Reordering of the incoming data stream when packets arrive out of order is included. Examples include: TCP, UDP, and SPX.9.You need to configure two Ezonexam switches to exchange VLAN information. Which protocol provides a method of sharing VLAN configuration information between these two switches?A. STPB. 802.1QC. VLSMD. ISLE. VTPF. HSRPG. None of the above正确答案:E解析:Explanation:VLAN Trunking Protocol (VTP) is a Cisco proprietary Layer2 messaging protocol that manages the addition, deletion, and renaming of VLANs ona network-wide basis. Virtual Local Area Network (VLAN) Trunk Protocol (VTP) reduces administration in a switched network. When you configure a new VLAN on one VTP server, the VLAN is distributed through all switches in the domain. This reduces the need to configure the same VLAN everywhere. To do this VTP carries VLAN information to all the switches in a VTP domain. VTP advertisements can be sent over ISL, 802.1q, IEEE 802.10 and LANE trunks. VTP traffic is sent over the management VLAN (VLAN1), so all VLAN trunks must be configured to pass VLAN1. VTP is available on most of the Cisco Catalyst Family products.10.Which Layer 4 protocol is used for a Telnet connection between two Ezonexam routers?A. IPB. ICMPC. DNSD. TCPE. UDPF. RTP正确答案:D解析:Explanation:TCP is a reliable connection-oriented protocol. TCP uses acknowledgments, sequencing, and flow control to ensure reliability. Telnet uses TCP port 23.11.You are trying to connect directly into the LAN prot of a Ezonexam router. You want to telnet to the local Cisco router using TCP/IP but cannot create a session.What should you do to resolve the problem?A. Use a straight-through cable to connect your computer’s COM port to the router’s console port.B. Use a crossover cable to connect your computer’s COM port to the router’s console port.C. Use a straight-through cable to connect your computer’s COM port to the router’s Ethernet port.D. Use a crossover cable to connect your computer’s Ethernet port to the router’s Ethernet port.E. Use a rollover cable to connect your computer’s Ethernet port to the router’s Ethernet port.F. Use a straight-through cable to connect your computer’sEthernet port to the router’s Ethernet port.G. None of the above正确答案:D解析:Explanation:In order to connect directly to a router via telnet, you must connect to the router via one of the LAN ports. When connecting directly to the Ethernet port with a PC without the use of a switch or hub, a crossover cable must be used.Incorrect Answers:A, B, C. In order to telnet directly into the router via a TCP/IP connection, the COM port of the PC can not be used. The COM port is used for direct terminal emulation programs such as HyperTerminal.E. Rollover cables are used for console connections into the router, not for TCP/IP connections.F. Straight through cables are used for connections into a switch or hub from the PC. It will not work for direct Ethernet connections into the router.12.You are unable to telnet to a router at address 203.125.12.1 from a workstation with the IP address 203.125.12.23. You suspect that there is a problem with the IP protocol stack in your PC. Which of the following actions is most likely to confirm your diagnosis?A. ping 127.0.0.0B. ping 203.125.12.1C. telnet 127.0.0.1D. ping 127.0.0.1E. tracert 203.125.12.1F. None of the above正确答案:D解析:Explanation:Every Windows based PC uses the 127.0.0.1 as the local loopback IP address. Every PC will respond to this local IP address if the TCP/IP stack is correctly installed and running on the machine. If you cannot ping the loopback address of 127.0.0.1, then something is wrong with the TCP/IP protocol stack多选题13.How could the Ezonexam corporation benefit from using VLANs on their network?(Select three answer choices.)A. VLANs allow access to network services based on department, not physical location.B. VLANs utilize packet filtering to enhance network security.C. VLANs provide a low-latency, high bandwidth internetworking alternative.D. VLANs provide a method of communication between IP addresses in large networks.E. VLANs establish segmented broadcast domains in switched networks.F. VLANs can greatly simplify adding, moving, or changing hosts on the network.正确答案:A,E,F解析:Explanation:VLANs establish broadcast domains in switched networks, so by virtue of having the option to create many efficient broadcast domains, congestion is reduced and network throughput is greatly enhanced. VLANs allow networks to be divided by department or resource needs, rather then by physical location. When people move departments, leave a department, or join a department, administration iseasy and convenient with a few keystrokes.Incorrect Answers:B, D. These would be router functions at layer 3. Switches and VLANs operate at layer 2 of the OSI model.C. The use of VLANs may actually increase the latency in some cases, as traffic from one VLAN to the other will need to be routed.14.An administrator would like to configure a switch over a virtual terminal connection from locations outside of the local LAN. Which of the following are required in order for the switch to be configured from a remote location? (Choose two)A. The switch must be reachable through a port connected to its management VLAN.B. The switch console port must be connected to the Ethernet LAN.C. The switch must be fully configured as an SNMP agent.D. The switch must be configured with an IP address, subnet mask, and default gateway.E. The switch management VLAN must be created and have a membership of at least one switch port.F. The switch must be connected to a router over a VLAN trunk.正确答案:A,D解析:Explanation:In order the telnet to any Cisco device, the device must be reachable from the remote location. For a Cisco switch to be reachable from remote locations, it must have an IP address, subnet mask, and default gateway munication with the switch management interfaces is through the switch IP address.The IP address is associated with the management VLAN, which by default is VLAN 115.Ezonexam has implemented the use of VLANs in their network. Which of the following are considered to be a benefit of VLANs? (Choose three)A. They increase the size of collision domains.B. They allow logical grouping of users by function.C. They can enhance network security,D. The increase the size of broadcast domains while decreasing the number of the broadcast domains.E. The increase the number of broadcast domains while decreasing the size of the broadcast domains.F. They simplify switch administration.正确答案:B,C,E解析:Explanation:There are many motivations for using VLANs, including these:1. To group users by department, or by groups that work together, instead of by physical location. (B)2. To reduce overhead by limiting the size of each broadcast domain (E)3. To enforce better security by keeping sensitive devices on a separate VLAN (C)4. To separate specialized traffic from mainstream traffic - for example, putting IP telephones on a separate VLAN form user PCs.16.Which encapsulation types are configurable on a Cisco switch for a trunk? (Select two answer choices)A. VTPB. ISLC. CDPD. 802.1QE. 802.1pF. LLCG. IETF正确答案:B,D解析:Explanation:Trunks are used to carry traffic belonging to multiple VLANsbetween devices over the same link. A device can determine which VLAN the traffic belongs to by its VLAN identifier. The VLAN identifier is a tag that is encapsulated with the data. ISL and 802.1q are two types of encapsulations used to carry data from multiple VLANs over trunk links. ISL is a Cisco proprietary protocol for interconnecting multiple switches and maintaining VLAN information as traffic goes between switches. ISL provides VLAN trunking capabilities while maintaining full wire speed performance on Ethernet links in full-duplex or half-duplex mode. ISL operates in a point-to-point environment and will support up to 1000 VLANs. In ISL, the original frame is encapsulated and an additional header is added before the frame is carried over a trunk link. At the receiving end, the header is removed and the frame is forwarded to the assigned VLAN. .ISL uses Per VLAN Spanning Tree (PVST) which runs one instance of Spanning Tree Protocol (STP) per VLAN. PVST allows for optimal root switch placement for each VLAN and supports load balancing of VLANs over multiple trunk links. 802.1Q is the IEEE standard for tagging frames on a trunk and supports up to 4096 VLANs. In 802.1Q, the trunking device inserts a four-byte tag into the original frame and re-computes the Frame Check Sequence (FCS) before sending the frame over the trunk link. At the receiving end, the tag is removed and the frame is forwarded to the assigned VLAN. 802.1Q does not tag frames on the native VLAN. It tags all other frames transmitted and received on the trunk. While configuring a 802.1 trunk, you must make sure that the same native VLAN is configured on both sides of the trunk. IEEE 802.1Q defines a single instance of spanning tree running on the native VLAN for all the VLANs in the network which is called Mono Spanning Tree (MST). This lacks the flexibility and load balancing capability of PVST available with ISL. However, PVST+ offers the capability to retain multiple Spanning Tree topologies with 802.1Q trunking.不定项选择题17.A new switch is installed in the Ezonexam network. This switch is to be configured so that VLAN information will be automatically distributed to all the other Cisco Catalyst switches in the network.Which of the conditions below have to be met in order for this to occur? (Choose all that apply).A. The switch that will share the VLAN information must be in the VTP Server mode.B. The switches must be in the same VTP domain.C. The switch that will share the VLAN information must be configured as the root bridge.D. The switches must be configured to use the same VTP version.E. The switches must be configured to use the same STP version.F. The switches must be configured to use the same type of ID tagging.G. The switches must be connected over VLAN trunks.正确答案:A,B,F,G解析:Explanation:For the VLAN information to pass automatically throughout the network, VTP must be set up correctly. In order for VTP to work, a VTP server is needed, the VLAN’s must be in the same VTP domain, and the encapsulation on eachend of the trunk must both set to either 802.1Q or ISL.Incorrect Answers:C. Root bridges and other functions of the Spanning Tree Protocol (STP) have no impact of the VTP configuration.D, E. There is only one version of VTP and STP.18.Which of the following correctly describe the various functions and virtues of a router? (Select all valid answer choices)A. Packet switchingB. Collision prevention on a LAN segment.C. Packet filteringD. Broadcast domain enlargementE. Broadcast forwardingF. Internetwork communicationG. None of the above 正确答案:A,C,F解析:Explanation:The main function of a router is to connect different, separated networks together. In doing so, switching packets from one network to another is a primary function, along with providing for communication between networks. As an additional feature, routers are capable of providing filtering on a network address and application port level, so choice C is also correct.Incorrect Answers:B. Routers can indeed be used to segment a network separate a collision domain, since routers do not forward LAN broadcasts and multicasts to other interfaces. However, routers alone can not prevent all collisions from occurring on any given LAN segment.D. Routers actually segment LANs into smaller broadcast domains.E. Routers do not forward broadcast and multicast traffic out the additional interfaces by default. Unless bridging or IP helpers are configured on the router, LAN broadcasts are blocked at the router level.19.You have a class B network with a 255.255.255.0 mask. Which of the statements below are true of this network? (Select all valid answers)A. There are 254 usable subnets.B. There are 256 usable hosts per subnet.C. There are 50 usable subnets.D. There are 254 usable hosts per subnet.E. There are 24 usable hosts per subnet.F. There is one usable network.正确答案:A,D解析:Explanation:The default subnet mask for Class B is 255.255.0.0. Thus an extra 8 bits have been used for the network portion, leaving 8 for hosts. The 2n - 2 formula (28 - 2 in this case for both the network and IP hosts) gives us 254 networks and 254 hosts per network.Incorrect Answers:B: We must remember to always subtract 2 (one for the network, and one for the broadcast) so the result is 254, not 256.C, E: No possible network mask would give us this exact number of subnets or hosts.F: This would be true if this were a class C network, not a class B.20.When a switch port is used as a VLAN trunk, which of the following trunk modes are valid? (Select all that apply.)A. BlockingB. AutoC. DesirableD. OnE. TransparentF. Learning正确答案:B,C,D解析:Explanation:A trunk port can be configured as one of the following 5different modes: on, off, desirable, auto, or nonegotiate.The table below is a summary of the configuration modes.。
思科认证考试试题

思科认证考试试题该公司针对其产品的网络规划和网络支持推出了工程师资格认证计划(Cisco Career Certification Program,简称CCCP),并要求其在各国的代理拥有这样的工程师,以提高对用户的'服务质量,建立Cisco产品网络工程师的资格认证体系。
ip classlessip default-network 198.0.18.0ip route 0.0.0.0 0.0.0.0 198.0.18.5ip http serverRTR_1#show ip route192.168.36.0/30 is subnetted, 1 subnetsC 192.168.36.12 is directly connected, Serial 0/0192.168.60.0/24 is variably subnetted, 5 subnets, 2 masksC 192.168.60.24/30 is directly connected, Serial0/1D 192.168.60.128/28 [ 90/21026560 ] via 192.168.60.26, 00:00:57, Serial 0/1D 192.168.60.144/28 [ 90/21026560 ] via 192.168.60.26, 00:00:57, Serial 0/1D 192.168.60.96/28 [ 90/21026560 ] via 192.168.36.14, 00:00:57, Serial 0/0192.168.77.0/30 is subnetted, 1 subnetsC 192.168.77.32 is directly connected, FastEthernet0/0C 192.0.18.0/24 is directly connected, Serial 1/0*S 0.0.0.0 via 198.0.18.5Explanation:Step1:Identify the faults in configuration on RTR_1 and RTR_2. As the SIM specifies all other inter connectivity and internet access for the existing locations of the company are working properly.Routing Protocols used in the SIM is EIGRP with AS 212 as provided by exhibit.Faults Identified:Wrong AS (EIGRP 22) provided at RTR_2 (New router)RTR_1 does not advertise the new network between RTR_1 and RTR_2 into EIGRP.We need to correct the above two configuration mistakes to have full connectivityStep2: Correcting the EIGRP AS to 212Wrong AS (EIGRP 22) provided at RTR_2 (New router)All routers that want to exchange routes within EIGRP needs to be in same Autonomous System.Step 2.1:First we need to remove the current wrong EIGRP AS 22 from Router RTR_2Click on Host-F to get CLI of RTR_2RTR_2>enablePassword : cisco (Provided by SIM Q )RTR_2#conf tRTR_2(conf)#Step 2.2:Removing the wrong EIGRP routing process with AS 22RTR_2(conf)#no router eigrp 22The above statement removes all the EIGRP configuration configured for AS 22 .Step 2.3:Adding the correct EIGRP configurationStart the EIGRP routing process with AS 212RTR_2(conf)#router eigrp 212Step 2.4:Advertise the directly connected networks into EIGRP on RTR_2Fa 0/0 - 192.168.77.34Fa 1/0 - 192.168.60.81Fa 0/1 - 192.168.60.65RTR_2(config-router)#network 192.168.60.0RTR_2(config-router)#network 192.168.77.0RTR_2(config-router)#no auto-summaryRTR_2(config-router)#endStep 2.5:Important save the changes made to router RTR_2RTR_2#copy run startStep 3:RTR_1 does not advertise the new network between RTR_1 and RTR_2 into EIGRP.Click on Host-G to get CLI of RTR_1The network 192.168.77.0 is used between RTR_1 Fa0/0 - RTR_2 Fa 0/0This network needs to be advertise into EIGRP routing process at RTR_1RTR_1>enablePassword : cisco (Provided by SIM Q )RTR_1#conf tRTR_1(conf)#Step 3.1:Enter EIGRP routing process for AS 212RTR_1(conf)#router eigrp 212Step 3.2:The network 192.168.77.0 is used between RTR_1 Fa0/0 - RTR_2 Fa 0/0 . Advertise this network into EIGRPRTR_1(config-router)#network 192.168.77.0RTR_1(config-router)#endStep 3.3:Important save the changes made to router RTR_1RTR_1#copy run startVerification:From RTR_2 CLIping RTR_1 Serial 1/0 IP address 198.0.18.6RTR_2#ping 198.0.18.6!!!!!A successful ping shows the new RTR_2 will have fullconnectivity with other routers.Any Questions are welcomed!!!!!。
Cisco认证实验考试经典题库CCIE_BootCamp3.0

Cisco认证实验考试经典题库CCIE_BootCamp3.0(第十章)137.20.0.0/24 is subnetted, 1 subnets c 137.20.20.0 is directly connected, ethernet 0 172.168.0.0/16 is variably subnetted, 7 subnets, 2 masks o ia 172.168.30.0/24 [110/65] via 172.168.100.3, 00:09:03, serial 1.1 i 172.168.40.0/24 [100/8576] via 172.168.200.2, 00:01:11, serial 1.2 o ia 172.168.60.0/24 [110/1572] via 172.168.65.1. 00:09:03, bri0 c 172.168.65.0/24 is directly connected, bri0 c172.168.100.0/24 is directly connected, serial 1.1 o172.168.100.0/24 [110/64] via 172.168.100.3, 00:09:13, serial 1.1 c 172.168.200.0/24 is directly connected, serial 1.2 o e1 192.168. 21.0/24 [110/21] via 137.20.20.1.00:09:03, ethernet 0 o e1 192.168. 17.0/24 [110/21] via 137.20.20.1. 00:09:03, ethernet 0 o e1 192.168. 70.0/24 [110/21] via 137.20.20.1. 00:09:03, ethernet 0 o*e10.0.0.0/0 [110/21] via 137.20.20.1. 00:09:03, ethernet 0r5#show ip ospf int bri0 bri0 is up, line protocol is up (spoofing) internet address 172.168.65.2/24, area 10 process id 1, router id 172.168.200.1, network typepoint_to_point, cost 1562 run as demand circuit donotage lsa allowed. transmit delay is 1 sec, state point_to_point,timer intervals configured, hello 10, dead 40, wait 40, retransmit 5 hello due in 00:00:06 neighbor count is 1, adjacent neighbor count is 1 adjacent with neighbor172.168.100.6 (hello suppressed) suppress hello for 1 neighbor(s) r5#show dialer bri0 – dialer type =isdn dial string successes failures last called last status 4930622 1 0 00:08:45 successful 0 incoming call(s) have been screened 0 incoming call(s) rejected for callback bri0:1 – dialer type =isdn idle time(45 secs), fast idle timer (20 secs) wait for carrier (30 secs), re-enable (15 secs) dialer state is idle bri0:2 – dialer type =isdn idle time(45 secs), fast idle timer (20 secs) wait for carrier (30 secs), re-enable (15 secs) dialer state is idle r5# now go back to router r7 and bring up router r7’s interface s4 again 3. ipx configuration –15 pts (1 hour) a. configure all the active interfaces, including loopbacks, on routers r1, r2, r3, r5, r6, and r8 for ipx. b. configure router r8 and the lan interfaces on routers r3, r4, r5 and r6 for ipx rip. c. configure router r1 & r2 for ipx nlsp. d. configure the serial interfaces on the rest of the routers for ipx eigrp( not routers r1& r2 these oly use nlsp), also make the ethernet interface on router r2 ipx eigrp only. e.configure the bri0 interfaces on routers r5 & r6 as ipx rip. f. after this point you should be able to see all the ipx networks in all the routers routing table. test connectivity with ipx ping.Cisco认证实验考试经典题库CCIE_BootCamp3.0(第九章)j. make the default route on r2 appear in he routing table of all the other routers. k. configure routers r1, r2’ss1, and router r8’s ethernet interface e0 for eigrp. configure router r8’s interface to0 for rip. l. redistribute all routers between all routing protocols such that all routes are visible in all routers and every router can ping each other’s ip interfaces (even the loopback on r2) as shown on the lab diagram lab 5a. m. make sure that all ospf external routes appear as type-1, verify your routes. are the routes appearing in the correctly routing protocol? n. configure router r5 such that the only route on r6 for the 137. 20.0.0 network appears exactly as follows; o 137.20.20.0 [110/65] via 172.168.100.5,00:51:03, serial 1. hint pay attention to the underlined value 65. o. configure routers r3 & r4 to resolve dns namesusing dns servers 207.238.183.71 &207.238.183.72. 2. ospf demand circuit –15 pts (1 hour) a. use network172.168.65.0/24 for the isdn interfaces on routers r5 &r6 and ass them to ospf. configure routers r5 & r6 to use the isdn interfaces for restoral[ 恢复]. the isdn link should only come up when you administratively shutdown the serial 4 interface on router r7, and there is interesting traffic trying to get between routers r5 & r6 (i.e. use ping as the interesting traffic to test. make sure you test from router r6 and from router r5. see the router ports/configuration into online for the phone #’s, spids, and switch type if you are using our remote racks. configure the isdn link so that it will shutdown 45 seconds after an inbound or outbound ping packet. both routers should shave full ospf routes when the frame link is functional or not. you are required to use ospf demand-circuit as your solution here, after the initial isdn call to synchronize ospf, your isdn interfaces should stay down unless you break the frame connection between r5 and r6 and there is interesting traffic. now go to router r7 and shut down interface s4, your isdn connection should kick in and provide a backup path for router r6 to reach the rest of the network, butonly when there is data to send. ospf router updates should not keep the isdn up. pretend [假装]your isdn line is charged at $5 per minute and it comes out of your check. at this point when router r7’s interfaces s4 (your frame connection) is still down. router r5 should have the following displays for:”show ip route”, “show ip ospfint bri0”, and “show dialer”notice that the isdn connection is down and router r5 has a routing table with ospf entries using interface bri0 to get to router r6’s ethernet network, and is suppressing ospf hellos for 1 neighbor. also pay attention to the ospf dead time on r5’s bri0 interface. output from router r5 r5# show ip route codes: c- connected, s-static i- igrp, r-rip, m-mobile, b-bgp, d-eigrp, ex-eigrp external, o-ospf, ia-ospf inter area, n1-ospf nssa external type 1, n2- ospf nssa external type2, e1- ospf external type 1, e2- ospf external type 2 e- egp i- is-is, l1- is-is lever-1, l2- is-is level-2, *- candidate default, u- per-user static route, o- od gateway of last resort is 137.20.20.1 to network0.0.0.0Cisco认证实验考试经典题库CCIE_BootCamp3.0(第八章)3. bgp configuration –15pts (1h)a. place router r4 in bgp as 1 and router r3 in bgp as 2. create two static routes to null0 using a class a address with a 24-bit mask on r4 and inject into bgp such that router r3 can see it. use loopbacks as the update source on both routers r3 and r4. create loopback interface as necessary.b. filter one of the static routes with a route-map statement on router r4.c. configure bgp on router r4 such that the sub-netted class a route is seen. for example, the bgp route on router r3 could be 41.1.1.0 not 41.0.0.0.d. configure a second loopback interface on router r4 at 200.200.200.1/24 and enable rip on this router for this network. inject this route and the previous one with a metric of 5.e. configure router r2, r1, and r5 in bgp as3. use only one neighbor x.x.x.x remote-as x statement on routers r2 andr5.f. create a static route on router r2 (ip route 22.1.1.0255.255.255.0 null0) inject this route into bgp. make sure the other routers running bgp can see this route.g. also make sure all routers can ping 200.200.200.1.you have completed lab 4 compare your configurations to the ones we provided. often there is more than one to complete a task so your configuration may be different than ours. if your configuration are different than ours make sure you understand how to complete the lab with our configurations toolab5at the end of this lab verify connectivity to all ports. you should be able to ping every interface from any router. (don’t worry about being able to ping a local frame-relay interface. please disregard this statement if you are asked to filter packets. routes or other specific tasks.)1. initial configuration & ospf -35pts (2 h)a. use the pre-configuration files to apply proper ip addresses to the router interfaces. add ip addresses as needed as shown on the network diagram. you may have to add additional ip addresses to complete some tasks.b. configure router r2’s ethernet interfaces with ip address 137.20.20.1/24 and router r2’s default route to137.20.20.2.c. use a 24-bit mask unless told to use otherwise.d. create a loopback interface on router r2 with200.200.200.1/24.e. connect router r3, r4, r5, and r6 over frame-relay. configure router r5 using sub-interfaces.f. connect routers r3, r4, r5 and r6 over frame-relay. configure router r5 and router r4 on a different subnet.g. configure ospf on router r3’s interface s1, router r6’s interface s1, and router r5’s sub-interface s1.1 for ospf area 10, place r5’s and r2’s ethernet interface in ospf area 0.h. configure the connection between router r5’s interface s1.2 and router r4 for igrp.i. configure router r6’s ethernet e0 as ospf area 6. configure router r3’s token-ring interface to0 as ospf area 3. configure two loopback interfaces on router r3 with networks that contain at most 30 hosts and put both loopbacks in the same area as the token-ring interface. summarize the loopback subnets and router r3’s interface to0 to appear as one route to ospf.Cisco认证实验考试经典题库CCIE_BootCamp3.0(第七章)d. routers r1, r3 and r5 should share network 10.10.x.x 255.255.0.0 on their frame-relay interfaces.e. routers r1 and r2 should share network 10.20.x.x255.255.0.0 on their frame-relay interfaces.f. router r1 should have network 10.1.x.x with a 9-bit subnet mask on its ethernet interface.(the mask should be 255.255.128.0) sue subnet-zero here.g. router r2 should have network 137.20.20.0 with a 24-bit mask on its ethernet interface.h. router r3 should have network 10.3.x.x with an 8-bit subnet mask on its token-ring interface. (the mask shouldbe 255.255.0.0)i. use network 11.1.x.x 255.255.0.0 between routers r5 &r6.2. ospf & other ip routing configuration –35 pts (1hous 30 mins)a. configure ospf area 0 on the frame-relay interfaces between routers r1,r3, and r5.b. place router r1’s ethernet in ospf area 1. place router r3’s interface to 0 in ospf area 2.c. place router r3’s interface serial 0, and all of router r4 in ospf area 3. make ospf area 3 a totally-stubby area.d. place r5 and r6 ethernet interface in ospf area 4. make this ospf area a nssa (not-so-stubby-area) make the default cost 20.e. configure router r6’s interface serial 0 and routerr8’s interfaces s0, e0,and loop 0 for eigrp.f. place router r2’s interface serial 0 and router r1’ss0.1 in ospf area 5.g. redistribute all routes so that you can see all routes and ping from everywhere.h. summarize the routers for router r8’s interface e0, loop0, and s0 that were redistributed into ospf by routerr6 on router r5 so that all of router r8’s networks appear as one route to the rest of the ospf routers except r6.i. when you redistribute eigrp into ospf make these routes appear as type-1 external routes.j. configure router r2 such that it propagates a default route the other ospf routers.k. create a second loopback interface on router r2 with an address of 20.1.1.1/24. make sure you can ping the second loopback interface on router r2 from other the routers.l. create two loopbacks on router r3 with networks that could contain at most 30 hosts. place the loopbacks onrouter r3 in one area and summarize such that one route appears for both loopacks.m. place the ethernet interface on router r2 in area 10. n. configure simple password authentication in ospf area 4. o. use the ip ospf priority command on router r5 to make it become the dr for ospf area 4.p. change the cost on router r5’s interface e0 using an ip ospf command to make it appear as 100mbps as it relates to ospf metrics.q. change the cost on r6’s e0 without using an ip ospf command to make it appear as 100mbps as it relates to ospf metics.Cisco认证实验考试经典题库CCIE_BootCamp3.0(第六章)d. configure two static saps on router r3. filter on router r5 such that routers r6 and r8 only see one of the saps.e. disable ipx on the between routers r3 &r4 all routes should still be seen by all routers running ipx.f. change the frequency of the rip updates across the r3-r4serial connection to once every 2 minutes.g. configure router r1’s ethernet with ipx 802.2 and 802.3 raw frame types.h. configure routers r3 and r4 to pass ipx netbios type-20 broadcasts between their lan interfaces.5. dlsw configuration – 10 pts (45 mins)a. configure dlsw between router r3’s interface token-ring0 and router r4’s interface ethernet 0.b. place router r2’s interface ethernet 0 into the dlsw network. make sure there is connectivity between all lan interfaces.c. configure a filter that blocks netbios packets with destination name ‘cciering1” from leaving router r3’s interface to0.d. setup a filter that would permit only sna traffic between routers r3 & r4.6. bgp configuration – 15 pts (1h)a. configure bgp on router r4 using as number 1. configure bgp on routers r1, r2, r3 and r5 using as number 2. you can only use one neighbor x.x..x.x remote-as 2 command on routers r2 and r5.b. configure two static routes to 172.168.1.0/24 and172.168.2.0/24 using the command ip route 172.168.1.0255.255.255.0 null 0 on router r4, redistribute the second route into bgp using the route-map command.c. make sure that router r5 can see the 172.168.2.0 route.d. setup router r8 with bgp in as number 3. on router r8 use the loopback interface lo0 as the source for its bgp connection to as2. make sure router r8 can see the specific 172.168.2.0 route, and not the aggregate 172.168.0.0you have completed lab 3. compare your configurations to the ones we provided. often there si more than one to complete a task so your configuration may be different than ours. if your configuration are different than ours make sure you understand how to complete the lab with our configurations too.lab4at the end of this lab verify connectivity to all ports. you should be able to ping every interface from any router. (don’t worry about being able to ping a local frame-relay interface. please disregard this statement if you are asked to filter packets. routes or other specific tasks.)1. initial configuration -10pts (30 mins)a. use the pre-configuration files to apply proper ip addresses to the router interfaces. add ip addresses as needed as shown on the network diagram. you may have to add additional ip addresses to complete some tasks.b. connect routers r1,r2,r3, and r5 over the frame-relay. configure router r1 using sub-interfaces. configure routers r2.r3, and r5 without using sub-interfaces.c. use only frame-relay pvc on routers r2, r3 and r5. the recommended dlci numbers 102.201.103.105, and 501 are indicated on the network diagram.Cisco认证实验考试经典题库CCIE_BootCamp3.0(5)i. configure the ethernet interface e0 on router r4 to bein ospf area 40. j. configure the r5, r6, and r8 ethernet 0 interface to use eigrp. k. configure r8’s interface loop5 as 192.168.100.1/24 and add it to rip l. redistribute routes between all protocols such that router r1 can ping any interface. m. configure 2 loopbacks interfaces onrouter r8 with 10.1.1.1/24 & 10.1.2.1/24. add there to rip and redistribute rip to eigrp. summarize such that allrouters only see one route to the loopback interfaces. test connectivity to loopback interface via ping. n. filter such that router r6 can ping the loopbacks on router r1, but not the ethernet interface on router r1. the route for the ethernet on router r1 should still be visible and all other traffic such as telnet should still pass unfiltered. o. filter on router r5 such that routers r1 r2, r3, and r4, don’t see the route to router r8’s interface loopback 5. p. create three loopback interfaces on router r8 and use 160.10.10.1/24 for loopback 2, q. 161.10.10.1/24 for loopback 3, and 170.10.10.1 for loopback 4. now summarize the three loopback networks into one route. when done router r1 should see only one route for these three loopback interfaces ana should be able to ping all three of them. hint, the route may not look like what you think. 3. ntp & access-list & other tasks -15 pts (30 mins) a. configure ntp between routers r2 &r3. make r2 the time source. set the correct time and date on router on router r2. set the time-zone on routers r2 & r3, verify that router r3 has synced with router r2 via ntp. b. configure queuing on router r3’s s0 interface such that telnet, ip, ipx, and everything else use 25% of the bandwidth each.configure the queuing such that none of the traffic defined at 25% above uses more than 1000 bytes per time slice. you are allowed to exceed 1000 bytes per time slice only if there is part of a remaining individual packet that needs to be emptied from the queue. c. configure the frame-relay interface on router r2’s interface so such that ip is discard eligible on the frame. d. create the following 6 static routes on router r6; suing the cisco ios command ip route 192.168.x.0 255.255.255.0 null 0. use the number1,2,3,4,5 and 6 for the variable x. redistribute the static routes such that they are seen by all the other routers. now filter on router r5 using any method that use an access list so that only the even routes (i.e. x=2,4,and 6) are seen past router r5 towards the ospf network. your access-list can only have two lines in it, not seven for this exercise. all the 192.168.x.0 routes must still be seen in router r5’s routing table.4. ipx configuration – 20 pts (1h) a. configure all interface(including loopbacks ) for ipx b. configure ipx eigrp on the nbma frame-relay network c. configure ipxrip/sap everywhere else.Cisco认证实验考试经典题库CCIE_BootCamp3.0(第四章)n. filter on router r5 such that the bgp route to null0 defined on router r4 isn’t seen on routers r6 &r8. o. hint the object of this bgp section is to provide end-to-end connectivity between all routers and interfaces. in this exercise you are not allowed to configure igp or two-way static route connectivity between routers r5 & r6, bgp should be providing the necessary routing information. you are allowed to setup a default route on router r6 to point to router r5. now that you have completed lab 2 check., the routing tables on all routers. do they make sense? ping all interfaces from all routers. can you ping everywhere? do the appropriate routers see the static route to null0 on r4 via bgp? go to every router and ping every interface. if you can’t ping everything you are not done yes. you have completed lab 2. compare your configuration to ones we provided. often there is more than one to complete a task so your configurations may be different than ours. if your configurations are different than ours make sure you understand how to complete the lab with our configurations too lab 3 at the end of this lab verify connectivity to allports. you should be able to ping every interface from any router. (don’t worry about being able to ping a local frame-relay interface. please disregard this statement if you are asked to filter packets. routes or other specific tasks. 1. initial configuration -5 pts (30 mins) a. use the pre-configuration files to apply proper ip addresses to the router interfaces. add ip addresses as needed as shown on the network diagram. you may have to add additional ip addresses to complete some tasks. b. configure lab 3 network using network 137.20.x.x c. create a loopback interface on router r2 with 172.168.32.1/24. d. connect routers r1,r2, r3, and r5 over frame-relay cloud. e. configure router r1 using sub-interfaces. f. configure router r2 without using sub-interfaces or frame-relay map commands. g. put routers r1 &r2 frame-relay interfaces on one subnet and routers r1, r3, and r5 on a different subnet. 2. ospf & other ip routing configuration -35 pts ( 2 h) a. configure ospf with the frame-relay cloud in ospf area 0 b. configure the r3-r4 serial connection to be in area 1. c. set the ring-speed on router r3 to 16 mbps. d. configure the loopback interface on router r2 in adifferent ospf area. e. configure the lan interfaces onrouters r1, r2,and r3 to be in different ospf areas. f. configure two loopbacks on router r3 using subnets thatwill contain at most 30 host ip addresses. g. configure two loopback interfaces on router r1 using subnets that will contain at most 14 host ip addresses. h. summarize the two loopback interfaces on routers r1 and r3 such that routerr2 only sees one route from each.Cisco认证实验考试经典题库CCIE_BootCamp3.0(第三章)k. configure router r6 for ospf with a different process id than used thus far. do not configure r6’s e0 for ospf. l. configure router r8 to be in the same ospf area as routerr6. put router r8’s interface e0&lo0 into the ospf routing process. configure router r6 so that its s1 interface speed is correctly reflected in the ospf metrics without using the “ip ospf cost xxx” command. m. configure ospf message-digest authentication between routers r6 & r8. n. change the ospf hello interval between routers r6 & r8 to 45 seconds. o. configure router r8 suing the “ip ospf cost” command such that the speed of the link forinterface s0 is correctly reflected in the ospf metrics. p.change the ospf transmit interval delay to 10 seconds between routes r6 & r8. q. add a default route to router r2 that points to 137.20.20.2. configure one static route on router r2 so that full connectivity to r4’s interface e0 is available. you will notice that the default gateway of router r2 has a lower administrative cost than the one learned via router r1. as a result, the other default route never makes it in the routing table for router r2. r. you will notice that r2 can’t ping the serial interfaces between routers r3 & r4. fix this problem by only making changes to router r3 without static routes. 3. bgp configuration -15 pts (1 hour) a. configure router r4 in bgp autonomous system 1. b. create a static route to null0 router r4 and redistribute into bgp. c. create a loopback interface on r4 and add its network to bgp d. when adding the first loopback to bgp use a class a address with a 24-bit mask. the network that was added to bgp from the first loopback address should appear in the routing table of other routers as “ b 44.1.1.0…” e. create another loopback on router r4 with a class a address and put this network into rip and redistribute rip into bgp. f. configure router r3 in bgp autonomous system 1 and useinterface loopback 0 as the update source. g. configure routers r1, r2, and r5 in bgp autonomous system 2, only use one neighbor x.x.x.x remote-as 2 command on routers r2, r3. &r5 for autonomous system 2. h. place routers r6 and r8 in bgp autonomous system 3. i. configure bgp authentication between router r6 & r8. j. configure a loopback interface on router r8 and enable rip for this network. redistribute this rip network into ospf. k. redistribute the ospf routing process that contains routers r6 and r8 into bgp. l. you are not allowed to add any static routes to routerr8 during this exercise. m. configure router r6 such that all bgp routes learned from router r5 have a local preference of 300.Cisco认证实验考试经典题库CCIE_BootCamp3.0(第二章)lab 2at the end of this lab verify connectivity to all ports. you should be able to ping every interface from and router. (don’t worry about being able to ping a local frame-relayinterface. please disregard this statement if you are asked to filter packets. routes or other specific tasks.)1. initial configuration – 5 pts (30 mins)a. use the pre-configuration files to apply proper ip addresses to the router interfaces. add ip addresses as needed as shown on the network diagram. you may have to add additional ip addresses to complete some tasks.b. connect routers r1, r2, r3, and r5 over the frame-relay cloud. configure router r1 using sub-interfaces. configure routers r2, r3, and r5 without using sub-interface.c. use only one frame-relay pvc on routers r2, r3, and r5, the recommended dlci numbers 102,201,103, 301,105, and 501 for the frame-relay pvc’s are indicated on the network diagram.d. routers r1,r3,and r5 should share network 10.10.x.x 255.255.0.0 on their frame-relay interfacese. routers r1 and r2 should share network 10.20.x.x255.255.0.0 on their frame-relay interfaces.f. router r1 should have network 10.1.x.x with an 8-bit subnet mask on its ethernet interface( the mask should be 255.255.0.0)g. router r2 should have network 137.20.20.0 with a 24-bit mask on its ethernet interface.h. router r3 should have network 10.3.x.x with an 8-bit subnet mask on its token-ring interface ( the mask shouldbe 255.255.0.0)2. ospf configuration –30 pts (2 hours 30 minutes)a. configure ospf area 0 on the frame-relay interfaces between routers r1, r3 and router r5.b. place router r1’s ethernet in ospf area 1. place router r5’s interface e0 in ospf area 0.c. setup a default static route (default gateway) from r3to r4. redistribute this default static route into ospfwith a metric-type of 1 and a metric of 500.d. configure router r3’s serial 1 interface as173.168.40.1/24 and router r4’s serial 0 interface as172.168.40.2/24.e. configure router r4’s e0 interface as 200.100.100.1/24.f. configure a default gateway on router r4 to route all packets for which it has no routes to router r3.g. configure two loopback interfaces on router r3 with networks that could have at most 254 hosts and put themboth in the same ospf area, but different from ospf area 0. summarize this route into ospf so that the two subnets appear as one route.h. configure router r2 for eigrp and put all interface in the routing process.i. configure router r1 with eigrp and redistribute with ospf. set the metric type to type-1 when you redistribute from eigrp to ospf. also, redistribute ospf into eigrp.j. configure router r1 so that it only listens to eigrp updates on e0 and s0.2.Cisco认证实验考试经典题库CCIE_BootCamp3.0(第一章)1- day format version 3.002- policy routing frame relay ospflab#1network learning, inc. r&s ccie practice lab 1 version2.00 1-day versionat the end of this lab verify connectivity to all ports. you should be able to ping every interface form any router. (don’t worry about being able to ping a local frame-relay interface. please disregard this statement if you are askedto filter packets, routers or other specific tasks.)1. initial configuration – 5 pts (30 minutes)a. use the pre-configuration files to apply proper ip addresses to the router interfaces. add ip addresses as needed as shown on the network diagram.b. configure router r7 as a frame-relay switch. refer to the diagram for interface connections to other routers connected to router r7.c. connect routers r1,r2, r3, and r5 over the frame-relay cloud. configure router r1’s s0 interface as a sub-interface. configure r2,r3, and r5 without using sub-interfaces. use only one frame-relay pvc on routers r2, r3, and r5. the recommended dlci numbers 102, 201,103,301,105, and 501 are indicated on the lab diagram.d. routers r1, r2, r3, and r5 should share network10.10.x.x 255.255.0.0 on their frame-relay interfaces.e. router r1 should have network 10.1.x.x with an 8-bit subnet mask on its ethernet interface( the mask should be 255.255.0.0)f. make sure all the ethernet interfaces are in their own broadcast domain if you are using an ethernet switch for your ethernet connections.2. ospf configuration –25pts (2 hours 30 minutes)a. configure ospf area 0 on the frame-relay interfaces between r1, r2, r3, and r5.b. configure router r1’s interface ethernet 0 for ospf area 1c. configure router r2’s interface e0 for ospf area 10d. configure router r3’s interface s 1 and all of router r4’s interface for ospf area 3.e. configure router r5’s interface e 0 for ospf area 4.f. create two loopback interface on r4 and put both of the associated subnets on these interfaces in ospf area 44.g. summarize the (2) loopback interface you just created on router r4 so they appear as one route to the rest of the ospf routers in your network..h. here is the tricky part. you can’t use the command ip ospf network xxxx anywhere in your router configurations.i. redistribute the default route on router r2 as type-1 with a metric of 100. this route is already part of the initial configurations we provided for you.j. also, one of the problems in this lab can be solved with multiple frame map ip statements, but that is not the solution we want you to use, solve the problem with。
Cisco认证模拟题

Cisco认证模拟题篇一:思科认证CCNP经典试题第一部分填空题1、在Cisco体系的IGP协议中,RIP的A-D管理距离是,EIGRP的域内A-D管理距离是,EIGRP的域外A-D管理距离是OSPF的A-D管理距离是。
BGP从EBGP学习到的路由学到路由的A-D管理距离是; BGP 从IBGP学习到的路由学到路由的A-D管理距离是。
2、BGP的默认MED值为;其中MED越越优选被用于选路;BGP 从邻居哪里学到的权重为;BGP自己本路由产生的路由(始发路由)产生权重是;BGP的默认本地优先级为:。
3、BGP的邻居分为和。
4、OSPF在那个区域(有区域0,区域1,区域2)广播多路访问(比如以太网,没有出现外部网络),在区域0可以看到类LSA。
如果想看到2类LSA,必须在网络类型;在NSSA区域可以看到类LSA,在纯粹的NASS区域内是否有5类LSA?(回答是或者否)。
5、HSRP包括哪六种状态?6、OSPF在MA网络链路类型的HELLO报文作用?(3种)7、IPV6的本地链路地址是。
(没有/10的写法)8、在选择STP的角色(身份)有哪些?默认STP的收敛时间为配置了portfast后,收敛时间会小于。
9、OSPF发送hello包的组播地址是,EIGRP组播地址是;HSRP发送hello包组播地址是;VRRP发送hello包的组播地址是。
10、目前以太通道最多可以使用通道方式有。
11、BGP在EBGP中使用AS间的环路(确保无环),该属性属于BGP的必遵属性,其中还有哪两个是BGP公认必遵属性为和。
第二部分选择1、在对基于CEF的多层交换(MLS)进行排错的时候,例如解决无法到达特定的IP目标等问题,首先需要先查看哪两张表去验证错误?()A、IP路由表和路由表B、IP路由和CEF邻接关系表C、TCAM中的IPCEFFIB和邻接关系表D、IP路由表和ARP表2、EIGRP位一个混合距离矢量协议,在METRIC值中使用K1-K5五个K值,默认情况下,使用K值分别是()A、K1,K2BK3,K4C、K1,K5D、K1,K33、OSPF中router-id能标识一台设备的身份,下面说法正确的是()A、先选举手工配置,然后选择设备loopback地址大的,在选运行了宣告进OSPF最大的物理接口最大的地址。
思科模拟试题及答案

思科模拟试题及答案一、选择题1. 以下哪个命令用于查看路由器的接口状态?A. show interfaceB. show ip interfaceC. show running-configD. show ip route答案:A2. 在思科路由器上配置默认网关的命令是什么?A. ip default-gatewayB. default gatewayC. ip route 0.0.0.0D. route 0.0.0.0答案:C3. 以下哪个协议用于在大型网络中自动发现路由?A. RIPB. OSPFC. BGPD. EIGRP答案:B4. 以下哪个命令用于查看当前路由器的配置?A. show running-configB. show startup-configC. show interfaceD. show ip route答案:A5. 以下哪个命令用于在路由器上配置静态路由?A. ip routeB. routeC. static routeD. configure static route答案:A二、填空题6. 思科的网络操作系统称为________。
答案:IOS7. 在思科设备上,使用________命令可以进入特权模式。
答案:enable8. 配置VLAN的命令是________。
答案:VLAN configuration mode9. 动态主机配置协议的缩写是________。
答案:DHCP10. 用于测试网络连通性的命令是________。
答案:ping三、简答题11. 简述什么是子网掩码,并说明其作用。
答案:子网掩码是一种用于区分IP地址中网络部分和主机部分的位模式。
它的作用是告诉路由器或交换机,IP地址的哪部分是网络地址,哪部分是主机地址,以便正确地进行路由和数据传输。
12. 描述什么是VLAN,以及它在网络中的作用。
答案:VLAN(虚拟局域网)是一种将局域网划分为多个虚拟网络的技术。
思科认证640-802模拟试卷25(题后含答案及解析)

思科认证640-802模拟试卷25(题后含答案及解析) 题型有:1. 单选题 2. 多选题单选题1.Host 1 receives a file from remote server 1.Which MAC address appears as the source address in the header of the frames received by Host 1?A.The MAC address of the NIC in Host 1 .B.The MAC address of the NIC in server 1.C.The MAC address of the Fa0/0 interface of router R1D.The MAC address of the s0/0/0 interface of the router R2正确答案:C2.Which additional configuration step is necessary in order to connect to an access point that has SSID broadcasting disabled?A.Set the SSID value in the client software to public.B.Configure open authentication on the AP and the client.C.Set the SSID value on the client to the SSID configured on the AP.D.Configure MAC address filtering to permit the client to connect to the AP.正确答案:C3.Refer to the exhibit.What is the meaning of the term dynamic as displayed in the output of the show frame-relay map command shown?正确答案:E解析:这是个关于MAP的知识。
思科认证640-802模拟试卷24(题后含答案及解析)

思科认证640-802模拟试卷24(题后含答案及解析) 题型有:1. 单选题 2. 多选题单选题1.Refer to the output from the show running-config command in the exhibit.What should the administrator do to allow the workstations connected to the FastEthernet 0/0 interface to obtain an IP address?A.Apply access-group 14 to interface FastEthernet 0/0.B.Add access-list 14 permit any any to the access list configuration.C.Configure the IP address of the FastEtherent 0/0 interface to 10.90.201.1.D.Add an interface description to the FastEthernet 0/0 interface configuration.正确答案:C2.Refer to the exhibit.Switch-1 needs to send data to a host with a MAC address of 00b0.d056.efa4.What will Switch-1 do with this data?A.Switch-1 will drop the data because it does not have an entry for that MAC address.B.Switch-1 will flood the data out all of its ports except the port from which the data originated.C.Switch-1 will send an ARP request out all its ports except the port from which the data originated.D.Switch-1 will forward the data to its default gateway.正确答案:B解析:首先Switch 1需要发送一个数据到MAC地址为00b0.d056.efa4的主机,了解到目的地后,就查看他的MAC 地址表,然后发现在MAC地址表中没有这个MAC地址的条目存在。
CCIE模拟考试题_思科认证考试.doc

CCIE模拟考试题_思科认证考试.docCCIE模拟考试题_思科认证考试1.What statement is FALSE with respect to the operation of Unidirectional Link Detection?A. It negotiates the Unidirectional Link Detection link state during physical signaling.B. It performs tasks that autonegotiation cannot perform.C. It works by exchanging protocol packets between the neighboring devices.D. Both devices on the link must support Unidirectional Link Detection and have it enabled on respective ports.2.What is true concerning Traffic contract, Traffic shaping, and Traffic policing in ATM networks?A. They are parameters of PNNI set during PNNI configuration.B. They are forms of QoS features used in ATM networks.C. They are types of SVCs.D. They are types of PVCs.E. They are only used between ATM switches to control traffic flows.3.Which are the primary reasons to use traffic shaping? (Select two)A. To control the maximum rate of traffic transmitted or received on an interface.B. To control access to available bandwidth.C. To define Layer 3 aggregate or granular incoming or outgoing bandwidth rate limits.D. To control the average queue size by indicating to the end hosts when they should temporarily slow down transmission ofpackets.E. To ensure that traffic conforms to the policies established for it.4.In a bridged network running IEEE 802.1d spanning tree, what parameter will a bridge take form the root bridge?A. MaxageB. Forwarding delayC. Hello timeD. All of the above5.What statement is FALSE concerning the use of SPAN on the Catalyst 6500?。
CCIE题库
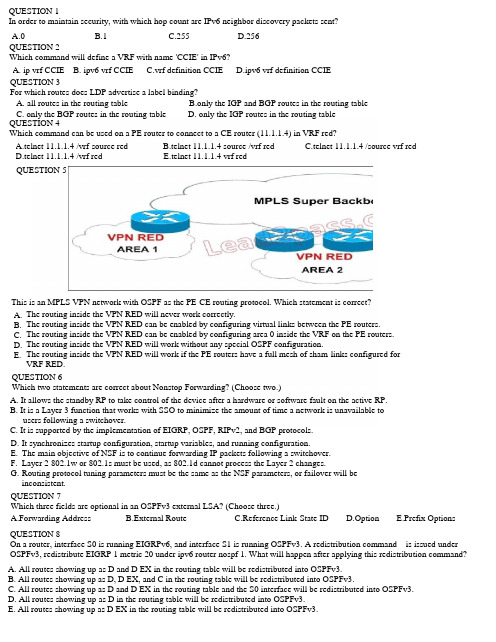
QUESTION 1In order to maintain security, with which hop count are IPv6 neighbor discovery packets sent?A.0B.1C.255D.256 QUESTION 2Which command will define a VRF with name 'CCIE' in IPv6?A. ip vrf CCIEB. ipv6 vrf CCIEC.vrf definition CCIED.ipv6 vrf definition CCIE QUESTION 3For which routes does LDP advertise a label binding?A. all routes in the routing tableB.only the IGP and BGP routes in the routing tableC. only the BGP routes in the routing tableD. only the IGP routes in the routing table The routing inside the VPN RED will never work correctly.The routing inside the VPN RED can be enabled by configuring virtual links between the PE routers. The routing inside the VPN RED can be enabled by configuring area 0 inside the VRF on the PE routers. The routing inside the VPN RED will work without any special OSPF configuration.The routing inside the VPN RED will work if the PE routers have a full mesh of sham-links configured for VRF RED. A. B. C. D. E. QUESTION 4Which command can be used on a PE router to connect to a CE router (11.1.1.4) in VRF red?A.telnet 11.1.1.4 /vrf-source redB.telnet 11.1.1.4 source /vrf redC.telnet 11.1.1.4 /source vrf redD.telnet 11.1.1.4 /vrf redE.telnet 11.1.1.4 vrf red QUESTION 5This is an MPLS VPN network with OSPF as the PE-CE routing protocol. Which statement is correct? QUESTION 6Which two statements are correct about Nonstop Forwarding? (Choose two.)A. It allows the standby RP to take control of the device after a hardware or software fault on the active RP.B. It is a Layer 3 function that works with SSO to minimize the amount of time a network is unavailable to users following a switchover.C. It is supported by the implementation of EIGRP, OSPF, RIPv2, and BGP protocols. It synchronizes startup configuration, startup variables, and running configuration.The main objective of NSF is to continue forwarding IP packets following a switchover. Layer 2 802.1w or 802.1s must be used, as 802.1d cannot process the Layer 2 changes.Routing protocol tuning parameters must be the same as the NSF parameters, or failover will beinconsistent. D. E. F. G. QUESTION 7Which three fields are optional in an OSPFv3 external LSA? (Choose three.)A.Forwarding AddressB.External RouteC.Reference Link-State IDD.OptionE.Prefix Options QUESTION 8On a router, interface S0 is running EIGRPv6, and interface S1 is running OSPFv3. A redistribution command is issued under OSPFv3, redistribute EIGRP 1 metric 20 under ipv6 router nospf 1. What will happen after applying this redistribution command? A. All routes showing up as D and D EX in the routing table will be redistributed into OSPFv3. B. All routes showing up as D, D EX, and C in the routing table will be redistributed into OSPFv3.C. All routes showing up as D and D EX in the routing table and the S0 interface will be redistributed into OSPFv3.D. All routes showing up as D in the routing table will be redistributed into OSPFv3.E. All routes showing up as D EX in the routing table will be redistributed into OSPFv3.QUESTION 9Which type of domains is interconnected using Multicast Source Discovery Protocol?A. PIM-SMB. PIM-DMC. PIM-SSMD. DVMRPQUESTION 10Which two multicast address ranges are assigned as source-specific multicast destination addresses and are reserved for use by source-specific applications and protocols? (Choose two.)A.232.0.0.0/8B.239.0.0.0/8C.232.0.0.0/4D.FF3x::/32E.FF2x::/32F.FF3x::/16QUESTION 11How is RPF used in multicast routing?A. to prevent multicast packets from loopingB. to prevent PIM packets from loopingC. to instruct PIM where to send a (*,G) or (S,G) join messageD. to prevent multicast packets from looping and to instruct PIM where to send a (*,G) or (S,G) join message QUESTION 12QUESTION 13Which interface(s) will show ip rpf 1.1.1.2 indicate as RPF interface(s)?A Ethernet 1/0B Ethernet 0/0C Both Ethernet 0/0 and Ethernet 1/0D RPF will fail QUESTION 14Apart from interdomain multicast routing, what else is MSDP used for?A Source Specific Multicast and IGMPv2B Announcing multicast sources to BGP speakersC Anycast RPD Intradomain multicast routingQUESTION 15Which IGMPv2 message contains a non-zero "Max Response Time"?A Membership QueryB Membership ReportC Membership DelayD Backward Compatible IGMPv1 Report Message QUESTION 16Which IGMPv2 message is displayed in the output of the packet capture?A. General QueryB. Membership ReportC. Membership QueryD. Membership Delay QUESTION 17What is Phantom RP used for?A. it is used for load balancing in bidirectional PIMB. it is used for redundancy in bidirectionalPIMC. it is used for redundancy in PIM-SMD. it is used for load balancing in PIM-SMQUESTION 19Which two statements are correct? (Choose two.)A. The hexadecimal value of the number of packets that hit the access list is 0x723E6E12.B. The access list has logging enabled.C. The packet was discarded.D. The command ip access-list logging hash-generation is enabled.E. The Telnet connection is successfully set up.QUESTION 20Which statement is correct?A. This configuration is not valid.B. Control Plane Policing is configured; however you cannot determine on which interface it is configured.C. NTP is not configured on the router.D. Telnet traffic will be dropped.QUESTION 22QUESTION 24What would be the security risk when you are using the above configuration? A. The locally configured users would override the TACACS+ security policy. B. It would be impossible to log in to the router if the TACACS+ server is down. C. The default login policy would override the TACACS+ configuration. D. If the TACACS+ server failed, no authentication would be required. QUESTION 25Which three protocols should be explicitly managed by using a CoPP policy on an Internet border router?(Choose three.)A. SMTPB. ICMPC. BGPD. SSHE. RTPF. BitTorrentG. VTPQUESTION 27QUESTION 23Which two statements are true about Unicast Reverse Path Forwarding Loose Mode? (Choose two.) A. B. C. D. E. It is used in multihome network scenarios.It can be used with BGP to mitigate DoS and DDoS. It does not need to have CEF enabled.It is enabled via the interface level command ip verify unicast reverse-path. It cannot be used with "classification" access lists.Which option best describes how the virtual MAC address is composed?QUESTION 28Which two commands are required to enable multicast on a router, knowing that the receivers only supportsIGMPv2? (Choose Two)A. IP PIM RP-addressB. IP PIM ssmC. IP PIM Sparse-modeD. IP PIM PassiveA. Increase the shaping rate for the priority queue.B. Remove the policer applied on the priority queue.C. Remove the shaper applied on the preiority queue.D. Increase the policing rate for the priority queue. QUESTION 31QUESTION 37QUESTION 42Which command is used to enable Etherchannel hashing for layer 3 IP and Layer 4 Port-based CEF?A. mpls ip cefB. port-channel ip cefC. mpls ip port-channel cefD. port-channel load balanceE. mpls ip load-balanceF. ip cef etherchannel channel-id XOR L4G. ip cef connection exchangeQUESTION 45 QUESTION 47QUESTION 48QUESTION 55 QUESTION 56QUESTION 57QUESTION 59 QUESTION 60QUESTION 61 QUESTION 62QUESTION 63 QUESTION 65QUESTION 68QUESTION 69Users that are connected to switch SWD are complaining about slow performance when they are doing large file transfers from a server connected to switch SWB. All switches are running PVST+. Which option will improve the performance of the file transfers?QUESTION 72Your network is suffering from regular outages. After troubleshooting, you learn that the transmit lead of a fiber uplink was damaged. Which two features can prevent the same issues in the future? (Choose two.) QUESTION 73QUESTION 76 QUESTION 78What can be done to remove the summary routes to Null0 on R3? QUESTION 81QUESTION 82QUESTION 83An OSPF virtual link is configured between R4 and R3. Based upon the show command output, why is the virtual-link down?QUESTION 85QUESTION 90QUESTION 112Refer to the exhibit. In the diagram, the switches are running IEEE 802.1s MST. Which ports are in the MSTblocking state?QUESTION 115Refer to the exhibit. Voice traffic is marked "precedence 5." How much bandwidth is allocated for voice traffic during periods of congestion?QUESTION 116Refer to the exhibit. Which of these is applied to the Bearer class?QUESTION 117Refer to the exhibit. What is the overall type of queuing being used on the outgoing data for interface Ethernet0/1?QUESTION 123Refer to the exhibit. When applying this policy map on the tunnel1 interface, you see packet loss for the TCP class starting at around 100000 b/s, instead of the configured 150000 b/s.What is the most likely cause of the discrepancy?\E. A VSS increases the size of the spanning-tree domain.E. Enable OSPF.QUESTION 186Refer to the exhibit. Look at the command output. What can you use to prevent this behavior?。
Cisco认证实验考试经典题库CCIE_BootCamp3.0(第八章)

Cisco认证实验考试经典题库CCIE_BootCamp3.0(第八章)3. bgp configuration –15pts (1h)a. place router r4 in bgp as 1 and router r3 in bgp as 2.create two static routes to null0 using a class a address with a24-bit mask on r4 and inject into bgp such that router r3 cansee it. use loopbacks as the update source on both routers r3and r4. create loopback interface as necessary.b. filter one of the static routes with a route-map statement on router r4.c. configure bgp on router r4 such that the sub-netted class a route is seen. for example, the bgp route on router r3could be 41.1.1.0 not 41.0.0.0.d. configure a second loopback interface on router r4 at200.200.200.1/24 and enable rip on this router for this network. inject this route and the previous one with a metric of5.e. configure router r2, r1, and r5 in bgp as3. use only one neighbor x.x.x.x remote-as x statement on routers r2 and r5.f. create a static route on router r2 (ip route 22.1.1.0 255.255.255.0 null0) inject this route into bgp. make sure theother routers running bgp can see this route.g. also make sure all routers can ping 200.200.200.1.you have completed lab 4 compare your configurations tothe ones we provided. often there is more than one to complete a task so your configuration may be different thanours. if your configuration are different than ours make sureyou understand how to complete the lab with our configurations toolab5at the end of this lab verify connectivity to all ports. youshould be able to ping every interface from any router. (don’t worry about being able to ping a local frame-relay interface.please disregard this statement if you are asked to filter packets. routes or other specific tasks.)1. initial configuration & ospf -35pts (2 h)a. use the pre-configuration files to apply proper ip addresses to the router interfaces. add ip addresses as neededas shown on the network diagram. you may have to add。
思科认证640-802模拟试卷20(题后含答案及解析)

思科认证640-802模拟试卷20(题后含答案及解析) 题型有:1. 单选题 2. 多选题单选题1.Refer to the exhibit.Which statement describes DLCI 17?A.DLCI 17 describes the ISDN circuit between R2 and R3.B.DLCI 17 describes a PVC on R2.It cannot be used on R3 or R1.C.DLCI 17 is the Layer 2 address used by R2 to describe a PVC to R3.D.DLCI 17 describes the dial-up circuit from R2 and R3 to the service provider.正确答案:C解析:DLCI号是一个二层地址,和mac类似2.What is the result of issuing the frame-relay map ip 192.168.1.2 202 broadcast command?A.defines the source IP address that is used in all broadcast packets on DLCI 202B.defines the DLCI that is used for all packets that are sent to the 192.168.1.2 IP addressC.defines the destination IP address that is used in all broadcast packets on DLCI 202D.defines the DLCI on which packets from the 192.168.1.2 IP address are received正确答案:B解析:题目是说,出现frame-relay map ip 192.168.1.2 202 broadcast 结果是什么?broadcast支持广播,命令也有说明映射关系.翻译选项A说------定义源ip地址--显然不对。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CCIE模拟考试题_思科认证考试
1.What statement is FALSE with respect to the operation of Unidirectional Link Detection?
A. It negotiates the Unidirectional Link Detection link state during physical signaling.
B. It performs tasks that autonegotiation cannot perform.
C. It works by exchanging protocol packets between the neighboring devices.
D. Both devices on the link must support Unidirectional Link Detection and have it enabled on respective ports.
2.What is true concerning Traffic contract, Traffic shaping, and Traffic policing in ATM networks?
A. They are parameters of PNNI set during PNNI configuration.
B. They are forms of QoS features used in ATM networks.
C. They are types of SVCs.
D. They are types of PVCs.
E. They are only used between ATM switches to control traffic flows.
3.Which are the primary reasons to use traffic shaping? (Select two)
A. To control the maximum rate of traffic transmitted or received on an interface.
B. To control access to available bandwidth.
C. To define Layer 3 aggregate or granular incoming or outgoing bandwidth rate limits.
D. To control the average queue size by indicating to the end hosts when they should temporarily slow down transmission of packets.
E. To ensure that traffic conforms to the policies established for it.
4.In a bridged network running IEEE 802.1d spanning tree, what parameter will a bridge take form the root bridge?
A. Maxage
B. Forwarding delay
C. Hello time
D. All of the above
5.What statement is FALSE concerning the use of SPAN on the Catalyst 6500?
A. It is possible to configure SPAN to have a Gigabit port, such as source port, and a 10/100 port as the destination port.
B. If the source port is configured as a trunk port, the traffic on the destination port will be tagged as well, regardless of the configuration on the destination port.
C. When a SPAN session is active the destination port does not participate in Spanning Tree.
D. With SPAN an entire VLAN can be configured to be the source.
E. In one SPAN session it is possible to monitor multiple ports that do not belong to the same VLAN.。
