DPtech UTM2000系列统一威胁管理安装手册v1.1
DPtech UTM2000-GS-N统一威胁管理安装手册

DPtech UTM2000-GS-N统一威胁管理安装手册杭州迪普科技有限公司为客户提供全方位的技术支持。
通过杭州迪普科技有限公司代理商购买产品的用户,请直接与销售代理商联系;直接向杭州迪普科技有限公司购买产品的用户,可直接与公司联系。
杭州迪普科技有限公司地址:杭州市滨江区火炬大道581号三维大厦B座901室邮编:310053声明Copyright 2009杭州迪普科技有限公司版权所有,保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本书内容的部分或全部,并不得以任何形式传播。
由于产品版本升级或其他原因,本手册内容有可能变更。
杭州迪普科技有限公司保留在没有任何通知或者提示的情况下对本手册的内容进行修改的权利。
本手册仅作为使用指导,杭州迪普科技有限公司尽全力在本手册中提供准确的信息,但是杭州迪普科技有限公司并不确保手册内容完全没有错误,本手册中的所有陈述、信息和建议也不构成任何明示或暗示的担保。
目录第1章产品介绍 1-11.1产品概述1-1 1.2DP TECH UTM2000-GS-N产品外观 1-1 1.3产品规格1-3 1.3.1存储器1-3 1.3.2外形尺寸和重量 1-3 1.3.3固定接口和槽位数 1-4 1.3.4输入电源 1-4 1.3.5工作环境 1-4第2章安装前的准备 2-12.1通用安全注意事项 2-1 2.2检查安装场所 2-1 2.2.2温度/湿度要求 2-1 2.2.3洁净度要求 2-2 2.2.4防静电要求 2-2 2.2.5抗干扰要求 2-3 2.2.6防雷击要求 2-3 2.2.7接地要求 2-3 2.2.8布线要求 2-3 2.3安装工具2-3第3章设备安装 3-13.1安装前的确认 3-1 3.2安装流程3-2 3.3安装设备到指定位置 3-2 3.3.2安装设备到工作台 3-3 3.3.3安装设备到19英寸机柜 3-4 3.4连接接地线 3-5 3.5连接接口线缆 3-6 3.5.1连接配置口线缆 3-6 3.5.2连接网络管理口 3-63.5.3连接业务口 3-7 3.6连接电源线 3-7 3.7安装后检查 3-7第4章设备启动及软件升级 4-14.1设备启动4-1 4.1.1搭建配置环境 4-1 4.1.2设备上电 4-4 4.1.3启动过程 4-5 4.2W EB默认登录方式 4-6第5章常见问题处理 5-15.1电源系统问题故障处理 5-1 5.2设备故障处理 5-1图形目录图1-1 DPtech UTM2000-GS-N前视图 1-1图1-2 DPtech UTM2000-GS-N前面板指示灯 1-3图1-3 DPtech UTM2000-GS-N后视图 1-3图3-1 设备安装流程 3-2 图3-2 安装设备于工作台 3-4图3-3 安装挂耳3-4图3-4 安装设备到机柜(为清晰起见省略了机柜) 3-4图3-5 固定设备3-5图3-6 连接接地线示意图 3-5图3-7 连接保护地线到接地排 3-6图3-8 电源线连接示意图 3-7图4-1 通过 Console口进行本地配置示意图 4-1图4-2 超级终端连接描述界面 4-1图4-3 超级终端连接使用串口设置 4-2图4-4 串口参数设置 4-3 图4-5 超级终端窗口 4-3 图4-6 终端类型设置 4-4 图4-7 Web网管登录页面 4-7表格目录表1-1 存储器规格1-3表1-2 外形尺寸和重量规格 1-3表1-3 固定接口规格 1-4 表1-4 输入电压1-4表1-5 工作环境1-4表2-1 机房温度/湿度要求 2-1表2-2 机房灰尘含量要求 2-2表2-3 机房有害气体限值 2-2表4-1 设置串接口属性 4-2第1章产品介绍1.1 产品概述DPtech UTM2000-GS-N统一威胁管理创新性地采用了“多业务并行处理引擎(MPE)”技术,在多功能开启情况下性能不受影响,能够满足防护混合威胁的安全需求。
UTM统一威胁管理操作指导

接入交换机
192.168.0.100
UTM Manager
Trust
192.168.0.0/24
需求: UTM 开启基本的防火墙功能, 同时开启防攻击、防病毒保护 以及带宽管理等深度检测功能。
36
开局准备:
1.版本是否正确? B5103及以前的版本:均为单系统版本,只有FW、VPN功能, 没有深度检测功能。 B5104及以后的版本:均为双系统版本,可以开启UTM所有 功能。 若版本不正确,开局前请务必升级到最新版本!!!
34
I-WARE基本功能配置:
1.特征库升级 2.IPS 3.AV
4.带宽管理
5.URL过滤
6.上网行为审计(结合UTM Manager)
35
配置举例:
Internet
UnTrust
G0/1:60.191.99.141
U200S
G0/0:192.168.0.1
VPN
提供远 程访问 数据的 防窃取 、防窜 改的安 全保证
入侵防御
防御最 新的安 全威胁 及恶意 攻击
防病毒
提供病 毒、蠕 虫、木 马、恶 意代码 的查杀 功能
URL过滤 应用控制 行为审计
屏蔽非 法网站 ,使用 户免受 干扰, 确保网 络健康 使用 限制 P2P/IM 应用, 保证关 键业务 的有效 带宽 对用户 的各种 上网行 为审计 、分析 、输出 报表
14
配置防火墙访问控制策略:
15
配置防火墙地址转换策略:
16
配置防火墙地址转换策略:
17
配置防火墙地址转换策略ACL:
18
配置防火墙地址转换策略ACL:
DPtech UTM2000-MA-N统一威胁管理安装手册

DPtech UTM2000-MA-N统一威胁管理安装手册杭州迪普科技有限公司为客户提供全方位的技术支持。
通过杭州迪普科技有限公司代理商购买产品的用户,请直接与销售代理商联系;直接向杭州迪普科技有限公司购买产品的用户,可直接与公司联系。
杭州迪普科技有限公司地址:杭州市滨江区火炬大道581号三维大厦B座901室邮编:310053声明Copyright 2009杭州迪普科技有限公司版权所有,保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本书内容的部分或全部,并不得以任何形式传播。
由于产品版本升级或其他原因,本手册内容有可能变更。
杭州迪普科技有限公司保留在没有任何通知或者提示的情况下对本手册的内容进行修改的权利。
本手册仅作为使用指导,杭州迪普科技有限公司尽全力在本手册中提供准确的信息,但是杭州迪普科技有限公司并不确保手册内容完全没有错误,本手册中的所有陈述、信息和建议也不构成任何明示或暗示的担保。
目录第1章产品介绍 1-11.1产品概述1-1 1.2DP TECH UTM2000-MA-N产品外观 1-1 1.3产品规格1-3 1.3.1存储器1-3 1.3.2外形尺寸和重量 1-3 1.3.3固定接口和槽位数 1-4 1.3.4输入电源 1-4 1.3.5工作环境 1-4第2章安装前的准备 2-12.1通用安全注意事项 2-1 2.2检查安装场所 2-1 2.2.2温度/湿度要求 2-1 2.2.3洁净度要求 2-2 2.2.4防静电要求 2-2 2.2.5抗干扰要求 2-3 2.2.6防雷击要求 2-3 2.2.7接地要求 2-3 2.2.8布线要求 2-3 2.3安装工具2-3第3章设备安装 3-13.1安装前的确认 3-1 3.2安装流程3-2 3.3安装设备到指定位置 3-2 3.3.2安装设备到工作台 3-3 3.3.3安装设备到19英寸机柜 3-4 3.4连接接地线 3-5 3.5连接接口线缆 3-6 3.5.1连接配置口线缆 3-63.5.2连接网络管理口 3-6 3.5.3连接业务口 3-7 3.6连接电源线 3-7 3.7安装后检查 3-7第4章设备启动及软件升级 4-14.1设备启动4-1 4.1.1搭建配置环境 4-1 4.1.2设备上电 4-4 4.1.3启动过程 4-5 4.2W EB默认登录方式 4-6第5章常见问题处理 5-15.1电源系统问题故障处理 5-1 5.2设备故障处理 5-1图形目录图1-1 DPtech UTM2000-MA-N前视图 1-1图1-2 DPtech UTM2000-MA-N前面板指示灯 1-3图1-3 DPtech UTM2000-MA-N后视图 1-3图3-1 设备安装流程 3-2 图3-2 安装设备于工作台 3-4图3-3 安装挂耳3-4图3-4 安装设备到机柜(为清晰起见省略了机柜) 3-4图3-5 固定设备3-5图3-6 连接接地线示意图 3-5图3-7 连接保护地线到接地排 3-6图3-8 电源线连接示意图 3-7图4-1 通过 Console口进行本地配置示意图 4-1图4-2 超级终端连接描述界面 4-1图4-3 超级终端连接使用串口设置 4-2图4-4 串口参数设置 4-3 图4-5 超级终端窗口 4-3 图4-6 终端类型设置 4-4 图4-7 Web网管登录页面 4-7表格目录表1-1 存储器规格1-3表1-2 外形尺寸和重量规格 1-3表1-3 固定接口规格 1-4 表1-4 输入电压1-4表1-5 工作环境1-4表2-1 机房温度/湿度要求 2-1表2-2 机房灰尘含量要求 2-2表2-3 机房有害气体限值 2-2表4-1 设置串接口属性 4-2第1章产品介绍1.1 产品概述DPtech UTM2000-MA-N统一威胁管理创新性地采用了“多业务并行处理引擎(MPE)”技术,在多功能开启情况下性能不受影响,能够满足防护混合威胁的安全需求。
ProSecure Unified Threat Management (UTM) 安装指南说明书
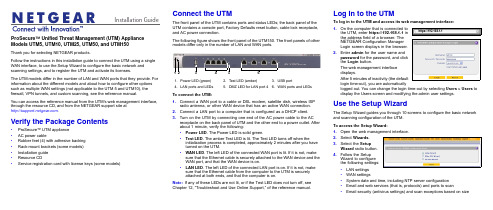
Installation Guide ProSecure™ Unified Threat Management (UTM) Appliance Models UTM5, UTM10, UTM25, UTM50, and UTM150Thank you for selecting NETGEAR products.Follow the instructions in this installation guide to connect the UTM using a single WAN interface, to use the Setup Wizard to configure the basic network and scanning settings, and to register the UTM and activate its licenses.The UTM models differ in the number of LAN and WAN ports that they provide. For information about the different models and about how to configure other options such as multiple WAN settings (not applicable to the UTM 5 and UTM10), the firewall, VPN tunnels, and custom scanning, see the reference manual.You can access the reference manual from the UTM’s web management interface, through the resource CD, and from the NETGEAR support site at.Verify the Package Contents•ProSecure™ UTM appliance•AC power cable•Rubber feet (4) with adhesive backing•Rack-mount brackets (some models)•Installation guide•Resource CD•Service registration card with license keys (some models)Connect the UTMThe front panel of the UTM contains ports and status LEDs; the back panel of theUTM contains a console port, Factory Defaults reset button, cable lock receptacle,and AC power connection.The following figure shows the front panel of the UTM150. The front panels of othermodels differ only in the number of LAN and WAN ports.To connect the UTM:1.Connect a WAN port to a cable or DSL modem, satellite dish, wireless ISPradio antenna, or other WAN device that has an active WAN connection.2.Connect a LAN port to a computer that is configured as a DHCP client.3.Turn on the UTM by connecting one end of the AC power cable to the ACreceptacle on the back panel of UTM and the other end to a power outlet. Afterabout 1 minute, verify the following:•Power LED. The Power LED is solid green.•Test LED. The amber Test LED is lit. The Test LED turns off when theinitialization process is completed, approximately 2minutes after you haveturned on the UTM.•WAN LED. The left LED of the connected WAN port is lit. If it is not, makesure that the Ethernet cable is securely attached to the WAN device and theWAN port, and that the WAN device is on.•LAN LED. The left LED of the connected LAN port is on. If it is not, makesure that the Ethernet cable from the computer to the UTM is securelyattached at both ends, and that the computer is on.Note:If any of these LEDs are not lit, or if the Test LED does not turn off, seeChapter 12, “Troubleshoot and Use Online Support,” of the reference manual.1.Power LED (green)2.Test LED (amber)B portN ports and LEDs5.DMZ LED for LAN port 46.WAN ports and LEDsLog In to the UTMTo log in to the UTM and access its web management interface:1.On the computer that is connected tothe UTM, enter https://192.168.1.1 inthe address field of a browser. TheNETGEAR Configuration ManagerLogin screen displays in the browser.2.Enter admin for the user name andpassword for the password, and clickthe Login button.The web management interfacedisplays.After 5 minutes of inactivity (the defaultlogin time-out), you are automaticallylogged out. You can change the login time-out by selecting Users > Users todisplay the Users screen and modifying the admin user settings.Use the Setup WizardThe Setup Wizard guides you through 10 screens to configure the basic networkand scanning configuration of the UTM.To access the Setup Wizard:1.Open the web management interface.2.Select Wizards.3.Select the SetupWizard radio button.4.Follow the SetupWizard to configurethe following settings:•LAN settings•WAN settings•System date and time, including NTP server configuration•Email and web services (that is, protocols) and ports to scan•Email security (antivirus settings) and scan exceptions based on sizehttps://192.168.1.1December 2012NETGEAR and the NETGEAR logo are registered trademarks of NETGEAR, Inc. in the United States and/or other countries. Other brand and product names are trademarks or registered trademarks of their respective holders. Information is subject to change without notice. © NETGEAR, Inc. All rights reserved.Intended for indoor use only in all EU member states, EFTA states, and Switzerland.•Web security (antivirus settings) and scan exceptions based on size•Web categories to be blocked•Email notification•Scan engine and signatures update settings5.Click the Apply button to save your changes.The UTM reboots. If the IP address of your computer is now on a differentsubnet, restart the computer to refresh its network settings so you can log in to the UTM again.Note:For detailed steps about how to configure the UTM by using the Setup Wizard, see Chapter 2, “Use the Setup Wizard to Provision the UTM in Your Network,” of the reference manual.Register the UTM and Activate the Licenses To receive threat management component updates and use telephone support, you need to register your UTM with NETGEAR. You might have purchased the UTM with a 1- or 3-year license. The UTM also comes with four 30-day trial licenses:•Web protection•Email protection•Support and maintenance•Application control and IPSIf your UTM is unregistered, you can use the 30-day trial period for all four types of licenses to perform the initial testing and configuration.Activating the licenses initiates their terms of use. Activate the licenses only when you are ready to start using the UTM. The 30-day trial licenses are revoked once you activate the purchased licenses.To register the UTM and activate the trial or purchased licenses:1.Make sure that the UTM has Internet access.2.Open the web management interface.3.Select Support > Registration. The Registration screen displays.4.Enter one of the license keys in the Registration Key field.plete the fields in the Customer Information and VAR Information sectionsof the screen.6.Click one of the following buttons:•Trial. Activates a trial license and registers the UTM with the NETGEARregistration and update server.•Register. Activates a purchased license and registers the UTM with theNETGEAR registration and update server.7.If necessary, repeat Step 4 and Step 6 for additional license keys.After the registration and activation are complete, the Registration screenshows the license keys and their expiration dates:Electronic Licensing OptionIf you have purchased the UTM with a 1- or 3-year license, you might be able to usethe electronic licensing option. When the UTM is connected to the Internet, youneed to enter only your customer information and optional value-added reseller(VAR) information on the Register screen but do not need to enter the licensenumbers. When you click the Register button, the UTM automatically downloadsand activates the license keys because the serial number of the UTM is linked to thelicense.If you have purchased a license from a VAR (either directly or over the web) afterpurchase of the UTM, the VAR should email you the license keys or provide them toyou in another way. To register and activate the license keys, follow the regularregistration procedure as explained in the previous section (see steps 1–7).Online Documentation and ResourcesFor extensive information about configuring and using your UTM, see the referencemanual, which you can access from or from theweb management interface.To access online documentation and resources:1.Open the web management interface.2.Select one of the following:•To view the reference manual, select Support > Documentation.•To view the product support page, select Support > Knowledge Base.Technical SupportVisit for product updates and web support.For the complete EU Declaration of Conformity, visit/app/answers/detail/a_id/11621/.NETGEAR recommends that you use only the official NETGEAR supportresources.。
UTM统一威胁管理阿呆书

UTM(统一威胁管理)阿呆书本书是Fortinet与你分享的一本有关UTM(统一威胁管理)的深入浅出的探讨与说明。
书中我们站在网络安全设备选购者、IT技术管理者的角度谈到了网络应用以及安全的演变,防火墙以及防御技术的进化,以及如果是你来选购网络安全方案会怎样?内容简单明了。
相信每一位读此书的人都会深有感受。
每本阿呆书都有图标标识说明,这本也不例外:记着此段文字,有益于在UTM世界中继续阅读。
我们有时候会分享一些技术定义说明,如果你不感兴趣,可以跳过。
有益网络安全的关键点哦。
目录_Toc321843036第一章 (5)综合网络安全需求所在 (5)好的方面:更多更好的网络接入方式 (5)坏的方面:“混水难御” (7)丑陋的:网络犯罪与破坏 (9)第二章 (16)传统防火墙为啥挡不住如今的威胁 (16)充其量是不充分的防御 (17)单机产品会降低网络安全的可见性 (18)多台设备部署造成了对性能的打击 (21)第三章 (24)UTM:平复防御的混乱 (24)迈入UTM时代 (25)UTM:灵活,设计为未来 (26)单窗格式管理 (27)始终保持能够防御不断变化的威胁 (31)第四章 (33)UTM细节 (33)对你的网络选择对的检测技术 (33)通用处理器 VS ASIC (35)第五章 (40)统一威胁管理在生效 (40)部分成就整体 (40)端到端的彻底的防御覆盖 (44)UTM用户的现身说法 (48)第六章 (51)评估UTM解决方案的十大关键问题(Ok,准确说是十一个) (51)衡量UTM方案的几步走方法? (51)UTM方案中包含哪些安全技术? (52)UTM设备支持哪些网络功能? (53)UTM本来就支持IPv6么? (54)是否在虚拟环境下运行良好? (54)UTM解决方案是否具有可扩展性? (54)是否提供高可用性(HA)? (55)管理与报告功能怎样? (55)UTM解决方案如何领先于安全威胁? (56)购买费用如何? (57)是单次认证许可么? (57)可提供哪些支持? (58)售后培训如何? (58)厂商是否可以提供全球性服务支持? (58)在用客户的评价如何? (59)第一章综合网络安全需求所在守护不断变化的网络安全驾驭应用抵御犯罪软件在如今这个移动无所不在的世界里,网络无时不刻在变化。
联想网御UTM产品白皮书

联想网御UTM产品白皮书1. UTM产品简述1.1 什么是UTMUTM是统一威胁管理(Unified Threat Management)的缩写。
UTM设备是指由硬件、软件和网络技术组成的具有专门用途的设备,它主要提供一项或多项安全功能,将多种安全特性集成于一个硬设备中,构成一个标准的统一安全管理平台。
UTM设备应该具备的基本功能包括VPN、网络防火墙、网络入侵检测/防御和网关防病毒等功能,这几项功能并不一定要同时都得到使用,不过它们应该是UTM设备自身固有的功能。
UTM安全设备也可能包括其它特性,例如内容过滤、安全审计、安全管理、日志、服务质量(QoS)、高可用性(HA)和带宽管理等。
下图显示了UTM 系统平台上可能综合的多项安全功能。
UTM(United Threat Management)意为统一威胁管理,是指由硬件、软件和网络技术组成的具有专门用途的设备,它主要提供一项或多项安全功能,将多种安全特性集成于一个硬设备中,构成一个标准的统一安全管理平台。
1.2 UTM的优点整合所带来的成本降低将多种安全功能整合在同一产品当中能够让这些功能组成统一的整体发挥作用,相比于单个功能的累加功效更强,颇有一加一大于二的意味。
现在很多组织特别是中小企业用户受到成本限制而无法获得令人满意的安全解决方案,UTM产品有望解决这一困境。
包含多个功能的UTM安全设备价格较之单独购买这些功能为低,这使得用户可以用较低的成本获得相比以往更加全面的安全防御设施。
降低信息安全工作强度由于UTM安全产品可以一次性的获得以往多种产品的功能,并且只要插接在网络上就可以完成基本的安全防御功能,所以无论在部署过程中可以大大降低强度。
另外,UTM安全产品的各个功能模块遵循同样的管理接口,并具有内建的联动能力,所以在使用上也远较传统的安全产品简单。
同等安全需求条件下,UTM安全设备的数量要低于传统安全设备,无论是厂商还是网络管理员都可以减少服务和维护工作量。
UTM设备安装指南说明书

Installation GuideFamiliarize yourself with the connectors and controls on the back of the unit.Complete the Basic SetupFollow these steps to quickly setup the UTM appliance.Connect the UnitFor initial setup, connect the WAN Ethernet port to an active WAN connection such as a broadband modern, connect a DHCP enabled PC to a LAN port, and turn on the unit.Verify the following:• Power LED : It takes about a minute to boot. The power LED should turn solidgreen. If it does not, see the Troubleshooting section of the Reference Manual . • Test LED : When you first turn on the unit, the amber test LED will be lit forapproximately 2 minutes.• WAN Status LED : The status LED on the connected WAN port should be lit. Ifnot, make sure the Ethernet cable is securely attached to the modem and the WAN port, and that the modem is powered on.• LAN Status LED : A LAN status LED should be lit. If not, ensure that the Ethernetcable from the computer to the unit is securely attached at both ends, and that the computer is turned on.Log in to the Unit1. Use a browser to connect tohttps://192.168.1.1.7. Kensington lock 8. Console port 9. Factory reset button10. Power connector7109https://192.168.1.12. When prompted, enter admin for the UserName and password for the Password. Click Login.You are now connected. After 5 minutes of inactivity (the default login time-out), you are automatically logged out.Note: When the unit scans secure HTTPS traffic, import its root CA certificate into client browsers. Click the link at the bottom of the login screen to download it.Use the Setup Wizard for Basic ConfigurationThe Setup Wizard will guide you through the basic network and scanning setup. Note: If you choose to bypass the Setup Wizard, be sure to configure an alerts email address and change the admin password.1. Start the Setup Wizard.Select Wizards > SetupWizard to start the wizard.For guidance on how to fill in the wizard screens, refer to the online help or the Reference Manual via a link in theSupport > Documentation page.2. Use the Setup Wizard to configure these basic network and scanning settings:• LAN and WAN network settings.• System time (NTP server) and time zone.• Scanning of network protocols and services.• Default scan actions when the unit detects threats.• Scan exceptions like the maximum file size.• Specify the notification server and notices to be used in email notifications.•Scan engine and signature updates.ProSecure™ Unified Threat Management (UTM) ApplianceFollow these instructions to configure your ProSecure Unified Threat Management appliance to use a single WAN interface, and enable the default threat management scanning. Then, consult the Reference Manual for instructions on configuring other options such as multiple WAN settings, VPN, firewall, and custom scanning. You can access the Reference Manual from the product management interface, via the Resource CD and from the NETGEAR support site: . Estimated time: 30 minutes.Verify the Package Contents• ProSecure™ UTM appliance. • Installation Guide.• Resource CD.• Rubber feet (4) with adhesive backing.• Rack mount brackets (some models).• Power cord.Familiarize Yourself with the UnitFamiliarize yourself with the ports and status lights on the front of the unit.1.Green power LED2.Amber test LEDB port (for future use)4.Gigabit LAN portsN port 4 DMZ identifier6.Gigabit WAN ports, dualWAN model shown12536November 2010This symbol was placed in accordance with the European Union Directive 2002/96 on the Waste Electrical and Electronic Equipment (the WEEE Directive). If disposed of within the European Union, this product should be treated and recycled in accordance with the laws of your jurisdiction implementing the WEEE Directive.©2010 by NETGEAR, Inc. All rights reserved. NETGEAR and the NETGEAR logo are registered trademarks of NETGEAR, Inc. in the United States and/or other countries. Other brand and product names are trademarks or registered trademarks of their respective holders. Information is subject to change without notice.3. Click Apply to save your changes.The unit will reboot. Your computer will lose its connection to the unit if its IP address is now on a different subnet. If so, restart the computer to refresh its network settings.LicensesYour unit is bundled with three 30-day trial licenses.• Web scanning • Email scanning• Support and maintenanceActivating the licenses starts their term of use. Activate the licenses only when you are ready to start using this unit. If your unit has never been registered before you can use the 30 day trial period for all 3 types of licenses to perform initial testing and configuration.Note: Be sure the unit has Internet access before registering the licenses.• Activate the trial licenses by selecting Support > Registration and click the “Trial ” button. Once you activate the trial licenses, you can then update the unit with the latest UTM build and signature & engines during the 30-day trialperiod.• If you purchase a license subscription bundled with your unit, a license will be assigned to your unit’s serial number. When you register your unit, the license key will automatically be downloaded to your unit. Select Support > Registration , fill out the registration page, and click “Register ” to activate the services. Note: the 30-day trial licenses will be revoked once you activate the purchased service license keys. The purchased service license keys offer one year or three years of service.For additional information on licenses see the reference manual.Register and Activate the LicensesNote: Be sure the unit has Internet access before registering the licenses.1. Log in to the unit.2. Select Support > Registrationto display the Registration tab.3. Enter the customer information. If using the trial licenses, click Trial . If youhave purchased licenses, click Register . The unit will activate the licenses. After registration is complete the unit will display the license keys and their expiration dates.Online Documentation and SupportSelect Support > Documentation to view the reference manual. Select Support > Knowledge Base to view the support page, which includes this document and the reference manual. Going to/support and selecting your product modelnumber takes you to the same page.Consult the reference manual for instructions on how to use the online supportremote diagnostics.Technical SupportThank you for selecting NETGEAR products.After installing your device, locate the serial number on the label of your product and use it to register your product at /register . Registration is required before you can use the telephone support service. Registration via our website is strongly recommended.Go to for product updates and Web support . For additional information about setting up, configuring, and using your Product Name Only, see the User Manual .For complete DoC please visit the NETGEAR EU Declarations of Conformity website at: /app/answers/detail/a_id/11621/。
DPtech UTM2000 统一威胁管理

DPtech UTM2000入侵防御技术白皮书1、概述本篇文章主要介绍DPtech UTM2000系列产品中入侵防御功能的相关技术1.1 相关术语段(segment):段是一个物理组网下对经过UTM设备数据的一个逻辑划分,通常是一对或者多对接口,或者包含VLAN ID的接口数据流,入侵防御相关的业务都基于segment进行配置。
1.2 网络安全现状融入全球化的Internet是企业网络发展的必然趋势,每个企业的Intranet都会有许多与外部连接的链路,如通过专线连入Internet,提供远程接入服务供业务伙伴和出差员工访问等,企业网络边界的淡化,企业面临的威胁的机会也增大了,只要一个访问入口防护不完整,则“黑客”将可以入侵企业,获取数据或者破坏。
1.3 基于网络的攻击与检测技术入侵防御的基本功能是识别尽可能多的攻击,同时又避免不必要的误报,同时也需要保证企业有限的带宽不被滥用,为了达到上述目标,单纯的采用一种技术手段是无法做到的,迪普创新性的融合了多种内容识别技术,保证了系统能够快速高效的发现异常流量并阻断,同时保证正常业务的开展,提供如下几项技术:基于流的状态特征检测技术,基于攻击固定特征的检测这是IDS/入侵防御最基本攻击检测技术,而基于流的状态特征检测技术与以往的不同的是,可以是基于协议上下文的特征检测技术,这样可以很好的避免误报的发生;如某一个特征只在三次会话之后的client方向发生,则检测时只会针对这部分数据流进行检测,而不会引起误报;·协议异常检测技术,通常也叫协议分析,即对照RFC规范对通讯的协议进行检查,这对于检测基于RFC 未规范一些未知攻击或新的攻击非常有效;同时对于基于固定特征的逃逸也具有先天的免疫;·智能的自适应多层次防护技术,可以很好的解决DoS/DDoS攻击防护问题,该技术通过对保护对象的流量进行流量学习和建模,针对不同的类型流量采用不同的动作,并通过不断的学习调整等过程,保证保护对象避免DDoS/DoS攻击的困扰;·在应用中识别威胁技术:融合协议识别和威胁识别的基础上进行有状态的深度威胁分析,从而更好减少误报;·基于滥用误用的带宽管理技术:在应用的智能识别基础上,对于识别出的滥用和误用协议可以进行多层次和多纬度的带宽管理;2、威胁的识别2.1基于滥用误用的带宽管理技术网络“以内容为王”造成了当前网络上应用的层出不穷,这种繁荣的背后意味着:必须对网络中的应用及其行为进行深入的感知和分析,对应用的流量和行为进行细粒度分层次的管理,从而预防可能的滥用和误用,杜绝各种应用所引入的潜在威胁。
DPtech IPS2000-GE-N抗DDOS攻击设备配置文档

1.3.3 固定接口和槽位数
表1-3 固定接口规格
项目
规格
管理口
1 个 Console 配置口 2 个 10/100/1000M 网络管理口
USB 接口
1 个 USB 口(Host)
PFP 接口
1 个 PFP 口,提供与 PFP 设备的连接
业务接口
图形目录
图 1-1 DPtech IPS2000-GE-N前视图
1-2
图 1-2 DPtech IPS2000-GE-N前面板指示灯
1-3
图 1-3 DPtech IPS2000-GE-N后视图
1-4
图 1-4 以太网接口
1-7
图 3-1 设备安装流程
3-2
图 3-2 安装设备于工作台
3-4
图 3-3 安装挂耳及外滑轨
表示系统告警
第 1 章 产品介绍
1-2
DPtech IPS2000-GE-N 抗 DDOS 攻击设备 安装手册
指示灯 (红色)
状态 常灭
说明 表示系统正常
快闪(8Hz) 表示系统异常
(12) 电源指示灯 PWR0(绿 色)
常亮 常灭
表示电源 0 工作正常 表示电源 0 不在位
快闪(8Hz) 表示电源 0 出现故障
3-3
iv
3.3.3 安装设备到 19 英寸机柜 3.4 连接接地线 3.5 连接接口线缆 3.5.1 连接配置口线缆 3.5.2 连接网络管理口 3.5.3 连接业务口 3.6 连接电源线 3.7 安装后检查
第 4 章 设备启动及软件升级
4.1 设备启动 4.1.1 搭建配置环境 4.1.2 设备上电 4.1.3 启动过程 4.2 WEB默认登录方式
Power Xpert Meter 2000系列网络安全指南说明书

Power Xpert Meter 2000 cyber security guidelinesTim Thompson Chief Engineer, Communications IntroductionConcerns for the security of communicatingelectronic devices and systems has increaseddramatically as cyber security attacks haveescalated. This white paper describes bestpractices in implementing cyber security in thePower Xpert E Meter 2000 Series. The followingguidelines include concrete steps to address cybersecurity risks, both in the 2000 Series meter andin the network enclave in which the meter resides,in accordance with the Information Assurancecontrols defined in the NIST Security andPrivacy Controls for Federal InformationSystems and Organizations (NIST.SP.800-53r4)and Department of Defense (DoD) InformationAssurance Certification and AccreditationProcess (DIACAP) (DODI 8500.2).In addition to the guidance provided in thiswhite paper, it is important to read and thoroughlyunderstand the security practices described indetail in Chapter 11 of the Power Xpert Meter2000 Series User and Installation Manual,document number IM02601001E, available at/meters.Address cyber security risksIn any given application, potential vulnerabilitiesneed to be defined. Knowing that no systemcan be 100 percent secure, protective measuresshould be taken based on the value of the assetsthat need to be protected.The DIACAP is a process to make sure that riskmanagement is applied on information systems.The process is formal and incorporates standardactivities for the certification and accreditationof DoD information security systems, so thatthey maintain information assurance positionsthroughout a system’s life.The 2000 Series meters can be secured toDIACAP standards through basic measuresincluding:• Securing physical access to the meter• Changing the default passwords• Using strong passwords and periodicallychanging them• Implementing session locking onhost computers• Enabling hypertext transfer protocolsecure (HTTPS)• Disabling unused ports• Enabling “trusted hosts”• Saving a configuration baseline• Checking the system log periodicallyfor unusual activity2White Paper WP049001ENEffective January 2014Power Xpert Meter 2000 cyber security guidelineseAton Access controlThe front panel of the 2000 Series meter provides direct access to many of the features and functions of the meter. Therefore, it is important to physically secure the meter by placing it in a locked room with restricted access to authorized personnel.Control access is provided to the meter from the front panel. Within the front panel, users can gain administrative access and change meter settings.The meter can also be accessed through its communication ports. It is designed so that users can point their Web browsers to the Internet Protocol (IP) address of the meter to gain access to its features and functions. However, care must be taken to control ethernet access to the meter.The 2000 Series provides two accounts for network access: user (“user”) and administrator (“admin”). The user account offers read-only access to the meter’s measured values. Through the administrator account, users can access the same features as the user account, with the addition of administrative functions. Access to the administrator account is necessary to make configuration changes or other modifications to the meter, such as upgrading its firmware. These two network accounts, combined with the front panel account, are used to separate the duties of users who access the meter so that each type of user has the least privilege necessary to perform their job function.Session locking should be implemented on the system used to access the meter (e.g., Microsoft Windows T screen saver) in order to prevent unauthorized access in the event that a user or administrator steps away from the computer.Transport Layer Security (TLS), widely known as Secure Socket Layer (SSL), is a flexible technology best known for securing Web browser sessions. It is also the standard for secure application networkcommunications within the enterprise, including machine-to-machine (M2M) communications, database access, and virtual privatenetworking. The Power Xpert Meter 2000 Series has the capability to use SSL certificates to protect the confidentiality and integrity of data in transit. The meter can be configured to require Hypertext Transfer Protocol Secure (HTTPS). When this feature is enabled, HTTP access is disabled and all communications with the meter Web server must be through HTTPS. Additional security can be achieved through the use of a Virtual Private Network (VPN) with blocking mode enabled, and remote access mediated through a managed access control point, such as a remote access server in a Demilitarized Zone (DMZ).Simple Network Management Protocol (SNMP) is a protocol commonly used by network management systems. SNMP Versions 1 and 2 are not considered secure. Without the strong authentication and privacy that is provided by the SNMP Version 3 User-based Security Model (USM), an attacker or other unauthorized users may gain access to detailed system management information and use that information to launch attacks against the system. In applications where security is imperative, the meter can be configured to disable SNMP services earlier than SNMPv3.The meter can also be configured so that only trusted computers (aka “hosts”) can access it. The “trusted host” feature isconfigurable on the meter’s Access Control Web page, where IP addresses or host names of trusted computers can be entered. SNMP , Modbus T /TCP , BACnet T /IP , and file transfer protocol (FTP) access are all restricted to trusted hosts by default; therefore, an empty list of IP addresses/hostnames means that the meter will not respond to these protocols by default.SSHv1 is not a DoD-approved protocol and has many well-known vulnerability exploits. Exploits of the SSH client could provide access to the system with the privileges of the user running the client. For this reason, SSH is disabled in the meter.Audit and accountabilityThe 2000 Series meter supports a system log function, whichrecords system events for audit report generation. For each system event, the system log records the user ID, the date/time of event, and the type of event, including successful logons and logoffs. The meter also supports export of the system log file to a comma-separated value (CSV) file for import into business software.The 2000 Series can save meter configuration settings and restore settings from the meter setup Web page. After installation and commissioning, a baseline should be saved in case it needs to be restored at a future time.The system log and current configuration should be checked periodically against the baseline to detect unauthorized access or modification to the meter’s configuration. These routine checks should be scheduled more frequently in critical infrastructure applications, and are recommended daily.A synchronized system clock is critical for the enforcement of time-based policies and the correlation of logs and audit records with other systems. For redundancy, two time sources are required so that synchronization continues to function even if one source fails. The 2000 Series meter uses a real-time clock for timekeeping. The meter can be configured to adjust for daylight saving time (DST) based on the time zone selection and to synchronize time using Network Time Protocol (NTP). By using NTP, time will be maintained by the real-time clock, and the real-time clock will be calibrated and time-corrected using NTP. The meter also supports the configuration of up to three time servers, in order to allow NTP to effectively exclude a time source that is not consistent with the others.Identification and authenticationEach 2000 Series meter has a unique serial number and media access control (MAC) ID. During installation and commissioning, ensure that a unique name and IP address are set for each meter. This will enable the supervisory system and users to uniquely identify and authenticate each device before establishing a network connection.The meter uses passwords to authenticate user access. Managing passwords effectively is of paramount importance. If attackers are able to acquire passwords, particularly the administrator’s password, then security of the meter can be compromised. The following are some ways to help ensure that passwords remain secure:•Both the user and the administrator accounts are password-protected, and both accounts have default passwords. One of the most important steps to take to secure the meter is to change the default passwords during installation and commissioning•The front panel account is also password-protected. The default password for the front panel account disables password checking at the front panel. Therefore, to secure front panel access, the default password must be changed•The administrator, user, and front panel passwords can be changed on the password configuration Web page, accessible through the meter’s Web user interface3White Paper WP049001ENEffective January 2014Power Xpert Meter 2000 cyber security guidelineseAton PasswordsChoosing strong passwords is essential to securing devices on a network. Guidelines for strong passwords are provided below:•The use of longer passwords reduces the ability of attackers to successfully obtain valid passwords by guessing or usingexhaustive search techniques because it increases the password search space. Passwords with a minimum length of 14 characters are recommended•The complexity of passwords also increases the password search space by requiring users to construct passwords from a larger character set than they may otherwise use. Complex passwords with at least one lower case, one upper case, one number, and one special character are recommended. Preferably, a thorough mixture of each is used. It is often best to avoid words that can be found in a dictionary. Additionally, passwords with excessive repeated characters can be more vulnerable to password-guessing attacks. For this reason, it can be best to use passwords with no more than three consecutive repeating characters •Passwords should also be changed periodically, about every 60 days. Limiting the lifespan of authenticators limits the period of time an unauthorized user has access to the system while using compromised credentials and reduces the period of time available for password-guessing attacks to run against a single password •To ensure that password changes are effective in their goals, the system must ensure that old and new passwords have significant differences. Without significant changes, new passwords may be easily guessed based on the value of a previously compromised password. Ensure that new passwords differ from previouspasswords by at least four characters. A good practice is to avoid using the same password twice for at least five iterations of password changesBoundary protectionCommunication traffic between the meter and the user orsupervisory system should be isolated from the business network using managed switches and firewalls. Network exposure should also be minimized for all system components in order to limit potential attack vectors. Critical system components should never directly face the Internet.It is best to use boundary defense mechanisms, including firewalls and network intrusion detection systems (IDS), deployed at the enclave boundary to the wide area network. When remote access is required, virtual private networks (VPNs) can be used to protect the integrity of system traffic. Managed switches should beconfigured to use whitelisting to govern which clients (e.g., users or supervisory systems) can access which information servers(e.g., meters). For an added measure of security, the meter’s trusted host feature can be used to whitelist access from client computers using SNMP , Modbus/TCP , BACnet/IP , and FTP , as described above.ConclusionThese guidelines are intended to help strengthen the security of the Power Xpert Meter 2000 Series. More specific guidance on enhancing the security of the meters is available in Chapter 11 of the 2000 Series User and Installation Manual.In accordance with proper configuration settings, there are external factors that are also important to consider. Restricting physical access to the meter is vitally important, as manyconfiguration settings are available through the front panel’s user interface. All such electronic devices and systems should be secured in a locked room with restricted access.In addition, electronic devices and systems should be protected by firewalls, preferably on virtual private networks using managed switches to restrict access to only those systems and users that are authorized. Security threats continue to evolve in sophistication, and cyber security countermeasures must evolve to keep pace, but these guidelines describe many important steps to take now that will aid in preventing the most common types of attacks.AuthorTim Thompson is chief engineer for communications in power components solutions at Eaton. He has held positions in design engineering and engineering management, and has over 20 years of experience in developing electronic power distribution products, including power quality meters, protective relays, electronic trip units, communications gateways, and enterprise software. He holds four patents, with several pending. Tim received his BSEE from the University of Pittsburgh, and his MSEE from Carnegie-Mellon University.References1. Power Xpert Meter 2000 Series User and Installation Manual,IM02601001E, /meters 2. NIST .SP .800-53r4, Security and Privacy Controls for FederalInformation Systems and Organizations, April 2013, /nistpubs/SpecialPublications/ NIST .SP .800-53r4.pdf 3. DoD Instruction 8500.2, Information Assurance (IA) Implementation, February 6, 2003,/whs/directives/corres/pdf/850002p.pdfEaton1000 Eaton Boulevard Cleveland, OH 44122 United States © 2014 EatonAll Rights ReservedPrinted in USAPublication No. WP049001EN / Z14720 January 2014Eaton is a registered trademark.All other trademarks are propertyof their respective owners.Power Xpert Meter 2000 cyber security guidelinesWhite Paper WP049001EN Effective January 2014。
DPtech IPS2000系列入侵防御系统开局指导

DPtech IPS2000开局指导杭州迪普科技有限公司2011年07月目录DPtech IPS2000开局指导 (1)第1章前期调研 (1)1.1调研内容 (1)1.2确定部署方案 (2)第2章实施步骤 (3)2.1准备工作 (3)2.2部署条件 (3)2.3安装断掉保护PFP(如需安装) (3)2.4实施方案 (4)2.4.1 基本配置方案1-旁路部署 (4)2.4.2 基本配置方案2-透明部署 (8)2.4.3 基本配置方案3-混合部署 (11)2.4.4 扩展配置 (12)2.4.5 高级配置 (13)2.4.6 其他配置 (14)第3章实施注意事项 (18)第1章前期调研1.1 调研内容1.2 确定部署方案根据调研及交流的结果,确定物理部署位置、逻辑部署位置、开启功能策略等第2章实施步骤2.1 准备工作向用户介绍入侵防御系统实施内容、产品与用户沟通入侵防御系统实际部署时间2.2 部署条件设备正常启动连接线(双绞线、光纤等)正常可用部署机柜满足部署条件(机柜空间、插座数、功率载荷)管理地址已分配,且满足互通等要求确定部署方式(组网模式、部署链路数)2.3 安装断掉保护PFP(如需安装)将PFP插卡板安装在PFP主机上将内网连接线(如SW引出)连接至PFP“1”口,外网连接线(如FW引出)连接至PFP“4”口,流量于1——4间物理透传,此时验证网络畅通性PFP插板“2、3”口平行连接IPS主机“A、B”口,即实施后的流量流向应为:局域网——PFP1口——PFP2口——IPSA口——IPSB口——PFP3口——PFP4口——互联网,链路上下行连接错误,会导致日志分析异常此时切忌连接PFP主机与IPS主机的“USB”连接线,需完成全部功能配置后,再连接“USB”连接线2.4 实施方案2.4.1 基本配置方案1-旁路部署组网拓扑图注意:此模式下只做检测,不做控制PC直连设备管理口,缺省IP地址为192.168.0.1;用户名:admin,密码:admin在【网络管理】->【组网模式】中,修改某一接口对组网模式为“旁路模式”注意:如上图所示,eth1/0与eth1/1接口对组网模式改为旁路模式后,此接口将无接口对概念,eth1/0与eth1/1独立存在,且均可作为旁路检测接口在【网络管理】->【网络用户组】中,添加IP用户组如果设备需要跨网段管理,则需在【网络管理】->【单播IPv4路由】中,添加指定或默认路由在【IPS规则】中创建规则后,引用到【IPS策略】中的指定旁路接口在【日志管理】->【业务日志】中,开启将IPS日志输出UMC功能(IP:UMC安装服务器的IP地址,PORT:9514)在【审计分析】->【流量分析】中,开启将流量分析日志输出UMC功能(IP:UMC 安装服务器的IP地址,PORT:9502)在服务器安装UMC后,用IE访问其网卡IP地址(注:UMC地址需与IPS管理地址互通),用户名:admin,密码:UMCAdministrator在【设备管理】->【设备列表】中,添加IPS设备在【系统管理】->【时间同步配置】中,点击“立即同步”(注:UMC与IPS时间不一致,会影响日志统计)在【网络监控】中查看流量分析日志,在【攻击监控】中查看IPS日志(如果未使用UMC,则在IPS设备【IPS日志】中查看)2.4.2 基本配置方案2-透明部署PC直连设备管理口,缺省IP地址为192.168.0.1;用户名:admin,密码:admin在【网络管理】->【网络用户组】中,添加IP用户组如果设备需要跨网段管理,则需在【网络管理】->【单播IPv4路由】中,添加指定或默认路由在【IPS规则】中创建规则后,引用到【IPS策略】中的指定旁路接口在【日志管理】->【业务日志】中,开启将IPS日志输出UMC功能(IP:UMC安装服务器的IP地址,PORT:9514)在【审计分析】->【流量分析】中,开启将流量分析日志输出UMC功能(IP:UMC 安装服务器的IP地址,PORT:9502)在服务器安装UMC后,用IE访问其网卡IP地址(注:UMC地址需与IPS管理地址互通),用户名:admin,密码:UMCAdministrator在【设备管理】->【设备列表】中,添加IPS设备在【系统管理】->【时间同步配置】中,点击“立即同步”(注:UMC与IPS时间不一致,会影响日志统计)在【网络监控】中查看流量分析日志,在【攻击监控】中查看IPS日志(如果未使用UMC,则在IPS设备【IPS日志】中查看)2.4.3 基本配置方案3-混合部署如上图所示,eth1/0与eth1/1为旁路模式,可独立做旁路检测(IDS);eth1/2与eth1/3,eth1/4与eth1/5为在线模式,存在接口对概念,可做在线检测(IPS);即实现了同时在线检测与旁路检测的混合模式2.4.4 扩展配置【防病毒】,在【常用功能】->【防病毒】中,添加防病毒策略;下图策略为:从eth1/0与eth1/1接口流入的流量,进行防病毒策略的安全匹配(流行度概念,请参见用户手册)【带宽限速】,在【扩展功能】->【应用防火墙】->【网络应用带宽限速】中,添加带宽限速策略;下图策略为:从eth1/0接口流入,且源IP组为test,目的IP组为All users的流量,P2P限速5000kbps(注意单位);从eth1/1接口流入,且源IP组为All users,目的IP组为test的流量,P2P限速5000kbps(注意单位)【访问控制】,在【扩展功能】->【应用防火墙】->【网络应用访问控制】中,添加访问控制策略;下图策略为:从eth1/0接口流入,且源IP组为test,目的IP组为All users的流量,阻断网络应用-即时通讯;从eth1/1接口流入,且源IP组为All users,目的IP组为test的流量,阻断网络应用-即时通讯【URL】,在【扩展功能】->【应用防火墙】->【URL过滤】中,添加URL过滤策略;下图策略为:从eth1/0接口流入,且源IP组为test的流量,对主机名为的URL进行过滤2.4.5 高级配置端口捆绑(注意:虚接口绑定遵循上下行,即上行口不能与下行口绑定)自定义IPS特征(根据报文参数,自定义设置IPS特征,并引入到IPS策略)带宽限速/访问控制自定义应用组(创建自定义网络应用组后,可应用到带宽限速/访问控制策略中)URL分类库及推送配置(注意:此功能在有URL License,且已经导入URL特征库的情况下,方可使用)2.4.6 其他配置添加管理员,并设置管理权限设置Web访问协议参数导入/出配置文件,需重启(推荐在同一软件版本下使用)修改接口同步状态(注意:当开启接口同步状态下,当接口对中的eth1/0口down后,在数秒种后,eth1/1口的管理状态会dwon,如恢复管理状态需在console口下操作,重新no shutdown该接口状态)创建IP用户组,IP用户群,IP用户簇(IP可实现分级管理,并应用到策略)Web页面修改管理口地址软件bypass,开启后流量不做安全检测(VIP流量概念,请参见用户手册)黑名单基础DDos配置(添加防护网段配置后,根据网络情况,下发DDos防护策略)基本攻击防护策略第3章实施注意事项管理服务器的安全性管理服务器安装Windows2003 Server或者Windows2008操作系统后,管理员一定要确保对Windows进行重要安全补丁修补,规范操作系统口令和密码设置,保证正常启动运行。
DPtech IPS2000-GC-N入侵防御系统安装手册V1.0

2.1 通用安全注意事项
在移动设备前,请先将设备断电。 请将设备放置在干燥通风的地方。不要让液体进入设备。 保持设备清洁。 不要在设备上堆积物品。 非专业维修人员,请不要随意打开设备机壳。
1.4.2 各类接口
1. Console 口 IPS 提供了一个 RS232 异步串行配置口(Console),可用来连接终端计算机,以进行系统的调 试、配置、维护、管理和主机软件程序加载等工作。 2. 以太网接口
(1) (2) (3) (4) (5) (6) (7) (8)
(1) 1000M 以太网光接口(0) (3) 10/100/1000M 以太网电接口(0) (5) 10/100/1000M 以太网电接口(2) (7) 10/100/1000M 以太网电接口 (4)
DPtech IPS2000-GC-N 前面板指示灯 2. 后视图
(2)
(1)
(1) 交流电源插座
(2) 接地端子
DPtech IPS2000-GC-N 后视图
1.3 产品规格
1.3.1 存储器
存储器规格
项目 Flash 内存类型及容量 CF 卡 规格 4MB外形尺寸和重量
外形尺寸和重量规格
项目 外型尺寸(W×D×H) 规格 430mm×261mm×44mm
第 1 章 产品介绍
3
DPtech IPS2000-GC-N 入侵防御系统 安装手册 项目 重量 规格 3.1Kg
1.3.3 固定接口和槽位数
固定接口规格
项目 PFP 接口 USB 接口 业务接口 规格 1 个 PFP 口,提供与 PFP 设备的连接 1 个 USB 口(Host) 固定接口: 6 个 10/100/1000M 电接口 2 个 1000M 光接口
(售前)DPtech FW、UTM培训胶片

安全威胁的演进
n 攻击方式越来越复杂,单 一攻击转向复合性攻击
ü 应用层攻击占据90%以上. ü 多种和混合式攻击 已经成 为常见的行为.
n 动机和关注点发生了变化
ü 从捣乱转向获取金钱. ü 盗取金钱和个人信息.
22
当前网络安全威胁
传统安全是不够的!
Internet
新建会话数 5000 并发会话数 100,000 IPSec 100M 电源 单电源
2010年5月推出
10
高性能——研发实力的最佳体现
FW1000-GT
n基于分布式硬件架构,集成多核+ASIC n采用Crosbar无阻塞交换技术 n提供12GE和2*10GE接口模块 n整机处理能力可达40G n报文处理时延仅20us
内部网络
Internet
办事处
禁止外网发起的 各种访问
外网用户
ACL 规则
公司总部
状态检测更安全
13
丰富的安全功能
NAT
安全区域
流量控制 攻击防范
FW1000 VPN n n n
……
双机热备 攻击防范和远程安全接入一体化 深度状态识别,提供基于状态的安全过滤 集成地址转换、流量控制等网络应用
Trust 可信区域
15
灵活智能NAT转换
n支持多个地址对一个地址的转换 n支持多个地址对多个地址的转换 n支持一对一地址转换 n支持基于端口的转换
USER1 SIP:192.168.0.1 USER2 SIP:192.168.0.1 USER3 SIP:192.168.0.1
FW1000防火墙 NAT
1. SIP:192.168.01=>SIP:10.153.100.1 2. SIP:192.168.02=>SIP:10.153.100.1 3. SIP:192.168.01=>SIP:10.153.100.1
DPtech UTM2000 系列产品彩页

⏹ 最全面的一体化安全设备,提供L2~7全面安全防护为了更好的应对混合型攻击,DPtech UTM2000采用L2~7融合操作系统ConPlat ,具备防火墙、入侵防御、防毒墙、内容过滤等诸多功能,是目前业界功能最丰富的UTM 产品,能够为用户提供L2~7完全融合的防御效果。
⏹ 采用先进的多核硬件架构,多种业务并行线速处理DPtech UTM2000基于迪普科技高性能硬件架构APP-X ,即使多功能开启、特征库增加,也不会影响设备性能和网络时延。
⏹ 有线无线一体化解决方案,提供多样的接入方式DPtech UTM2000支持有线无线一体化,通过WiFi 和3G 网络,可以提供全面的无线网络安全防护以及线路备份解决方案,帮助用户实现降低建设成本、简化网络结构、易于管理等需求,是用户综合安全保障的最佳选择。
⏹ 专业的特征库团队,特征库自动升级,持续安全防护迪普科技拥有一支专业的特征库团队,实时跟踪网络安全领域的最新动态,提供应用识别与威胁特征库APP-ID ,设备可及时自动升级,能够为用户网络提供实时的防御能力。
⏹ 丰富的防火墙功能DPtech UTM2000 支持先进的应用防火墙技术,可以提供灵活的安全区域隔离功能,能够按区域进行重点安全防护,并且支持NAT 、虚拟防火墙、MCE 等功能。
⏹ 全内置IPSec VPN 、SSL VPN 硬件加密 面对用户分支互联、移动办公的需求,DPtech UTM2000全内置IPSec VPN 、SSL VPN 硬件加解密功能,在简化网络结构的基础上,极大的提升了用户网络安全建设的性价比。
⏹ 专业的系统漏洞防护,实现虚拟软件补丁技术DPtech UTM2000 通过分析漏洞攻击产生原理,定义攻击类型的统一特征,可以不受攻击变种的影响,并且采用虚拟补丁技术,极大减少了网络运维人员的工作量。
⏹ 专业的防病毒引擎,可防御各类病毒采用专业病毒库,并且支持新一代虚拟脱壳和行为判断技术,可以准确查杀文件型、网络型和混合型等各类病毒。
SonicWall TZ系列统一威胁管理(UTM)防火墙说明书

The SonicWall TZ series of Unified Threat Management (UTM) firewalls is ideally suited for any organization that requires enterprise-grade network protection. SonicWall TZ series firewalls provide broad protection with advanced security services consisting of on-box and cloud-based anti-malware,anti-spyware, application control, intrusion prevention system (IPS), and URL filtering. To counter the trend of encrypted attacks, the TZ series has the processing power to inspect encrypted SSL/TLS connections against the latest threats. Combined with Dell X-Series switches, selected TZ series firewalls can directly manage the security of these additional ports.Backed by the SonicWall Global Response Intelligent Defense (GRID) network, the SonicWall TZ series delivers continuous updates to maintain a strong network defense against cybercriminals. The SonicWall TZ series is able to scan every byte of every packet on all ports and protocols with almost zero latency and no file size limitations.The SonicWall TZ series features Gigabit Ethernet ports, optional integrated 802.11ac wireless*, IPSec and SSL VPN, failover through integrated 3G/4G support, load balancing and network segmentation. The SonicWall TZ series UTM firewalls also provide fast, secure mobile access over Apple iOS, Google Android, Amazon Kindle, Windows, Mac OS X and Linux platforms.The SonicWall Global Management System (GMS) enables centralized deployment and management of SonicWall TZ series firewalls from a single system.Managed security for distributed environments Schools, retail shops, remote sites, branch offices and distributed enterprises need a solution that integrates with their corporate firewall. SonicWall TZ series firewalls share the same code base—andsame protection—as our flagship SuperMassive next-generation firewalls. This simplifies remote site management, as every administrator sees the same user interface (UI). GMS enables network administrators to configure, monitor and manage remote SonicWall firewalls through a single pane of glass. By adding high-speed, secure wireless, the SonicWall TZ series extends the protection perimeter to include customers and guests frequenting the retail site or remote office.SonicWall TZ seriesExceptional security and stellar performance at a disruptively low TCOBenefits:• Enterprise grade networkprotection• Deep packet inspection of all trafficwithout restrictions on file size orprotocol• Secure 802.11ac wirelessconnectivity using integratedwireless controller or viaexternal SonicPoint wireless accesspoints• SSL VPN mobile access for AppleiOS, Google Android, AmazonKindle, Windows, Mac OS andLinux devices• Over 100 additional ports canbe securely managed by theTZ console when deployed incombination with Dell X-SeriesswitchesFor emerging enterprises, retail and branch offices looking for security performance at a value price, the SonicWall TZ600 next-generation firewall secures networks with enterprise-class features and uncompromising performance.USB port (3G/4G WAN Failover)Link and activityIndicator LEDsPower LEDTest LEDPort X1 WANPortpower8x1GbE switch (configurable)Console port Expansion module Slot (future)SonicWall TZ500 seriesFor growing branch offices and SMBs, the SonicWall TZ500 series delivers highly effective, no-compromise protection withnetwork productivity and optional integrated 802.11ac dual-band wireless.(3G/4G WAN Failover)X1 WAN Port poweractivity Indicator LEDs(configurable)portFor small business, retail and branch office locations, the SonicWall TZ400 series delivers enterprise-grade protection. Flexible wireless deployment is available with either external SonicPoint Access points or 802.11ac wireless integrated into the unit.SonicWall TZ300 seriesThe SonicWall TZ300 series offers an all-in-one solution that protects networks from attack. Unlike consumer grade products, the SonicWall TZ300 series firewall combines effective intrusion prevention, anti-malware and content/URL filtering with optional802.11ac integrated wireless and broadest secure mobile platforms support for laptops, smartphones and tablets.(3G/4G WAN Failover)X0 LANPort X1WAN PortpoweractivityIndicator LEDs3x1GbE switch(configurable)portUSB port (3G/4G WANFailover)X1 WAN Port powerLink and activity IndicatorLEDsPower LED Test LED(configurable)portFor wired and wireless small and home office environments, the SonicWall SOHO series delivers the same business-class protectionlarge organizations require at a more affordable price point.USB port (3G/4G WAN Failover)X0 LAN Port X1 WAN PortpowerLink andactivityIndicator LEDsPower LED Test LED(configurable)portExtensible architecture for extreme scalabilityand performanceThe Reassembly-Free Deep Packet Inspection (RFDPI) engineis designed from the ground up with an emphasis on providingsecurity scanning at a high performance level, to match boththe inherently parallel and ever-growing nature of networktraffic. When combined with multi-core processor systems, thisparallel-centric software architecture scales up perfectly toaddress the demands of deep packet inspection at high trafficloads. The SonicWall TZ Series platform relies on processorsthat, unlike x86, are optimized for packet, crypto and networkprocessing while retaining flexibility and programmability inthe field — a weak point for ASICs systems. This flexibility isessential when new code and behavior updates are necessaryto protect against new attacks that require updated and moresophisticated detection techniques.branch officeX-series switchGlobal management and reportingFor larger, distributed enterprise deployments, the optional SonicWall Global Management System (GMS) provides administrators a unified, secure and extensible platform to manage SonicWall security appliances and Dell X-Series switches. It enables enterprises to easily consolidate the management of security appliances, reduce administrative and troubleshooting complexities and governs all operational aspects of the security infrastructure including centralized policy management and enforcement, real-time event monitoring, analytics and reporting, and more. GMS also meets the firewall change management requirements of enterprises through a workflow automation feature. GMS provides a better way to manage network security by business processes and service levels that dramatically simplify the lifecycle management of your overall security environments rather than on a device-by-device basis.Reassembly-Free Deep Packet Inspection (RFDPI) engineThe RFDPI engine provides superior threat protection and application control without compromising performance. This patented engine inspects the traffic stream to detect threats at Layers 3-7. The RFDPI engine takes network streams through extensive and repeated normalization and decryption in order to neutralize advanced evasion techniques that seekto confuse detection engines and sneak malicious codeinto the network. Once a packet undergoes the necessary preprocessing, including SSL decryption, it is analyzed against a single proprietary memory representation of three signature databases: intrusion attacks, malware and applications. The connection state is then advanced to represent the position of the stream relative to these databases until it encountersa state of attack, or another “match” event, at which point a pre-set action is taken. As malware is identified, the SonicWall firewall terminates the connection before any compromise can be achieved and properly logs the event. However, the engine can also be configured for inspection only or, in the case of application detection, to provide Layer 7 bandwidth management services for the remainder of the applicationstream as soon as the application is identified.Security and protectionThe dedicated, in-house SonicWall Threat Research Team workson researching and developing countermeasures to deploy to the firewalls in the field for up-to-date protection. The team leverages more than one million sensors across the globe for malware samples, and for telemetry feedback on the latest threat information, which in turn is fed intothe intrusion prevention, anti-malware and application detection capabilities. SonicWall firewall customers with current subscriptions are provided continuously updated threat protection aroundthe clock, with new updates taking effect immediately without rebootsor interruptions. The signatures onthe appliances protect against wide classes of attacks, covering up to tensof thousands of individual threats witha single signature. In addition to the countermeasures on the appliance, all SonicWall firewalls also have accessto the SonicWall CloudAV service, which extends the onboard signature intelligence with more than 17 million signatures, and growing. This CloudAV database is accessed via a proprietary light-weight protocol by the firewall to augment the inspection done on the appliance. With Geo-IP and botnet filtering capabilities, SonicWall next-generation firewalls are able to block traffic from dangerous domains or entire geographies in order to reduce the riskprofile of the network. Application intelligenceand controlApplication intelligence informs administrators of application traffic traversing the network, so they can schedule application controls based on business priority, throttle unproductive applications and block potentially dangerous applications. Real-time visualization identifies traffic anomalies as they happen, enabling immediate countermeasures against potential inbound or outbound attacks or performance bottlenecks. SonicWall application traffic analytics providegranular insight into applicationtraffic, bandwidth utilization andsecurity threats, as well as powerfultroubleshooting and forensicscapabilities. Additionally, secure singlesign-on (SSO) capabilities enhance theuser experience, increase productivityand reduce support calls. Managementof application intelligence and controlis simplified by using an intuitive web-based interface.Flexible and secure wirelessAvailable as an optional feature, high-speed 802.11ac wireless* combineswith SonicWall next-generationfirewall technology to create a wirelessnetwork security solution that deliverscomprehensive protection for wired andwireless networks.This enterprise-level wirelessperformance enables WiFi-ready devicesto connect from greater distancesand use bandwidth-intensive mobileapps, such as video and voice, inhigher density environments withoutexperiencing signal degradation.* 802.11ac currently not available on SOHO models; SOHO models support 802.11a/b/g/nFeaturesSonicOS feature summaryFirewall• Stateful packet inspection• Reassembly-Free Deep PacketInspection• DDoS attack protection(UDP/ICMP/SYN flood)• IPv4/IPv6 support• Biometric authentication for remote access• DNS proxy• Threat APISSL/SSH decryption and inspection1• Deep packet inspection for TLS/SSL/SSH • Inclusion/exclusion of objects, groups or hostnames• SSL controlCapture Advanced Threat Protection1• Cloud-based multi-engine analysis• Virtualized sandboxing• Hypervisor level analysis• Full system emulation• Broad file type examination• Automated & manual submission• Real-time threat intelligence updates • Auto-Block capabilityIntrusion prevention1• Signature-based scanning• Automatic signature updates• Bidirectional inspection engine• Granular IPS rule capability• GeoIP/Botnet filtering2• Regular expression matchingAnti-malware1• Stream-based malware scanning• Gateway anti-virus• Gateway anti-spyware• Bi-directional inspection• No file size limitation• Cloud malware database Application identification1• Application control• Application visualization2• Application component blocking• Application bandwidth management• Custom application signature creation• Data leakage prevention• Application reporting over NetFlow/IPFIX• User activity tracking (SSO)• Comprehensive application signaturedatabaseWeb content filtering1• URL filtering• Anti-proxy technology• Keyword blocking• Bandwidth manage CFS ratingcategories• Unified policy model with app control• Content Filtering ClientVPN• Auto-provision VPN• IPSec VPN for site-to-site connectivity• SSL VPN and IPSec client remote access• Redundant VPN gateway• Mobile Connect for iOS, Mac OS X,Windows, Chrome, Android and KindleFire• Route-based VPN (OSPF, RIP)Networking• PortShield• Enhanced logging• Layer-2 QoS• Port security• Dynamic routing• SonicPoint wireless controller• Policy-based routing• Asymmetric routing• DHCP server• NAT• Bandwidth management• High availability - Active/Standby withstate sync3• Inbound/outbound load balancing• L2 bridge mode, NAT mode• 3G/4G WAN failover• Common Access Card (CAC) supportVoIP• Granular QoS control• Bandwidth management• DPI for VoIP traffic• H.323 gatekeeper and SIP proxy supportManagement and monitoring• Web GUI• Command line interface (CLI)• SNMPv2/v3• Centralized management and reportingwith SonicWall GMS• Logging• Netflow/IPFix exporting• Single Sign-On (SSO)• Terminal service/Citrix support• Application and bandwidth visualization• IPv4 and IPv6 management• Dell X-Series switch managementIPv6• IPv6 filtering• 6rd (rapid deployment)• DHCP prefix delegation• BGPWireless• Dual-band (2.4 GHz and 5.0 GHz)• 802.11 a/b/g/n/ac wireless standards2• Wireless intrusion detection andprevention• Wireless guest services• Lightweight hotspot messaging• Virtual access point segmentation• Captive portal• Cloud ACLRequires added subscriptionNot available on SOHO seriesState sync high availability only on SonicWall TZ500 and SonicWall TZ600 modelsSonicWall TZ series system specifications*Future use.Testing Methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services. Full DPI/GatewayAV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs.VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. All specifications, features and availability are subject to change. BGP is available only on SonicWall TZ400, TZ500 and TZ600.All TZ integrated wireless models can support either 2.4GHz or 5GHz band. For dual-band support, please use SonicWall's wireless access points products (SonicPoints)SonicWall TZ Series ordering information© 2017 SonicWall Inc. ALL RIGHTS RESERVED. SonicWall is atrademark or registered trademark of SonicWall Inc. and/or its affiliates SonicWall, Inc.5455 Great America Parkway | Santa Clara, CA 95054 About UsSonicWall has been fighting the cyber-criminal industry for over 25 years, defending small, medium size businesses and enterprises worldwide. Our combination of products and partners has enabled a real-time cyber defense solution tuned to the specific needs ofthe more than 500,000 global businesses in over 150 countries, so you can do more business with less fear.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
DPtech UTM2000系列统一威胁管理安装手册杭州迪普科技有限公司为客户提供全方位的技术支持。
通过杭州迪普科技有限公司代理商购买产品的用户,请直接与销售代理商联系;直接向杭州迪普科技有限公司购买产品的用户,可直接与公司联系。
杭州迪普科技有限公司地址:杭州市滨江区通和路68号中财大厦6层邮编:310052声明Copyright2009杭州迪普科技有限公司版权所有,保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本书内容的部分或全部,并不得以任何形式传播。
由于产品版本升级或其他原因,本手册内容有可能变更。
杭州迪普科技有限公司保留在没有任何通知或者提示的情况下对本手册的内容进行修改的权利。
本手册仅作为使用指导,杭州迪普科技有限公司尽全力在本手册中提供准确的信息,但是杭州迪普科技有限公司并不确保手册内容完全没有错误,本手册中的所有陈述、信息和建议也不构成任何明示或暗示的担保。
目录第1章产品介绍1-11.1产品概述1-1 1.2产品型号及规格介绍1-1 1.3前后面板介绍1-3 1.3.1UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N产品外观1-3 1.3.2UTM2000-GS-N/UTM2000-GM-N产品外观1-5 1.3.3UTM2000-CA-N产品外观1-7 1.3.4UTM2000-GA-N产品外观1-9 1.3.5UTM2000-GE-N/UTM2000-TS-N产品外观1-11 1.4端口介绍1-14 1.4.1C ONSOLE口1-14 1.4.210/100/1000B ASE-T以太网电接口1-14 1.4.3SFP口1-16 1.5产品组件1-18 1.5.1处理器及存储器1-18 1.5.2各类接口1-18第2章安装前的准备2-222.1通用安全注意事项2-22 2.2检查安装场所2-22 2.2.1温度/湿度要求2-22 2.2.2洁净度要求2-23 2.2.3防静电要求2-23 2.2.4抗干扰要求2-24 2.2.5防雷击要求2-24 2.2.6接地要求2-24 2.2.7布线要求2-24 2.3安装工具2-25第3章设备安装3-13.1安装前的确认3.2安装流程3-2 3.3安装设备到指定位置3-2 3.3.2安装设备到工作台3-3 3.3.3安装设备到19英寸机柜3-4 3.4连接接地线3-5 3.5连接接口线缆3-6 3.5.1连接配置口线缆3-6 3.5.2连接网络管理口3-7 3.5.3连接业务口3-7 3.6连接电源线3-7 3.7安装后检查3-7第4章设备启动及软件升级4-14.1设备启动4-1 4.1.1搭建配置环境4-1 4.1.2设备上电4-4 4.1.3启动过程4-5 4.2W EB默认登录方式4-6第5章常见问题处理5-15.1电源系统问题故障处理5-1 5.2设备故障处理5-1图形目录图1-1UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N前视图1-3图1-2UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N前面板指示灯1-4图1-3UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N后视图1-5图1-4UTM2000-GS-N/UTM2000-GM-N前视图1-5图1-5UTM2000-GS-N/UTM2000-GM-N前面板指示灯1-6图1-6UTM2000-GS-N/UTM2000-GM-N后视图1-7图1-7UTM2000-CA-N前视图1-7图1-8UTM2000-CA-N前面板指示灯1-8图1-9UTM2000-CA-N后视图1-8图1-10UTM2000-GA-N前视图1-9图1-11UTM2000-GA-N前面板指示灯1-11图1-12UTM2000-GA-N后视图1-11图1-13UTM2000-GE-N/UTM2000-TS-N前视图1-12图1-14UTM2000-GE-N/UTM2000-TS-N前面板指示灯1-13图1-15UTM2000-GE-N/UTM2000-TS-N后视图1-14图1-16RJ45水晶头外观1-15图1-17以太网电缆的示意图1-15图1-18LC型连接器外观1-17图1-19SC型连接器外观1-17图1-20光模块示意图1-18图1-21UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N以太网接口1-19图1-22UTM2000-GS-N/UTM2000-GM-N以太网接口1-19图1-23UTM2000-CA-N以太网接口1-20图1-24UTM2000-GA-N以太网接口1-20图1-25UTM2000-GE-N/UTM2000-TS-N以太网接口1-21图3-1设备安装流程3-2图3-2安装设备于工作台3-4图3-3安装挂耳3-4图3-4安装设备到机柜(为清晰起见省略了机柜)3-4图3-5固定设备3-5图3-6连接接地线示意图3-5图3-7连接保护地线到接地排3-6图4-1通过Console口进行本地配置示意图图4-2超级终端连接描述界面图4-3超级终端连接使用串口设置4-2图4-4串口参数设置4-3图4-5超级终端窗口4-3图4-6终端类型设置4-4图4-7Web网管登录页面4-7表格目录表1-1Console口属性表1-14表1-2千兆以太网电接口属性表:1-14表1-3千兆以太网光接口属性1-16表2-1机房温度/湿度要求2-22表2-2机房灰尘含量要求2-23表2-3机房有害气体限值2-23表4-1设置串接口属性4-2第1章产品介绍1.1产品概述DPtech UTM2000系列统一威胁管理创新性地采用了“多业务并行处理引擎(MPE)”技术,在多功能开启情况下性能不受影响,能够满足防护混合威胁的安全需求。
可以提供防火墙、VPN、漏洞防护、防病毒、防垃圾邮件、URL过滤和行为审计等功能,是综合安全业务保障的最佳选择。
UTM2000具有高密度接口满足多ISP的冗余需求,高扩展性可以降低后续投入成本。
适用于中小型网络出口和数据中心。
1.2产品型号及规格介绍DPtech UTM2000统一威胁管理目前包含机型如下:l UTM2000-MA-N UTM2000-ME-N UTM2000-MS-N UTM2000-CS-Nl UTM2000-GS-N UTM2000-GM-Nl UTM2000-CA-Nl UTM2000-GA-Nl UTM2000-GE-N UTM2000-TS-N各款机型的规格如下:1.3前后面板介绍1.3.1UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N 产品外观1.前视图(1)10/100/1000M 以太网电接口(2)CONSOLE 配置口(3)系统运行指示灯(RUN)(4)电源指示灯(POWER)(5)插槽指示灯(0)(6)插槽指示灯(1)(7)10/100/1000M 以太网电接口指示灯(8)USB 接口图1-1UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N 前视图图1-2UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N前面板指示灯2.后视图(1)接地标识(2)接地端子(3)交流电源插座图1-3UTM2000-MA-N/UTM2000-ME-N/UTM2000-MS-N/UTM2000-CS-N后视图1.3.2UTM2000-GS-N/UTM2000-GM-N产品外观1.前视图(1)1000M以太网光接口(2)10/100/1000M以太网电接口(3)CONSOLE配置口(4)系统运行指示灯(RUN)(5)电源指示灯(PWR0)(6)电源指示灯(PWR1)(7)插槽指示灯(SLOT)(8)1000M以太网光接口指示灯(9)10/100/1000M以太网电接口指示灯(10)USB接口图1-4UTM2000-GS-N/UTM2000-GM-N前视图图1-5UTM2000-GS-N/UTM2000-GM-N 前面板指示灯2.后视图(1)交流电源插座(2)接地端子图1-6UTM2000-GS-N/UTM2000-GM-N 后视图1.3.3UTM2000-CA-N 产品外观1.前视图(1)10/100/1000M 以太网电接口(0)(2)1000M 以太网光接口(7)(3)1000M 以太网光接口指示灯(8)(4)1000M 以太网光接口指示灯(7)(5)1000M 以太网光接口(8)(6)电源指示灯(PWR)(7)系统运行指示灯(RUN)(8)10/100/1000M 以太网电接口指示灯(0)图1-7UTM2000-CA-N 前视图图1-8UTM2000-CA-N前面板指示灯2.后视图(2)RST按键1~5S复位系统(1)USB接口按键5S以上恢复出厂设置(3)电源插座(4)接地标识(5)接地端子图1-9UTM2000-CA-N后视图1.3.4UTM2000-GA-N产品外观1.前视图(1)10/100/1000M以太网电接口(2)1000M以太网光接口(3)LCD显示屏(4)CONSOLE配置口(5)USB口(6)10/100/1000M以太网电接口(0/0)(7)10/100/1000M以太网电接口(0/1)(8)10/100/1000M以太网电接口指示灯(9)1000M以太网光接口指示灯(10)系统运行指示灯(RUN)(11)系统告警指示灯(ALM)(12)电源指示灯(PWR)(13)10/100/1000M以太网电接口指示灯(0/0)(14)10/100/1000M以太网电接口指示灯(0/1)图1-10UTM2000-GA-N前视图图1-11UTM2000-GA-N前面板指示灯2.后视图(1)交流电源插座(2)接地端子图1-12UTM2000-GA-N 后视图1.3.5UTM2000-GE-N/UTM2000-TS-N 产品外观1.前视图(1)10/100/1000M 以太网电接口(2)1000M 以太网光接口(3)LCD 显示屏(4)CONSOLE 配置口(5)10/100/1000M 以太网电接口(6)10/100/1000M 以太网电接口指示灯(7)1000M 以太网光接口指示灯(8)10000M 以太网光接口(9)10000M 以太网光接口指示灯(10)系统运行指示灯(RUN)(11)系统告警指示灯(ALM)(12)电源指示灯(PWR0)(13)电源指示灯(PWR1)(14)USB 接口(15)10/100/1000M 以太网电接口指示灯图1-13UTM2000-GE-N/UTM2000-TS-N 前视图图1-14UTM2000-GE-N/UTM2000-TS-N前面板指示灯2.后视图(1)交流电源插座(1)(2)交流电源插座(2)(3)接地端子图1-15UTM2000-GE-N/UTM2000-TS-N后视图1.4端口介绍1.4.1Console口UTM2000系列前面板均有一个RS232异步串行配置口(CON),可用来连接终端计算机,以进行系统的调试、配置、维护、管理和主机软件程序加载等工作。
